This document introduces a new symmetric encryption system that combines an evolutionary algorithm-based ciphering system with a fragmentation method to enhance character frequency alteration and security. The encryption process involves generating two symmetric keys and applying evolutionary techniques to optimize the distribution of characters, followed by a fragmentation step to create uniformly sized lists for encryption. Decryption is conducted in two stages, utilizing the generated keys to recover the original message, and experimental results demonstrate the effectiveness of the proposed method.
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 DOI:10.5121/ijcsit.2015.7603 39 NEW SYMMETRIC ENCRYPTION SYSTEM BASED ON EVOLUTIONARY ALGORITHM A. Mouloudi Department of Computer Sciences, Ibn Tofail University, Kenitra, Morocco ABSTRACT In this article, we present a new symmetric encryption system which is a combination of our ciphering evolutionary system SEC [1] and a new ciphering method called “fragmentation”. This latter allows the alteration of the appearance frequencies of characters from a given text. Our system has at its disposed two keys, the first one is generated by the evolutionary algorithm, the second one is generated after “fragmentation” part. Both of them are symmetric, session keys and strengthening the security of our system. KEYWORDS Cryptography, cipher, symmetric encryption, evolutionary algorithm. 1. INTRODUCTION Basic cryptographic algorithms split into two families: symmetric algorithms, otherwise known as secret-key algorithms, which normally require a key to be shared and simultaneously kept secret within a restricted group, and public-key algorithms where the private key is almost never shared. From outside, this may give the impression that symmetric techniques become obsolete after the invention of public-key cryptography in the mid 1970's. However, symmetric techniques are still widely used because they are the only ones that can achieve high-speed or low-cost encryption. Today, we find symmetric algorithms in GSM mobile phones, in credit cards, in WLAN connections... Therefore, symmetric cryptology is a very active research area which is stimulated by a pressing industrial demand for low-cost implementations (in terms of power consumption, gate count...). In the article [1], we presented a new symmetric encryption system called ciphering evolutionary system (SEC). This system is based on techniques of the evolutionary algorithm [2],[3],[4]. This article was followed by another article, where we introduced a new system based on SEC [5], called “fusion” which is safer. In the article [6] we have generalized the SEC system at any chain formed of blocks of bits. In this paper we present a new encryption system based on the SEC system. This new system uses a different technique called “fragmentation”. It proceeds by a change of frequency of occurrence of characters of the clear message, using the SEC algorithm. After, it uses the fragmentation technique in order to have the character positions lists with approximately the same size, by a fragmentation of lists which have larger sizes, adding new characters. 2. SYSTEM DESCRIPTION Let M the message to be encrypted, consisting of n characters.](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-1-2048.jpg)
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 40 2.1. Problem formalization c1, c2, ..., cm are the different characters of M (m ≤ 256). Denote by Li (1≤ i≤m) the list of positions of the character ci in M and Card(Li) the number of his occurrences in M. Note: Li ∩Lj is empty, for i, j ∈[1, m], with i≠j. L1, L2, ..., Lm is a partition of the set {1, 2, ..., n}. The message M can be represented by the vector below: Table 1: Representation of the message by a vector Our goal is to change the maximum frequency of appearance of characters in the message M and thus establish the more disorder in their positions. For this, we change iteratively distribution lists on the different characters of M such that the difference between the cardinal of the new list L’i assigned to character ci and the cardinal of the initial list Li of ci is maximized. There, we realize that we are in front of an optimization problem. As evolutionary algorithms have proven effective in solving this problem, so we are appealing to these algorithms, including those applied to permutations problems. 2.2. First encryption: Application of the SEC algorithm Step 0: Coding An individual (or chromosome) is a vector of size m. Genes are the Lpi lists (1 ≤i ≤m). The Lpi th gene contains the new positions will be taken by the character. Step 1: Creating the initial population P0 composed of q individuals: X1, X2, ..., Xq. We call initial Ch-chromosome genes the lists L1, L2, ..., Lm (placed in that order) that represent the message before the application of the algorithm. We apply q permutations on Ch_initial in order to obtain an initial population who is q potential solutions to the problem. i: = 0. Step 2: Evaluation of individuals Xj is a Pi individual genes are: Lj1, Lj2, ..., Ljm. We define the evaluation function F of all individuals by F(Xj): )L(card)L(card)X(F i m 1i jj i −= ∑= Step 3: Selection of the best individuals We use the traditional method of the wheel to retain the strongest individuals. We introduce a control function that will eliminate individuals for which only minority of genes have changed values compared to the Ch_initial original chromosome. Since we are brought back to a problem of permutations with constraints, we then apply genetic operators adapted to this kind of problem. (c1, L1) (c2, L2) … (cm, Lm)](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-2-2048.jpg)
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 41 Step 4: Applications of genetic operators - Crossing MPX (Maximal Preservative X) This crossing is applied to selected individuals with a specific rate. According to [7] the best rate is on the order of 60% to 100%. - Transposition mutation: We choose the mutation that is to randomly switch between two genes on a chromosome. This operator is applied to the individuals produced by crossing with a suitable rate, preferably from 0.1% to 5% [7], [8] Place new offspring in a new population Pi+1. Repeating steps 2, 3 and 4 until a stop criterion. Set the stop condition: The function F is bounded for any individual Xk. Indeed, Theoretically and mathematically speaking, the function F admits a maximum since it is bounded. According to some research findings convergence of an evaluation function is provided. This is confirmed in the working examples. Last phase of our algorithm: Final_Ch denote the final solution given by our evolutionary algorithm. Swapping that can go from Ch_initial to Ch_final is our symmetric key. This key will be called genetic key. 2.3. Second encryption: Fragmentation of the lists 2.3.1 Informal description of the algorithm The message M’ obtained in the first part consists of the same characters c1, c2, ..., cm in M which are associated lists L'1, L'2, ..., L’m. These lists are generally of different sizes. The purpose of the second part of our system is to transform the message M’ in a message M” whose lists associated with its characters are almost the same size, this by breaking down the lists of larger sizes in other lists, which are associated with new characters. n*2))L(card)L(card( )L(card)L(card)X(F ik m 1i ik m 1i k i i ≤+≤ −= ∑ ∑ = =](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-3-2048.jpg)
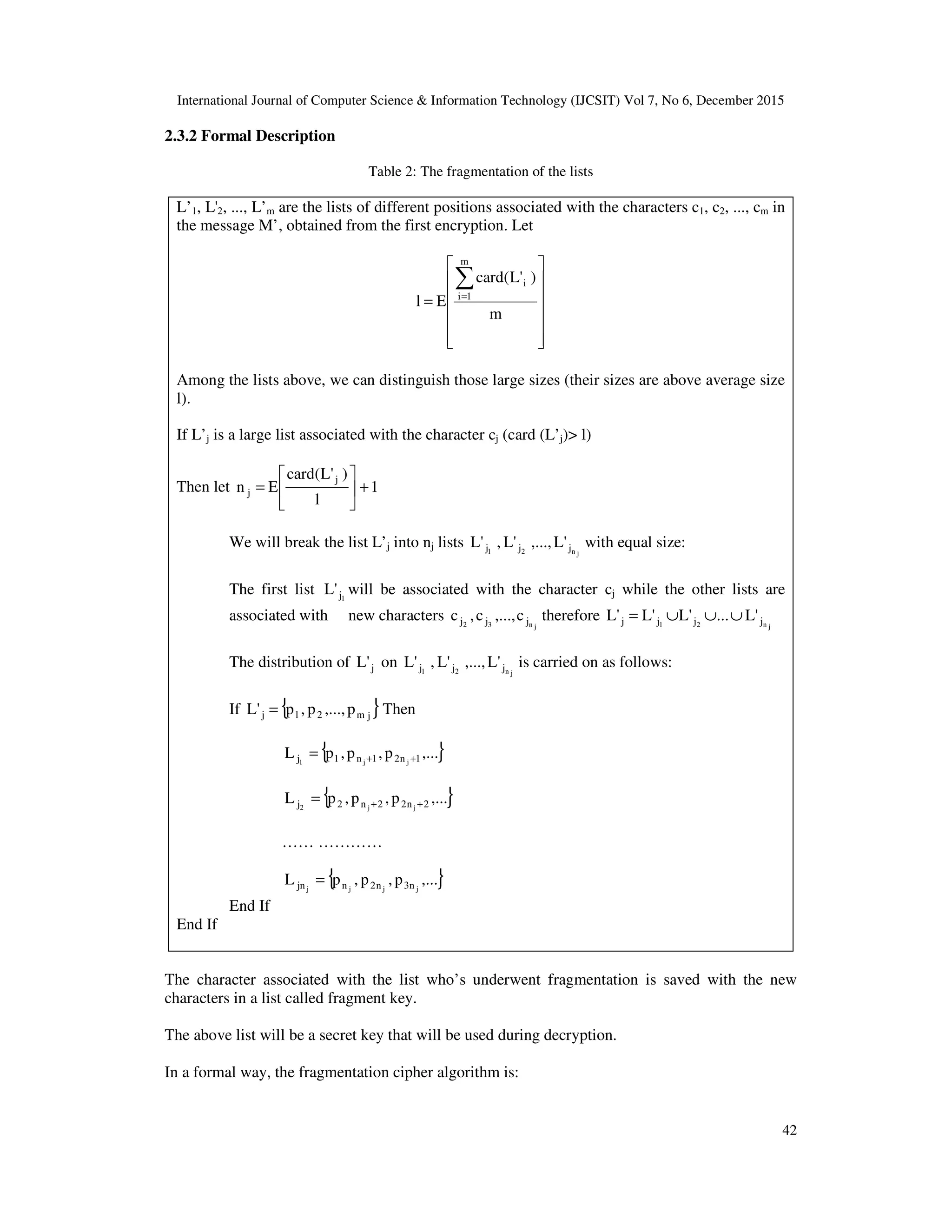
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 43 Table 3: The fragmentation cipher algorithm Data: Message M', obtained from the evolutionary algorithm SEC Results: Encrypted Message M" and the fragment key Beginning of the algorithm Determine the lists of character positions m21 'L,...,'L,'L associated with characters m21 c,...,c,c of the message M'. Let = ∑= m )i'L(card El m 1i , where E [x] is the integer part of x (ie the largest integer less than or equal to x). For j: = 1 to m do If l)'L(card j > then / * j'L is a large list * / Let 1 l )'L(card En j j + = and )'L(cardm jj = / * Fragmentation of j'L */ Let jn lists jn21 jjj 'L,...,'L,'L initially empty, such as 1j'L is associated with jc and jn2 jj 'L,...,'L are associated respectively with novels characters jn2 jj c,...,c / * Distribution of j'L on jn21 jjj 'L,...,'L,'L */ Suppose { }jm21j p,...,p,p'L = For k = 1 to jm do )nmod(k:d j= (i.e, d is the remainder of the integer division jn by k) Move kp to list dj'L End of For Add [ ])c,...,c,c( jn2 jjj to fragment key End If End of For End of the algorithm](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-5-2048.jpg)
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 44 2.4 Decryption Decryption is performed in two essential steps: First step: From the message M" and using fragment key we find the message M'. Second Step: From the message M' and using genetic key we find the message M. 2.4.1 First decryption For each key-element fragment [ ])c,...,c,c( jn2 jjj we replace in M'' all occurrences of the characters jn32 jjj c,...,c,c by character jc . This gives the message M’. 2.4.2 Second decryption Decrypting the message M’ is done in two steps: In the first step, we represent the cipher text, by a vector of lists as we have done for the plaintext message. Denote c'1, c'2, ..., c'm the different characters of M’ and L'1, L'2, ..., L’m the lists their respective positions in M'. In the second step, through genetic key, the characters will find their corresponding position lists in the plaintext message. Indeed, the genetic Key is a permutation of {1, 2, ..., m} that we can represent by a vector with size m, denoted Key, such that: Key (1) = p1, Key (2) = p2, ..., Clef (i) = pi, ..., Clef (m) = pm where The c'p1 character will be associated with the list L’1, the c'p2 character will be associated with the list L’2. The c'pm character will be associated to the list L'm. Thus, we get the message M. 3. EXPERIMENTATION We applied our algorithm to several messages of different sizes, and for each of them, we make the application for different sizes of population. Then we record the value of the convergence of the fitness function, the number of the generations reached at the time of this convergence. Thus we can select the size of population that gives best value of evaluation function. In this paper, we consider for example two messages. For each message we applied, first, the SEC algorithm, leading to a new message M ', after using the deduced genetic key. Then, and as the second step of encryption, we cut the lists of positions associated with the most frequent characters of the message M into lists hose size is in the average. These new lists will be assigned to new characters, to finally obtain the encrypted message M ". First message: (The Size is 882)](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-6-2048.jpg)


![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 47 Table 11: Message deduced, after first step of encryption E bsMpCypn,iby itycrf, cs. proters Ehe cotfipwntyalityAEf mescagTr, but other terhniquercE. Mrstypl Ebederwto prMtyct the intygripyAand autherbypstyAof E.mersage; fotMexampCo, v erif)cs.ipn of a mersage Euthentipatyotbcstwr(MAC) or a digipy. EcgnatujM.gStanbw.ds for Esyptygraphic Eof)ware E.bwha.dwarerto perf)tm EnbrMption E.e wqpwry availo.no,ibut sucssrsfulooAujipg EncsypCyon tyterburerEerurityAmay be a chS.oonging pCMblem.gA sc pgTo errotMin EcAtem dwrignbEr exerujyotbcan aloow sujcersful E.ta.k;.gSumetimkr an E .werMa.y ca.bobny.n unerbrMptedwEnformatipn withoujyEwpMctyy ujdoing thSrenbr Mptipt.gSee, e.g., Eraff)c E.alysip, TEMPEST, otMTrojan hSrsc.DigTpy.oEigTatujM anb wenbrMptiotbmuscybeE.plopd to thSrciphertexeywhenbit EpcEsMatyrw(typica.loAEn Eh erscme devips ujcrwto compCte thermersage) to avotd EympCripg; Etherwipe anyAnotw betw qerbthe senderManbwEhSrerbrMptyon Egent csujd poterbialoy tamper withSEp. EnbsMpCing E. thSrtime of)creayptbipconly serure if thSrencsMptyotbEwvips ityerf has nbtybnenbtympe red wqph.. After applying second encryption step we obtain the following fragmentation key: Table 12: The fragmentation key of the second message ( ; (!,",#,$));(s; (%));(e;(&,',*,+));(t; (-,/,0));(I; (1,2)); (o; (3.4)); (l; 5)); (n; (6,7));(c;(8));(r; (9,:));(y ; (<));(a ; (=,>));(d; (?)) And the following encrypted message: Table 13: Message deduced after the second step of encryption E bsMpCyp6,ib<1-ycrf,!8s."p93/&rs#Eh'$84tf2pw6-y=51/yAEfm+%c>gTr,!bu0"3th&: #'rh72qu*rcE.Mr%/yp5Eb&?'rw04"p9Mty8-#/h+$160yg:2p<A=7?>u-h&rbyps0yA3f"E .m'r%=g*;$f4tM+x>mpCo,v&92f)8s.1p6!3f"=#m'r%>g*$Eu-h+7/2p=0y4tb8stwr(MA C)!3:">#?1g2py.$Ecg6=-ujM.gS/>7bw.?%f4:!Es<p0yg9=ph18"E3f)w>:'#E.bwh=.?w >9*r-4p+:f)tm!E6b9Mp/237"E.&#wqpwr<$=v>15o.no,ibu0%u8ssr%fu5ooAuj2pg"E 68s<pCy47#-yt&rbu9'rE*ru:1/yAm=<!b+">#8hS.oo6g27g$pCMb5&m.gA%cpgTo!* 9:4tM16#EcA0+m$?wr2g7bE9&x'rujy3tb8=6">5oow#%uj8*r%fu5$E./=.k;.gSum+ 01mkr>7!E.w&:M=.<"8>.b3bny.6$u7'rb9Mp-*?wE6f4:m=/1p7w20h3ujyEwpM8-y<" uj?416g#/hSr&7b9Mp02pt.gS'*,+.g.,!E:>ff)8"E.=5<%1p,#TEMPEST,$3tMT94j>7- hS:%c.D2gTpy.oE1gT=/ujM">6bw'7b9Mp023tbmu%cyb*E.p5op?!-4"/hSr81ph& :0'xeywh*6b2-EpcEsM=/yrw(0<p18>.5oAE7$Eh&r%cm'?*v2ps!ujcrw-3#84m pCt&$/h'rm*r%=g+)03!>v4t?"EympC91pg;#Eth&:w2p'$=6<A73twb+/wq&r b0h'"%*6?+rM>7bwEhSr&rb9Mp-y46Eg'7/!8suj?"p30*rb1=5o<#->mp+:$w2/hSEp.- E6bsMpC17g!E."/hSr02m&$4f)89'=.yptb1pc365<"%*ru:+#2f$-hSr&78sMp/y4tbEwv 1ps!20y+rf"h>%#6btybn&7b-ymp'9*?wqph.. Compared with IDEA and AES systems [9], [10], we noted that our system is extremely fast, either in encryption or decryption.](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-9-2048.jpg)
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 48 4. DISCUSSION We will compare our encryption system in a well-known symmetric encryption system. This is IDEA. The latter is considered by specialists as one of the best private key crypto systems. It is used by PGP (Pretty Good Privacy) to encrypt data. The length of the key is 128 bits. As for our system the key is automatically generated and it is at least of the order of 30 * 8 = 240 bits (it can even go up to 256 * 8), because we can always assume that the number of different characters in the text is at least equal to 30 (if we can add it so that it is); even larger because more resistant to cryptanalysis by exhaustive search. In addition, this key is truly random whereas IDEA is not. IDEA operates on the plaintext, block by block; which is an asset to differential cryptanalysis, while our system acts on the plaintext in a comprehensive manner. So it is, firstly, away from such a cryptanalysis, on the other hand, it is less expensive. However, the only formidable cryptanalysis in our case is that based on the study of the frequency of occurrence of letters in the text. Now with change frequencies of appearance of characters, performed on the plaintext, and the introduction of new characters, thus ending any attempt of this kind of attack. 5. CONCLUSION In this paper we have introduce a new symmetric ciphering system, based on evolutionary techniques. Our system possesses two keys, the genetic key and the fragment key. The genetic key is generated by the evolutionary algorithm, and whose size is very important. It resists much better to cryptanalysis via exhaustive search. The fragment key is generated by the fragmentation algorithm. Its application enhances the security of the system against attacks based on the study of frequencies. These keys are session keys and randomly generated by our system, Contrary to well-known crypto-system such as DES, IDEA or AES [9], [10]. Through this work, we reached two objectives. The first one is the introduction of new method of ciphering whose major advantage is strengthening the system against the most formidable attacks, as for the other advantages, they are mentioned above in the discussion. The second objective is to exploit the evolutionary algorithms in order to conceive and realize a ciphering system that benefits from all its qualities. Despite the advantages of our system over other symmetric systems, we can’t mathematically prove, nor claim, that our system is unconditionally secure, nor perfectly secure. Only Vernam cipher or on-time-pad is proved unconditionally secure. Shannon himself has demonstrated in the article [11]. REFERENCES [1] F. Omary, A. Tragha, A. Bellaachia, A. Mouloudi "An Evolutionary Algorithm to Cryptography ". ICCMSE 2005 [2] Catherine KhamPhang. BOUNSAYTHIP "Algorithmes heuristiques et évolutionnistes" Thèse de doctorat université de Lille.Octobre 1988. [3] Goldberg D.E. " Genetic algorithms in search optimisation & Machine Learning " (Addison-Wesley. Publishing Company, Inc) 1989. [4] Mühlenbein H., "Evolutionary Algorithms: Theory and applications" (Wiley) 1993. Lecture Series on computer and Computational Sciences Vol.4, 2005, pp. 1749-1752 [5] F. Omary, A. Mouloudi, A. Tragha, A. Bellaachia, “ A new ciphering method associated with evolutionary algorithm” December 2005. Accepted by ICCSA 2006 and will be published by Springer-Verlag Lecture Notes in Computer Science series (LNCS, SCIE).](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-10-2048.jpg)
![International Journal of Computer Science & Information Technology (IJCSIT) Vol 7, No 6, December 2015 49 [6] A. Mouloudi, F. Omary , A. Tragha, A. Bellaachia, “An Extension of Evolutionary Ciphering System”, 2006 International Conference on Hybrid Information Technology. November 9th ~ 11th, 2006, Korea [7] Grenfenslette,j.j, "optimisation of control parameters for genetic algorithms", IEEE translation on systems Man, and cybernetics, Vol 16 N°1 pp122-128.1986. [8] Christophe Caux, Henri Pierreval, Marie-Claude Portmann, " Les algorithmes génétiques et leur application aux problèmes d’ordonnancement ", APII. Volume 29-N° 4-5/1995, pp. 409 - 443. [9] Alfred J.Menzes , Paul C. Van Dorschot , Scott A. Vanstone, Handbook of Applied Cryptography CRC Press fifth Printing (August 2001) [10] Douglas R. Stinson, Cryptography – Theory and Practice, CRC Press 1995 ISBN 0-8493-8521-0 [11] Claude Shannon, “ Communication Theory of Secrecy Systems”, Bell Systems Technical Journal (1949). AUTHORS A. MOULOUDI was born in 1959 in Morocco. He received the B.S degree in applied mathematics from Mohamed V University in Morocco at 1982; Master in Computer Science from the University Mohammed V, at 1984; Ph.D in Computer Science from the same university, at 1988. He obtains Habilitation to direct academic research in Computer Science, from Ibn Tofail University in Morocco, at 2008. Currently, A. MOULOUDI is a member of the laboratory MISC (Information Modeling and Communication System), at the sciences faculty, Ibn Tofail University, in Morocco.](https://image.slidesharecdn.com/7615ijcsit03-160108053114/75/NEW-SYMMETRIC-ENCRYPTION-SYSTEM-BASED-ON-EVOLUTIONARY-ALGORITHM-11-2048.jpg)