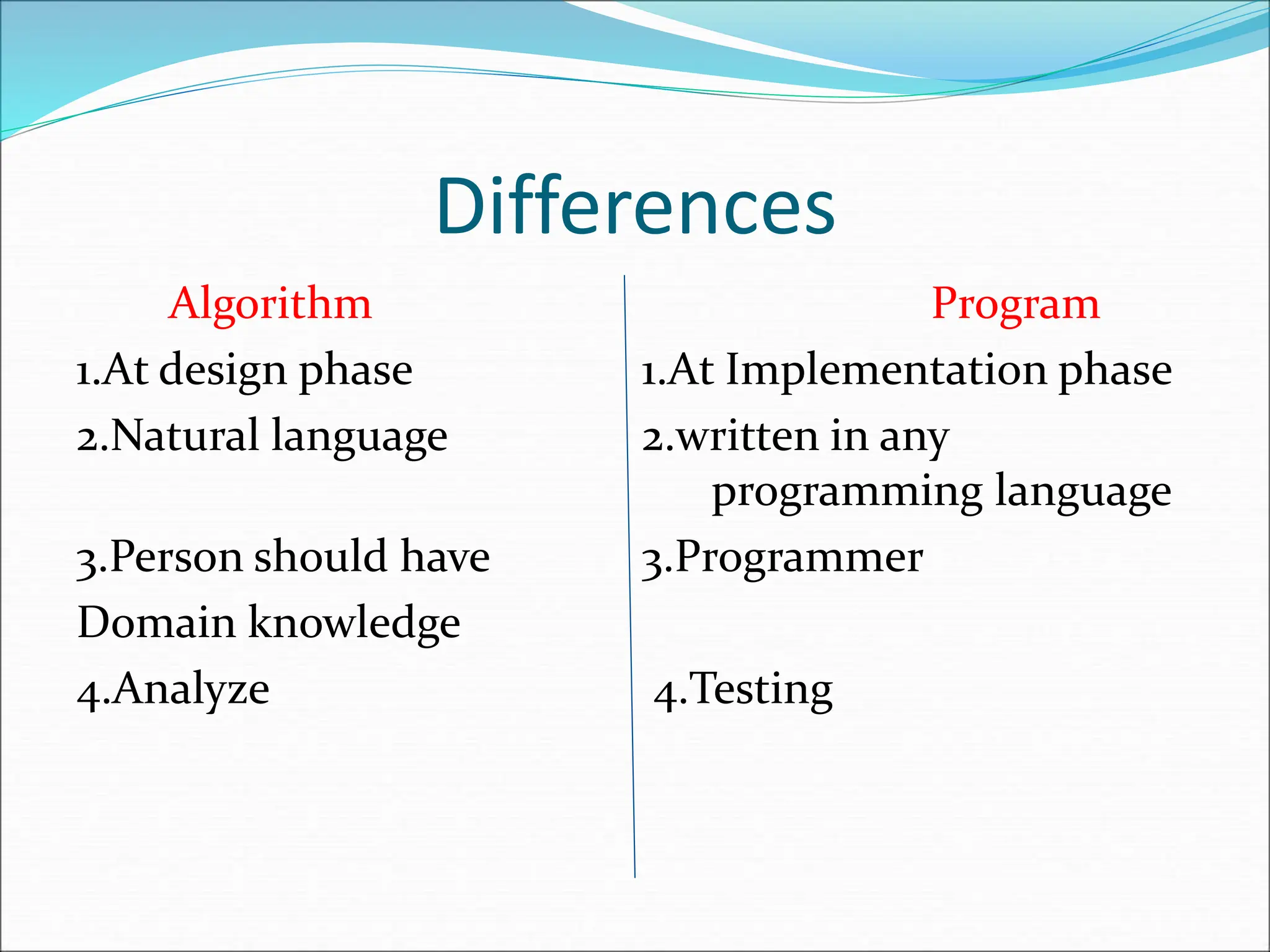
This document contains the syllabus for the subject "Design and Analysis of Algorithms" for the 3rd year 1st semester students of CMR Engineering College. It includes 5 units - Introduction, Disjoint Sets and Backtracking, Dynamic Programming and Greedy Methods, Branch and Bound, and NP-Hard and NP-Complete problems. The introduction covers topics like algorithm complexity analysis and divide and conquer algorithms. The syllabus outlines core algorithms topics and applications like binary search, quicksort, dynamic programming, shortest paths, knapsack etc. that will be covered in the course.








![10. There is only one type of procedure: Algorithm, the heading takes the form, Algorithm Name (Parameter lists) consider an example, the following algorithm fields & returns the maximum of n given numbers: 1. algorithm Max(A,n) 2. // A is an array of size n 3. { 4. Result := A[1]; 5. for i:= 2 to n do 6. if A[i] > Result then 7. Result :=A[i]; 8. return Result; 9. } Contd…](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-18-2048.jpg)

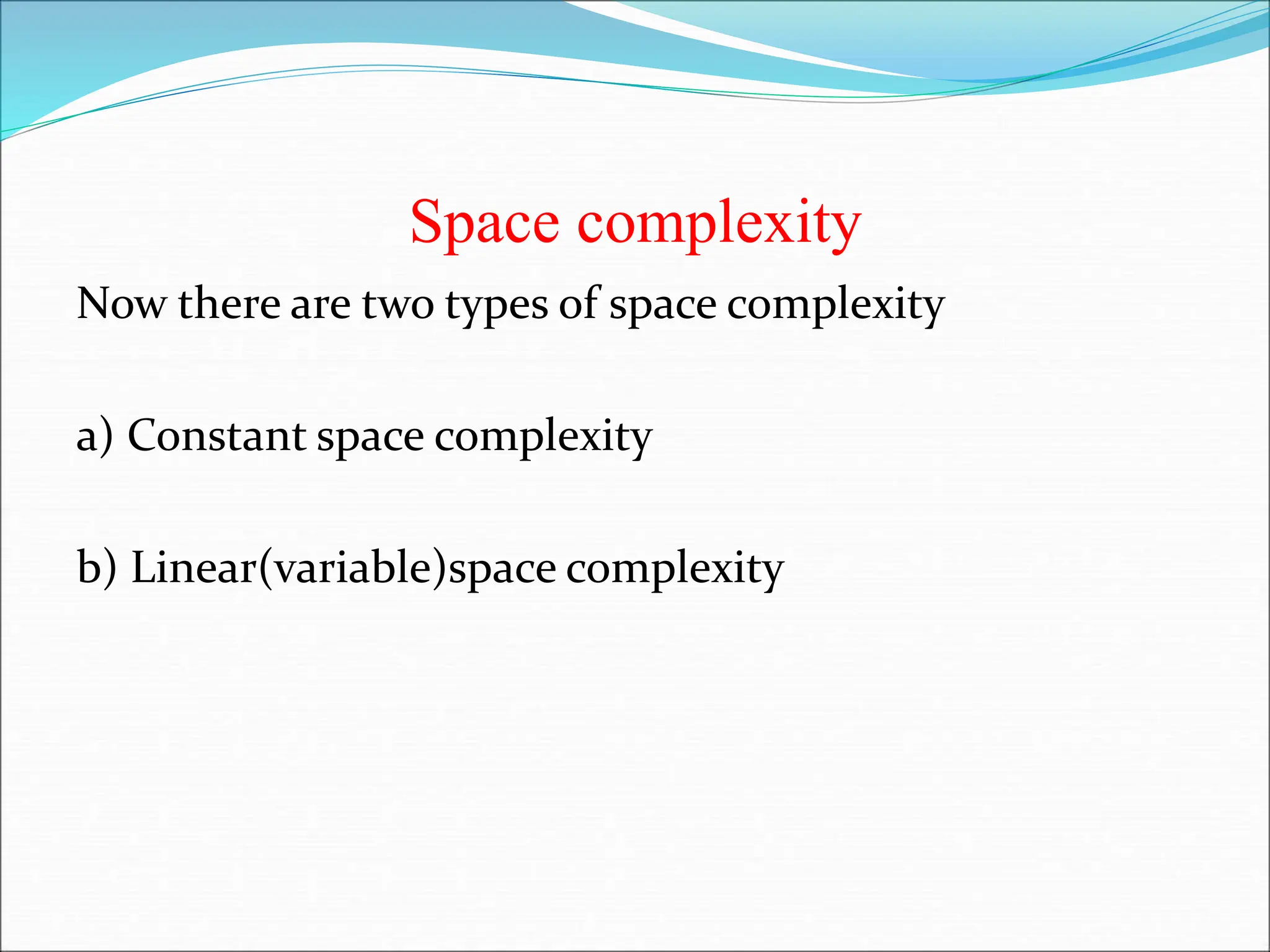
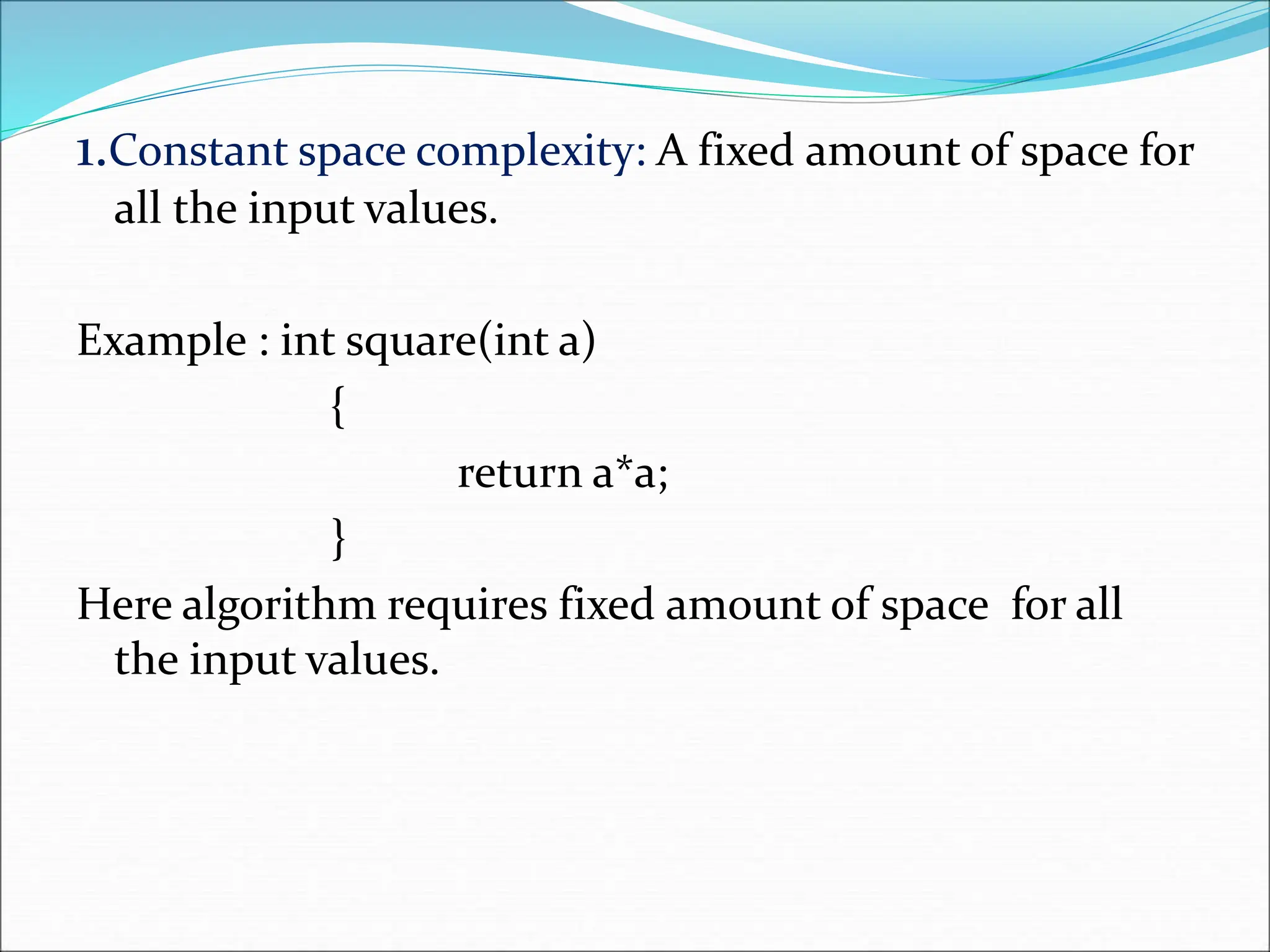
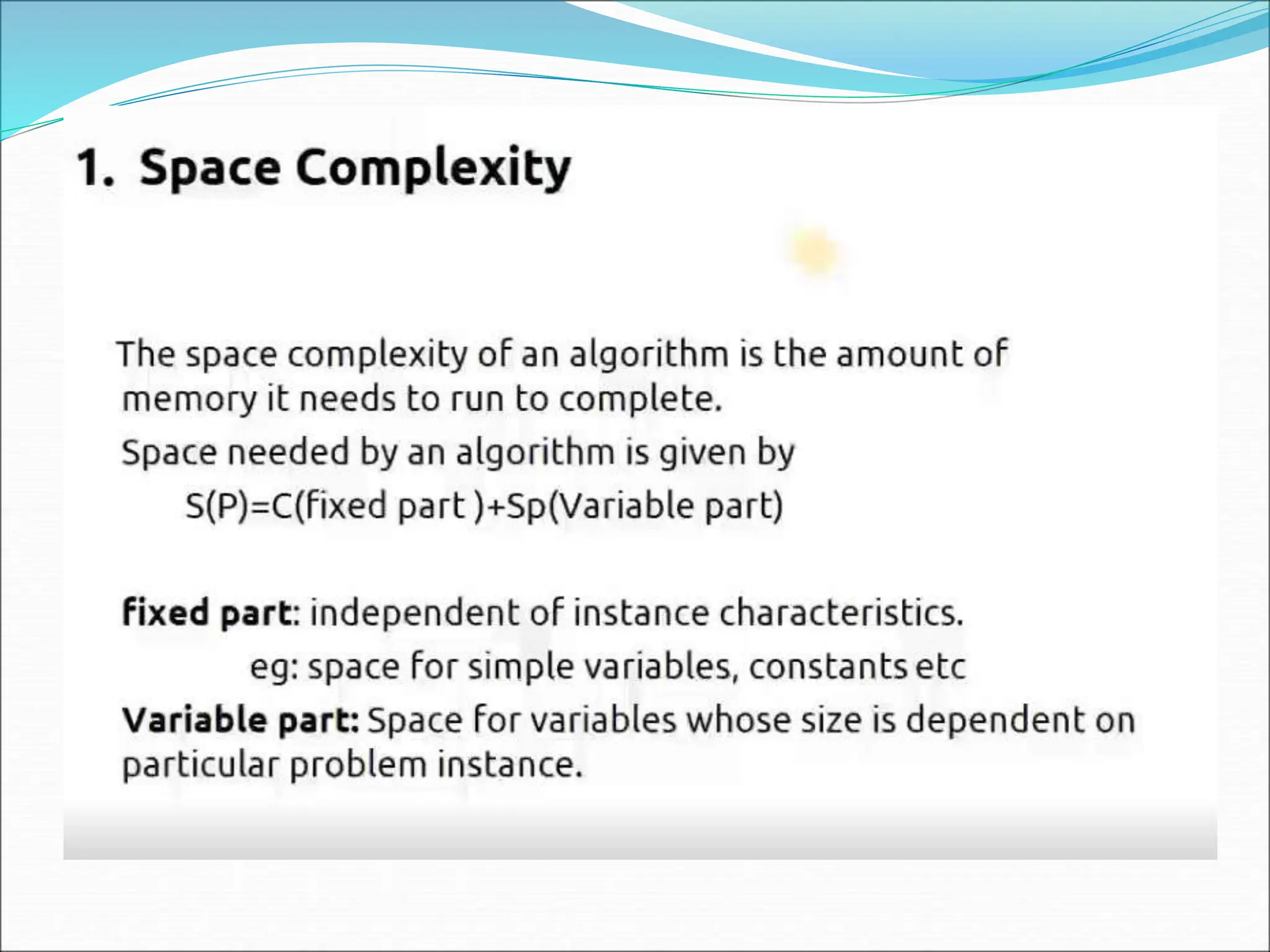
![2.Linear space complexity: The space needed for algorithm is based on size. Size of the variable ‘n’ = 1 word Array of a values = n word Loop variable = 1 word Sum variable = 1 word Example: int sum(int A[],int n) { n int sum=0,i; 1 for (i=0;i<n;i++) 1 Sum=sum+A[i]; 1 Return sum; } Ans : 1+n+1+1 = n+3 words](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-28-2048.jpg)

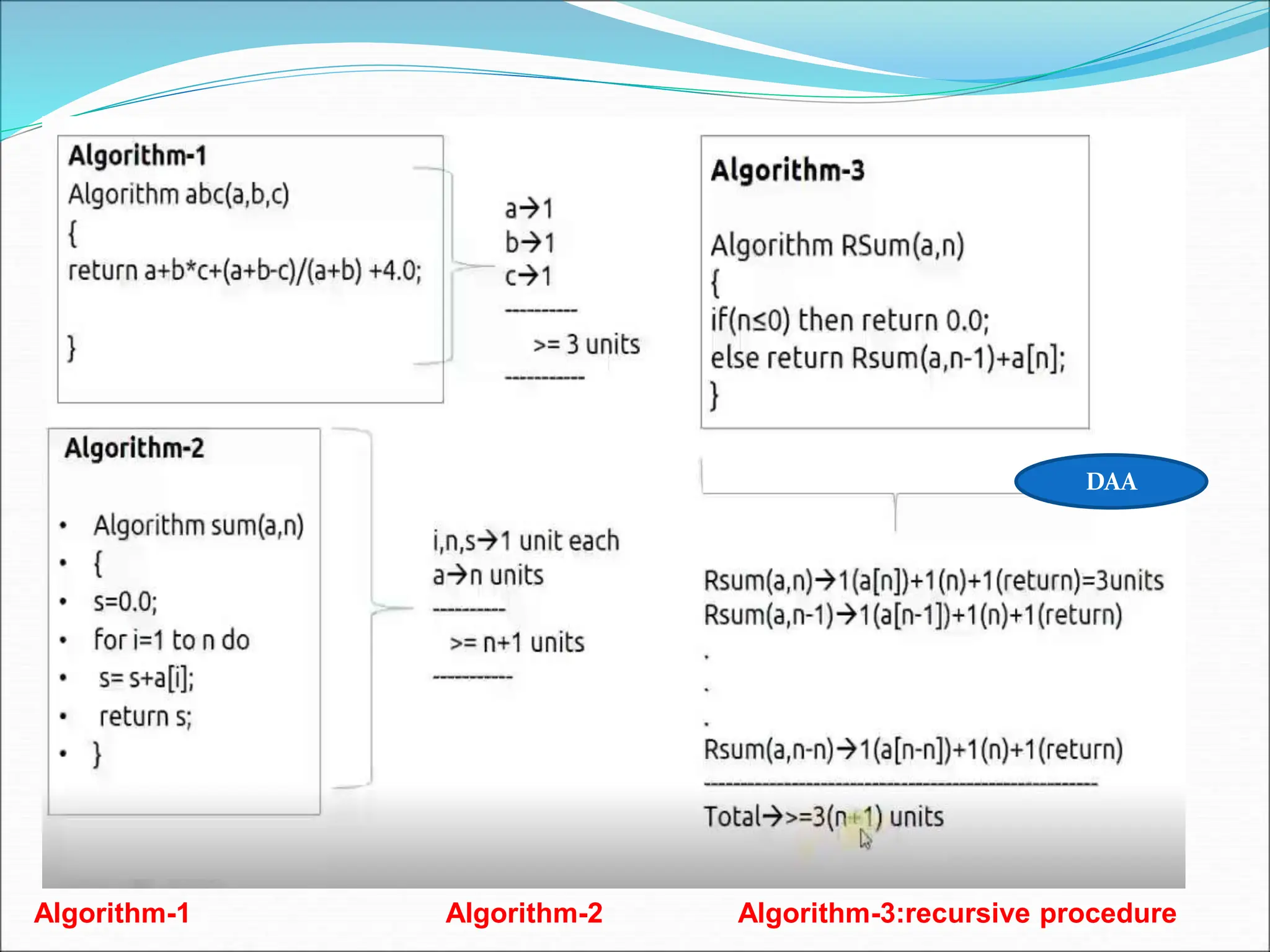
![2. algorithm sum(a,n) { total-=0; - 1 Fori=1 to n do -1,1 Total=total+a[i]--n Return total](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-31-2048.jpg)

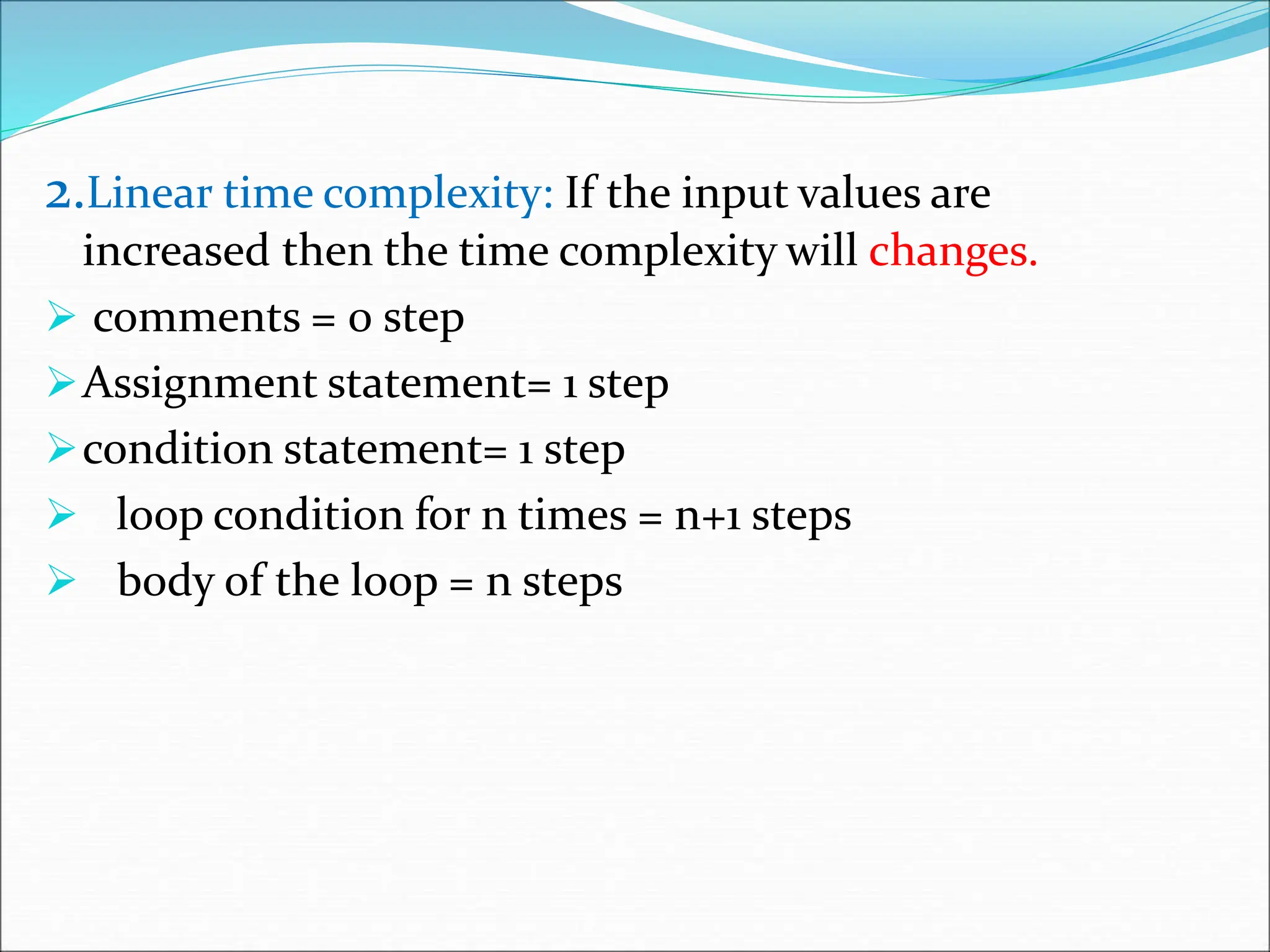
![Example : int sum(int A[],int n) { int sum=0,i; for (i=0;i<n;i++) sum=sum+A[i]; return sum; cost repetation total 1 1 1 1+1+1 1+(n+1)+n 2n+2 2 n 2n 1 1 1 4n+4](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-36-2048.jpg)
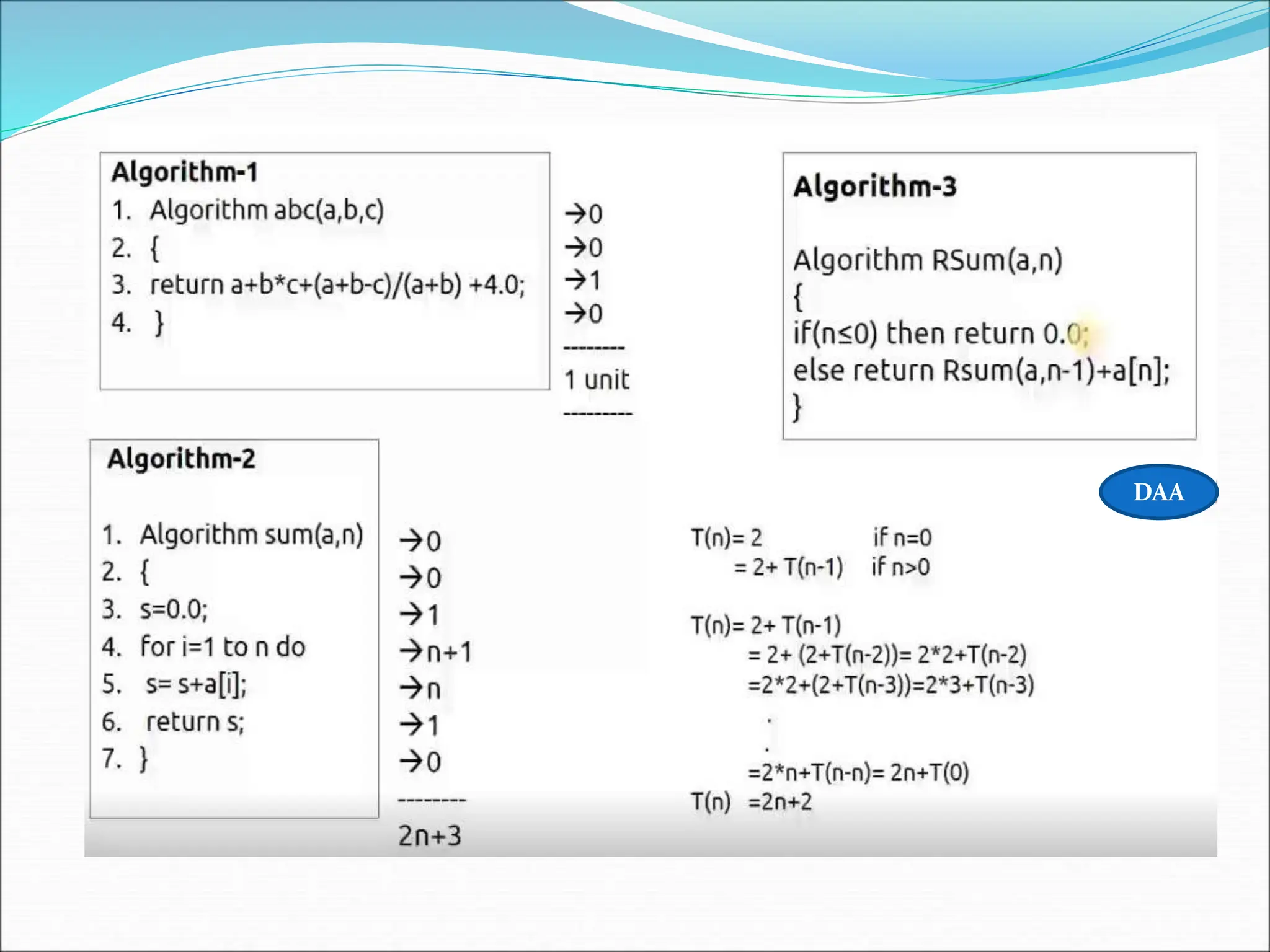
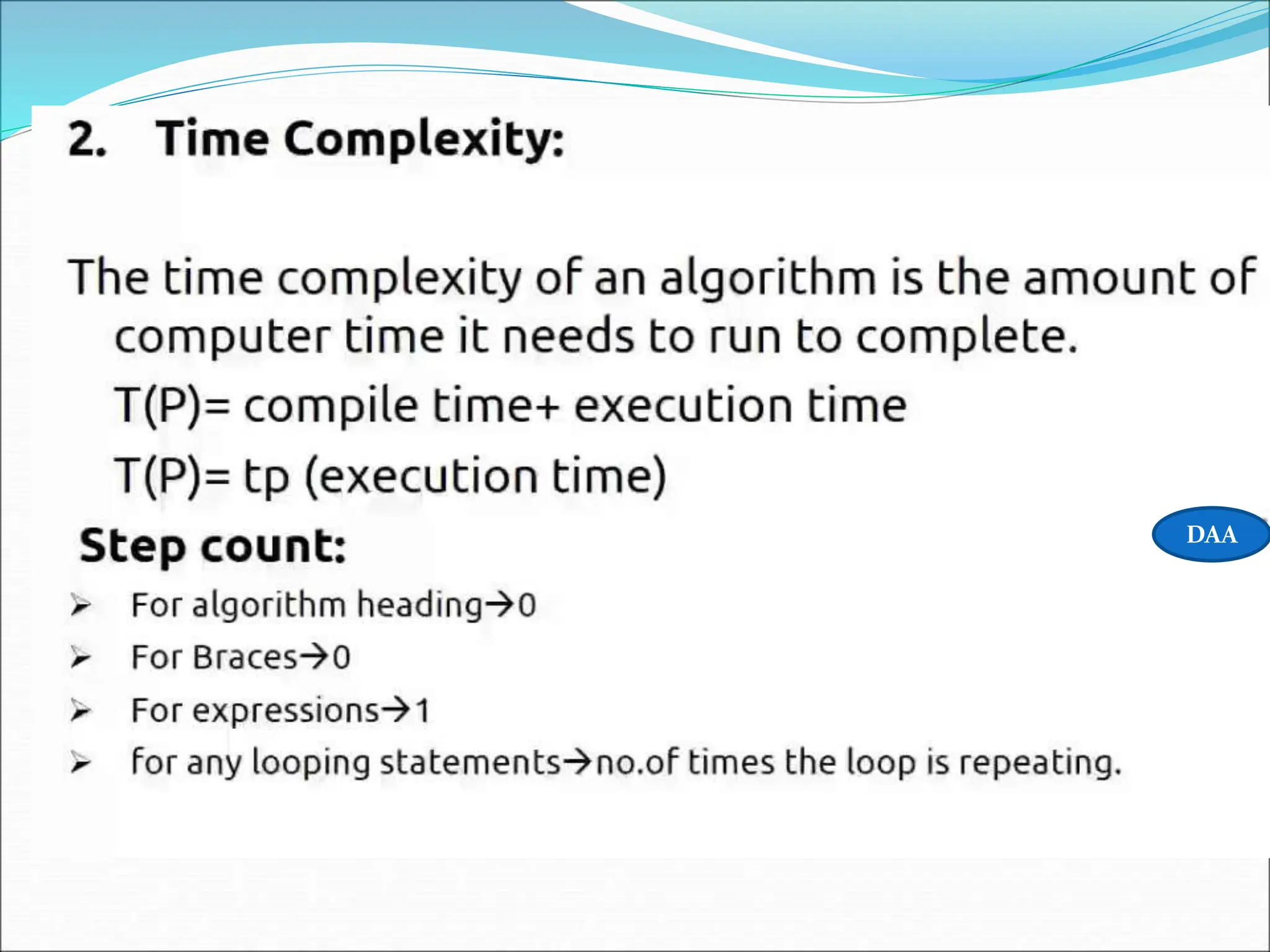
![Statement S/e Frequency Total 1. Algorithm Sum(a,n) 0 - 0 2.{ 0 - 0 3. S=0.0; 1 1 1 4. for i=1 to n do 1 n+1 n+1 5. s=s+a[I]; 1 n n 6. return s; 1 1 1 7. } 0 - 0 Total 2n+3 The time T(p) taken by a program P is the sum of the compile time and the run time(execution time) TIME COMPLEXITY](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-38-2048.jpg)

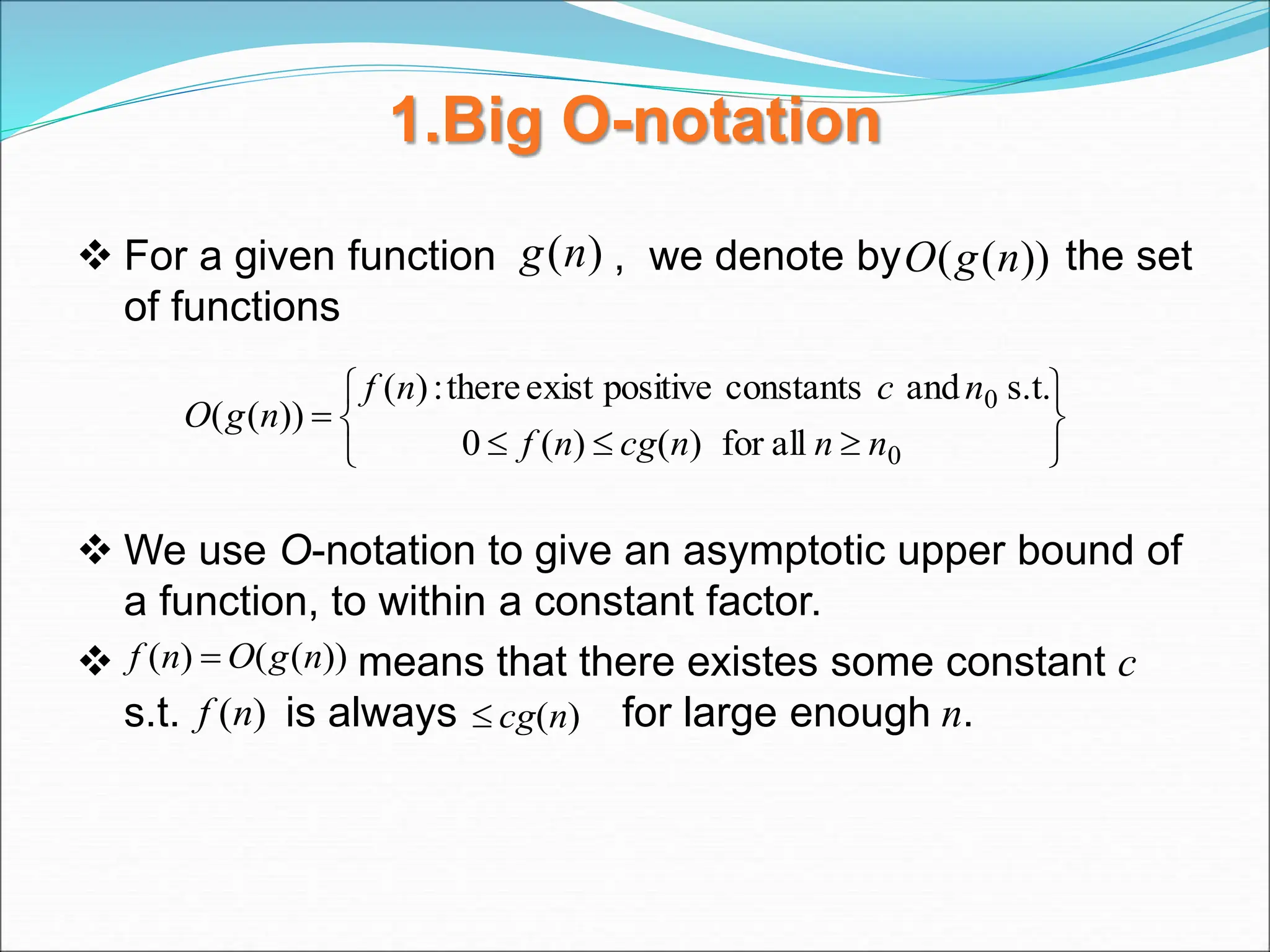
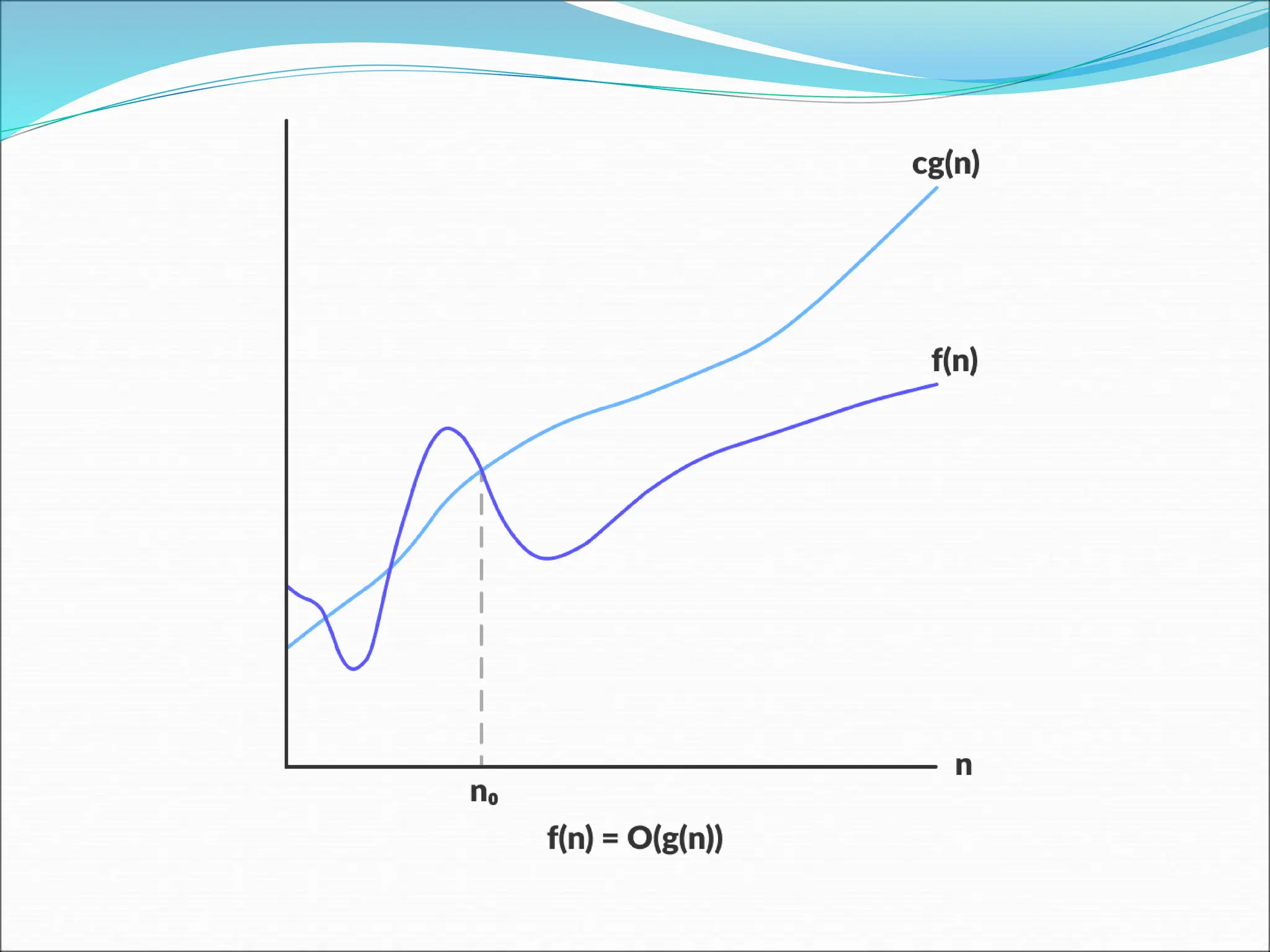
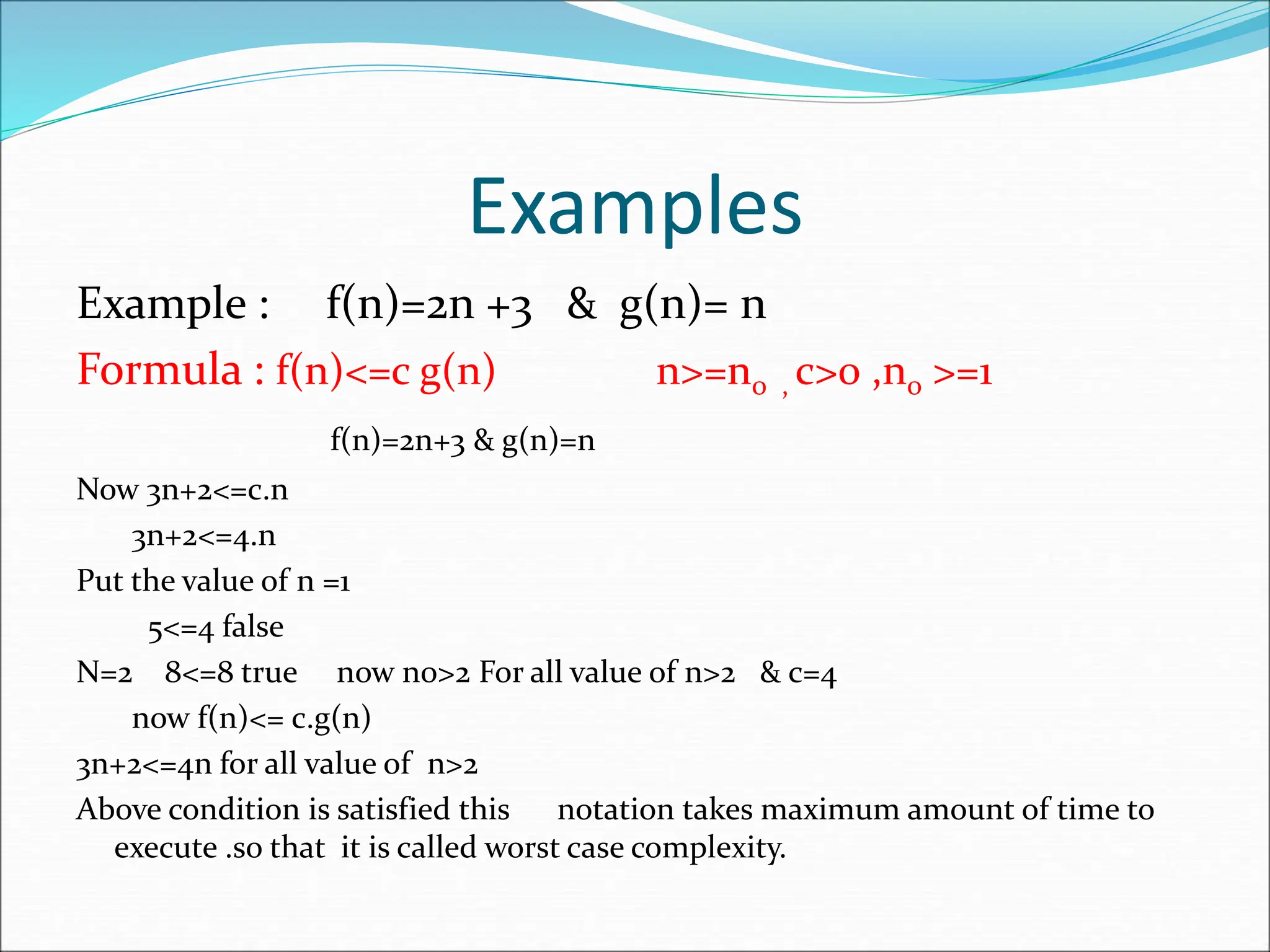

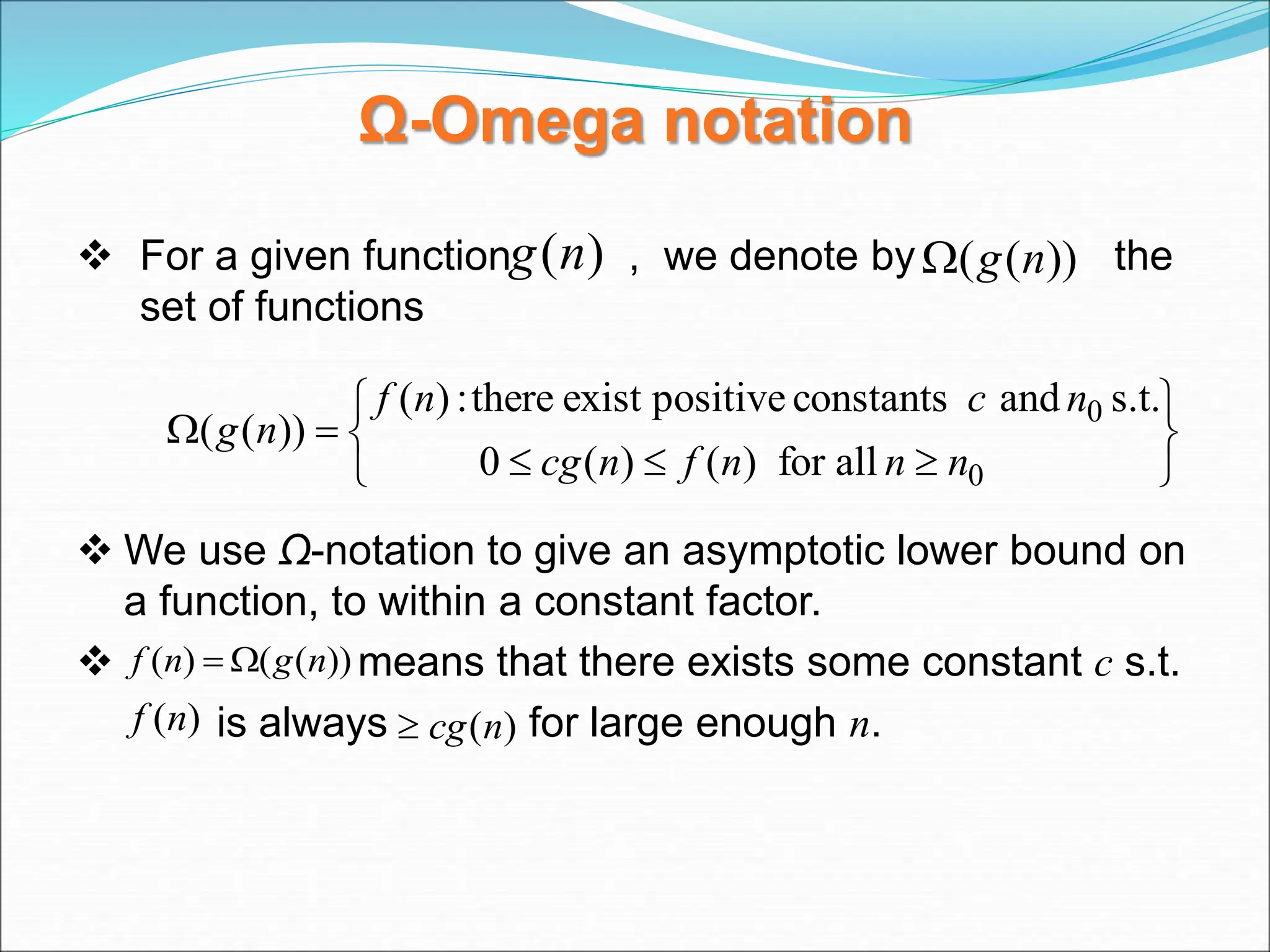
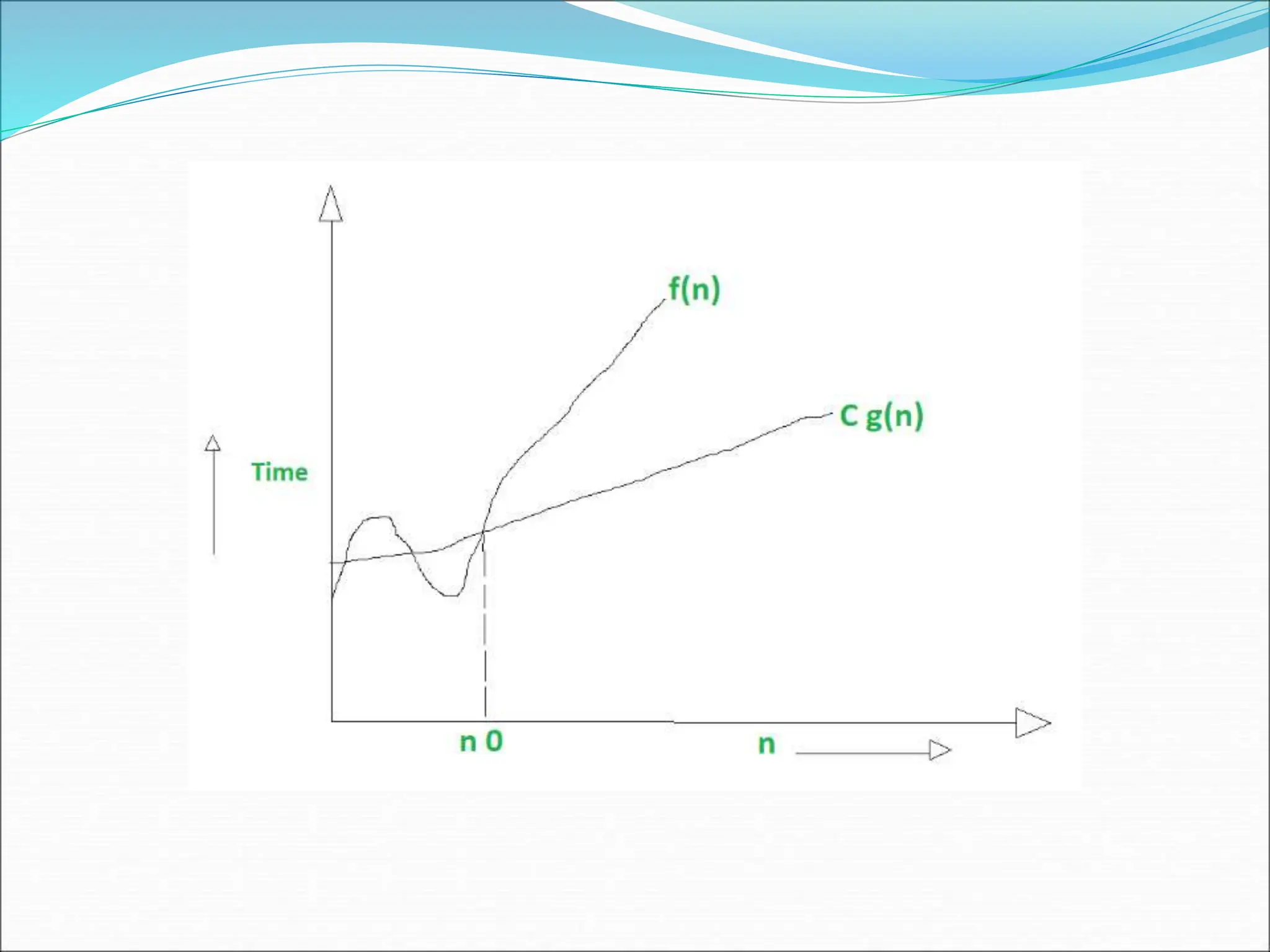
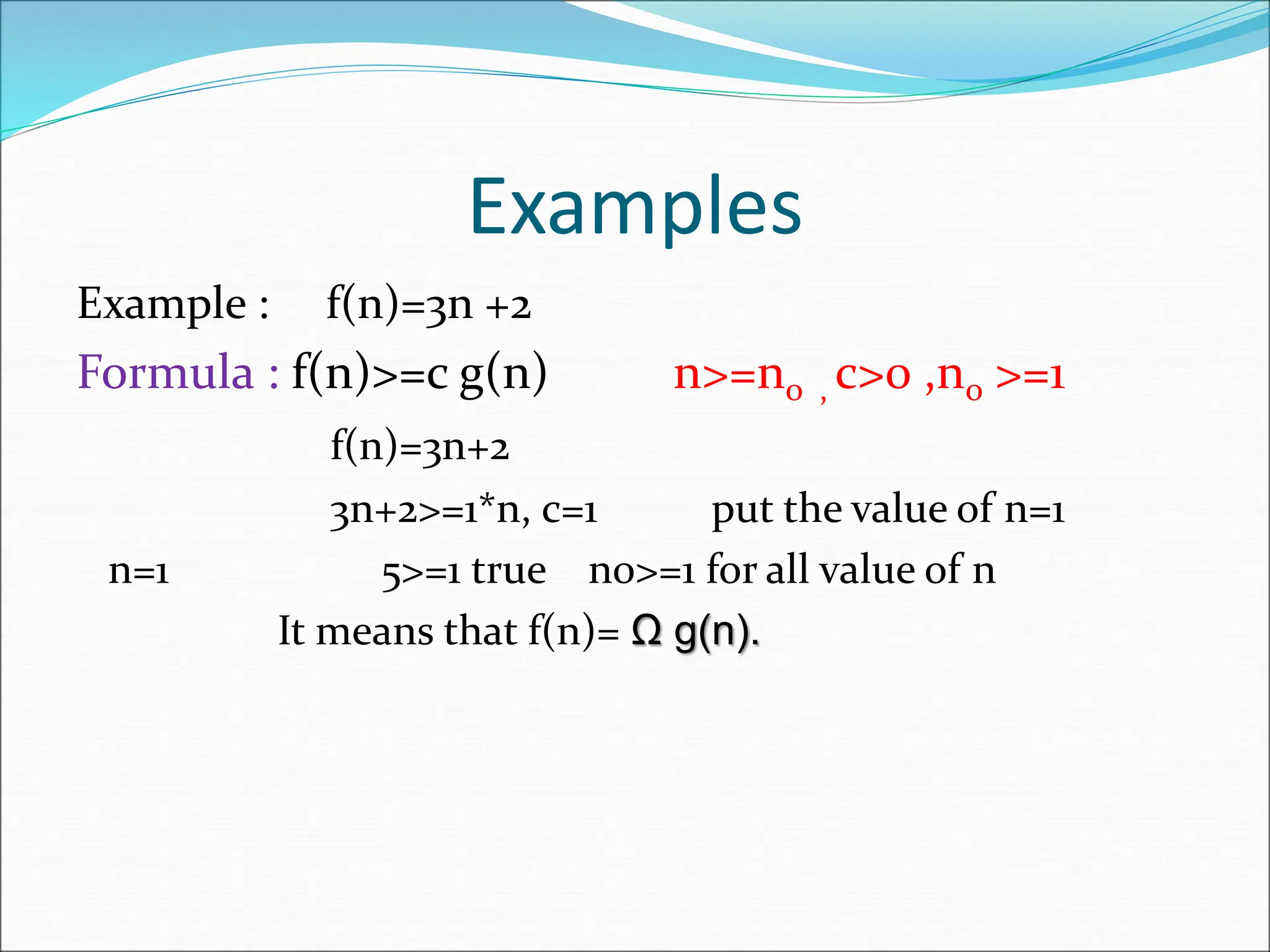

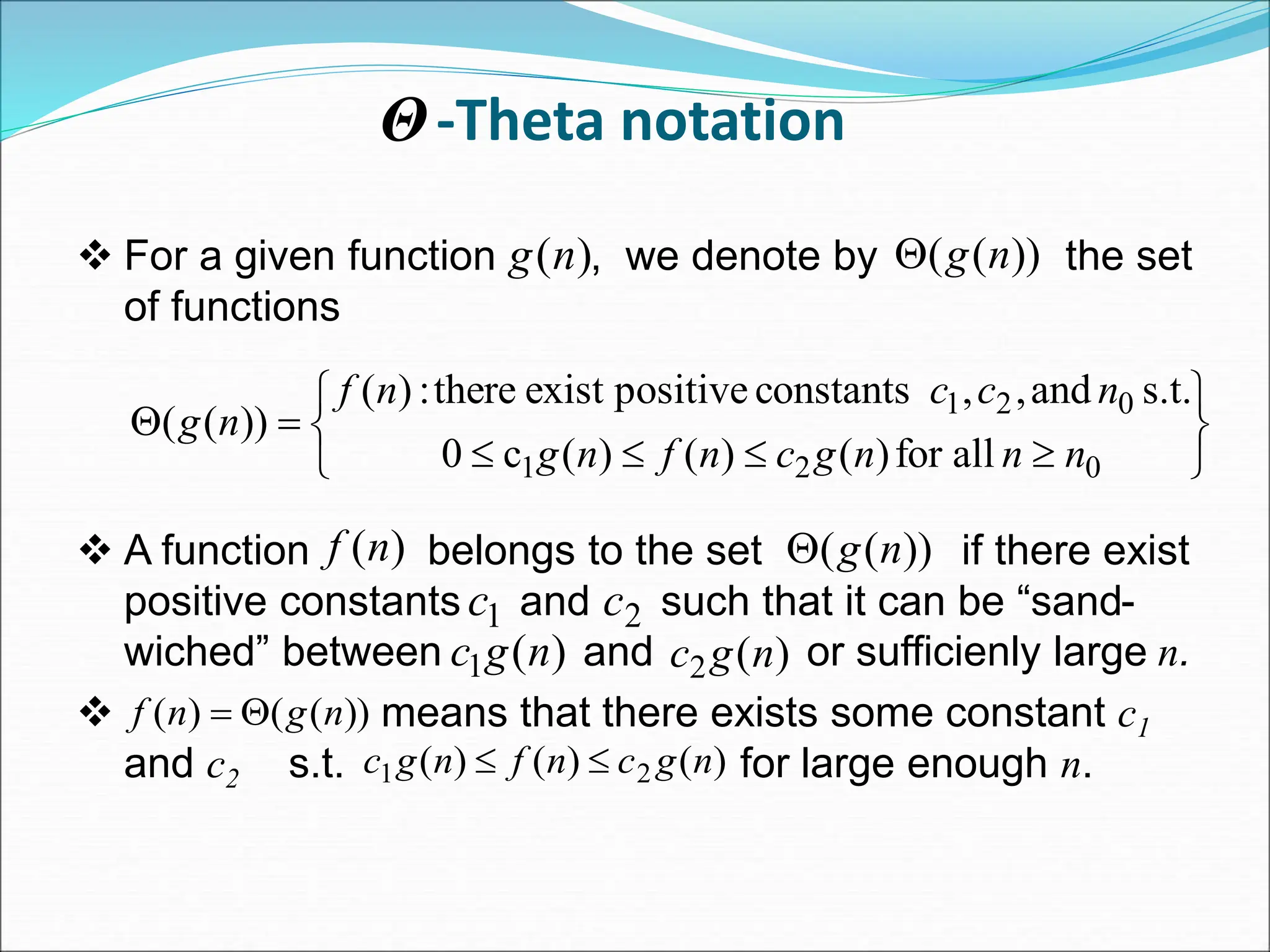
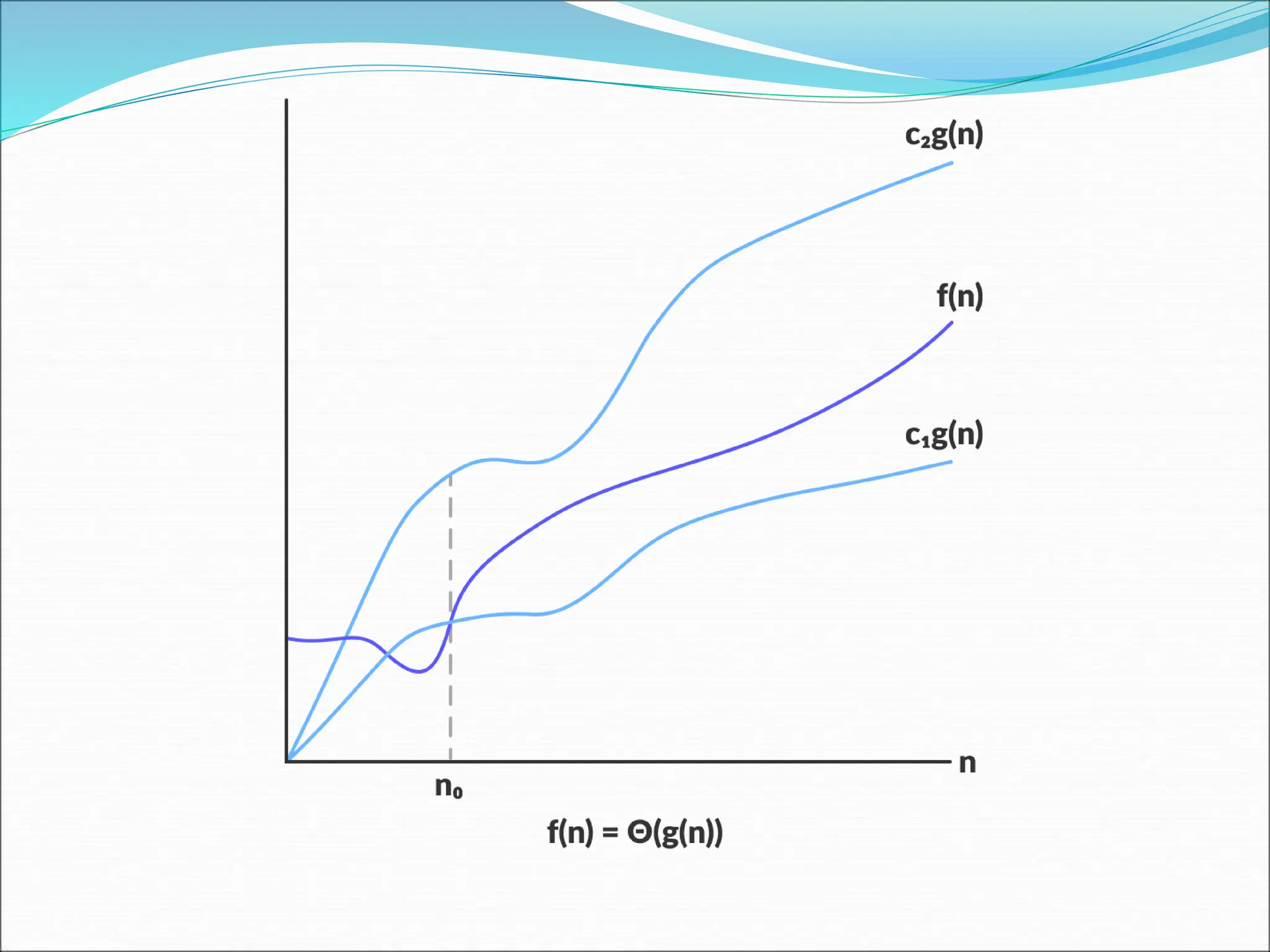





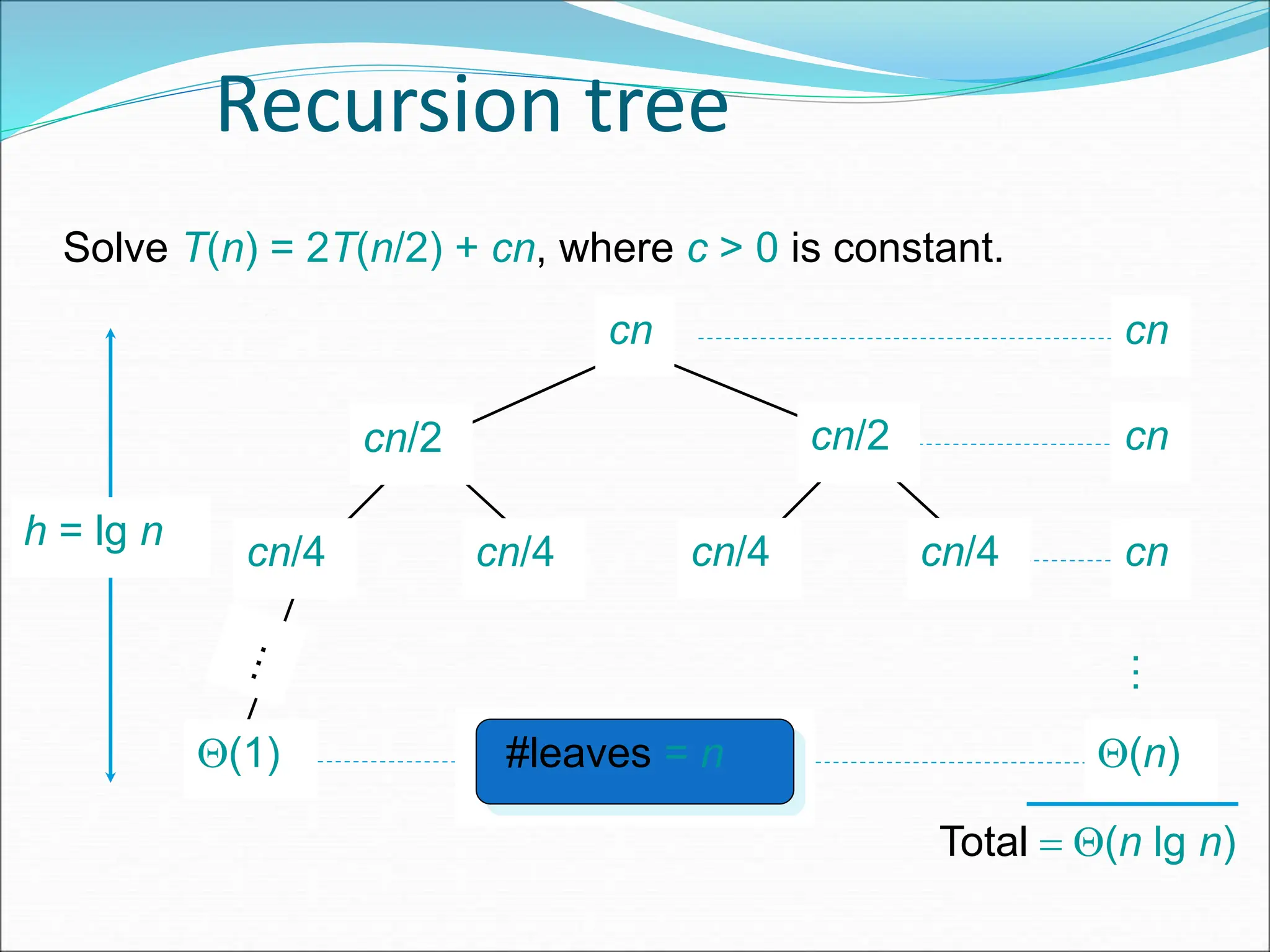
![EXAMPLE Consider the case in which a=2 and b=2. Let T(1)=2 & f(n)=n. We have, T(n) = 2T(n/2)+n 2[2T(n/2/2)+n/2]+n [4T(n/4)+n]+n 4T(n/4)+2n 4[2T(n/4/2)+n/4]+2n 4[2T(n/8)+n/4]+2n 8T(n/8)+n+2n 8T(n/8)+3n](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-69-2048.jpg)



![1. Algorithm Bin search(a,n,x) 2. // Given an array a[1:n] of elements in non-decreasing 3. //order, n>=0,determine whether x is present and 4. // if so, return j such that x=a[j]; else return 0. 5. { 6. low:=1; high:=n; 7. while (low<=high) do 8. { 9. mid:=[(low+high)/2]; 10. if (x<a[mid]) then high; 11. else if(x>a[mid]) then 12. low=mid+1; 13. else return mid; 14. } 15. return 0; } BINARY SEARCH](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-73-2048.jpg)
![EXAMPLE 1) Let us select the 14 entries. –15,6,0,7,9,23,54,82,101,112,125,131,142,151. Place them in a[1:14] and simulate the steps Binsearch goes through as it searches for different values of x. Only the variables low, high & mid need to be traced as we simulate the algorithm. We try the following values for x: 151, -14 and 9. for 2 successful searches & 1 unsuccessful search.](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-74-2048.jpg)

![ Another application of Divide and conquer is merge sort. Given a sequence of n elements a[1],…,a[n] the general idea is to imagine then split into 2 sets a[1],…..,a[n/2] and a[[n/2]+1],….a[n]. Each set is individually sorted, and the resulting sorted sequences are merged to produce a single sorted sequence of n elements. Thus, we have another ideal example of the divide-and-conquer strategy in which the splitting is into 2 equal-sized sets & the combining operation is the merging of 2 sorted sets into one. MERGE SORT](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-76-2048.jpg)
![ALGORITHM FOR MERGE SORT Algorithm MergeSort(low,high) //a[low:high] is a global array to be sorted //Small(P) is true if there is only one element //to sort. In this case the list is already sorted. { if (low<high) then //if there are more than one element { //Divide P into subproblems //find where to split the set mid = [(low+high)/2]; //solve the subproblems. mergesort (low,mid); mergesort(mid+1,high); //combine the solutions . merge(low,mid,high); } }](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-77-2048.jpg)
![Algorithm: Merging 2 sorted subarrays using auxiliary storage. 1. Algorithm merge(low,mid,high) 2. /*a[low:high] is a global array containing two sorted subsets in a[low:mid] and in a[mid+1:high].The goal is to merge these 2 sets into a single set residing in a[low:high].b[] is an auxiliary global array. */ 3. { 4. h=low; I=low; j=mid+1; 5. while ((h<=mid) and (j<=high)) do { 6. if (a[h]<=a[j]) then { 7. b[I]=a[h]; 8. h = h+1; } 9. else { 10.b[I]= a[j]; 11.j=j+1; } 12.I=I+1; } 13.if (h>mid) then 14.for k=j to high do { 15.b[I]=a[k]; 16.I=I+1; 17.} 18.else 19.for k=h to mid do 20.{ 21.b[I]=a[k]; 22.I=I+1; } 23.for k=low to high do a[k] = b[k]; }](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-78-2048.jpg)
![ Consider the array of 10 elements a[1:10] =(310, 285, 179, 652, 351, 423, 861, 254, 450, 520) Algorithm Mergesort begins by splitting a[] into 2 sub arrays each of size five (a[1:5] and a[6:10]). The elements in a[1:5] are then split into 2 sub arrays of size 3 (a[1:3] ) and 2(a[4:5]) Then the items in a [1:3] are split into sub arrays of size 2 a[1:2] & one(a[3:3]) The 2 values in a[1:2] are split to find time into one-element sub arrays and now the merging begins. EXAMPLE](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-79-2048.jpg)
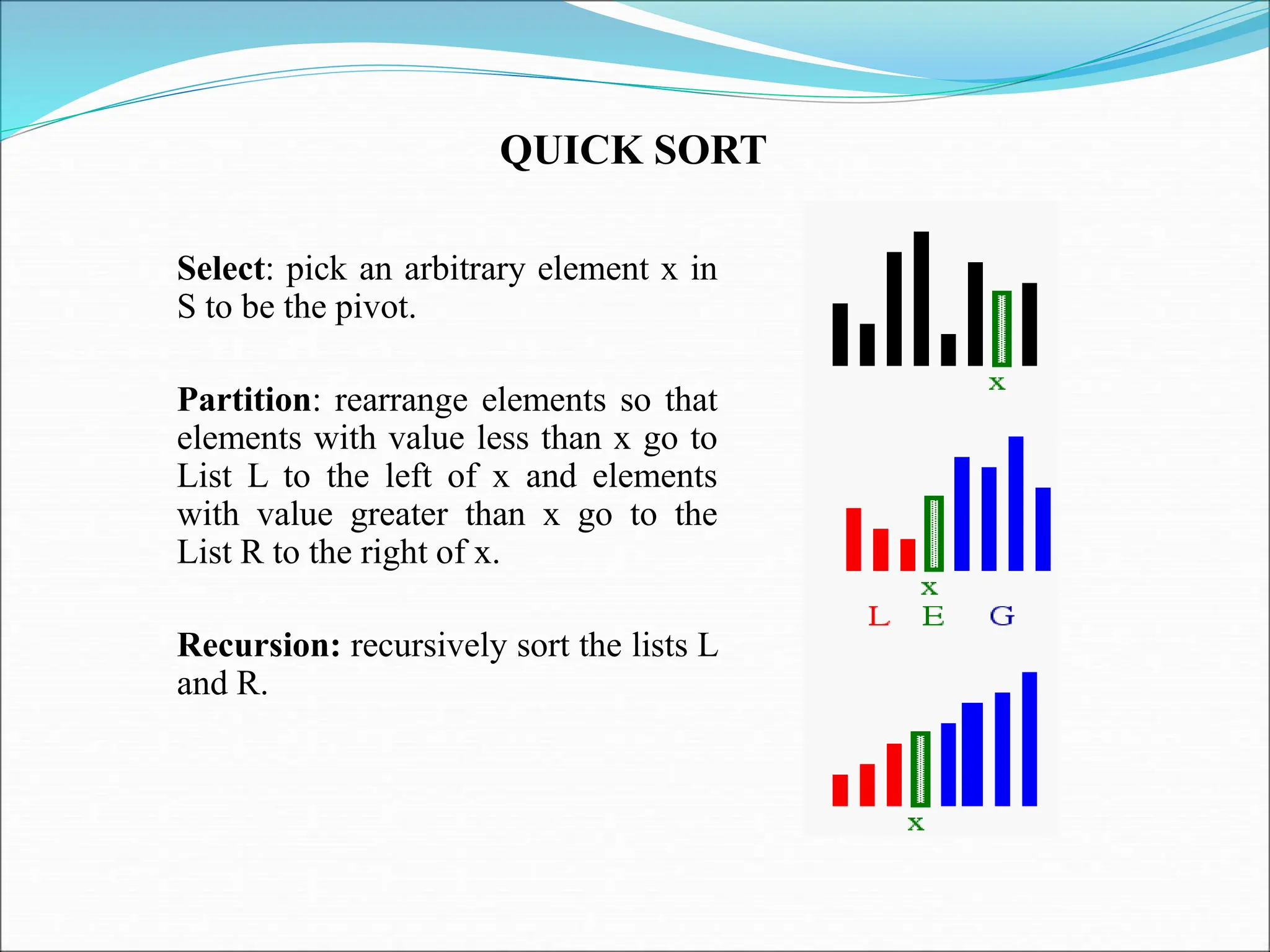
![ In Quick sort, the division into 2 sub arrays is made so that the sorted sub arrays do not need to be merged later. This is accomplished by rearranging the elements in a[1:n] such that a[I]<=a[j] for all I between 1 & n and all j between (m+1) & n for some m, 1<=m<=n. Thus the elements in a[1:m] & a[m+1:n] can be independently sorted. No merge is needed. This rearranging is referred to as partitioning. QUICK SORT](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-81-2048.jpg)
![1. Algorithm: Partition the array a[m:p-1] about a[m] 2. Algorithm Partition(a,m,p) 3. /*within a[m],a[m+1],…..,a[p-1] the elements are rearranged in such a manner that if initially t=a[m],then after completion a[q]=t for some q between m and 4. p-1,a[k]<=t for m<=k<q, and a[k]>=t for q<k<p. q is returned Set a[p]=infinite. */ 5. { 6. v=a[m];I=m;j=p; 7. repeat 8. { 9. repeat 10. I=I+1; 11. until(a[I]>=v); 12. repeat 13. j=j-1; 14. until(a[j]<=v); 15. if (I<j) then interchange(a,i.j); 16. }until(I>=j); 17. a[m]=a[j]; a[j]=v; 18. retun j; 19. } 20. Algorithm Interchange(a,I,j) //Exchange a[I] with a[j] 21. { 22. p=a[I]; 23. a[I]=a[j]; 24. a[j]=p; 25. }](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-82-2048.jpg)
![ Algorithm: Sorting by Partitioning Algorithm Quicksort(p,q) //Sort the elements a[p],….a[q] which resides //is the global array a[1:n] into ascending //order; a[n+1] is considered to be defined // and must be >= all the elements in a[1:n] { if(p<q) then // If there are more than one element { // divide p into 2 subproblems j=partition(a,p,q+1); //‟j‟ is the position of the partitioning element. //solve the subproblems. quicksort(p,j-1); quicksort(j+1,q); //There is no need for combining solution. } }](https://image.slidesharecdn.com/unit-1-ppts-daa-240215032310-2890067e/75/Introduction-to-Design-Algorithm-And-Analysis-ppt-83-2048.jpg)



