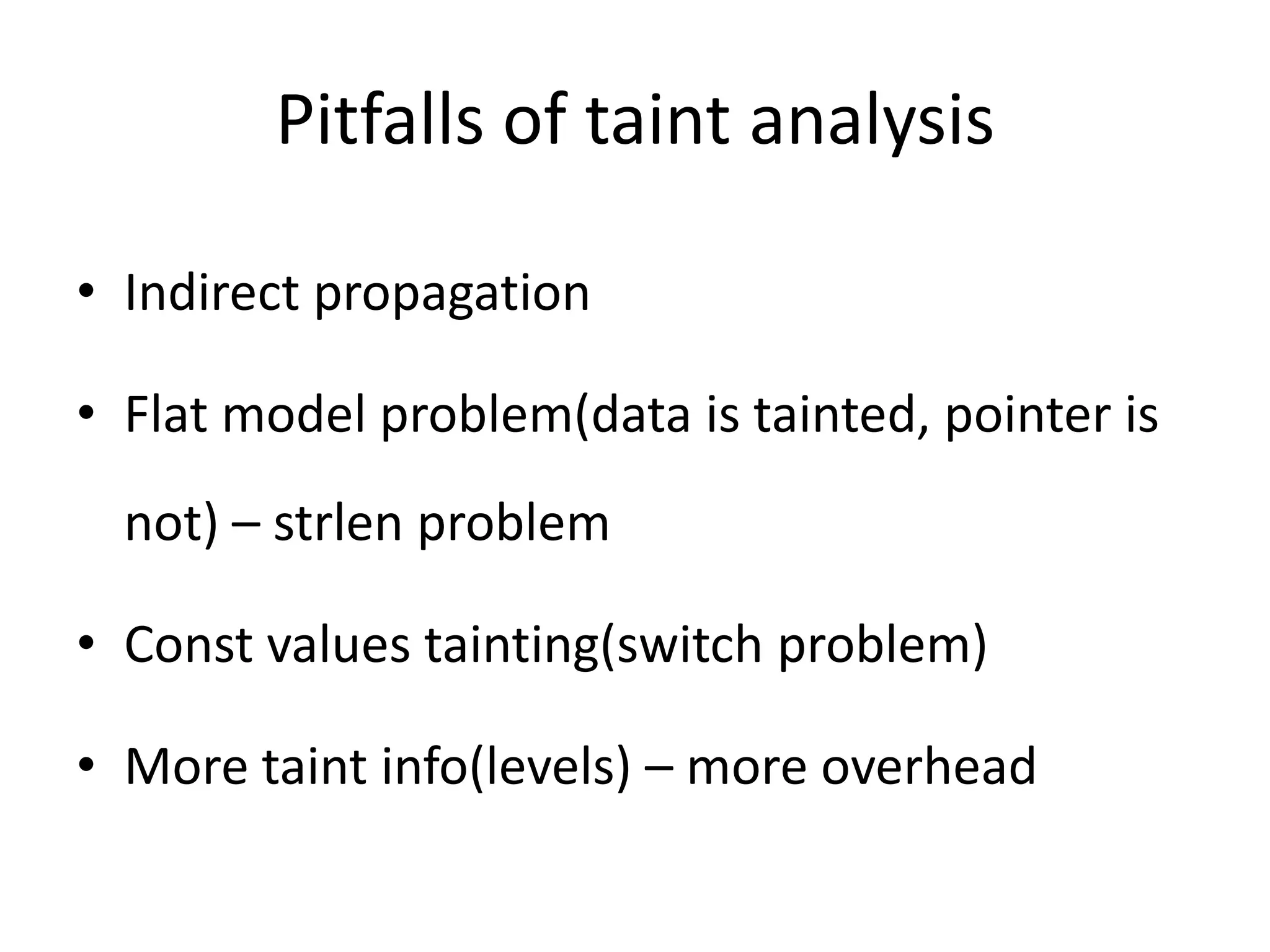
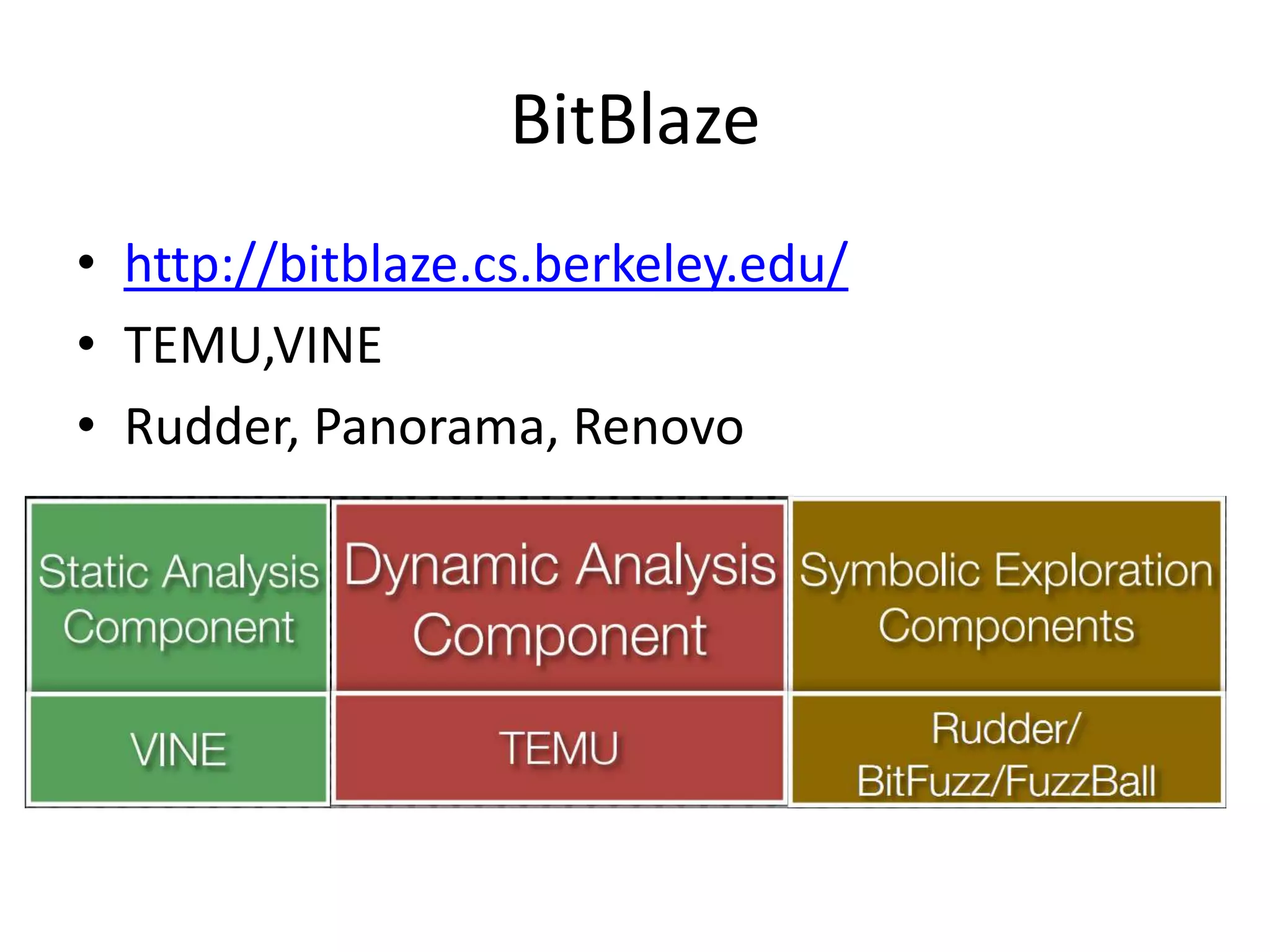
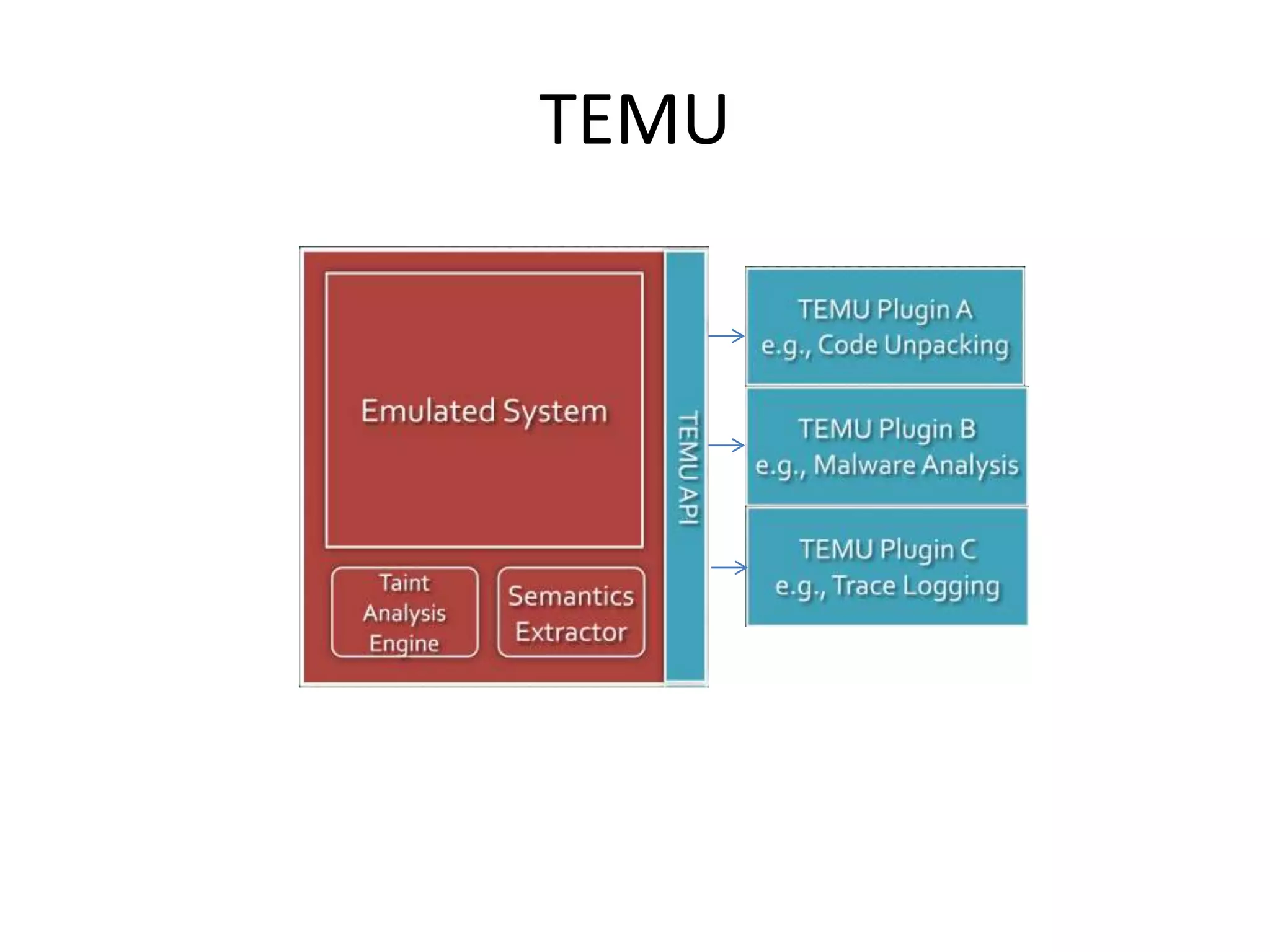
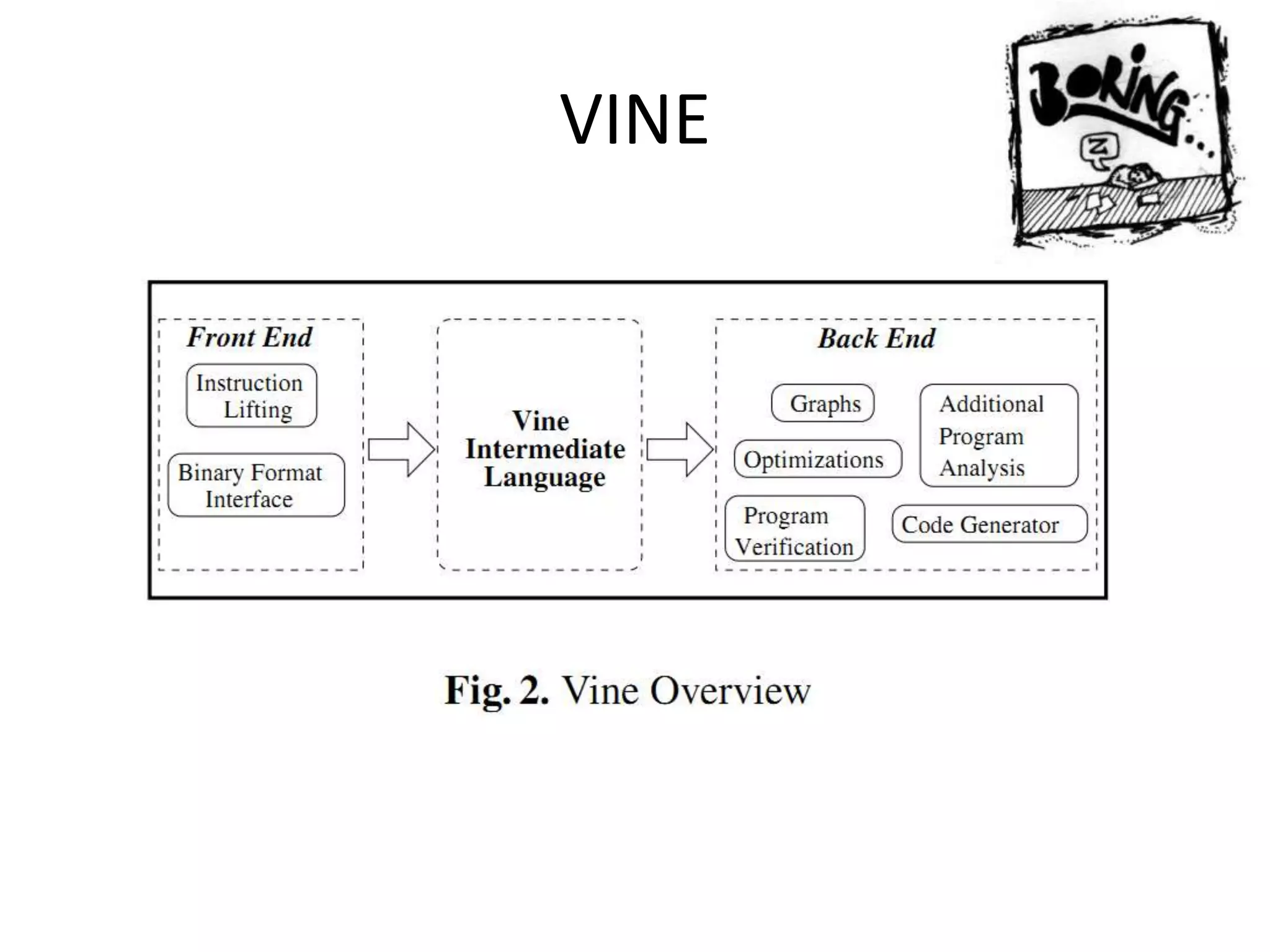
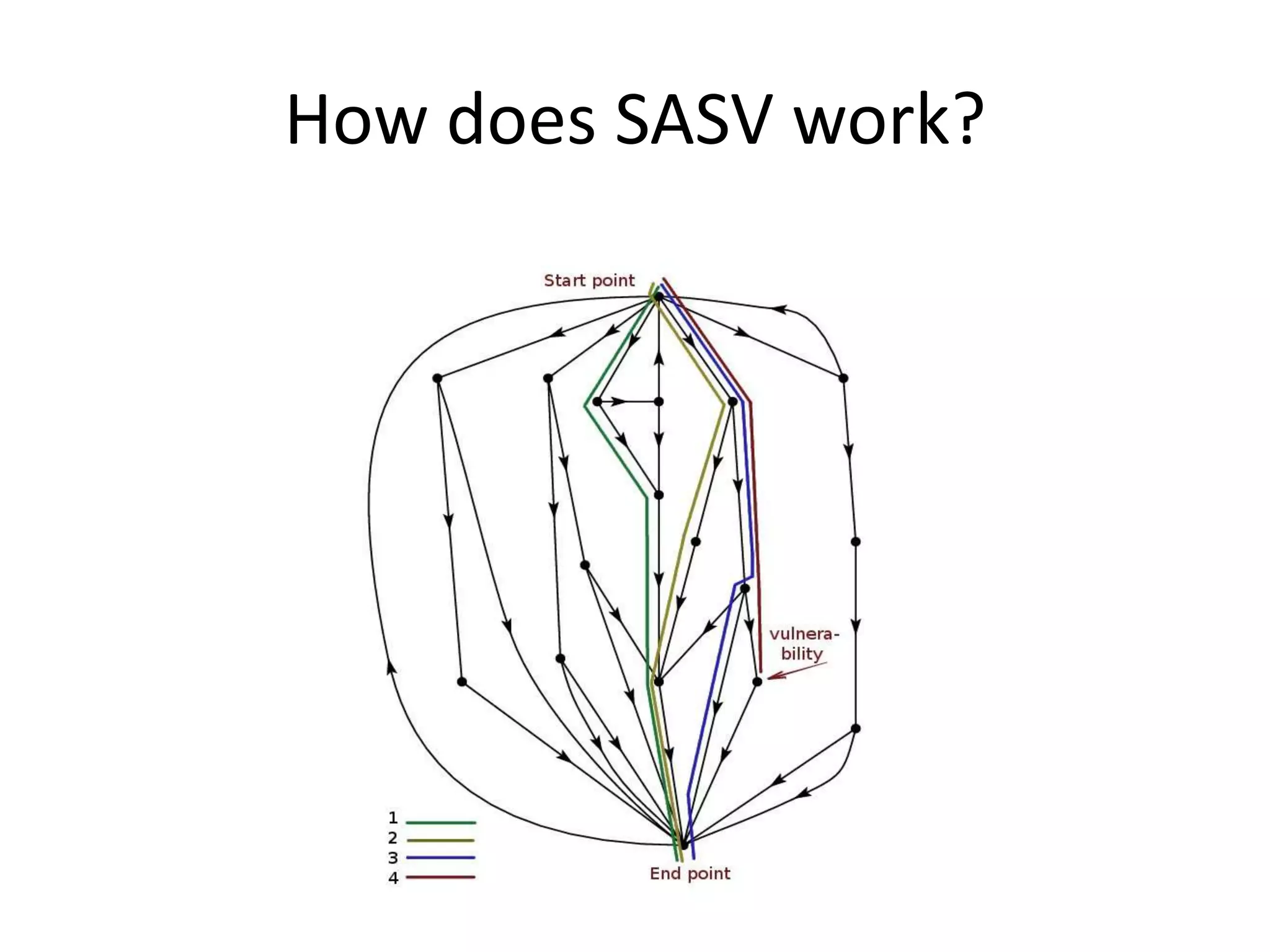
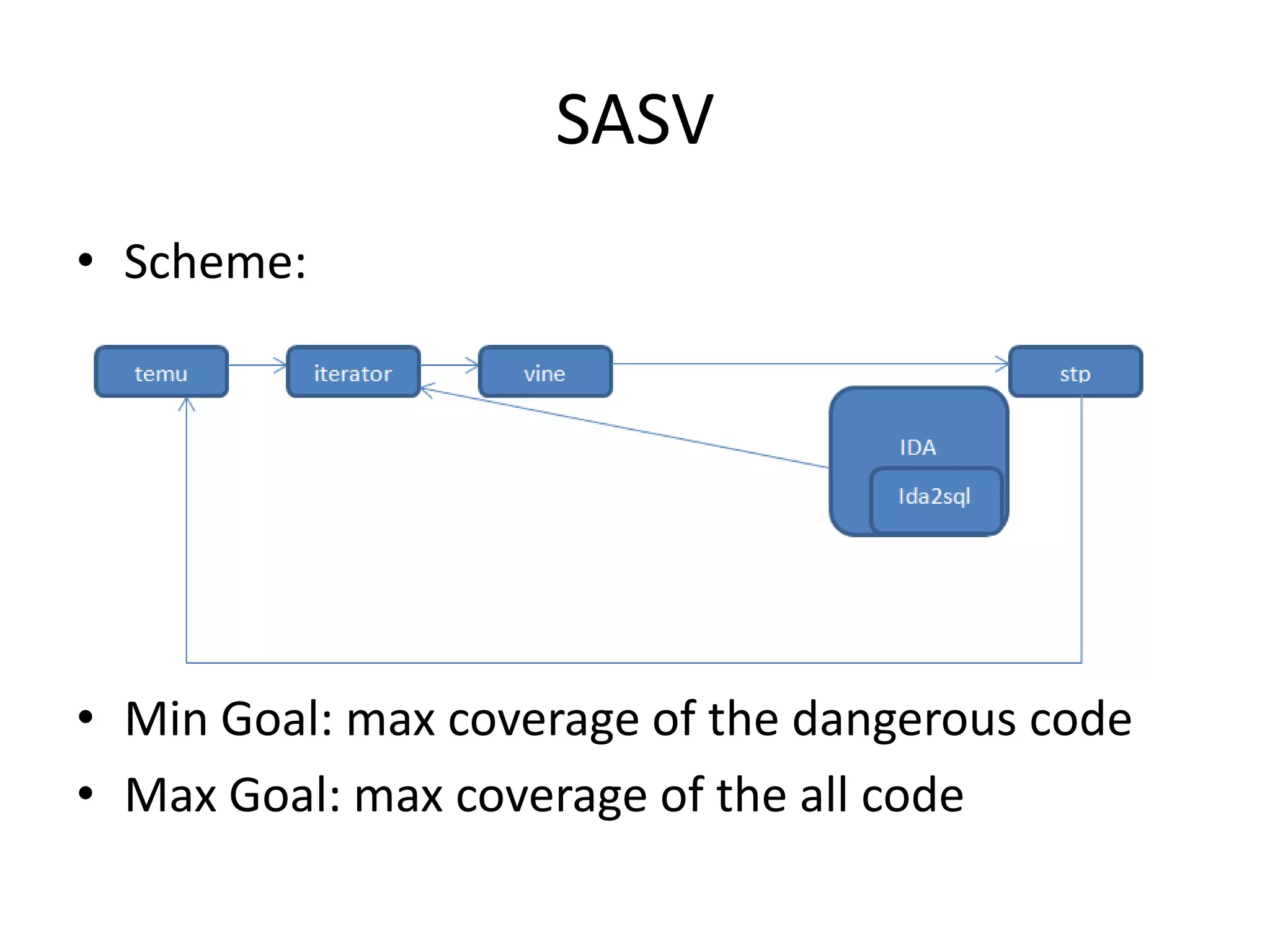
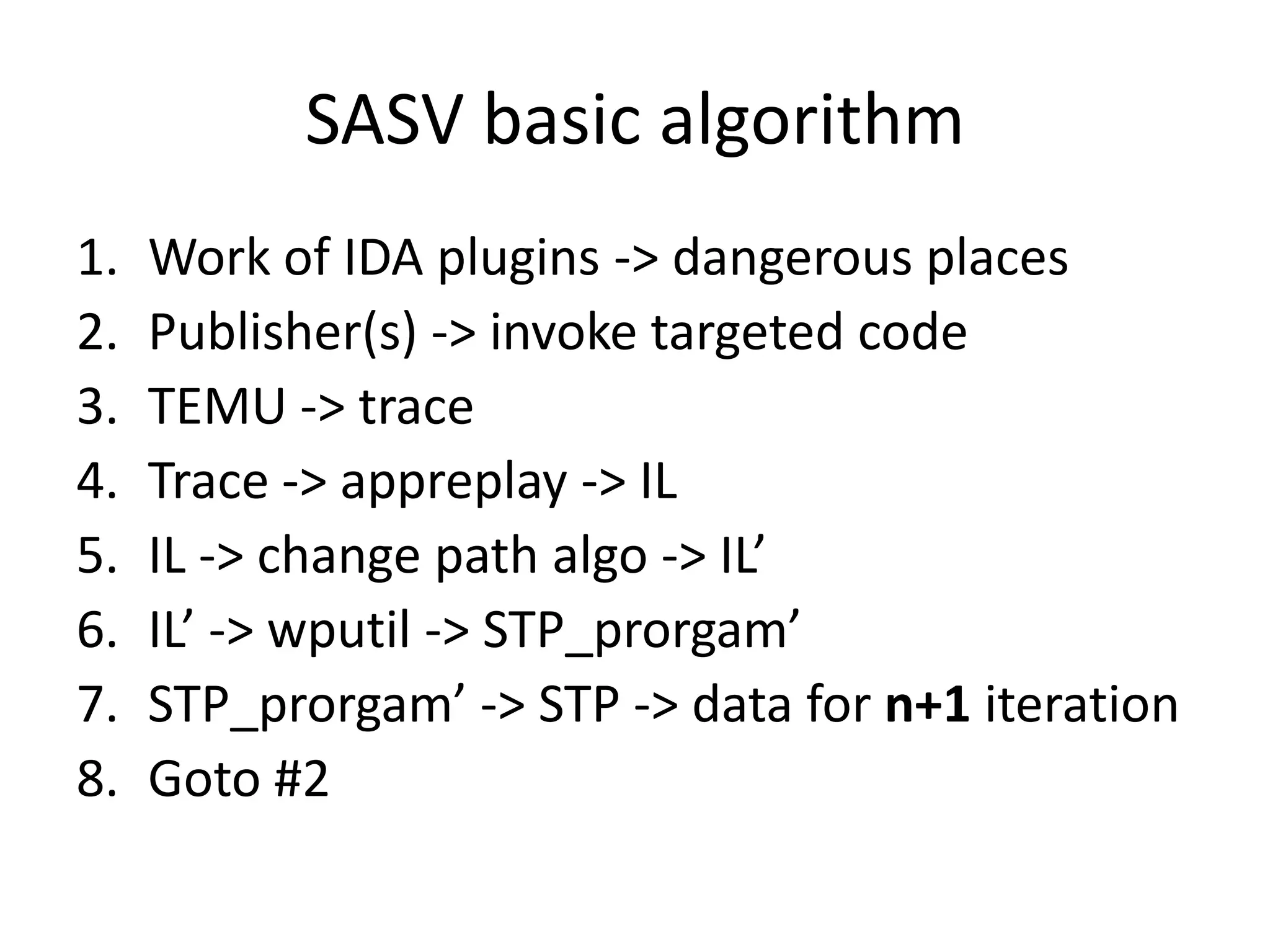
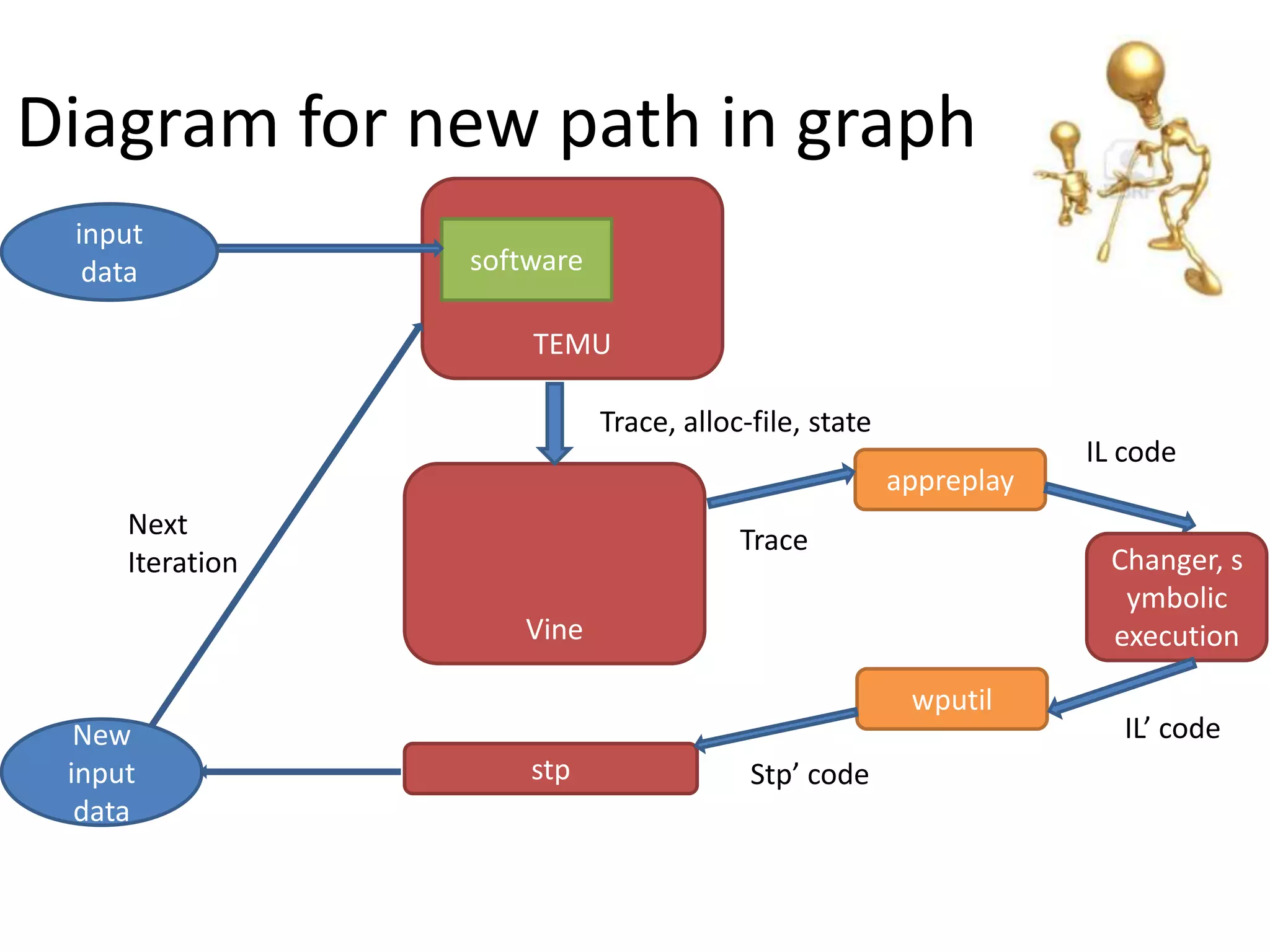
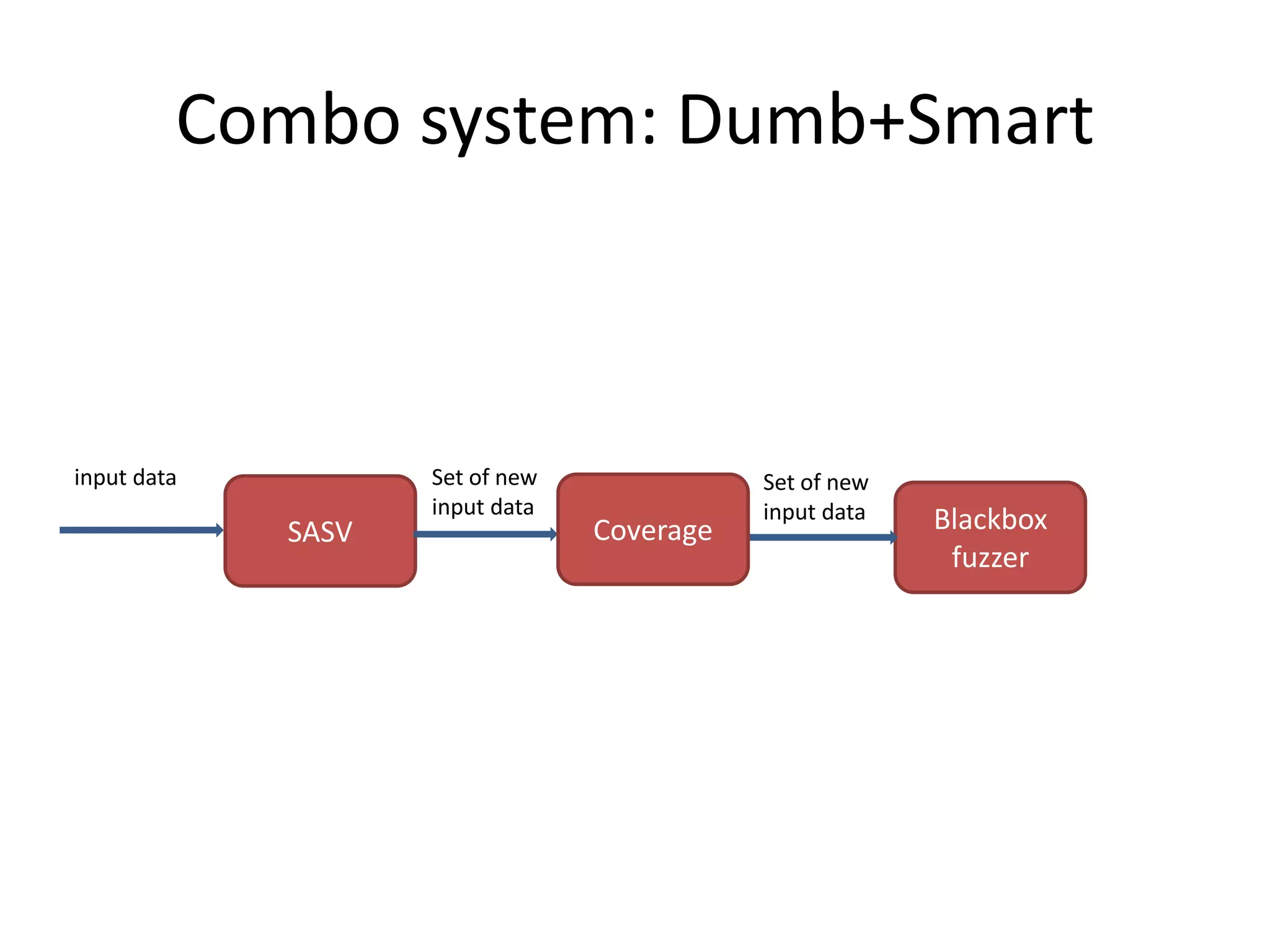
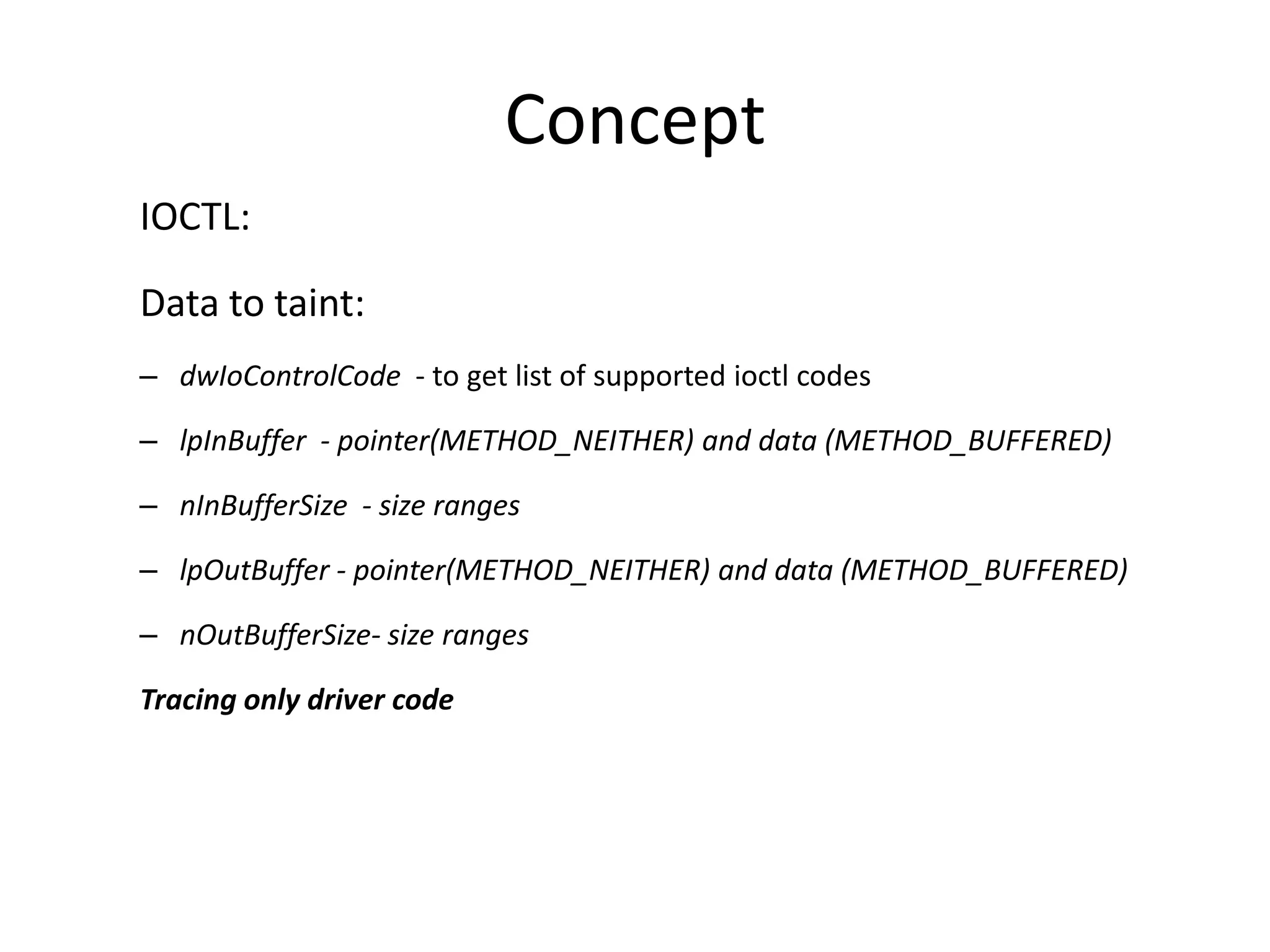
This document discusses using taint analysis to automatically find vulnerabilities. It describes Alex Bazhanyuk and Nikita Tarakanov, who work on security research projects. Their presentation covers the System of Automatic Searching for Vulnerabilities (SASV), which uses taint analysis, BitBlaze tools like TEMU and VINE, and the STP constraint solver to automatically find vulnerabilities. SASV traces target programs, converts the traces to intermediate language code, and uses path exploration and symbolic execution to generate new test inputs that maximize code coverage and have the potential to trigger vulnerabilities.


![Who is Nikita Tarakanov • Independent Security Researcher • Author of some articles in ][akep magazine • Likes to reverse engineer r0 parts • Discovered a lot of LPE vulns • Solves problems of automation of RE](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-3-2048.jpg)



![Example of disasm: fc32dcec: rep stos %eax,%es:(%edi) R@eax[0x00000000][4](R) T0 R@ecx[0x00000002][4](RCW) T0 M@0xfb7bfff8[0x00000000][4](CW) T1 {15 (1231, 69624) (1231, 69625) (1231, 69626) (1231, 69627) } fc32dcec: rep stos %eax,%es:(%edi) R@eax[0x00000000][4](R) T0 R@ecx[0x00000001][4](RCW) T0 M@0xfb7bfffc[0x00000000][4](CW) T1 {15 (1231, 69628) (1231, 69629) (1231, 69630) (1231, 69631) } fc32dcee: mov %edx,%ecx R@edx[0x0000015c][4](R) T0 R@ecx[0x00000000][4](W) T0 fc32dcf0: and $0×3,%ecx I@0×00000000[0x00000003][1](R) T0 R@ecx[0x0000015c][4](RW) T0 fc32dcf5: andl $0×0,-0×4(%ebp) I@0×00000000[0x00000000][1](R) T0 M@0xfb5ae738[0x00000002][4](RW) T0 fc32dcf9: jmp 0x00000000fc32c726 J@0×00000000[0xffffea2d][4](R) T0 fc32c726: cmpl $0×0,-0×58(%ebp) I@0×00000000[0x00000000][1](R) T0 M@0xfb5ae6e4[0x00000000][4](R) T0](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-17-2048.jpg)
![Taint info • T0 - means that the statement is not tainted. • T1 - means that the instruction tainted in curly brackets can be seen that there tainted and what it depends. • Here's an example of: • fc32dcec: rep stos% eax,% es: (% edi) R @ eax [0x00000000] [4] (R) T0 R @ ecx [0x00000001] [4] (RCW) T0 M @ 0xfb7bfffc [0x00000000] [4] (CW) T1 {15 (1231, 628) (1231, 629) (1231, 630) (1231, 631)} • 4 bits of information tainted and they depend on the offset: 628, 629, 630, 631. 1231 - this number is origin(kind of ID that TEMU plugin sets).](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-18-2048.jpg)

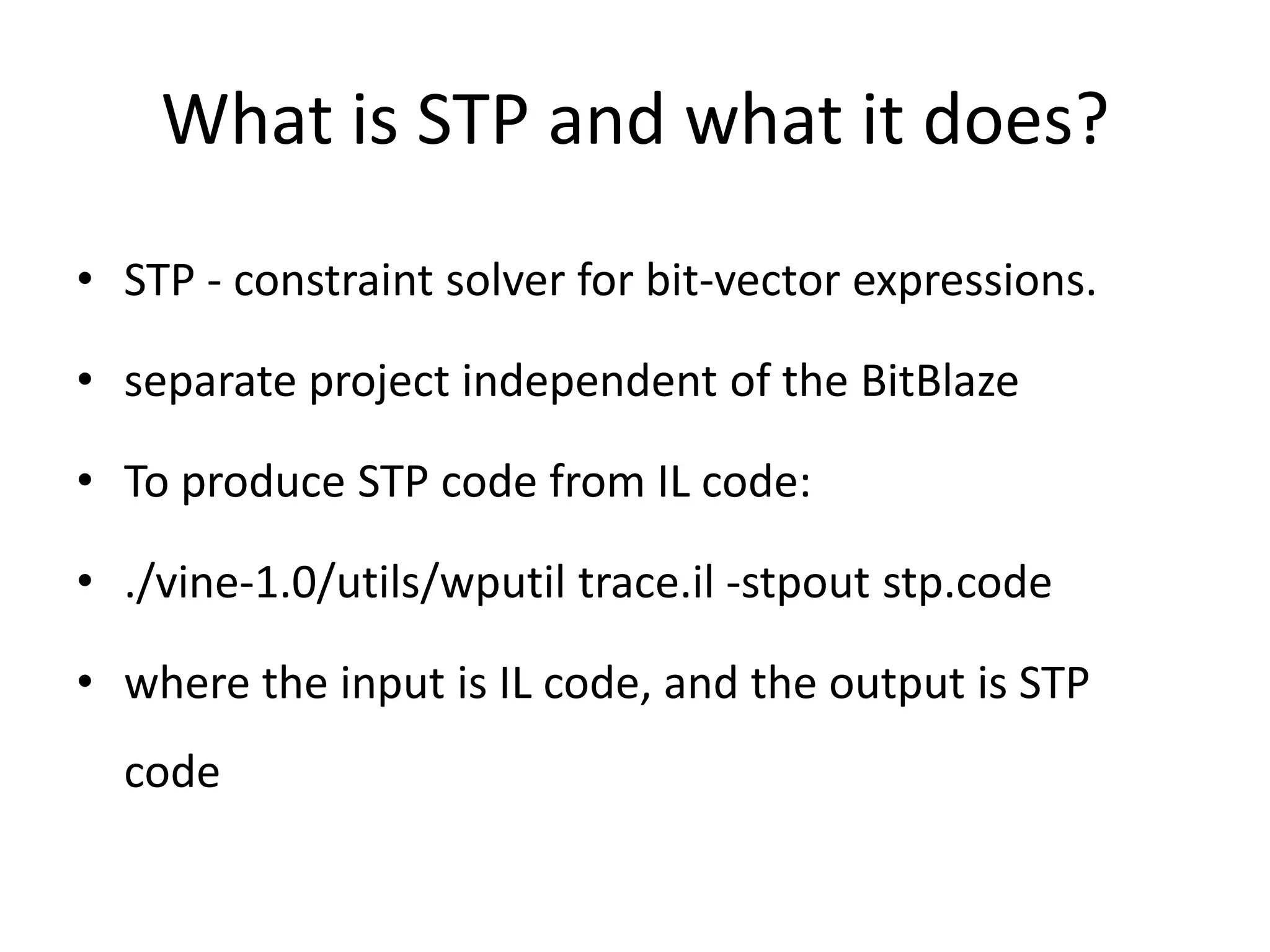
![Example of IL code: • Begins with the declaration of variables: • INPUT - it's free memory cells, those that are tested in the very beginning (back in temu), input into the program from an external source. var cond_000017_0x4010ce_00_162:reg1_t; var cond_000013_0x4010c3_00_161:reg1_t; var cond_000012_0x4010c0_00_160:reg1_t; var cond_000007_0x4010b6_00_159:reg1_t; var INPUT_10000_0000_62:reg8_t; var INPUT_10000_0001_63:reg8_t; var INPUT_10000_0002_64:reg8_t; var INPUT_10000_0003_65:reg8_t; var mem_arr_57:reg8_t[4294967296]; – memory as an array var mem_35:mem32l_t;](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-20-2048.jpg)
![T_32t2_60:reg32_t = R_EAX_5:reg32_t = R_ESP_1:reg32_t; T_32t1_59:reg32_t = 0×73657930:reg32_t; T_32t2_60:reg32_t + { 0x1c8:reg32_t; T_32t3_61:reg32_t =(( var idx_144:reg32_t; cast(mem_arr_57[T_32t1_59:reg32_t + 0:reg32_t]:reg8_t)U:reg32_t var val_143:reg8_t; << 0:reg32_t | idx_144:reg32_t = cast(mem_arr_57[T_32t1_59:reg32_t 0x12fef0:reg32_t; + 1:reg32_t]:reg8_t)U:reg32_t << 8:reg32_t) val_143:reg8_t = | cast(mem_arr_57[T_32t1_59:reg32_t INPUT_10000_0000_62:reg + 2:reg32_t]:reg8_t)U:reg32_t 8_t; << 0×10:reg32_t) | mem_arr_57[idx_144:reg32 cast(mem_arr_57[T_32t1_59:reg32_t _t + 0:reg32_t]:reg8_t = + 3:reg32_t]:reg8_t)U:reg32_t << 0×18:reg32_t cast((val_143:reg8_t & ; R_EAX_5:reg32_t = 0xff:reg8_t) >> T_32t3_61:reg32_t; 0:reg8_t)L:reg8_t; }](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-21-2048.jpg)
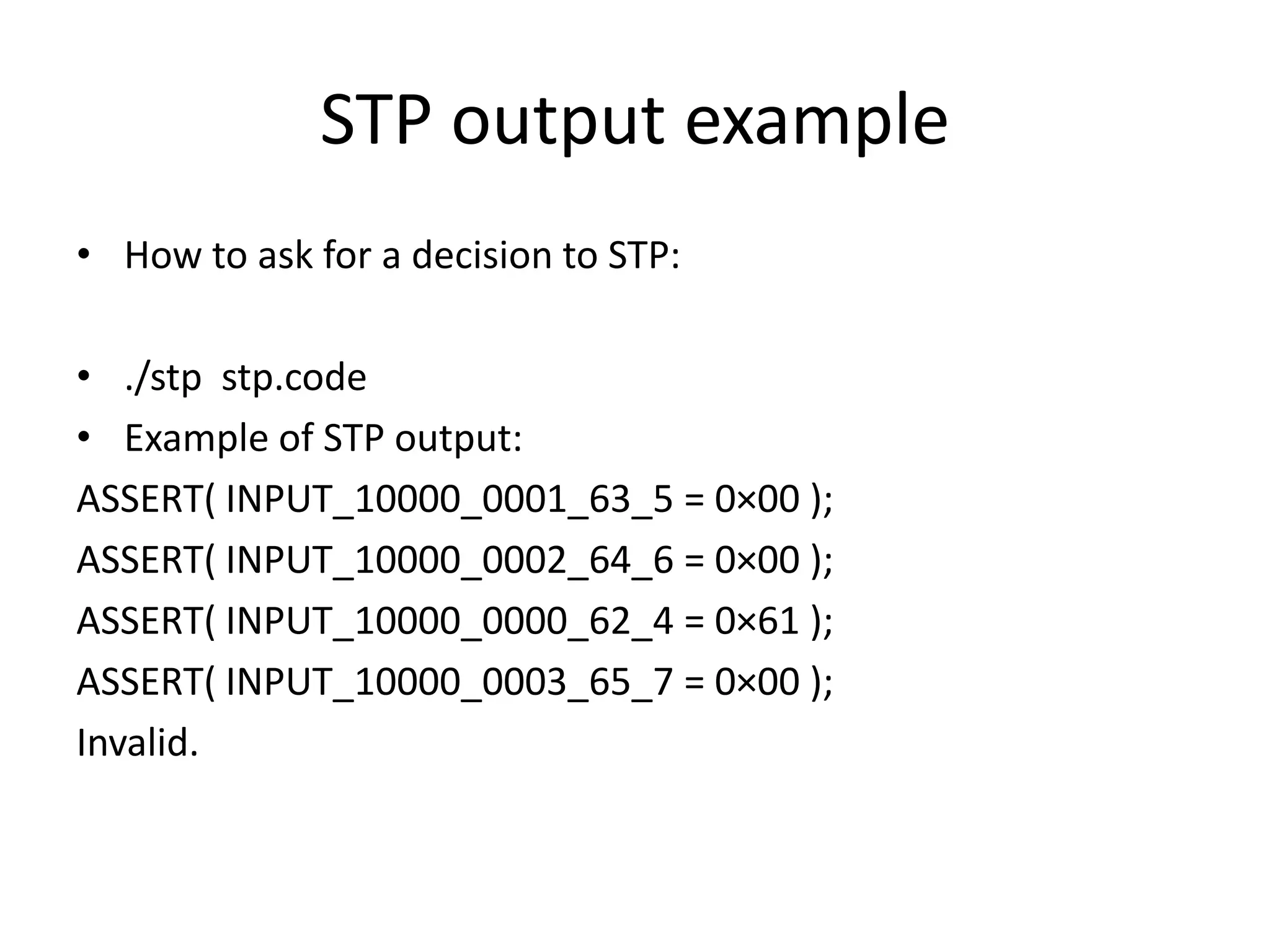
![STP program example mem_arr_57_8 : ARRAY BITVECTOR(64) OF BITVECTOR(8); INPUT_10000_0000_62_4 : BITVECTOR(8); ASSERT( 0bin1 = (LET R_EAX_5_232 = 0hex73657930 IN (LET idx_144_233 = 0hex0012fef0 IN (LET val_143_234 = INPUT_10000_0000_62_4 IN (LET mem_arr_57_393 = (mem_arr_57_8 WITH [(0bin00000000000000000000000000000000 @ BVPLUS(32, idx_144_233,0hex00000000))] := (val_143_234;0hexff)[7:0]) ……. IN (cond_000017_0x4010ce_00_162_392;0bin1)))))))); Is this expression false? QUERY (FALSE); And give a counter example: COUNTEREXAMPLE;](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-23-2048.jpg)





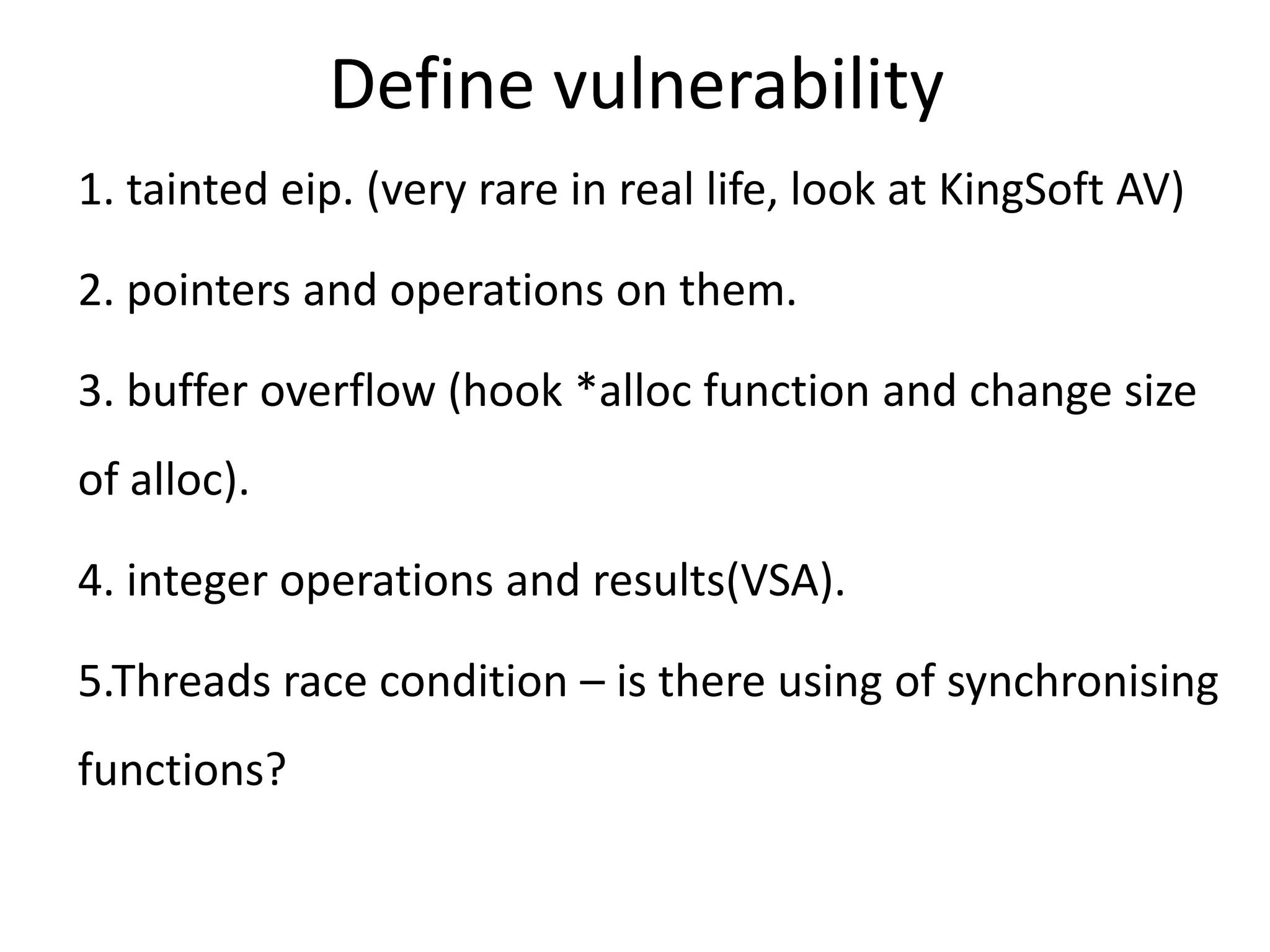
![Define Vulnerability (Memory corruption) • var = var1 operation var2 • Mem = alloc(heap, stack)(var) • Mem[var3] = var4 • Could var3 > var (write out-of-bounds) ?](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-39-2048.jpg)
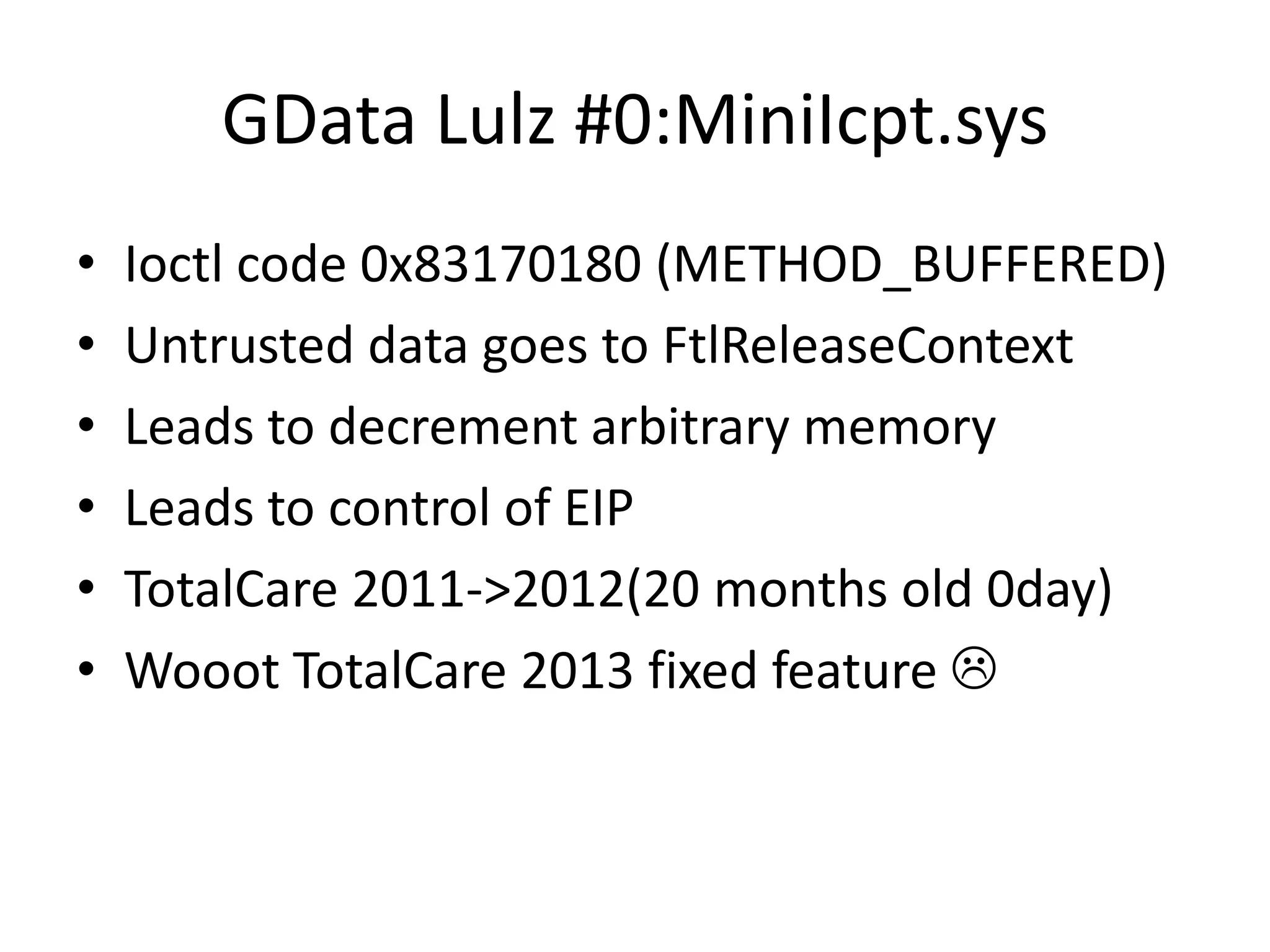


![TrendMicro tmtdi.sys #1 • .text:0001D881 mov edi, [ebx+0Ch] • .text:0001D884 push edi ; our buffer • .text:0001D885 call esi ; MmIsAddressValid • .text:0001D887 test al, al • .text:0001D889 jz loc_1DDAB • .text:0001D88F push [ebp+output_buff_size] • .text:0001D892 push edi • .text:0001D893 push offset rules_list • .text:0001D898 call ioctl_0x220044_vuln • [..]](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-48-2048.jpg)
![TrendMicro tmtdi.sys #1 • .text:000156EA mov ebx, [ebp+our_buffer_size_controlled] • .text:000156ED mov [ebp+NewIrql], al • .text:000156F0 mov eax, dword_22CA0 • .text:000156F5 mov edx, offset dword_22CA0 • .text:000156FA cmp eax, edx • .text:000156FC jz short loc_15748 • [..] • .text:00015700 mov ecx, [eax+0Ch] • .text:00015703 mov [ebx], ecx • .text:00015705 mov ecx, [eax+10h] • .text:00015708 mov [ebx+4], ecx • .text:0001570B mov ecx, [eax+14h] • .text:0001570E mov [ebx+8], ecx write outside of the pool chunk • .text:00015711 mov ecx, [eax+18h] • .text:00015714 mov [ebx+0Ch], ecx](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-49-2048.jpg)
![TrendMicro tmtdi.sys #2 • .text:0001D704 cmp [ebp+inbuff_size], 2AAh • .text:0001D70B jb loc_1DDAB • .text:0001D711 mov esi, 4D0h • .text:0001D716 cmp [ebp+output_buff_size], esi • .text:0001D719 jb loc_1DDAB • .text:0001D71F push 746D74h ; Tag • .text:0001D724 push esi ; NumberOfBytes • .text:0001D725 push 0 ; PoolType • .text:0001D727 call ds:ExAllocatePoolWithTag • [..]](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-51-2048.jpg)
![TrendMicro tmtdi.sys #2 • .text:0001D74B push edi ; pool_mem_const_size • .text:0001D74C lea eax, [ebp+output_buff_size] • .text:0001D74F push eax ; output_buff_size • .text:0001D750 push [ebp+NewIrql] ; inbuff • .text:0001D753 push 220030h ; ioctl_code • .text:0001D758 call ioctl_several_ioctl_codes • [..] • .text:00014918 mov esi, [ebp+output_buff_size] • [..] • .text:00014977 push dword ptr [esi] ; • .text:00014979 push 0 ; • .text:0001497B push [ebp+pool_mem_const_size] ; • .text:0001497E call memset](https://image.slidesharecdn.com/abazhanyukntarakanovphdays2012-120619032557-phpapp01/75/The-System-of-Automatic-Searching-for-Vulnerabilities-or-how-to-use-Taint-Analysis-to-find-vulnerabilities-52-2048.jpg)