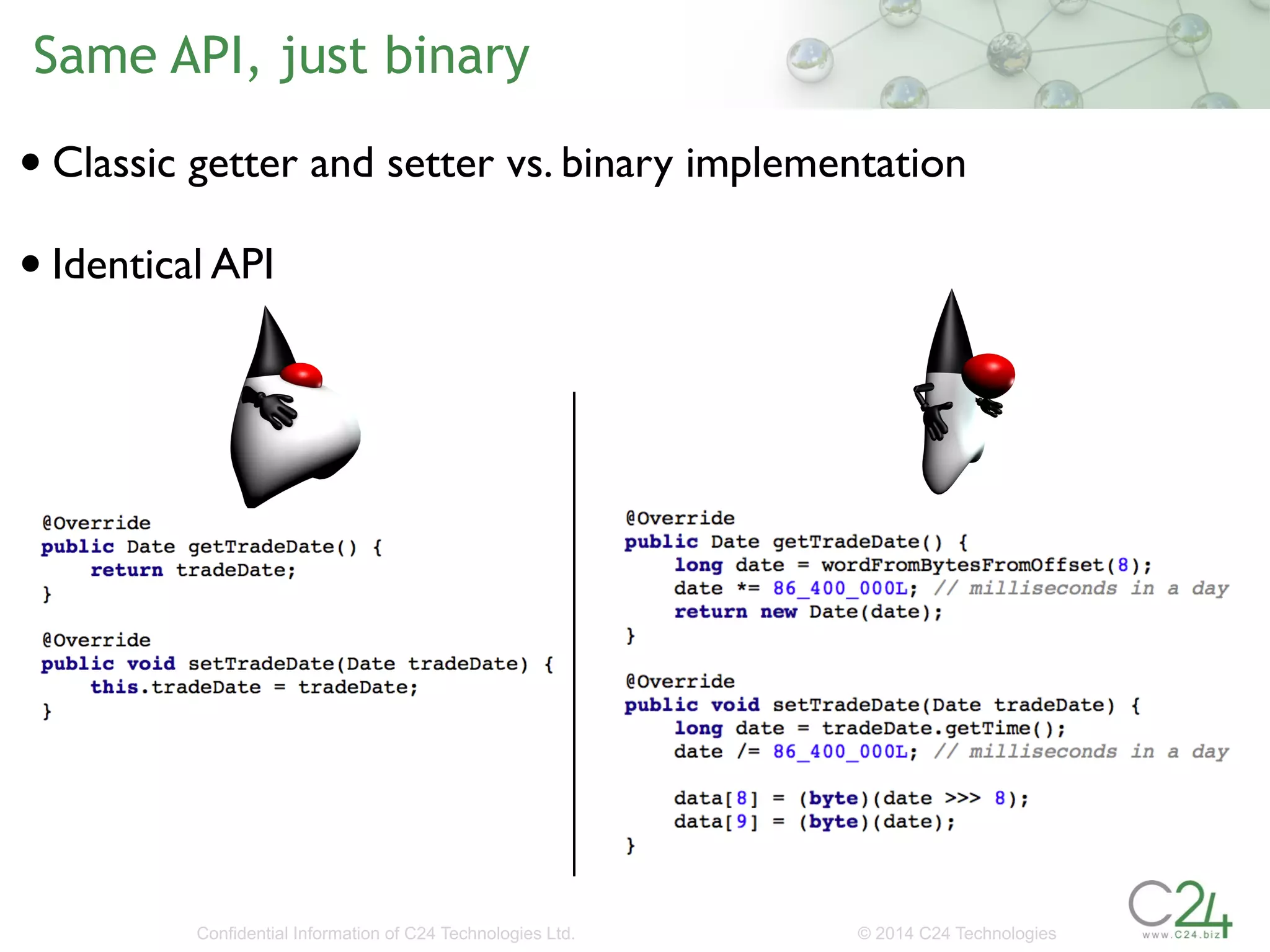
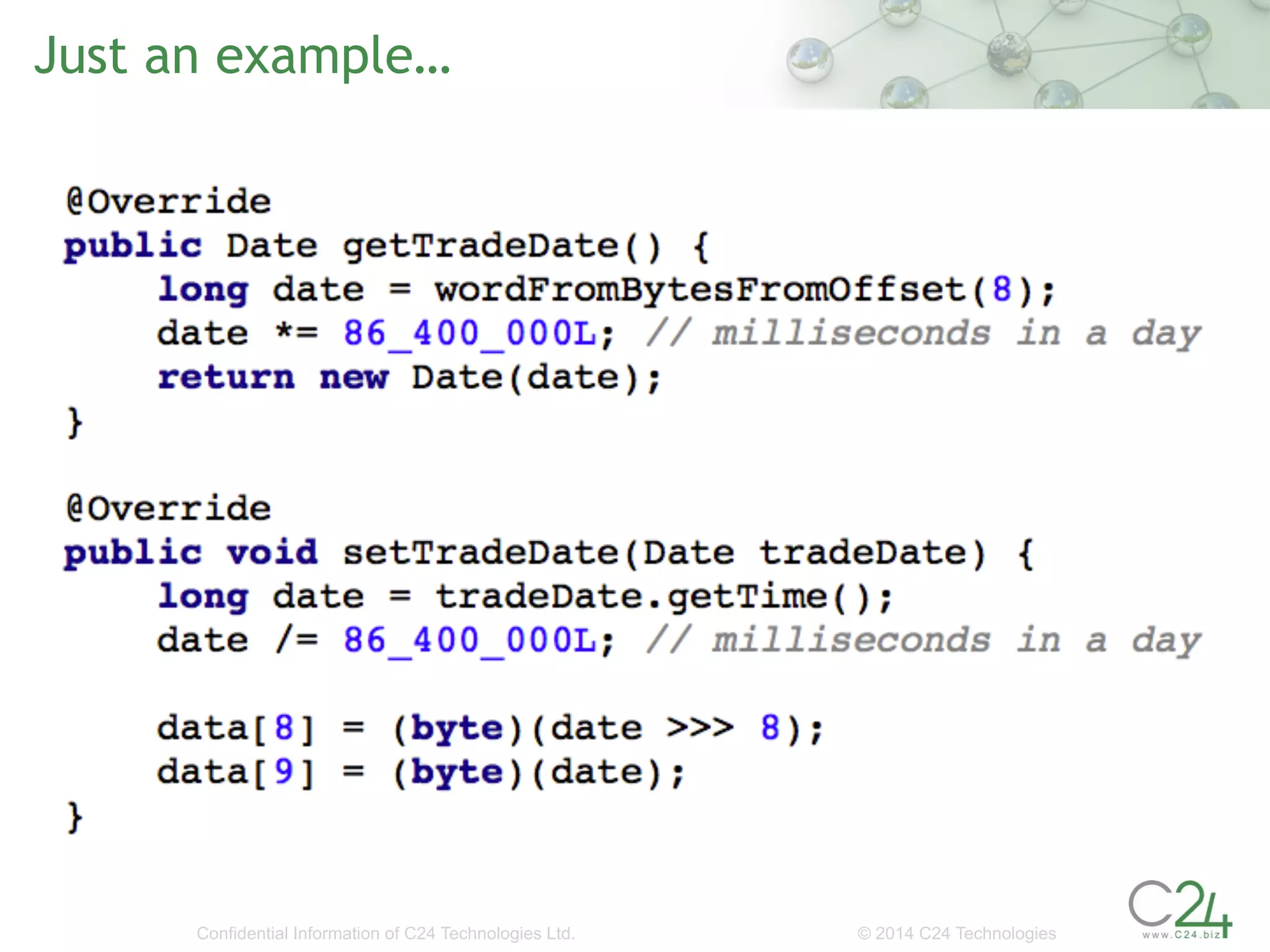
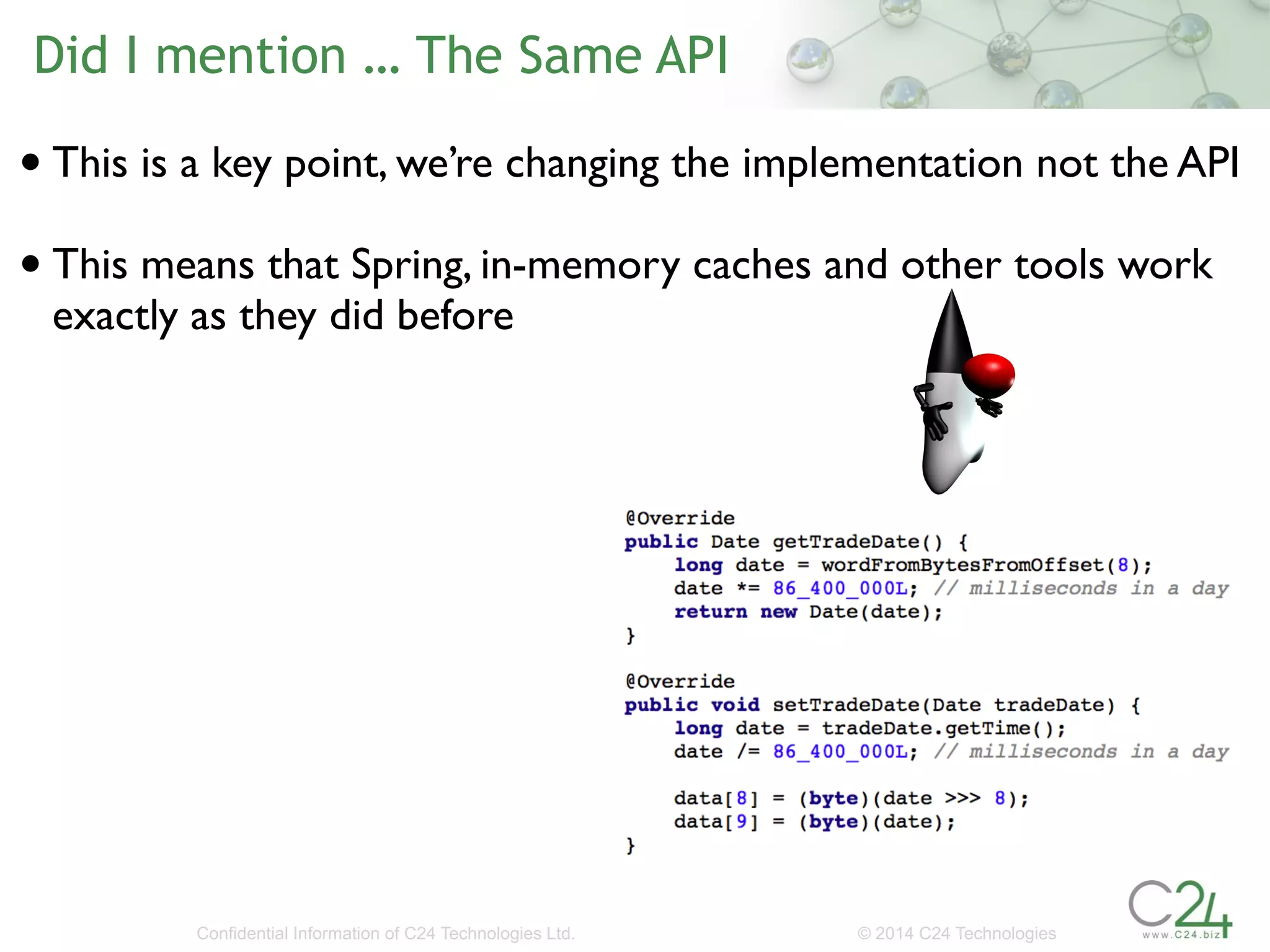
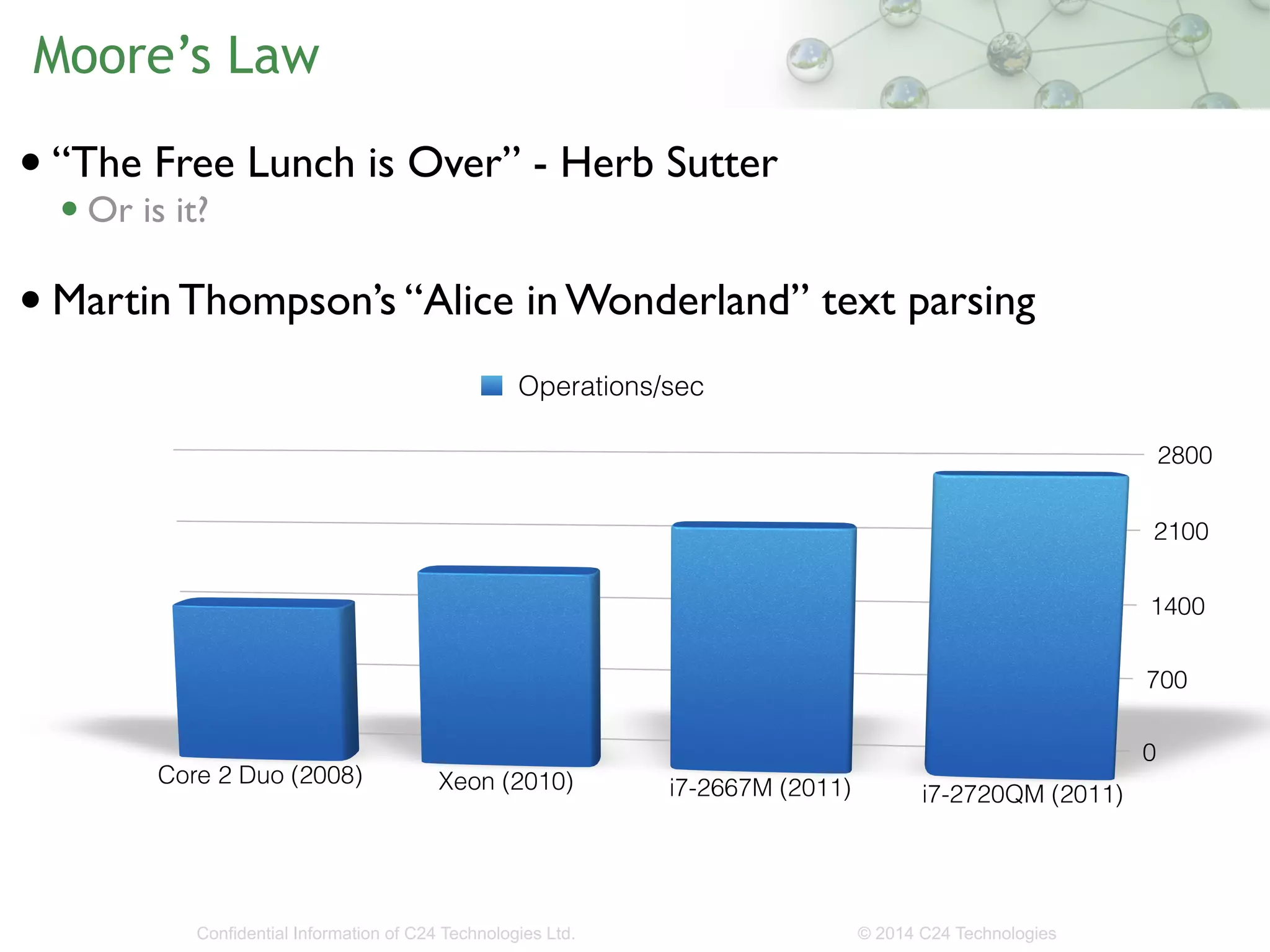
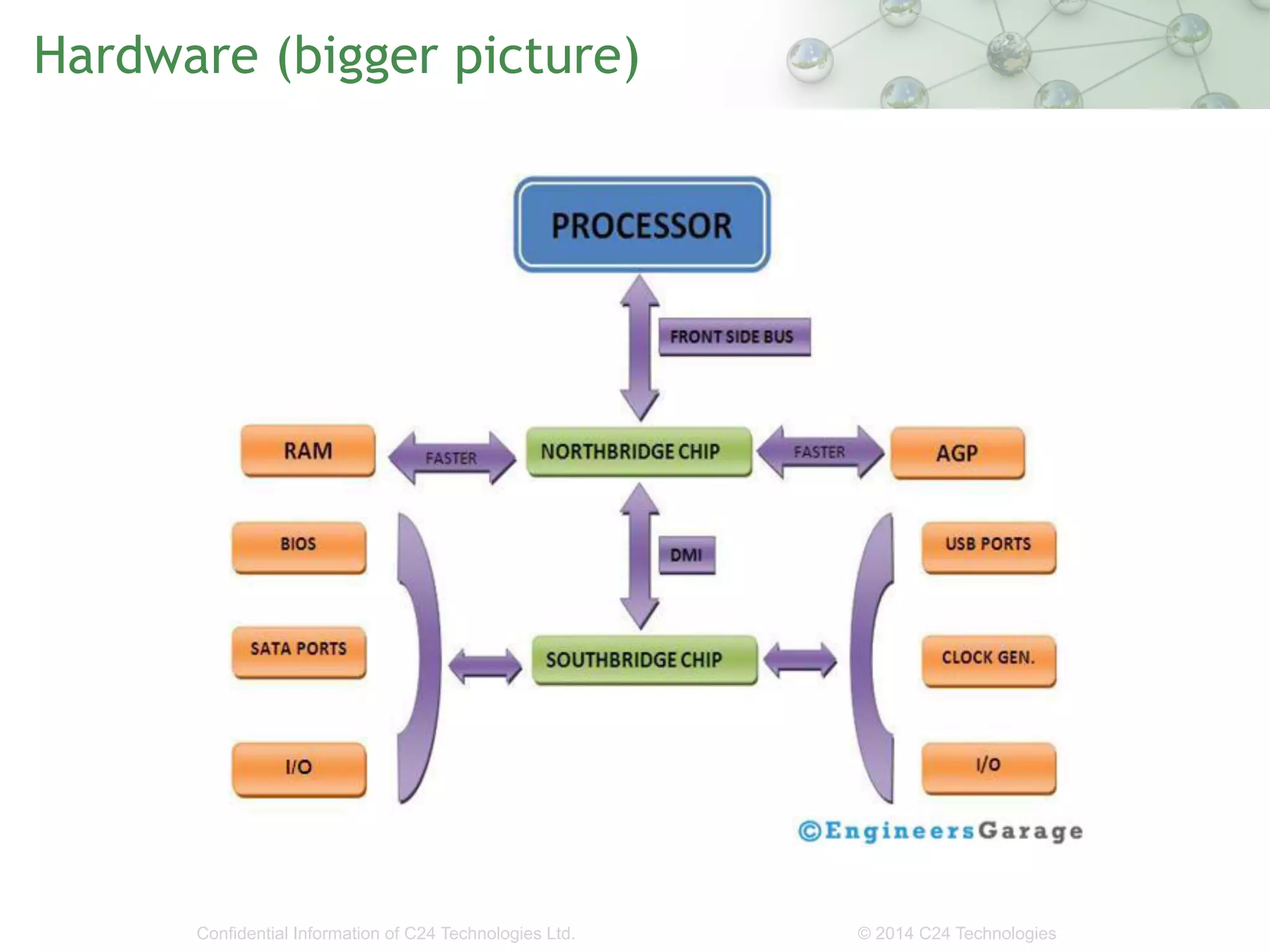
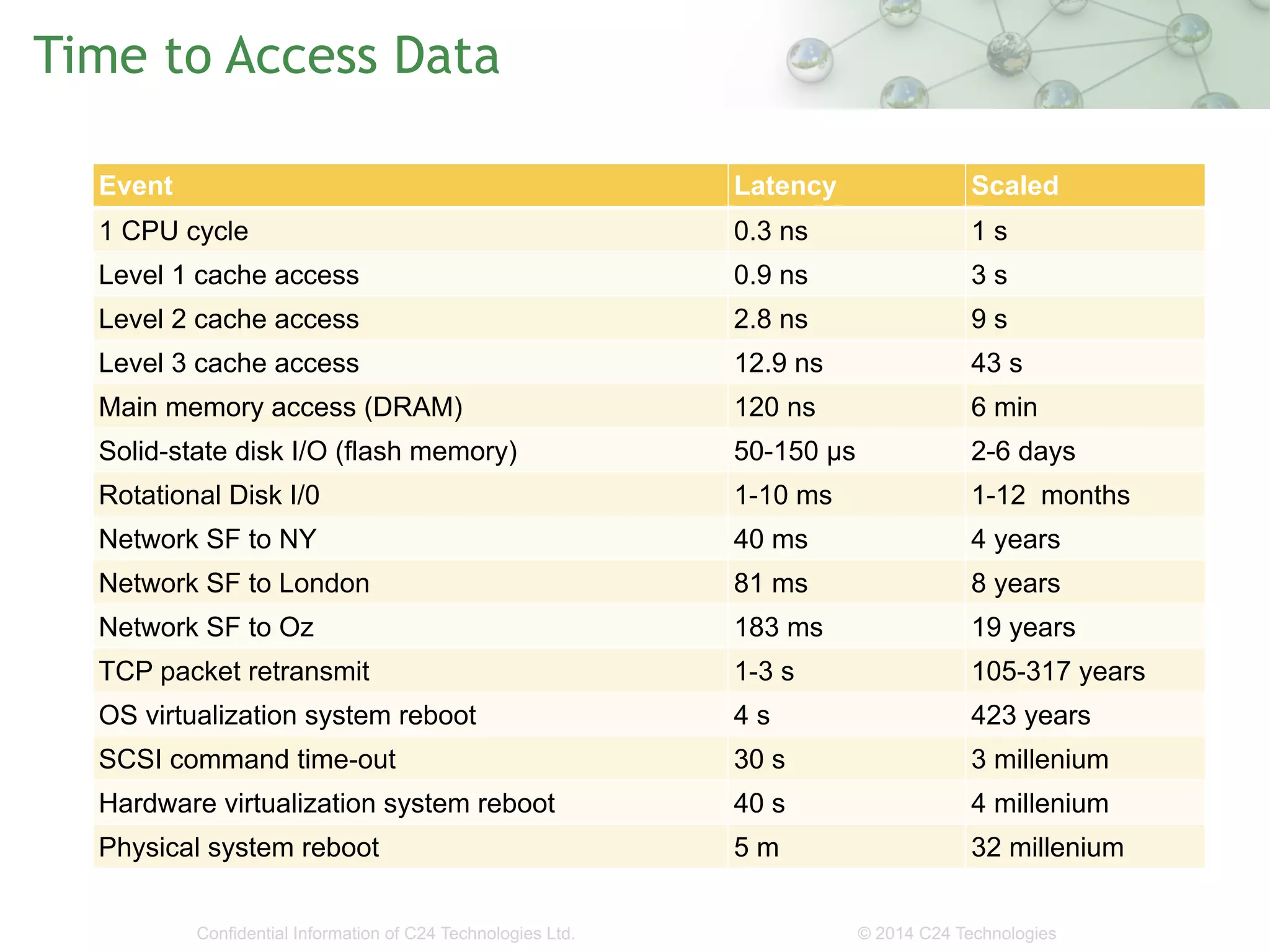
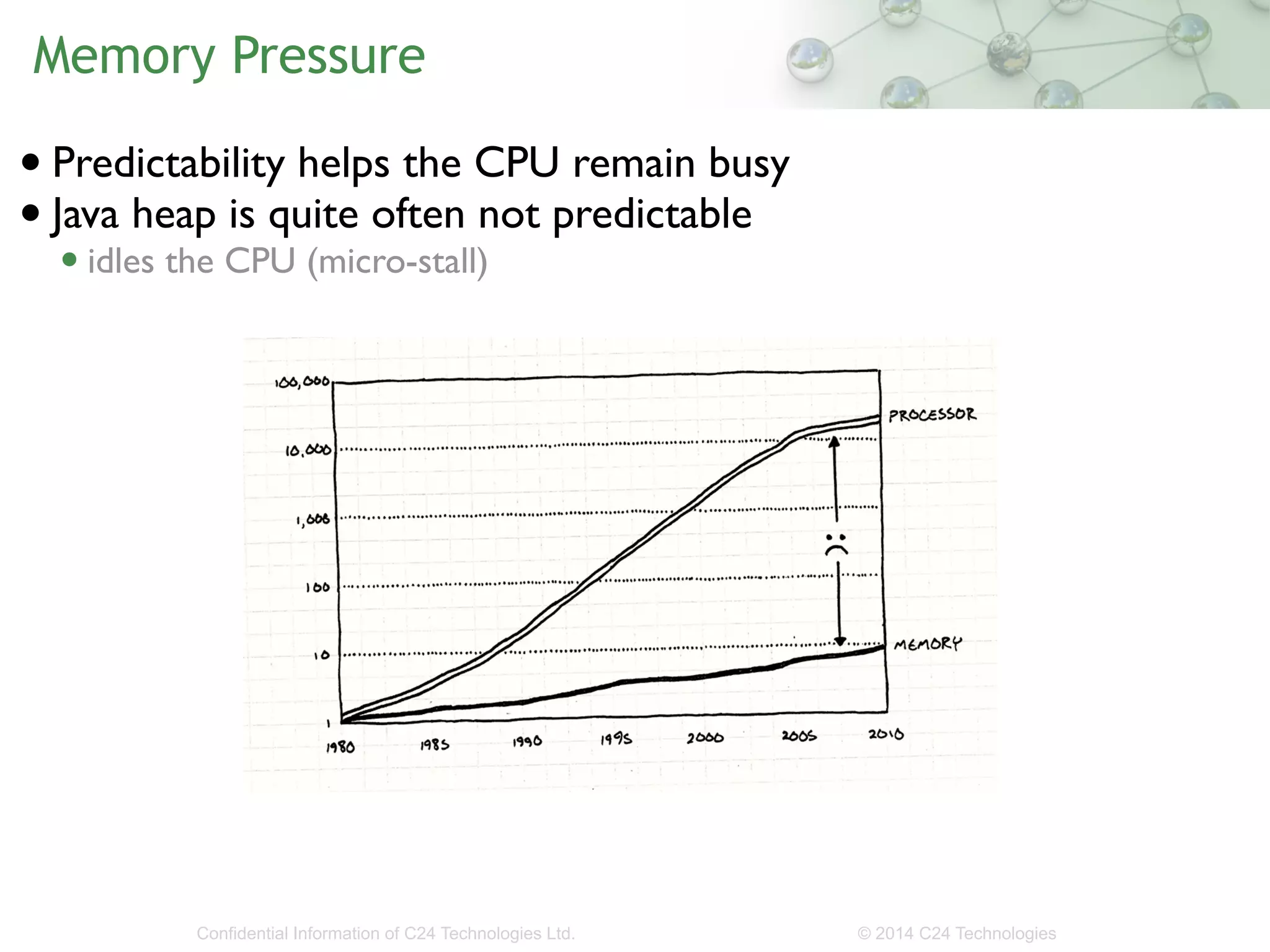
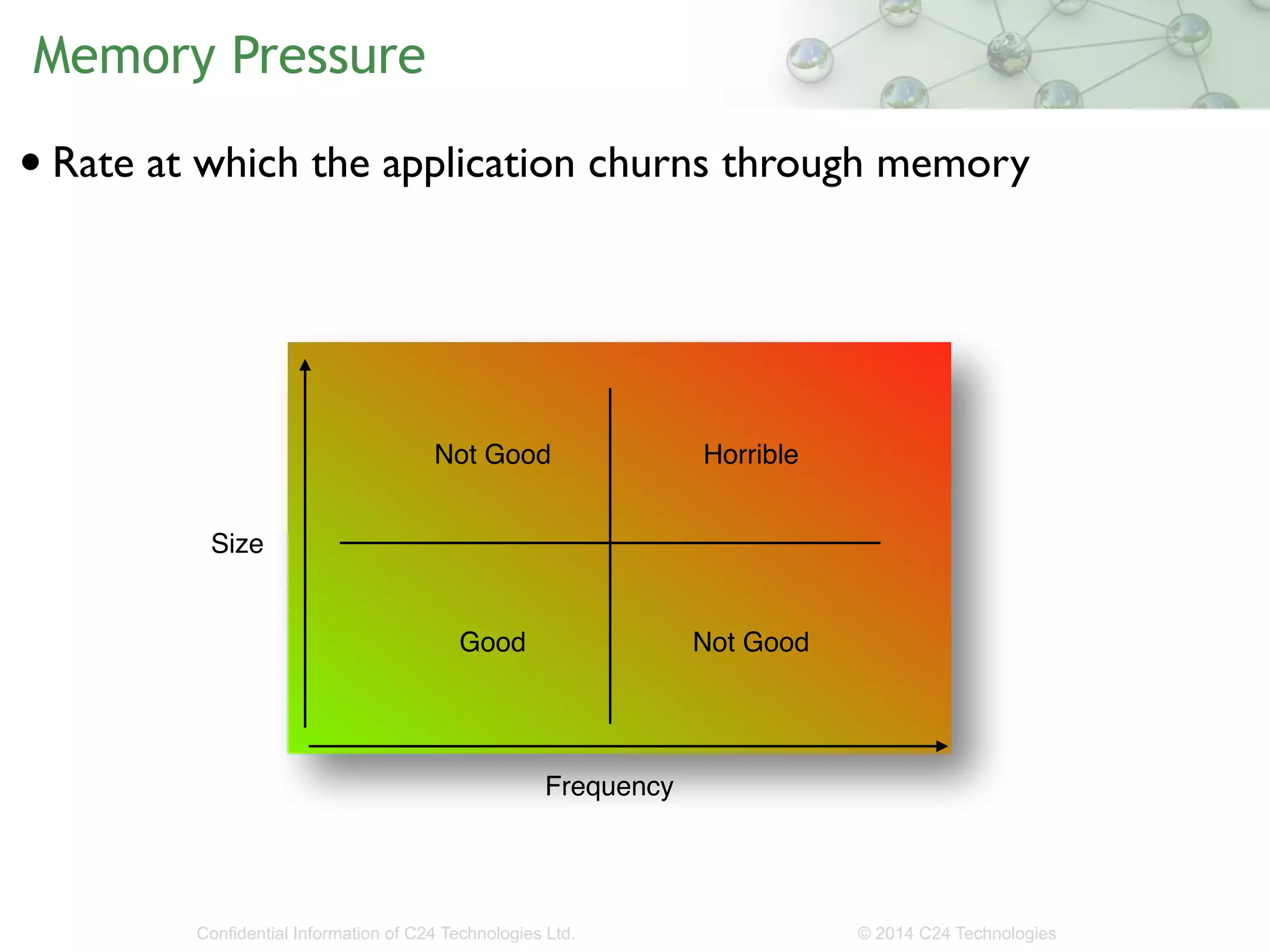
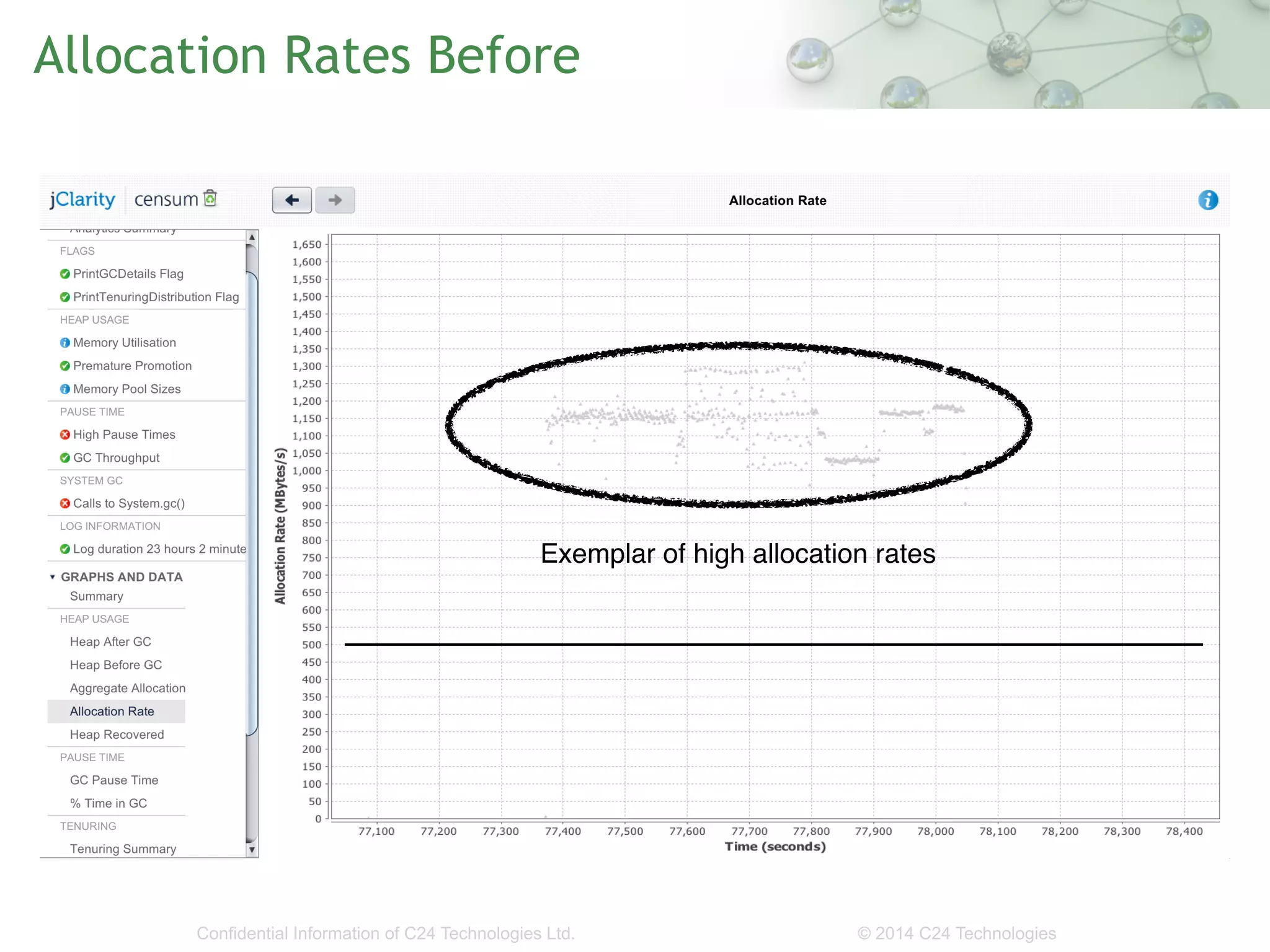
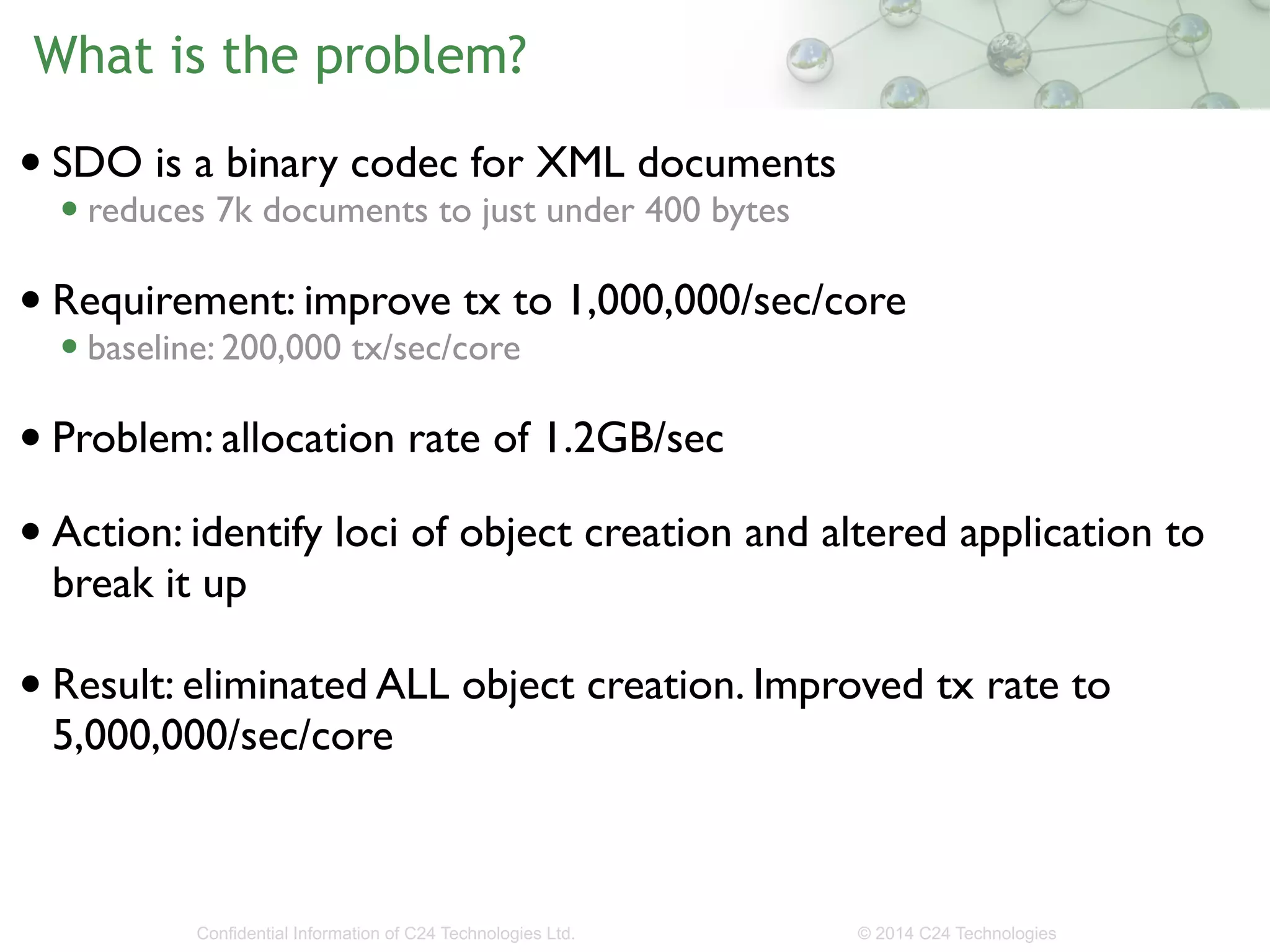
The document discusses the importance of low-latency requirements in Java applications, particularly in industries like high-frequency trading where even microseconds matter. It highlights the necessity for developers to understand the Java Virtual Machine (JVM) and hardware interactions, as well as the impact of memory pressure and object allocation rates on performance. Solutions proposed include using binary codecs for efficient memory usage and improving transaction rates significantly.






![Object Layouts Object[] String char[] String char[] Confidential Information of C24 Technologies Ltd. © 2014 C24 Technologies](https://image.slidesharecdn.com/towardlow-latencyjavaapplications-javaone2014-141004143914-conversion-gate02/75/Toward-low-latency-Java-applications-javaOne-2014-21-2048.jpg)

![Memory Footprint of SDO • SDOs were designed for two main purposes • Reduce memory footprint - by storing data as byte[] rather than fat Objects • Increase performance over “classic” Java Objects ! • Java is in many cases worse than XML for bloating memory usage for data • A simple “ABC” String takes 48 bytes!!! ! •We re-wrote an open source Java Binding tool to create a binary codec for XML (and other) models ! •We can reduce complex XML from 8k (an FpML derivative trade) and 25k as “classic” bound Java to under 400 bytes •Well over 50 times better memory usage! Confidential Information of C24 Technologies Ltd. © 2014 C24 Technologies](https://image.slidesharecdn.com/towardlow-latencyjavaapplications-javaone2014-141004143914-conversion-gate02/75/Toward-low-latency-Java-applications-javaOne-2014-25-2048.jpg)