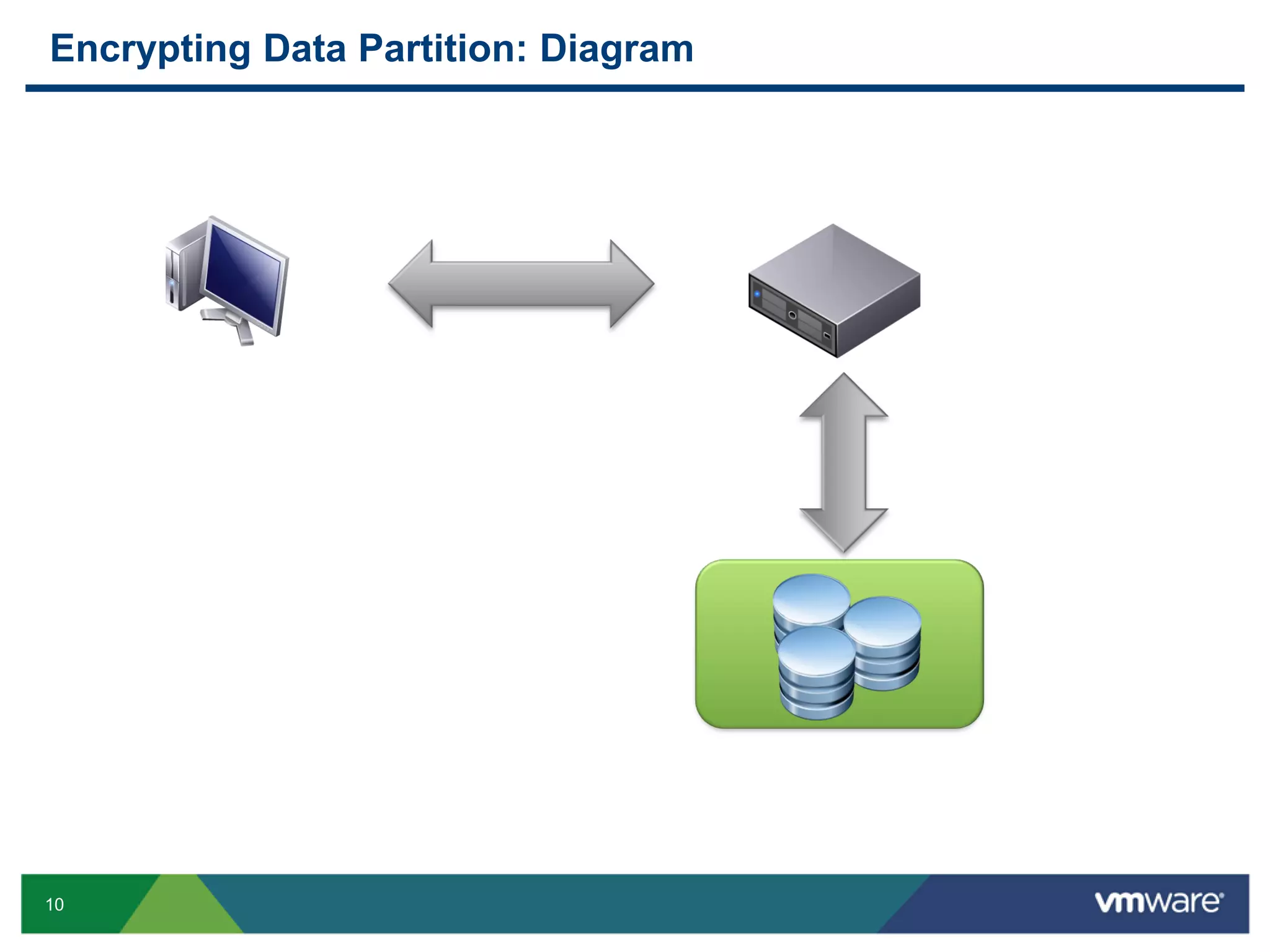
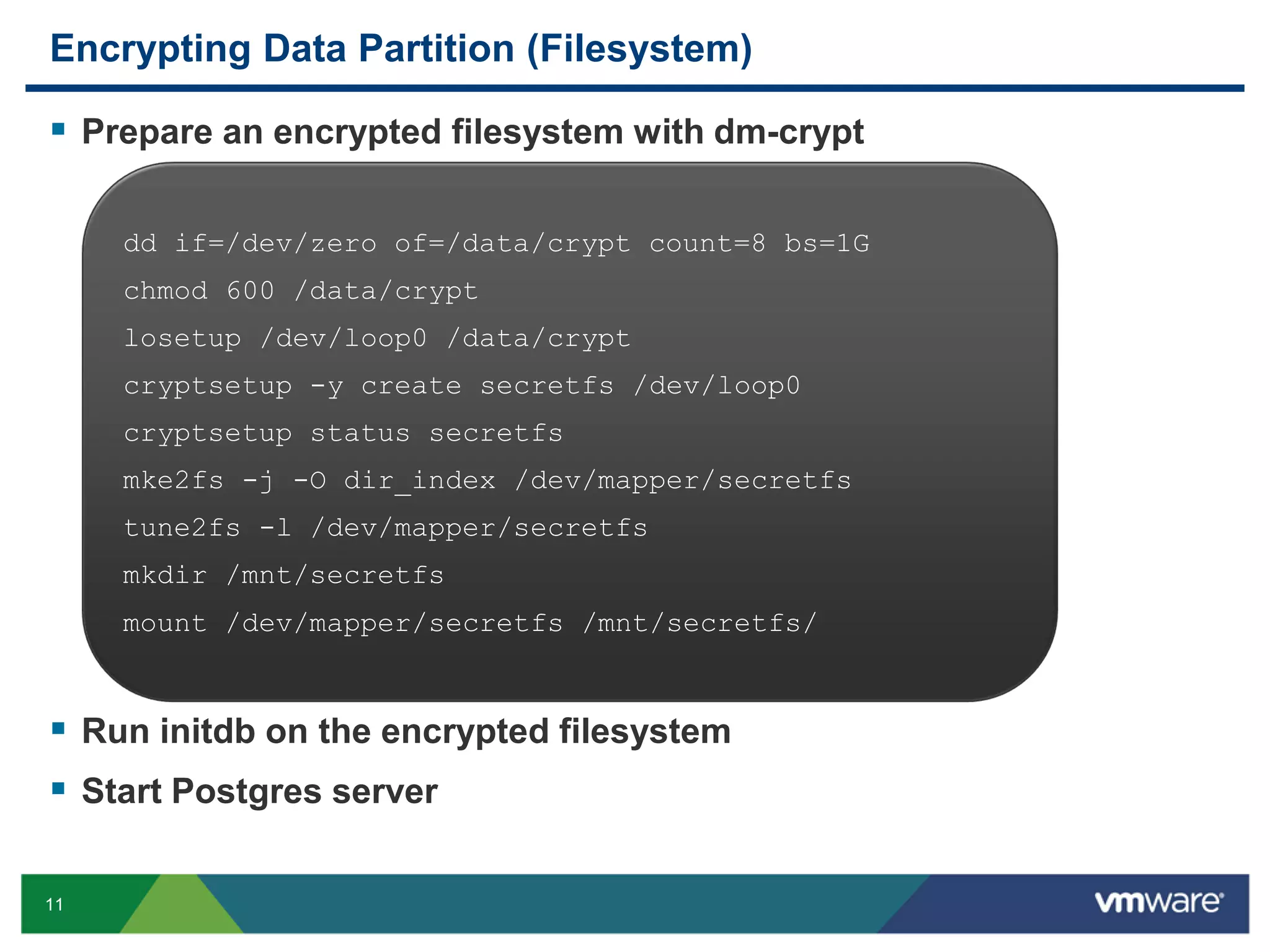
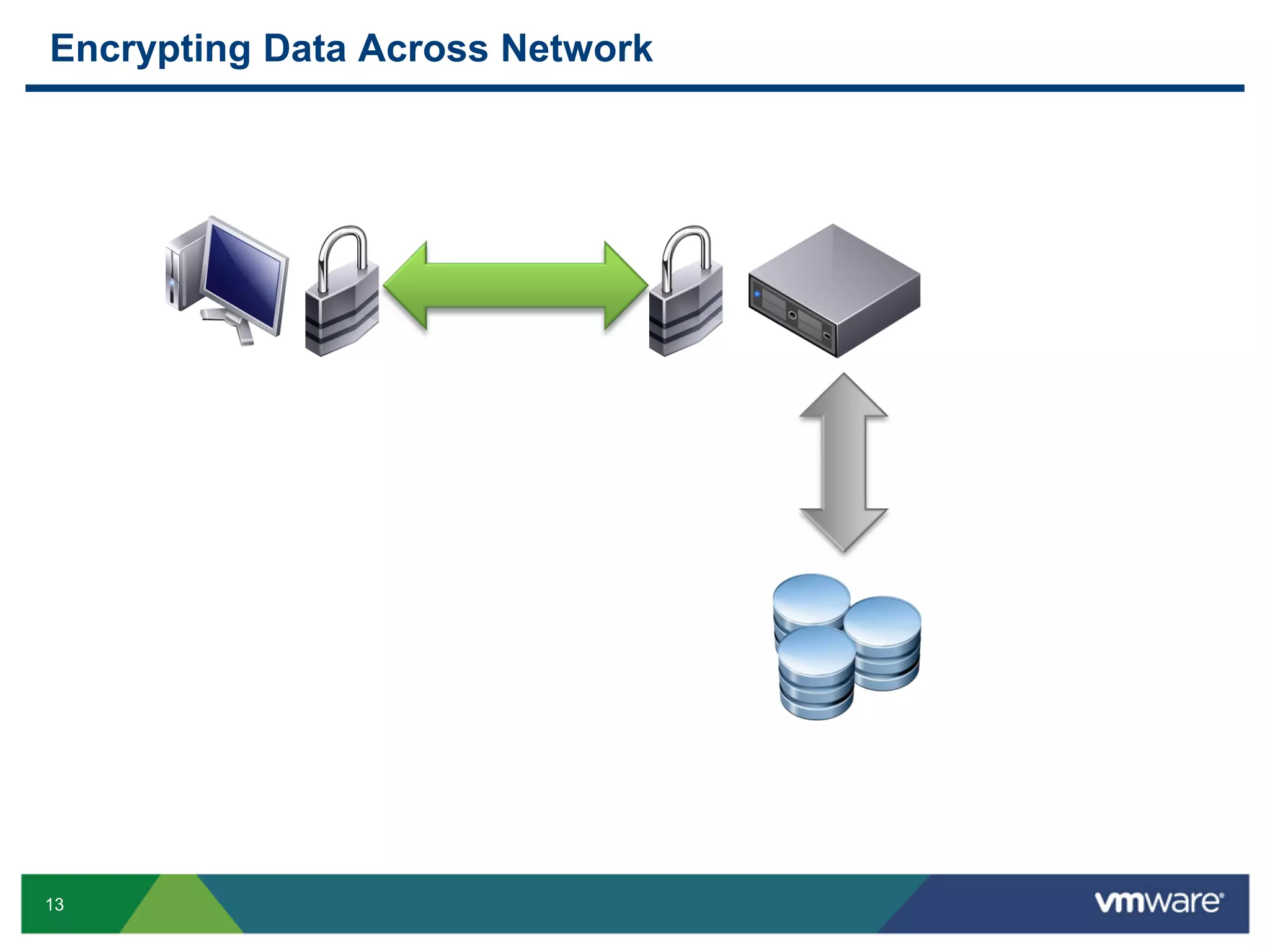
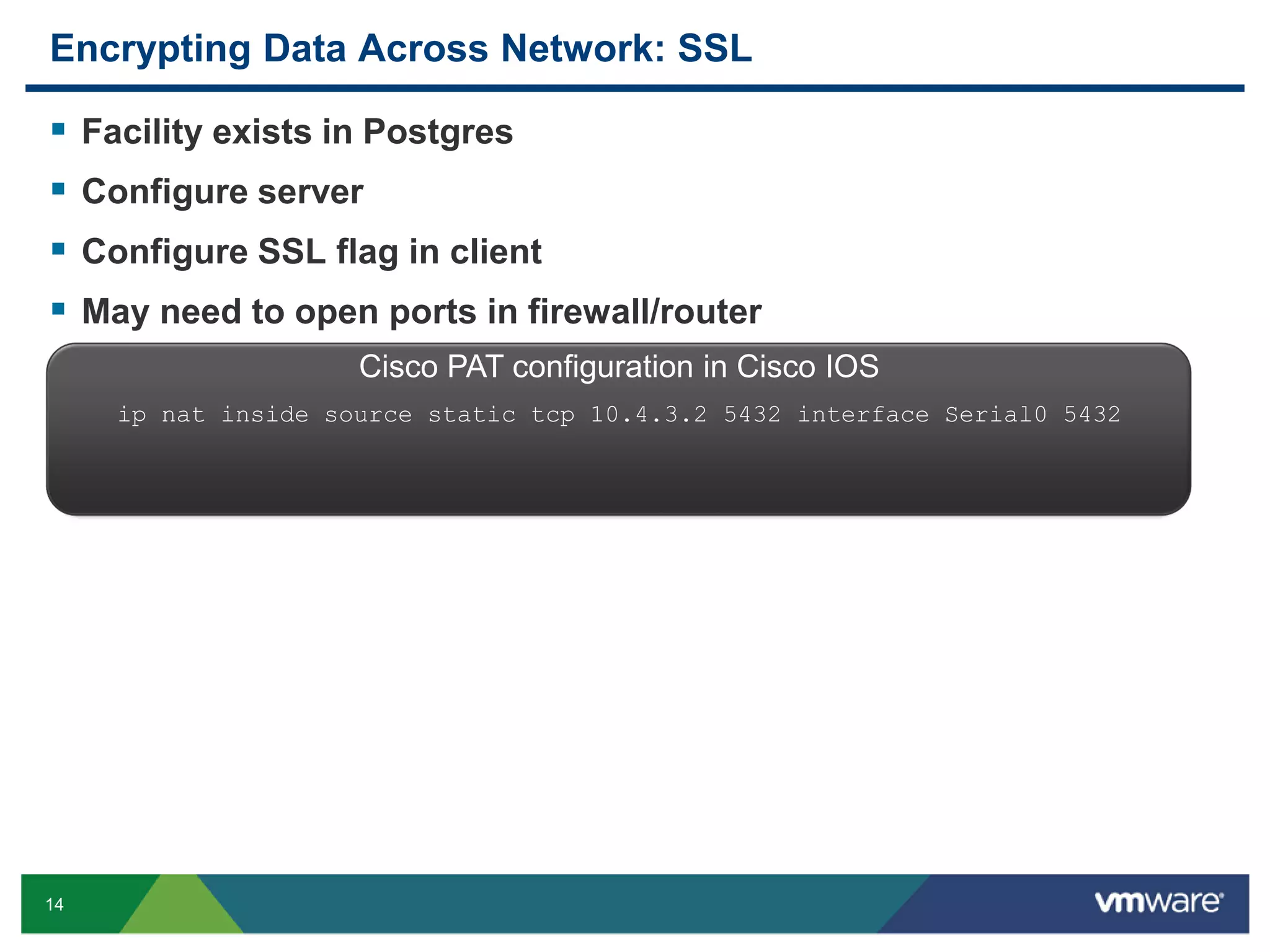
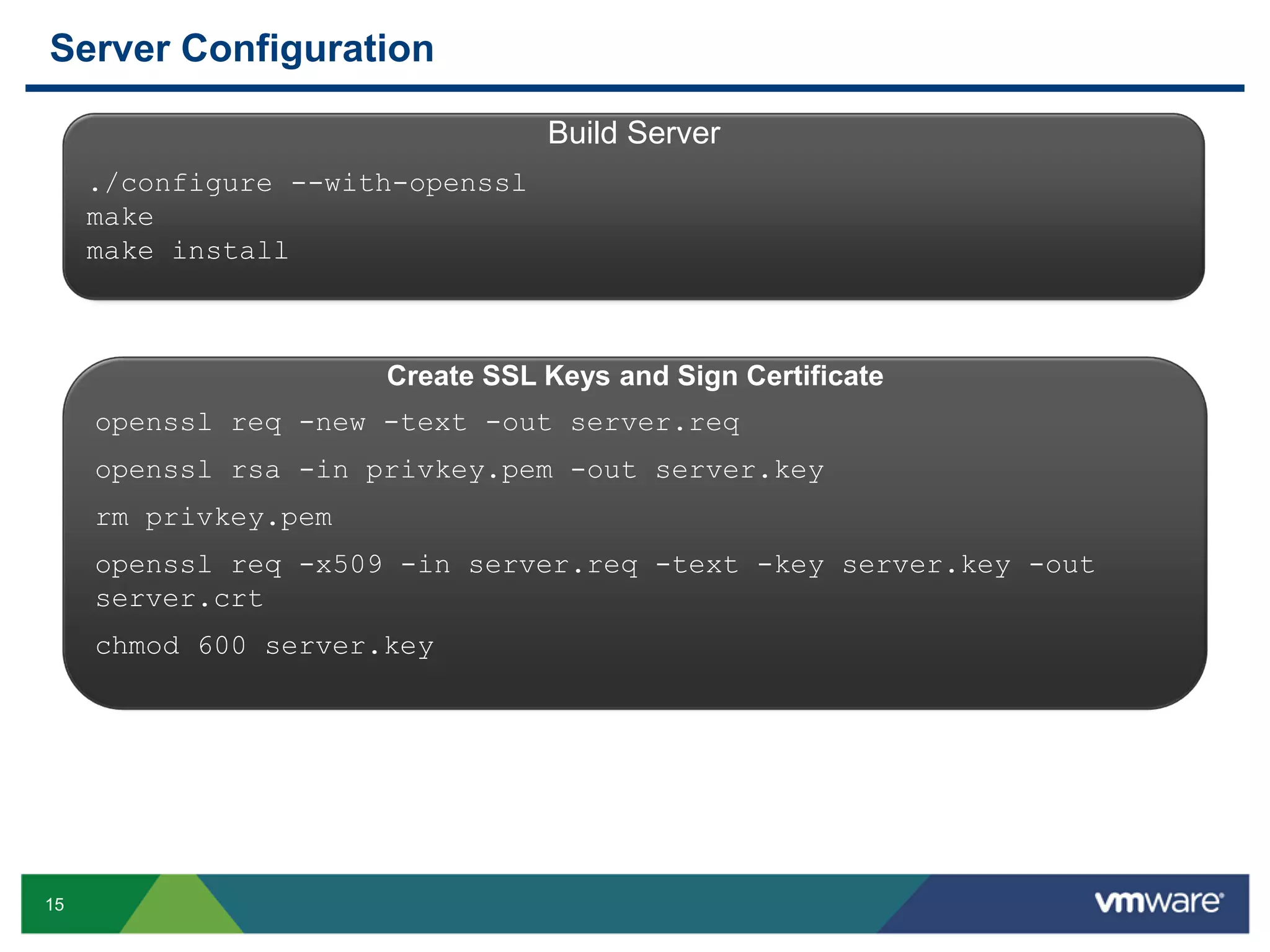
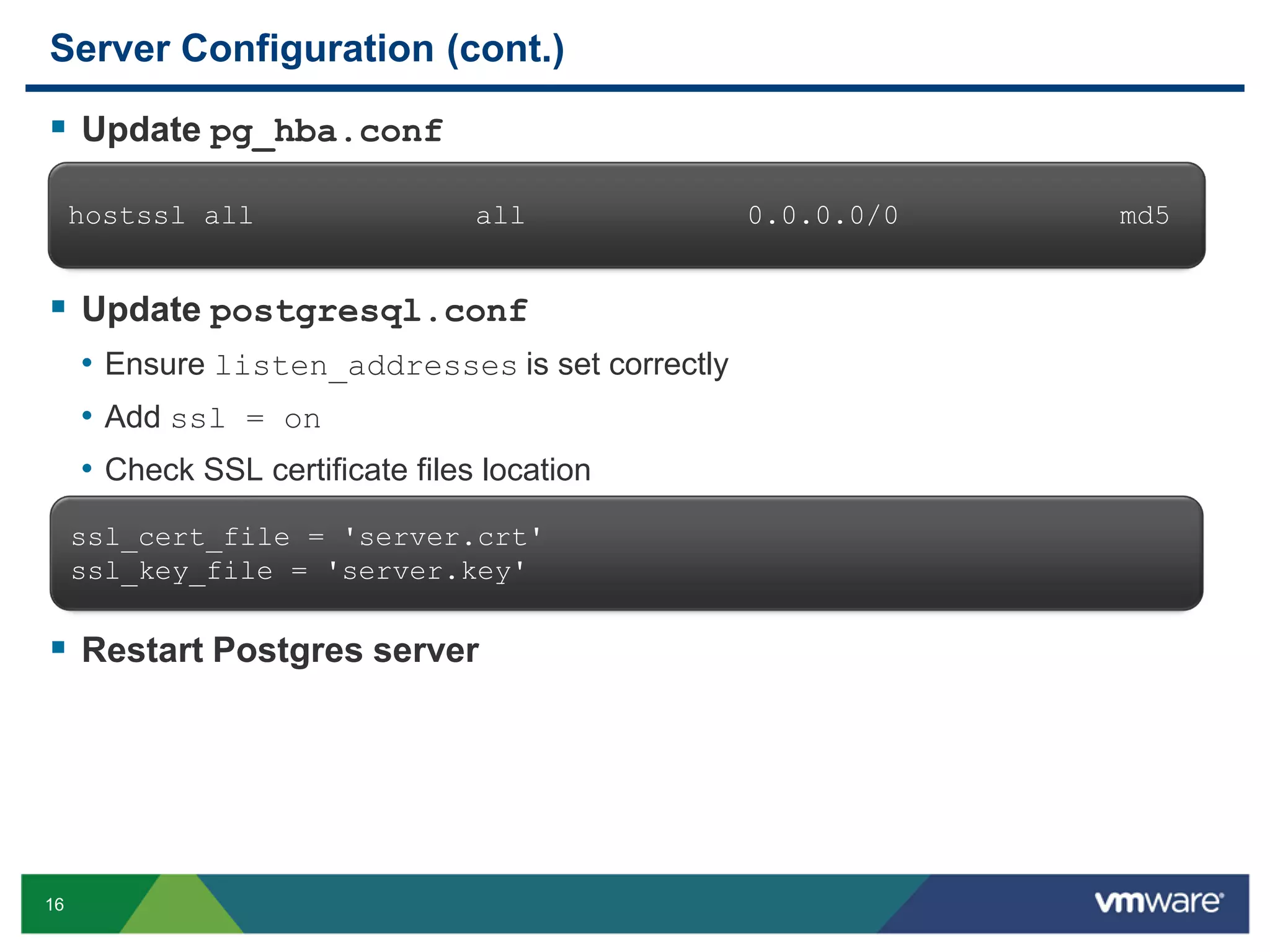
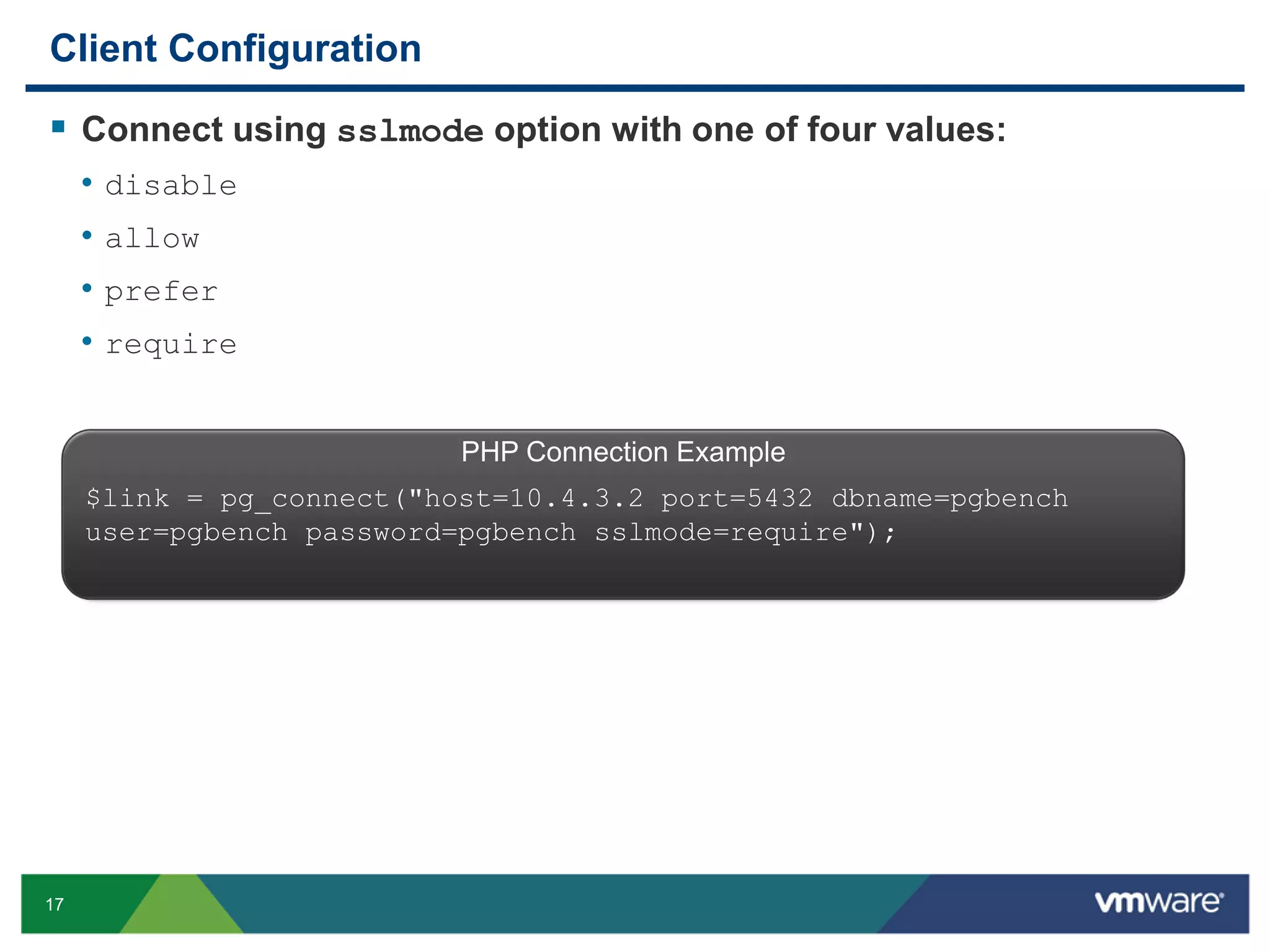
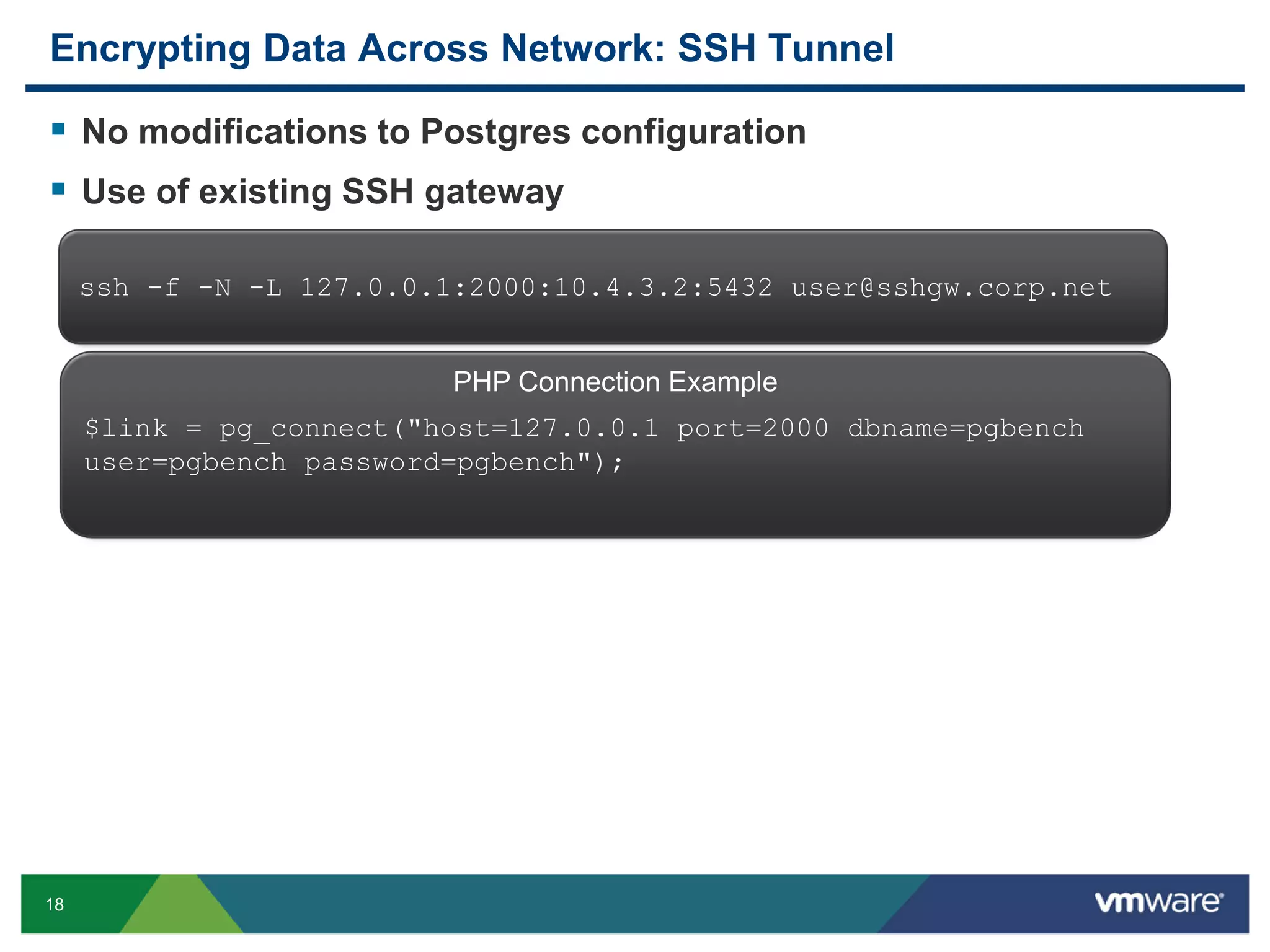
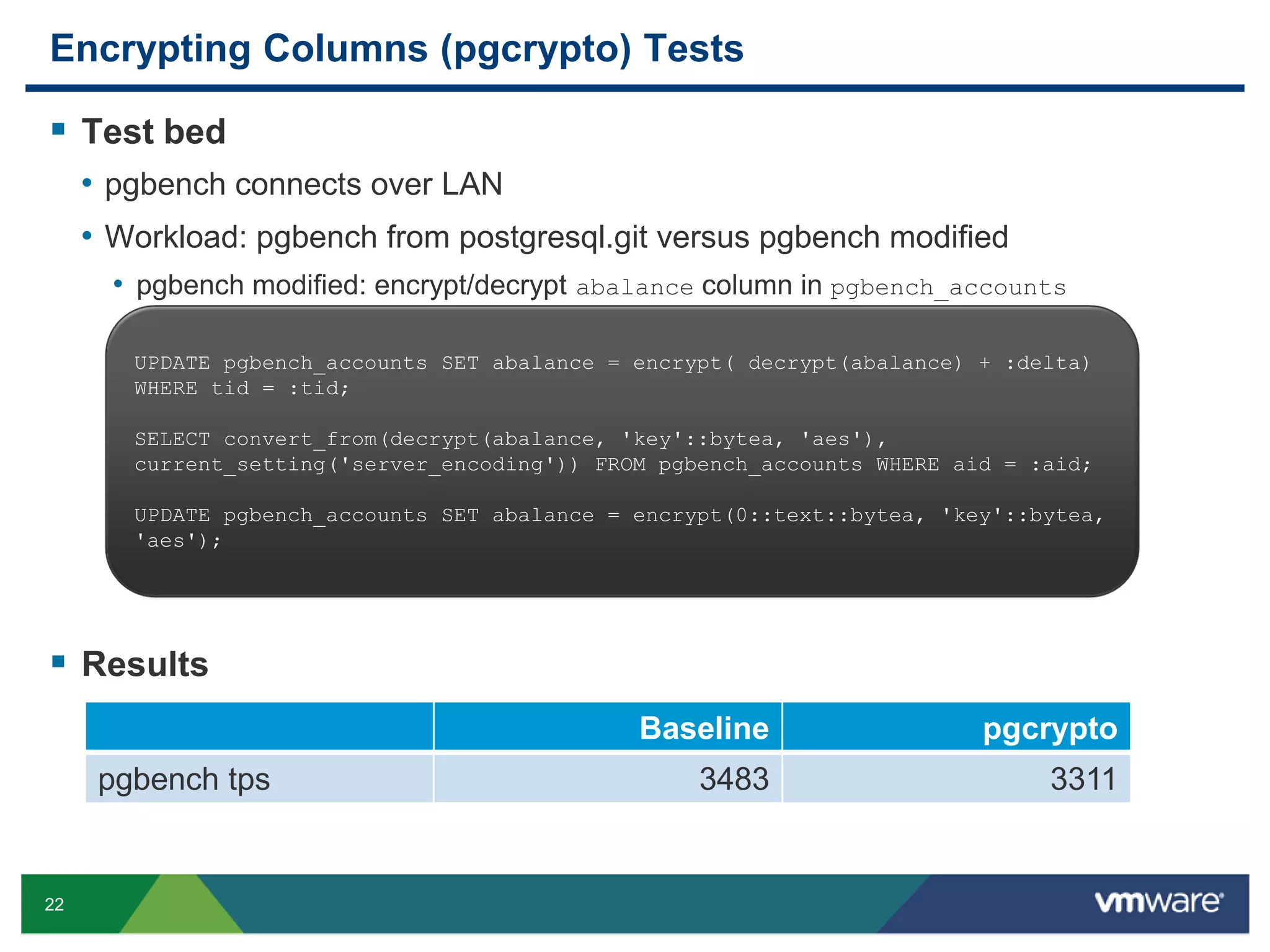
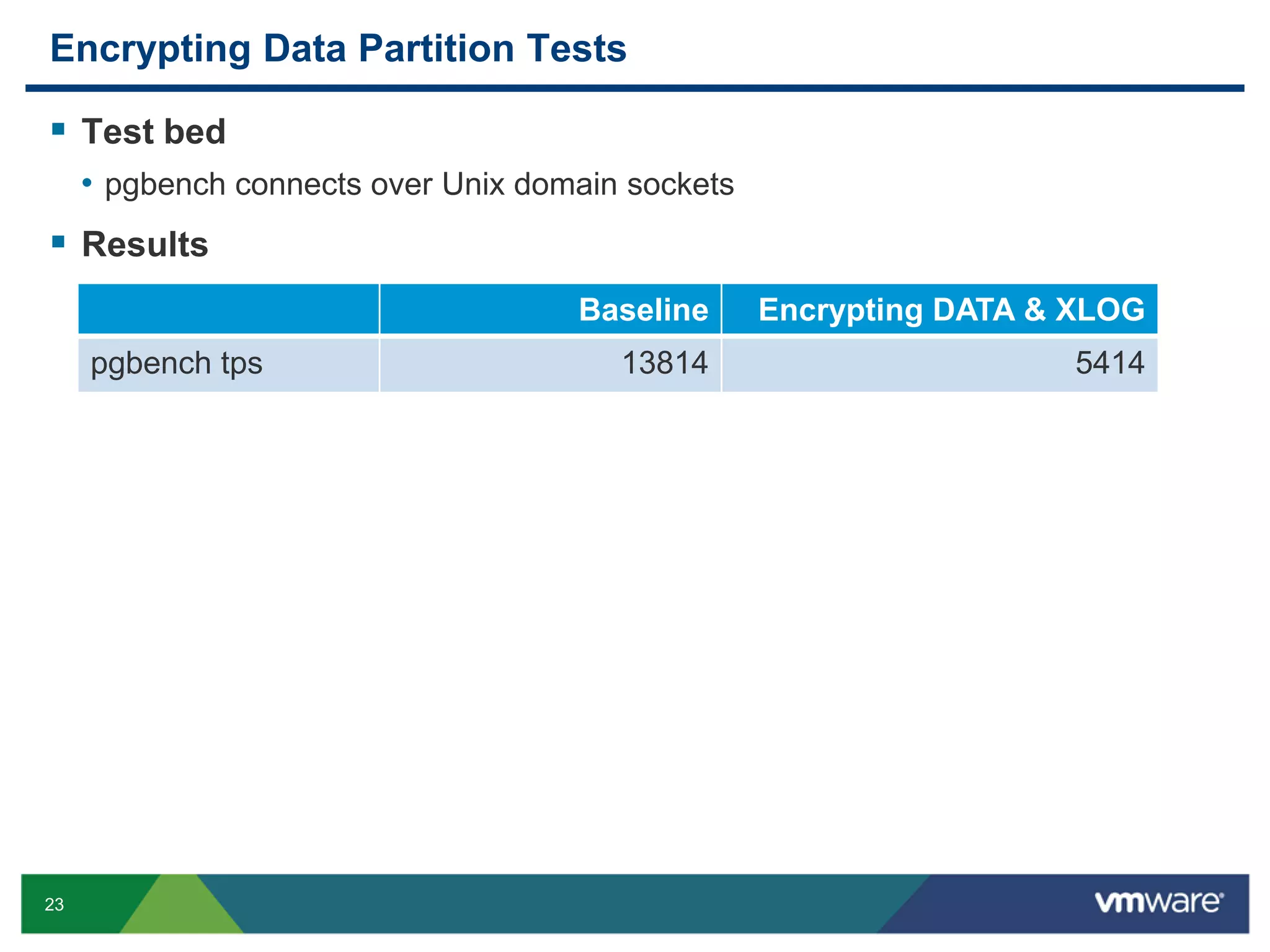
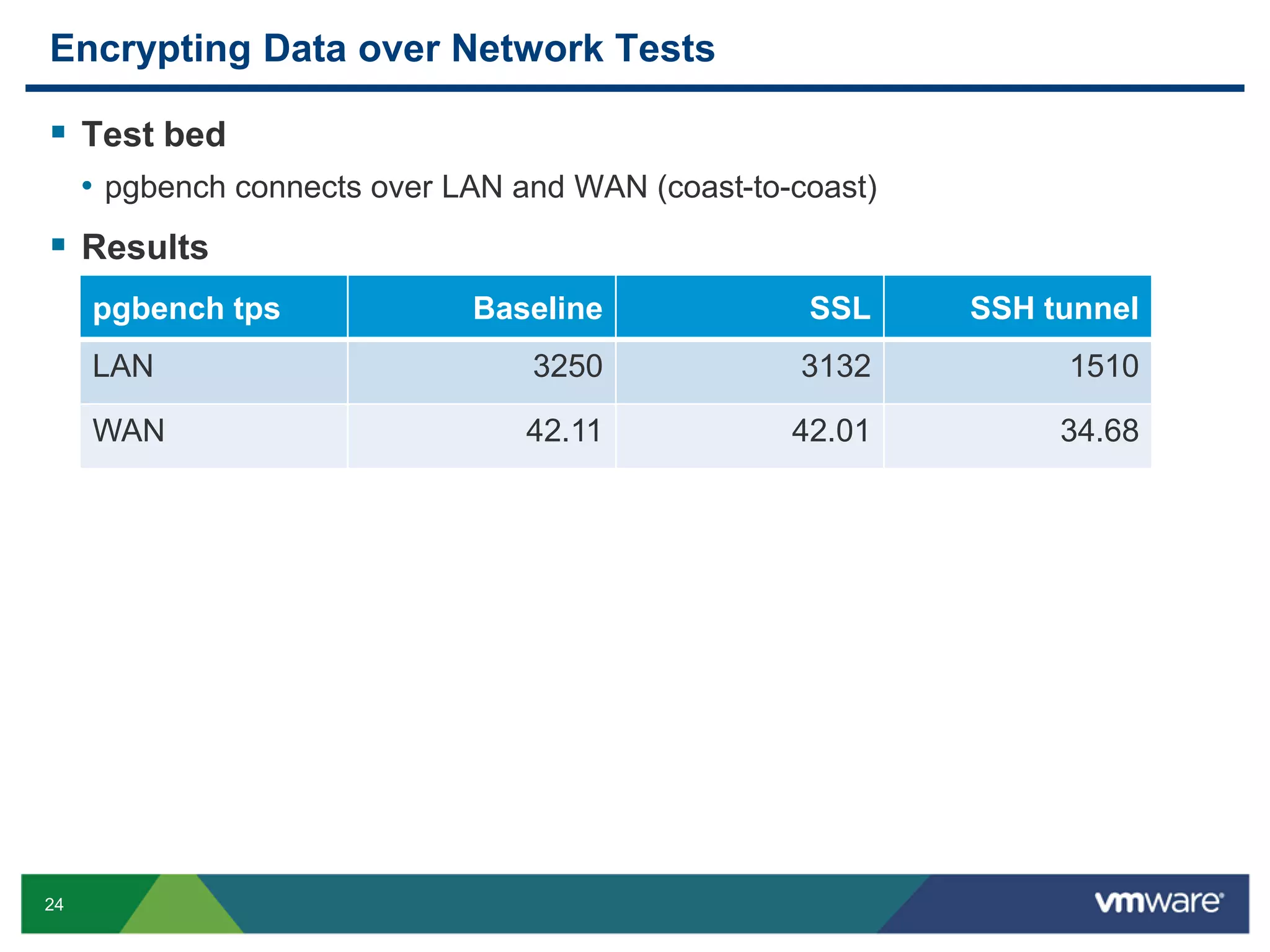
The document discusses various PostgreSQL encryption options, emphasizing the importance of encrypting sensitive data for compliance and security. It covers methods such as column encryption using pgcrypto, encrypting data partitions, and securing data in transit with SSL or SSH tunneling. Performance benchmarks and real-world use cases demonstrate the practical application of these encryption techniques in scenarios like e-commerce and patient information management.