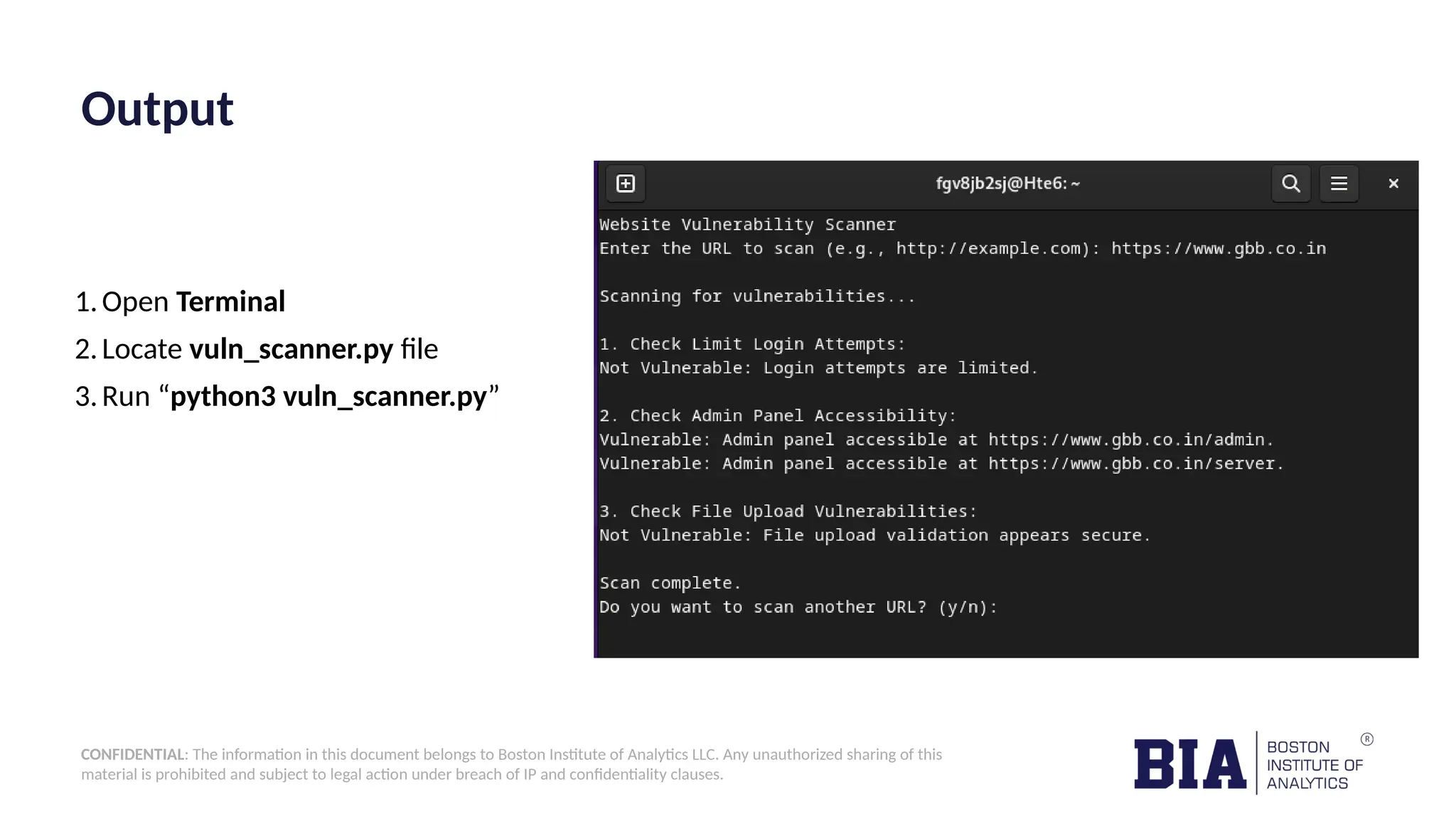
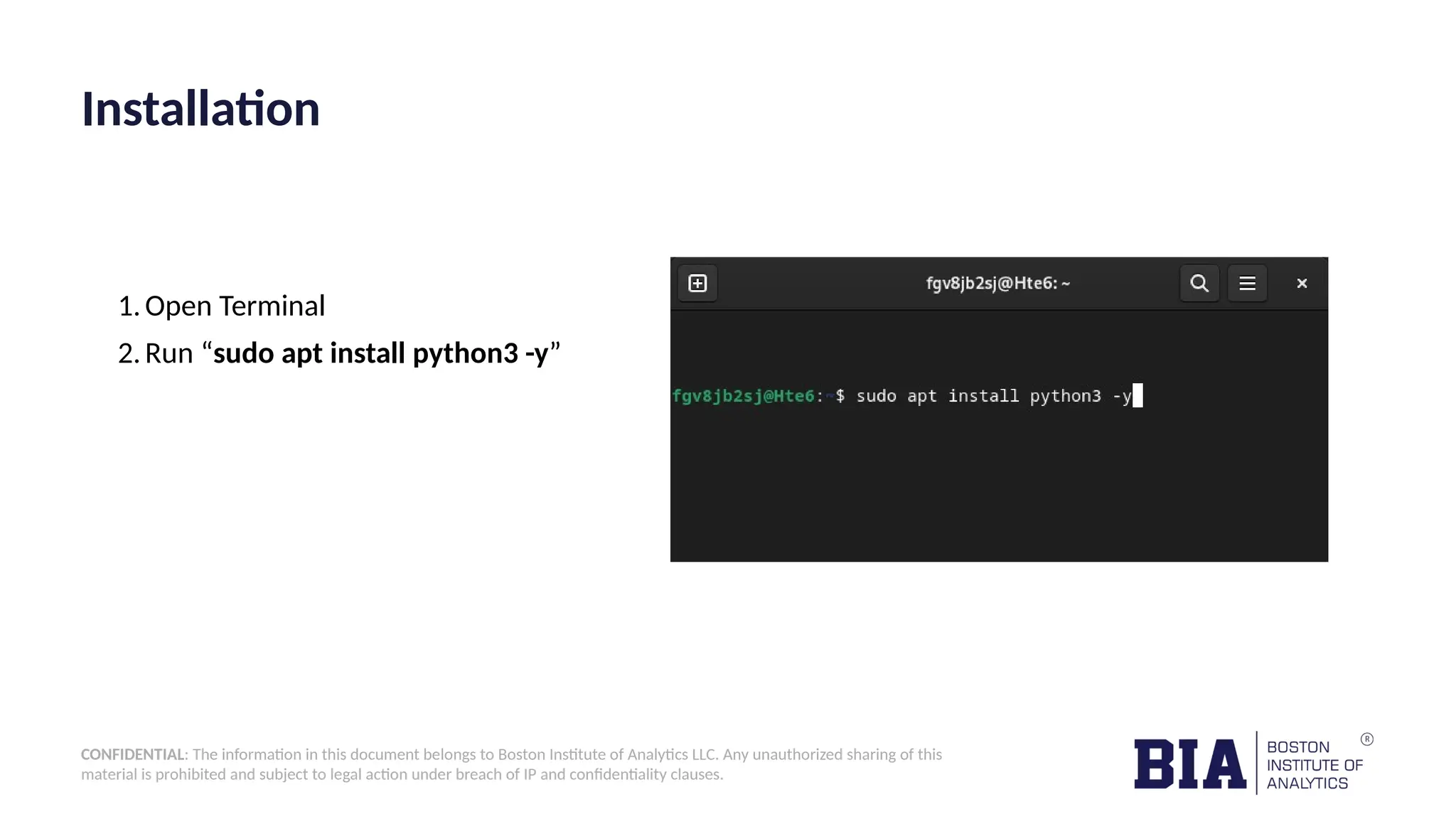
The document outlines the development of a Python tool designed for website vulnerability scanning, aiming to identify security weaknesses such as excessive login attempts, accessible admin panels, and file upload vulnerabilities. It details the procedure and necessary prerequisites for implementing the tool, as well as the mitigation strategies for common vulnerabilities. Additionally, it provides a proof of concept demonstrating vulnerabilities in a specific website and emphasizes the importance of security measures.


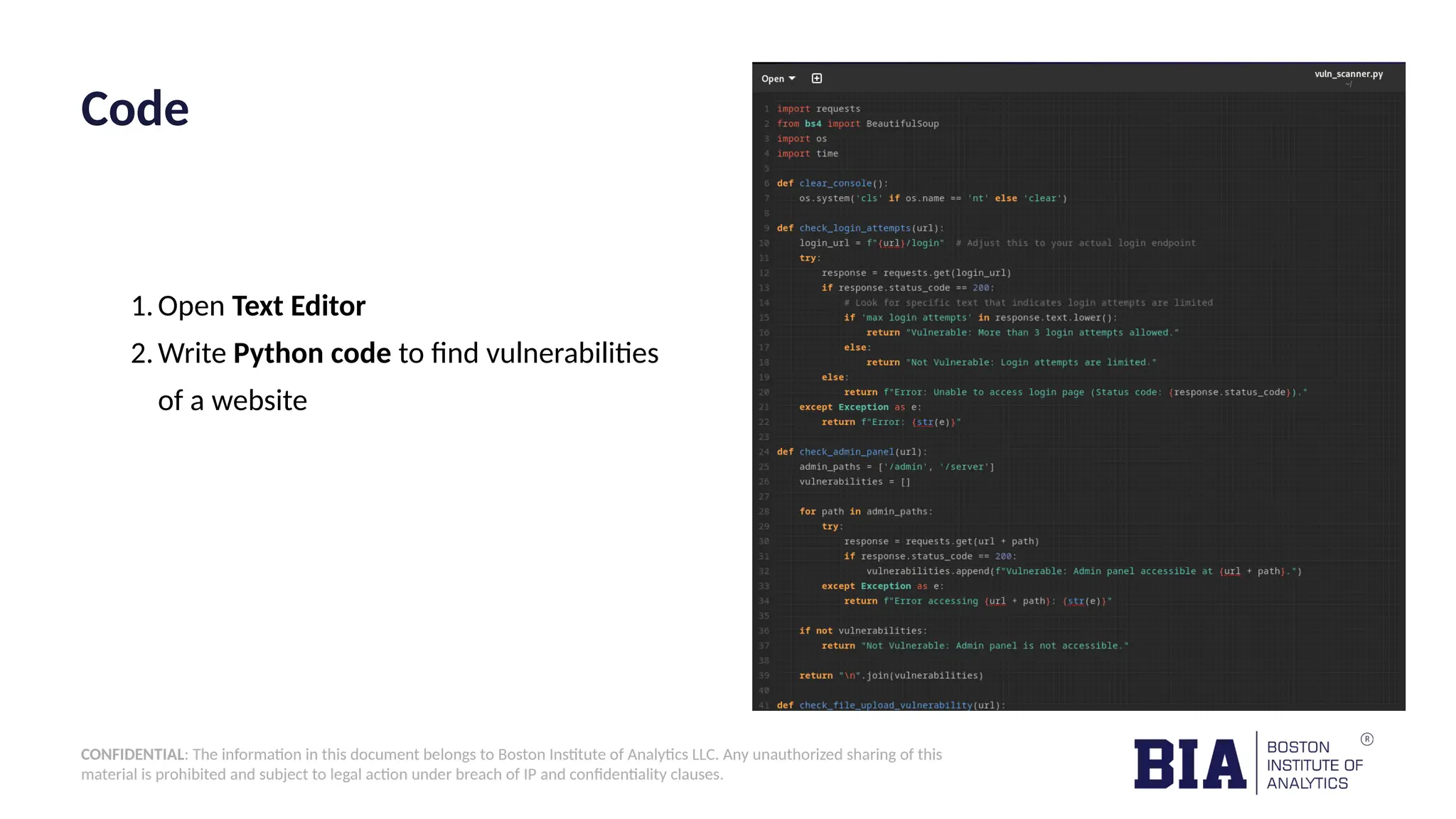
![CONFIDENTIAL: The information in this document belongs to Boston Institute of Analytics LLC. Any unauthorized sharing of this material is prohibited and subject to legal action under breach of IP and confidentiality clauses. Code-Picture1&2 import requests from bs4 import BeautifulSoup import os import time def clear_console(): os.system('cls' if os.name == 'nt' else 'clear') def check_login_attempts(url): login_url = f"{url}/login" # Adjust this to your actual login endpoint try: response = requests.get(login_url) if response.status_code == 200: # Look for specific text that indicates login attempts are limited if 'max login attempts' in response.text.lower(): return "Vulnerable: More than 3 login attempts allowed." else: return "Not Vulnerable: Login attempts are limited." else: return f"Error: Unable to access login page (Status code: {response.status_code})." except Exception as e: return f"Error: {str(e)}" def check_admin_panel(url): admin_paths = ['/admin', '/server'] vulnerabilities = [] for path in admin_paths: try: response = requests.get(url + path) if response.status_code == 200: vulnerabilities.append(f"Vulnerable: Admin panel accessible at {url + path}.") except Exception as e: return f"Error accessing {url + path}: {str(e)}" if not vulnerabilities: return "Not Vulnerable: Admin panel is not accessible." return "n".join(vulnerabilities)](https://image.slidesharecdn.com/capstoneppt-241113132354-d894618e/75/Developing-a-Simple-Python-Tool-for-Website-Vulnerability-Scanning-9-2048.jpg)
![CONFIDENTIAL: The information in this document belongs to Boston Institute of Analytics LLC. Any unauthorized sharing of this material is prohibited and subject to legal action under breach of IP and confidentiality clauses. Code-Picture3&4 def check_file_upload_vulnerability(url): upload_url = f"{url}/upload" # Adjust this to your actual upload endpoint malicious_files = ['malicious.exe', 'malicious.php', 'malicious.js'] vulnerabilities = [] for file in malicious_files: try: with open(file, 'wb') as f: # Create a dummy malicious file f.write(b'This is a test for malicious file upload.') files = {'file': (file, open(file, 'rb'))} response = requests.post(upload_url, files=files) if response.status_code == 200 and 'success' in response.text.lower(): vulnerabilities.append(f"Vulnerable: File upload accepts malicious file {file}.") except Exception as e: return f"Error during file upload test: {str(e)}" if not vulnerabilities: return "Not Vulnerable: File upload validation appears secure." return "n".join(vulnerabilities) def main(): while True: clear_console() print("Website Vulnerability Scanner") target_url = input("Enter the URL to scan (e.g., http://example.com): ").strip() if not target_url.startswith("http"): print("Invalid URL. Please enter a valid URL starting with http or https.") continue print("nScanning for vulnerabilities...n") # Check for login attempts print("1. Check Limit Login Attempts:") print(check_login_attempts(target_url)) print("n2. Check Admin Panel Accessibility:") print(check_admin_panel(target_url)) print("n3. Check File Upload Vulnerabilities:") print(check_file_upload_vulnerability(target_url)) print("nScan complete.") # Ask the user if they want to scan again or exit user_choice = input("Do you want to scan another URL? (y/n): ").strip().lower() if user_choice != 'y': print("Exiting the scanner. Goodbye!") break if __name__ == "__main__": try: main() except KeyboardInterrupt:](https://image.slidesharecdn.com/capstoneppt-241113132354-d894618e/75/Developing-a-Simple-Python-Tool-for-Website-Vulnerability-Scanning-10-2048.jpg)