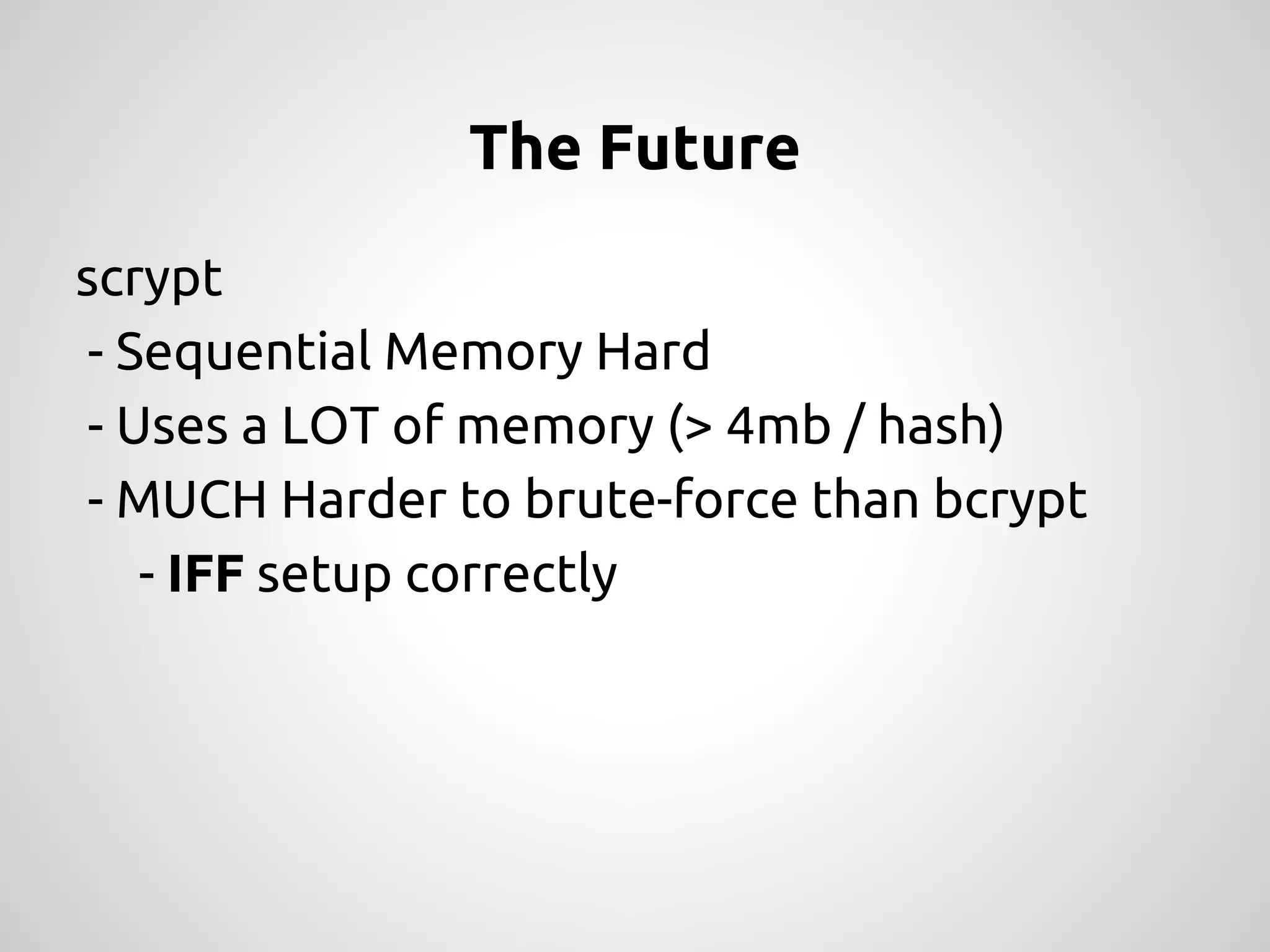
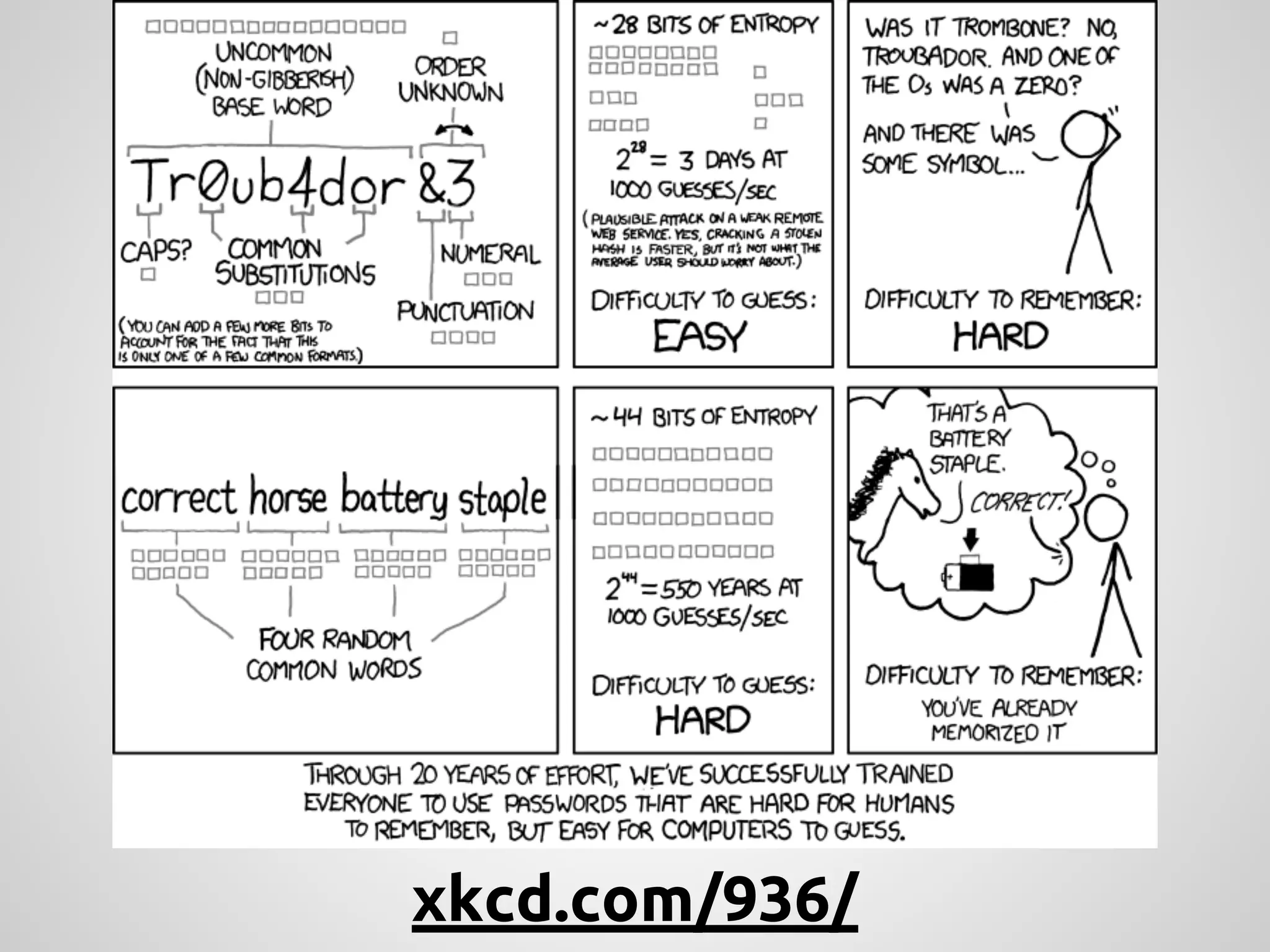
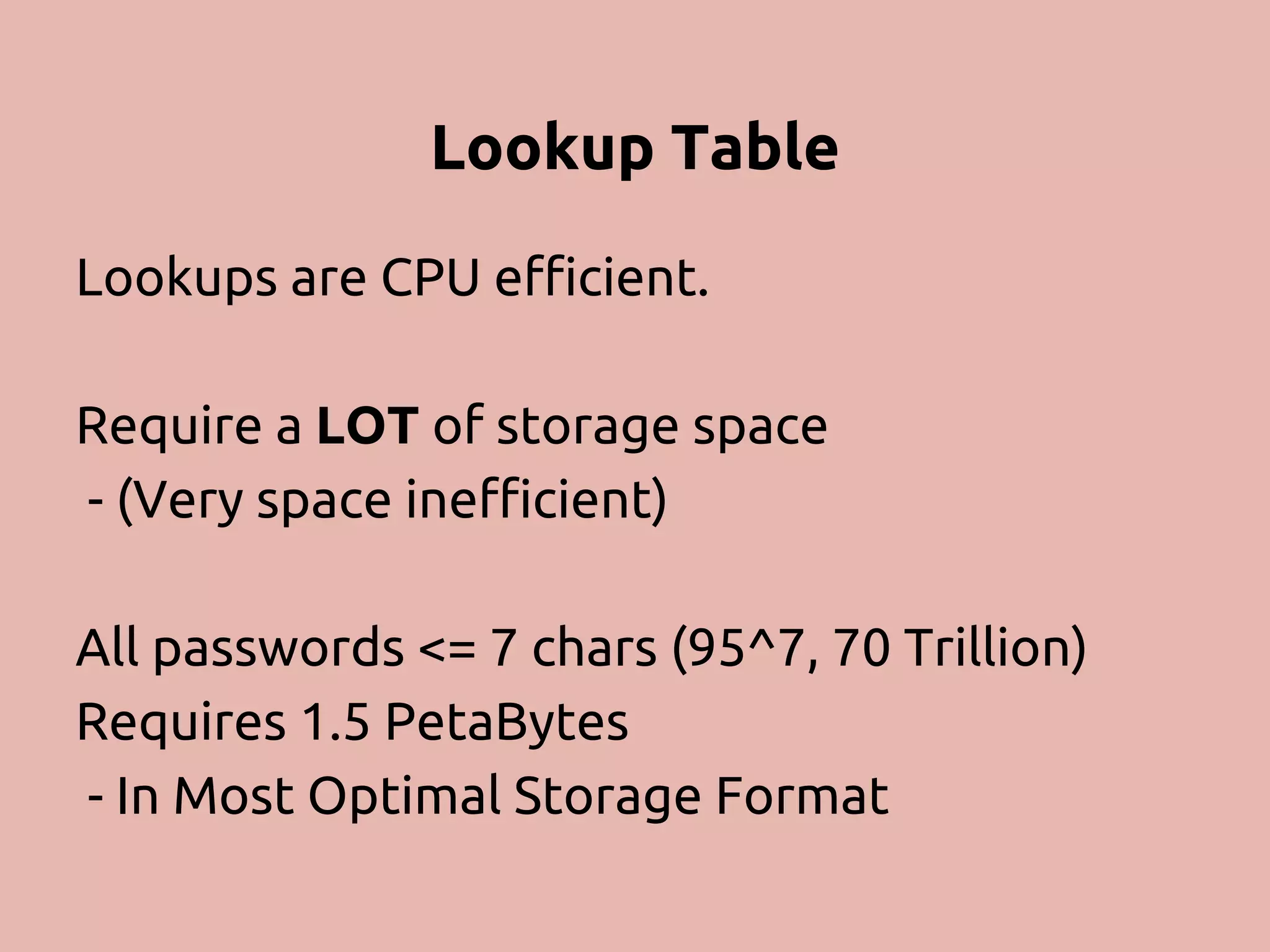
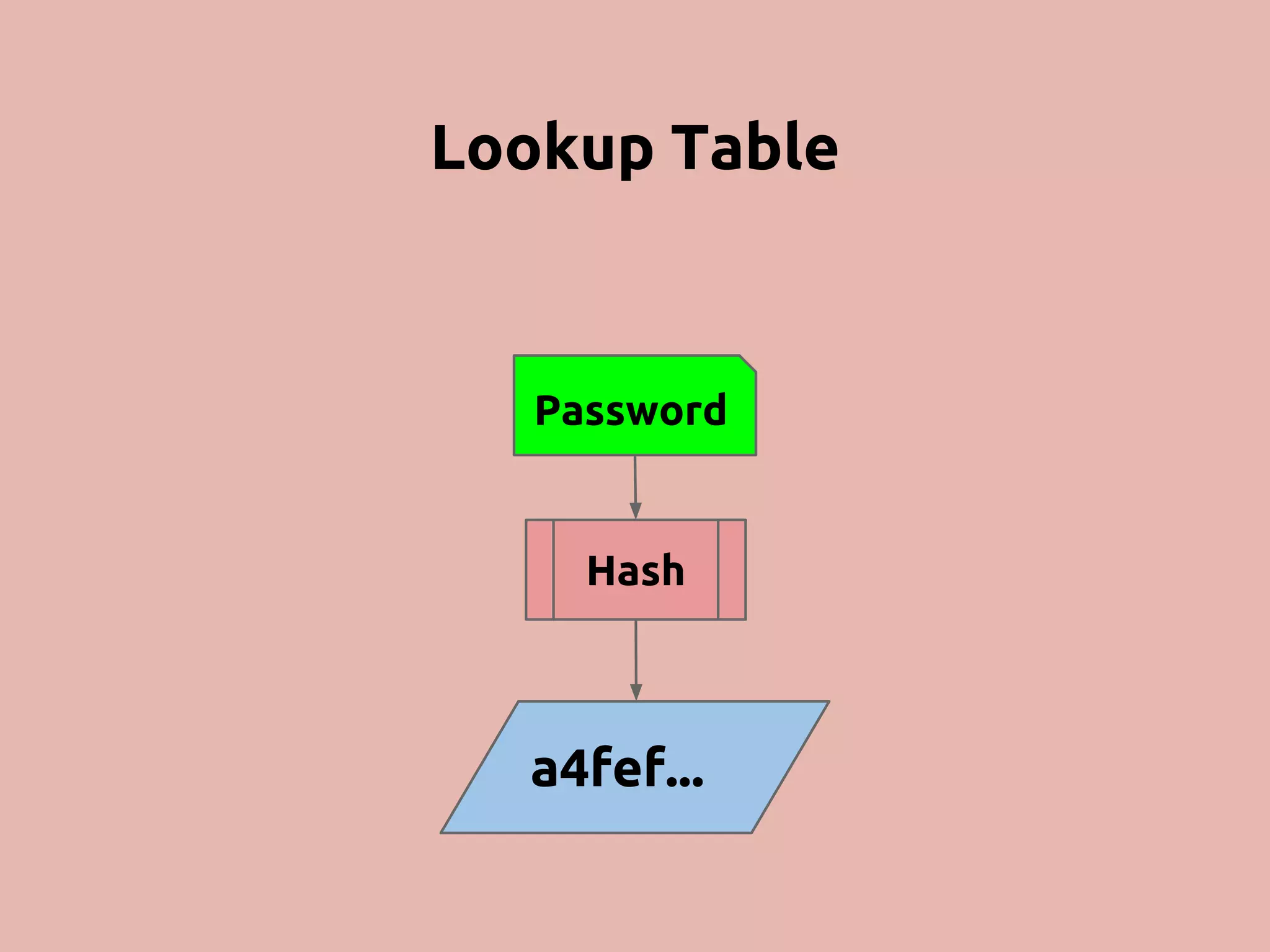
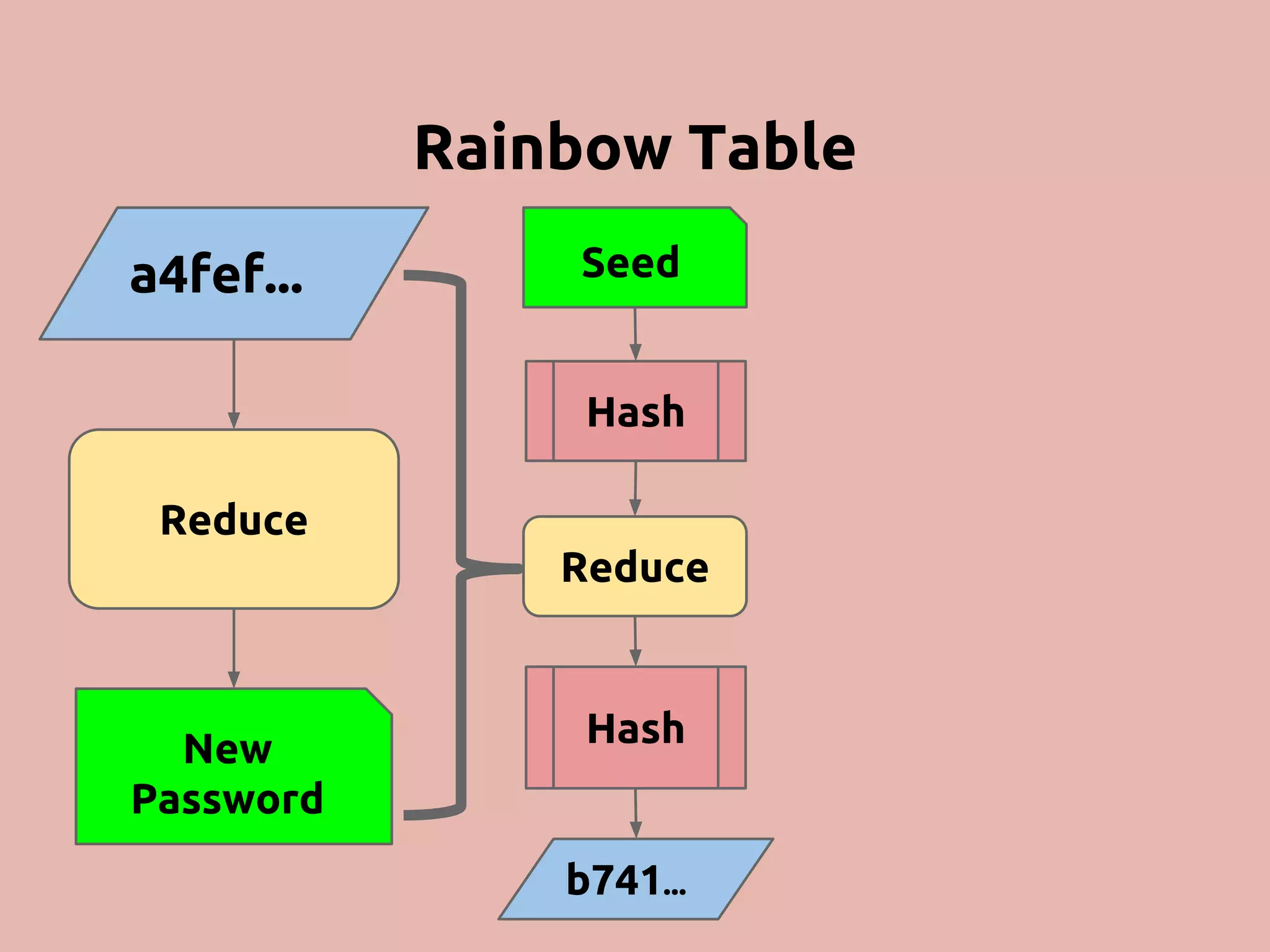
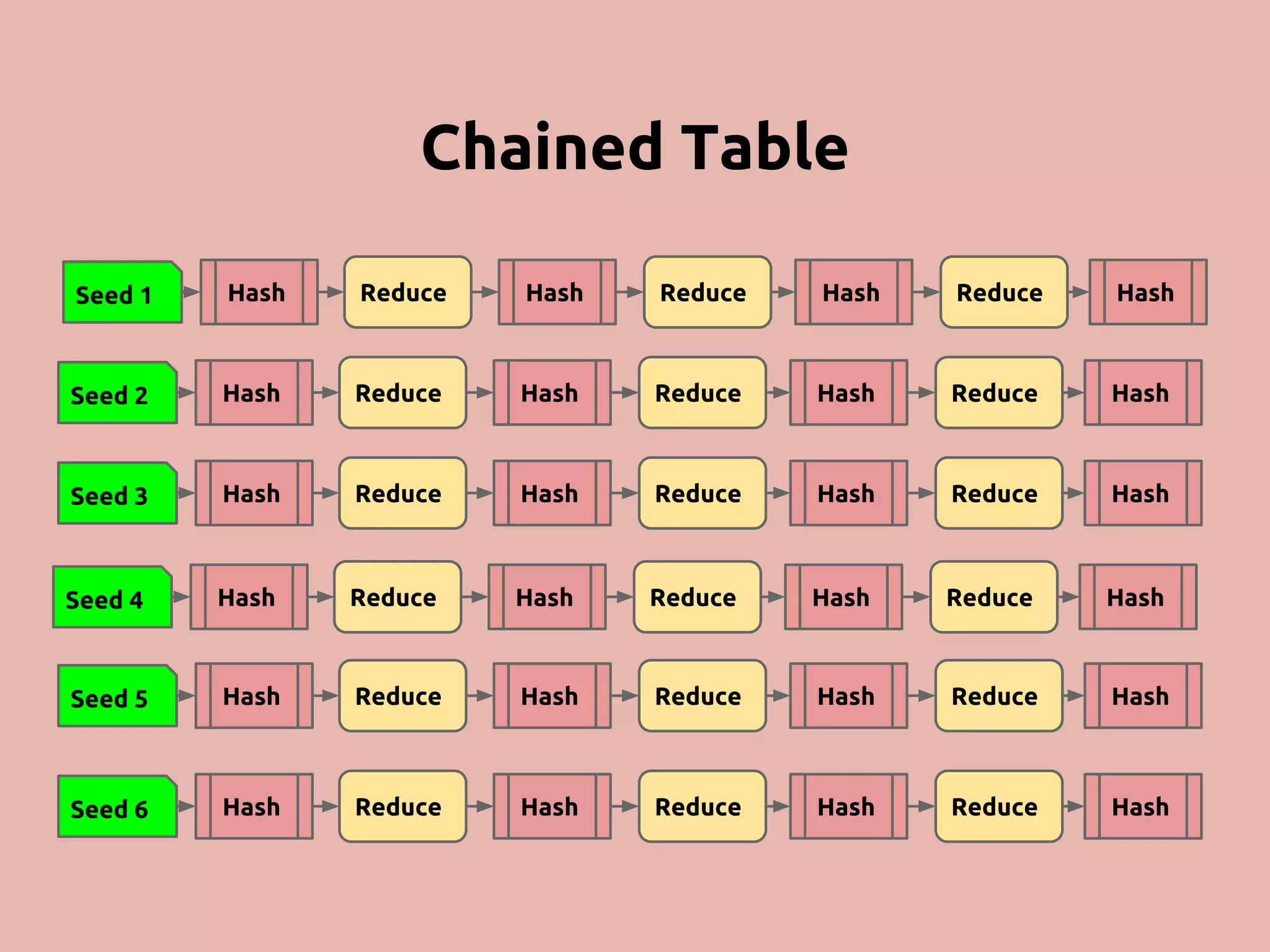
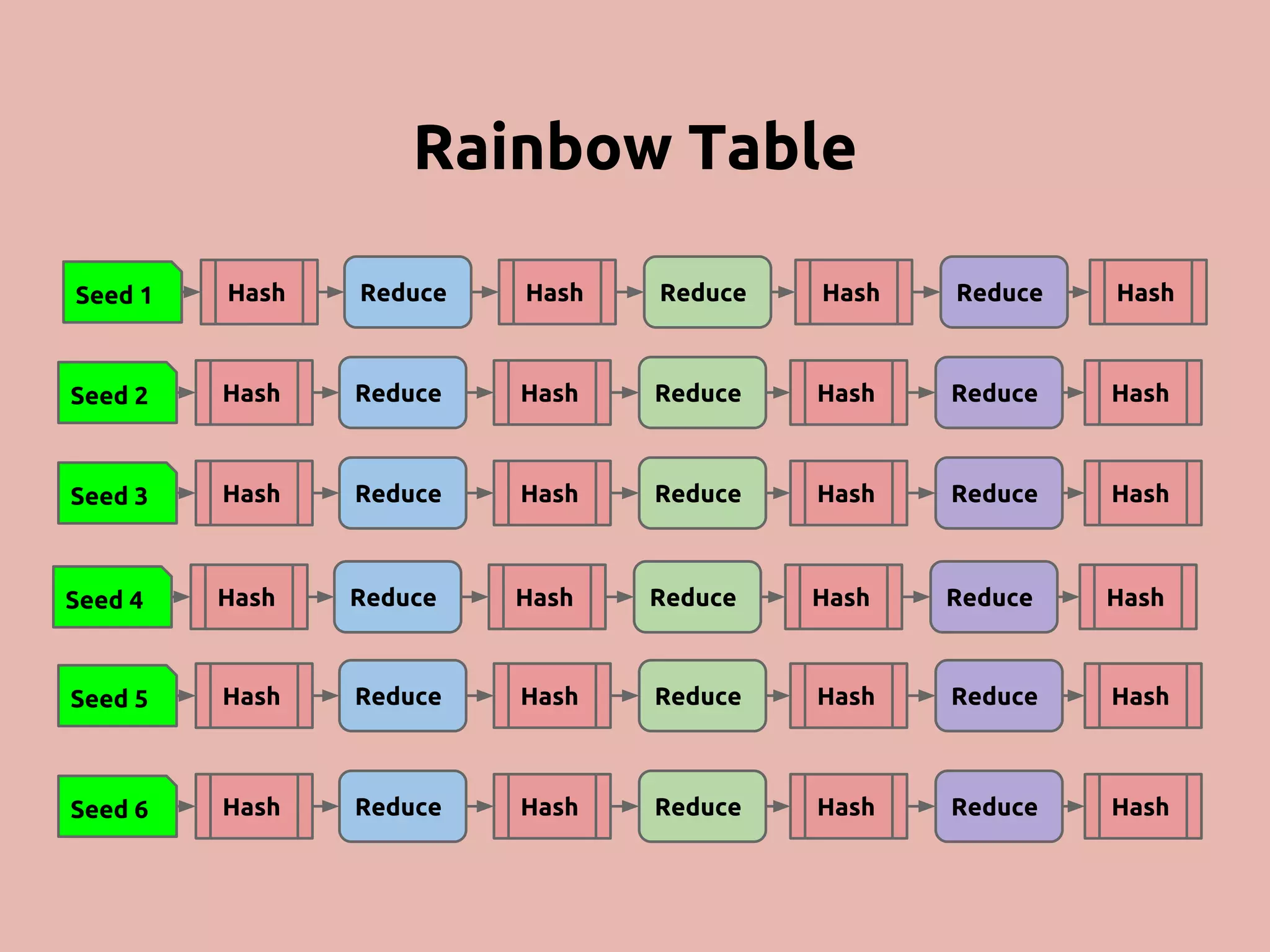
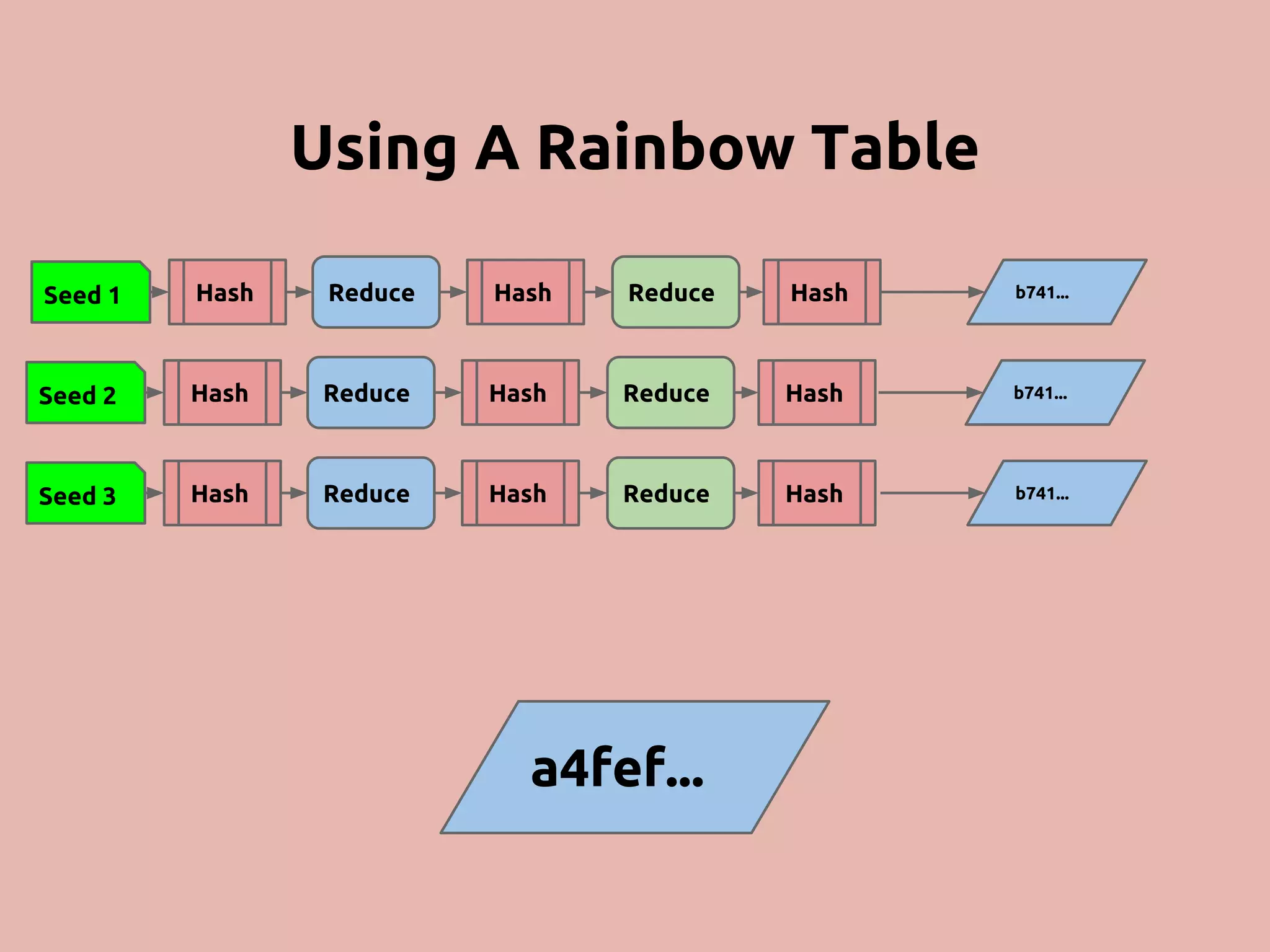
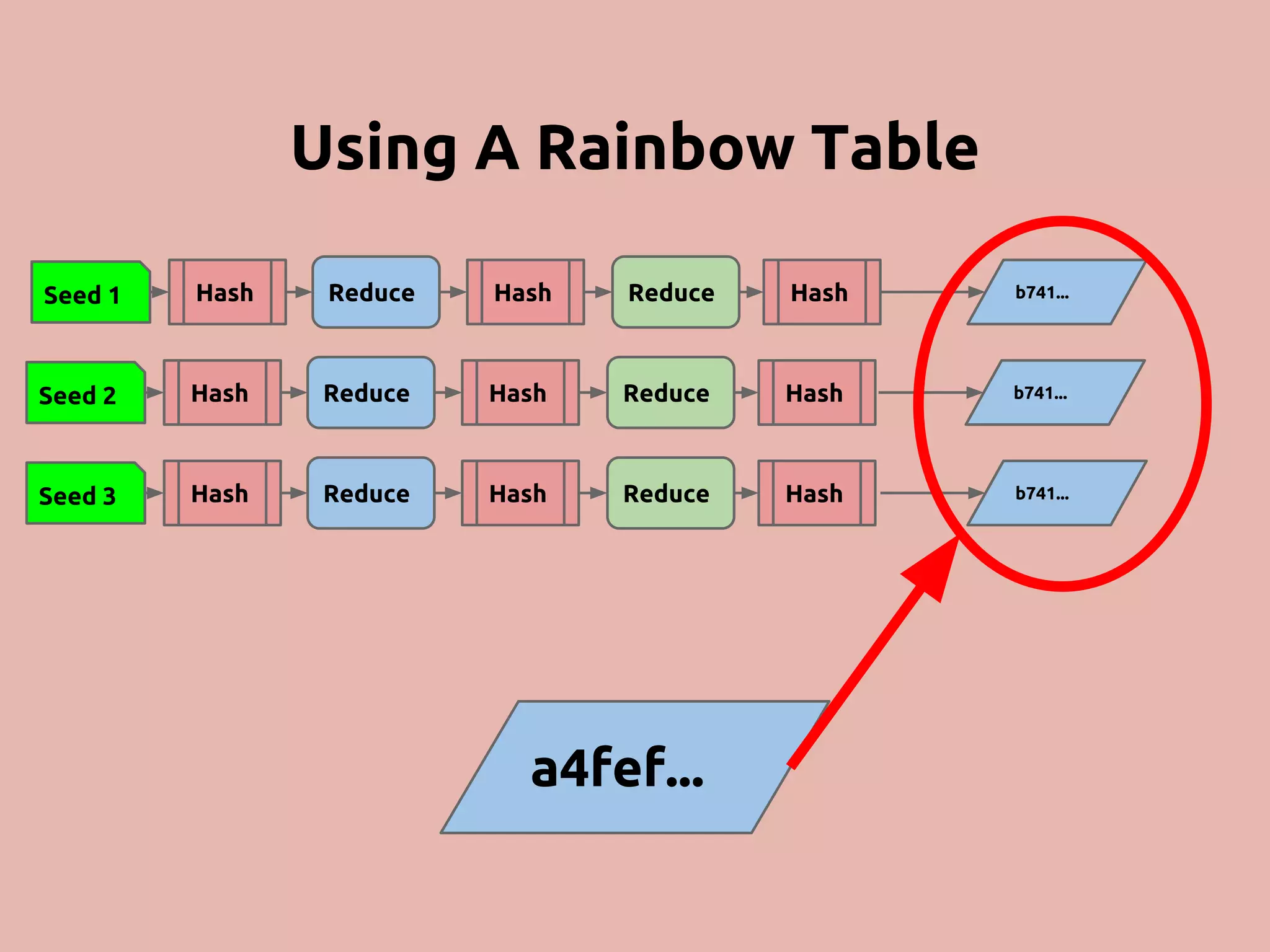
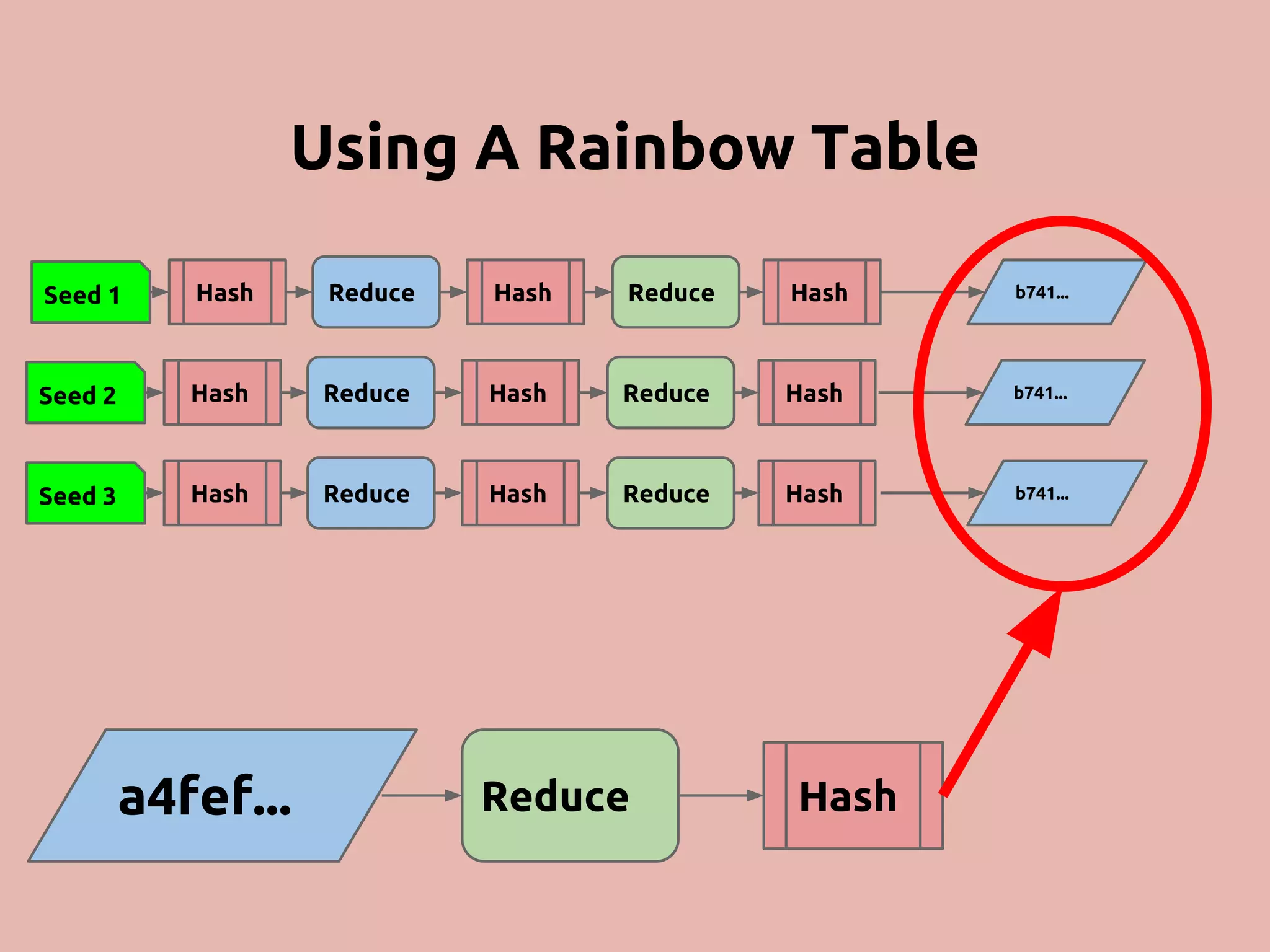
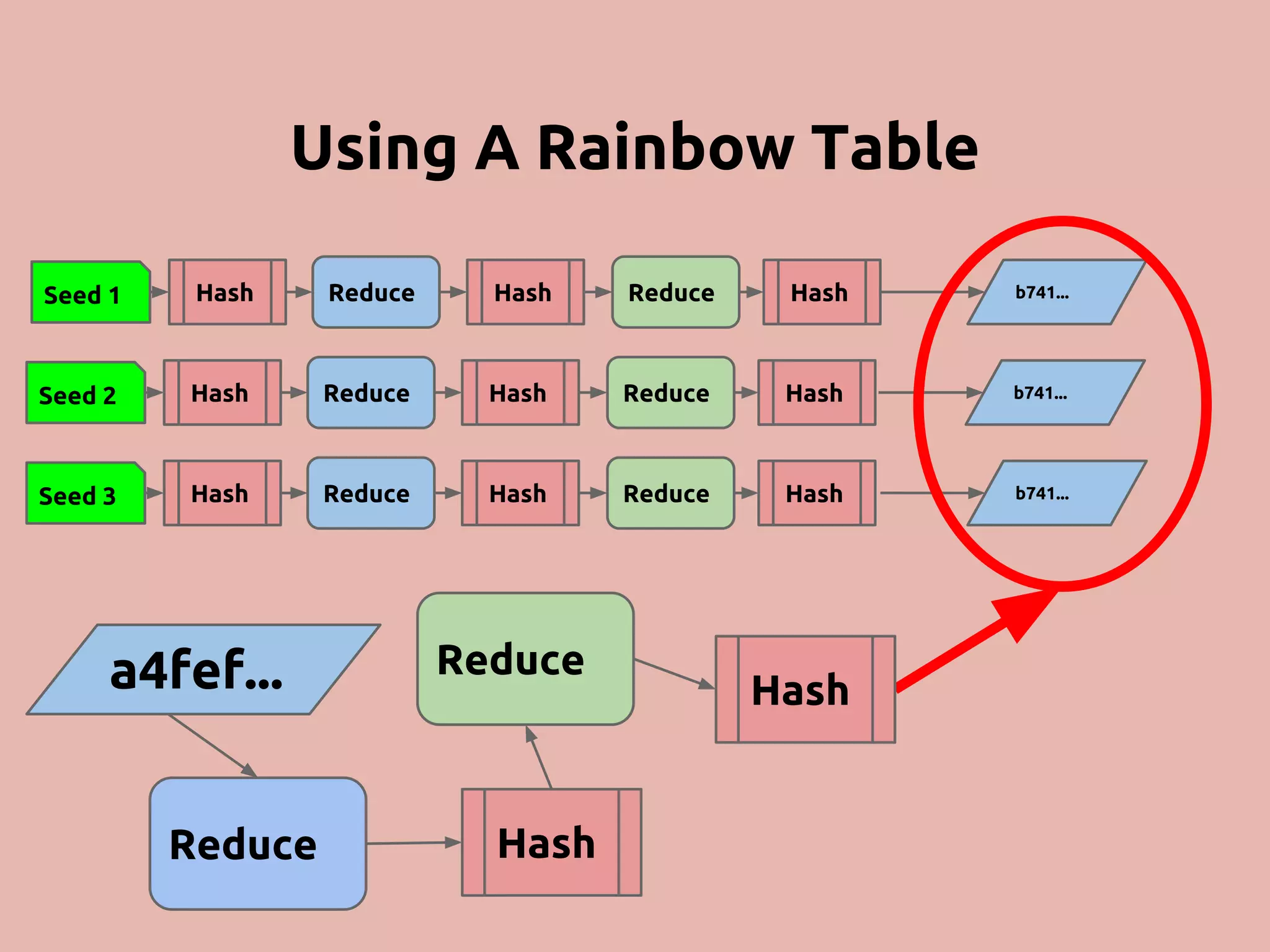
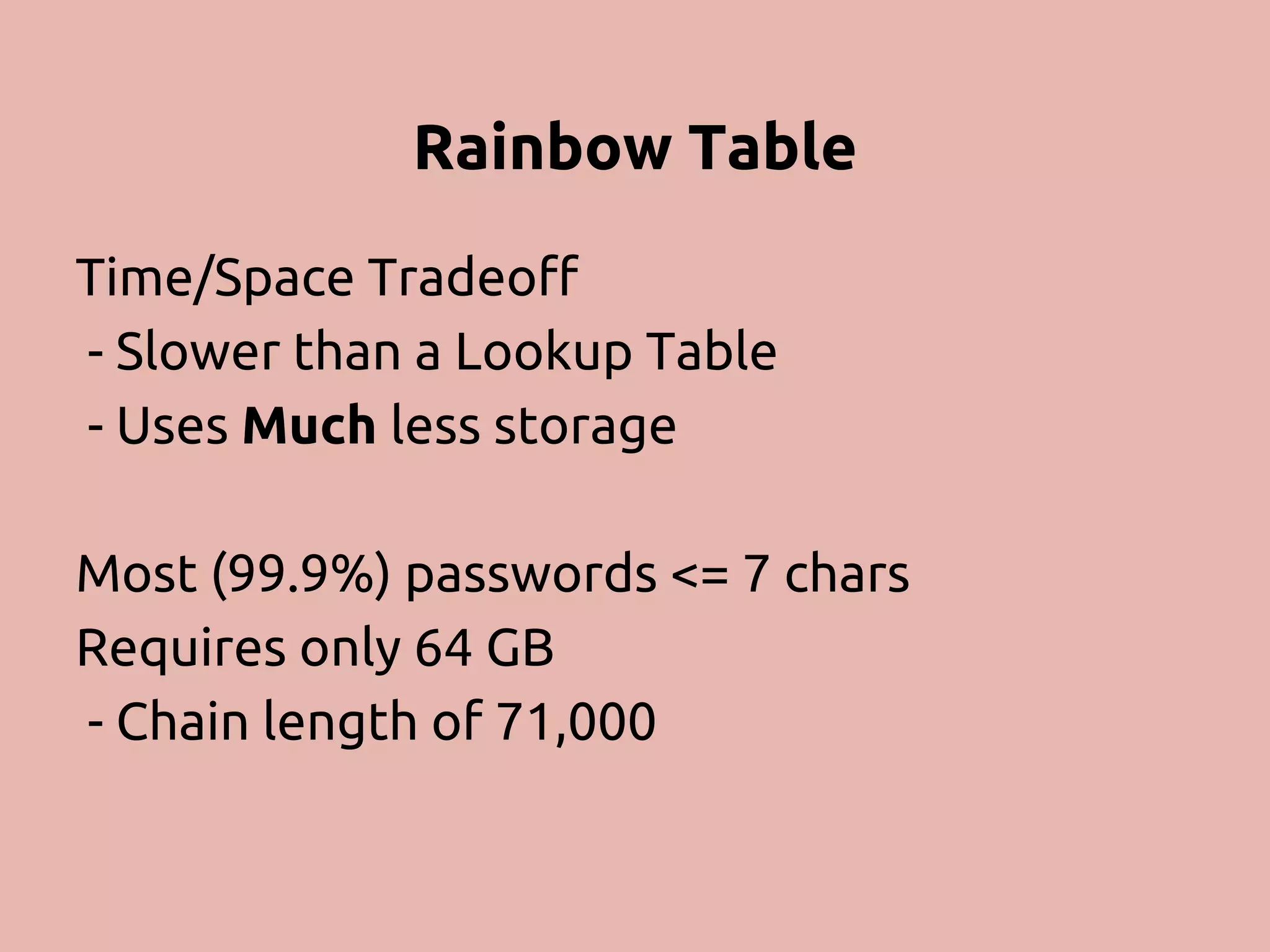
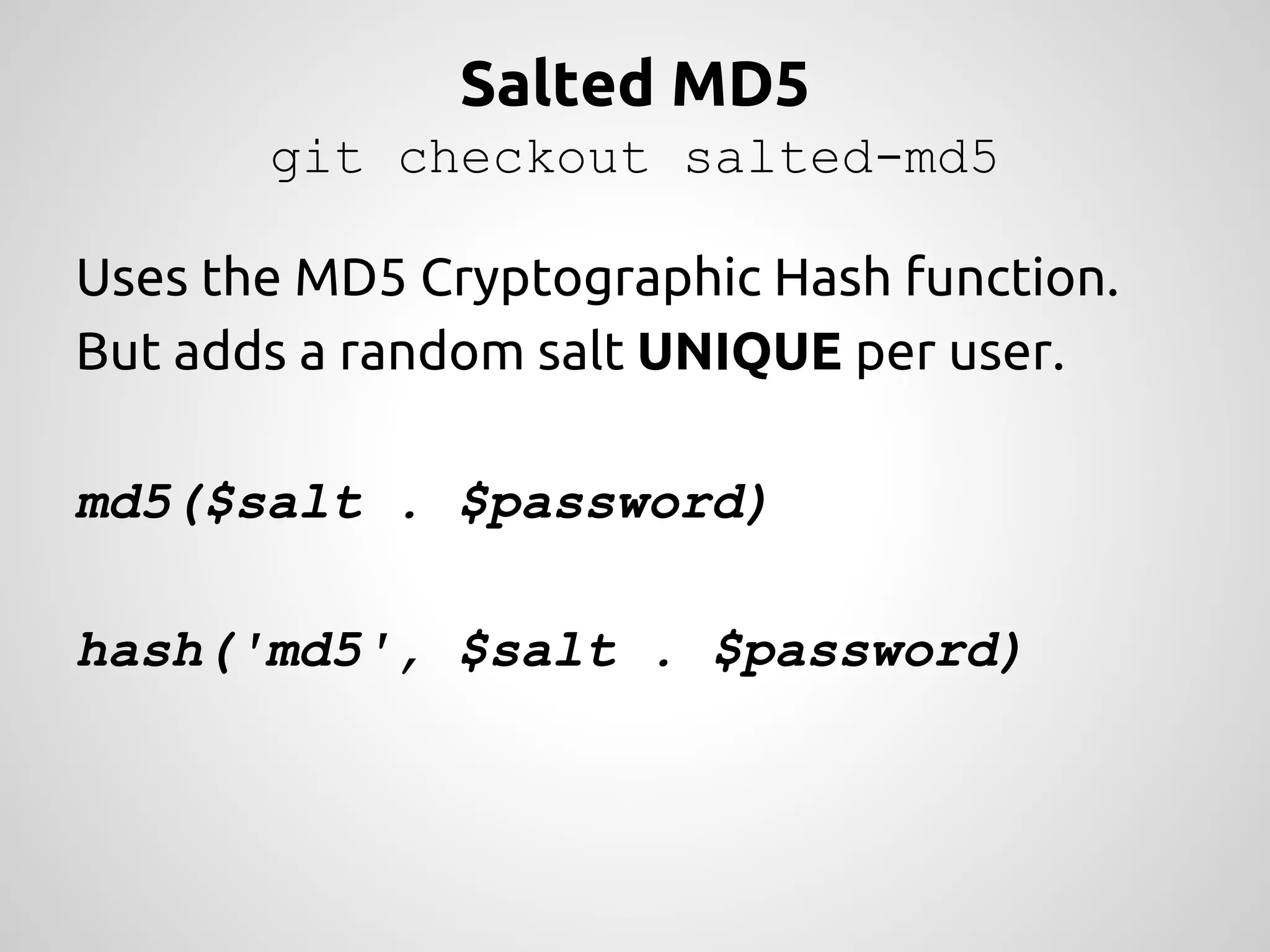
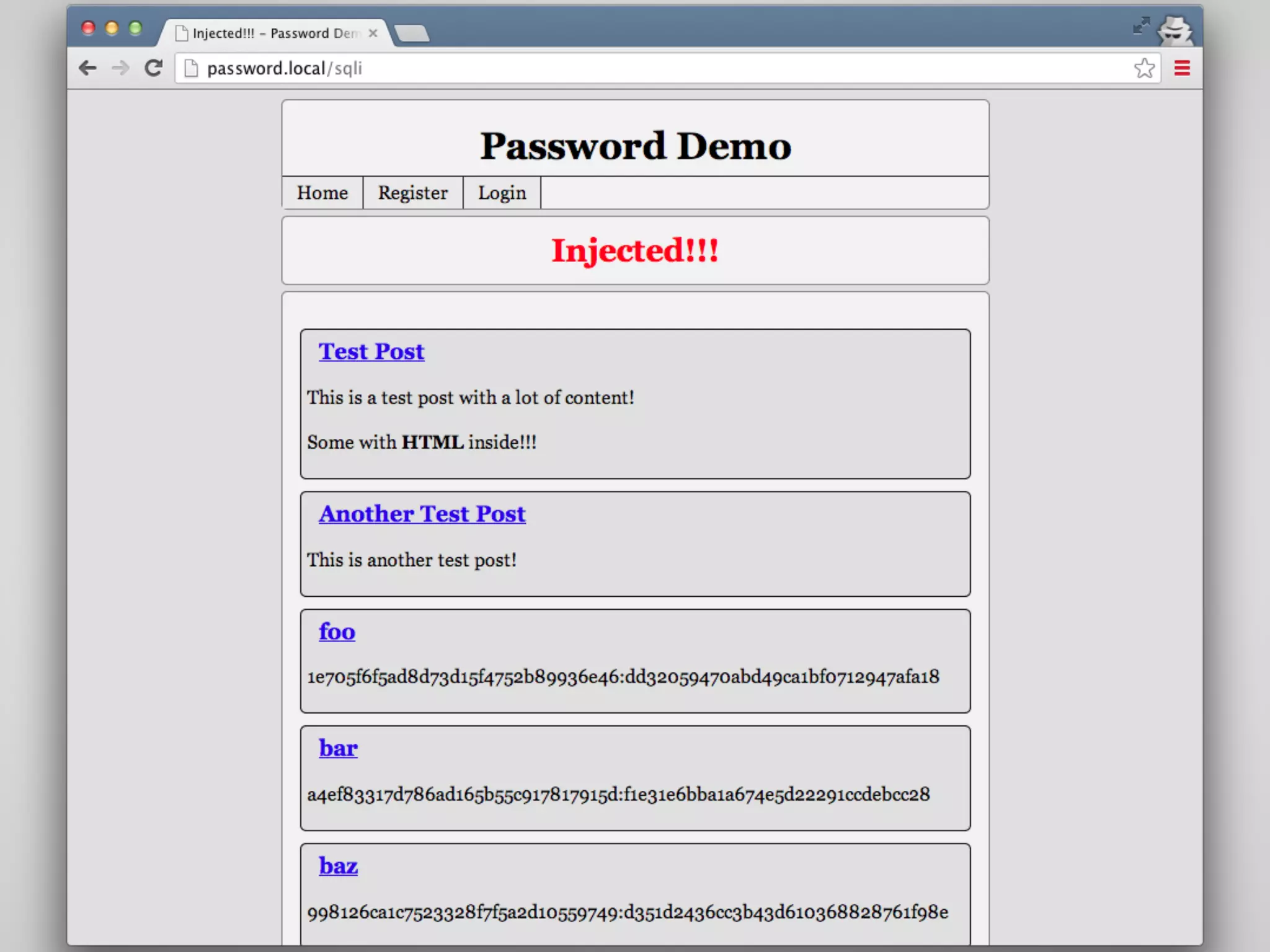
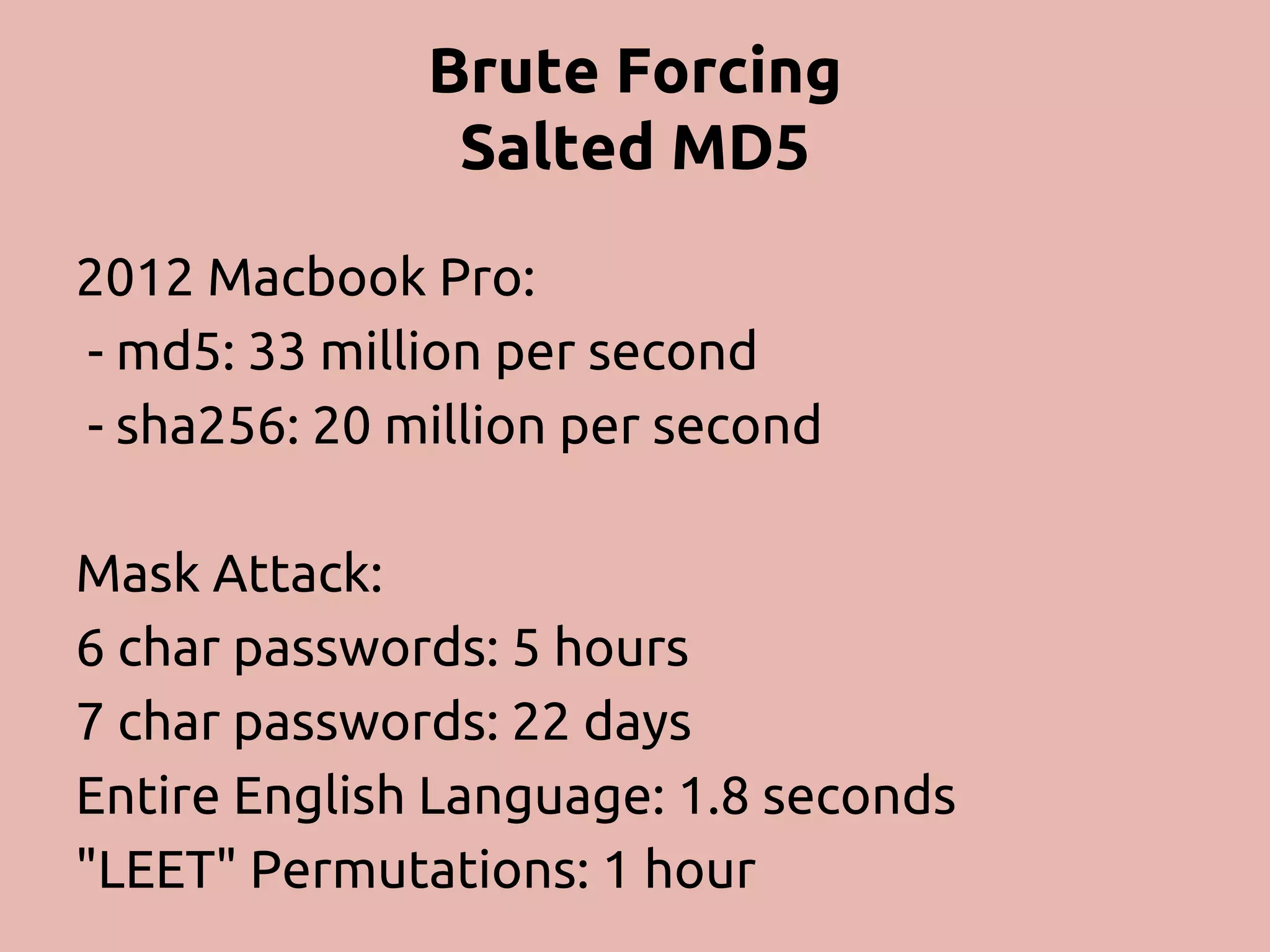
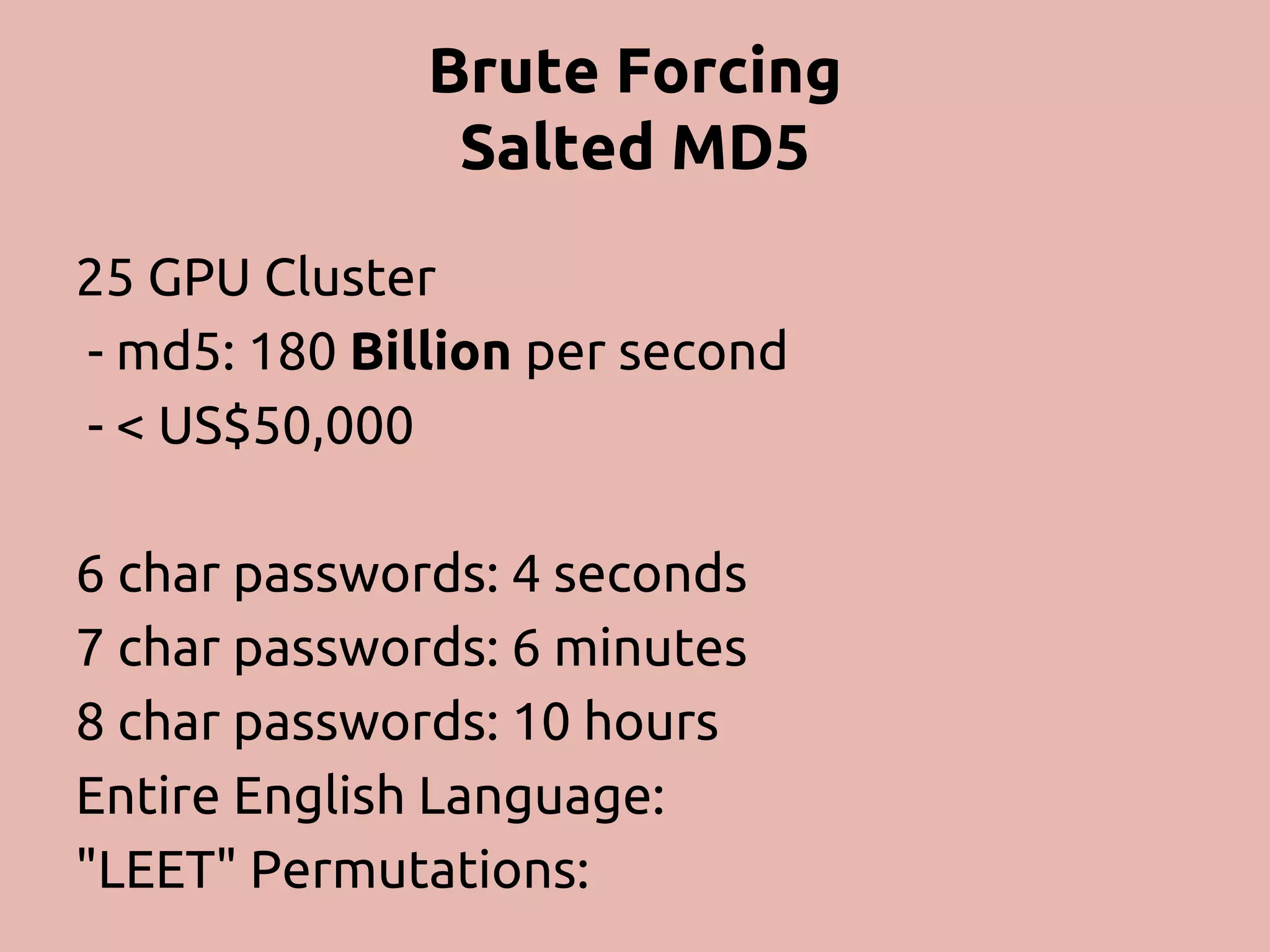
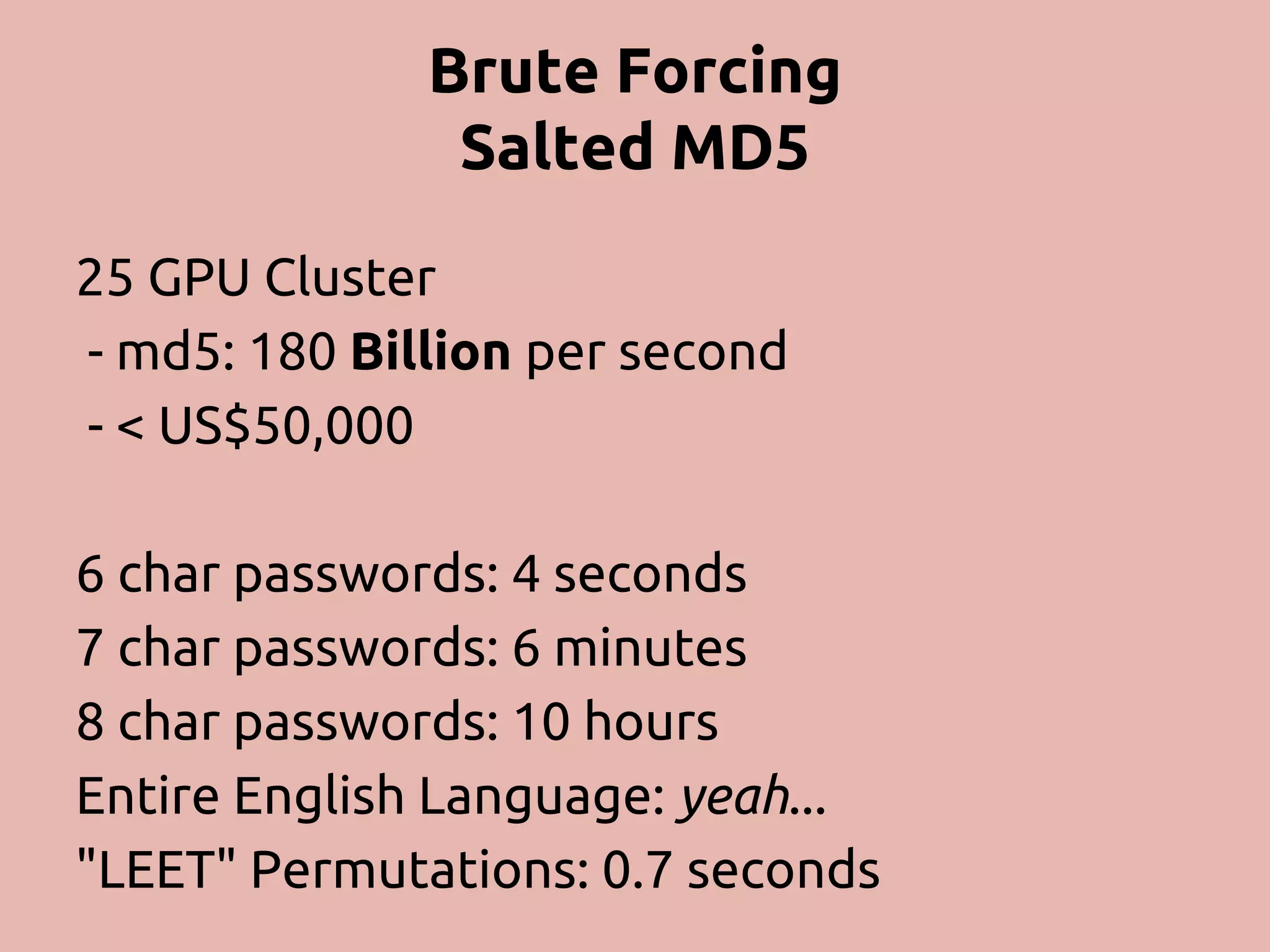
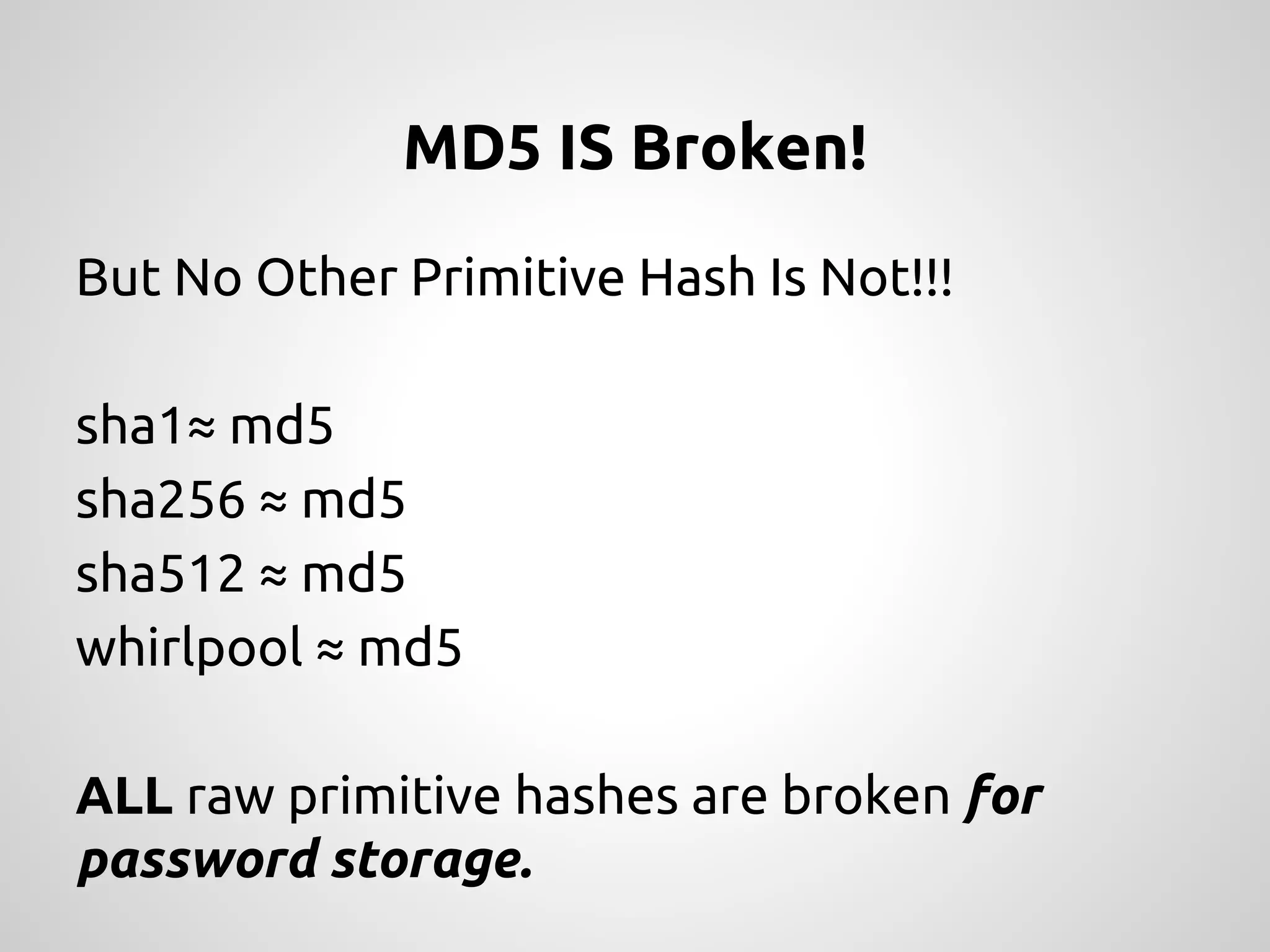
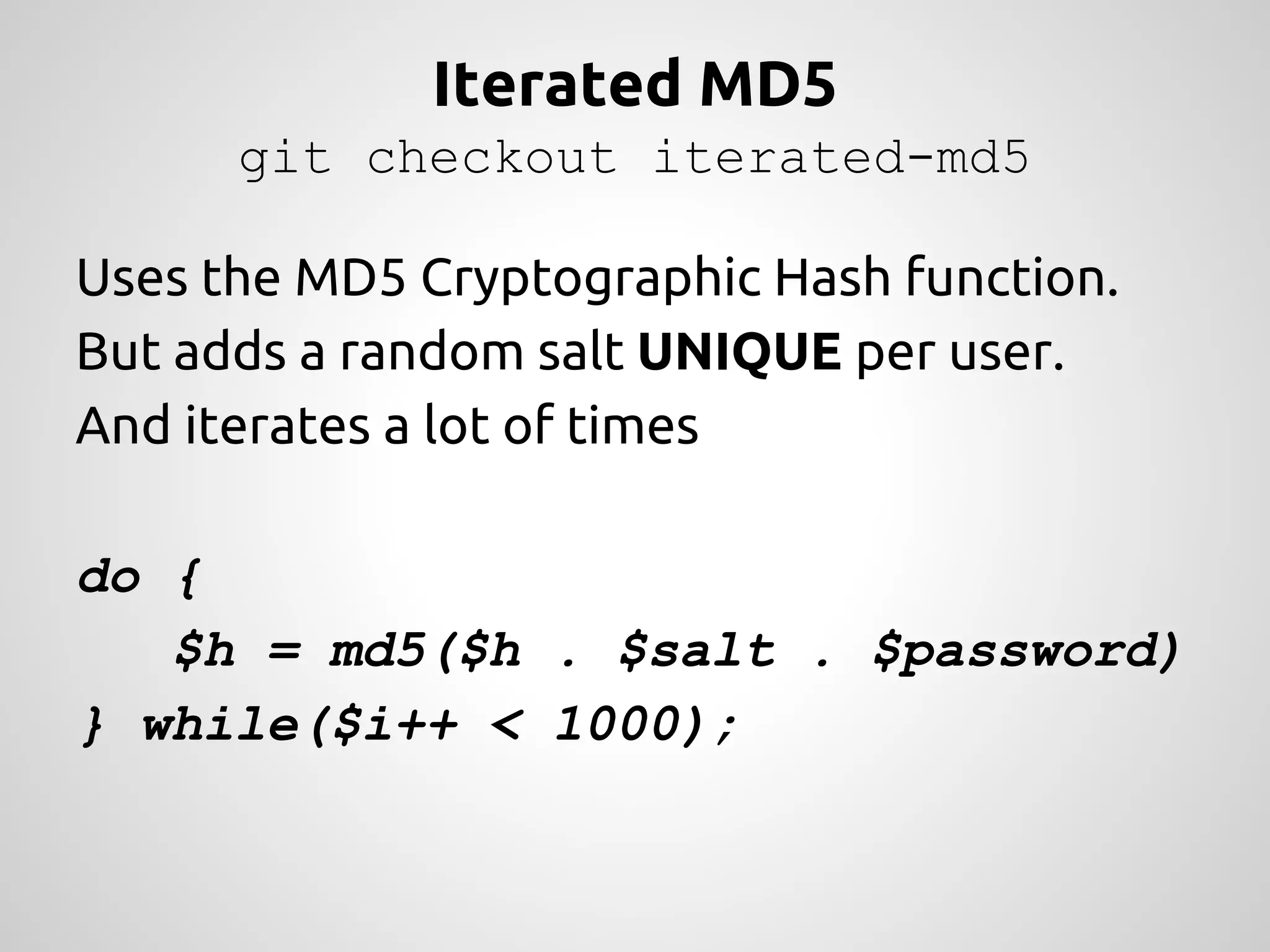
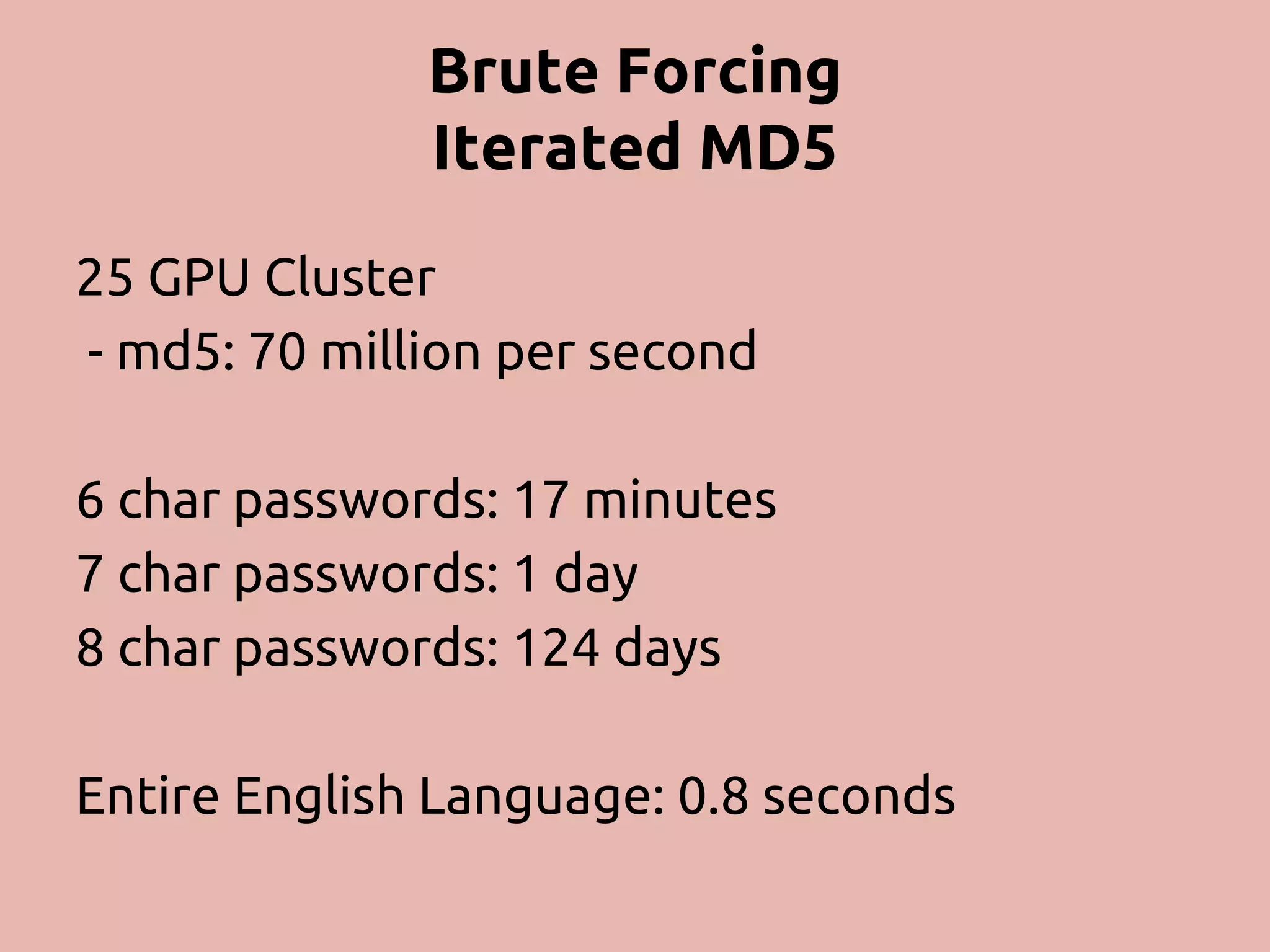
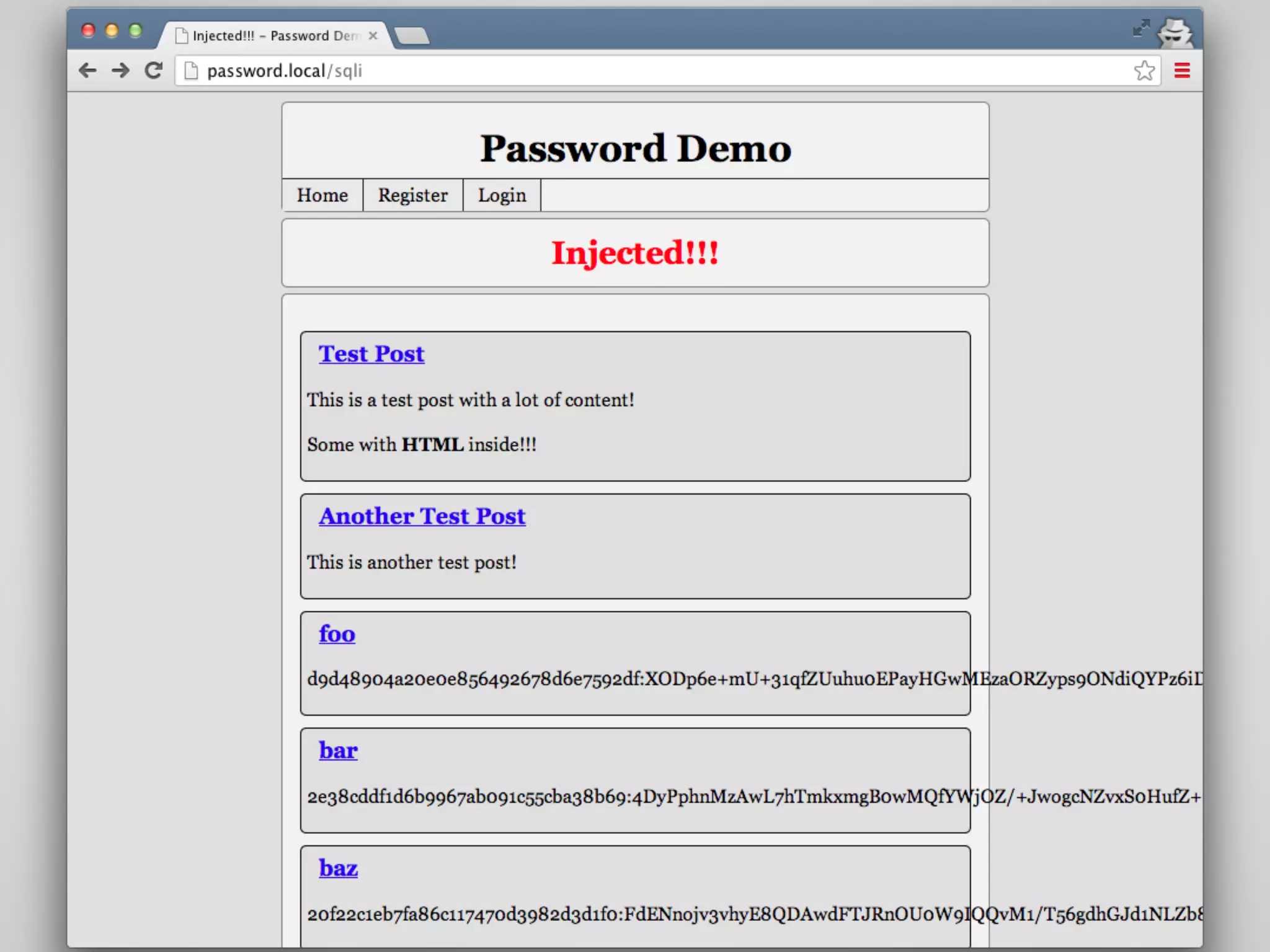
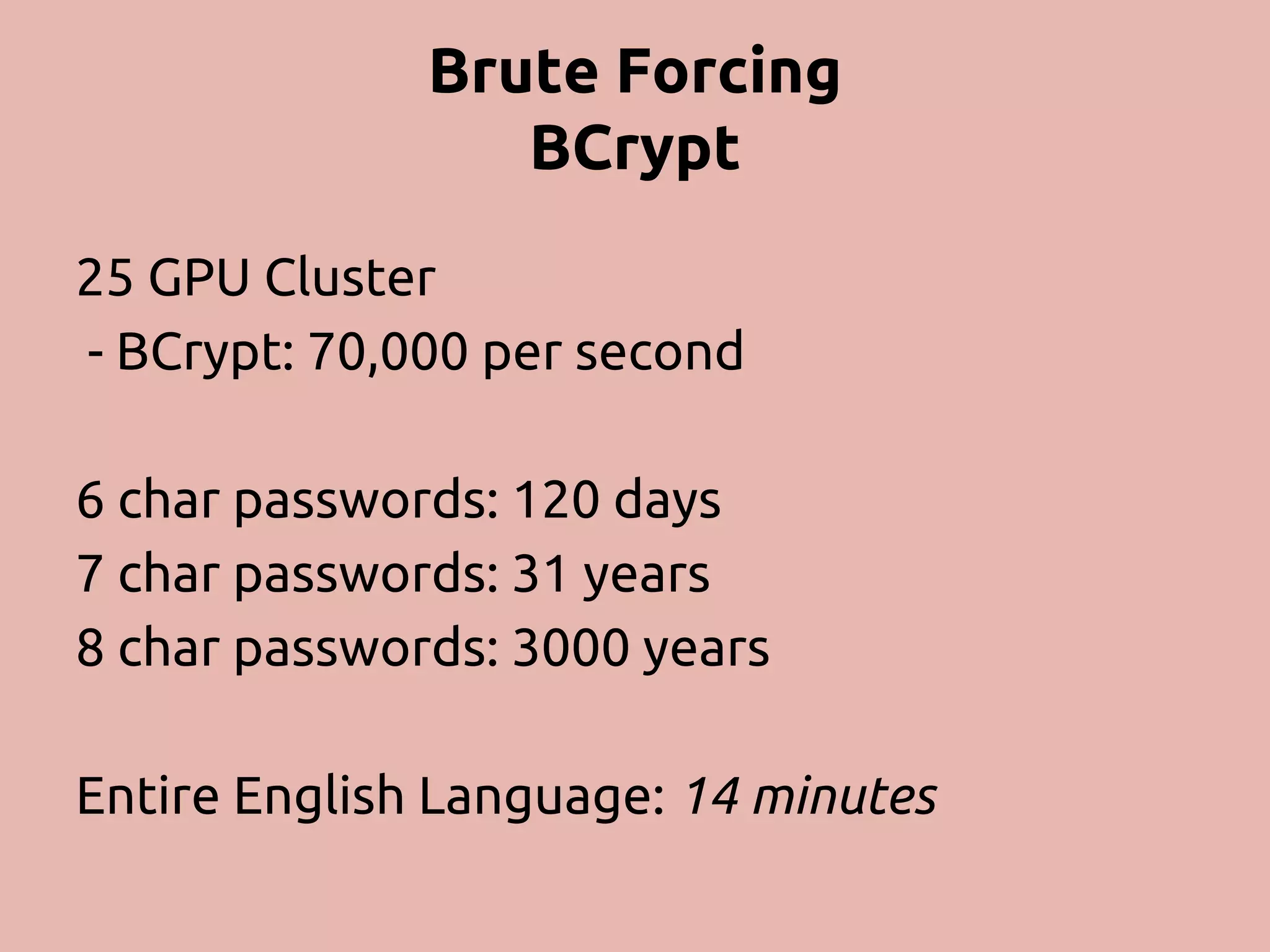
The document discusses various methods and strategies for password storage and attack prevention in PHP, emphasizing the vulnerabilities of plain-text and hash storage systems. It highlights the use of salting and various hash functions like MD5, PBKDF2, and bcrypt to improve security, as well as the limitations and effectiveness of brute-force attacks against these methods. Additionally, it introduces advanced concepts such as scrypt and the importance of using strong, random passwords and password managers.





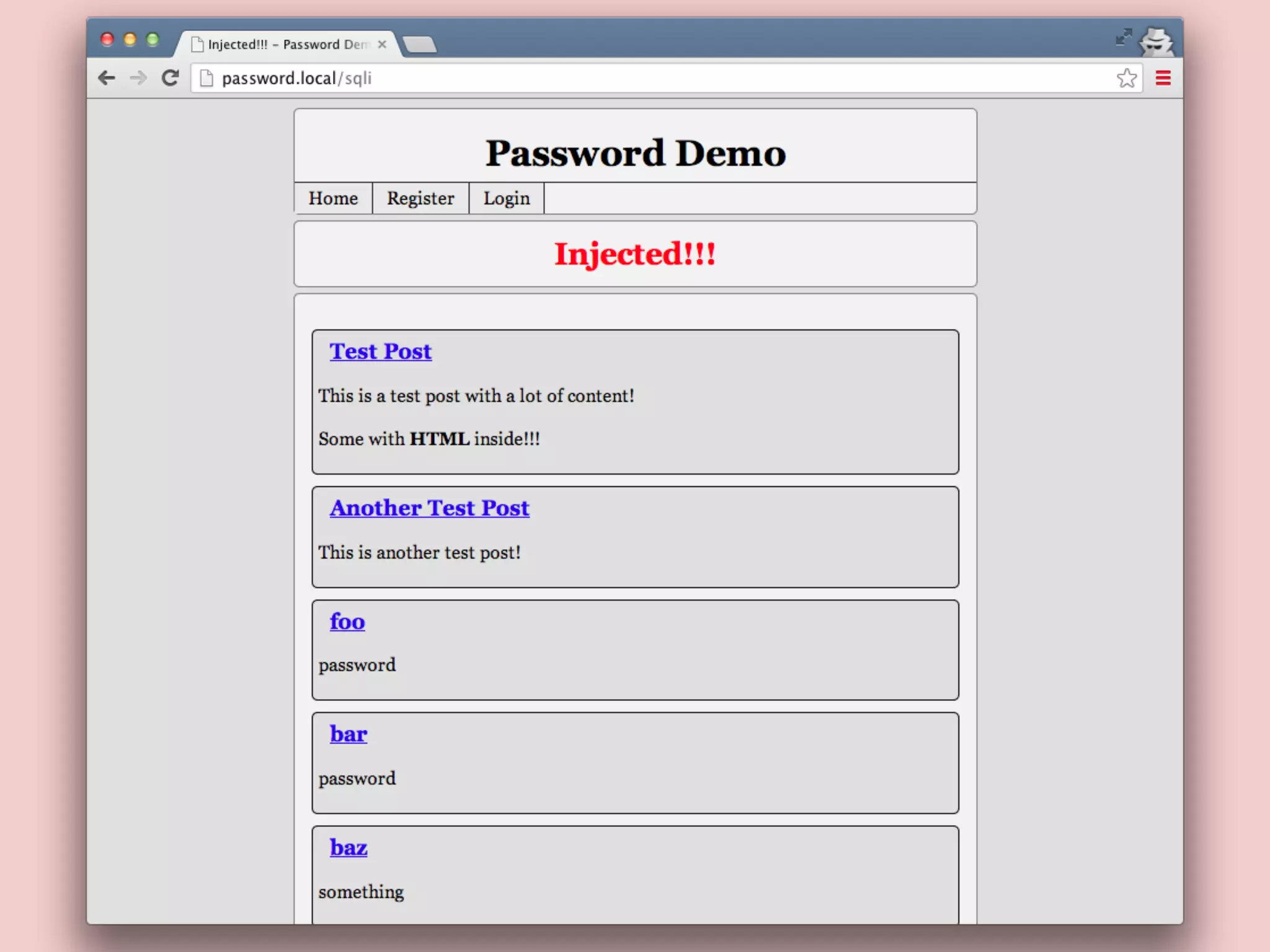







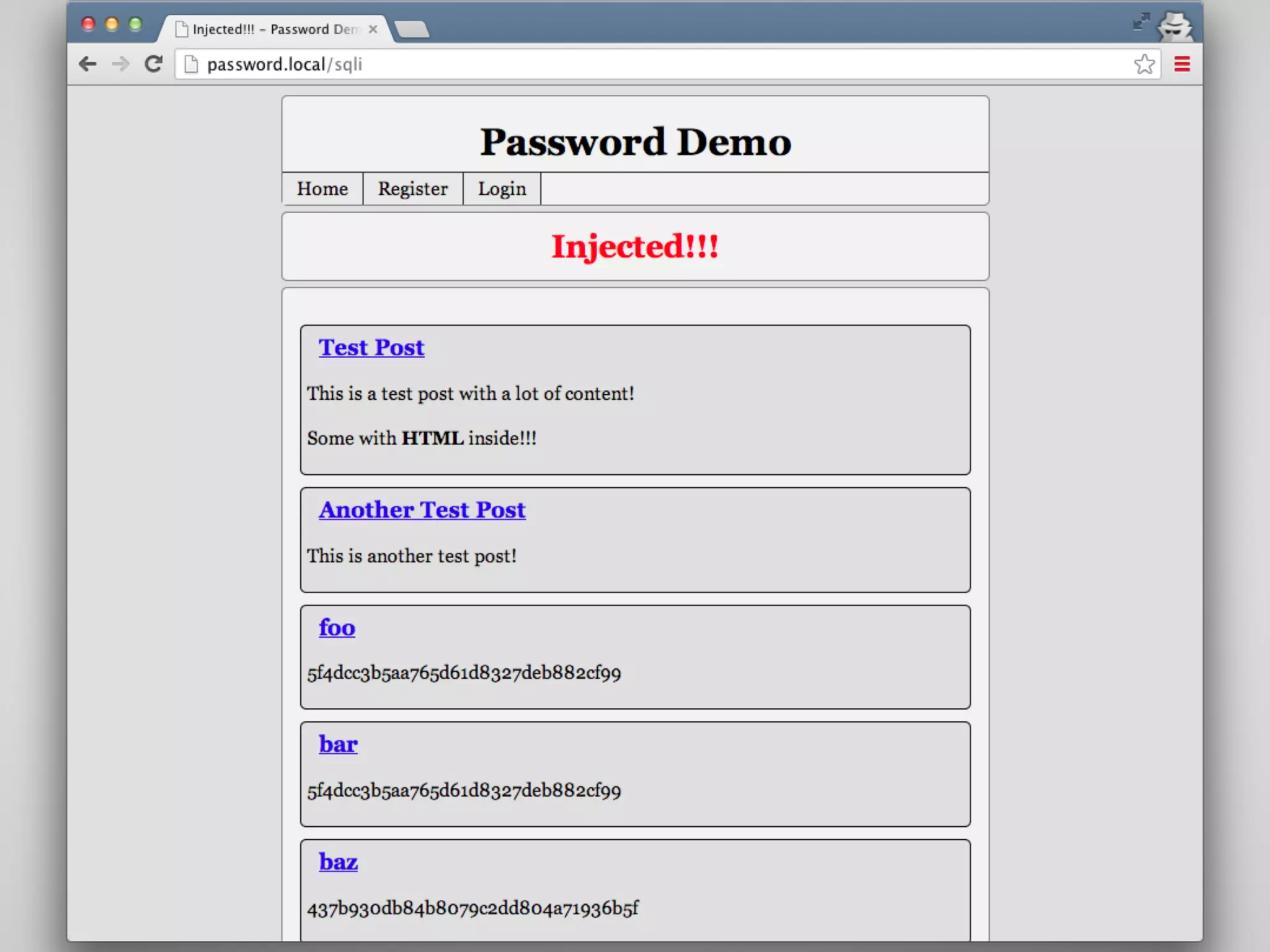

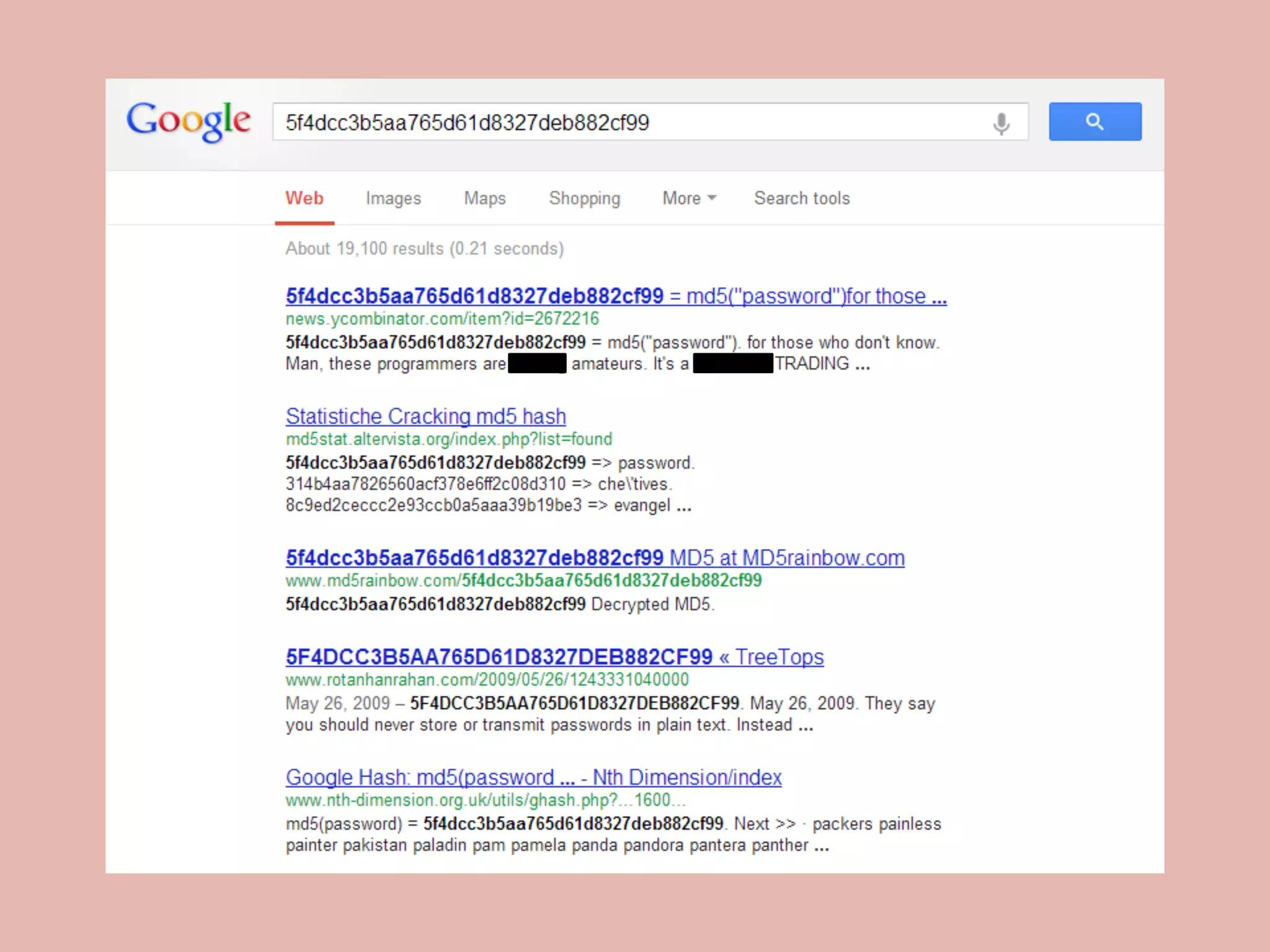
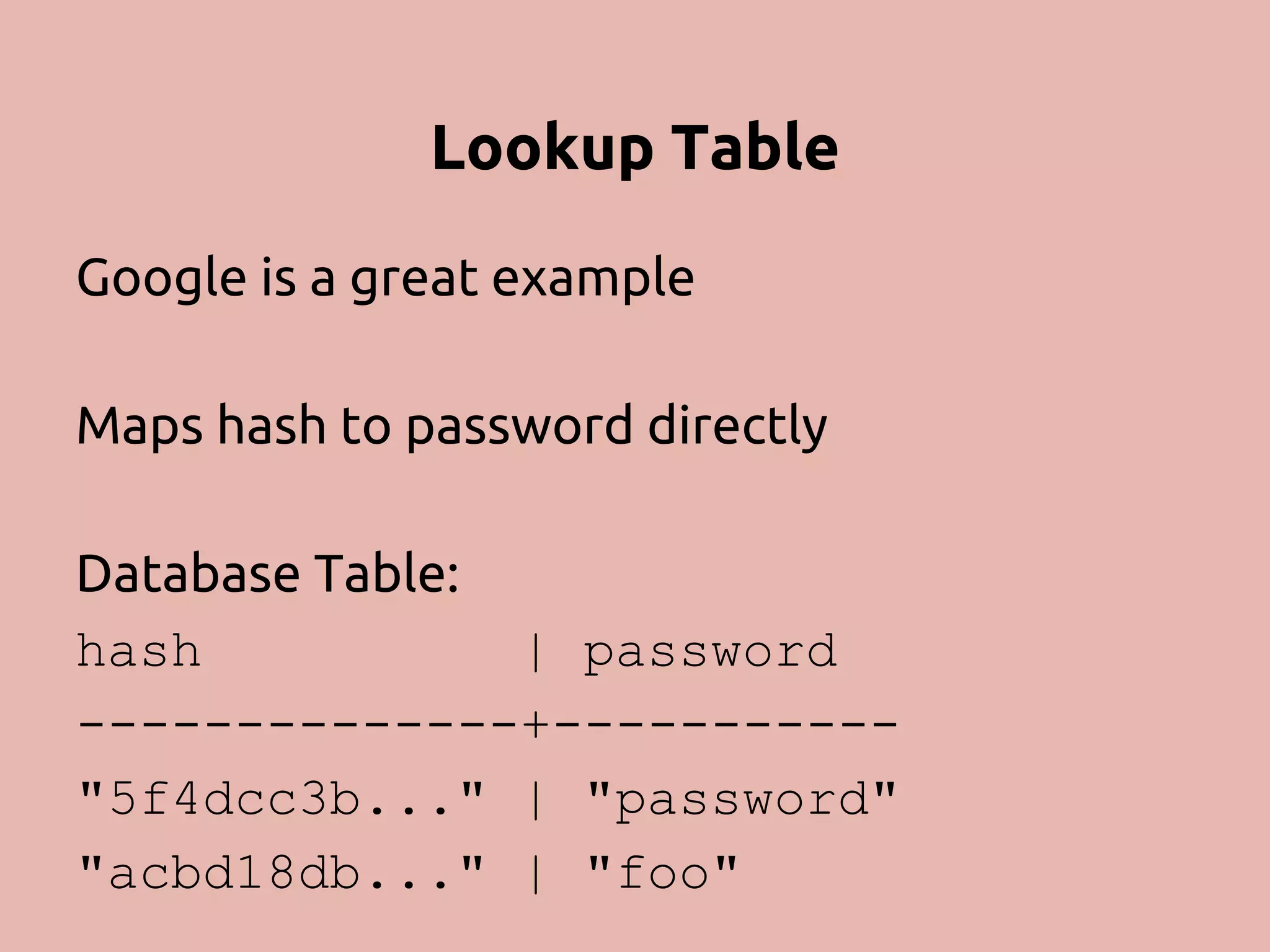





















![PHP 5.5 Password Hashing API git checkout password-compat A thin wrapper over crypt() - Simplifies implmentation - Strong random salt generation - Can specify cost as int option password_hash($pass, $algo, [$opts]) password_verify($pass, $hash) github.com/ircmaxell/password_compat](https://image.slidesharecdn.com/passwordstorageandattacking-phpargentina-141108051844-conversion-gate01/75/Password-Storage-And-Attacking-In-PHP-PHP-Argentina-63-2048.jpg)