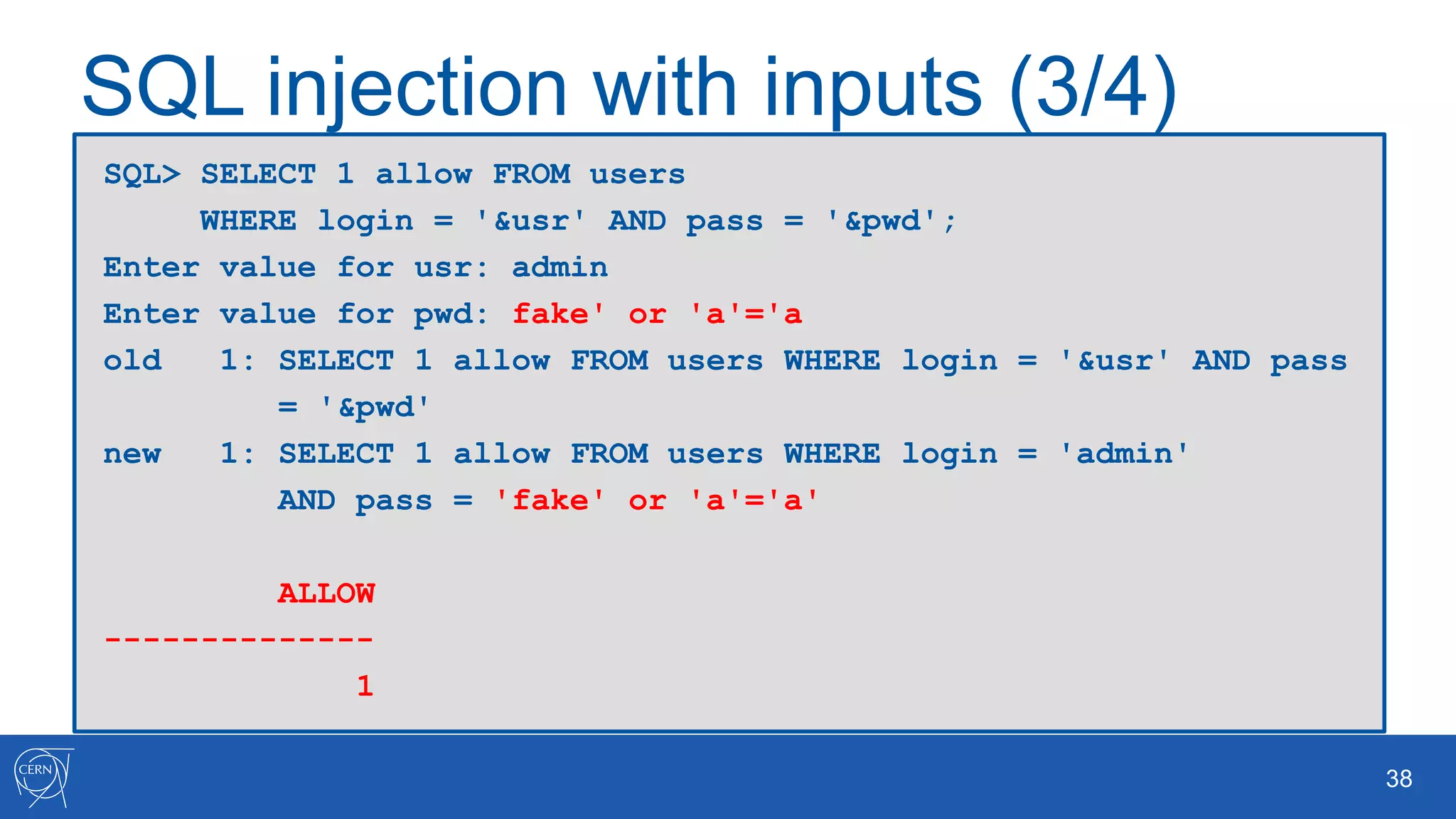
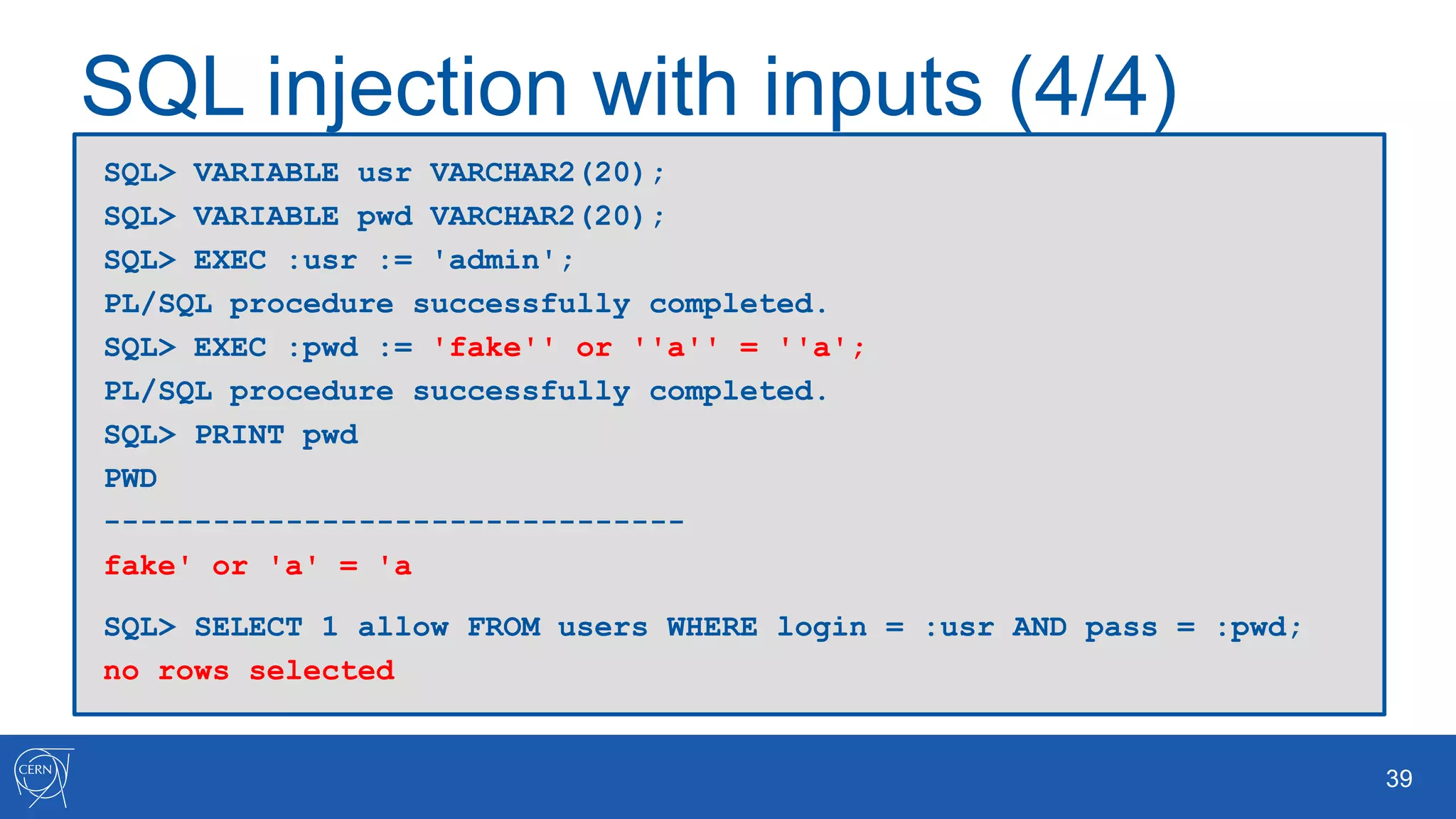
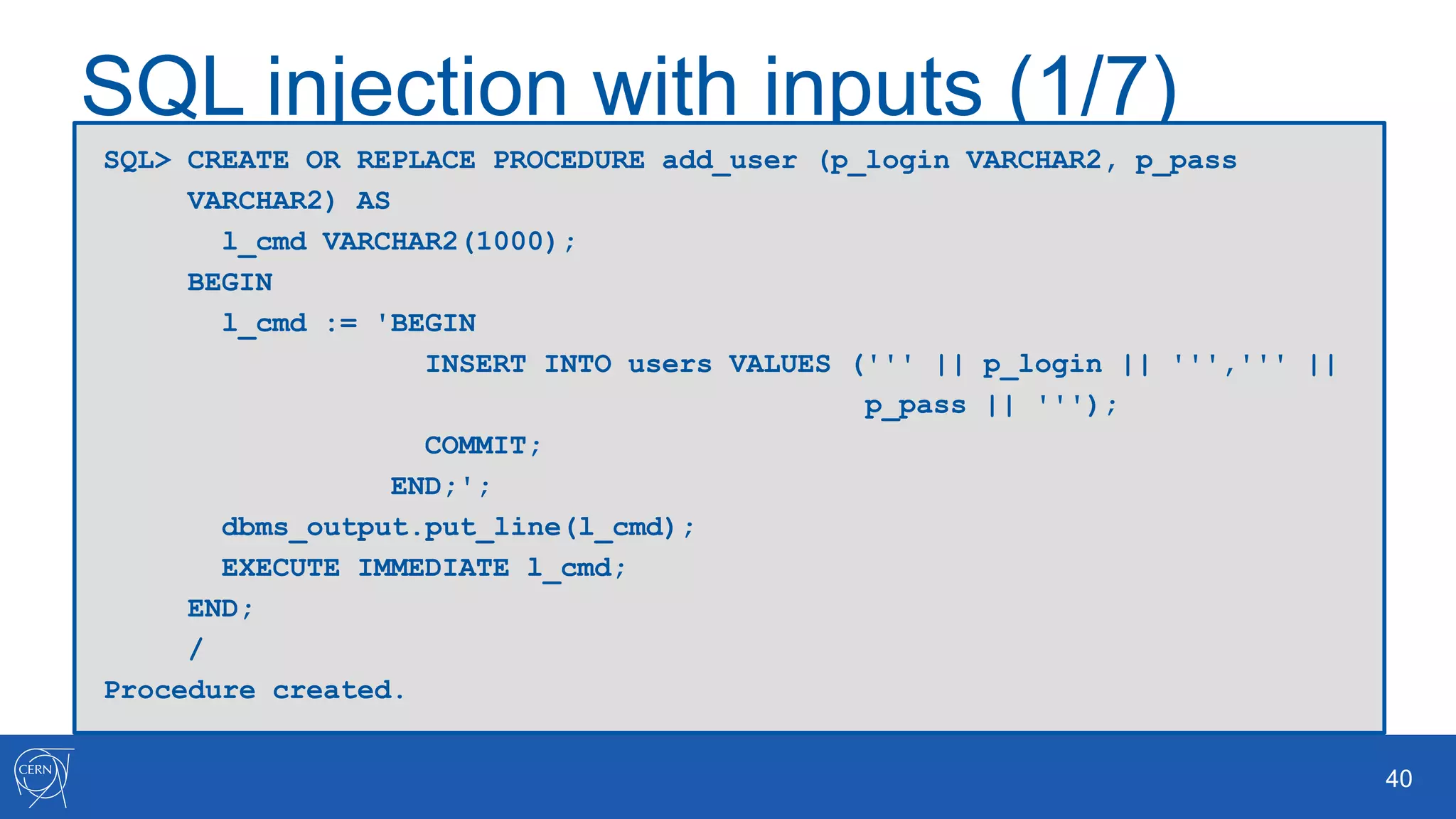
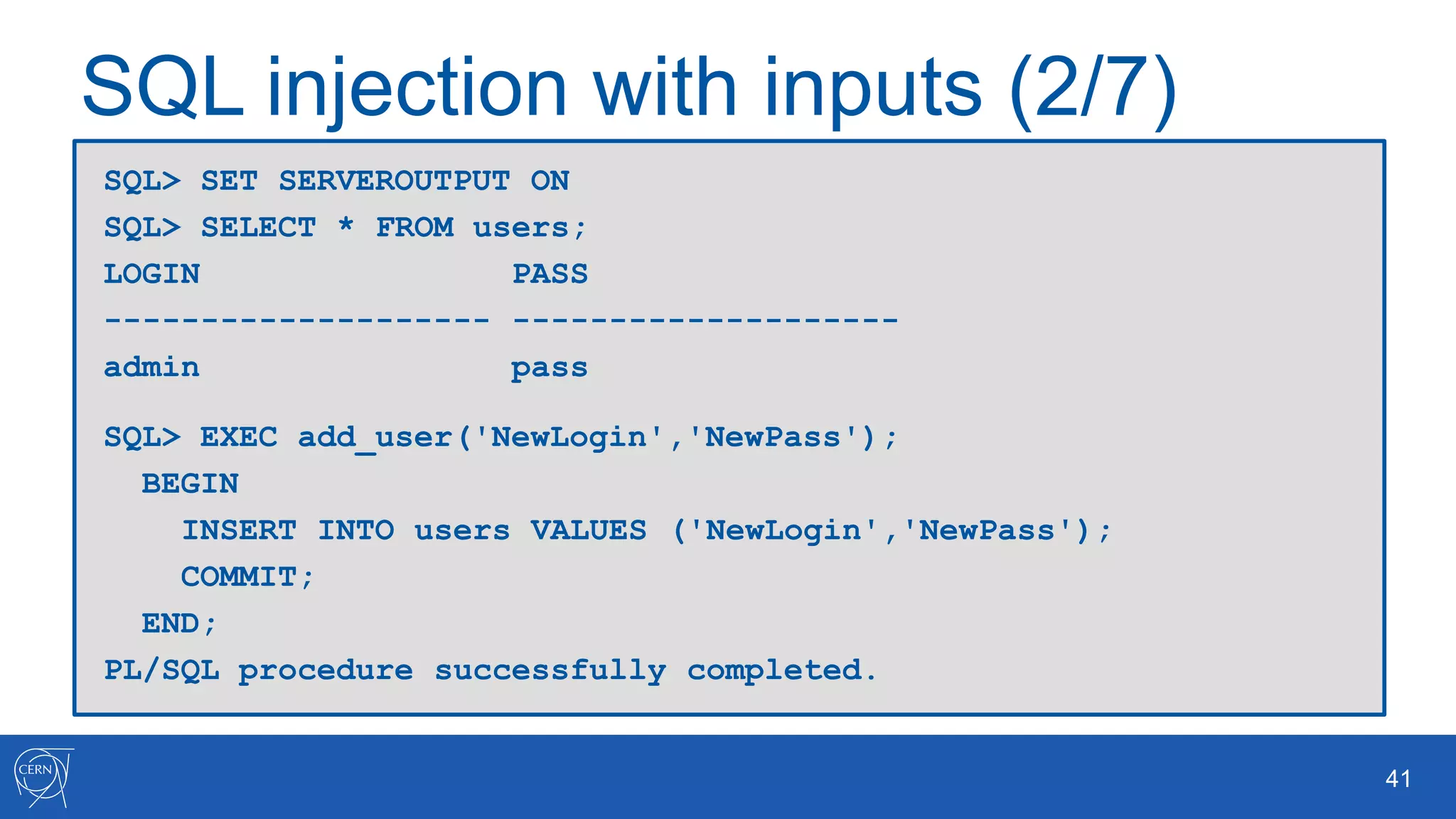
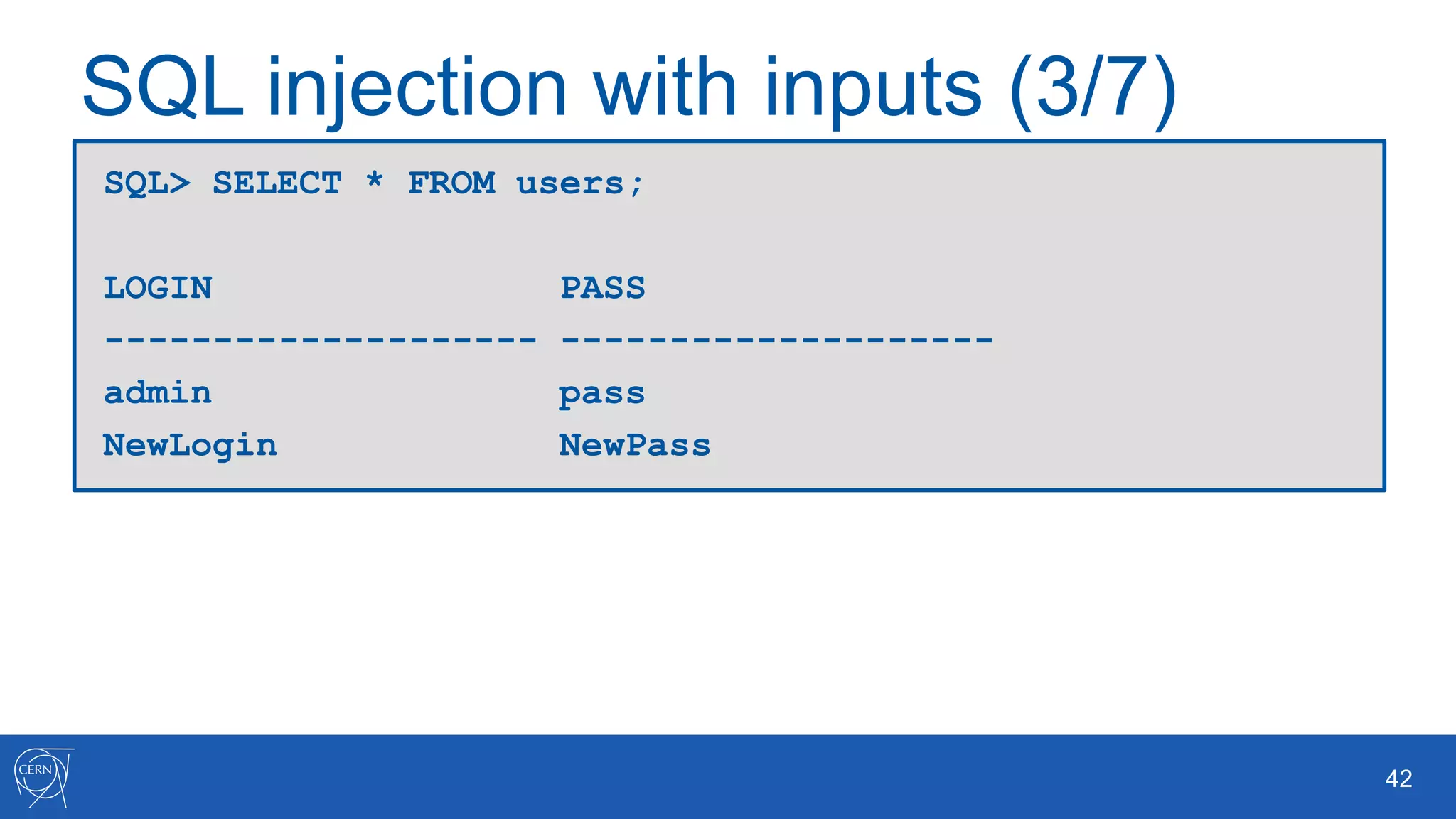
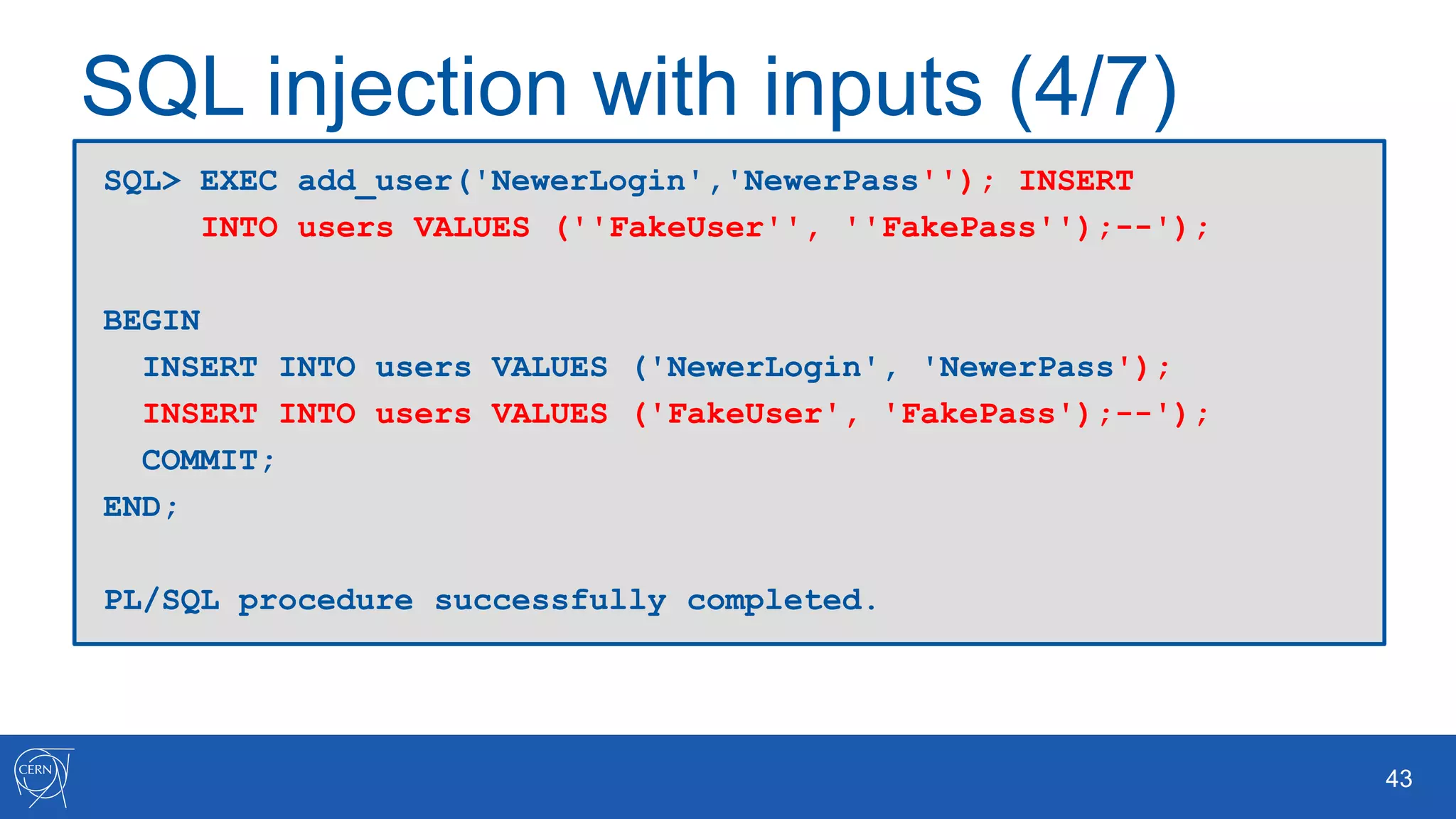
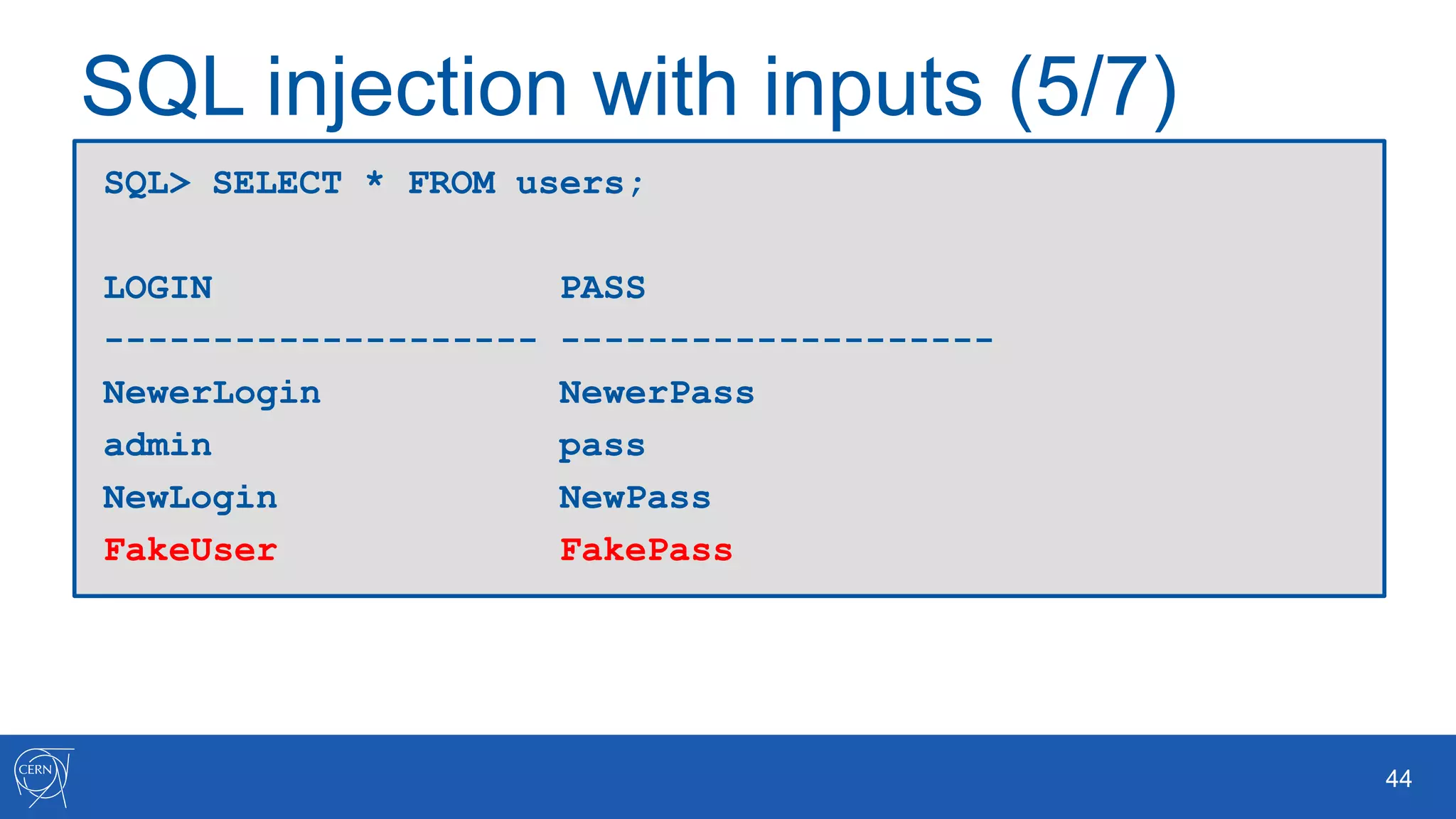
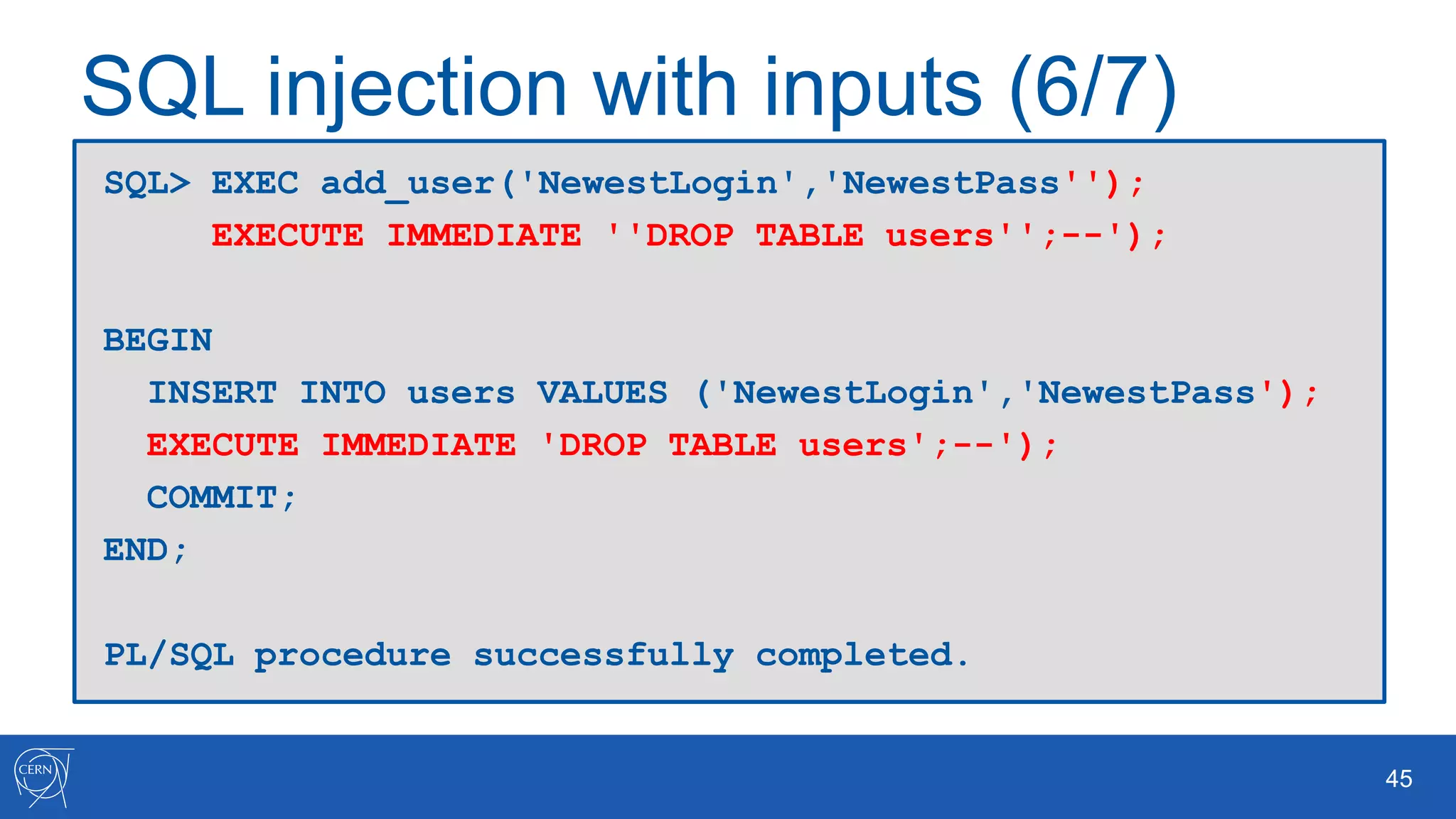
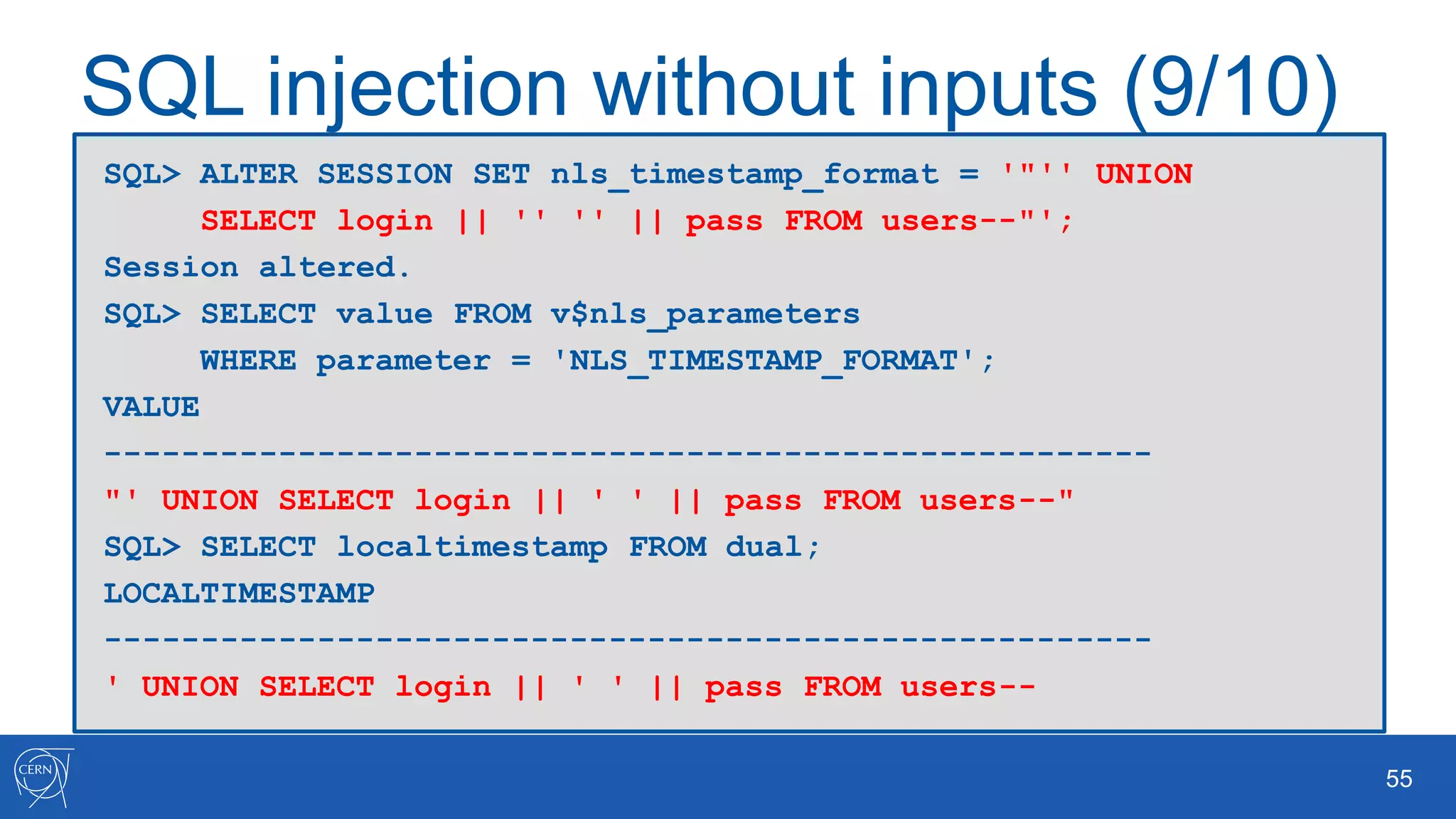
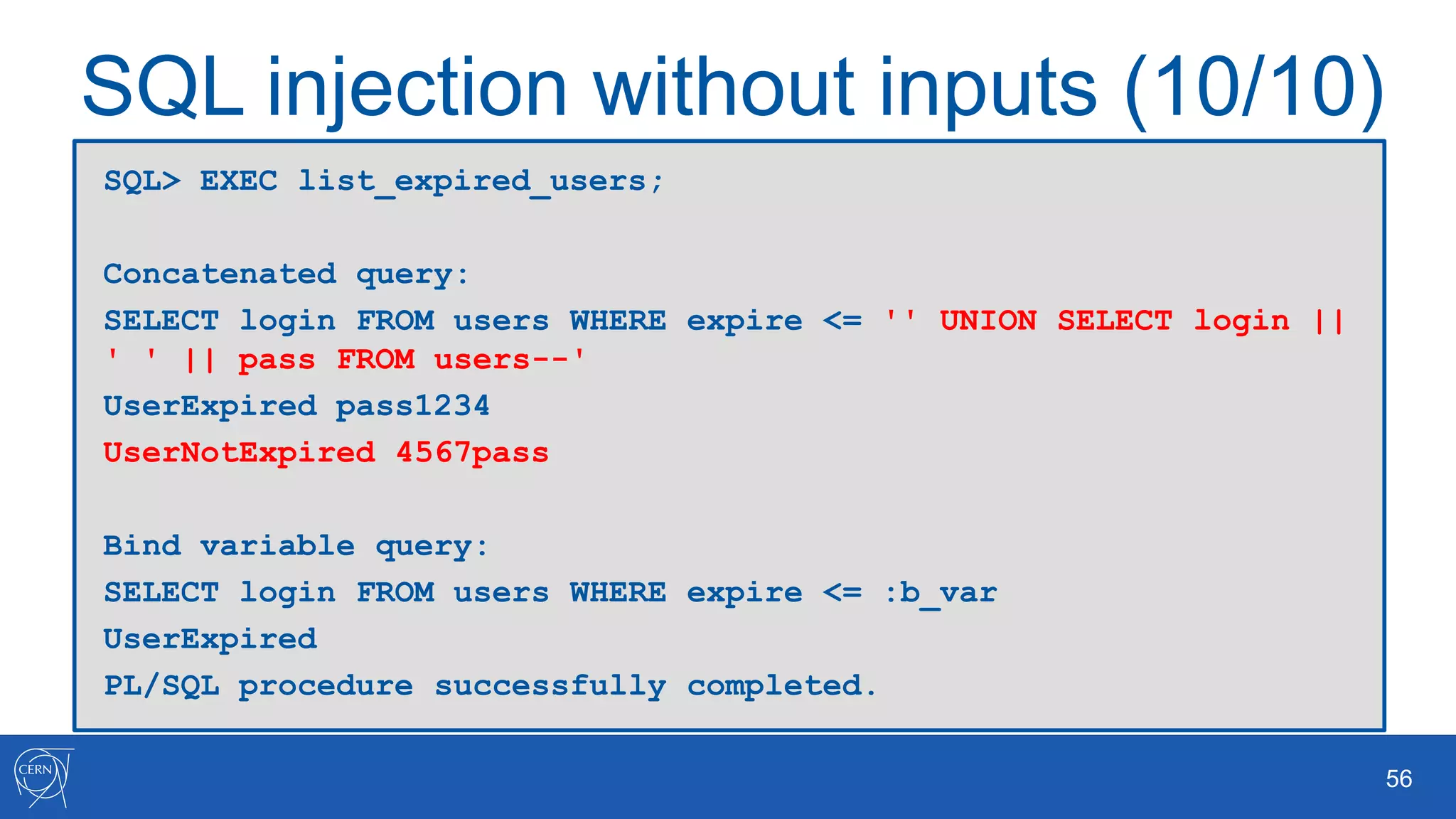
The document outlines key aspects of Oracle database user management, including user creation, roles, privileges, and encryption. It details password policies, SQL injection risks, and best practices for securing applications, emphasizing the importance of using bind variables and proper input handling to prevent SQL injection attacks. Additionally, encryption methods for protecting sensitive data and ensuring secure communication are discussed.








![17 Useful privilege-related views View name Describes [ALL|USER]_COL_PRIVS Column object grants for which the current [user or PUBLIC|user] is owner, grantor or grantee [ALL|USER]_COL_PRIVS_MADE Column object grants for which the current user is object [owner or grantor|owner] [ALL|USER]_COL_PRIVS_RECD Column object grants for which the current [user or PUBLIC|user] is grantee [ALL|USER]_TAB_PRIVS_MADE Object grants [made by the current user or made on the objects owned by current user|made on the objects owned by current user] [ALL|USER]_TAB_PRIVS_RECD Object grants for which the [user or PUBLIC|user] is the grantee [ALL|USER]_TAB_PRIVS Grants on objects where the current [user or PUBLIC|user] is grantee USER_SYS_PRIVS System privileges granted to the current user SESSION_PRIVS Privileges currently enabled for the current user](https://image.slidesharecdn.com/oracletutorials2013-oracledatabasesecurityfordevelopers-130502035302-phpapp01/75/Oracle-Database-Security-For-Developers-17-2048.jpg)