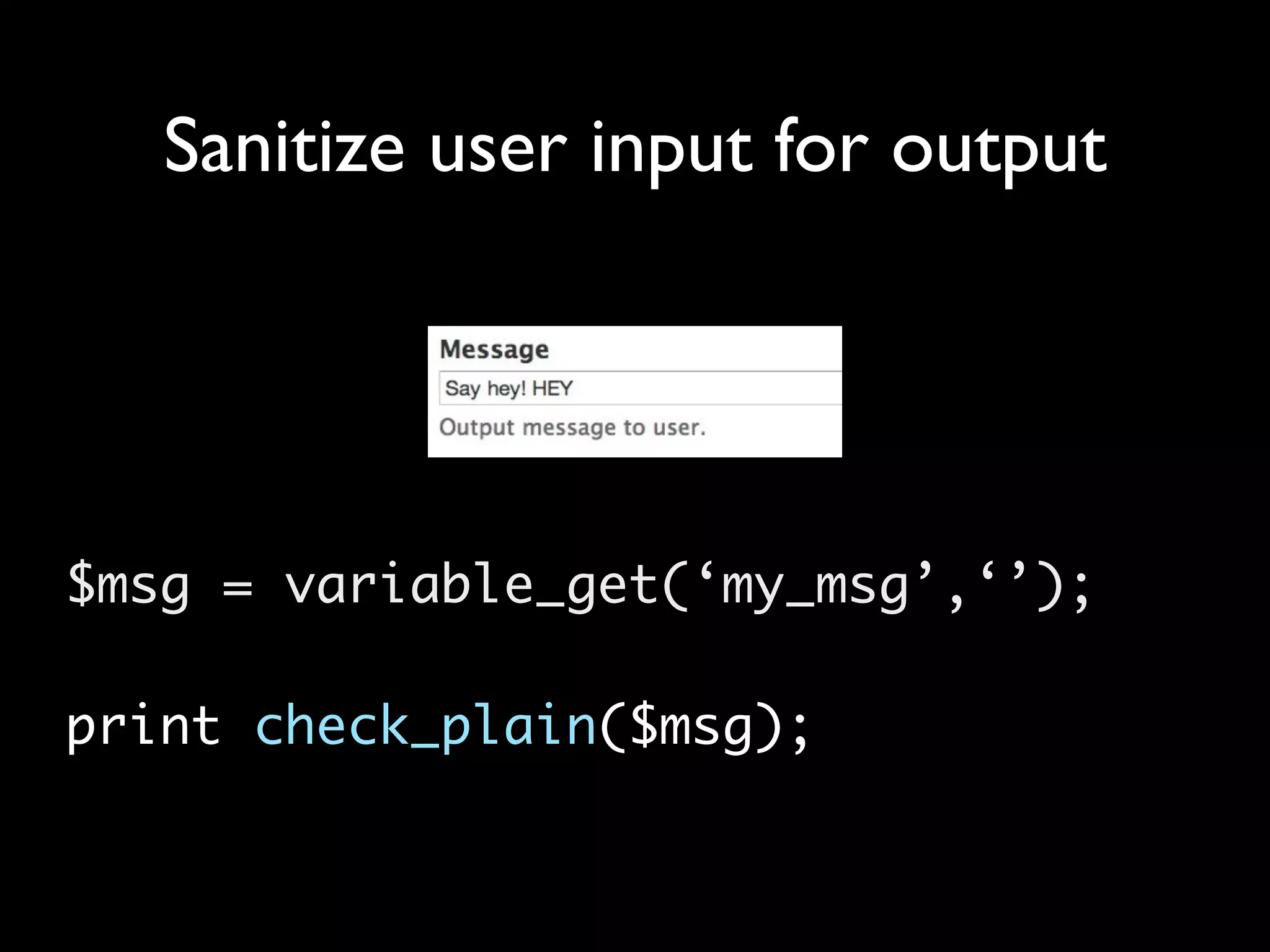
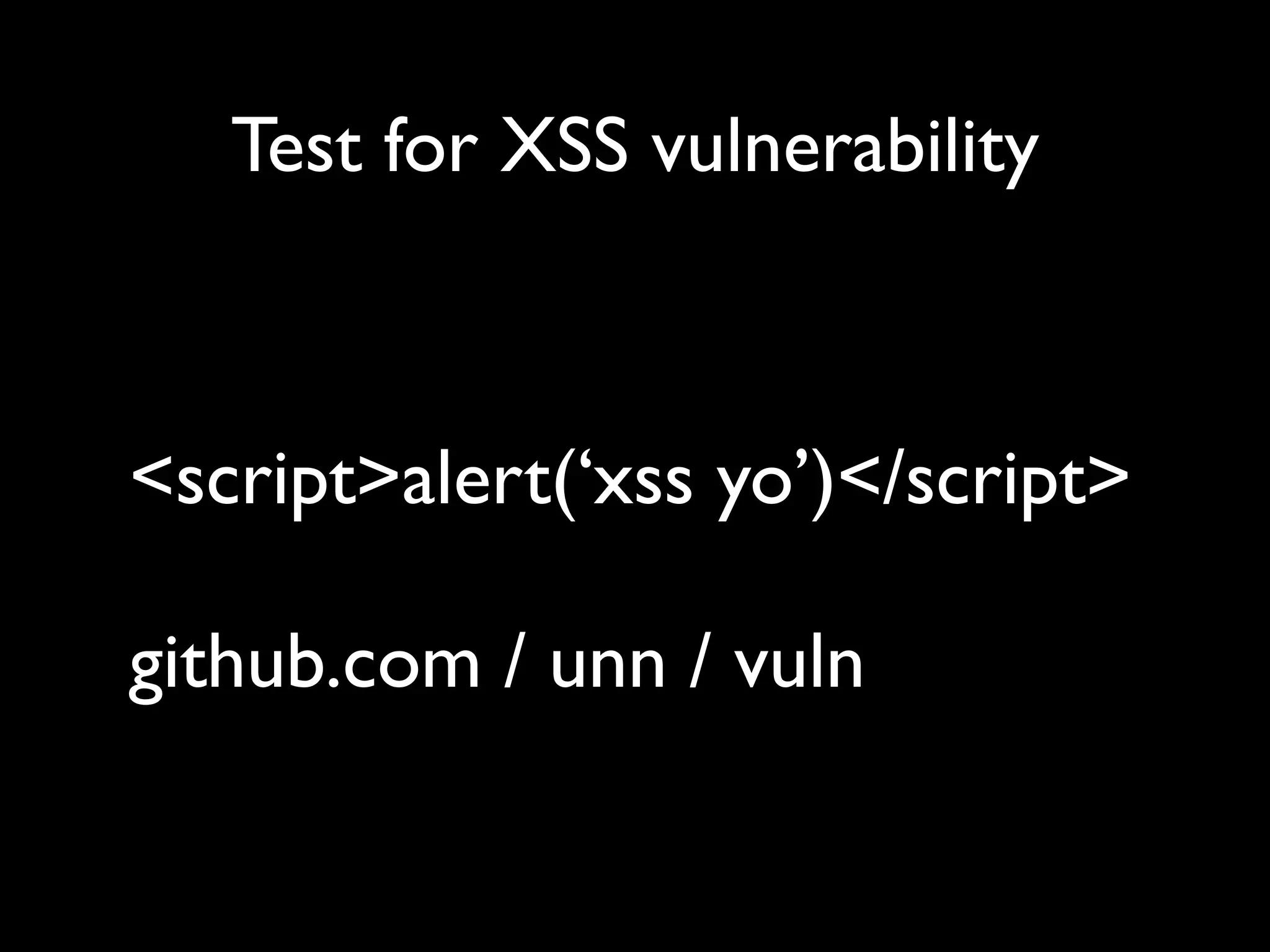
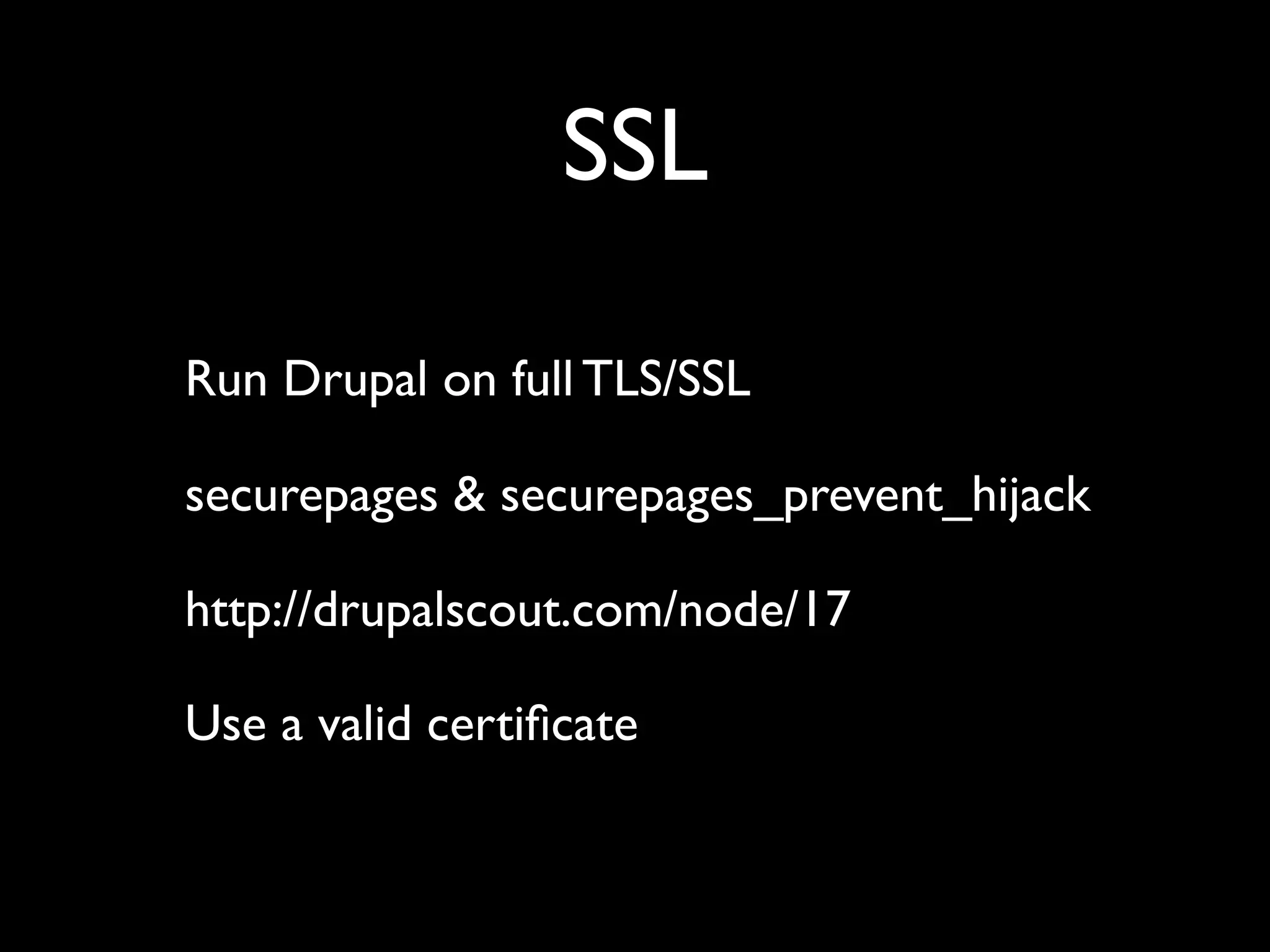
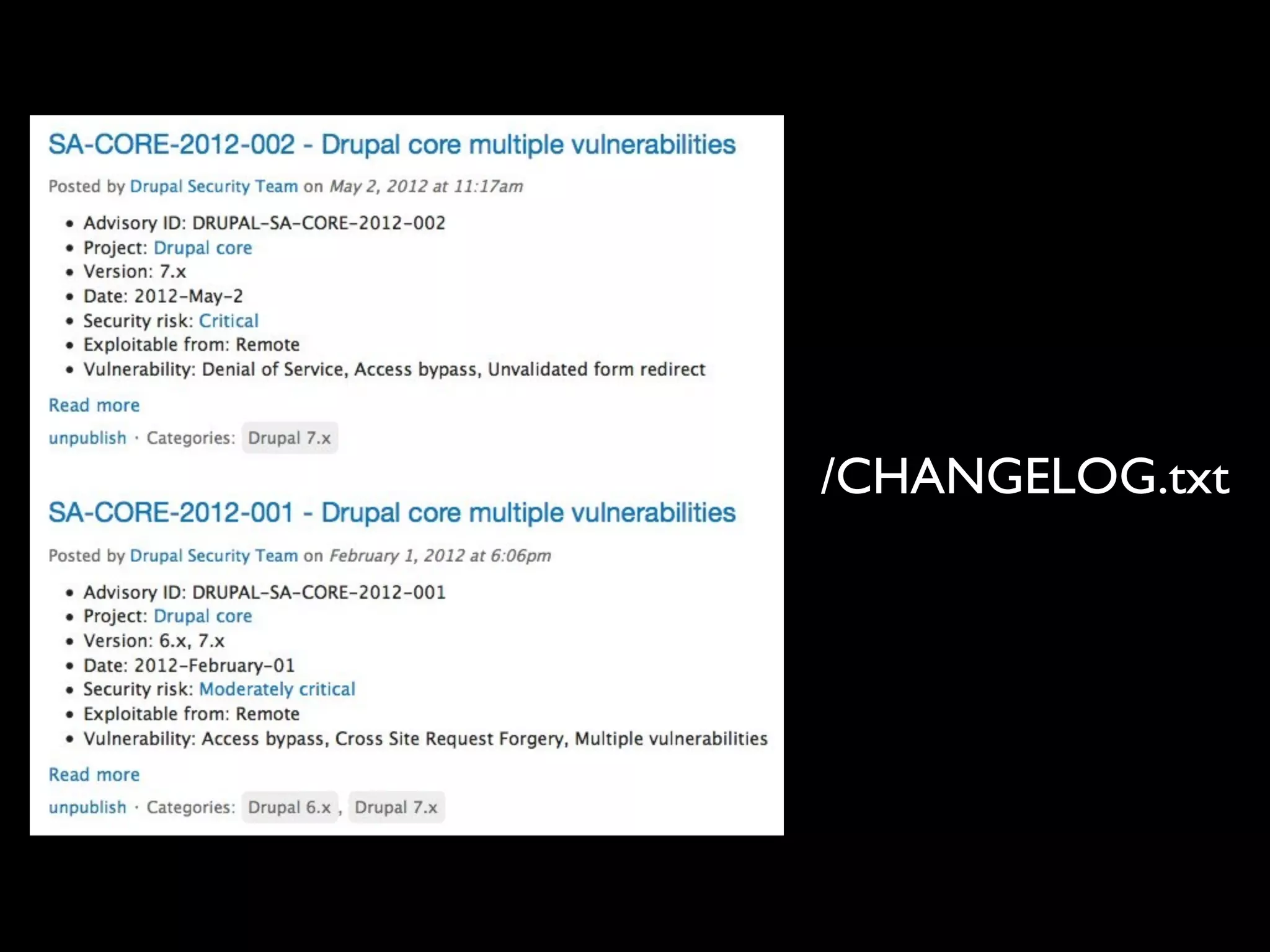
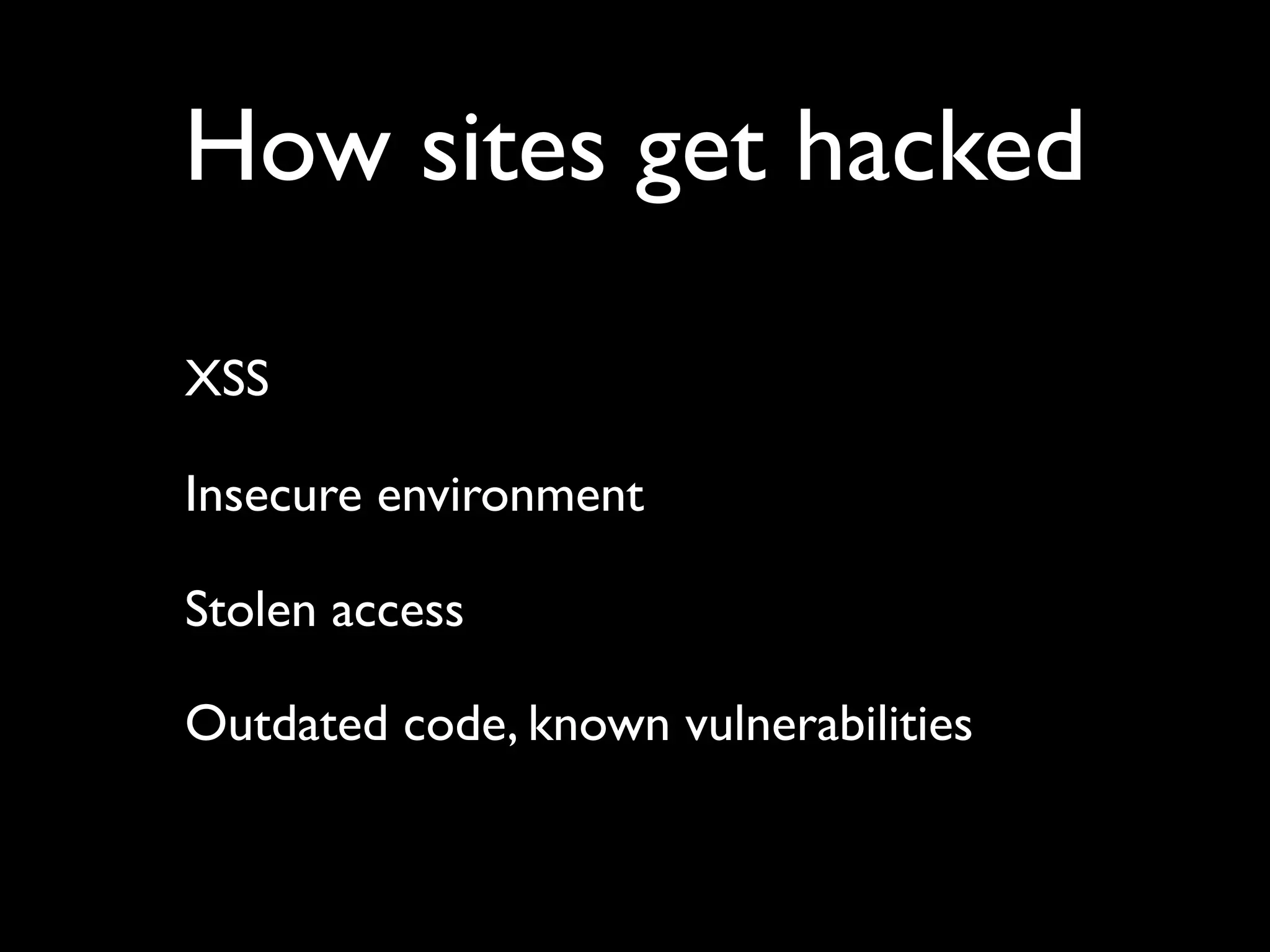
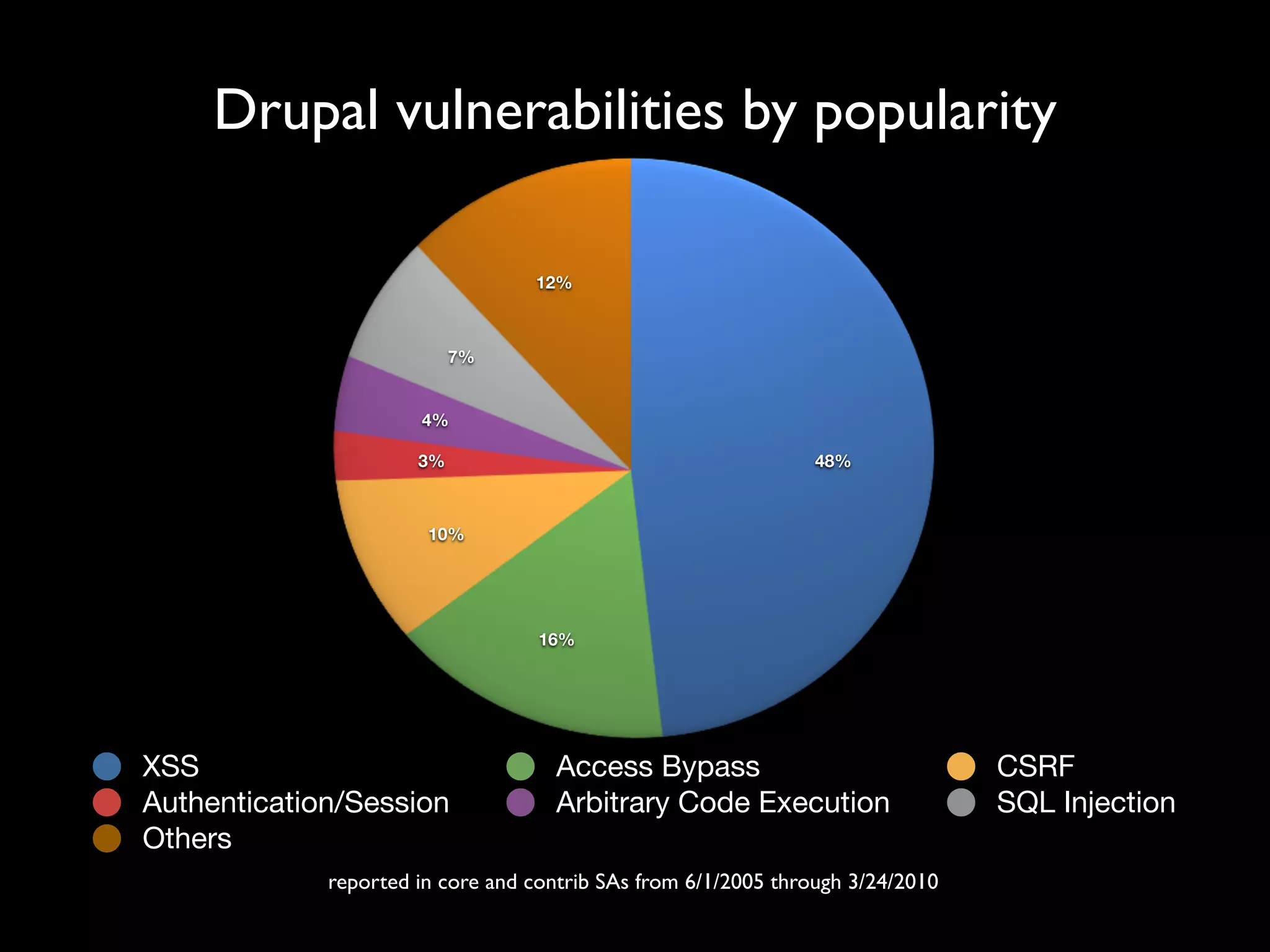
The document outlines security vulnerabilities in Drupal, focusing on risks such as cross-site scripting (XSS) and emphasizing the importance of secure coding practices. It provides practical steps for identifying and mitigating XSS threats, along with recommendations for securing the Drupal environment. Additionally, it highlights the necessity of regular updates and secure access protocols to protect against hacking attempts.







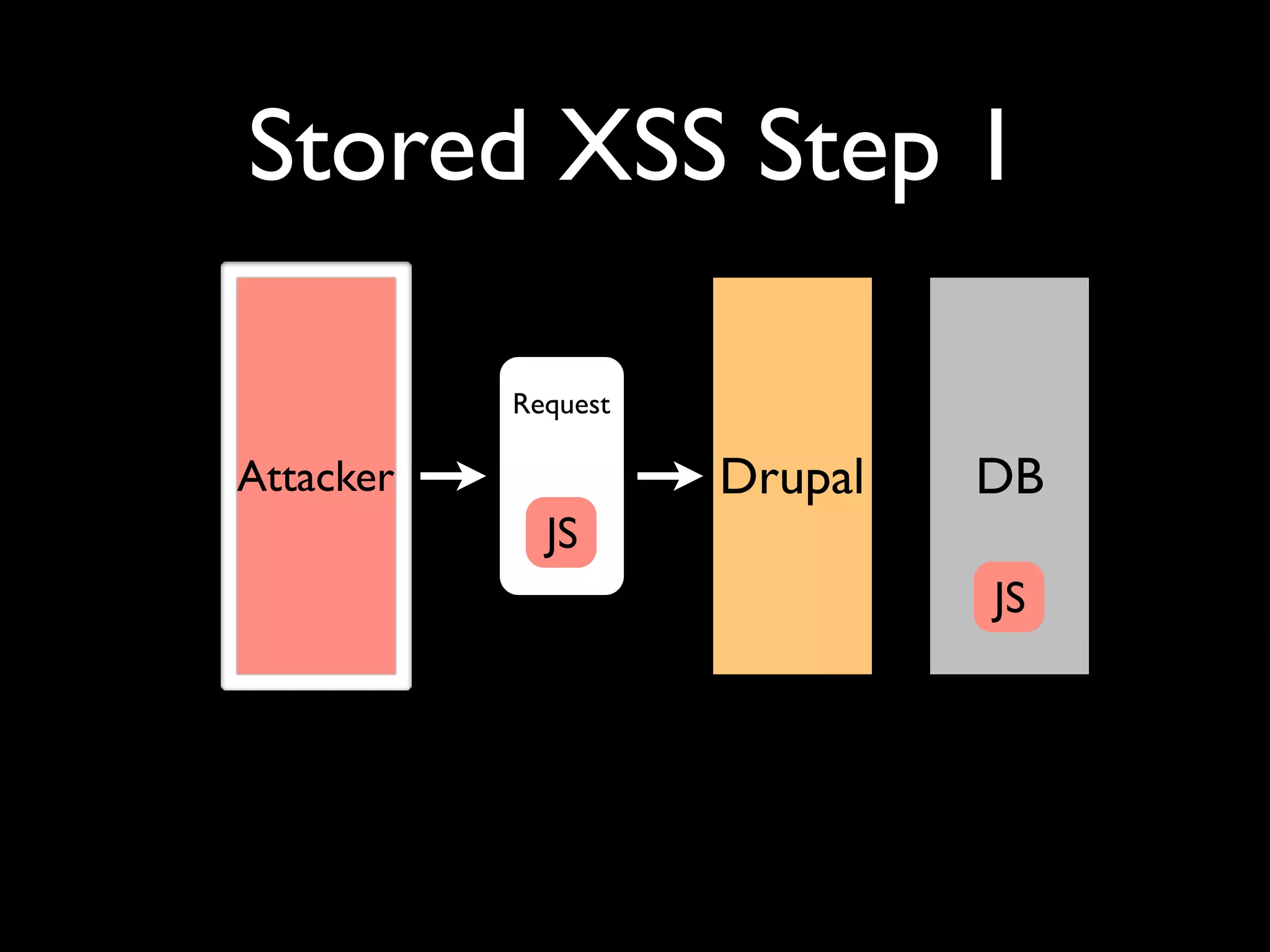
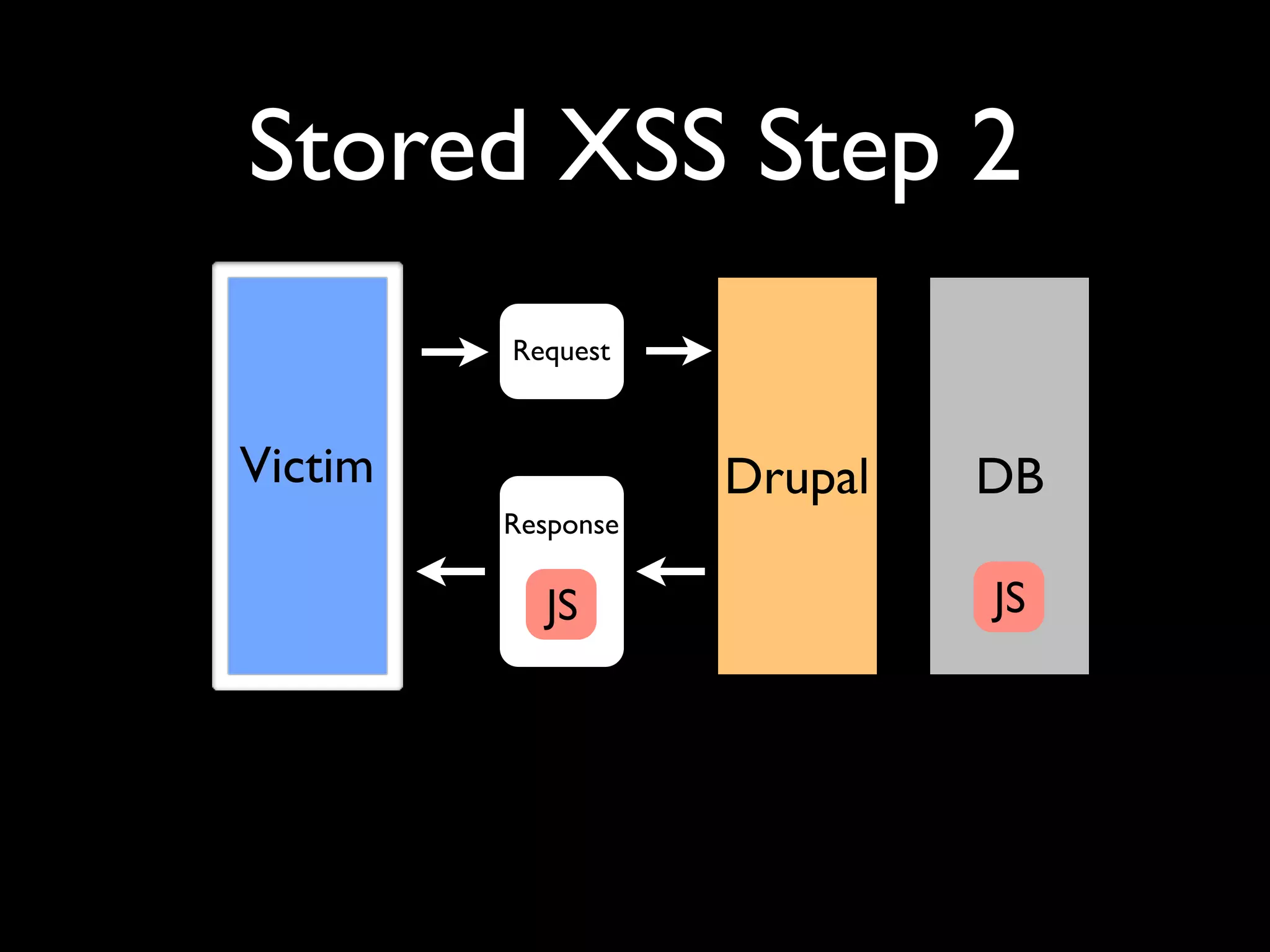
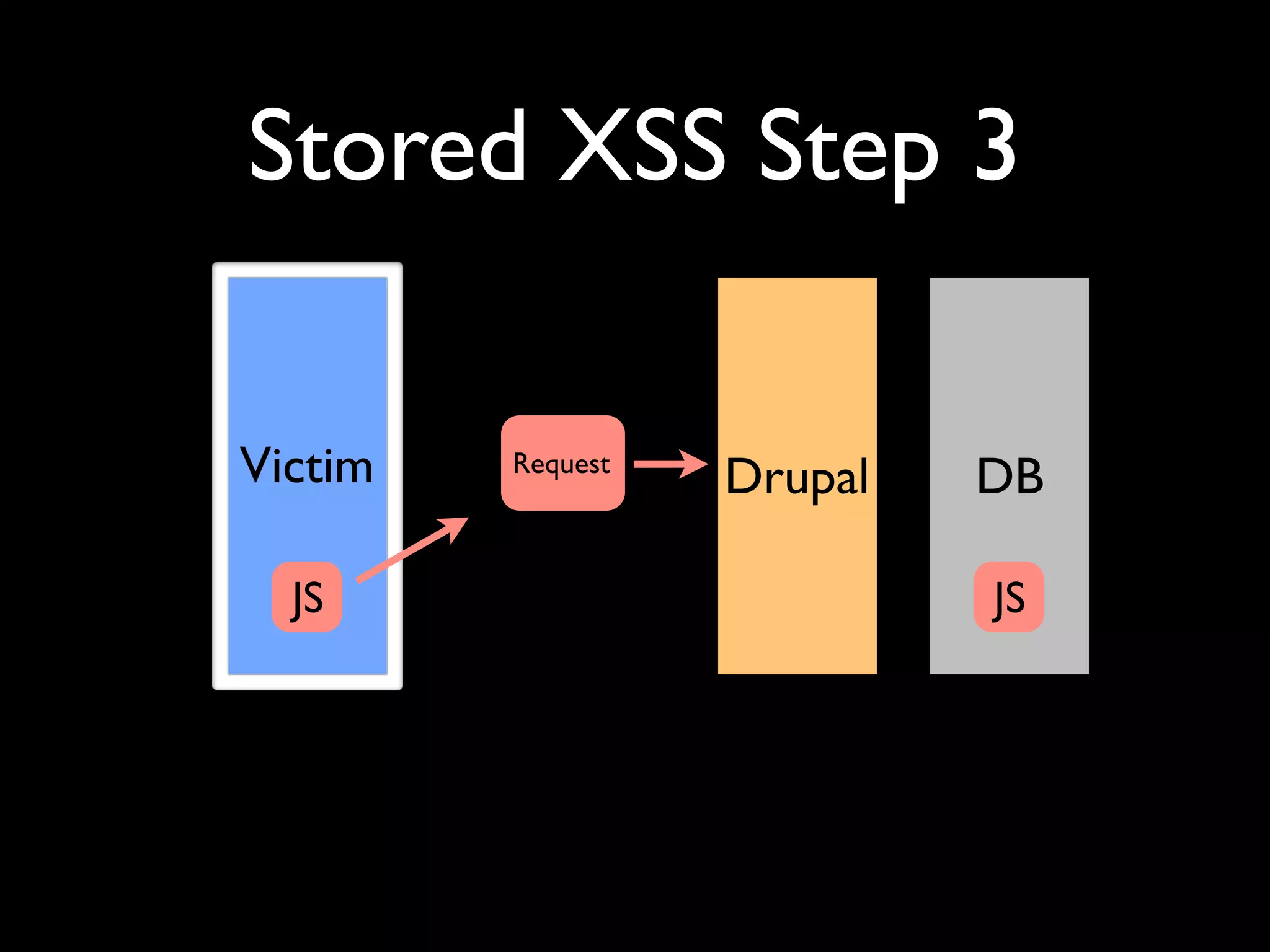
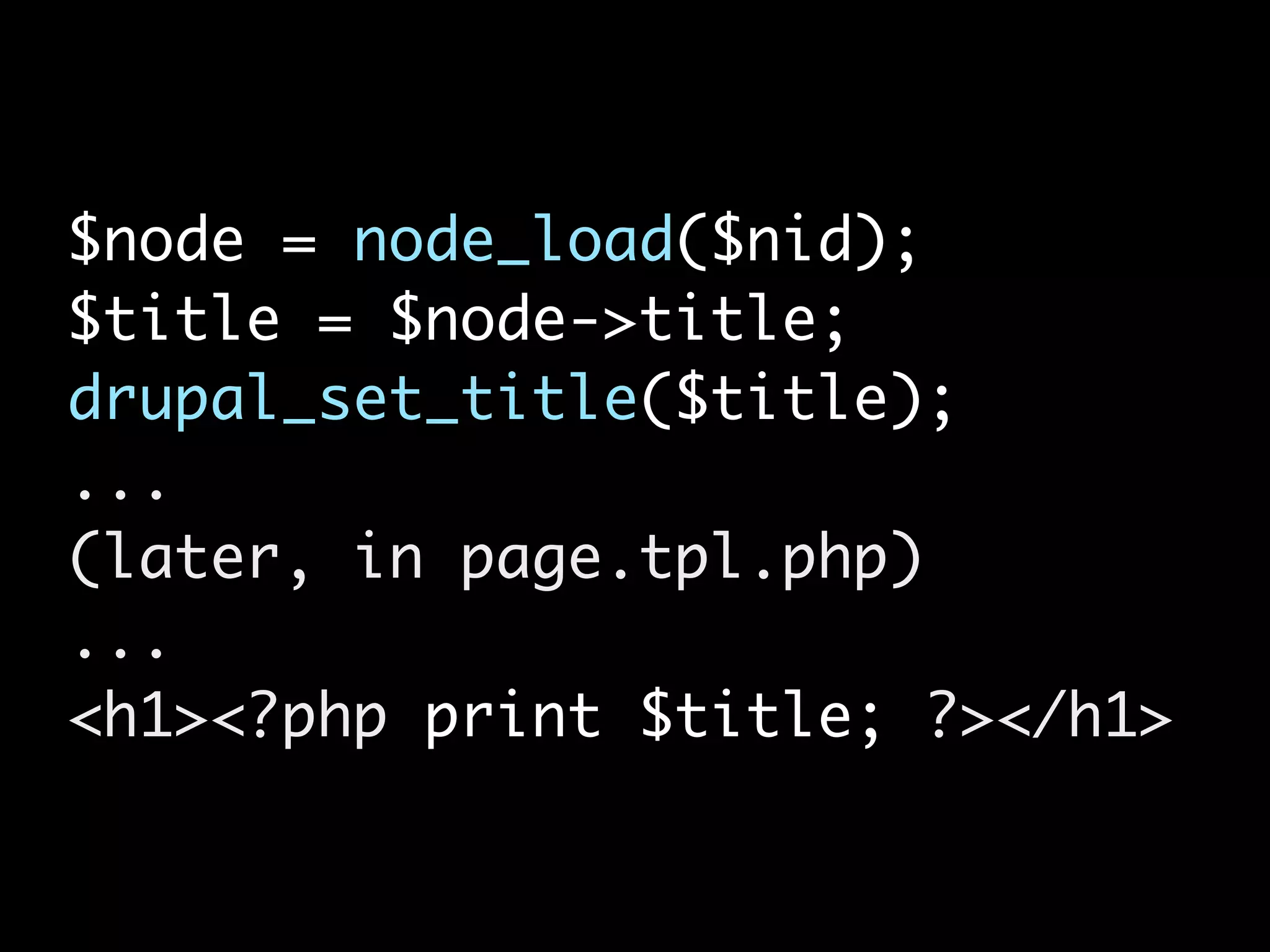



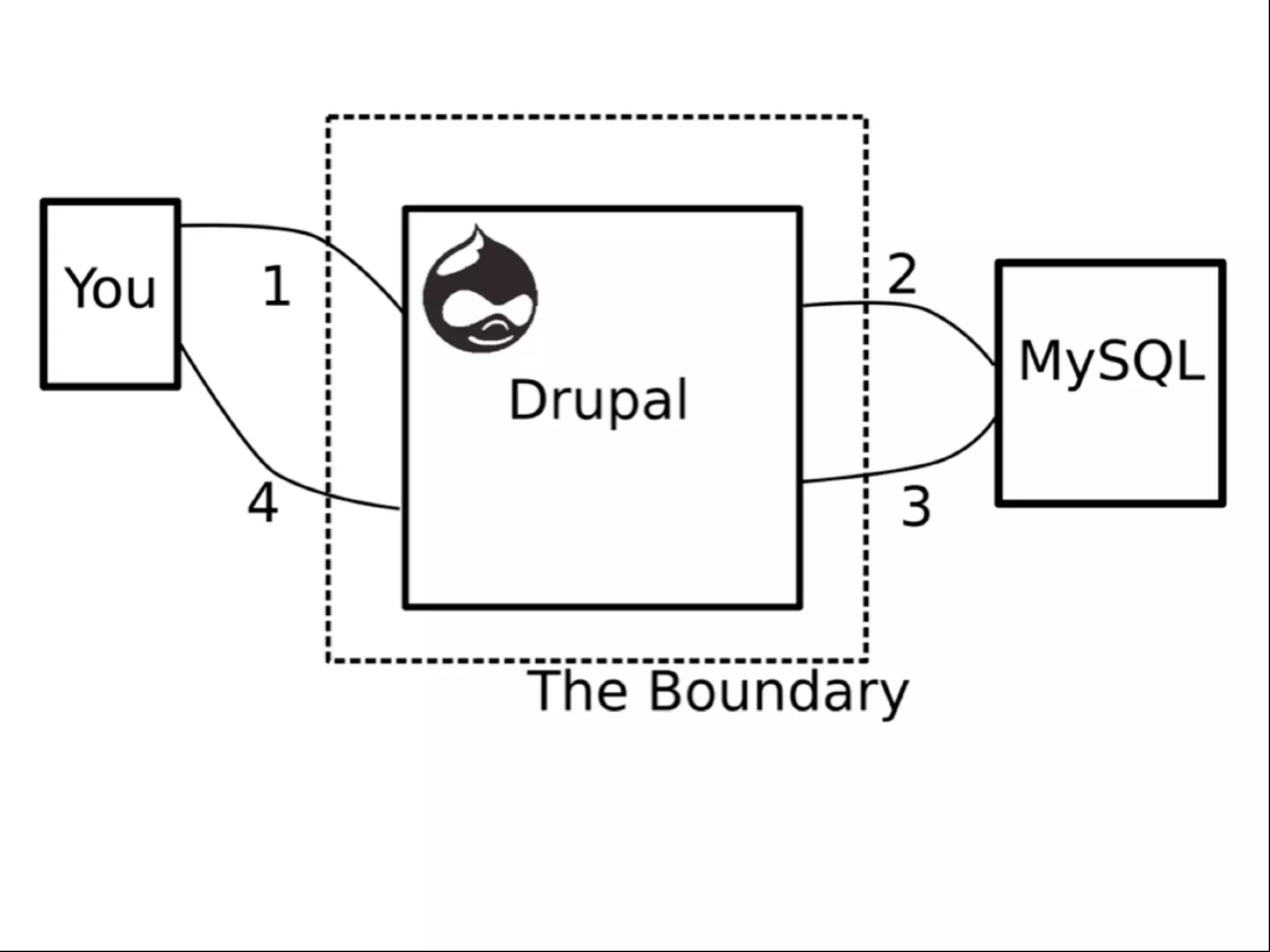
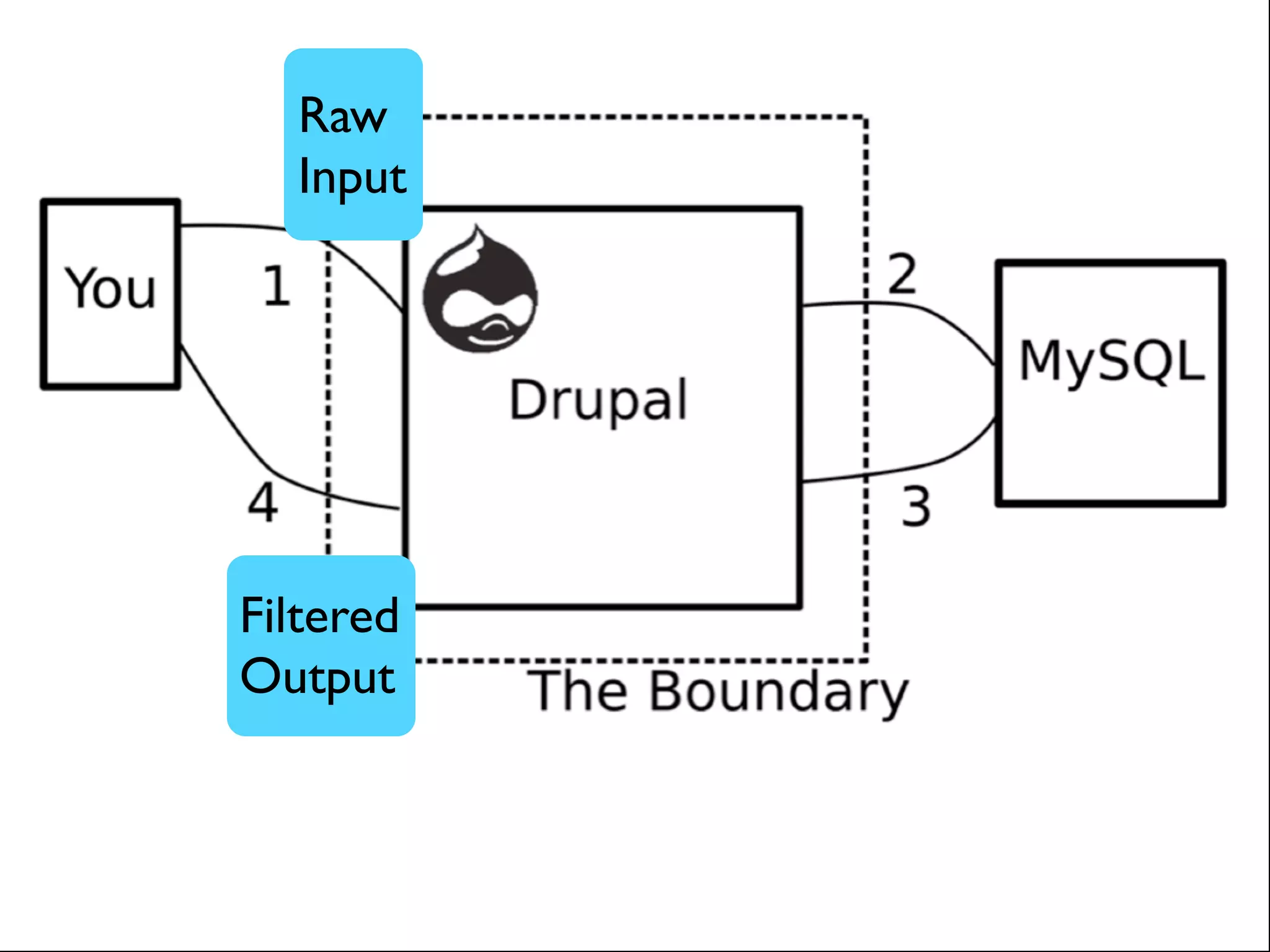
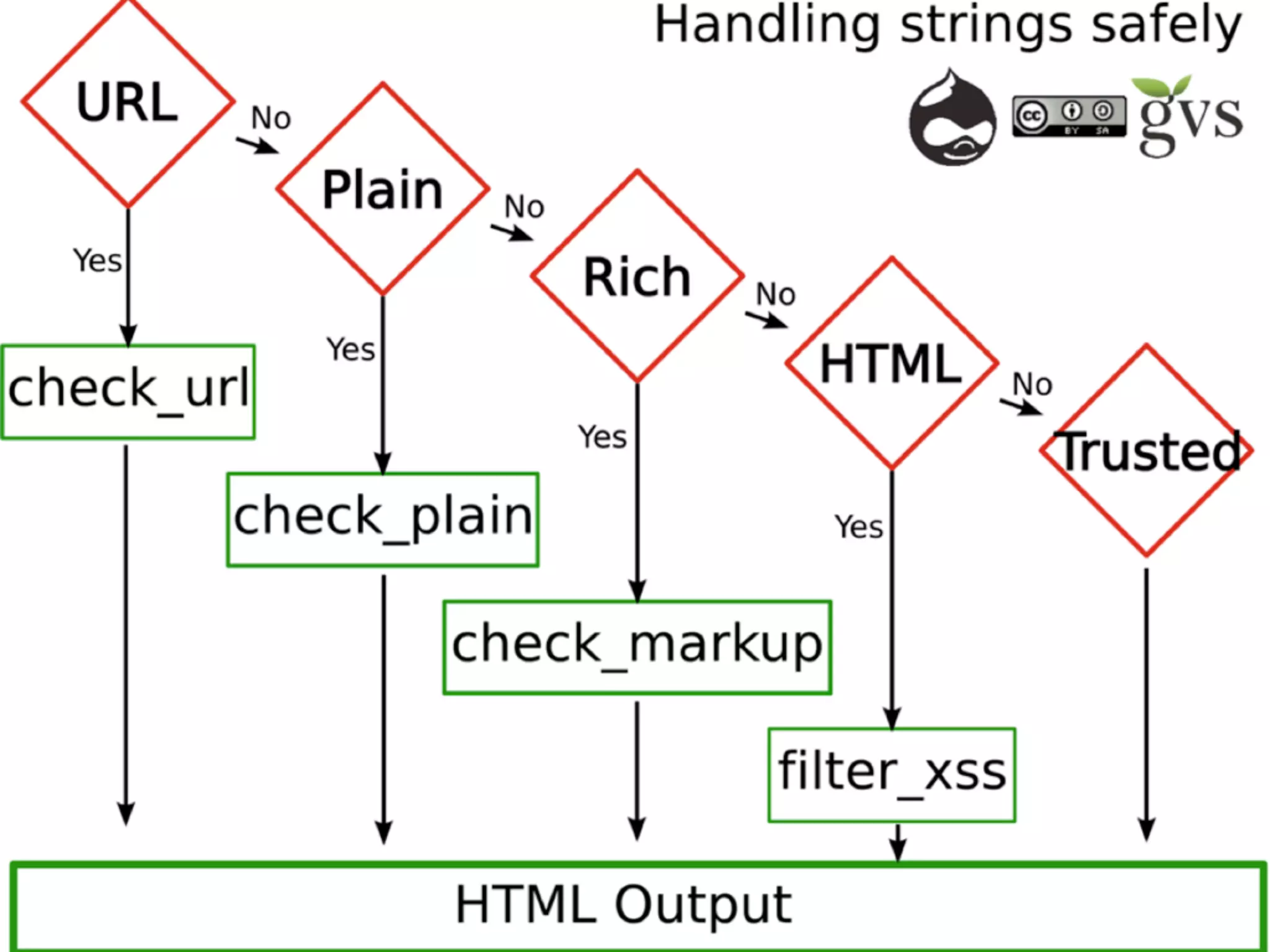
![XSS in Themes <div class=”stuff”> <?php print $node->field_stuff[0][‘value’]; ?>](https://image.slidesharecdn.com/nyccamp-drupal-security-hack-into-120725131446-phpapp02/75/Hack-Into-Drupal-Sites-or-How-to-Secure-Your-Drupal-Site-24-2048.jpg)
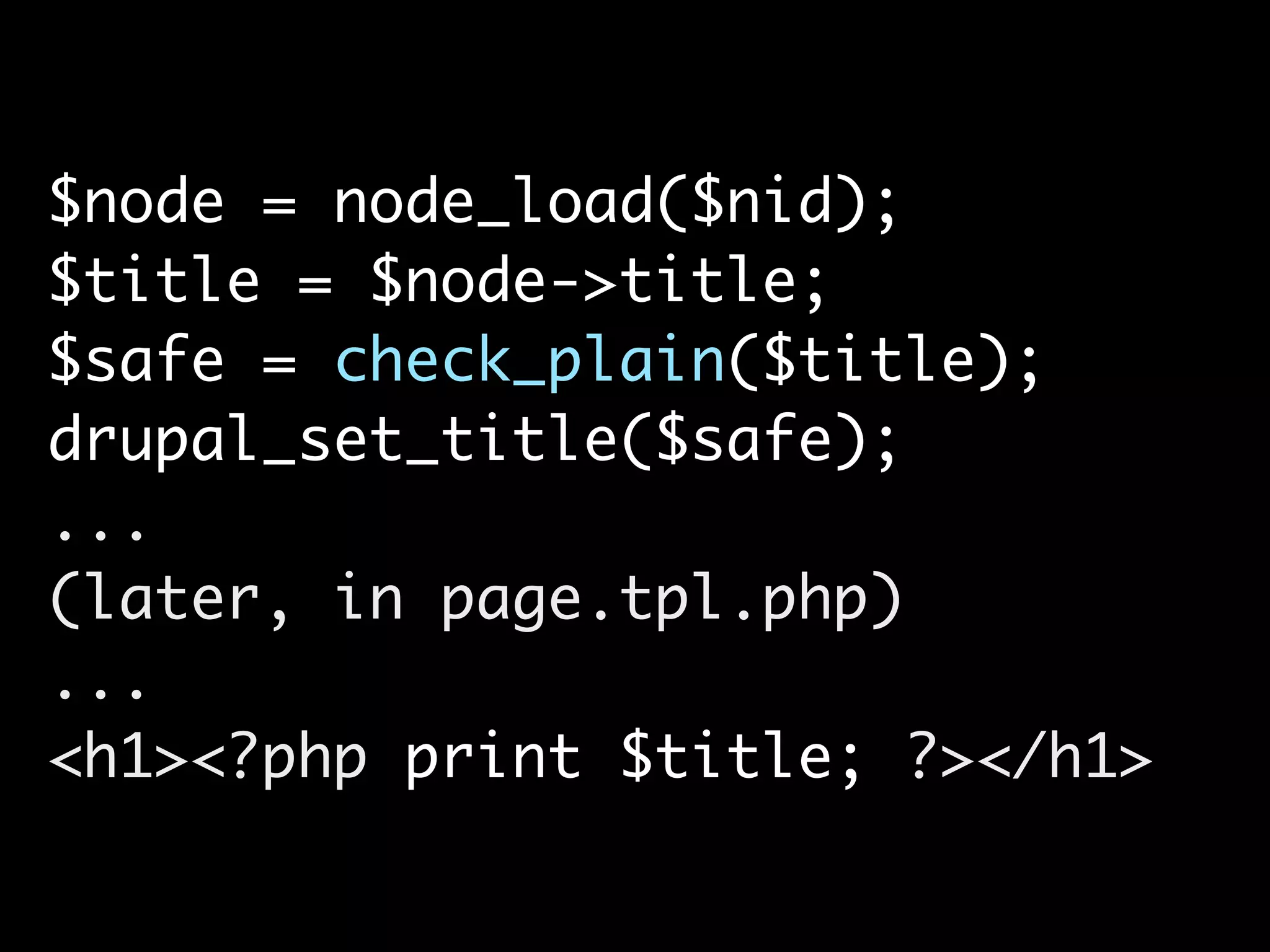
![<div class=”stuff”> <?php print $node->field_stuff[0][‘safe’]; // OR $stuff = $node->field_stuff[0]; print content_format(‘field_stuff’, $stuff); ?>](https://image.slidesharecdn.com/nyccamp-drupal-security-hack-into-120725131446-phpapp02/75/Hack-Into-Drupal-Sites-or-How-to-Secure-Your-Drupal-Site-25-2048.jpg)