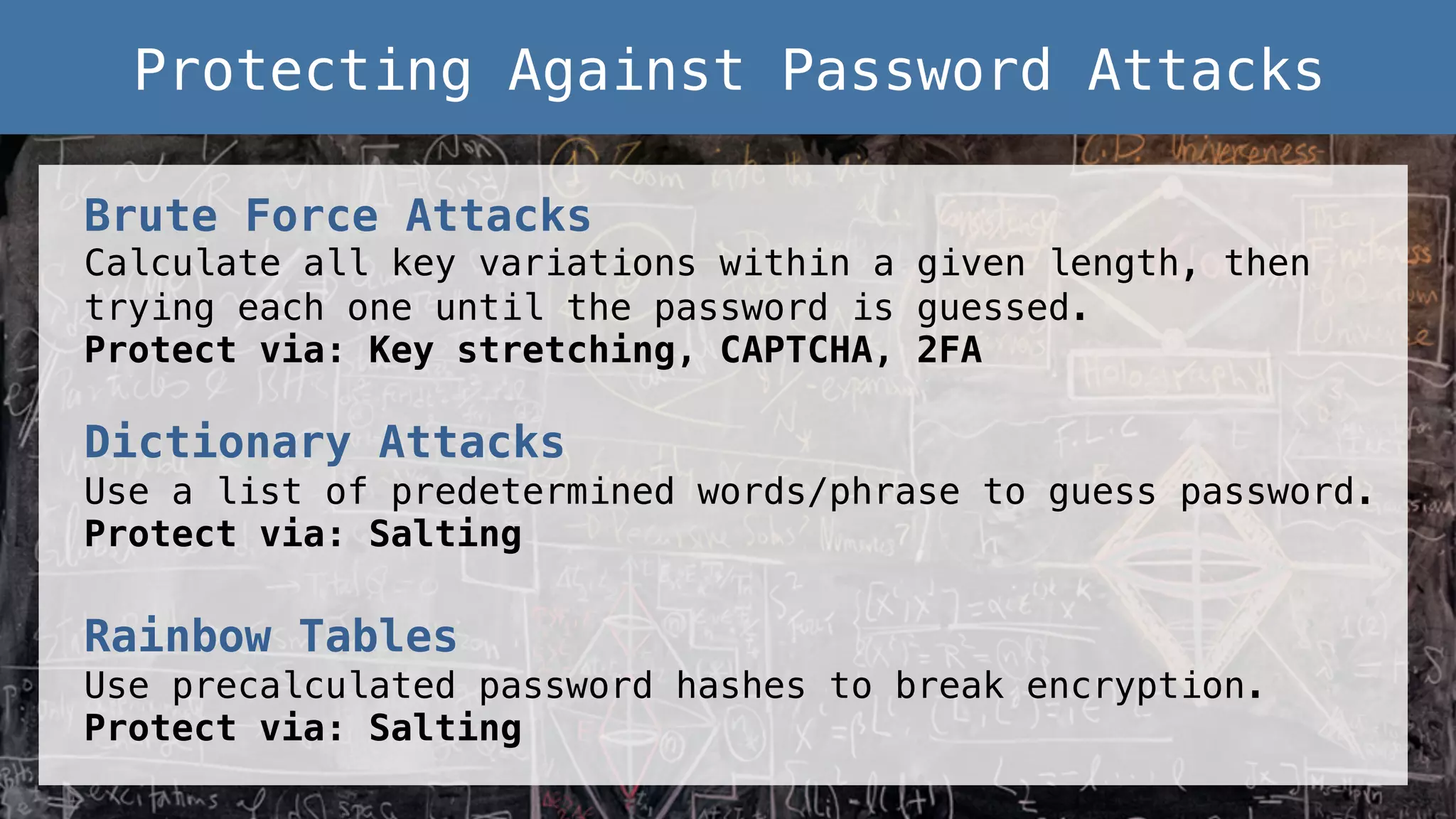
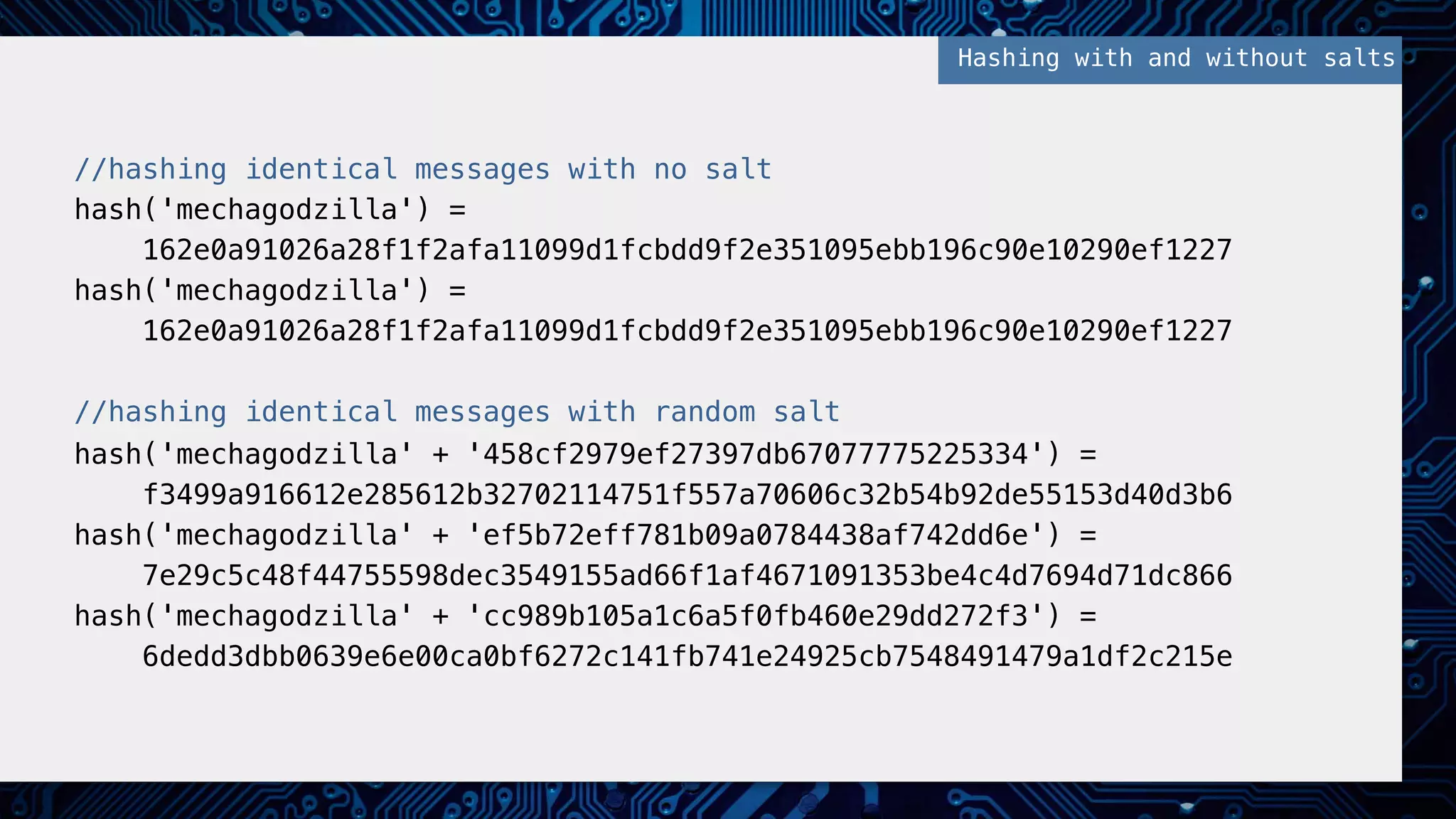
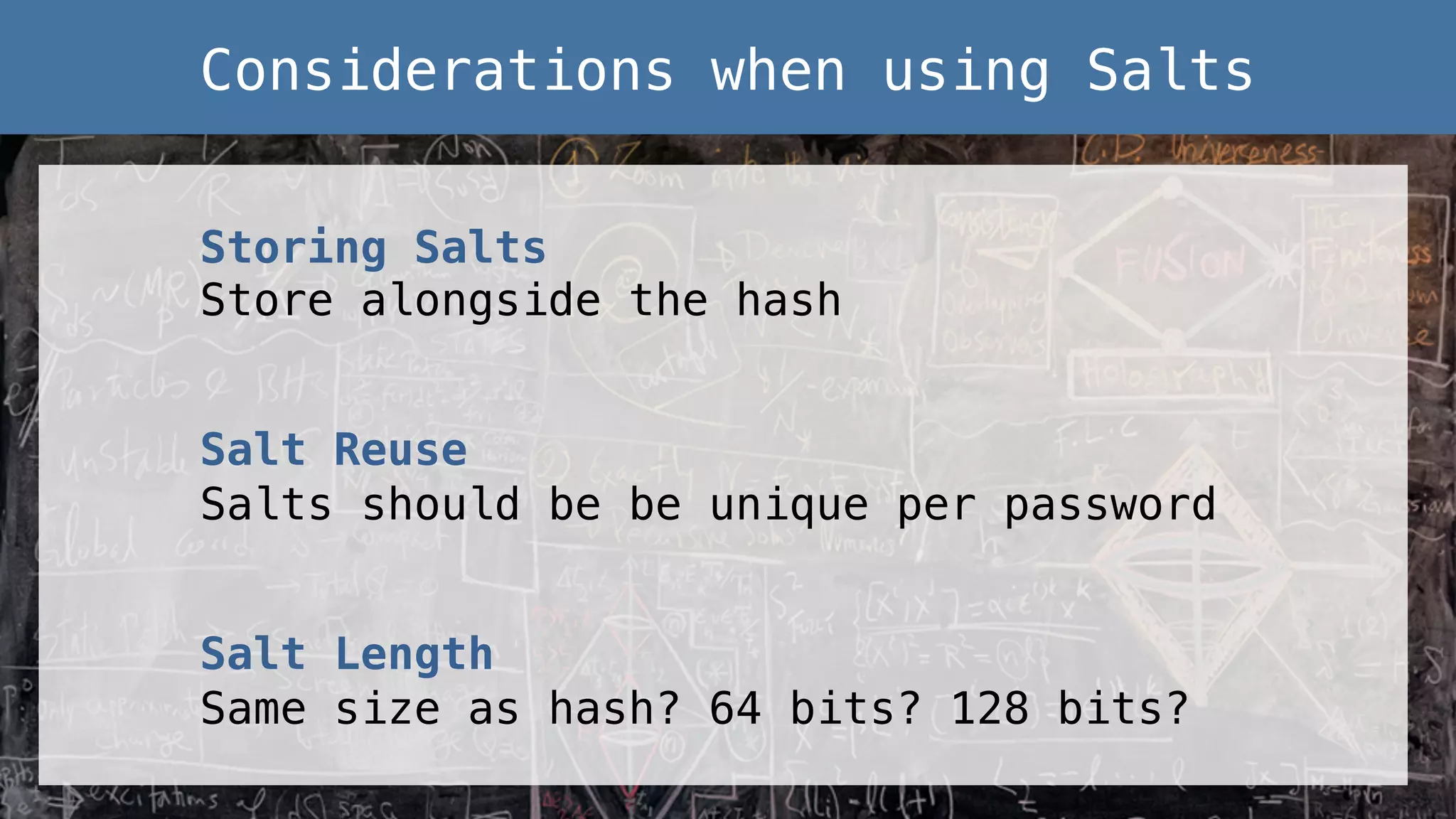
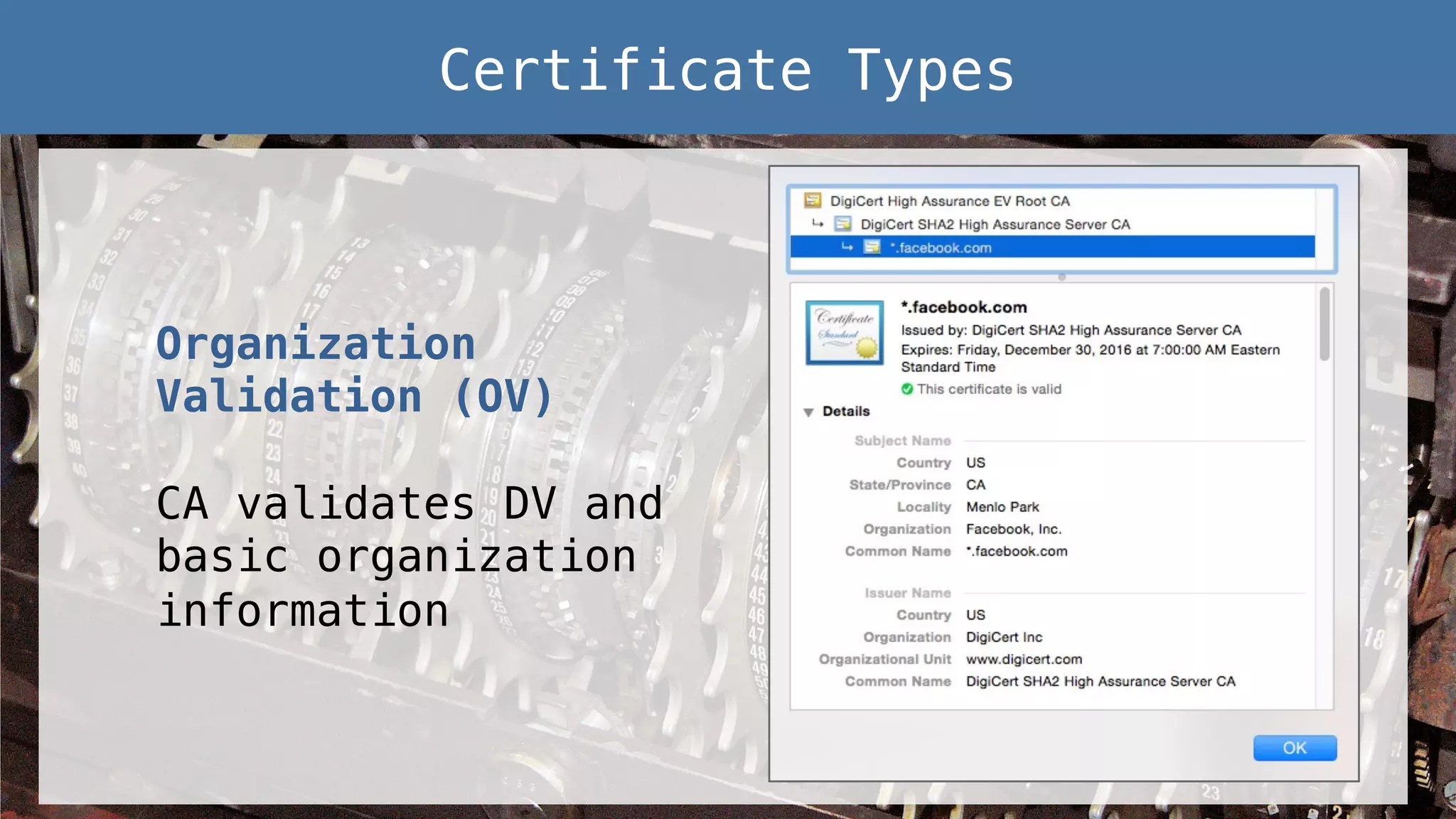
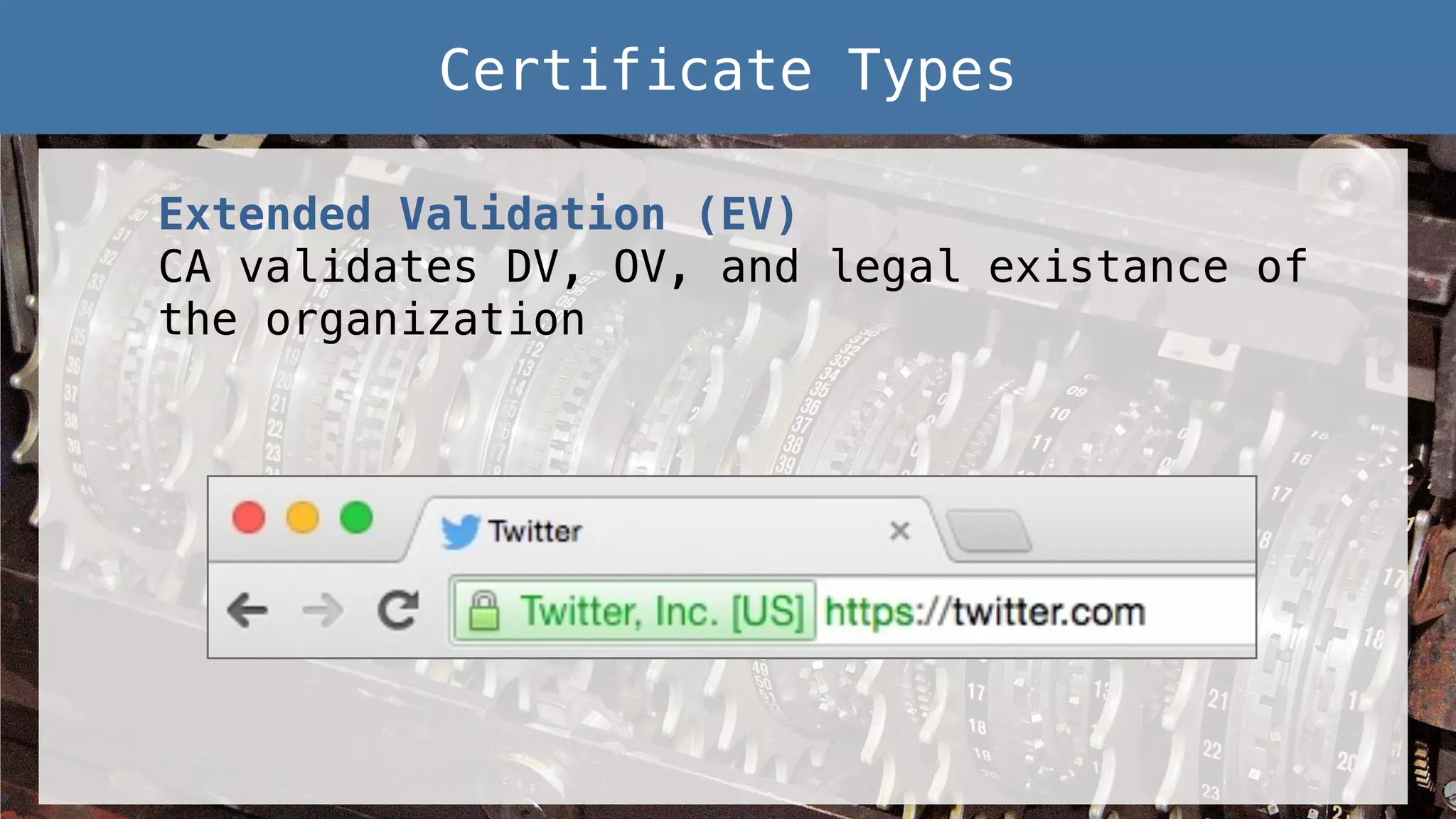
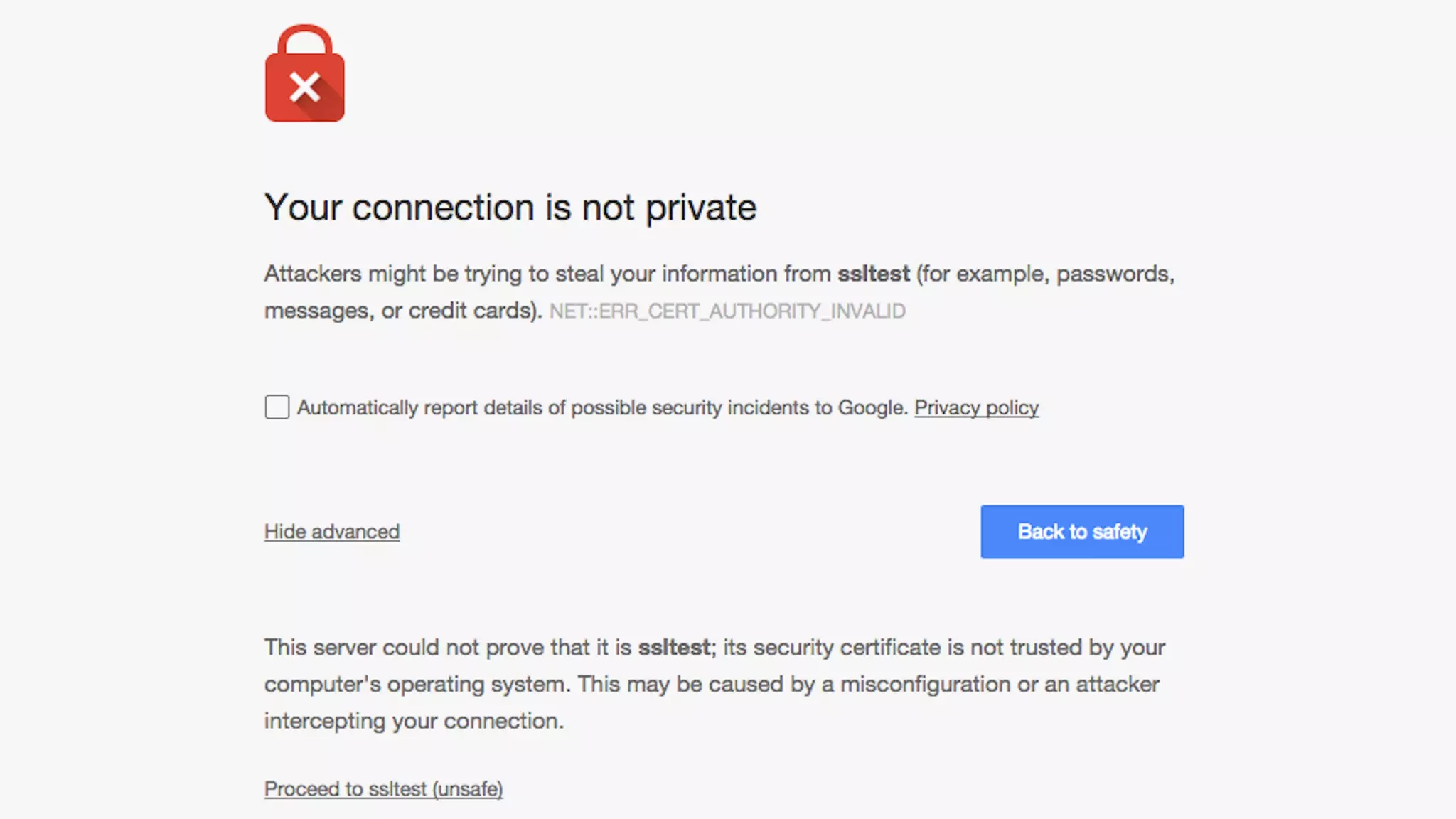
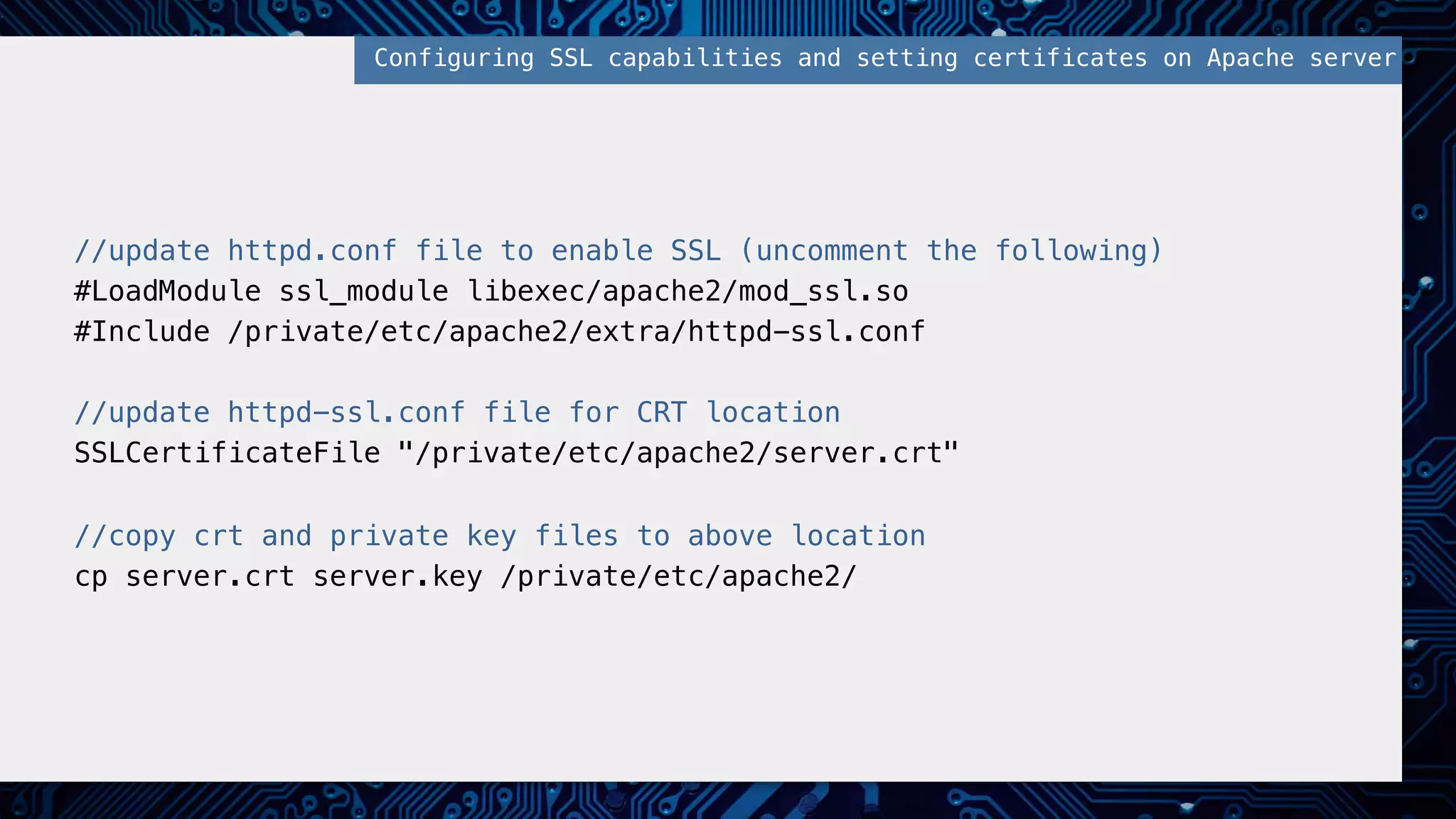
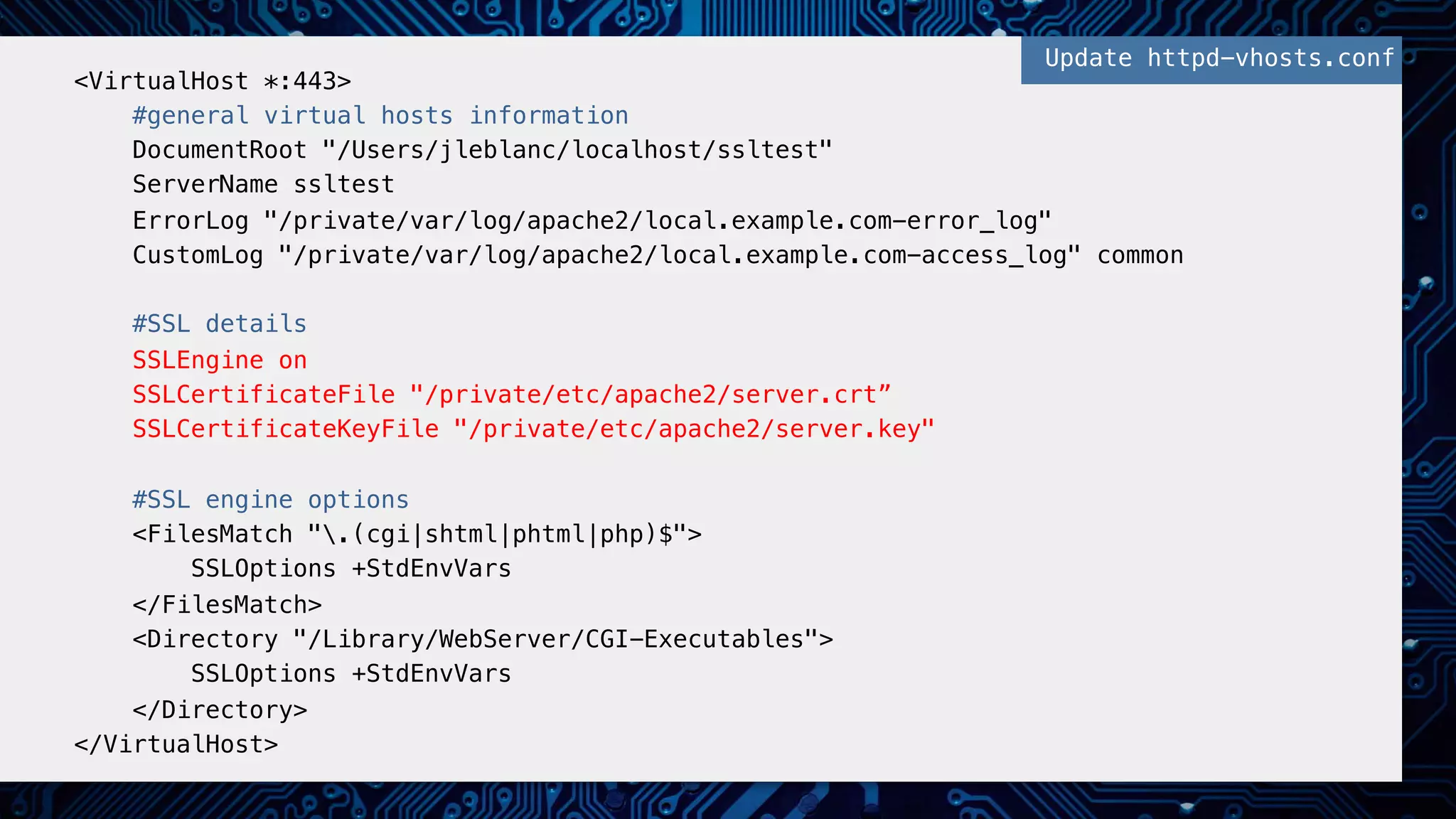
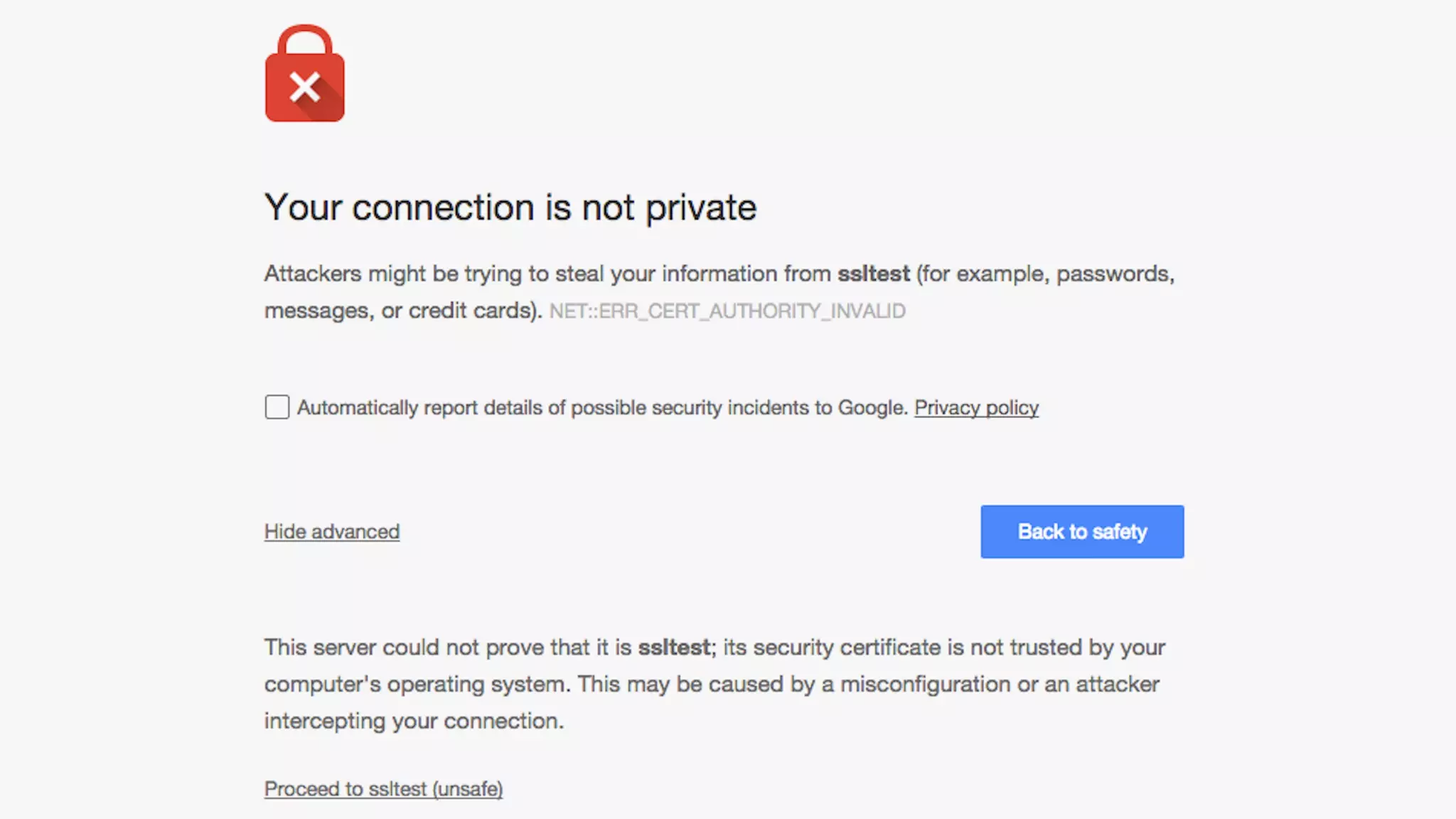
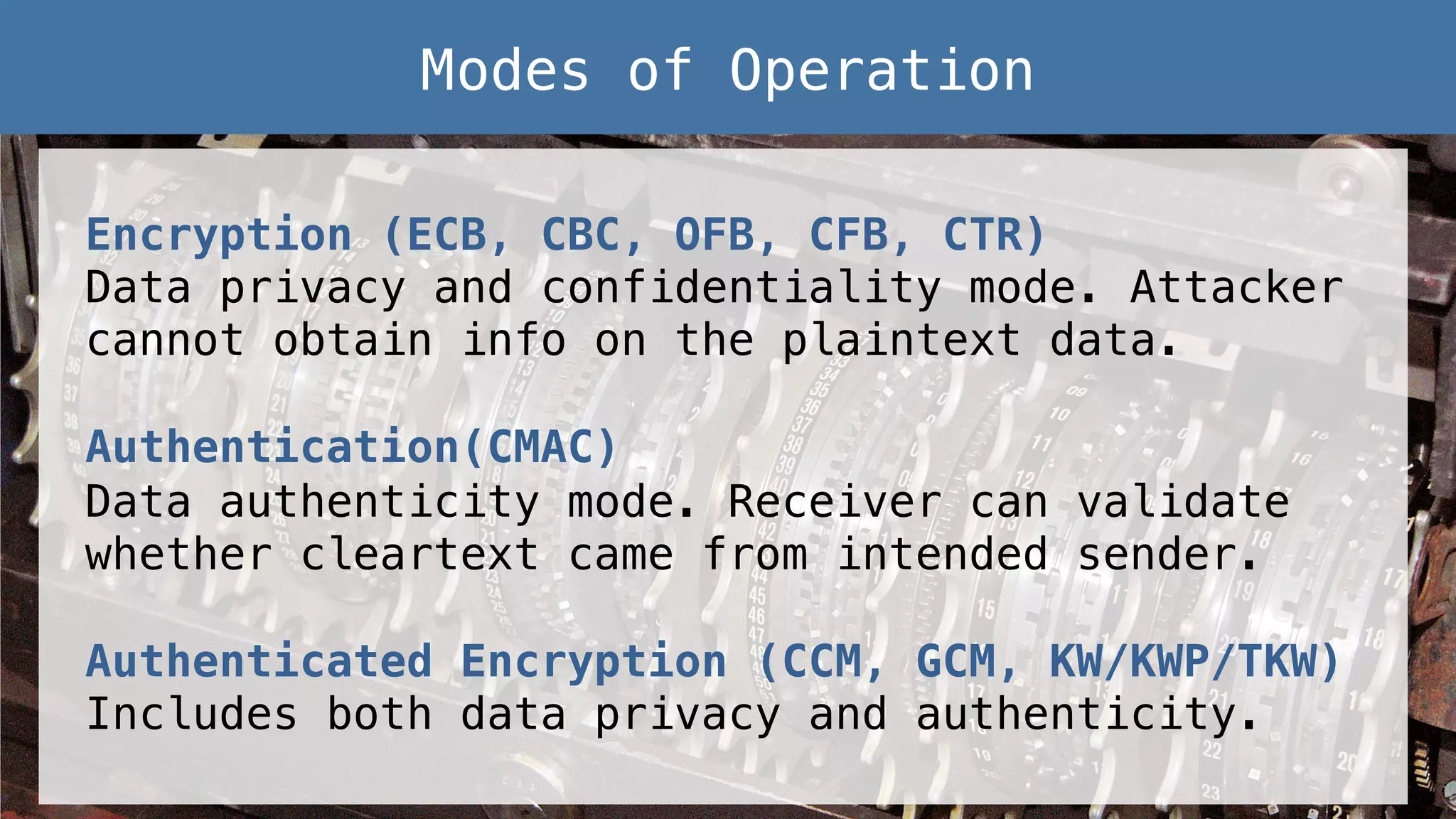
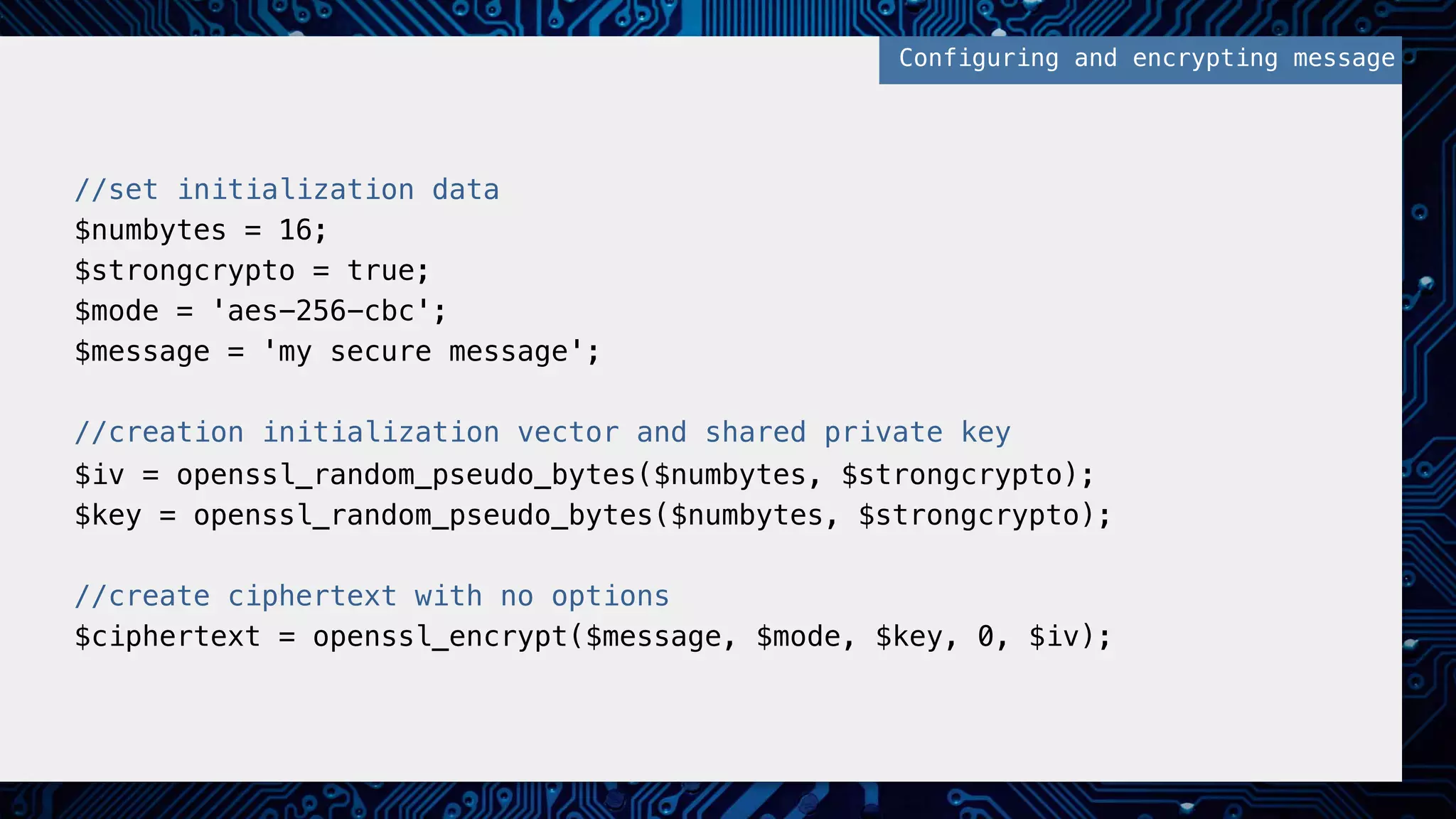
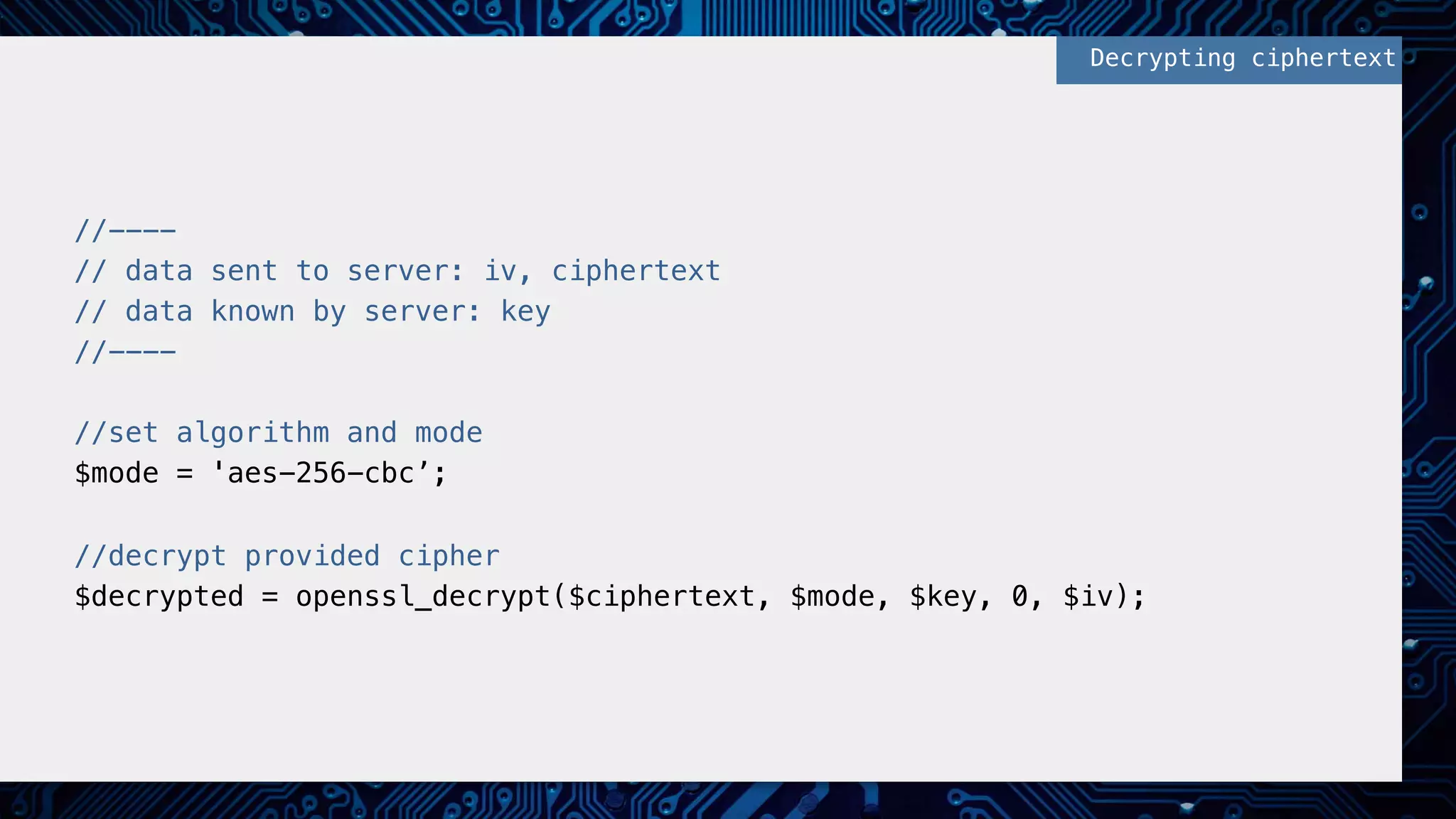
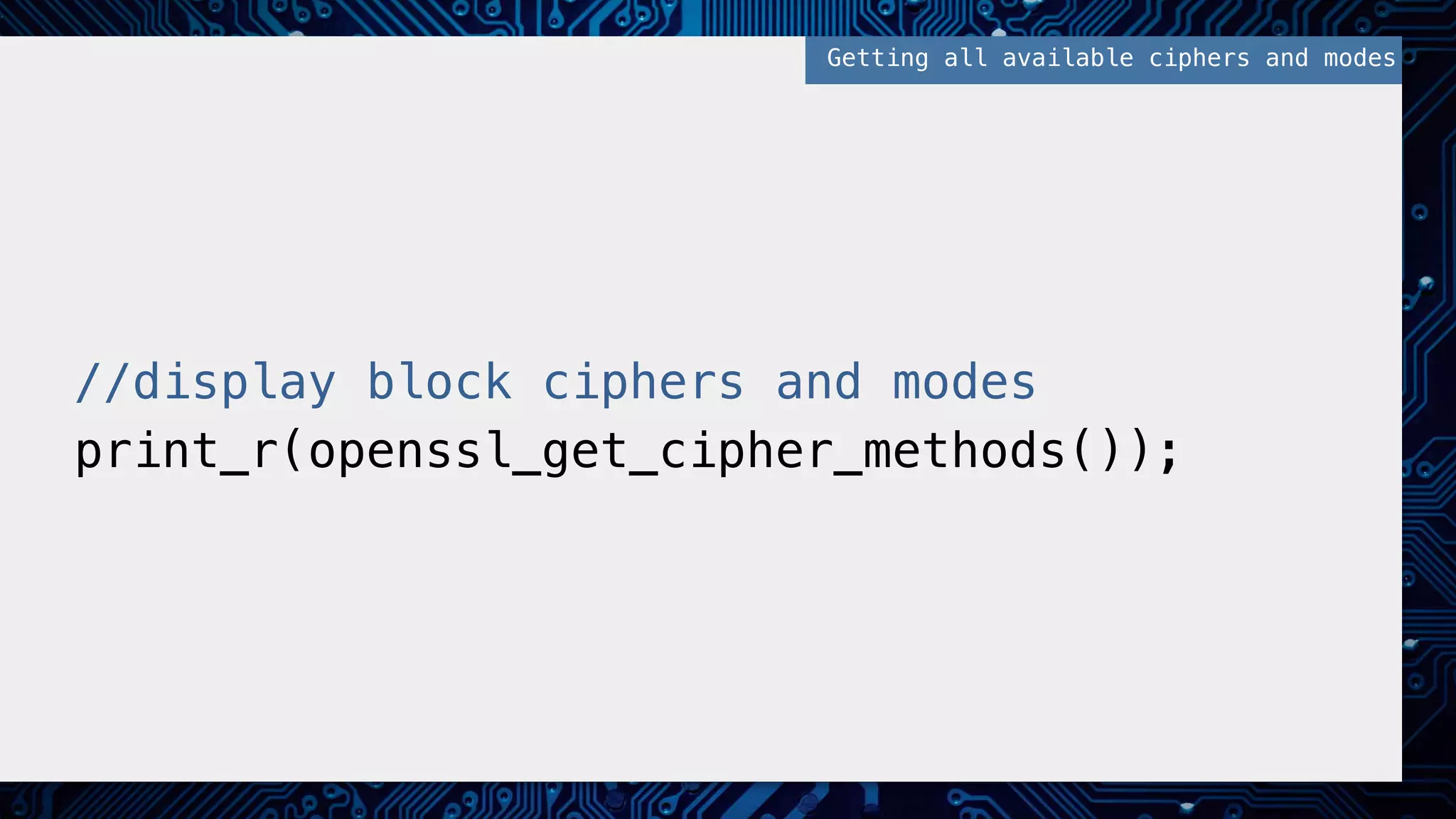
This document provides an overview of password and data security best practices for PHP applications. It discusses common password attacks and how to protect against them using techniques like salting, key stretching algorithms and two-factor authentication. It also covers encrypting data using symmetric and asymmetric cryptography algorithms like AES, RSA and digital signatures. The document provides code examples for hashing and validating passwords, encrypting and decrypting messages and data at rest or in transit.






![! //fetch password from user creation request! $password = $_POST['password'];! ! //salt option deprecated in PHP 7.0.0+! $options = [! 'cost' => 12! ];! ! //create 60 character hash, with default unique salt, and options ! $hash = password_hash($password, PASSWORD_BCRYPT, $options);! ! //STORE HASH IN USER DATABASE RECORD! //SALT IS BUILT INTO HASH! Hashing with bcrypt!](https://image.slidesharecdn.com/2016febphpidentitydatasecurity-160204170910/75/PHP-Identity-and-Data-Security-13-2048.jpg)
![//fetch login request information! $username = $_POST['username'];! $password = $_POST['password'];! ! //fetch user record from database! $user = fetchDBRecord($username);! ! //verify if login attempt password matches stored user hash! if (password_verify($password, $user->hash)){! echo "password matches";! } else {! echo "password doesn't match";! }! Login Hash Comparison with bcrypt!](https://image.slidesharecdn.com/2016febphpidentitydatasecurity-160204170910/75/PHP-Identity-and-Data-Security-14-2048.jpg)
![! ! //fetch password from user creation request! $password = $_POST['password'];! ! //set iterations and random initialization vector! $iterations = 1000;! $salt = mcrypt_create_iv(16, MCRYPT_DEV_URANDOM);! ! //hash password using sha256! $hash = hash_pbkdf2("sha256", $password, $salt, $iterations, 20);! ! //STORE HASH AND SALT IN USER DATABASE RECORD! Hashing with PBKDF2!](https://image.slidesharecdn.com/2016febphpidentitydatasecurity-160204170910/75/PHP-Identity-and-Data-Security-15-2048.jpg)
![! //fetch login request info and set iterations! $username = $_POST['username'];! $password = $_POST['password'];! $iterations = 1000;! ! //fetch user record from database! $user = fetchDBRecord($username);! ! //manually hash the login attempt password! $loginhash = hash_pbkdf2("sha256", $password, $user->salt, $iterations, 20);! ! //validate if hashes match! if (hash_equals ($loginhash, $user->hash)){ ! echo 'password match';! } else {! echo 'password mismatch';! }! ! Login Hash Comparison with PBKDF2!](https://image.slidesharecdn.com/2016febphpidentitydatasecurity-160204170910/75/PHP-Identity-and-Data-Security-16-2048.jpg)


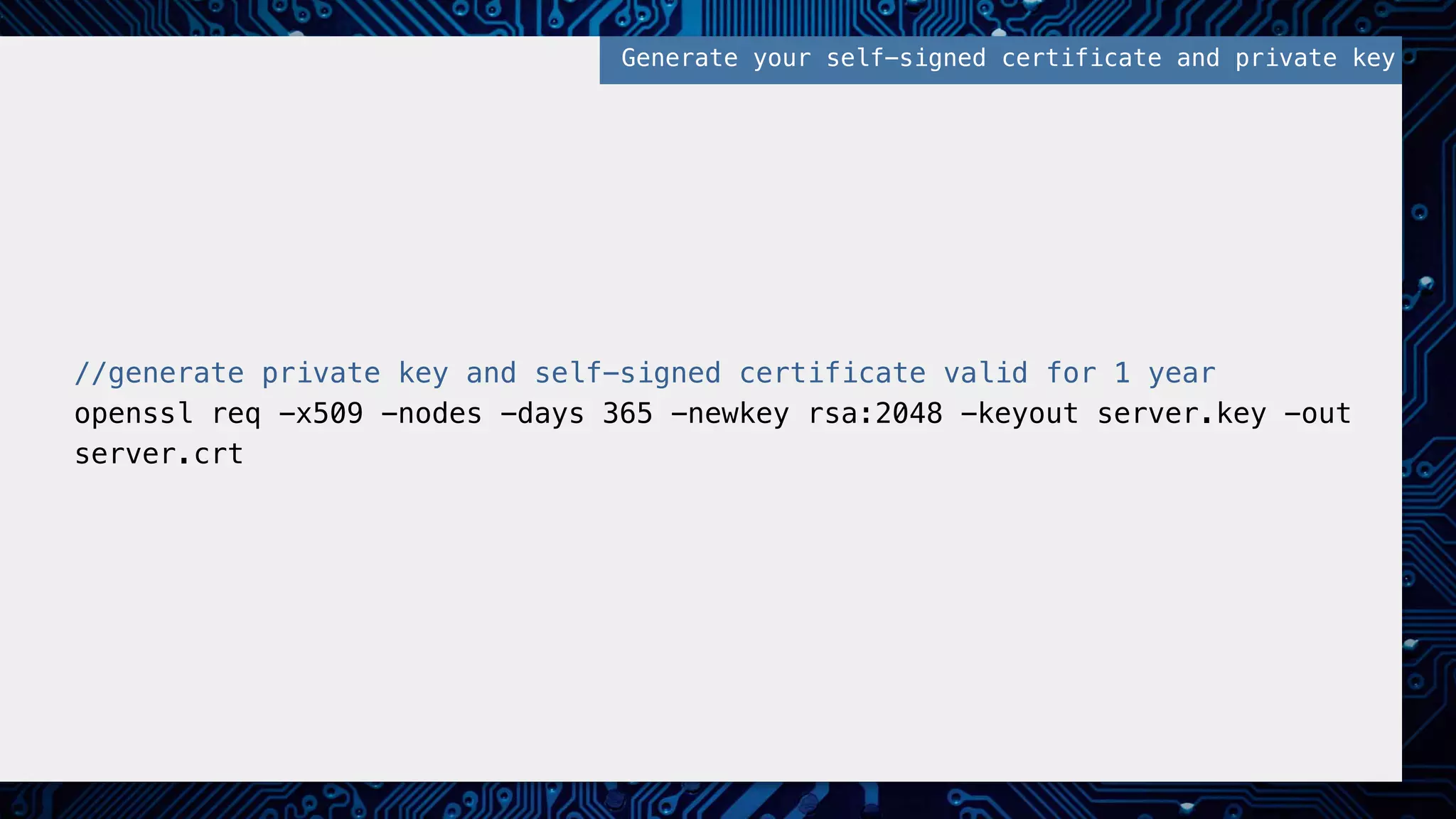

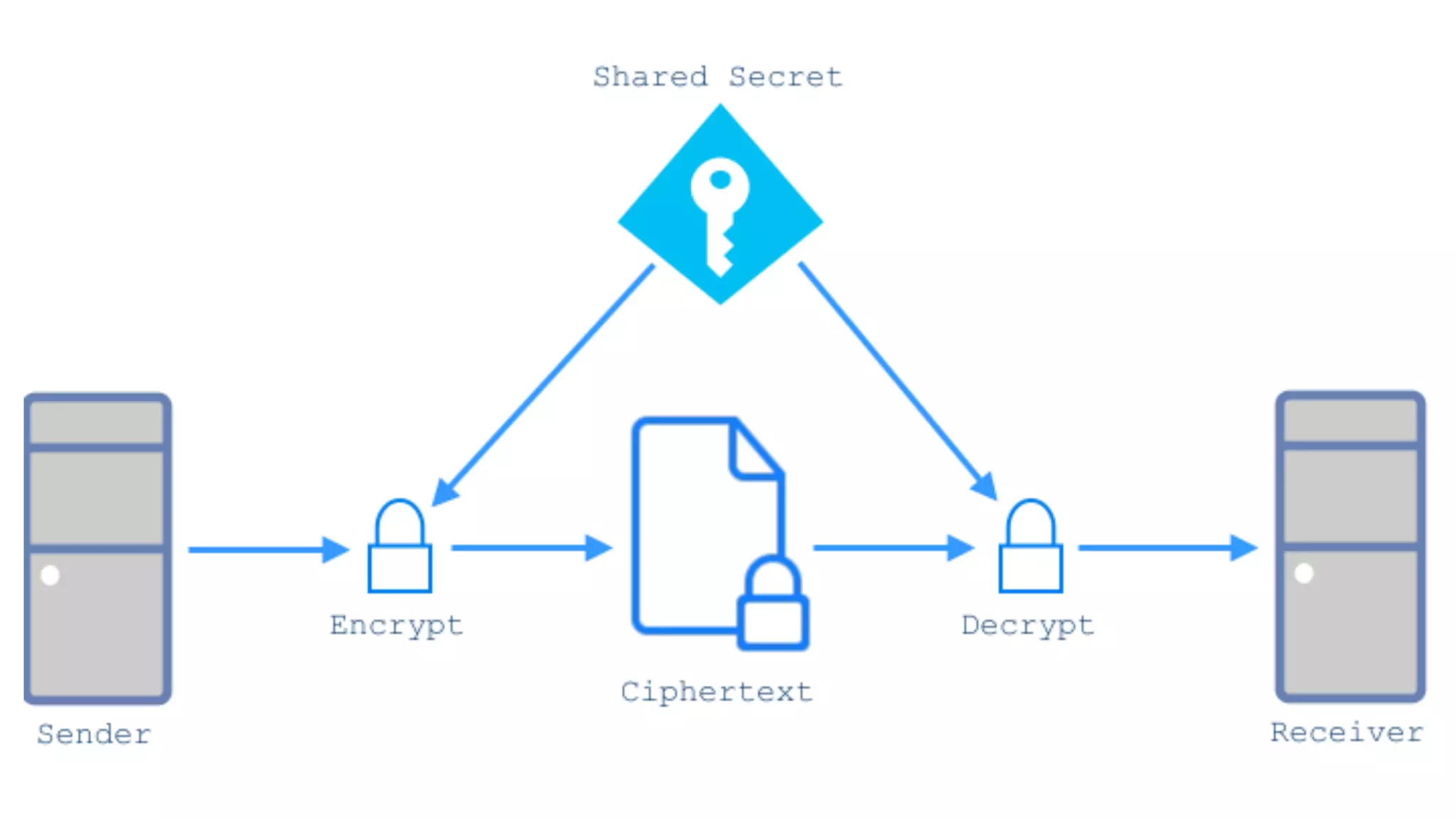


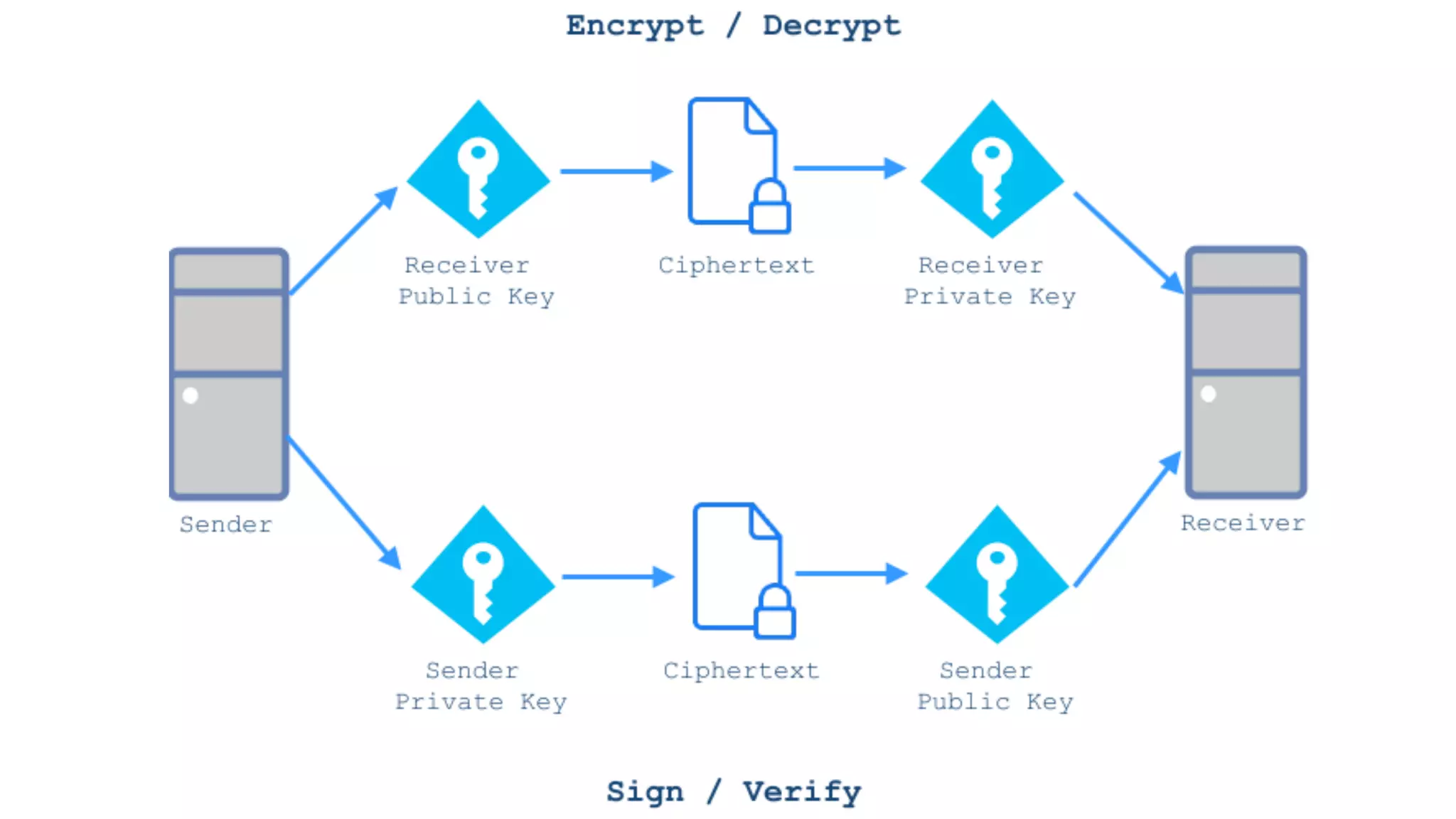

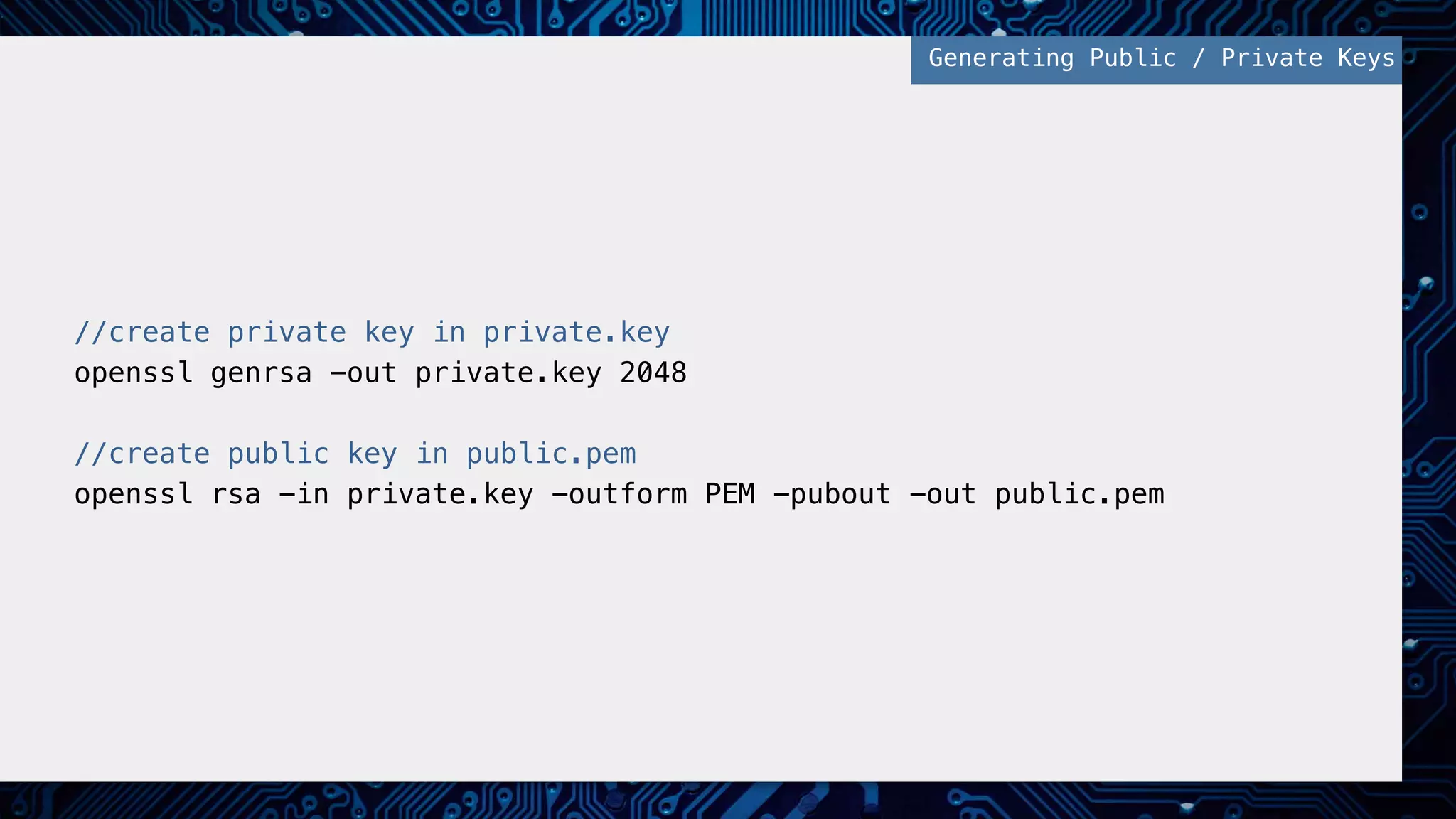
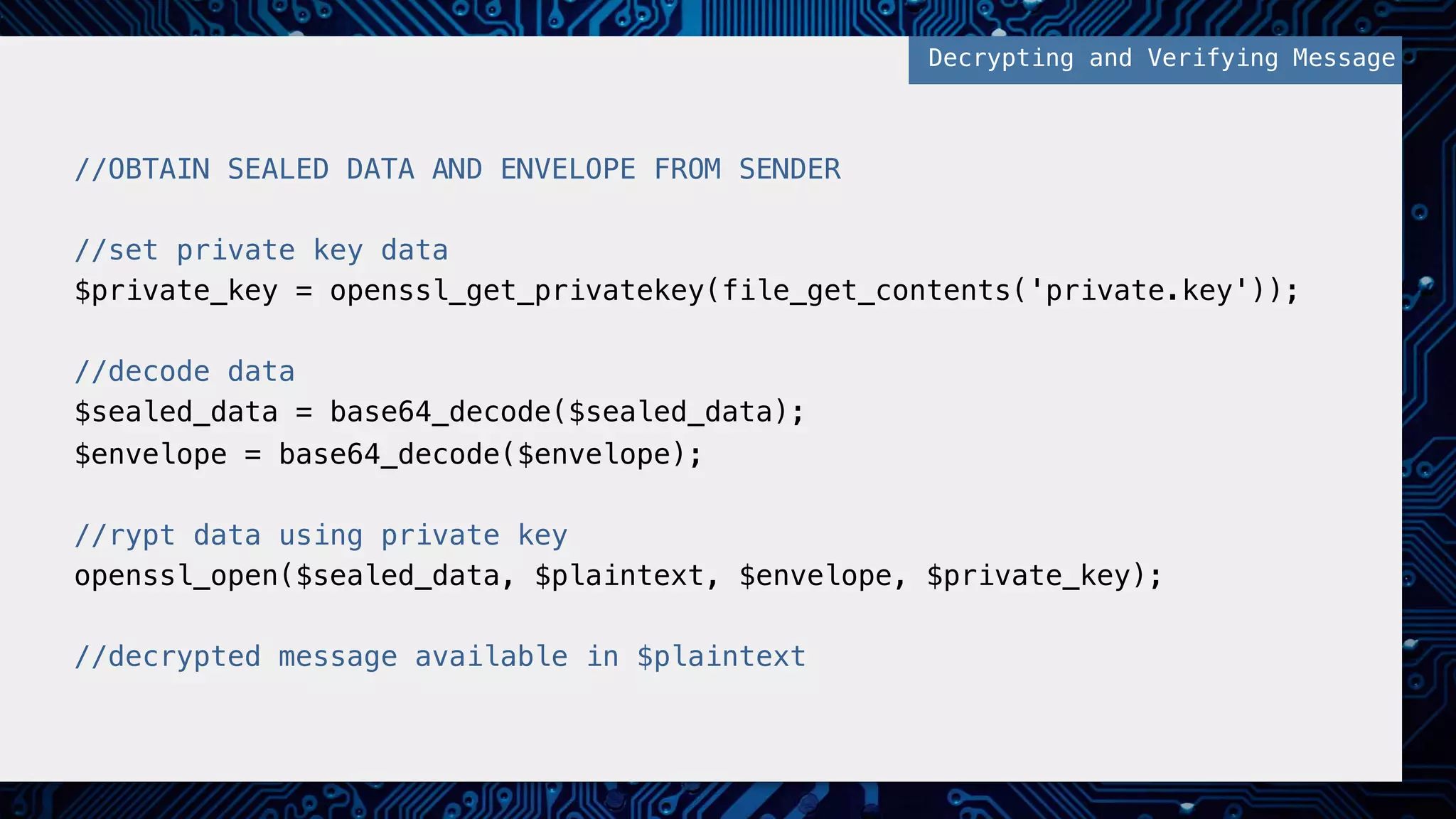
![//set public key data from files and object to send! $public_key = openssl_get_publickey(file_get_contents('public.pem'));! $data = '{"message": "my super secure message"}';! ! //encrypt object and public keys! openssl_seal($data, $encrypted, $encpub, array($public_key));! ! //encrypted data and encrypted public key! $sealed_data = base64_encode($encrypted);! $envelope = base64_encode($encpub[0]);! ! //SEND SEALED DATA AND ENVELOPE TO RECIPIENT! Preparing Message, Encrypting, and Signing!](https://image.slidesharecdn.com/2016febphpidentitydatasecurity-160204170910/75/PHP-Identity-and-Data-Security-38-2048.jpg)