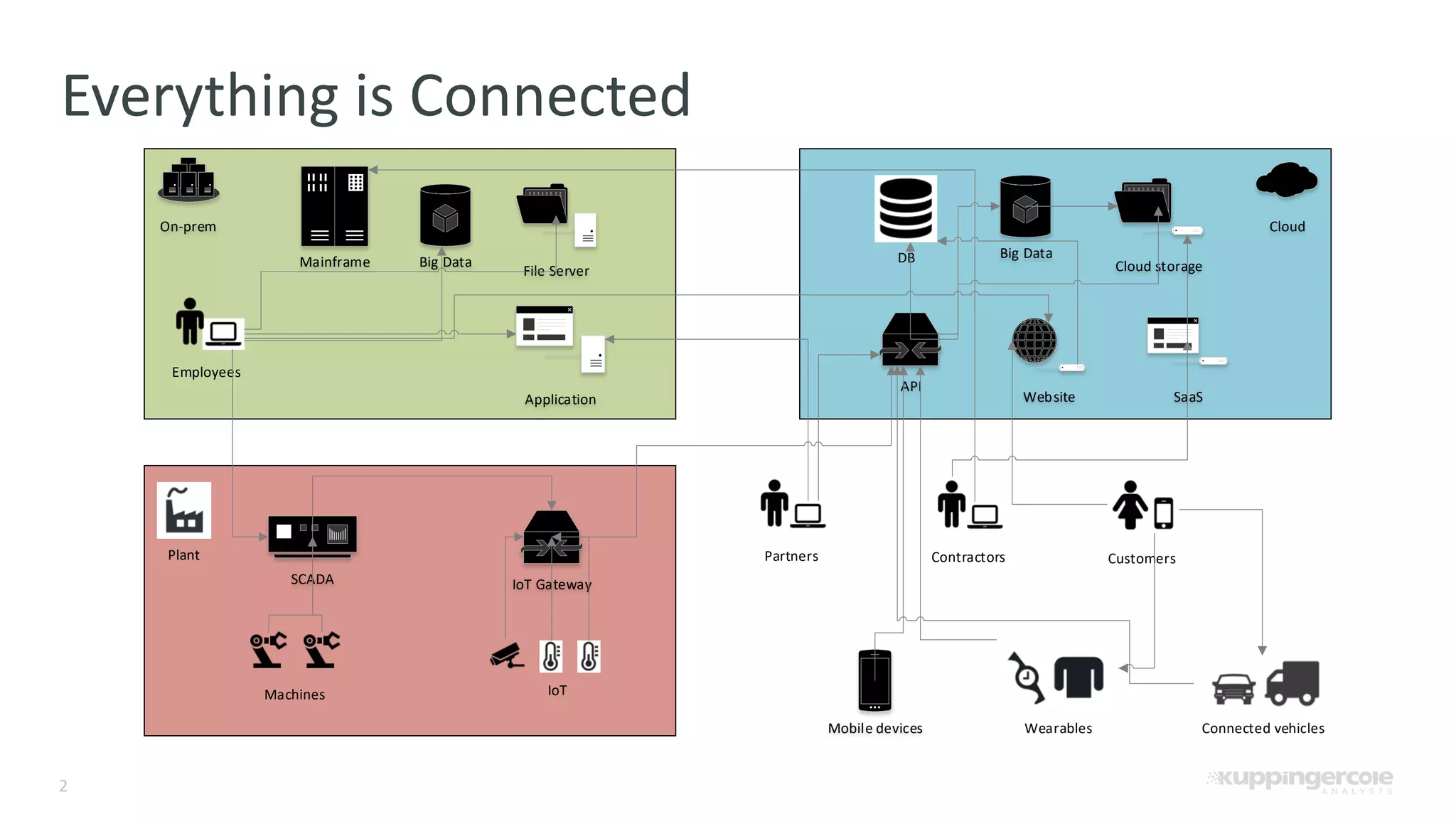
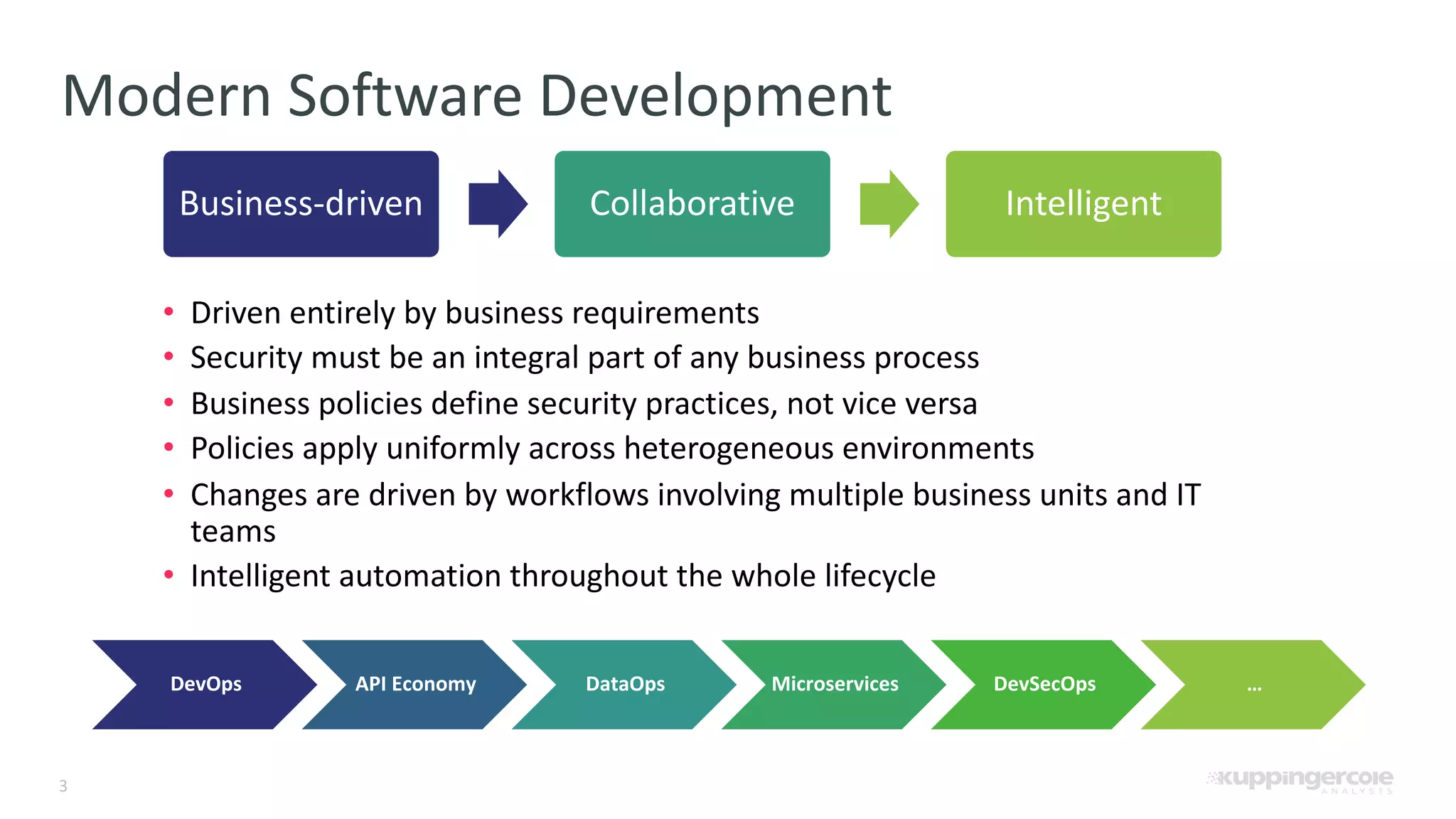
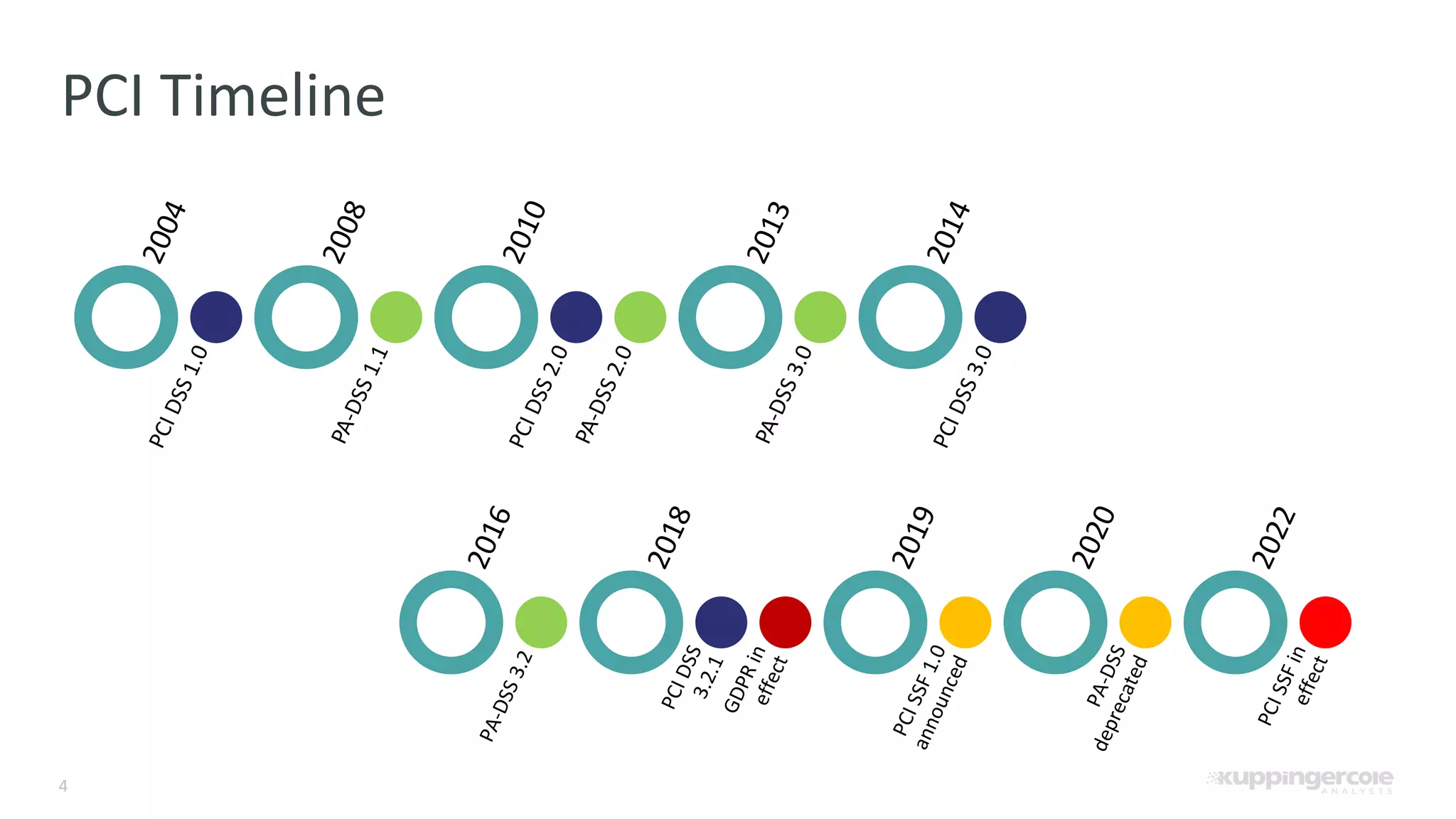
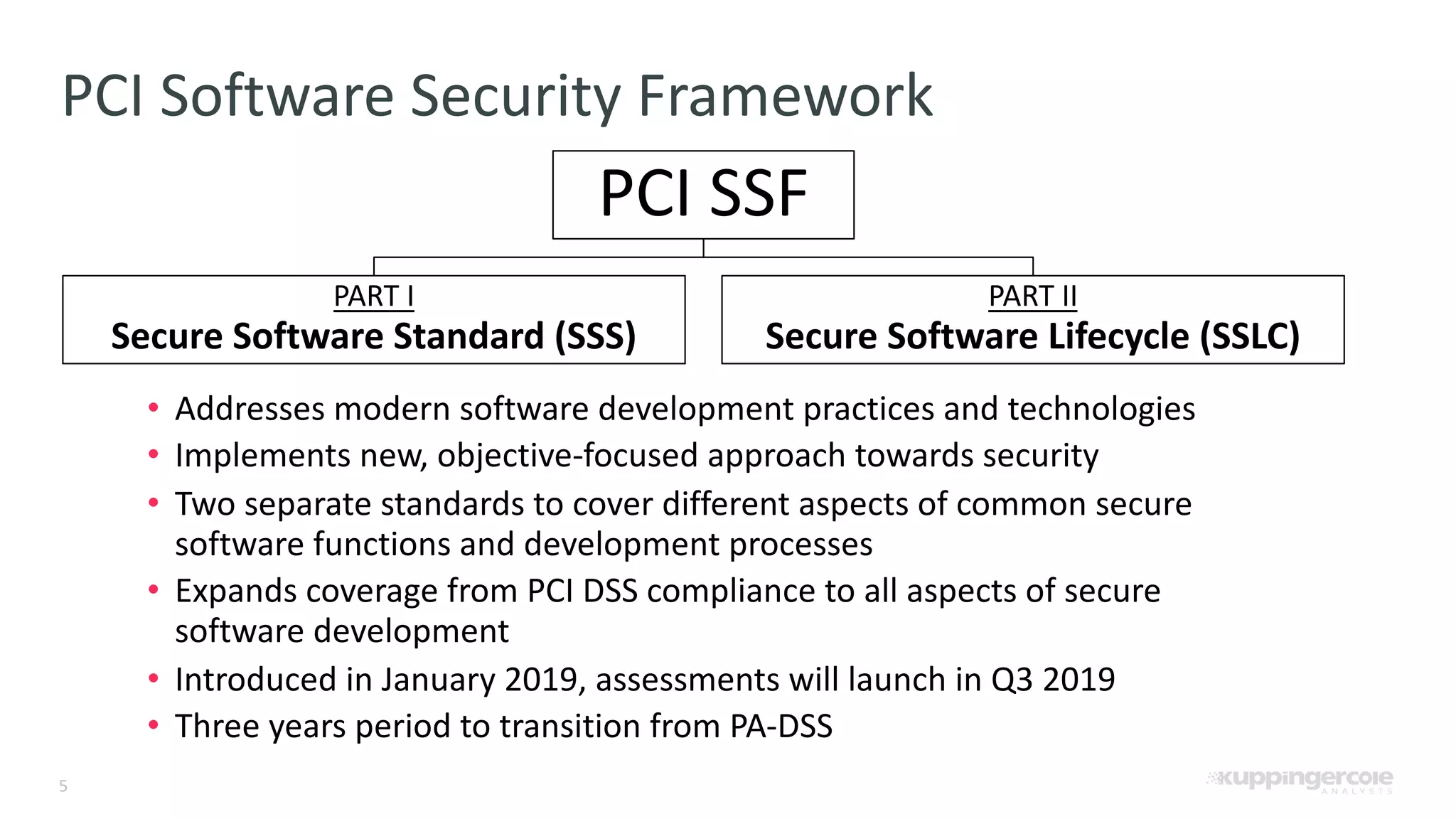
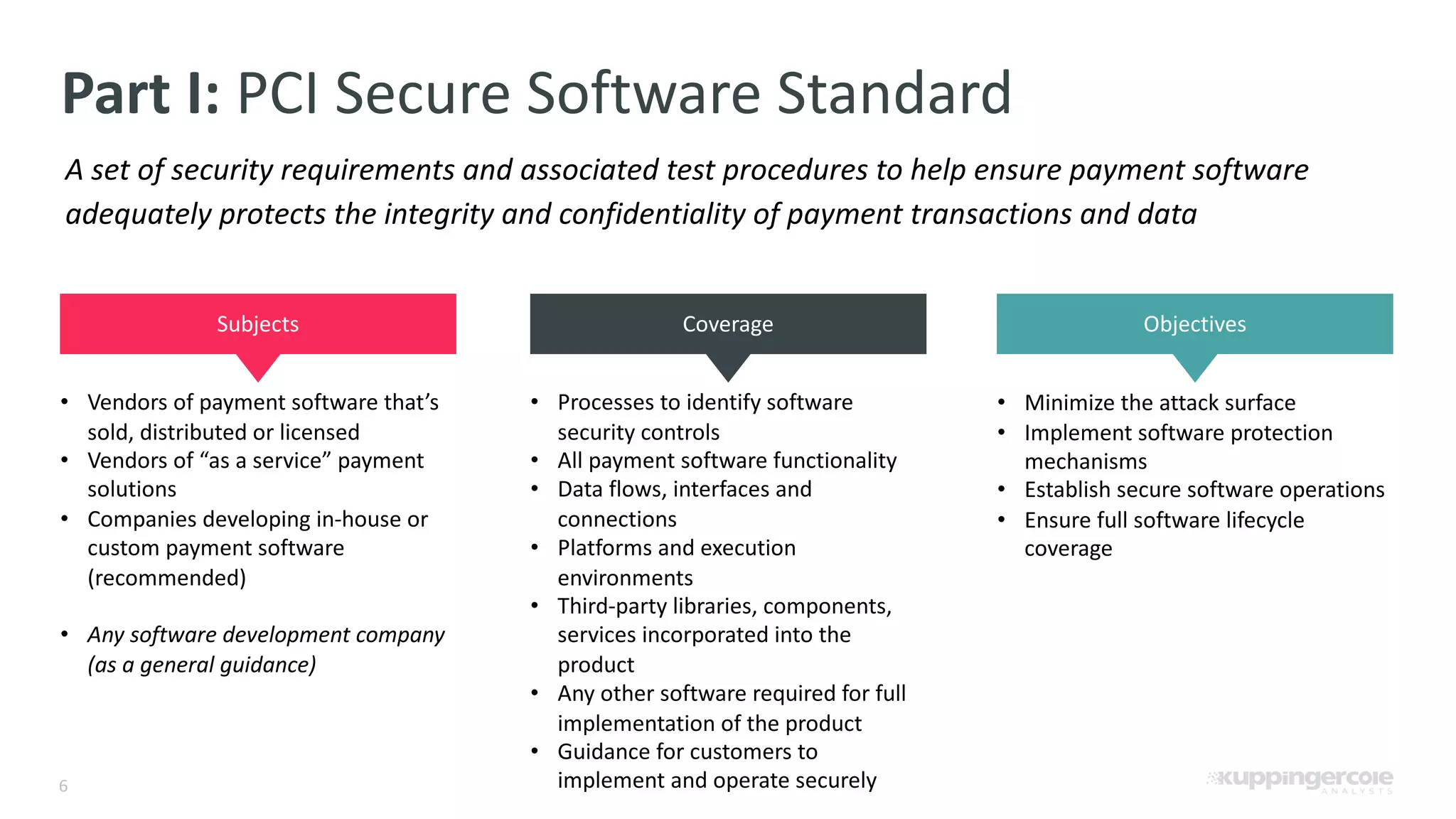
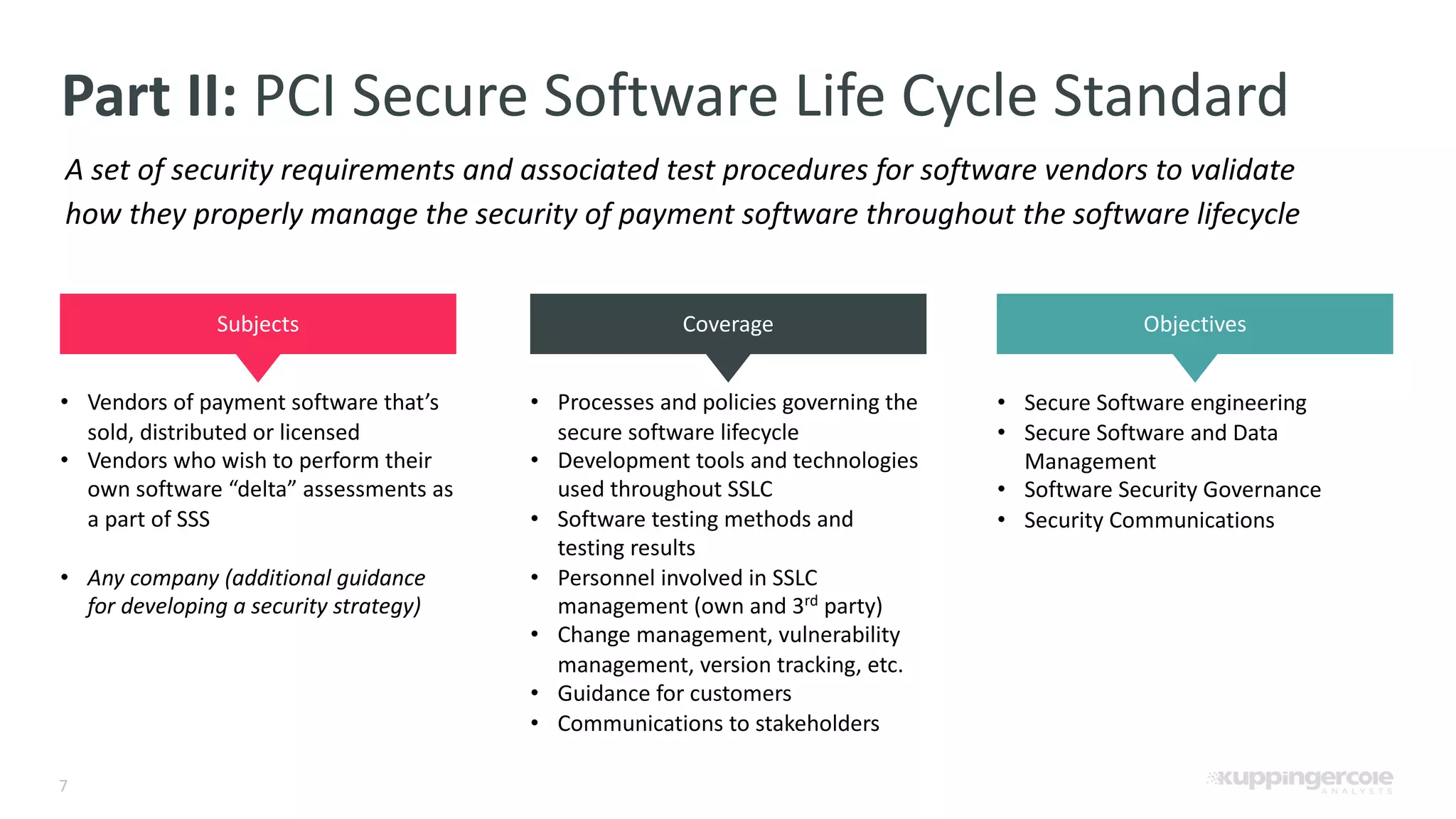
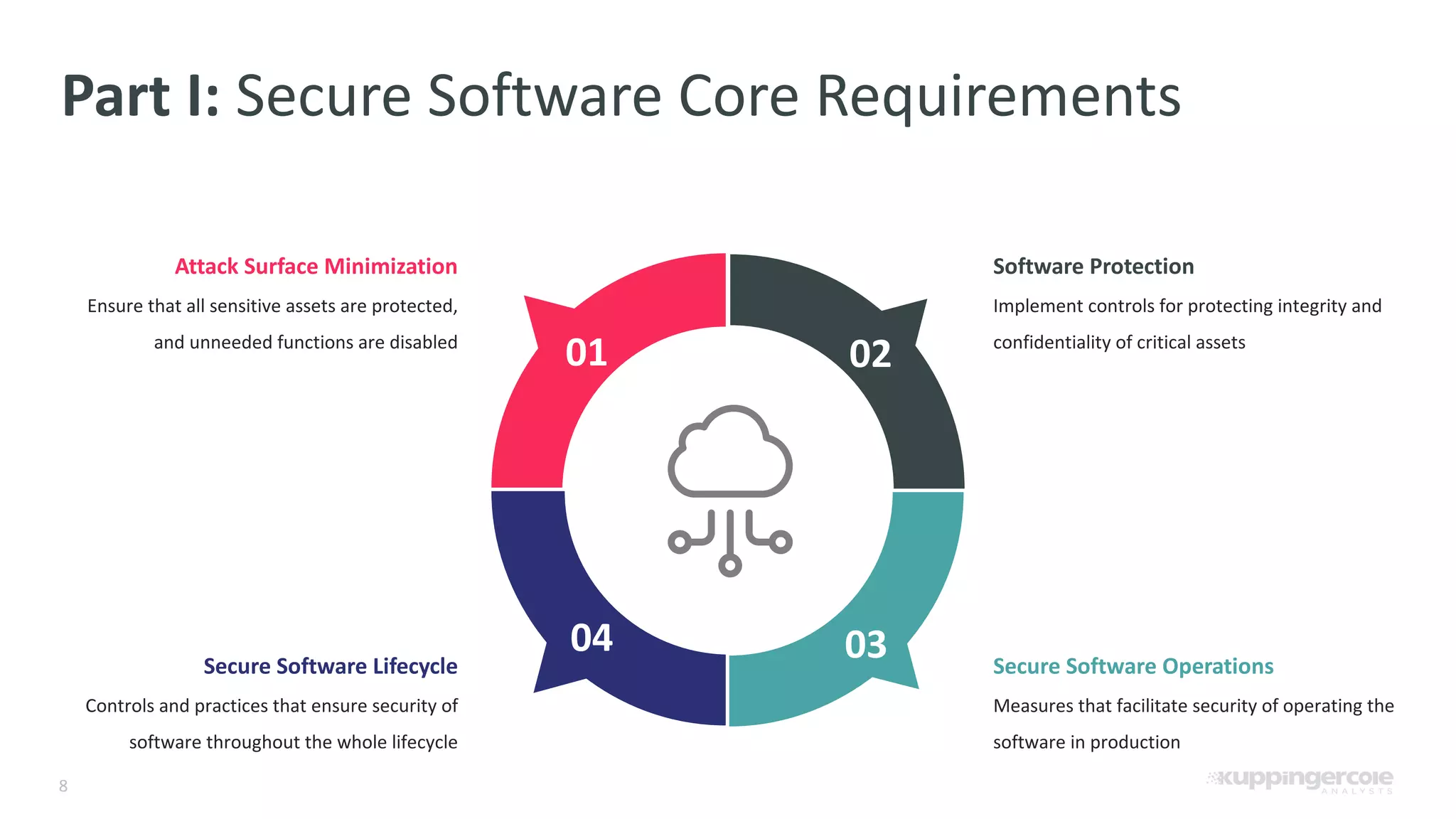
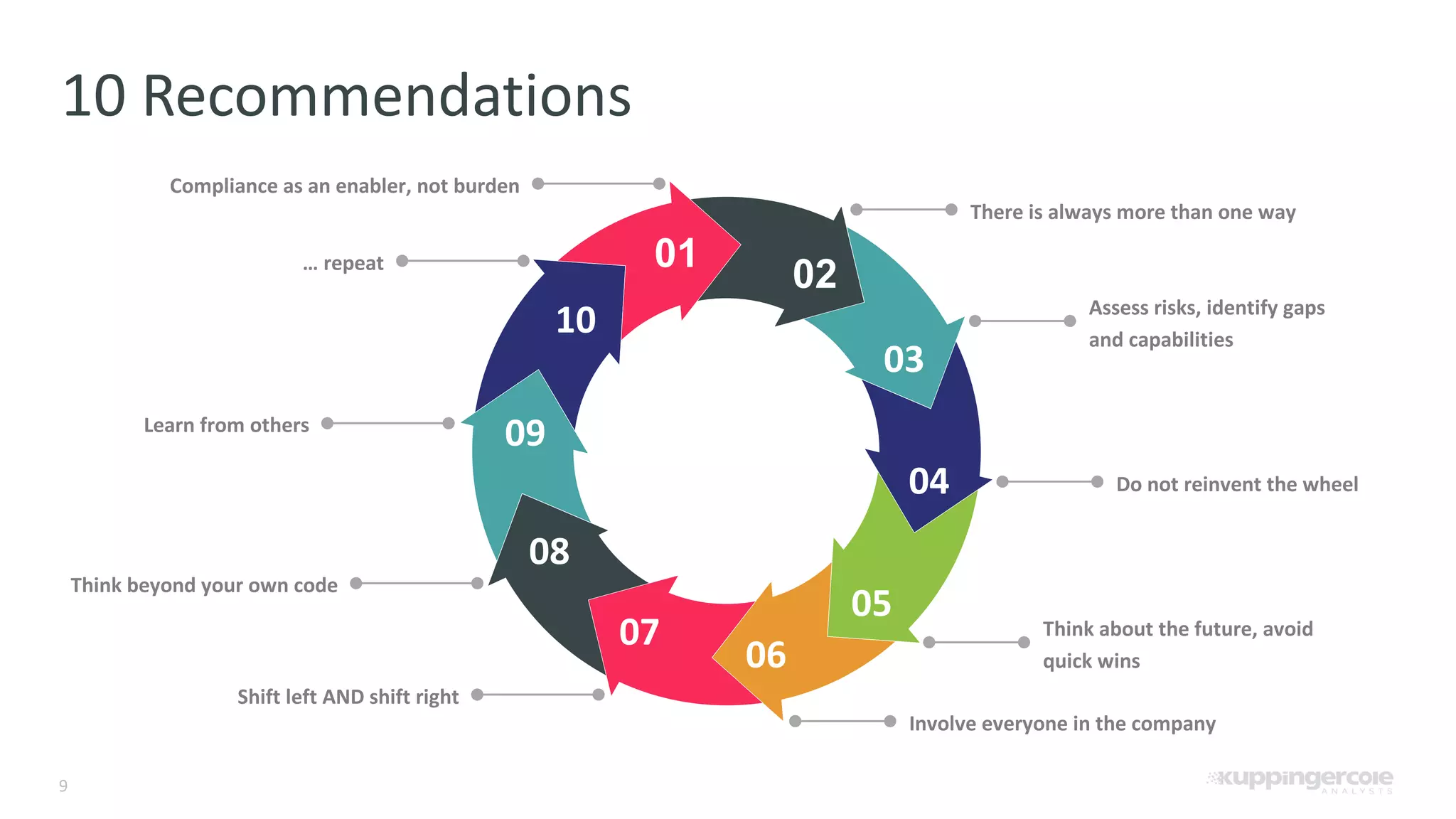
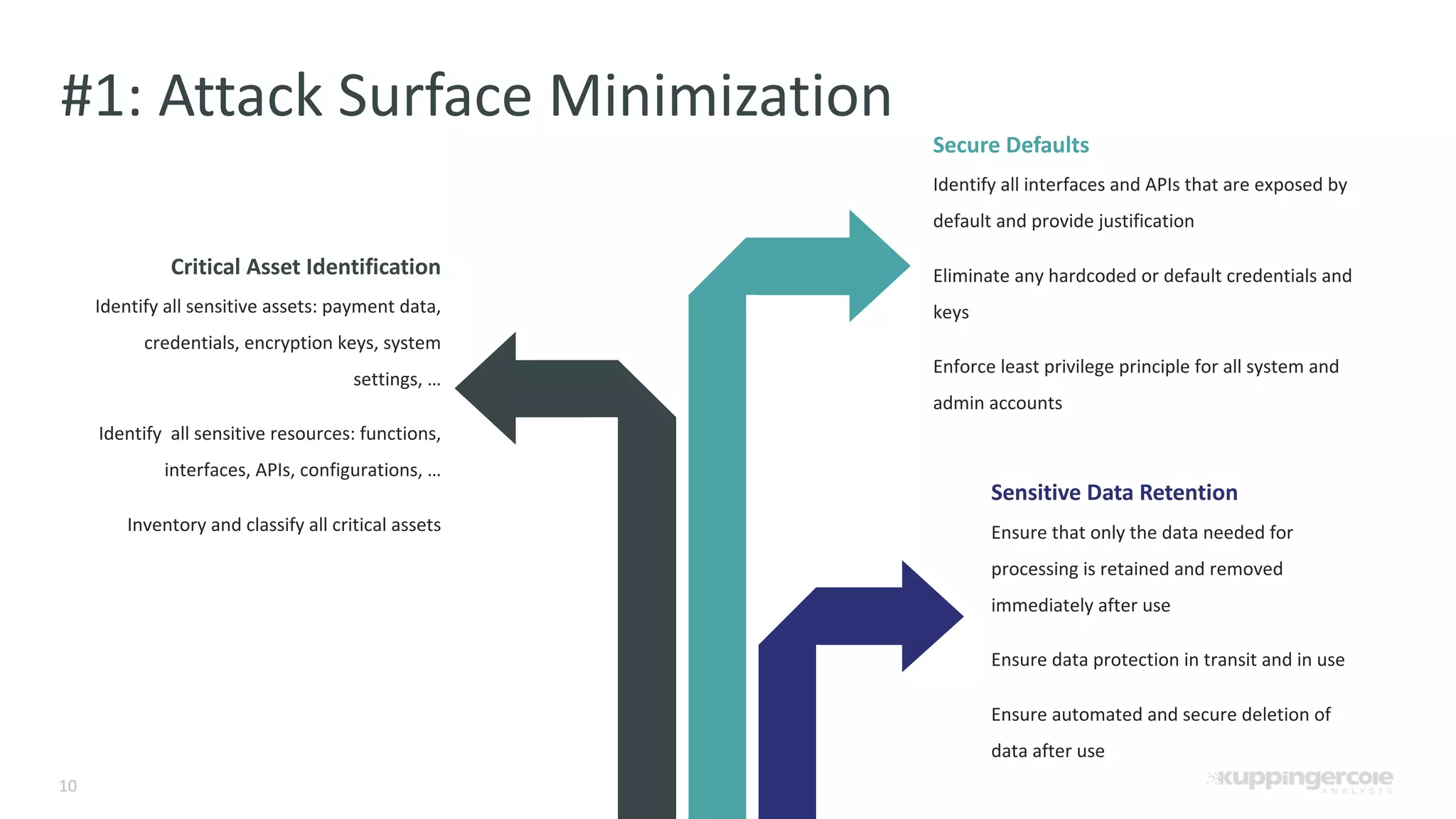
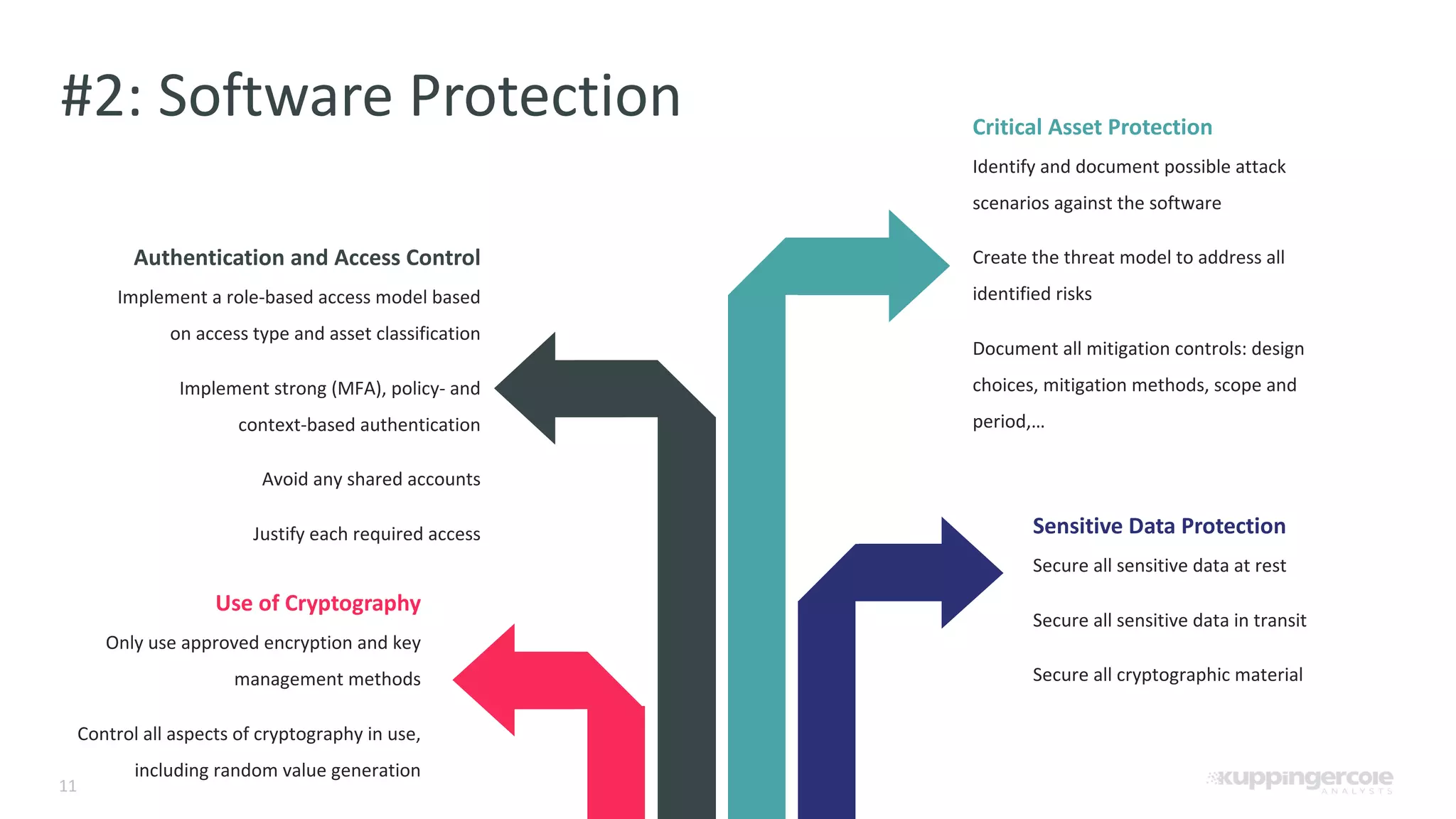
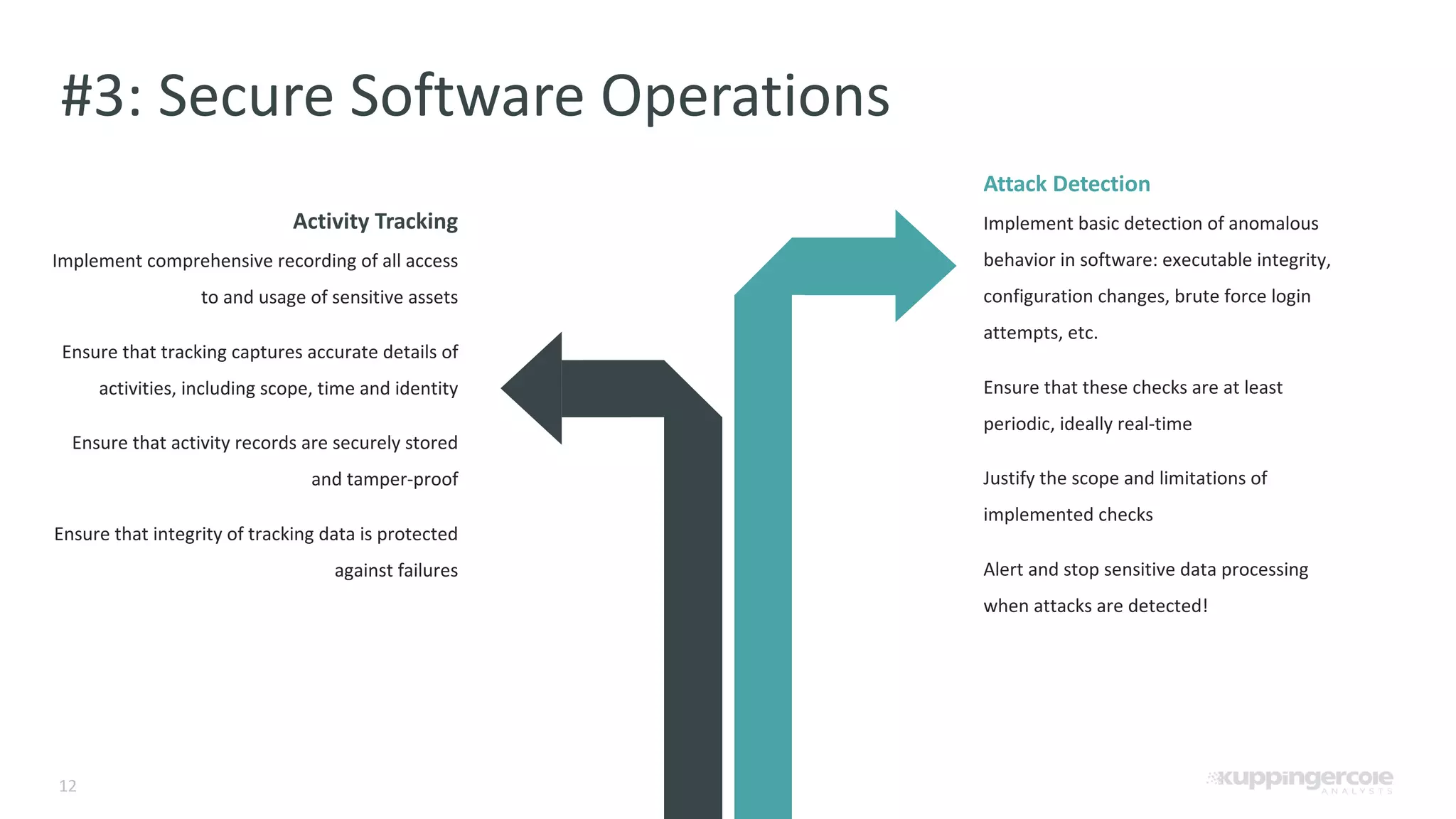
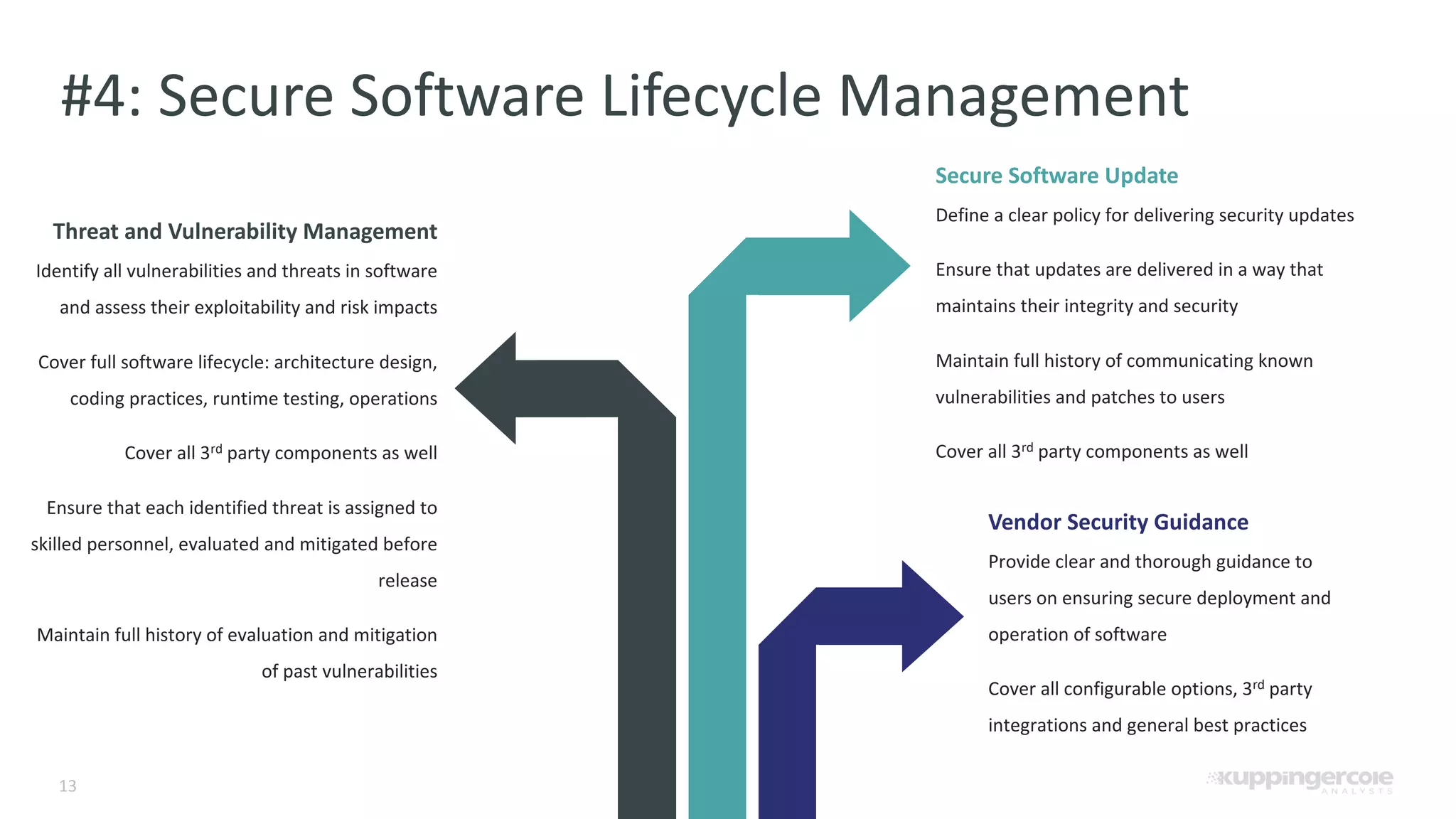
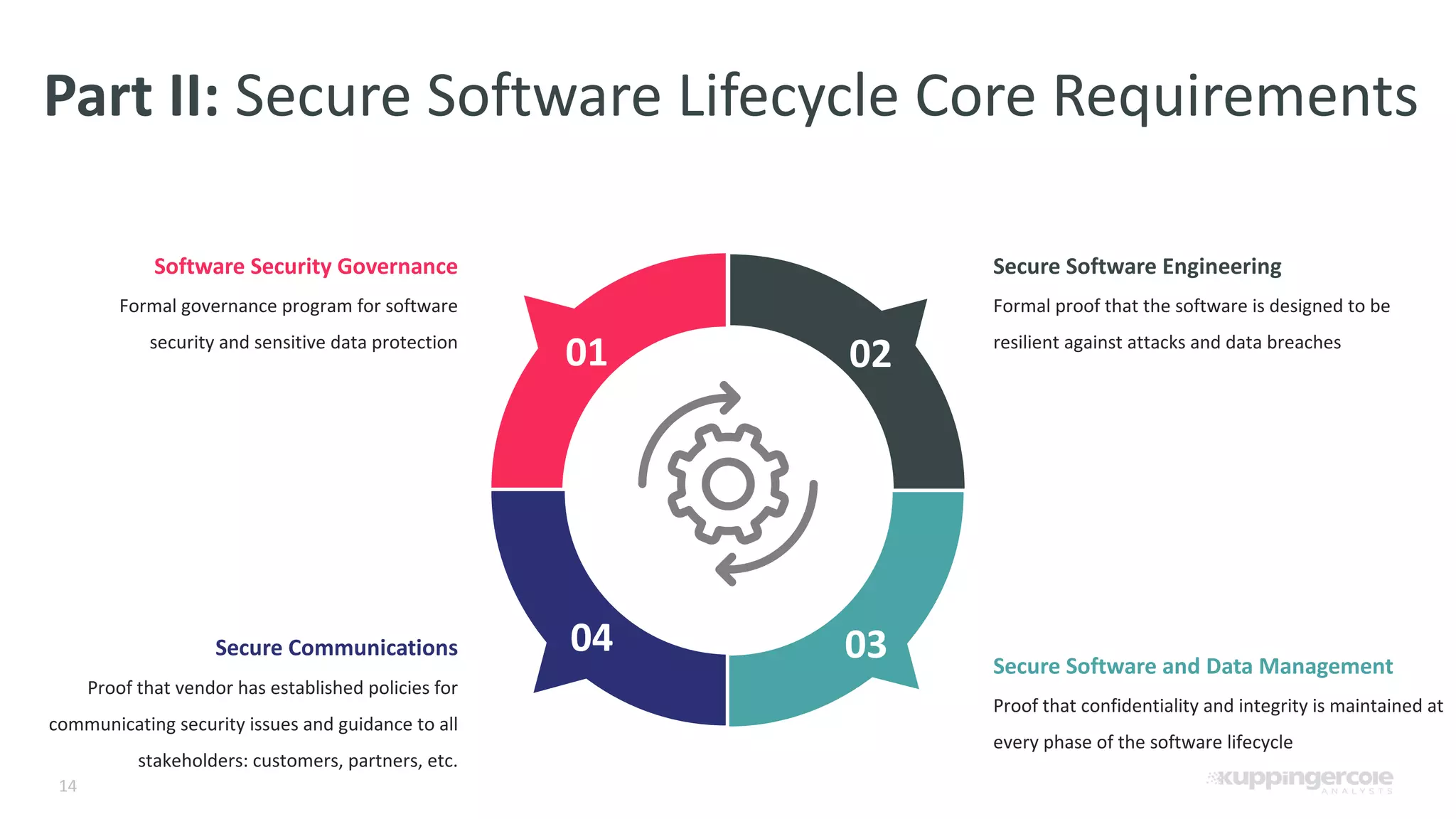
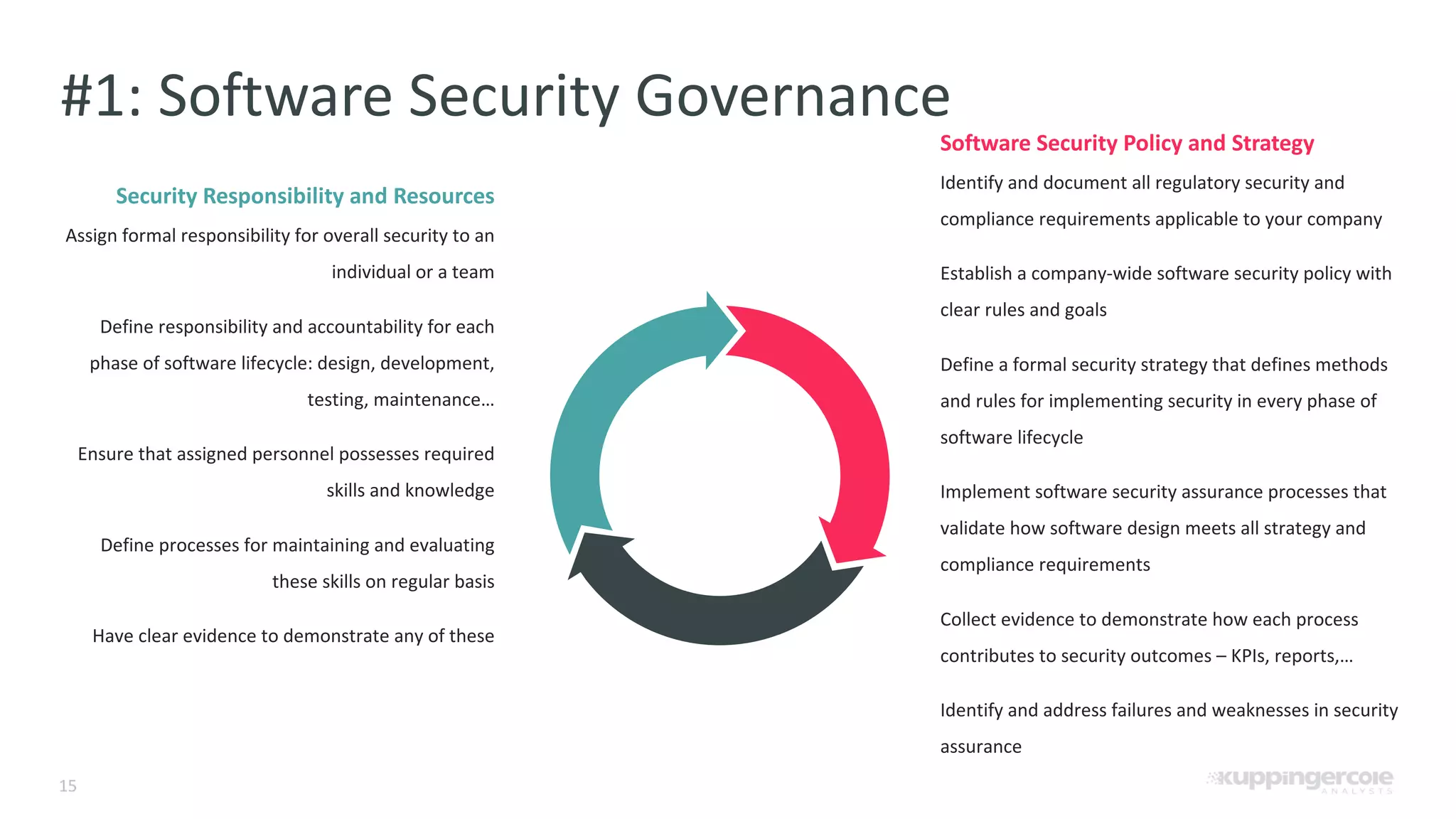
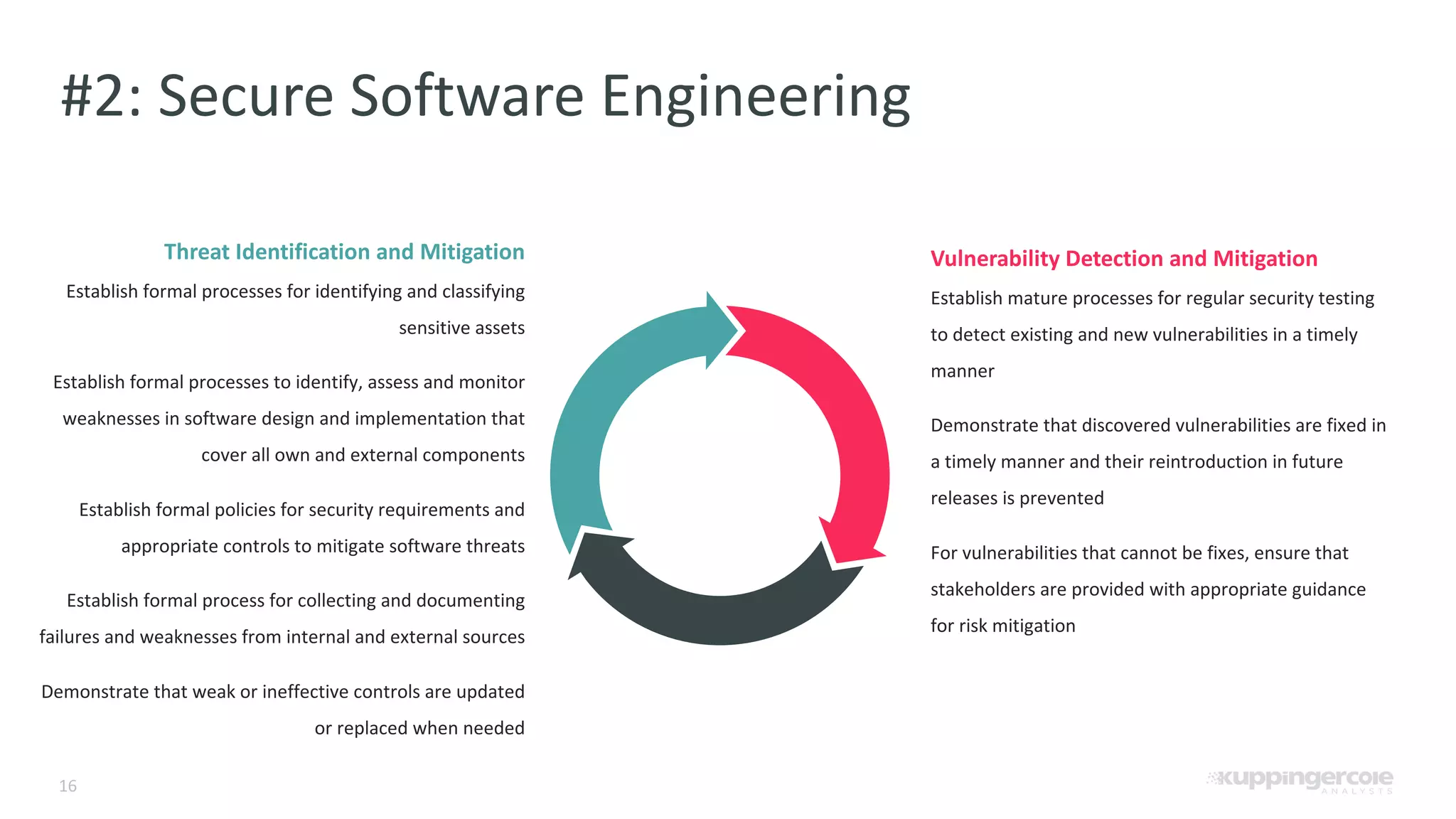
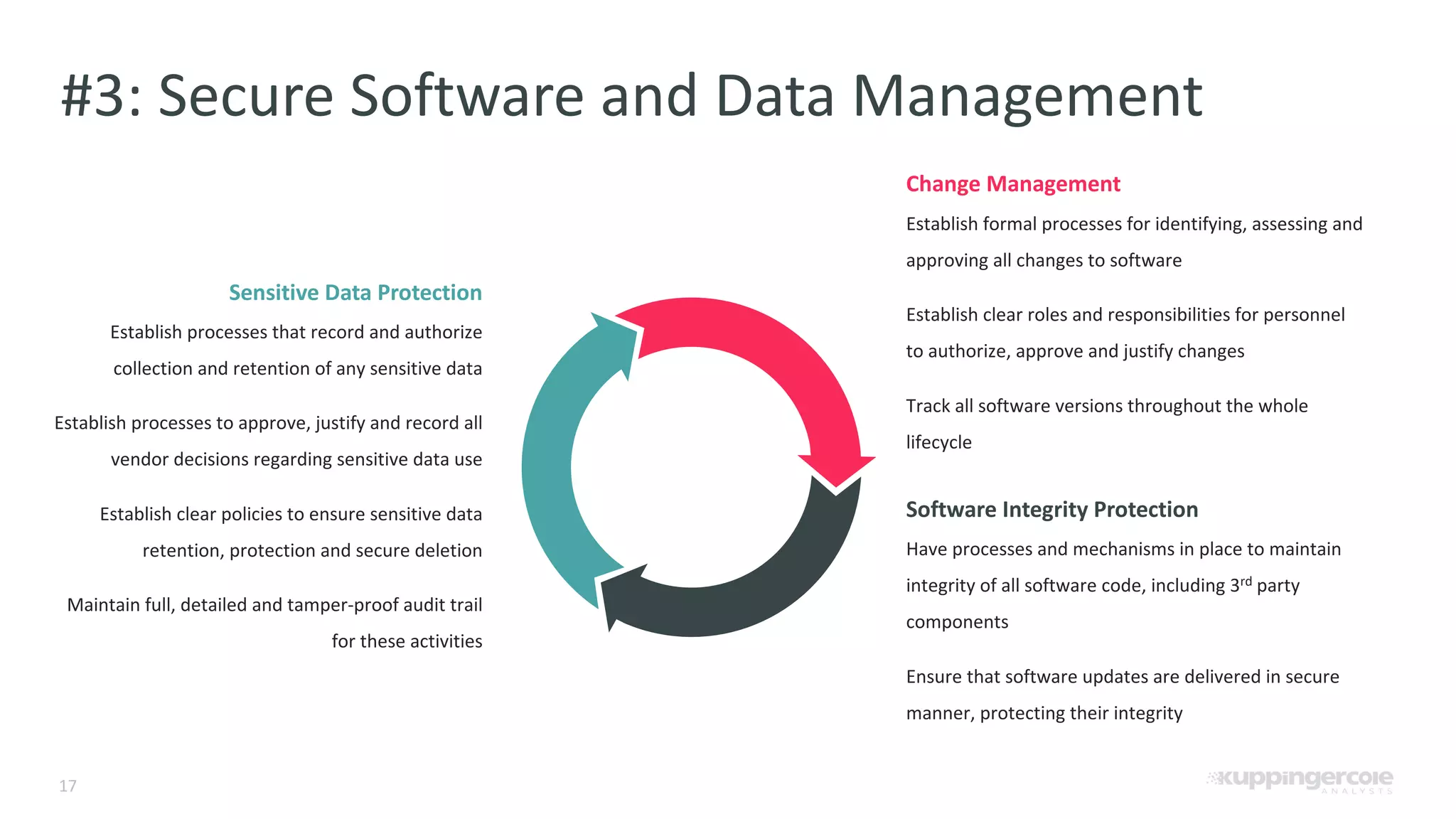
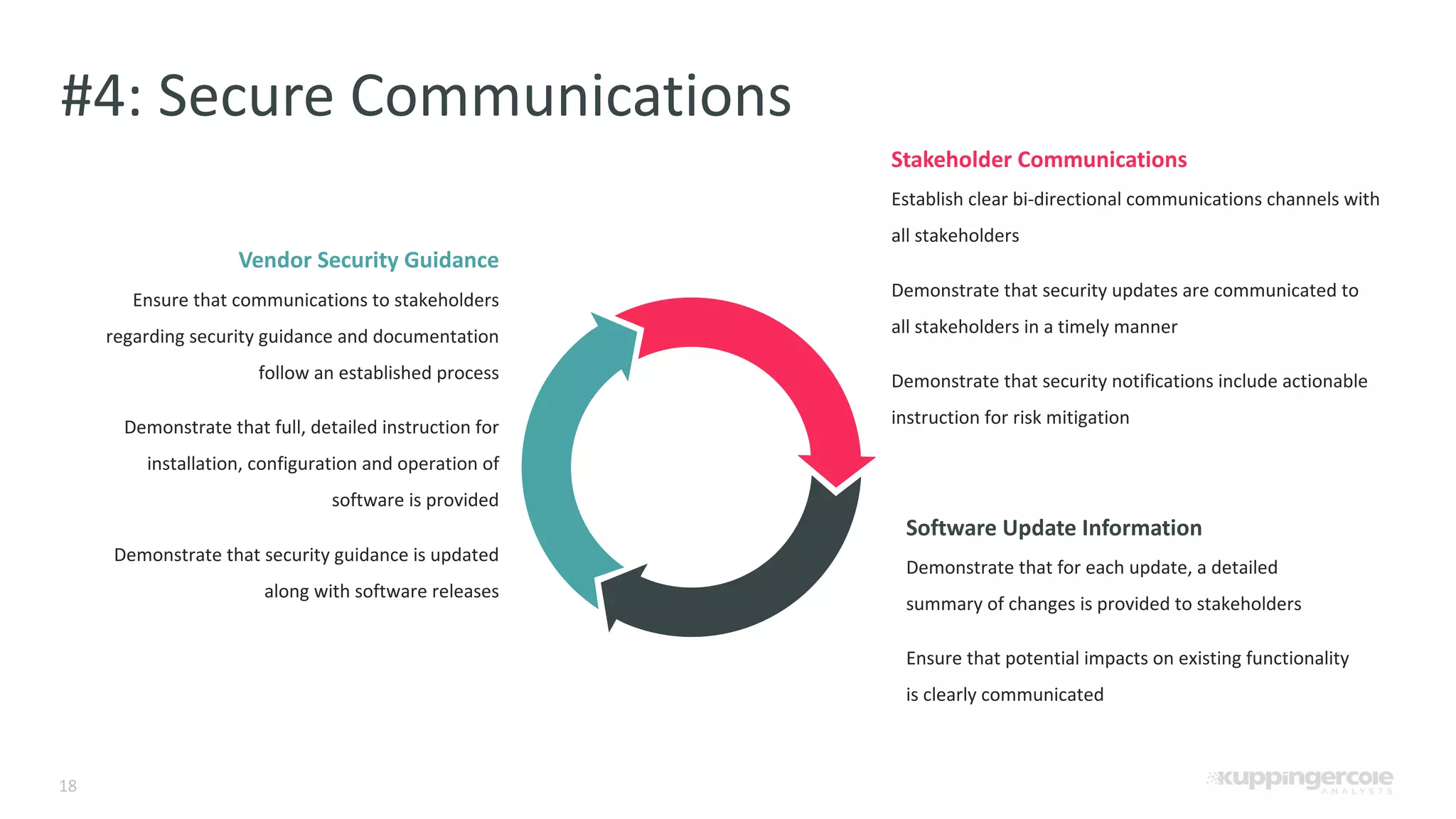
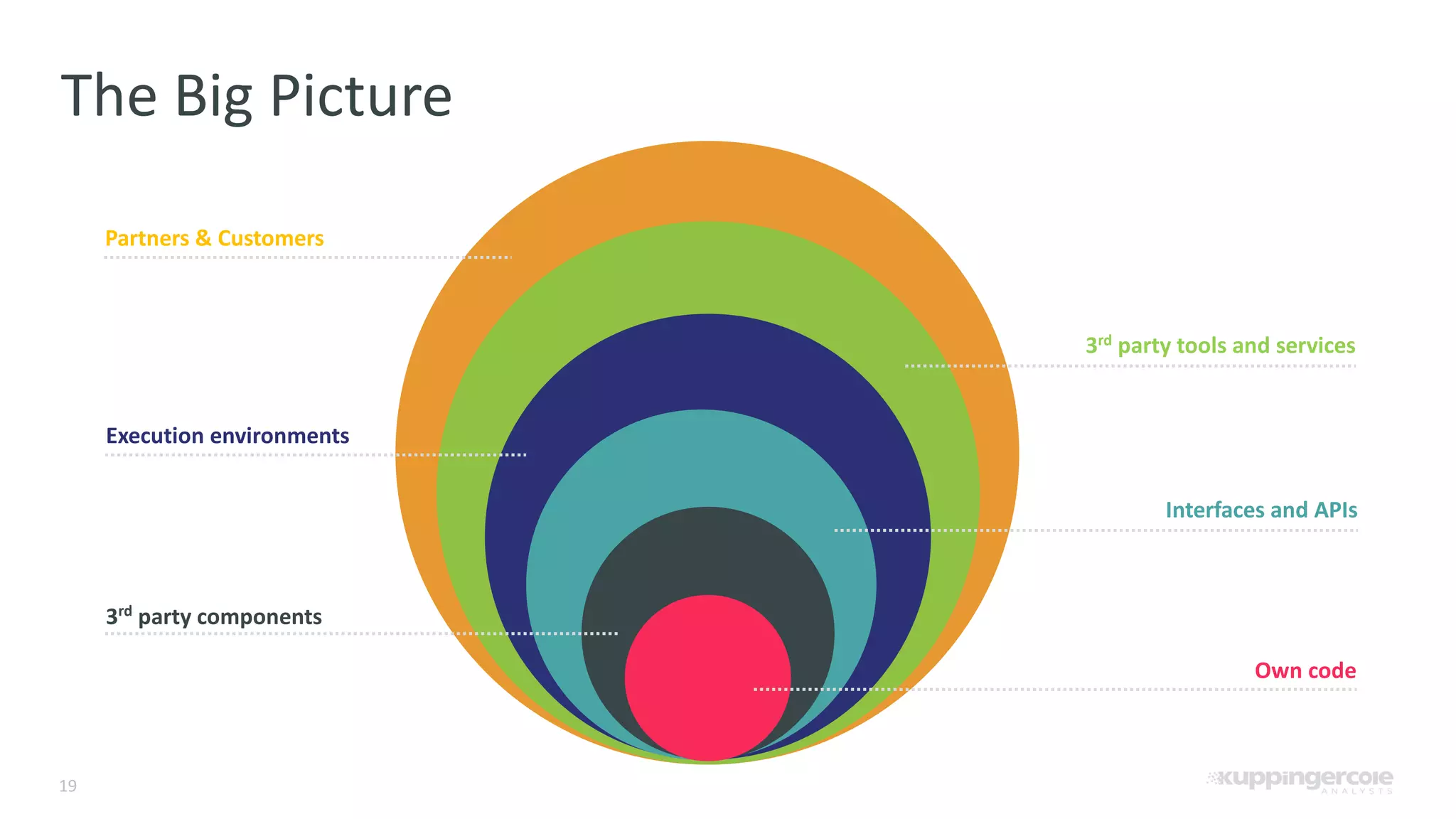
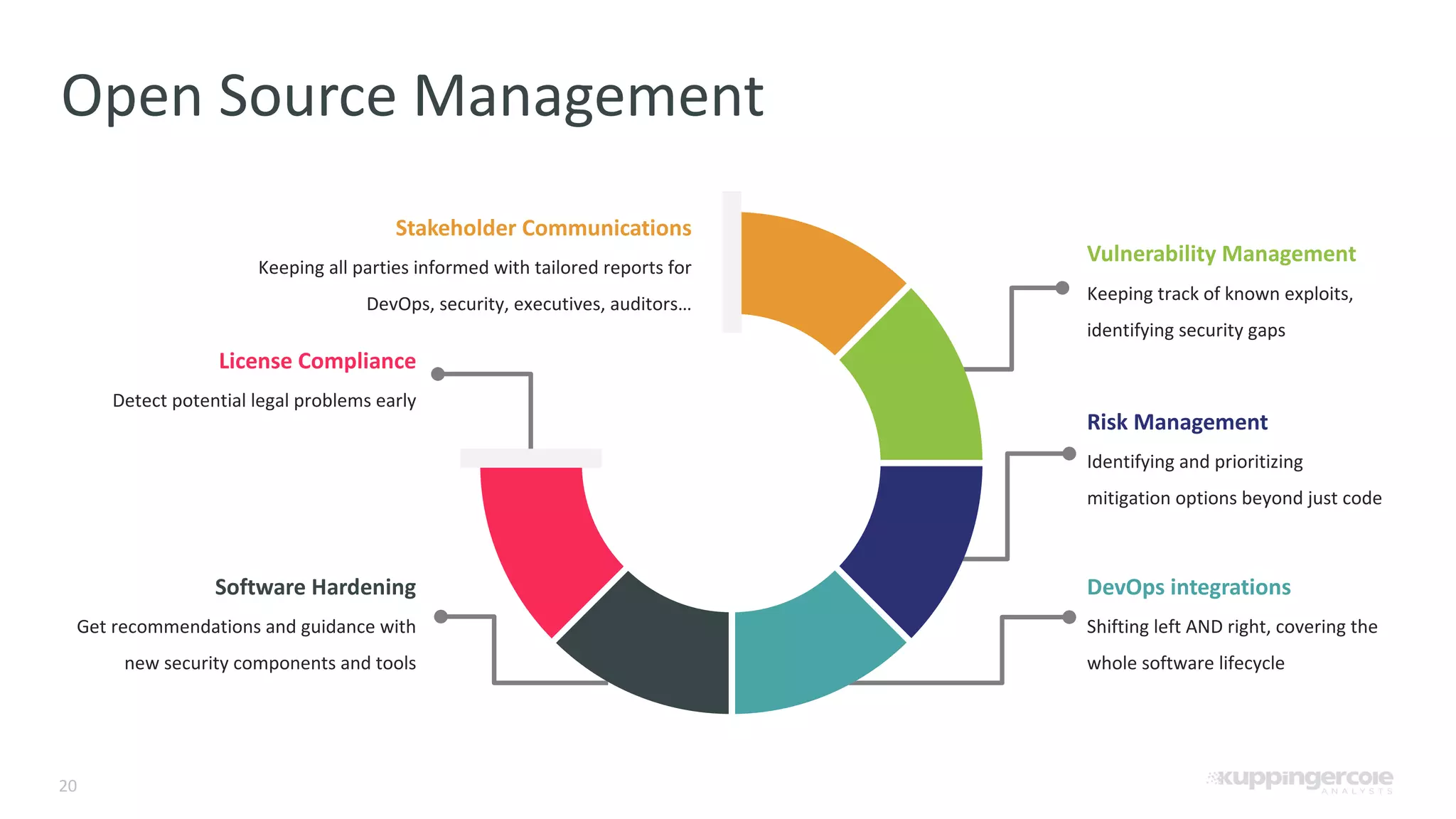
The document outlines the PCI Software Security Framework, consisting of two key standards: the Secure Software Standard (SSS) and the Secure Software Lifecycle Standard (SSLC), aimed at enhancing the security of payment software across its development and operational lifecycle. It emphasizes the integration of security into business practices, highlights critical software protection requirements, and offers recommendations for effective risk management, vulnerability detection, and secure operations. The framework also underscores the importance of stakeholder communication and governance to ensure ongoing compliance and security protections.