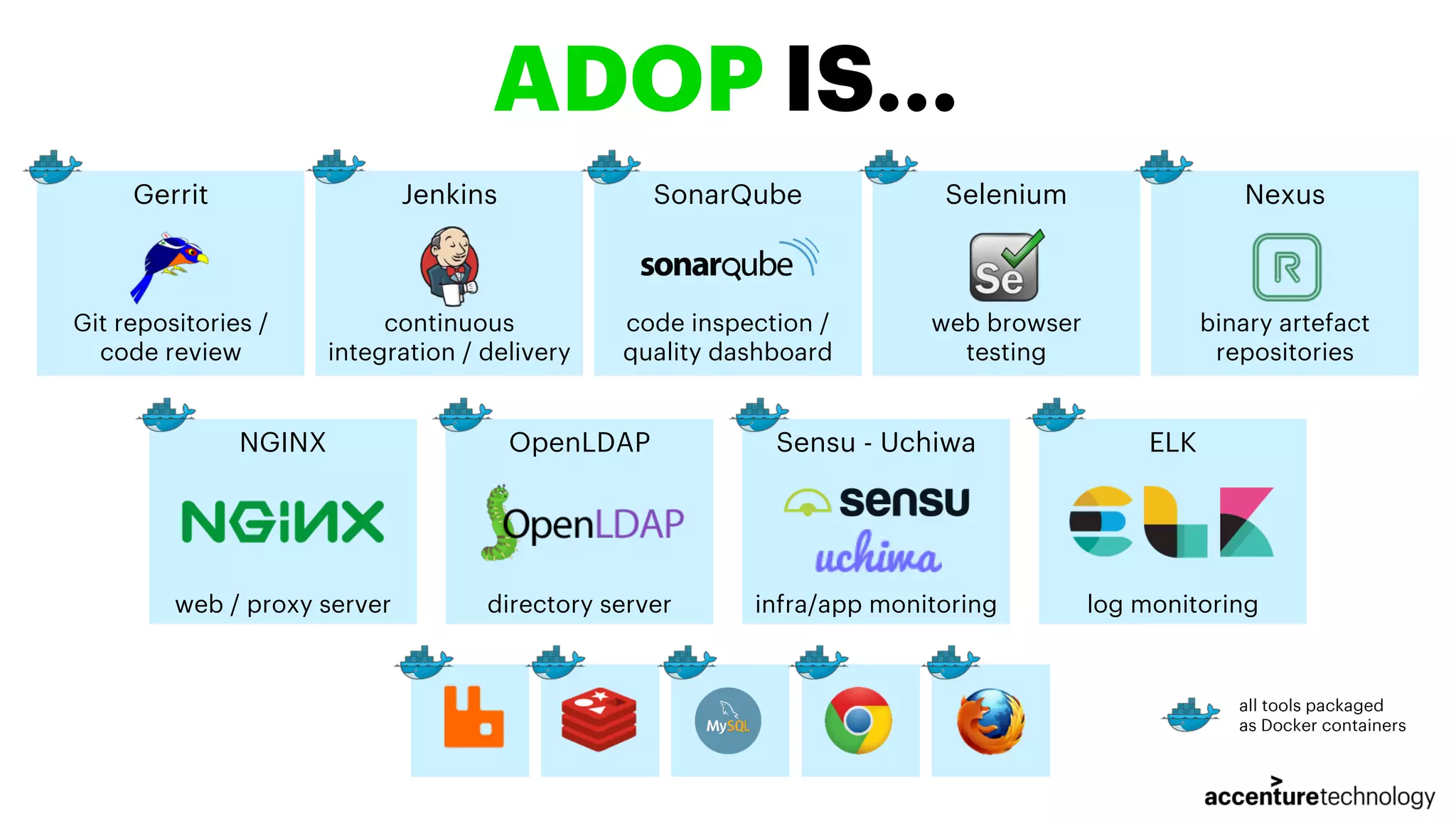
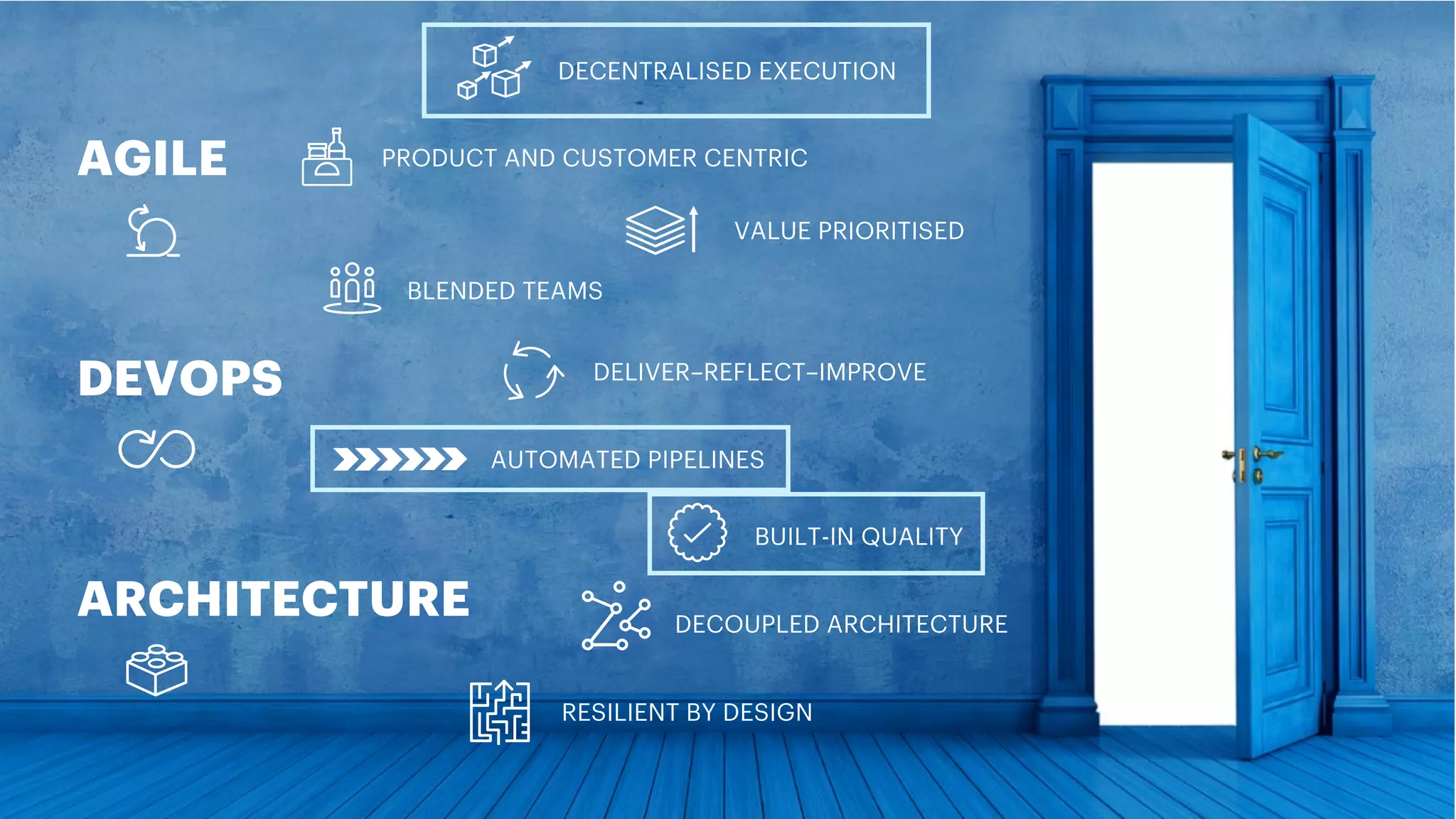
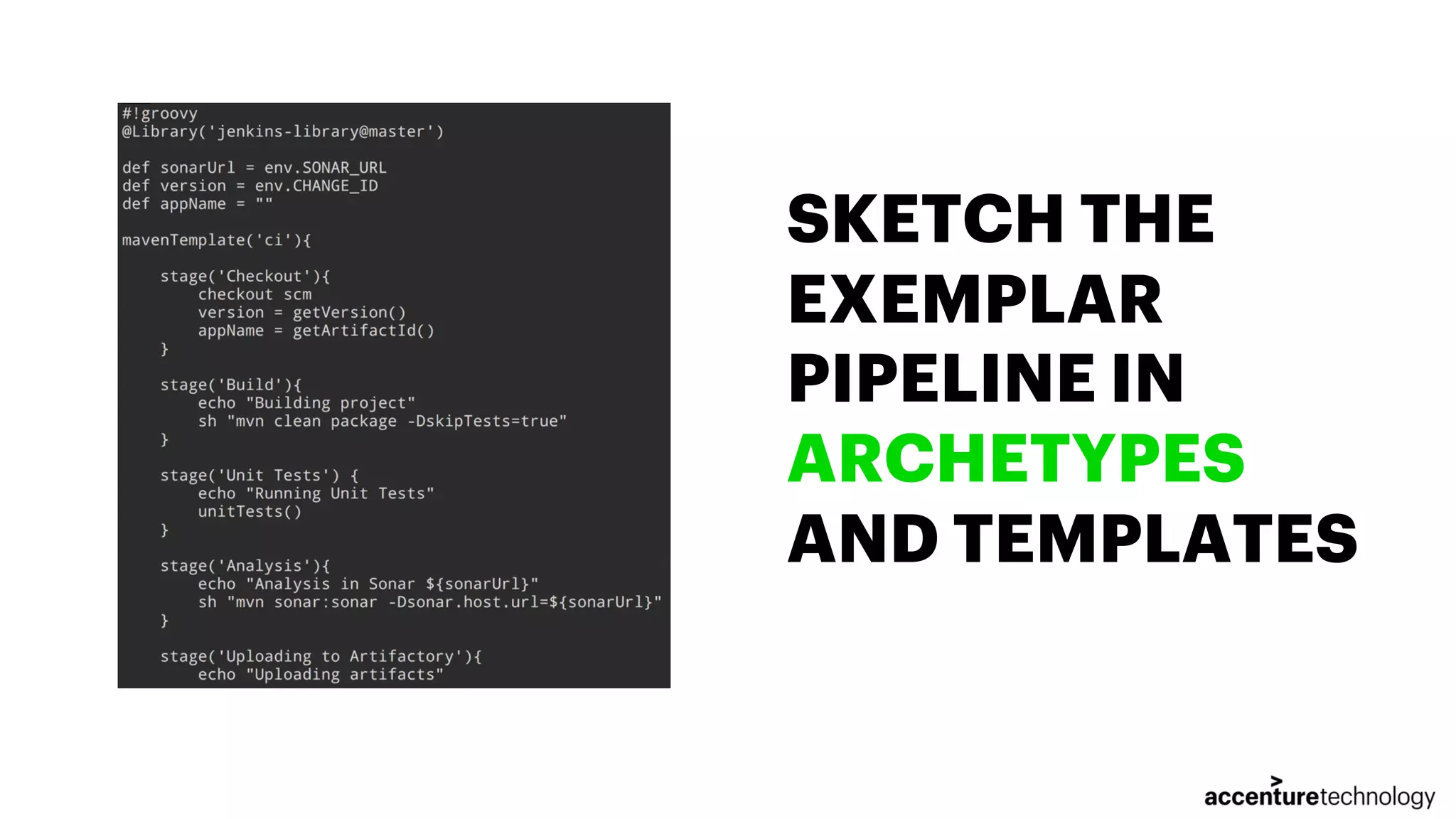
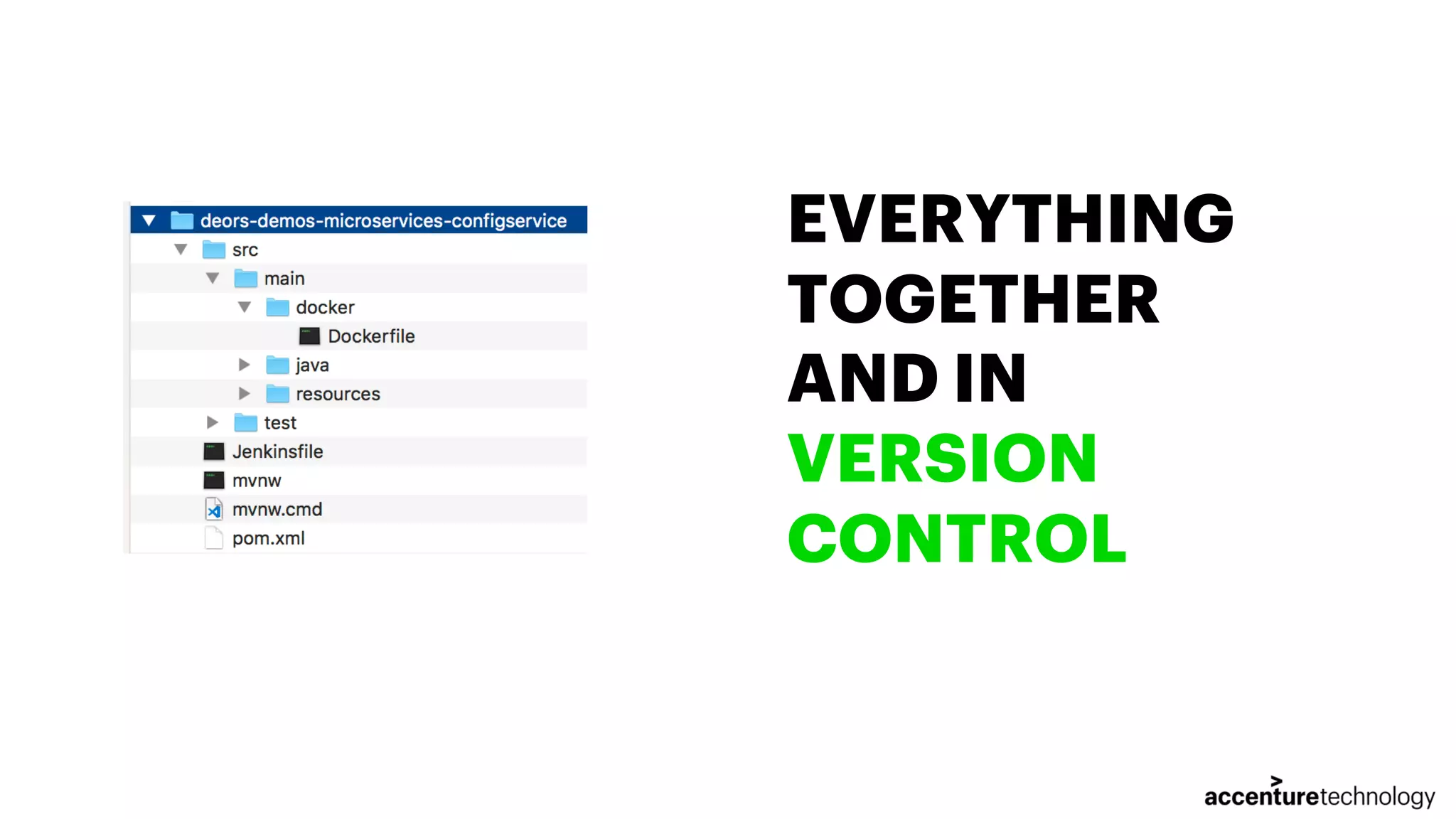
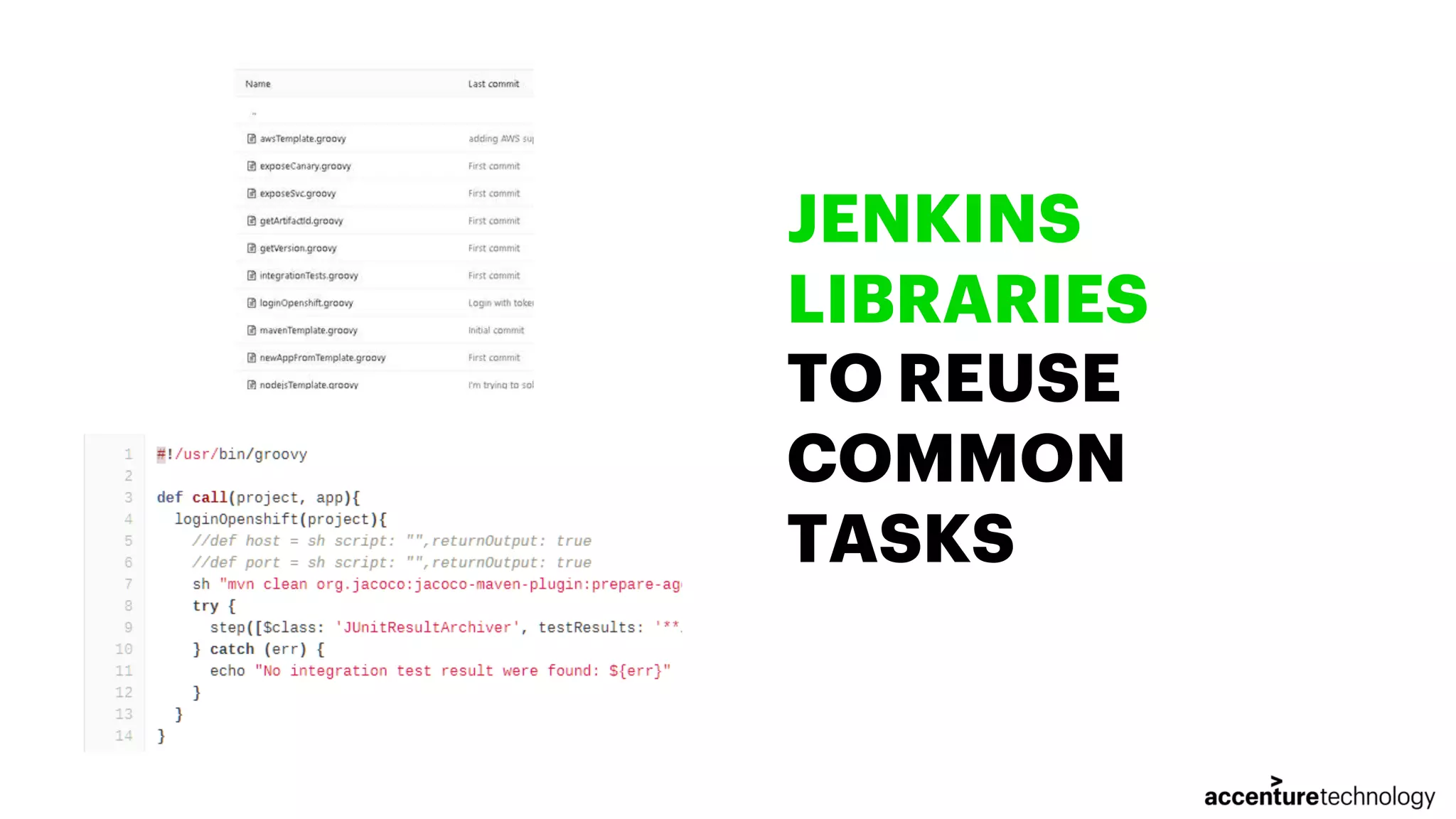
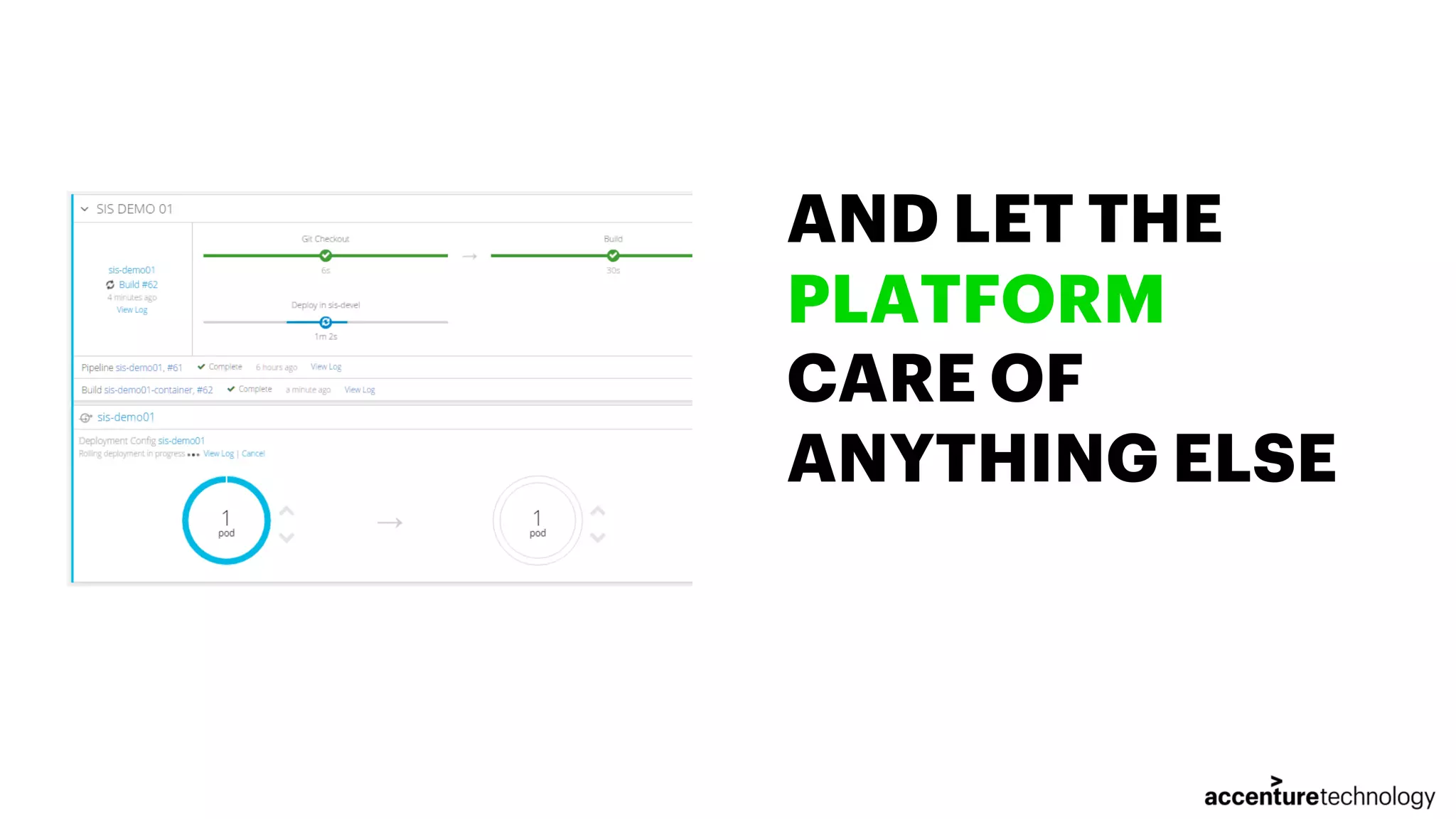
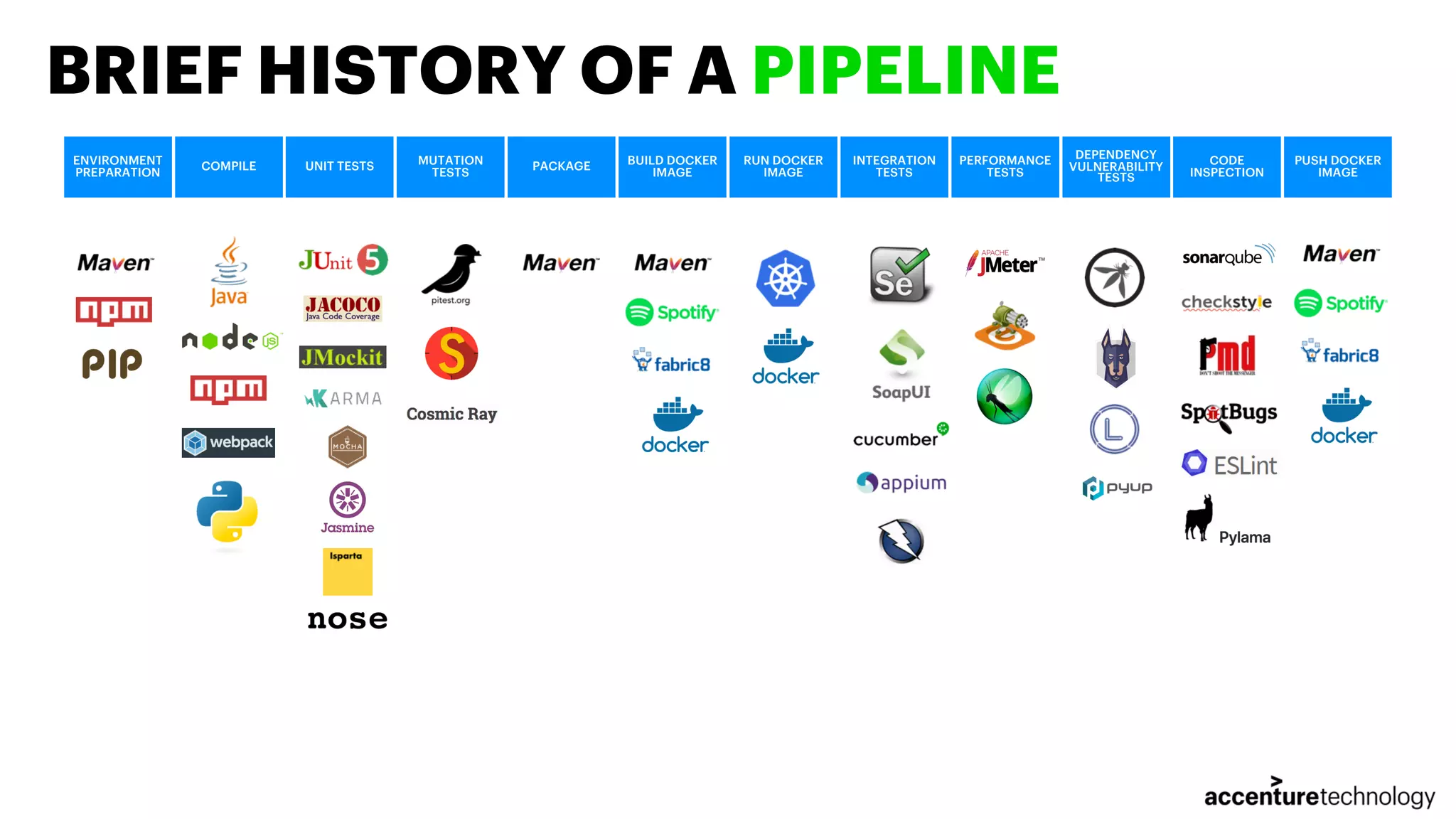
The document discusses the implementation of multilanguage pipelines using Jenkins, Docker, and other tools, emphasizing automation and DevOps principles. It outlines the pipeline process from environment preparation to code inspection, detailing each testing stage and the importance of code quality measures. The authors, Jorge Hidalgo and Julio Palma, encourage collaboration and provide online resources for further exploration.