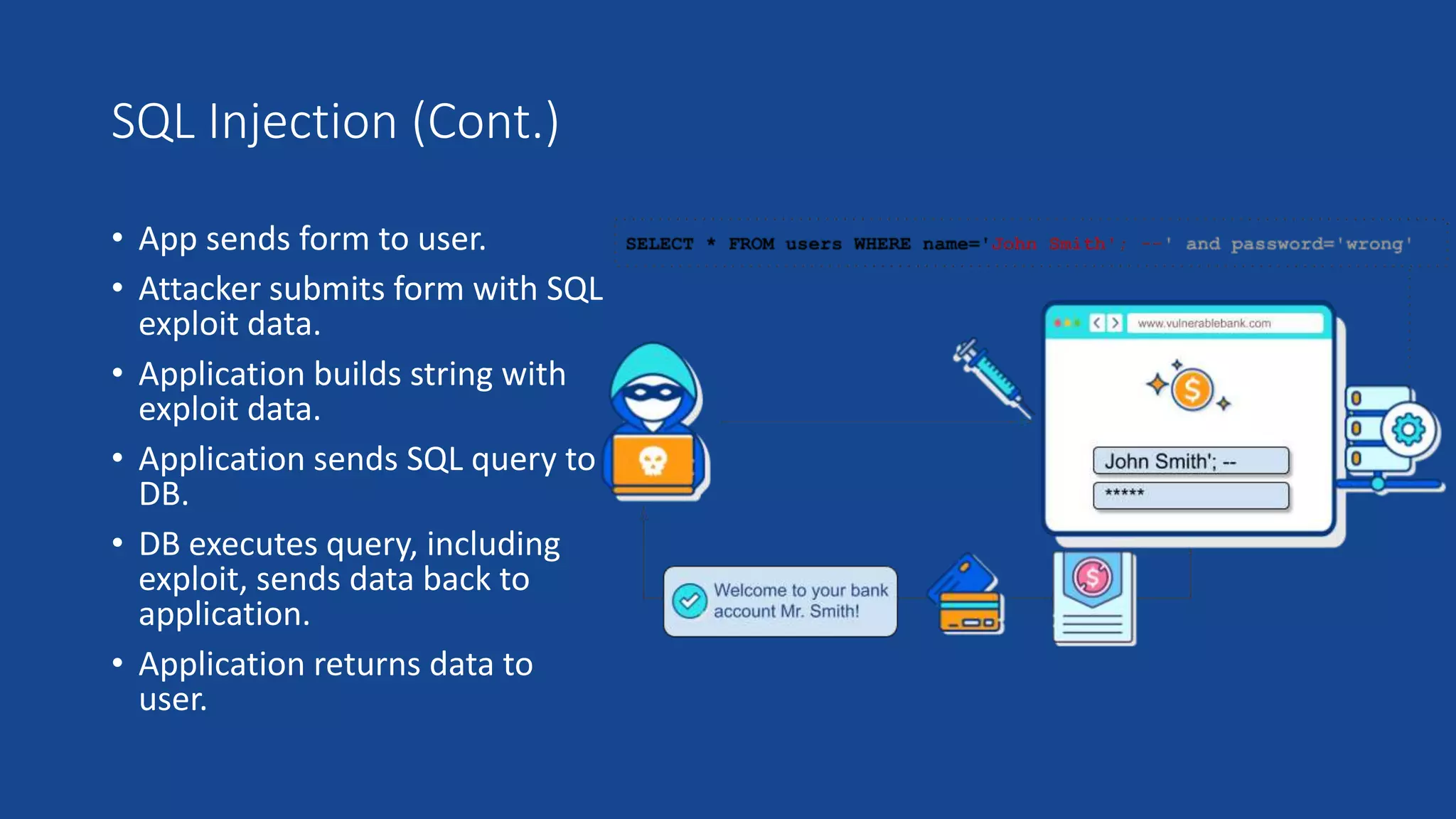
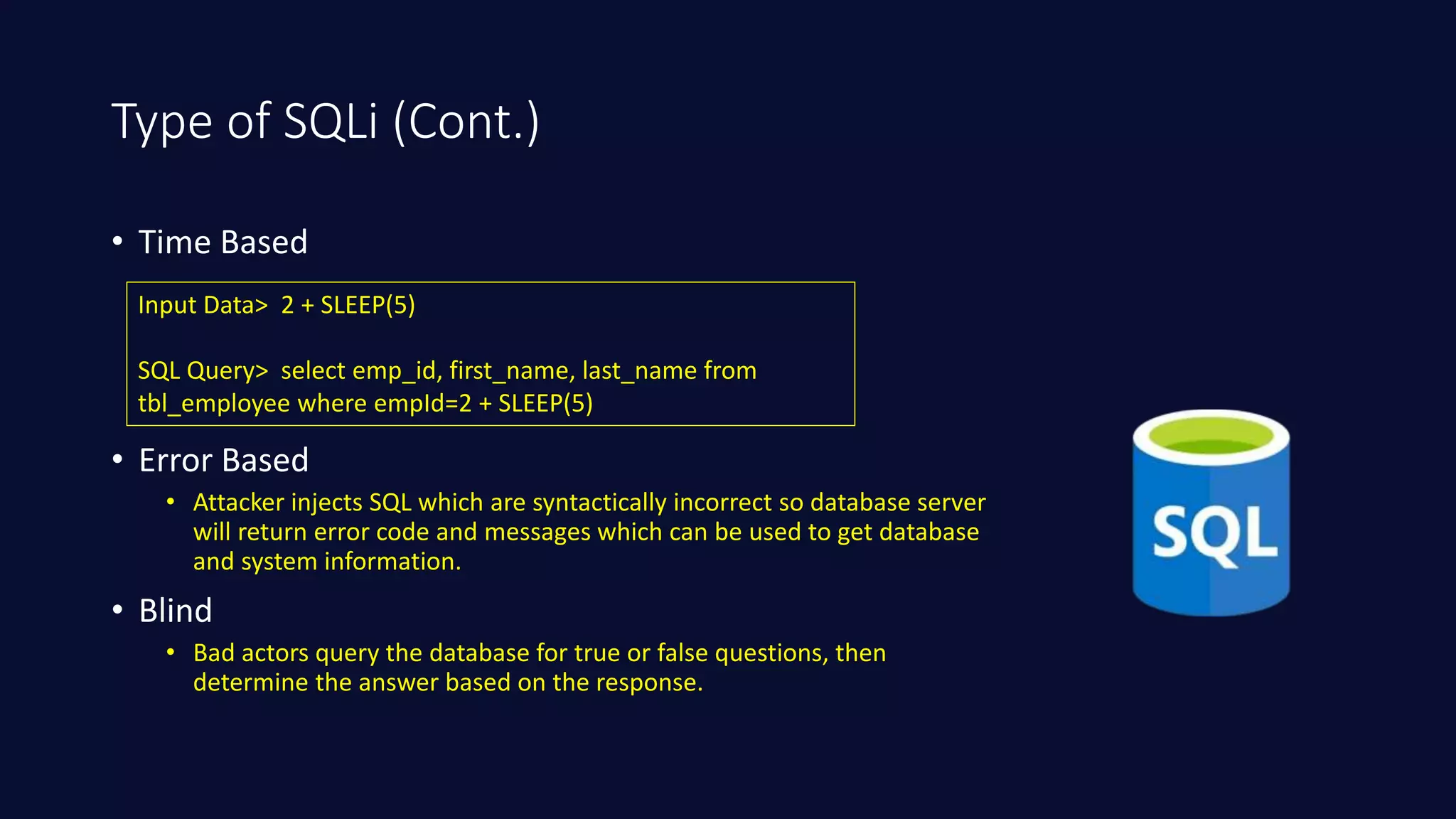
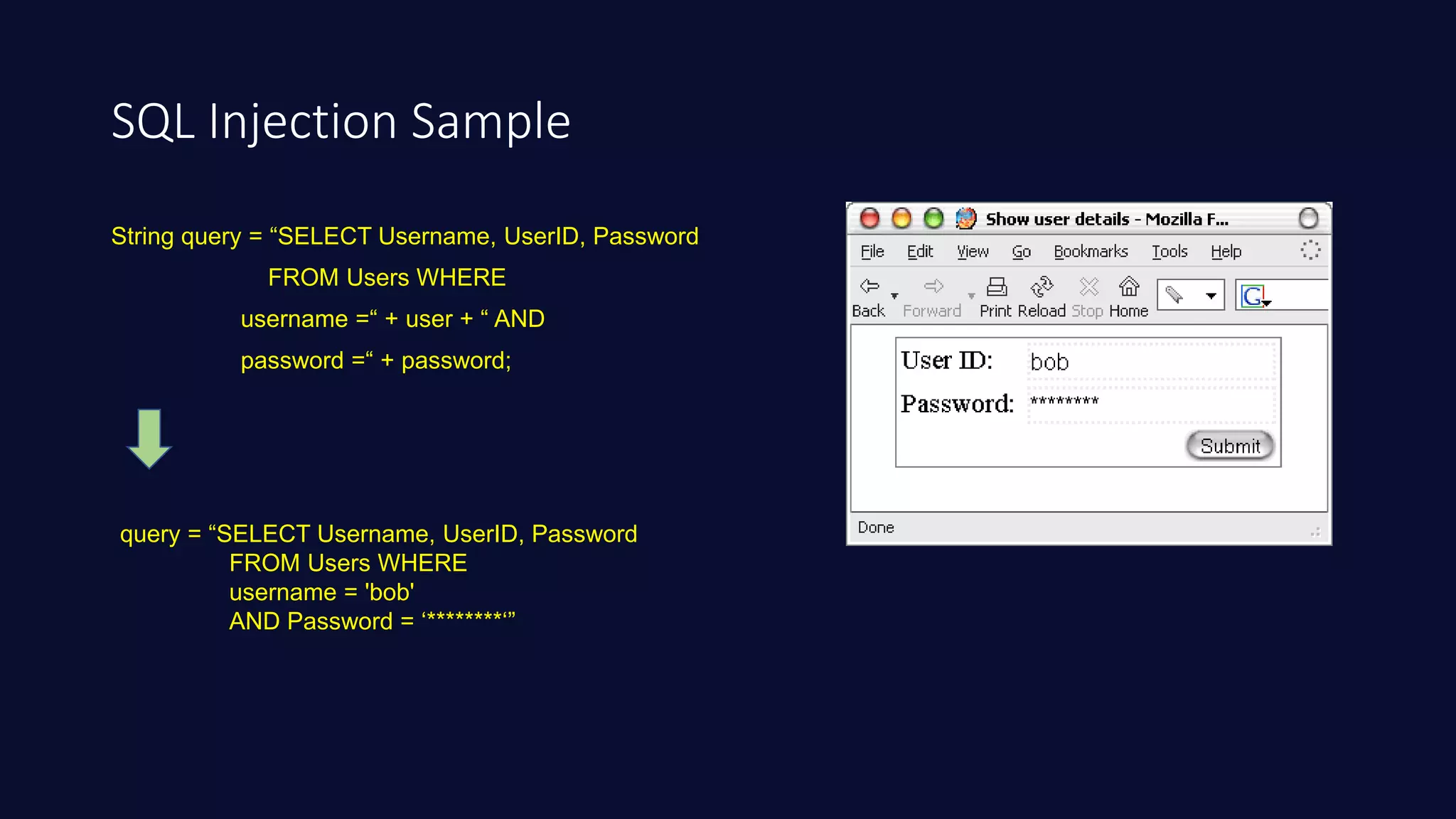
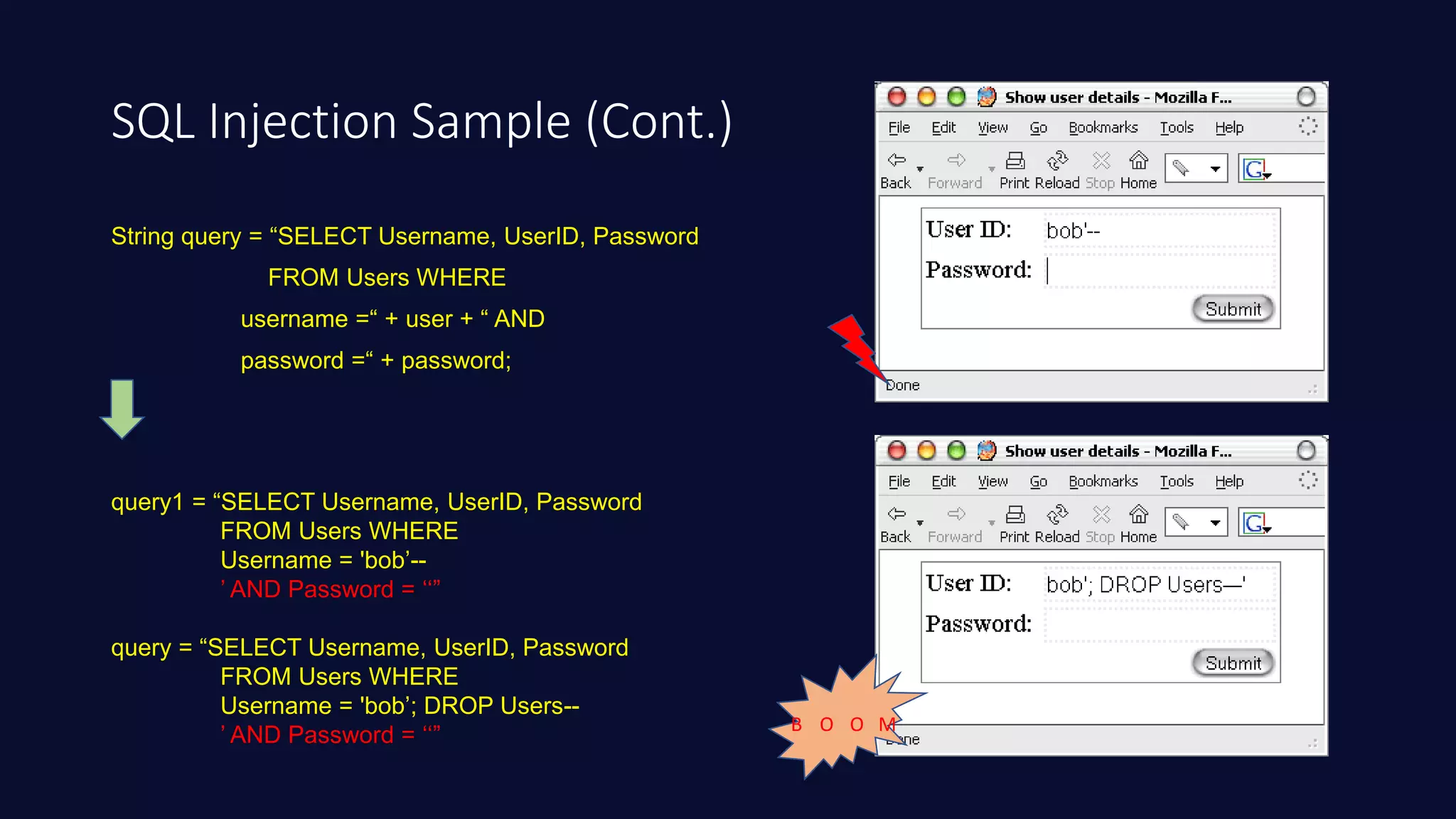
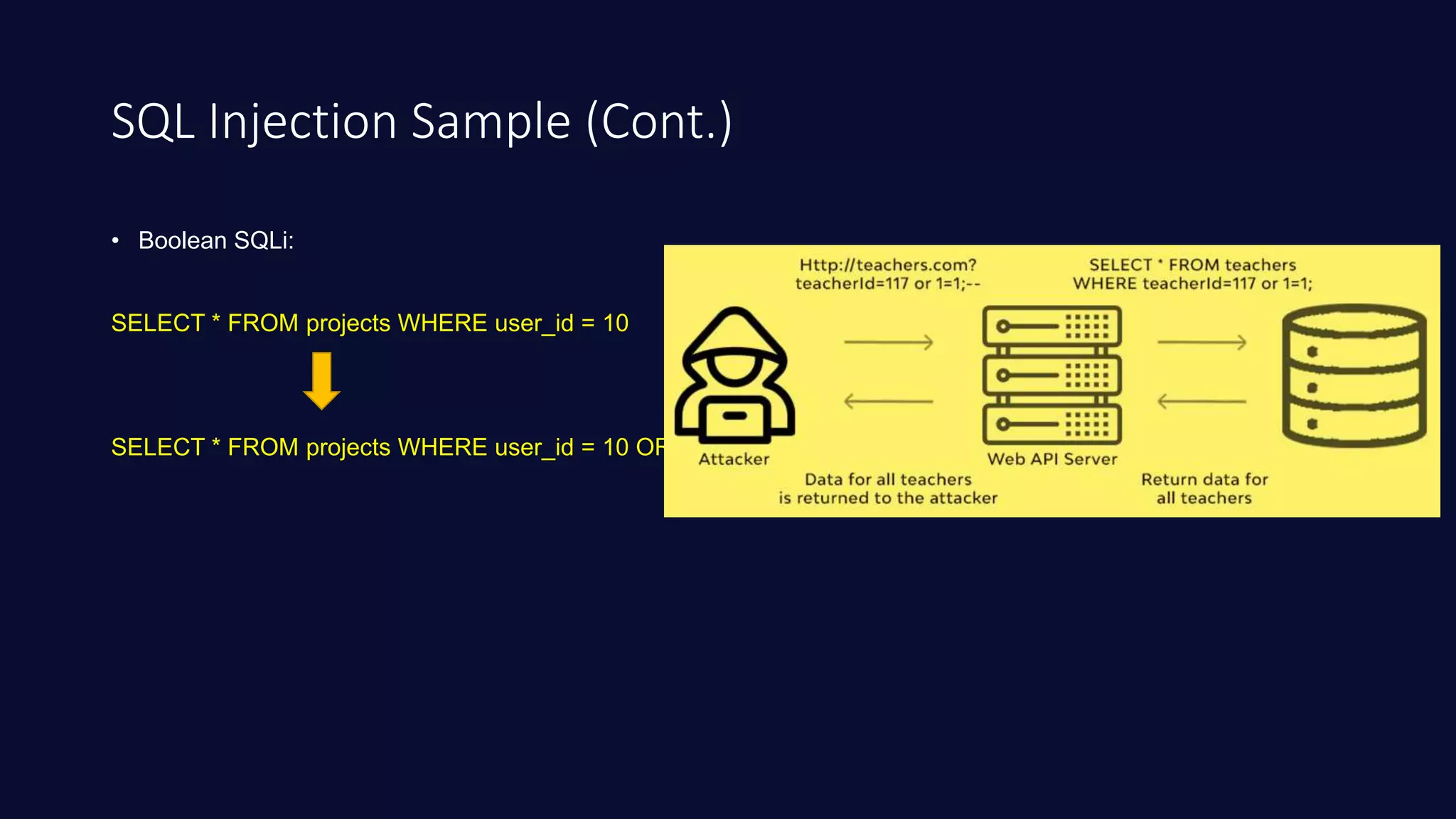
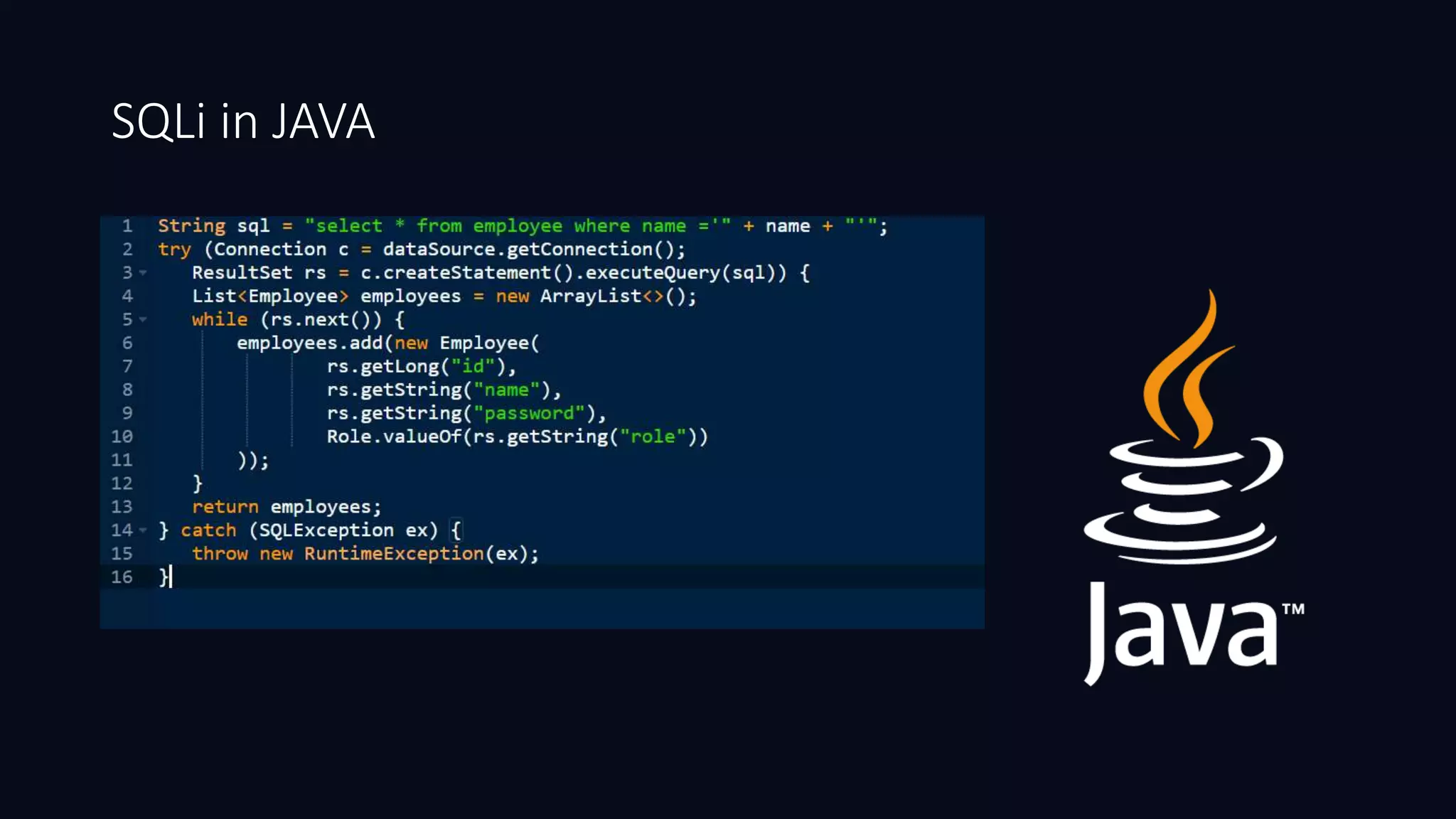
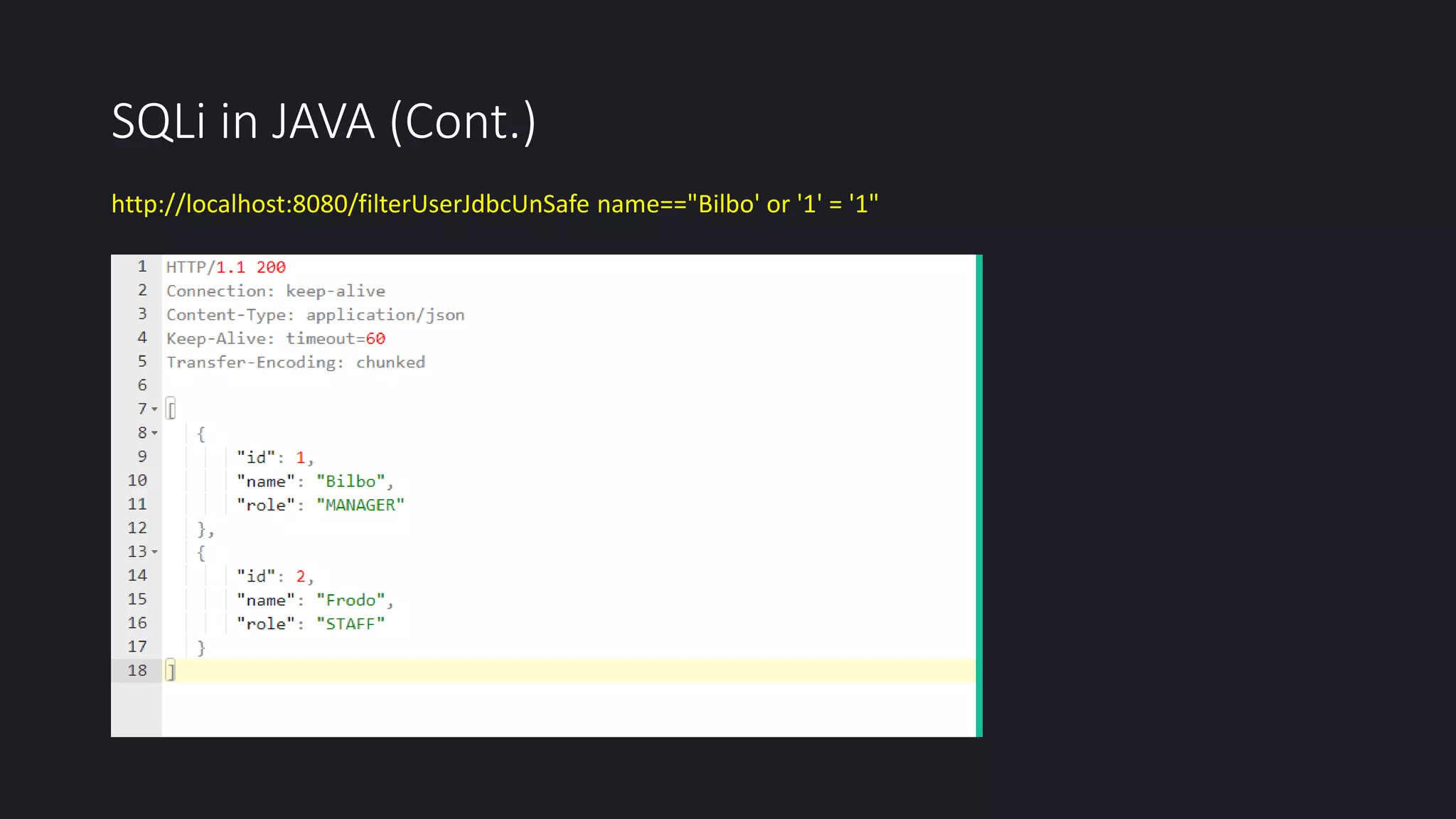
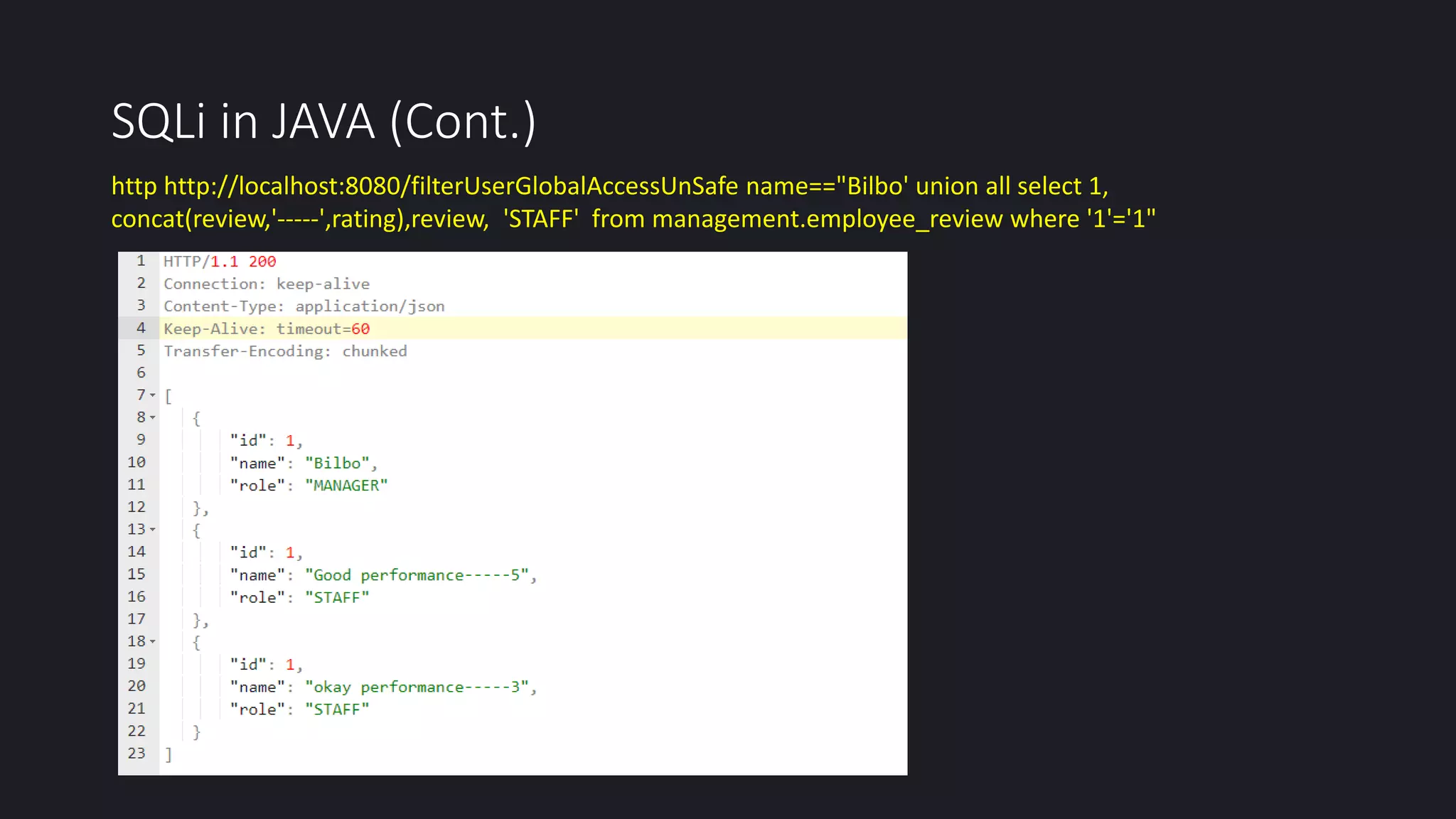
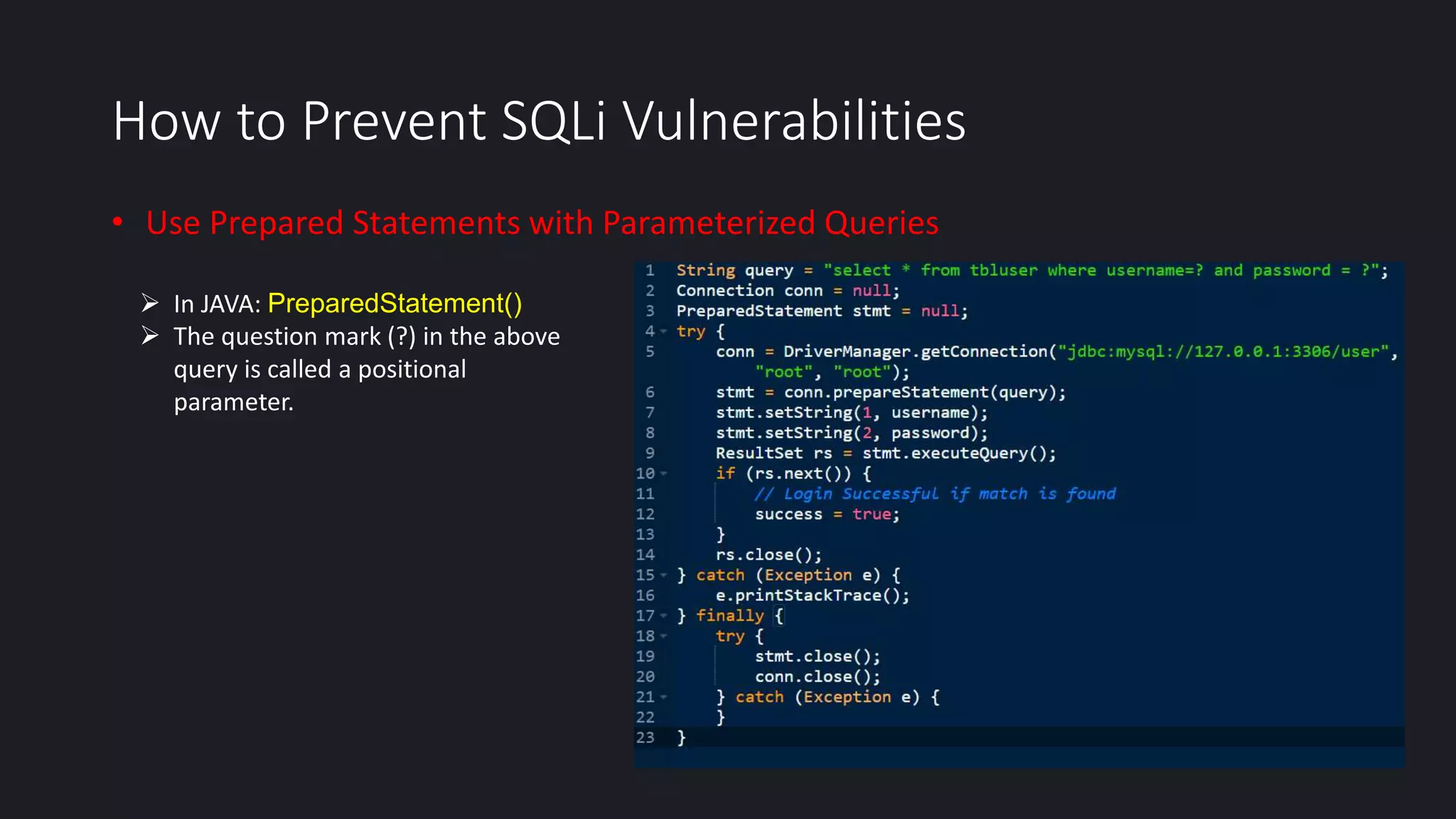
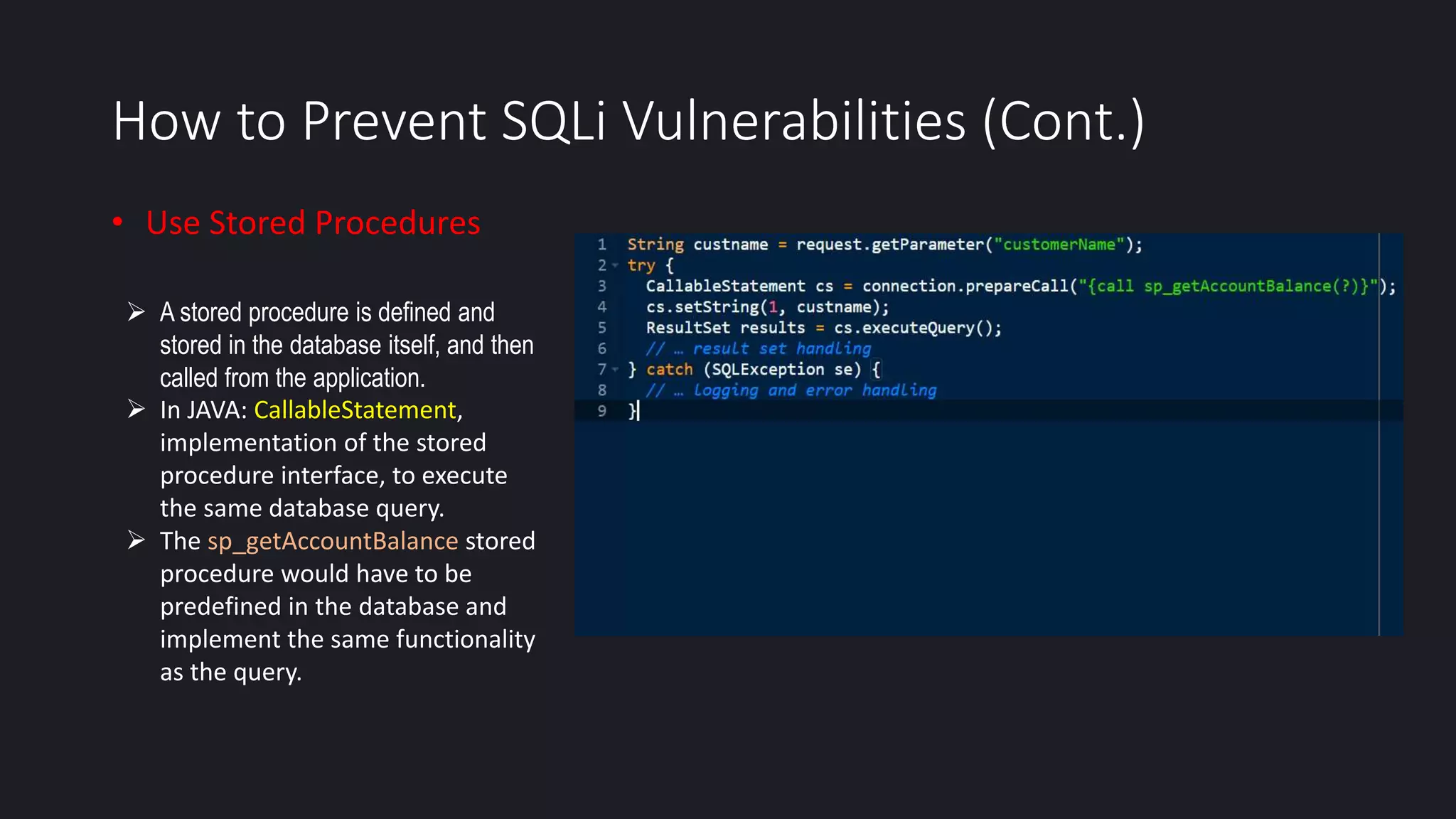
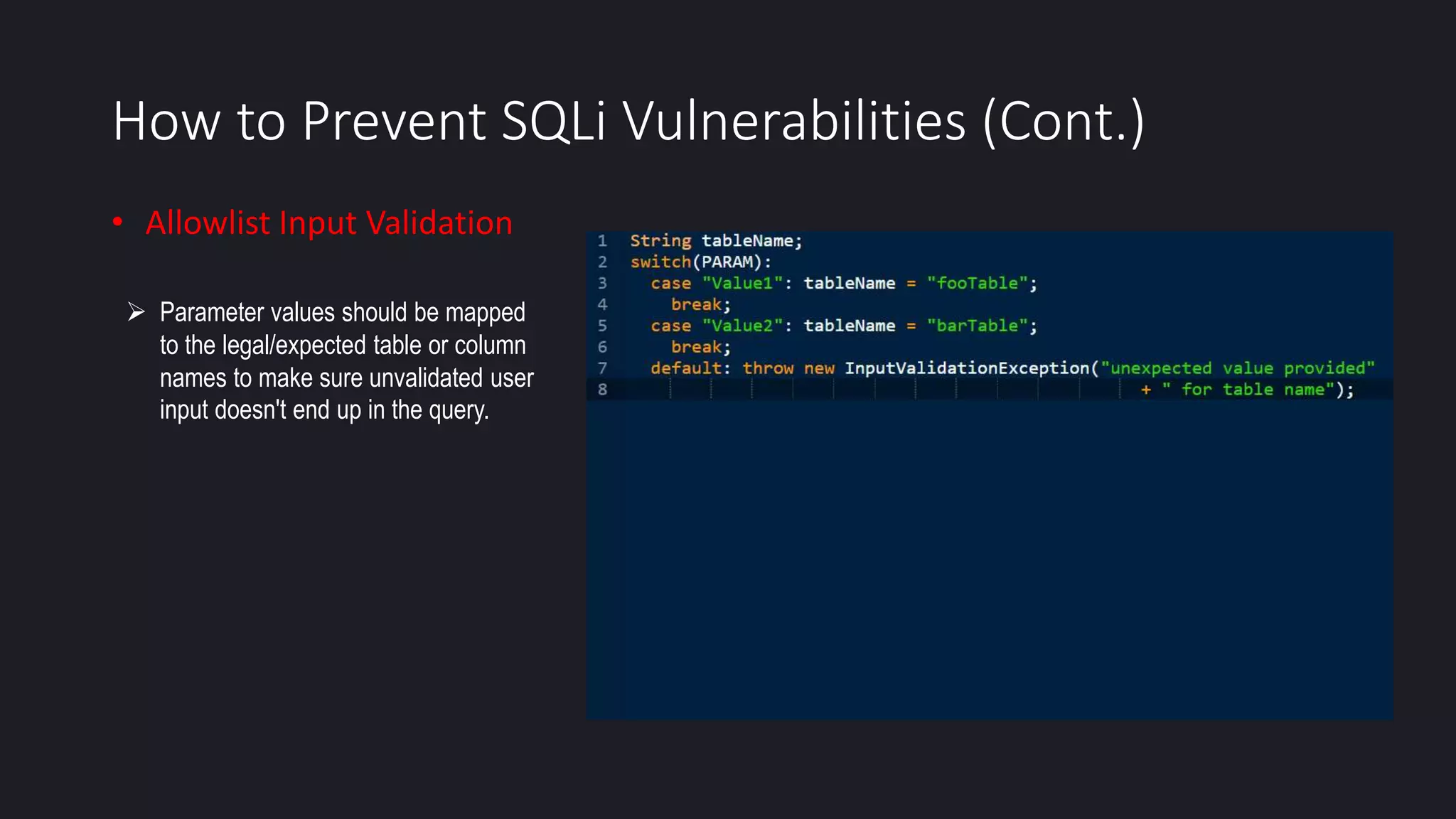
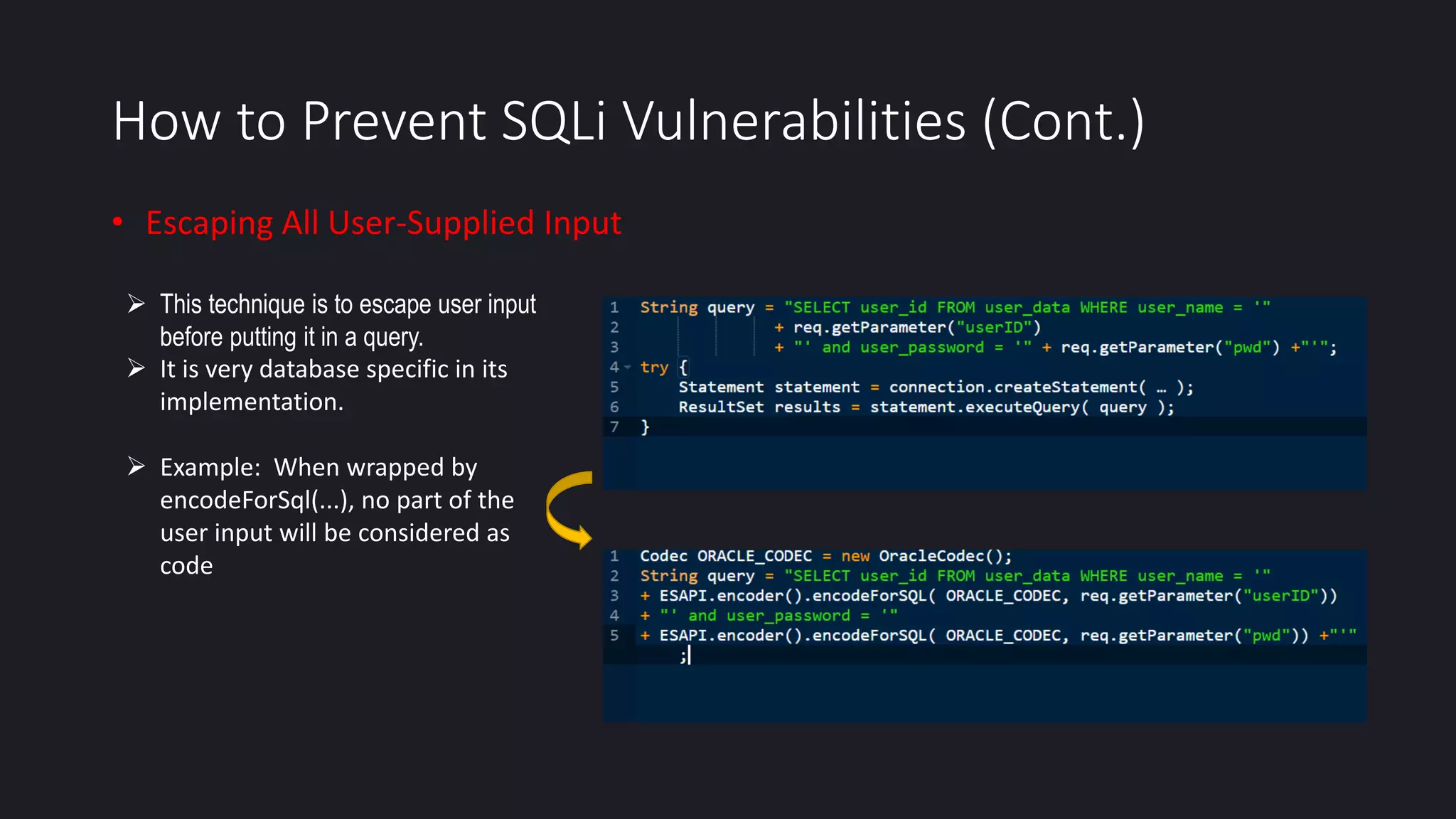
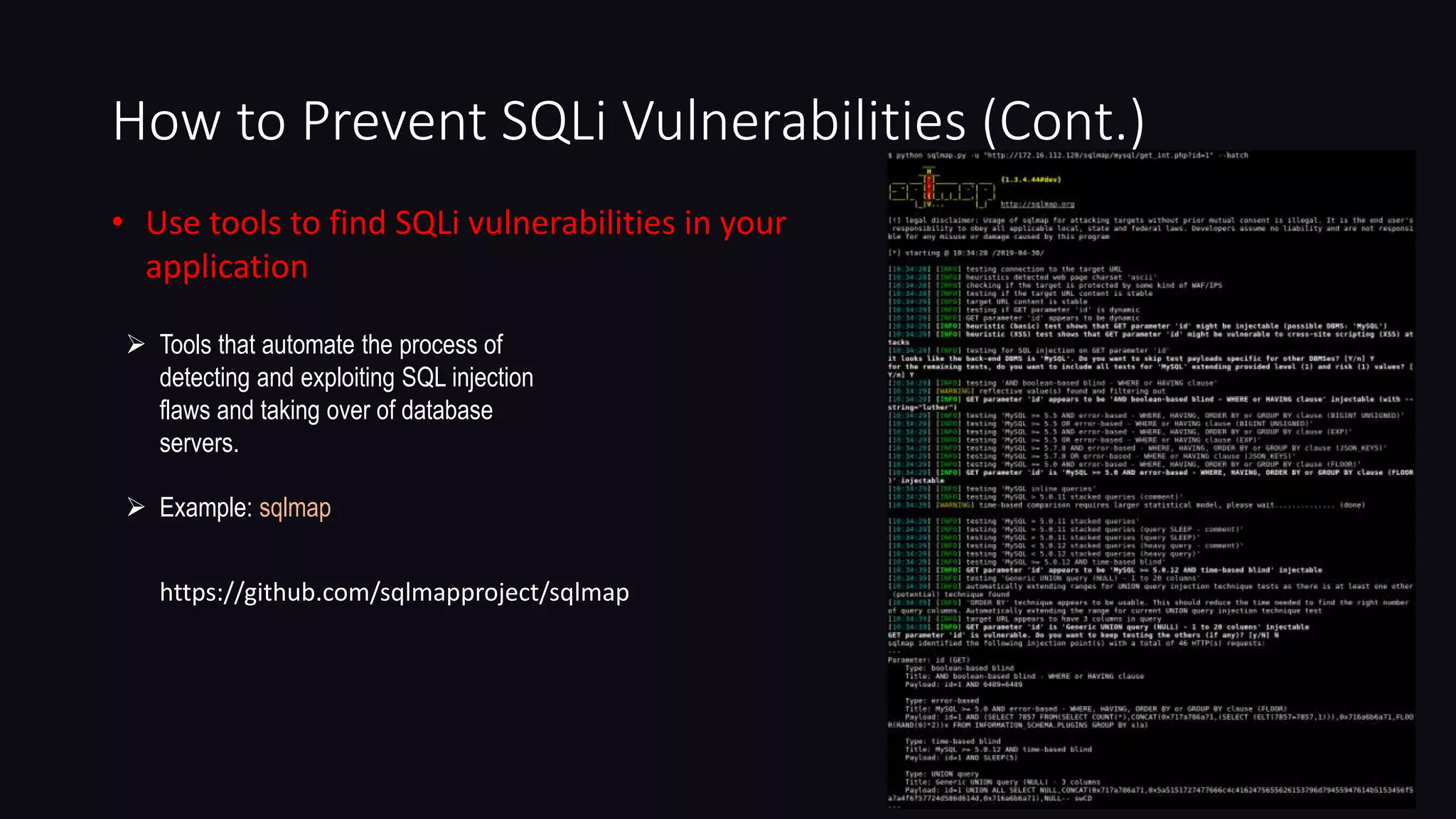
This document discusses SQL injection in Java applications. It defines SQL injection as a vulnerability that allows attackers to hijack databases. The document covers different types of SQL injections like boolean-based, union-based, time-based, and error-based injections. It provides examples of SQL injection vulnerabilities in Java code and how to prevent them by using prepared statements with parameterized queries, stored procedures, input validation, escaping user input, enforcing least privilege, and using tools to detect vulnerabilities.