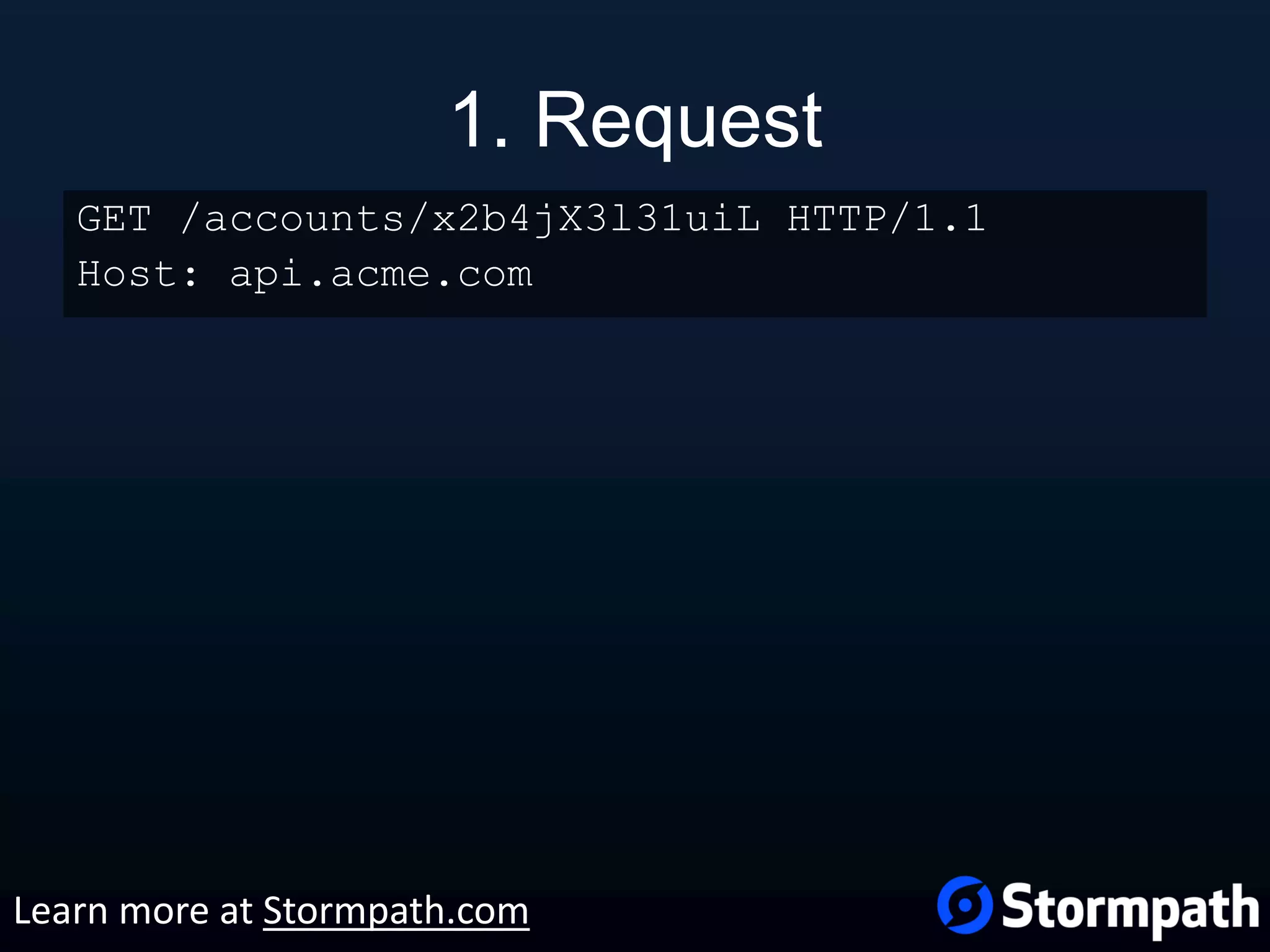
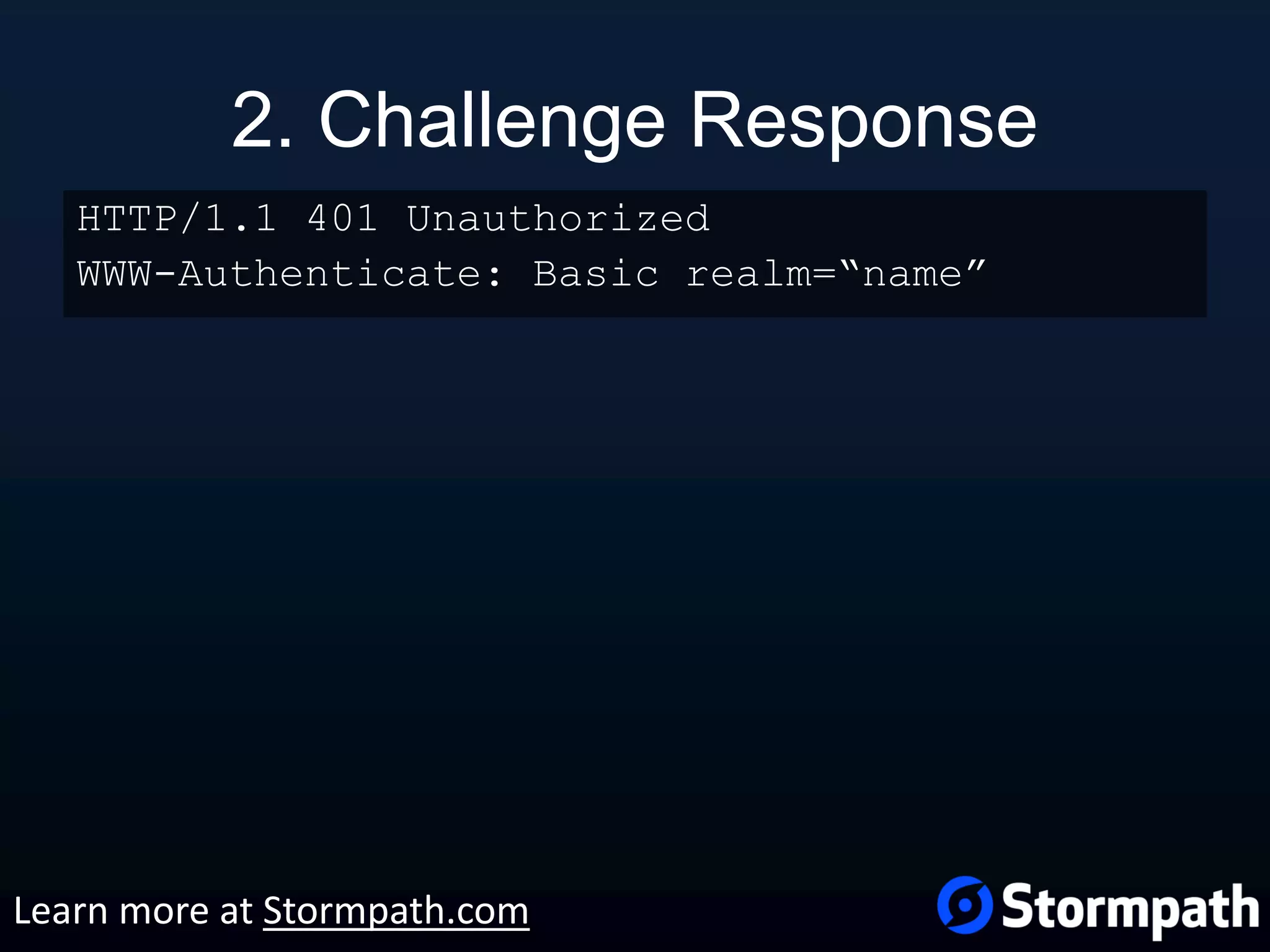
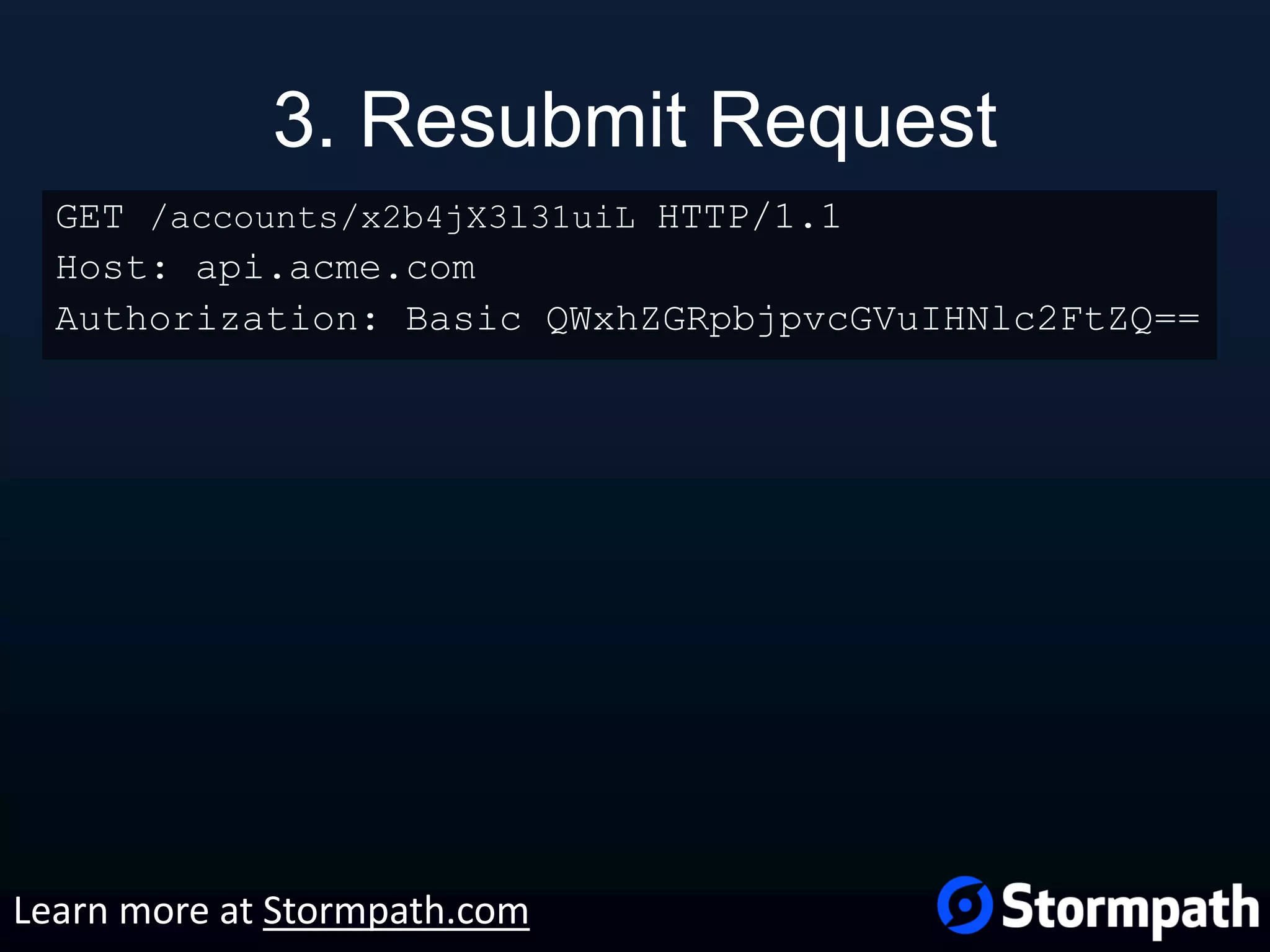
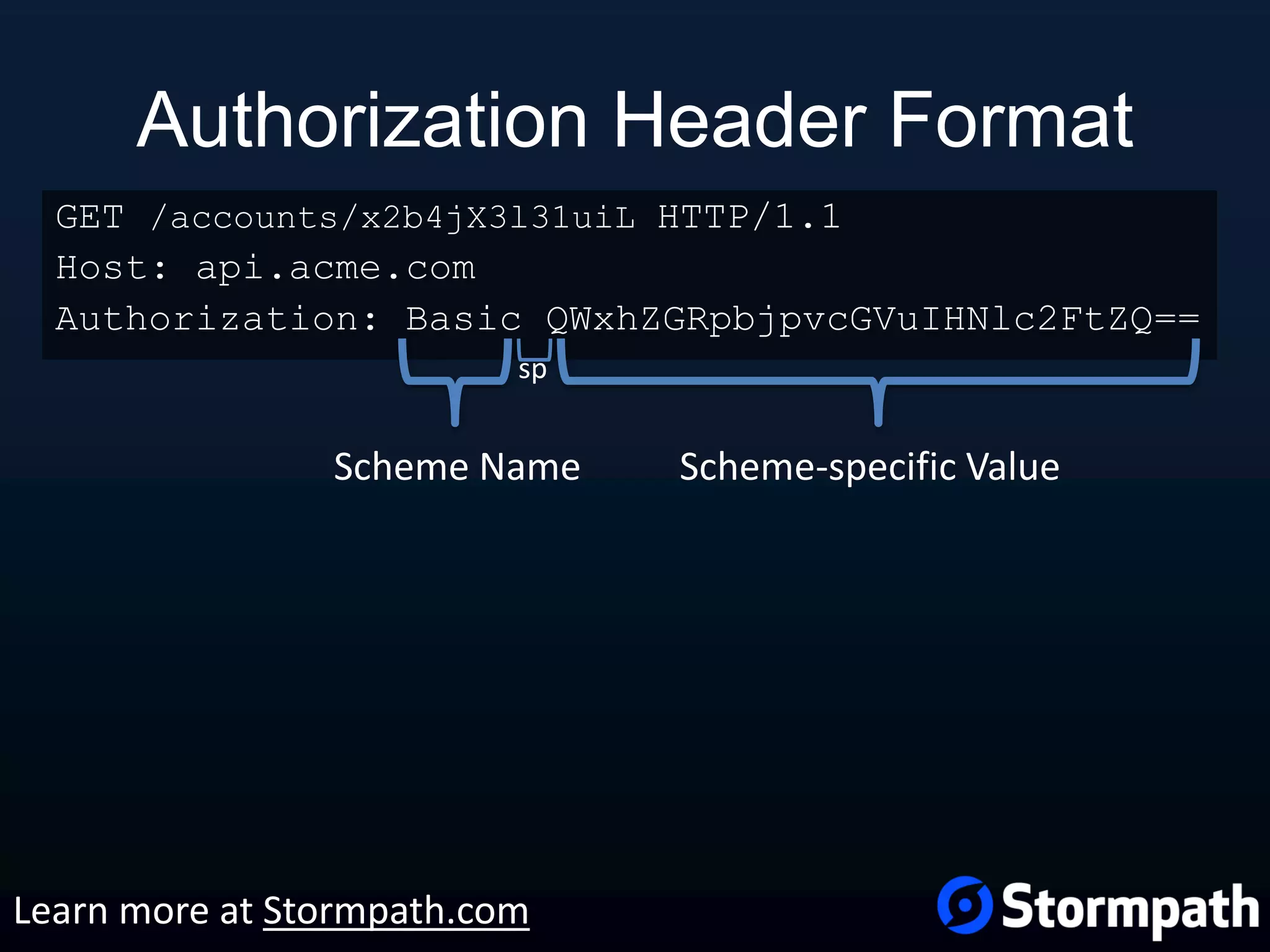
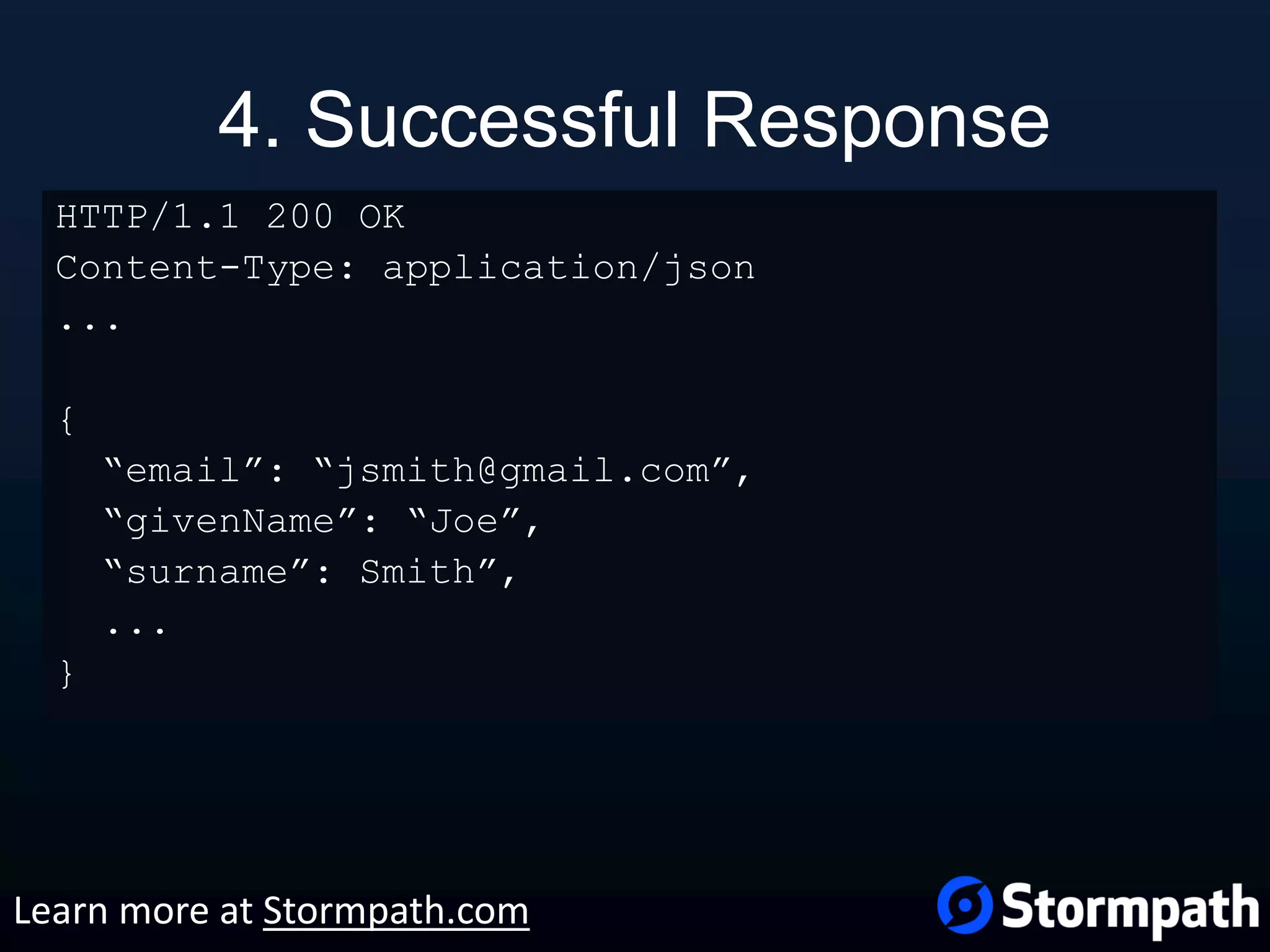
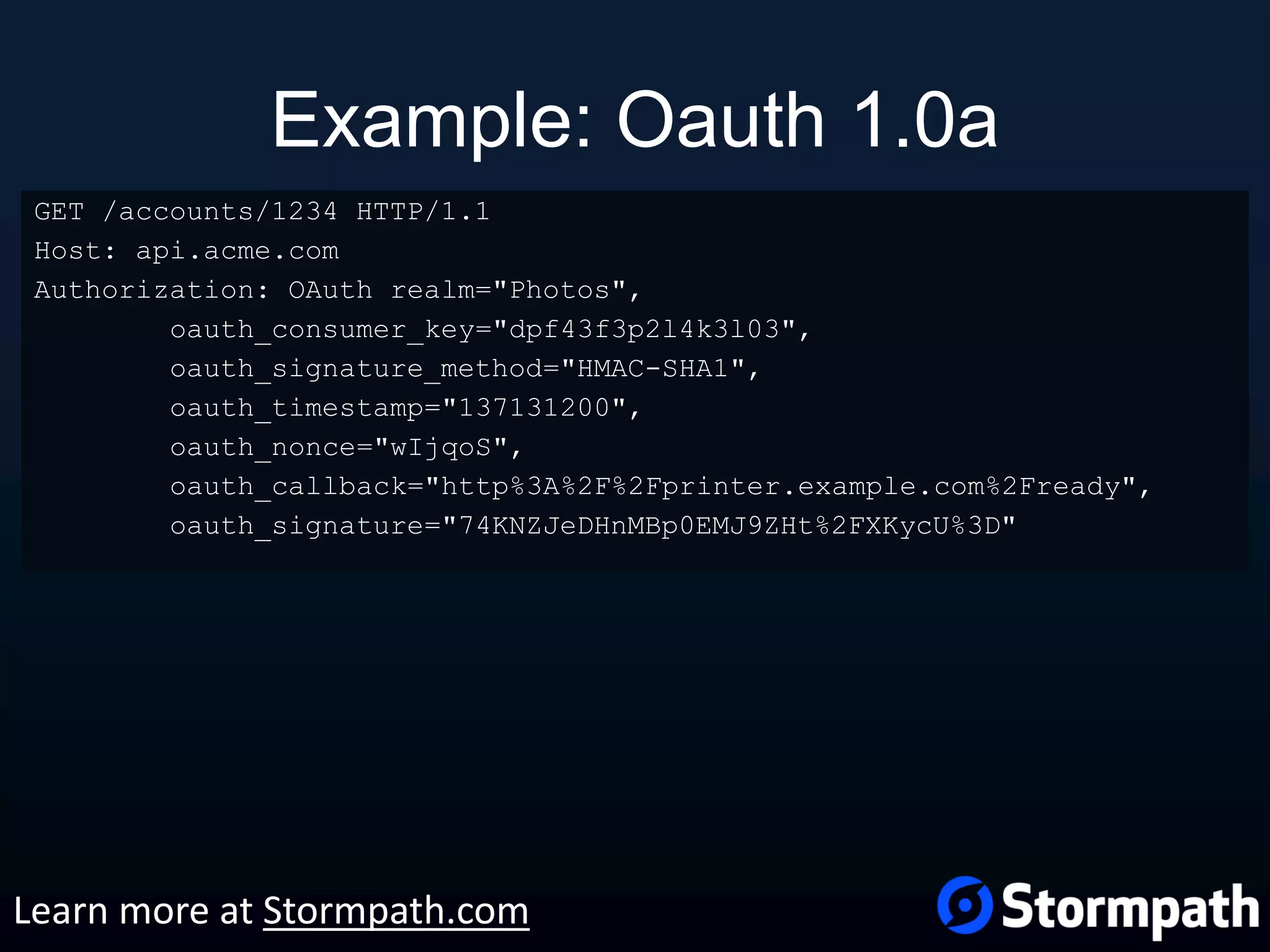
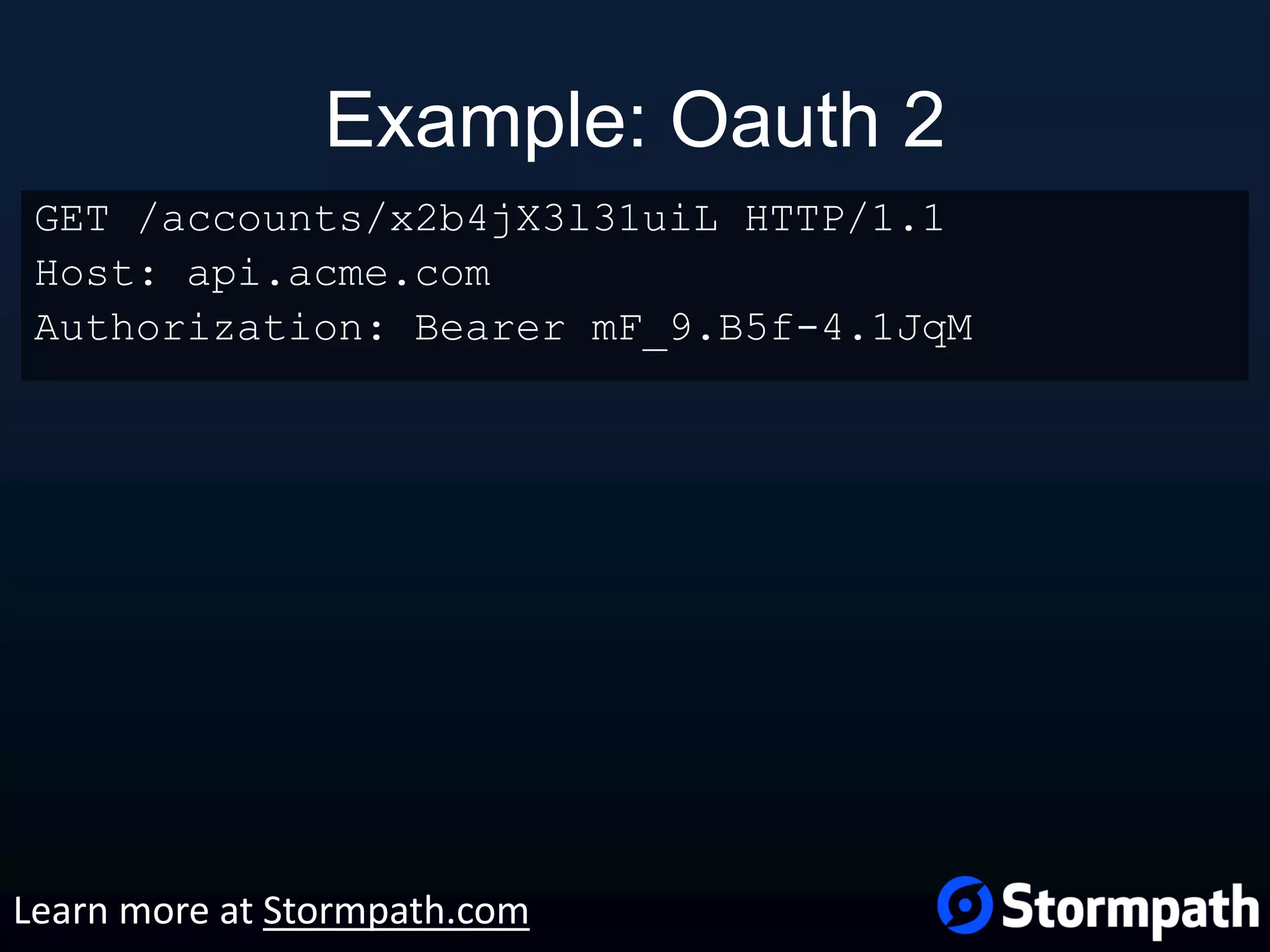
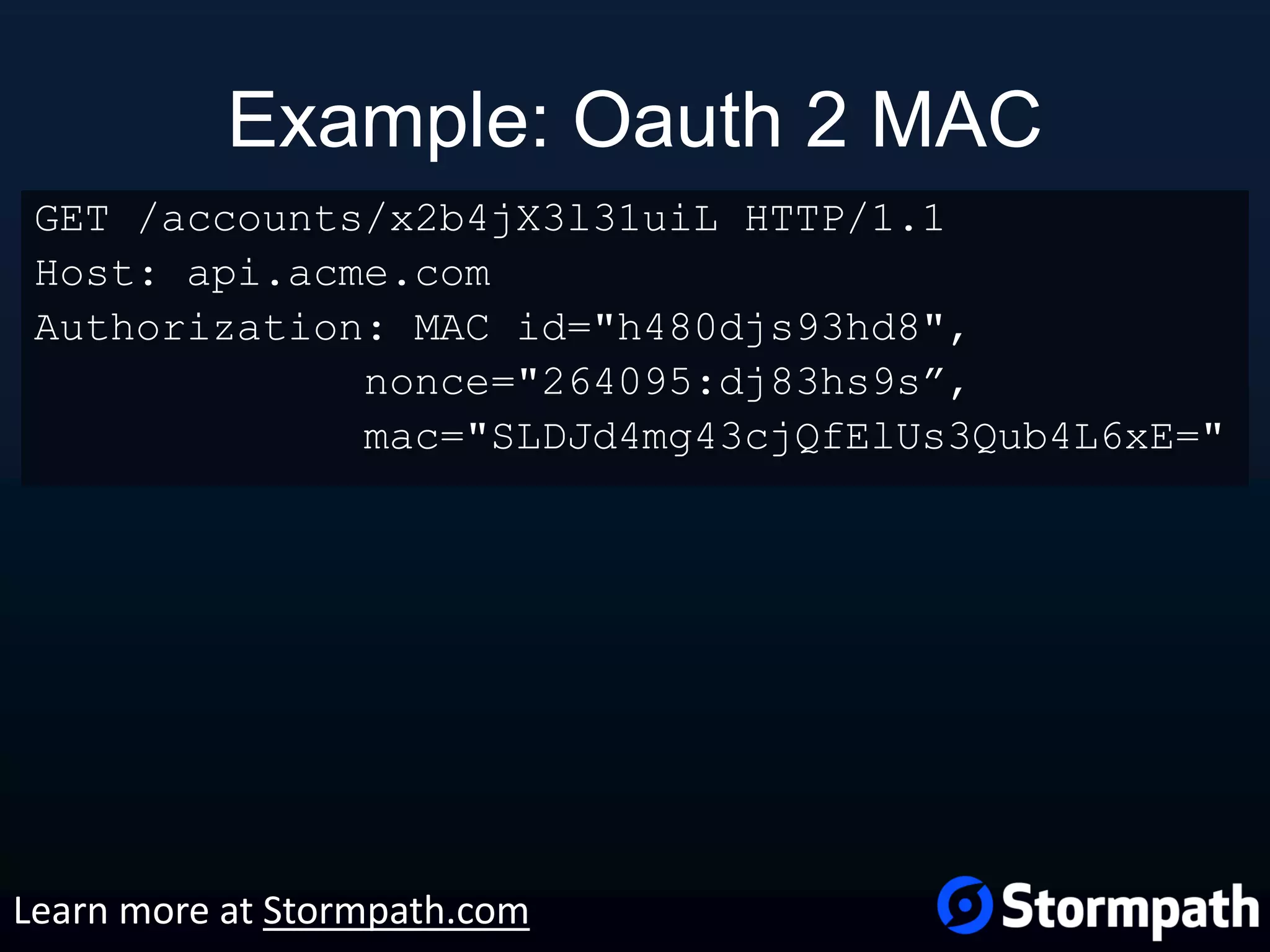
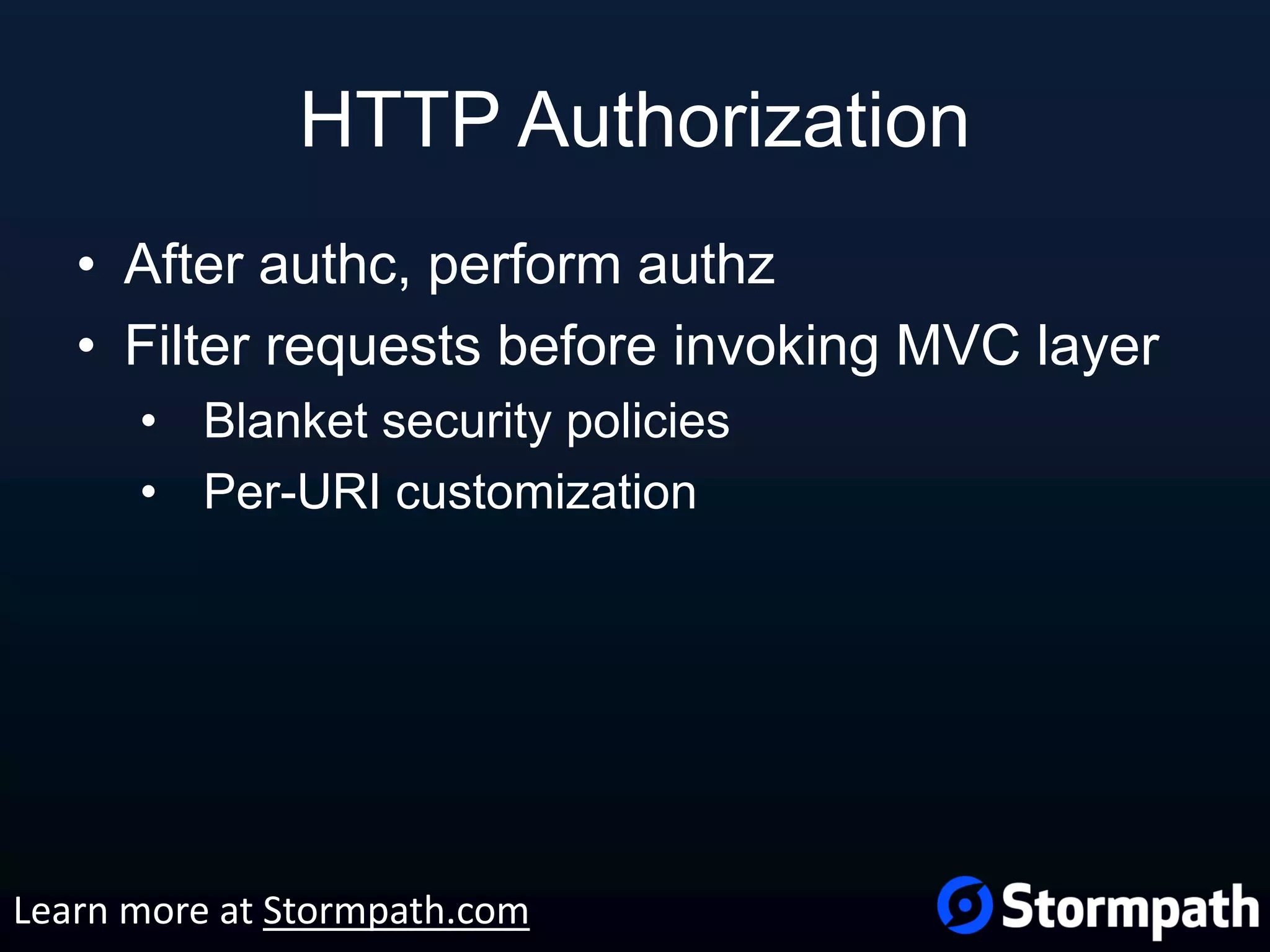
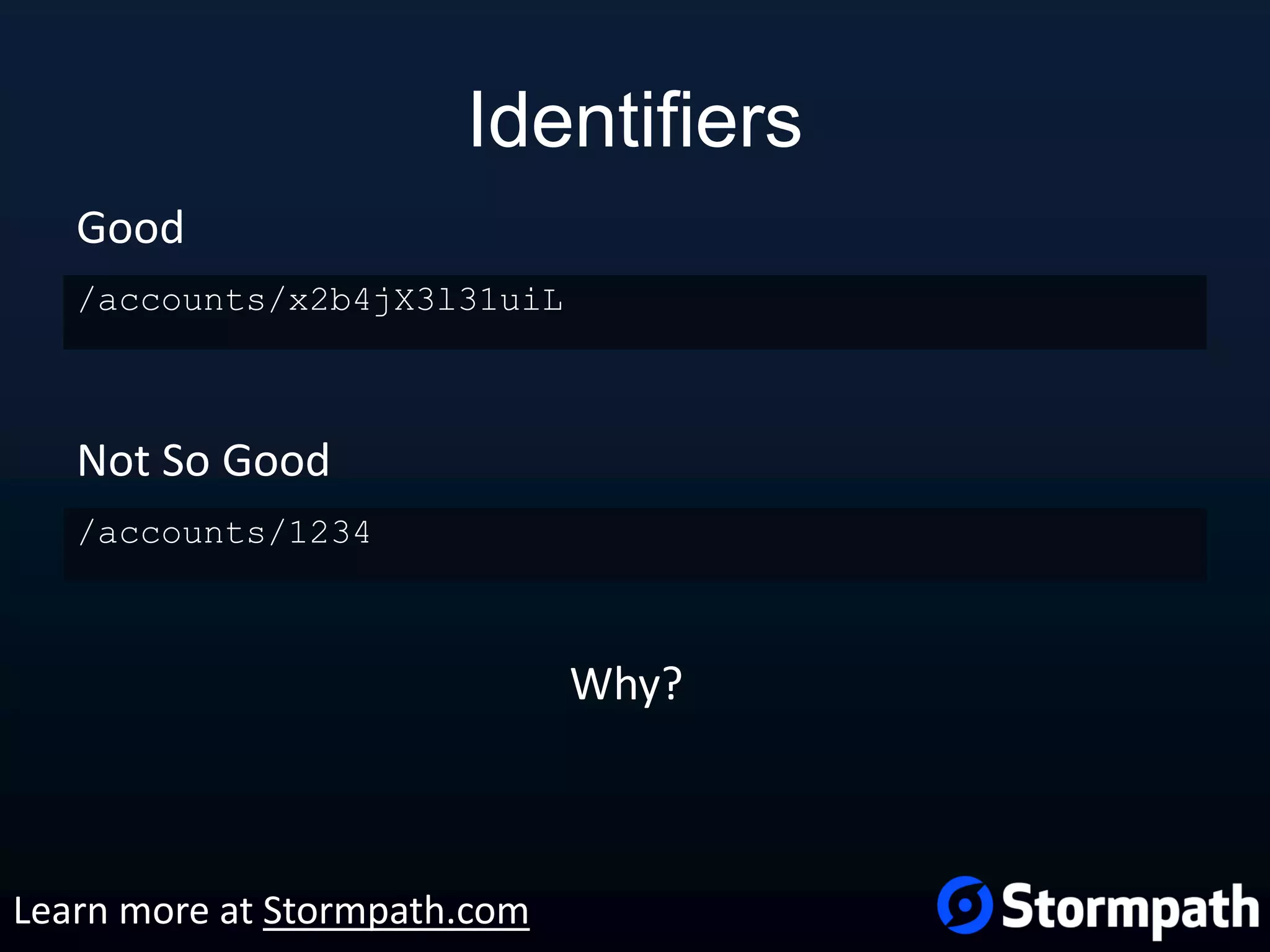
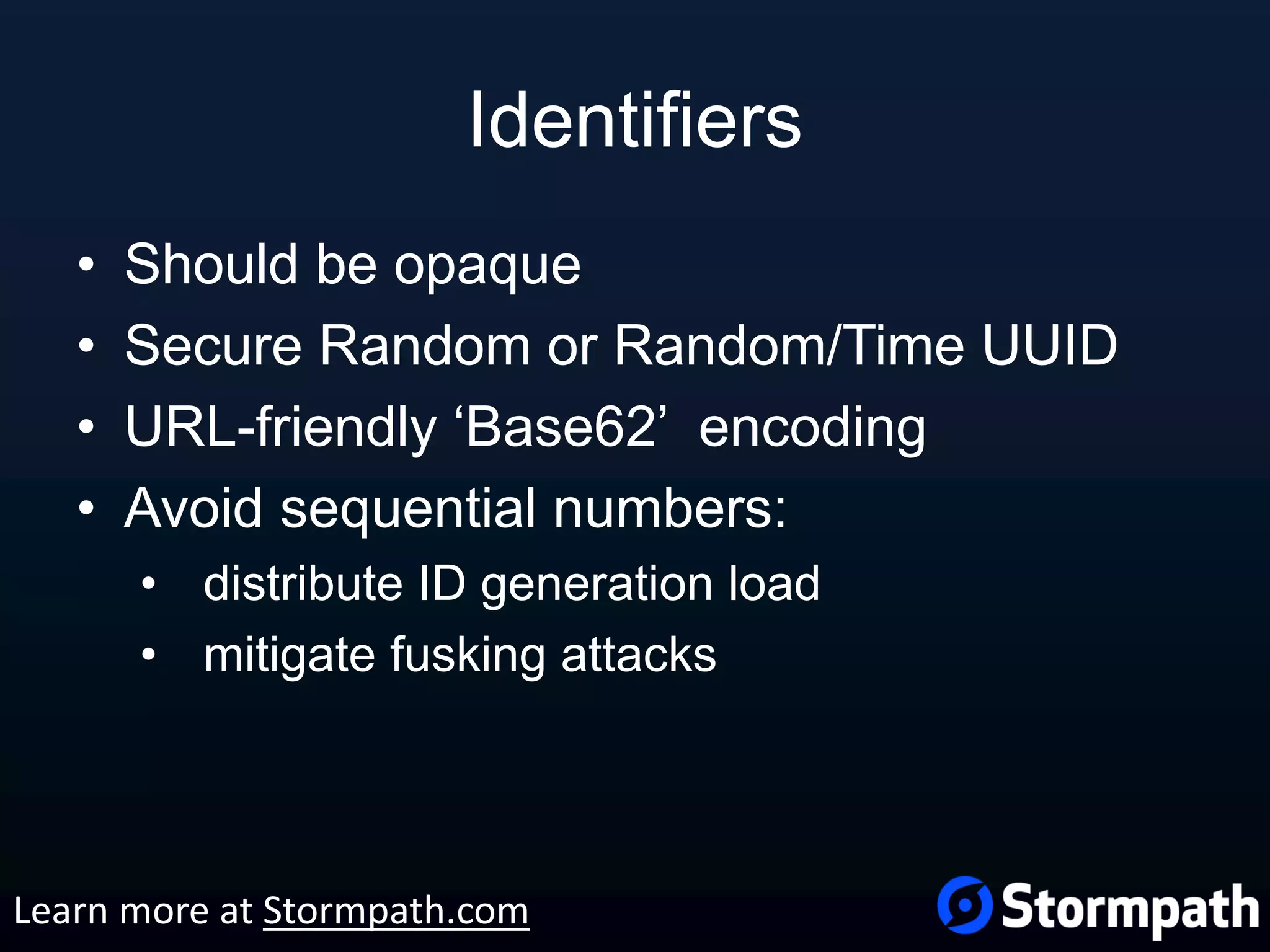
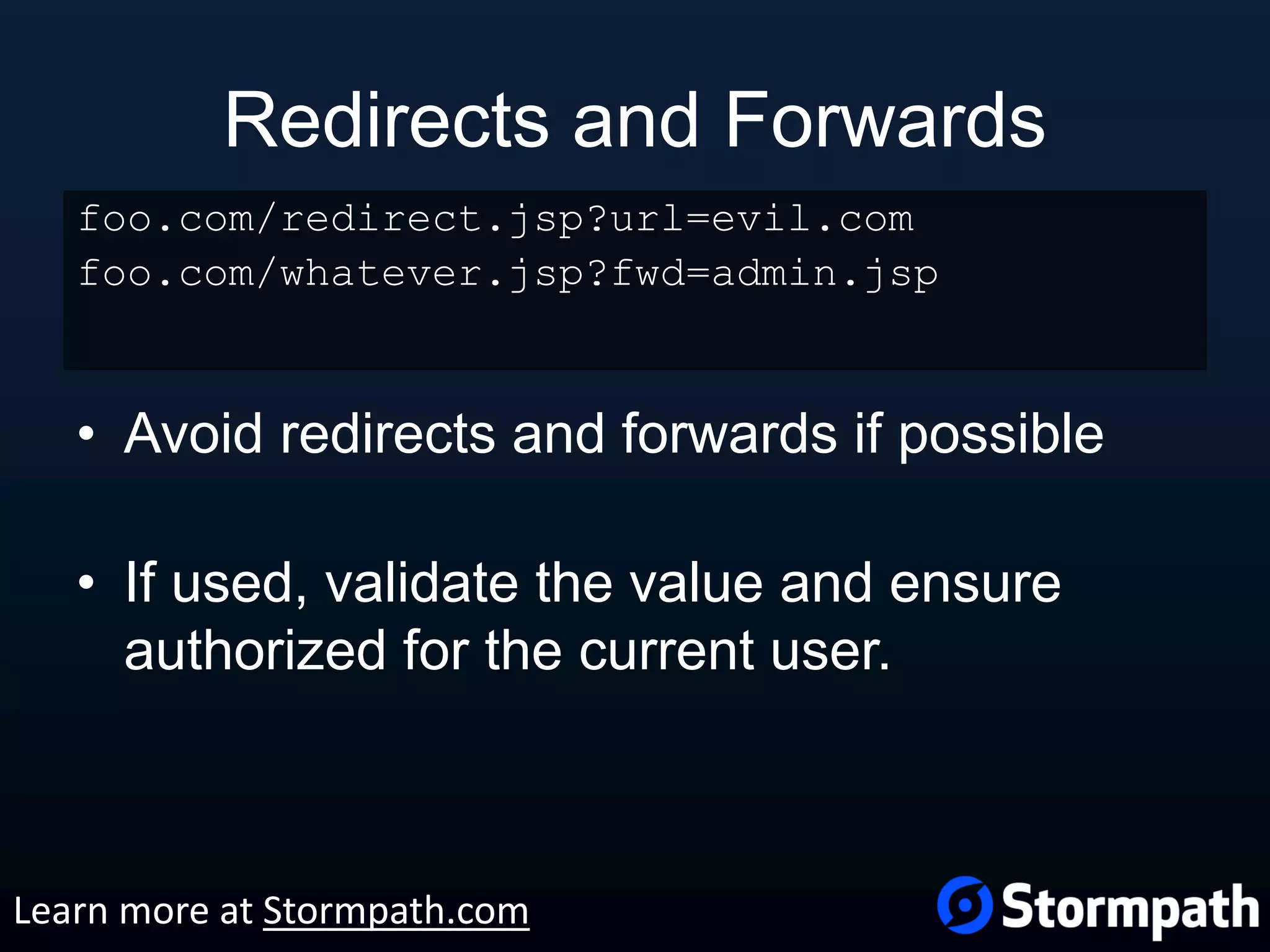
The document outlines best practices for securing REST APIs, focusing on user management, authentication methods, and security workflows. It emphasizes using OAuth 1.0a or OAuth 2 with MAC, avoiding basic authentication, and implementing proper authorization checks along with secure API key management. Additionally, it covers the importance of TLS, configuration management, and efficient storage of sensitive data to protect against vulnerabilities.