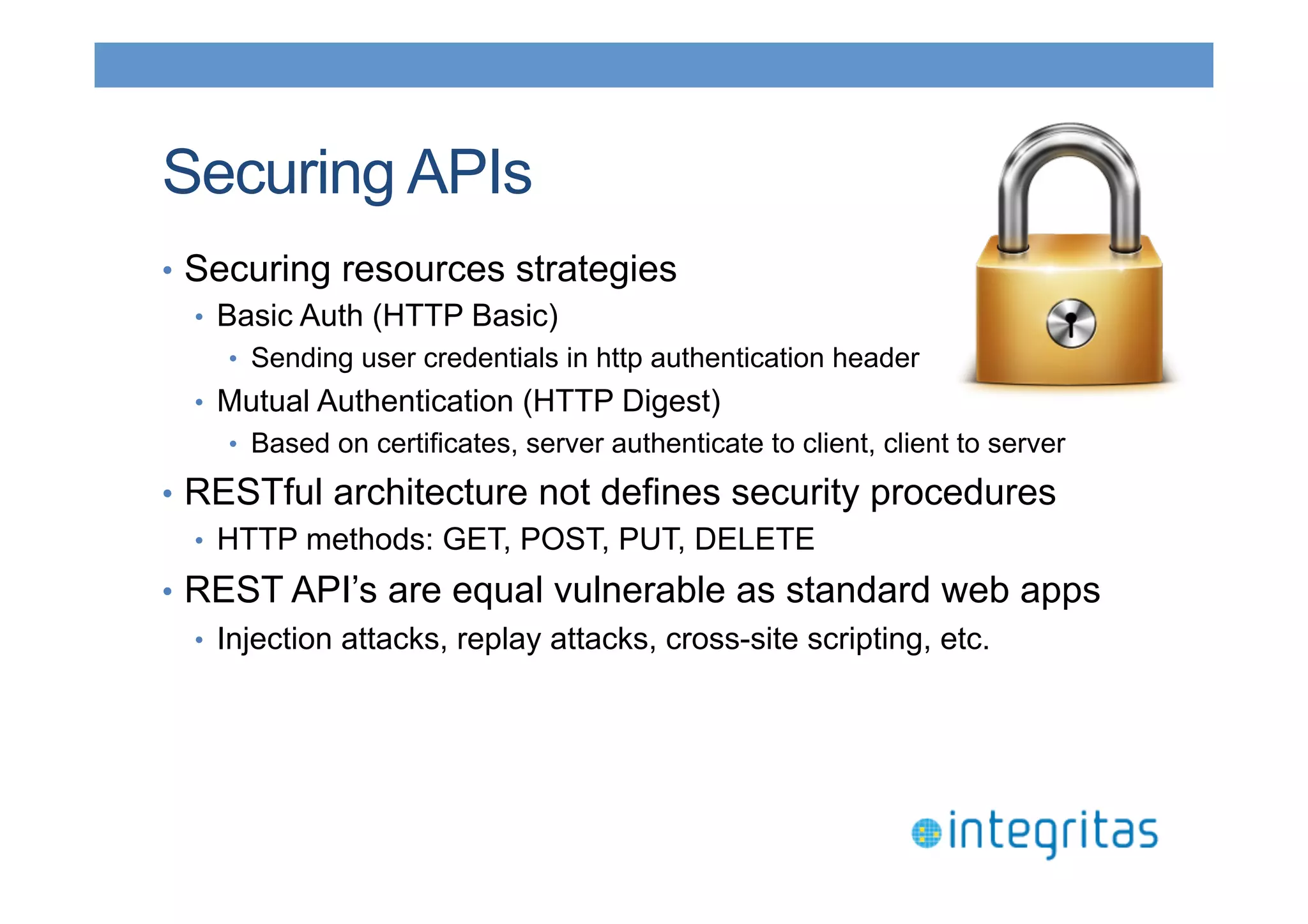
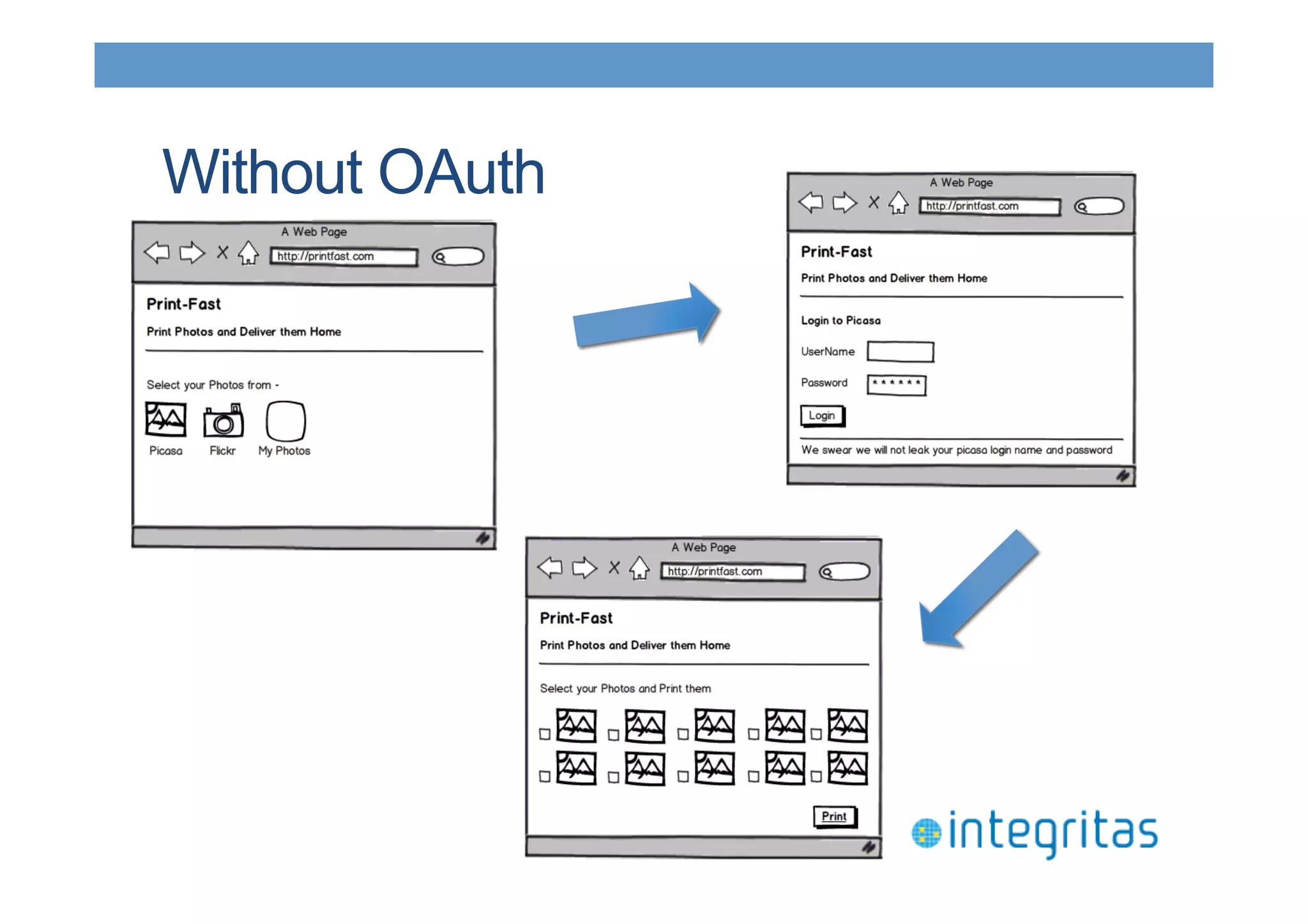
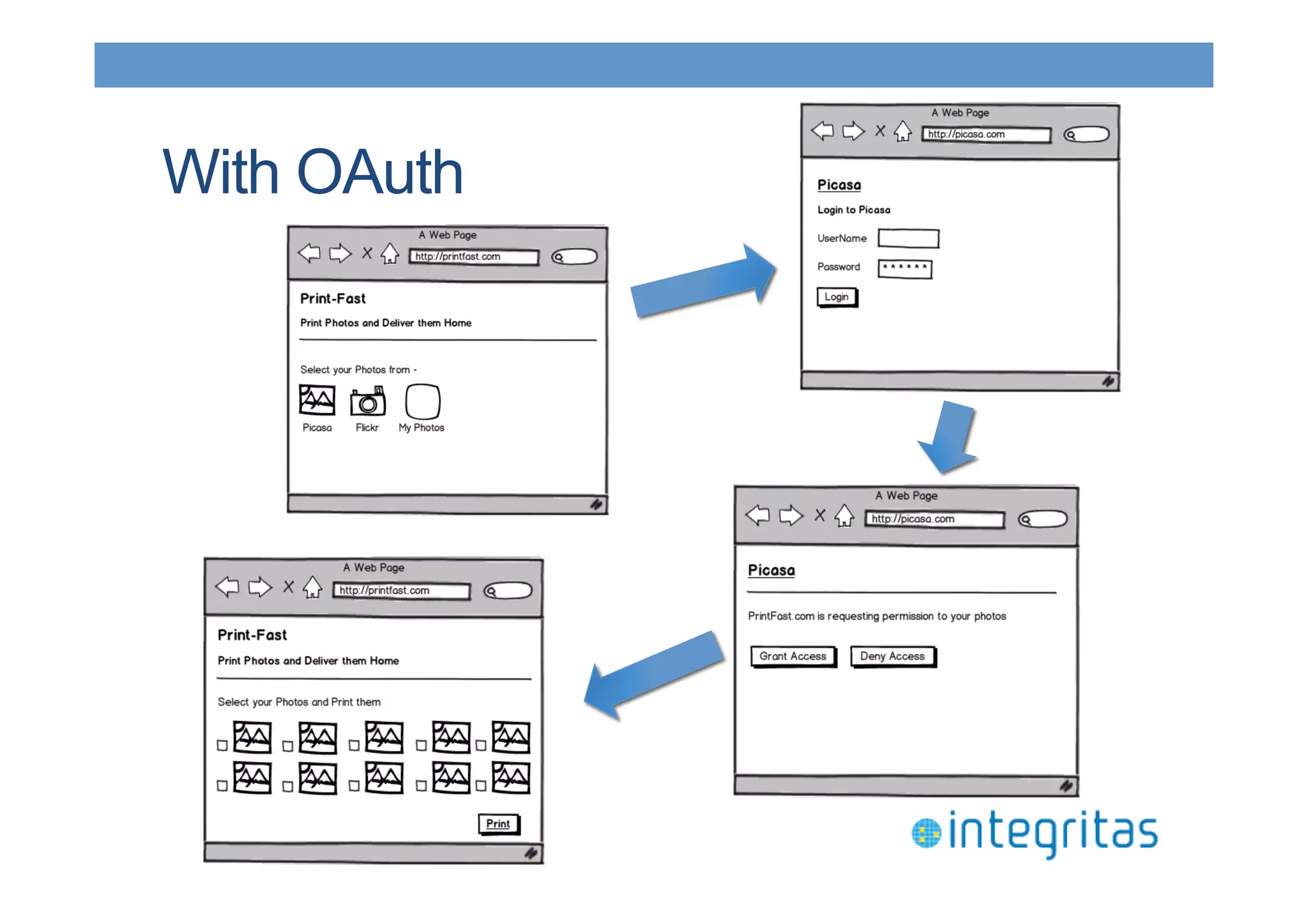
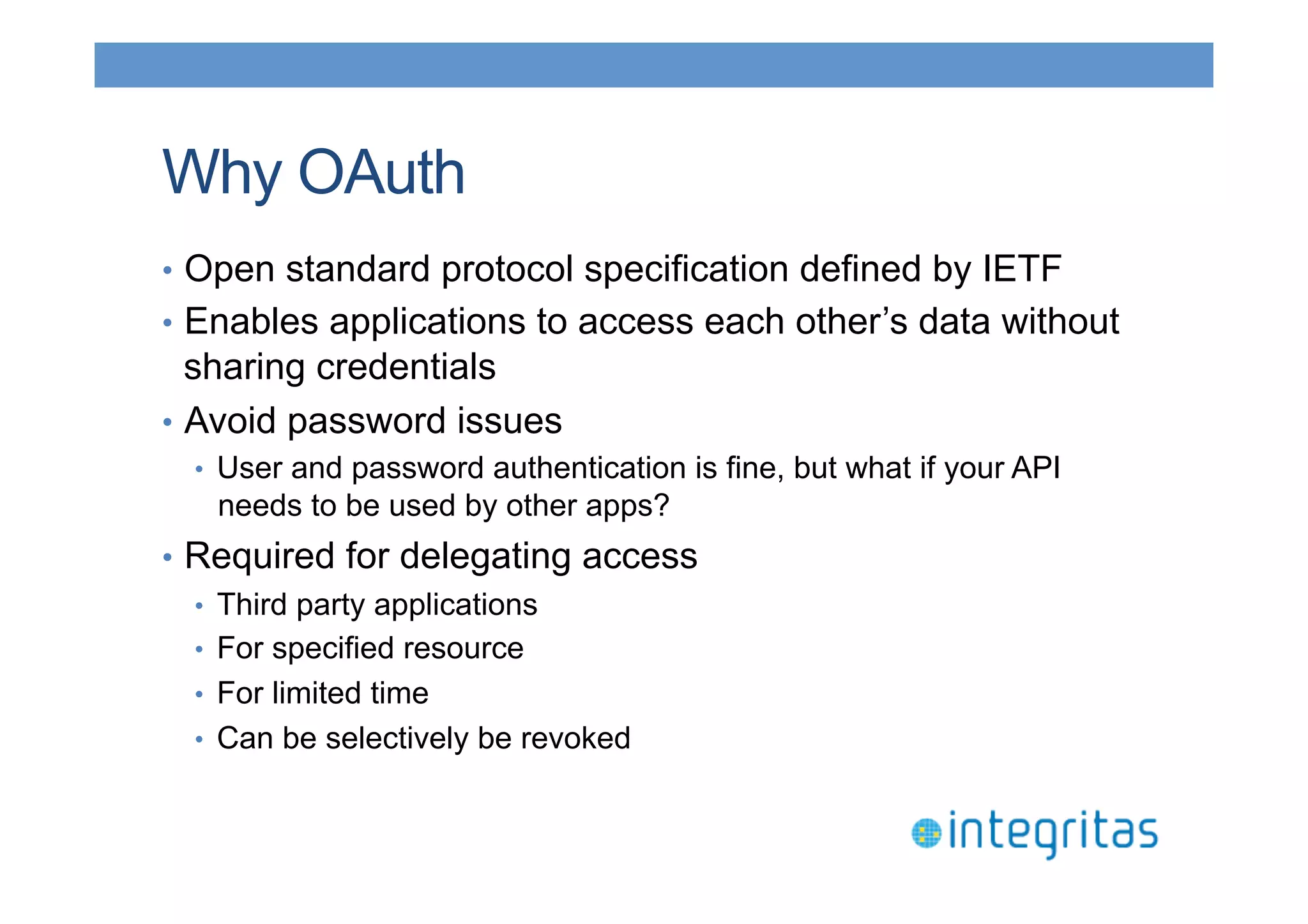
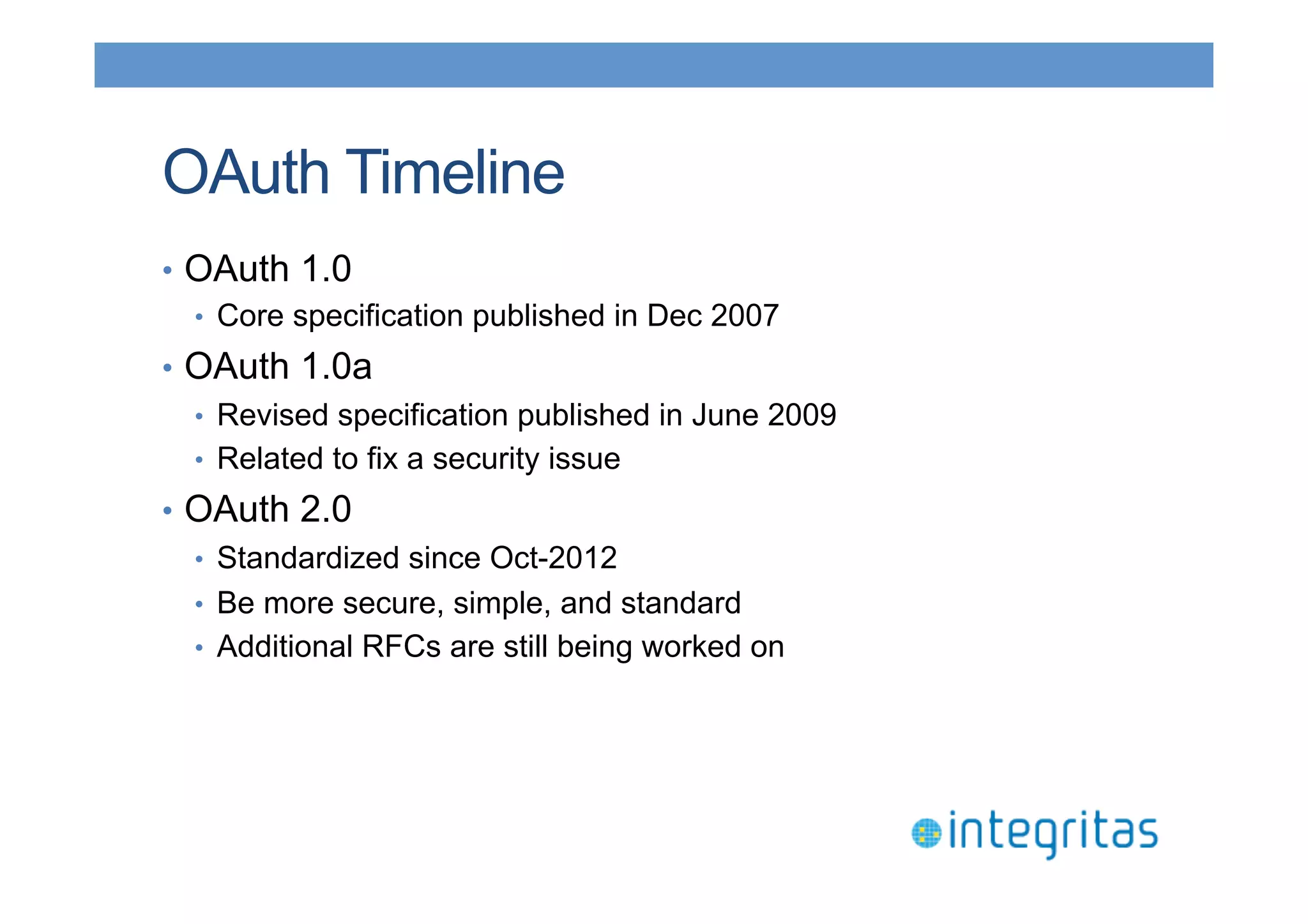
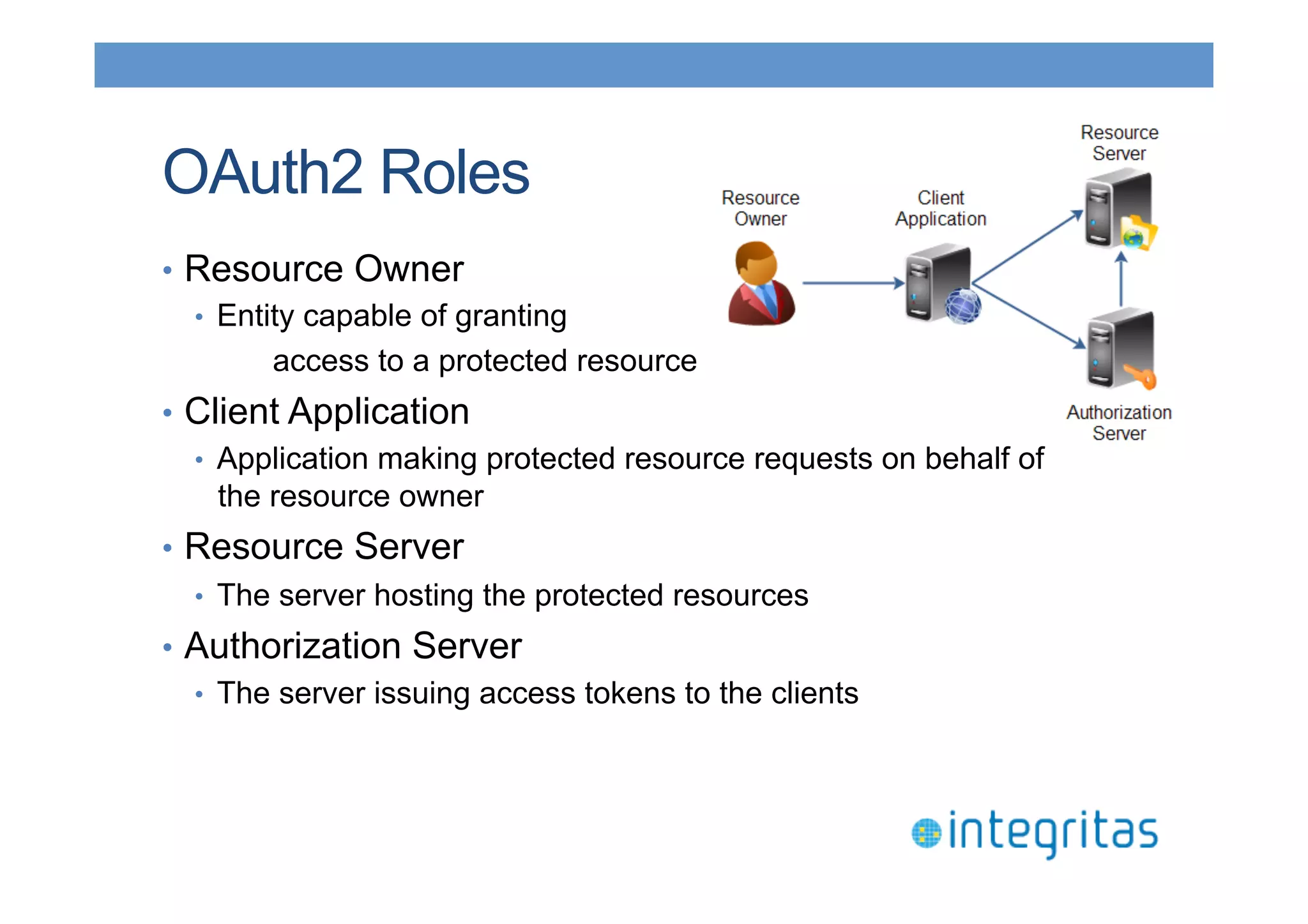
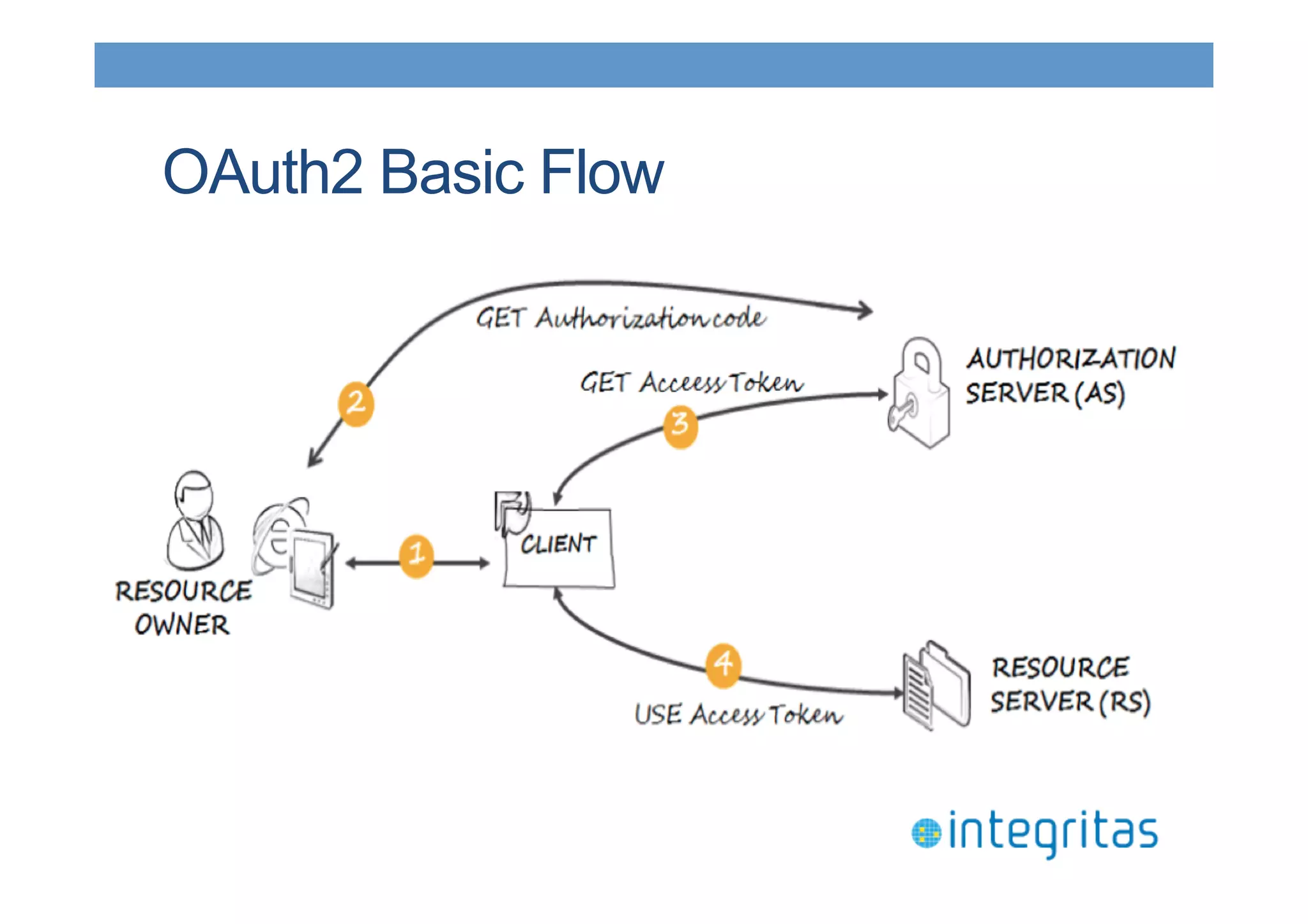
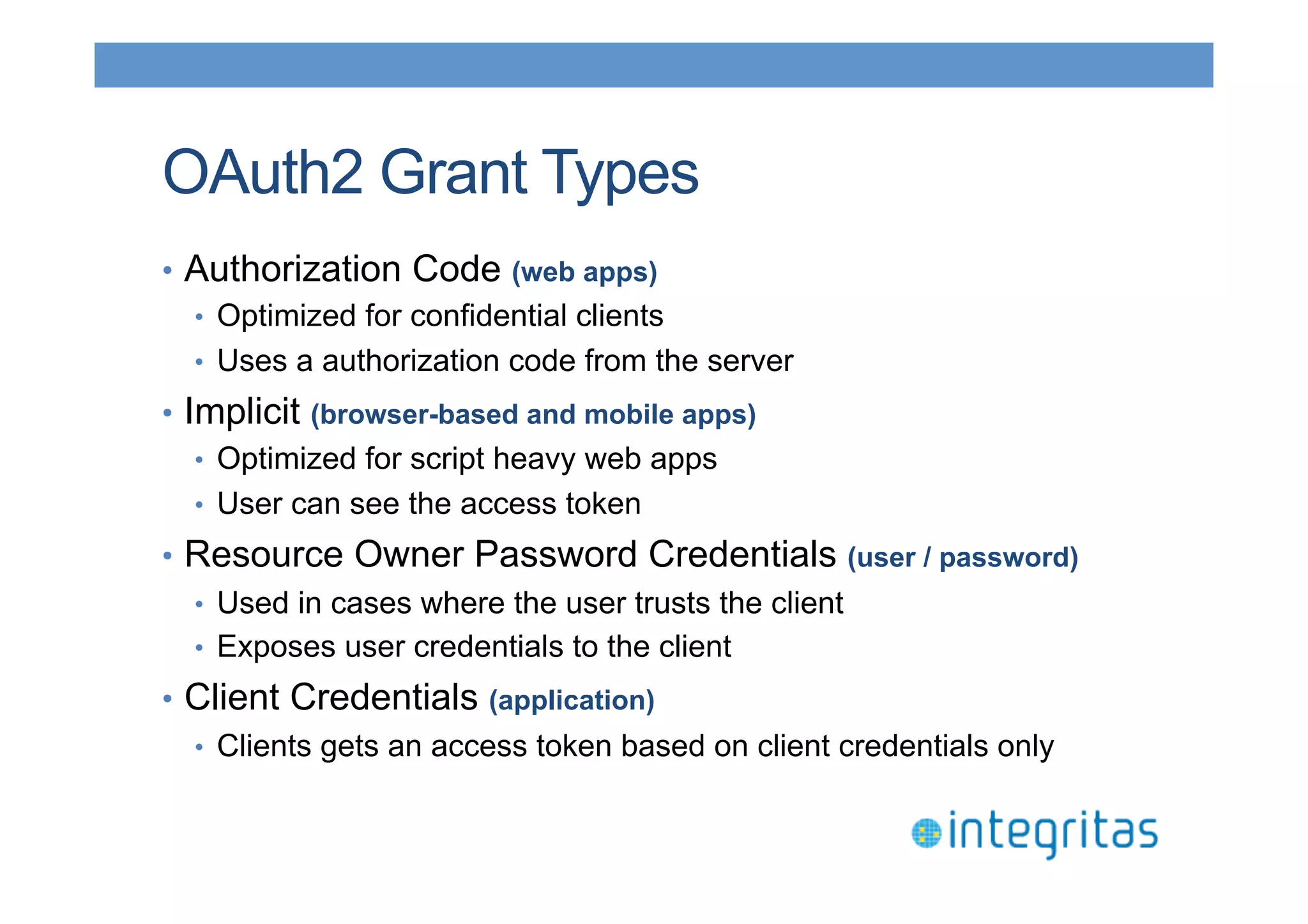
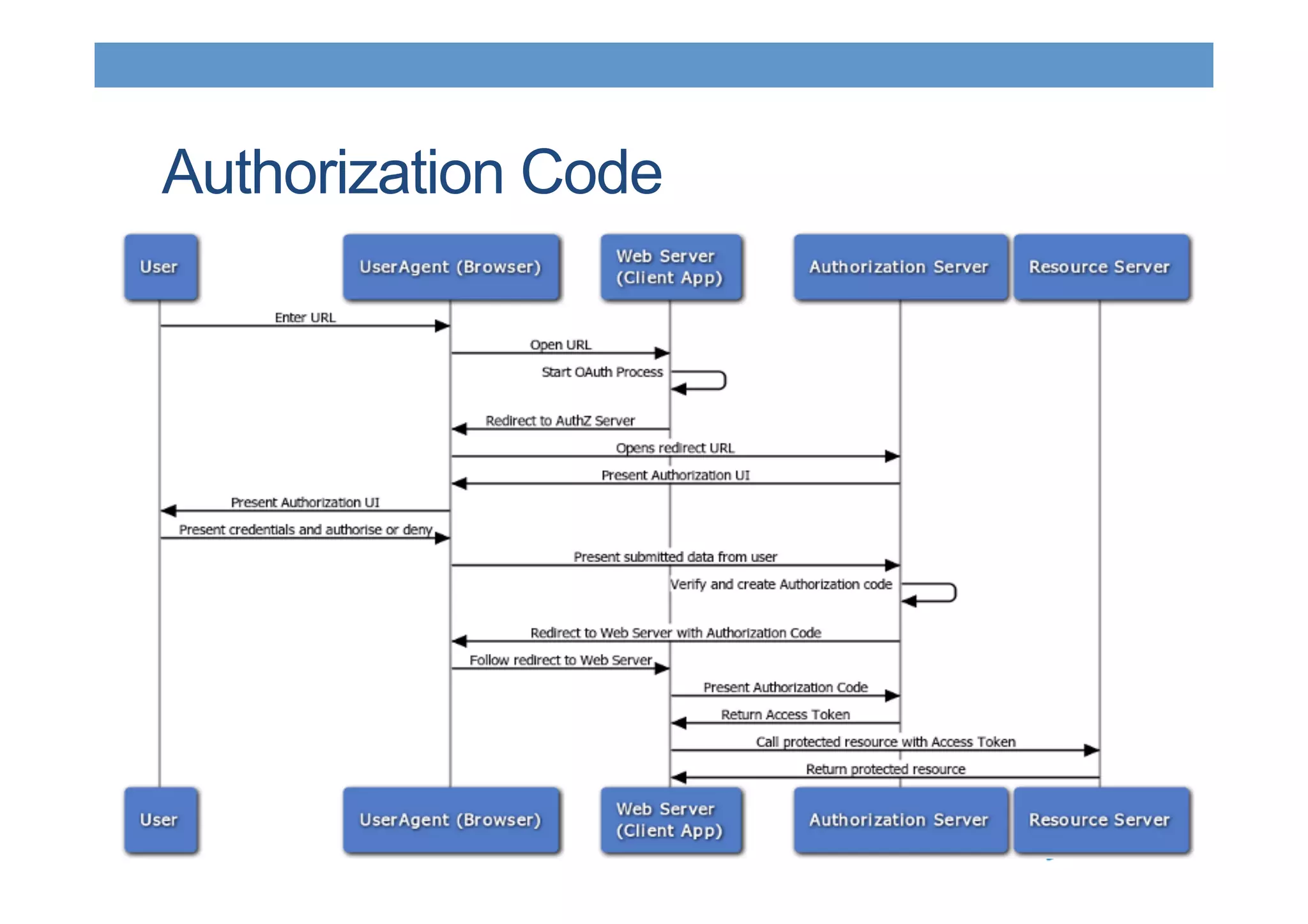
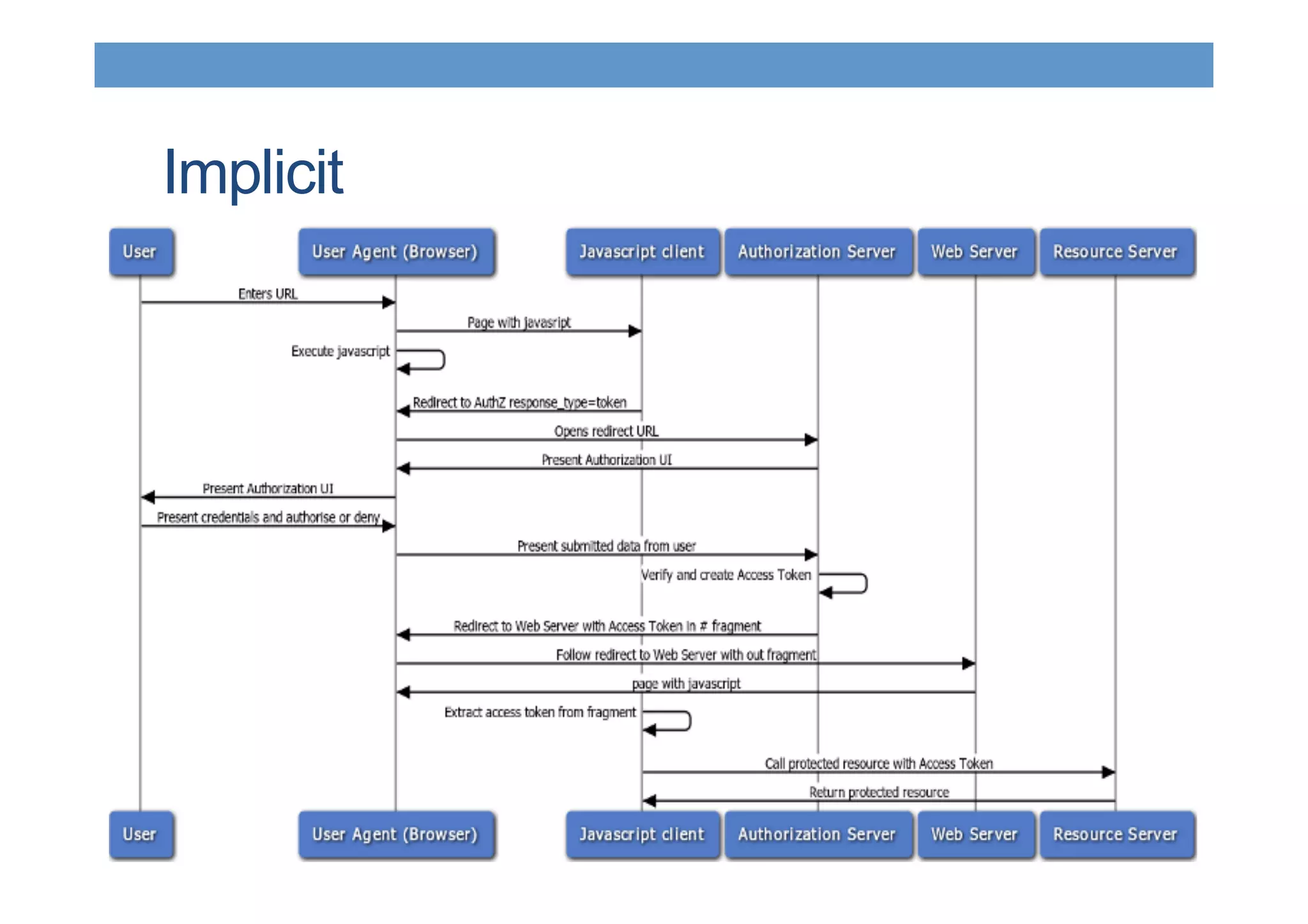
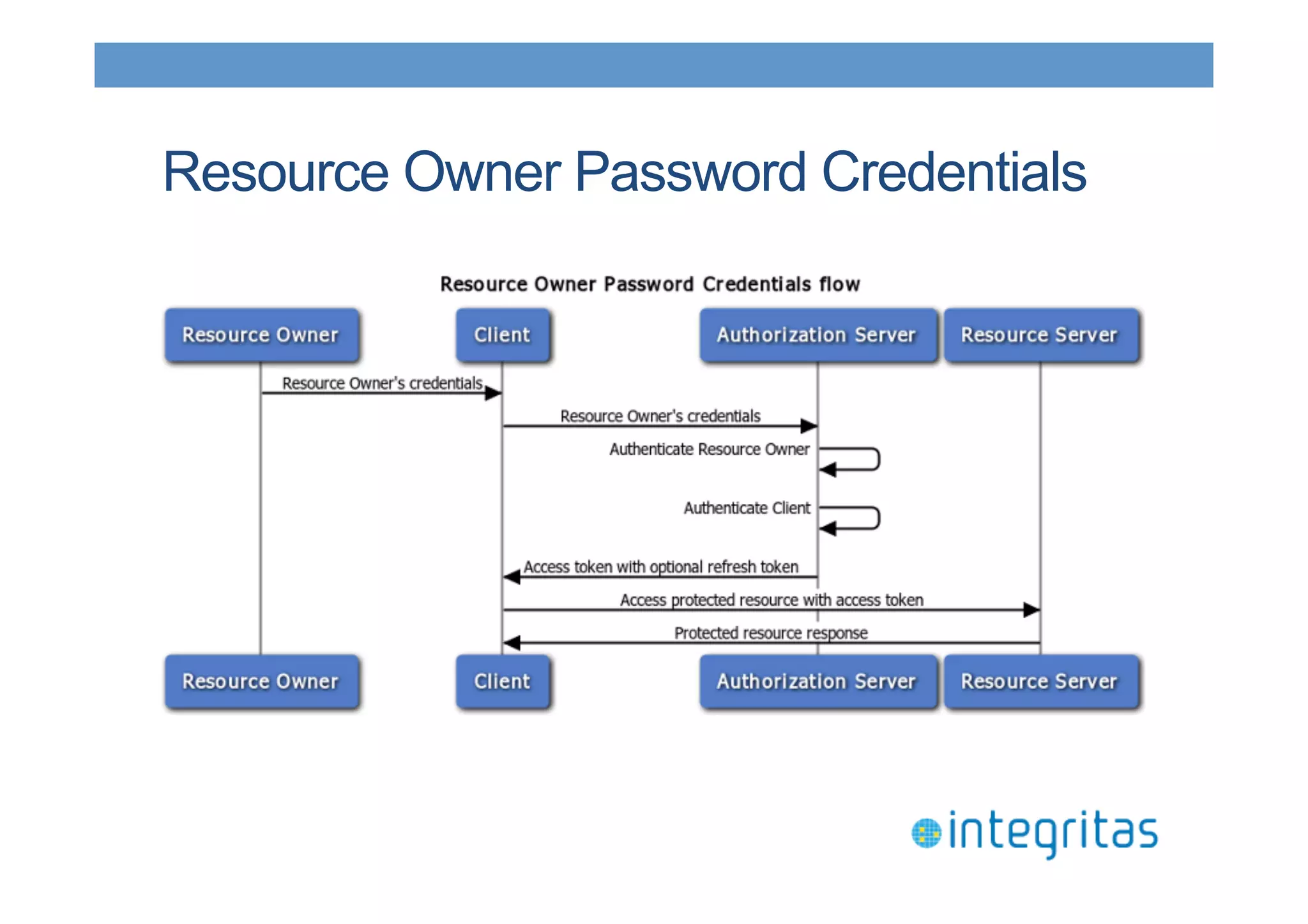
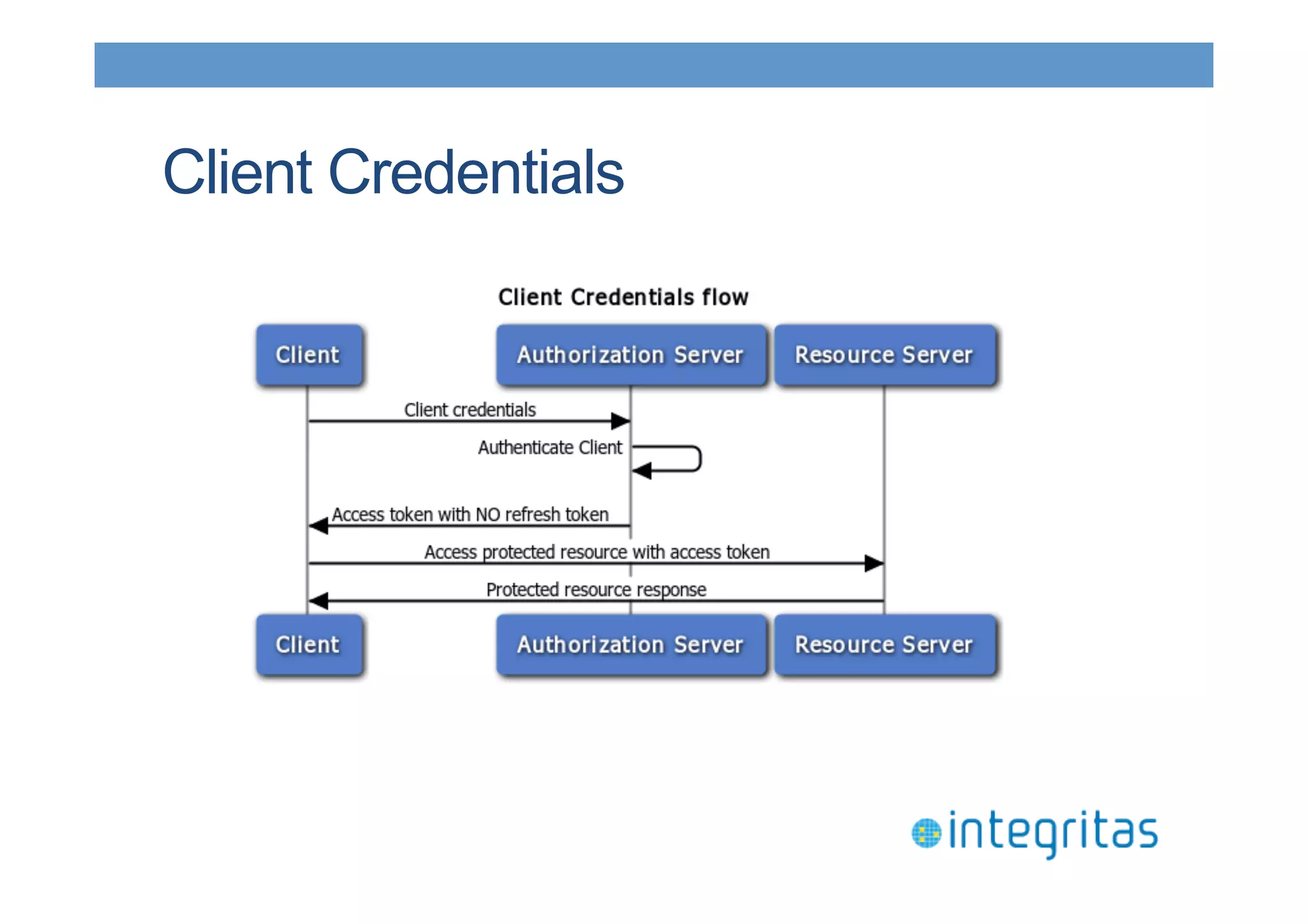
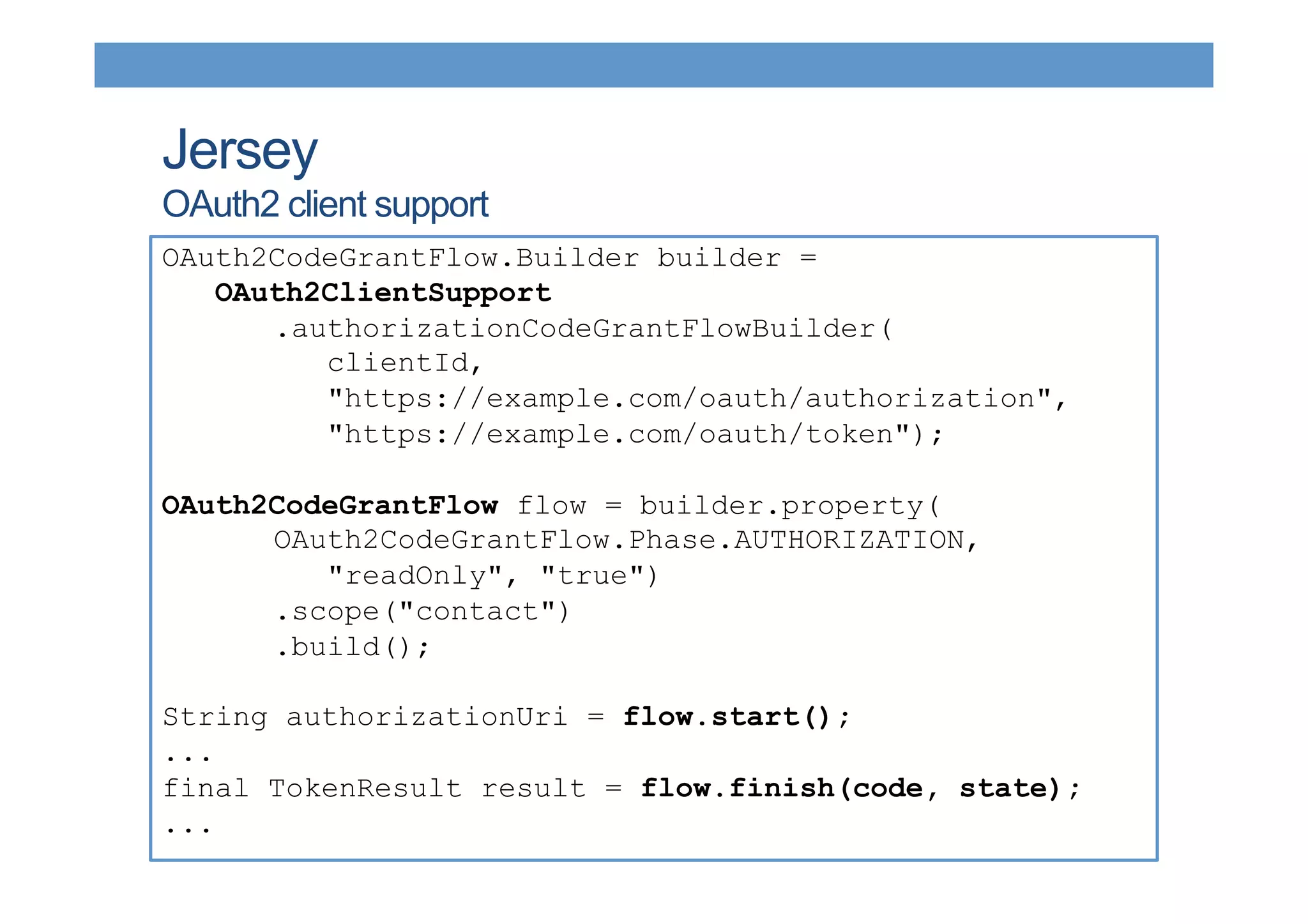
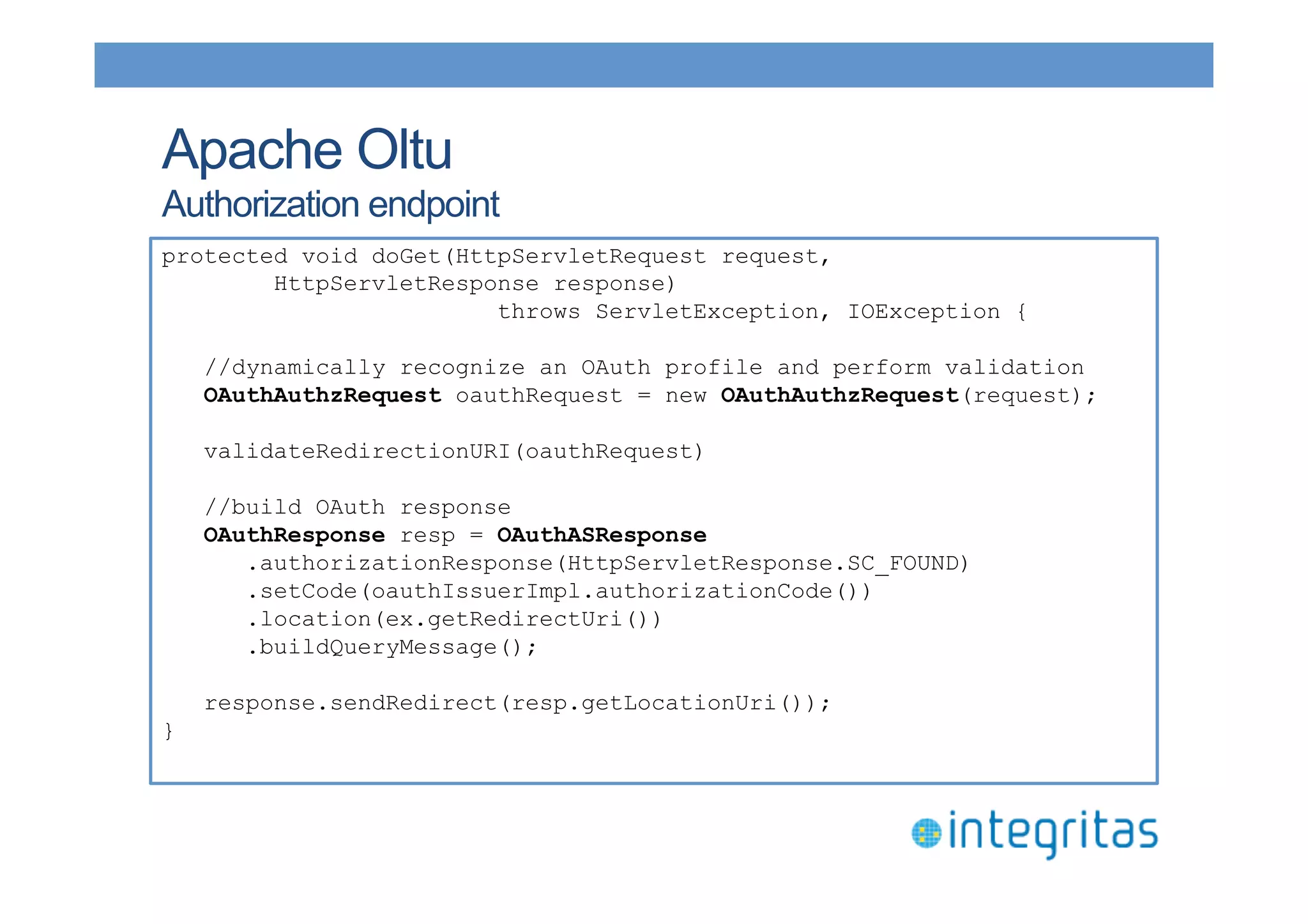
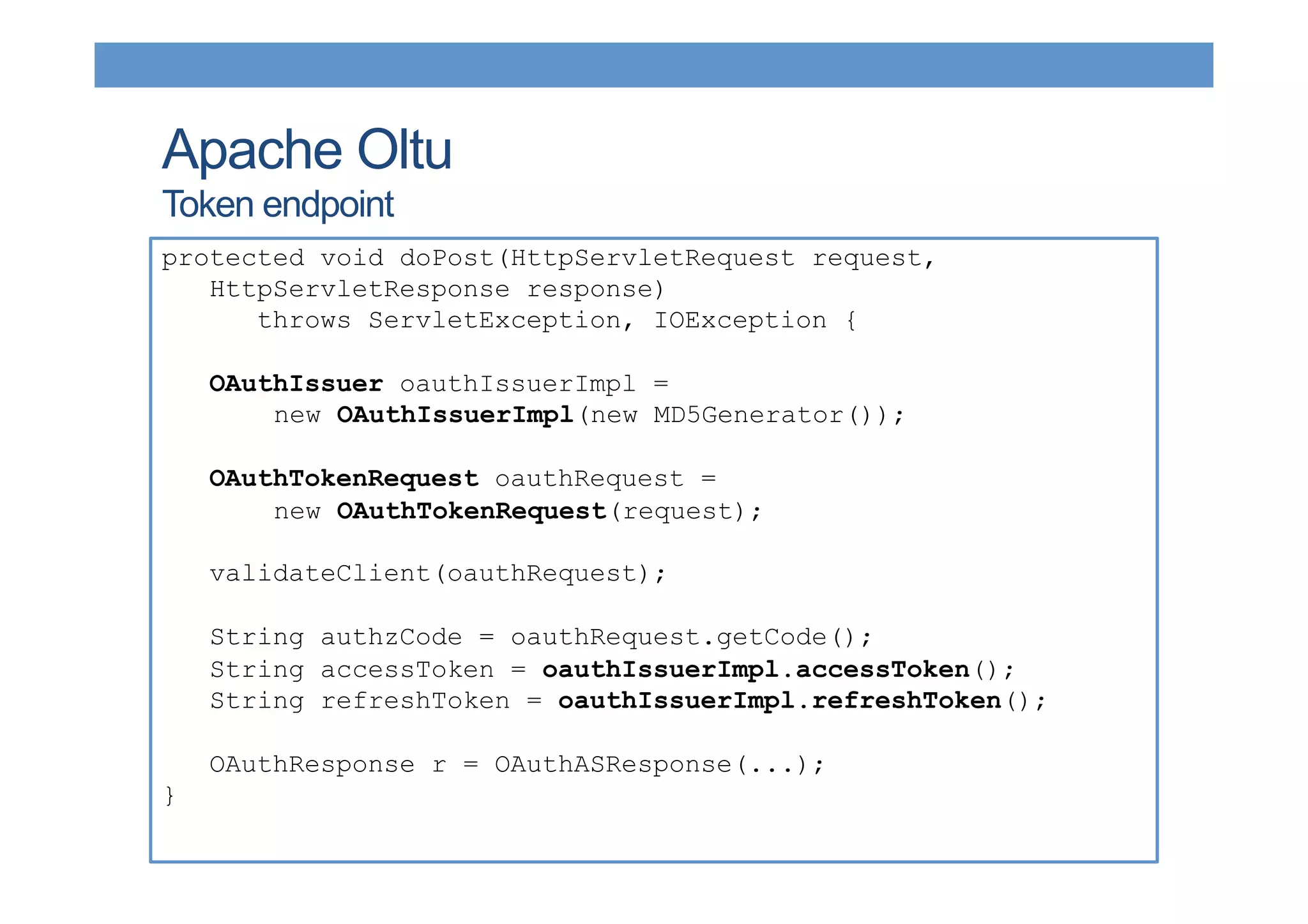
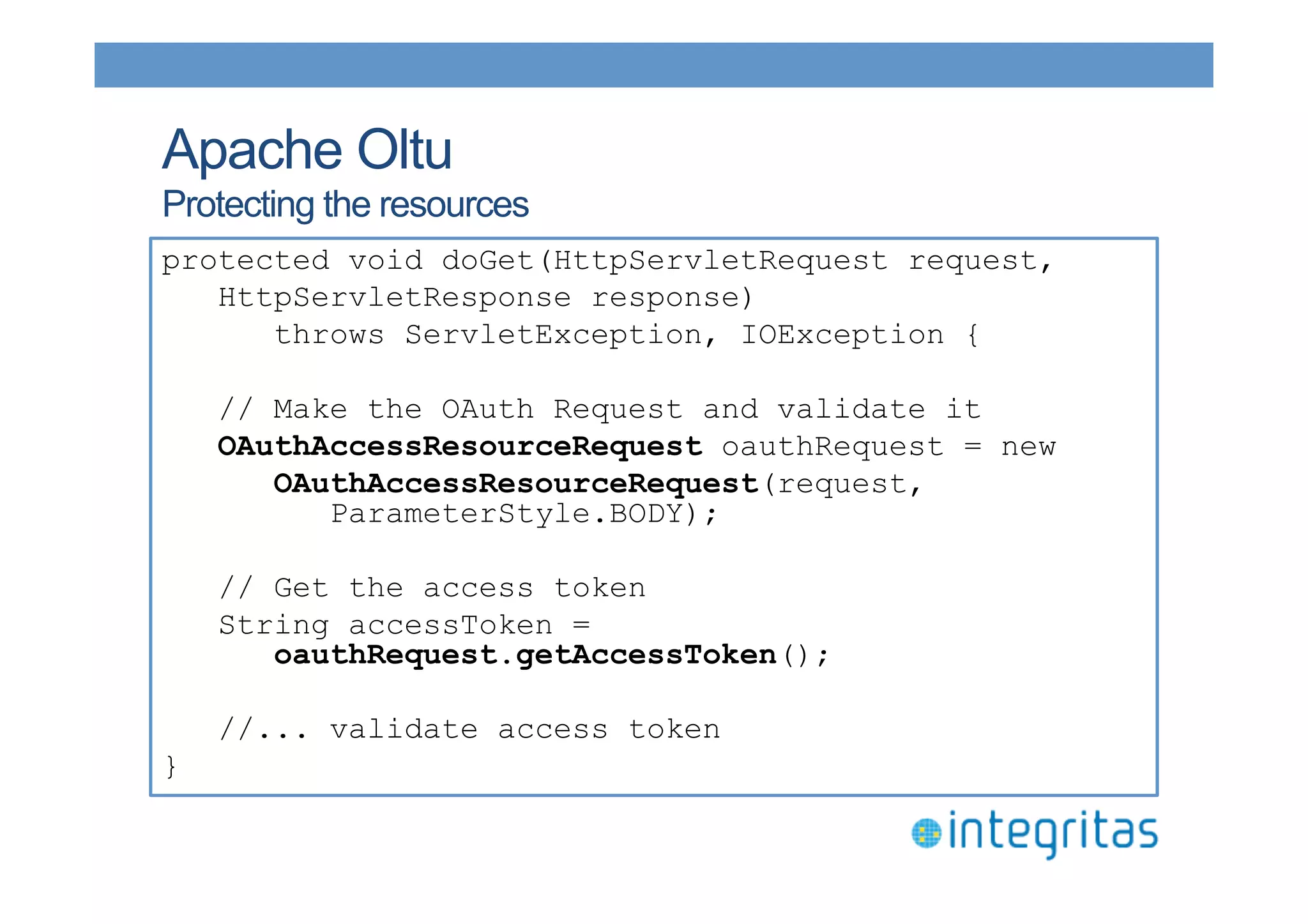
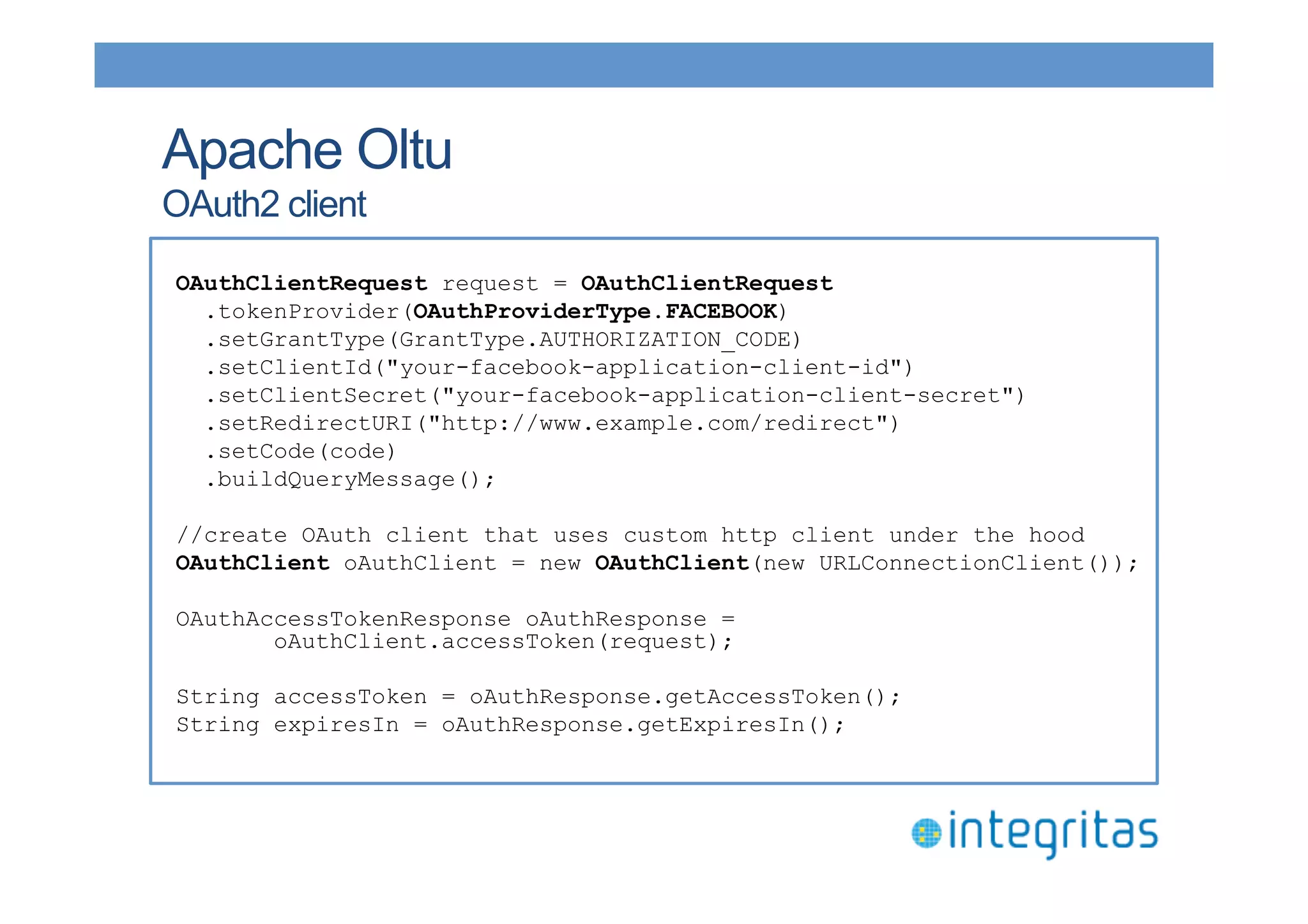
The document discusses securing RESTful resources using OAuth2, highlighting its importance for application data access without credential sharing. It covers key concepts like grant types, tokens, and Java implementations, emphasizing OAuth2's security benefits and its architecture's vulnerabilities. The presentation outlines various OAuth2 roles, flow, and pros and cons while providing examples of Java frameworks that support OAuth2 integration.