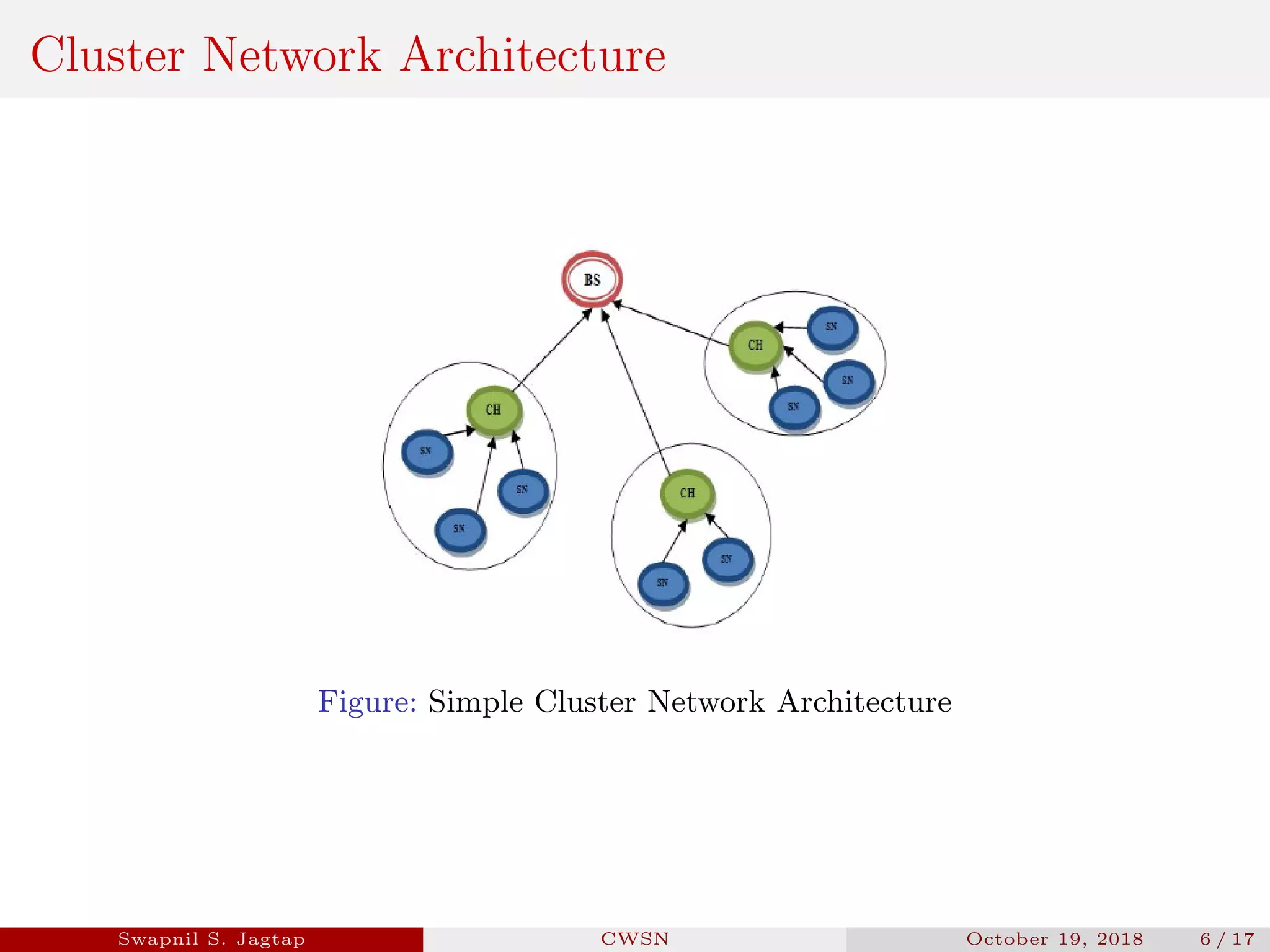
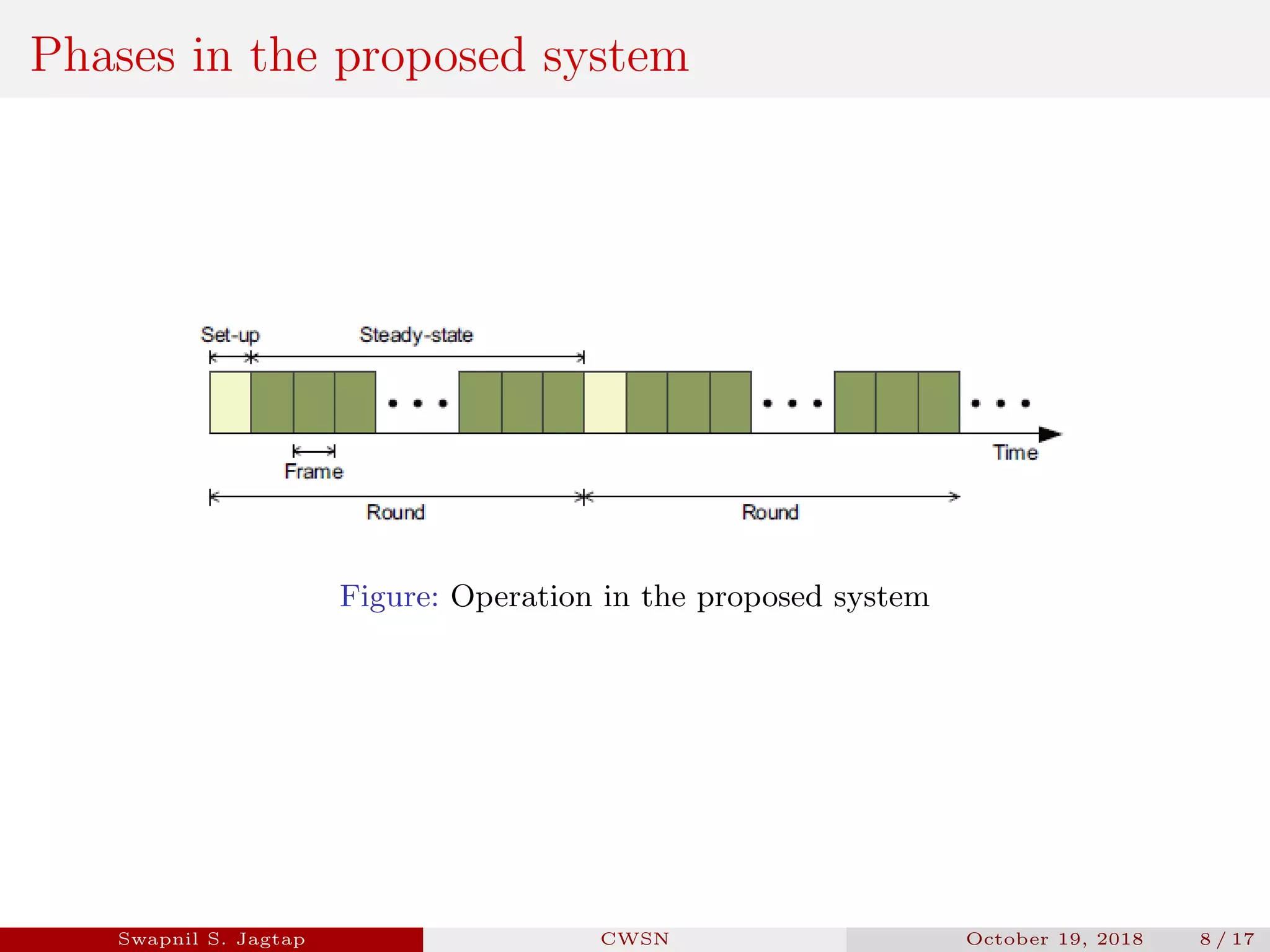
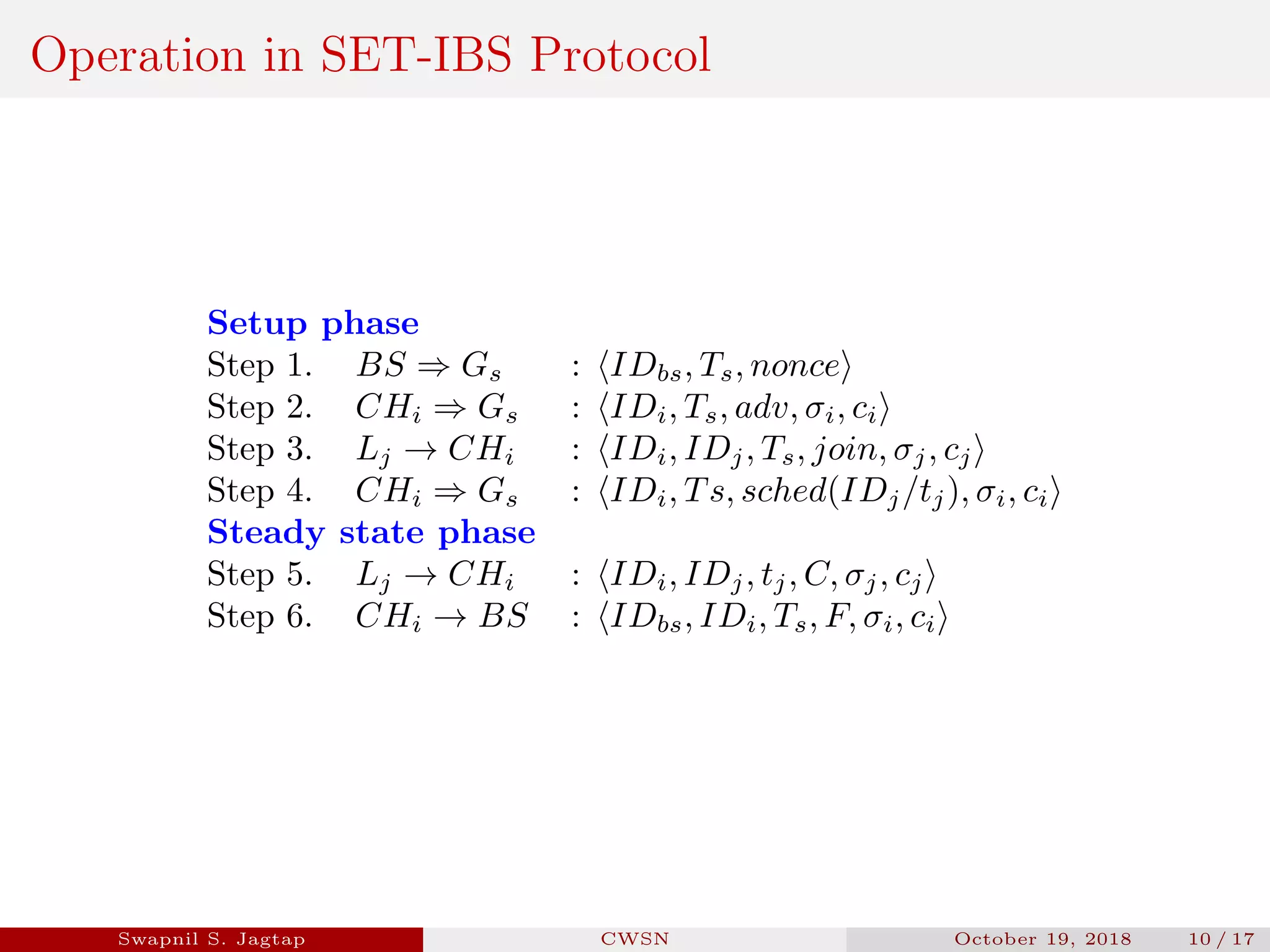
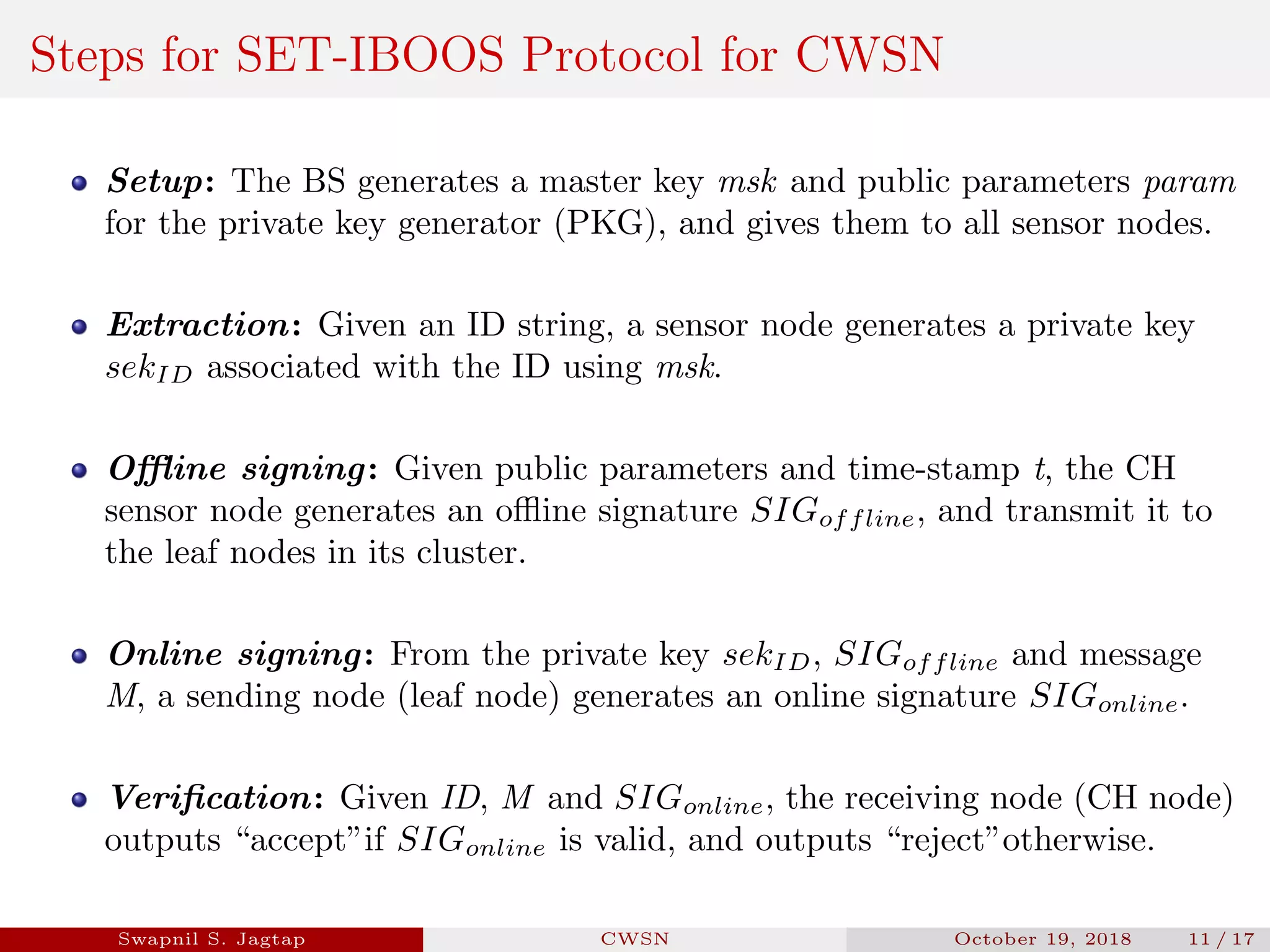
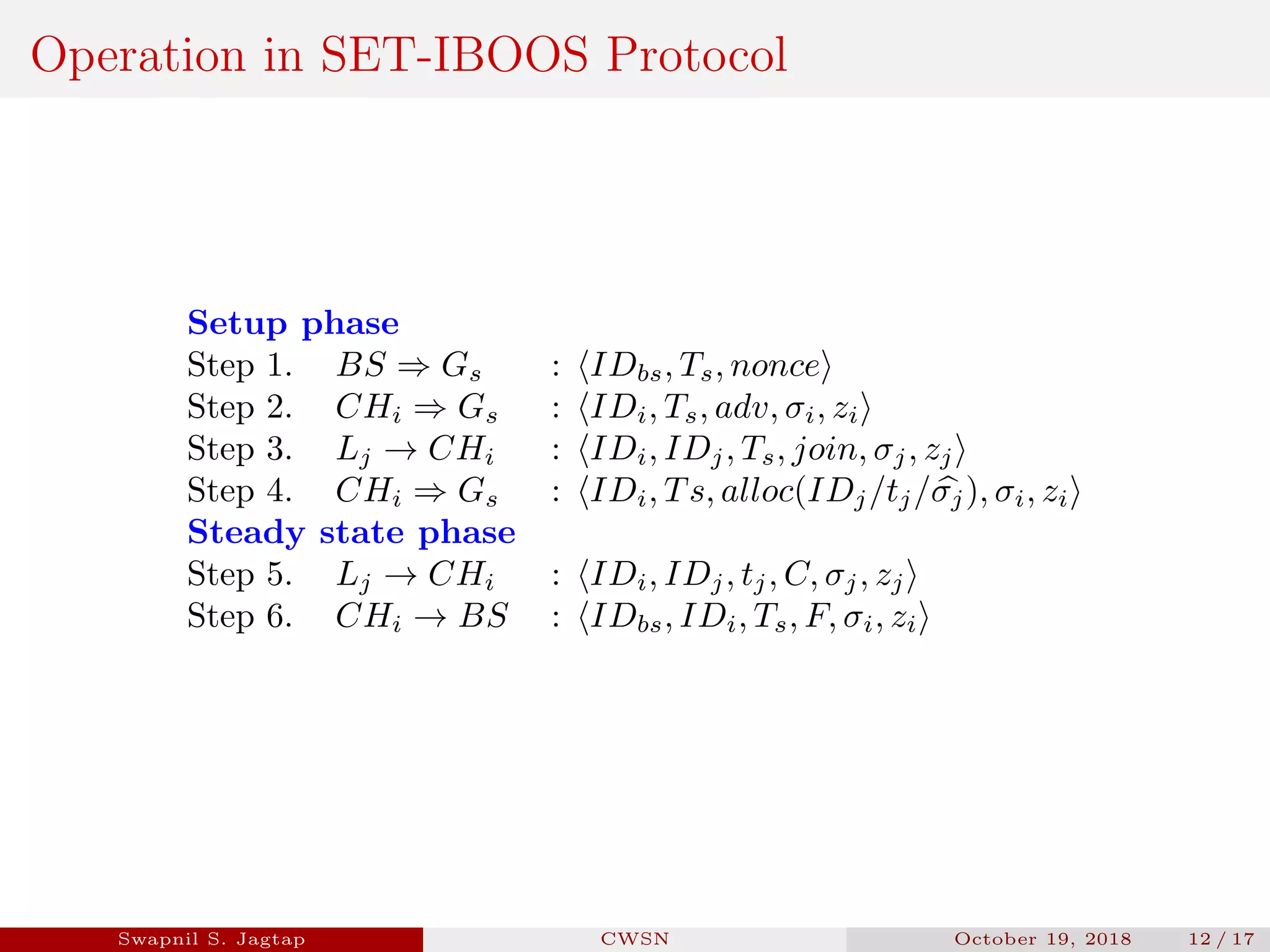
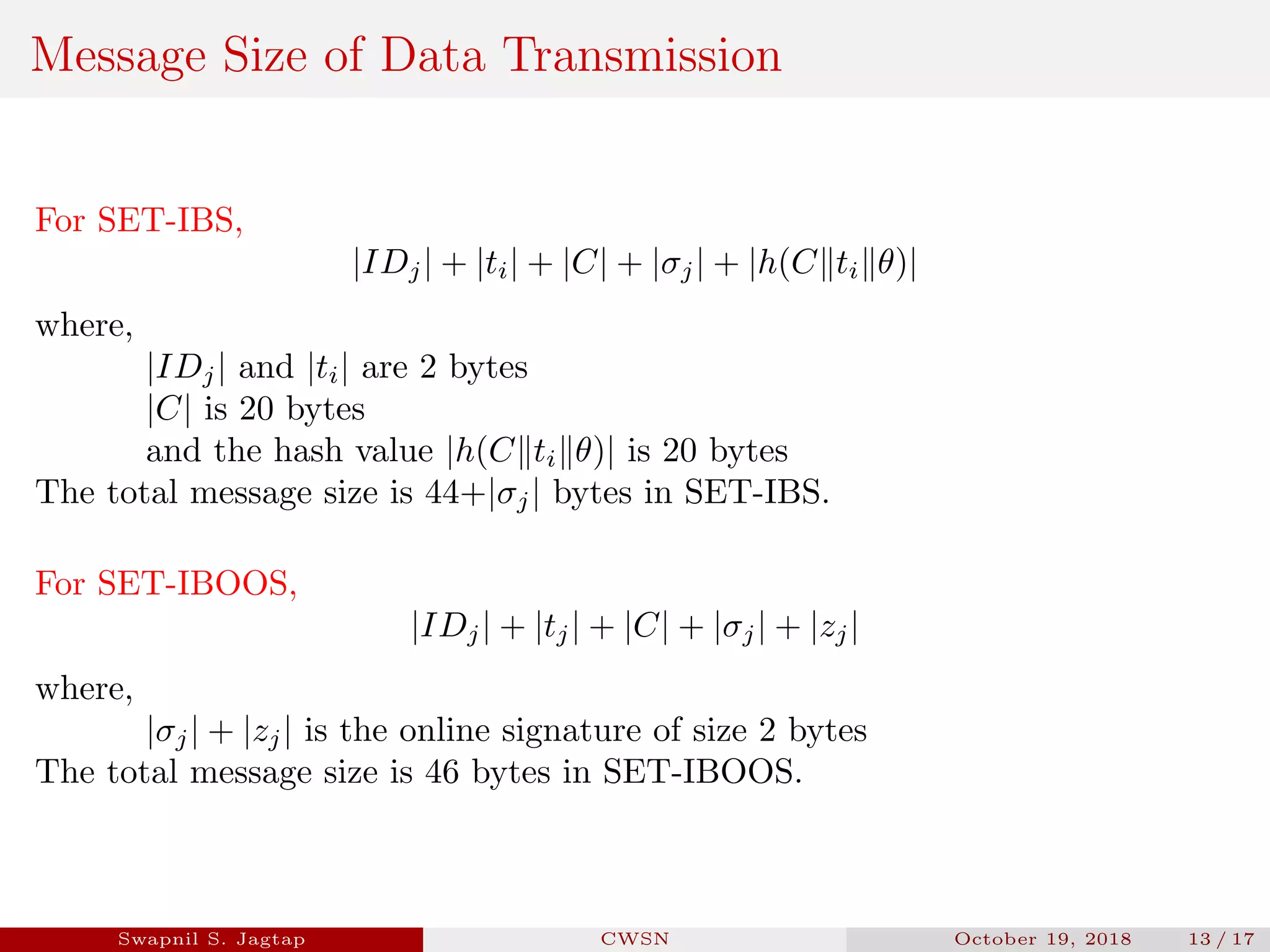
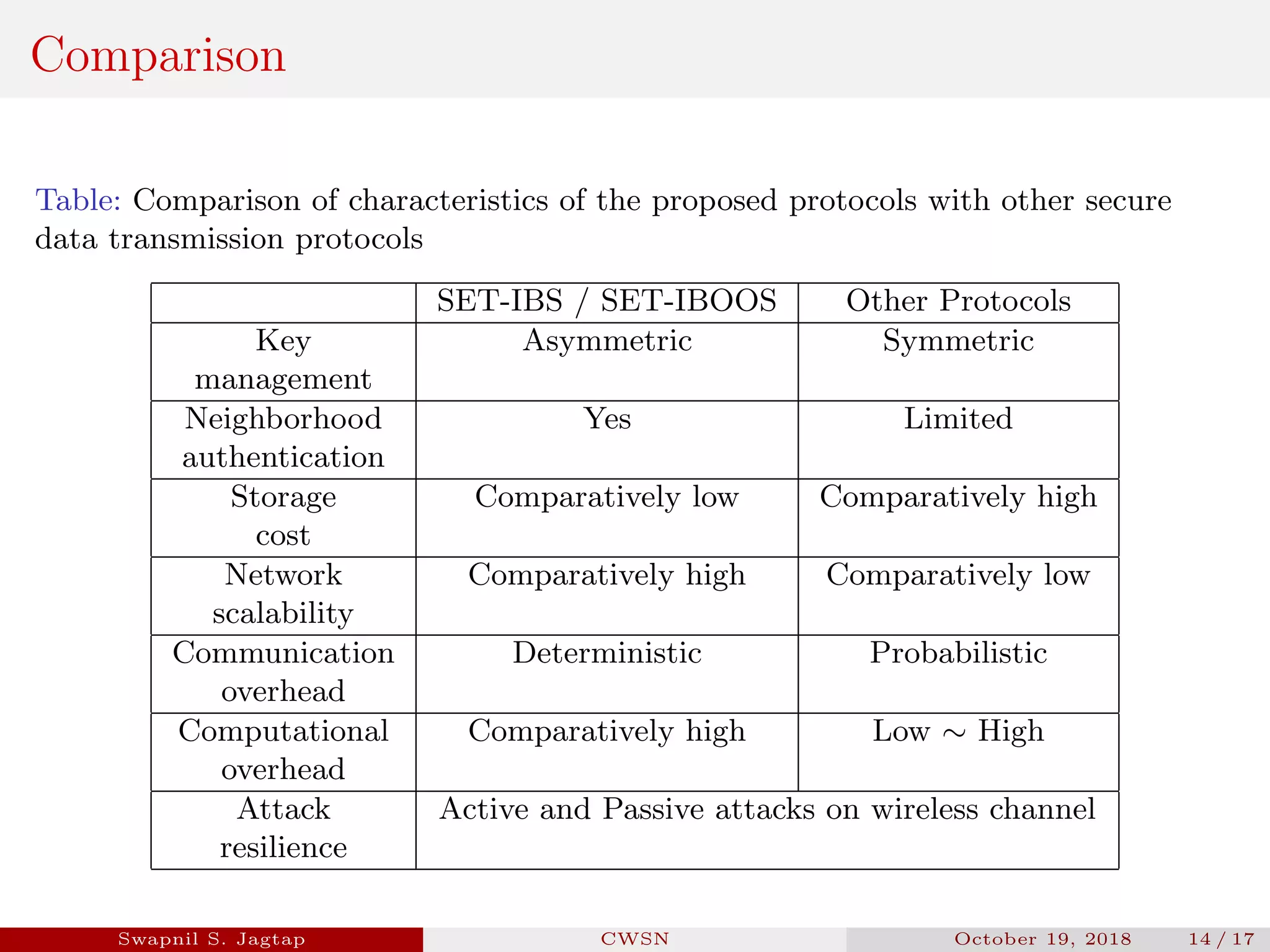
Swapnil S. Jagtap presented a seminar on secure and efficient data transmission methods for cluster-based wireless sensor networks. The presentation covered cluster network architecture, two proposed protocols called SET-IBS and SET-IBOOS, and compared the characteristics of the proposed protocols to other secure data transmission protocols. The protocols aim to securely and efficiently transmit data in cluster-based wireless sensor networks through the use of identity-based digital signatures.