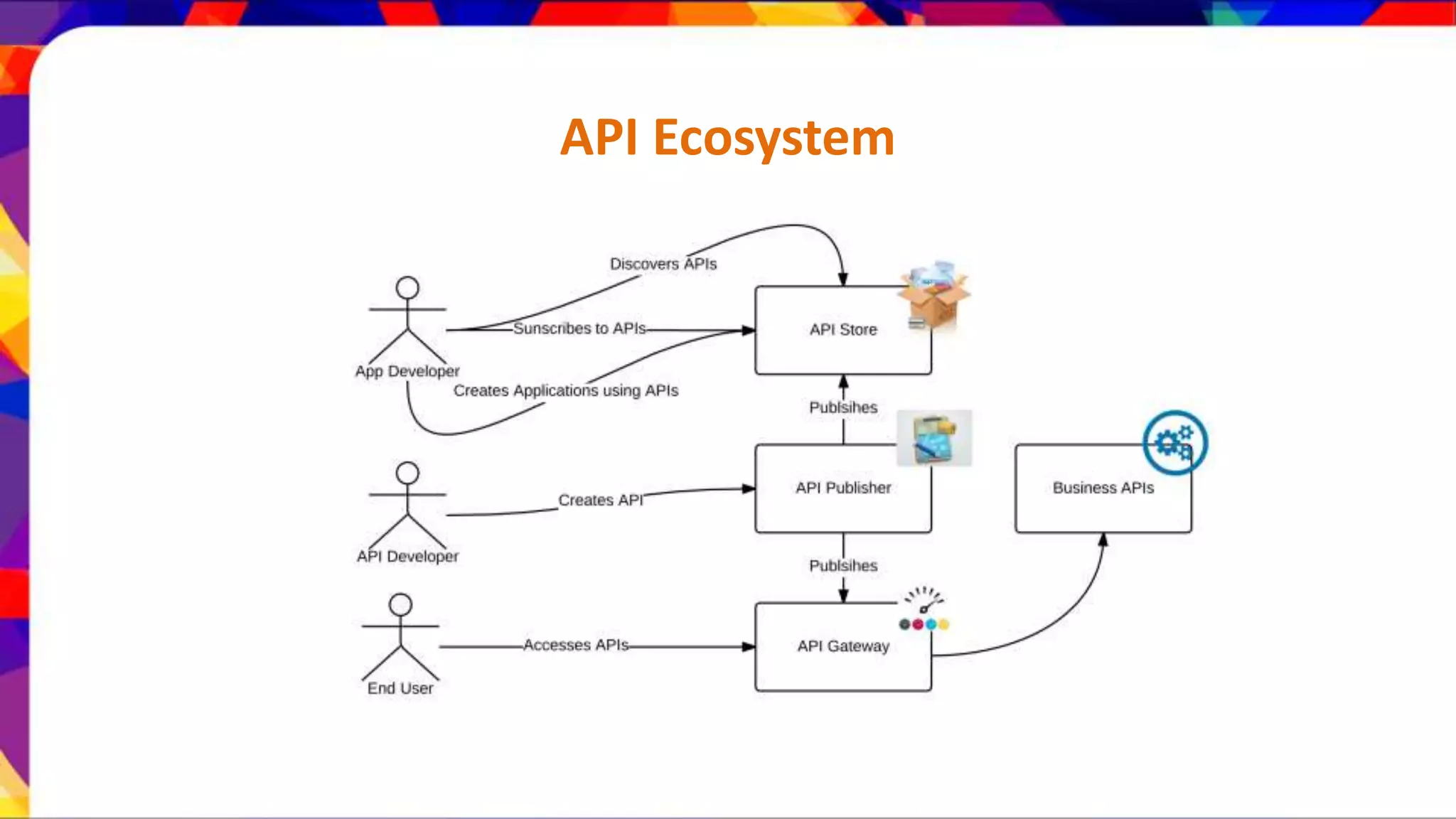
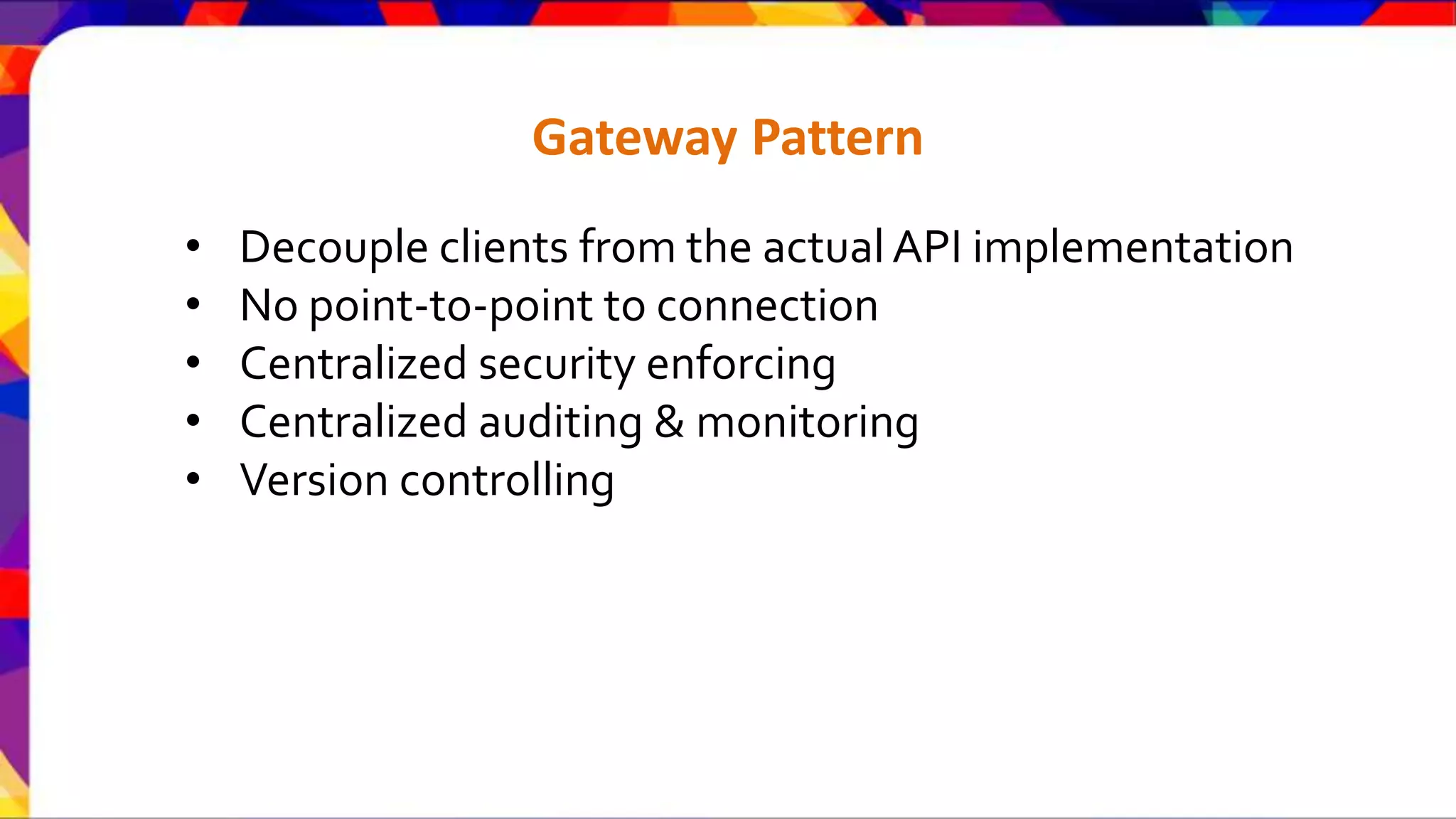
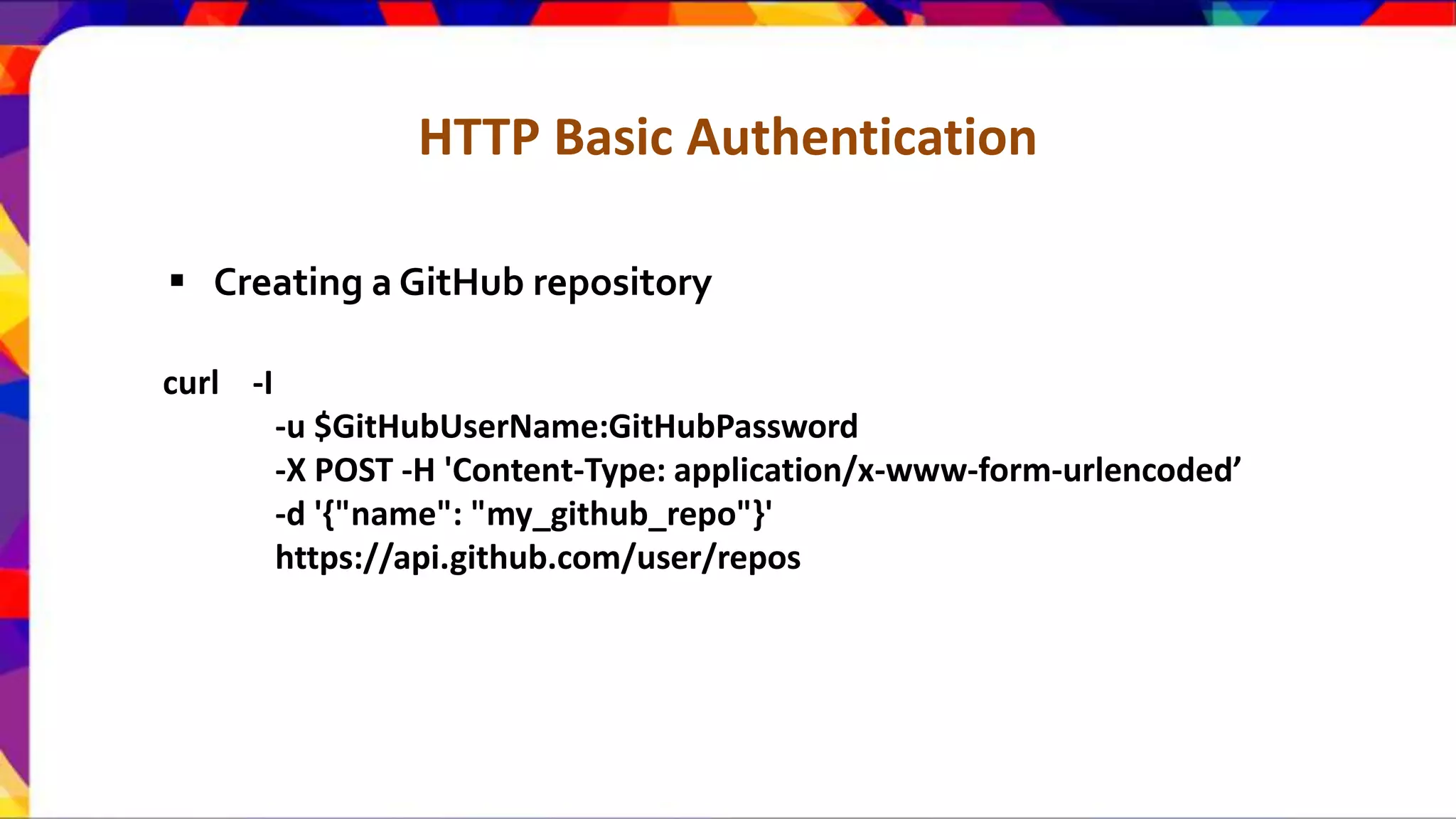
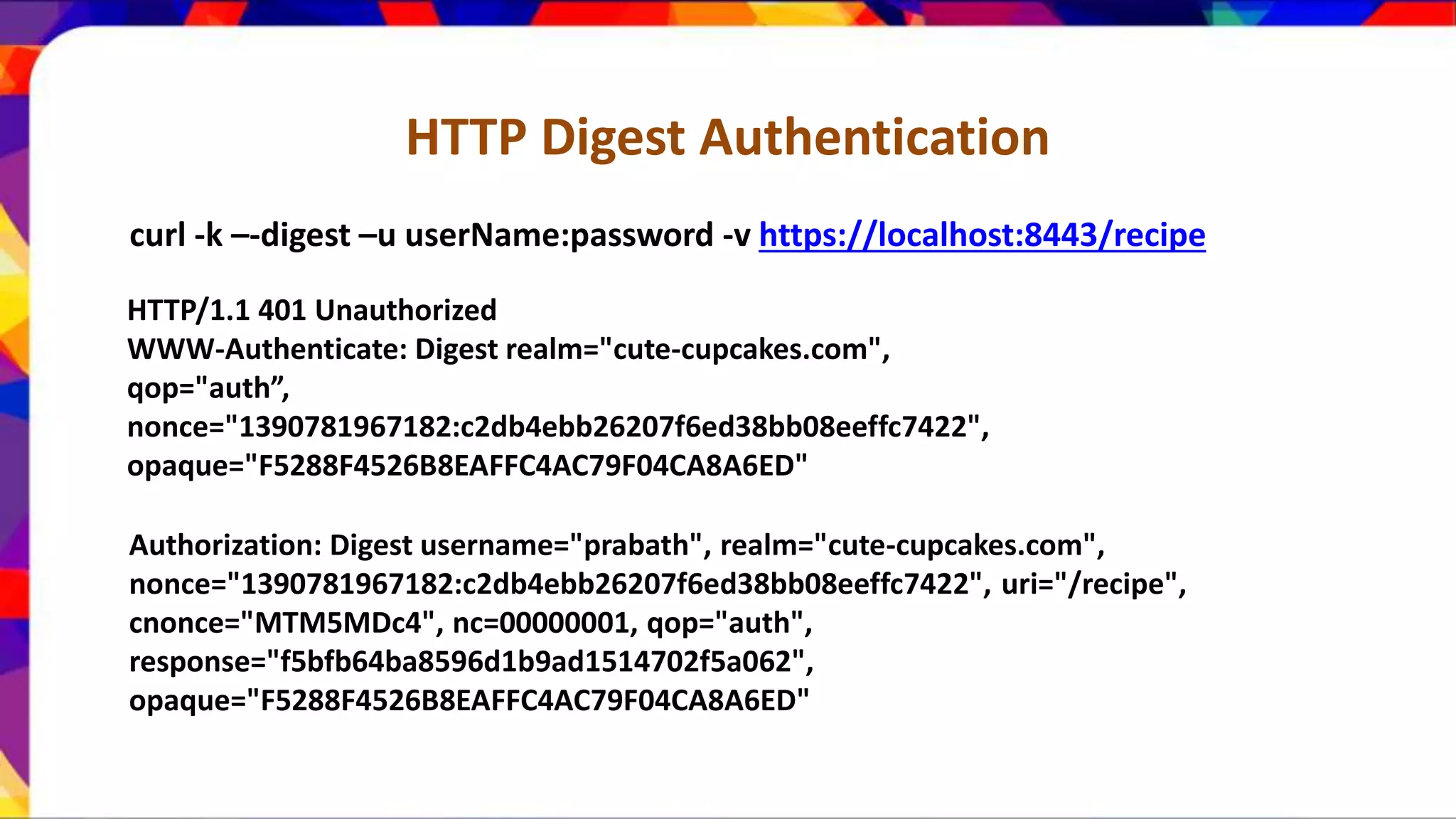
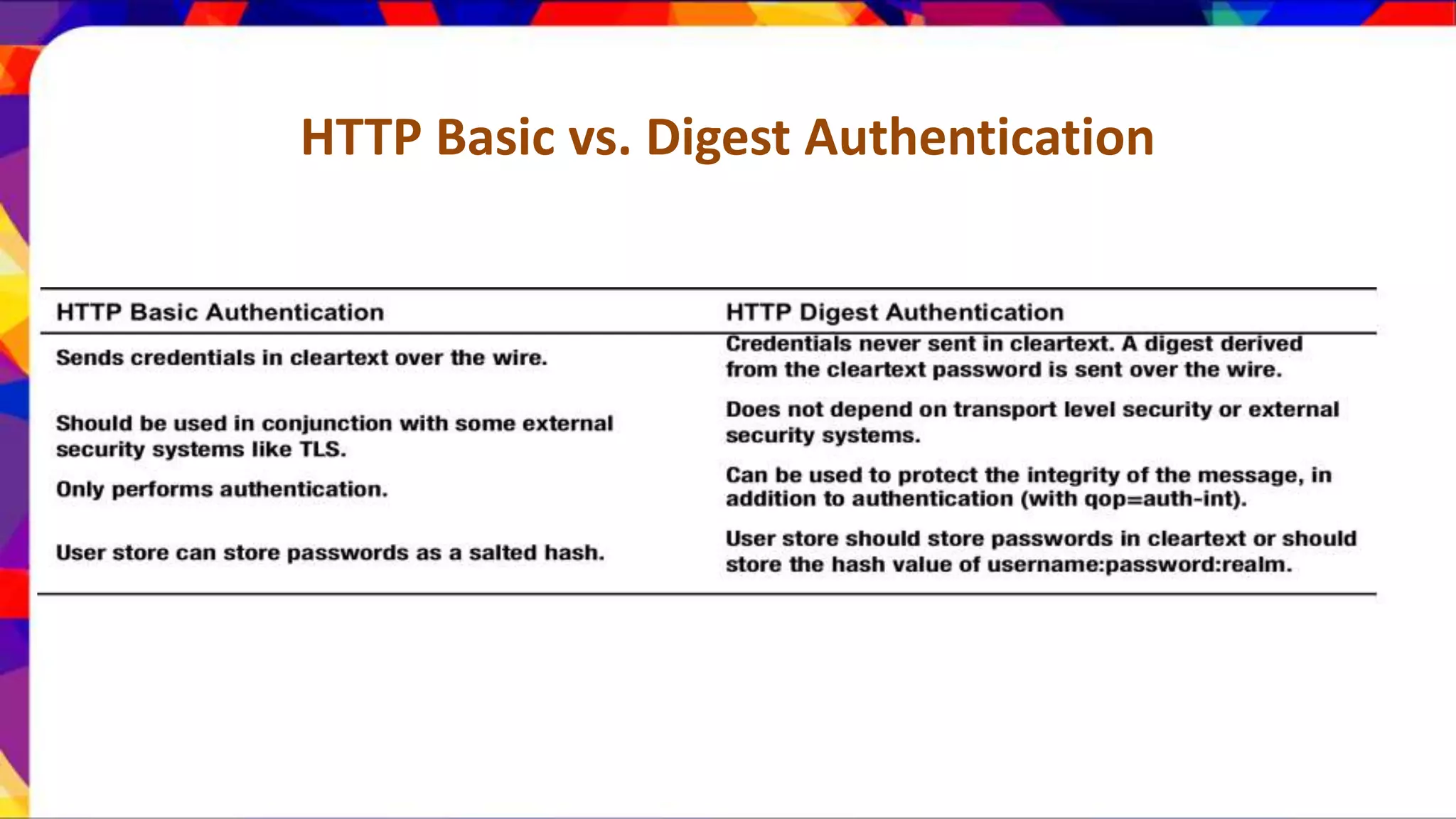
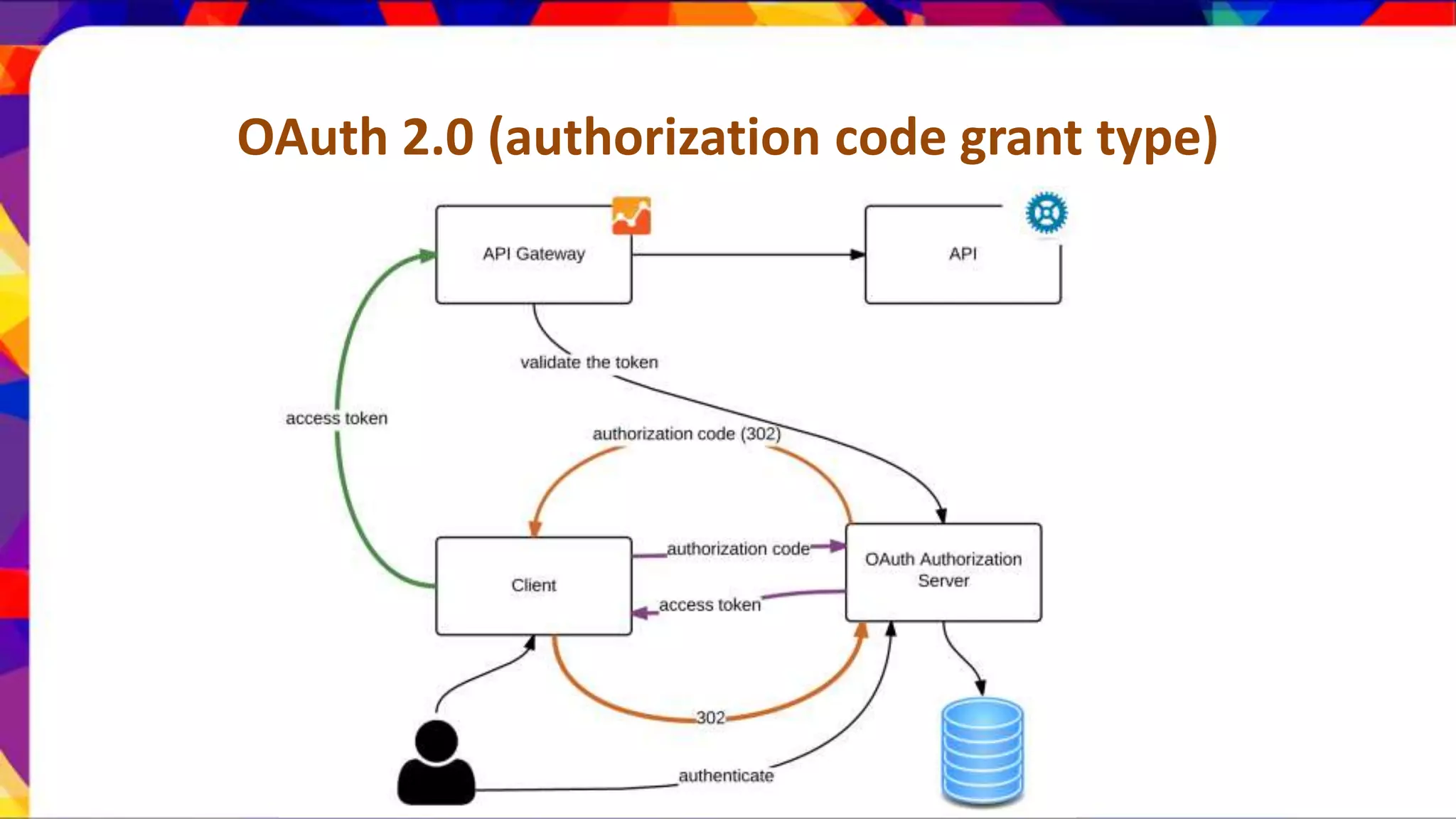
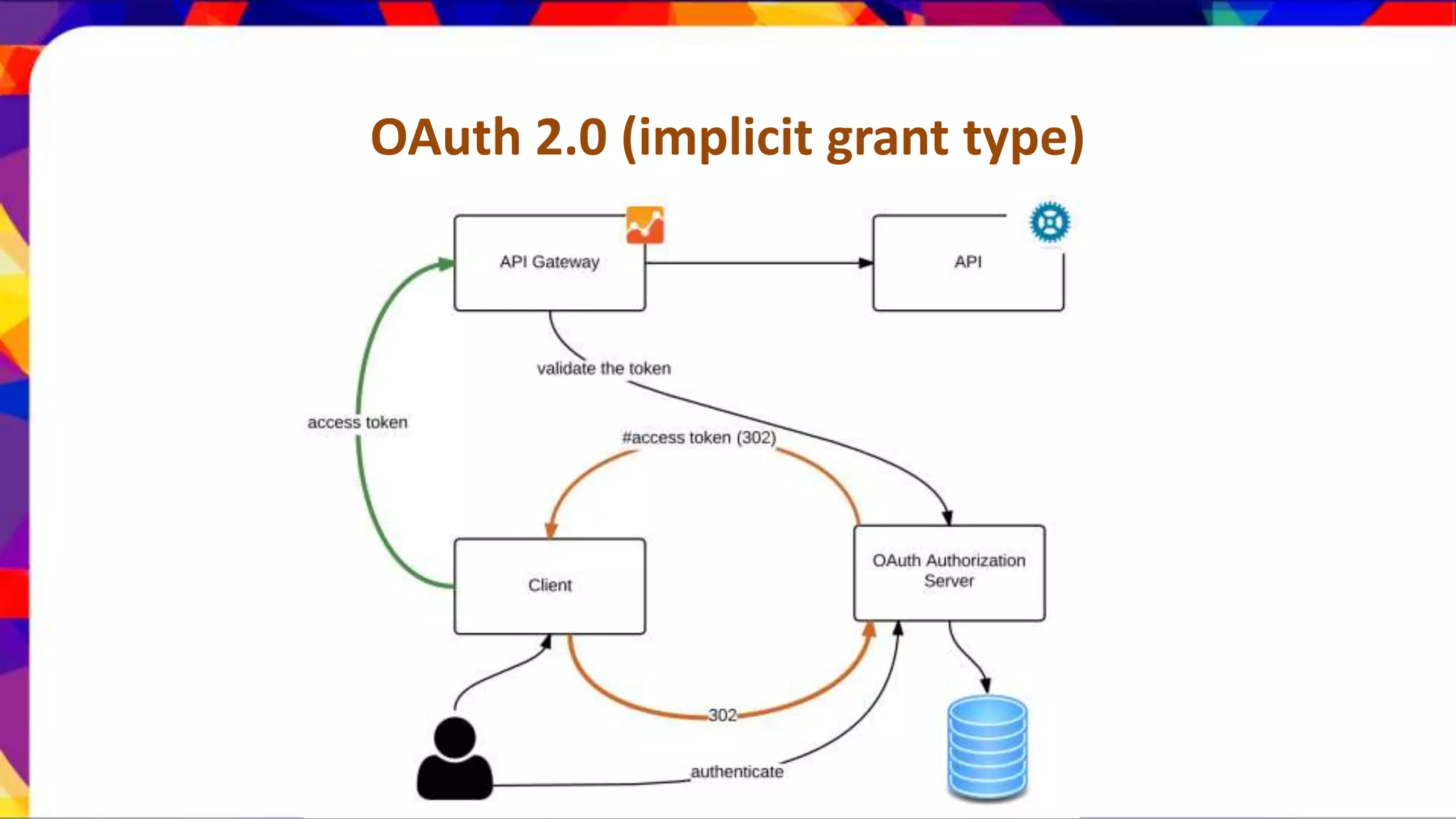
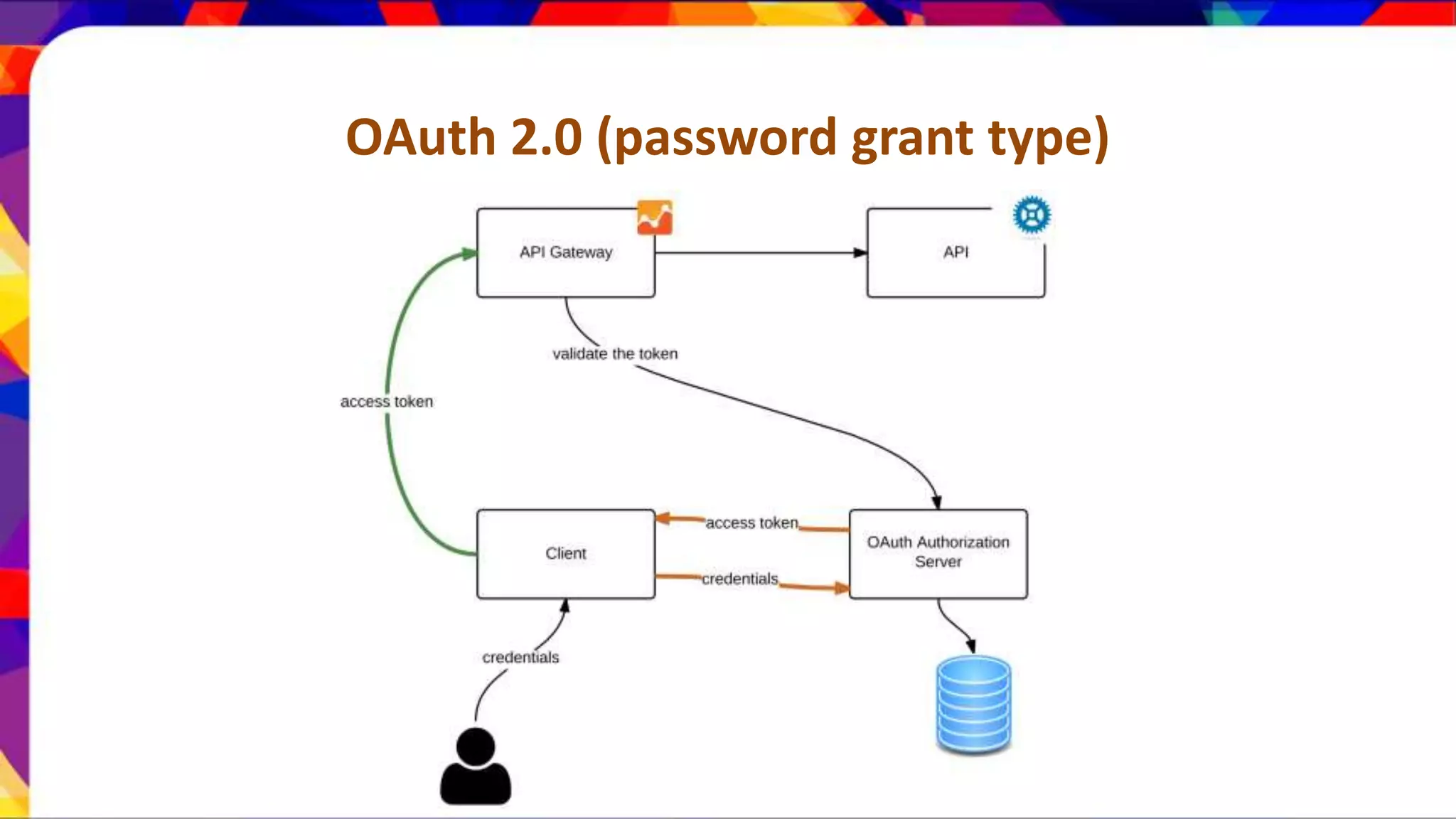
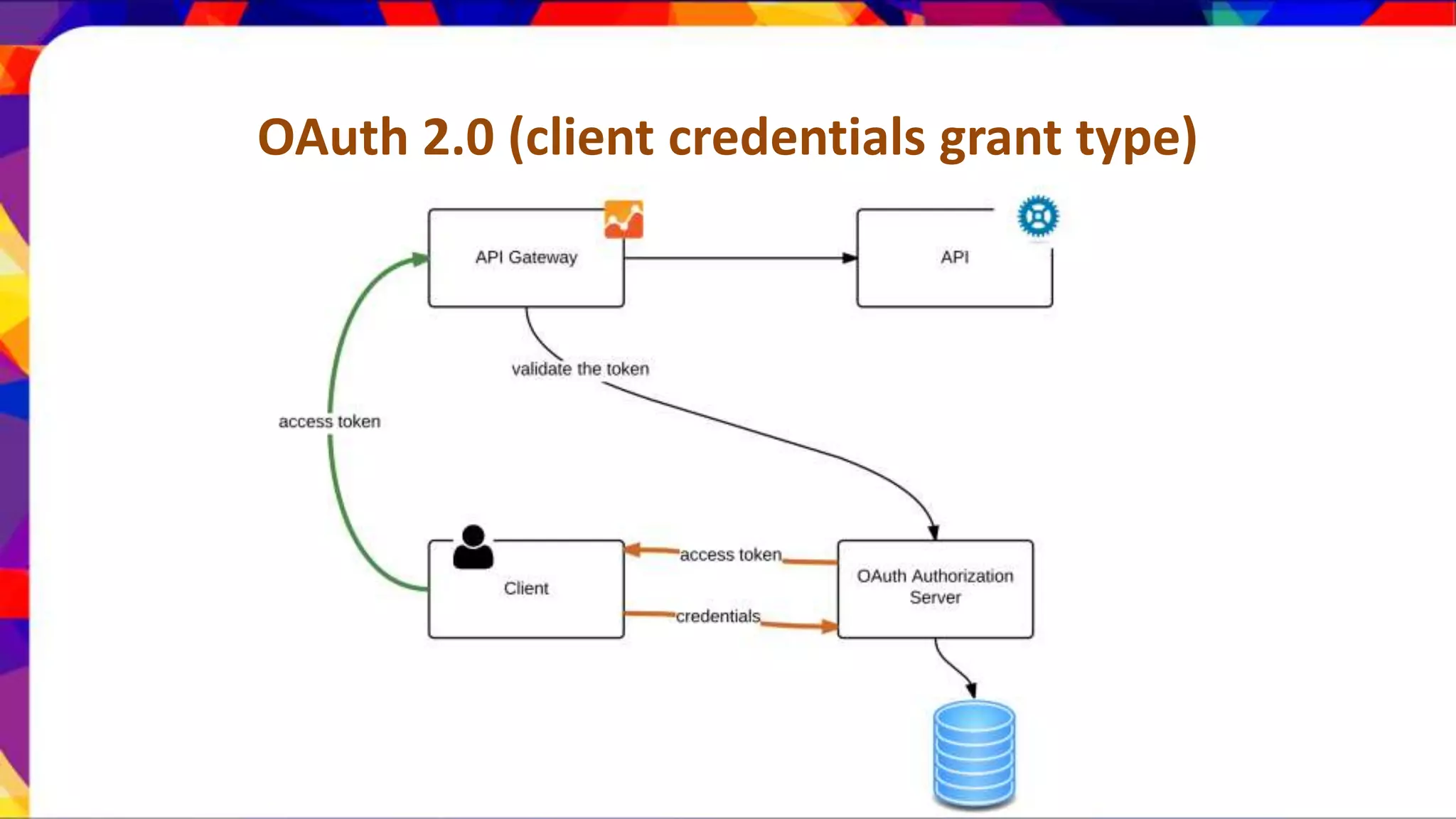
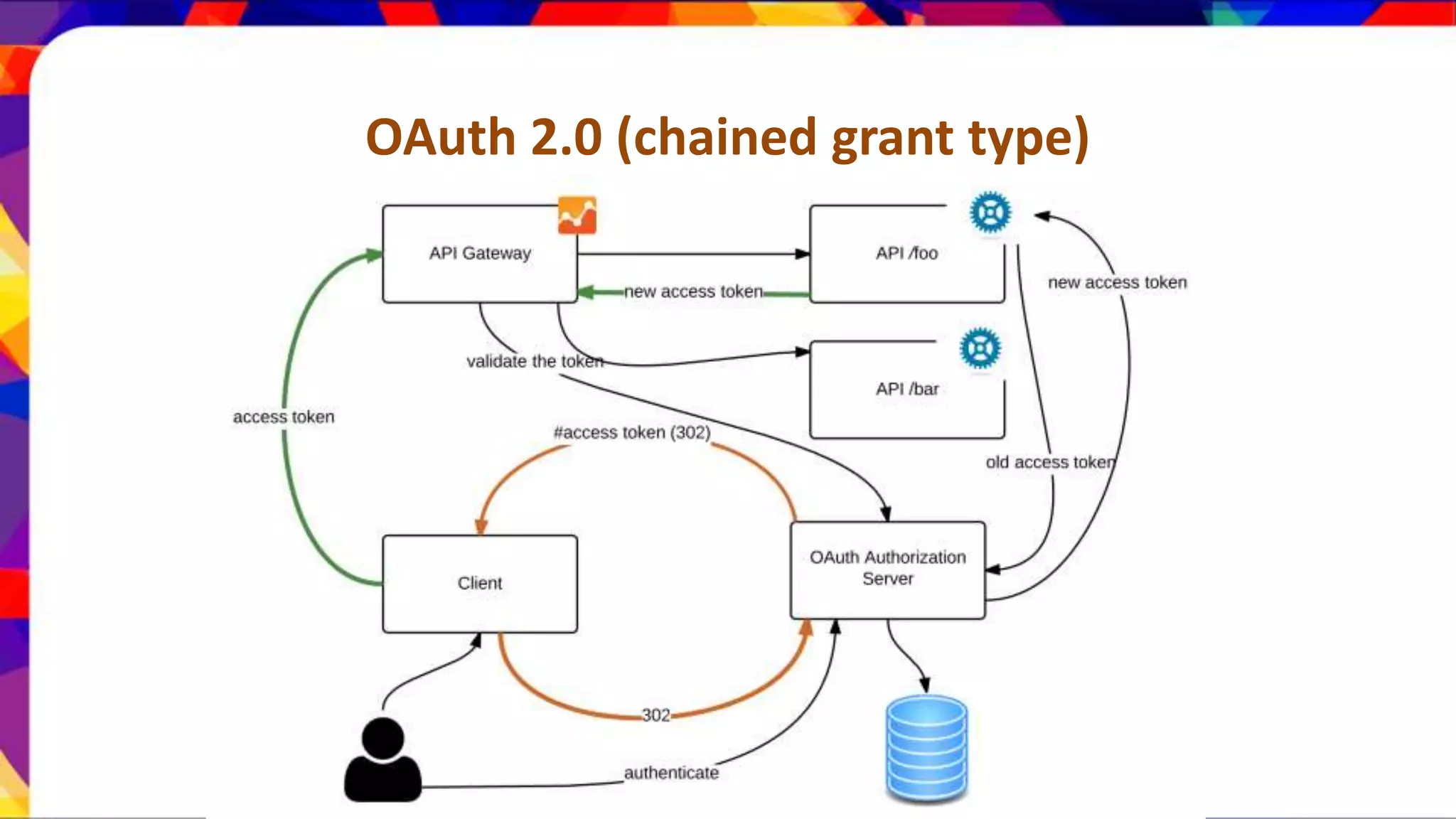
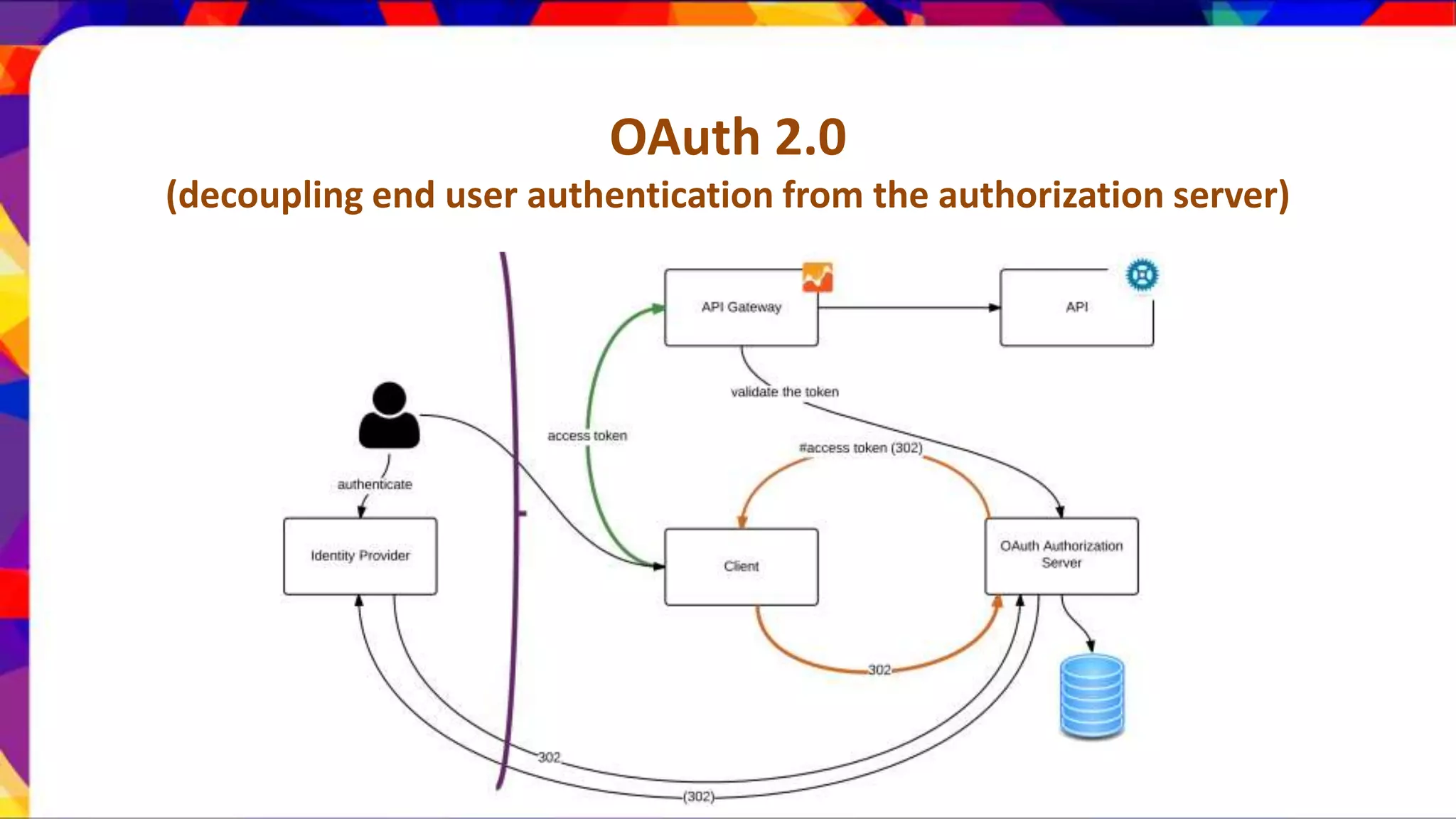
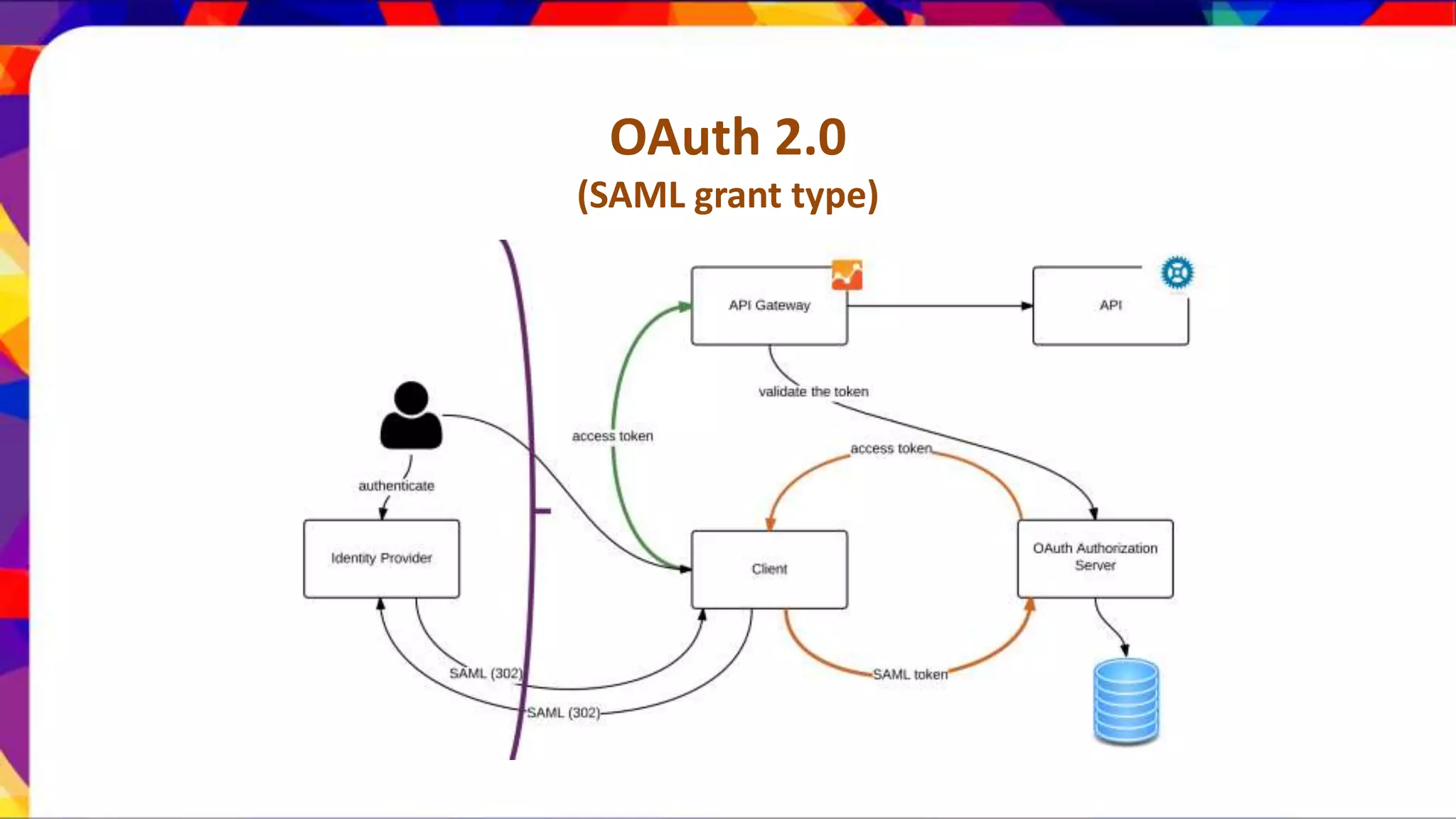
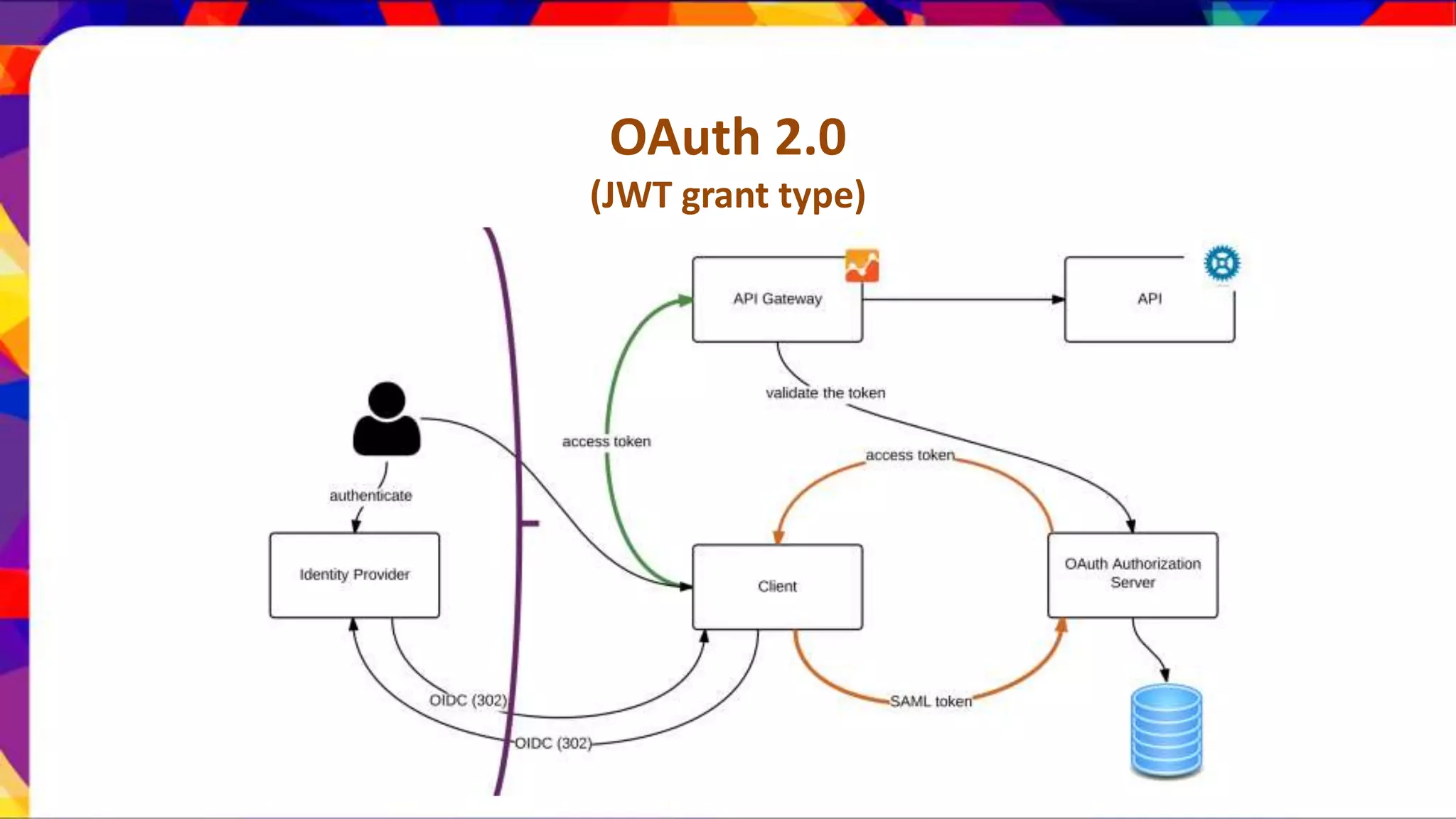
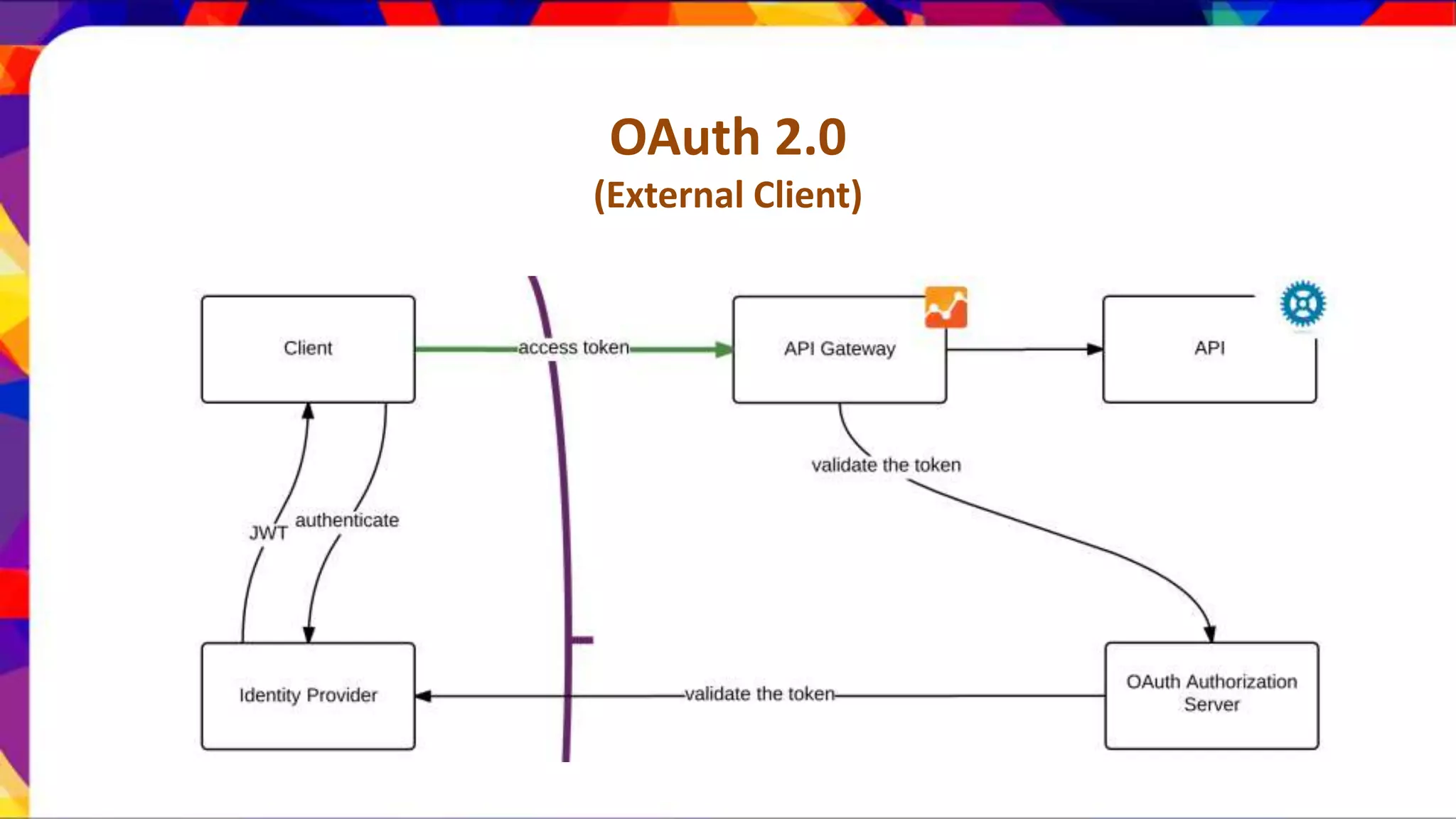
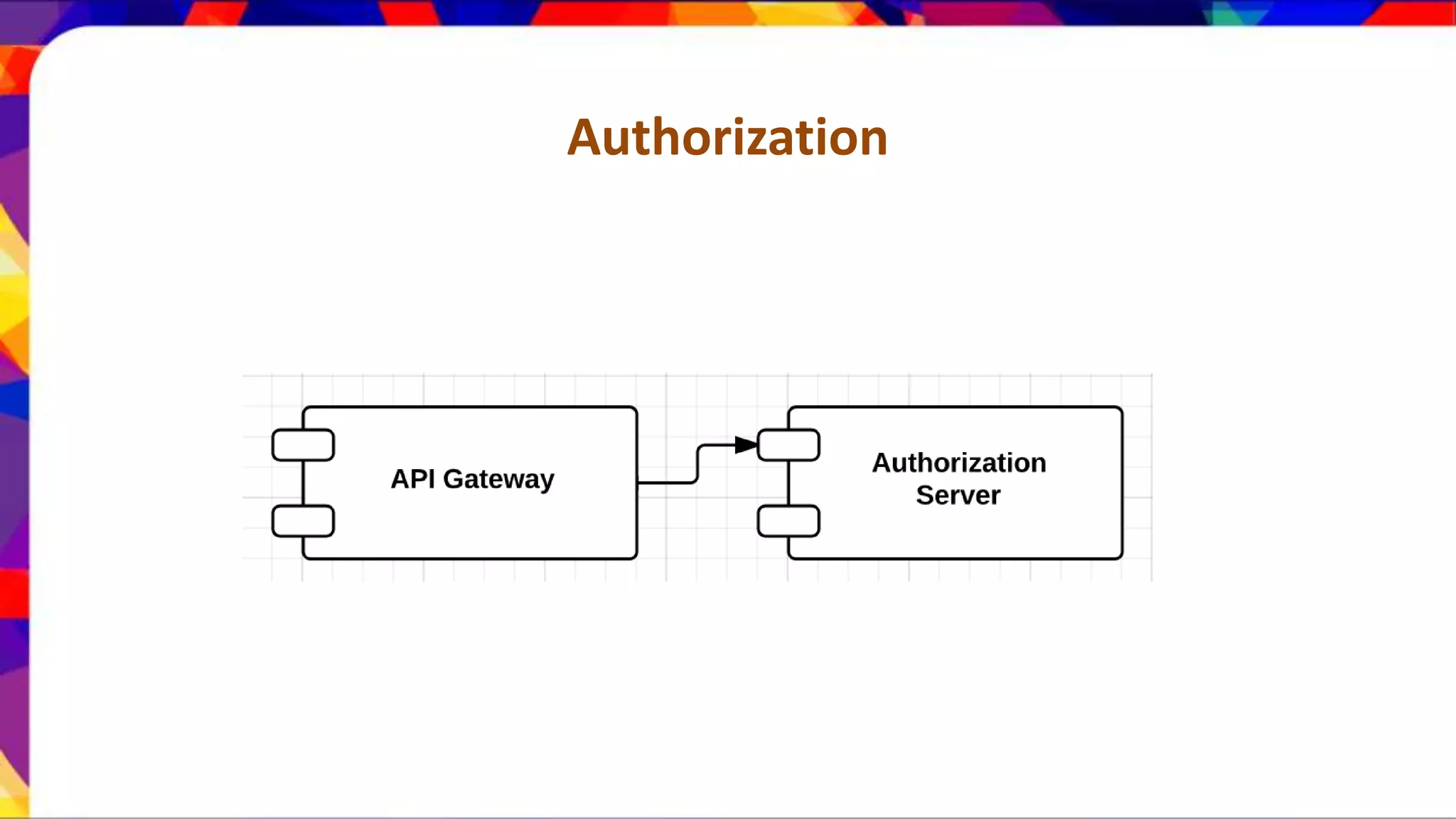
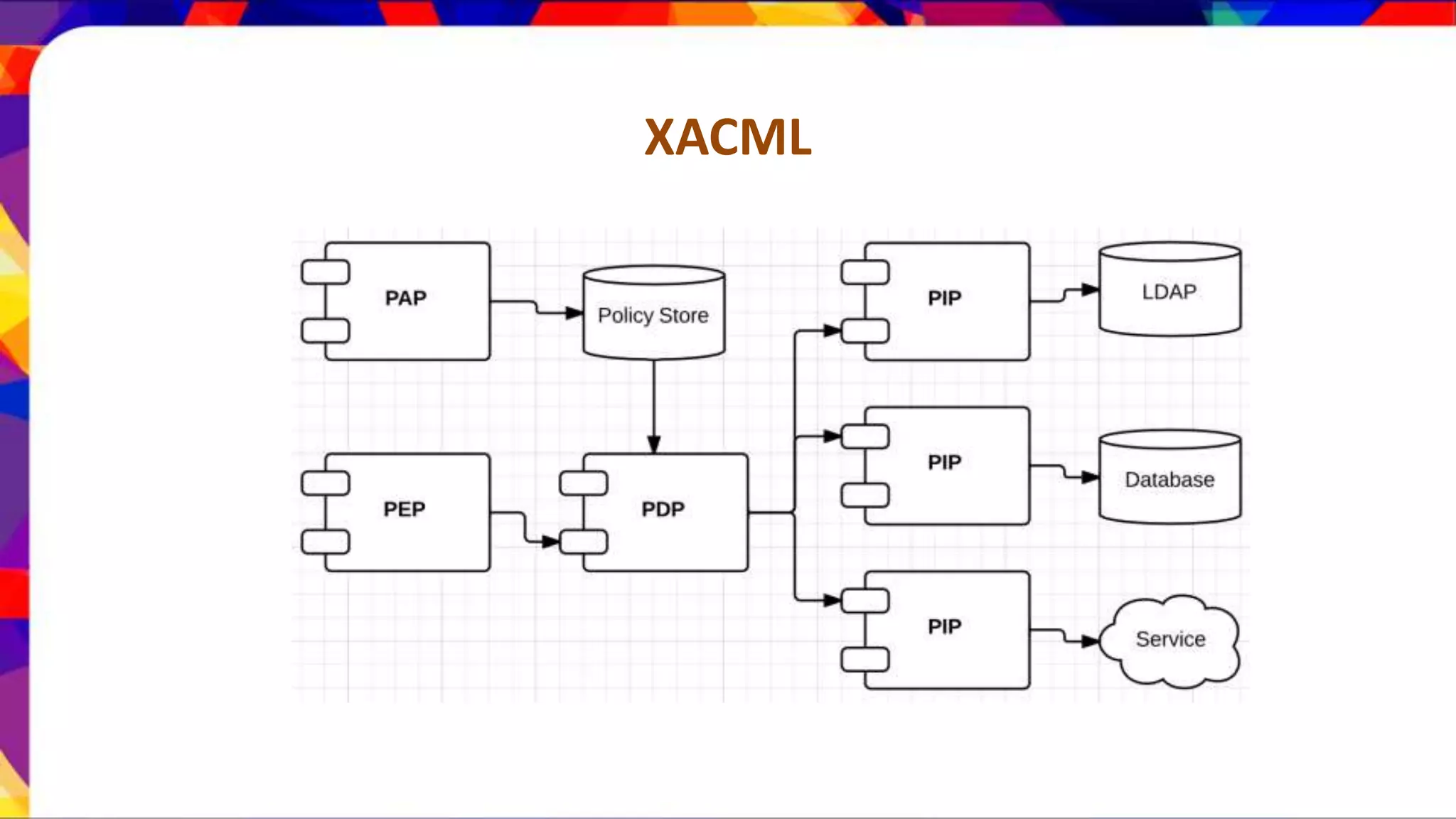
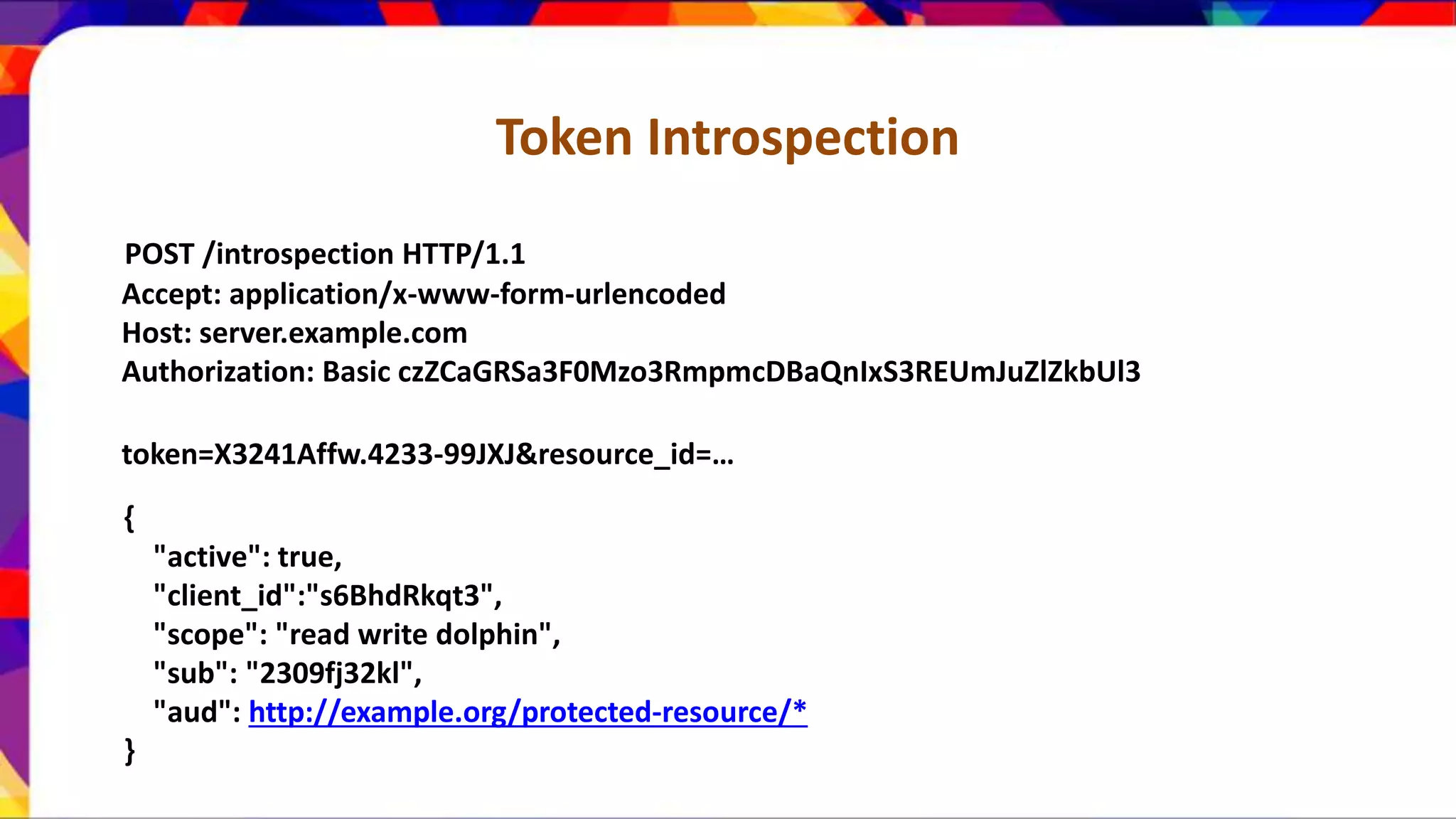
The document discusses API security patterns and practices. It covers topics like API gateways, authentication methods like basic authentication and OAuth 2.0, authorization with XACML policies, and securing APIs through measures like TLS, JWTs, and throttling to ensure authentication, authorization, confidentiality, integrity, non-repudiation, and availability. Key points covered include the gateway pattern, direct vs brokered authentication, JSON web tokens for self-contained access tokens, and combining OAuth and XACML for fine-grained access control.