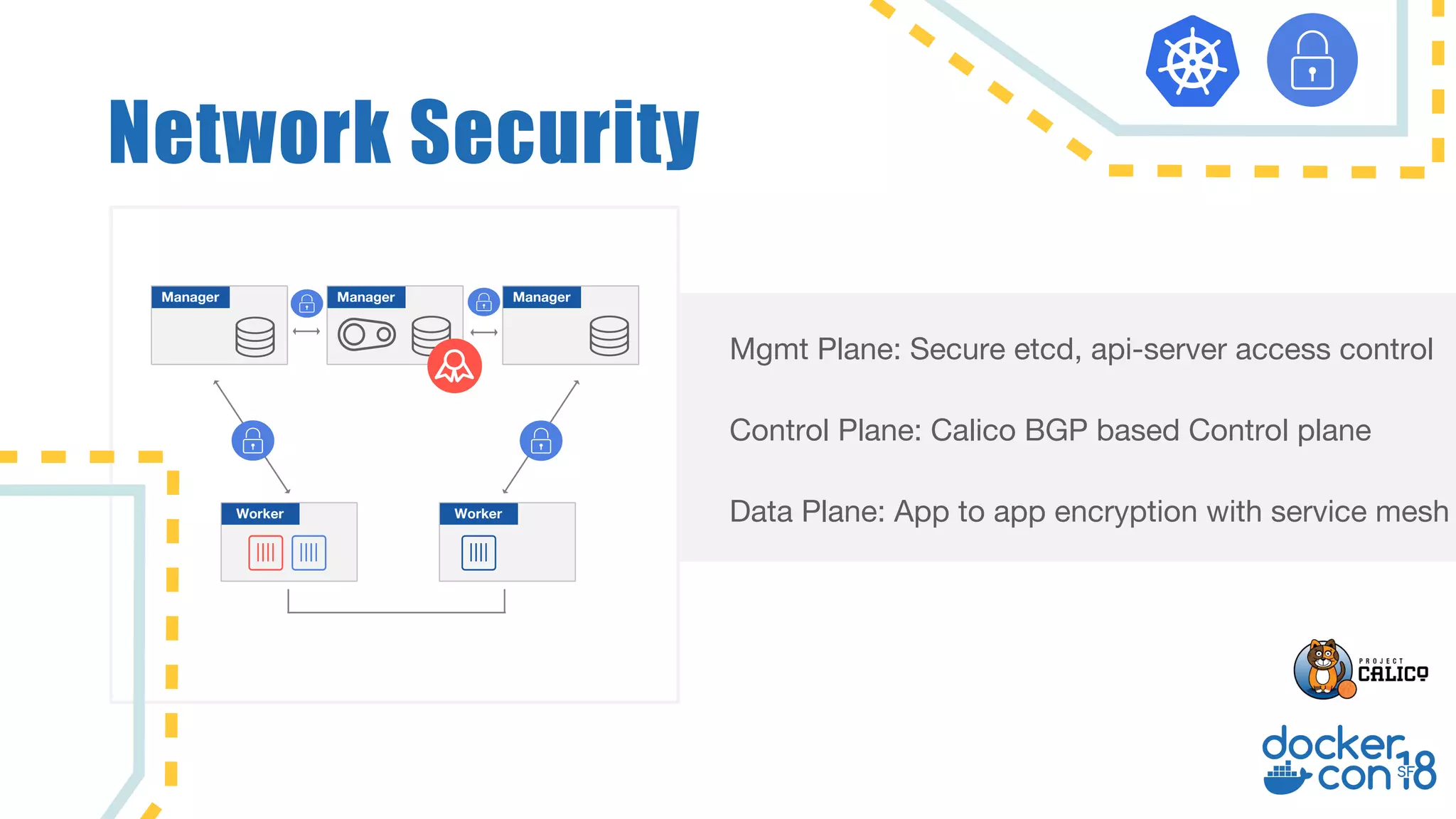
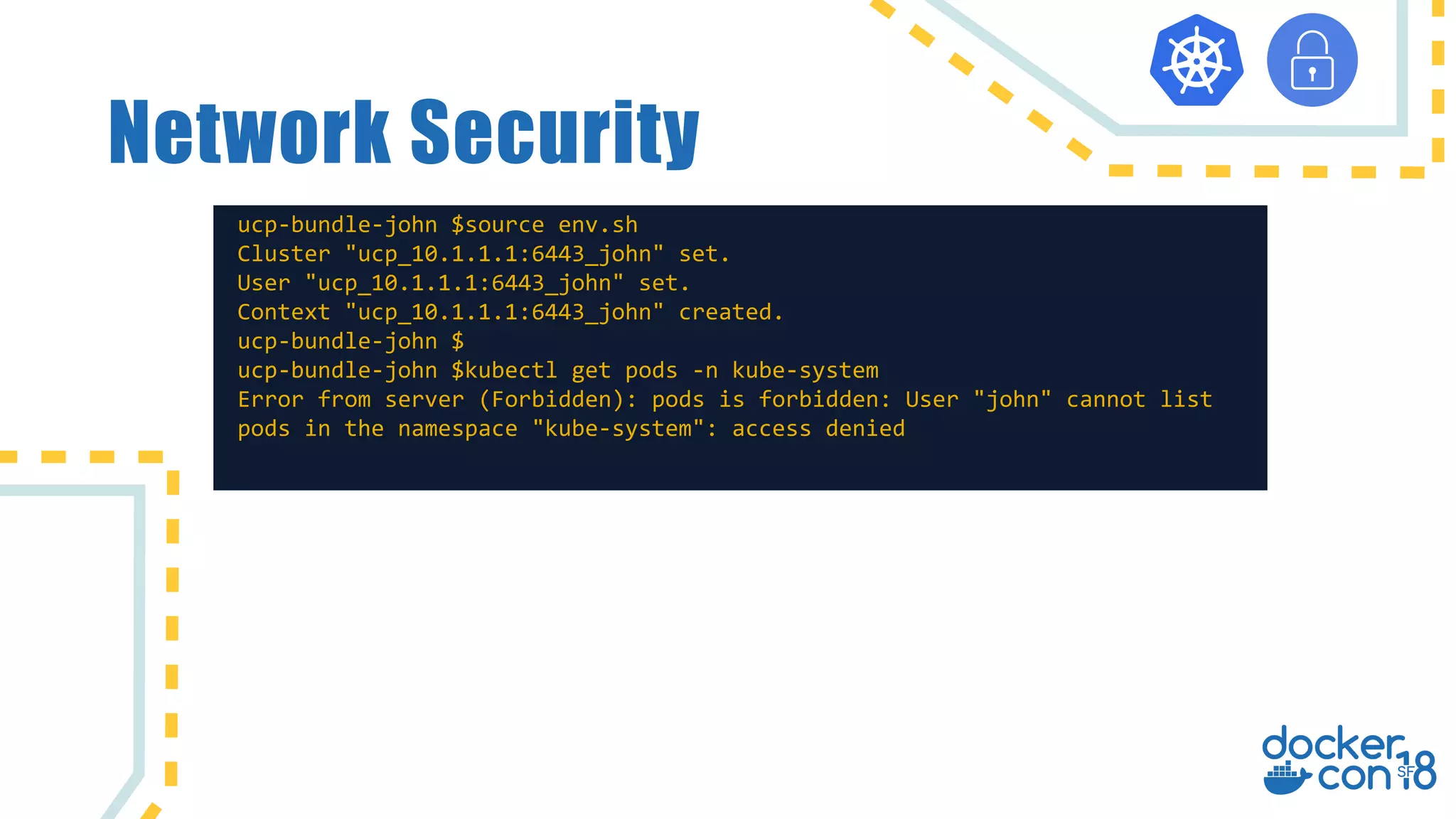
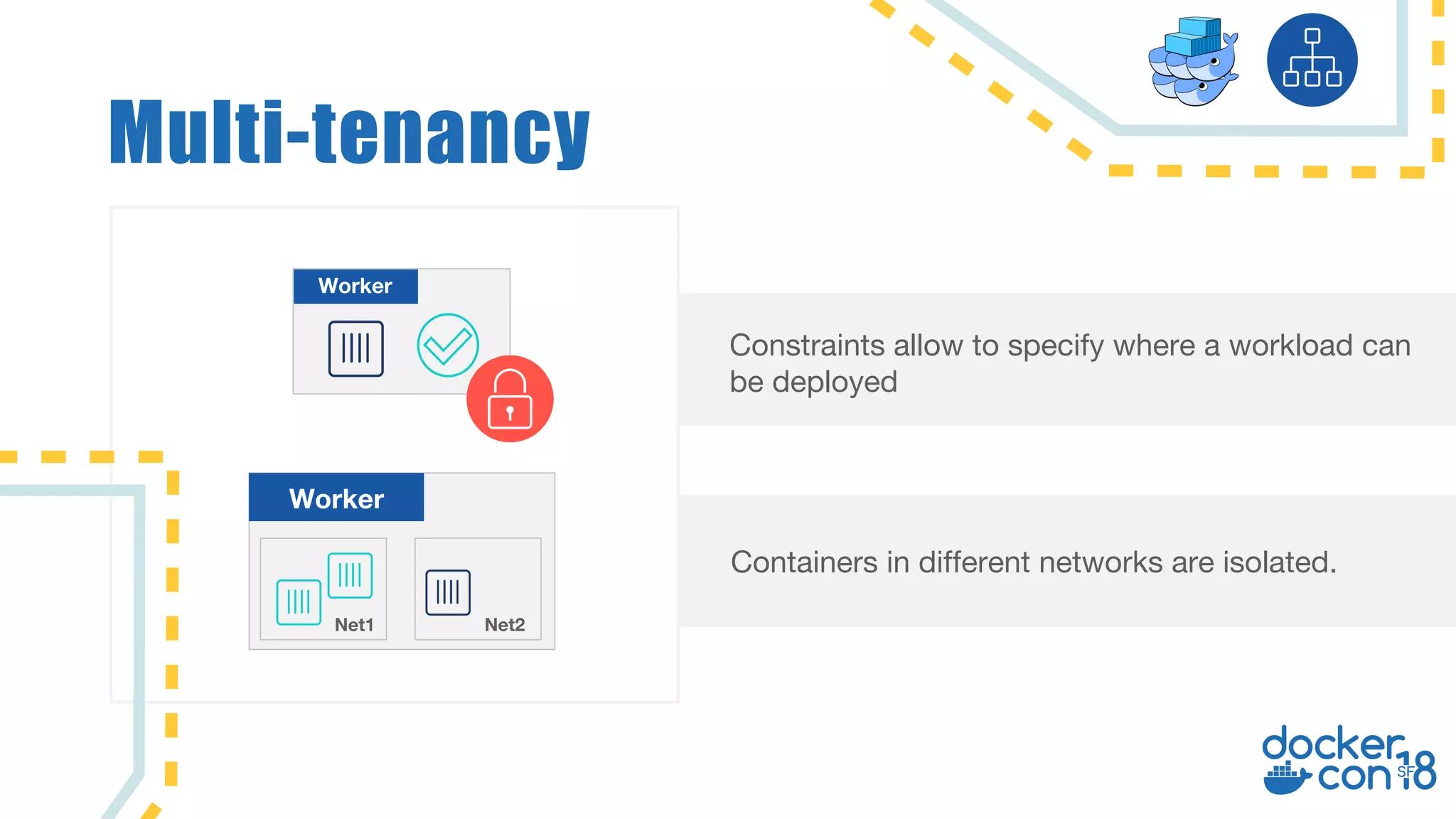
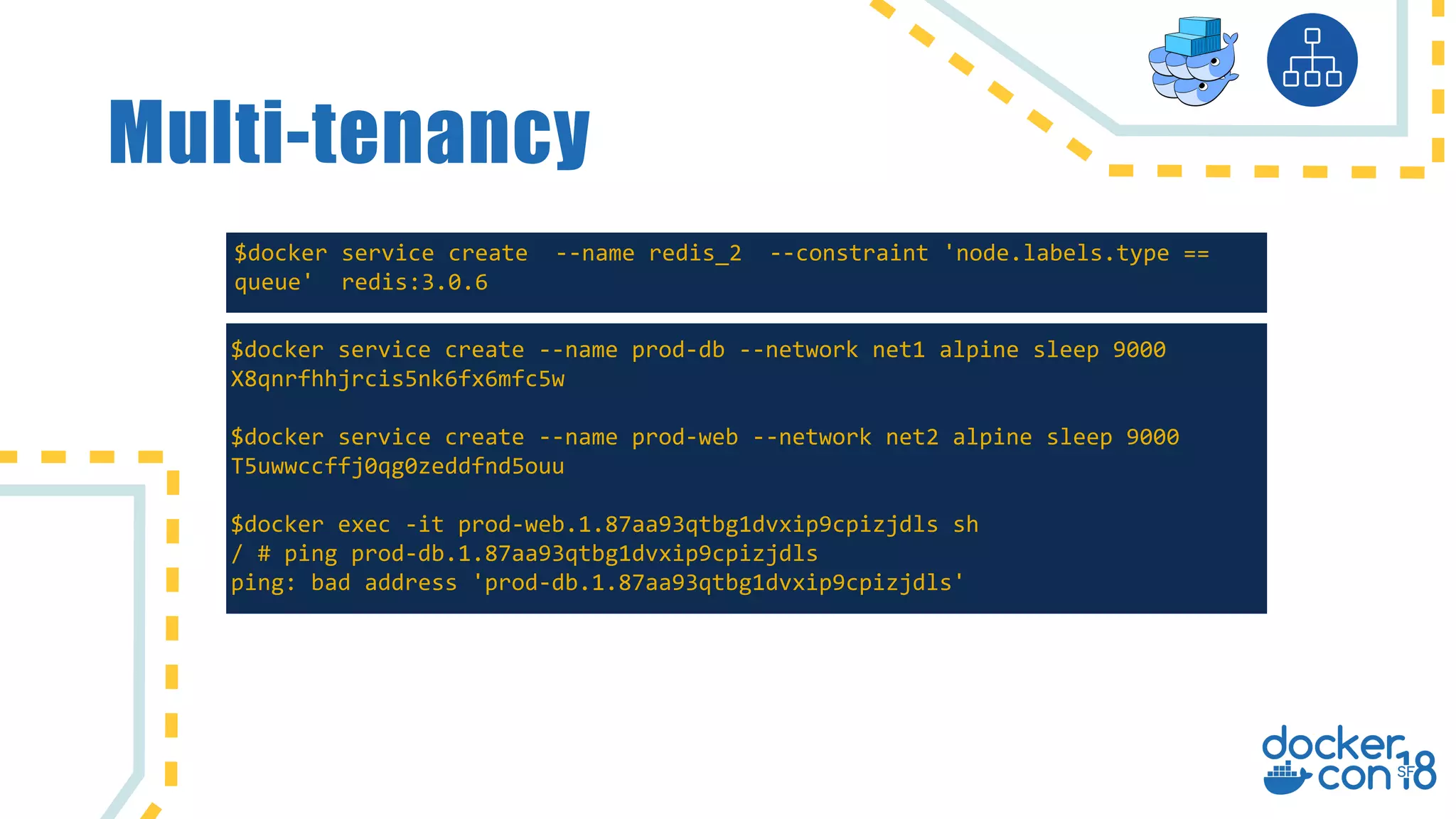
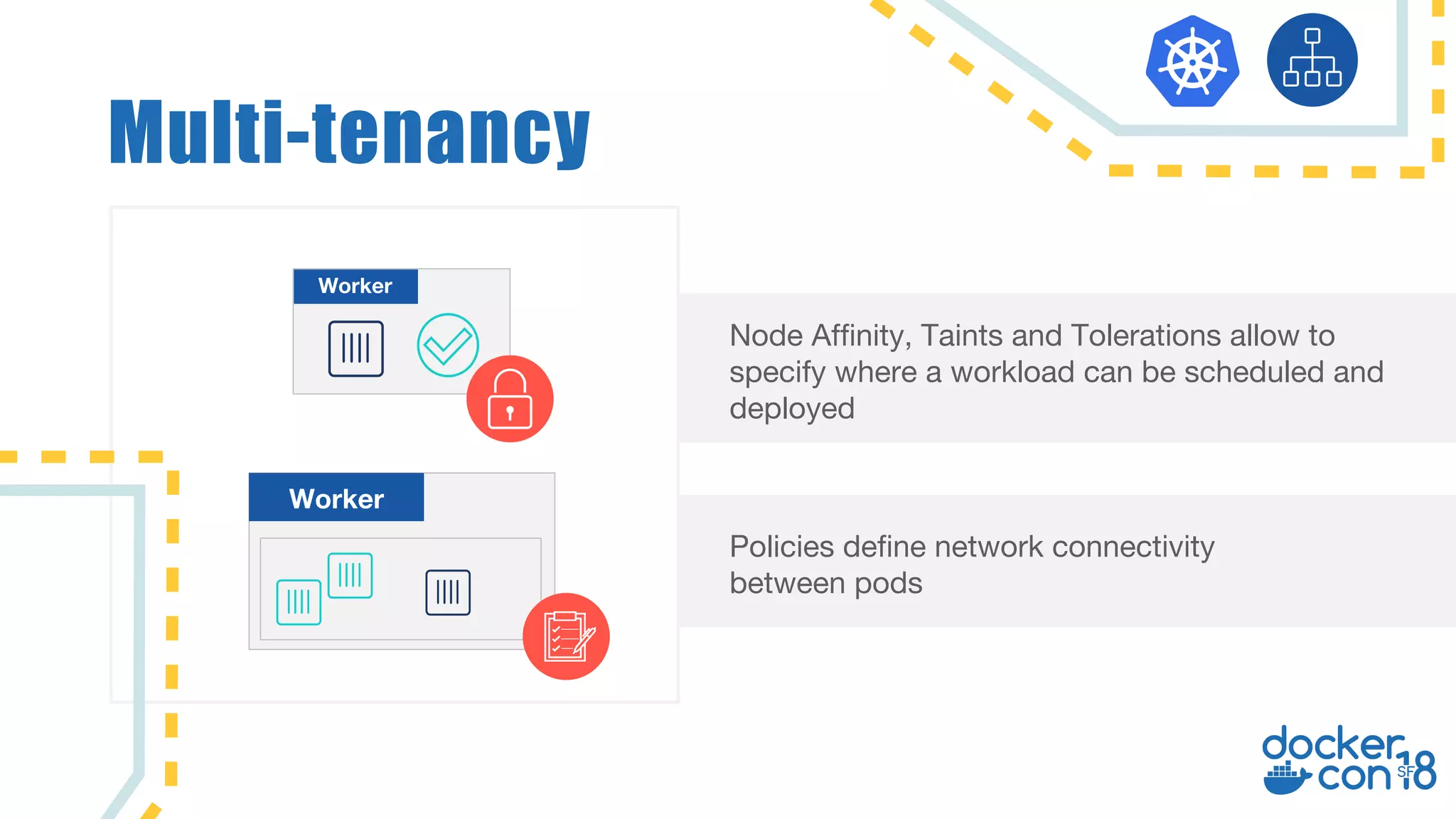
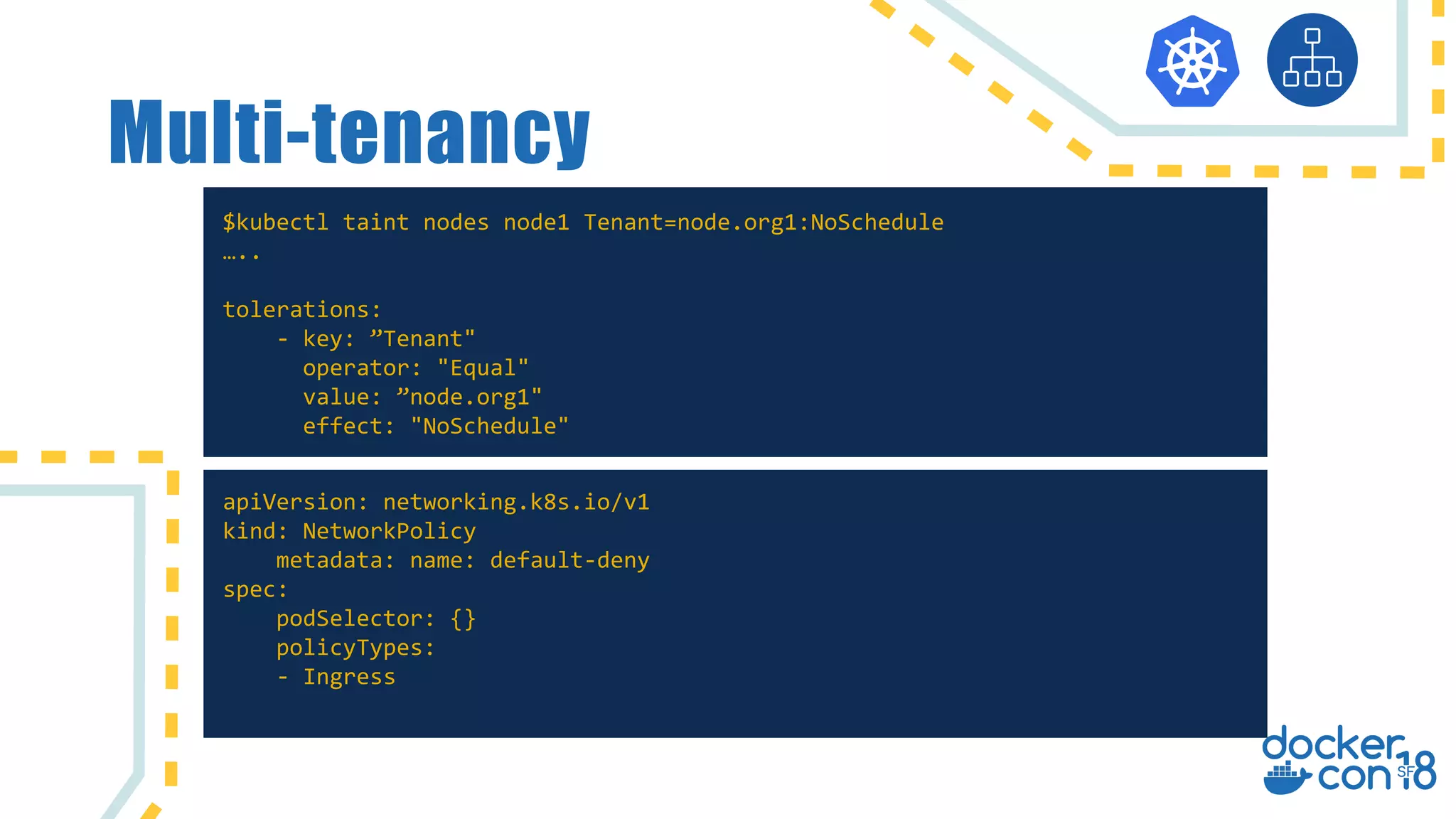
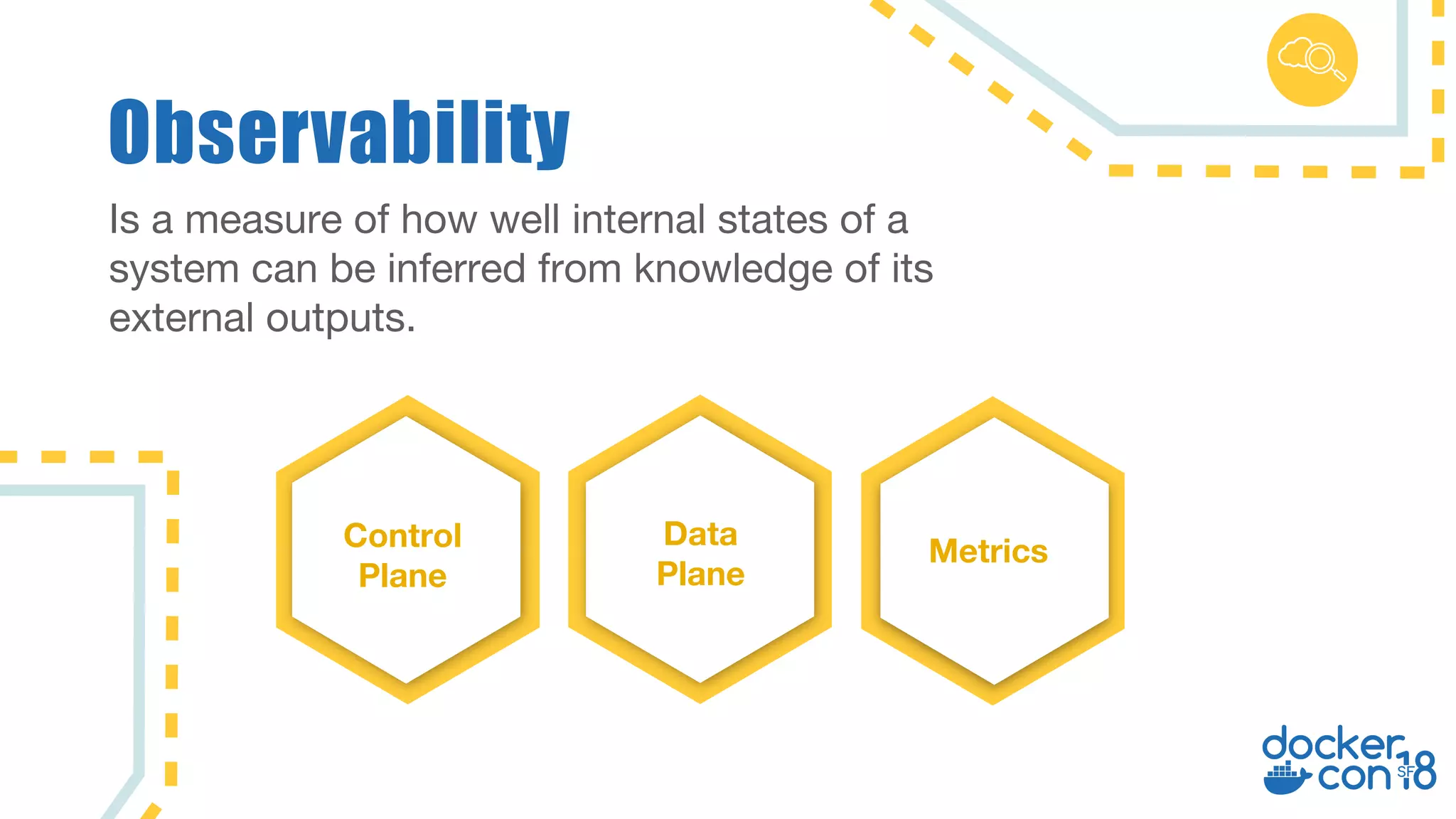
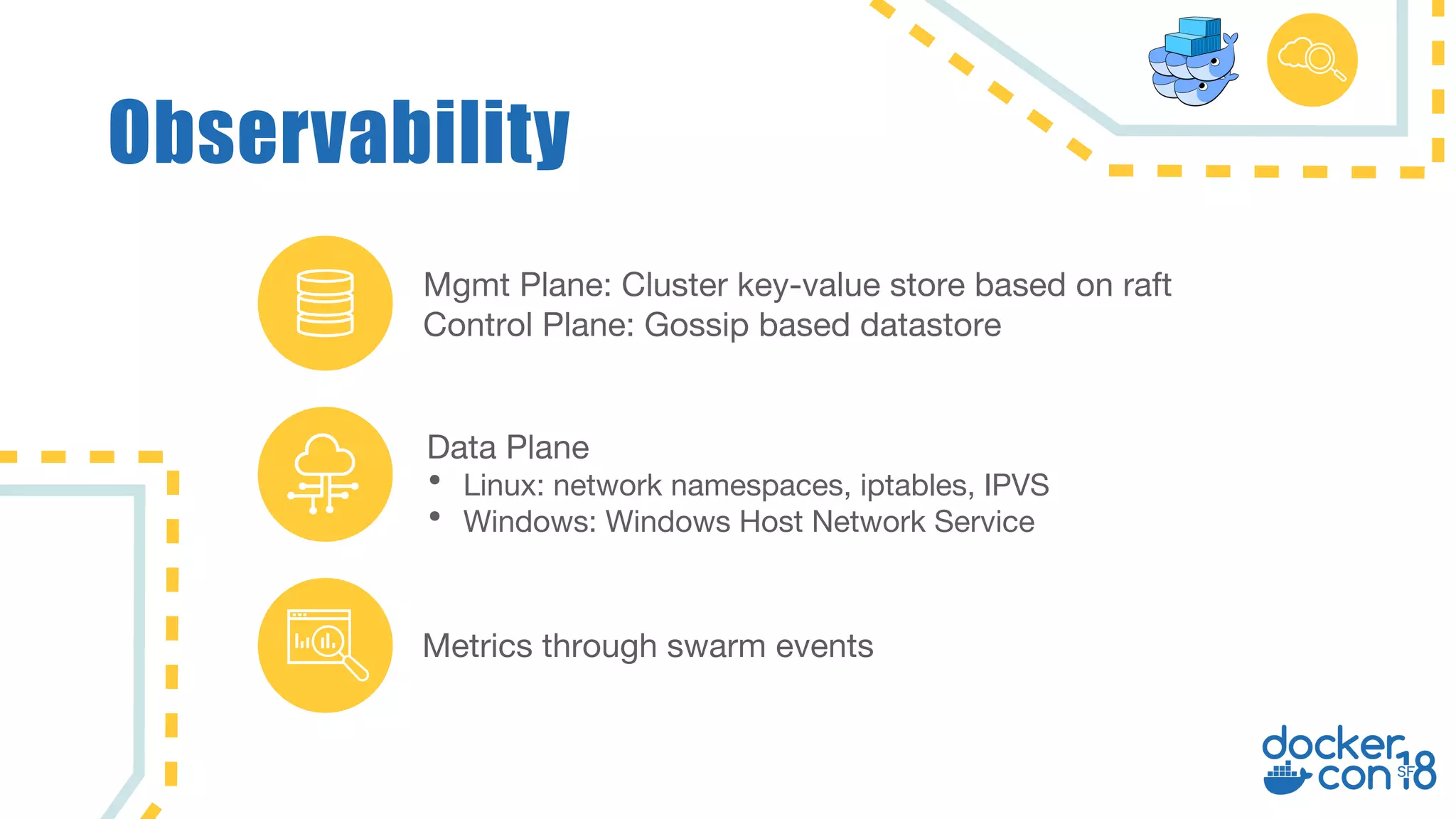
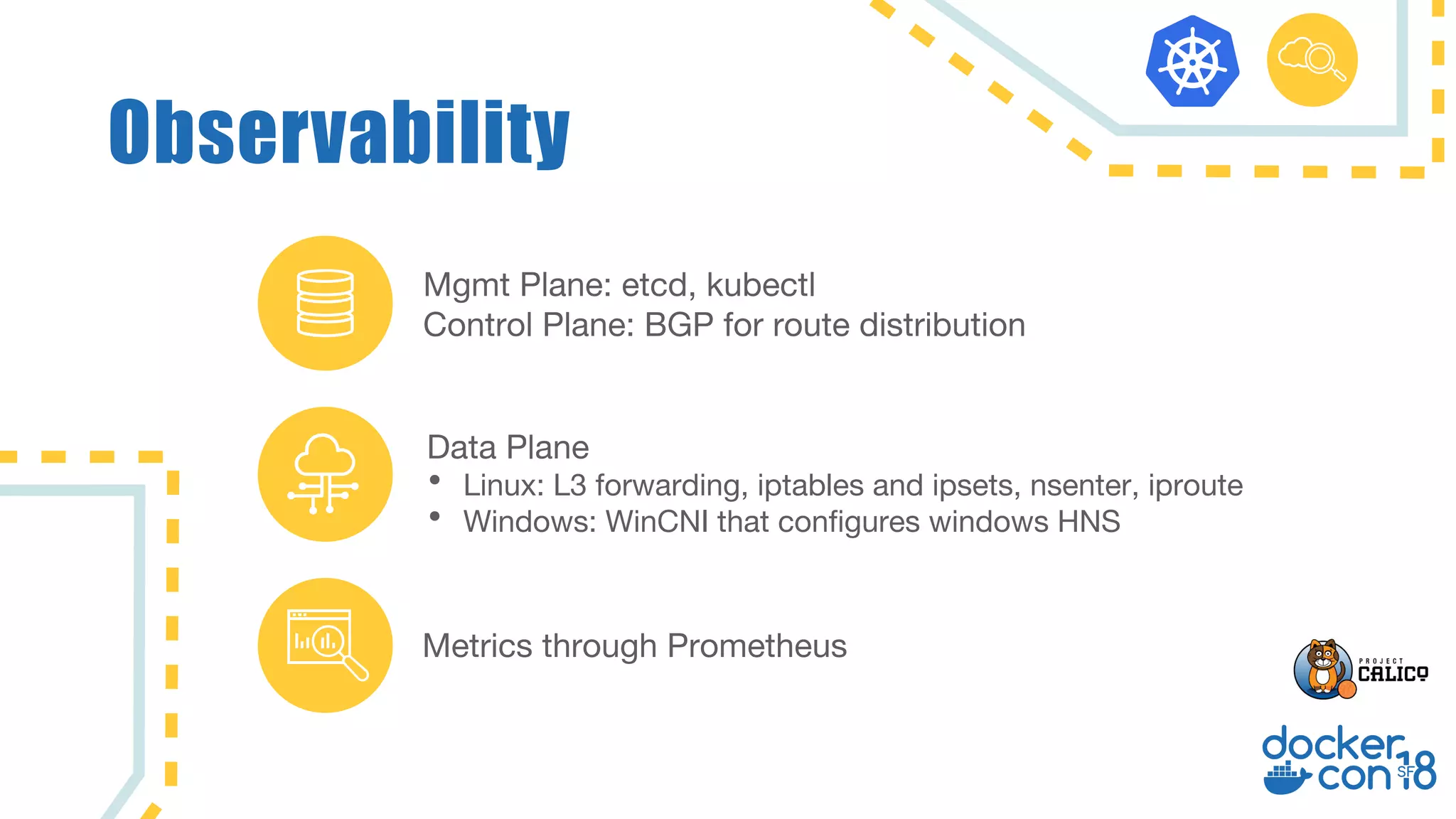
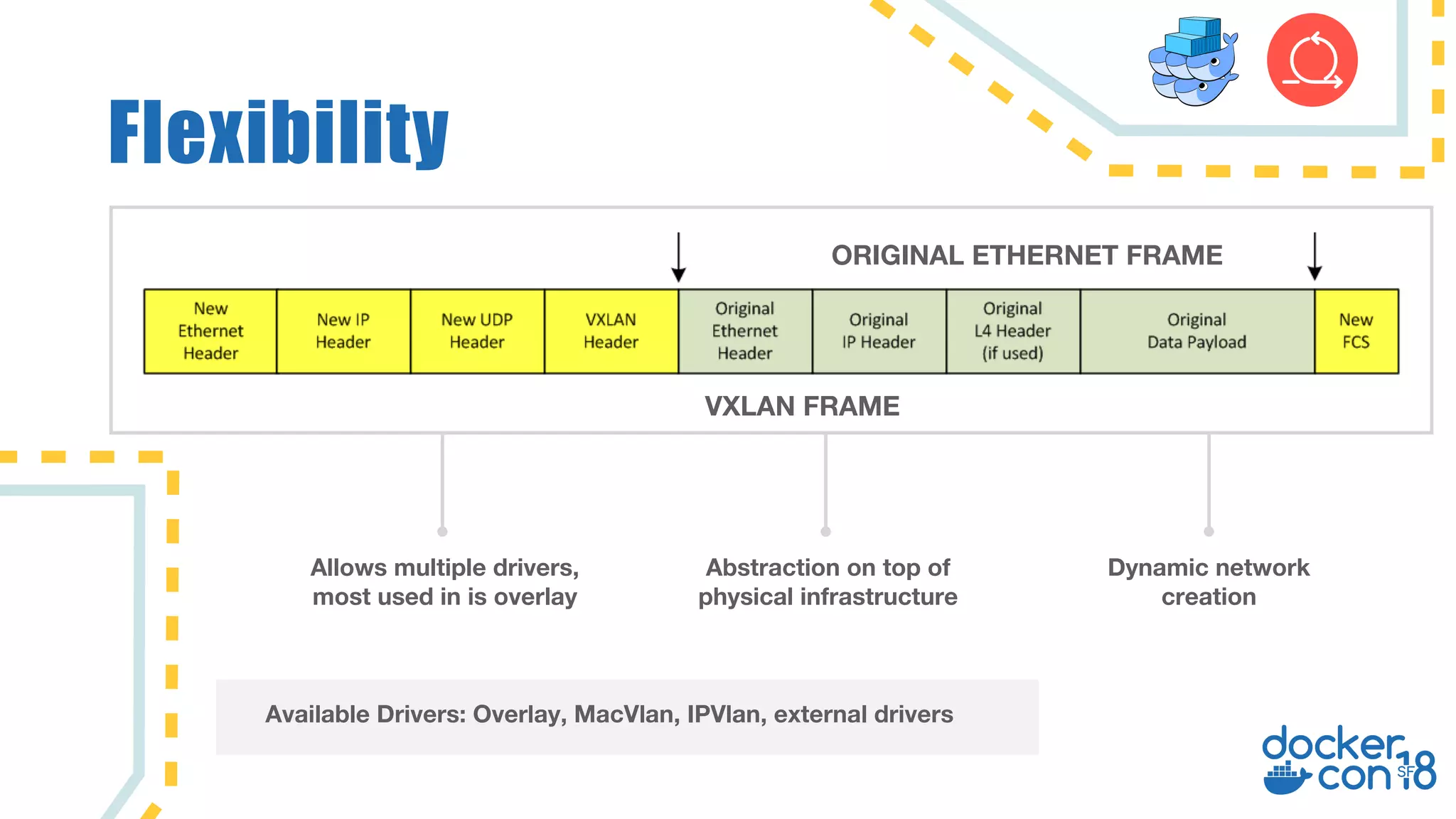
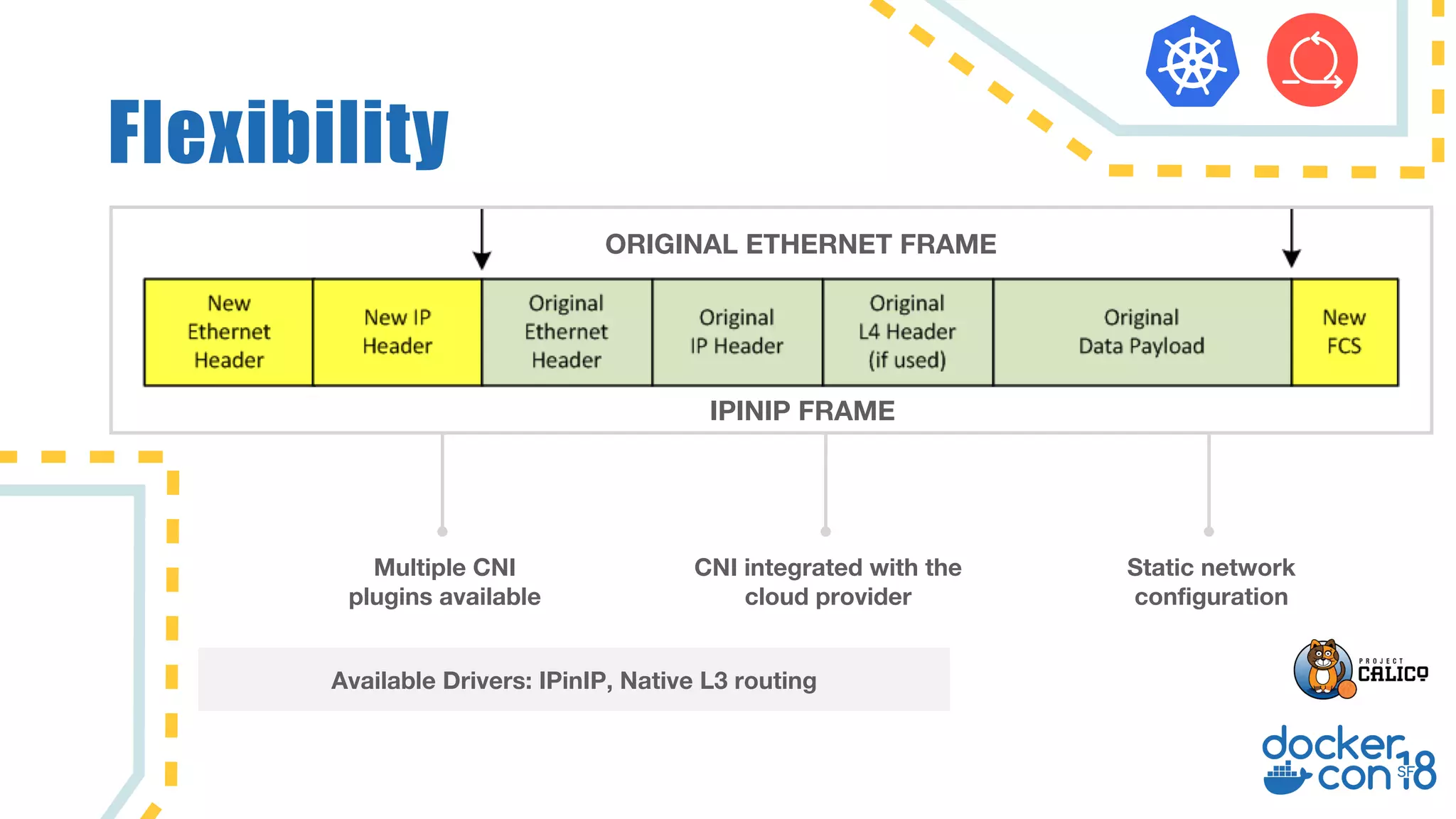
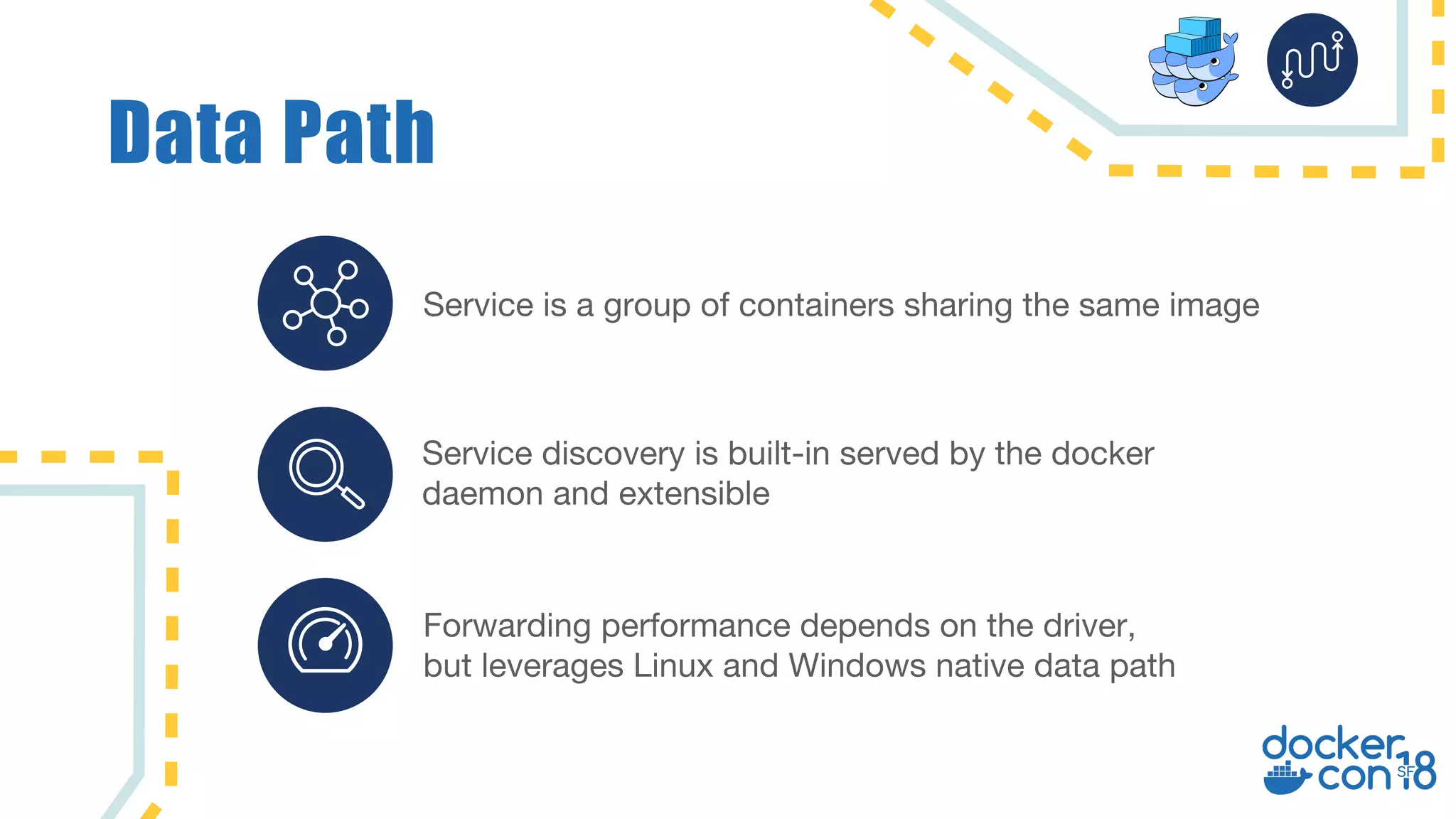
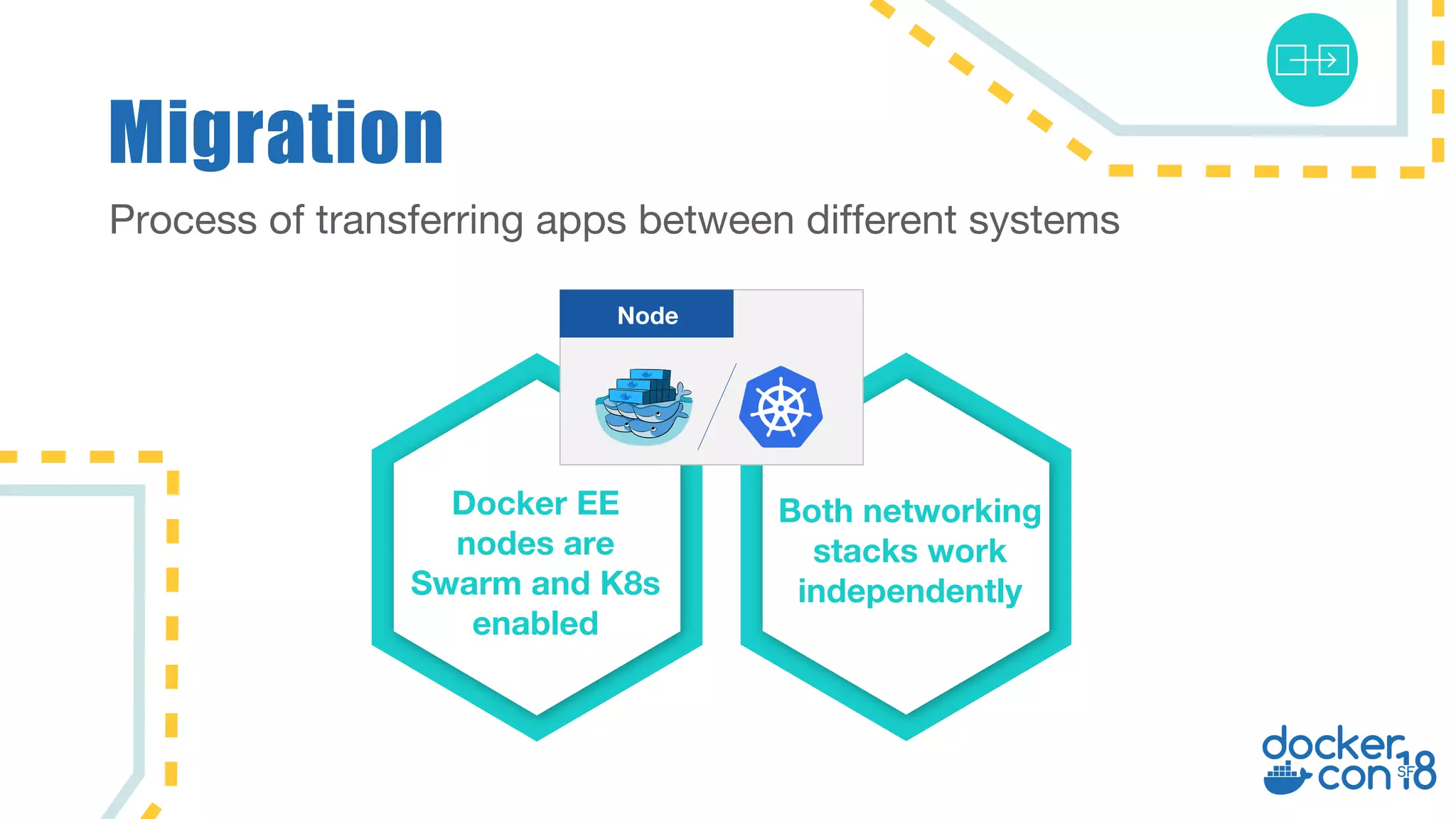
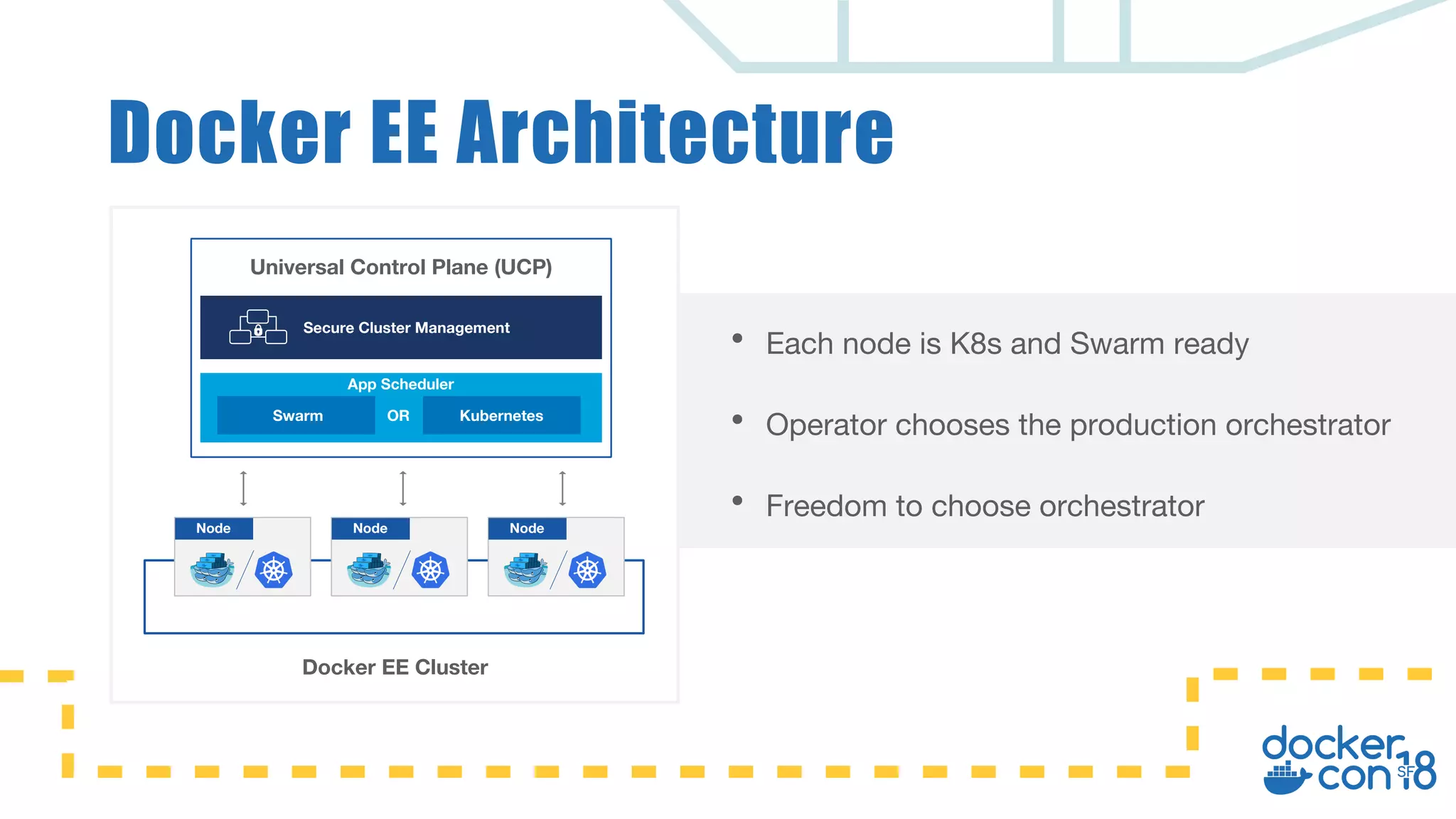
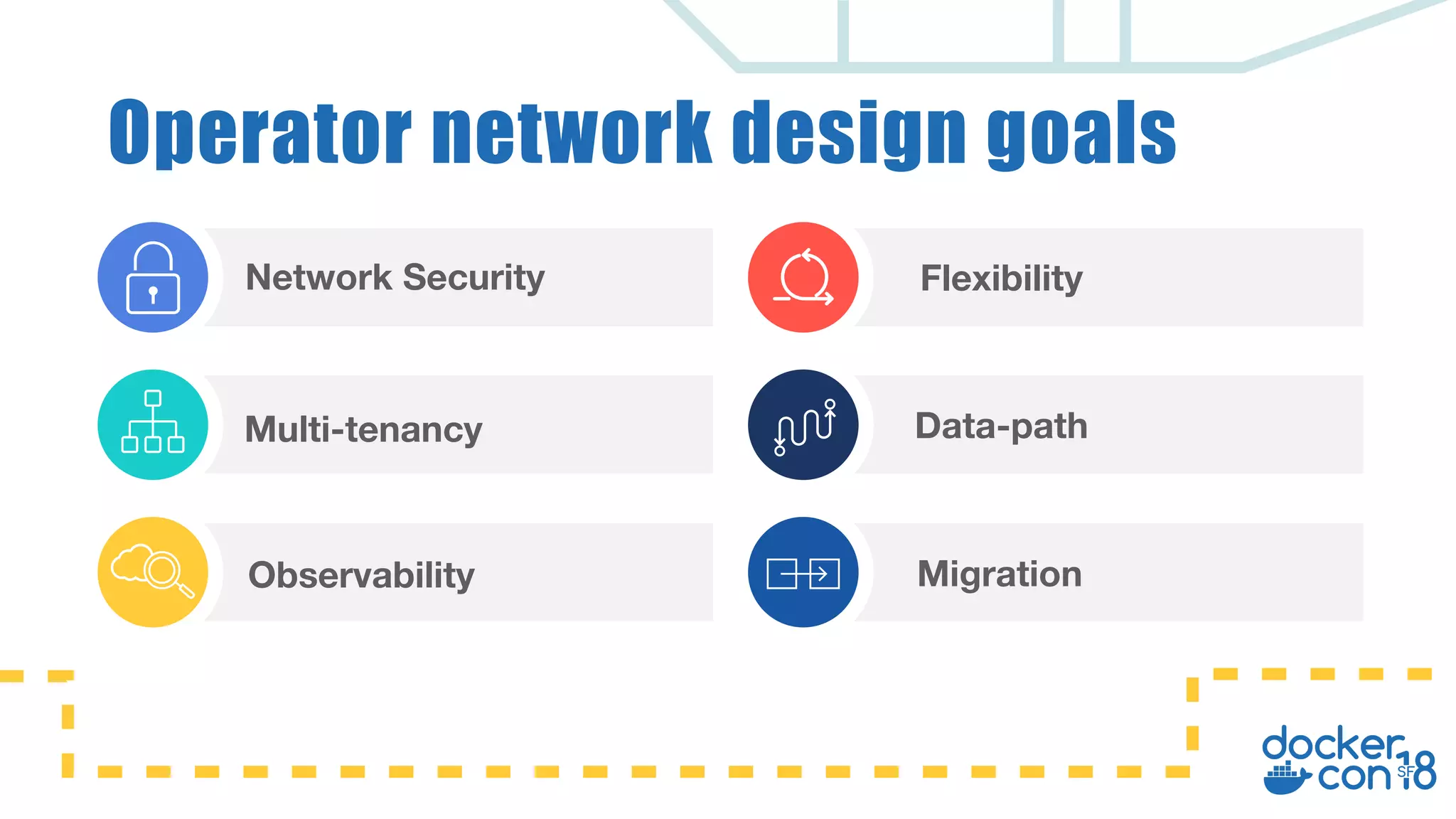
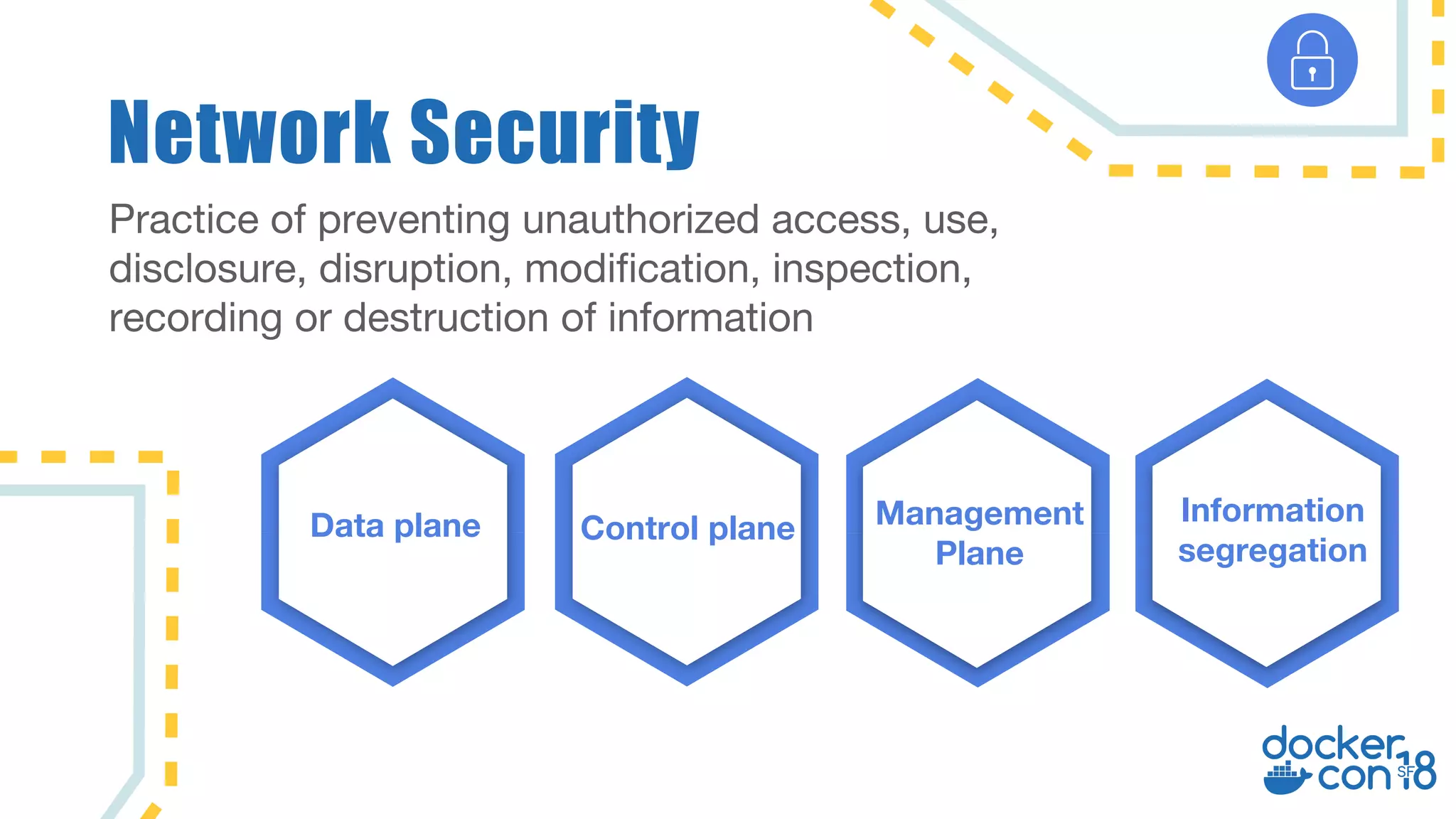
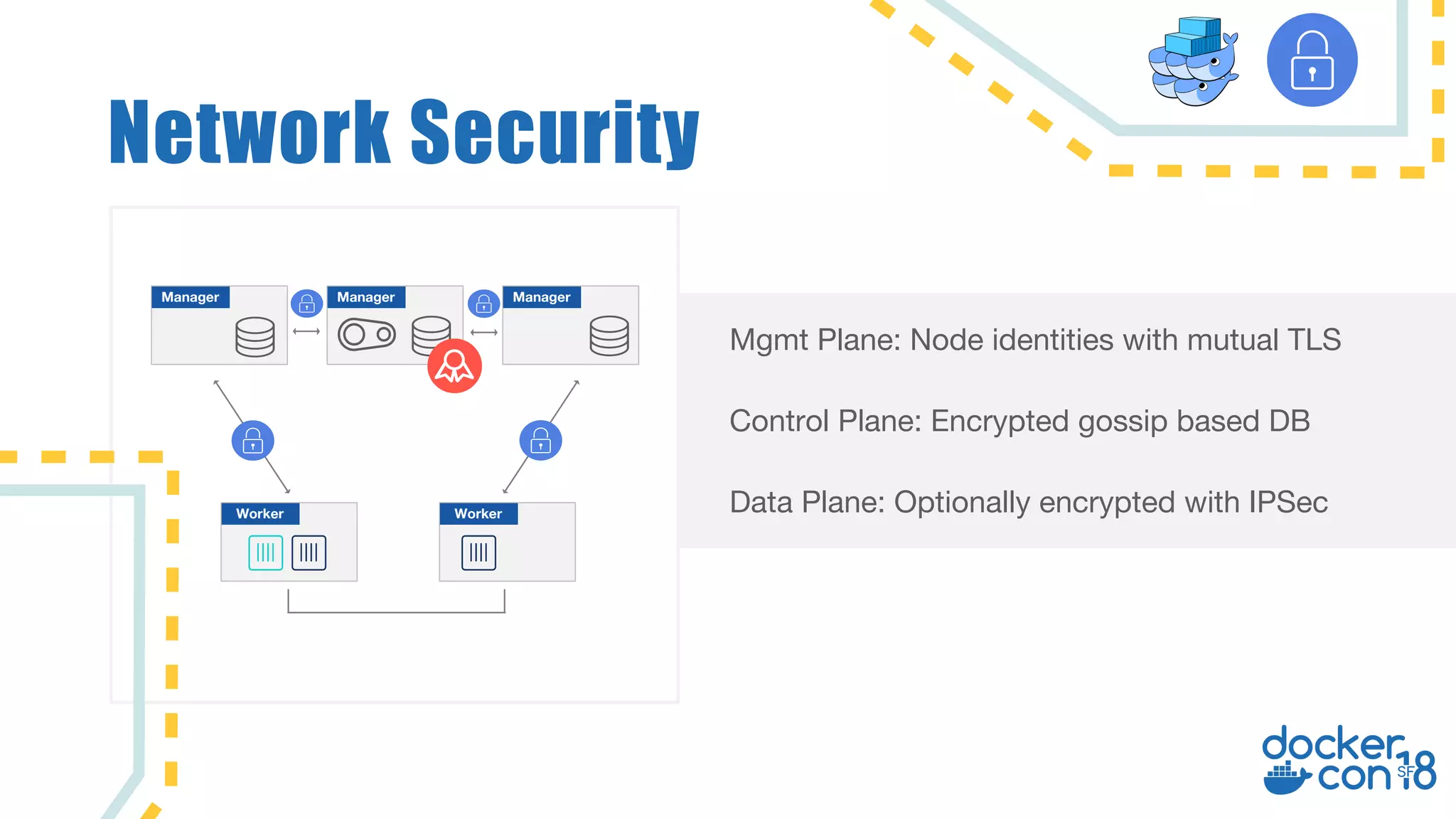
The document discusses networking principles in Docker EE 2.0 with Kubernetes and Swarm, highlighting design objectives, security, multi-tenancy, and observability. It emphasizes the flexibility in choosing orchestrators and network configurations to ensure secure and efficient application deployment. Key takeaways include the importance of operator selection and the capabilities of Docker EE to adapt to various needs and environments.

![Network Security ucp-bundle-john $docker network create -d overlay john-network Error response from daemon: access denied: no access to Network Create, on collection ucp-bundle-admin $source env.sh Cluster "ucp_10.1.1.1:6443_admin" set. User "ucp_10.1.1.1:6443_admin" set. Context "ucp_10.1.1.1:6443_admin" created. ucp-bundle-admin $docker network create --opt encrypted --driver overlay net1 l5vtb59oqk6r7fgzrjlou6llg Jun 11 21:13:57 ubuntu-1 dockerd[4721]: time="2018-06-11T21:13:57.200950113Z" level=debug msg="Initial encryption keys: [(key: dda14, tag: 0x1eb1) (key: b6b91, tag: 0x1eb0) (key: 0e8a0, tag: 0x1eb2)]" Jun 11 21:13:57 ubuntu-1 dockerd[4721]: time="2018-06-11T21:13:57.201251695Z" level=debug msg="Initial encryption keys: [(key: dda14, tag: 0x1eb1) (key: b6b91, tag: 0x1eb0) (key: 0e8a0, tag: 0x1eb2)]"](https://image.slidesharecdn.com/networkingindockereewithkubernetesandswarm-180620234959/75/Networking-in-docker-ee-with-kubernetes-and-swarm-9-2048.jpg)