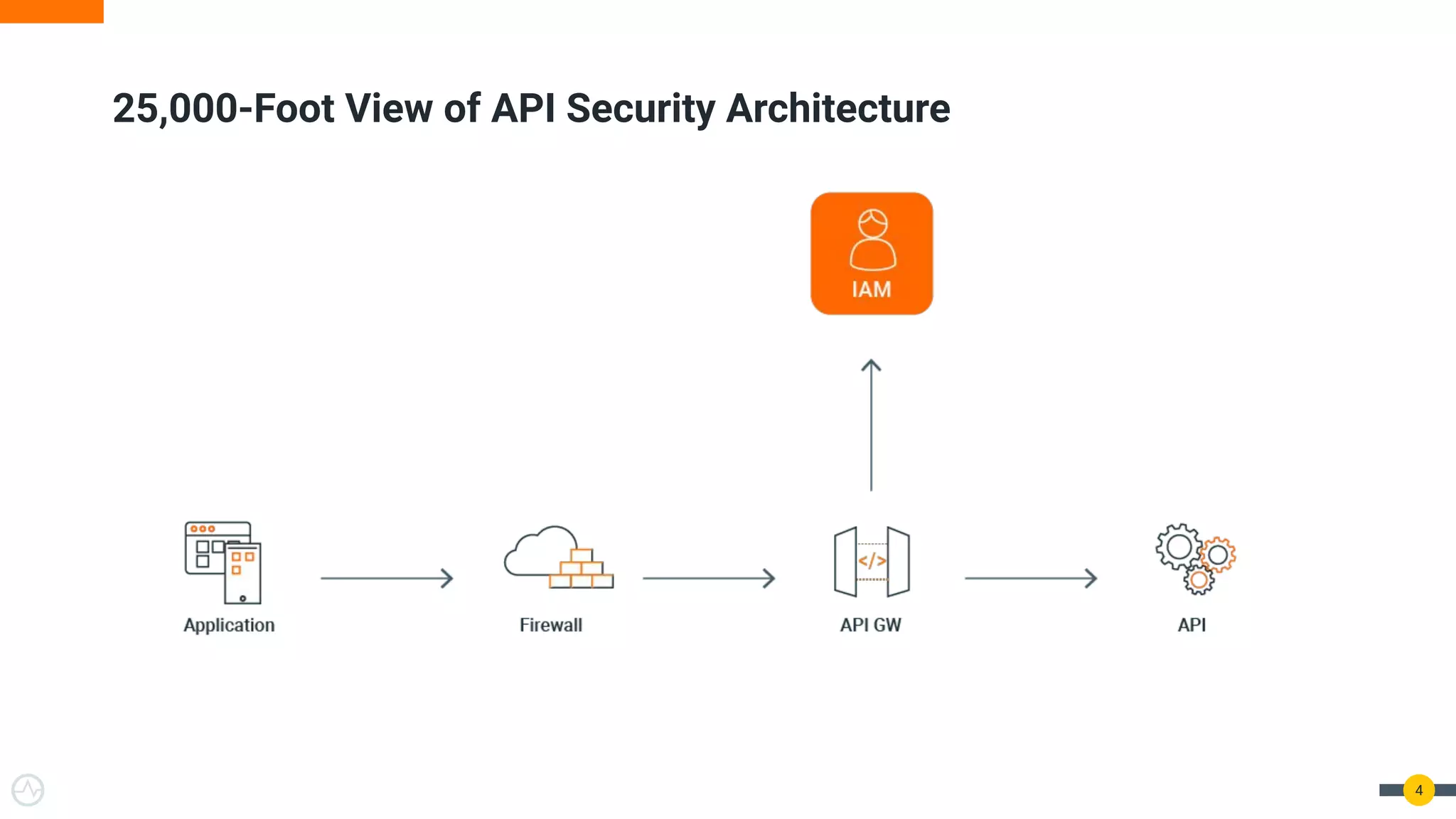
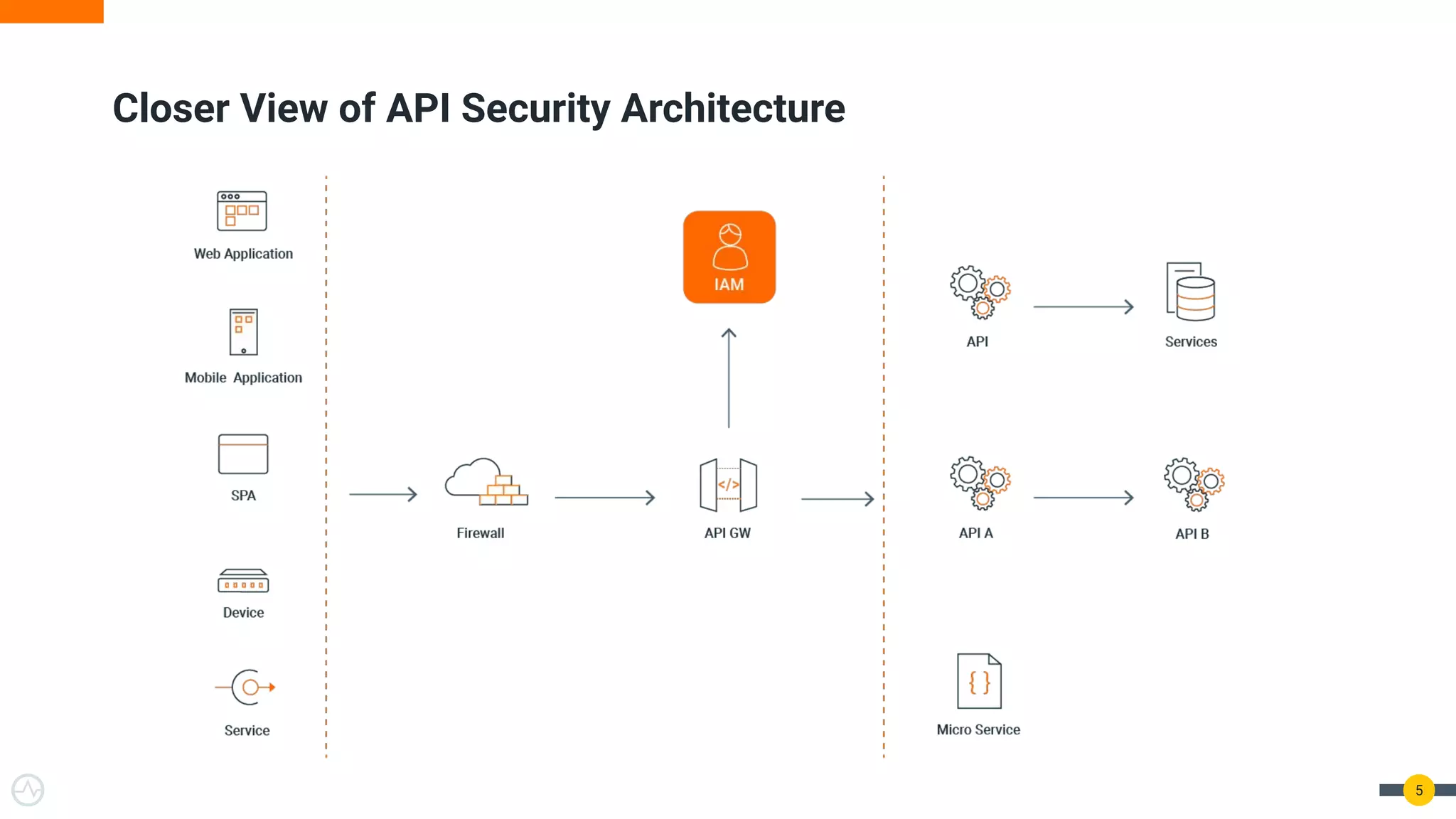
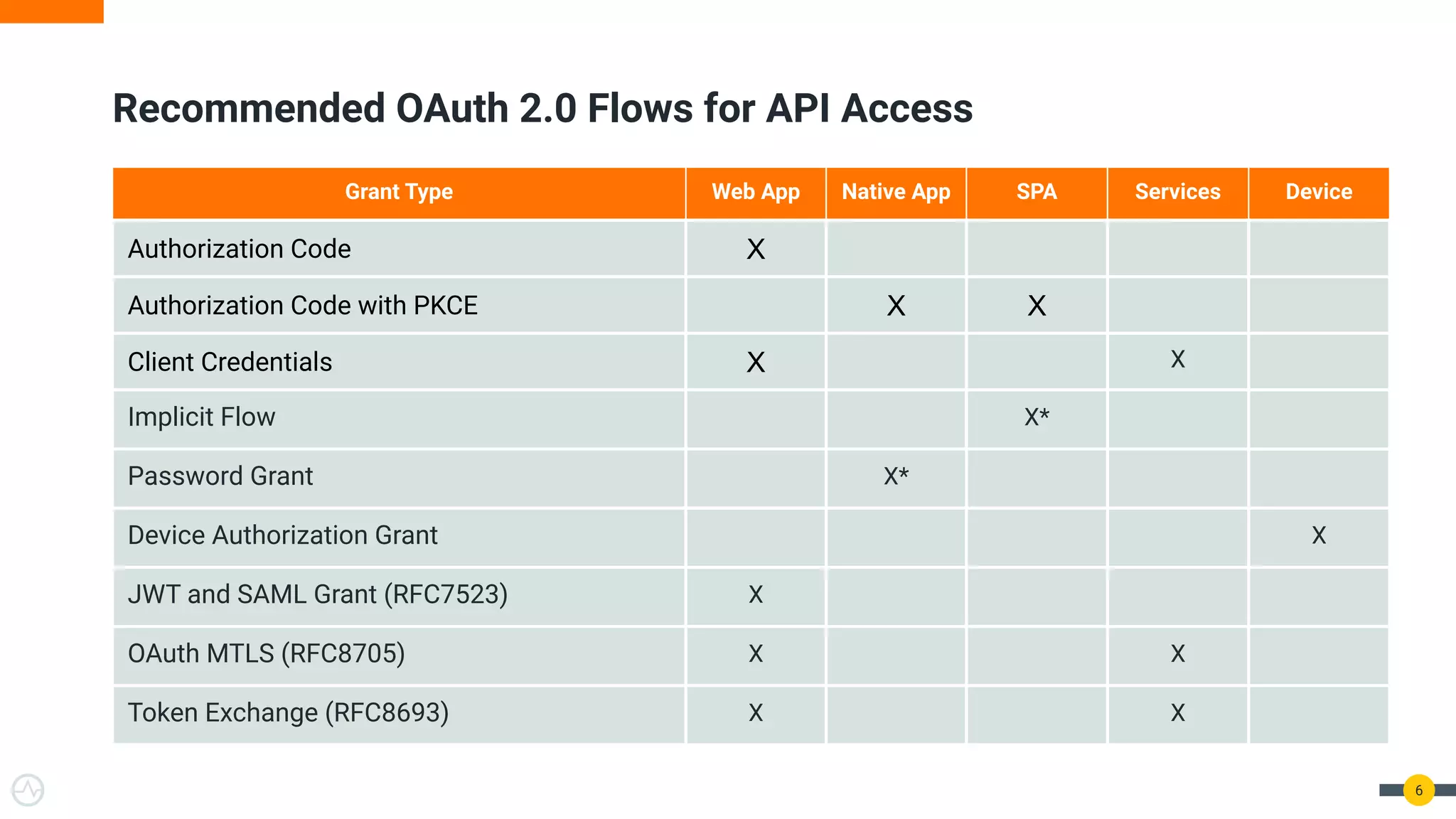
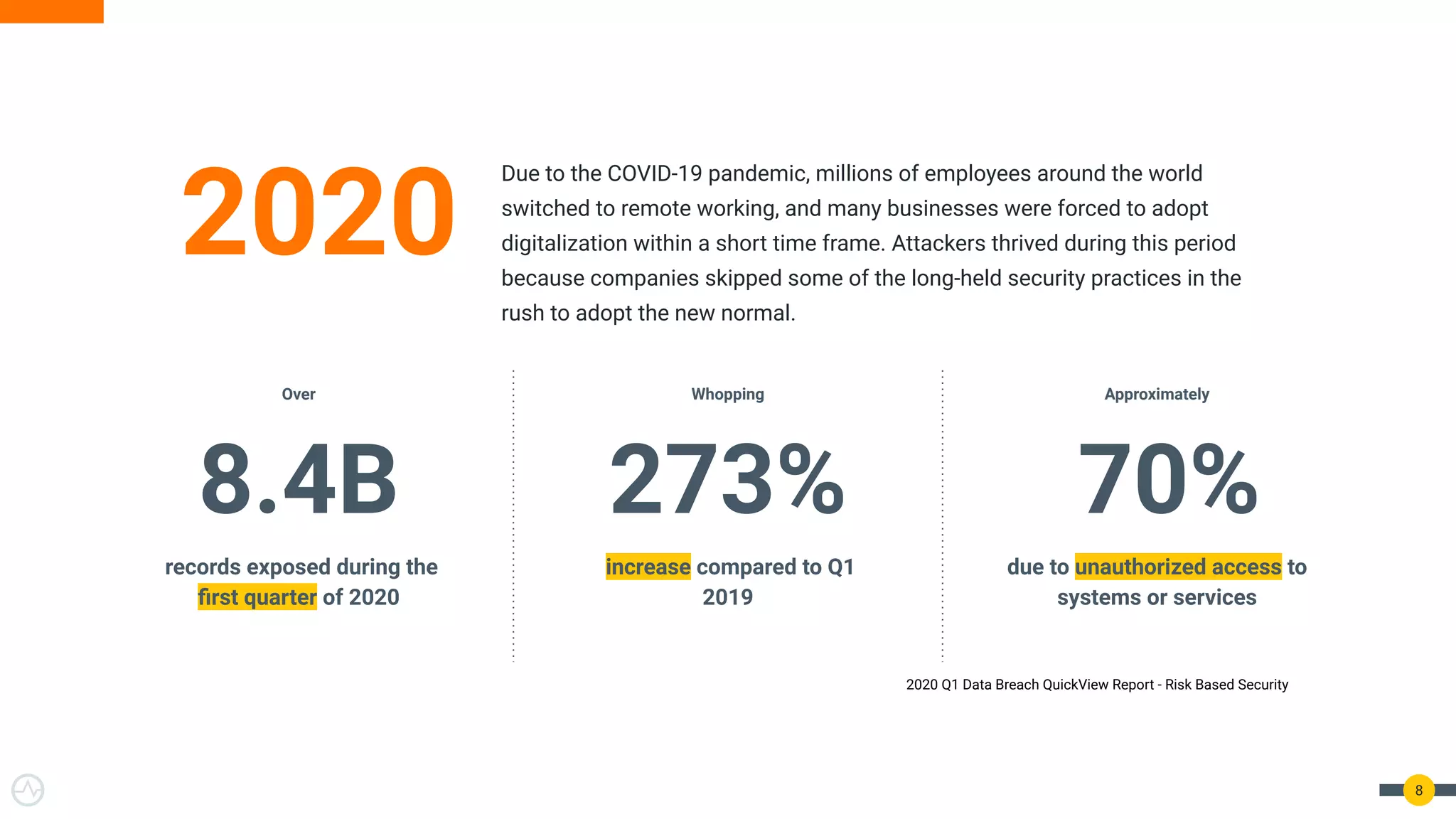
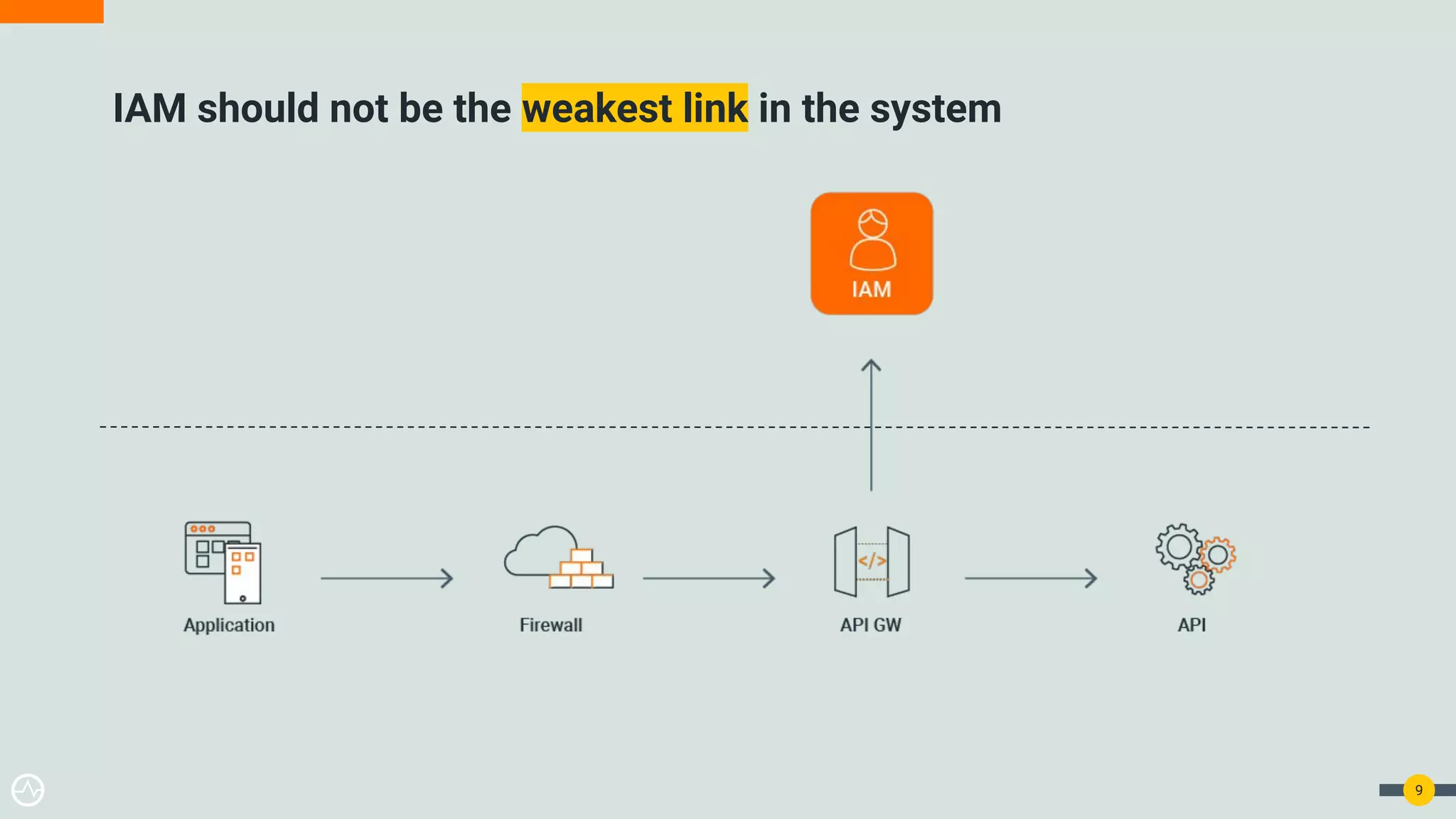
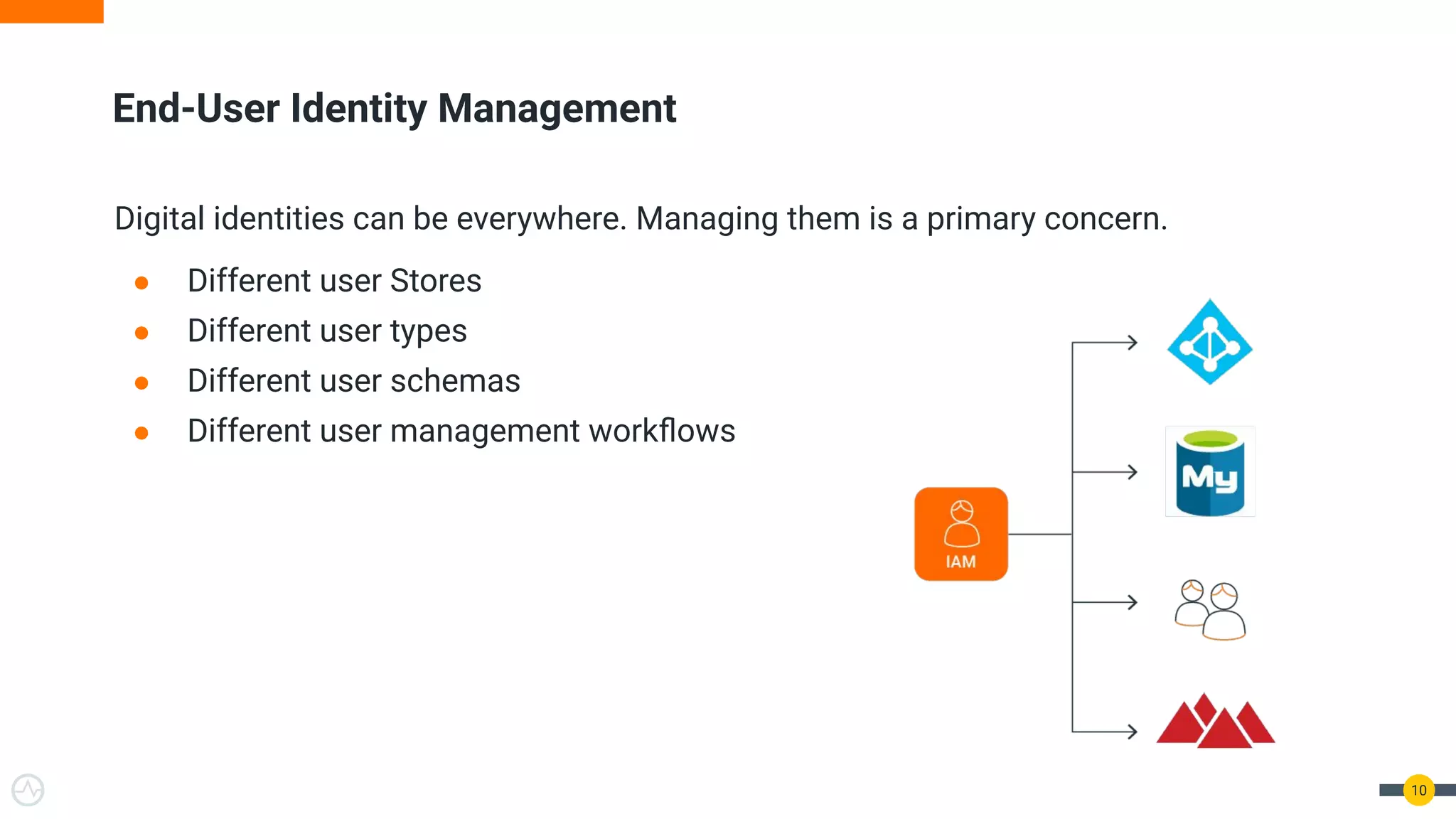
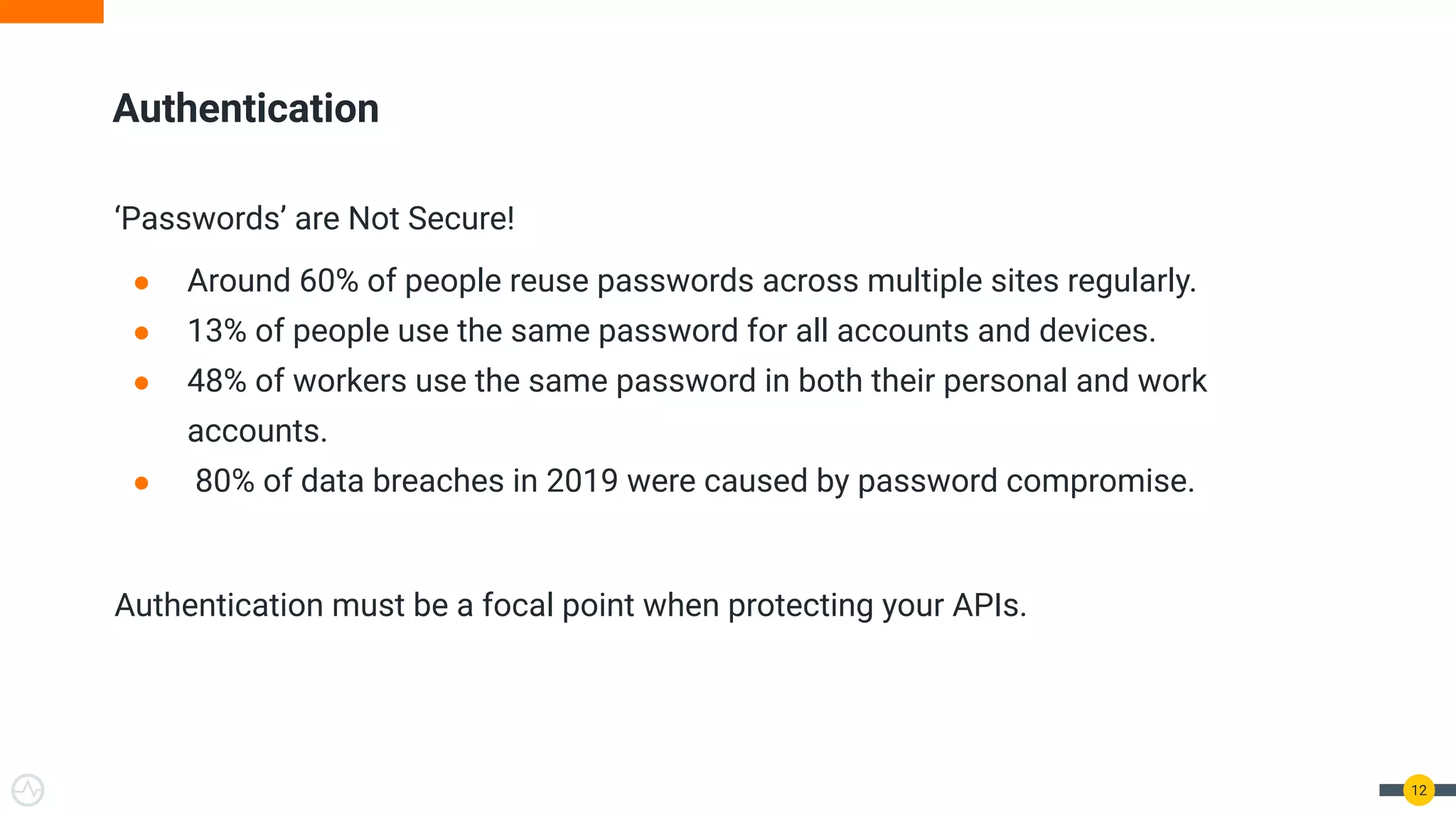
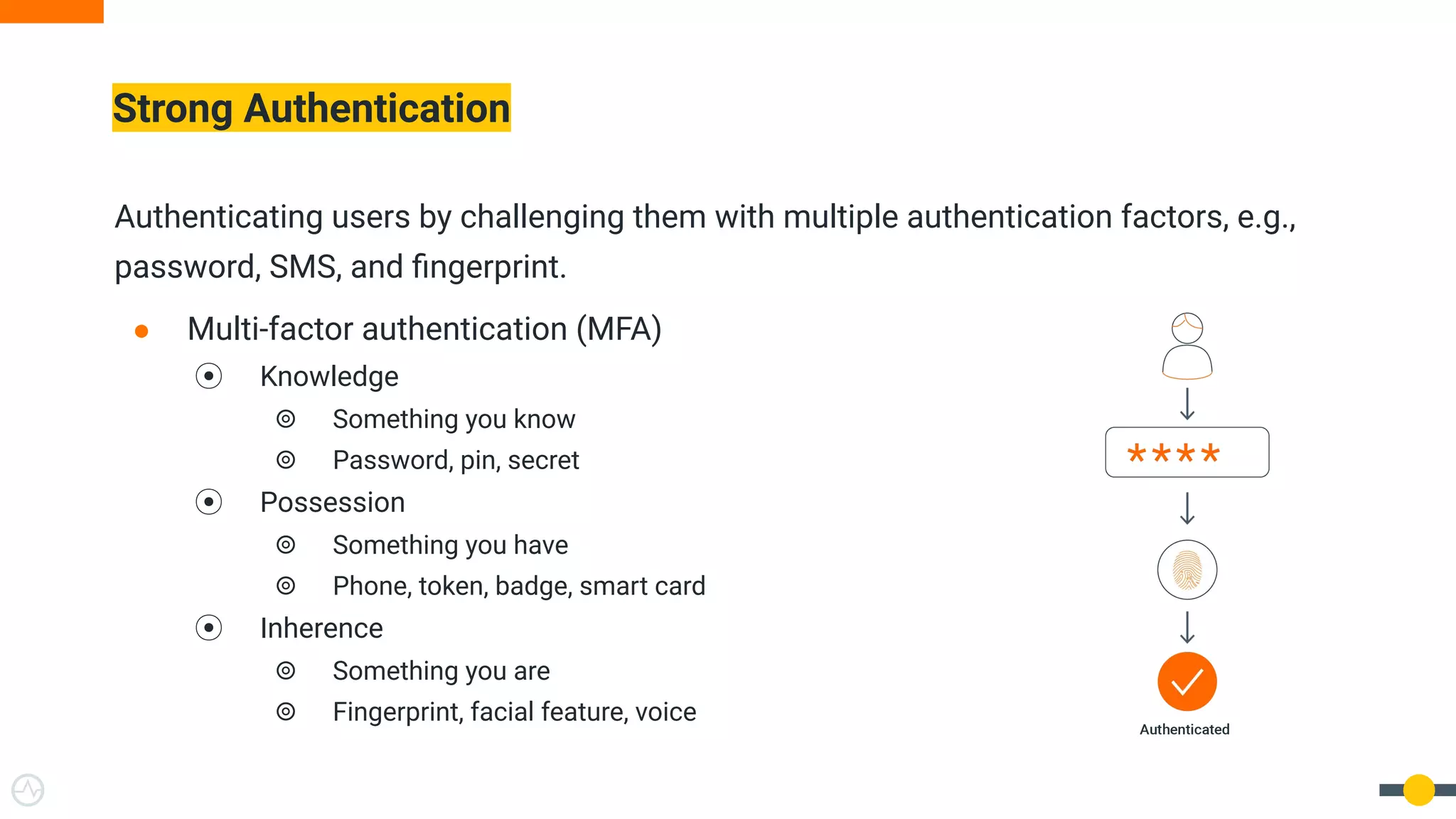
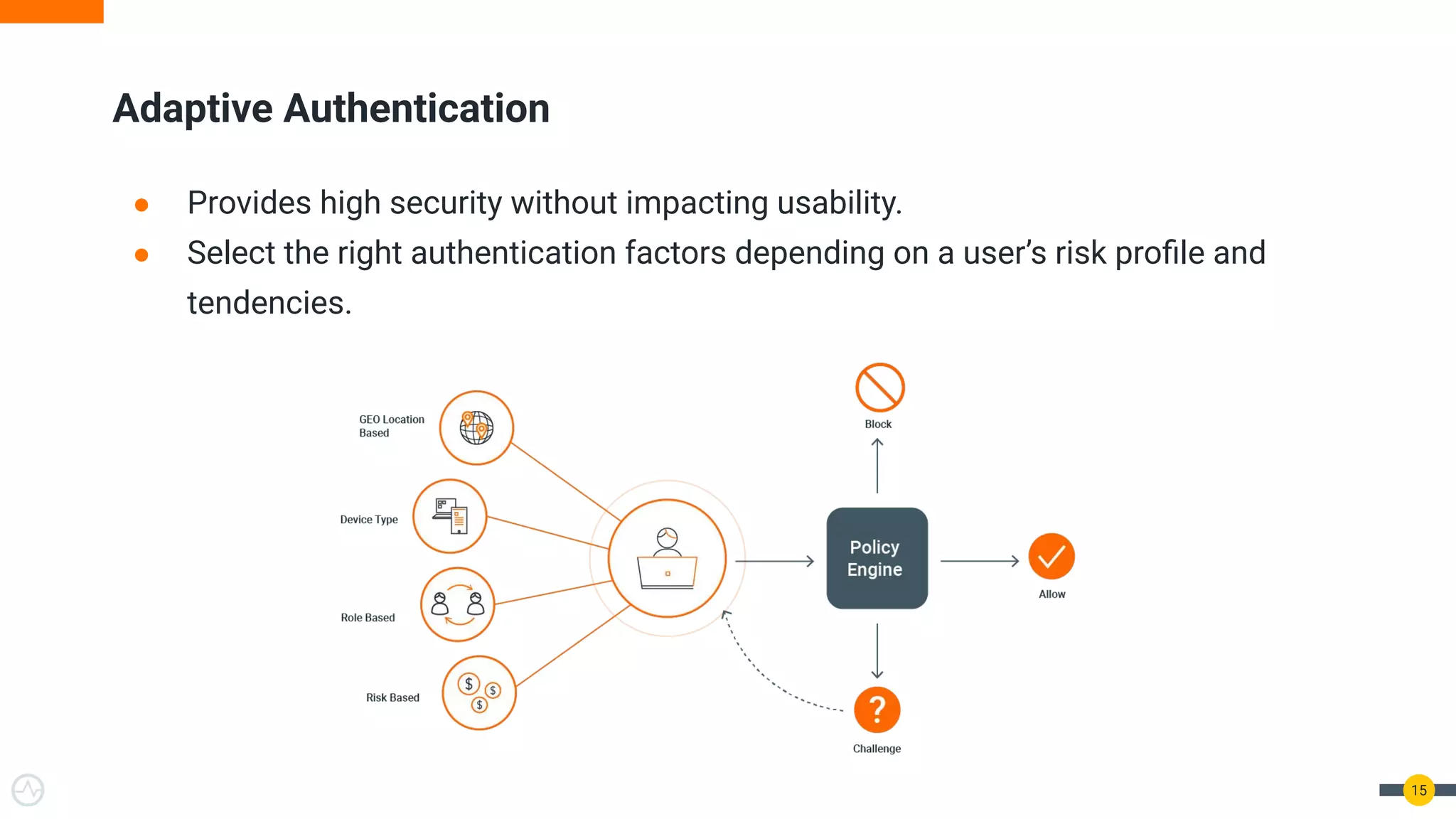
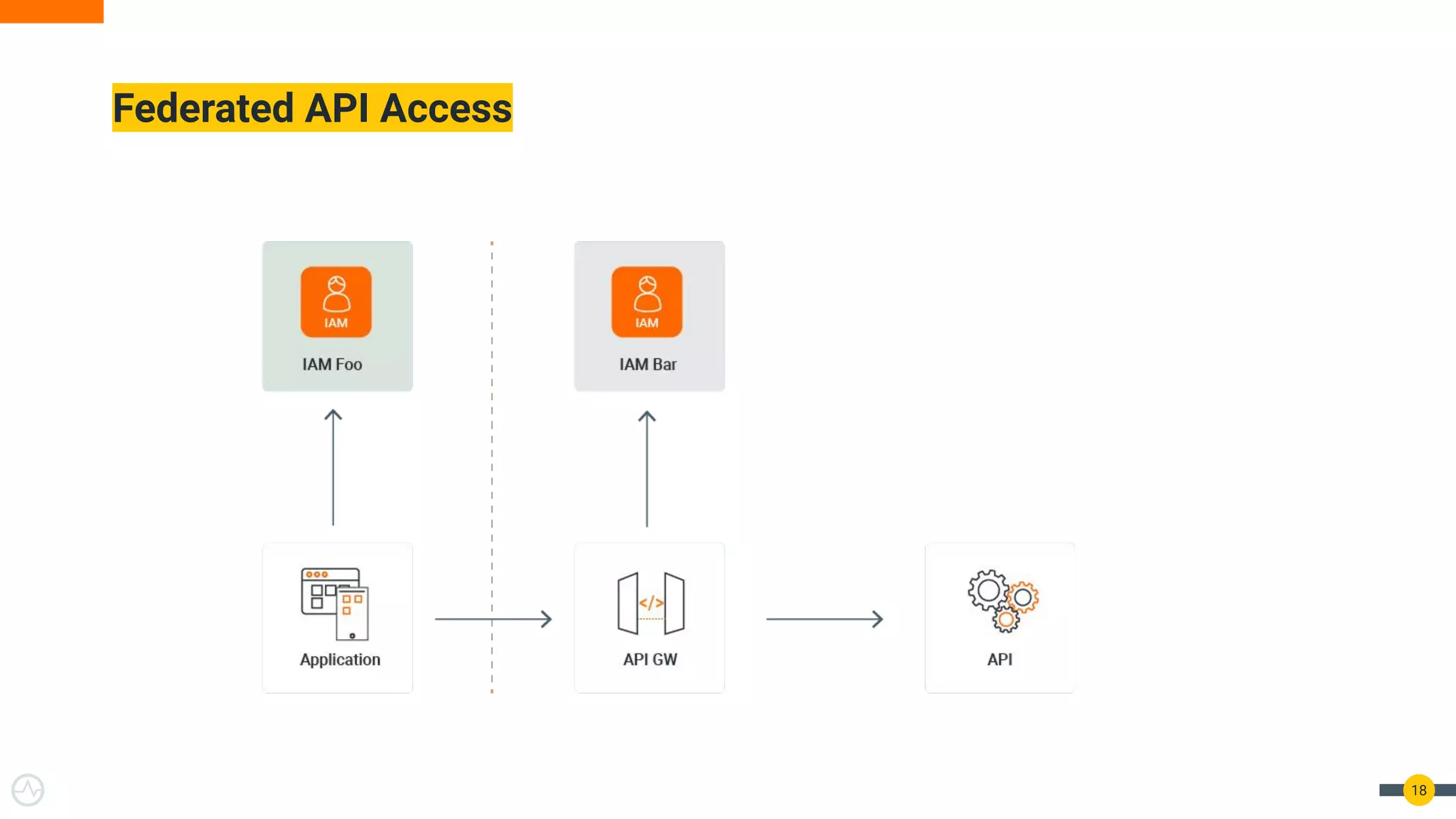
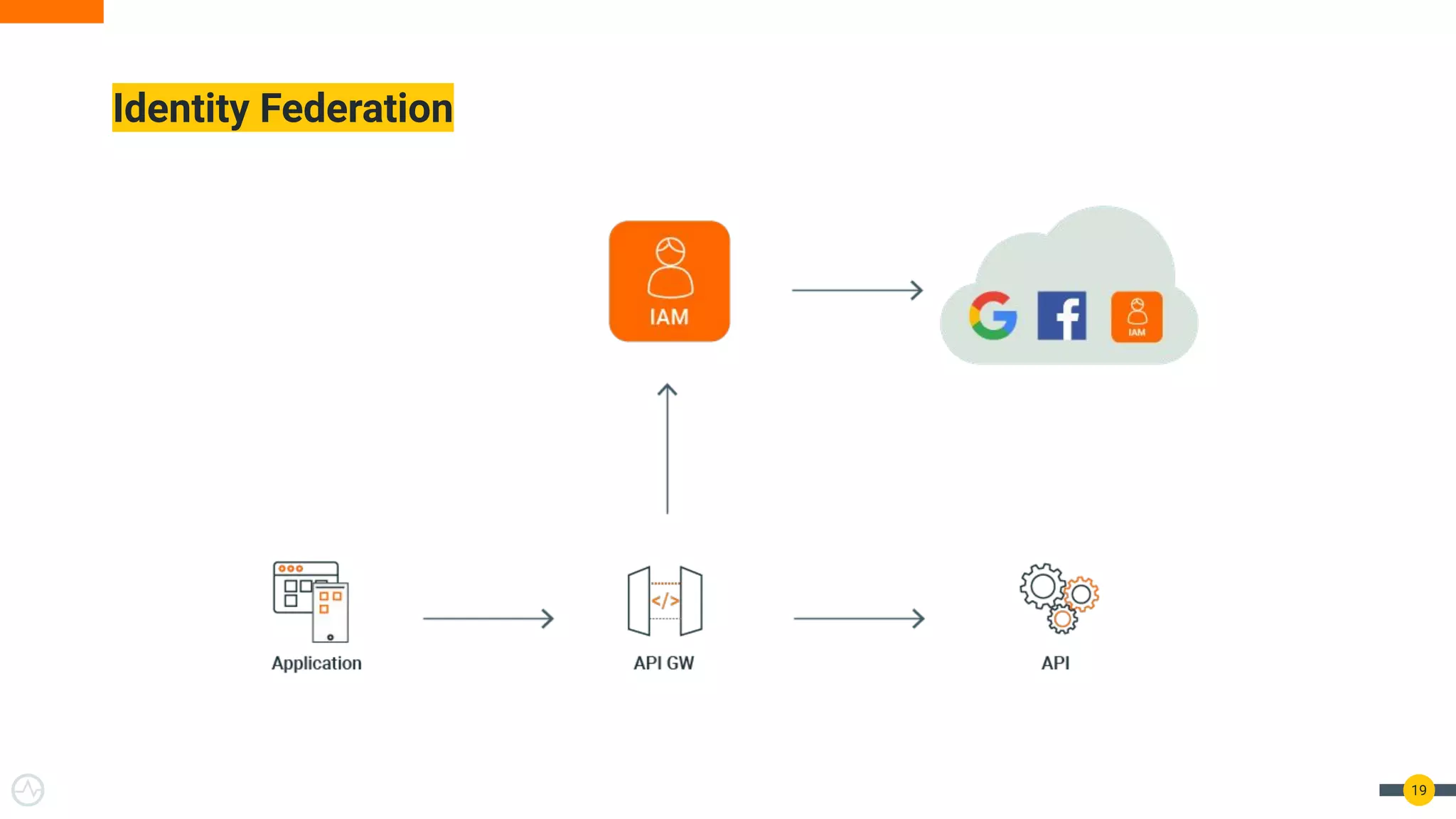
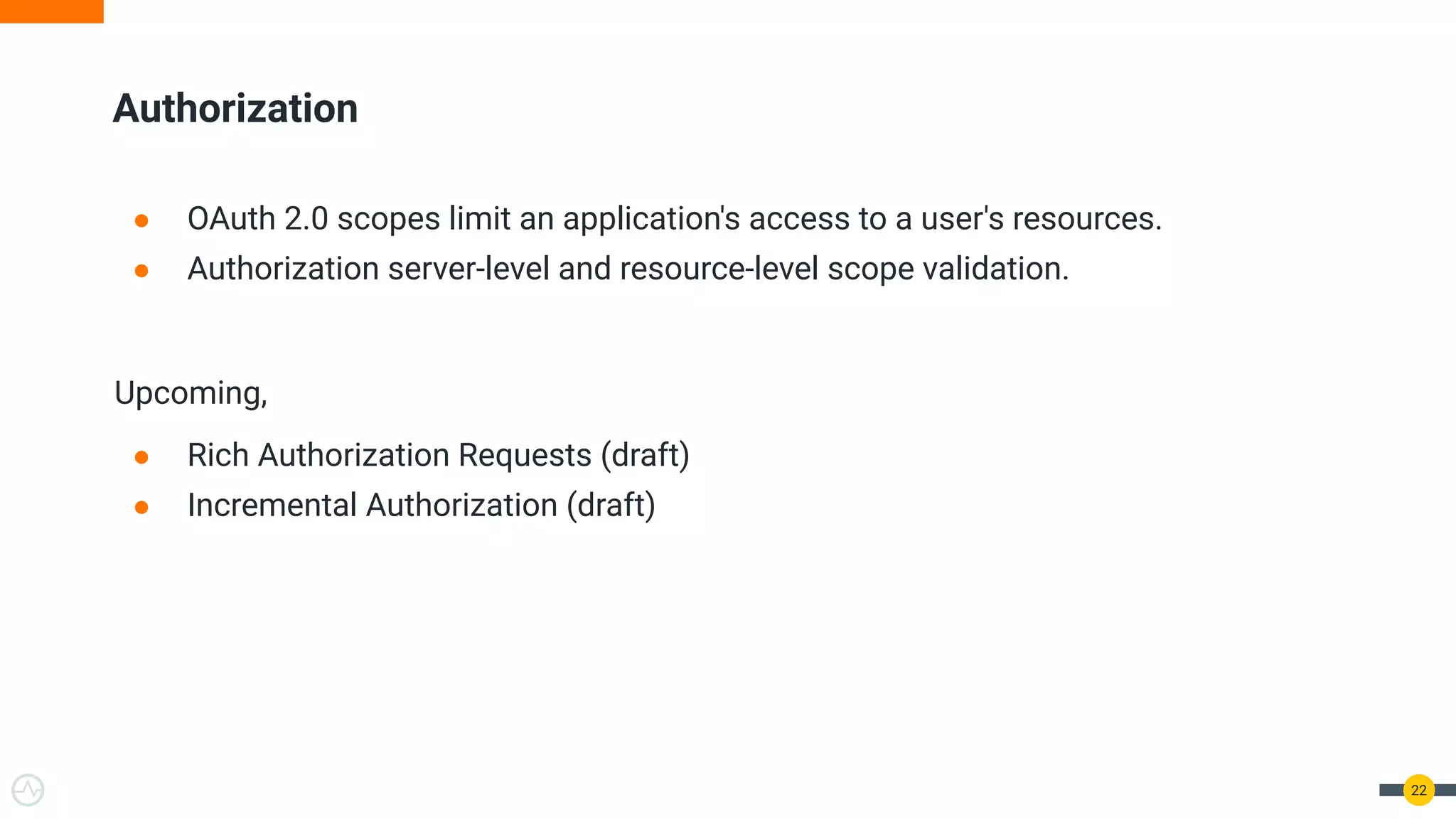
The document outlines best practices for API authentication and authorization in 2021, emphasizing the need for strong security measures due to a significant increase in data breaches. It covers the importance of protecting APIs using OAuth 2.0 flows, multi-factor authentication, and dynamic authentication methods to enhance user security. The document also highlights the role of authorization in limiting access to resources and implementing fine-grained access controls.