The document analyzes the security of the Advanced Encryption Standard (AES) algorithm and proposes a modification to enhance its security. It summarizes AES, including its key expansion process, rounds, and steps. It then evaluates AES-128 security based on time security against brute force attacks and avalanche effect criteria. The authors propose modifying AES by XORing an additional random byte with the s-box value to increase time security and strict avalanche criterion. Security measurements of the modified AES sometimes fluctuate due to the random additional key.
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 DOI: 10.5121/ijcnc.2017.9206 69 SECURITY ANALYSIS OF AES AND ENHANCING ITS SECURITY BY MODIFYING S-BOX WITH AN ADDITIONAL BYTE Abdullah Al- Mamun1 , Shawon S. M. Rahman, Ph.D.2 , Tanvir Ahmed Shaon1 and Md Alam Hossain1 1 Department of Computer Science and Engineering Jessore University of Science and Technology,Jessore-7408,Bangladesh 2 Associate Professor, Department of Computer Science Majmaah University, Majmaah, Kingdom of Saudi Arabia ABSTRACT Secured and opportune transmission of data alwaysis a significant feature for any organization. Robust encryption techniques and algorithms always facilitate in augmenting secrecy, authentication and reliability of data. At present, Advanced Encryption Standard (AES) patronized by NIST is the most secure algorithm for escalating the confidentiality of data. This paper mainly focuses on an inclusive analysis related to the security of existing AES algorithm and aim to enhance the level security of this algorithm. Through some modification of existing AES algorithm by XORing an additional byte with s-box value, we have successfully increased the Time Security and Strict Avalanche Criterion. We have used random additional key for increasing security. Since this key is random, result of security measurement sometimes fluctuates. KEYWORDS Cryptography;Advanced Encryption Standard;secure algorithm;s-box; Ciphertext; Avalanche Effect; SAC; 1. INTRODUCTION AND HISTORY Security is an issue to defend anything from danger or threat. From the very beginning of humankind, Security was major concern to protect valuable things. Nowadays information has become more and more important.Before 19th century information was stored as hard copy and people used physical media to store &classical cryptography to protect that. But in 20th century digital way was invented to store and share information using computer and Internet. Internet is a common place for storing & sharing data. Everyone has free accessibility to it. So there is a question to protect information from unauthorized access. And so, modern cryptography has initialized. Cryptography is a way of storing and transmitting data in a scramble form that can only be understood and processed by intended persons [1][20]. The many schemes used for encryption constitute the area of study known cryptography. Such a scheme is known as cryptographic system or a cipher. Encryption is a process of secure one’s data from unauthorized access. Our data in readable form is called plaintext; data in encoded or unreadable form is called cipher text.](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-1-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 70 The process of converting or translating plaintext to cipher text is called encryption and its reverse is called decryption. Figure 1 shows encryption and decryption process. In modern cryptography, complex algorithms or functions are used for encryption and decryption. All these algorithms use keys of different size for encryption and decryption. The strength of cryptography depends on the algorithm and key used. The key can be private or public. In public key Cryptography, pair of key is used[20][21][22]. One key is private and other is public. Both sender and receiver generate their own pair of key. Receiver distributes the public key to the intended senders and keep private key secret. Sender encrypts data with receiver’s public key and sends the ciphertext to the receiver. The receiver decrypts that ciphertext with own private key to generate plaintext. In private key cryptography same key is used for both encryption and decryption. The key is always kept secret. Sender encrypts the plaintext with the private key and sends to the receiver. The receiver decrypts the ciphertext with same key. Figure 1 (a) Encryption Process (b) Decryption Process 2. BACKGROUND STUDY 2.1.AES Description Advanced Encryption Standard (AES) is a symmetric cipher and it always uses the same key for encryption and decryption. This key is called cipher key. AES is also a block cipher and splits it input stream into block of fixed size. It allows a verity of block and key size. The size can be 128, 160, 192, 224 and 256 bits (multiple of 32 bits and from minimum 128 to maximum 256 [2]). But the standard is that, the input block size will always be fixed at 128 and the key size will be any of 128, 192 and 256. AES follows the substitution permutation network structure and so it has several working rounds depending on the key size. AES works in 10 rounds for 128 bits key, 12 rounds for 192 bits key and 14 rounds for 256 bits key. Nowadays, most commonly used key size is 128. In inner work of AES, cipher key is expanded into 11, 13 or 15 keys respectively for 10, 12 or 14 rounds. Then the input block is copied into an array named state array. State array is 4x4 matrixes. Afterword the state array is XOR’ed with first round key and this step is known as AddRoundKey. Finally, AES perform 10, 12 or 14 rounds of computation on state array according to key size. Each round contains four different steps and last round contains three steps. AES steps are [3]:](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-2-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 71 1. Key expansions:Rijndaelkey scheduleexpands all round keysfrom cipher key. 2. Initial round: AddRoundKey – The state array is XOR’ed with the first round key. 3. Rounds: Each roundexcept last round performs these four steps. SubBytes on state array using s-box. A permutation ShiftRows on state array. MixColumns on state array. AddRoundKey with state array. 4. Final round: This round does not contain MixColumns and it performs following three steps. SubBytes on state array using s-box. A permutation ShiftRows on state array. AddRoundKeywith state array. 2.2.Key Expansion In cryptography , each round consist of same set of operations but some parameter like cipher key or round key are different from each other. A Key Schedule is an algorithm that gives those round keys for each round [4]. Suppose, each word length wi= 32 bits = 4 bytes. So a key consists of 4 words (4*32=128) and the initial round key is w0 + w1+ w2+ w3. Others words will be calculated as follows: wi = wi-1 Xor wi-4 for all values of i that are not multiple of 4. For the words with indices that are a multiple of 4 (w4k): RotWord: Bytes of w4k-1 are rotated left shift (nonlinearity). SubWord (rsw): SubBytes function is applied to all four bytes (Diffusion). The result (rsw) is XOR’ed with w4k-4 and round constant rcon. That is: w4k= rsw Xor w4k-4 Xor rcon. Figure 1. Diagram of Key Expansion](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-3-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 72 2.3.AddRoundKey AddRoundKey is the initial step of encryption and decryption process. It is also a step in every rounds of AES algorithm. In AddRoundKey step, the plaintext array that means state array is being XOR’ed with round key. In this step 16 byte state array XOR’ed with 16 byte (4 words) round key and generate 16 byte (128 bit) output. Figure 2. State array XOR'ed with Round Key 2.4.SubBytes SubBytes mean substitution of byte of the state array by searching in lookup table which is called substitution box or S-box. S-box is a 16*16 lookup table and it contains 256 different values. The S-box table contains all possible values for 8 bit sequence that means in decimal 0 to 255. Each byte of the state array is the input of this SubBytes step and the input byte is alternated by a corresponding value. Figure 4 shows S-box. Each byte is mapped into a new byte in the following way: the left most 4 bits denotes the row and right most 4 bits denotes the column of s-box. Suppose the input byte in s-box is b7 (in binary 10110111). The left most 4 bits means 1011 (b) denotes the row number and 0111 (7) denotes the column number of S-box. So the output value for input b7 is a9 (in binary 10101001)[5]. Figure 3. 16*16 Look up Table 2.5.ShiftRows ShiftRows step perform shifting of bytes among the columns of a state array. The state array contains 4 rows and 4 columns. This step perform left shift of certain offset in different rows cyclically. For 128 bit and 192 bit data block ShiftRows rules are given bellow: First rows will be unchanged. Second row will be shift 1 byte to left.](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-4-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 73 Third row will be shift 2 bytes to left. Fourth row will be 3 bytes to left. In general, row ‘a’ is left shifted cyclically for (a-1) bytes. For 256 bit block data ShiftRows rules step are: First rows will be unchanged. Second row will be shifted 1 byte to left. Third row will be shifted 3 bytes to left. Fourth row will be 4 bytes to left. Figure 4. ShiftRows The importance of this step is to avoid the columns being linearly independent.In decryption, the Inverse ShiftRows step perform opposite route shifting of each of the last three rows. 2.6.Mix Columns MixColumns step offer diffusion in AES encryption. Each column of state array enters in MixColumns step and produces four output columns. This step takes a column of state array and performs matrices multiplication with a fixed matrix and produces an output column. 3.SECURITY MEASUREMENT CRITERIA Security is the key term of Advanced Encryption Standard. Security of AES means how resistant this system is against active or passive attack. We measure the security based on three criteria [6]. Time Security Avalanche Effect Strict Avalanche Condition](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-5-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 74 3.1.Time Security It depict the potency of cryptographic method against brute force attack with different key size and time it takes to effectively mount a brute force attack.Brute force attack means thoroughly checking all probable key combinations until the accurate key is originate. For a 3 bit key, Brute force attack will take maximum 8 rounds to check every possible key arrangement. Maximum key combination for different key size is given in table 1. From table 1, for 128 bit key brute force attack must check maximum 3.403 x 1038 key combinations. Now the brute force attacking time based on processing speed of latest super computer can be measured. Table 1. Maximum Key Combination Faster Super Computer: 33.86 PFLOP/s = 33.86 x 10 15 FLOP/s. 33.86 Quadrillion keys per second. [1 Quadrillion=1,000,000,000,000,000;one thousand million million; 1015 ; prefix peta-] 1 year=365*24*60*60=31536000s. So, 31536000*3.386 x 1016 = 1.067 x 1024 keys per year. So, Brute force attack time to break 256 bit key is = ଵ.ଵହ଼ ଵ.ୣଶସ years = 1.0844 x 1053 years So 1.0844 x 1053 years need to break the 256-bit AES key using brute force attack Table 2. Estimation of Years to Break AES As shown in table 2, even with a supercomputer, it would take 1 billion billion years to crack the 128-bit AES key using brute force attack. 3.1.Avalanche Effect Avalanche effect is a property that is very crucial for block cipher and cryptographic hashfunction. A cryptosystem has avalanche property if for flipping or change just a single bit in plaintext or in secret key the output change significantly (about half of the output). Key size Possible Combination Key size Possible Combination 1 bit 2 32 bit 4294967296 2 bit 4 64 bit 1.8447 x 1019 4 bit 16 128 bit(AES) 3.403 x 1038 8 bit 256 192 bit(AES) 6.278 x 1057 16 bit 65536 256 bit(AES) 1.158 x 1077 No Key size Years Need 01 128 bit 3.19 x 1014 years 02 192 bit 5.88 x 10 33 years 03 256 bit 1.0844 x 1053 years](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-6-2048.jpg)
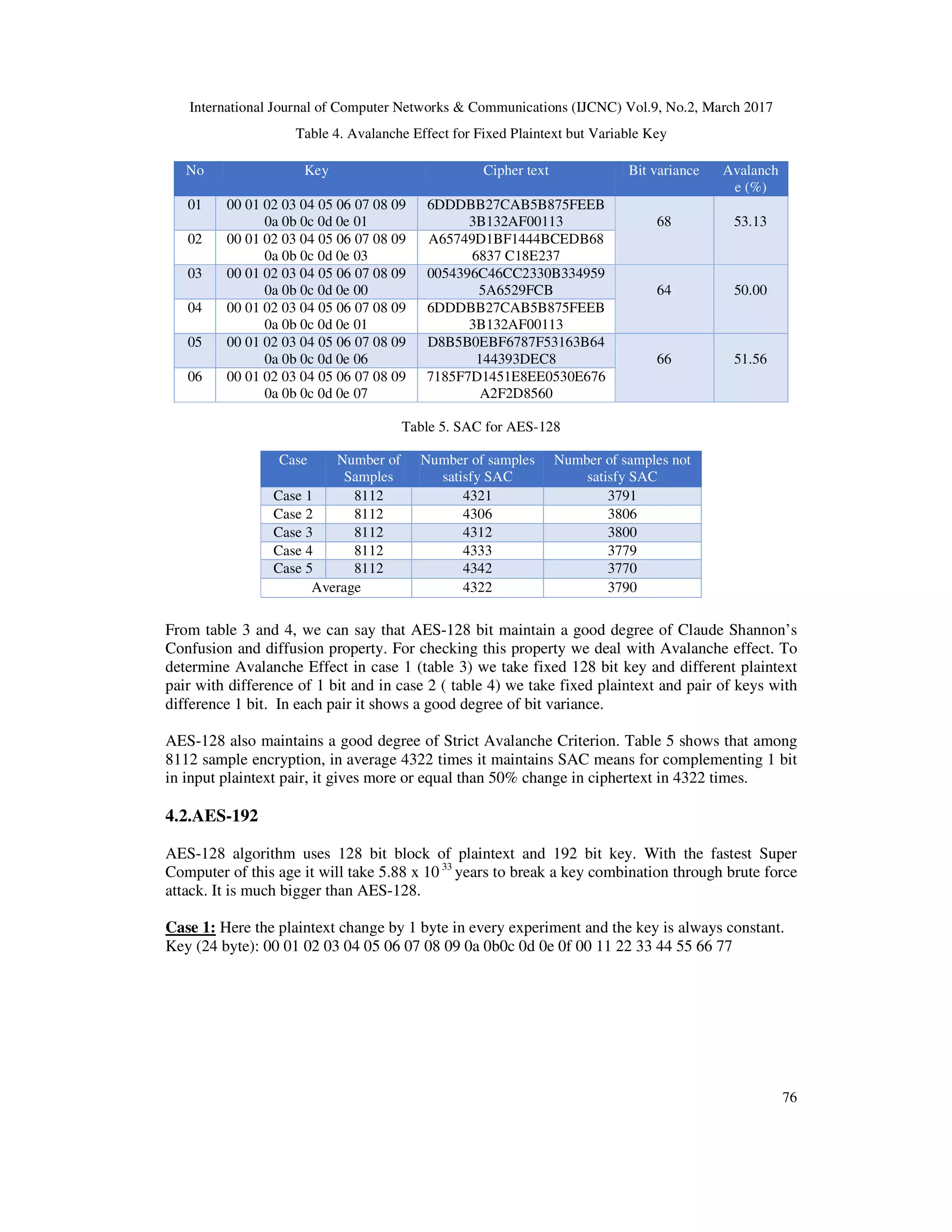
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 75 If a cipher does not show desirable degree of avalanche effect then the cryptanalysts can guess the plaintext by analyzing the Cipertext. So they can be able to break the cipher. Avalenche effect = Hamming distance Block size ∗ 100% Humming Distance:The Hamming Distance is a digit used to indicate the variation between two binary strings. It is a tiny section of a broader set of formulas used in information analysis. Specifically, Hamming's formulas allow computers to detect and correct error on their own [7]. 3.2. Strict Avalanche Criterion For symmetric key cryptographic algorithms Strict Avalanche Criterion is a wanted property. In block cipher context the SAC is said to be maintained by algorithms if, one bit complemented either in key or in plaintext causes a drastic change in ciphertext- about one half of the ciphertext. This SAC completely depends on algorithms confusion and diffusion property. In this AES symmetric key context SubBytes step, ShiftRows step and MixColumns step gives a desirable degree of confusion and diffusion. 4. SECURITY ANALYSIS OF EXISTING AES 4.1.AES-128 AES-128 algorithm uses 128 bit block of plaintext and 128 bit key. With the fastest Super Computer of this age it will take 3.19 x 1014 years to creak a key combination through brute force attack. So it is not possible not only for a human but also for a generation to break a key with checking all key combinations [8]. Case 1: Here the plaintext change by 1 byte in every experiment and the key is always constant. Key (16 byte): 00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f Table 3. Avalanche Effect for fixed key 128 bit Case 2:Here the plaintext is always constant and the key will be changed by 1 bit. Input plaintext (16 bytes): ABCDEFGHIJKLMNOP No Plaintext (Alphabet) Ciphertext (Hex.) Bit variance Avalanche (%) 1 ABCDEFGHIJKLMNOP 9CDD85DE85B48BED892F02D 8A5CBDACB 63 49.222 ABCDEFGHIJKLMNOQ ACE7083761553A6B3A97BCB1 740B176A 3 ABCDEFGHIJKLMNOB 0026D76C52B61B9A76445035F D4D342B 69 53.914 ABCDEFGHIJKLMNOC E930AC10030FA5DB617AF6DF A741ADE4 5 ABCDEFGHIJKLMNOS DA5D2C1E67818646AC2D955E 0FAB4C3B 61 47.666 ABCDEFGHIJKLMNOR 7A6EEC02FCADA2FB323D672 B3D2EF396](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-7-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 79 128 bit key and different plaintext pair with difference of 1 bit and in case 2 (table 10) we take fixed plaintext and pair of keys with difference 1 bit. In each pair it shows a good degree of bit variance. With fixed plaintext and variable key almost all the time it shows avalanche affect more than 50%. Table 11. SAC for AES-256 AES-256 also maintains a good degree of Strict Avalanche Criterion. Table 11 shows that among 8112 sample encryption, in average 4377 times it maintains SAC means for complementing 1 bit in input plaintext pair, it gives more or equal than 50% change in ciphertext in 4377 times. Figure 5. SAC Property of AES 5. PROPOSED SYSTEM FOR AES 5.1.Changes to Existing System AES is already a secured algorithm beyond all cryptanalysis. For cryptanalysis, hackers always try to find the cipher key by which the cipher text can be decrypt. In theory, brute force is the most common cryptanalysis, which can be used against all cryptographic algorithms. In brute force attack, hackers search the cipher key among all possible combination of keys. They compute every possible combination of keys and perform a trail decryption for testing if it is the accurate key. Now the question is that, how long time is needed for brute force to find the actual key? The time for brute force attack depends on the key size. If the key size is small, it can be found very quickly. But if the key size is longer, then it may be take very long time to find the actual key[8]. Case Number of Samples Number of samples satisfy SAC Number of samples not satisfy SAC Case 1 8112 4388 3724 Case 2 8112 4311 3801 Case 3 8112 4317 3795 Case 4 8112 4495 3617 Case 5 8112 4375 3737 Average 4377.2 3734.8](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-11-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 80 To increase the brute force attack time in our propose plan of new AES, we increase the key size by 8 bits. That means the existing key size is extended from 128 to 136, 192 to 200 and 256 to 264. This additional 8 bits are generated by a user defined function named getRandKey for encryption and are stored secretly for further use in decryption. The 8 bits key is used in the time of getSBoxValue execution. In getSBoxValue function, the 8 bit random key is Xor’ed the substituted s-box value during the key expansion and the execution of SubBytes step for each round. As a result, the key expansion time increases significantly which makes the brute force attack more time consuming. On the other hand, the additional key also increases the time security more than 2^8 times. To implement our propose plan we have to change the existing AES both for encryption and decryption. 5.2.Encryption 5.2.1getRandKey The getRandKey is a user defined function used in encryption algorithm for our proposed plan in addition with the existing AES. This function is used to generate 8 bits random key. As getRandKey is a user defined function, the consumer can use any kind of random generator to generate the 8 bits random key. The user must have to generate the key before key expansion in main algorithm and store the key for decryption. 5.2.2.getSBoxValue In existing AES, getSBoxValue is a function to substitute a value with a corresponding value in s- box. This function is used during the key expansion and the execution of SubBytes in each round for encryption algorithm. In our propose plan, every time the corresponding s-box value are Xor’ed with the 8 bits key. 5.3.Decryption The cipher text generated by our proposed algorithm can be decrypted by usual AES decryption algorithm using the additional 8 bits key which was generated during encryption algorithm. In proposed AES decryption algorithm the 8 bits key is Xor’ed with each cipher byte before substituting with s-box value and all other task in decryption processes are remain unchanged. 6. SECURITY ANALYSIS OF PROPOSED AES In section3, we have discussed about security measurement criteria for AES cryptosystem. Now, we will measure the security for all 128, 192 & 256 bits proposed AES based on three criteria. 6.1 128 Bit Proposed AES 6.1.1.Time Security In section3, we have calculated that, brute force attack must check maximum 3.403x1038 key combinations for existing AES-128 and it needs almost 3.19 x 1014 years to find the key with the fastest Super Computer of this age. In our proposed AES-128,[12][7] the plaintext block size is 128, key size is 128 and additional random key size is 8. For this additional 8 bits, brute force attack has to check maximum 3.403+E38 x 28 (8.712 x 1040 )key combinations and it needs maximum 3.19+E14 x 28 (8.165 x 1016 ) years to crack the proposed AES-128 with the fastest](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-12-2048.jpg)
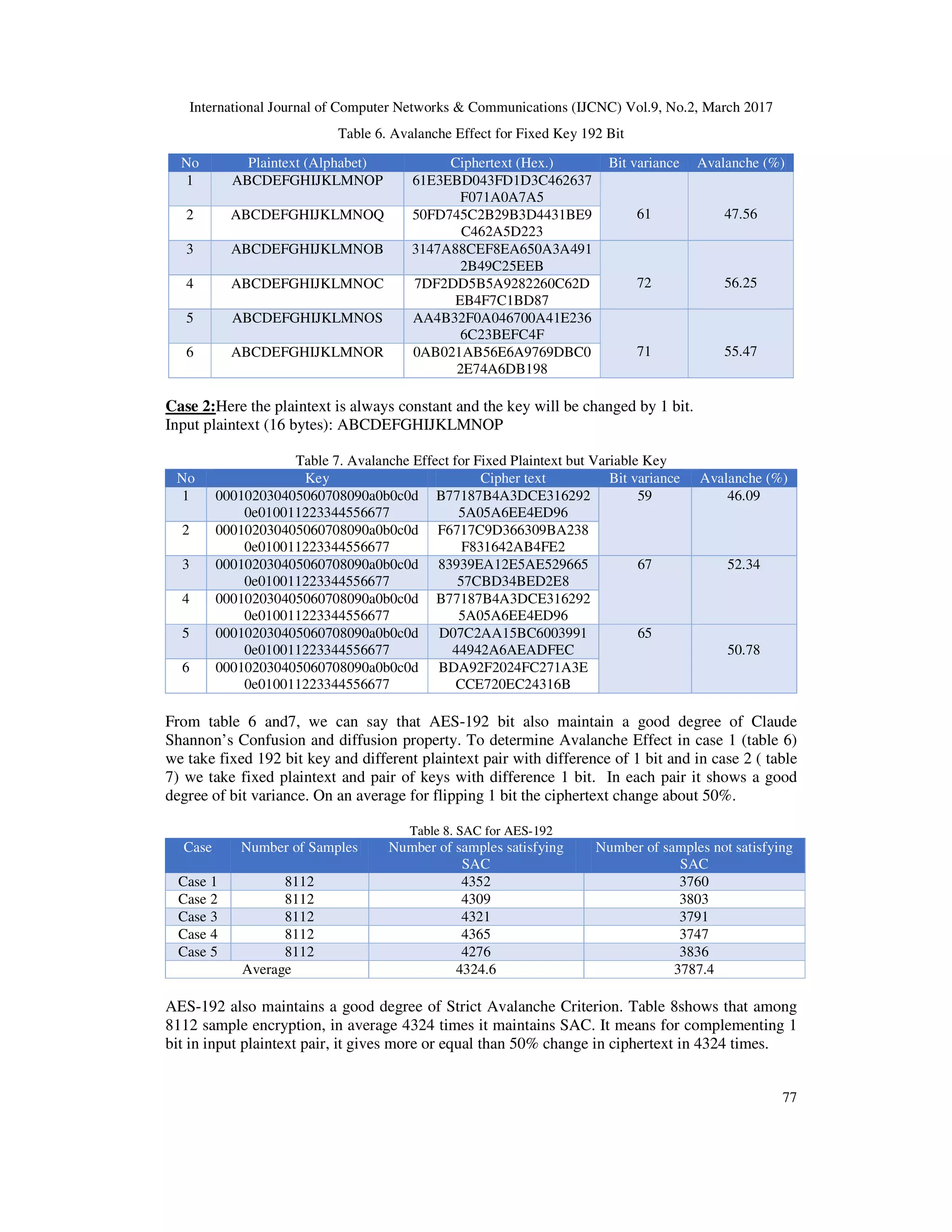
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 81 Super Computer of this age. So, it is not possible for human being to check all the key combination. 6.1.2.Avalanche Effect To compute the avalanche effect of proposed AES-128, we consider two case[18][19] Case 1: Here, the plaintext changes by 1 bit in every experiment, the 128 bit key is always constant and the additional 8bit key is random. Key (16 byte): 00 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F Table 12. Avalanche Effect for Fixed 128 Bit Key and Variable Input Block Case 2:In this case, the plaintext is always constant; the key changes by 1 bit and the additional 8bit key is random. Input plaintext (16 bytes): 00 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 Table 13. Avalanche Effect for Fixed Plaintext but Variable Key No Key Cipher text Bit variance Avalanche (%) 01 ABCDEFGHIJKLMAAB 0FBF2E621156D6D4388304 C11496166C 70 54.69 02 ABCDEFGHIJKLMAAC 332AAF8DEF11A6F2B3D49 5341E5EECD3 03 ABCDEFGHIJKLMAAR 8B84E4D40048BD63E6EB0F 712EA825C2 61 47.66 04 ABCDEFGHIJKLMAAS A05F3A439058794D33548D B7B5AE2EE6 05 ABCDEFGHIJKLMAEJ FB8A1570B3A4400212C958 2384DB3FE6 73 57.03 06 ABCDEFGHIJKLMAEK CE7228908E0F971E832F1FE 963B443D5 Table 12 shows that, single bit variance in input plaintext shows a large number of bit variance in output. Again table 13 also shows that, single bit variance in 128 bit key shows a large number of bit variance in output. After all from both table we can say that, our proposed AES-128 maintains a good degree of Claude Shannon’s Confusion and Diffusion property. No Plaintext (Alphabet) Ciphertext (Hex.) Bit variance Avalanche (%) 1 ABCDEFGHIJKLMAAB AB008578C77D2A09C0D9963 631CD158B 63 49.22 2 ABCDEFGHIJKLMAAC 2CA28FF350D43C76EA63009 0F6BD5CB1 3 ABCDEFGHIJKLMAAP 393A42E7681CA8659B48DA2 022771CD7 72 56.25 4 ABCDEFGHIJKLMAAQ FF59F19913AD598154775653 87D36494 5 ABCDEFGHIJKLMABT 8E61F8C978621C3397120176 FEEB1B65 73 57.03 6 ABCDEFGHIJKLMABU 332B18222296ABEABC2F90 A581C7AA59](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-13-2048.jpg)
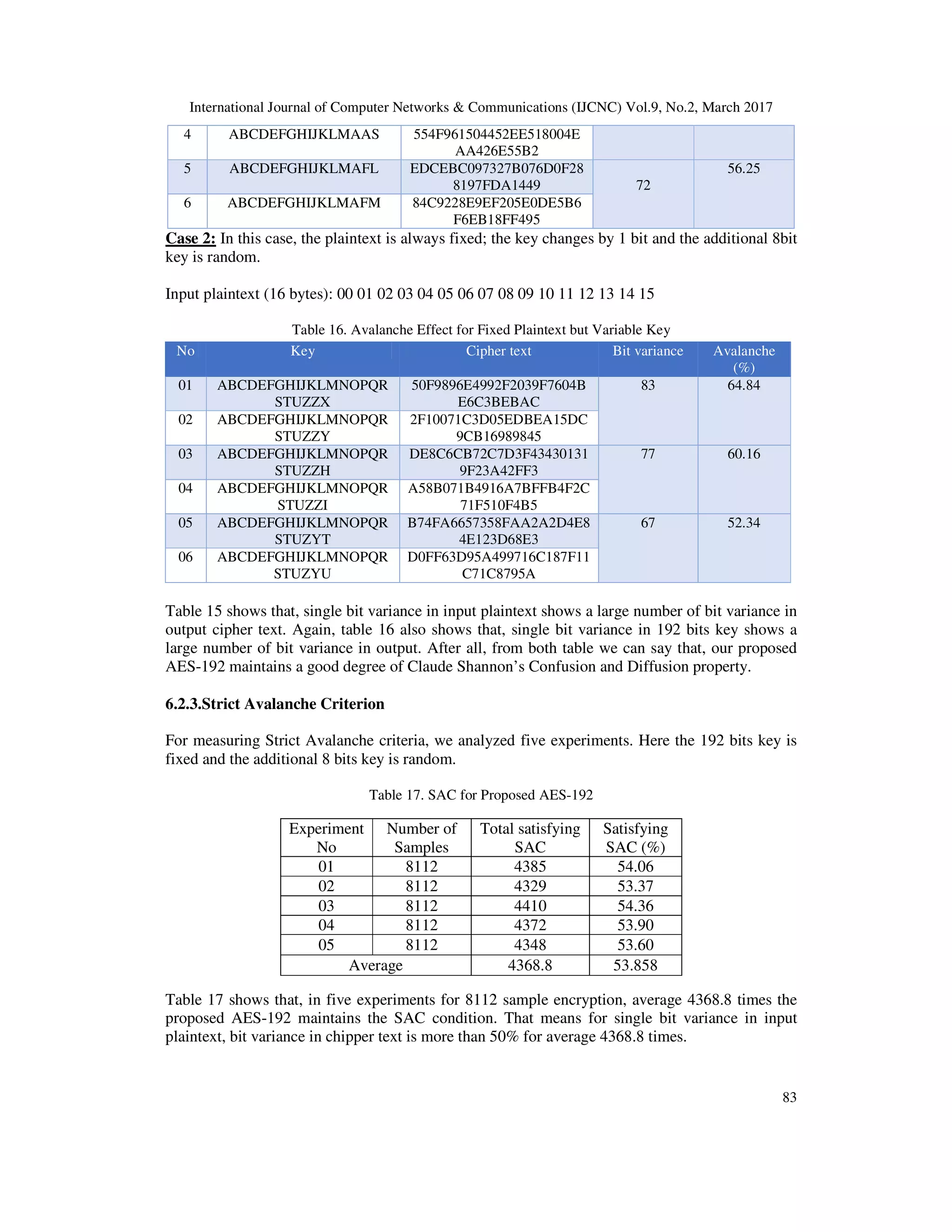
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 82 6.2.4.Strict Avalanche Criterion For measuring Strict Avalanche criteria, we analyzed five experiments. Here the 128 bits key is fixed and the additional 8 bits key is random. Table 14. SAC for Proposed AES-128 Table 14 shows that, in five experiments for 8112 sample encryption, average 4347 times the proposed AES-128 maintains the SAC condition. That means for single bit variance in input plaintext, bit variance in chipper text is more than 50% for average 4347 times. 6.2 192 Bits Proposed AES 6.2.1.Time Security For existing AES-192 we have calculated in section3 that, brute force attack has to check maximum 6.278 x 1057 key combinations to find the key and it needs almost 5.88 x 10 33 years to crack AES-192 [1]with the fastest Super Computer of this age. In our proposed AES-192, the plaintext block size is 128, key size is 192 and additional random key size is 8. For this additional 8 bits, brute force attack has to check maximum6.278+E57 x 28 (1.607 x 1060 ) key combinations to find the key and it needs maximum 5.88+E33 x 28 (1.505 x 1036 ) years to crack the proposed AES- 192 with the fastest Super Computer of this age. So, it is not possible for human being to check all the key combination. 6.2.2.Avalanche Effect To compute the avalanche effect of proposed AES-192, we consider two cases. Case 1: Here, the plaintext changes by 1 bit in every experiment, the 192 bit key is always fixed and the additional 8 bit key is random. Key (24 byte): 00 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F FF EE DD CC BBAA 99 88 Table 15. Avalanche Effect for Fixed 192 Bit Key and Variable Input Block Exp. No Number of Samples Total satisfying SAC Satisfying SAC (%) 1 8112 4353 53.66 02 8112 4361 53.76 03 8112 4333 53.42 04 8112 4366 53.82 05 8112 4322 53.27 Average 4347 53.587 No Plaintext (Alphabet) Cipher text (Hex.) Bit variance Avalanche (%) 1 ABCDEFGHIJKLMAAH 967F4C15877D78715A3570 D7056E6B6F 61 47.66 2 ABCDEFGHIJKLMAAI 41DAC48B55ACE7D2A473 7BF31224437D 3 ABCDEFGHIJKLMAAR E655CB7A0438DC3E9302A D6B92C0CC6D 68 53.13](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-14-2048.jpg)
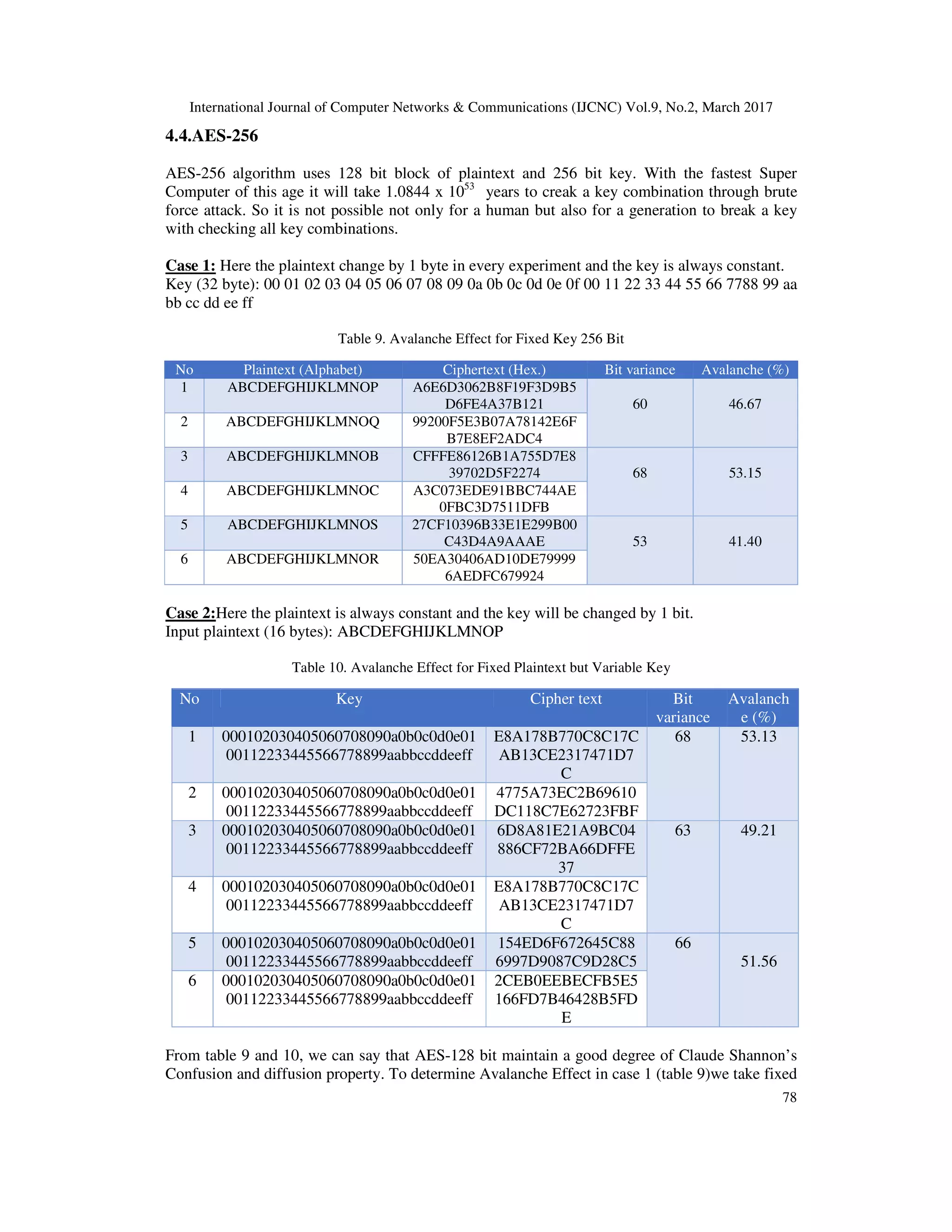
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 84 6.3 256 Bit Proposed AES 6.3.1 Time Security For existing AES-256 brute force attack checks maximum 1.158 x 1077 key combinations to find the key and it needs almost 5.88 x 10 33 years to crack AES-256 with the fastest Super Computer of this age. In our proposed AES-256, the plaintext block size is 128, key size is 256 and additional random key size is 8. For this additional 8 bits, brute force attack has to check maximum 1.158+E77 x 28 (2.965 x 1079 ) key combinations to find the key and it needs maximum 1.0844+E53 x 28 (2.776 x 1055 ) years to crack the proposed AES-256[15][12]with the fastest Super Computer of this age. So, it is not possible for human being to check all the key combinations. 6.3.2 Avalanche Effect To compute the avalanche effect of proposed AES-256, we consider two cases. Case 1: Here, the plaintext changes by 1 bit in every experiment, the 256 bit key is always fixed and the additional 8 bits key is random. Key (32 byte): 00 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F FF EE DD CC BB AA 99 88 77 66 55 44 33 22 11 2A Table 18. Avalanche Effect for Fixed 256 Bit Key and Variable Input Block Case 2: In this case, the plaintext is always fixed; the 256 bit key changes by 1 bit and the additional 8 bits key is random. Input plaintext (16 bytes): 00 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 Table 19. Avalanche Effect for Fixed Plaintext but Variable Key No Key Cipher text Bit variance Avalanche (%) 01 1234ABCDEFGHIJKLMNOP QRSTUVWRXP F74AEE57EFE17B4B35EA 6439665DFD32 71 55.47 02 1234ABCDEFGHIJKLMNOP QRSTUVWRXQ CCC3E46A61368F5457F57 84343EF4F85 03 1234ABCDEFGHIJKLMNOP A9889A3DBC7A893754541 77 60.16 No Plaintext (Alphabet) Cipher text (Hex.) Bit variance Avalanche (%) 1 ABCDEFGHIJKLMYWJ 23EE09863ECF2D1756CA 4F940D183CD0 78 60.94 2 ABCDEFGHIJKLMYWK DC5CFEDE24DA768ACE2 DB1A556E3C802 3 ABCDEFGHIJKLMYVF AE22A21F677E4330D14E B22667351327 71 55.47 4 ABCDEFGHIJKLMYVG 5B3536BD332118FF8BB8 B8DB16F59DFA 5 ABCDEFGHIJKLMXVL 32CE61C5C6A549C9ABB4 51EAA17CAADB 67 52.34 6 ABCDEFGHIJKLMXVM DCAE188970EDD3AF1445 9304135AA5BE](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-16-2048.jpg)
![International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 87 Figure 8. SAC Comparisons between Existing and Proposed AES REFERENCES [1] Guy-Armand Yandji, Lui Lian Hao, Amir-Eddine Youssouf, Jules Ehoussou, “RESEARCH ON A NORMAL FILE ENCRYPTION AND DECRYPTION” in proceedings of IEEE 2011. [2] Hyubgun Lee, Kyounghwa Lee, Yongtae Shin, “AES Implementation and Performance Evaluationon 8-bit Microcontrollers”, International Journal of Computer Science and Information Security,Vol. 6 No. 1, 2009 [3] “Specification for the ADVANCED ENCRYPTION STANDARD (AES)”, Federal Information Processing Standards Publication 197 November 26, 2001 [4] Saberi, I. Shojaie, B. ; Salleh, M. “Enhanced Key Expansion for AES-256 by using Even-Odd method”, Research and Innovation in Information Systems (ICRIIS), 23-24 Nov. 2011 [5] Liam Keliher ,“Substitution-Permutation Network Cryptosystems Using Key-Dependent Boxes”, http://www.researchgate.net/publication/2822741, ARTICLE • NOVEMBER 1997 [6] Krishnamurthy G N and V Ramaswamy, "Making AES Stronger: AES with Key Dependent S-Box." International Journal of Computer Science and Network Security, VOL.8 No.9, September 2008 [7] Mohan H. S. and A Raji Reddy, “ Performance Analysis of AES and MARS Encryption Algorithms”, IJCSI International Journal of Computer Science Issues, Vol. 8, Issue 4, No 1, July 2011 [8] Manisha S. Mahindrakar’ “Evaluation of Blowfish Algorithm based on Avalanche Effect”, International Journal of Innovations in Engineering and Technology (IJIET), Vol. 4 Issue 1 June 2014 [9] Akash Kumar Mandal1, Mrs. Archana Tiwari, “Analysis of Avalanche Effect in Plaintext of DES using Binary Codes”, International Journal of Security, Privacy and Trust Management, Volume 1, Issue 3, September – October 2012 [10] SriramRamanujam and MarimuthuKaruppiah, “Designing an algorithm with high Avalanche Effect”, International Journal of Computer Science and Network Security, VOL.11 No.1, January 2011 [11] K.Anchugam and M.Tamilselvi “New Data Encryption Standard Algorithm” , International Journal of Computer Science and Network Security, VOL.13 No.4, April 2013 [12] M.Abirami, S. Chellaganeshavalli, “Performance Analysis of AES and Blowfish Encryption Algorithm”, International Journal of Innovative Research in Science, Engineering and Technology, Vol. 2, Issue 11, November 2013 [13] AbdulkarimAmerShtewi, BahaaEldin M. Hasan and Abd El Fatah .A. Hegazy,” An Efficient Modified Advanced Encryption Standard (MAES) Adapted for Image Cryptosystems”, International Journal of Computer Science and Network Security, VOL.10 No.2, February 2010 [14] Nidhi Singhal and J.P.S.Raina, Comparative Analysis of AES and RC4 Algorithms for Better Utilization, International Journal of Computer Trends and Technology- July to Aug Issue 2011 [15] M.Abirami, S. Chellaganeshavalli, “Performance Analysis of AES and Blowfish Encryption Algorithm”, International Journal of Innovative Research in Science,Engineering and Technology, Vol. 2, Issue 11, November 2013 [16] Chandra Prakash Dewangan,Shashikant Agrawal, A Novel Approach to Improve Avalanche Effect of AES Algorithm, International Journal of Advanced Research in Computer Engineering & Technology Volume 1, Issue 8, October 2012 [17] Amish Kumar , Mrs. Namita Tiwari, “EFFECTIVE IMPLEMENTATION AND AVALANCHE EFFECT OF AES”, International Journal of Security, Privacy and Trust Management ( IJSPTM), Vol. 1, No 3/4, August 2012](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-19-2048.jpg)
![International Journal of Computer Netw [18] Akash Kumar Mandal, Mrs. Archana Tiwari, “Analysis of Avalanche Effect in Binary Codes”, International Journal of Security, Privacy and Trust Management ( IJSPTM), Volume 1, Issue 3, September – October 2012 [19] Jayant P. Bhoge, Dr. Prashant N. Chatur,” Avalanche Effect of AES Algorithm”, International Jou Computer Science and Information Technologies, Vol. 5 (3), 2014, 3101 [20] Opala, Omondi John; Rahman, Shawon; and Alelaiwi, Abdulhameed; “The Influence of Information Security on the Adoption of Cloud computing: An Exploratory Analysis”, In Computer Networks & Communications (IJCNC), Vol.7, No.4, July 2015 [21] Rader, A., Marc and Rahman, Syed (Shawon); “Exploring Historical and Emerging Phishing Techniques and Mitigating the Associated Security Risks”; International Jo Applications (IJNSA), ISSN:0974 [22] Opala, John, Omondi; Rahman, Shawon and Alelaiwi, Abdulhameed ; “An Analysis on the Factors Influencing Managers’ Decision to Adopt of Cloud Computing”; " Handbook Trends in Service-Driven Computing" IGI Global in 2014,DOI: 10.4018/978 Authors Abdullah Al- Mamun: Abdullah Al & Engineering in Jessore University of Science & Technolo graduation degree in CSE from same university in 2015. His research focus is on information security, cloud technology and specially on encryption technology. Mamun has two years of work experience in the field of web application development. Dr. Shawon Rahman: Dr. Shawon S. M. Rahman is an Associate Professor in the Department of Computer Science at the Rahman’s research interests include Engineering education, Software Testing & QA, Cloud Computing, Mobile Application Development, and Web Accessibility. He has published over 100 peer-reviewed articles and is a member of many professional organizations including IEEE, ACM, ASEE, ASQ, ISACA, and UPE. Tanvir Ahmed Shaon: Tanvir Ahmed Shaon has earned his master’s degree in Computer Science and Engineering from Military institute of science and technology. His research focus is on Ad BSc in Computer Science and Engineering in the field of web technology Md Alam Hossain: Md. Alam Hossain is working as an Assistant Professor at the department of Computer Science & Engineering in Jessore University of Science & Technology (JUST), Jessore, Bangladesh. Prior to that, he joined as Lecturer at the same department. He completed his B.Sc a & Engineering from Islamic University, Kushtia, Bangladesh. Currently he is pursuing PhD on Cloud Computing Security. His research interest fields are Cloud Computing, Cloud Computing Architecture, Cloud Computing Secur Cloud Computing Application Services and Quality, Cyber Security, Banking Solutions Security, Network Security, Digital Forensic Science, Steganography, Information Security, Internet Security. International Journal of Computer Networks & Communications (IJCNC) Vol.9, No.2, March 2017 Akash Kumar Mandal, Mrs. Archana Tiwari, “Analysis of Avalanche Effect in Plaintex of DES using Binary Codes”, International Journal of Security, Privacy and Trust Management ( IJSPTM), Volume 1, October 2012 Jayant P. Bhoge, Dr. Prashant N. Chatur,” Avalanche Effect of AES Algorithm”, International Jou Computer Science and Information Technologies, Vol. 5 (3), 2014, 3101 – 3103 Opala, Omondi John; Rahman, Shawon; and Alelaiwi, Abdulhameed; “The Influence of Information Security on the Adoption of Cloud computing: An Exploratory Analysis”, International Journal of Computer Networks & Communications (IJCNC), Vol.7, No.4, July 2015 Rader, A., Marc and Rahman, Syed (Shawon); “Exploring Historical and Emerging Phishing Techniques and Mitigating the Associated Security Risks”; International Journal of Network Security & Its Applications (IJNSA), ISSN:0974-9330(online); 0975-2307 Opala, John, Omondi; Rahman, Shawon and Alelaiwi, Abdulhameed ; “An Analysis on the Factors Influencing Managers’ Decision to Adopt of Cloud Computing”; " Handbook of Research on Architectural Driven Computing" IGI Global in 2014,DOI: 10.4018/978-1-4666-6178-3 Abdullah Al- Mamun is doing MSc in Computer Science & Engineering in Jessore University of Science & Technology. He earned his graduation degree in CSE from same university in 2015. His research focus is on information security, cloud technology and specially on encryption technology. Mamun has two years of work experience in the field of web application : Dr. Shawon S. M. Rahman is an Associate Professor in the Department of Computer Science at the Majmaah University, Majmaah, KSA. Dr. research interests includeInformation Assurance and Security, Software ion, Software Testing & QA, Cloud Computing, Mobile Application Development, and Web Accessibility. He has published over 100 reviewed articles and is a member of many professional organizations including IEEE, ACM, ASEE, ASQ, ISACA, and UPE. Tanvir Ahmed Shaon has earned his master’s degree in Computer Science and Engineering from Military institute of science and technology. His research focus is on Ad-hoc network security. He also holds an BSc in Computer Science and Engineering. Shaon has two years’ work experience Md. Alam Hossain is working as an Assistant Professor at the department of Computer Science & Engineering in Jessore University of Science & , Bangladesh. Prior to that, he joined as Lecturer at the same department. He completed his B.Sc and M.Sc (Thesis) in Computer Science & Engineering from Islamic University, Kushtia, Bangladesh. Currently he is pursuing PhD on Cloud Computing Security. His research interest fields are Cloud Computing, Cloud Computing Architecture, Cloud Computing Security Issues, Cloud Computing Application Services and Quality, Cyber Security, Banking Solutions Security, Network Security, Digital Forensic Science, Steganography, Information Security, Internet Security. orks & Communications (IJCNC) Vol.9, No.2, March 2017 88 Plaintex of DES using Binary Codes”, International Journal of Security, Privacy and Trust Management ( IJSPTM), Volume 1, Jayant P. Bhoge, Dr. Prashant N. Chatur,” Avalanche Effect of AES Algorithm”, International Journal of Opala, Omondi John; Rahman, Shawon; and Alelaiwi, Abdulhameed; “The Influence of Information ternational Journal of Rader, A., Marc and Rahman, Syed (Shawon); “Exploring Historical and Emerging Phishing Techniques urnal of Network Security & Its Opala, John, Omondi; Rahman, Shawon and Alelaiwi, Abdulhameed ; “An Analysis on the Factors of Research on Architectural 3](https://image.slidesharecdn.com/9217cnc06-170411121743/75/Security-Analysis-of-AES-and-Enhancing-its-Security-by-Modifying-S-Box-with-an-Additional-Byte-20-2048.jpg)