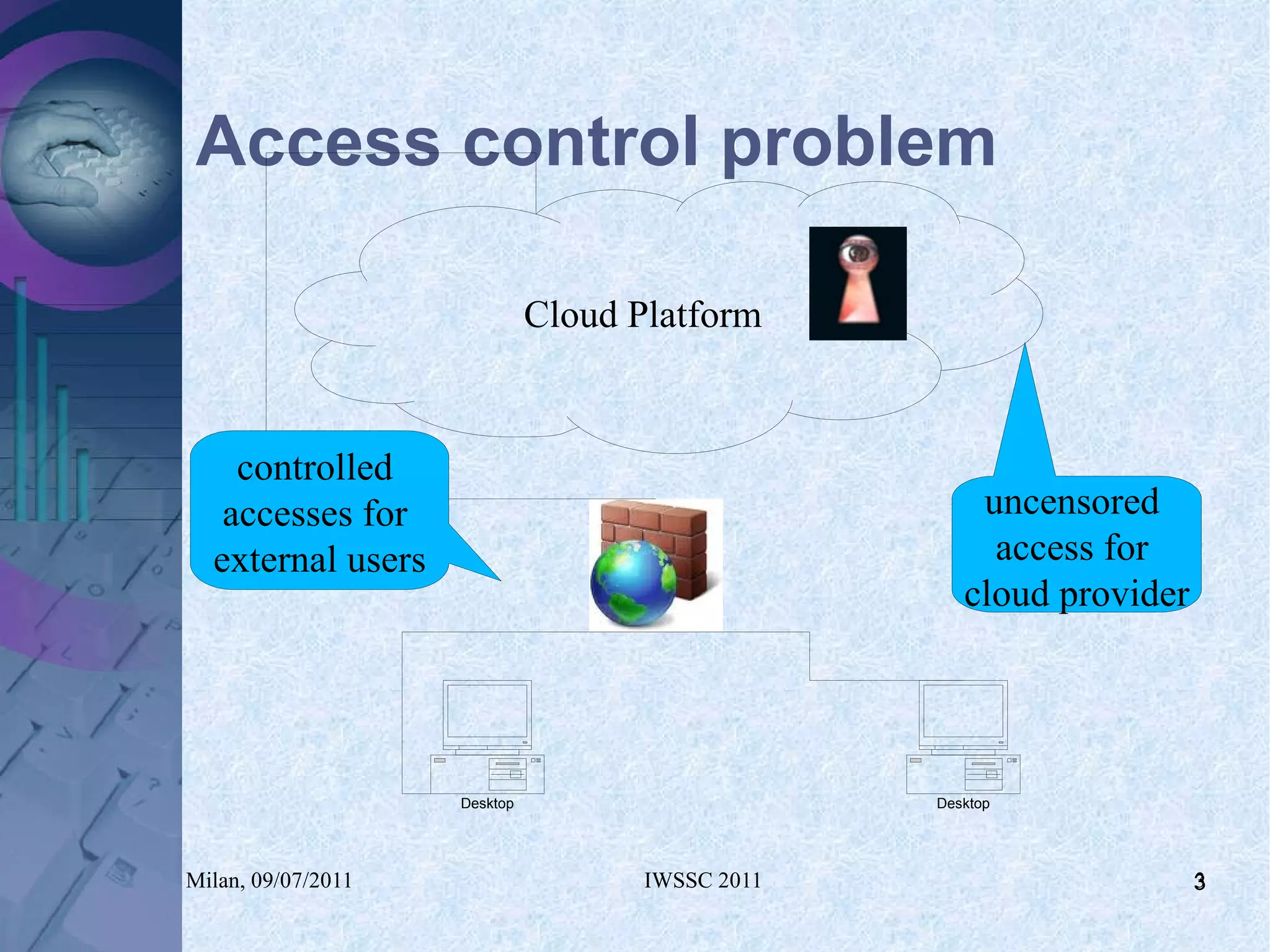
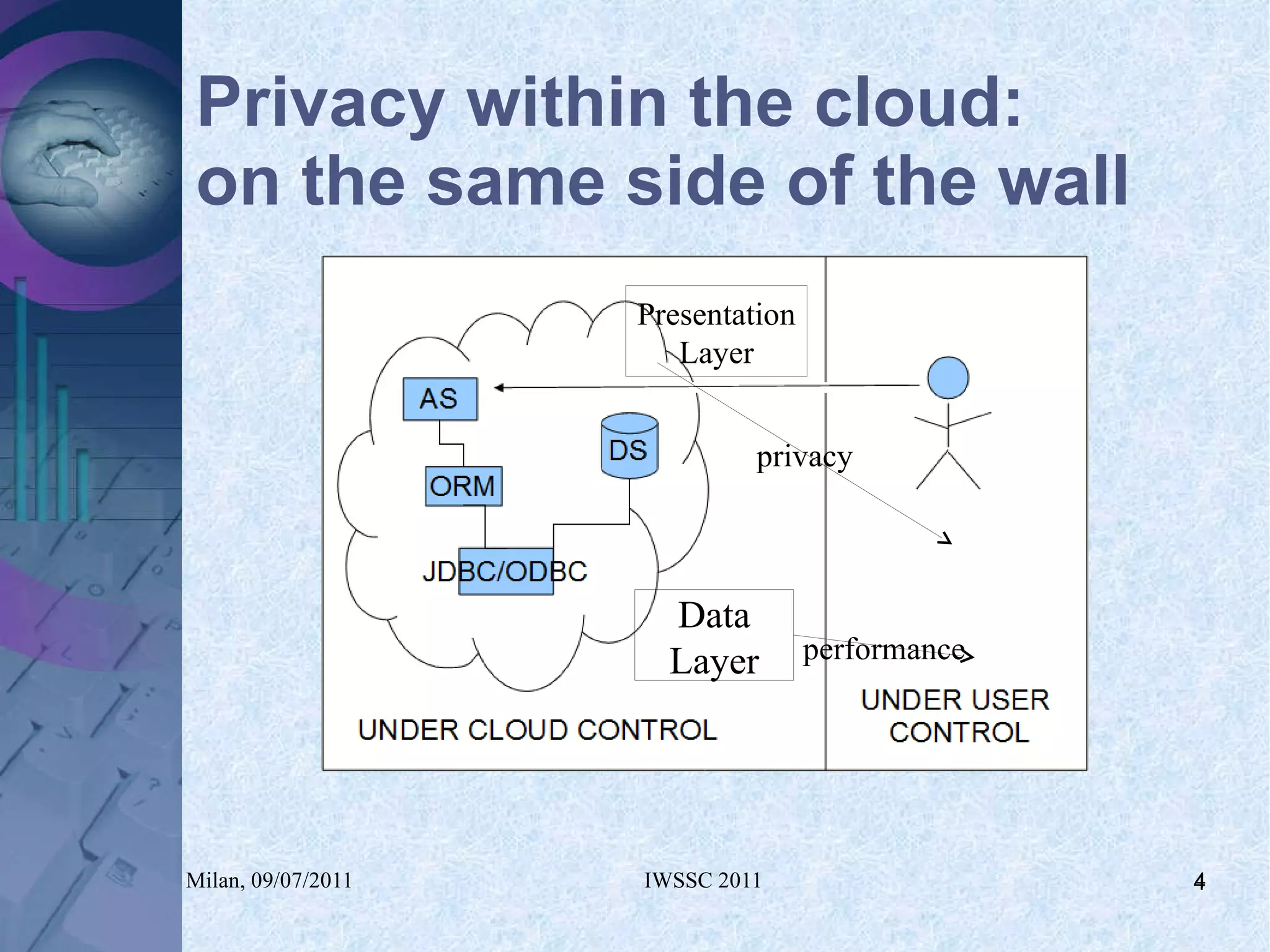
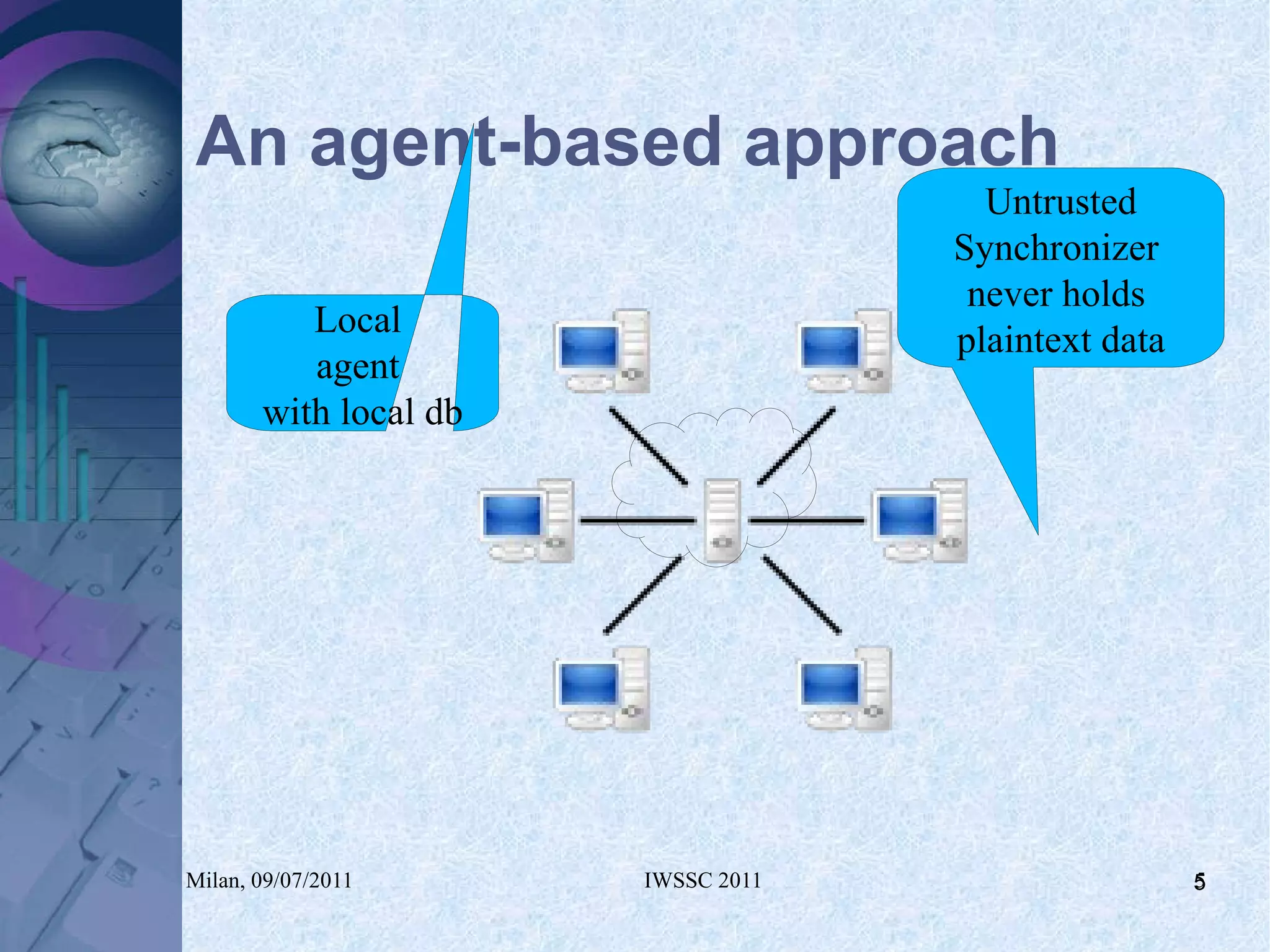
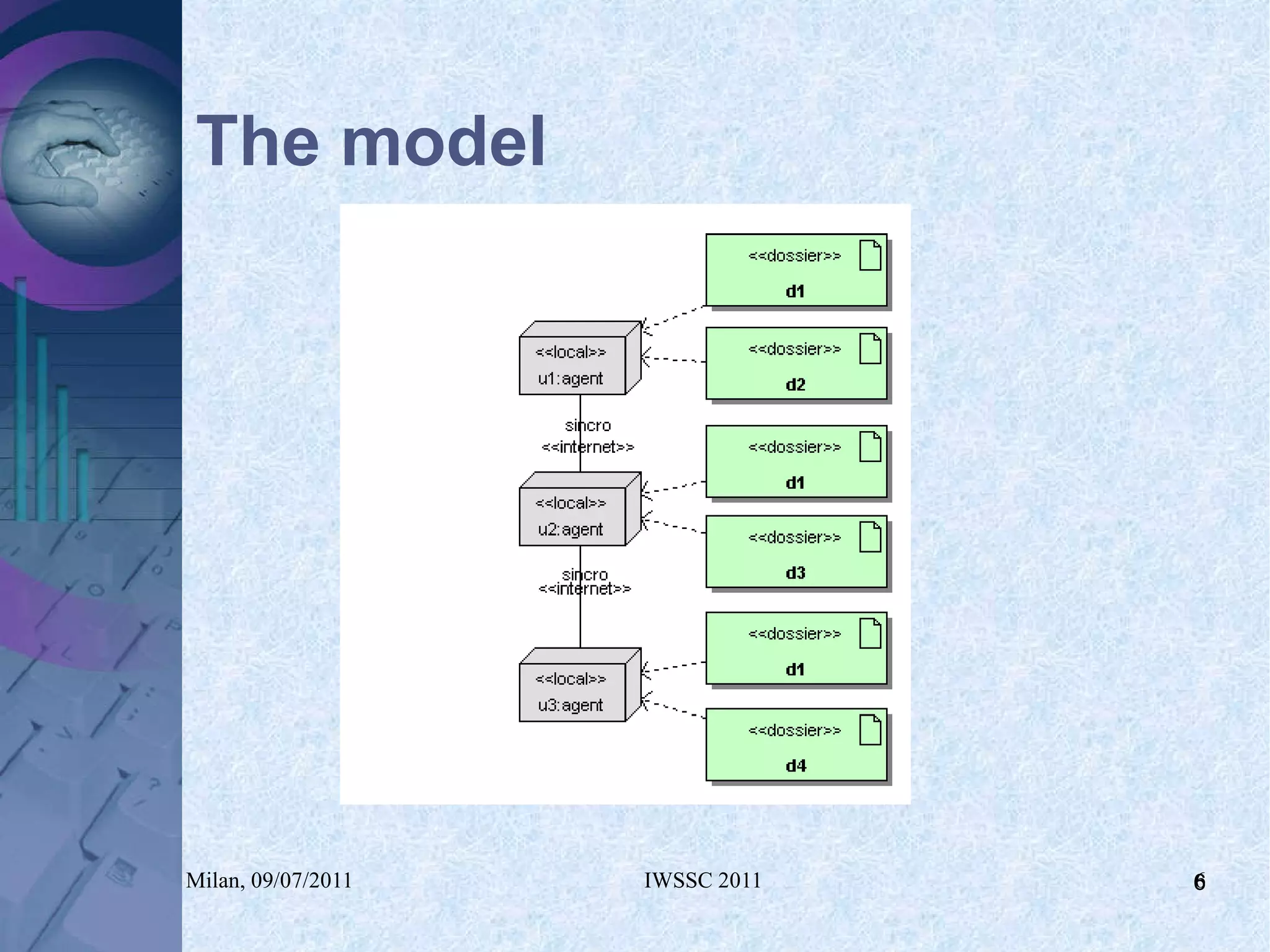
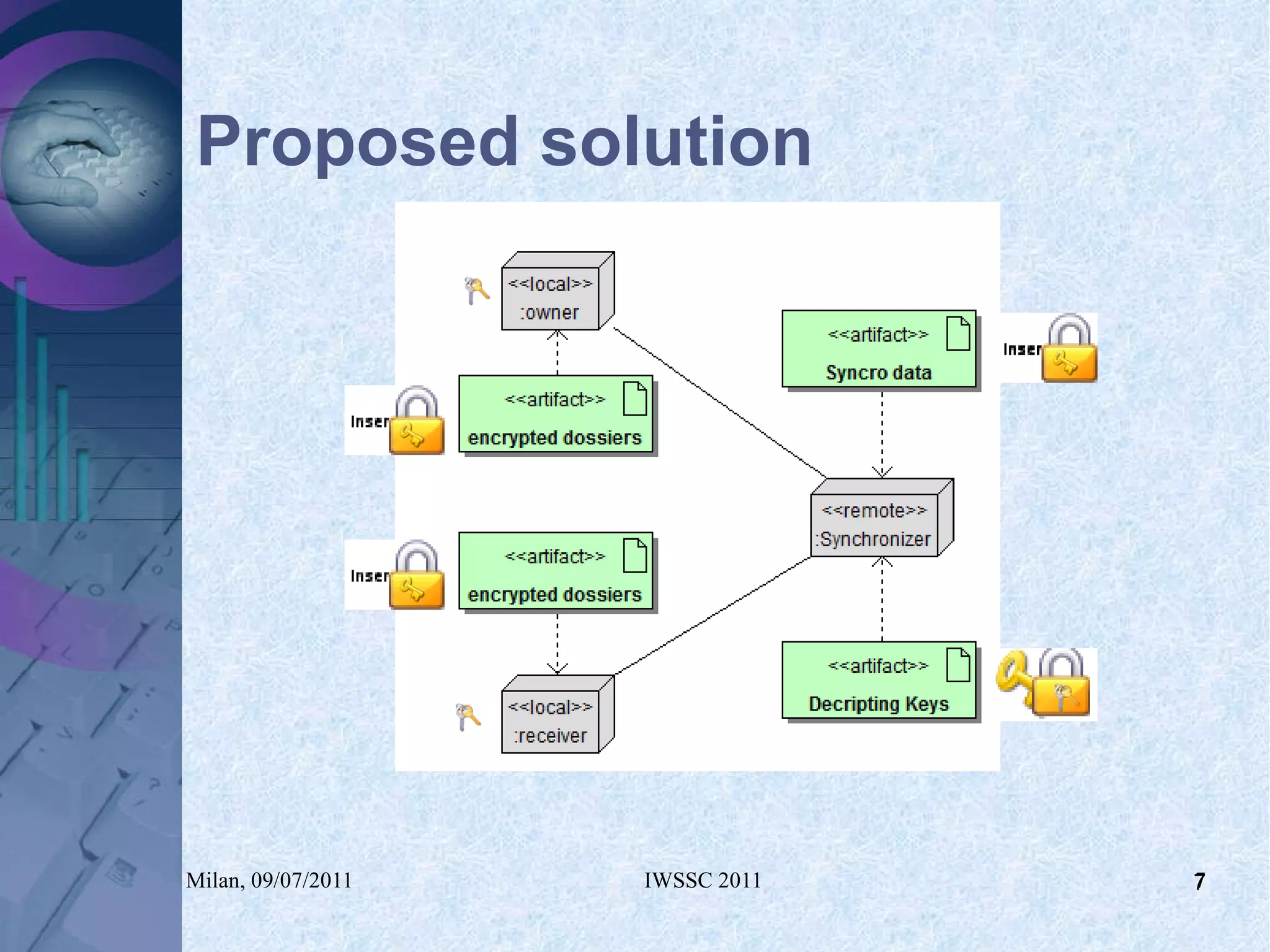
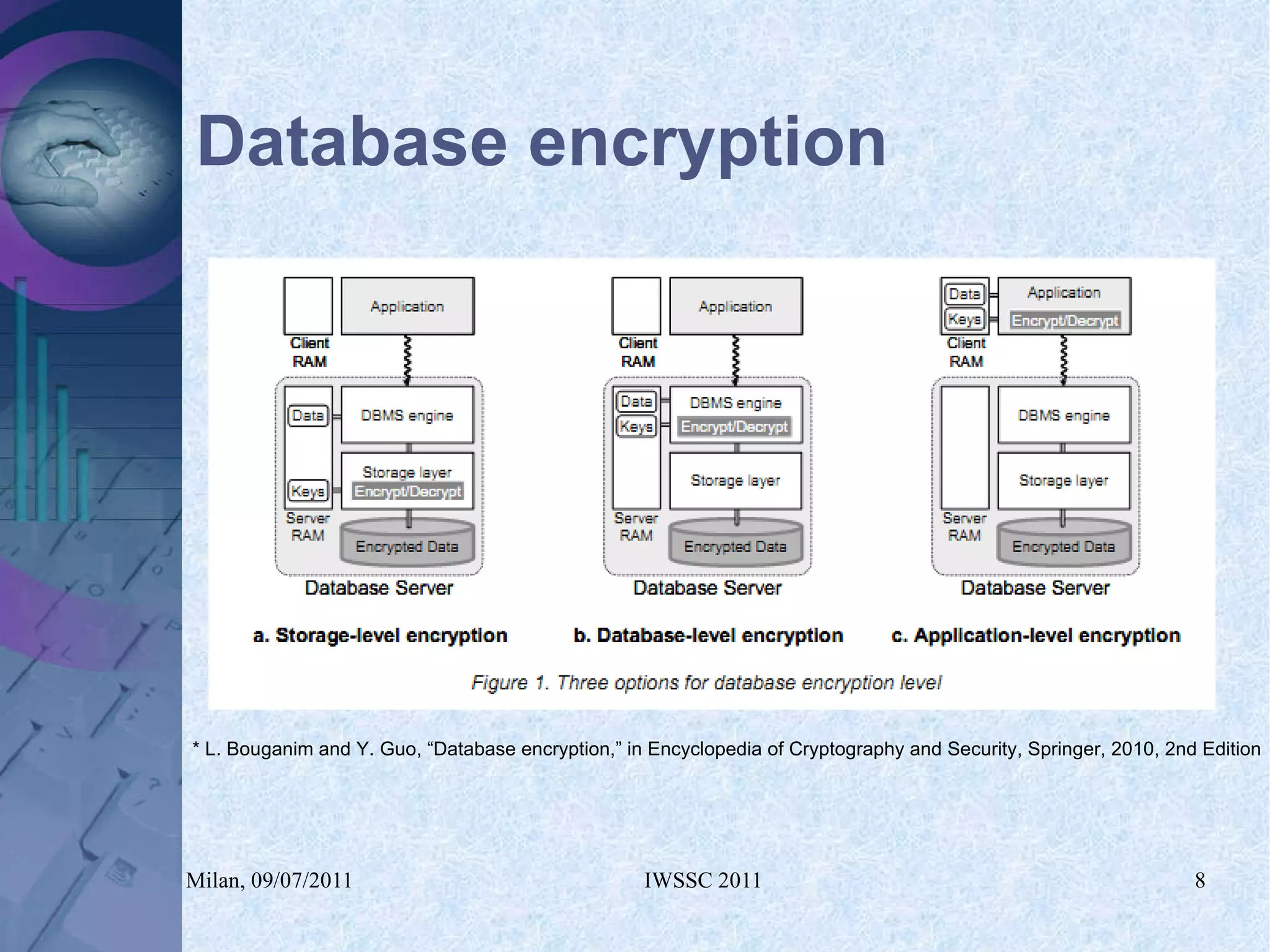
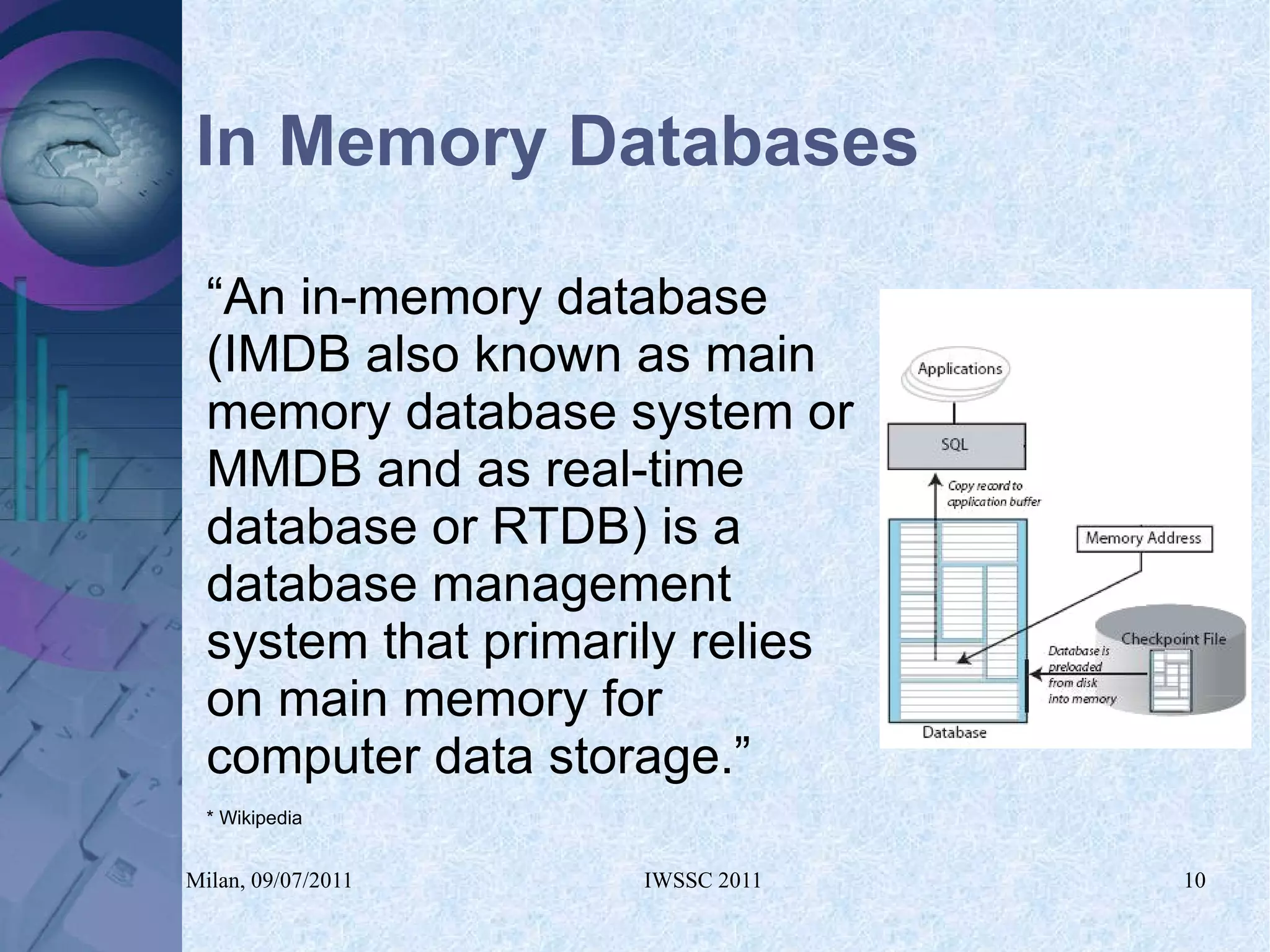
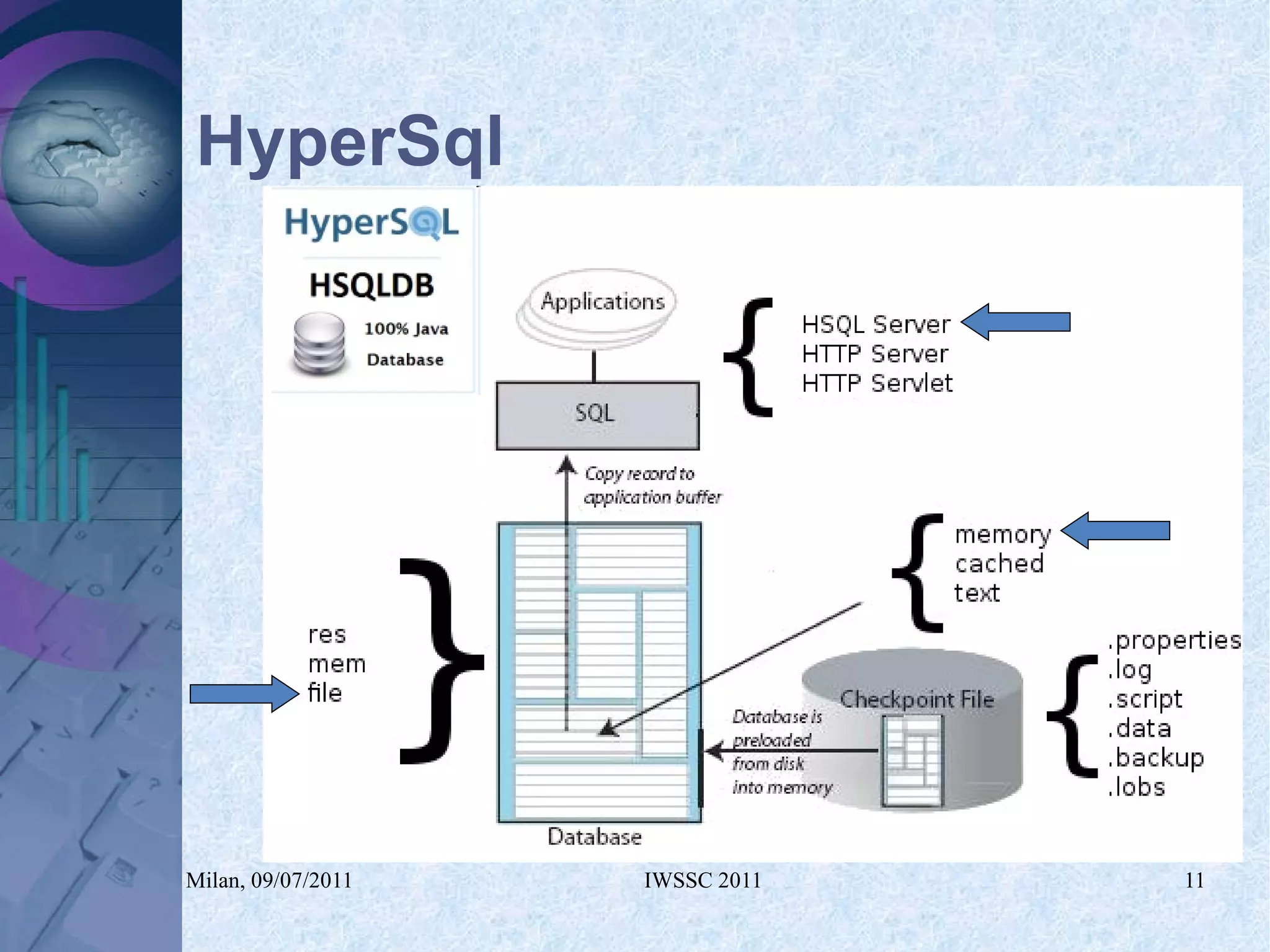
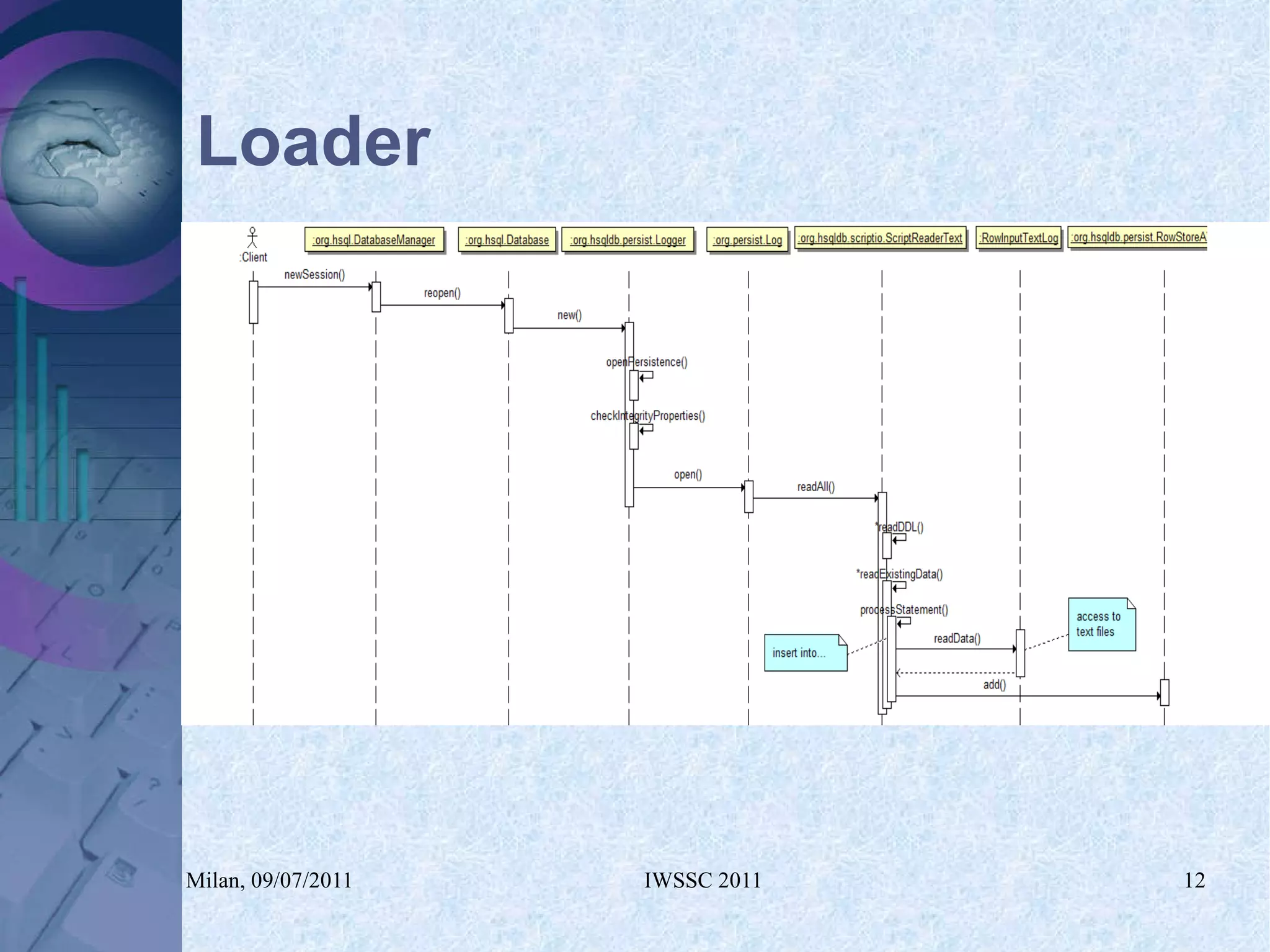
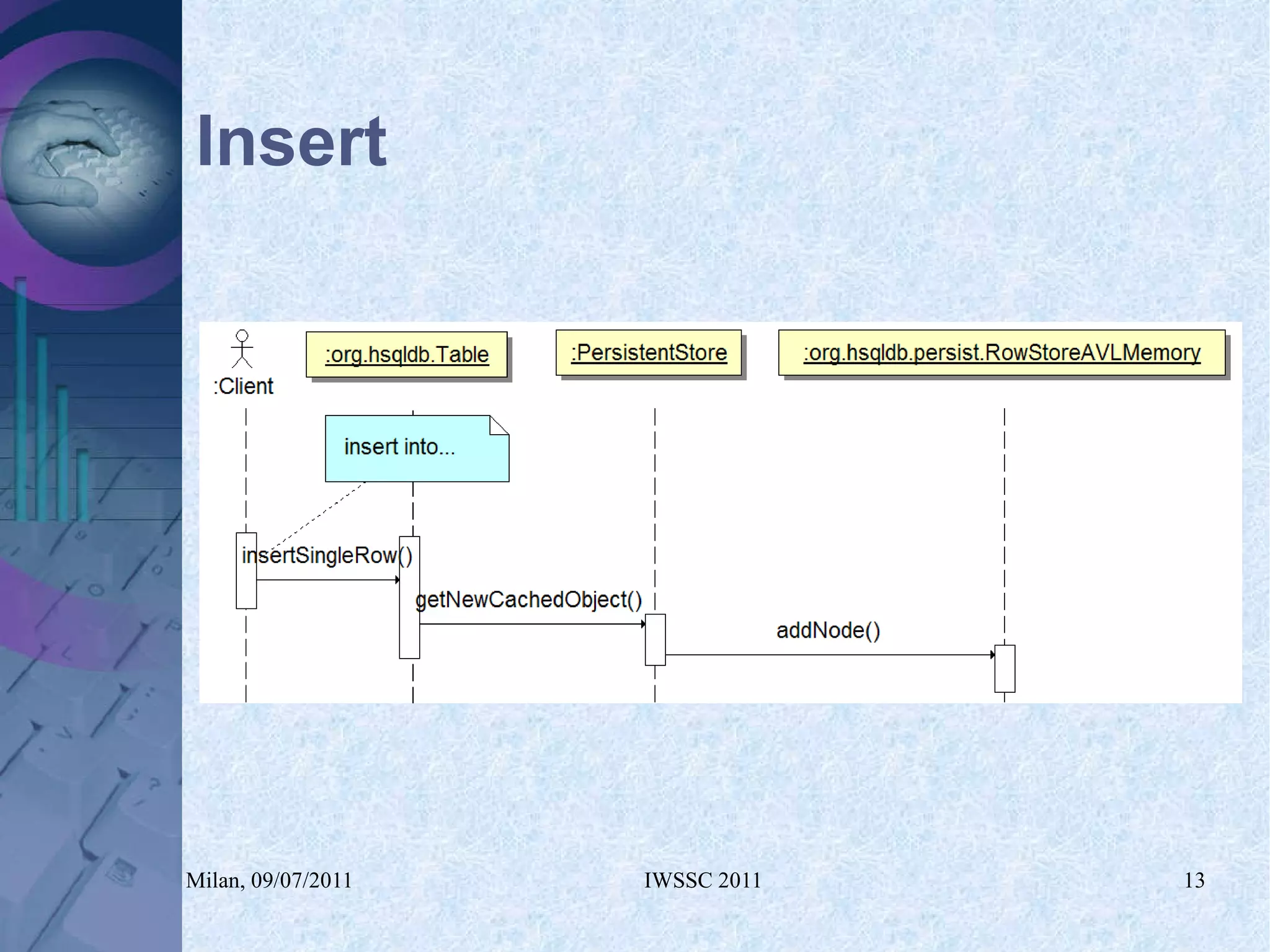
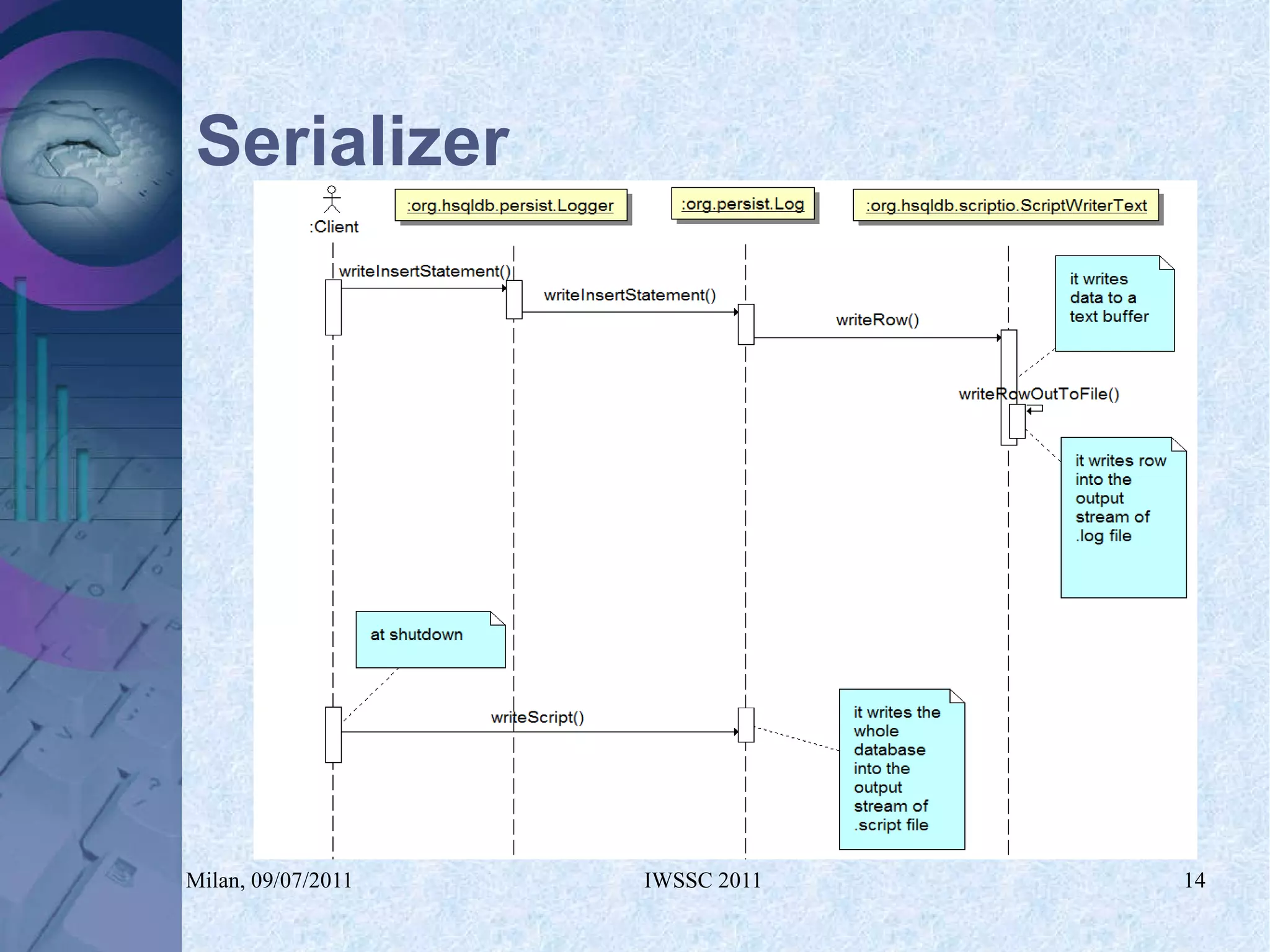
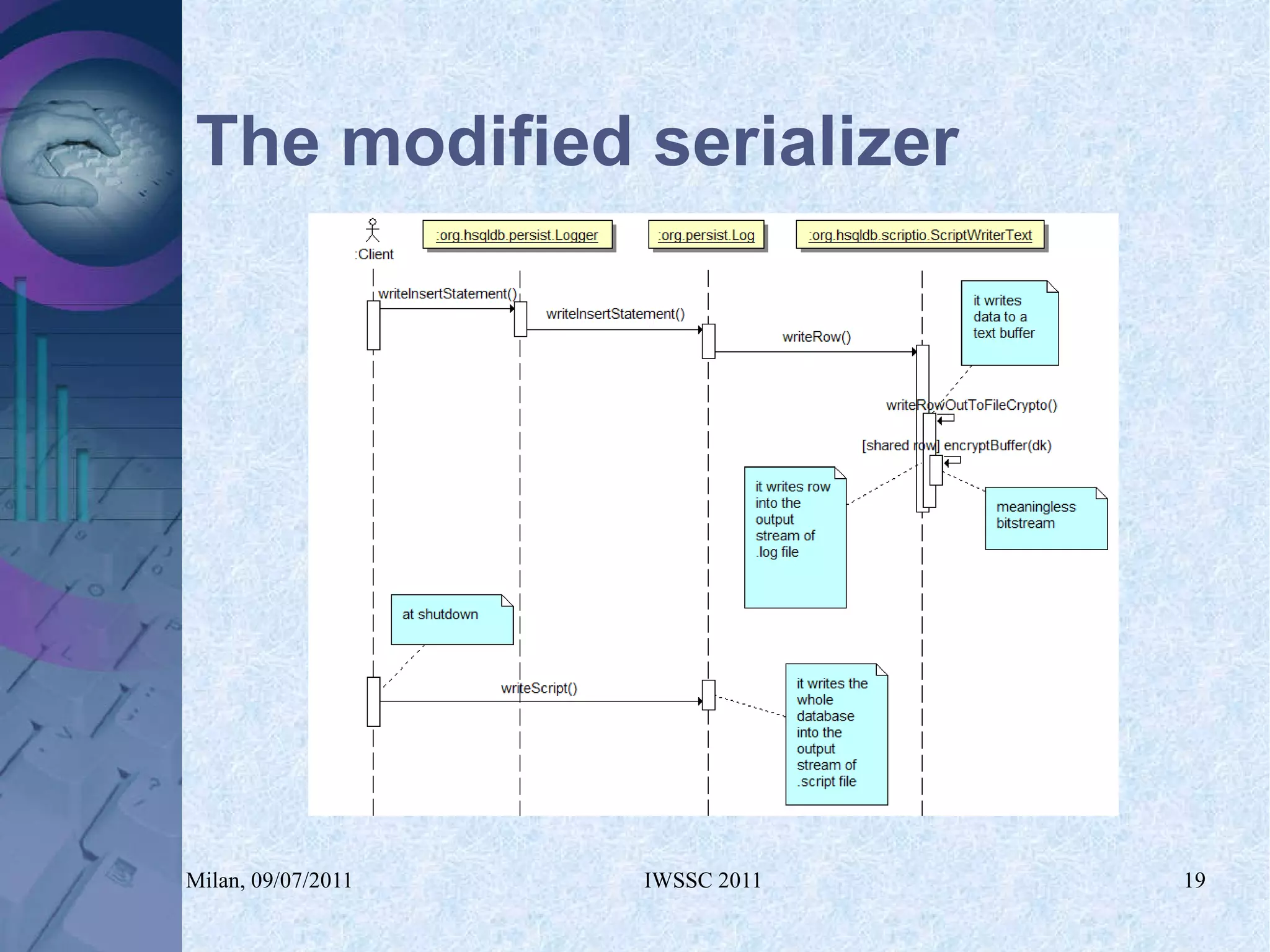
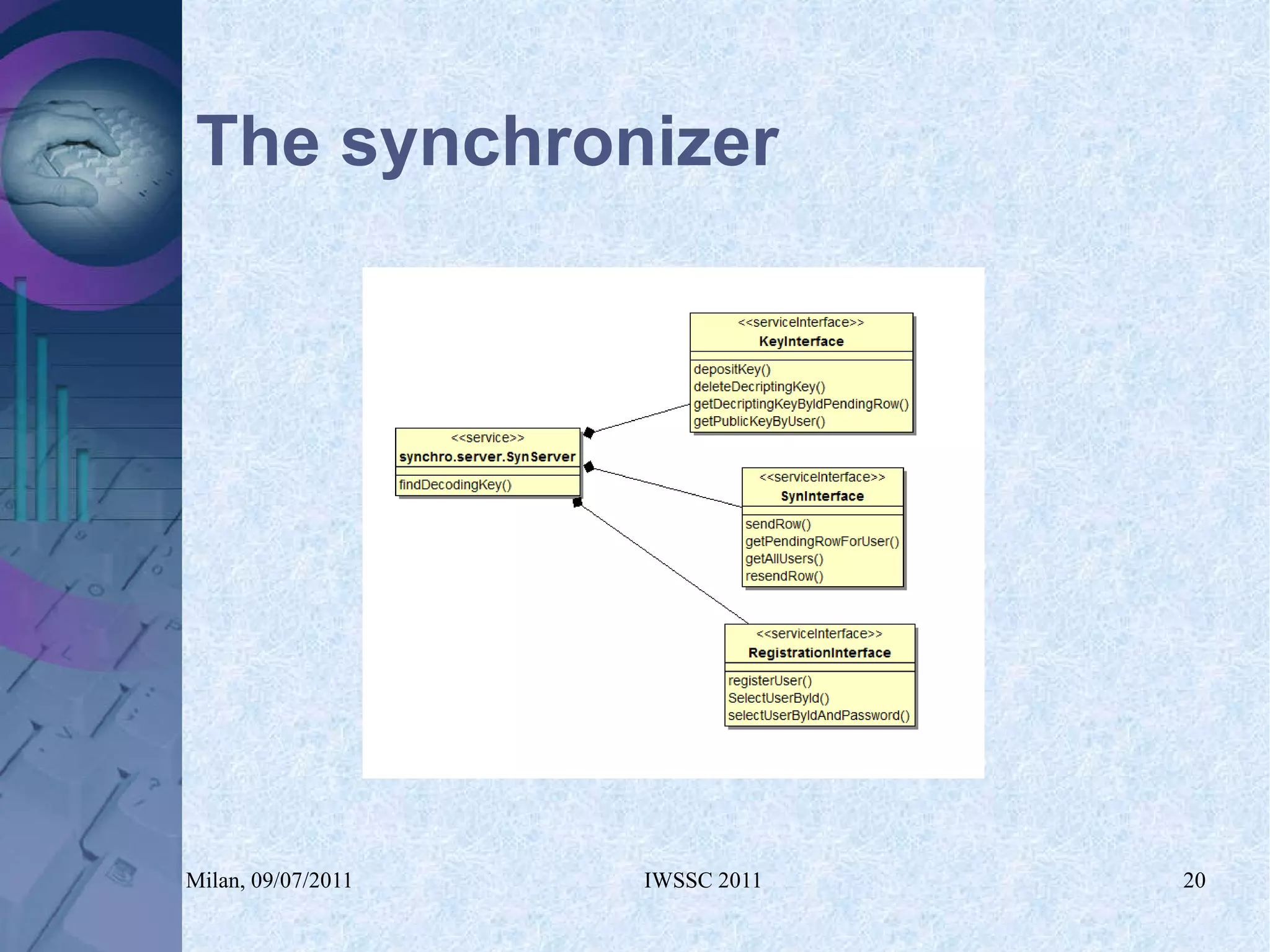
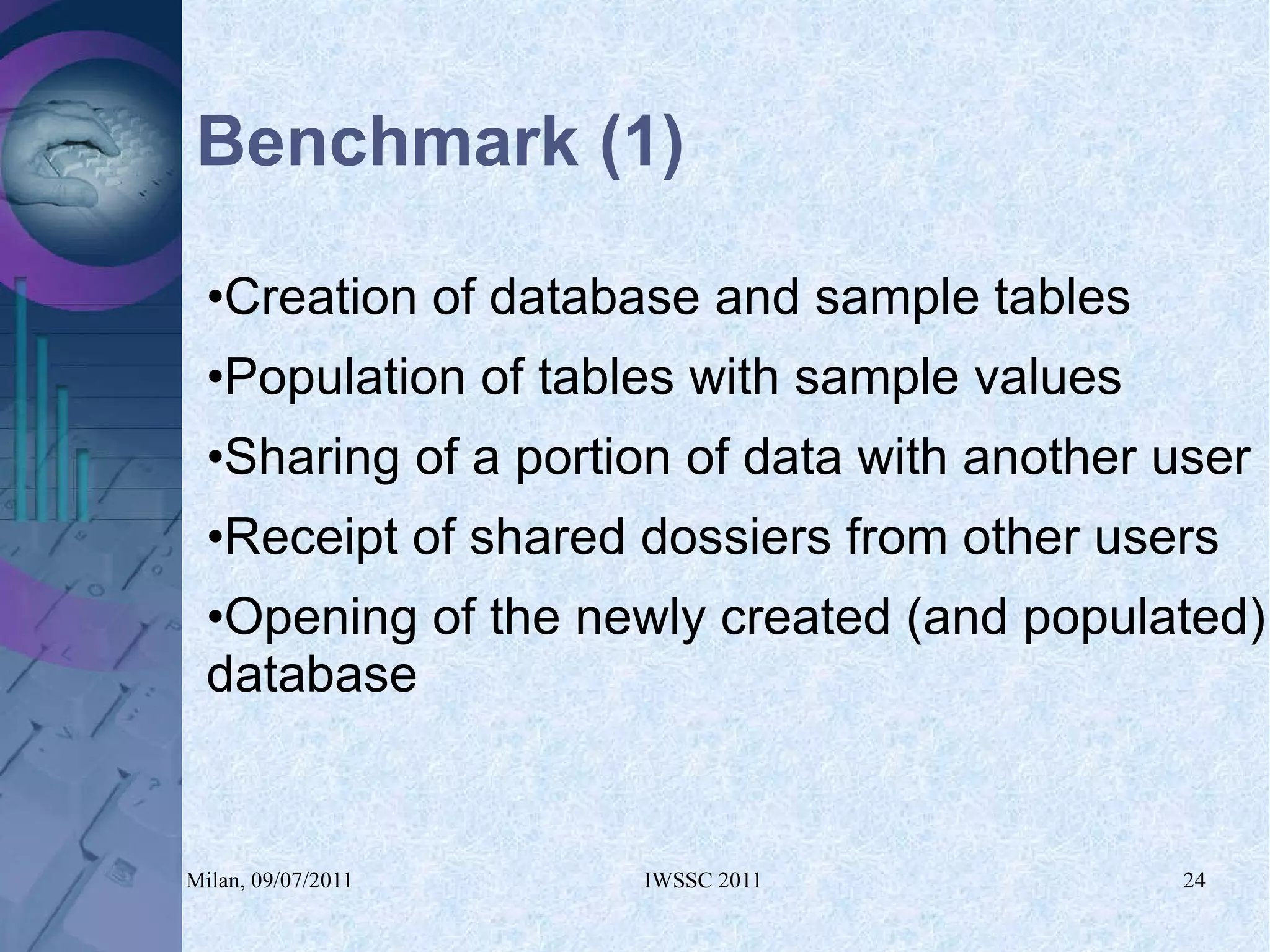
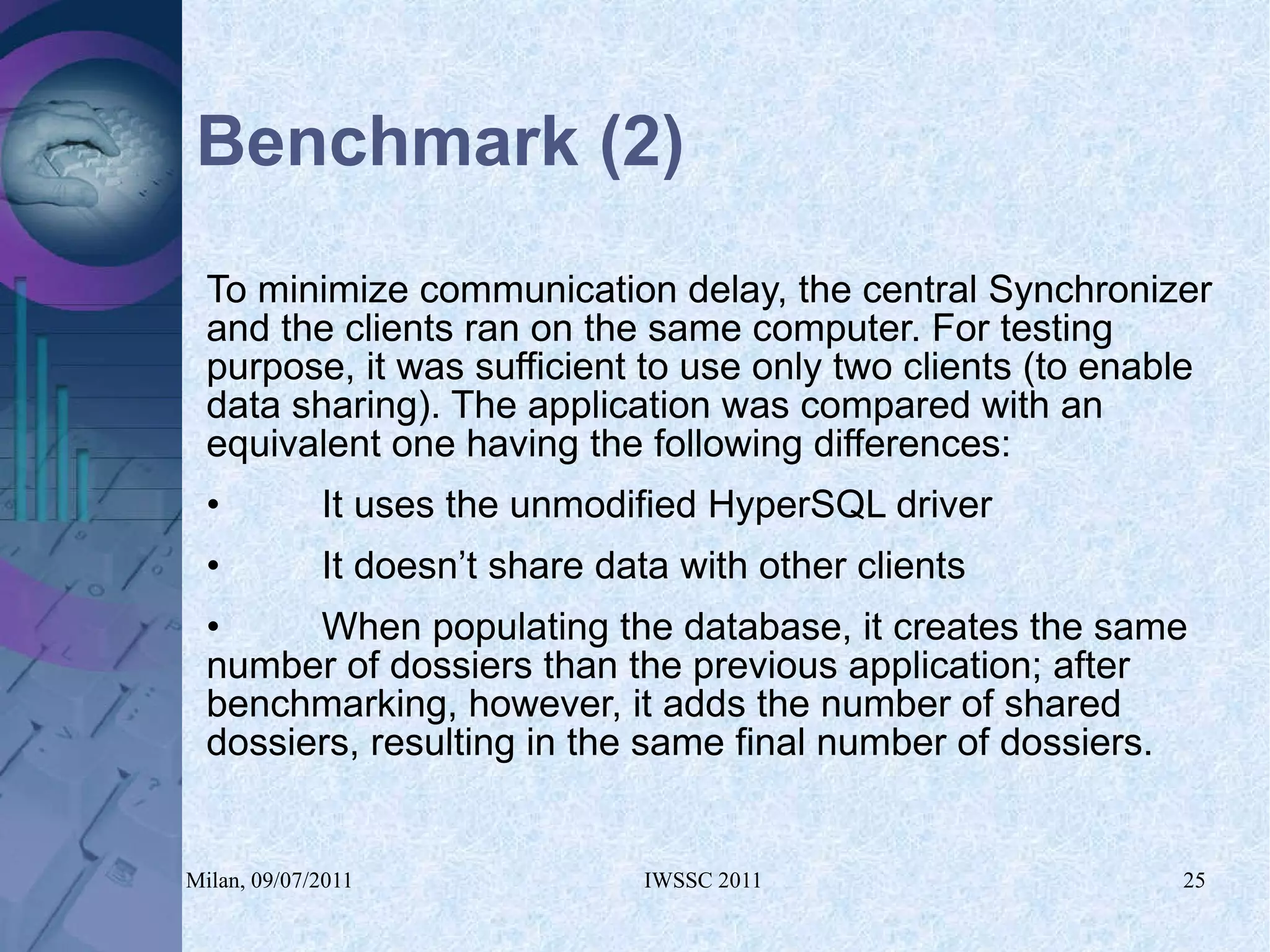
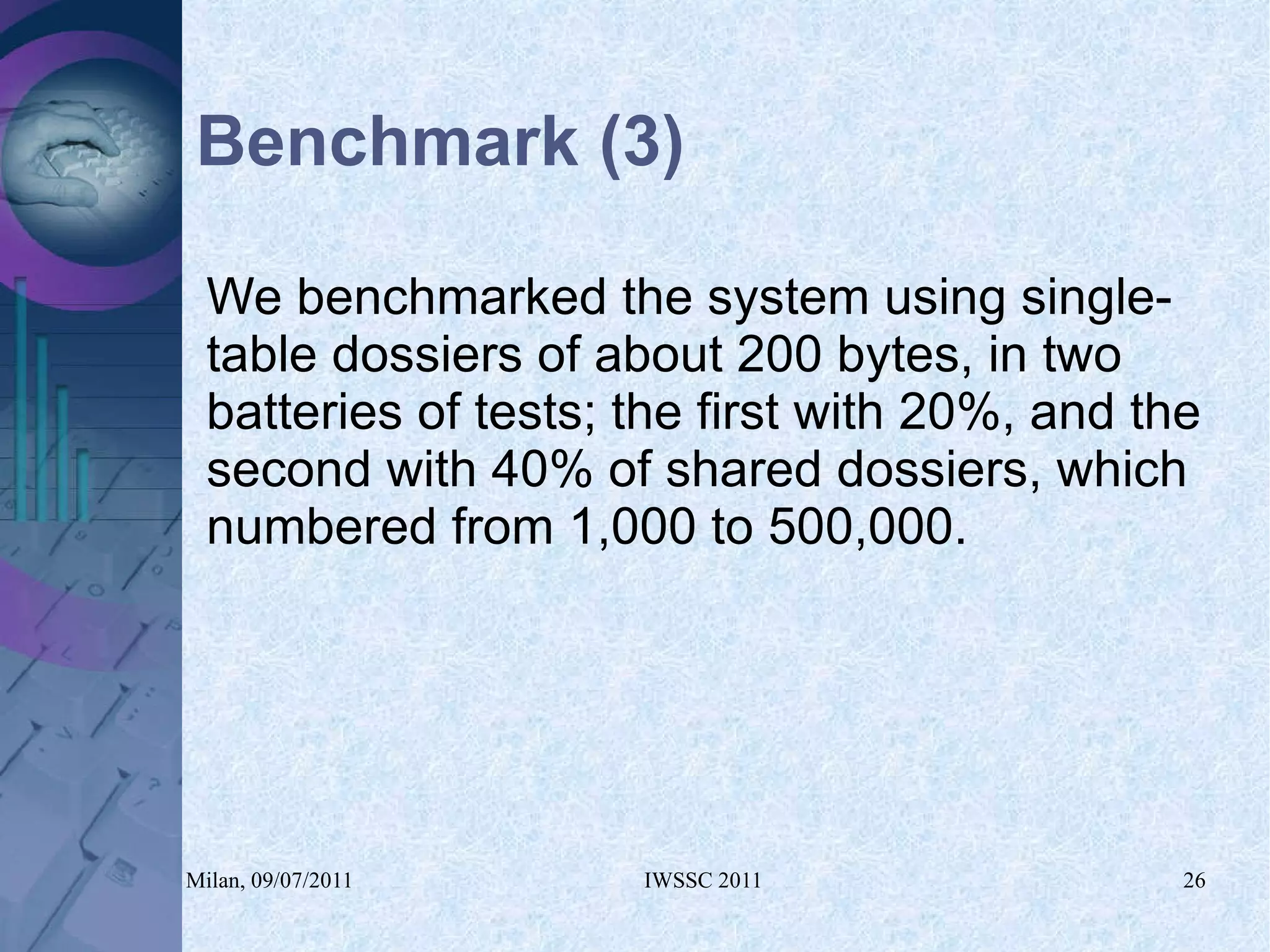
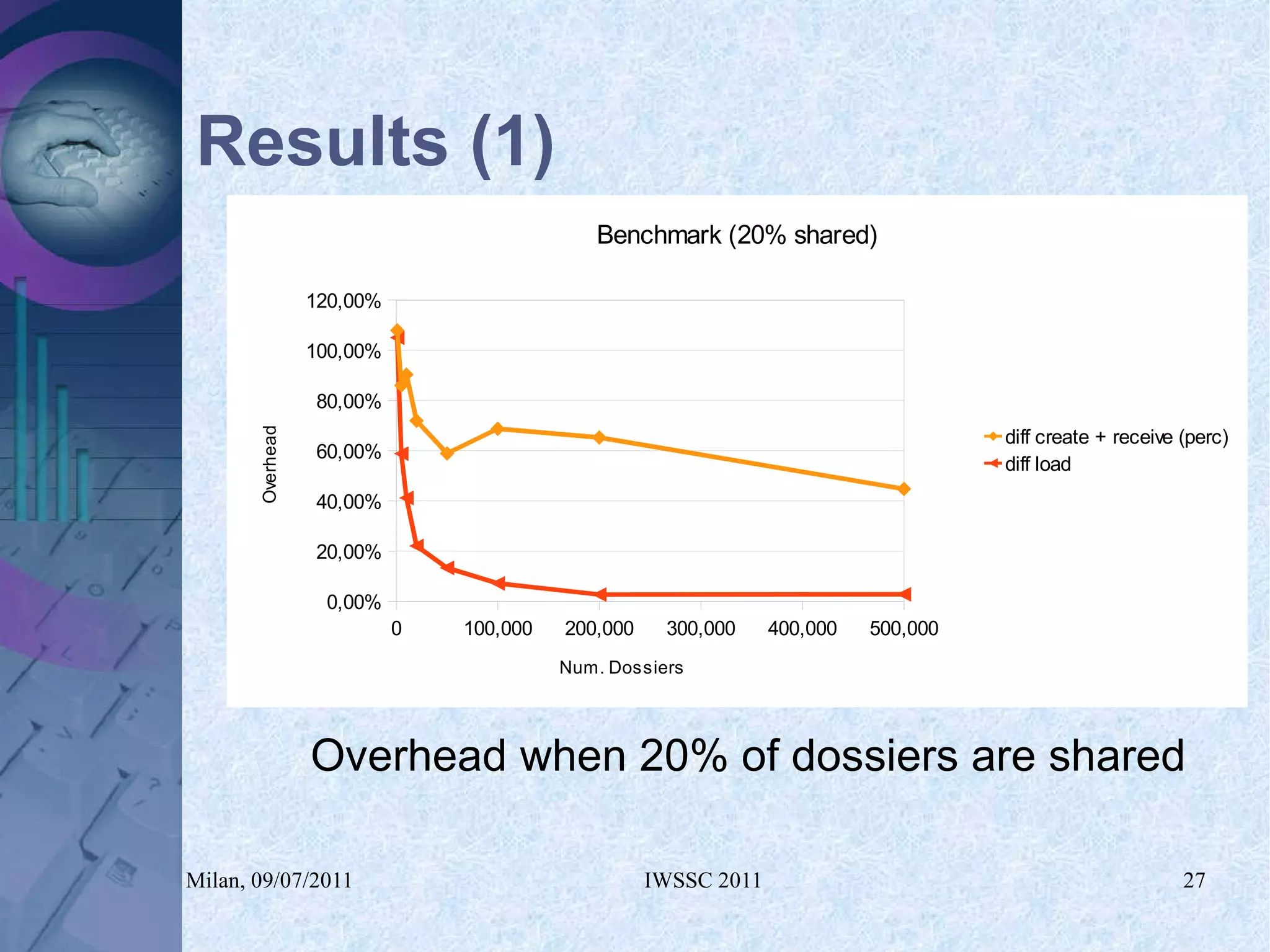
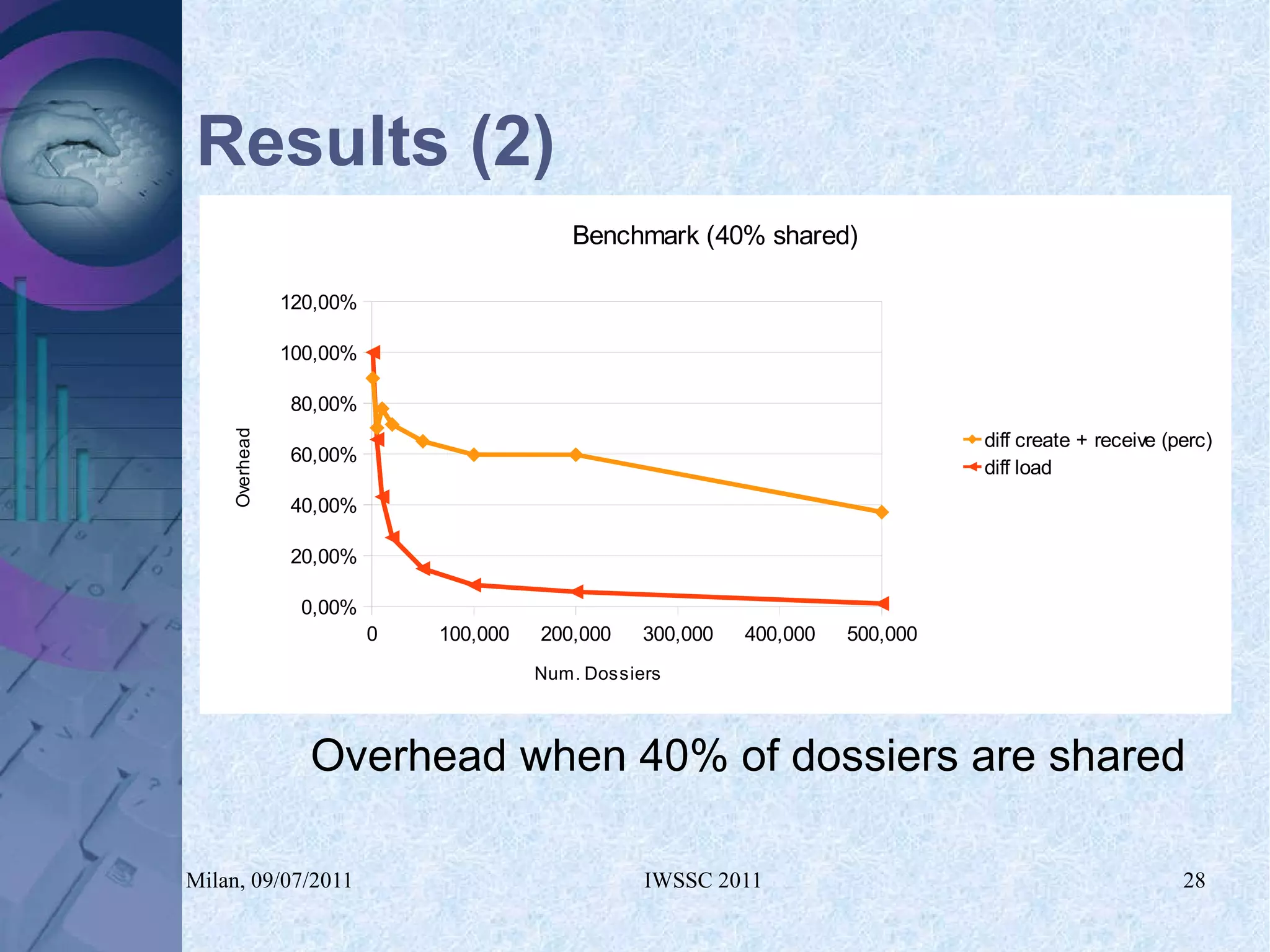
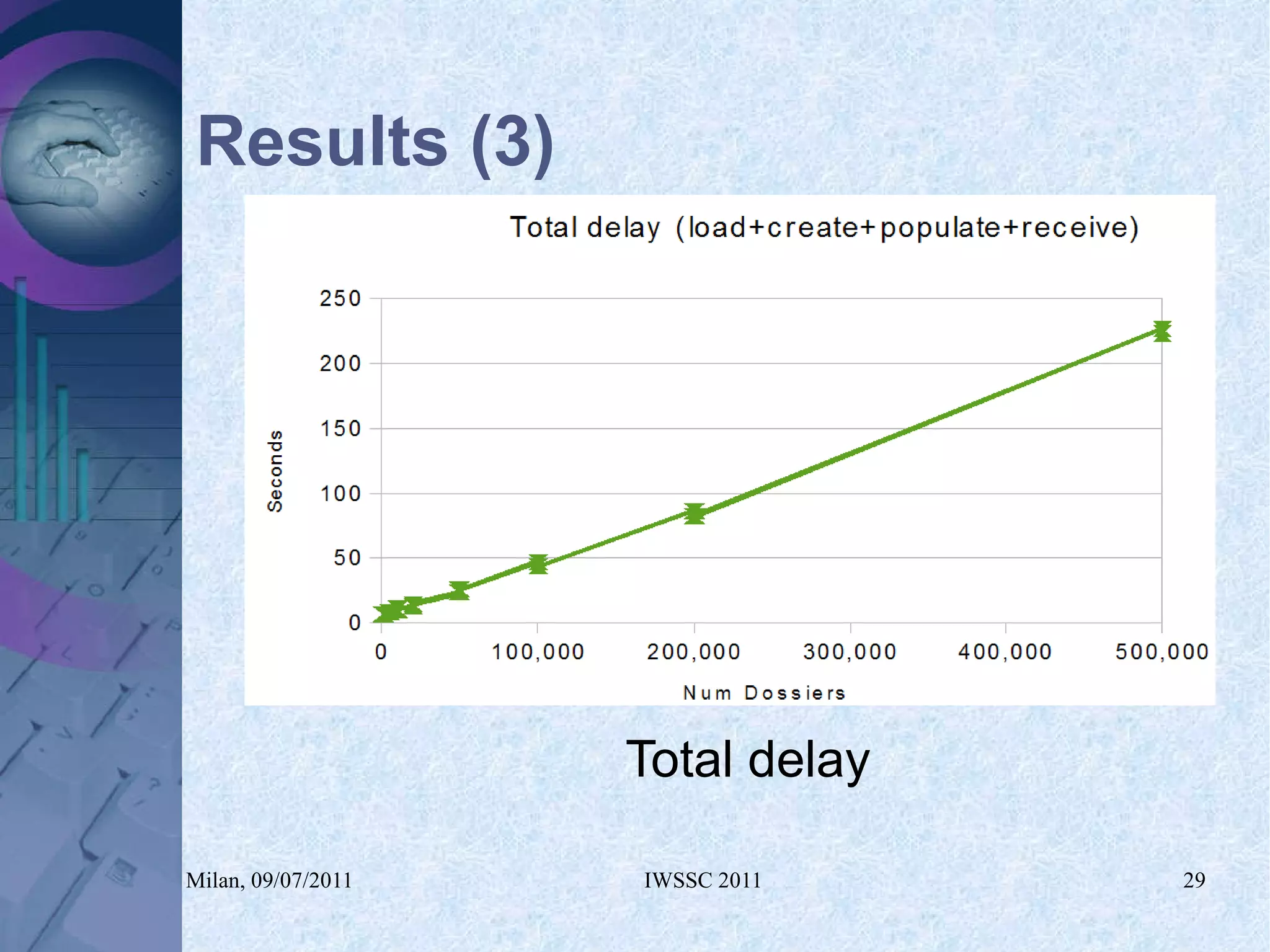
The document proposes using in-memory encrypted databases on the cloud to address privacy issues. It presents an agent-based approach where each user has a local database encrypted with a key only available to a trusted synchronizer. This allows data to be shared securely while minimizing encryption/decryption overhead. A prototype was implemented using HyperSQL. Benchmark results showed the overhead of the proposed solution is low, especially for read operations, making it suitable for privacy-focused applications like professional networks that require frequent data sharing.
![Using In-Memory Encrypted Databases on the Cloud Francesco (and Davide) Pagano [email_address] Department of Information Technology Università degli Studi di Milano - Italy](https://image.slidesharecdn.com/presentazionepagano1-110906092153-phpapp02/75/Using-In-Memory-Encrypted-Databases-on-the-Cloud-1-2048.jpg)