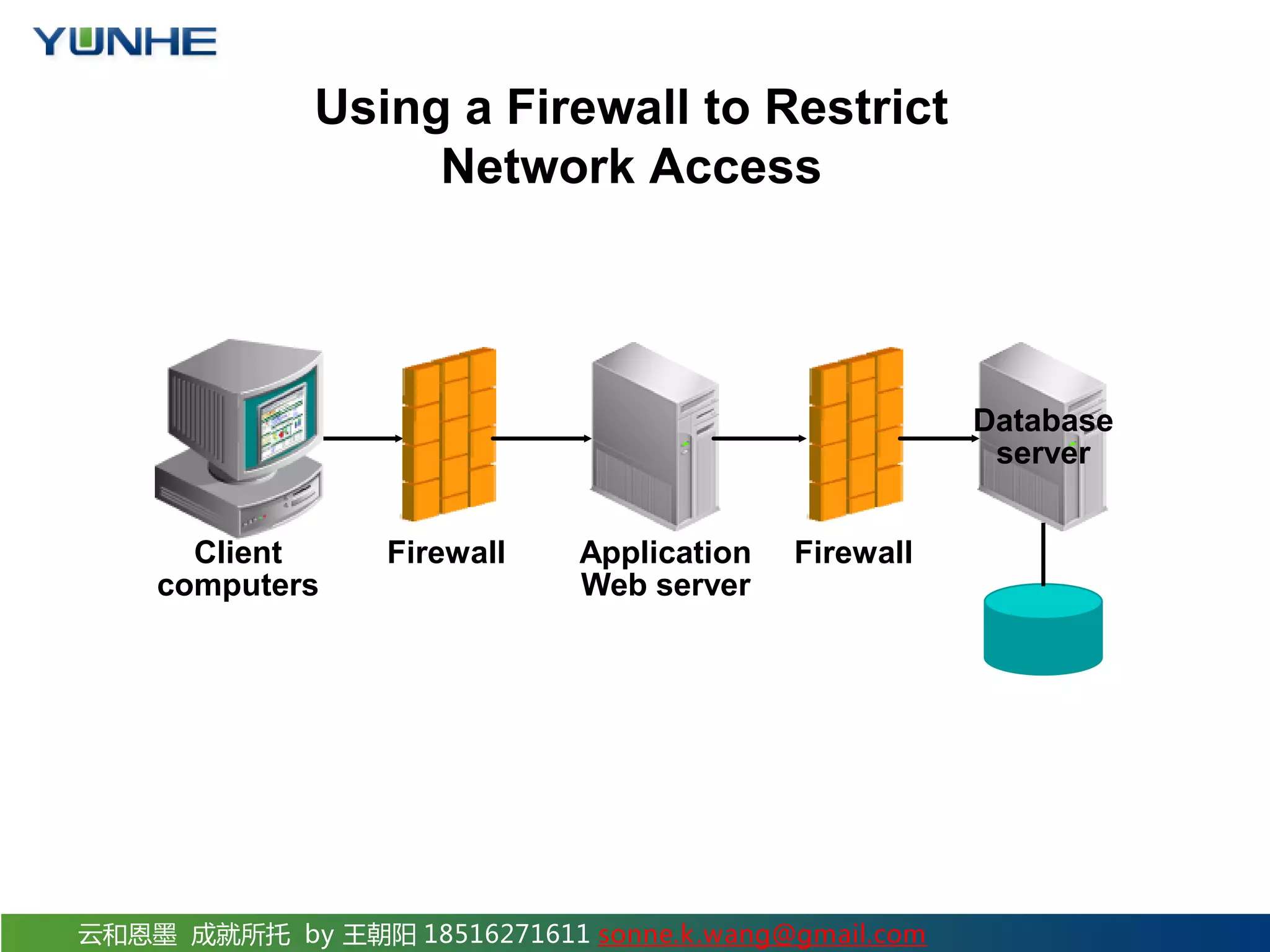
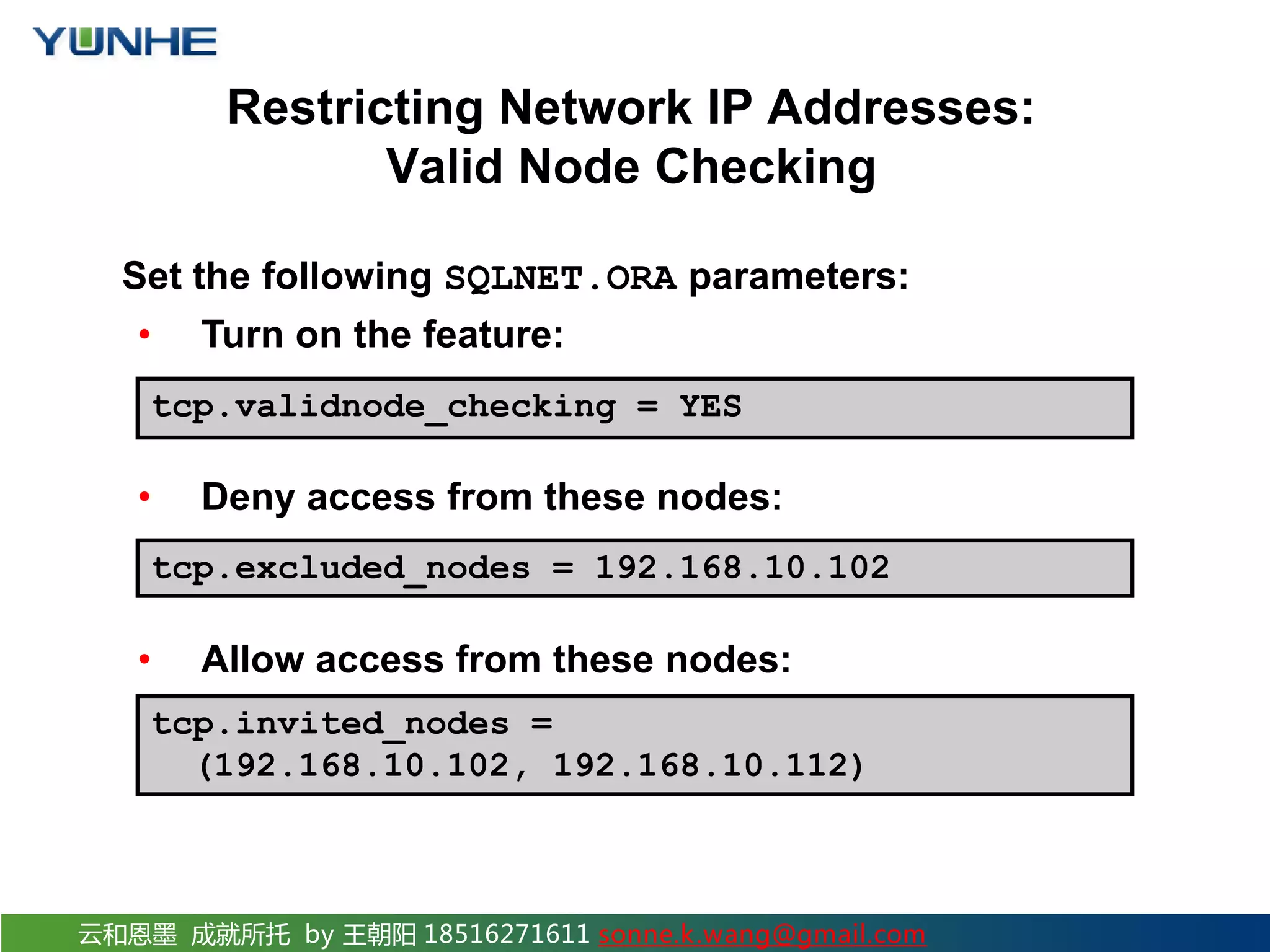
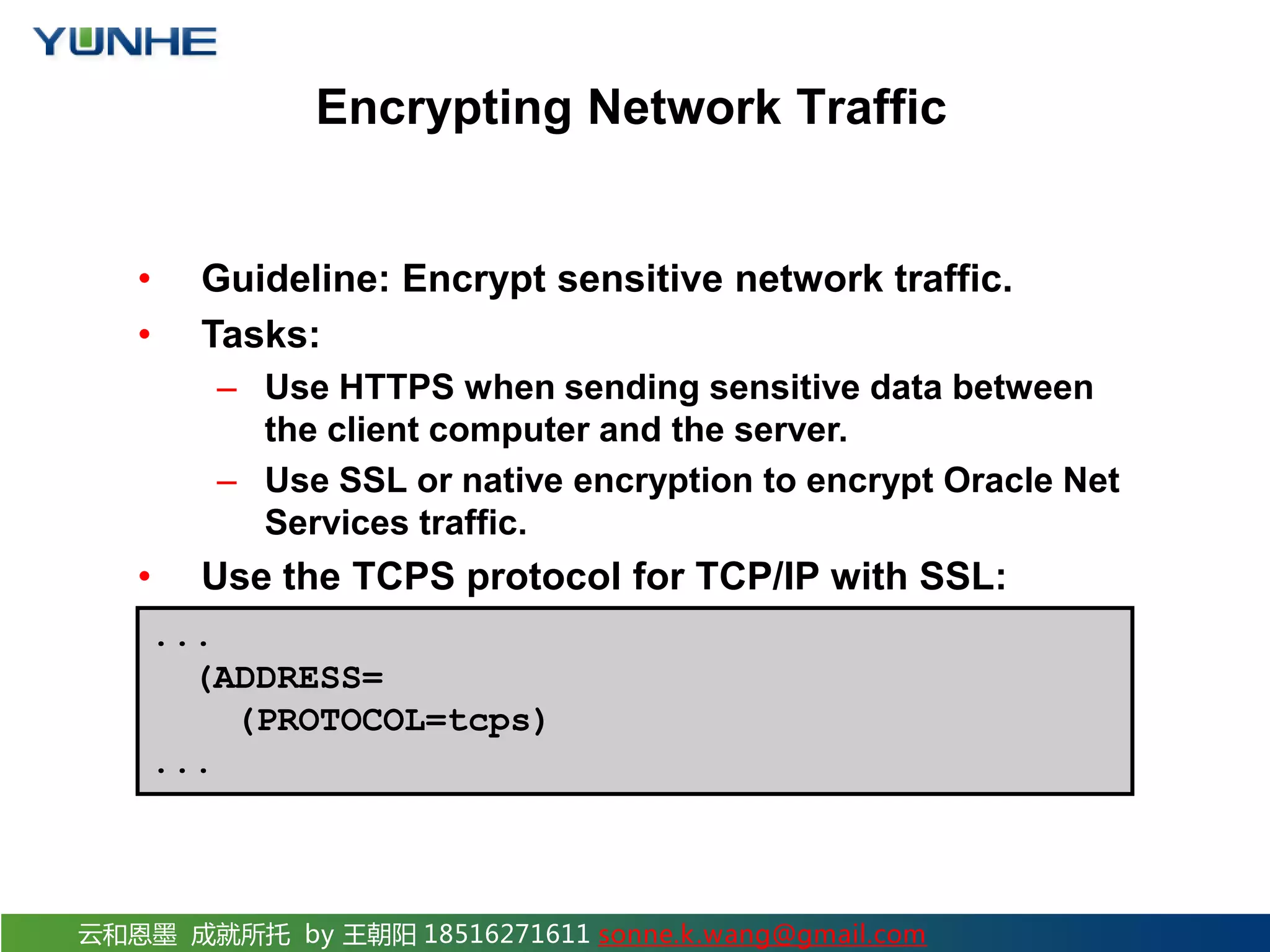
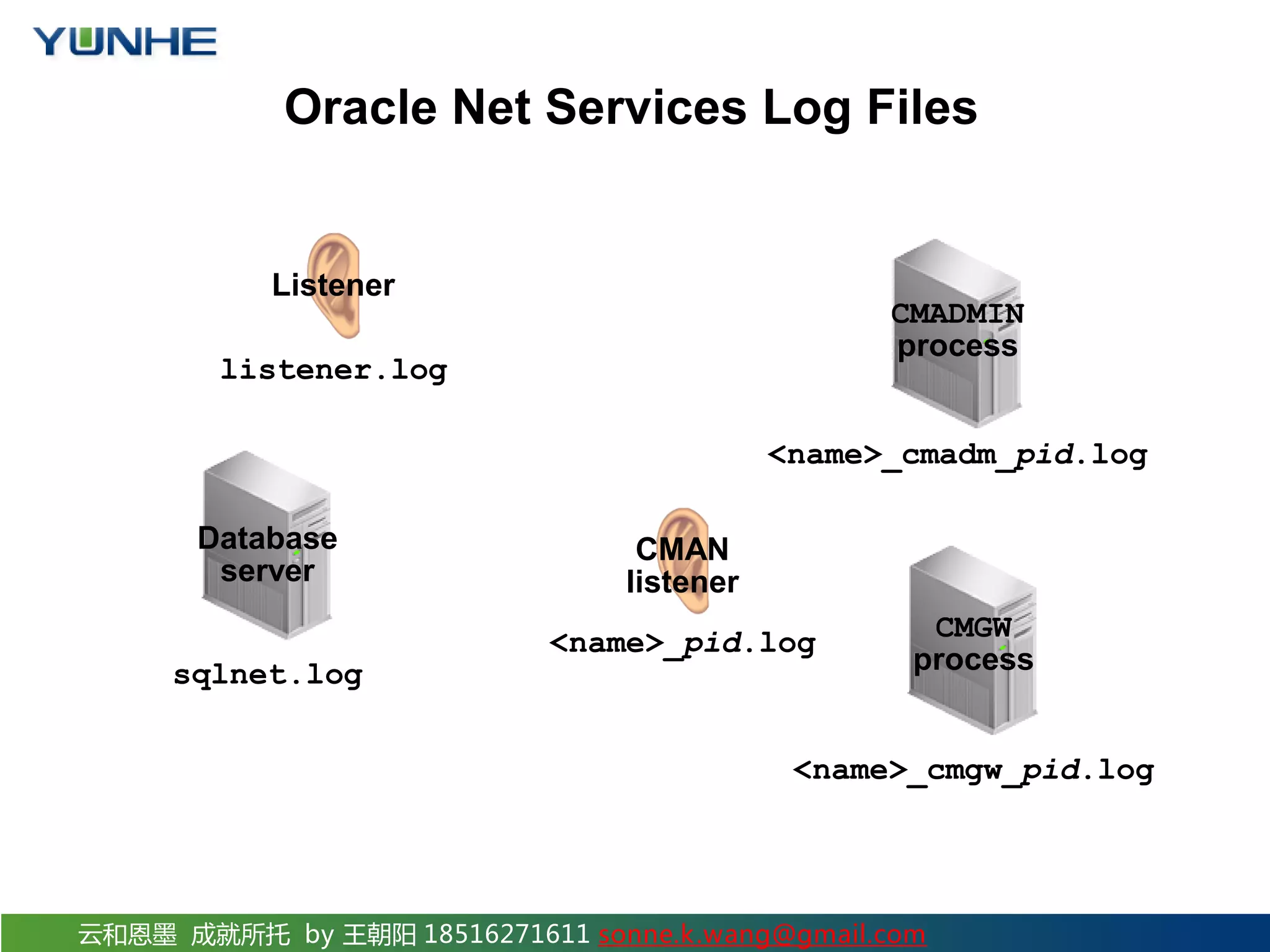
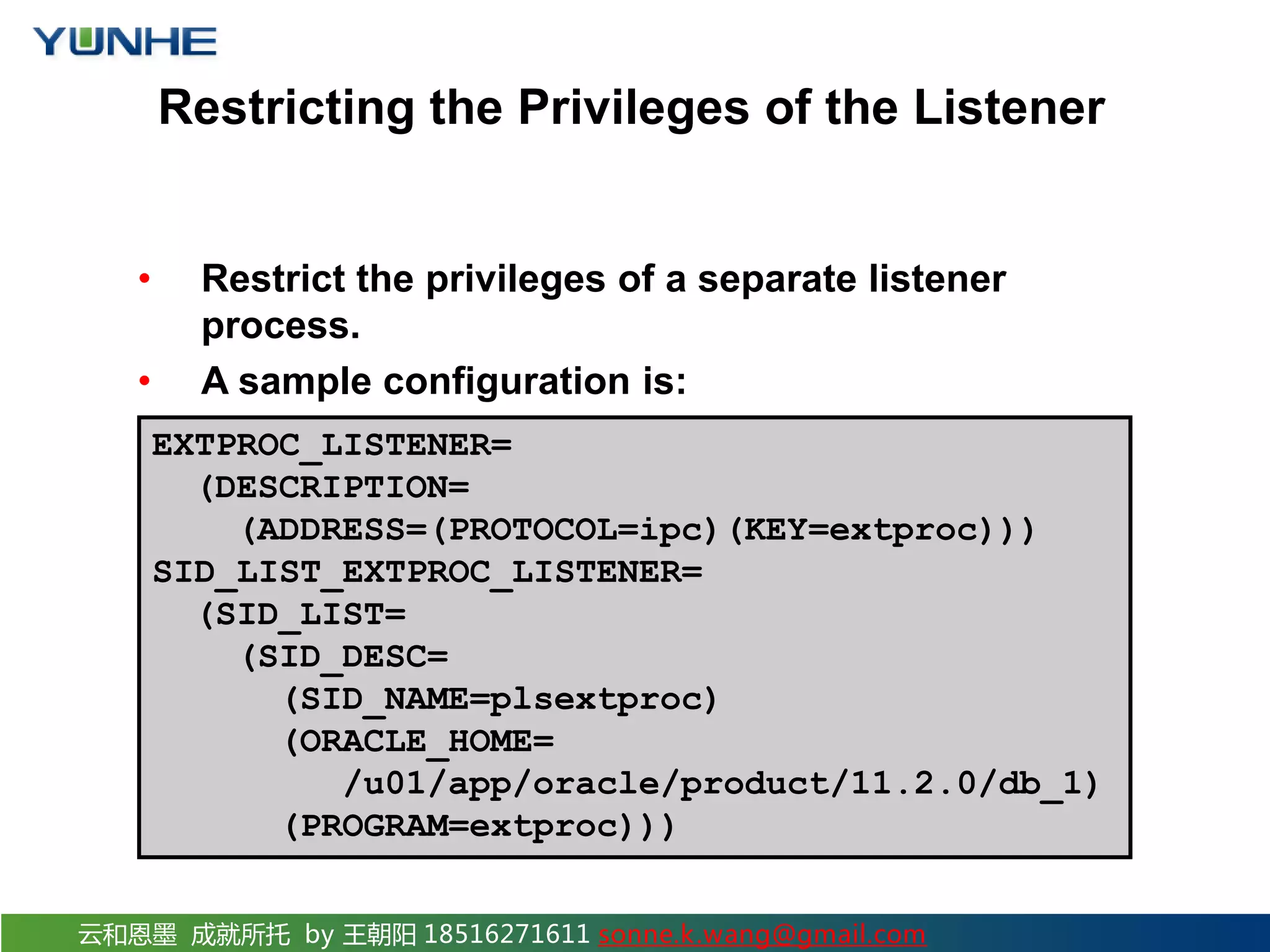
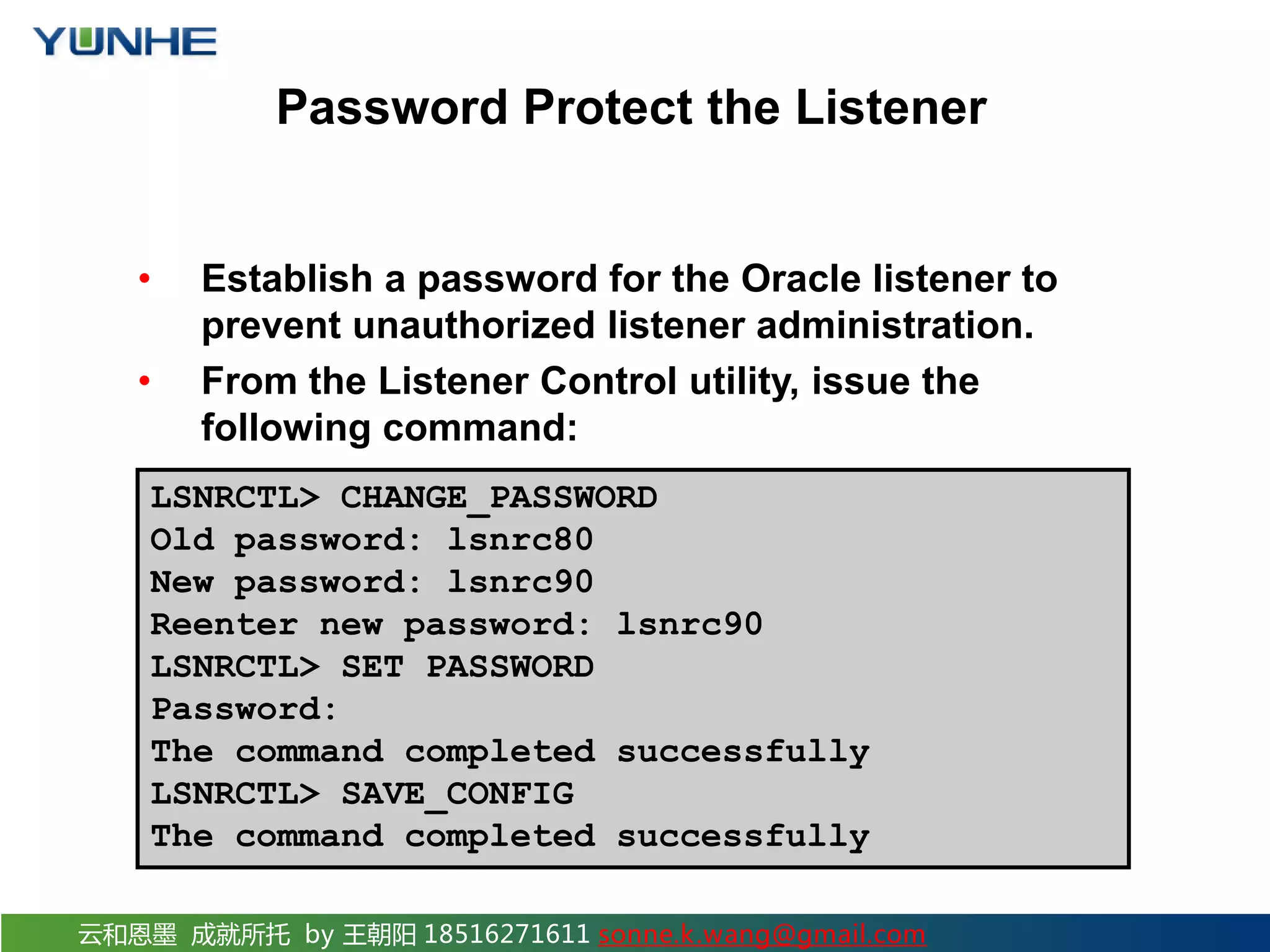
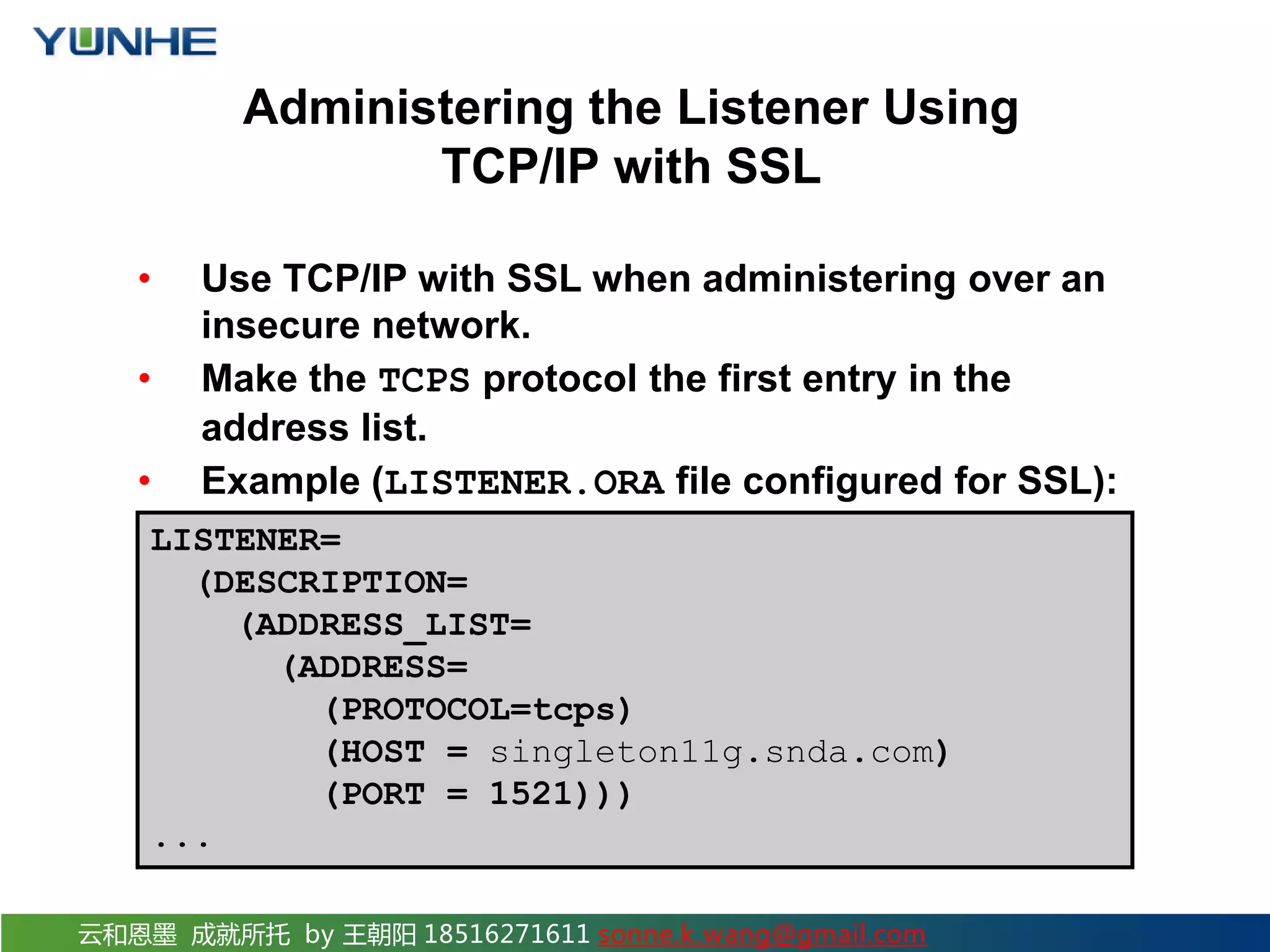
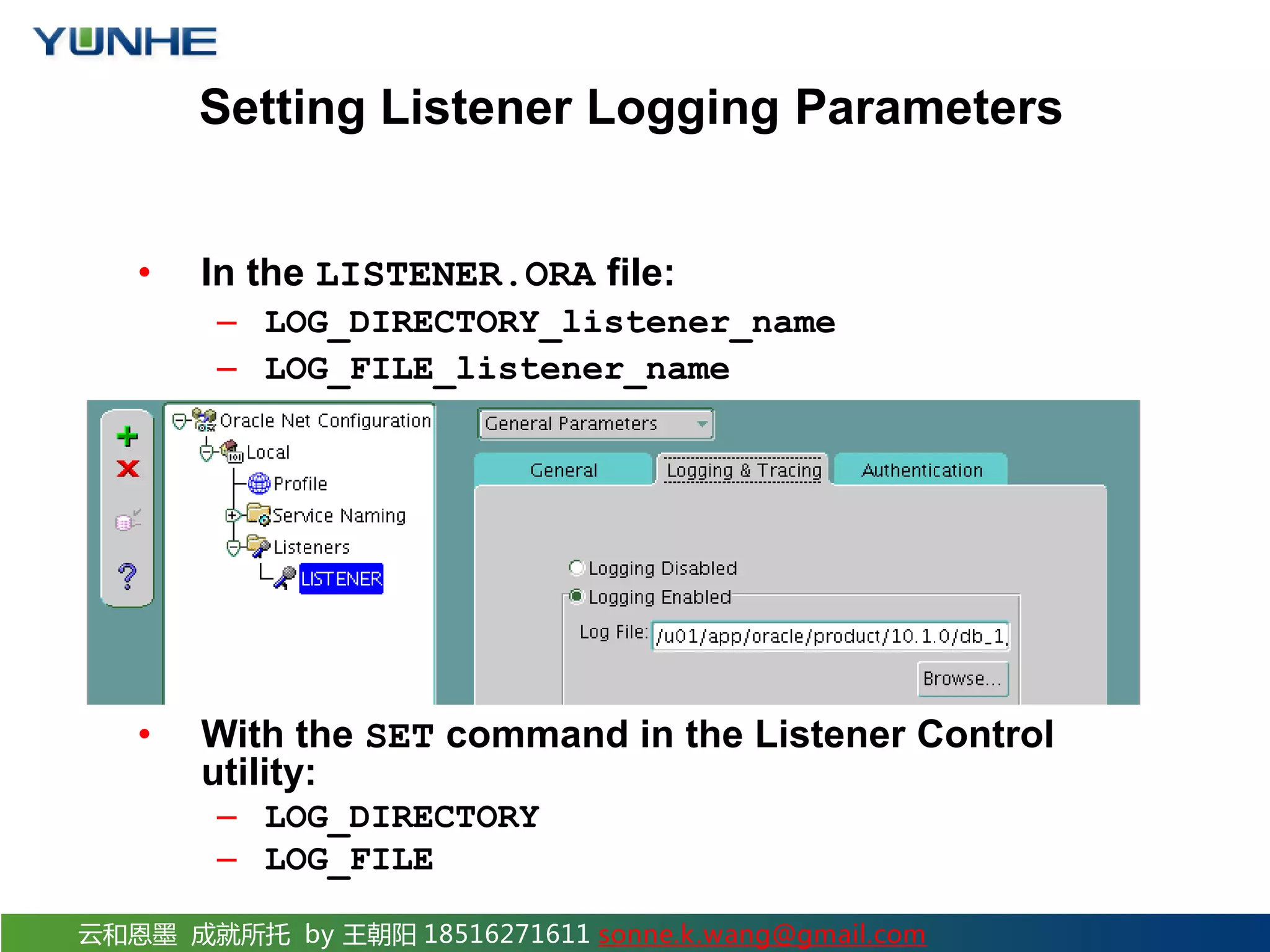
The document discusses securing Oracle Network services. It provides checklists and procedures for securing clients, the network, and the listener. It recommends configuring clients and browsers with authentication and encryption. It also recommends restricting network access through firewalls and IP address validation. For the listener, it suggests restricting privileges, password protecting administration, and monitoring logs to analyze activity and potential attacks. The goal is to describe how to securely administer the network and listener to restrict access and analyze logs for security.