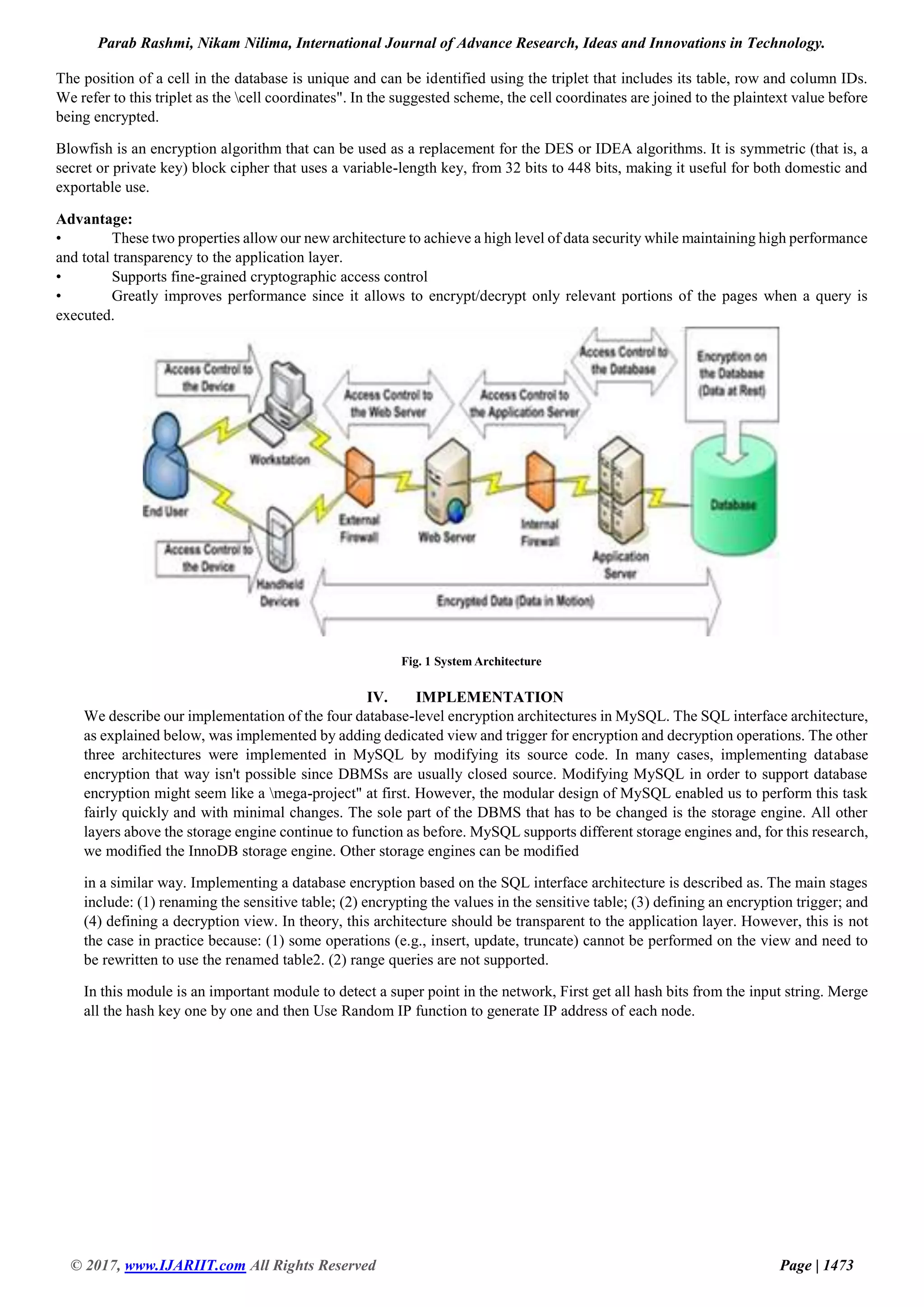
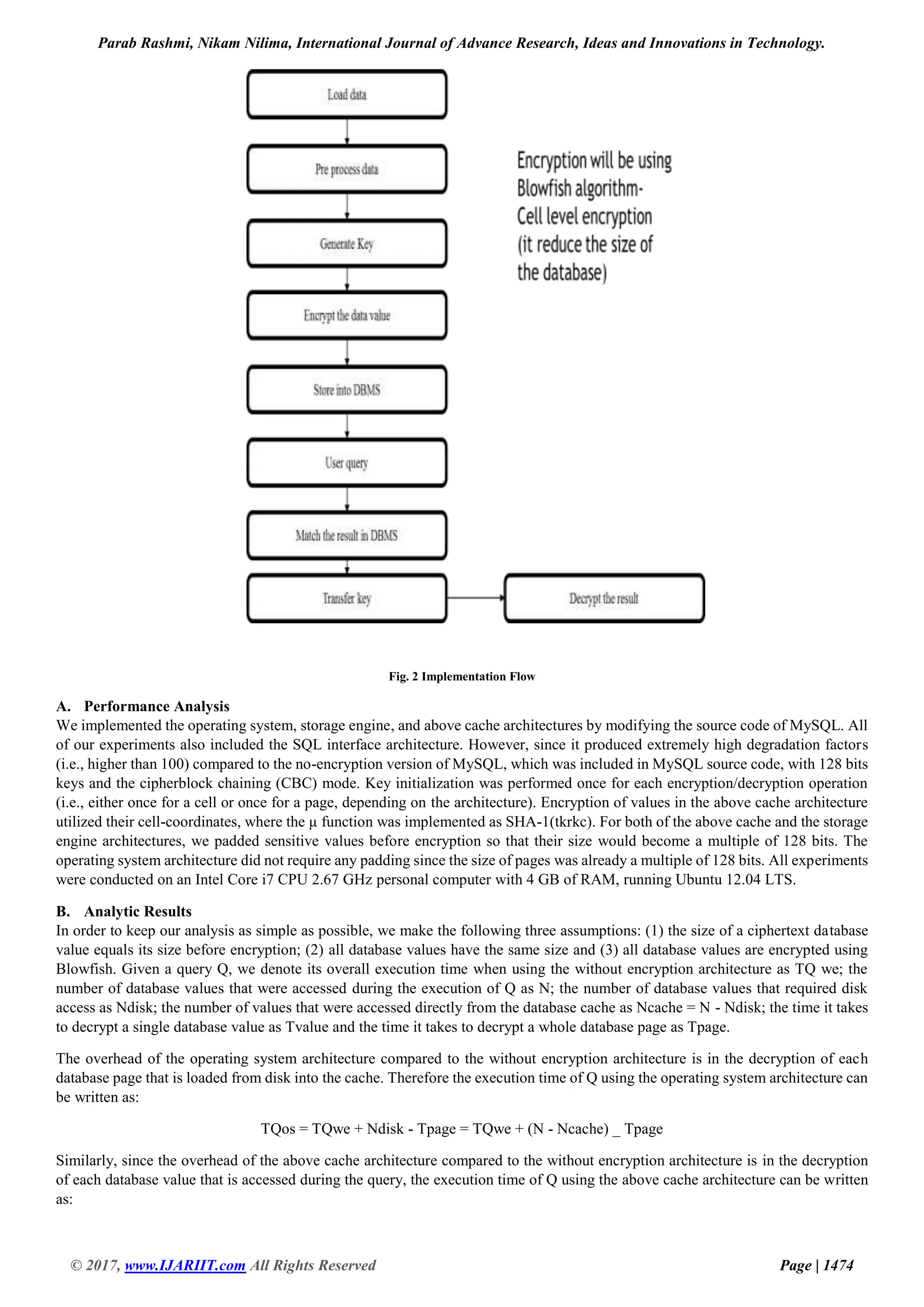
The document discusses the increasing reliance on corporate data for critical decisions and the need for robust database security to protect against data loss or corruption. It analyzes and compares five traditional architectures for database encryption, revealing their performance weaknesses and security risks, before proposing a novel architecture that integrates encryption within the database management software, ensuring high security with minimal performance impact. The paper concludes by emphasizing the proposed architecture's ability to achieve strong data security while remaining transparent to application layers.