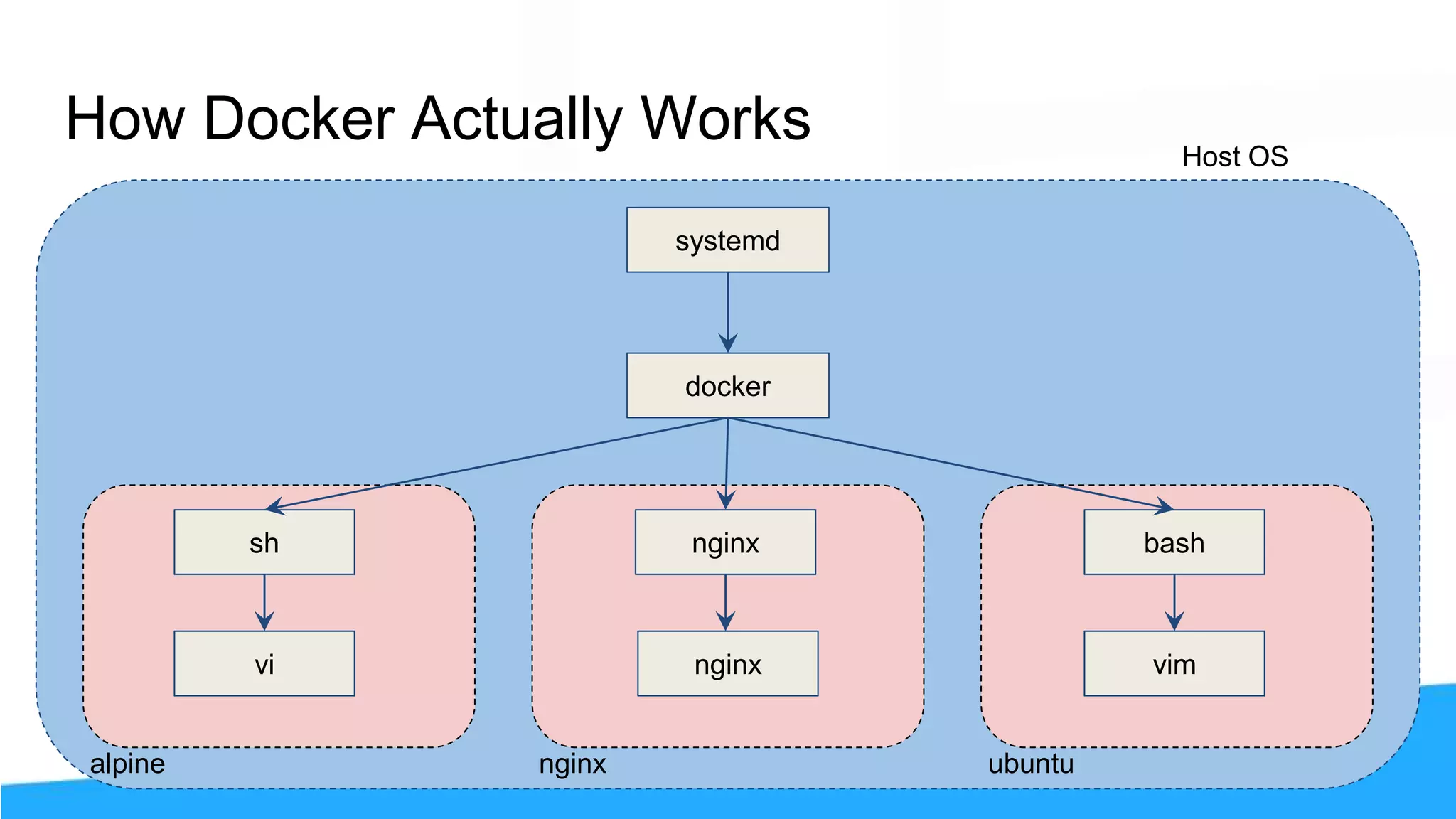
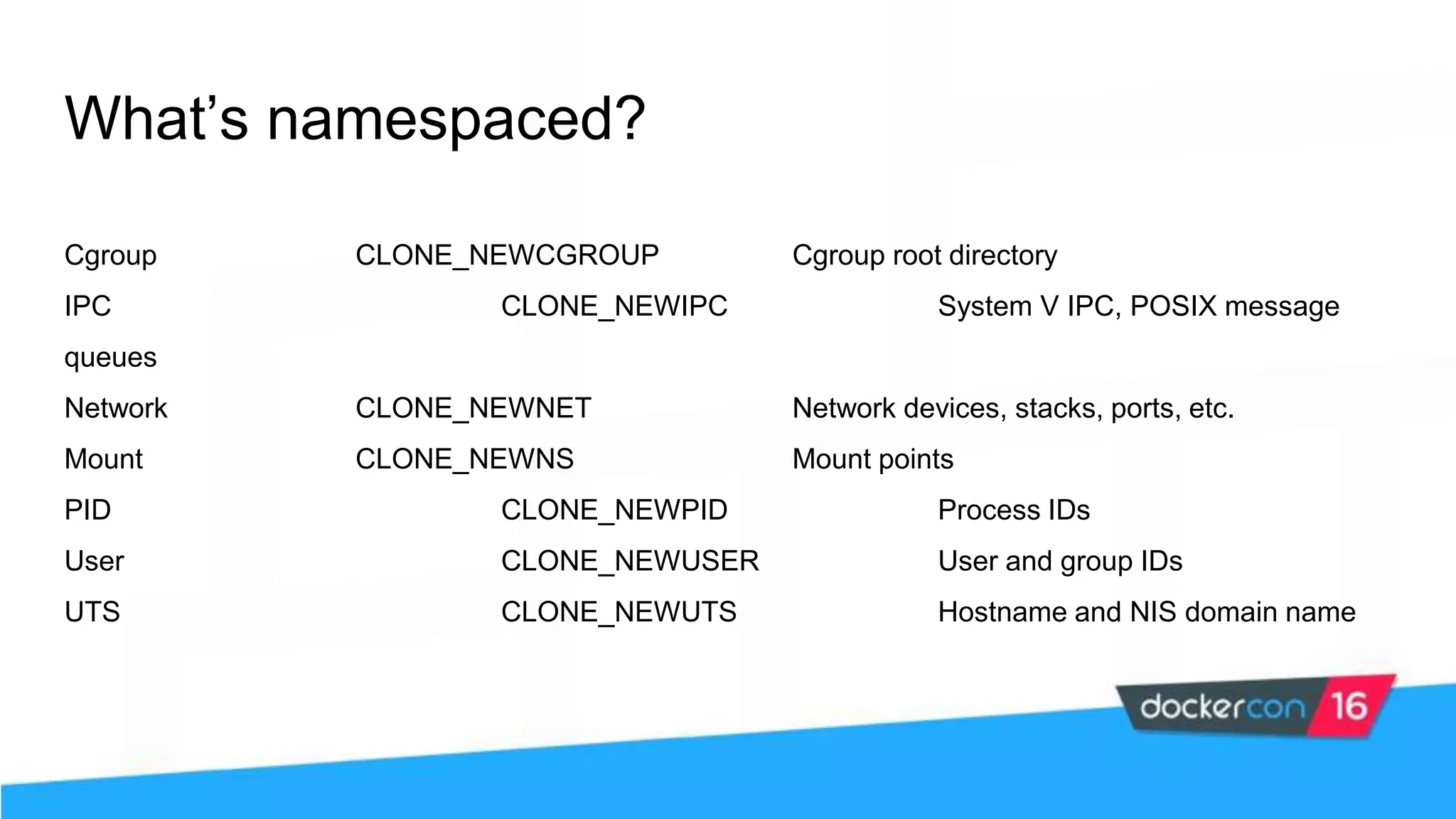
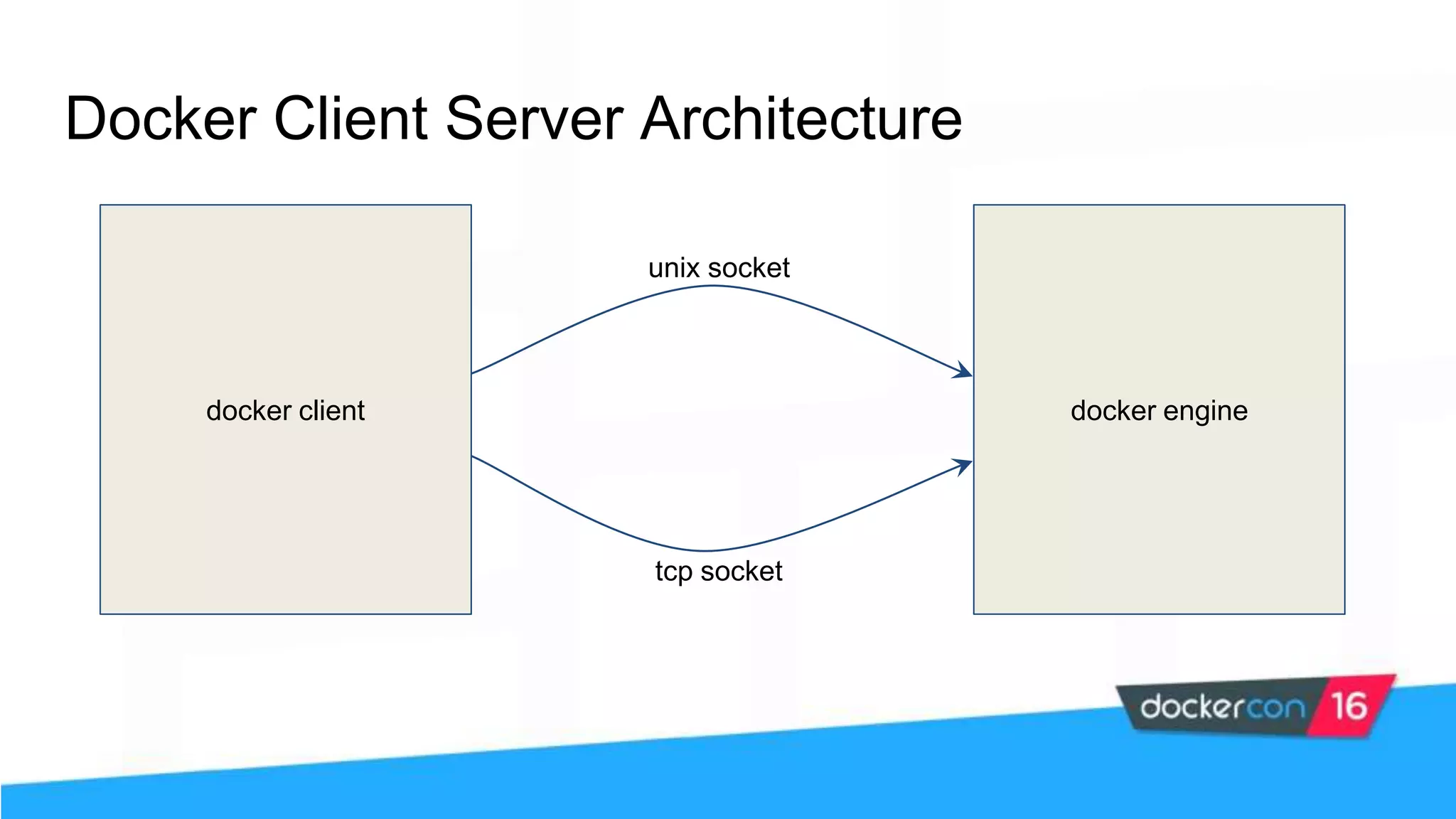
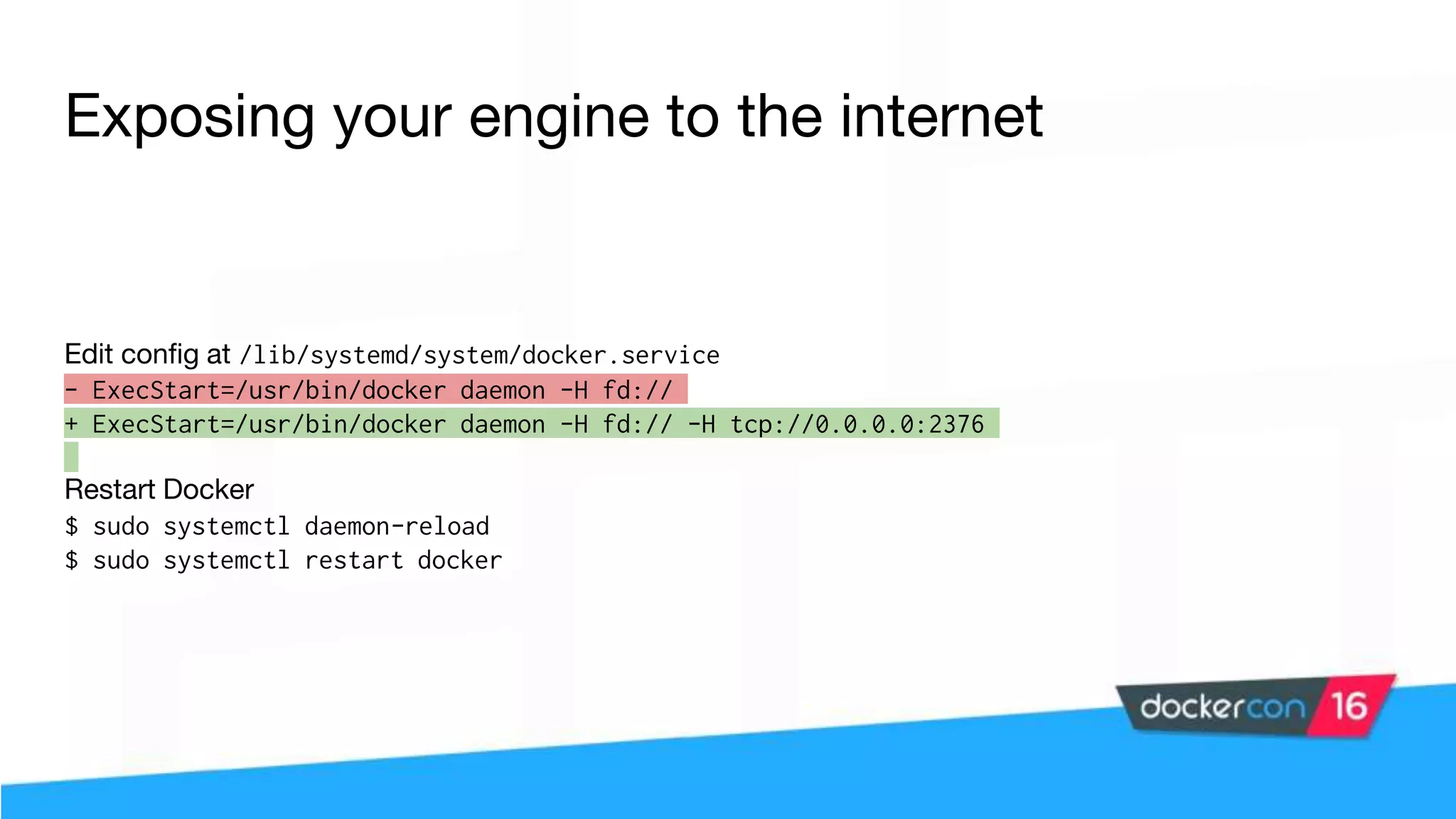
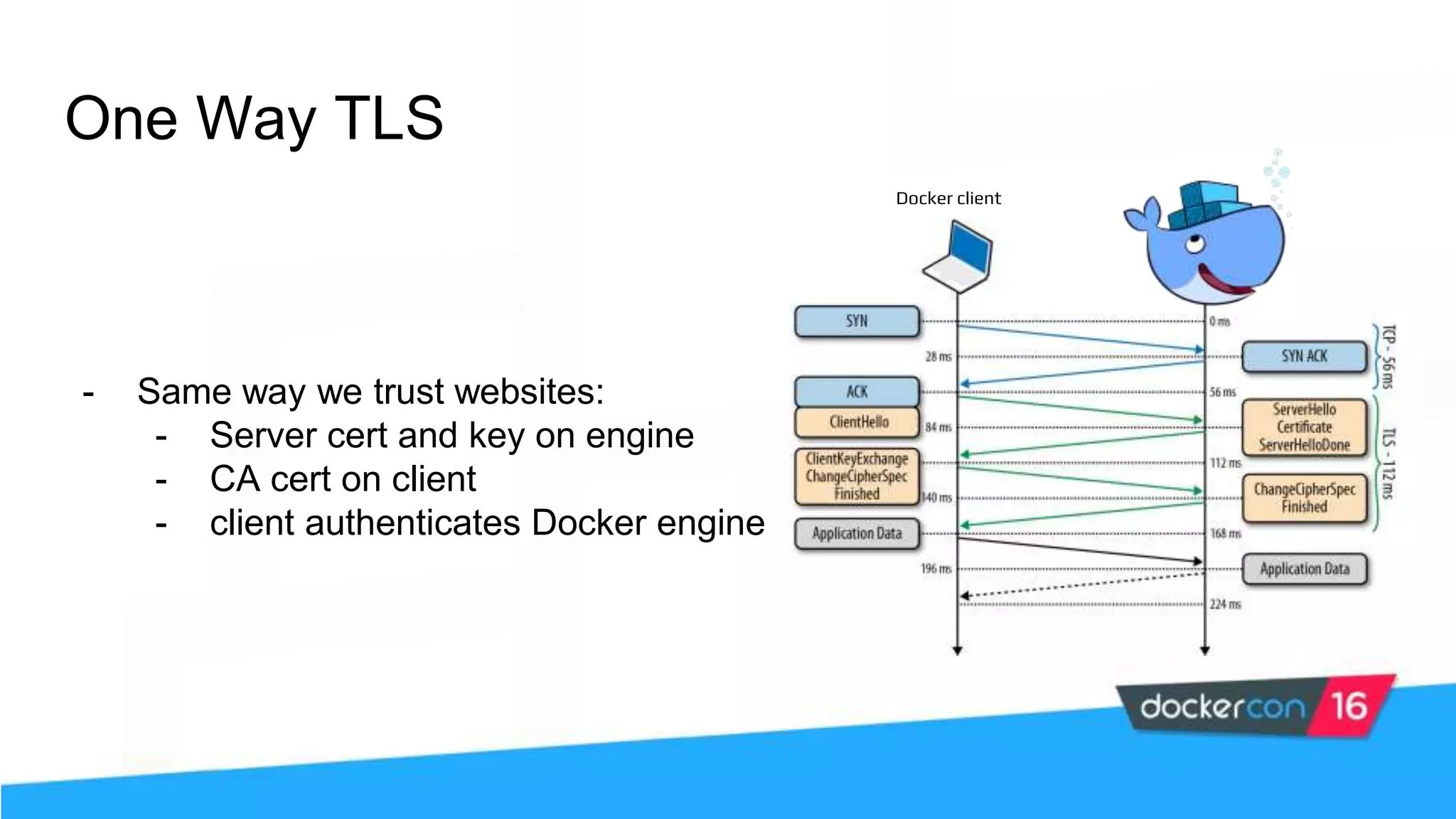
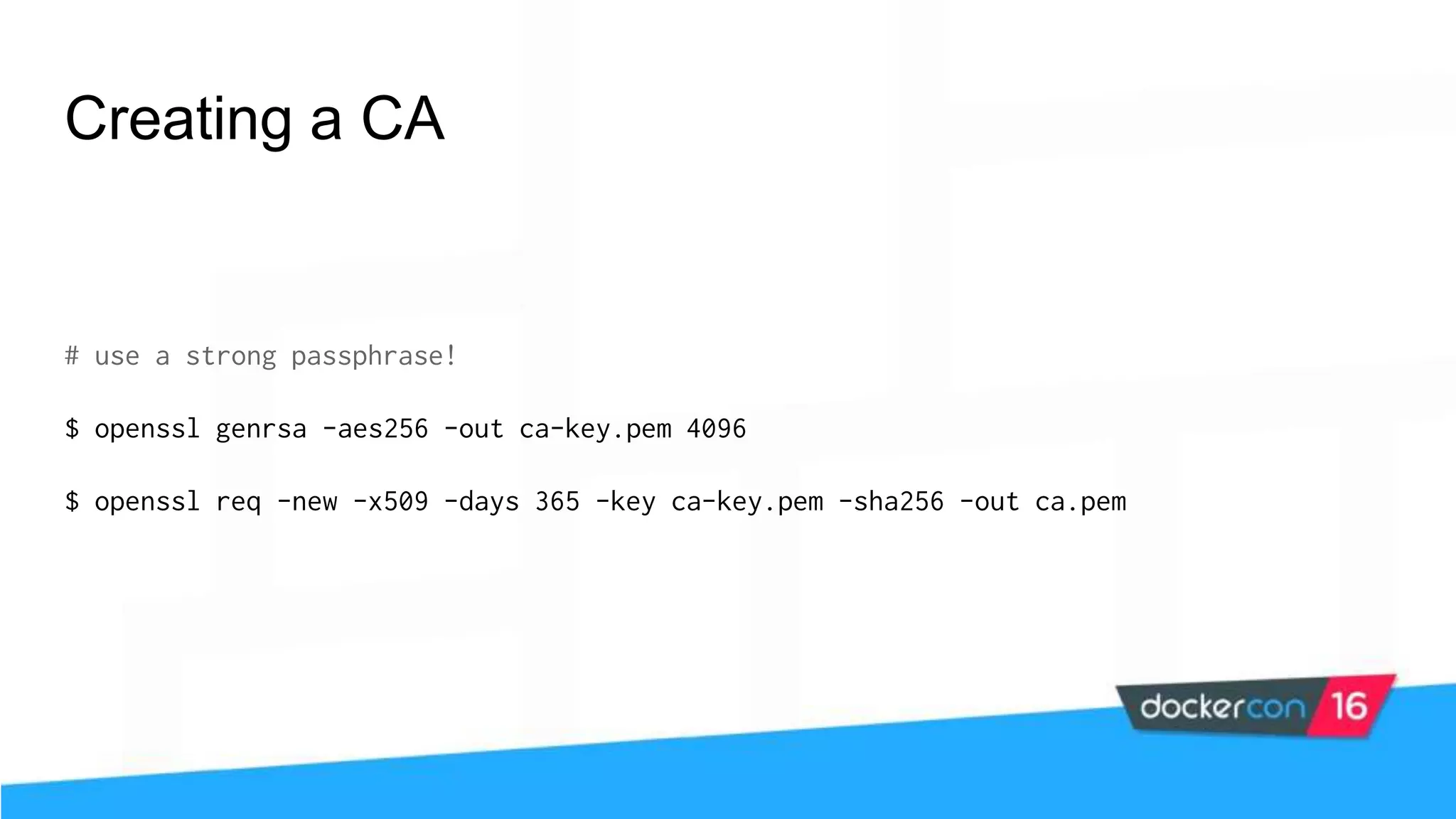
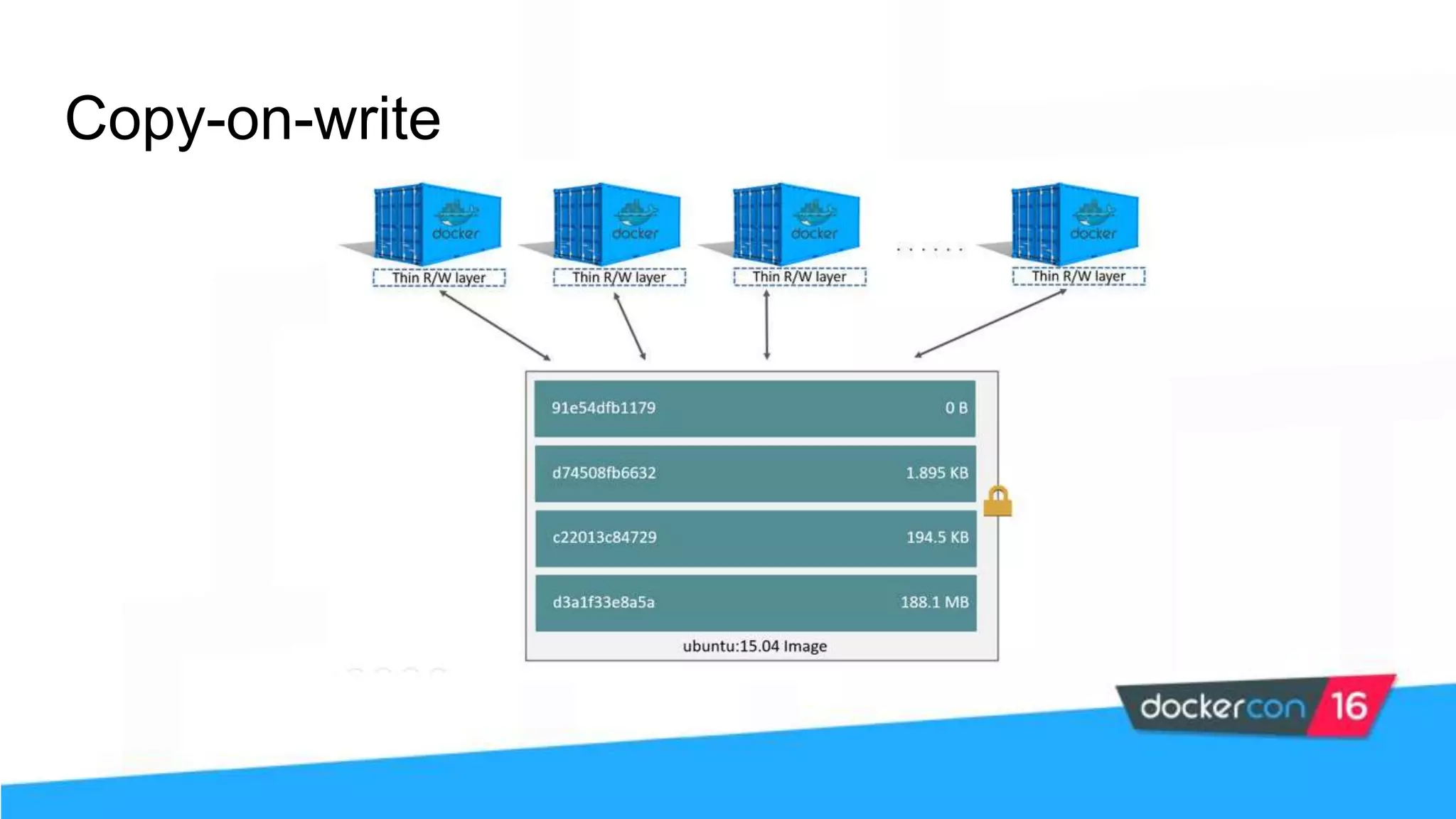
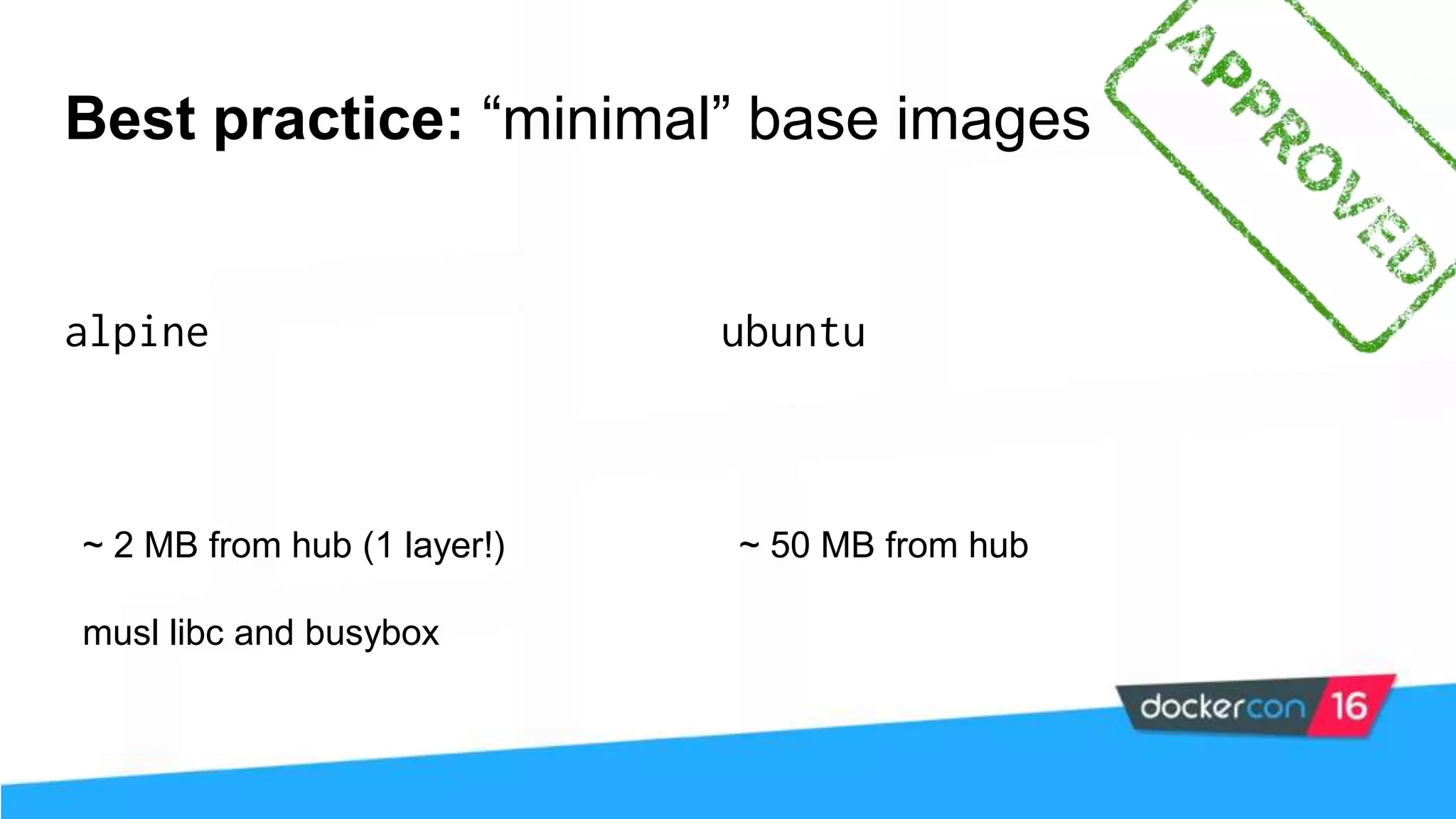
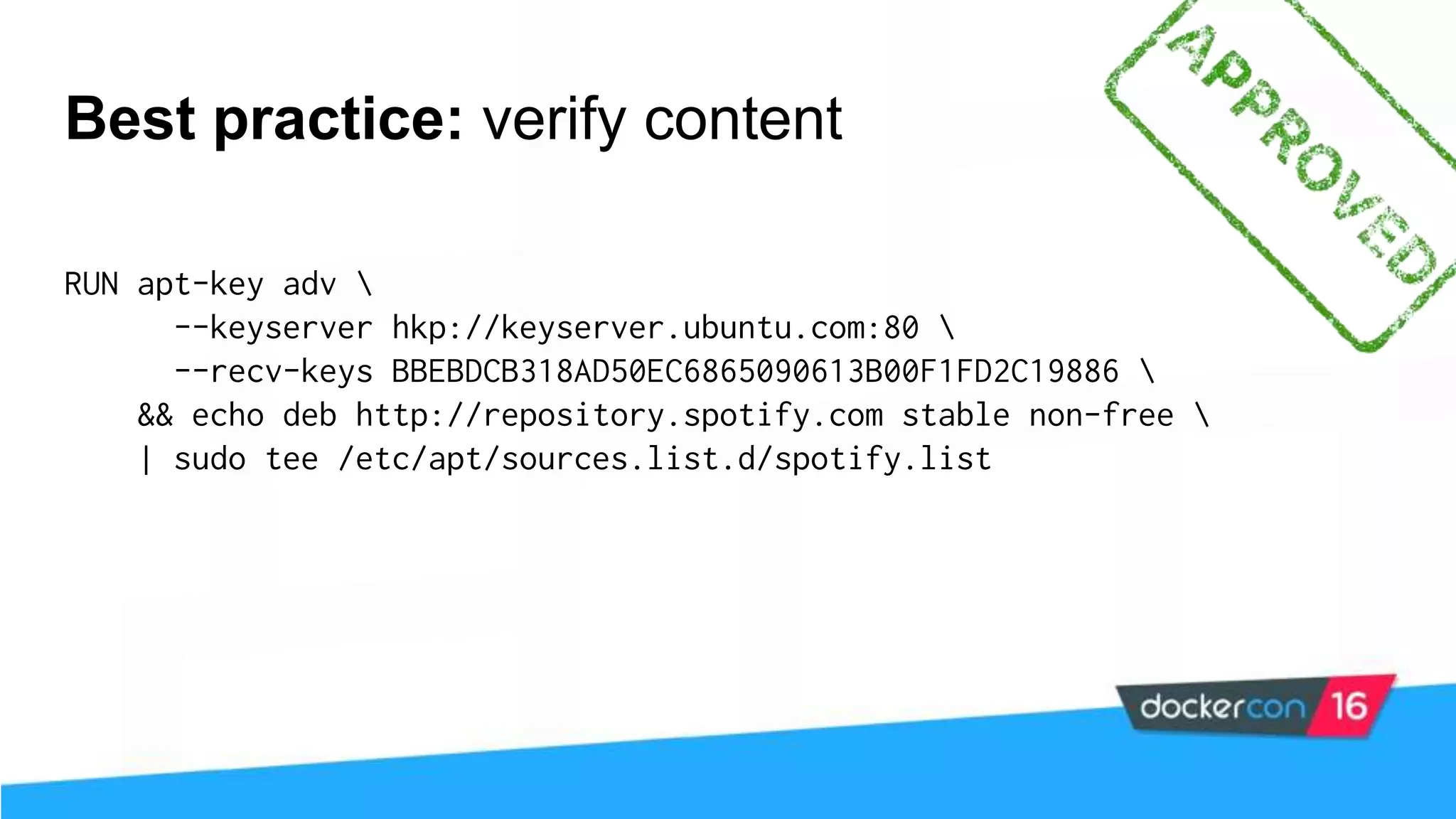
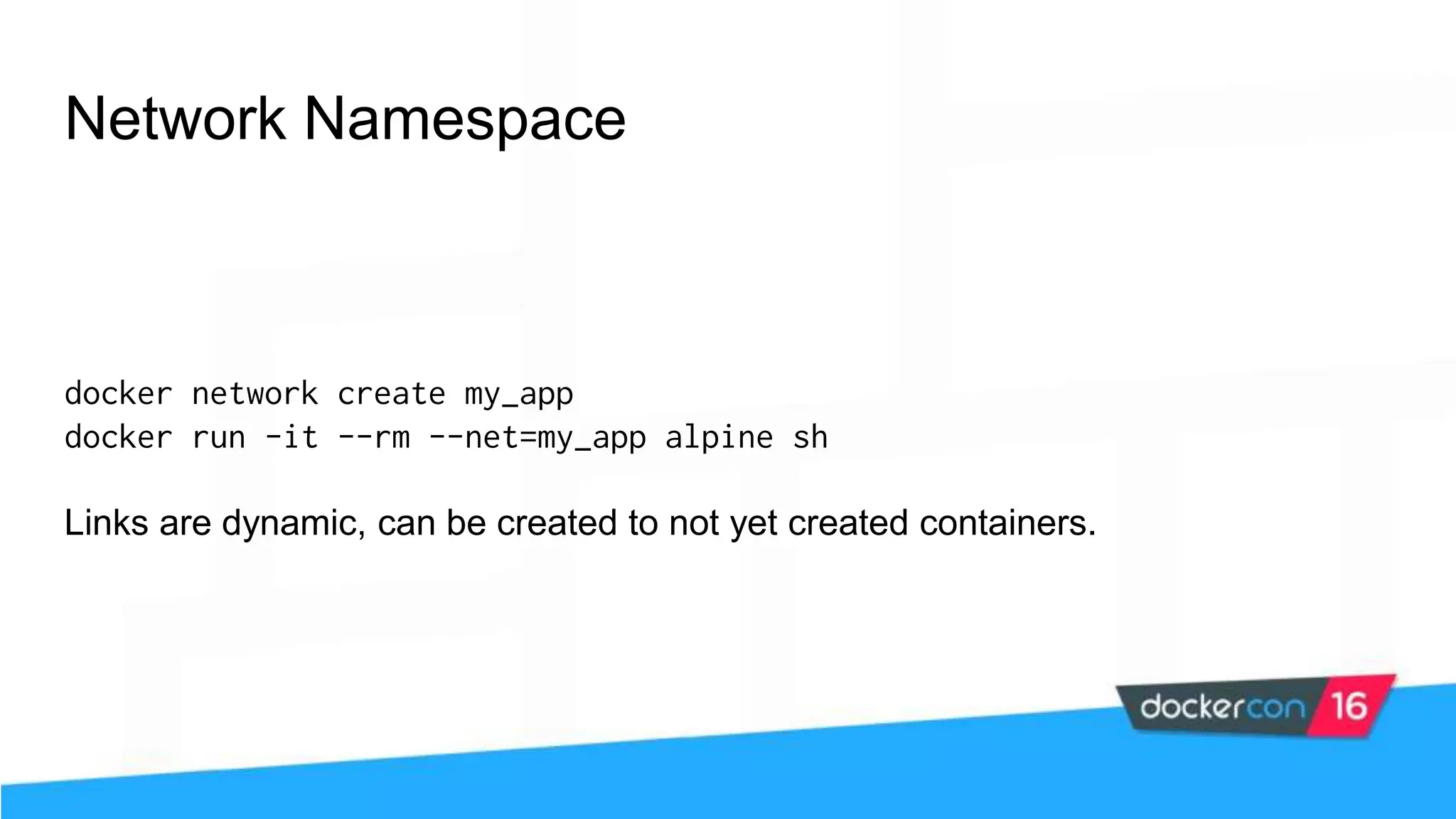
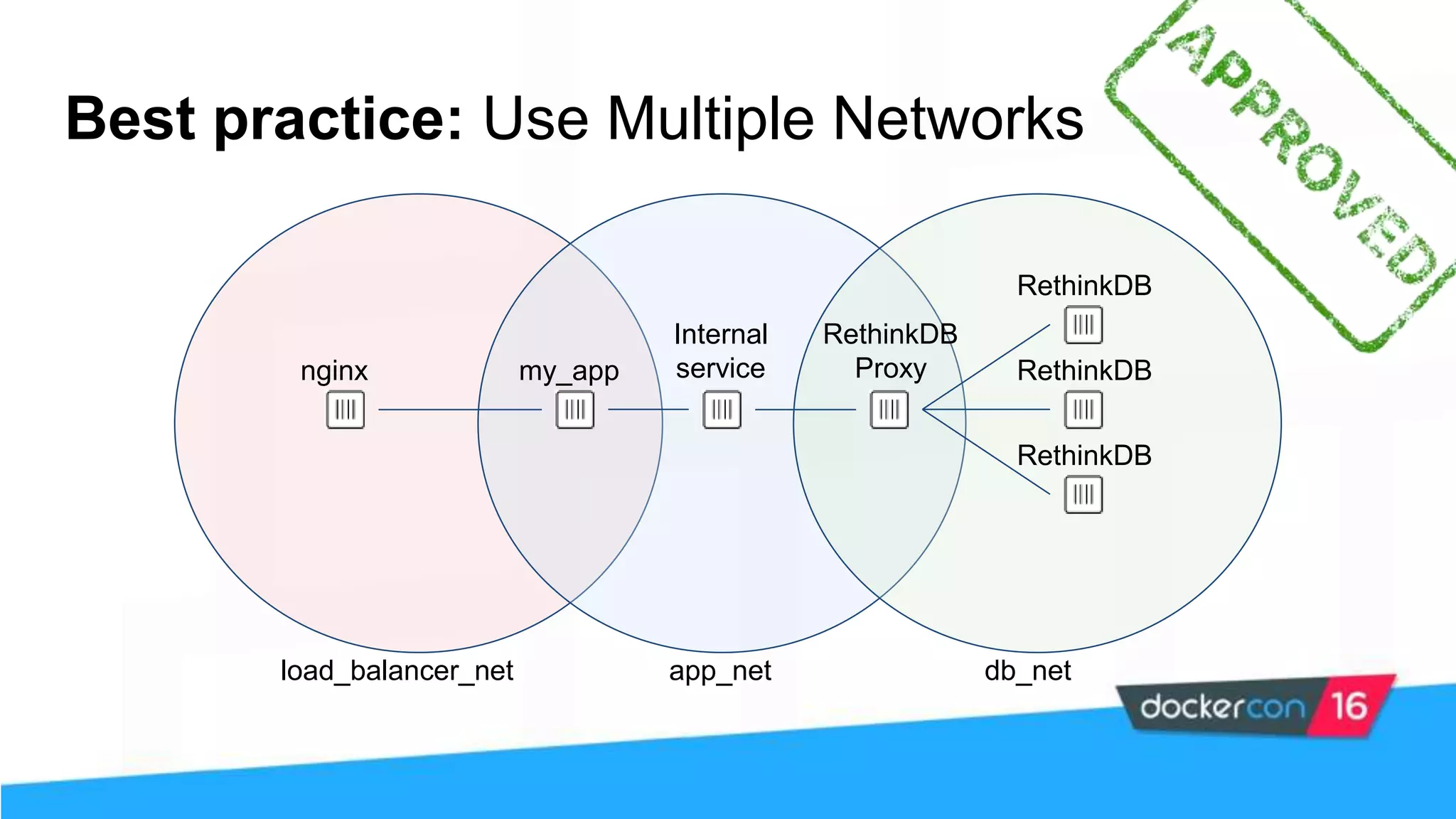
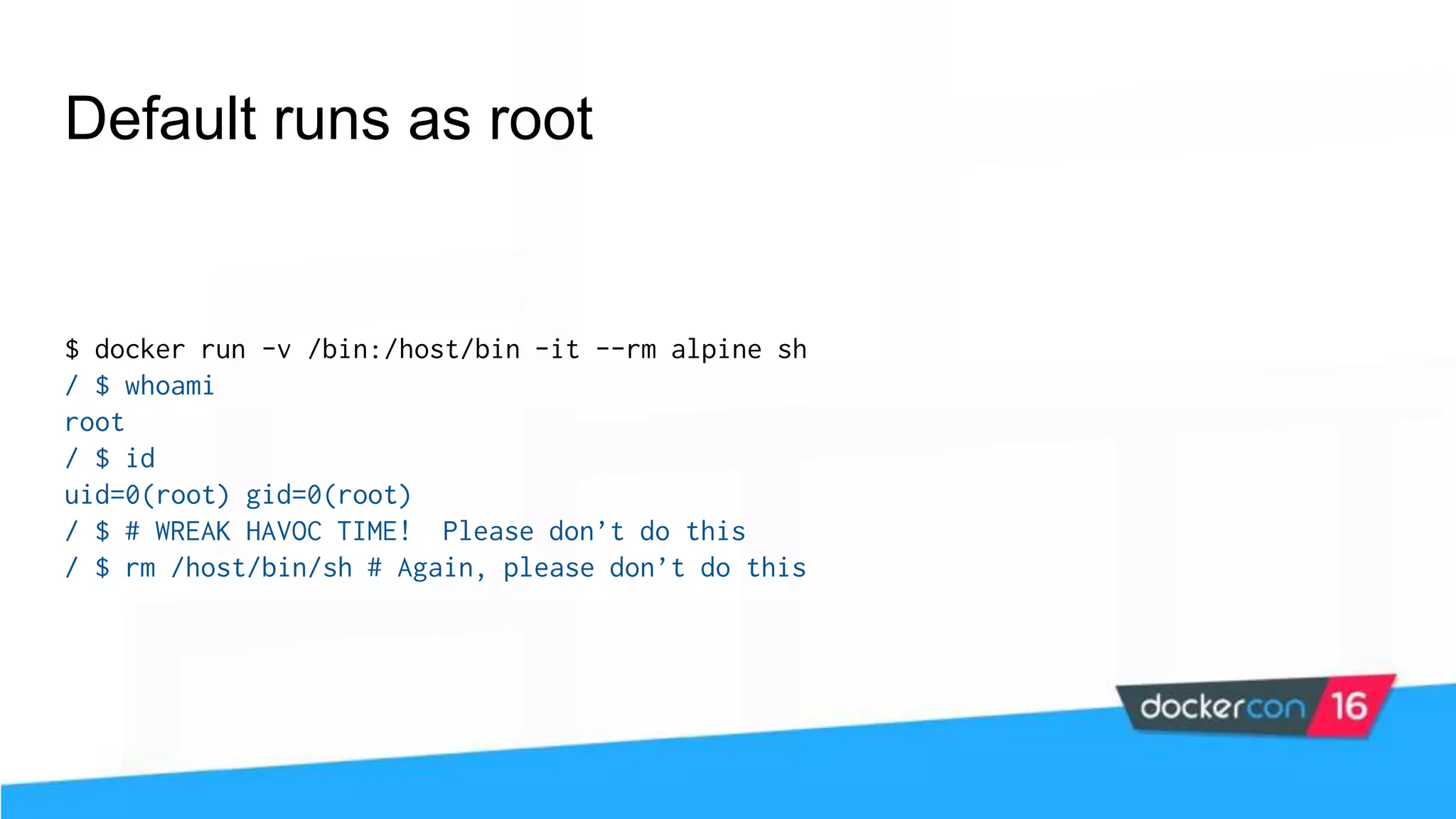
The workshop focuses on Docker security, covering features, tools, best practices, and practical exercises on securing Docker environments. It includes understanding container architecture, namespaces, control groups, and implementing TLS for secure communications. Additionally, it discusses security practices like minimal base images, image provenance, Docker content trust, capabilities management, and seccomp configurations.

































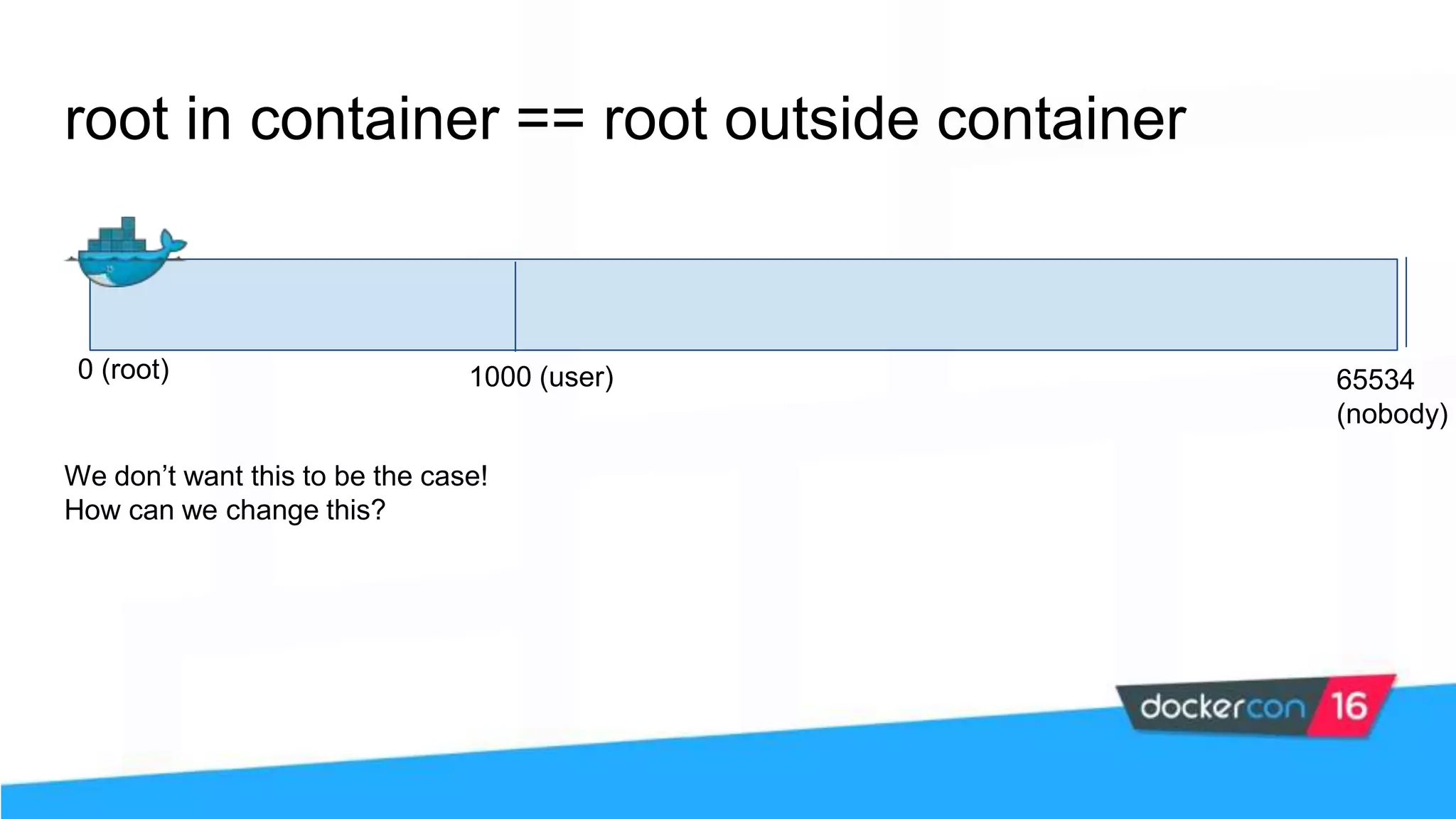
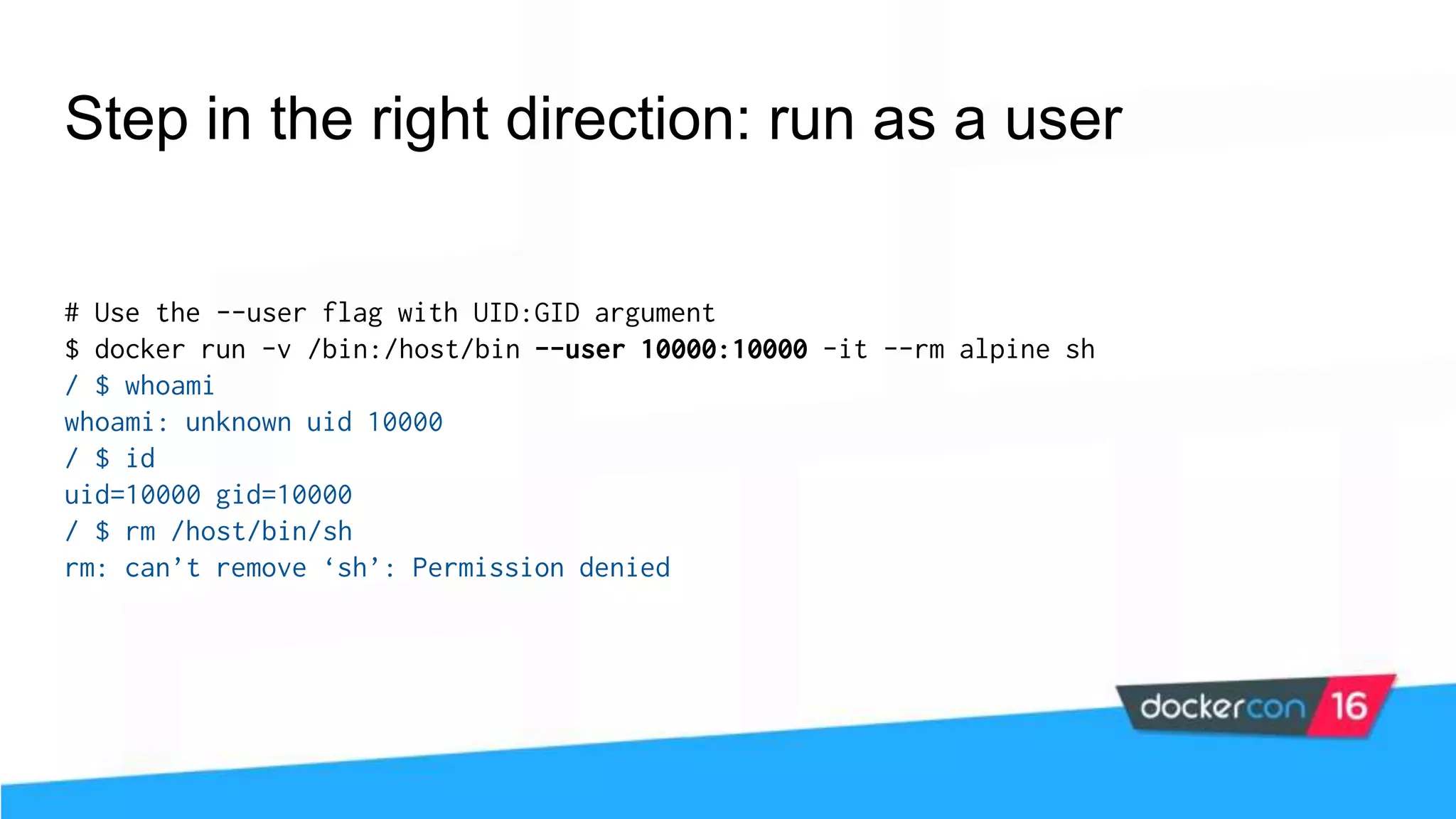
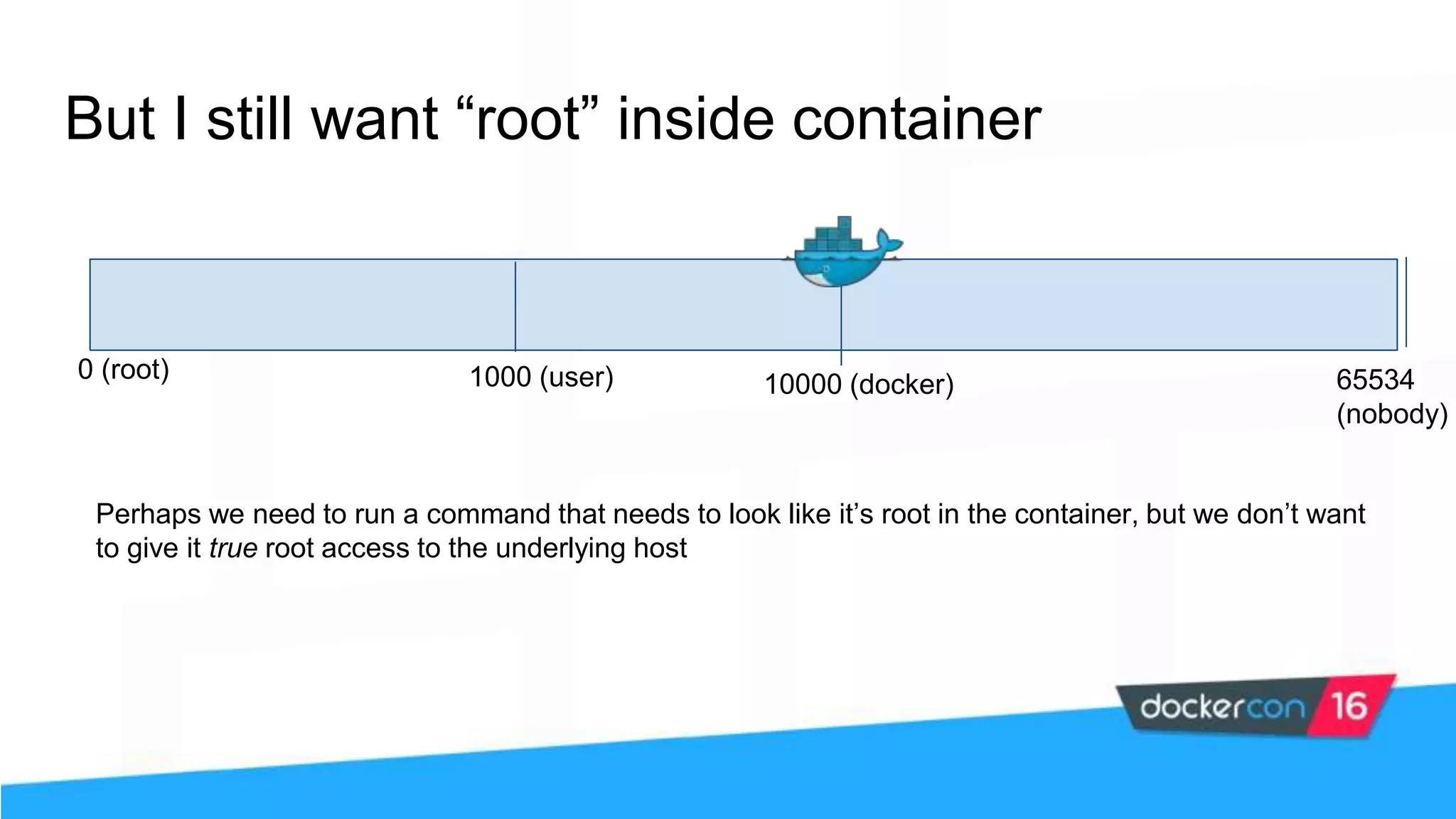
![$ docker daemon --userns-remap [uid[:gid]] Enable user namespaces 0 (root) 1000 (user) 65534 (nobody) 10000 (docker) “0” “root”](https://image.slidesharecdn.com/securityworkshop-160627214820/75/Docker-Security-workshop-slides-62-2048.jpg)
![$ docker daemon --userns-remap [uid[:gid]] Will need to re-pull images and re-create volumes due to container resource and image layer permissions Leave this feature on in production; switching back and forth should only be done in development Enable user namespaces - common pitfalls 0 (root) 1000 (user) 65534 (nobody) 10000 (docker) “0” “root”](https://image.slidesharecdn.com/securityworkshop-160627214820/75/Docker-Security-workshop-slides-63-2048.jpg)




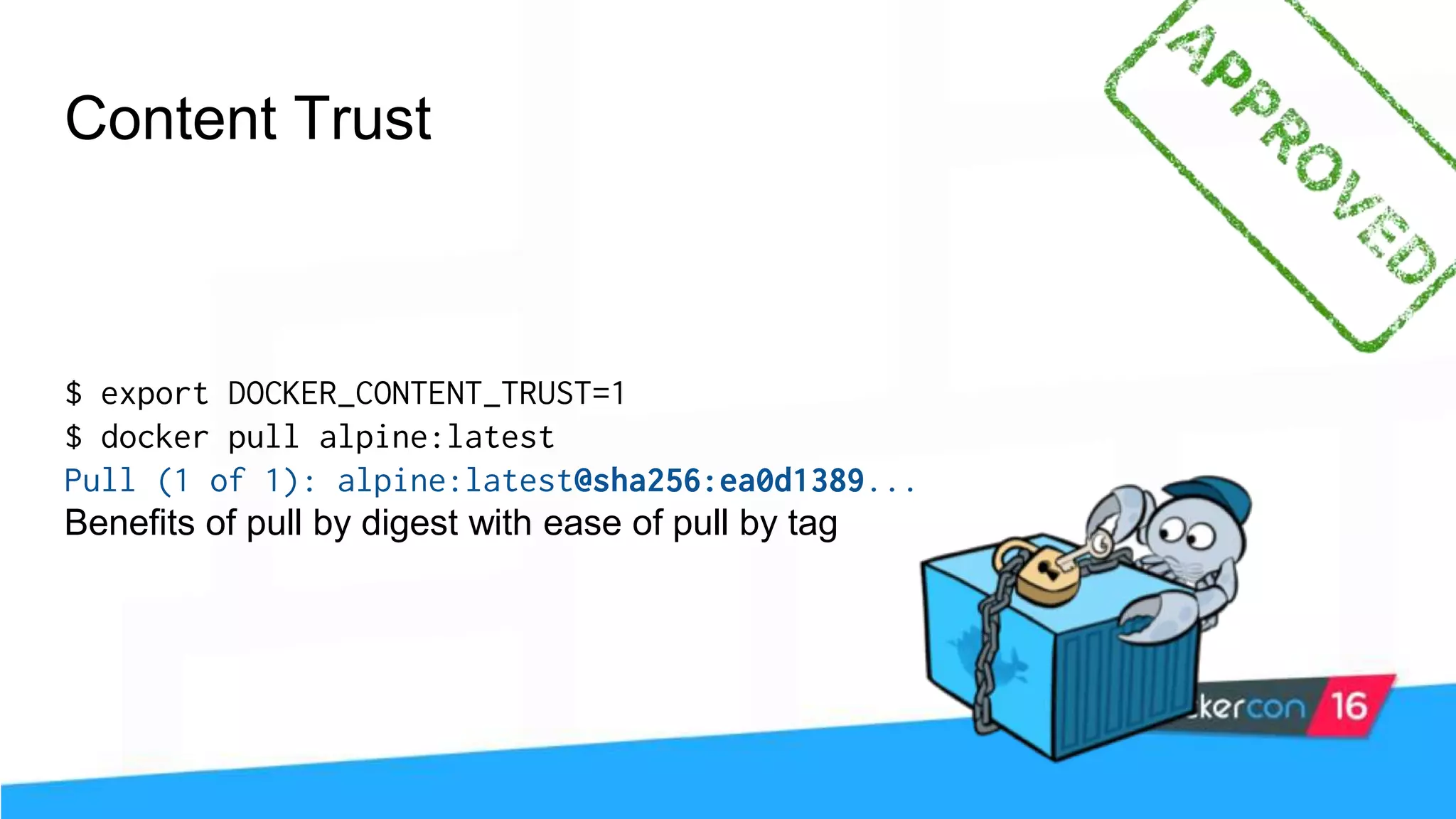
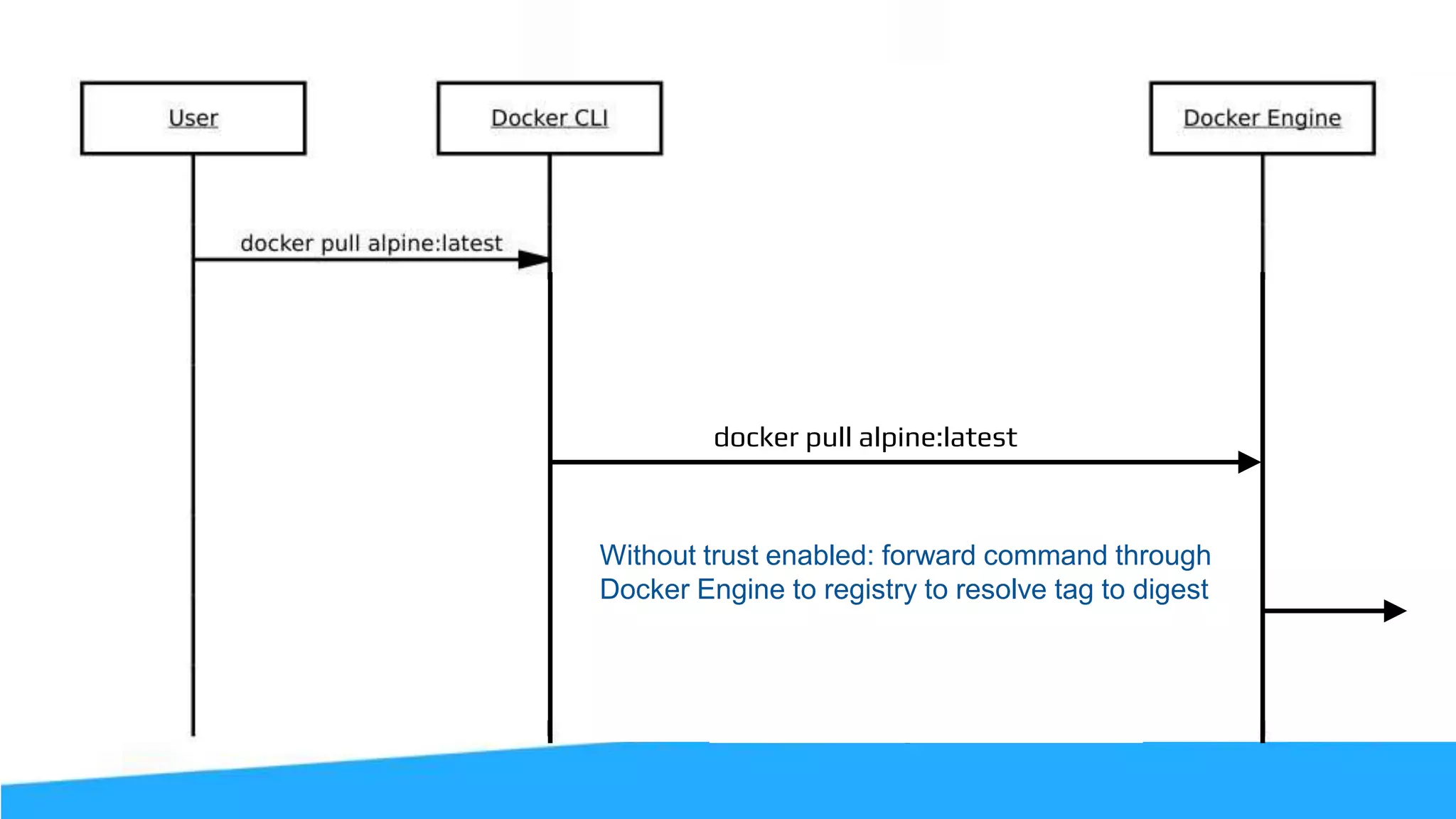
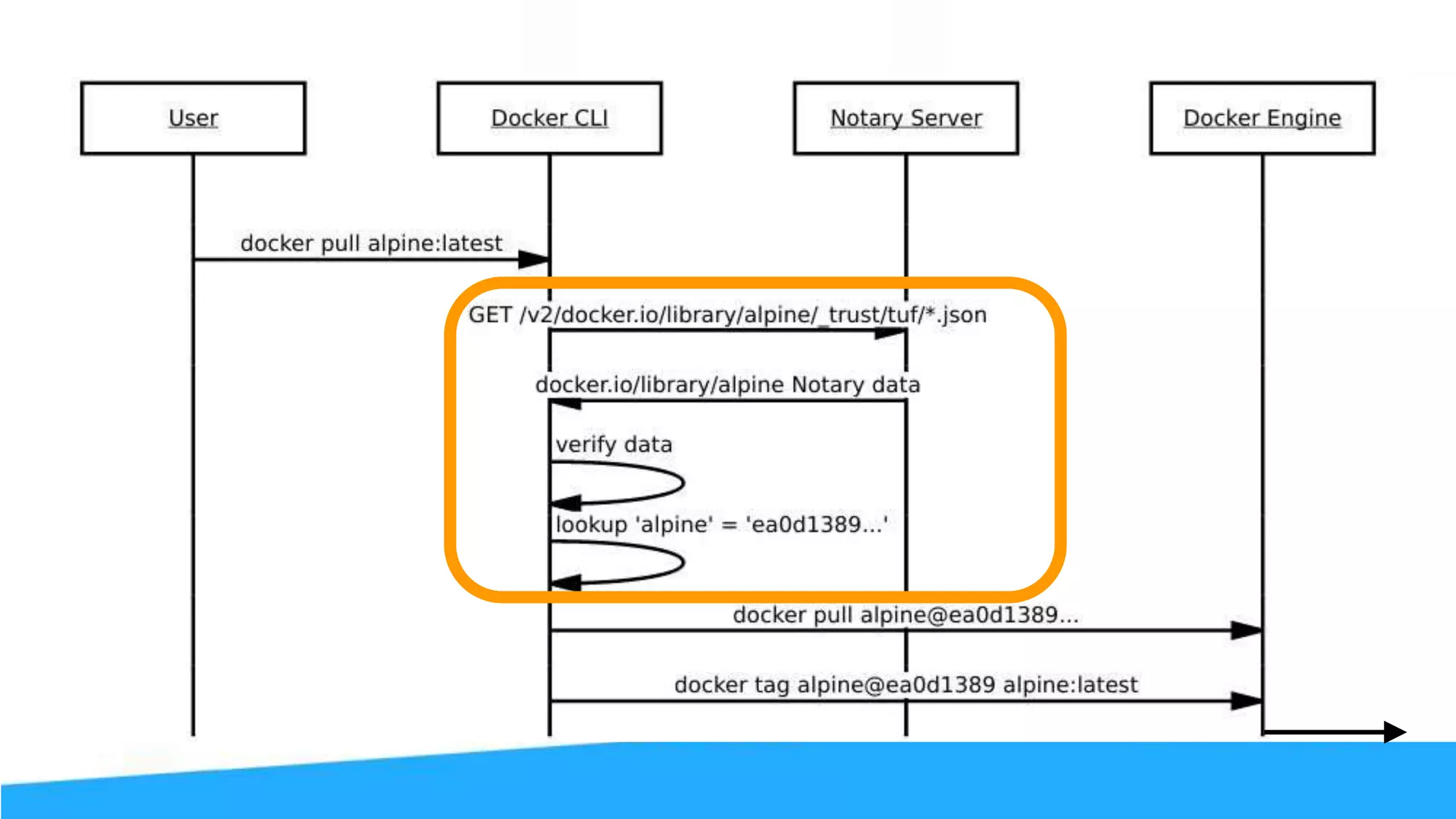
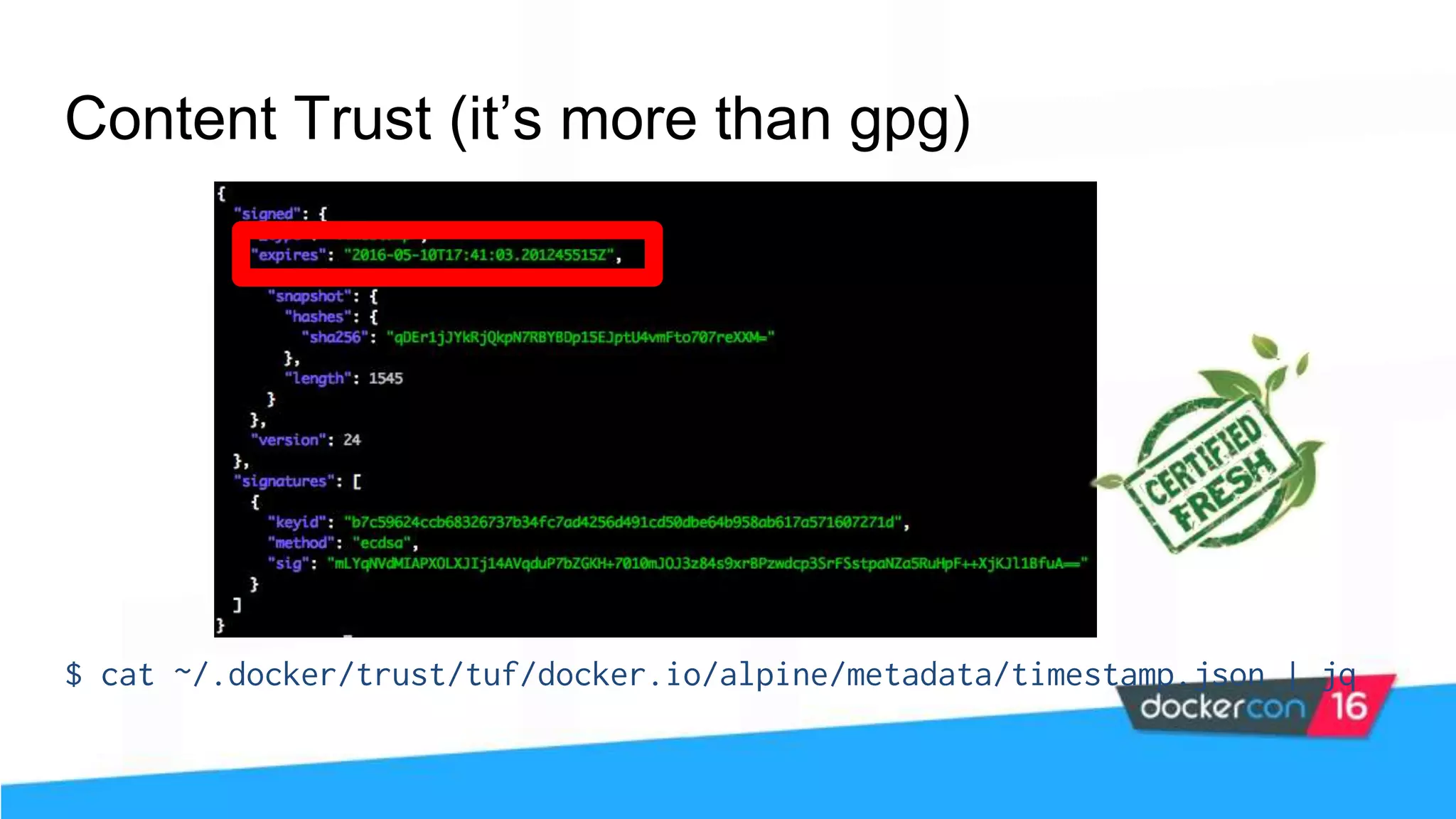
![Content Trust (it’s more than gpg) The push refers to a repository [<user>/alpine] 77f08abee8bf: Pushed trust: digest: sha256:d5de850d728... size: 1355 Signing and pushing trust metadata Enter passphrase for root key with ID e83f424: Enter passphrase for new repository key with ID f903fc9 (docker.io/<user>/alpine): Repeat passphrase for new repository key with ID f903fc9 (docker.io/<user>/alpine): Finished initializing "docker.io/<user>/alpine" Successfully signed "docker.io/<user>/alpine":trust](https://image.slidesharecdn.com/securityworkshop-160627214820/75/Docker-Security-workshop-slides-73-2048.jpg)













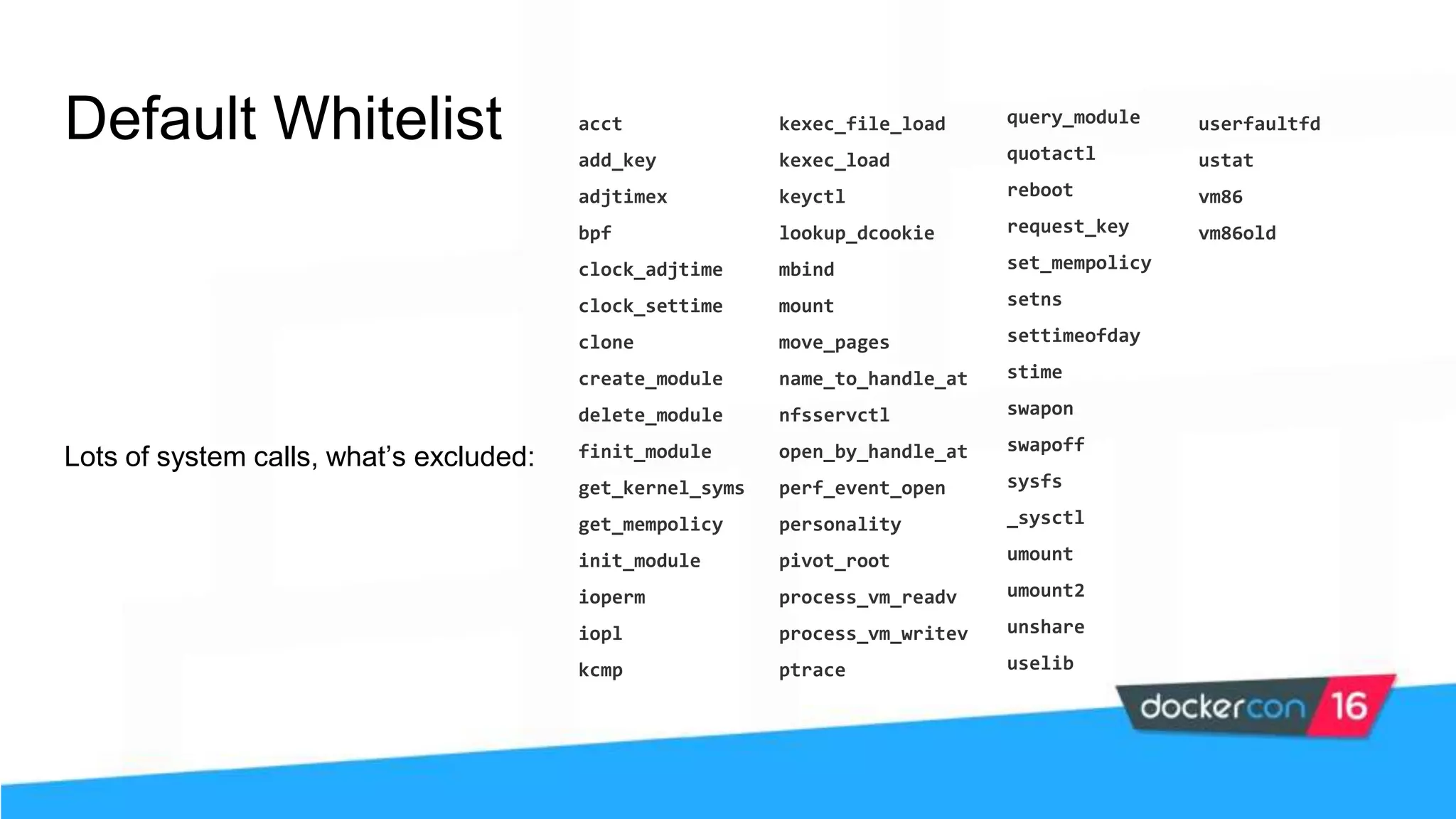
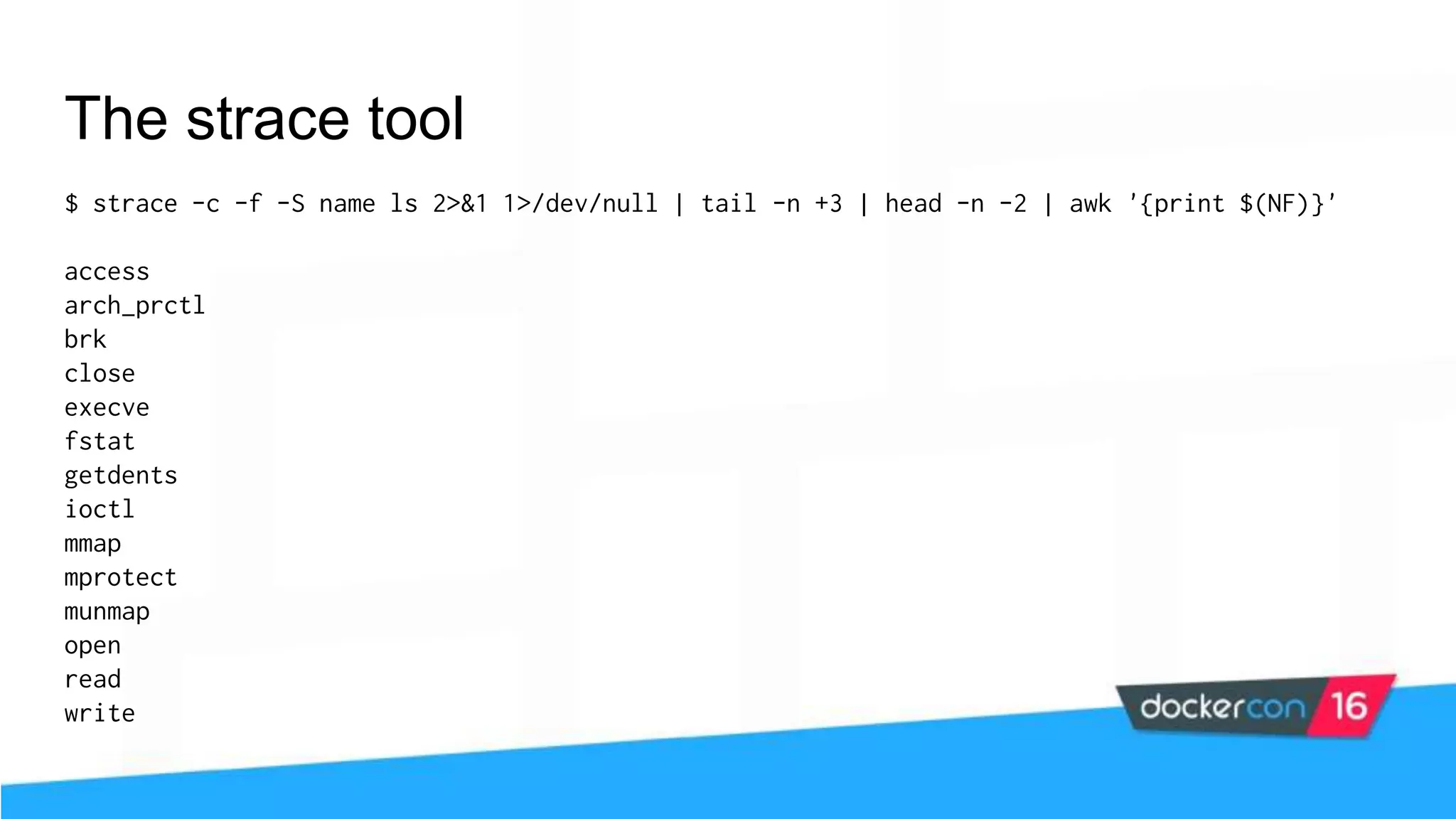
![Docker seccomp profile DSL Seccomp policy example: { "defaultAction": "SCMP_ACT_ERRNO", "architectures": [ "SCMP_ARCH_X86_64", "SCMP_ARCH_X86", "SCMP_ARCH_X32" ], "syscalls": [ { "name": "accept", "action": "SCMP_ACT_ALLOW", "args": [] }, ... ] } Possible actions: SCMP_ACT_KILL SCMP_ACT_TRAP SCMP_ACT_ERRNO SCMP_ACT_TRACE SCMP_ACT_ALLOW](https://image.slidesharecdn.com/securityworkshop-160627214820/75/Docker-Security-workshop-slides-99-2048.jpg)
![Docker seccomp profile DSL More complex filters: "args": [ { "index": 0, "op": "SCMP_CMP_MASKED_EQ", "value": 2080505856, "valueTwo": 0 } ] 2080505856 == 0x7C020000](https://image.slidesharecdn.com/securityworkshop-160627214820/75/Docker-Security-workshop-slides-100-2048.jpg)