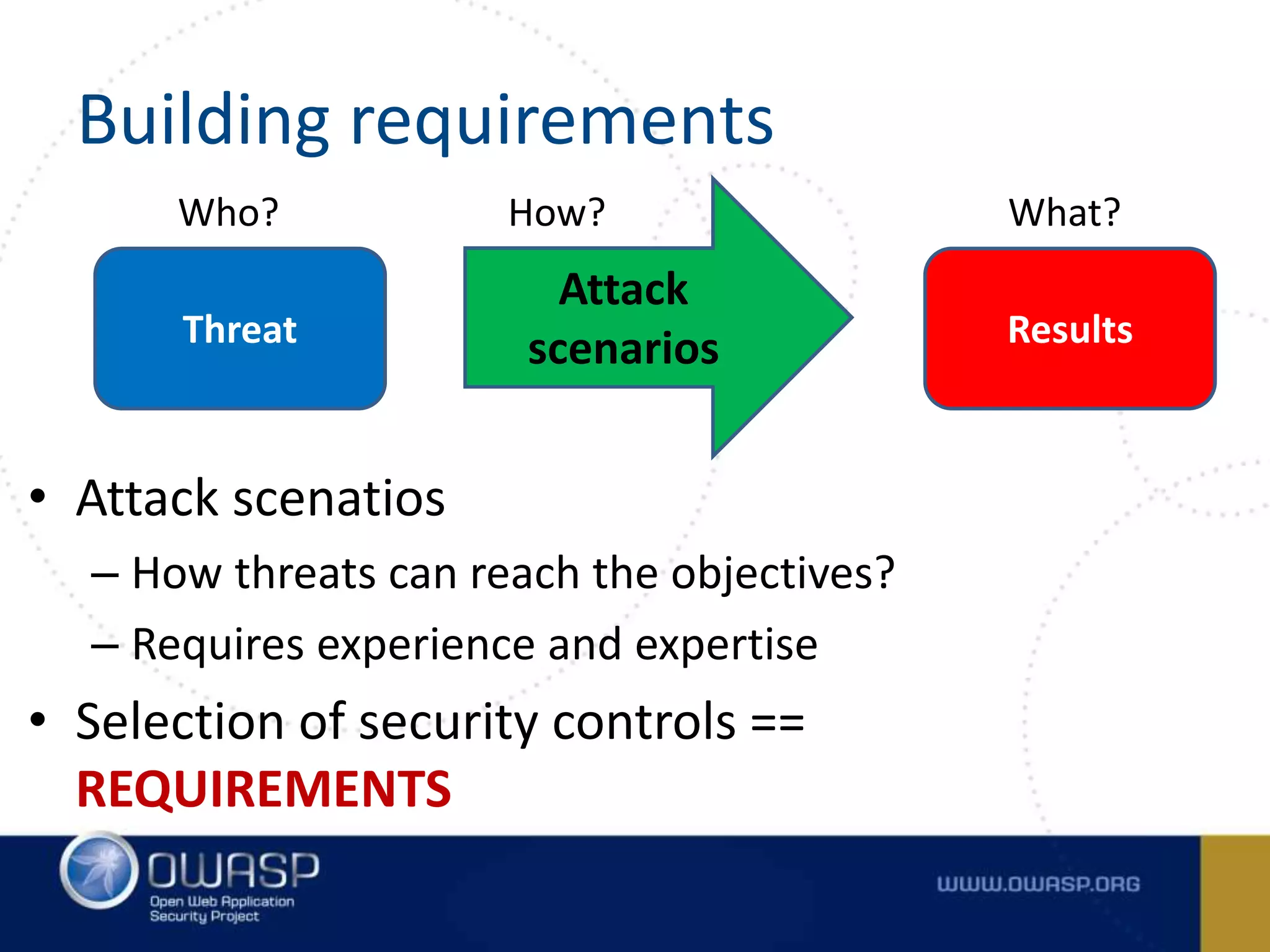
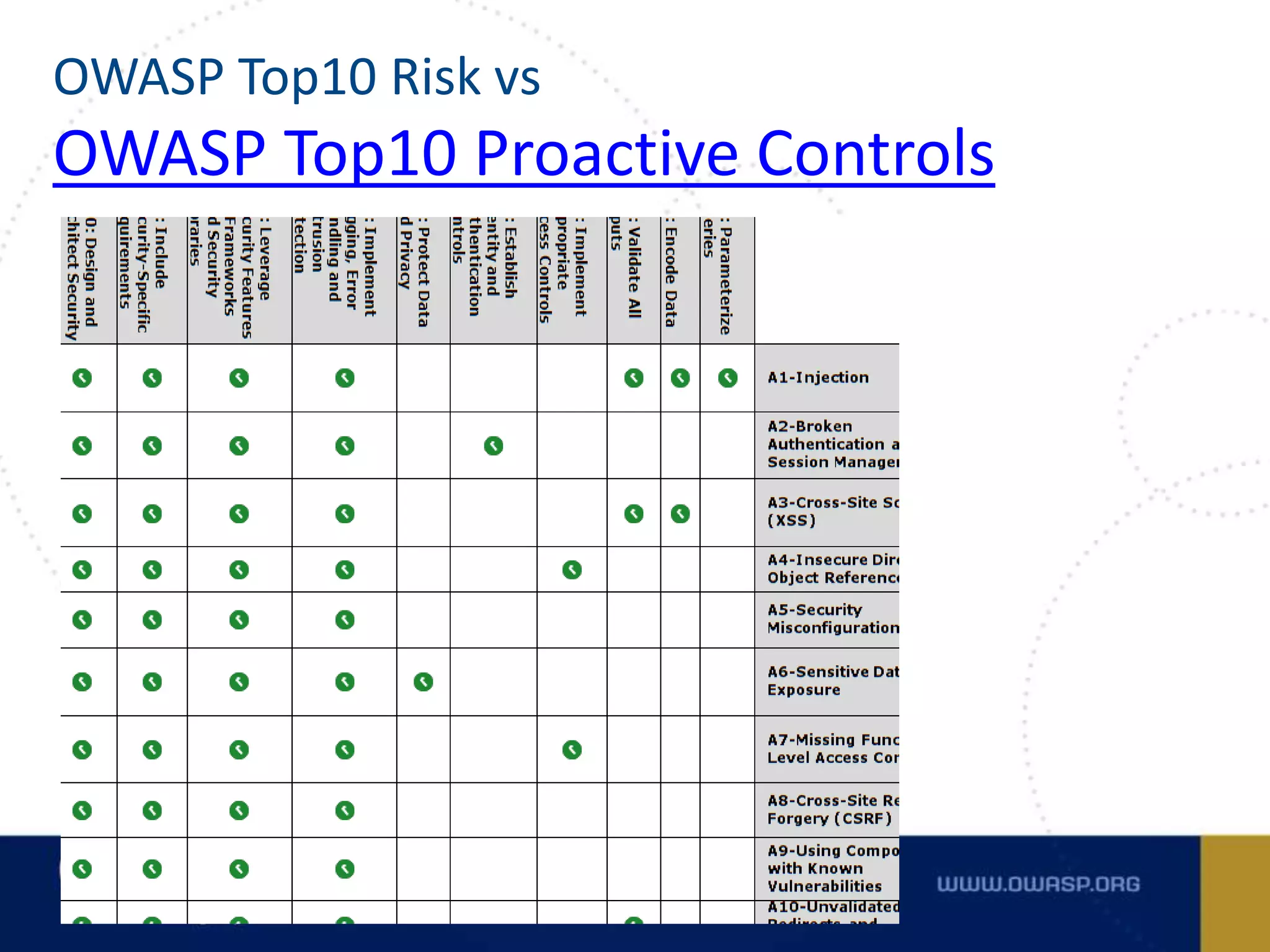
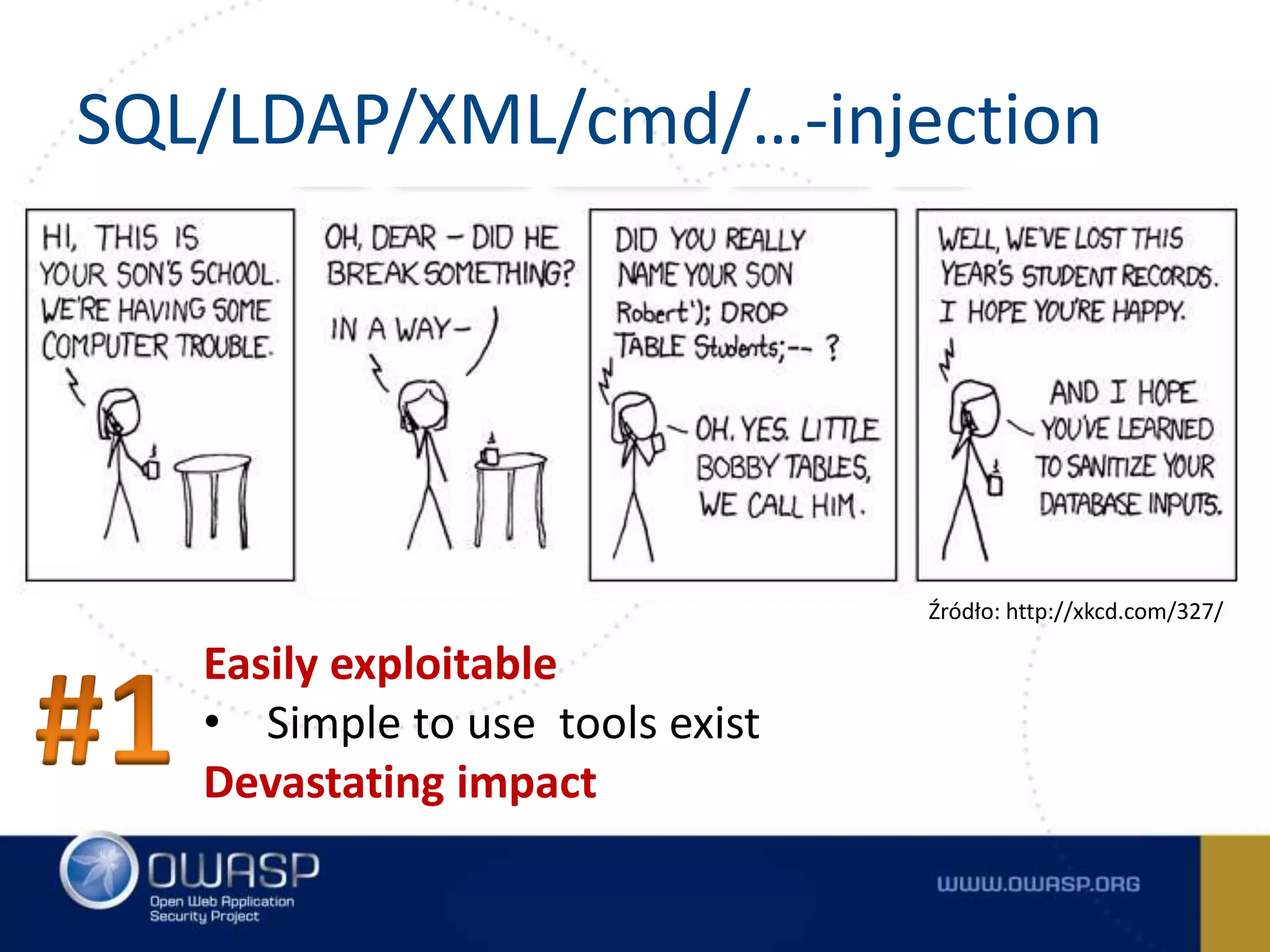
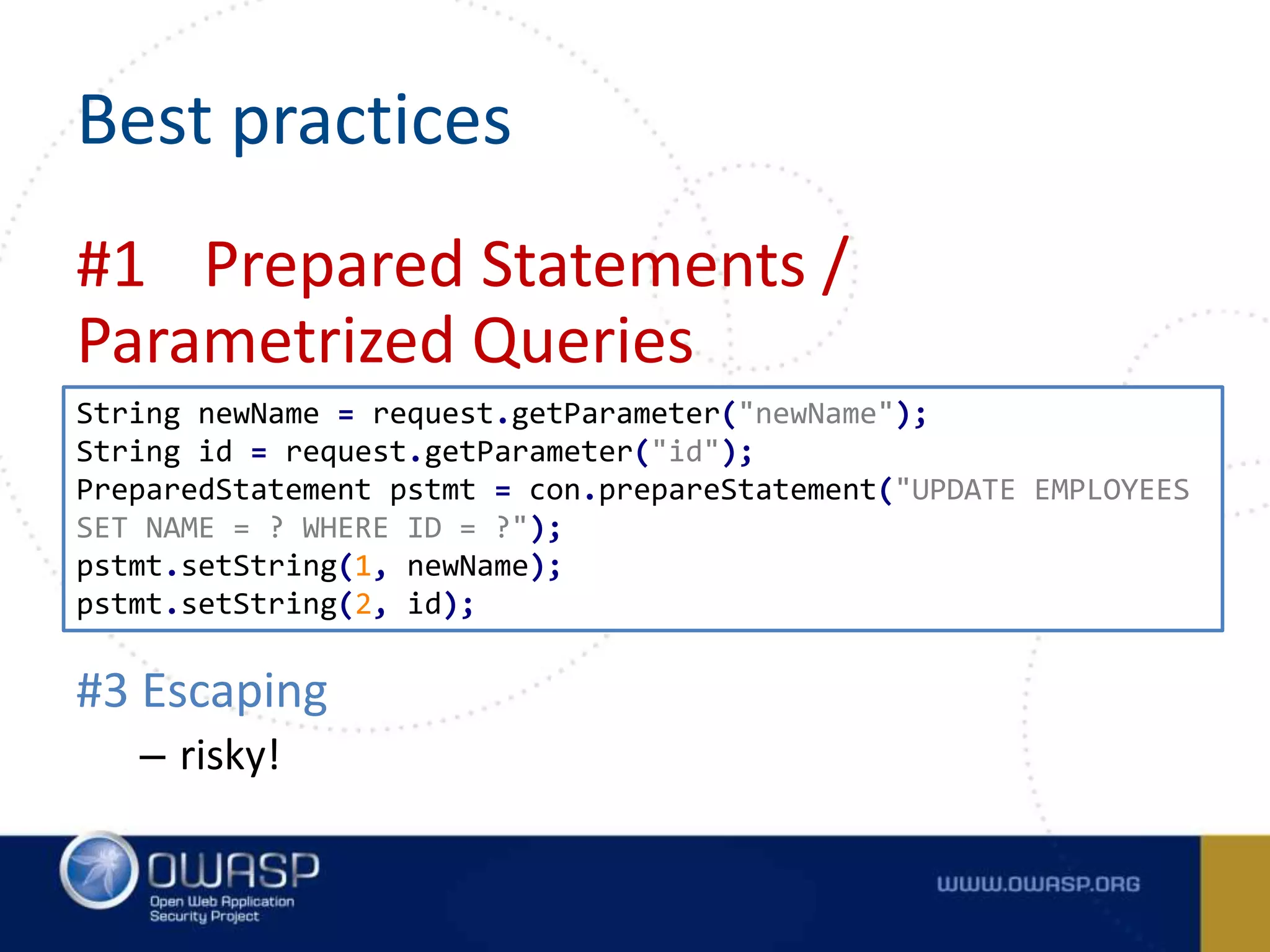
The document outlines the OWASP Top Ten Proactive Controls for secure coding, emphasizing practices such as input validation, parameterization, and access control to mitigate security vulnerabilities. It highlights the importance of education for developers in application security and provides best practices for each commandment. The summary concludes that while these practices are crucial, each application should have its own risk profile tailored to its specific threats.


















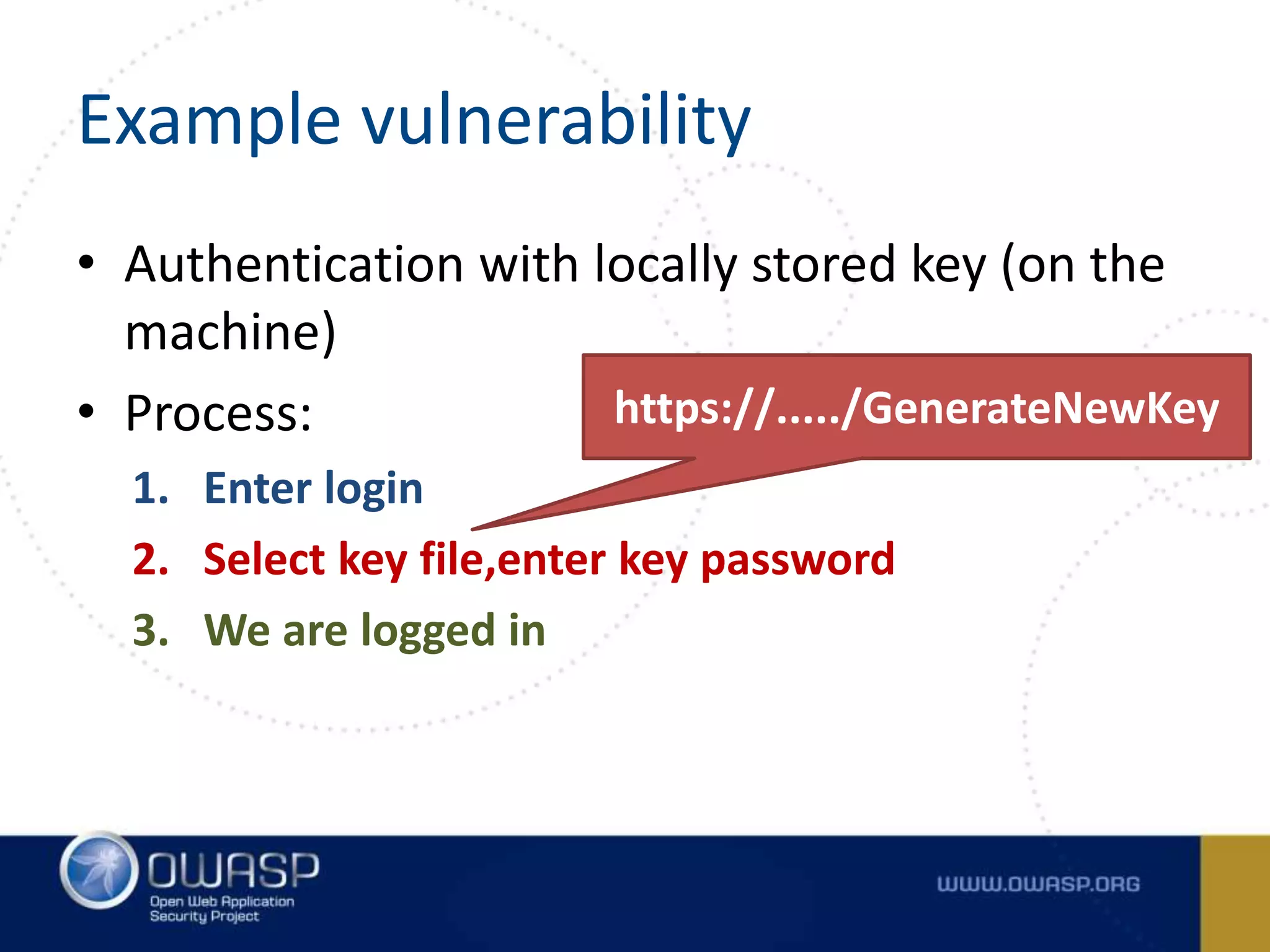


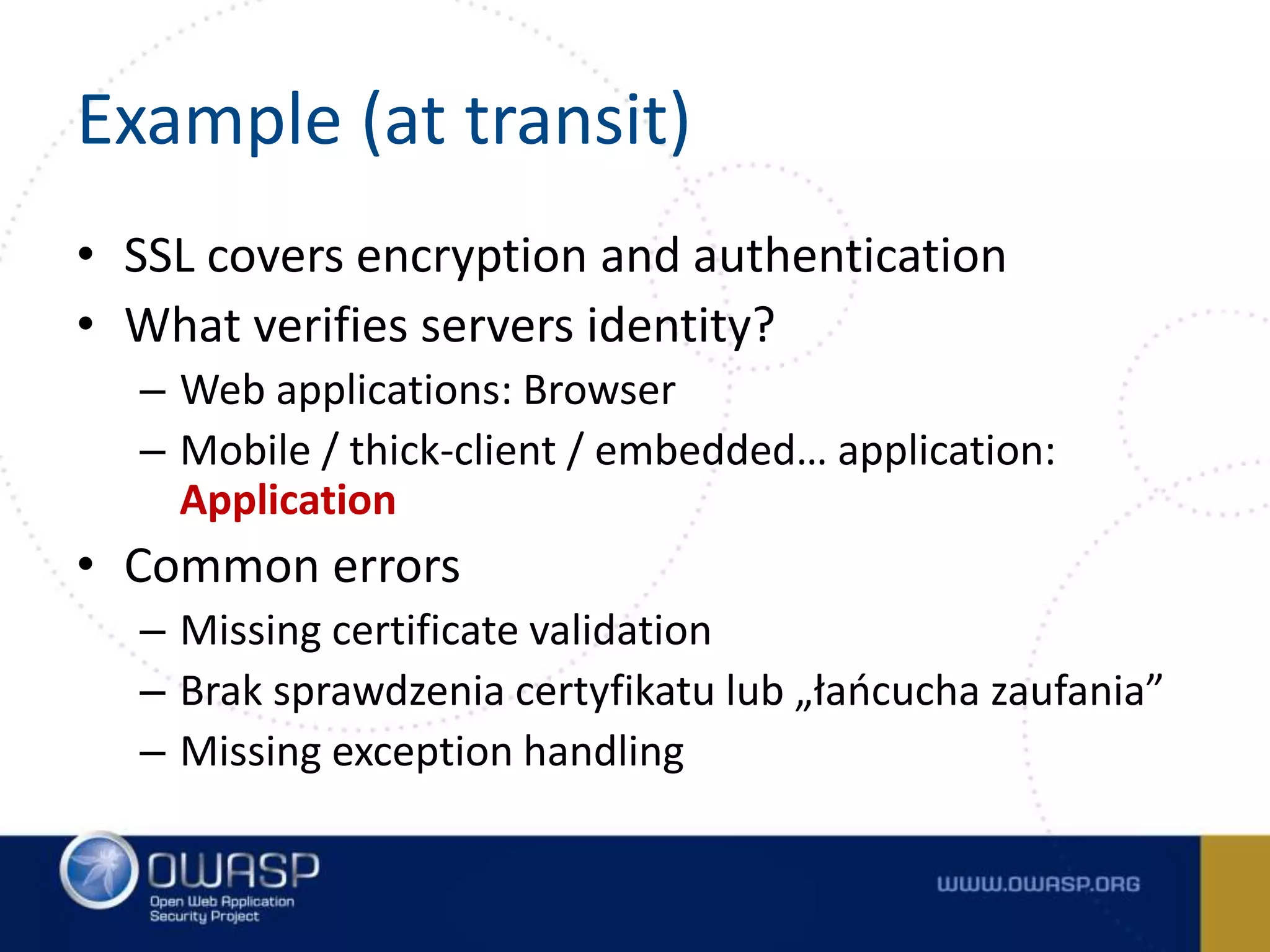
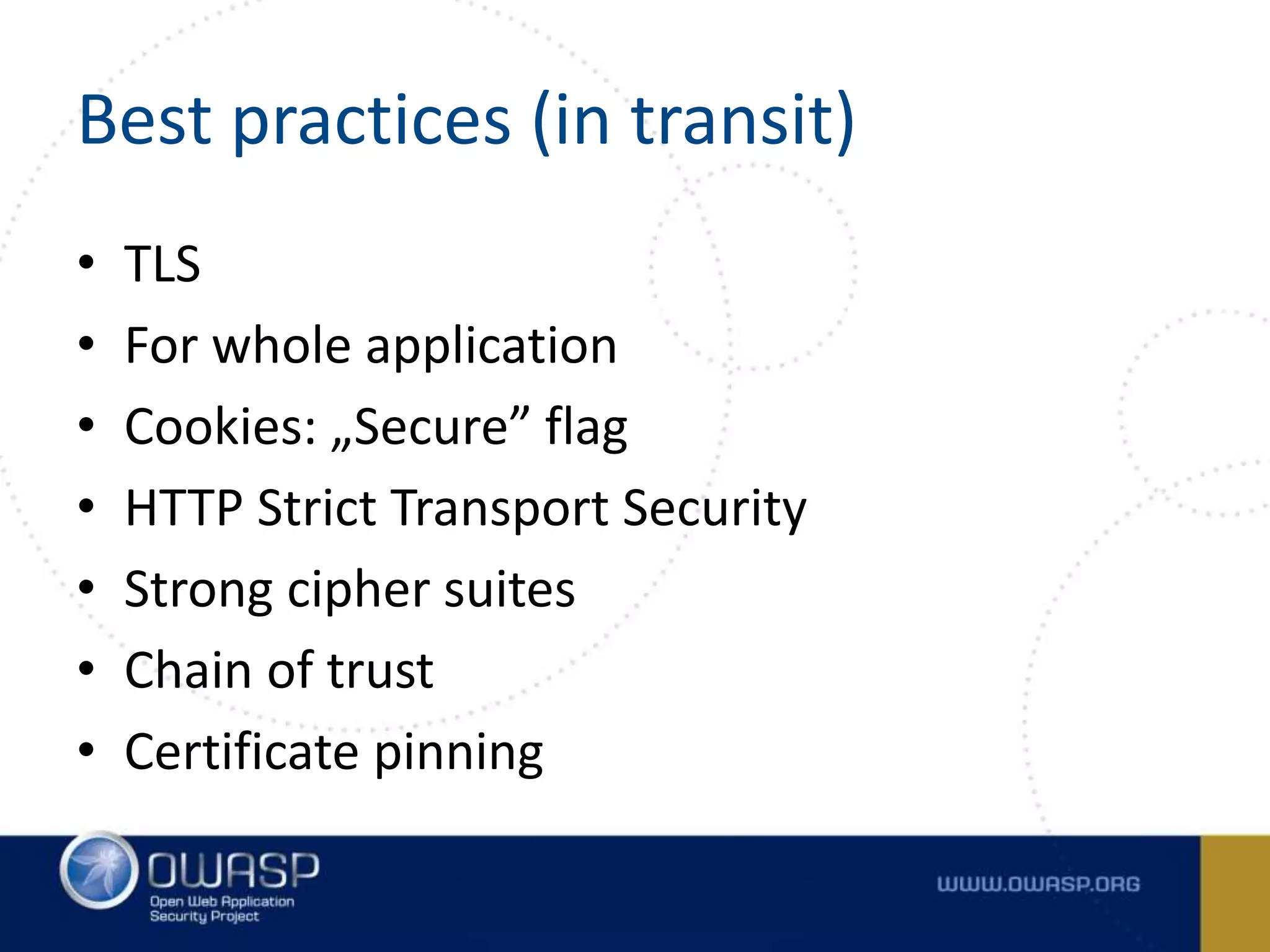
![Example (at rest) • Storing password • „Own” SHA1 function public static String encrypt(byte [] in) { String out = ""; for(int i = 0; i < in.length; i++) { byte b = (byte)(in[i] ^ key[i%key.length]); out += "" + hexDigit[(b & 0xf0)>>4] + hexDigit[b & 0x0f]; } return out; }](https://image.slidesharecdn.com/tencommandmentsofsecurecoding-150522085323-lva1-app6891/75/Ten-Commandments-of-Secure-Coding-37-2048.jpg)