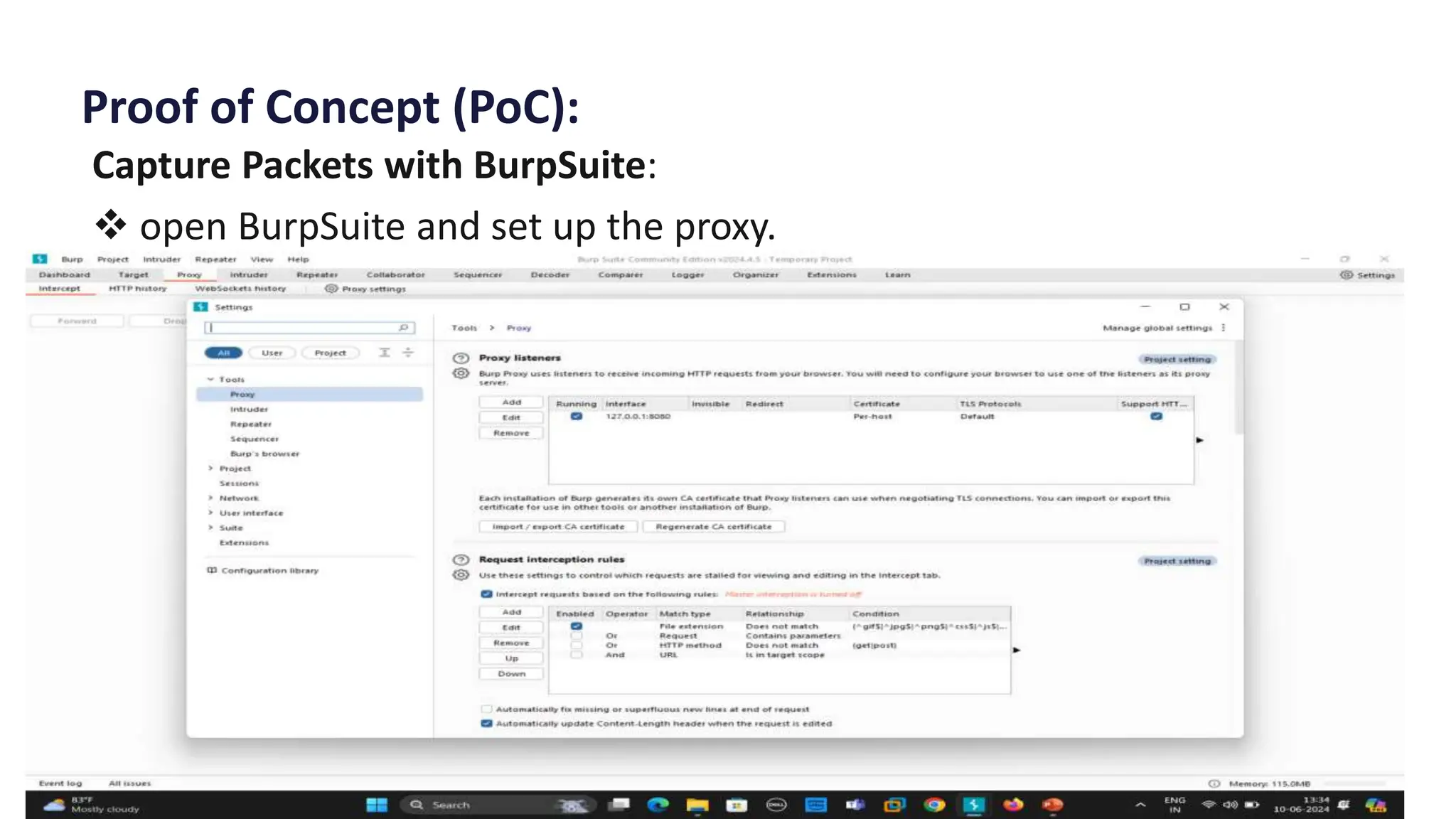
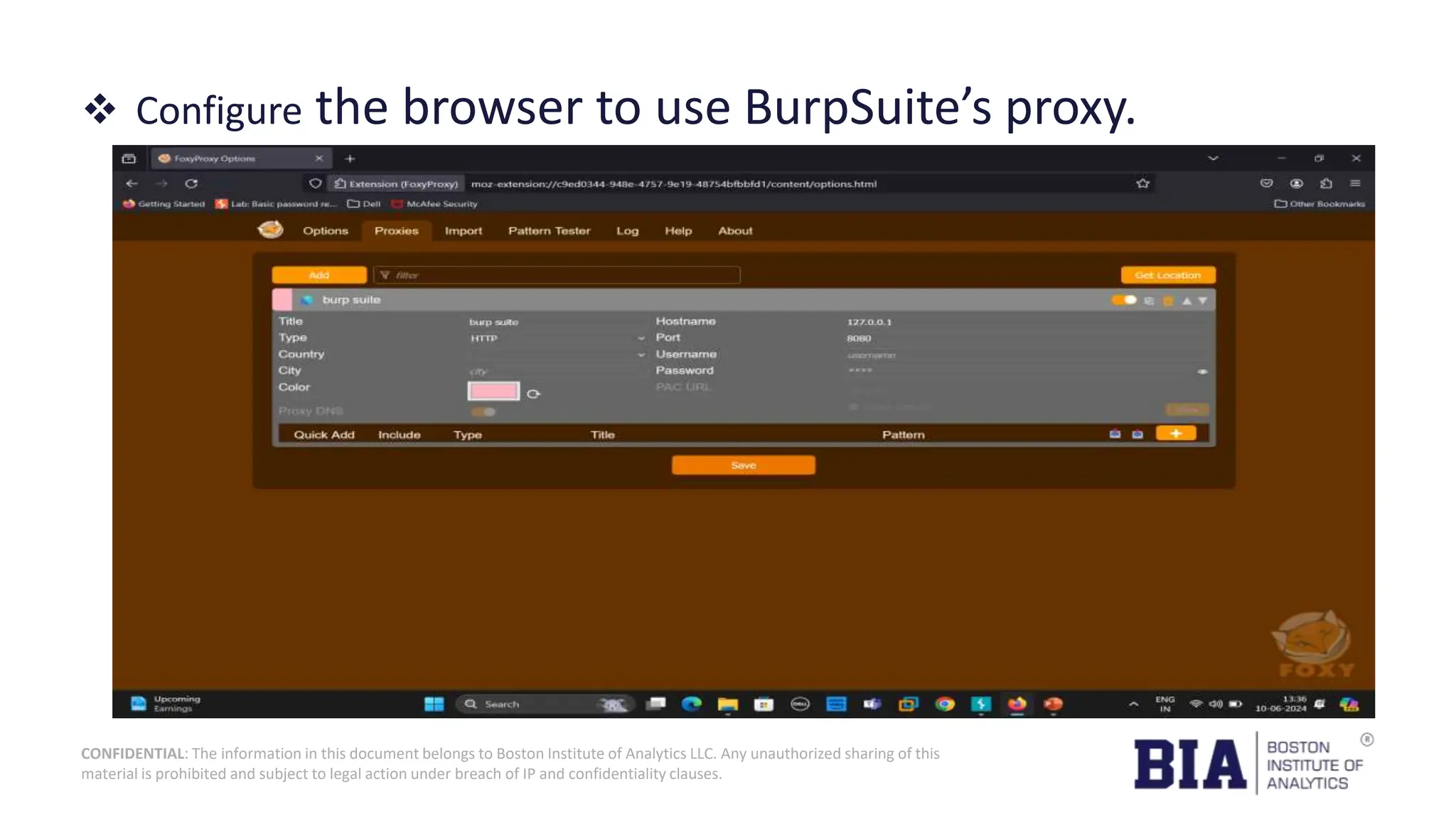
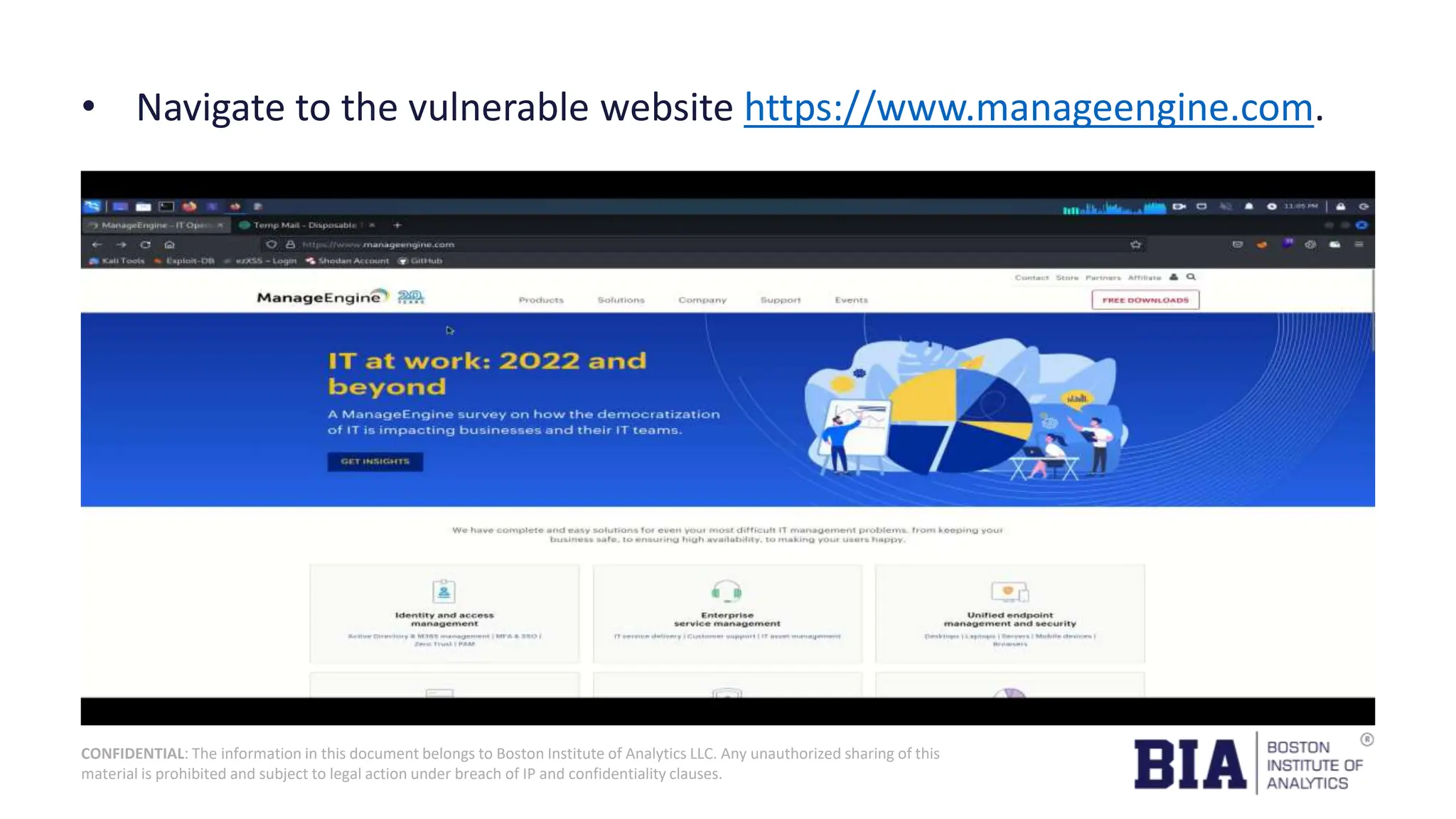
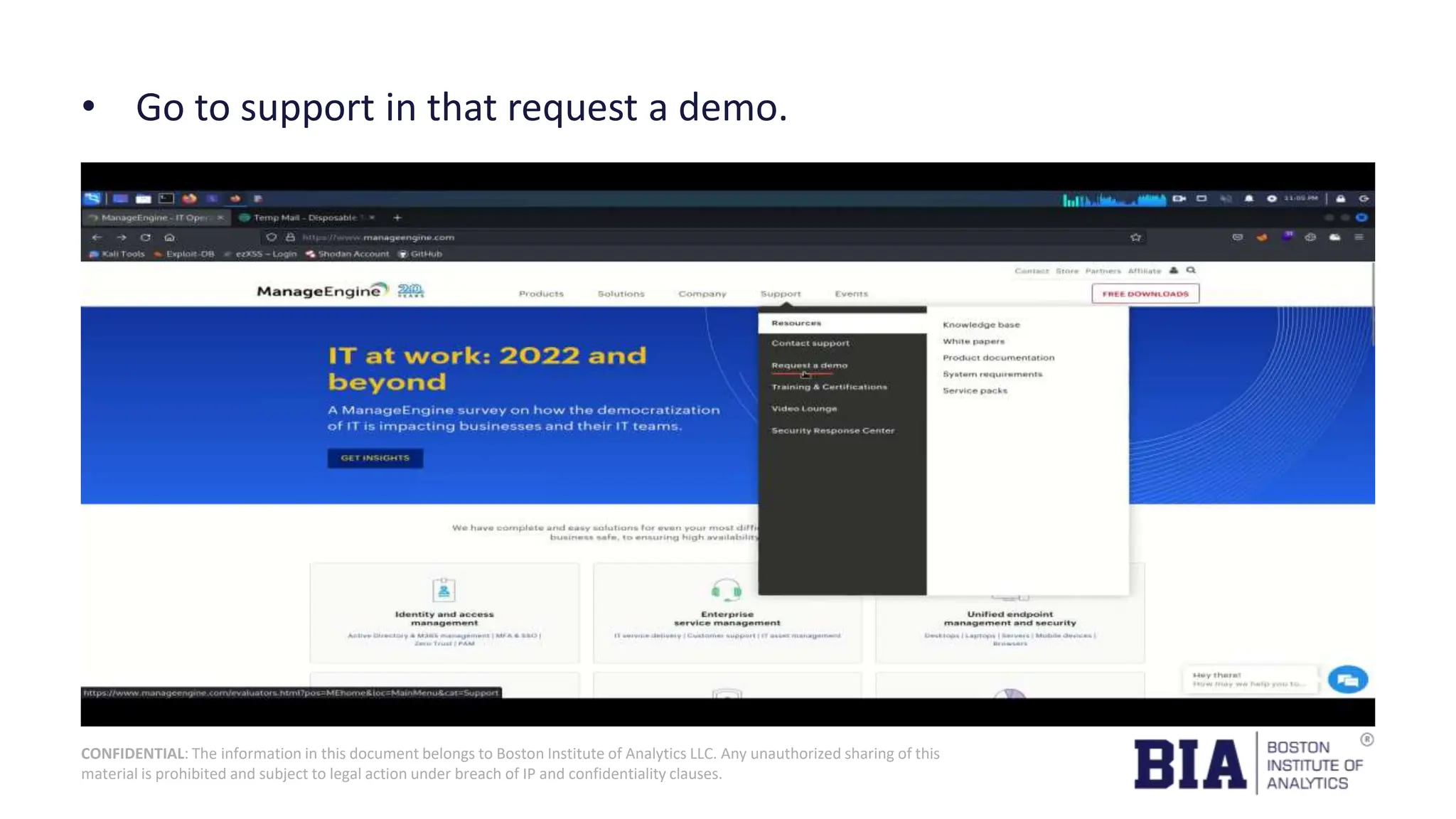
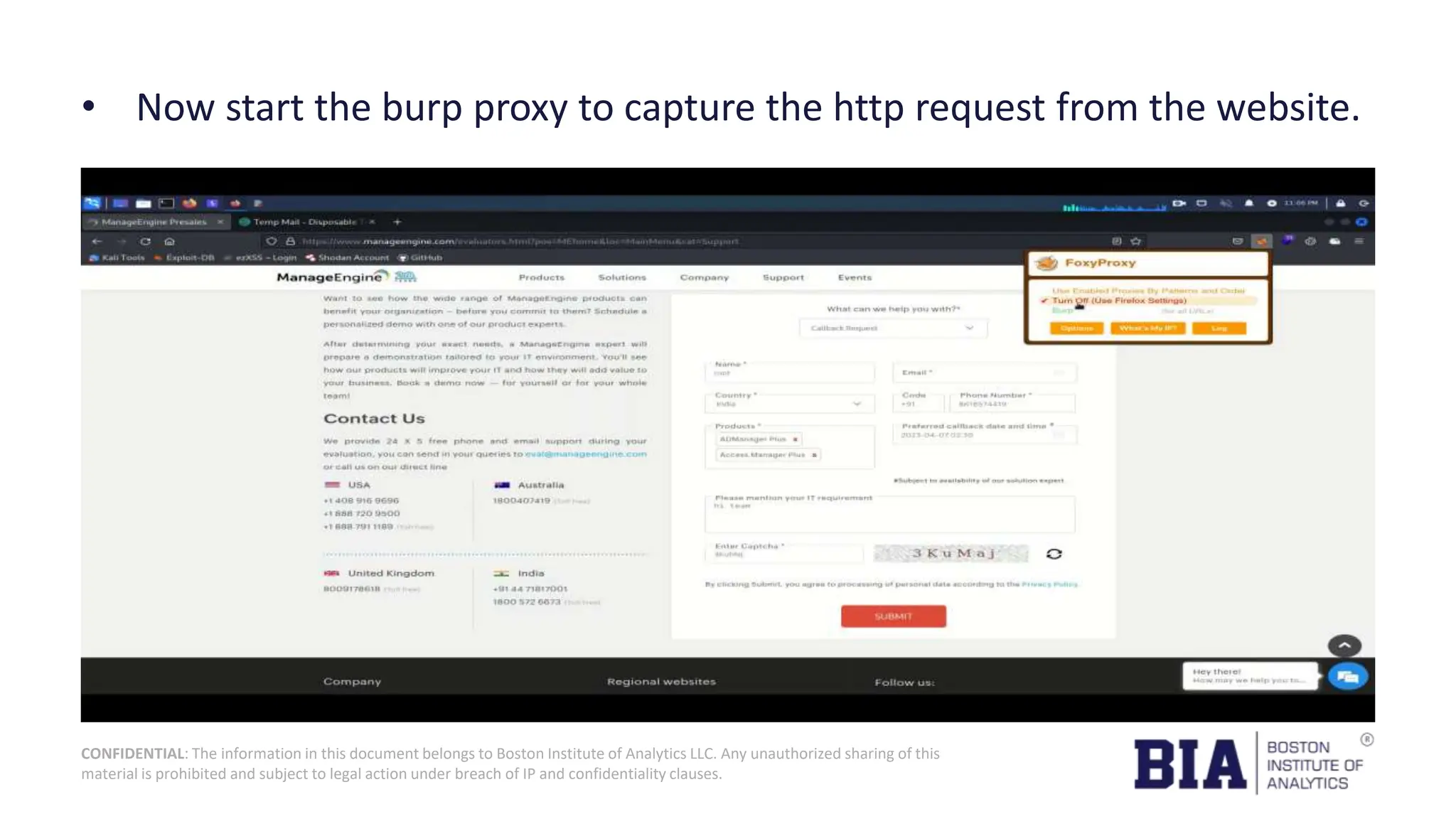
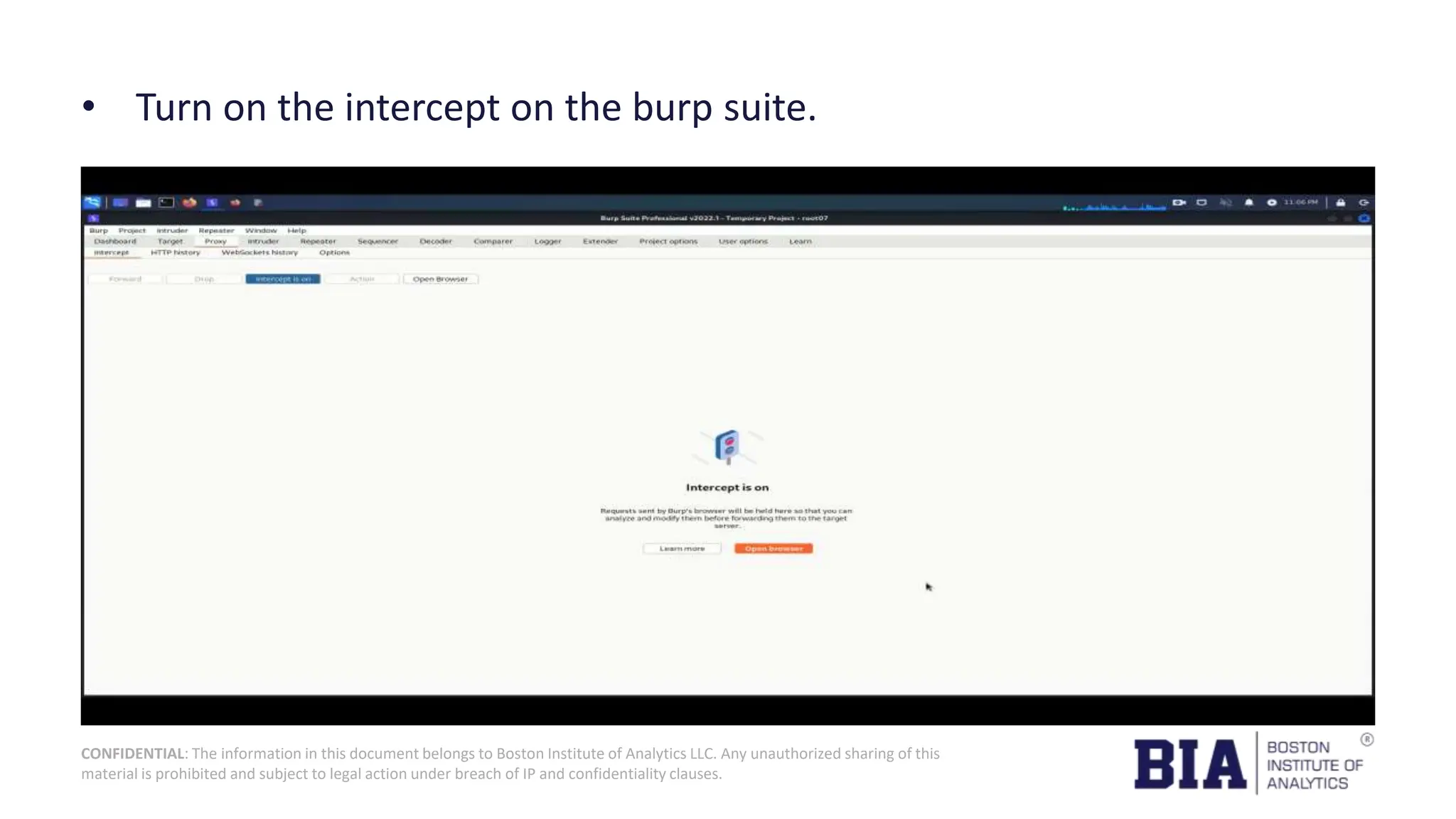
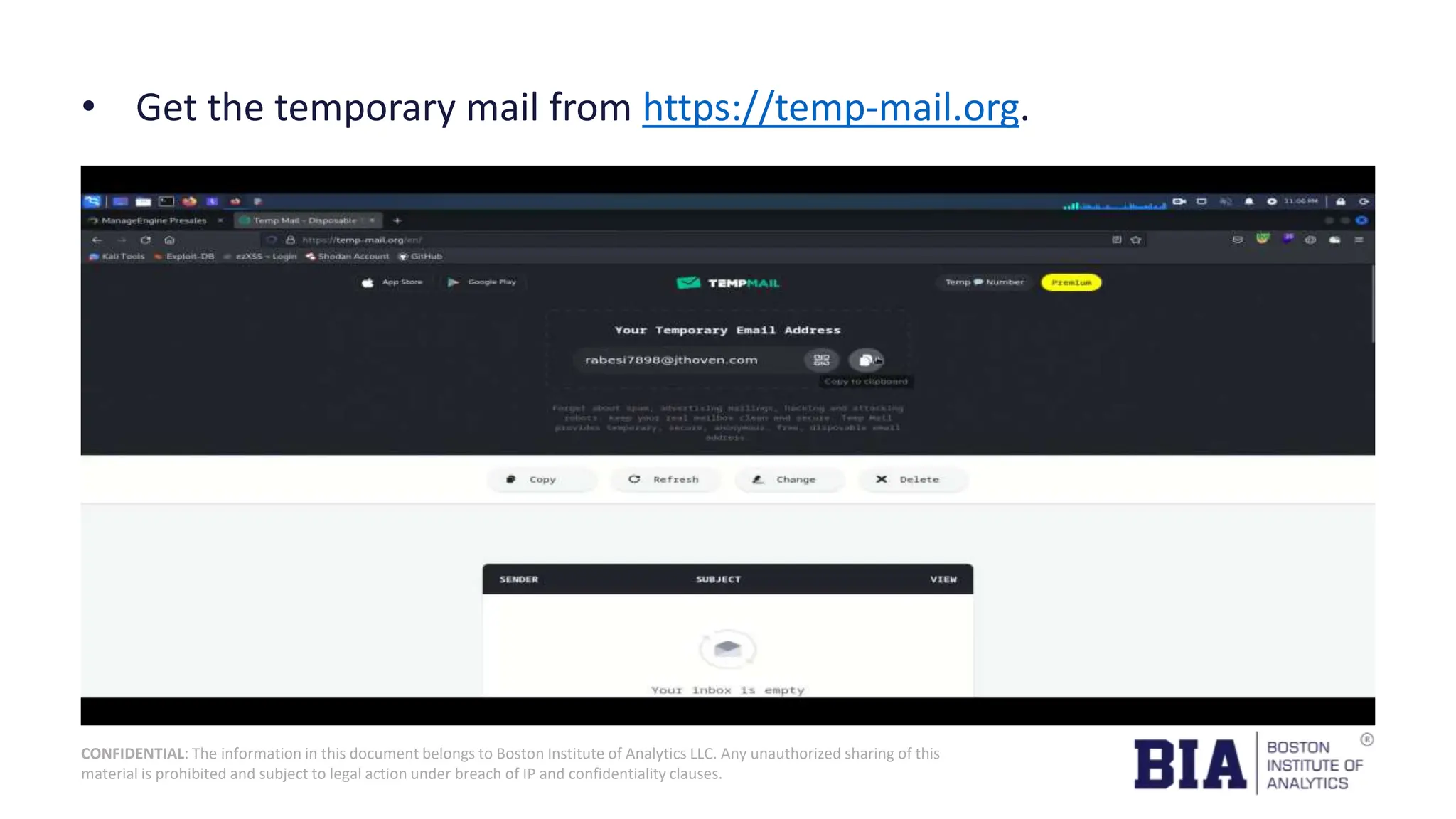
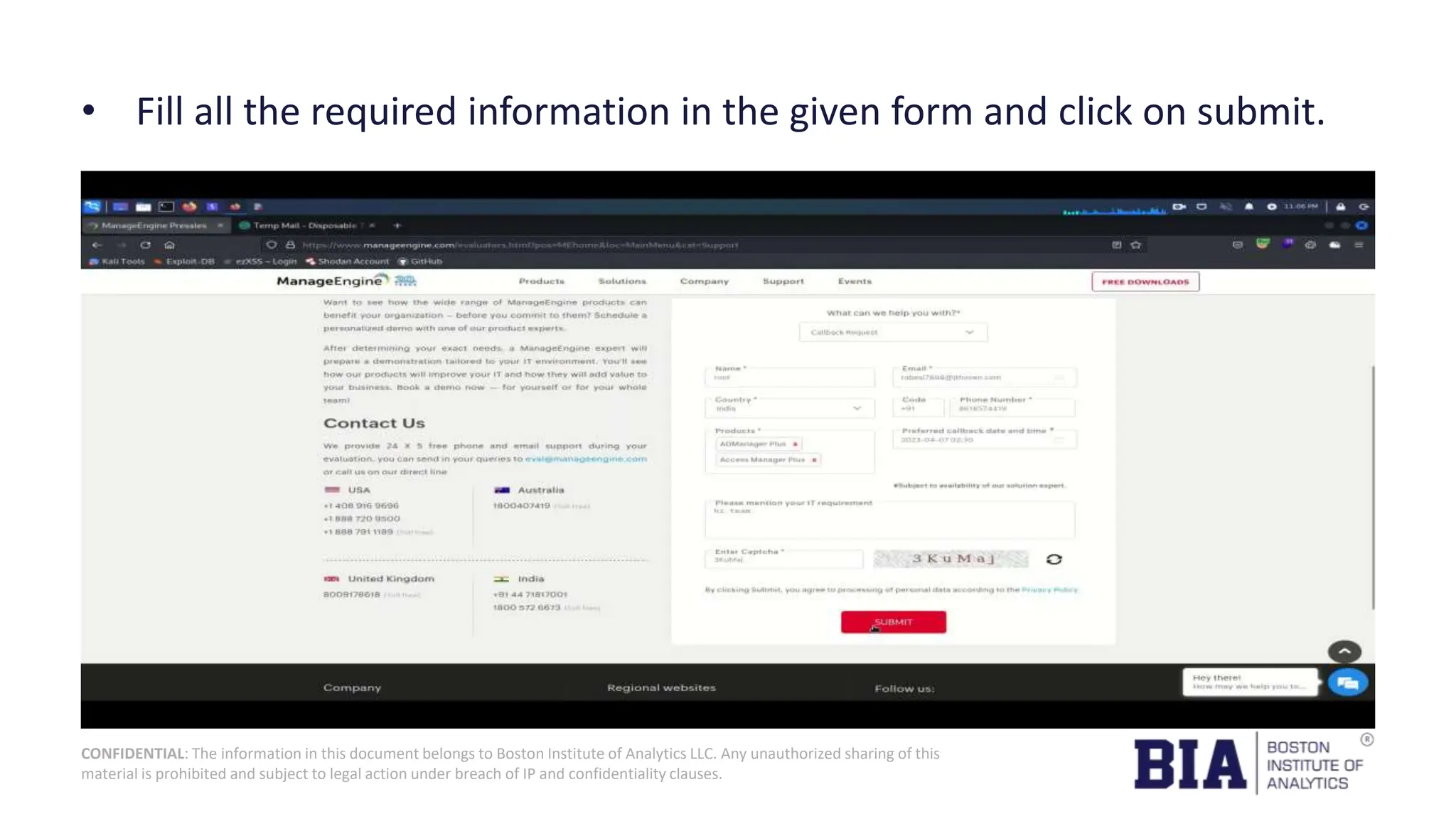
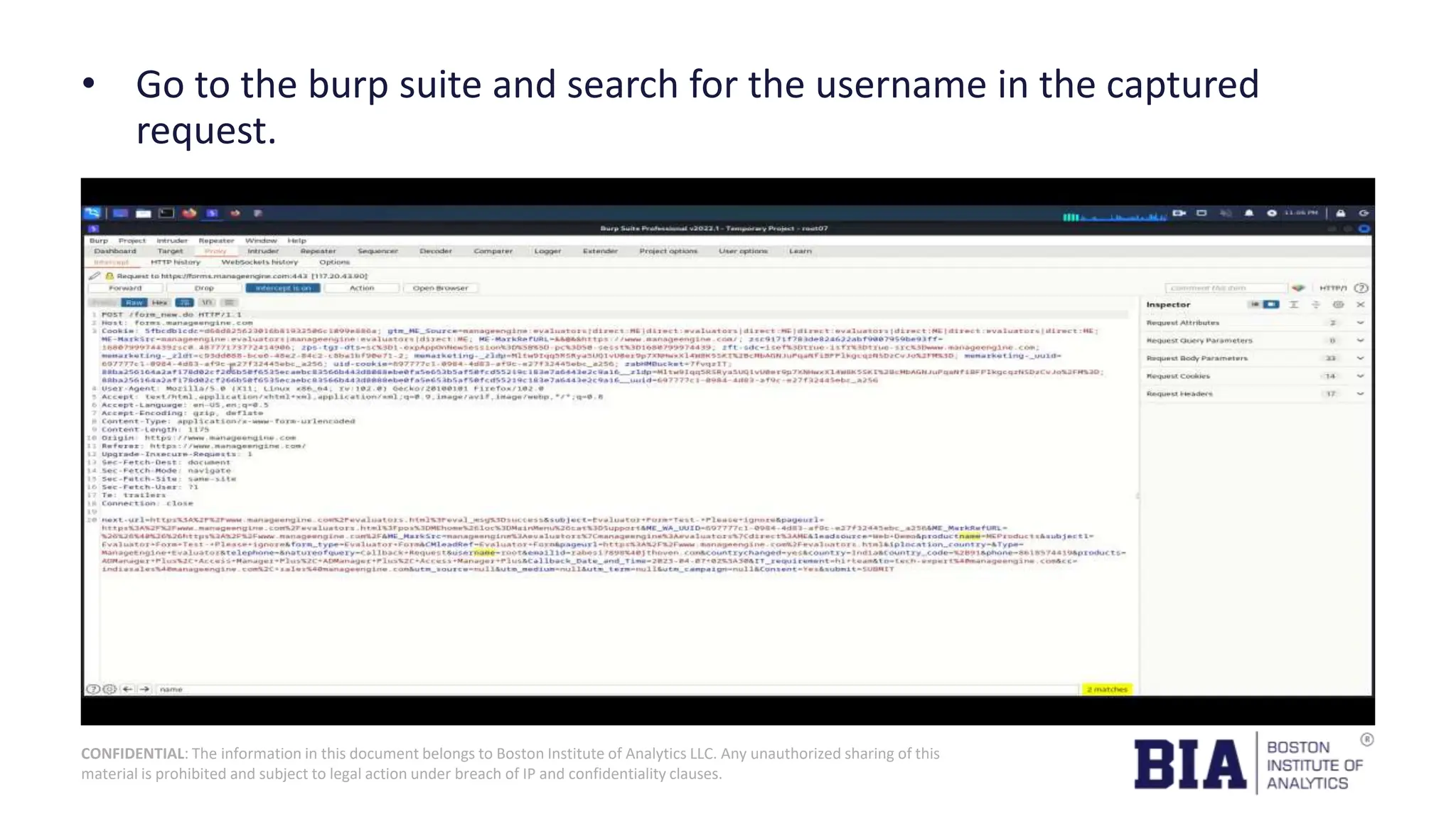
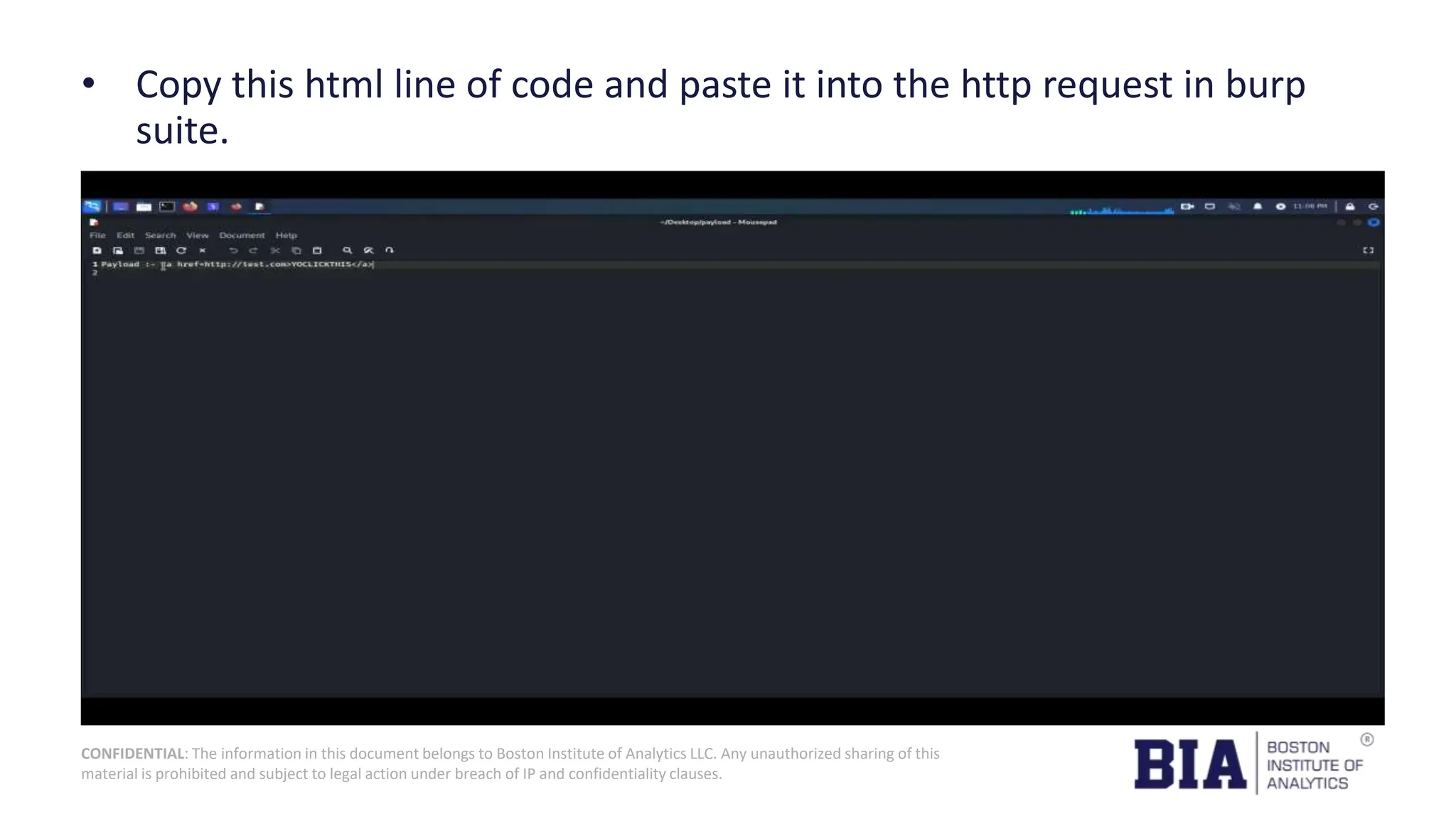
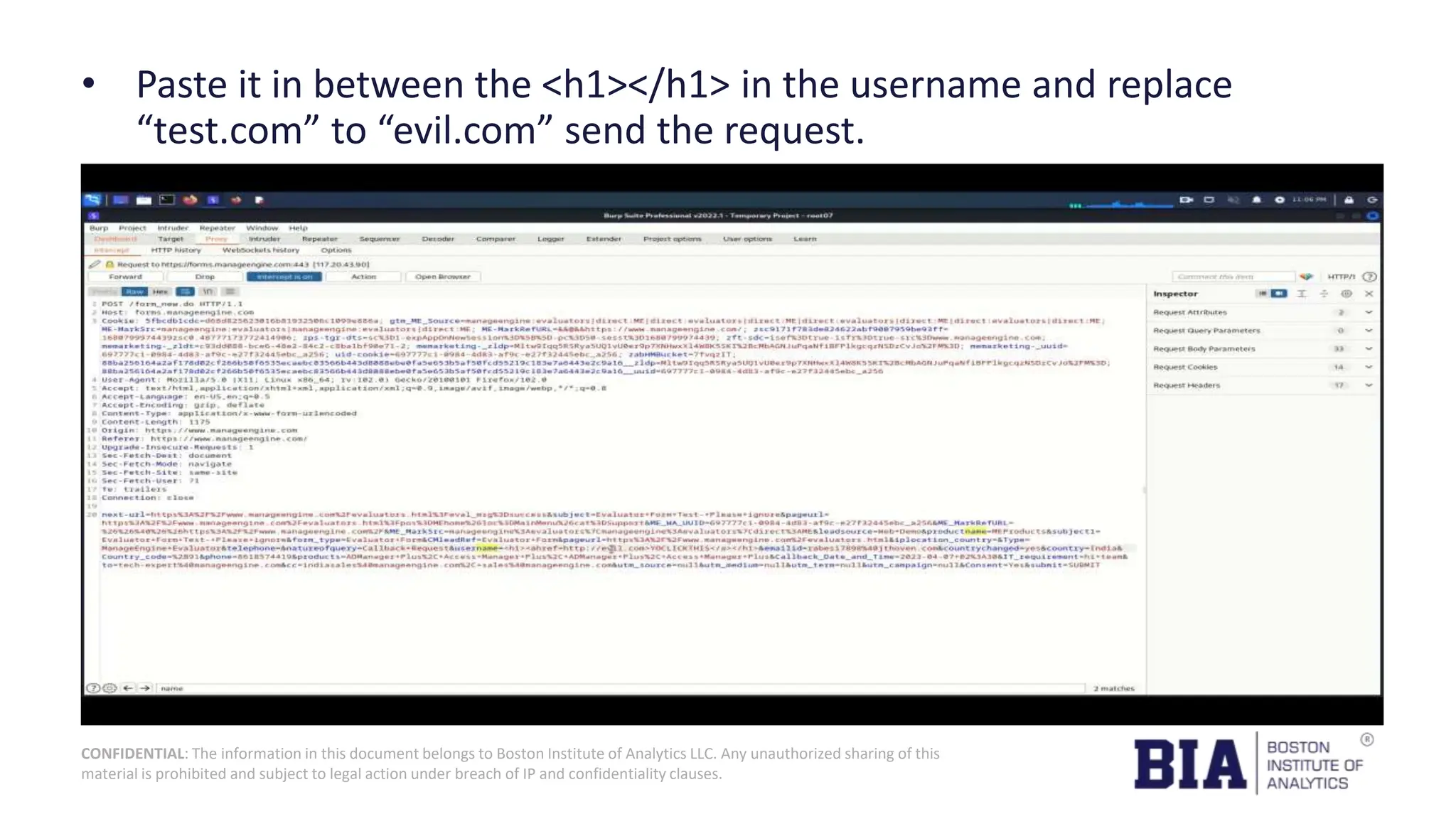
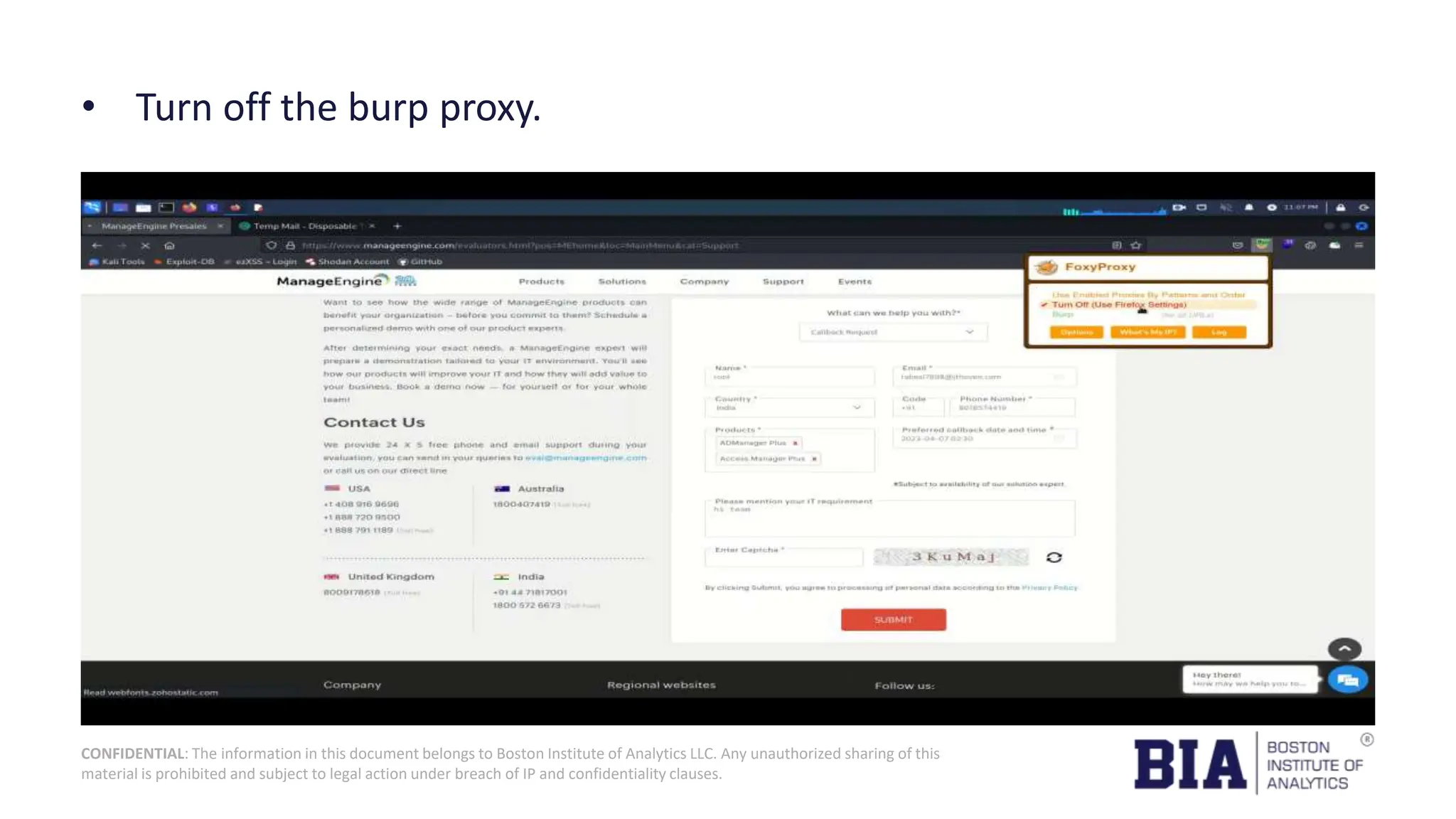
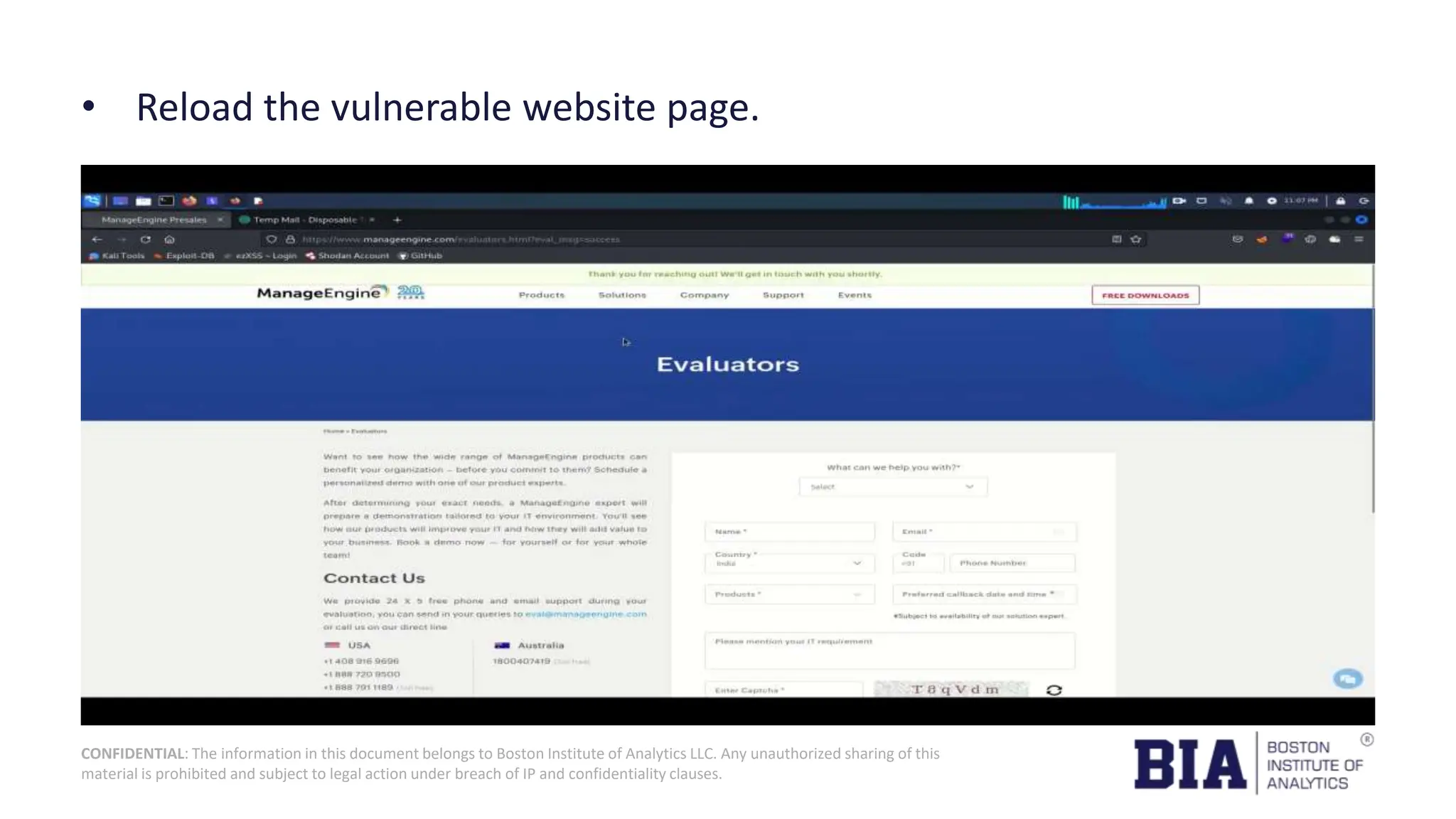
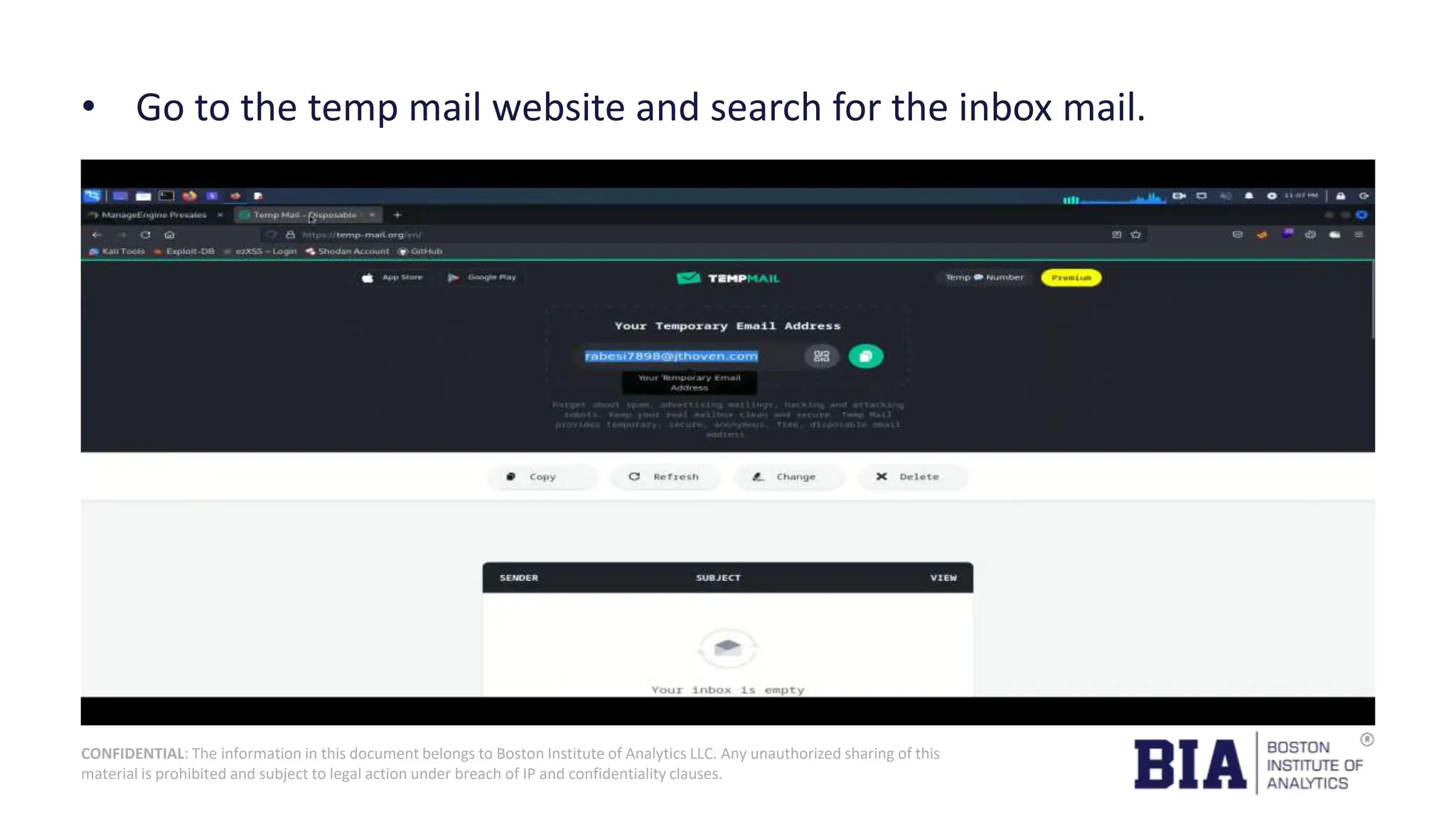
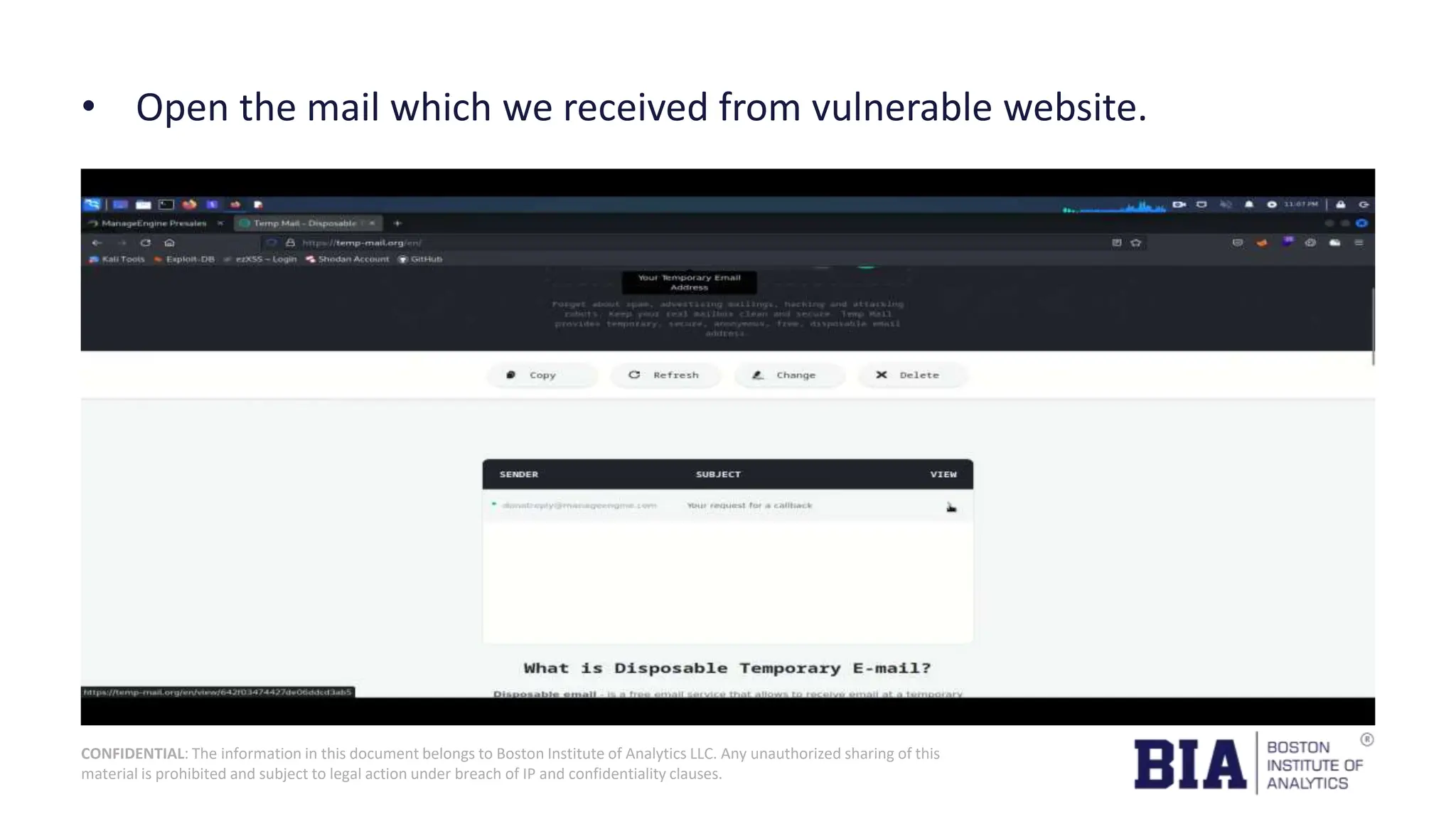
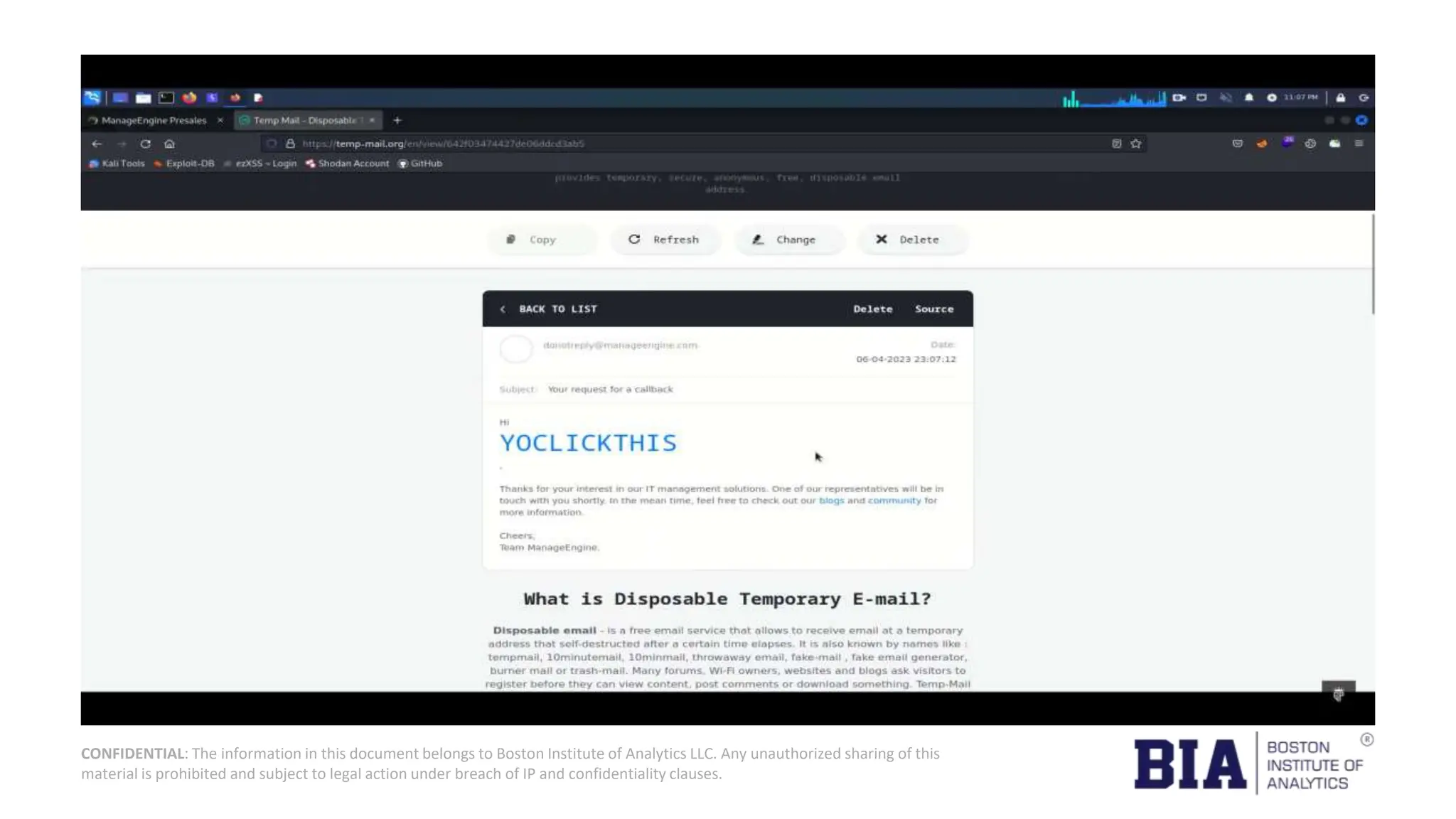
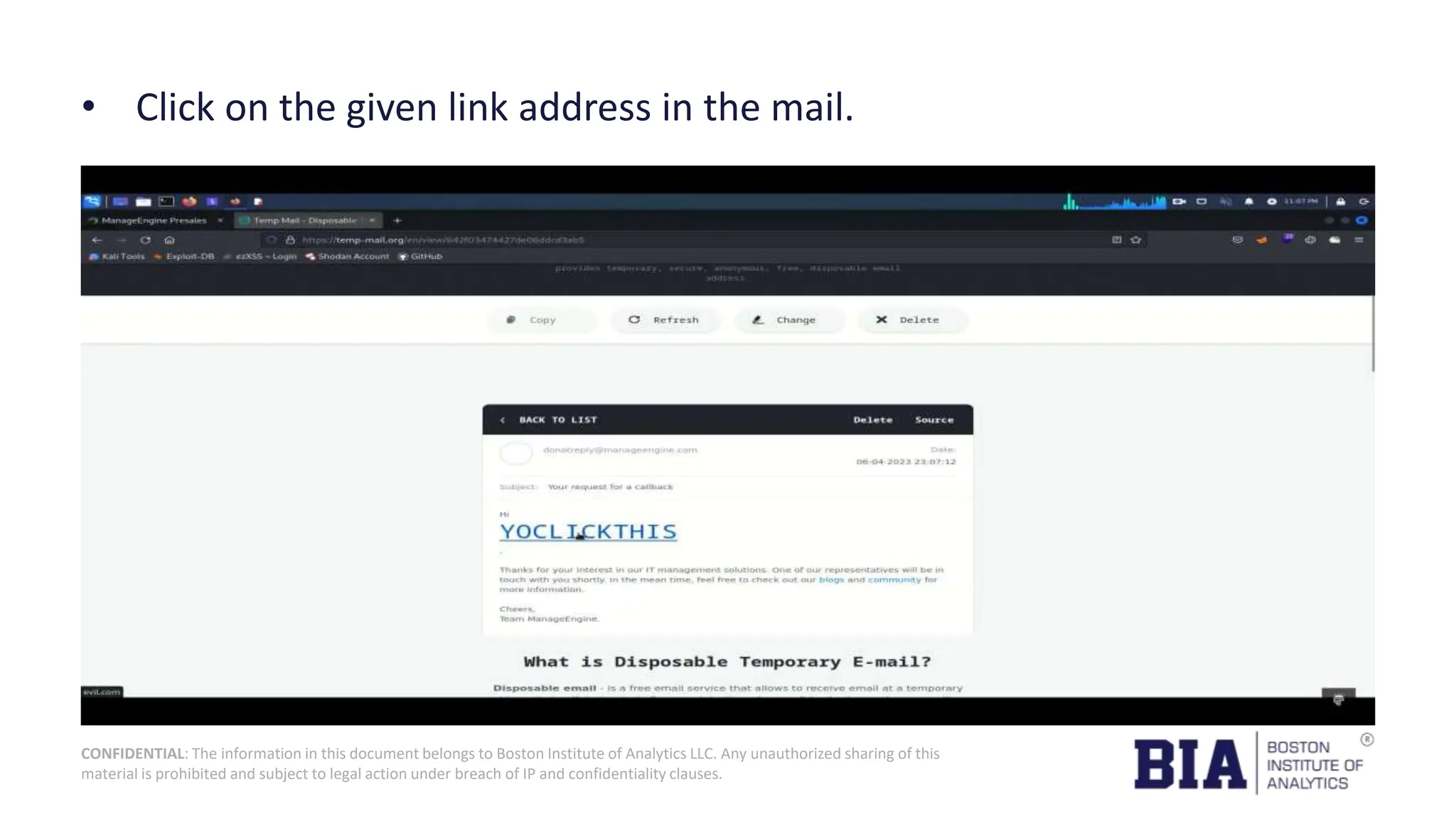
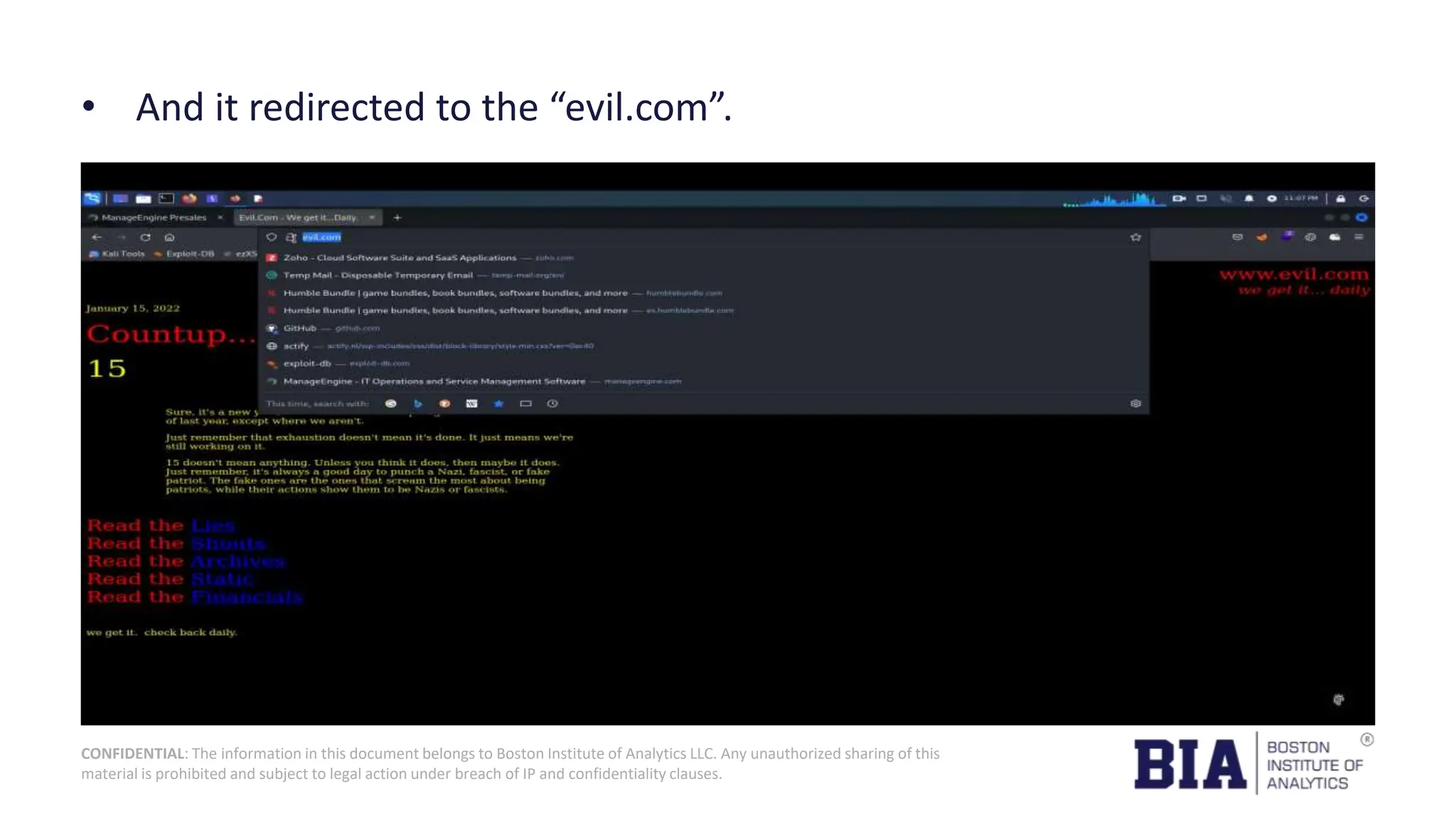
This document presents a project report on HTML injection vulnerabilities in web applications, specifically targeting the Manage Engine website. The report outlines the research methodology, findings on potential impacts of such vulnerabilities, and detailed recommendations for mitigation including input validation and content security policies. A proof of concept demonstrates how an HTML injection can be exploited, highlighting the importance of proper security measures to prevent these vulnerabilities.