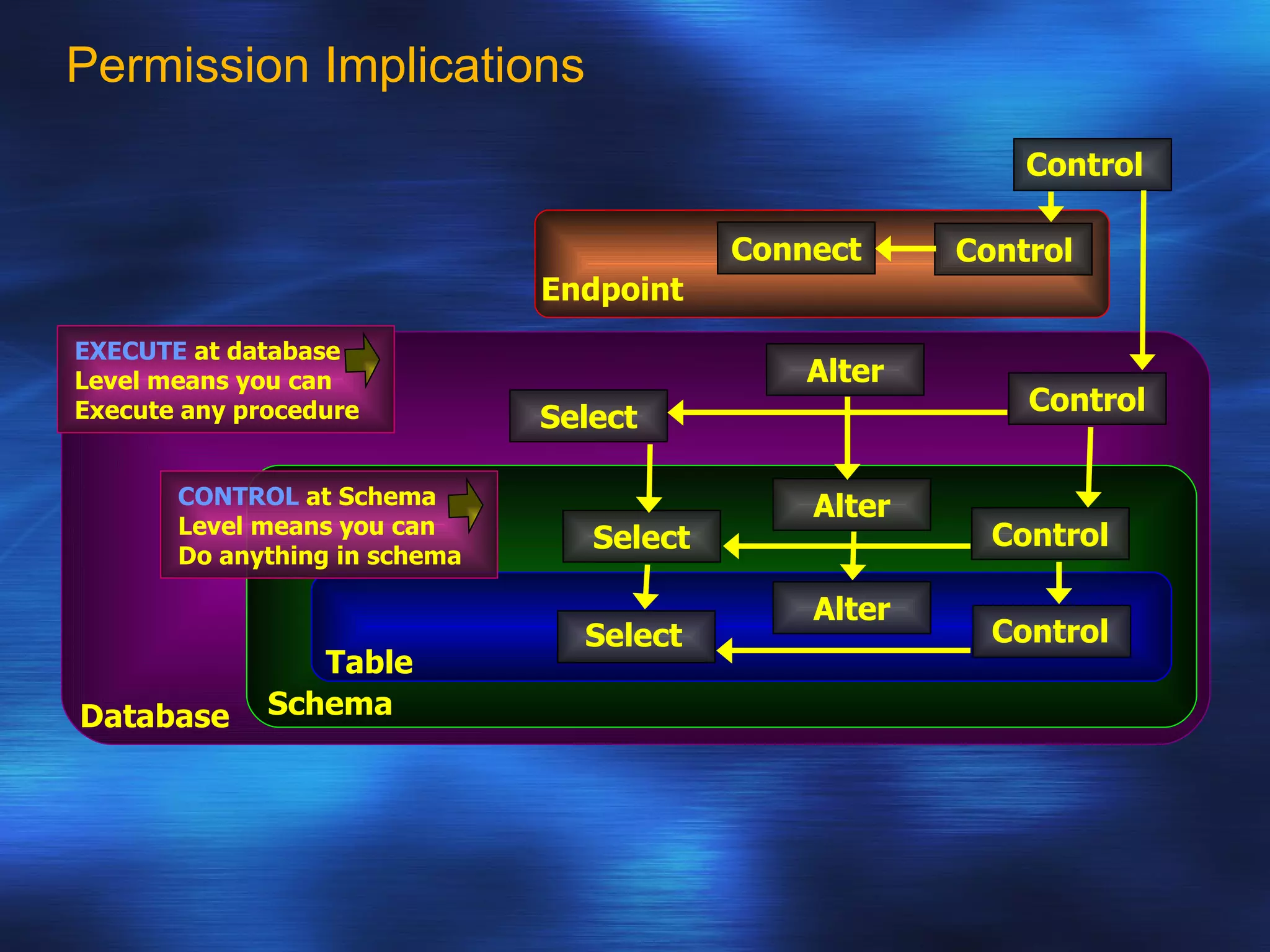
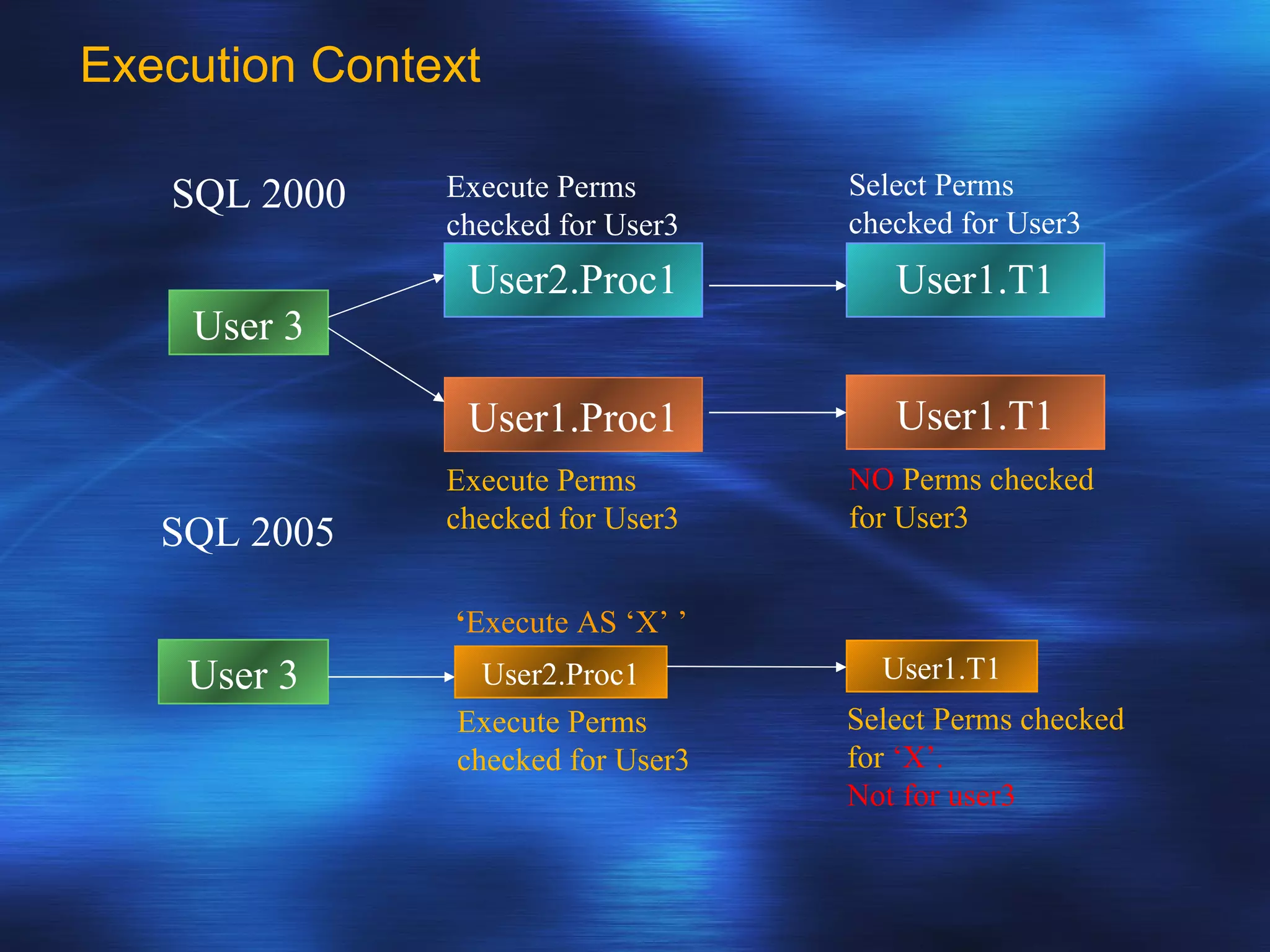
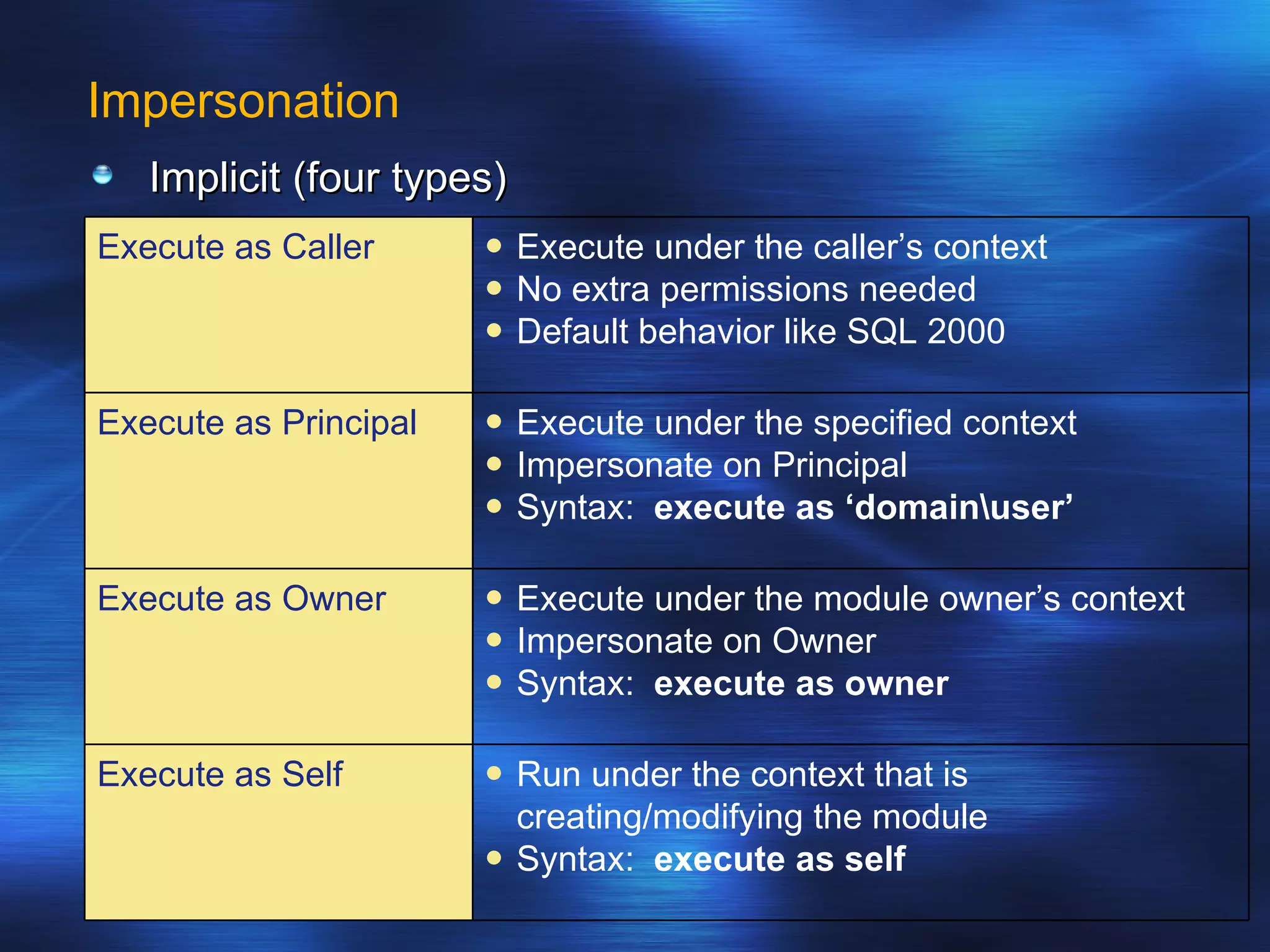
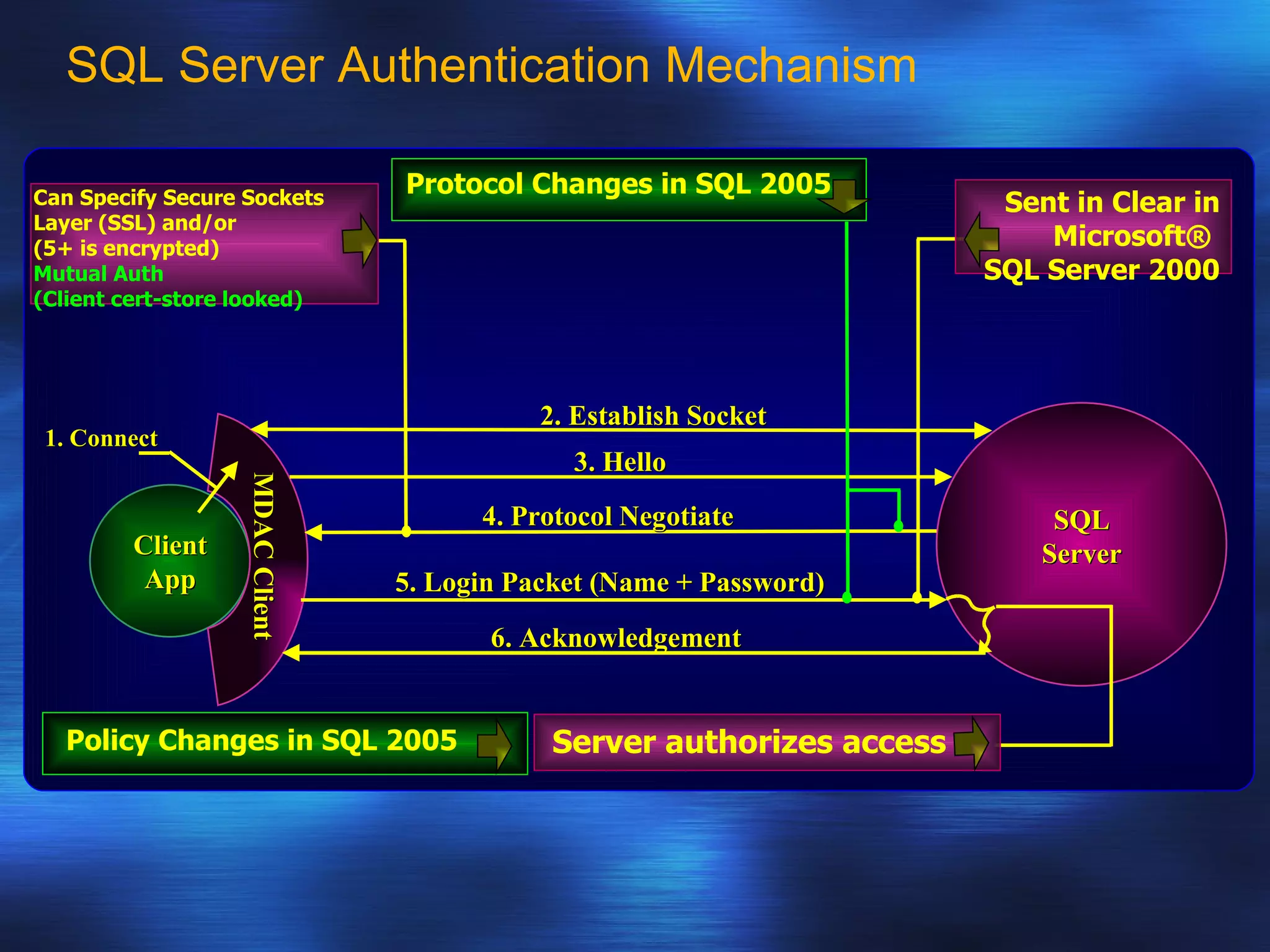
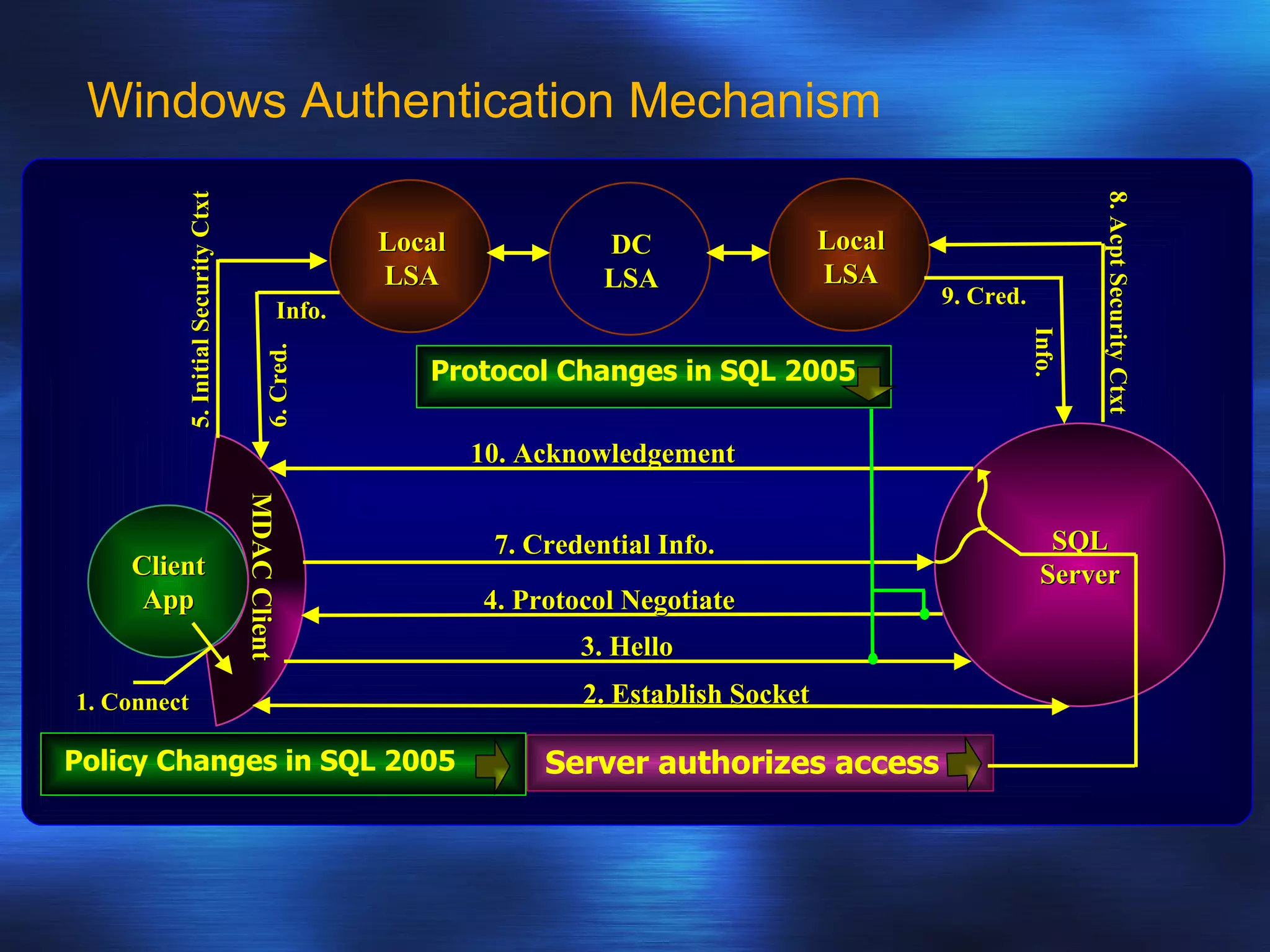
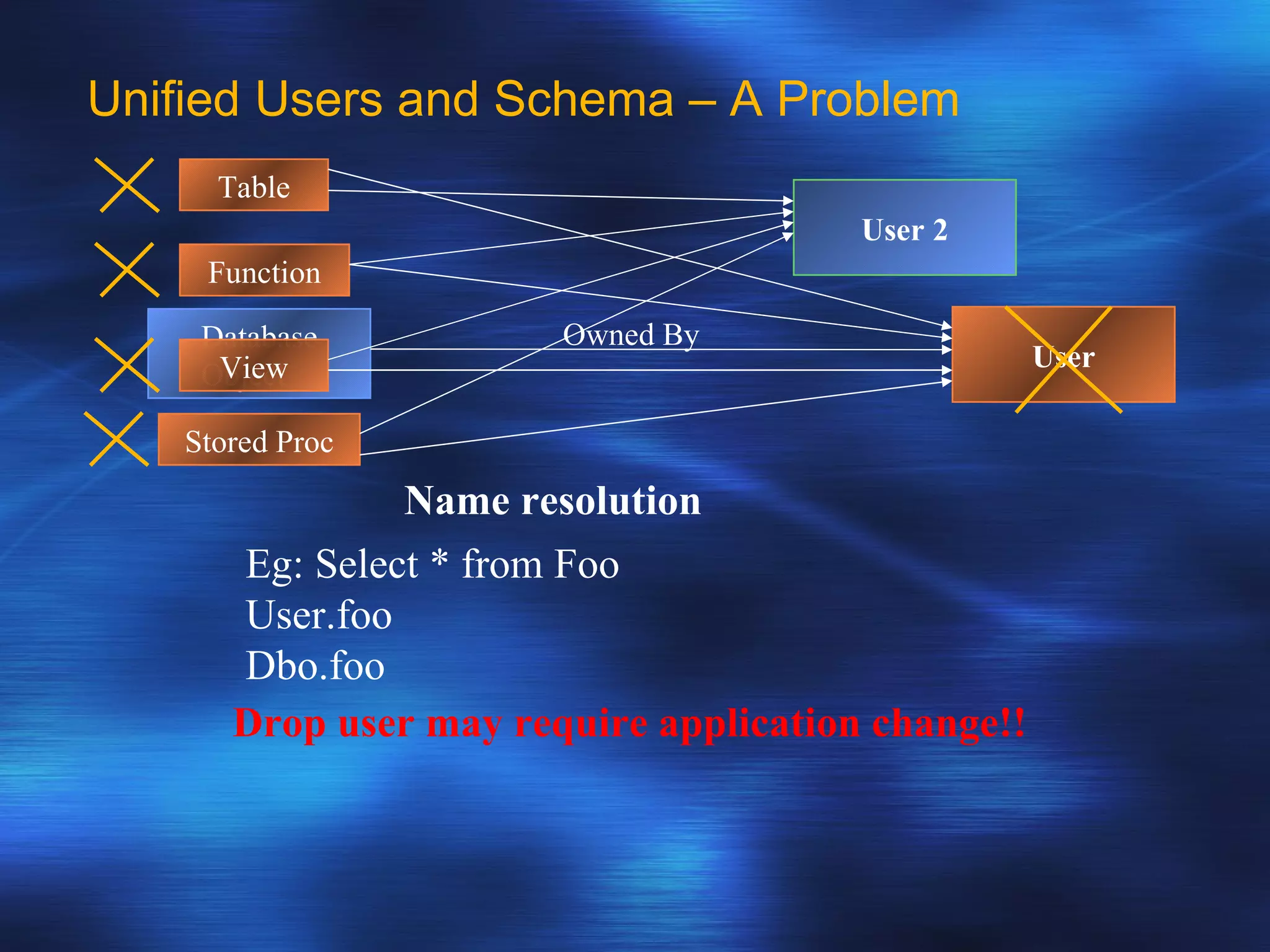
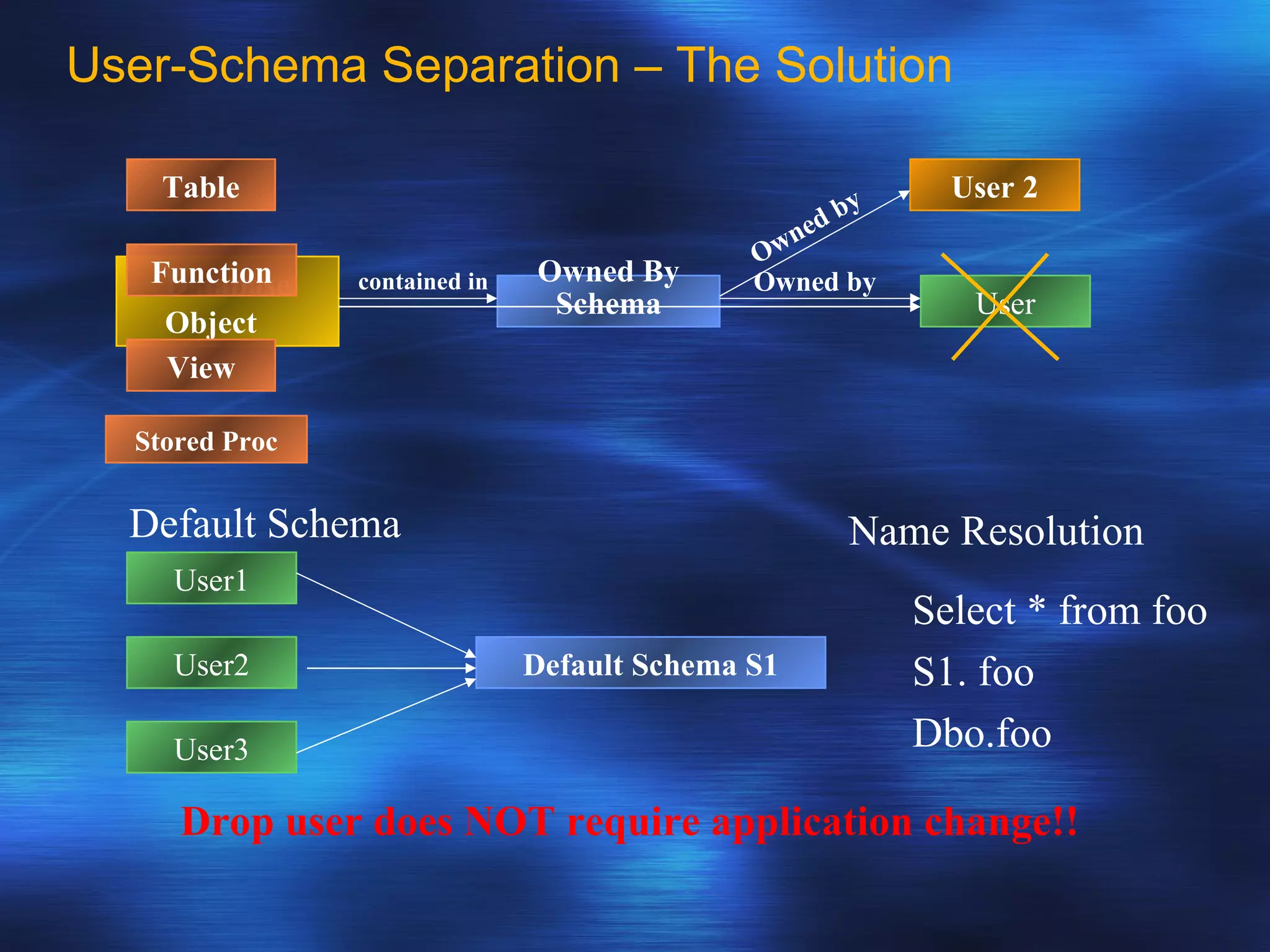
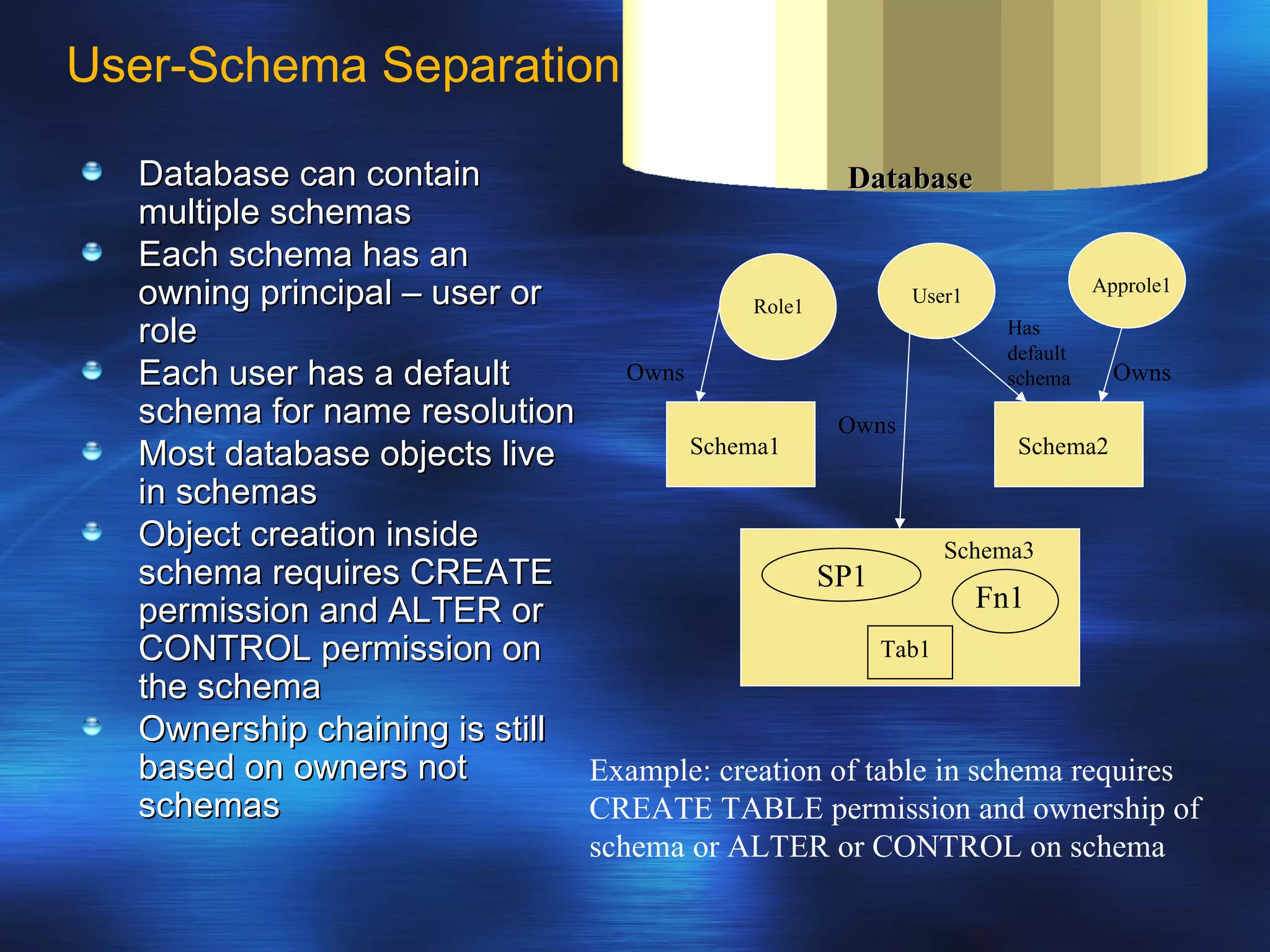
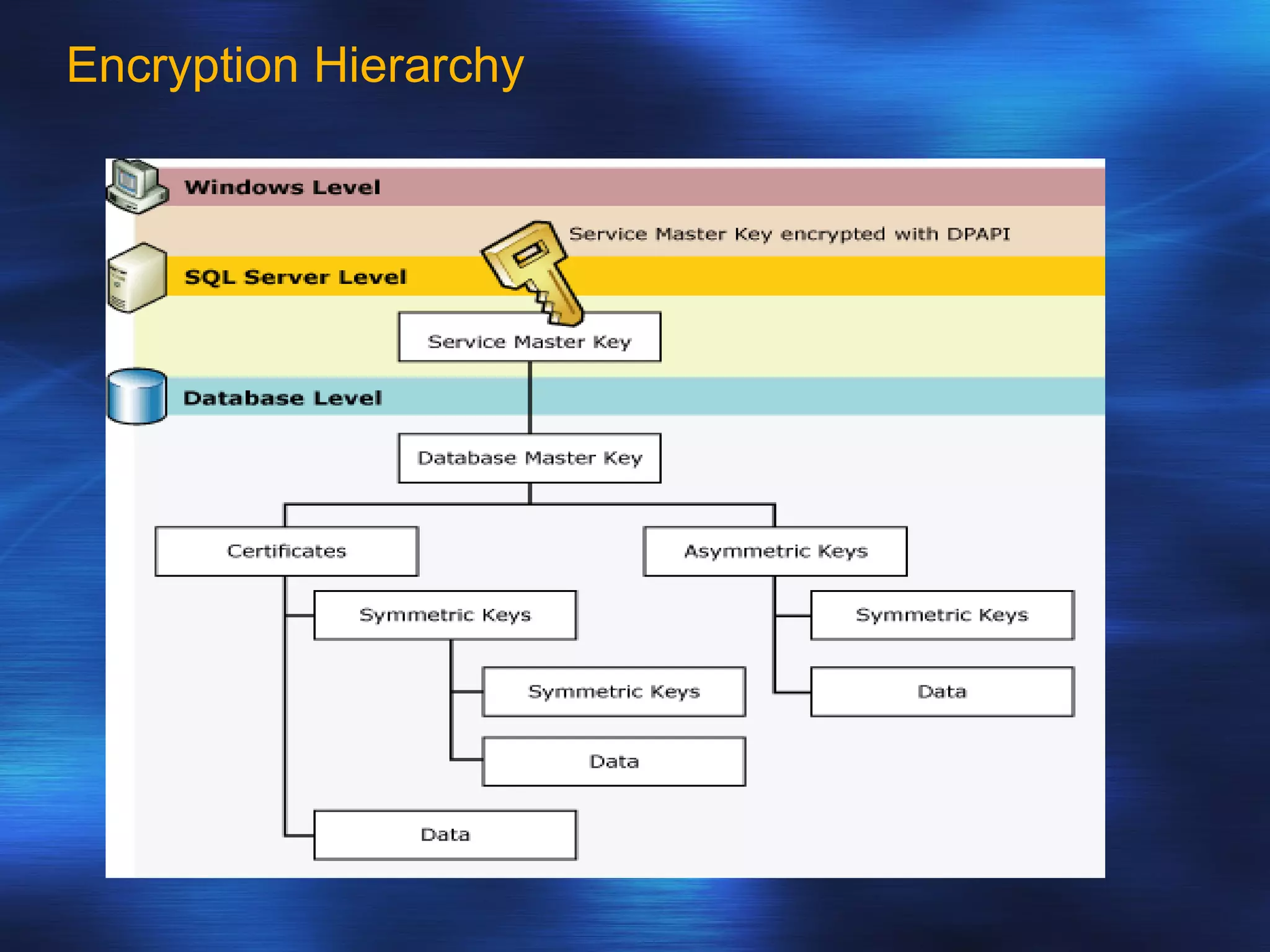
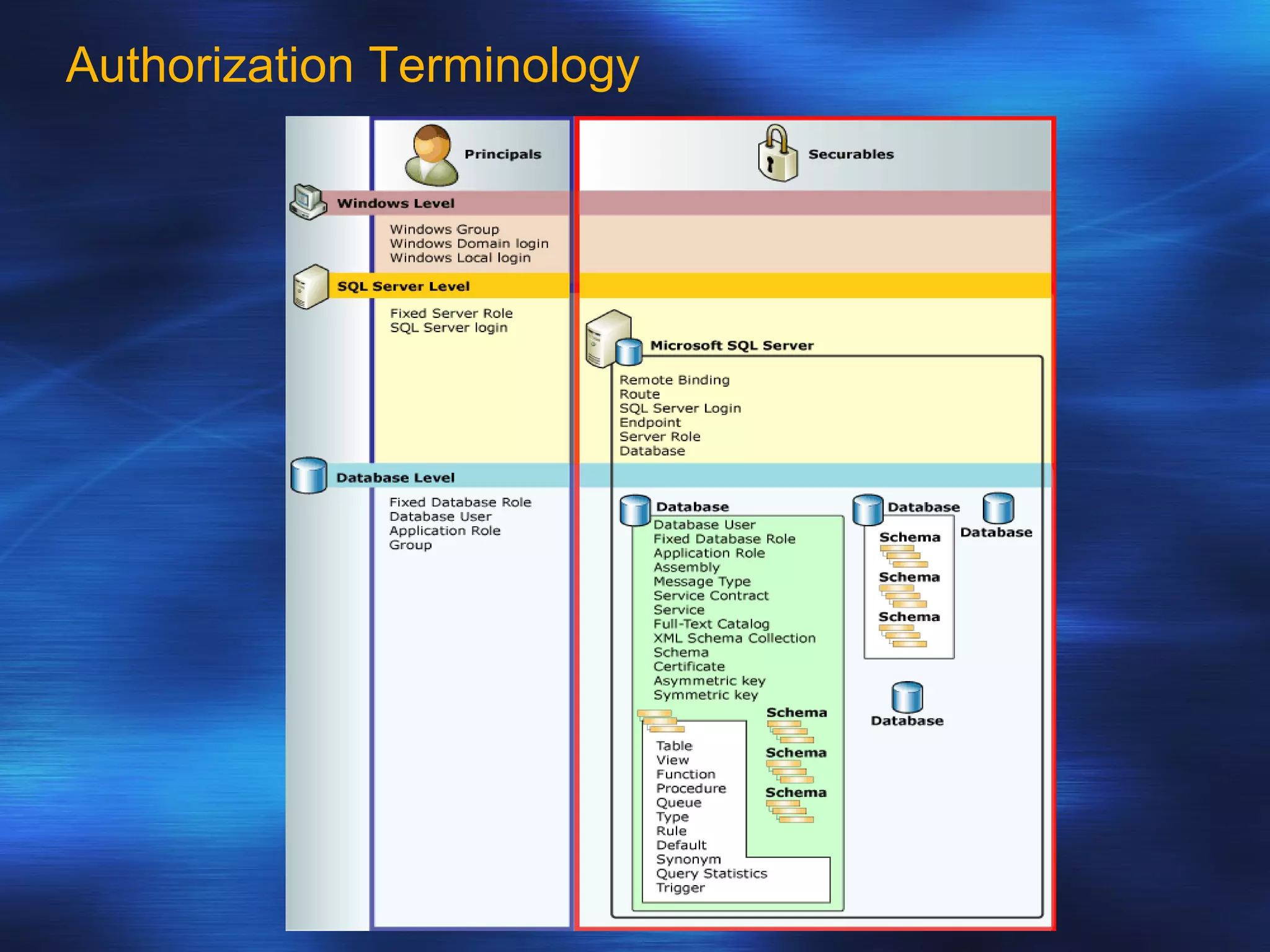
SQL Server 2005 introduced enhancements to security including: 1. Authentication can specify SSL or mutual authentication with client certificates. Authorization establishes login credentials and permissions within a database. 2. A new security model separates users from schemas, allowing dropping a user without breaking applications. Users have a default schema and objects are contained within schemas. 3. Cryptography support provides encryption, decryption, signing and verification functions including symmetric and asymmetric keys. Permissions in SQL 2005 allow finer-grained control at the row level and module execution context.




![Authorization Model - Permissions New permissions for finer grained control Permissions associated with semantics Not with statements Permissions can imply others Example: CONTROL It implies all other permissions Four states of permissions Grant (+) Deny (-) Revoke (take away) - + Deny Deny Revoke [deny] Revoke Grant Grant](https://image.slidesharecdn.com/sqlserversecurity-090417054750-phpapp01/75/Sql-Server-Security-12-2048.jpg)