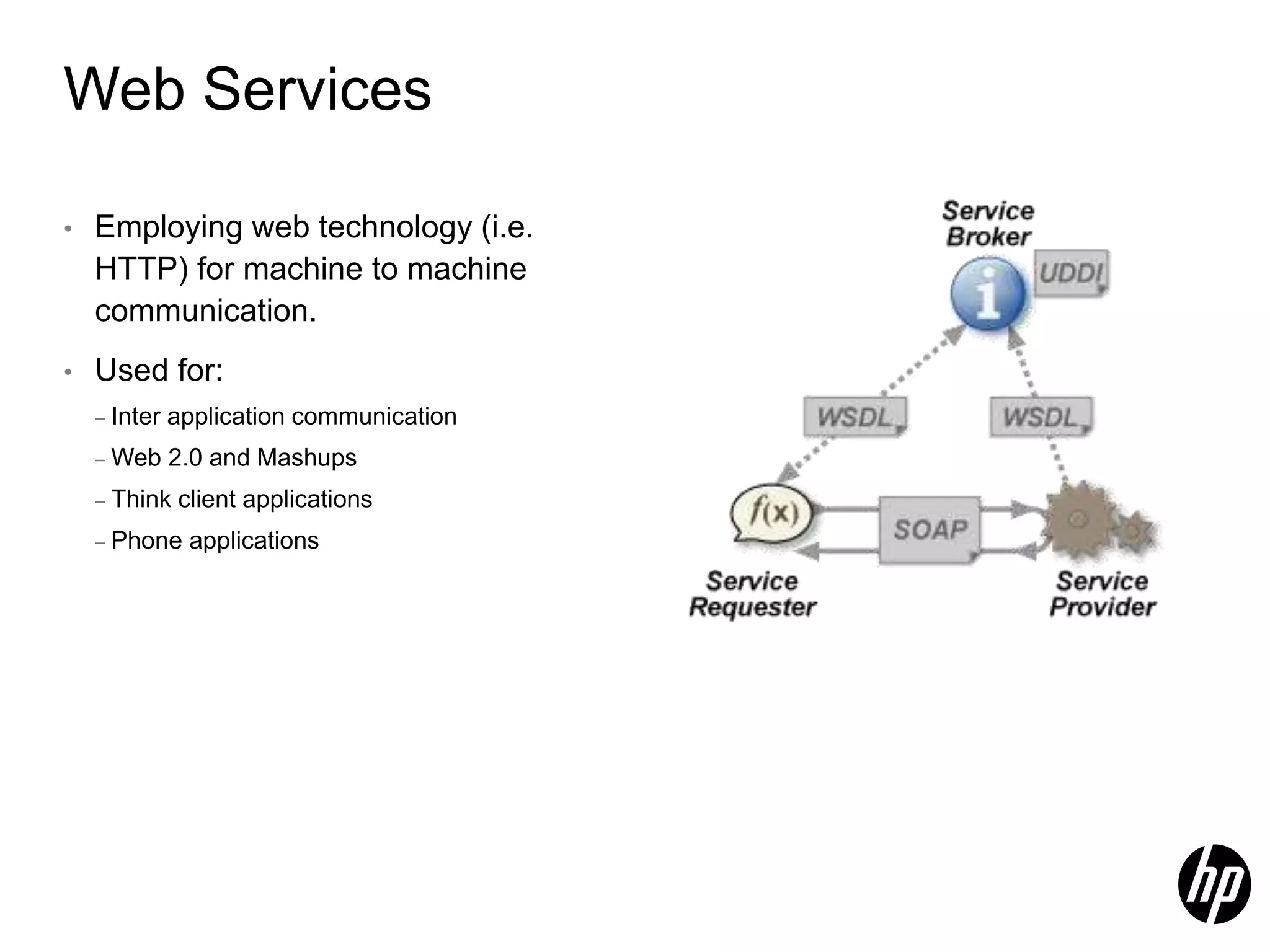
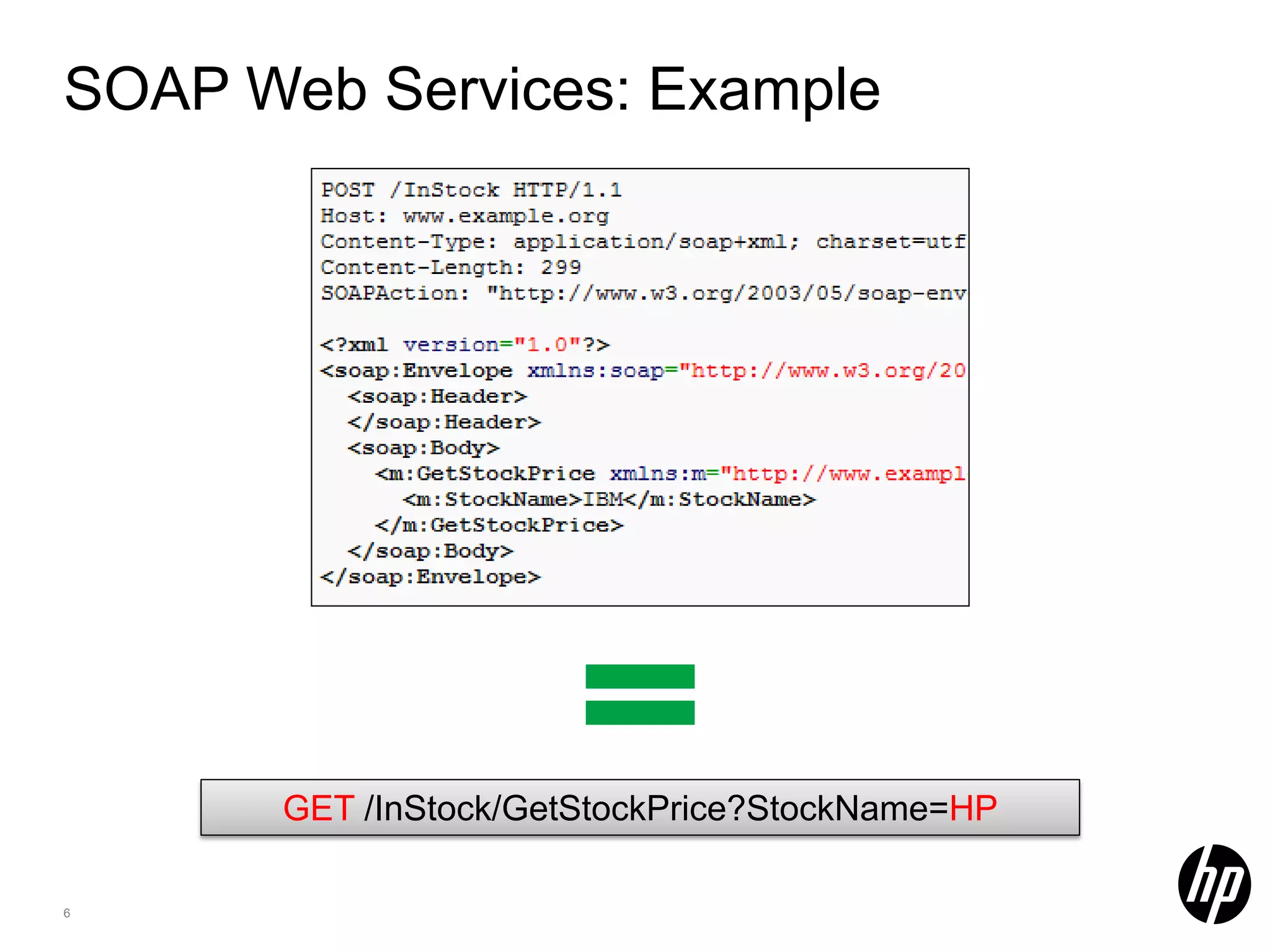
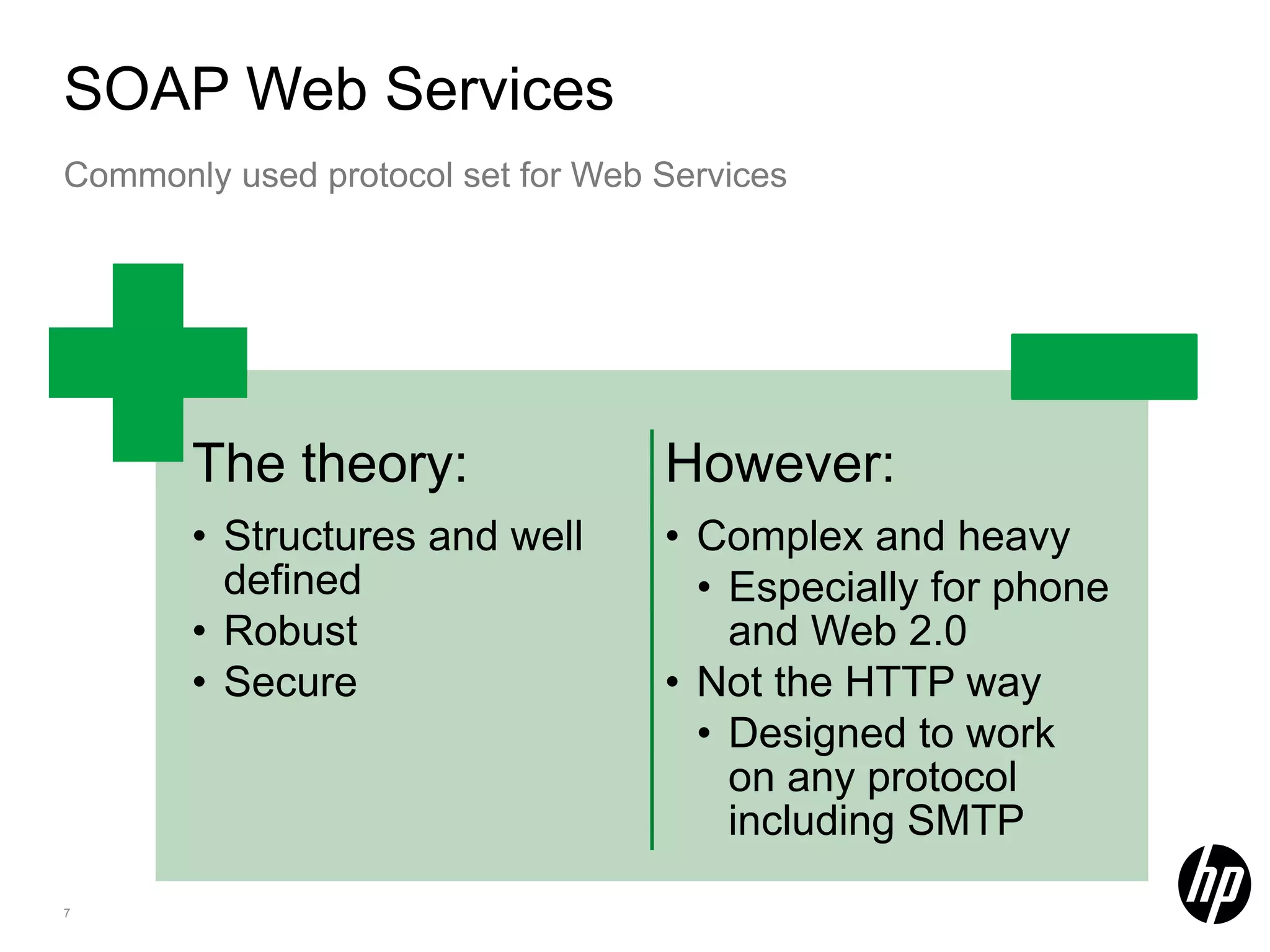
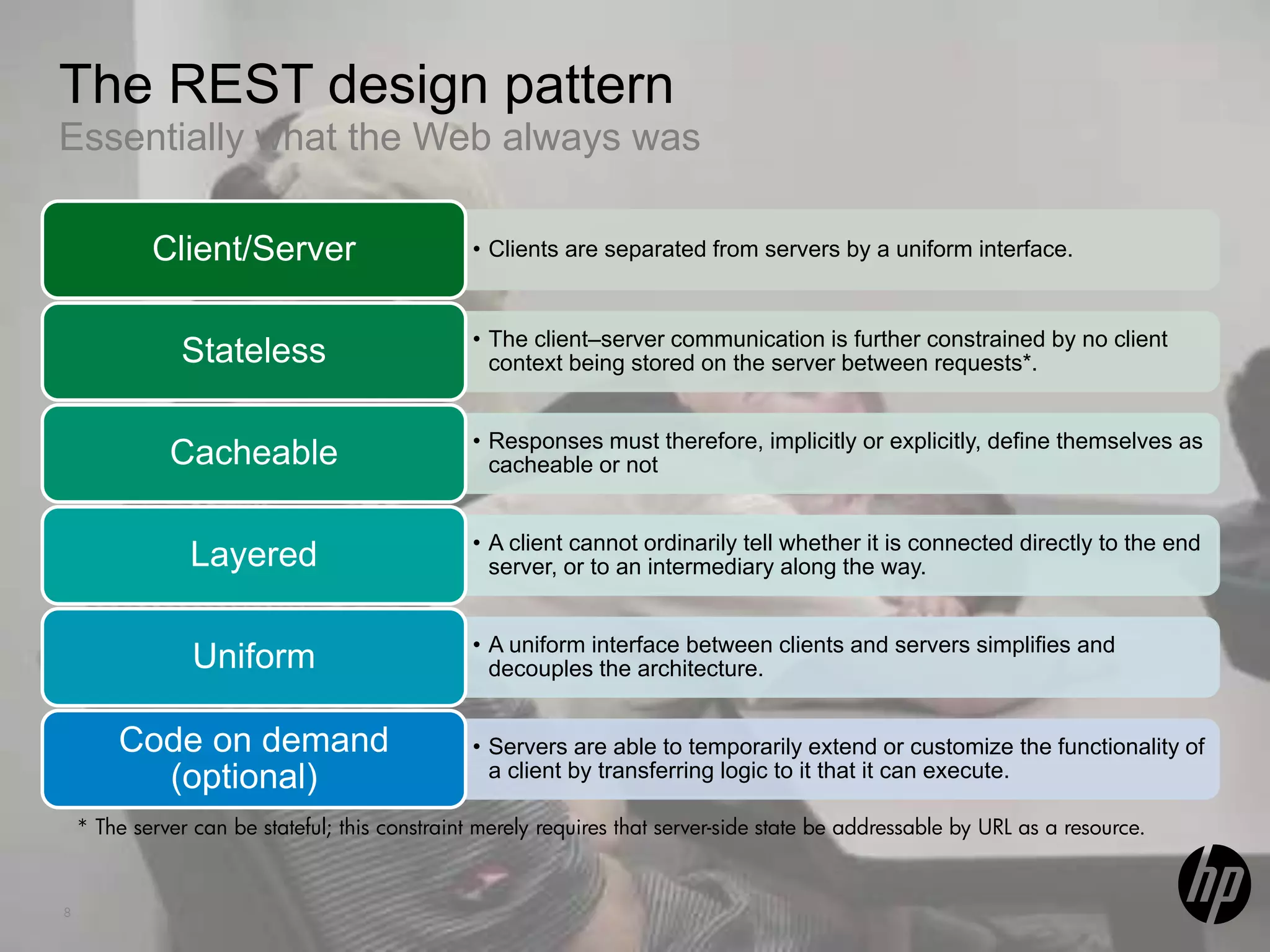
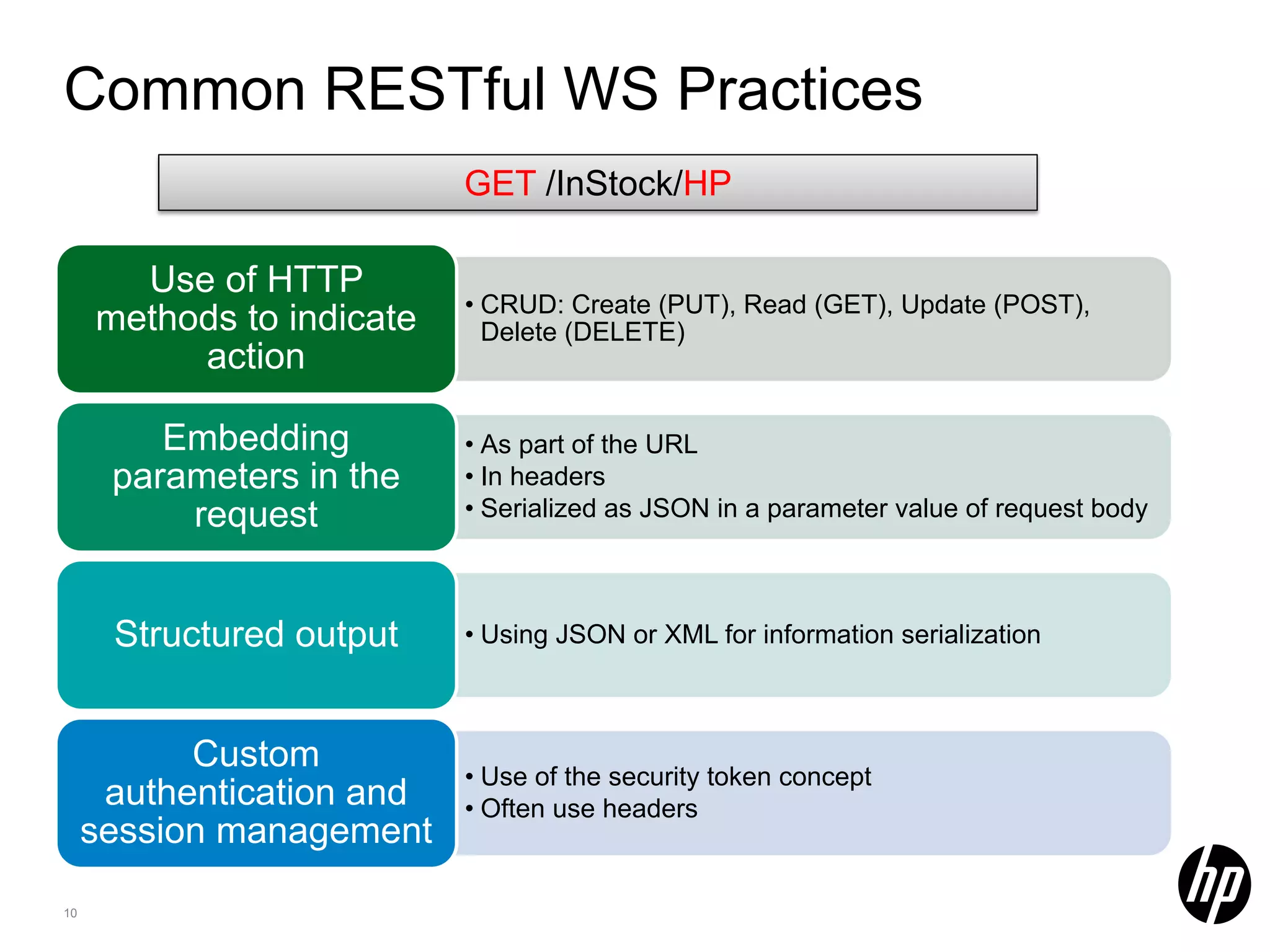
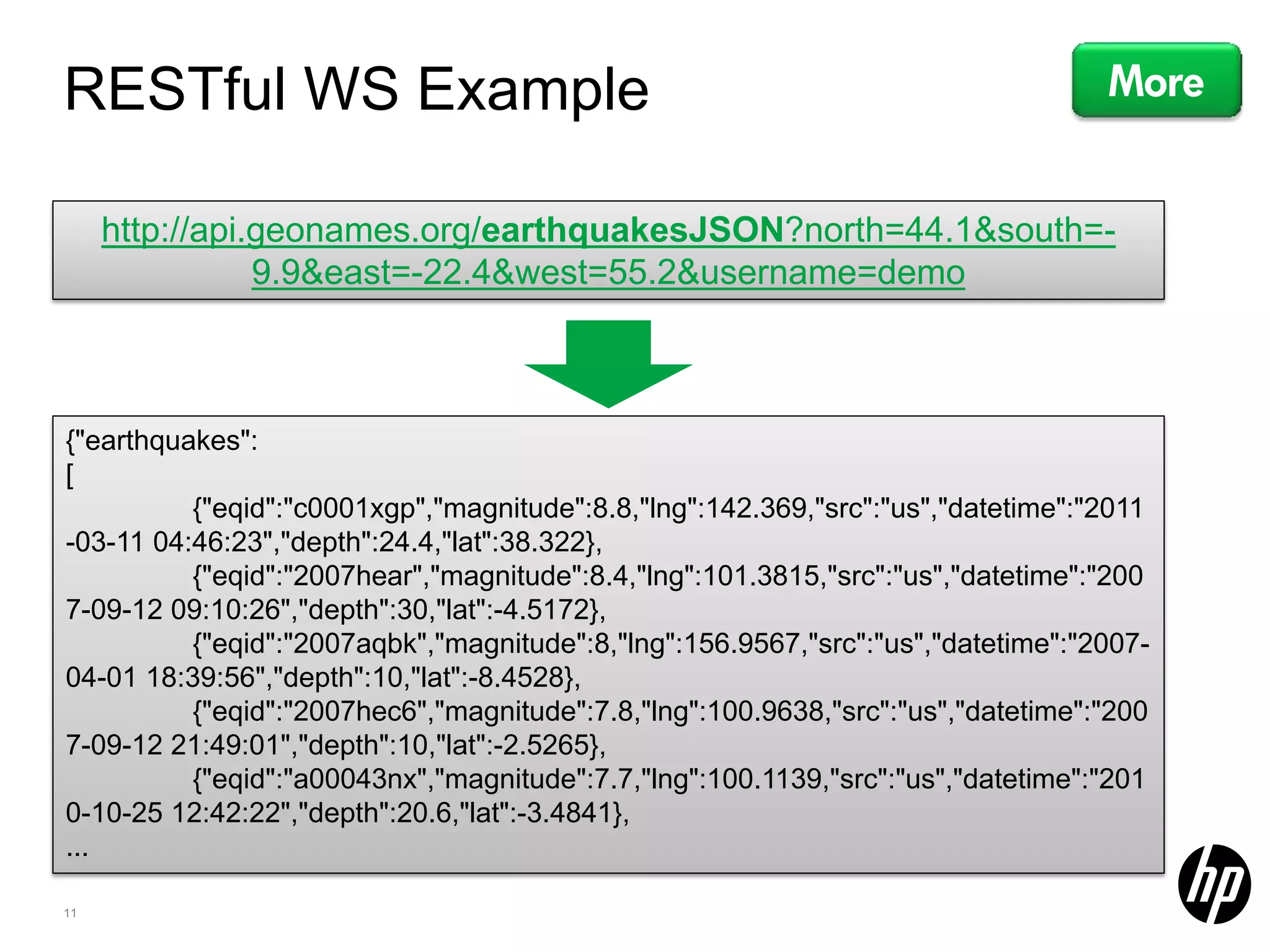
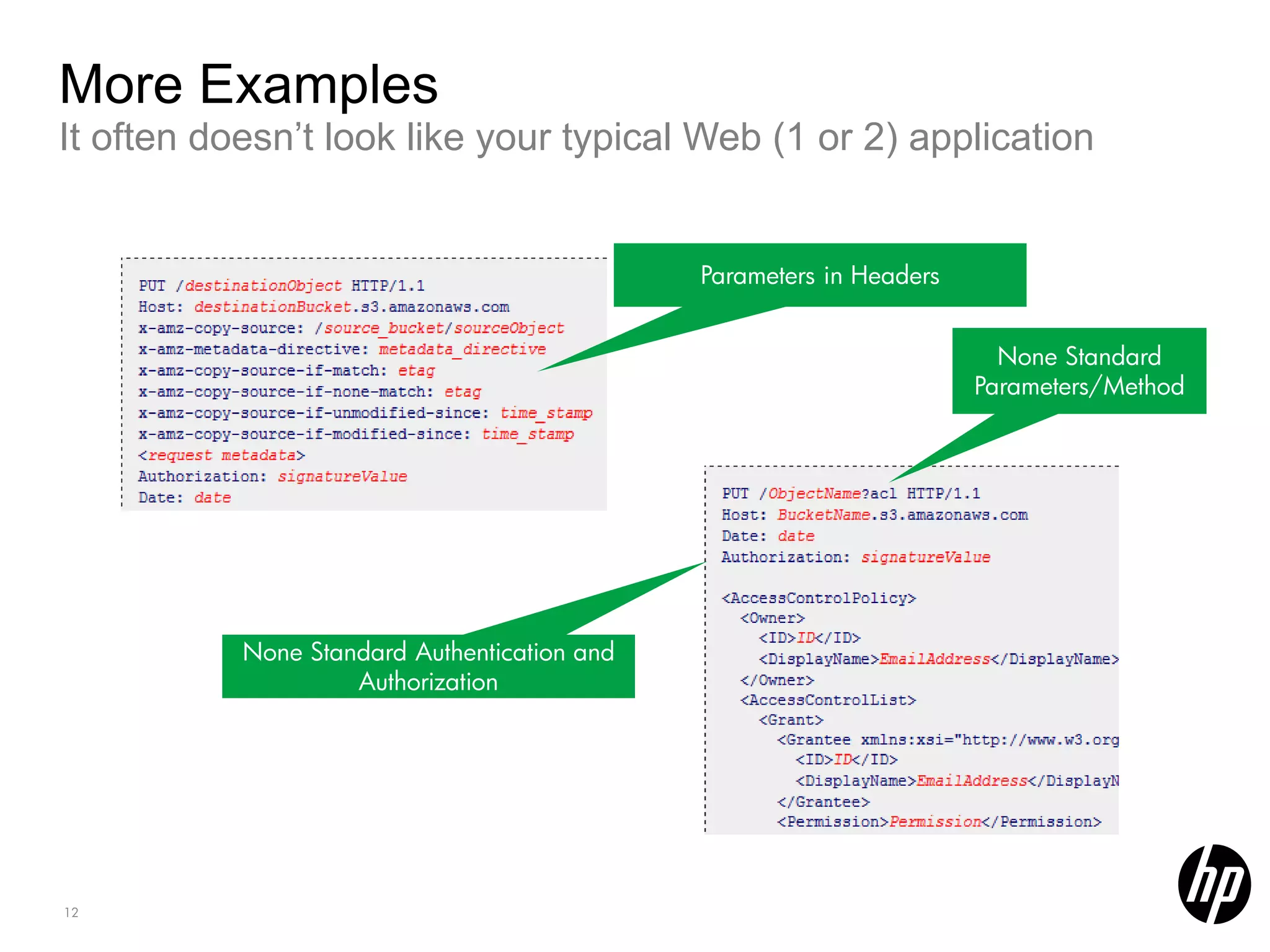
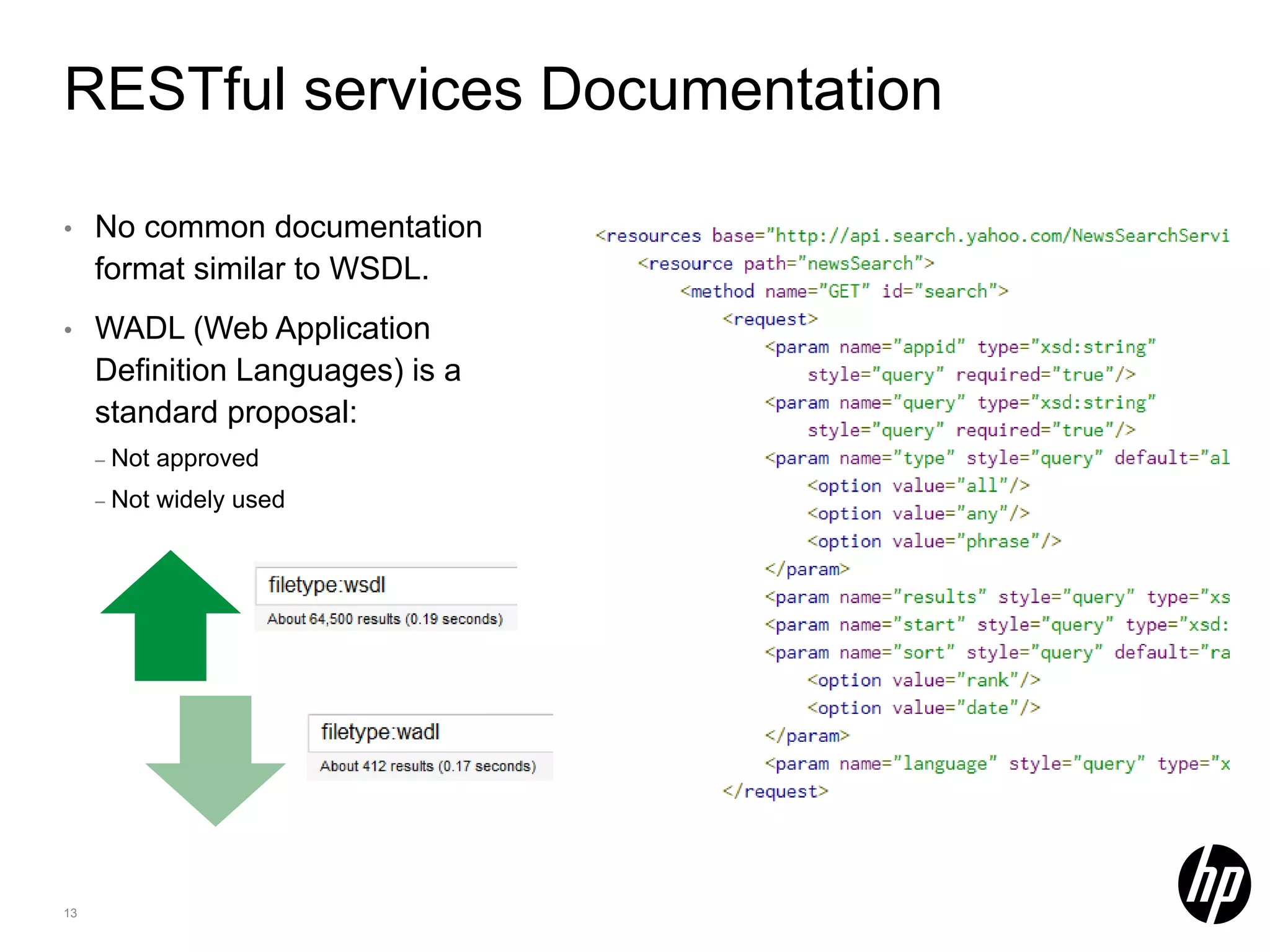
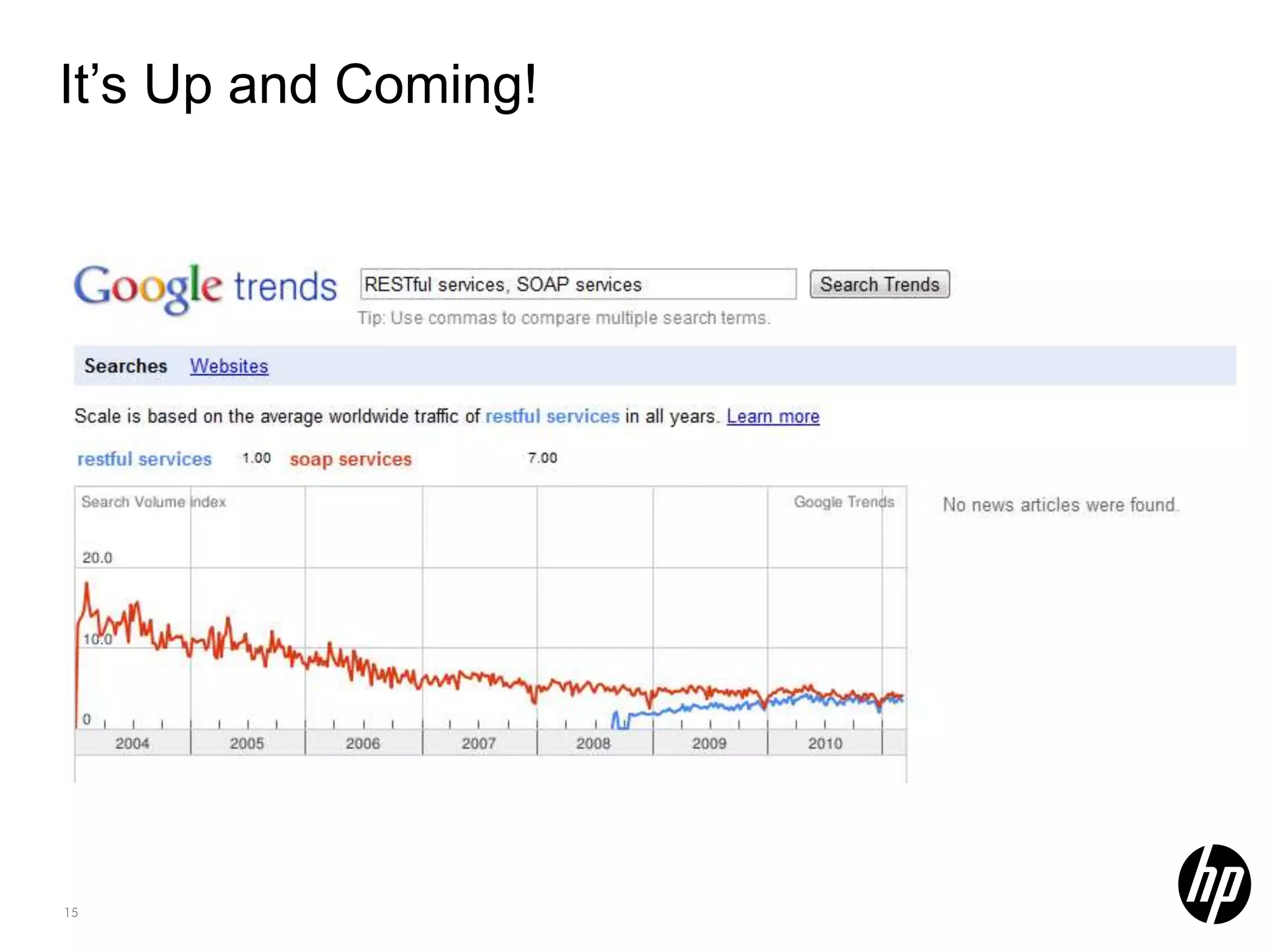
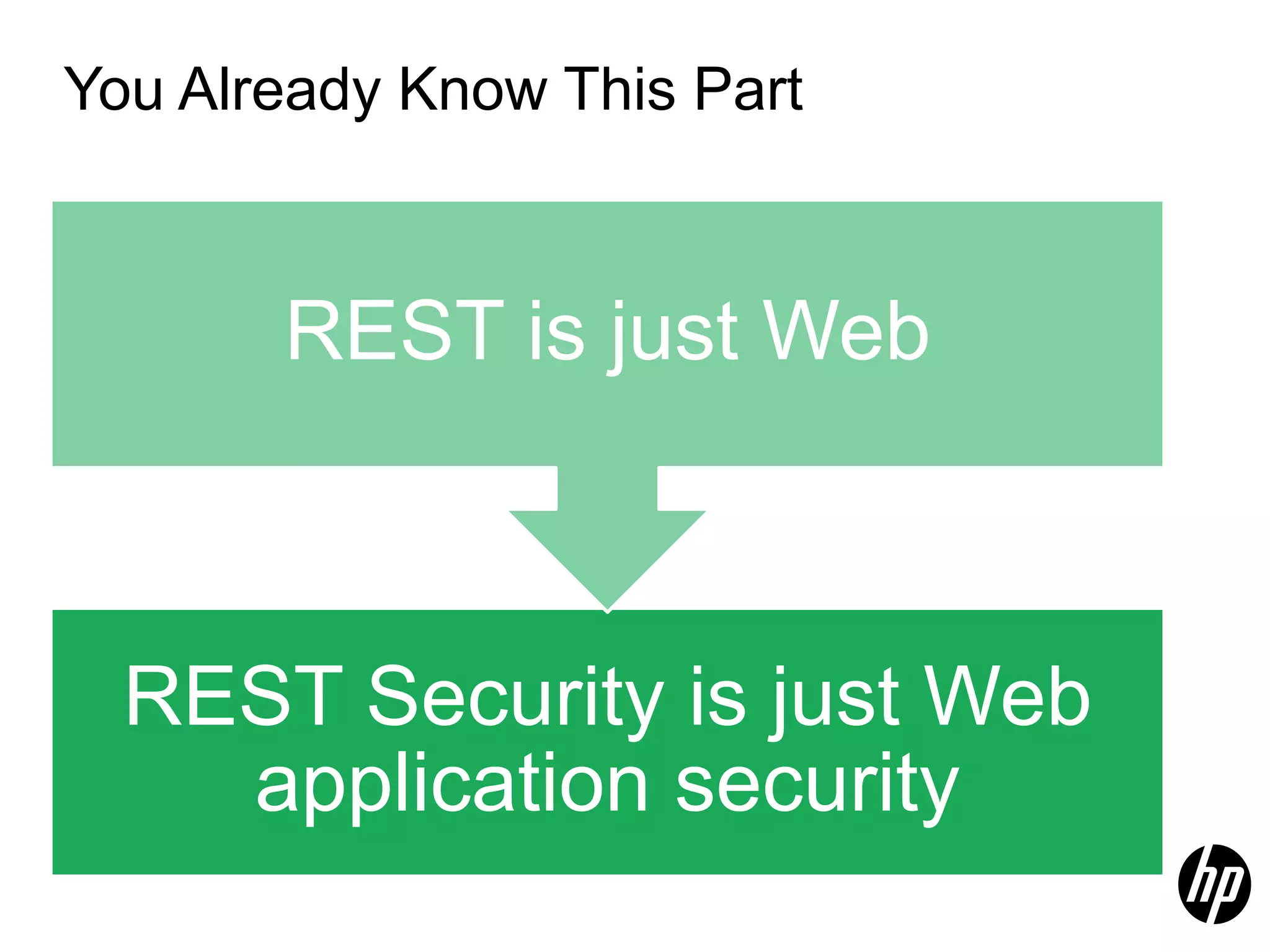
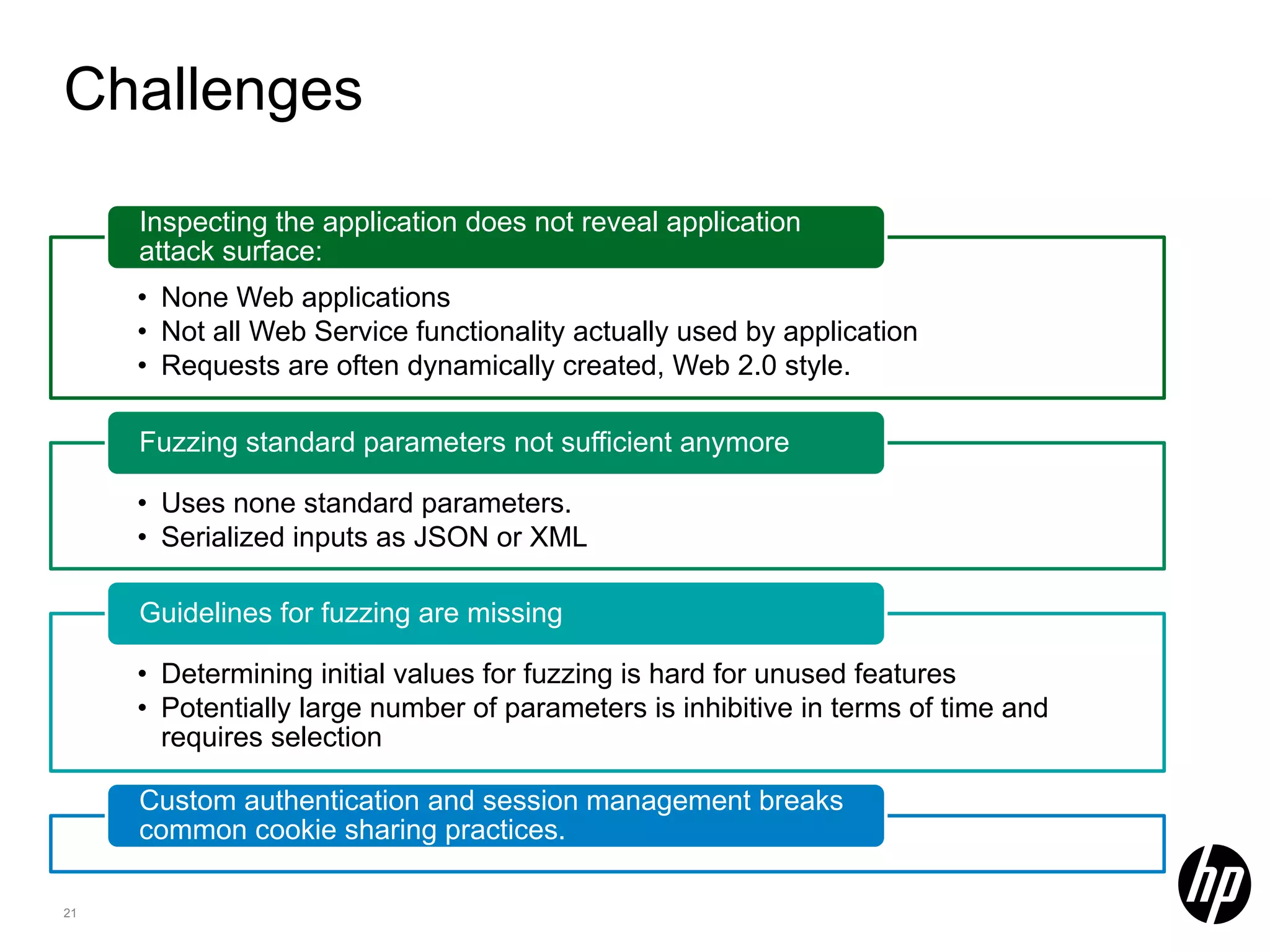
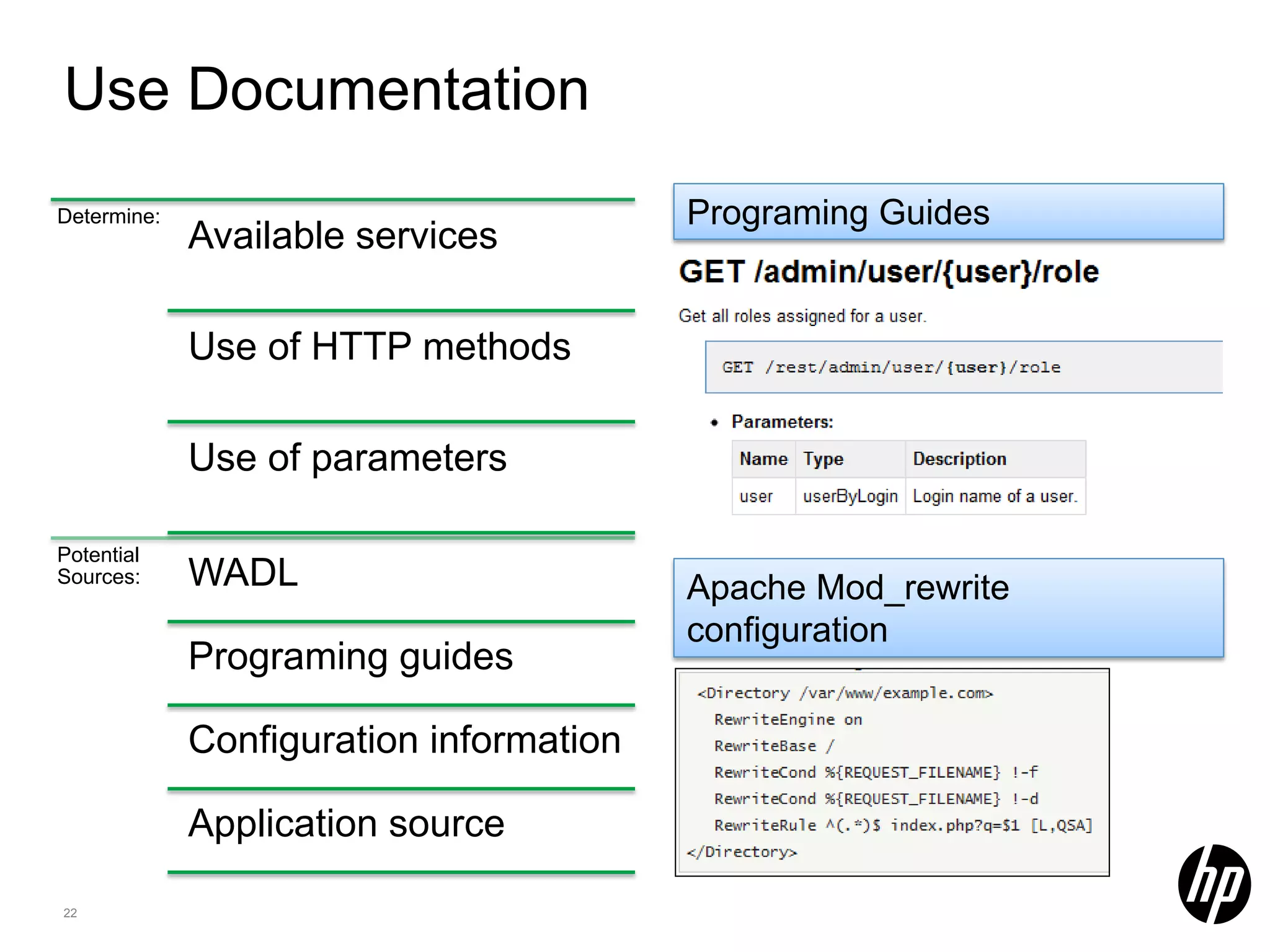
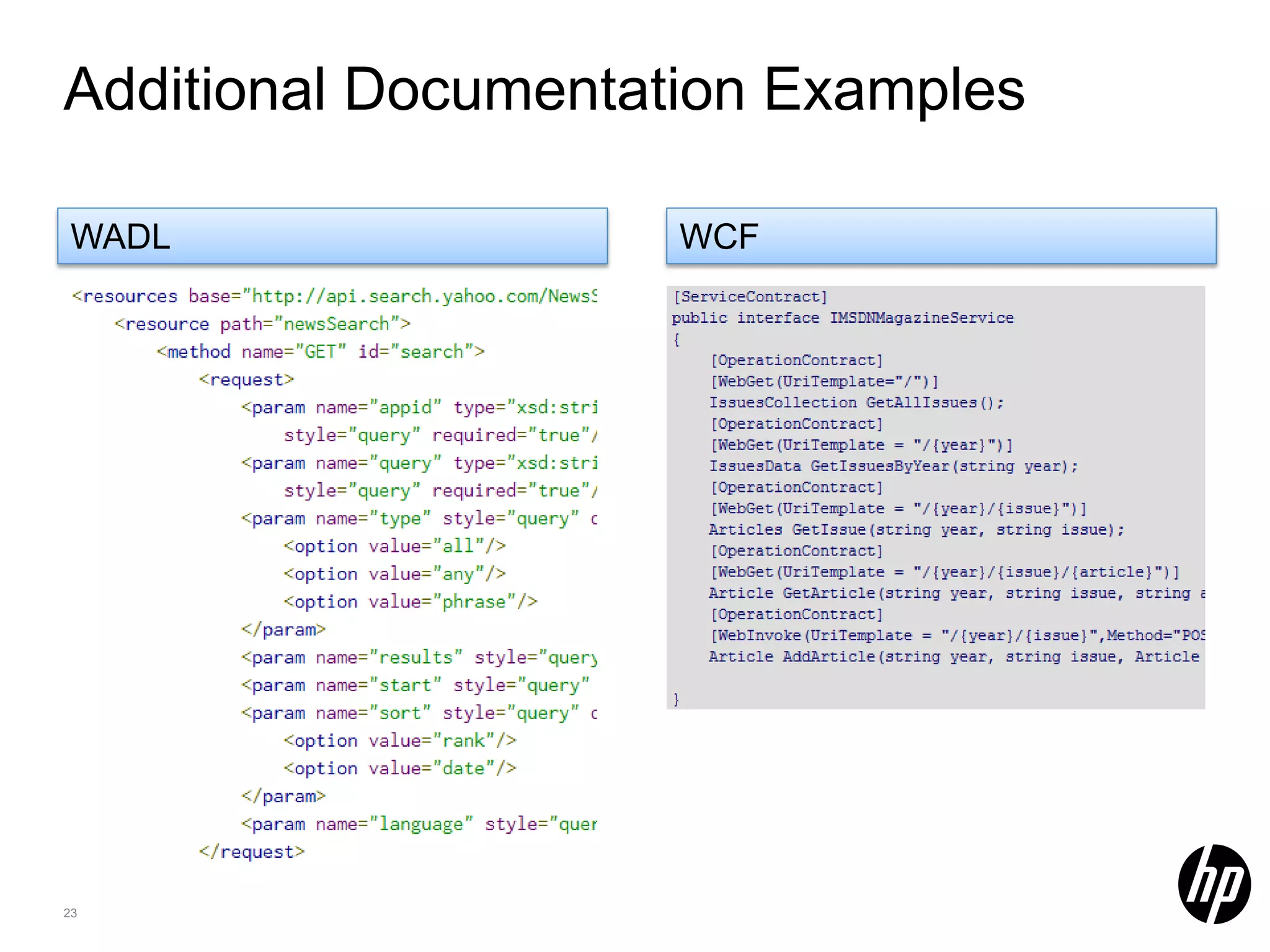
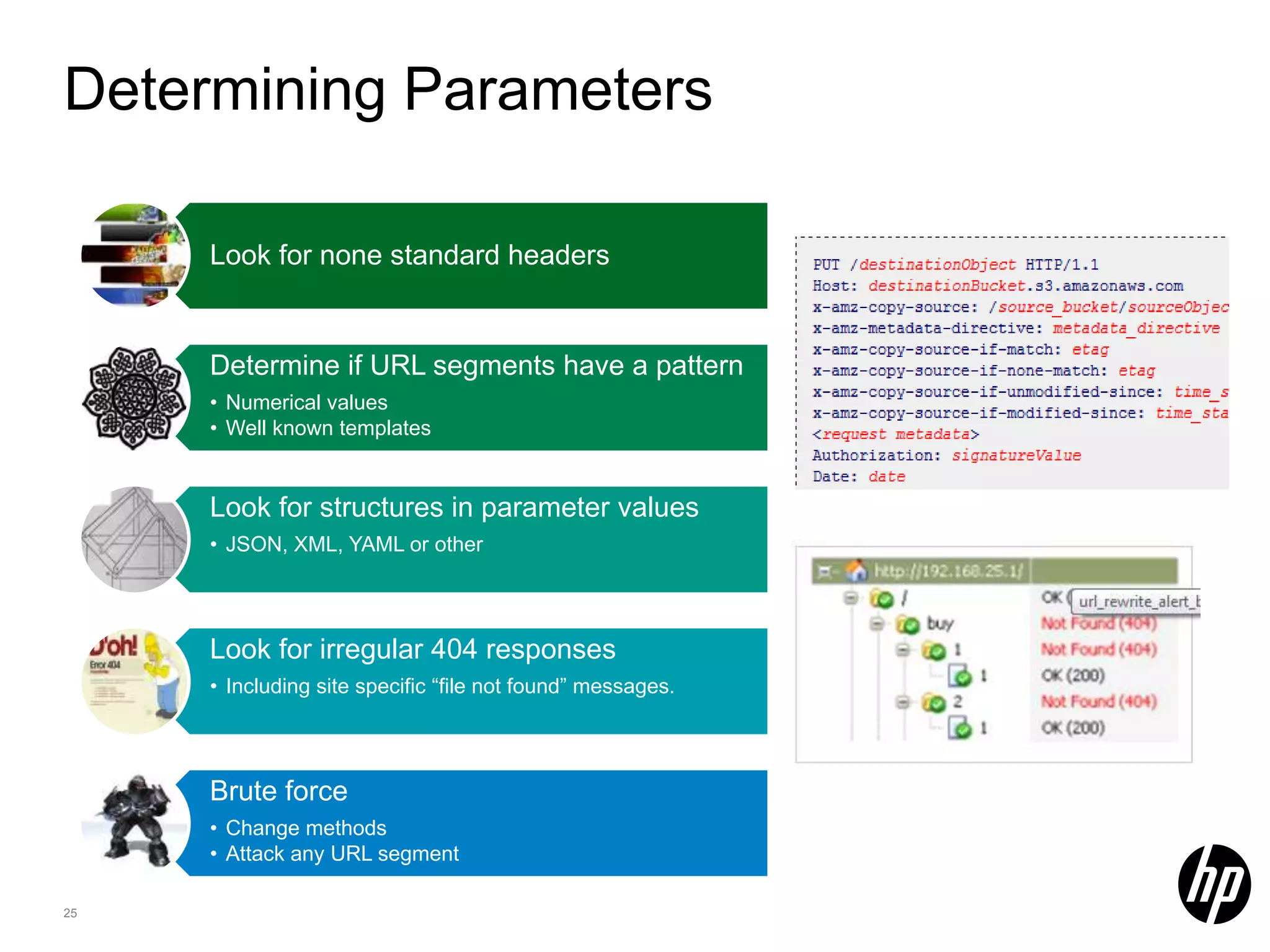
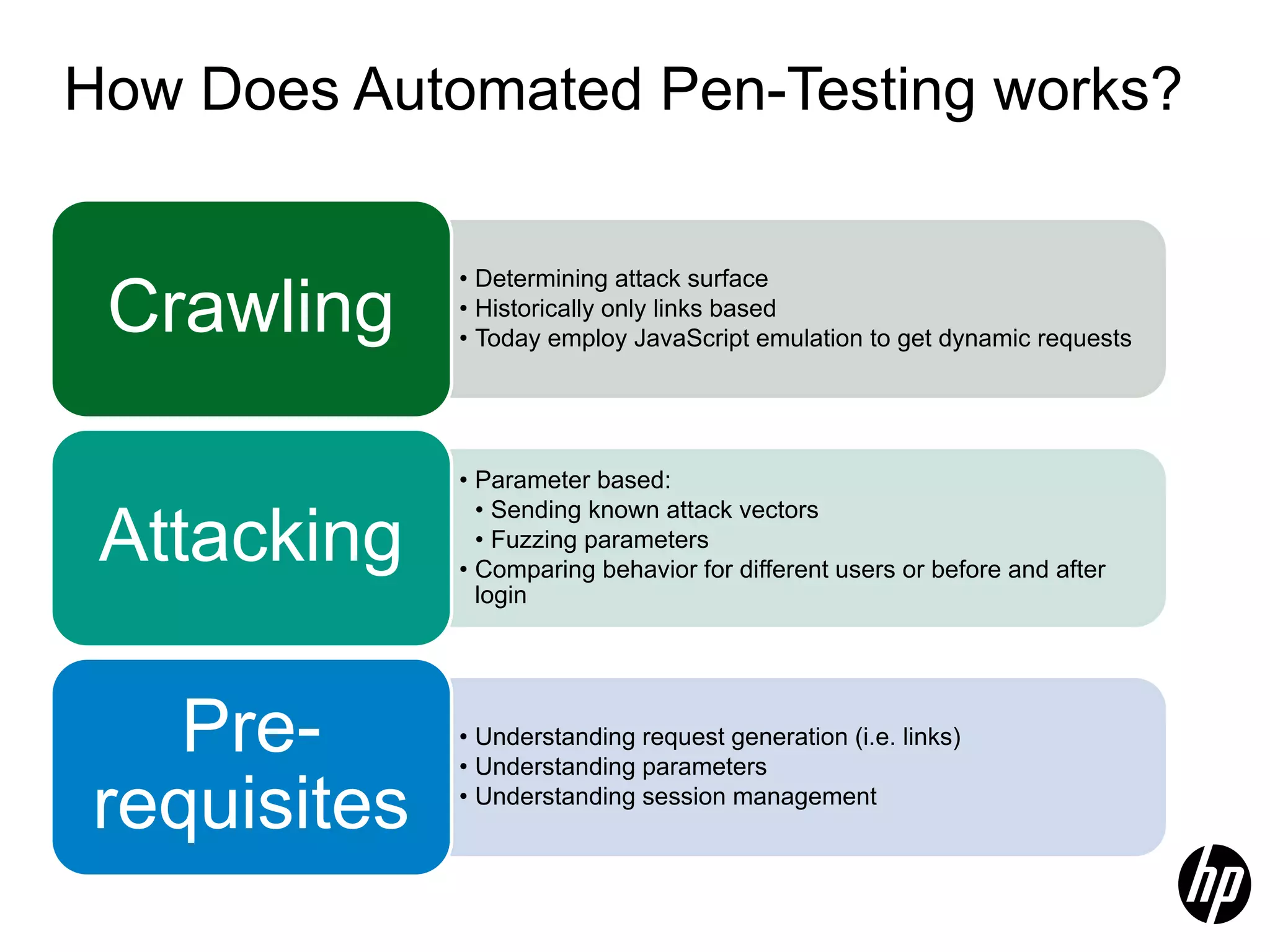
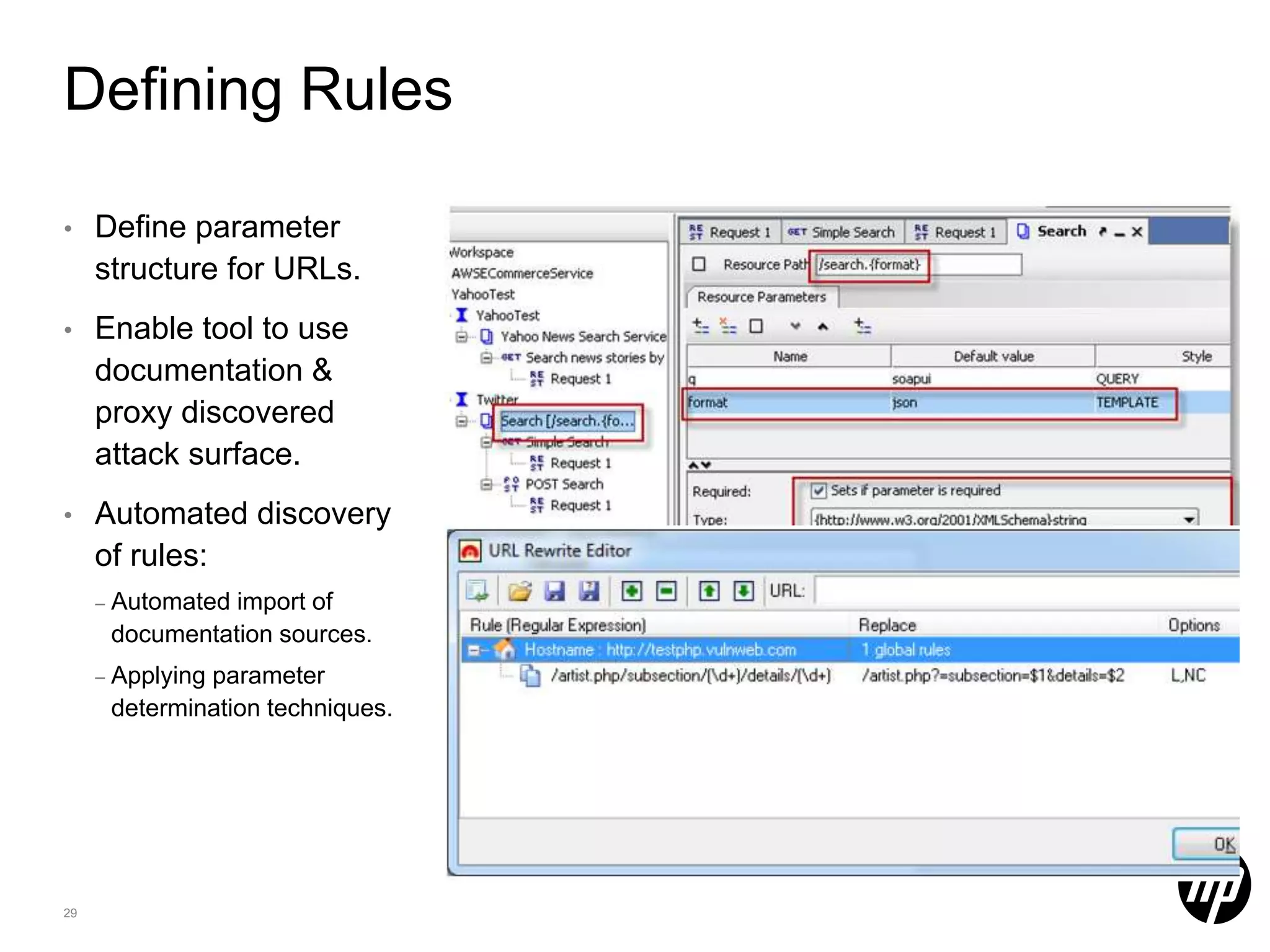
This document discusses security testing for RESTful applications. It begins with an introduction to RESTful web services and how they differ from SOAP web services in using HTTP methods to indicate actions and embedding parameters in requests. It notes challenges in testing RESTful applications including that documentation may not reveal the full attack surface and requests can be dynamically generated. It recommends using documentation, proxies, and fuzzing to determine parameters and potential vulnerabilities. The document concludes by discussing how automated pen testing works by crawling to determine the attack surface through both links and emulated JavaScript to find dynamic requests.