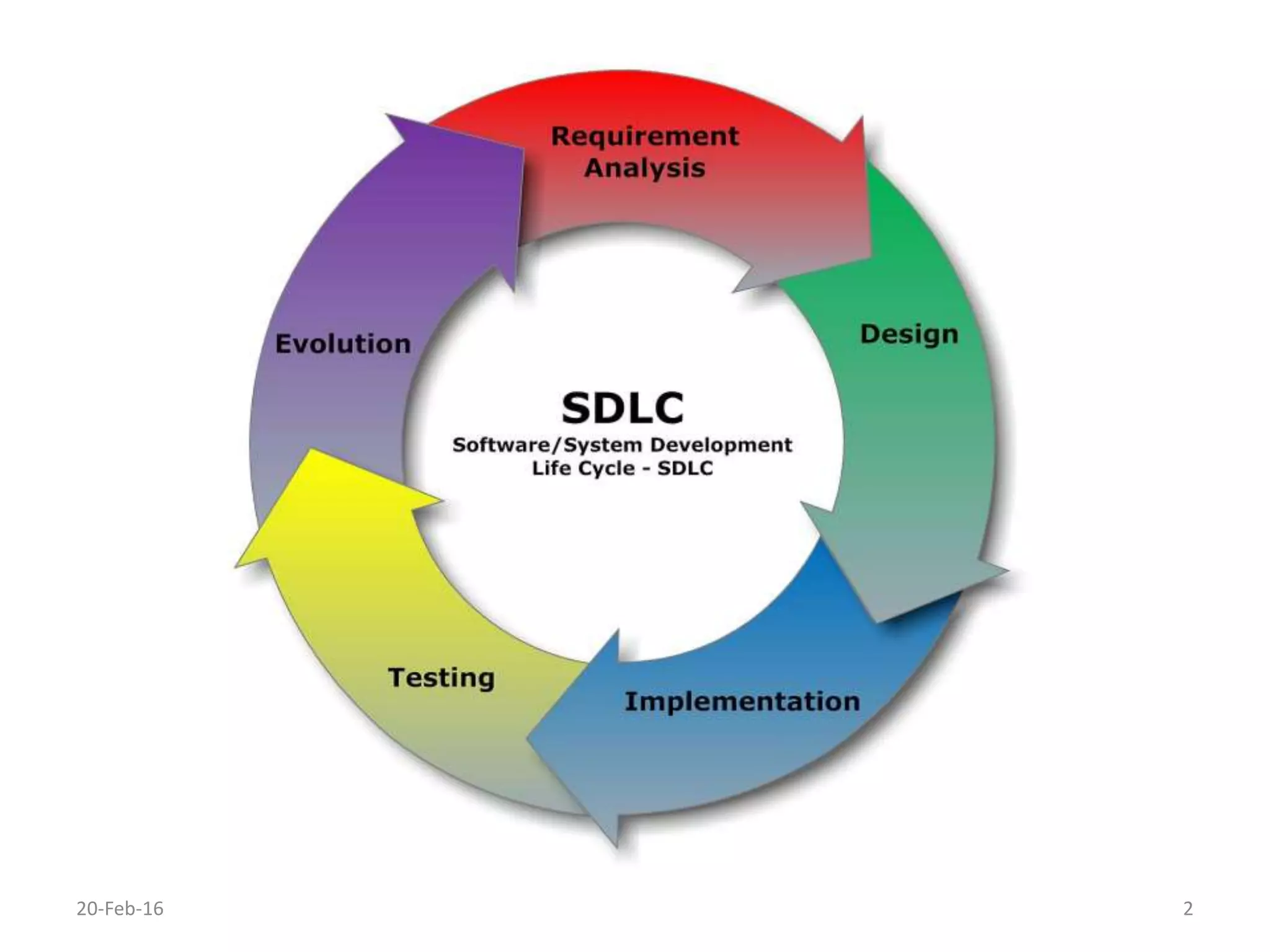
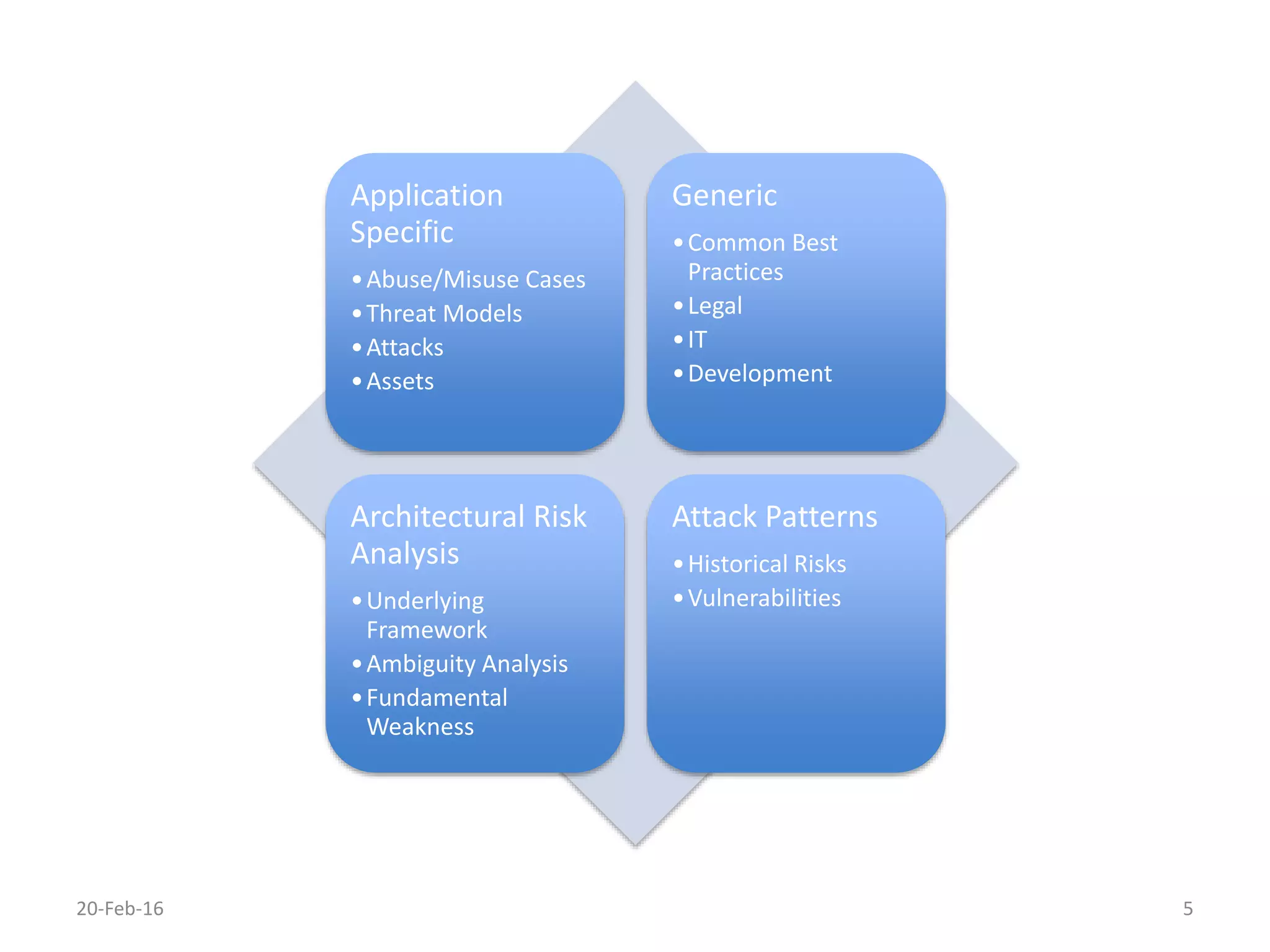
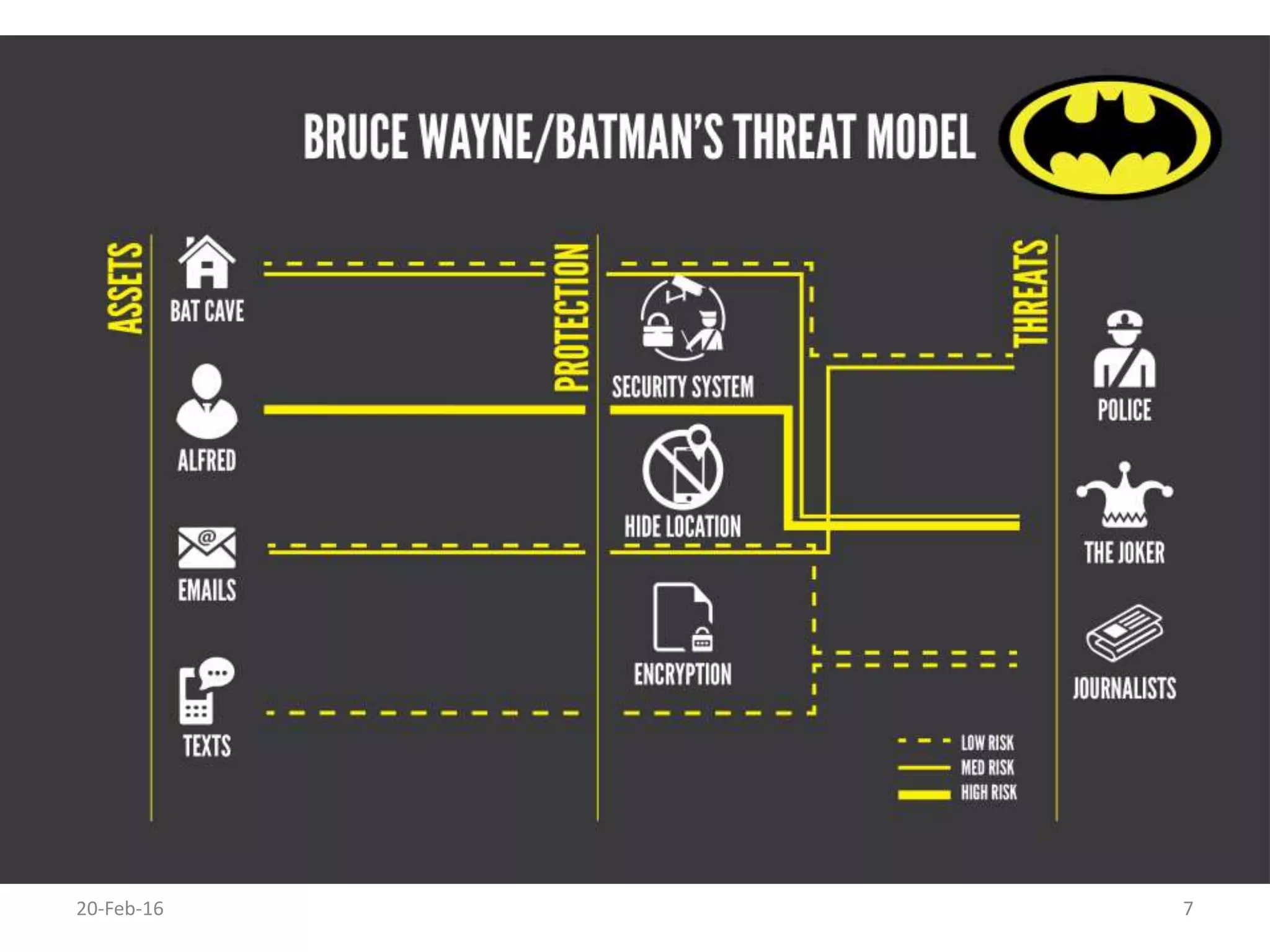
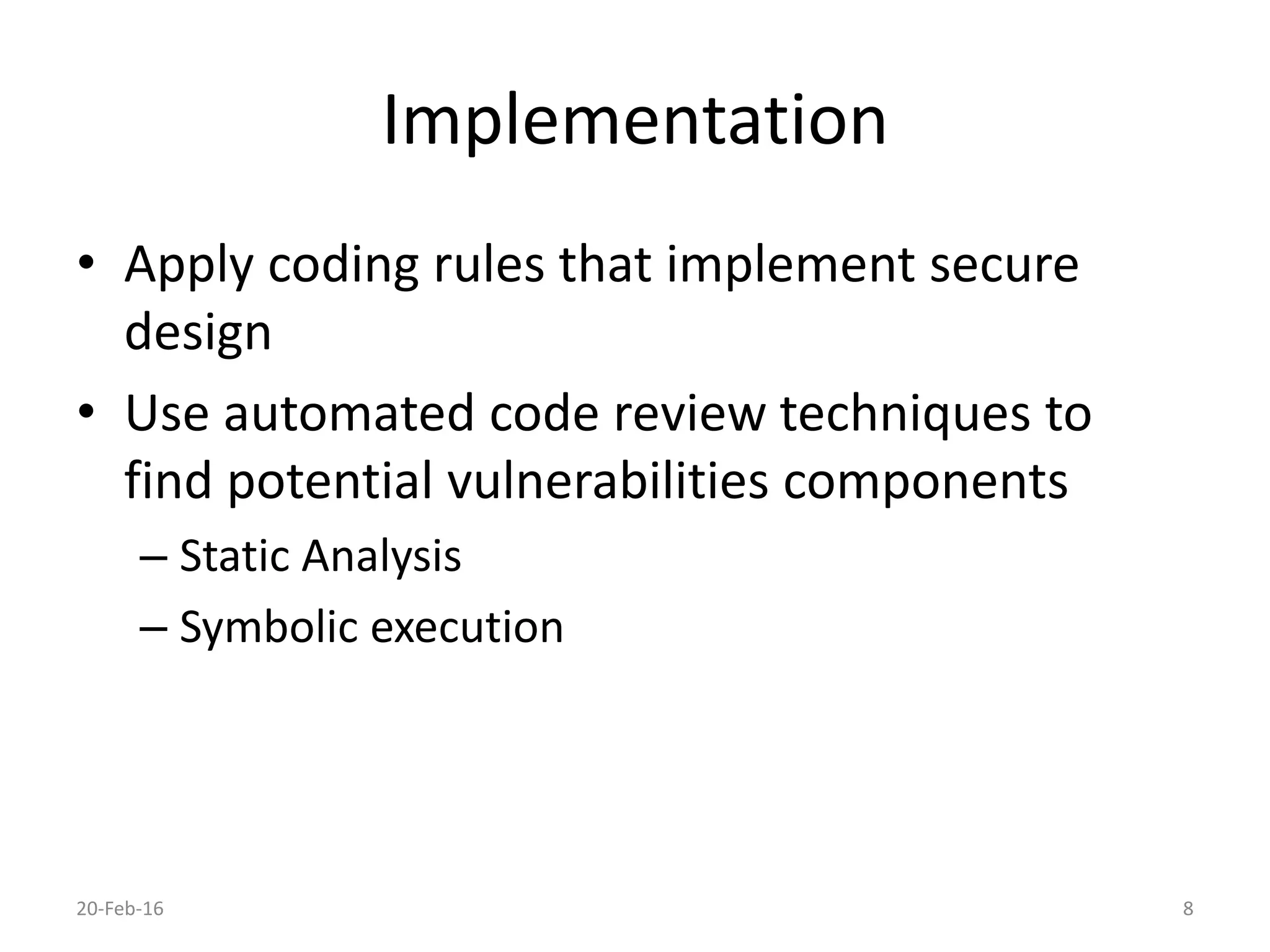
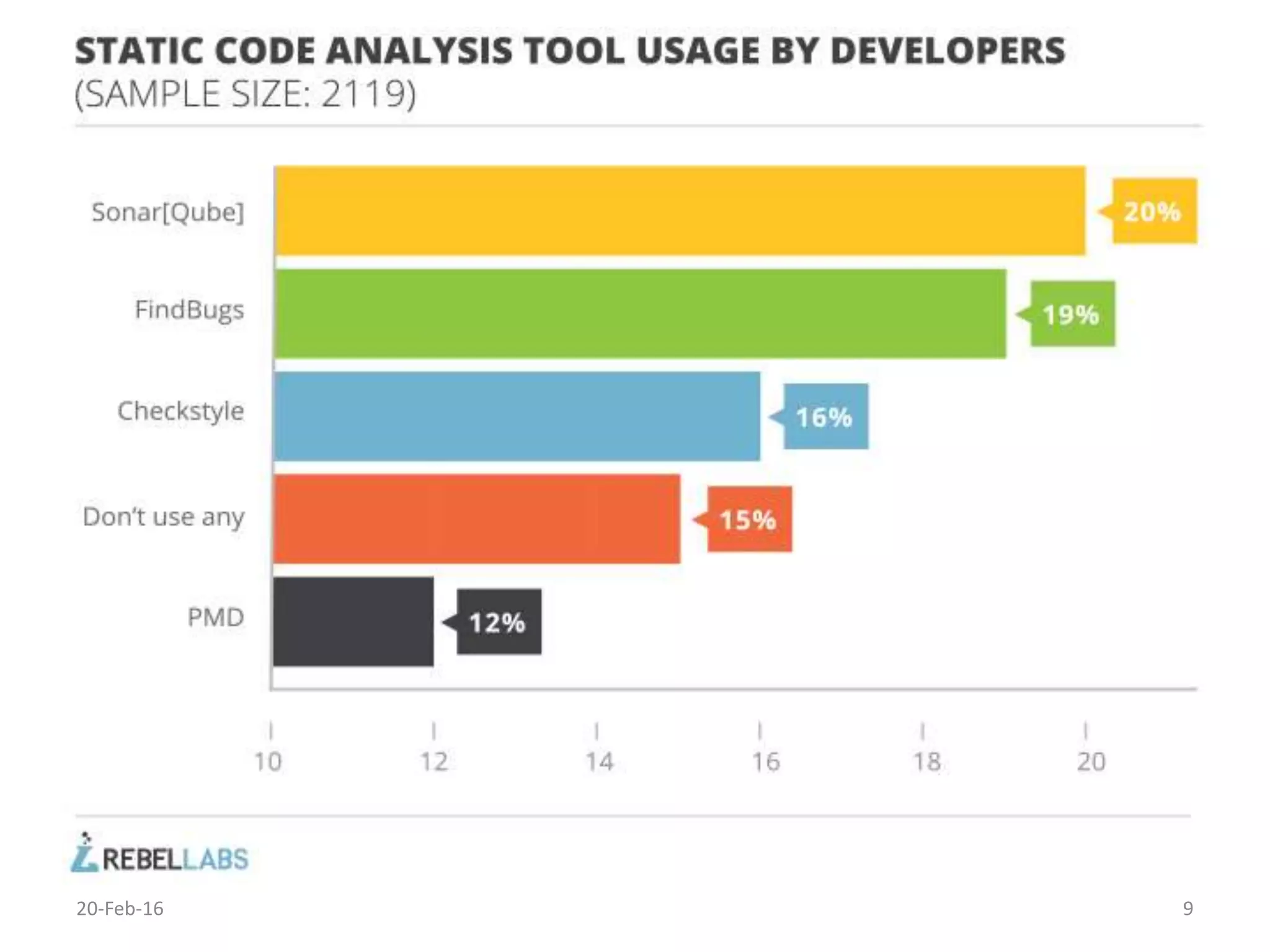
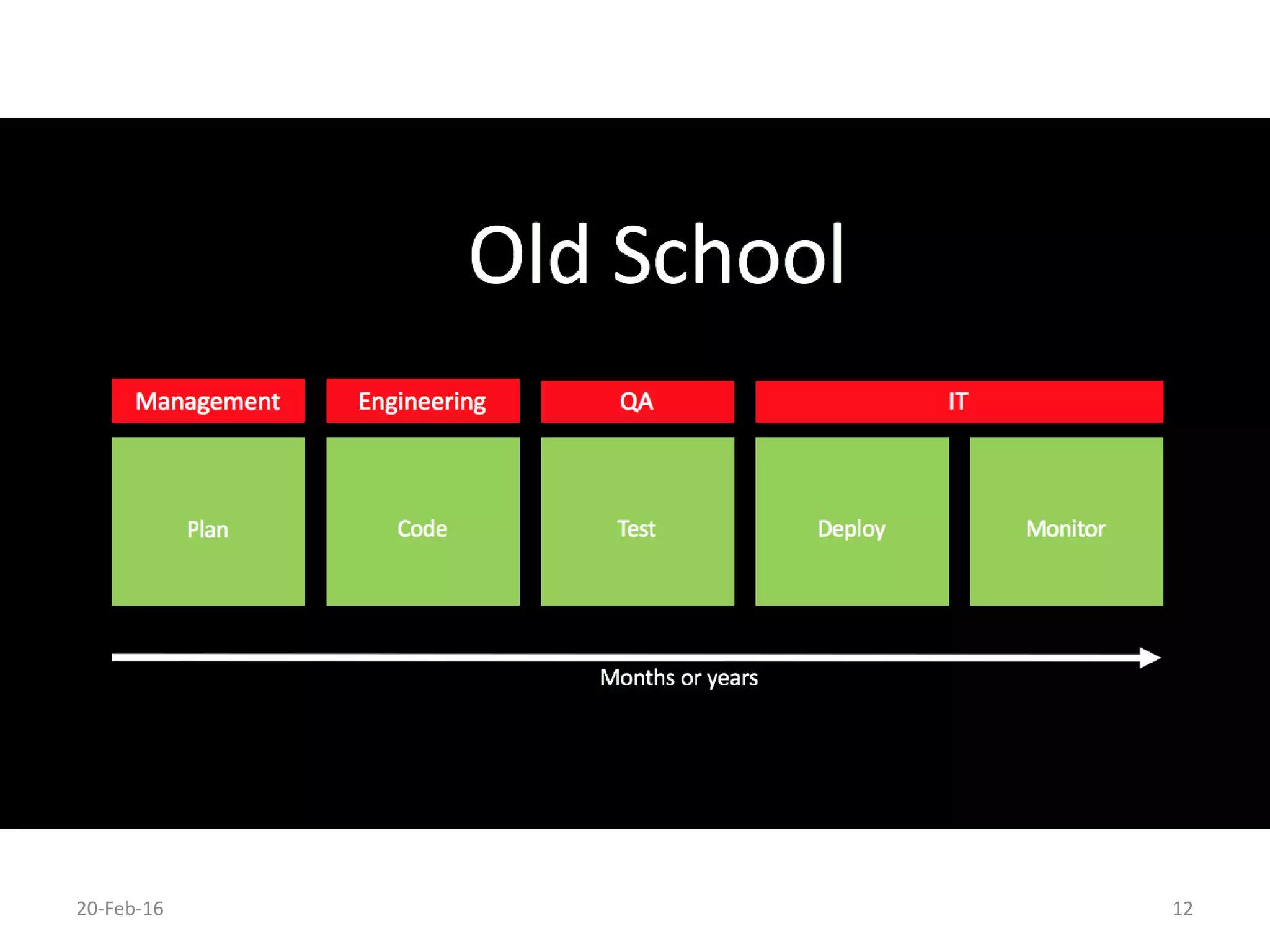
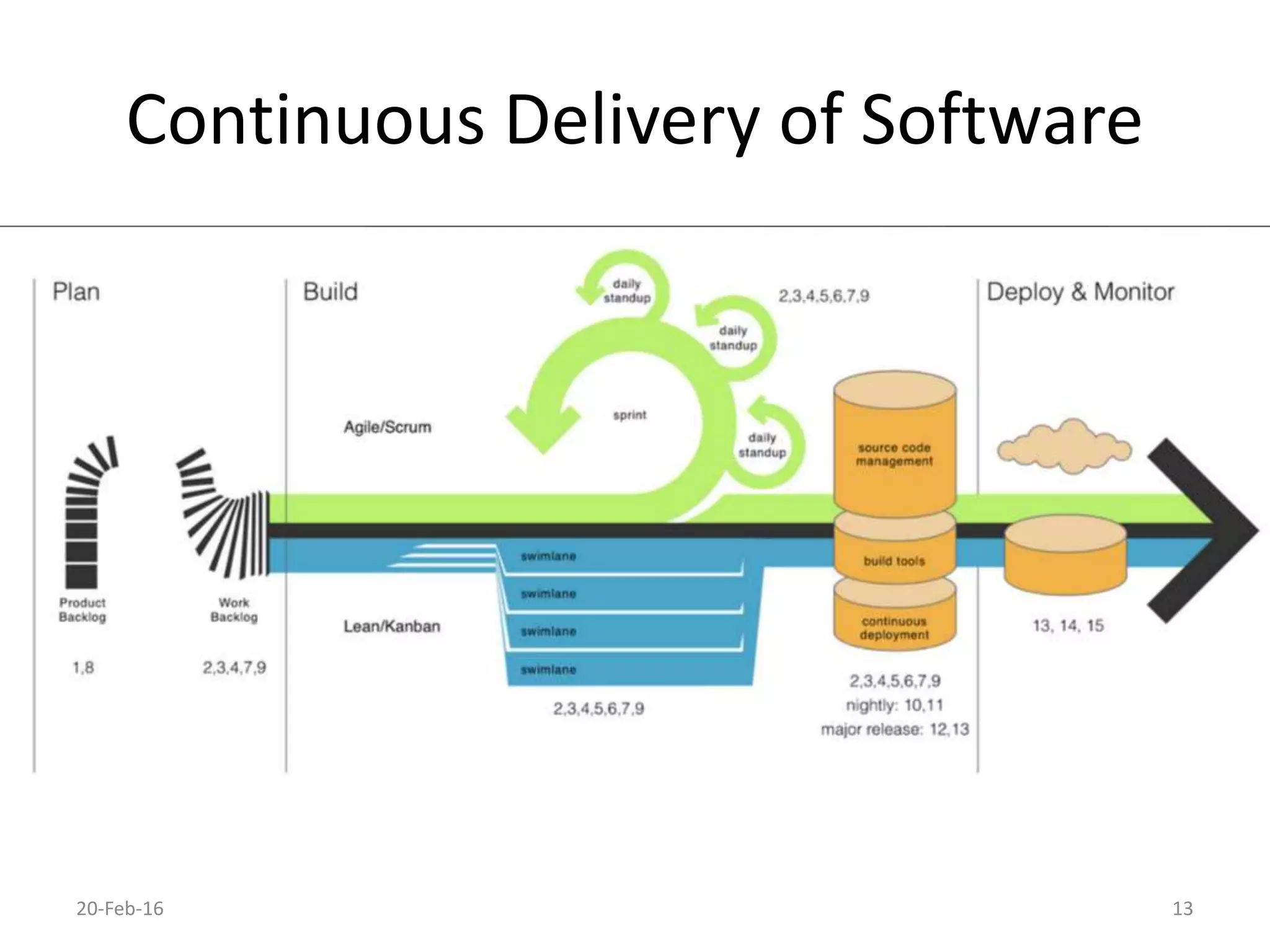
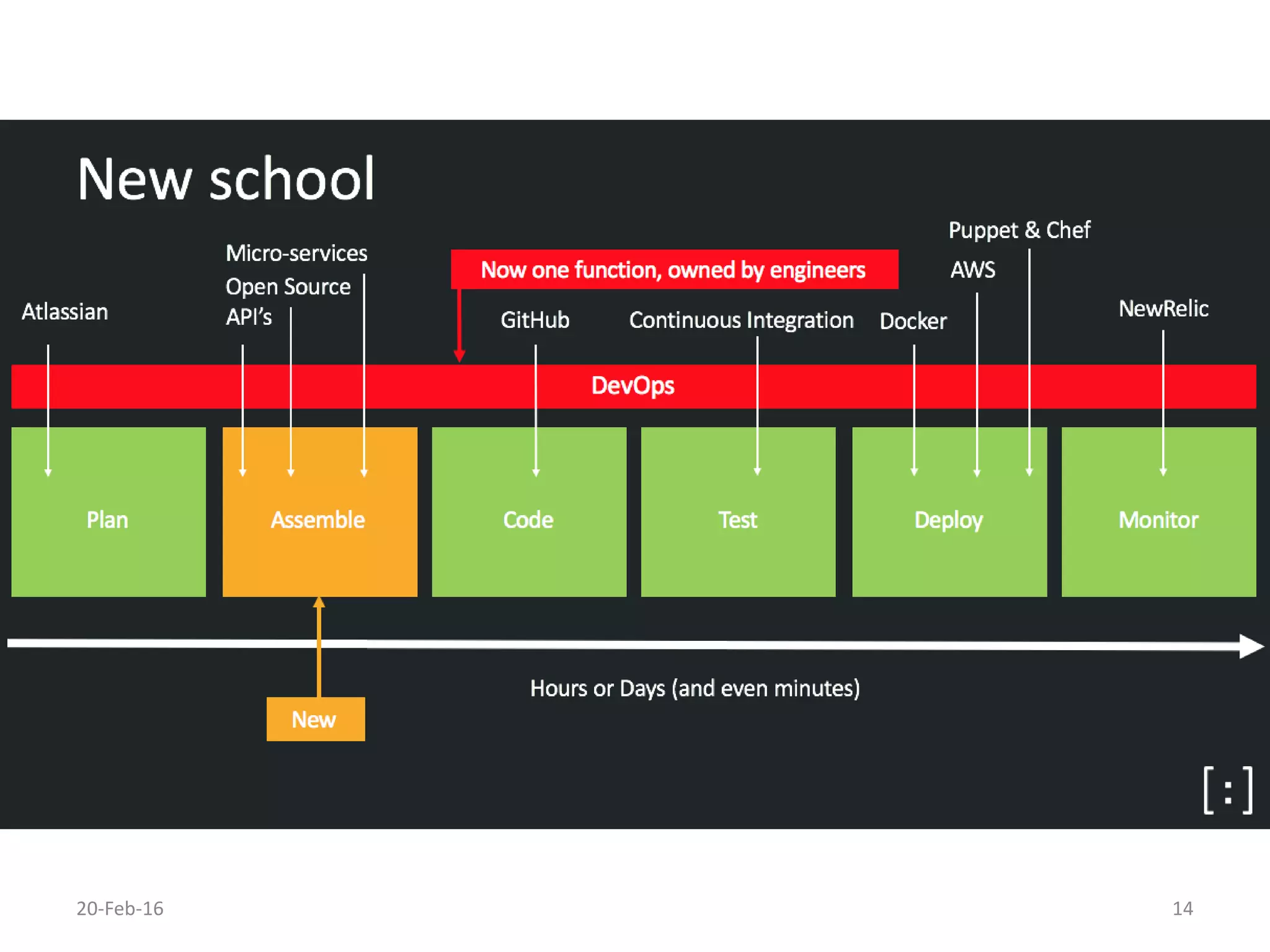
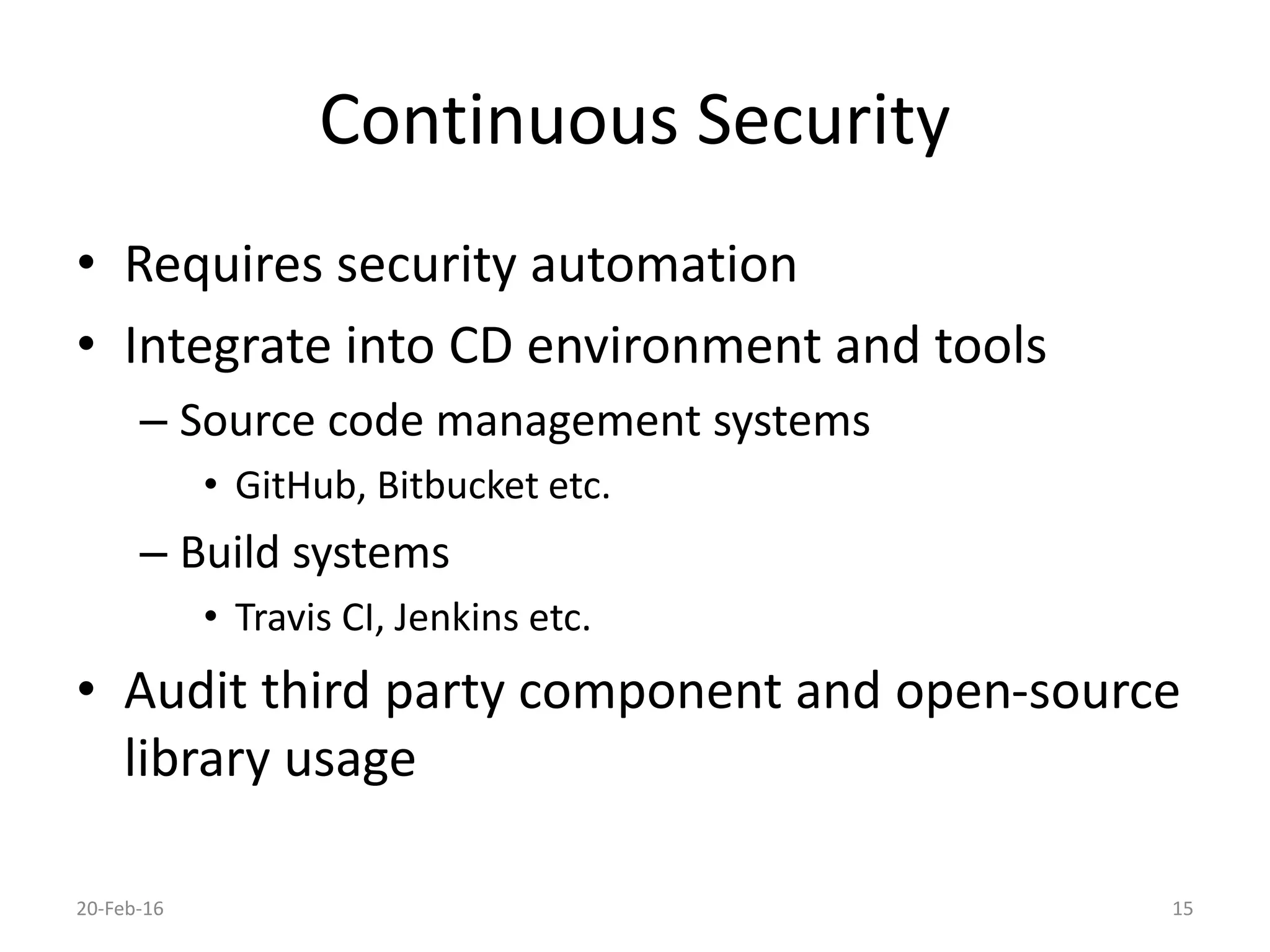
The document discusses secure software development. It recommends considering security throughout the software development lifecycle, from requirements to deployment. Key aspects discussed include identifying security requirements for sensitive data, applying principles for secure design like simplicity and defense in depth, implementing secure coding rules through code reviews and testing with techniques like fuzzing and penetration testing. The document also discusses methodologies like BSIMM and SDL and notes that continuous delivery requires continuous security integration and automation.