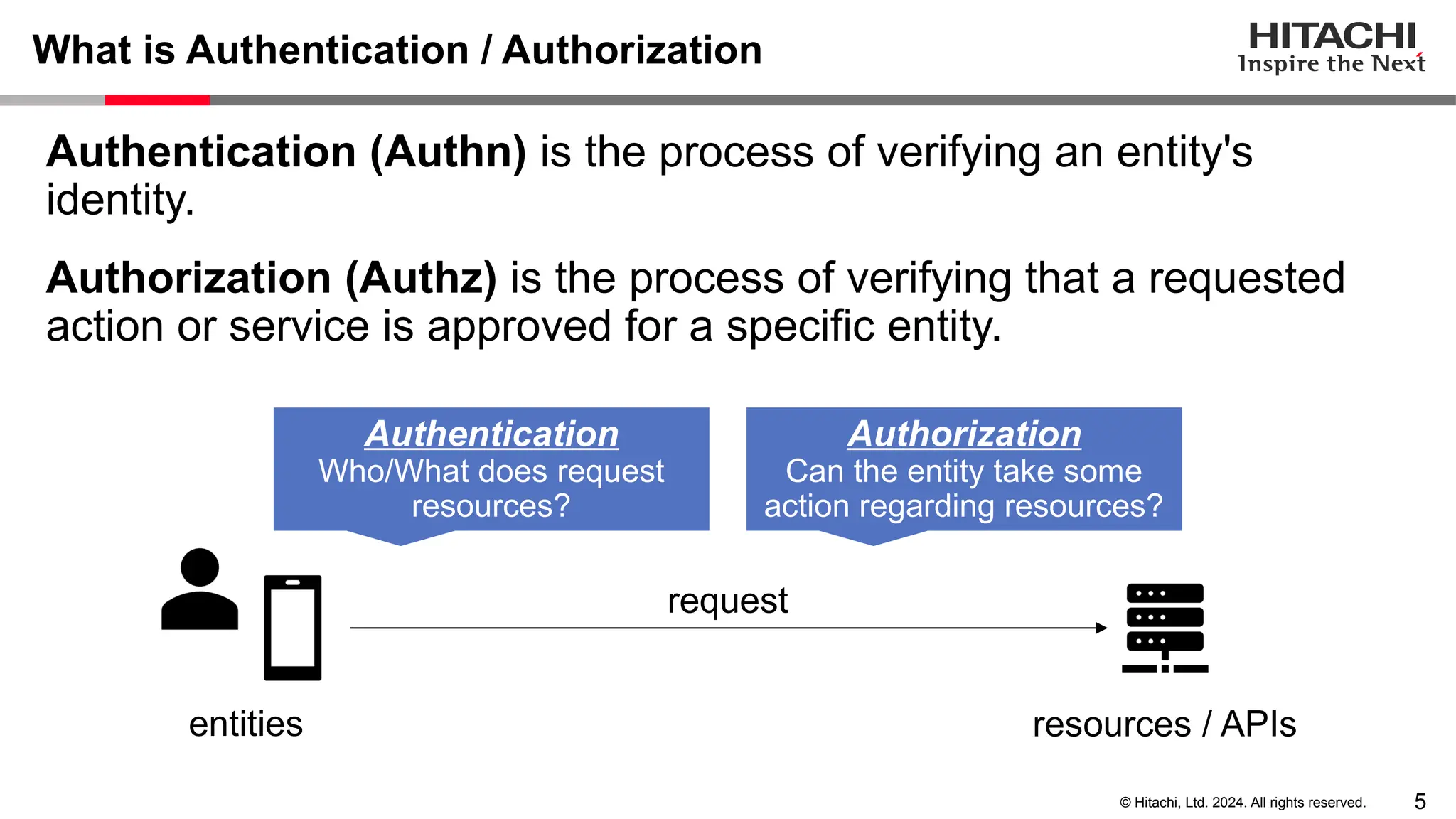
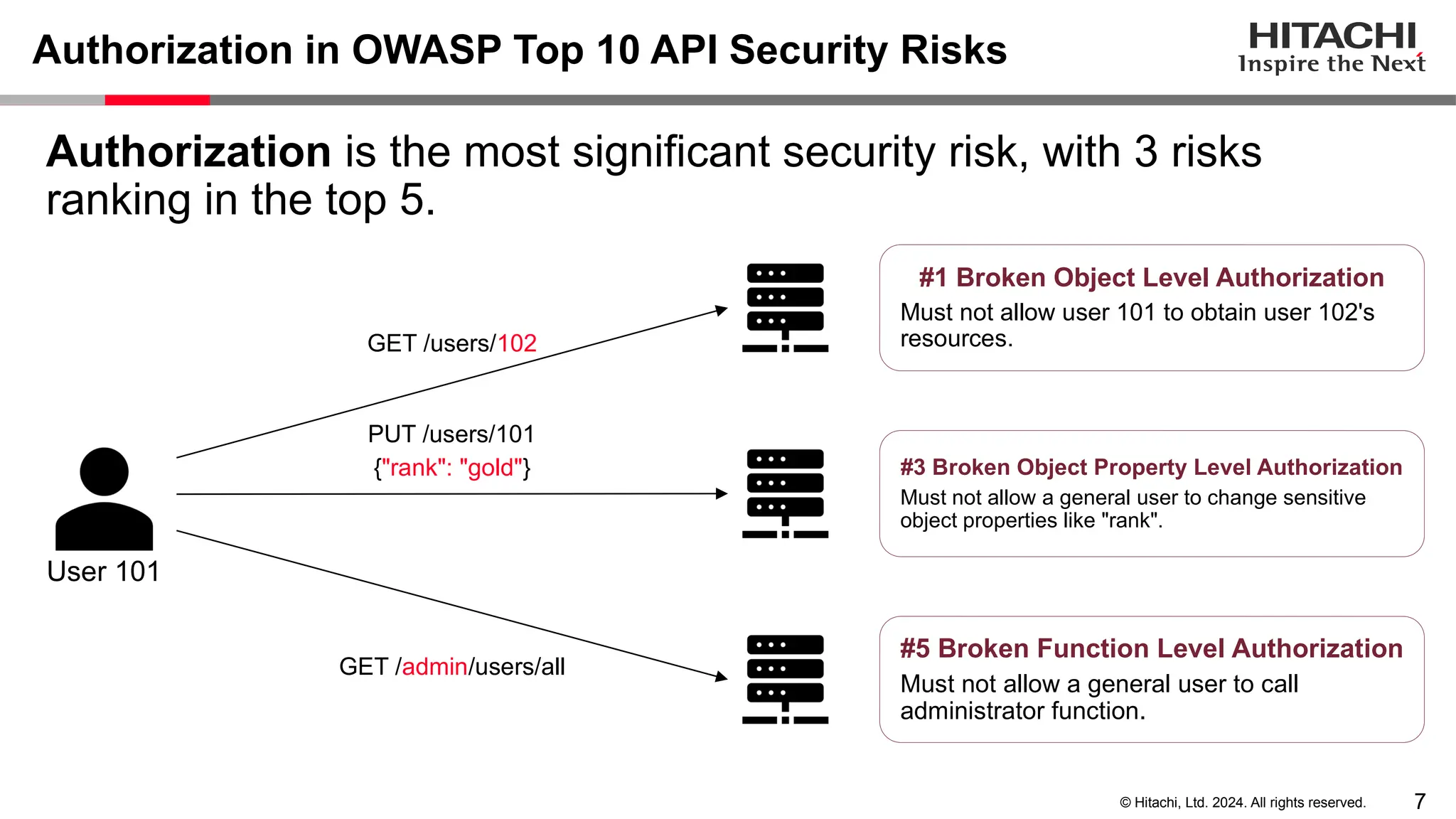
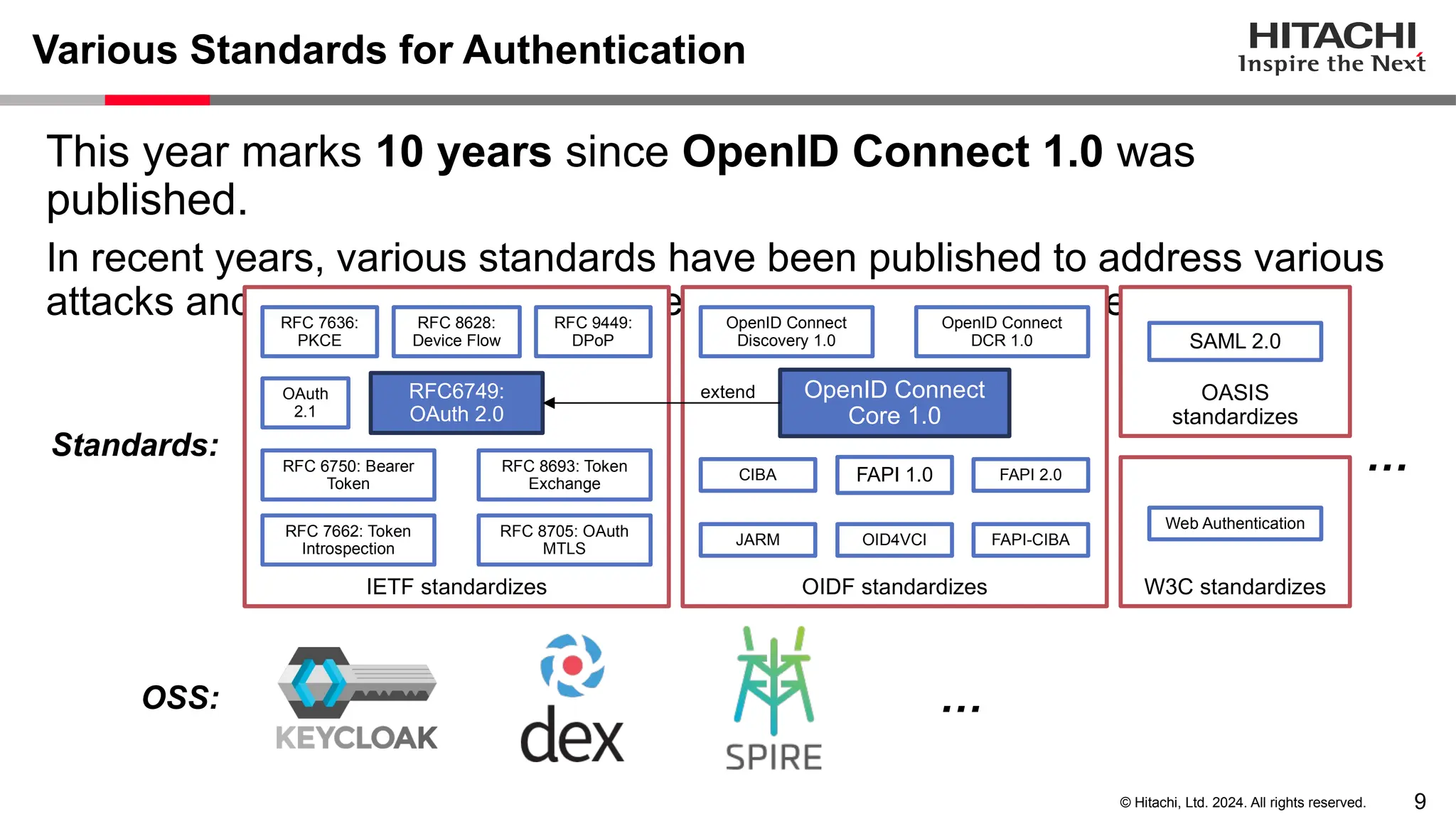
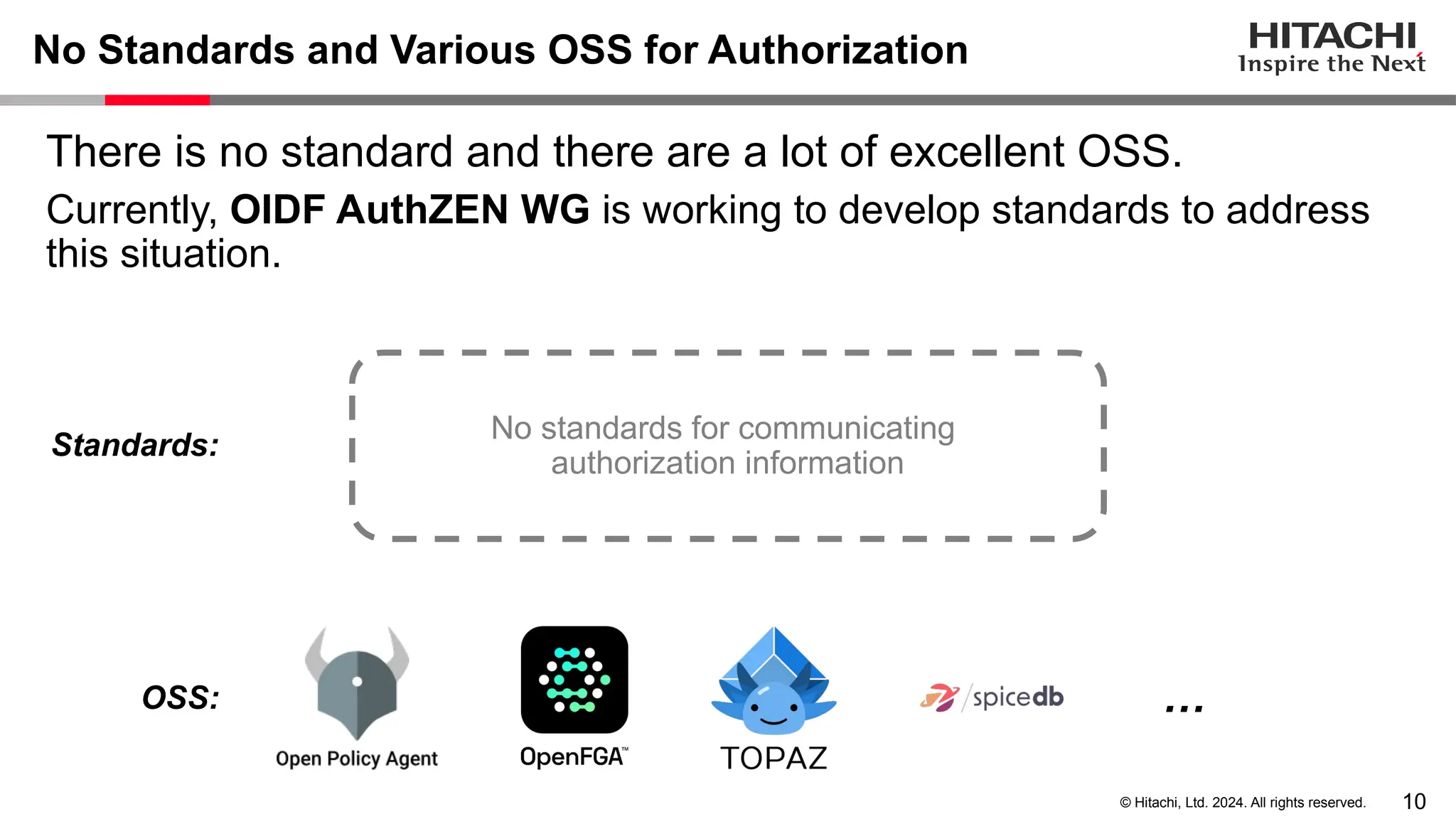
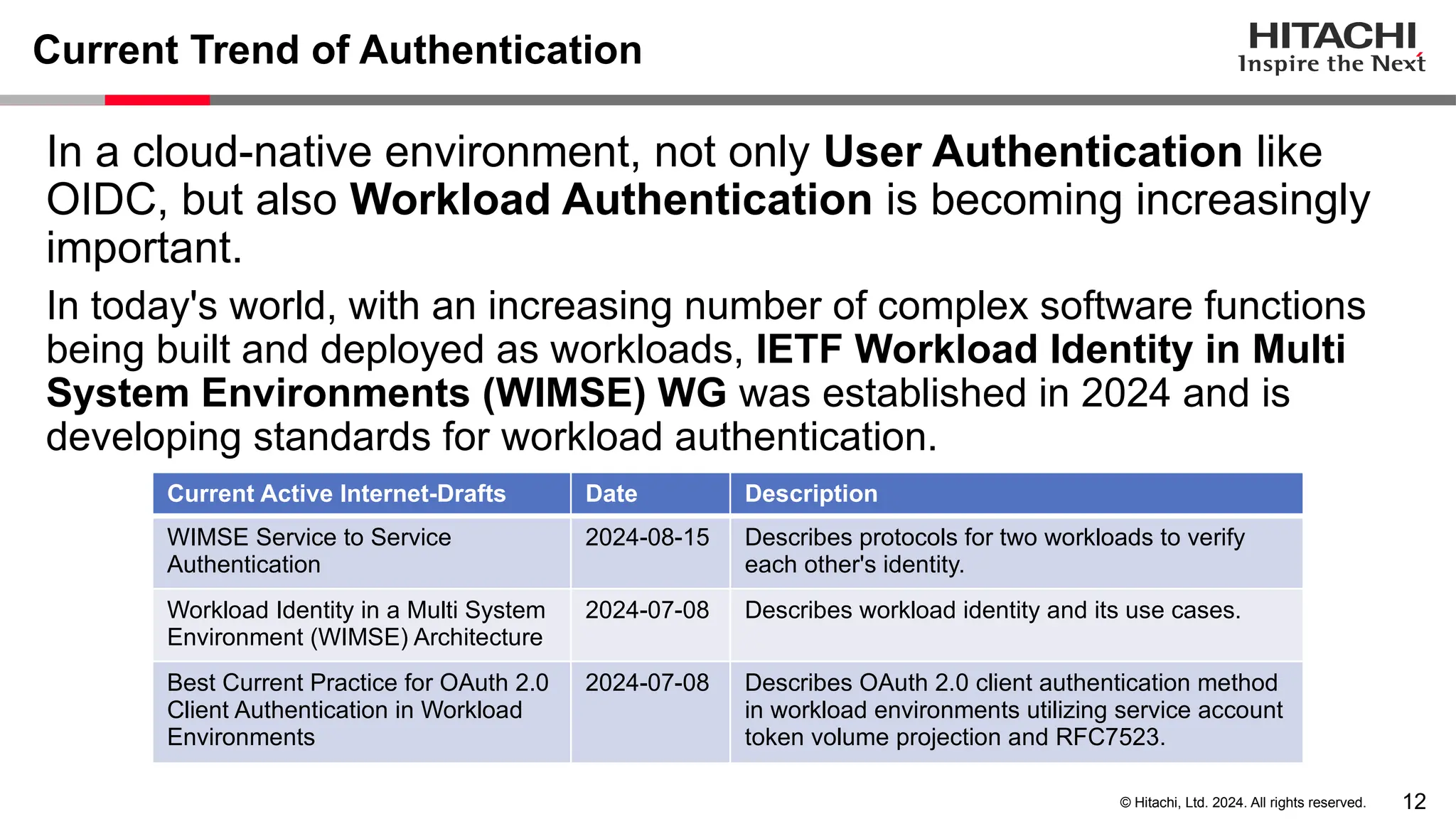
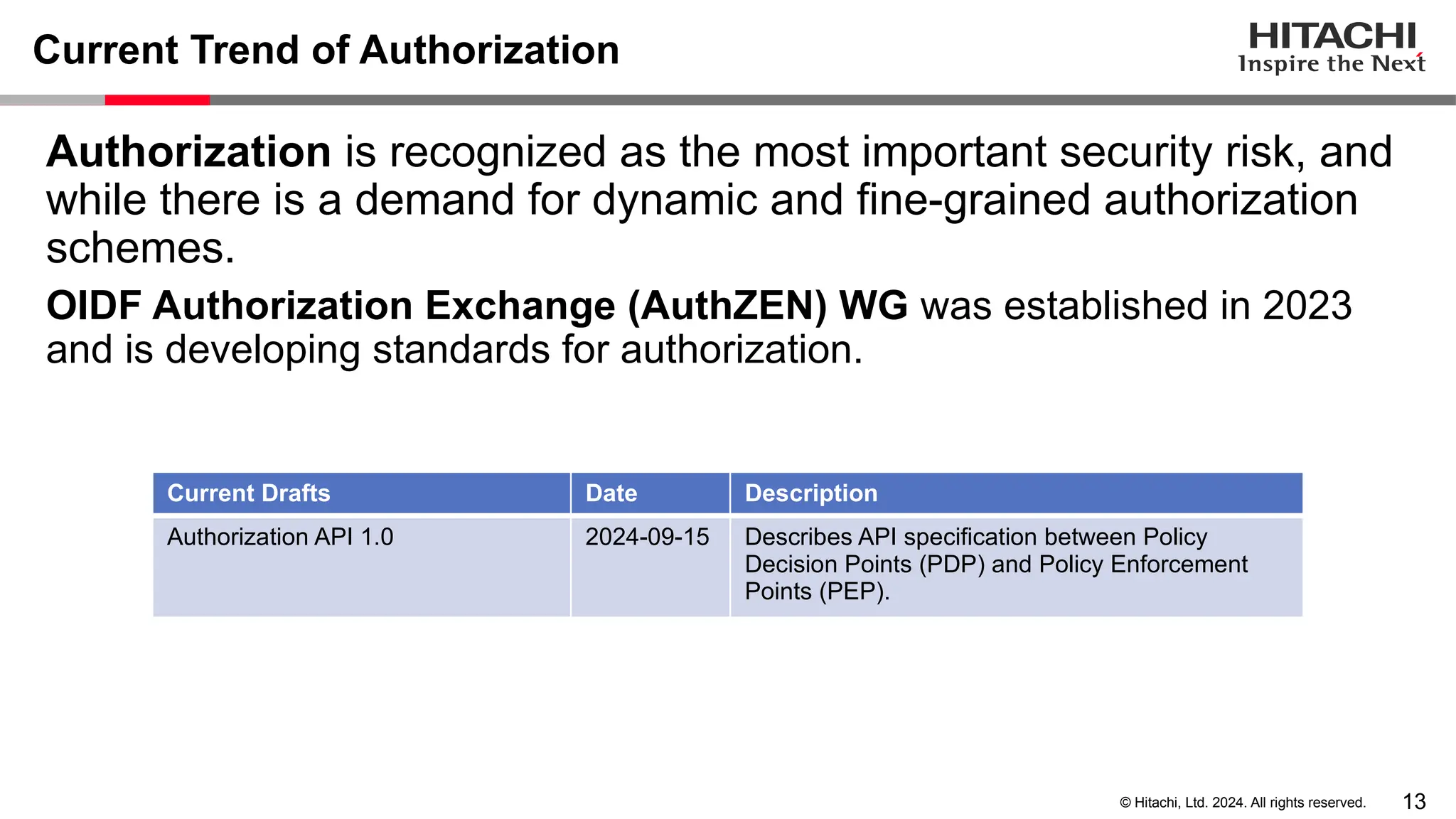
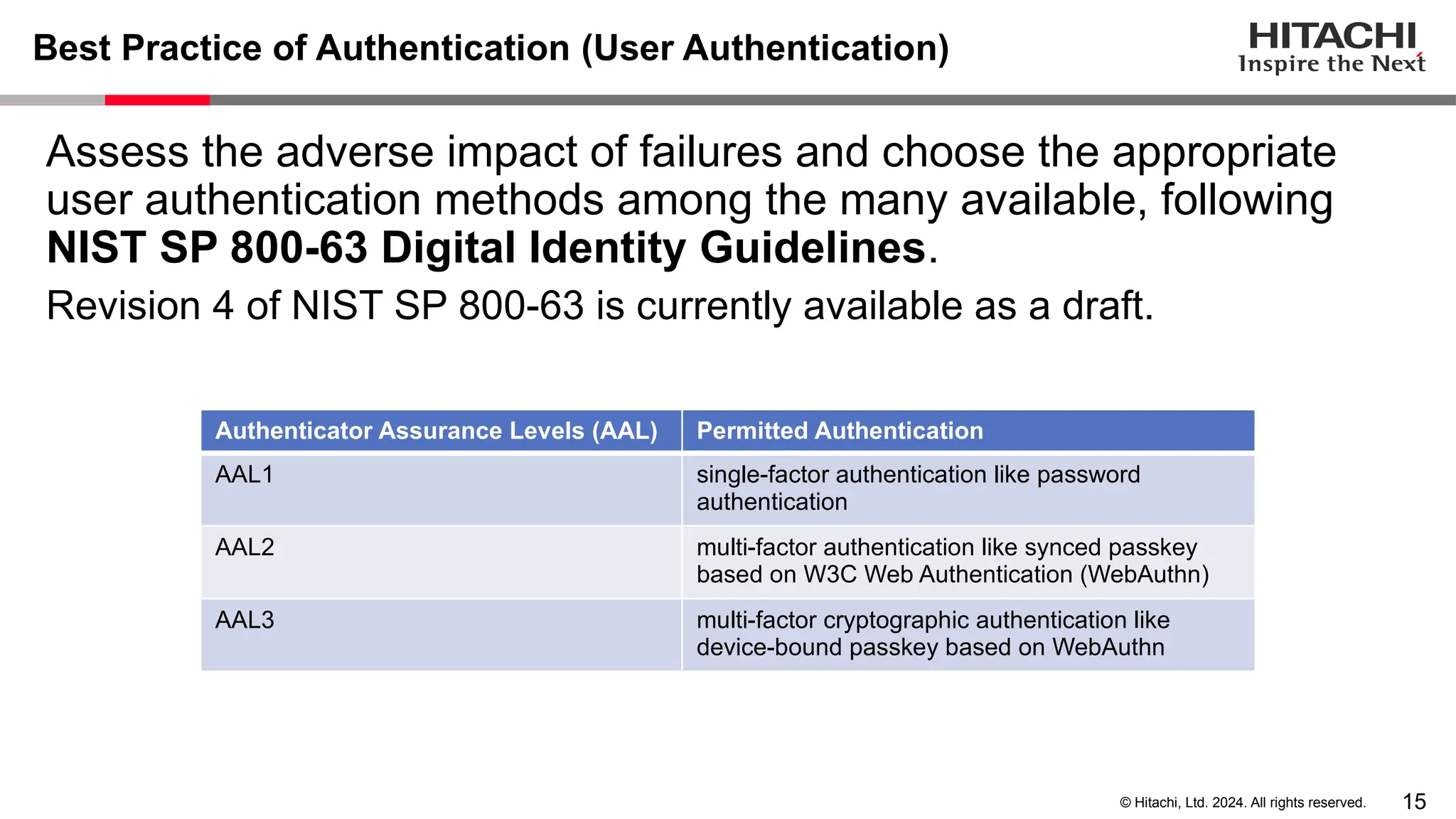
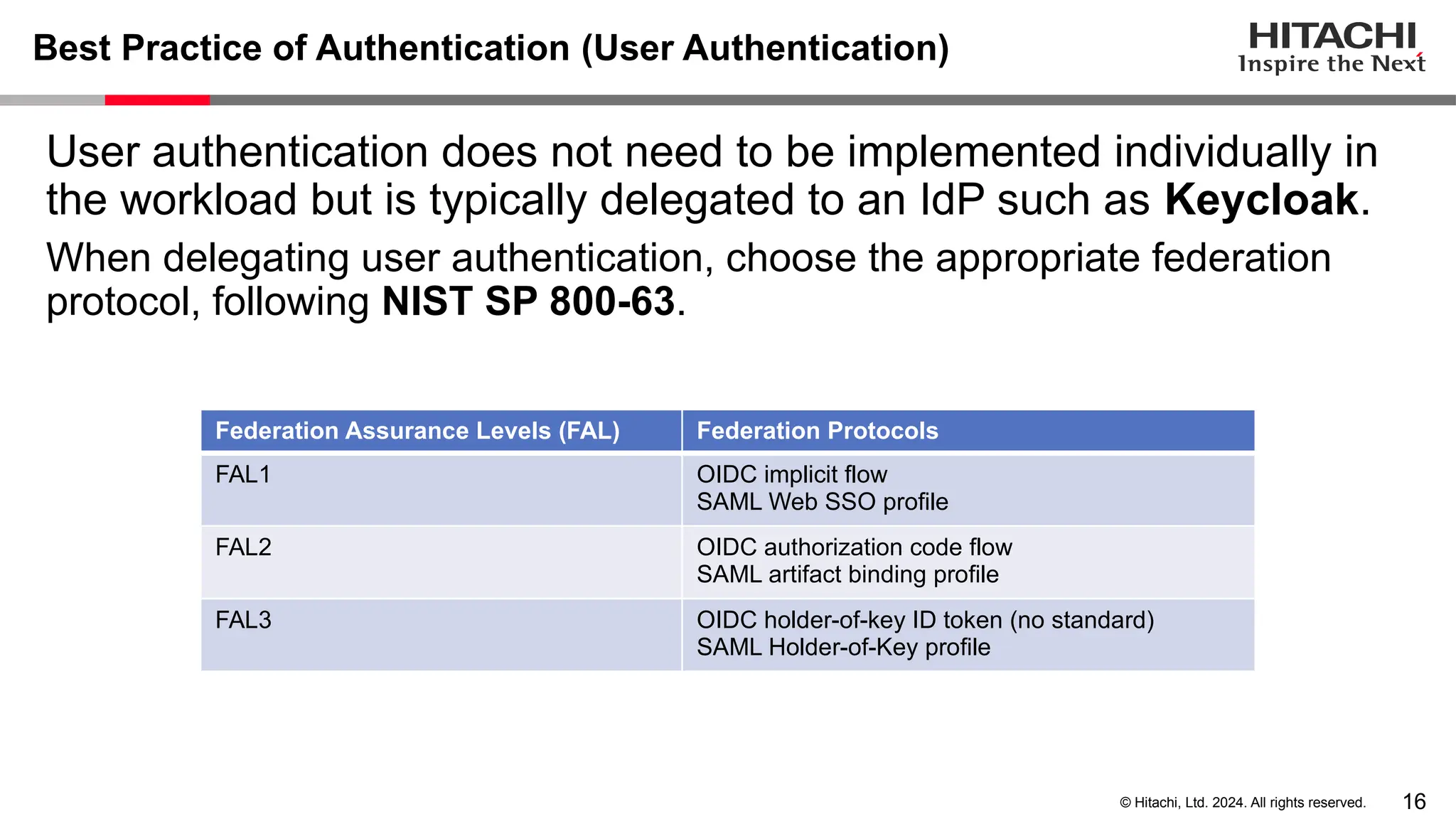
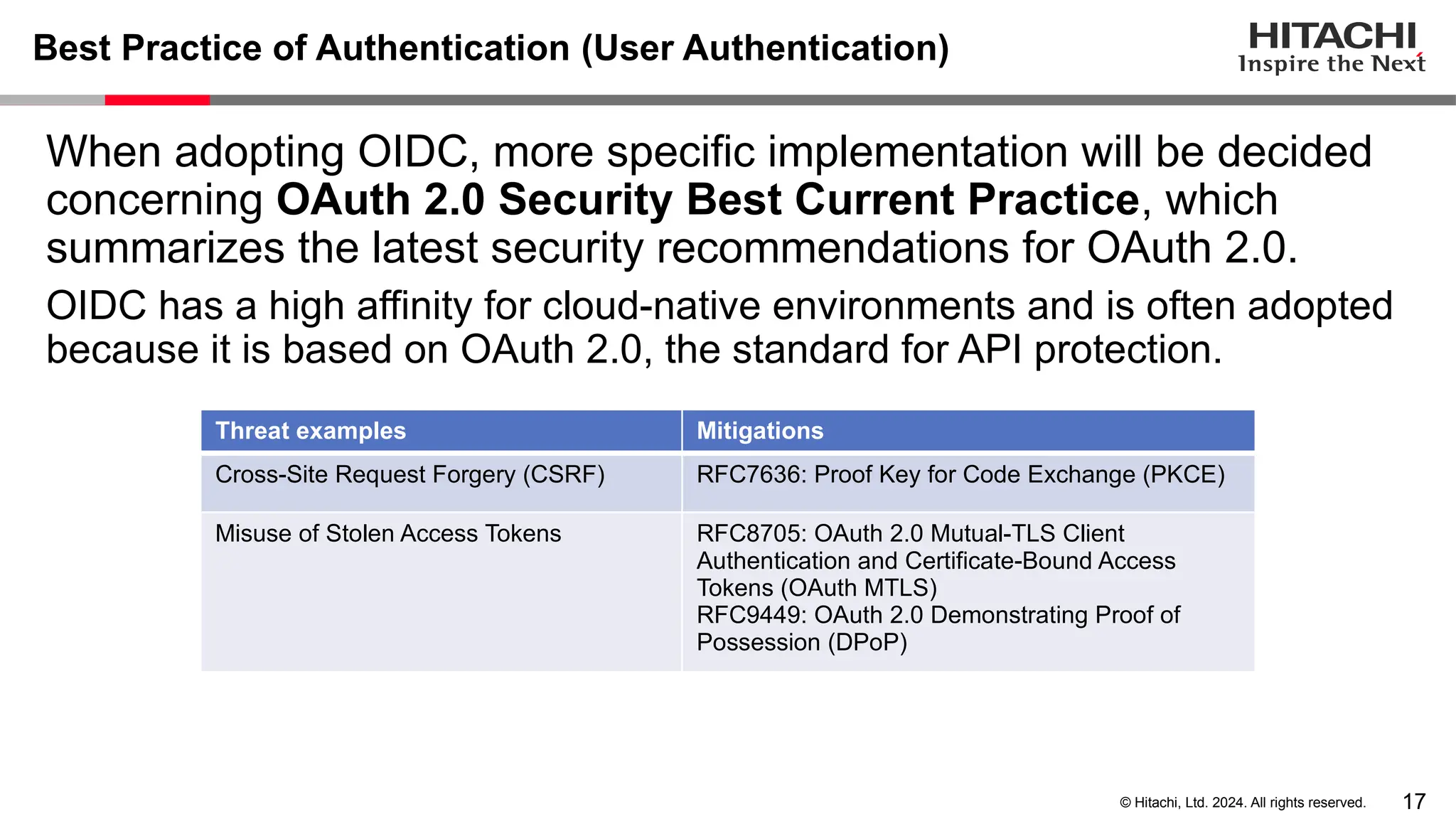
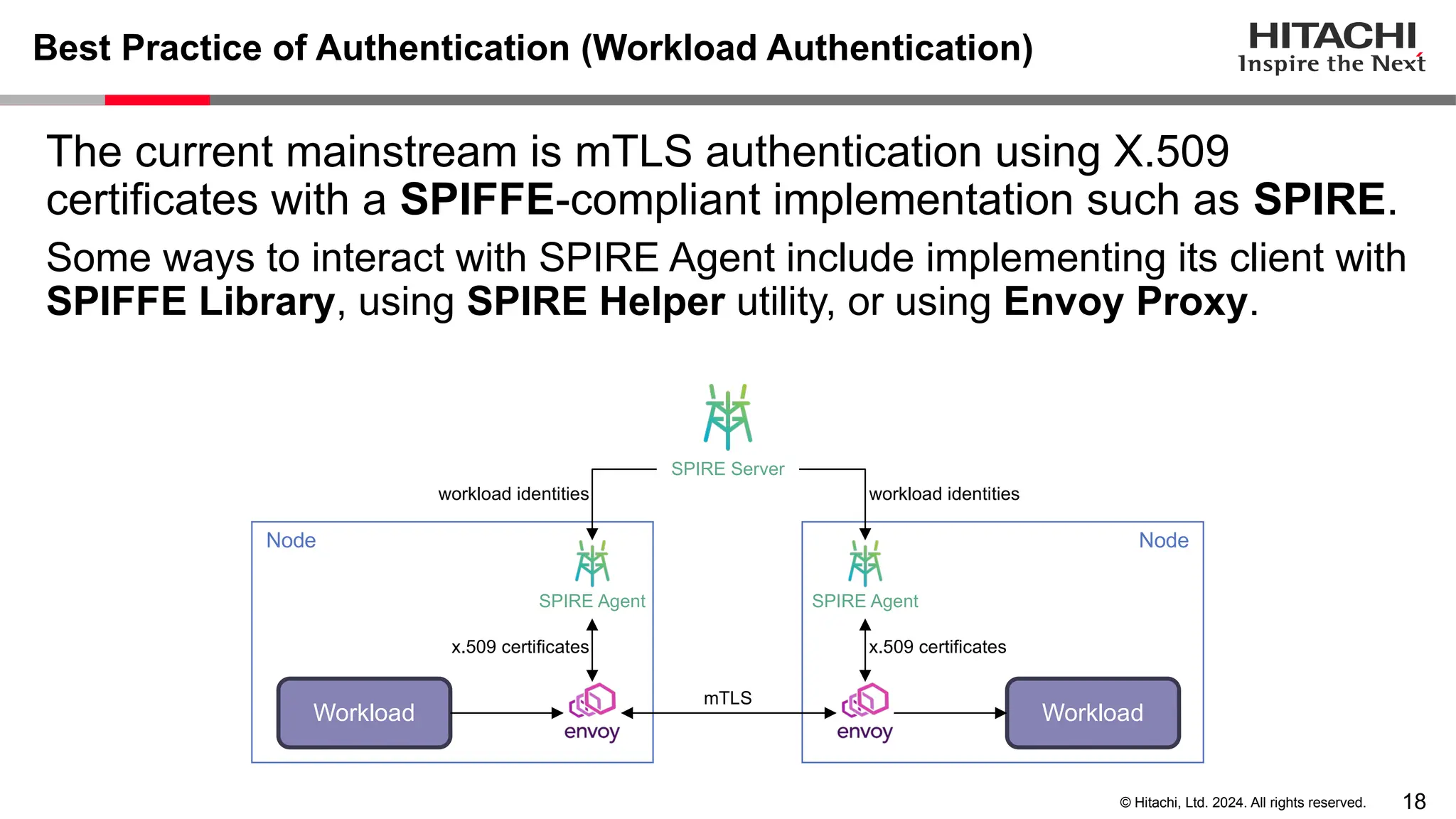
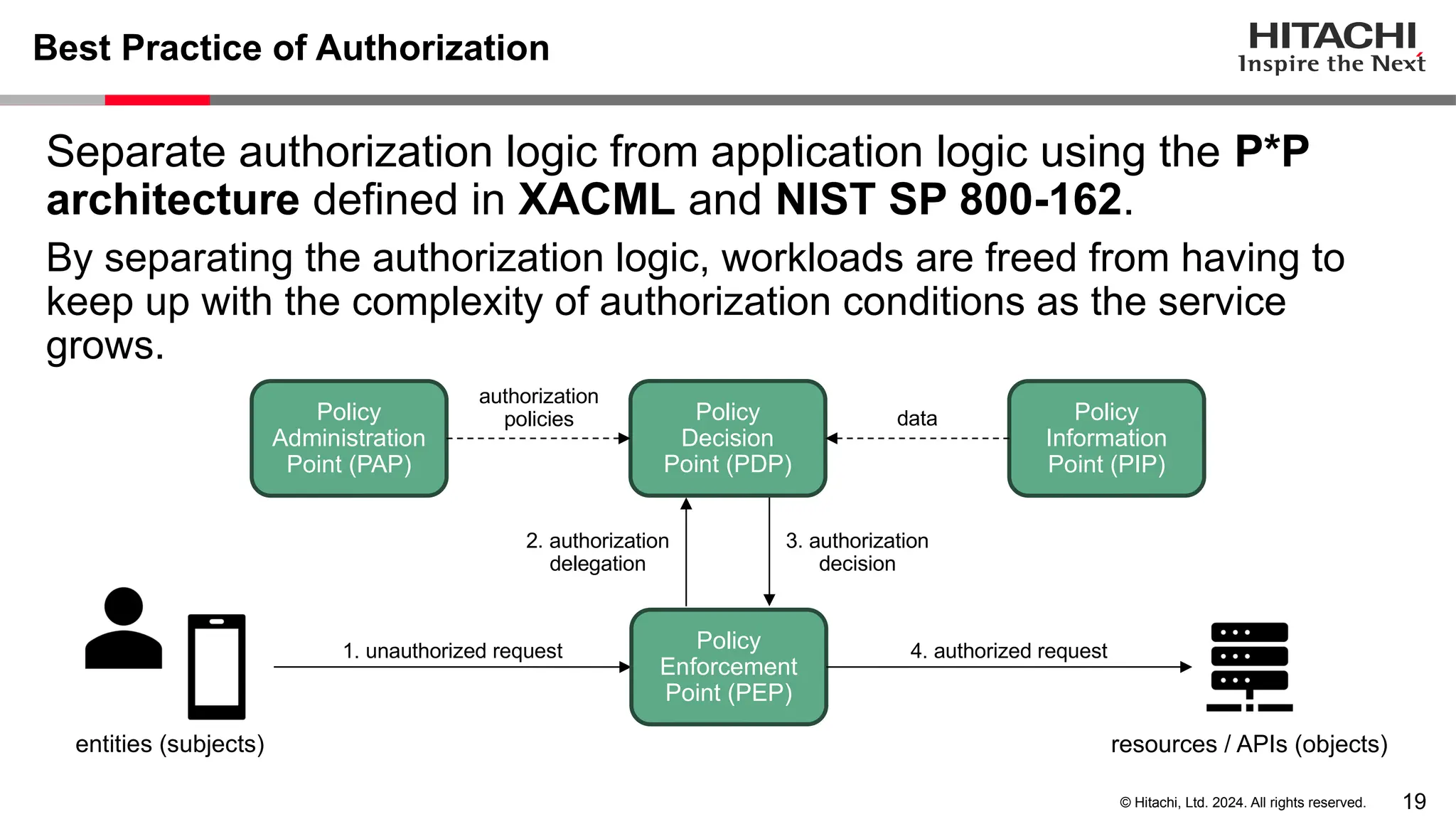
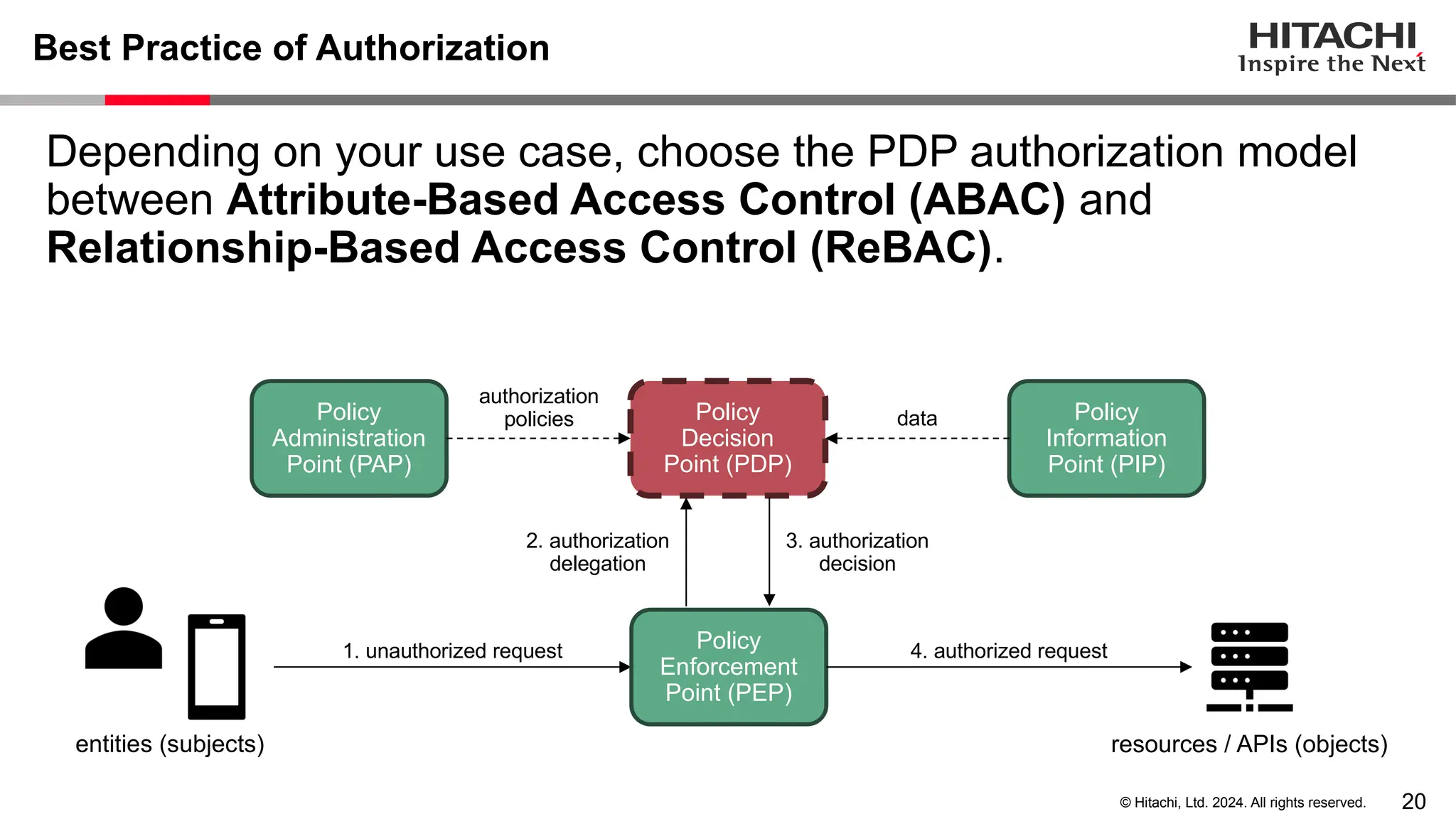
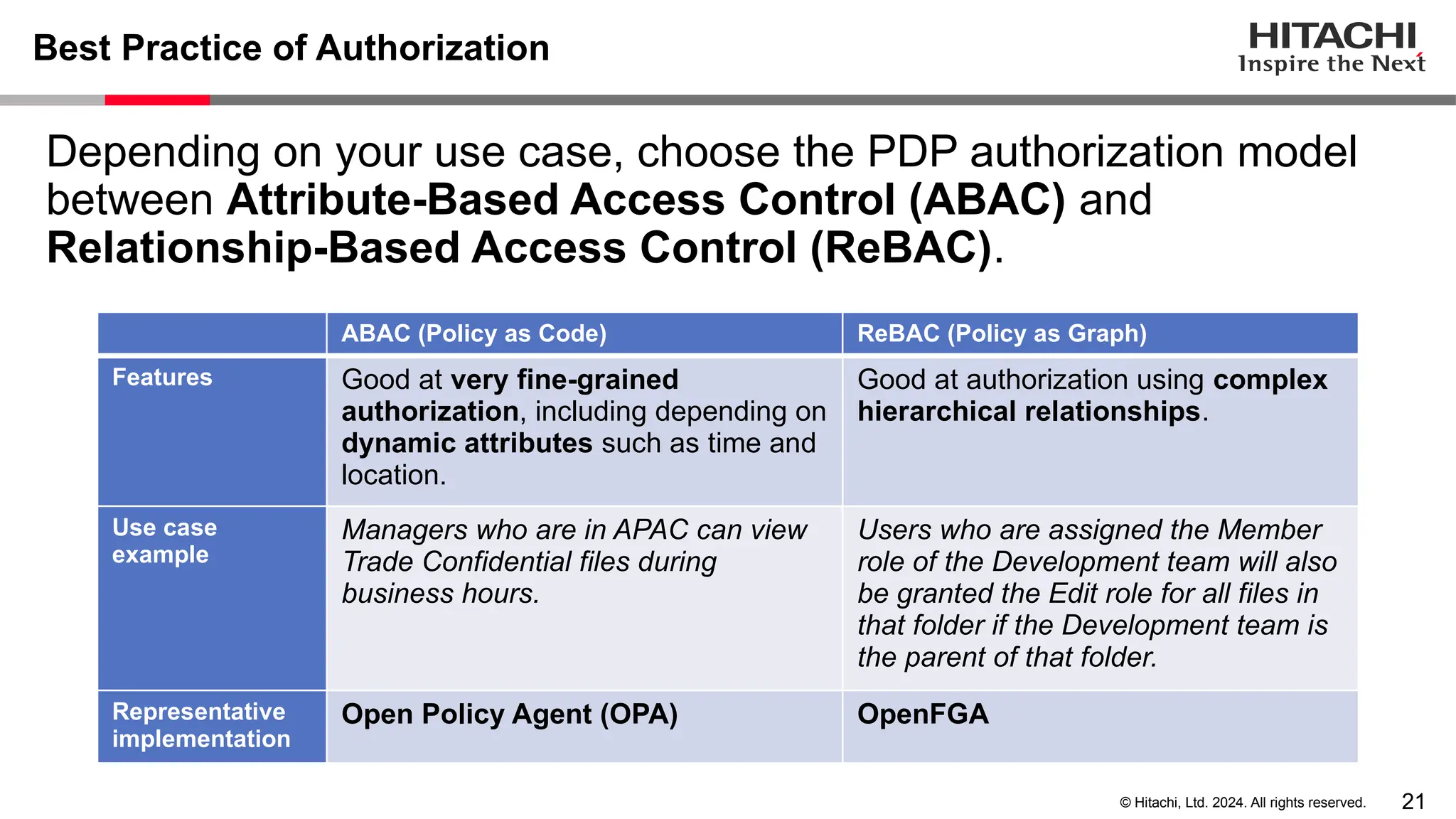
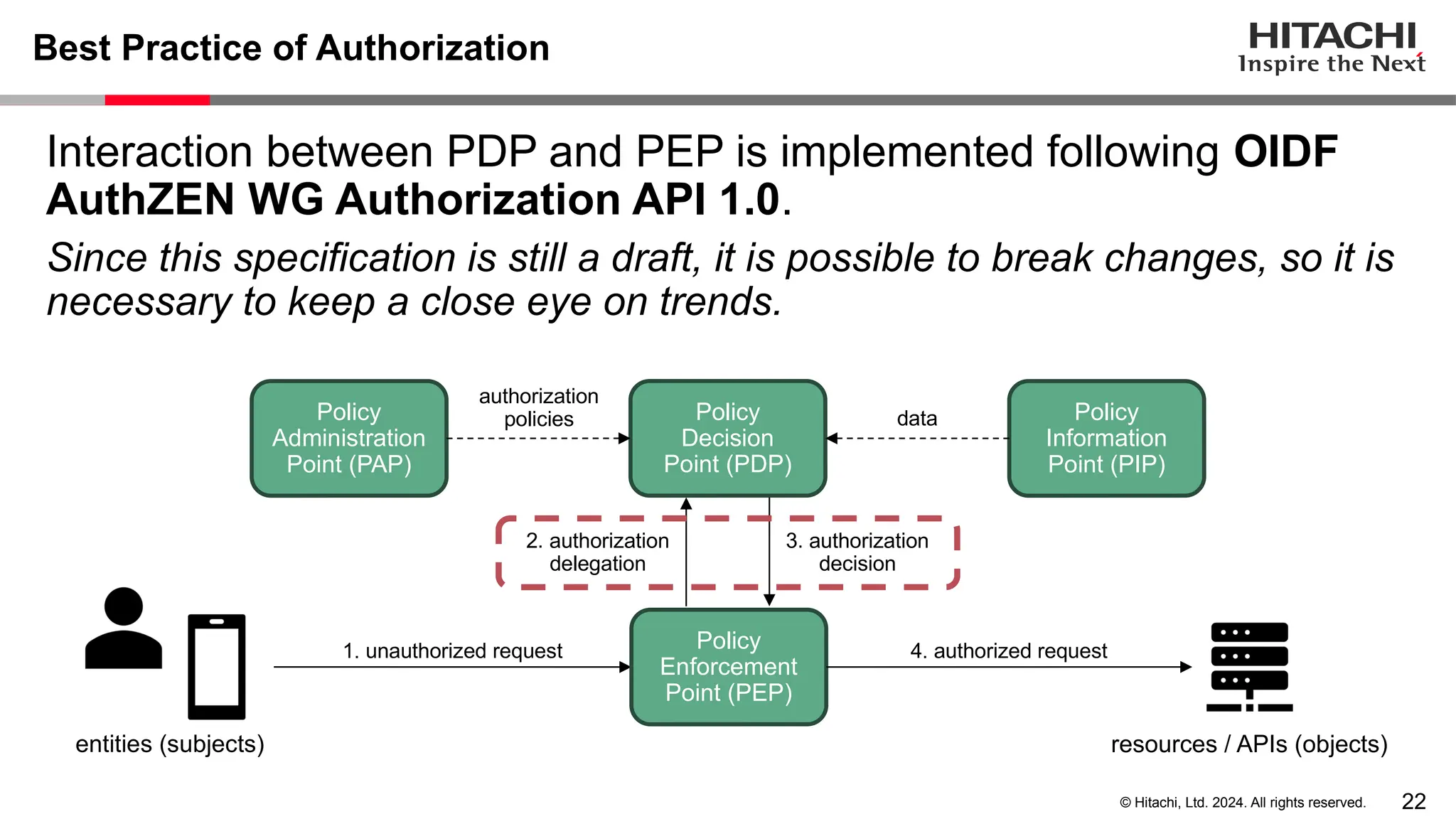
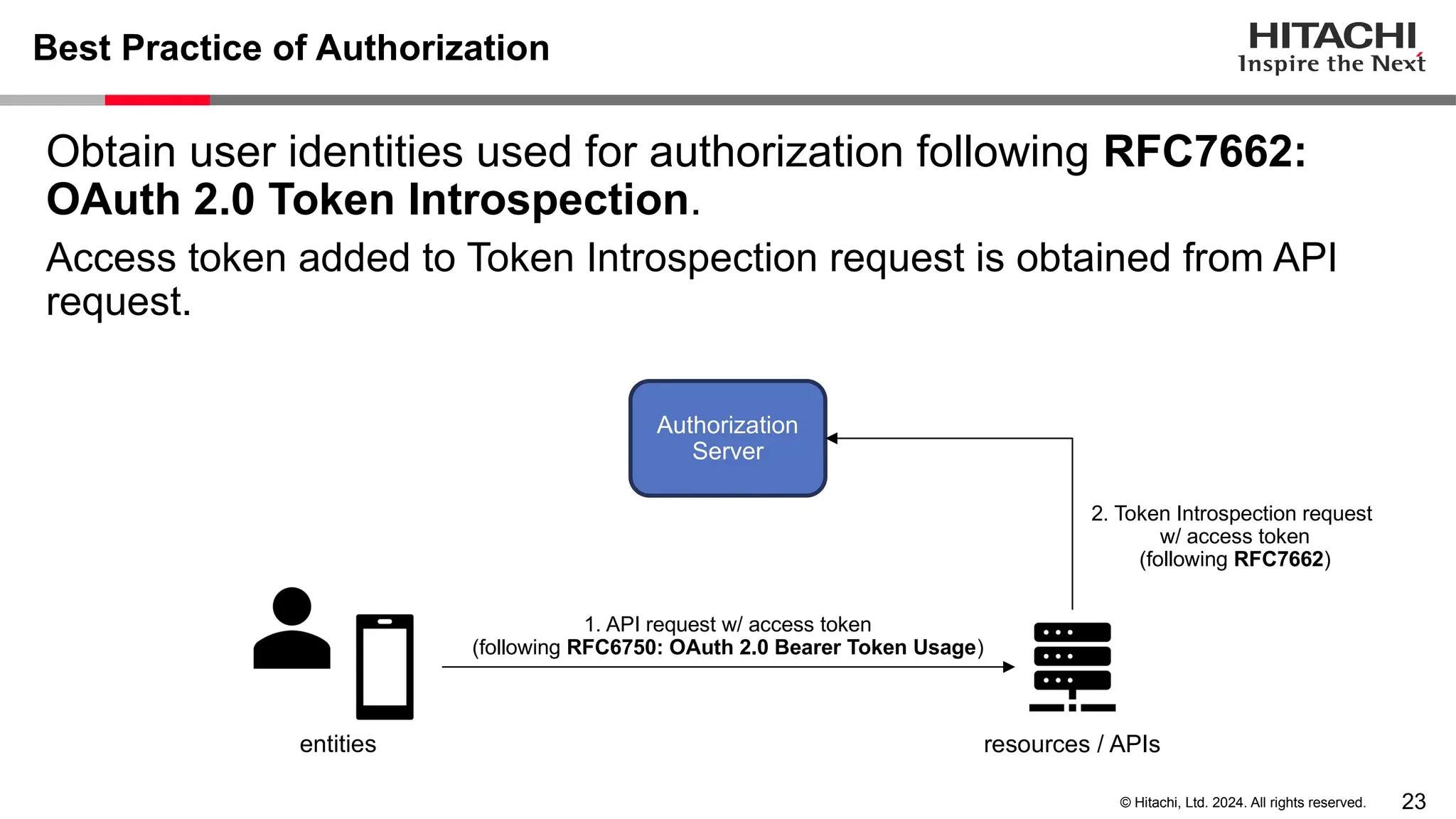
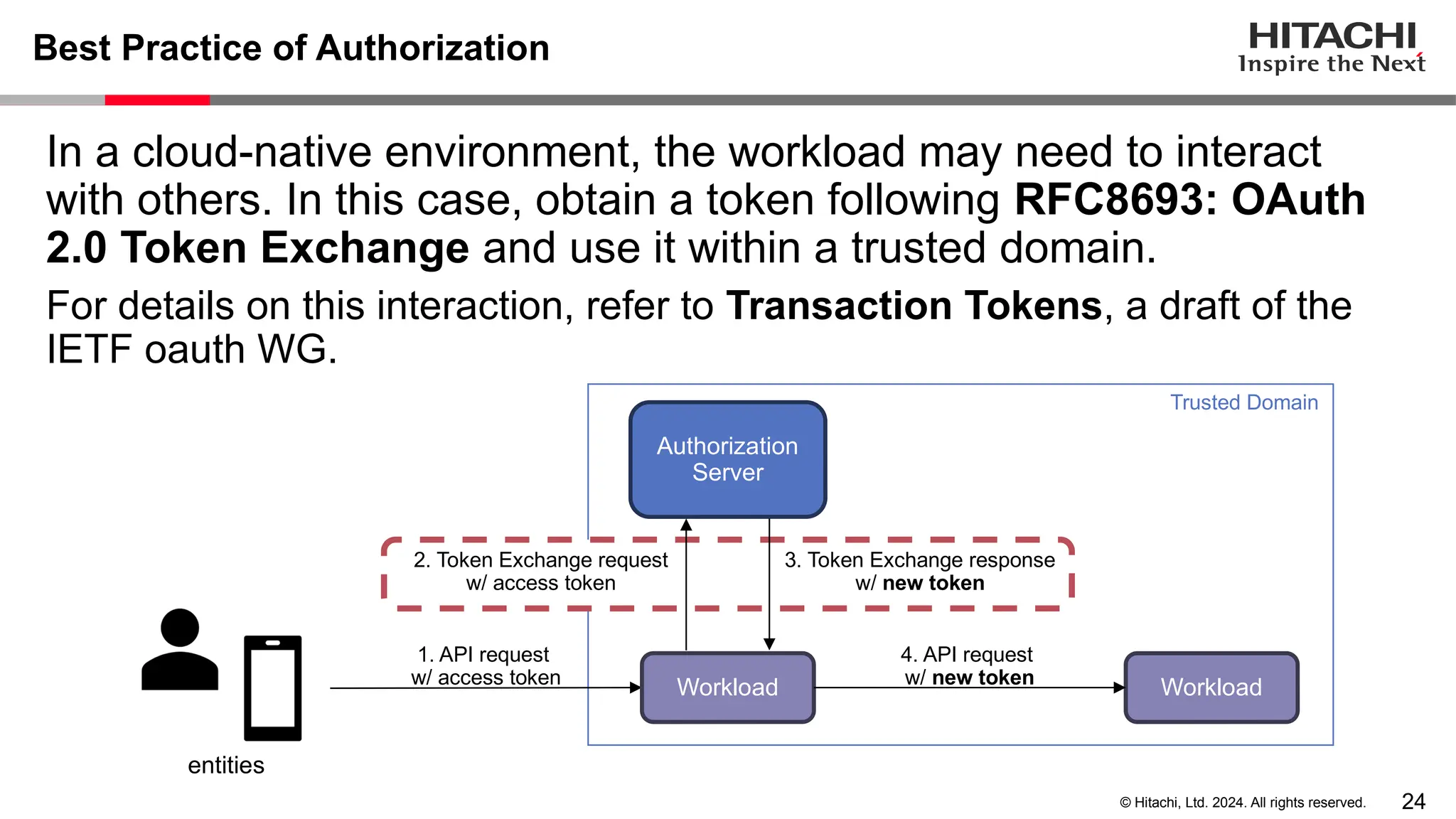
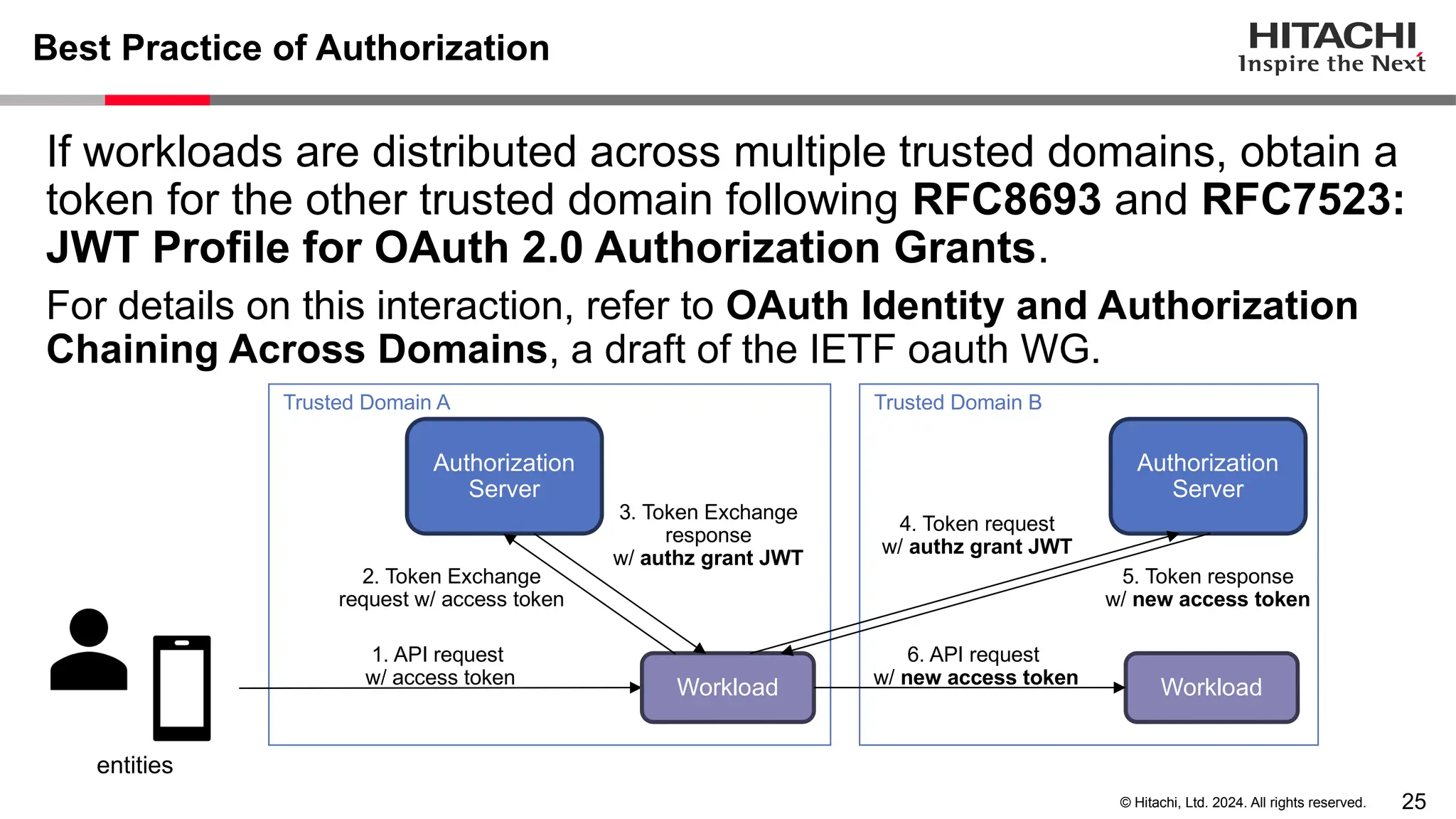
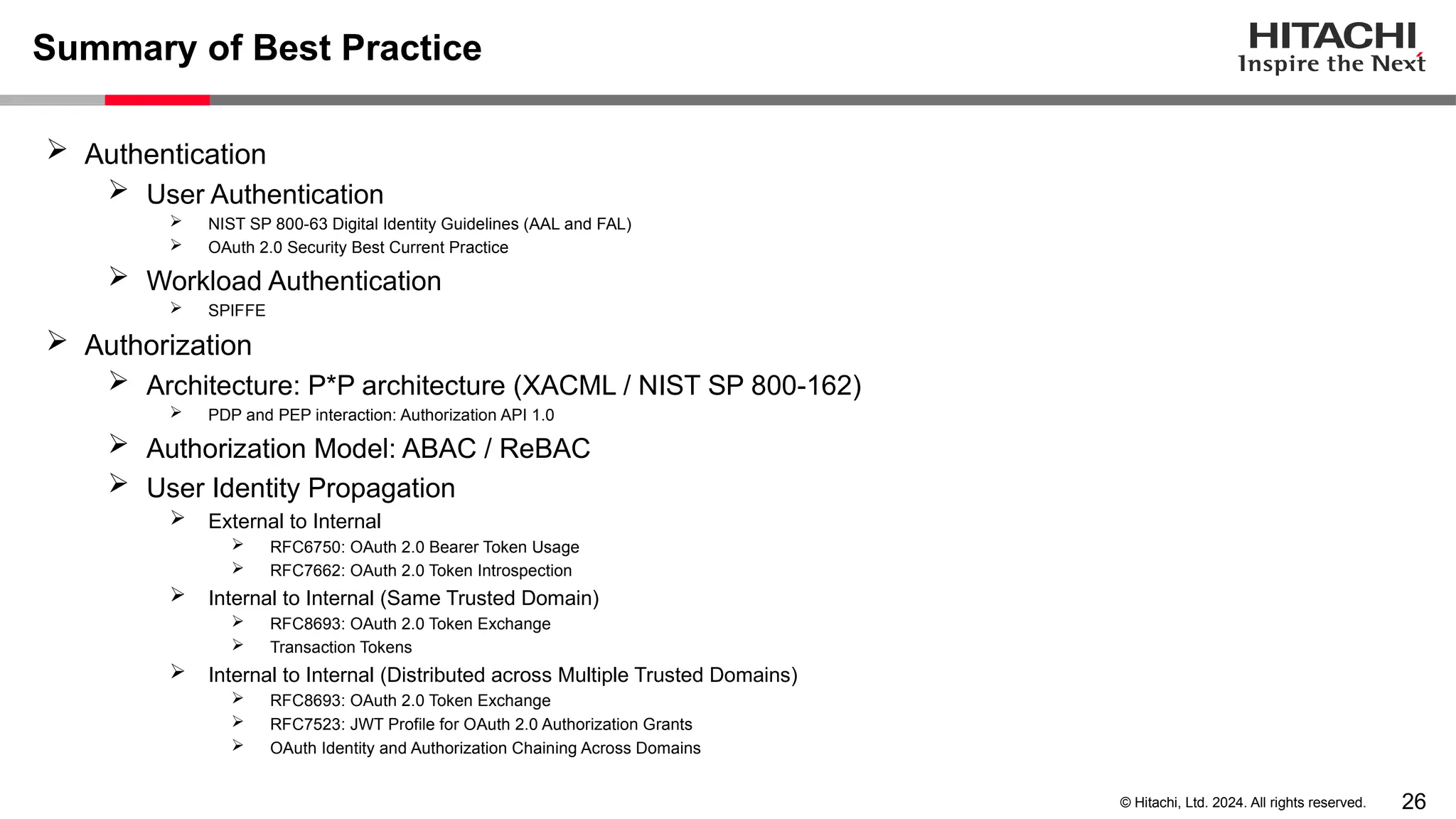
The document discusses best practices for implementing authentication (authn) and authorization (authz) in cloud-native environments, emphasizing their importance and current trends. It outlines security risks related to authn/authz as per OWASP, standards for user and workload authentication, and various authorization models like attribute-based and relationship-based access control. Additionally, it provides recommendations based on NIST guidelines and mentions ongoing projects related to identity and access management.