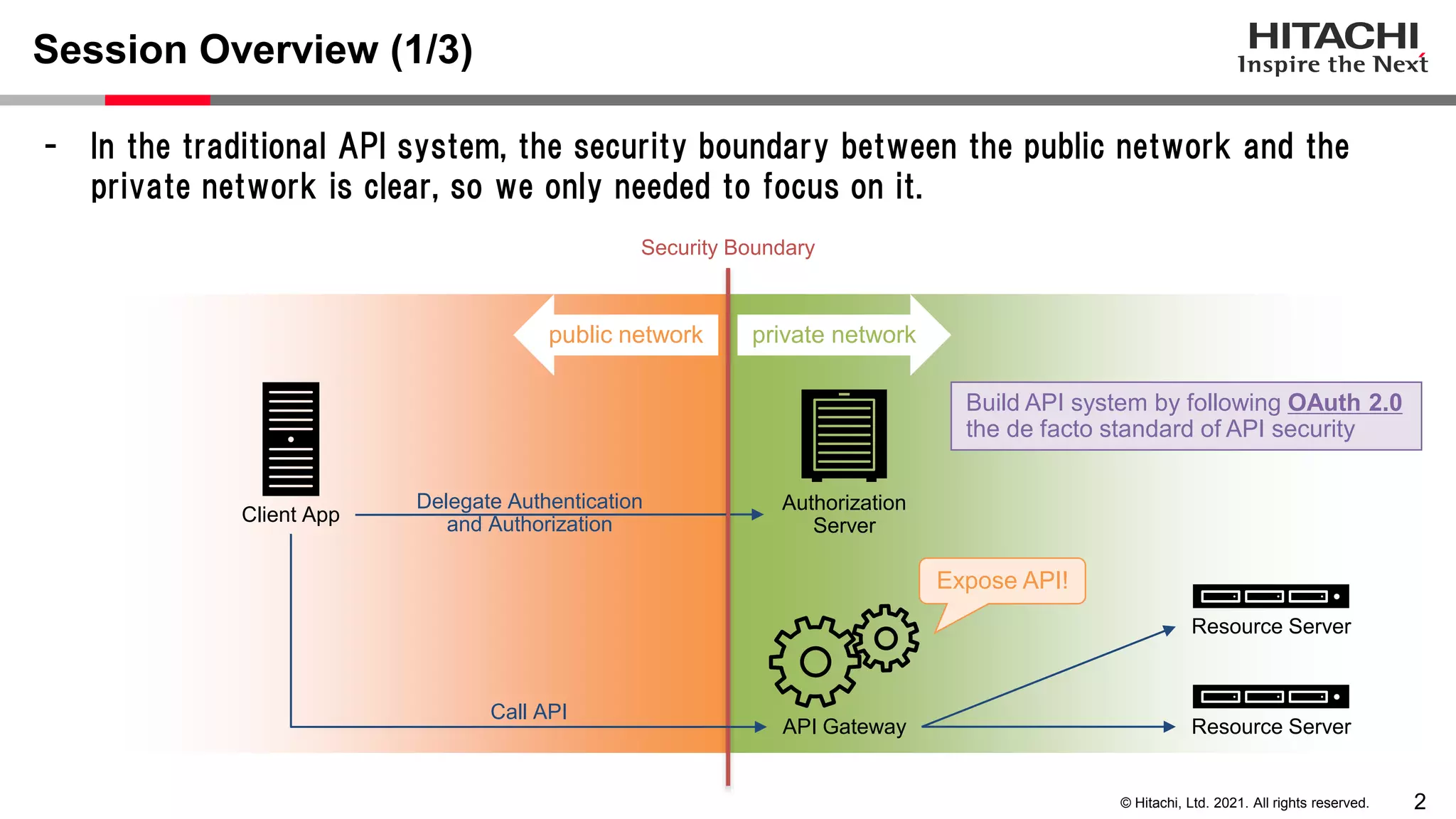
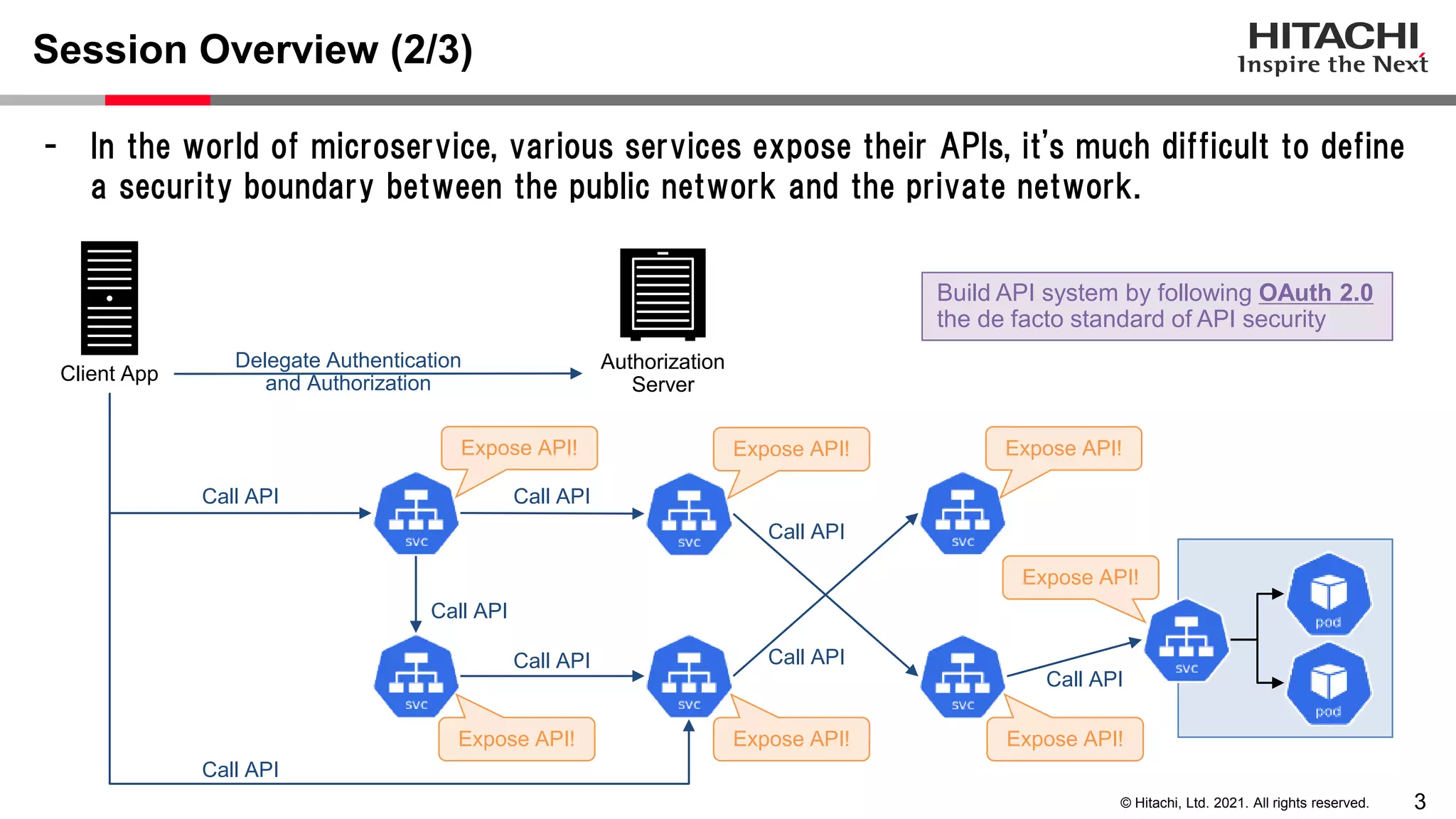
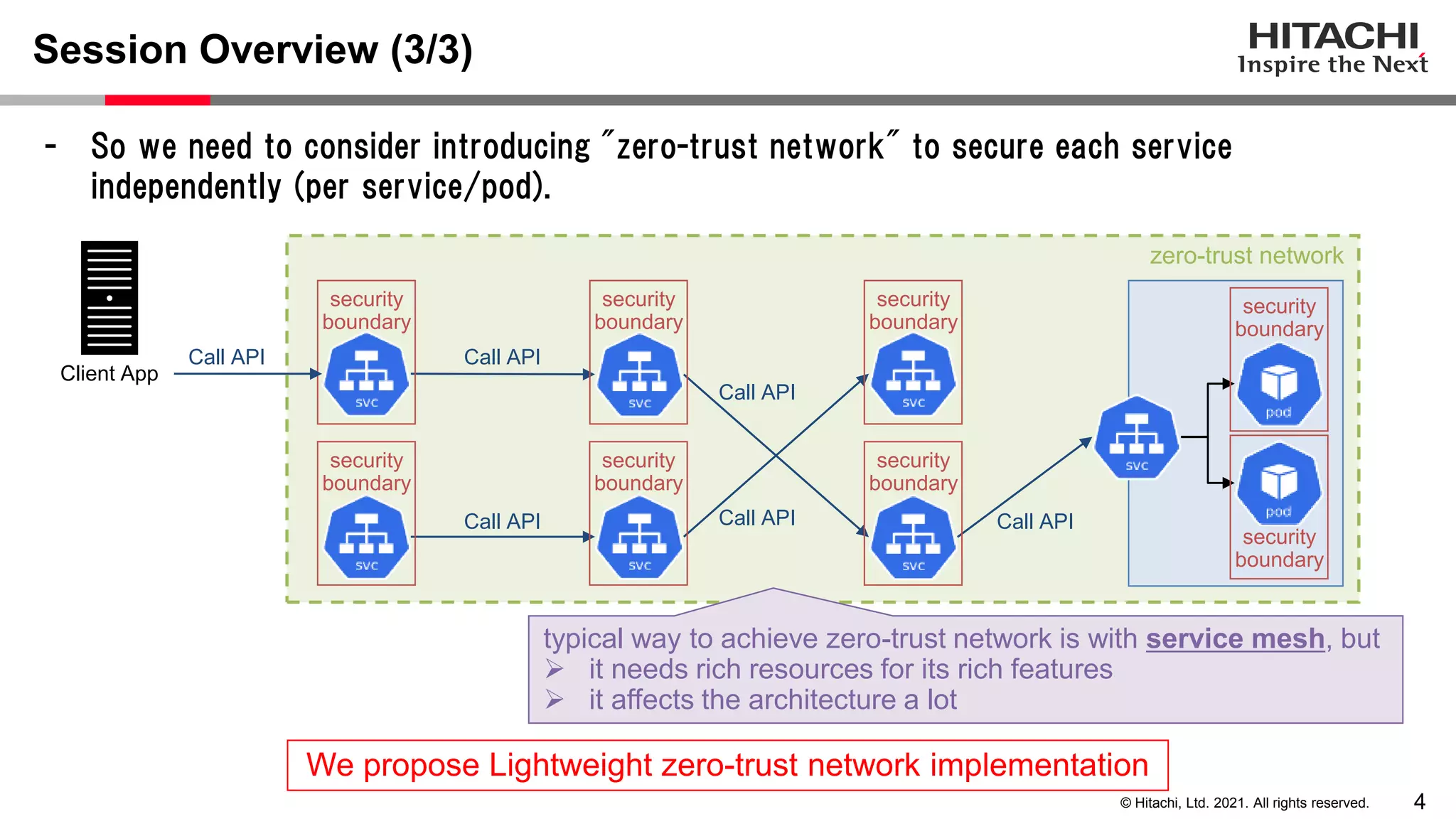
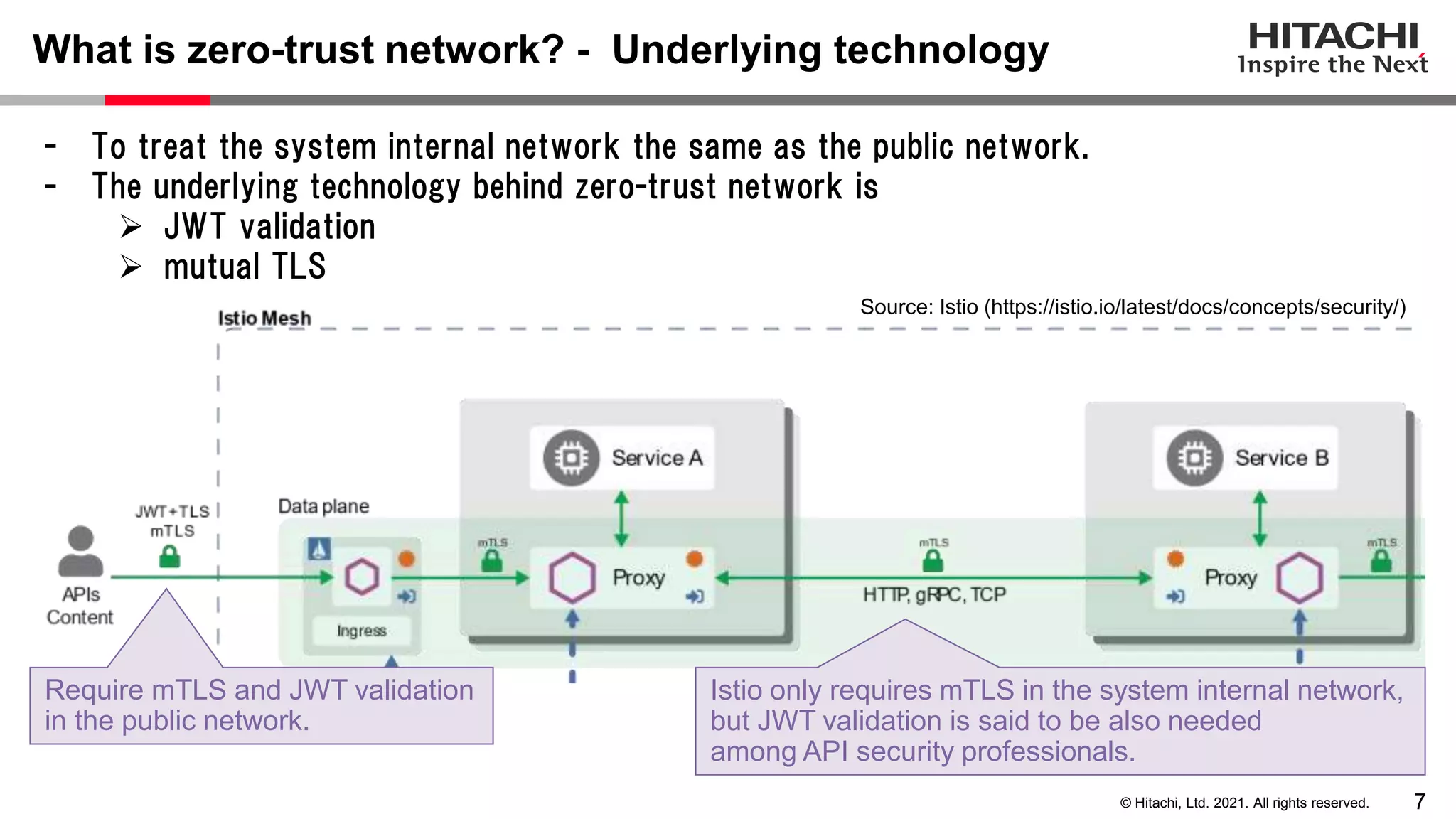
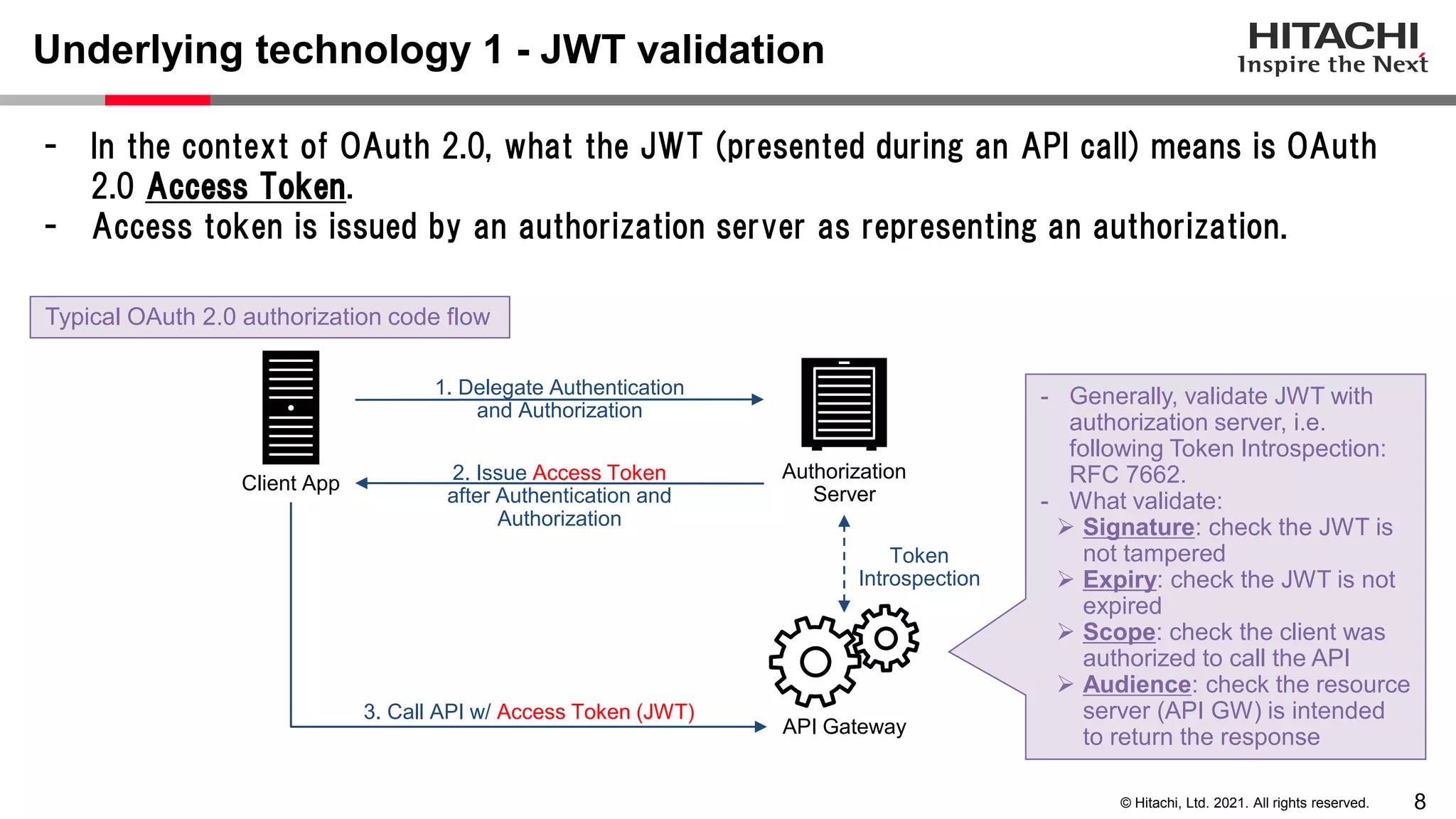
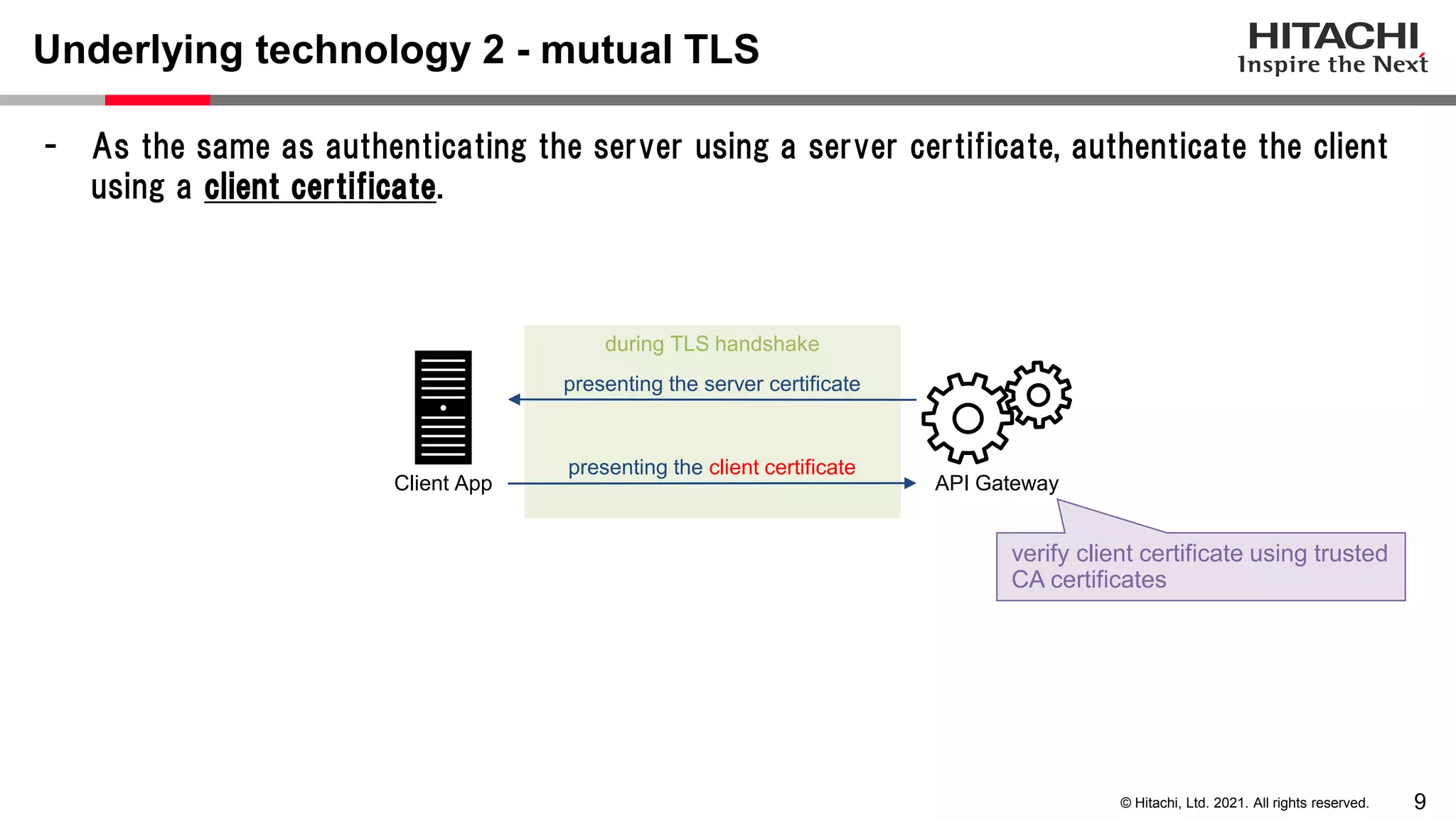
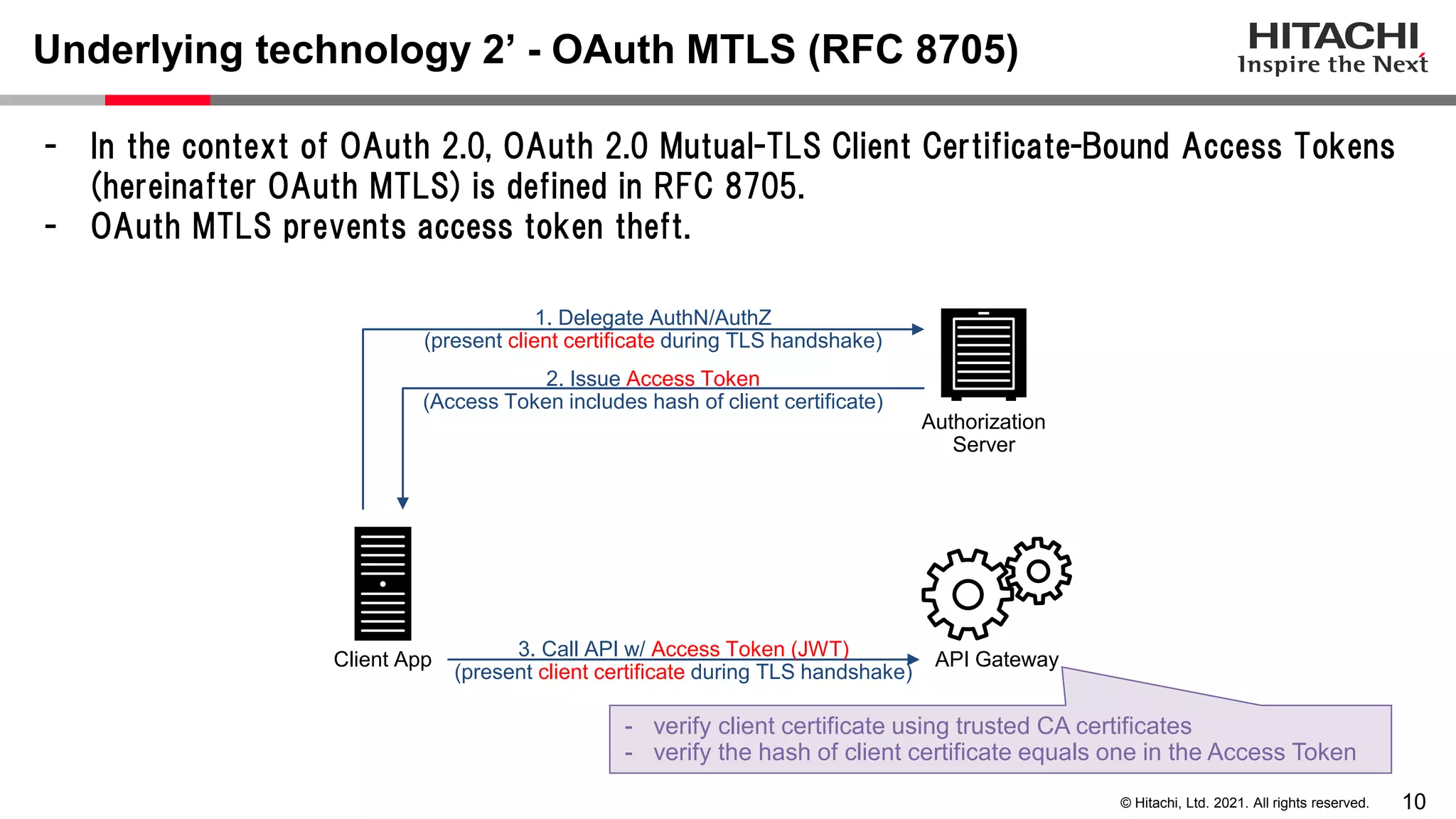
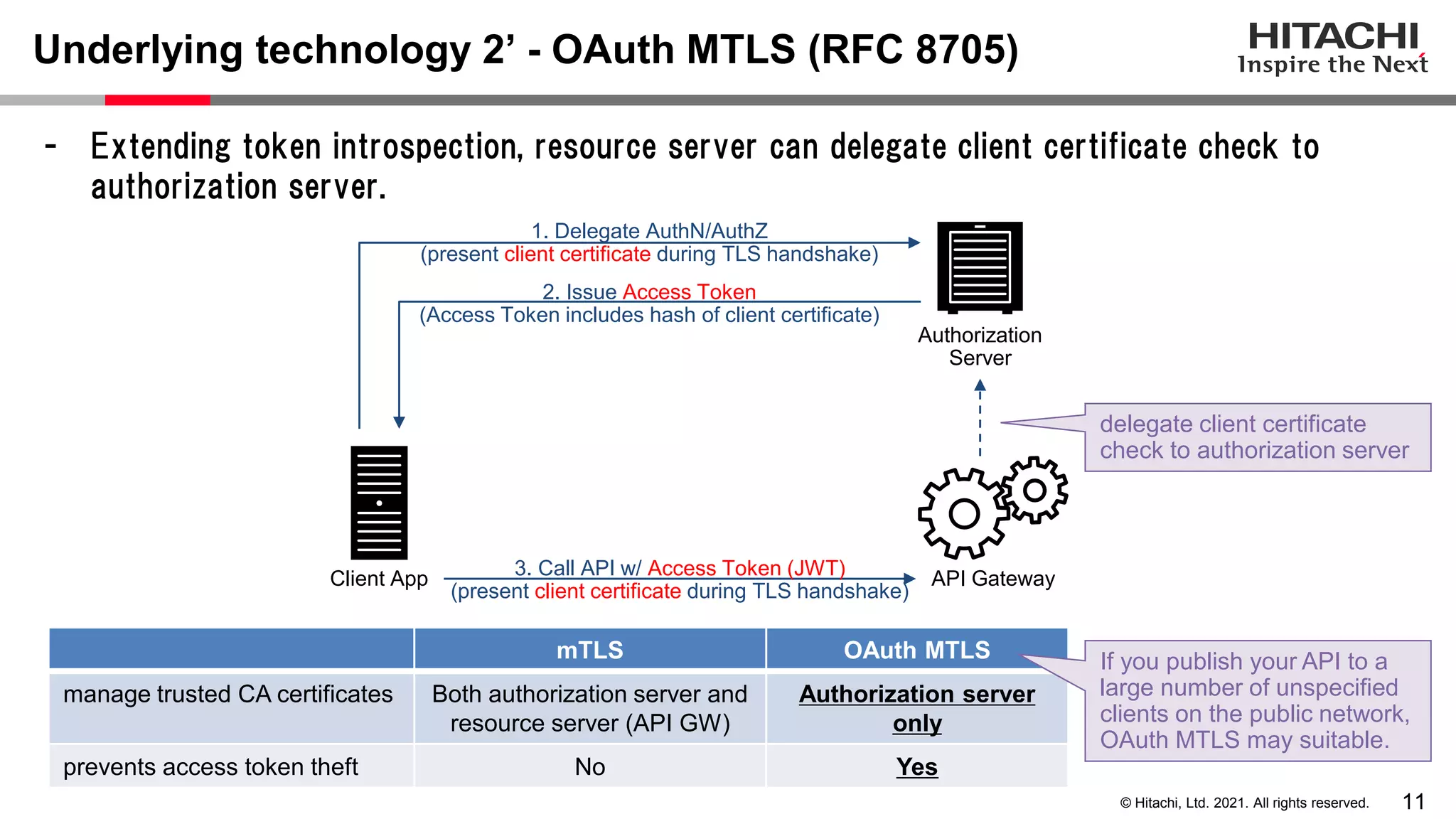
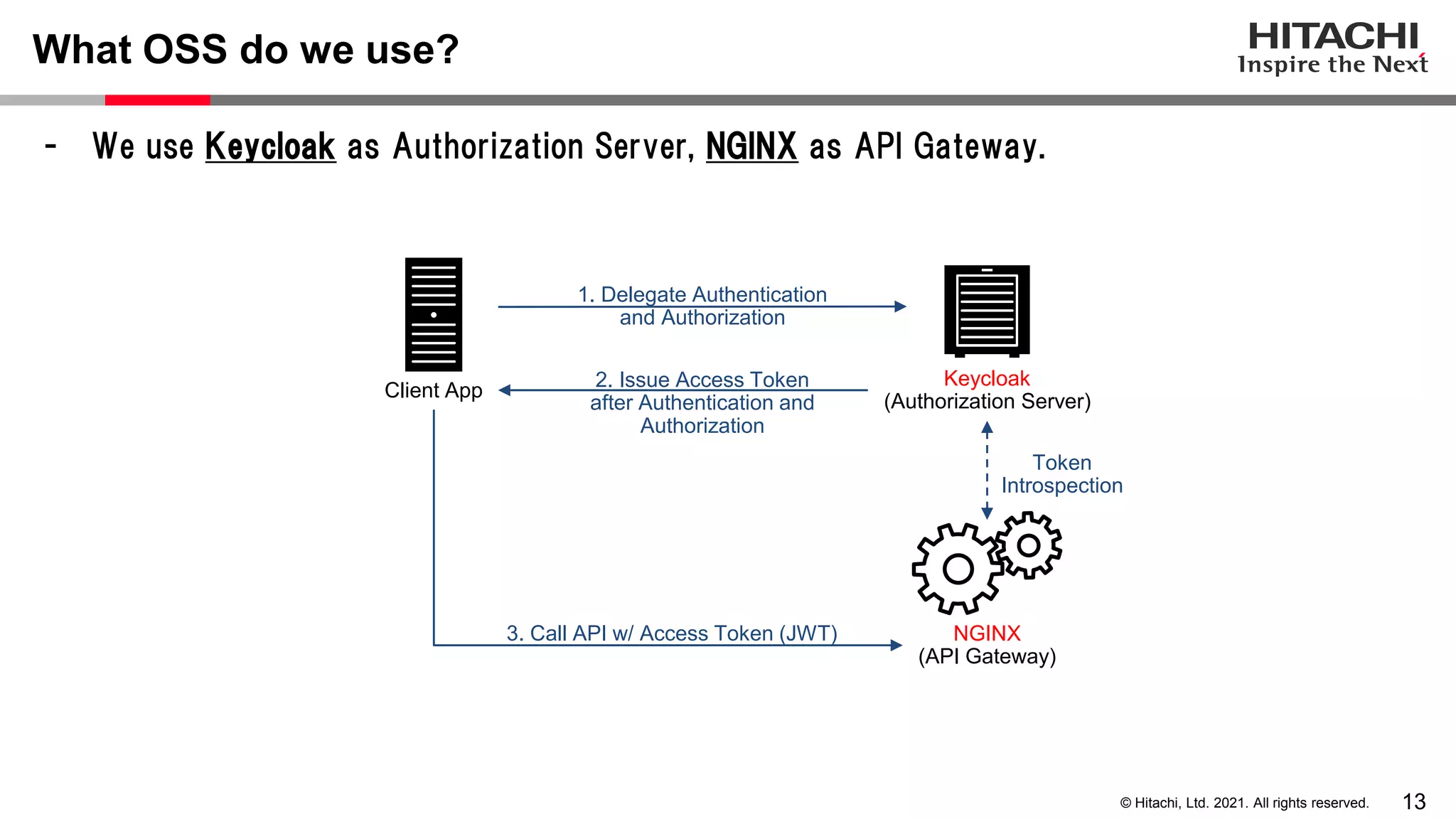
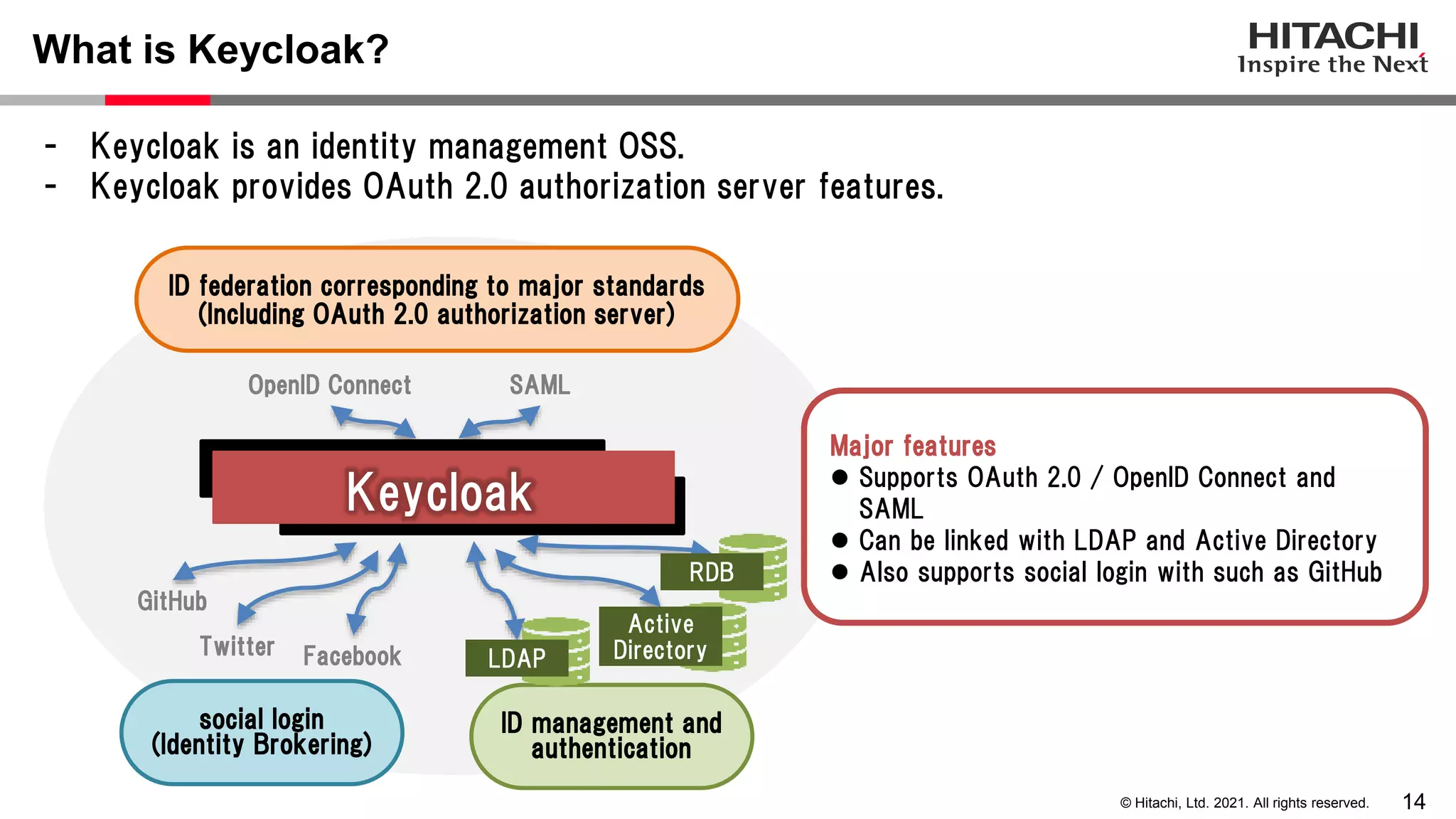
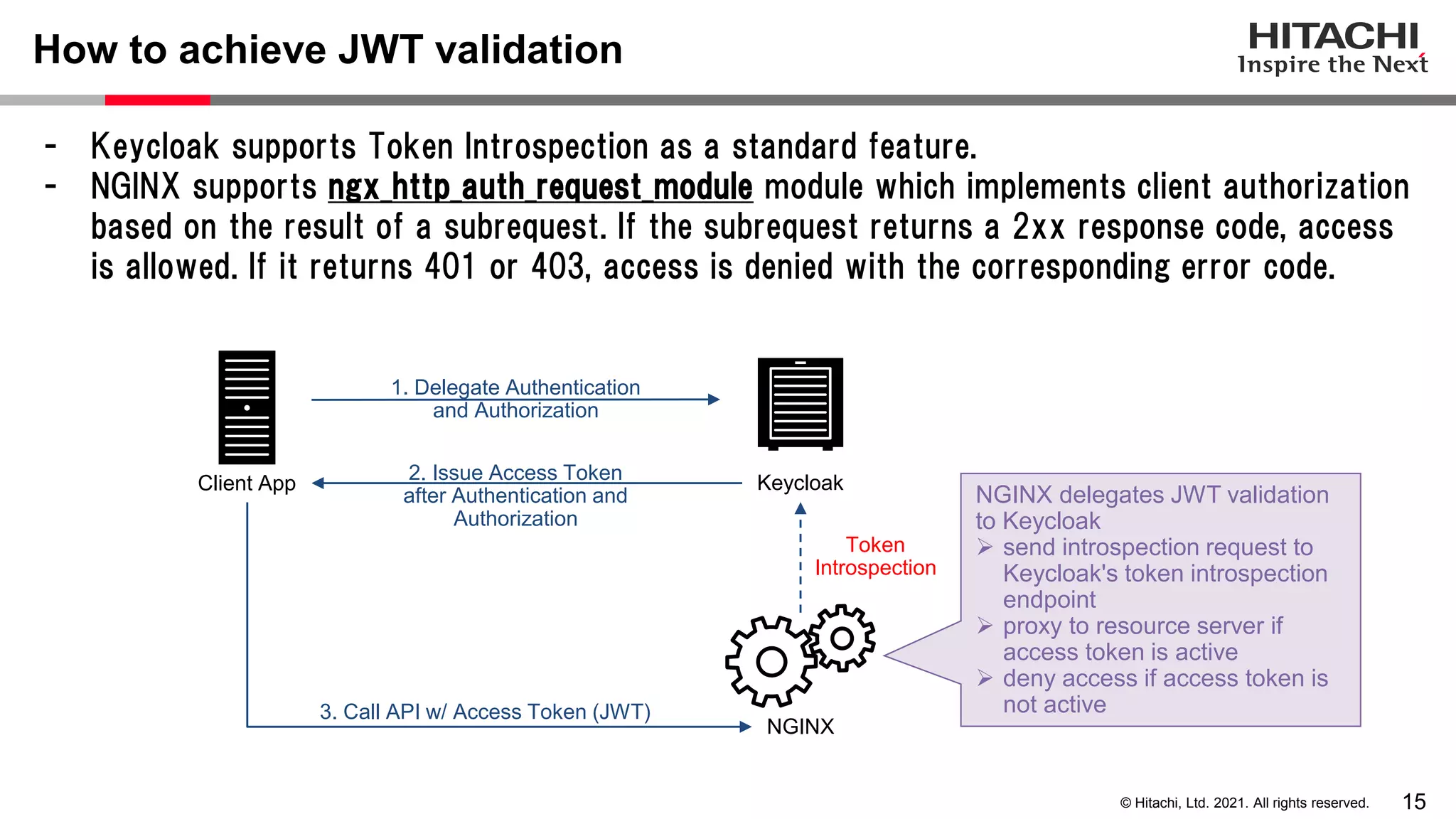
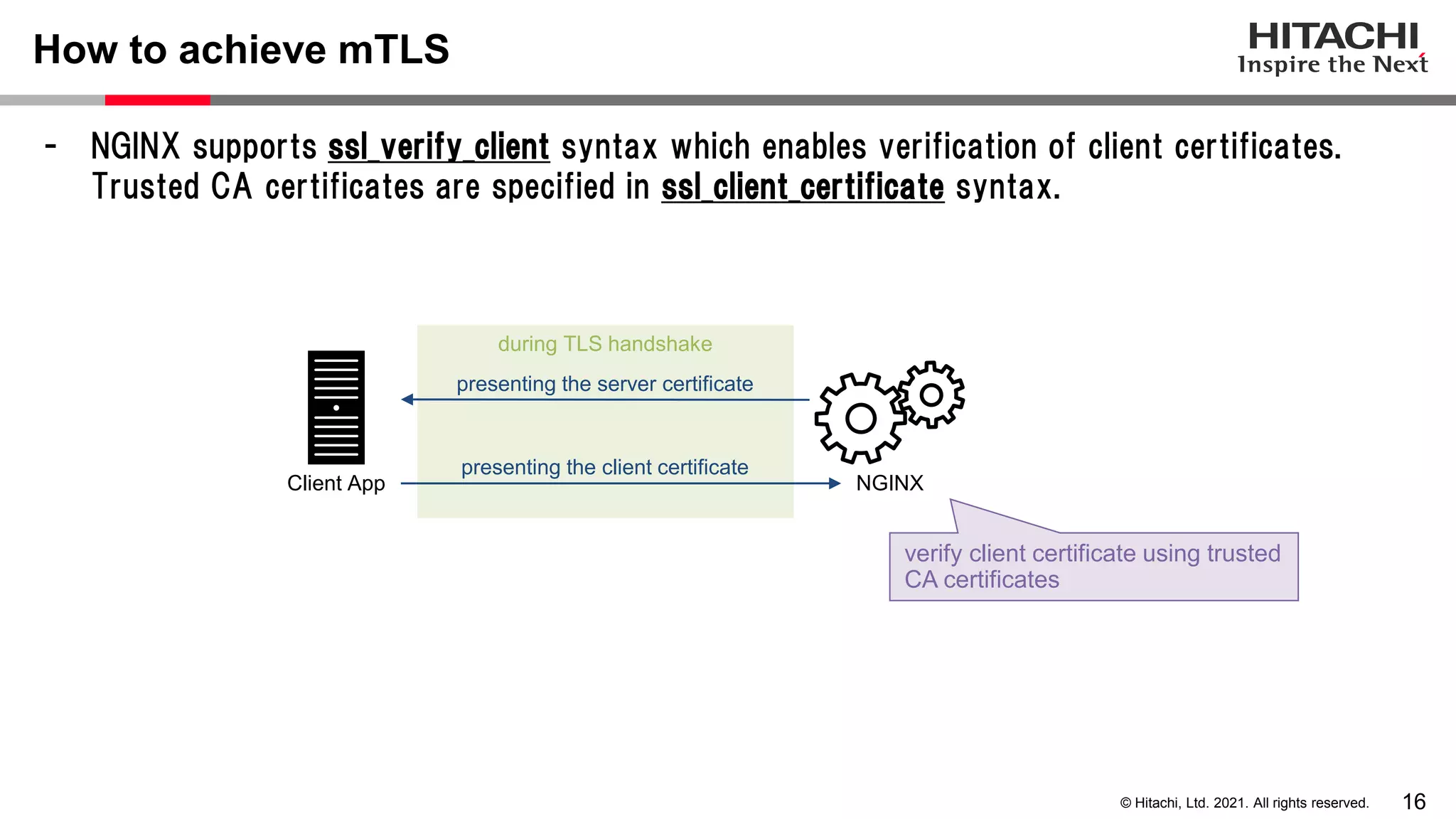
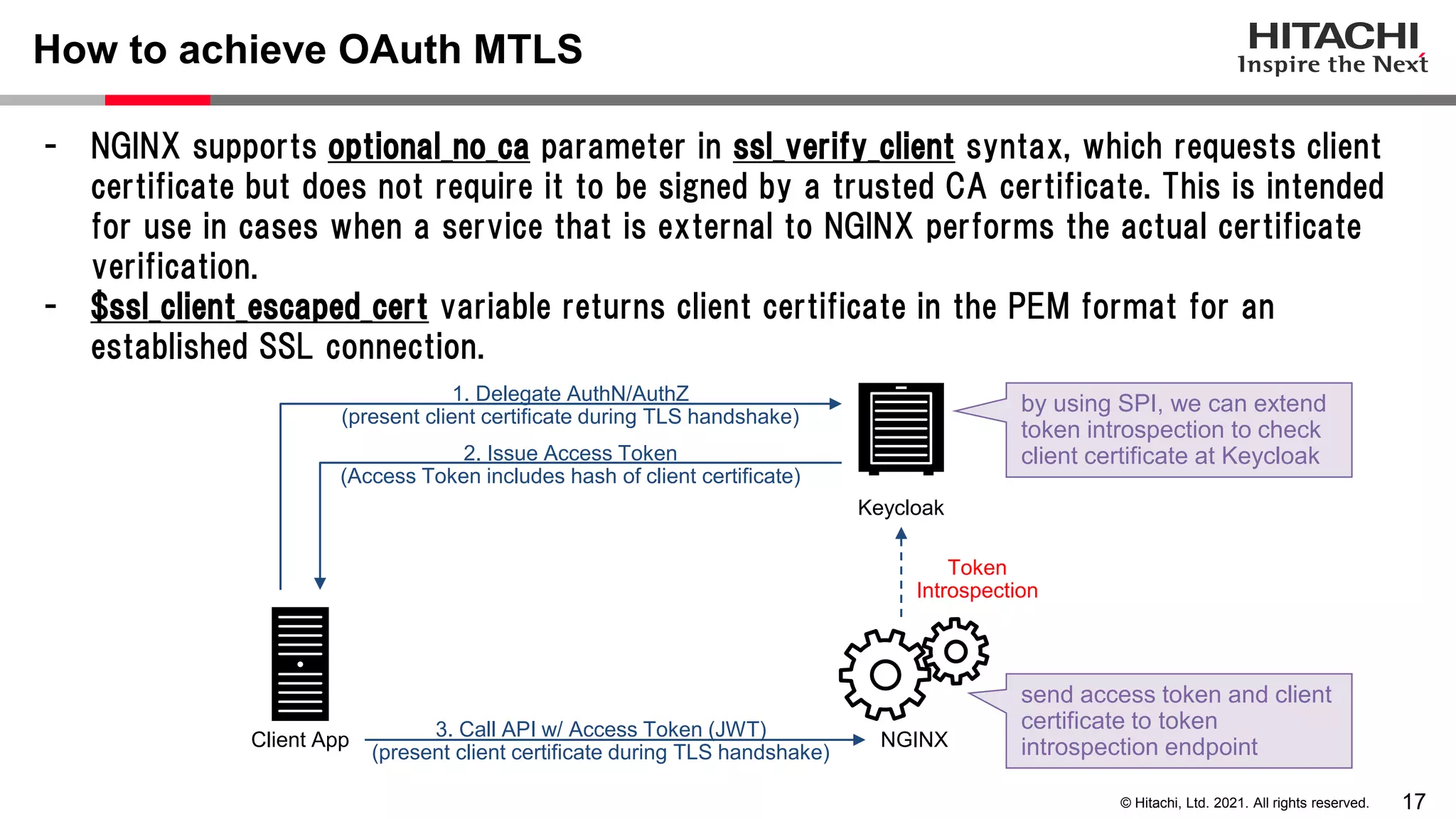
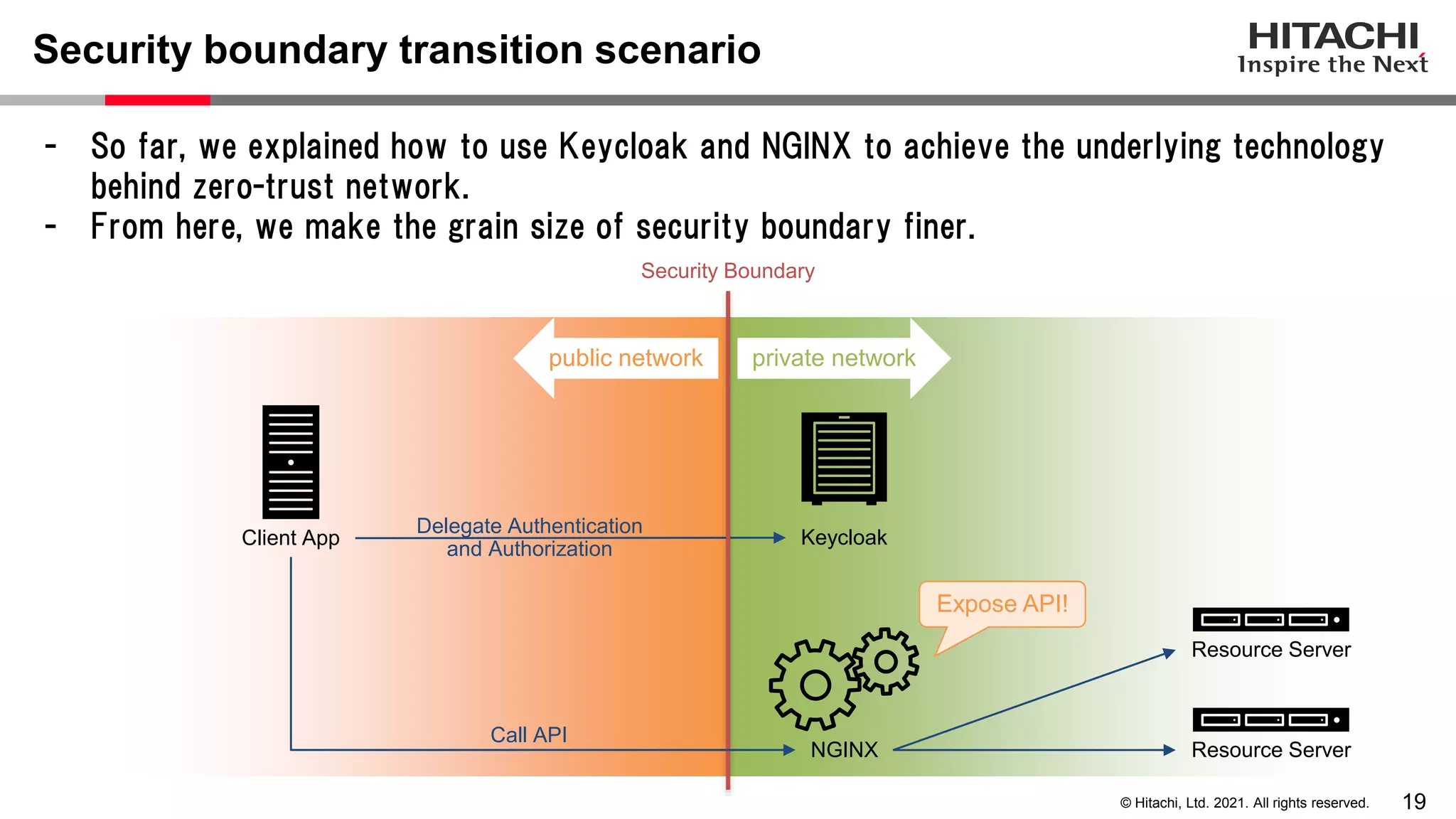
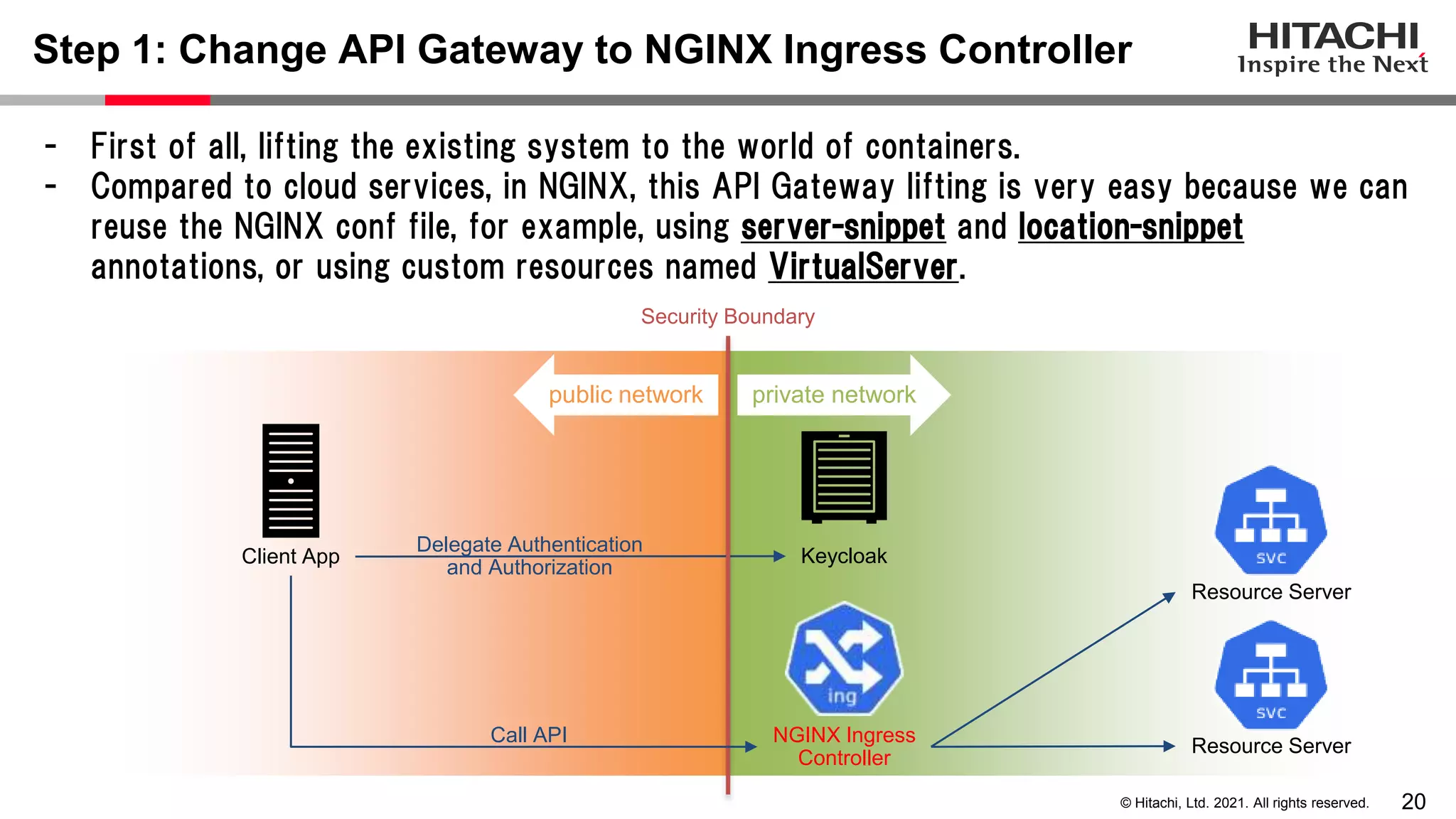
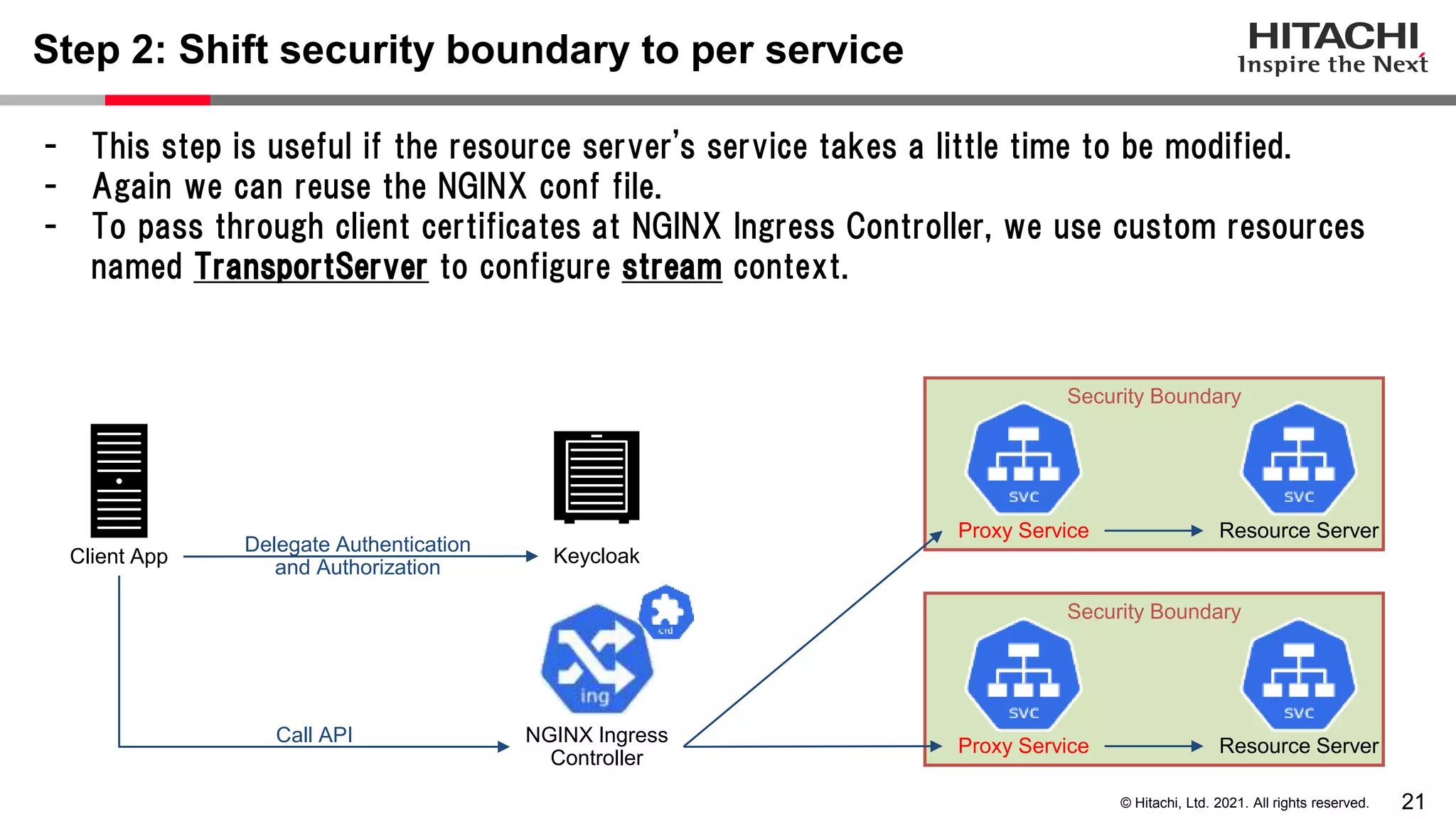
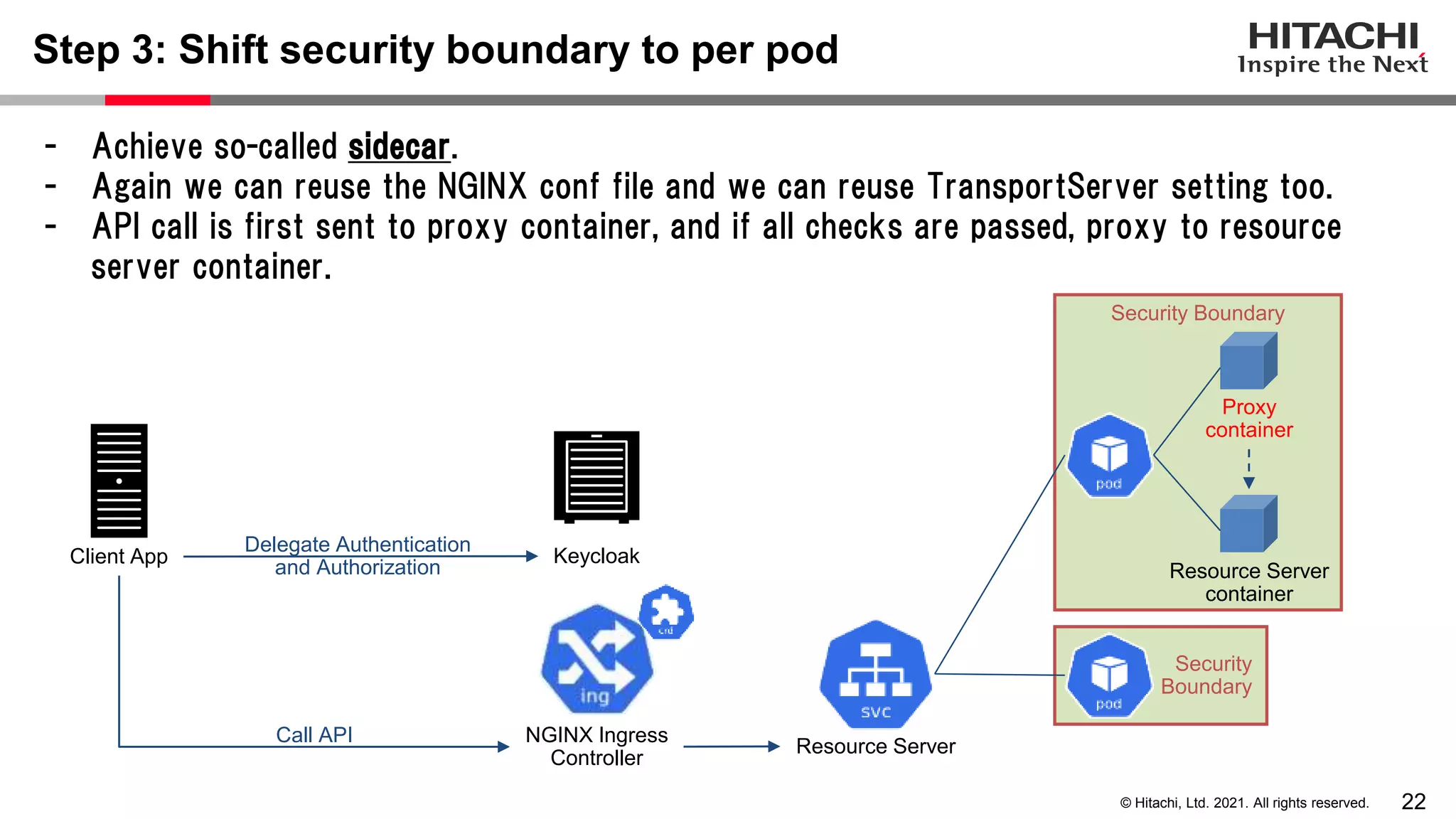
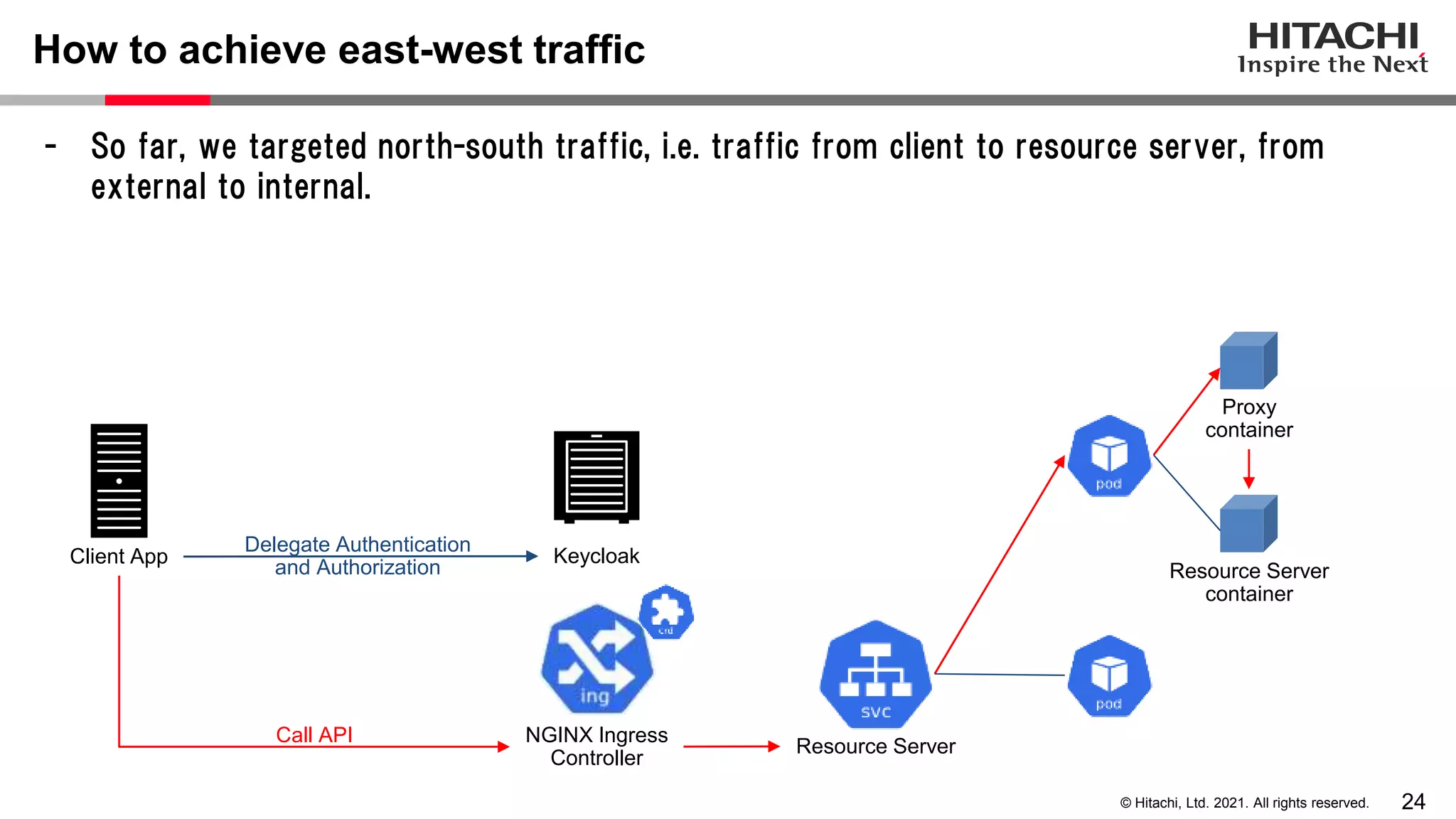
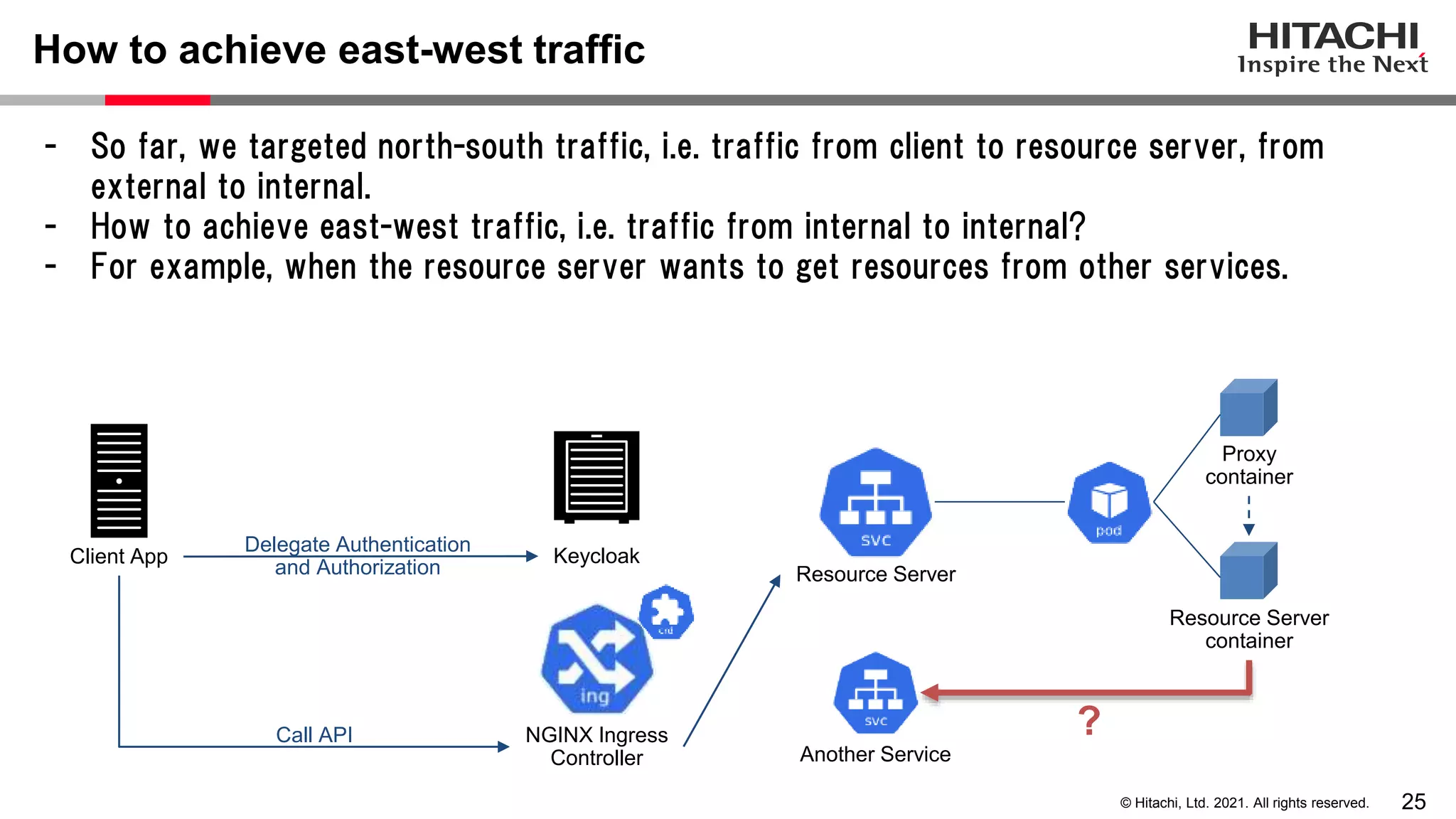
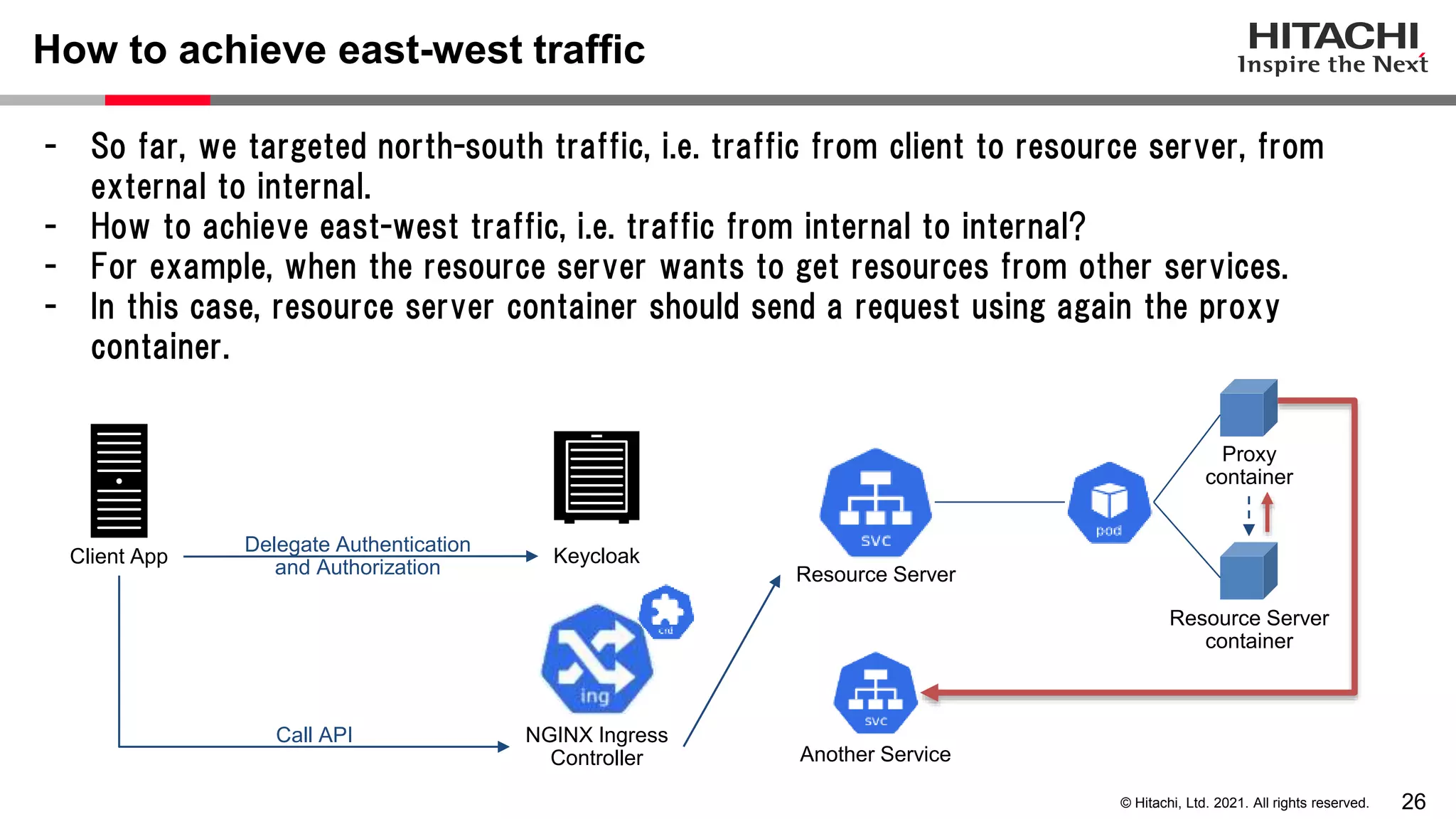
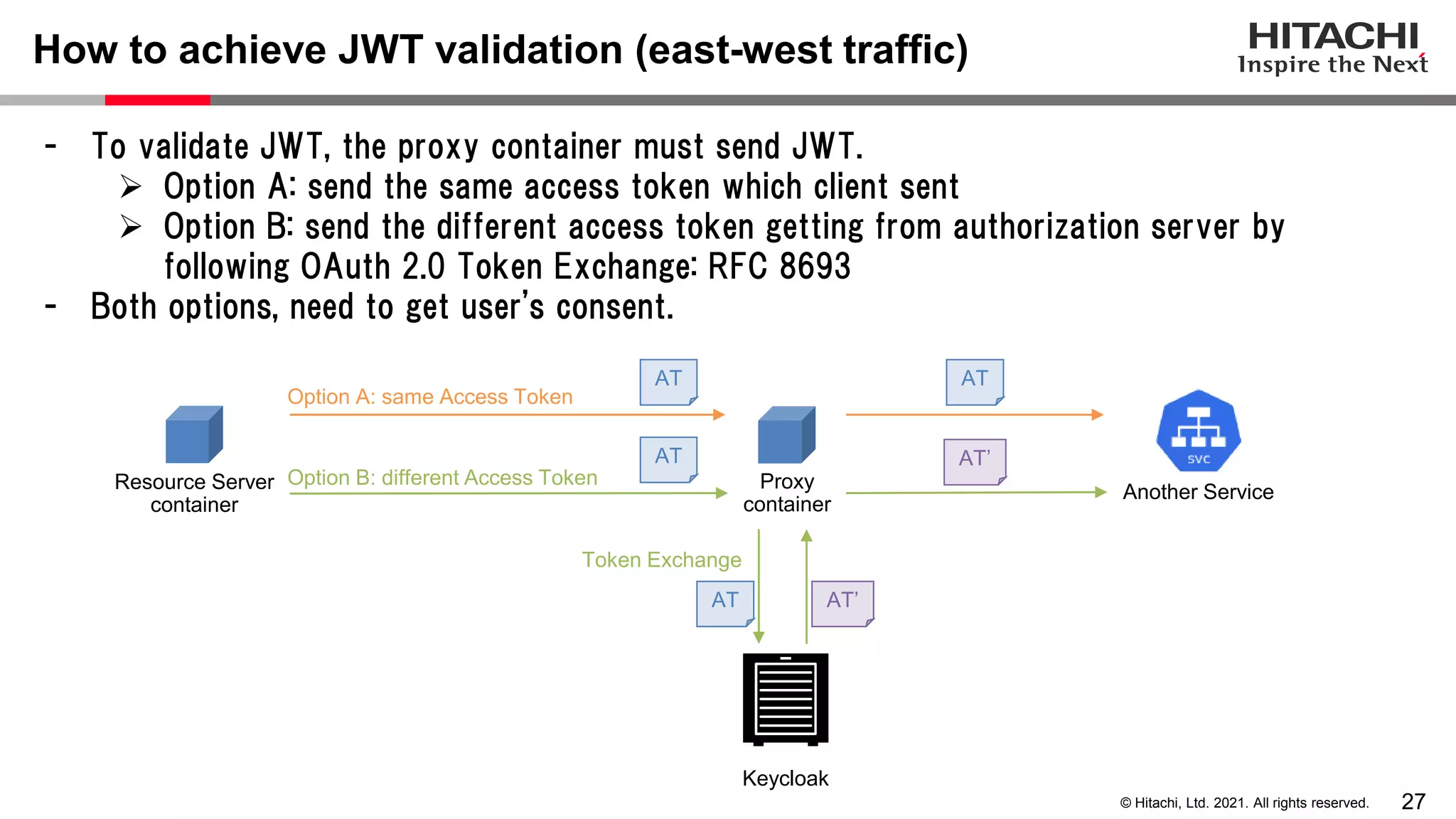
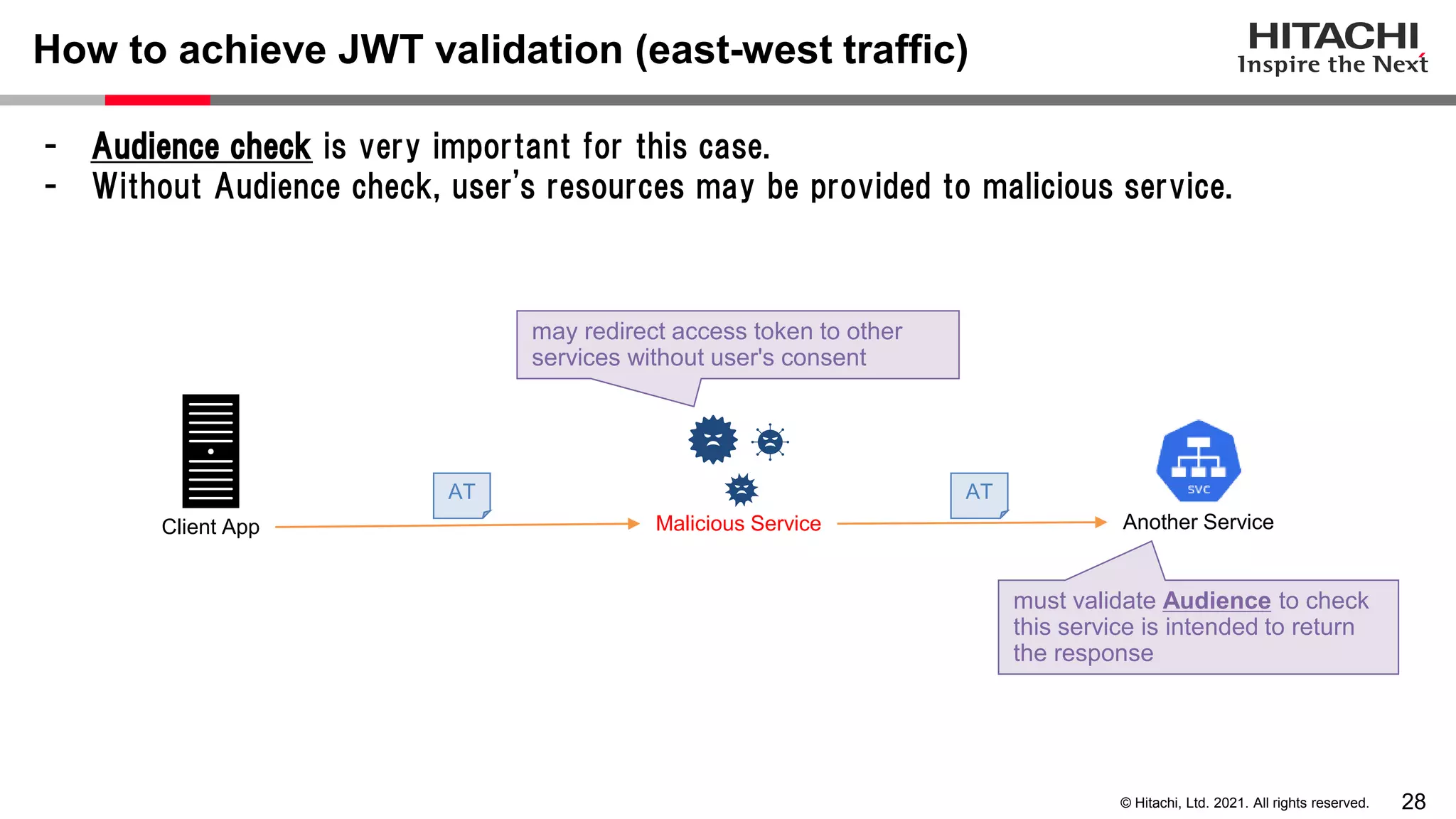
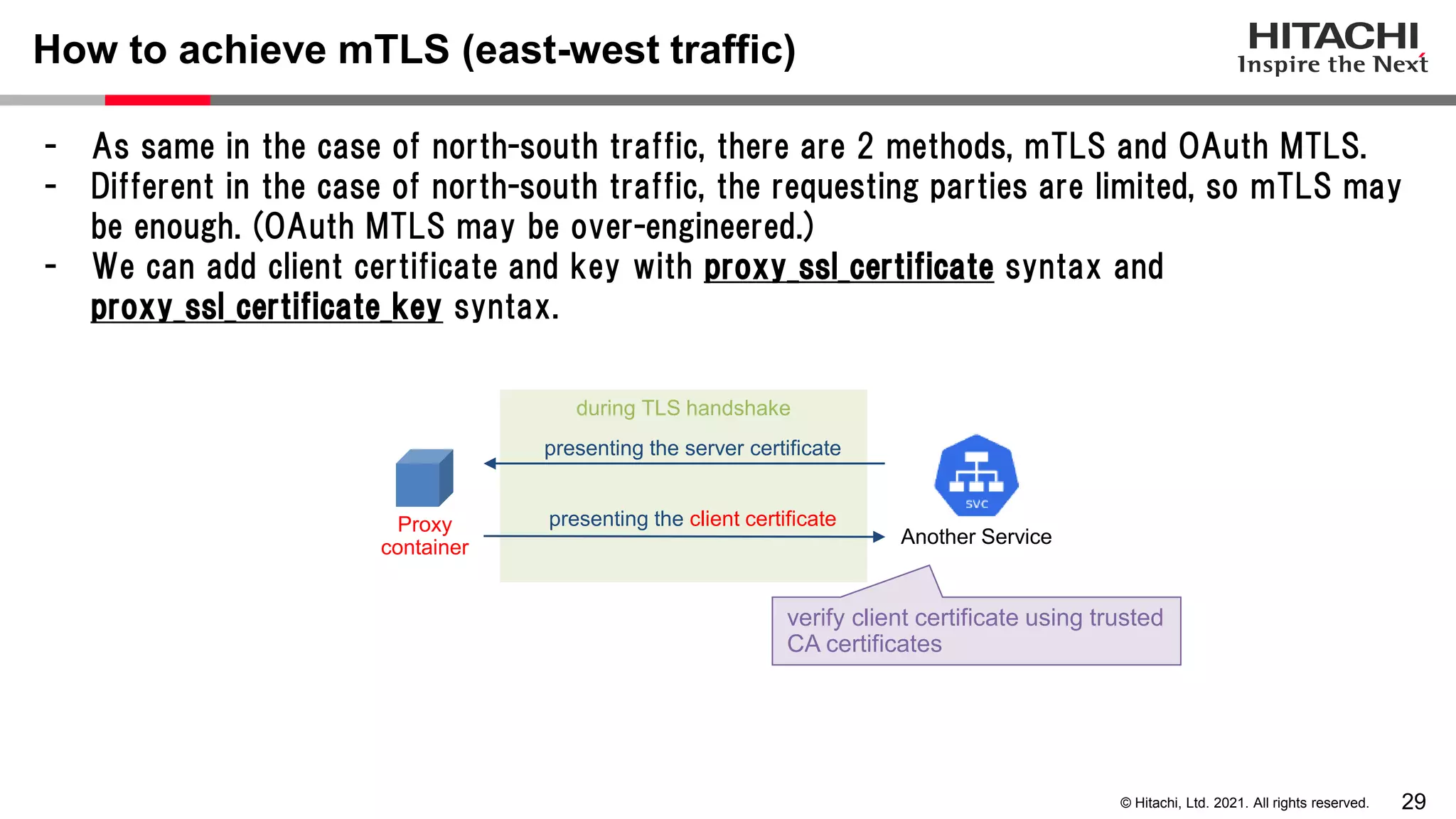
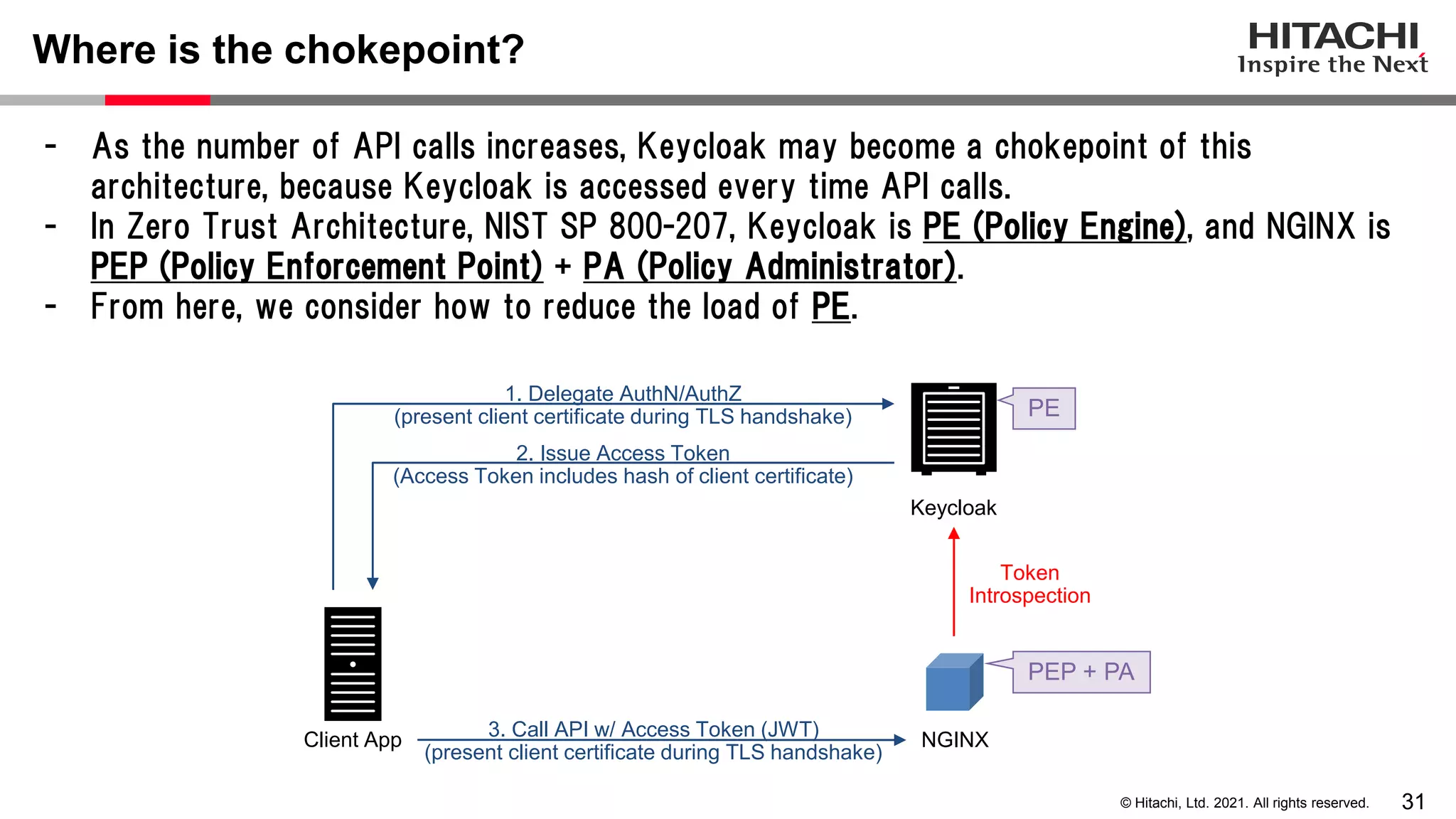
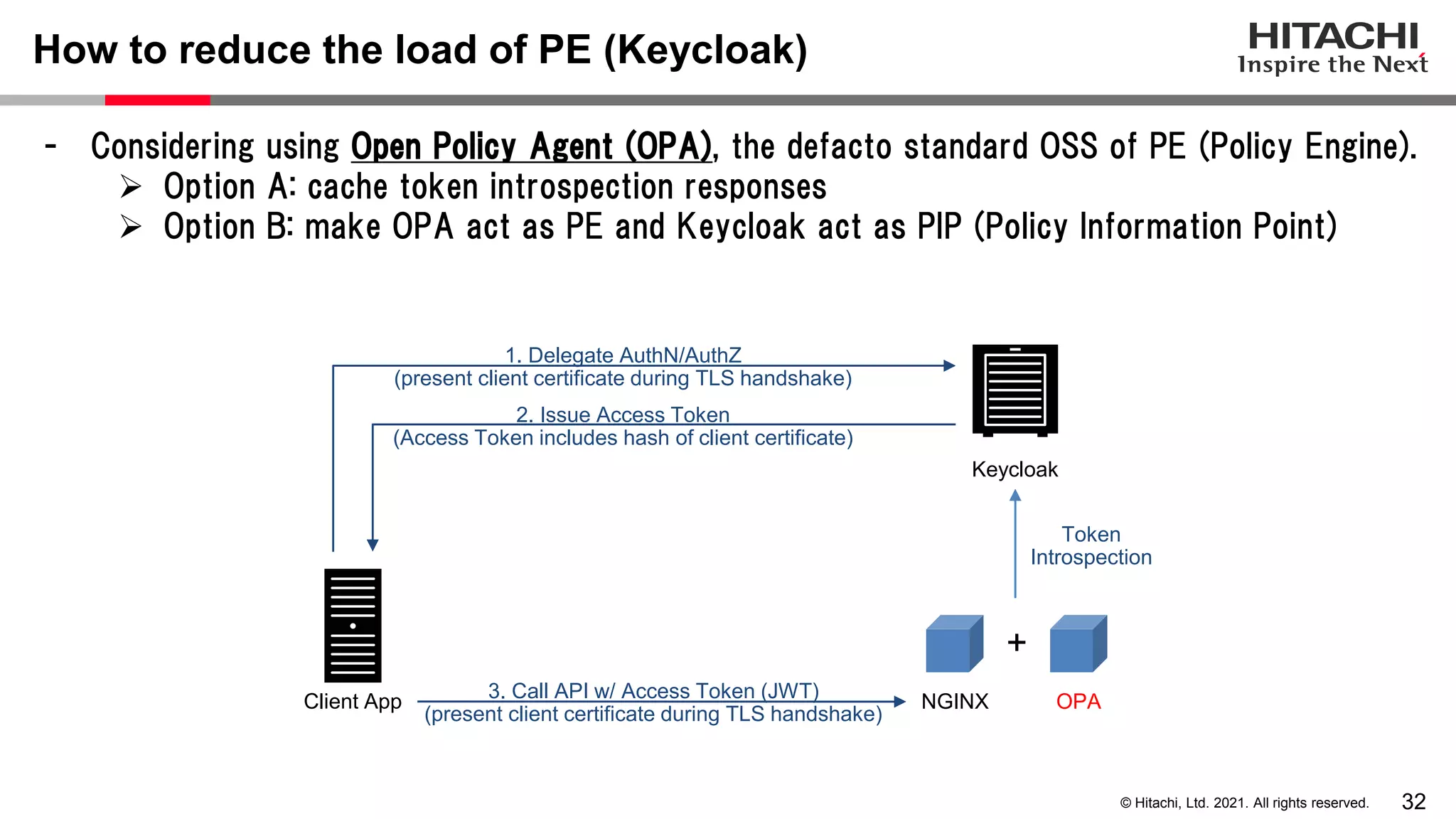
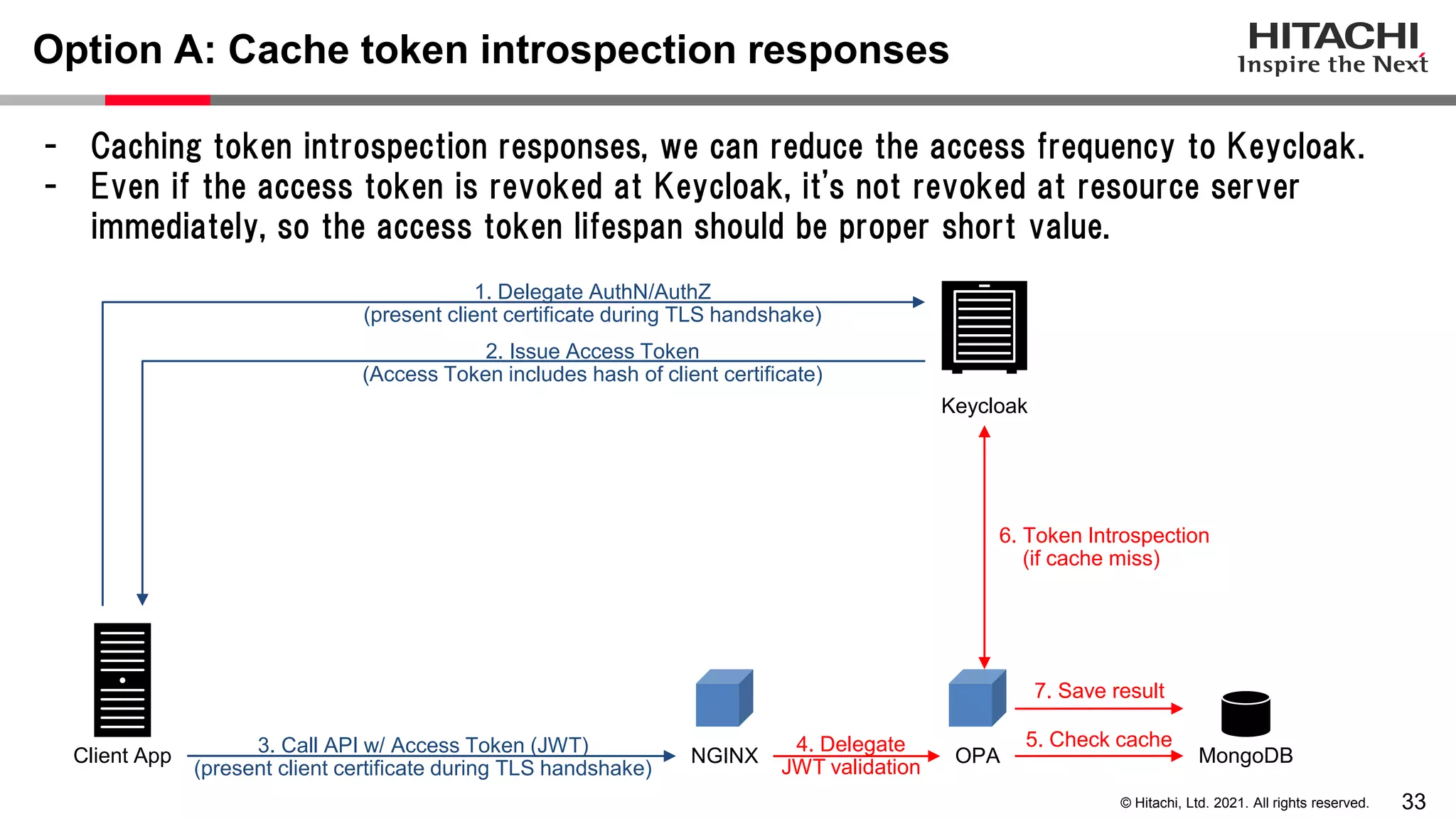
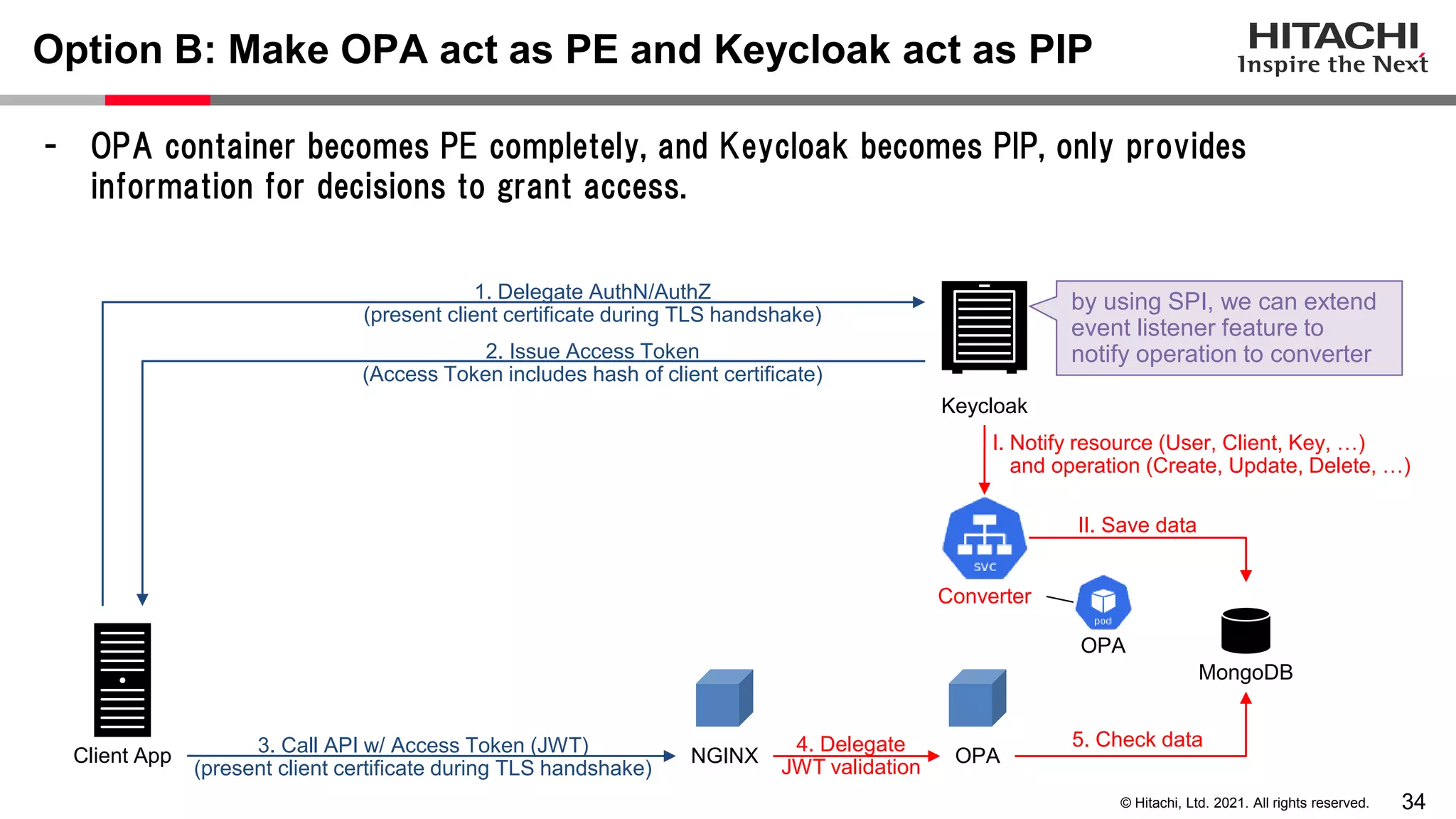
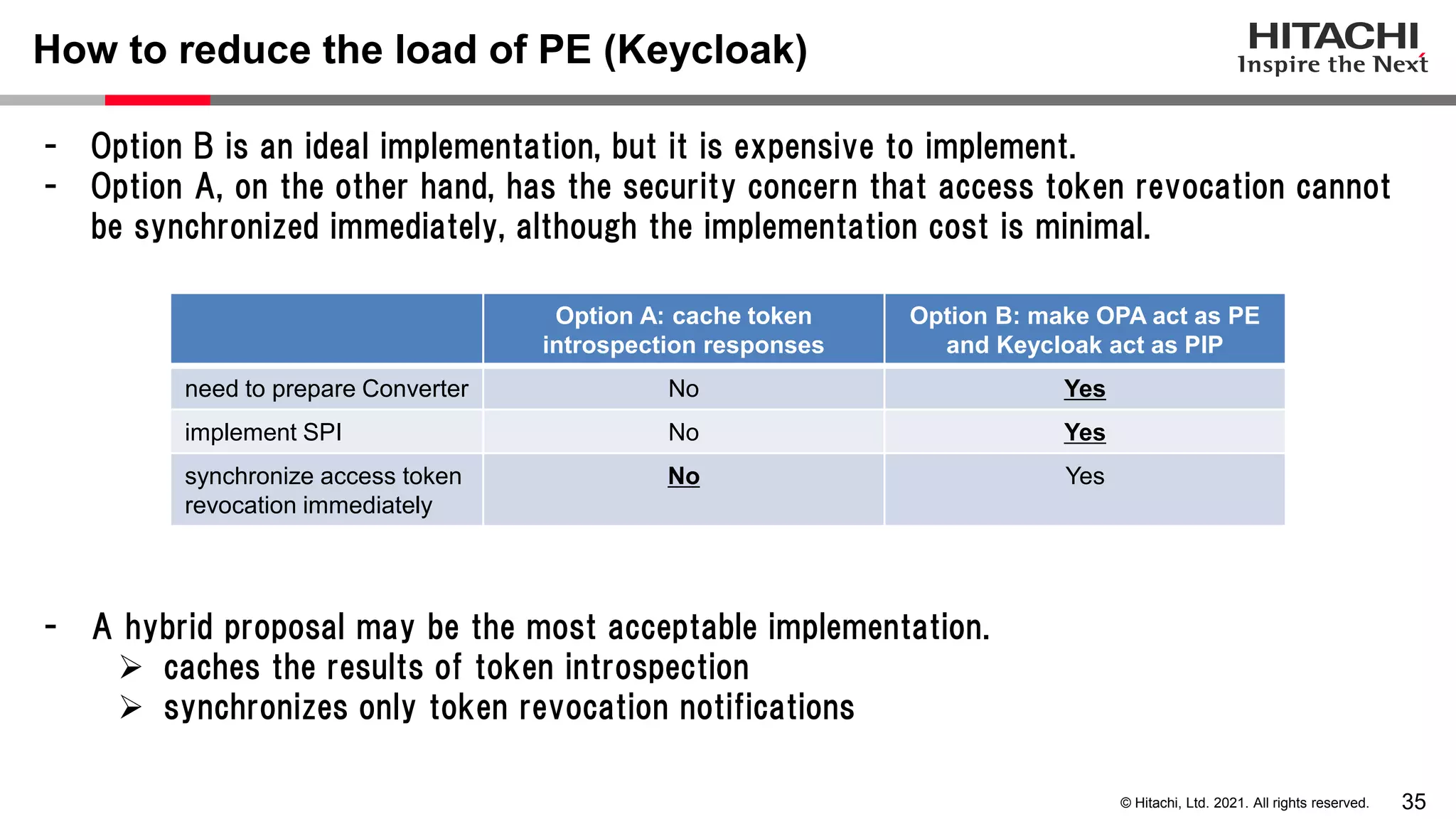
This document discusses implementing a lightweight zero-trust network using the open source tools Keycloak and NGINX. It begins by explaining the transition from a traditional network security model with clear boundaries between public and private networks to a zero-trust model where security boundaries are defined individually for each service or pod. It then covers how to implement the underlying technologies of JWT validation, mutual TLS authentication, and OAuth MTLS using Keycloak as an authorization server and NGINX as an API gateway. Additional topics discussed include how to secure east-west internal traffic and resolve potential policy decision point chokepoints.