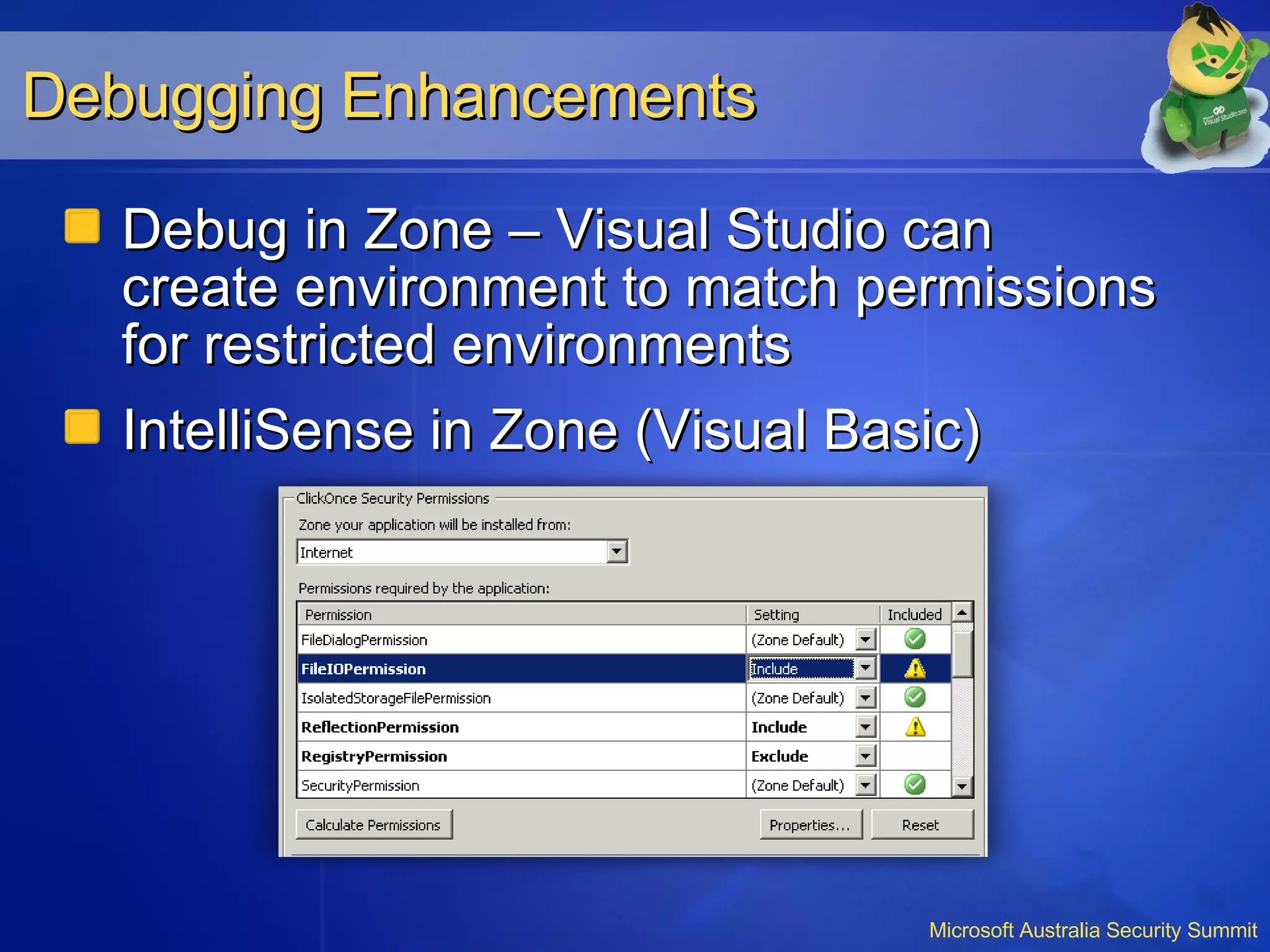
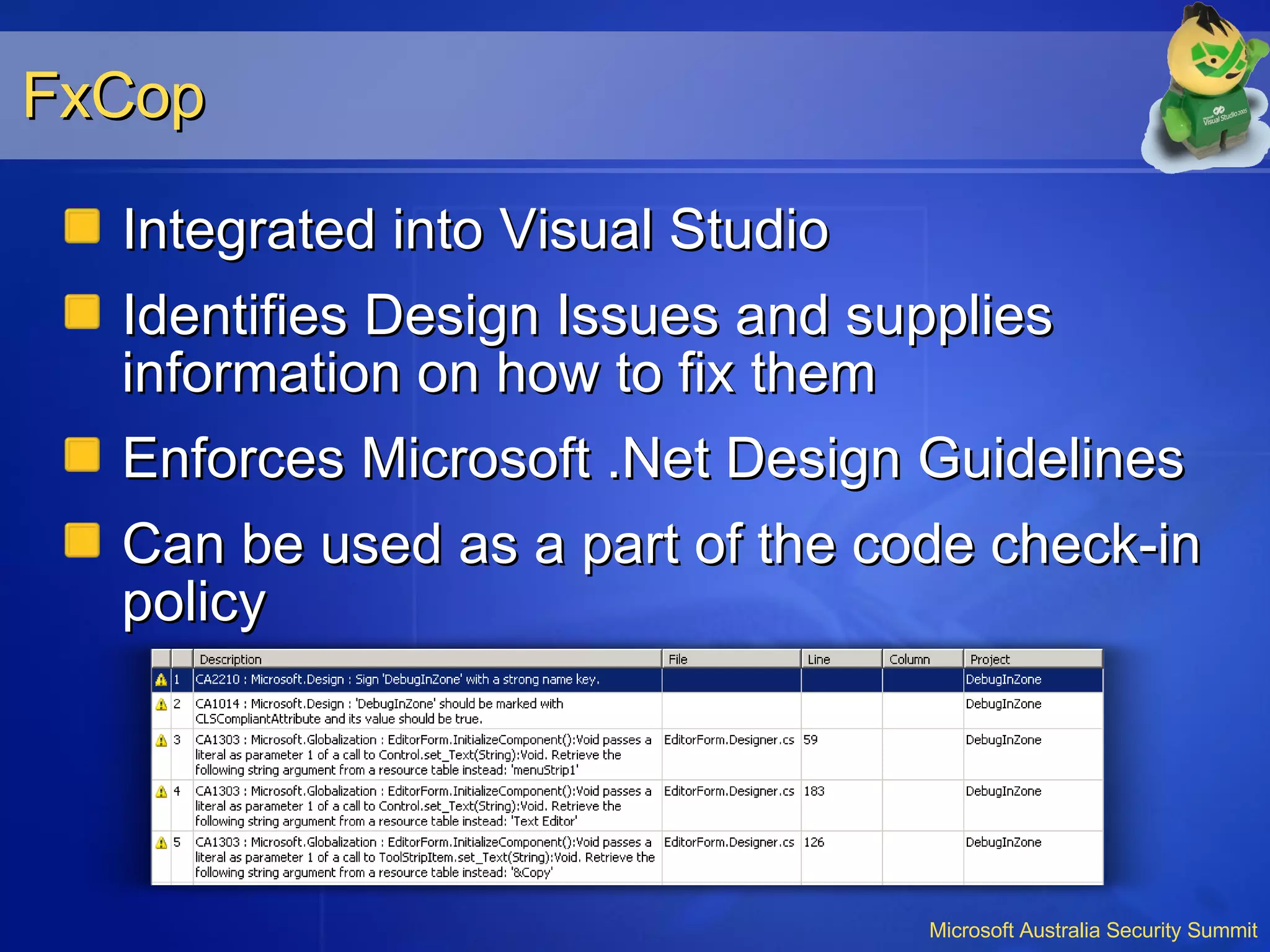
The document summarizes security enhancements in Visual Studio 2005 and SQL Server 2005, including managed code security improvements like running under less privileged accounts, code access security, and debugging/IntelliSense in restricted permission zones. It also describes SQL Server 2005 features like secure defaults, strengthened authentication, granular permissions, encryption and execution context.











![Sandboxing Application Domains can be created to sandbox assemblies Process for creating a sandbox has been simplified under the 2.0 framework API is exposed as a new overload of AppDomain.CreateDomain AppDomain.CreateDomain( string friendlyName, Evidence securityInfo, AppDomainSetup info, PermissionSet grantSet, params StrongName[] fullTrustAssemblies );](https://image.slidesharecdn.com/creating-secure-applications-1203401263642323-4/75/Creating-Secure-Applications-15-2048.jpg)