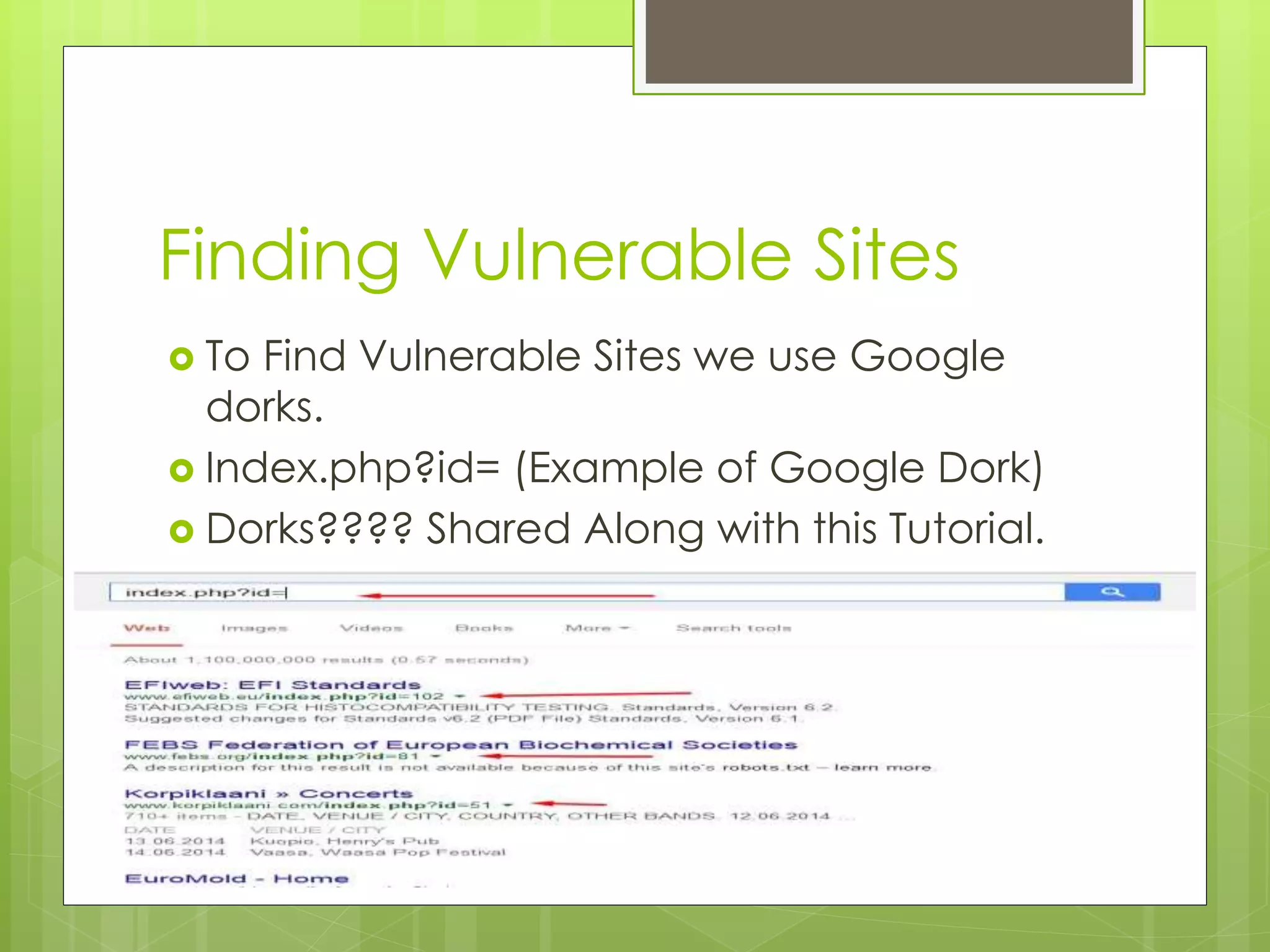
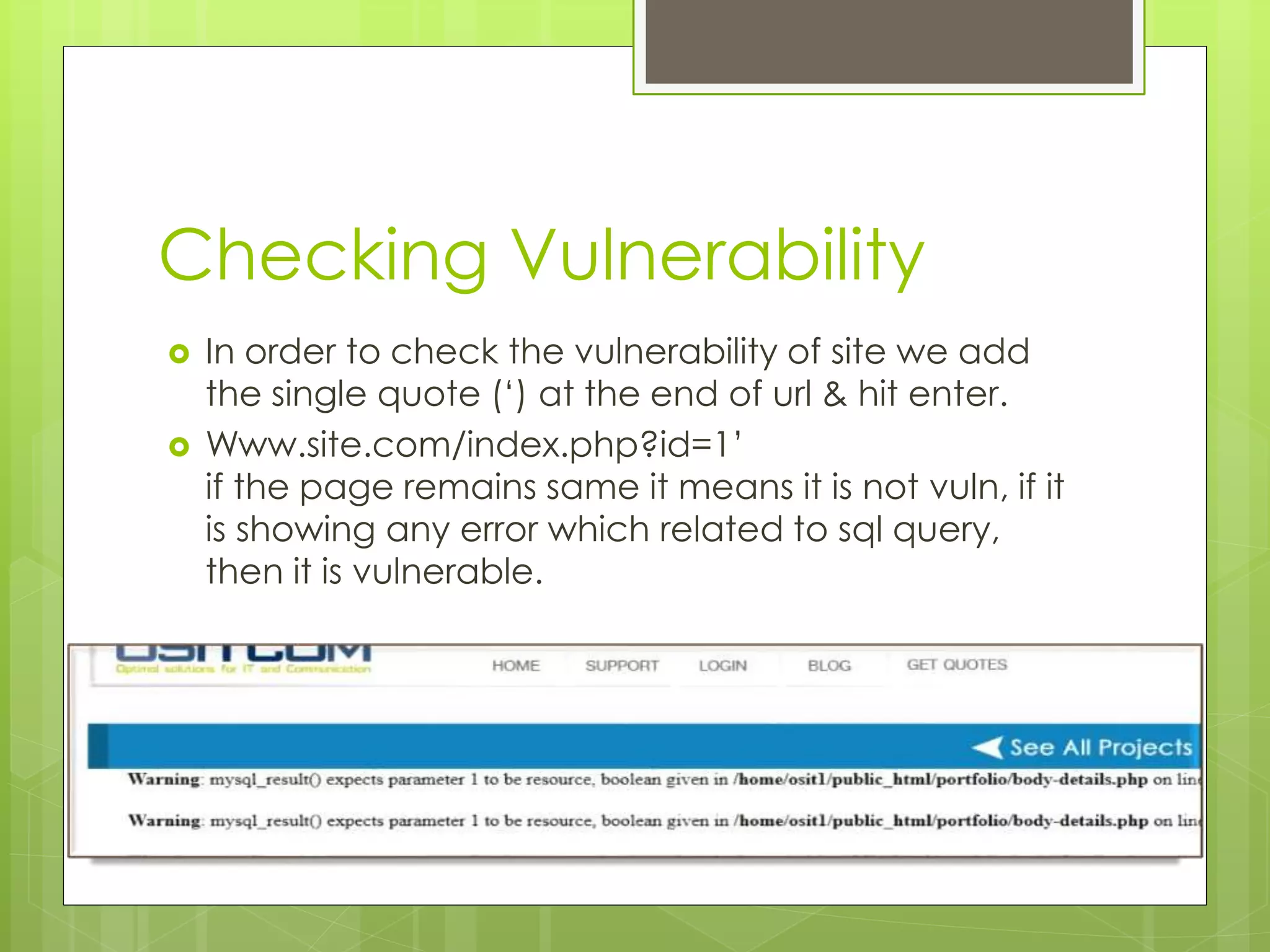
The document outlines a tutorial on manual SQL injection techniques, including using Google dorks to find vulnerable sites and checking their vulnerability with SQL queries. It explains how to identify the number of columns, find vulnerable columns, and extract database information such as usernames and passwords. Additionally, it provides instructions for defacing websites and mentions resources for decrypting hashed passwords.