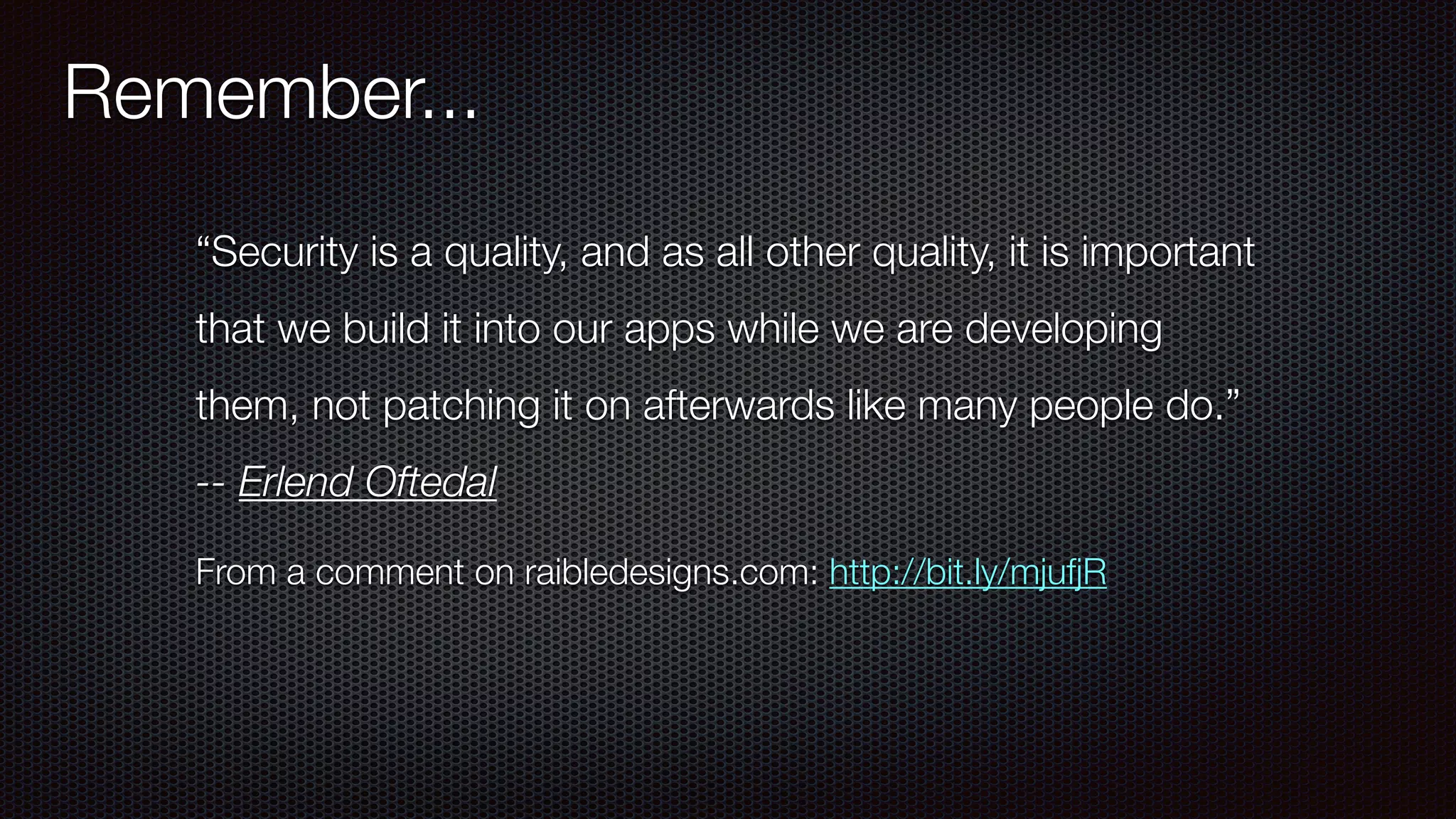
The document discusses Java web application security, covering various frameworks like Java EE 7, Spring Security, and Apache Shiro. It emphasizes best practices for implementing security measures, penetration testing, and the OWASP Top 10 vulnerabilities, while also providing code examples and configuration tips. Additionally, it highlights tools and resources for enhancing application security and the importance of integrating security into the development process.













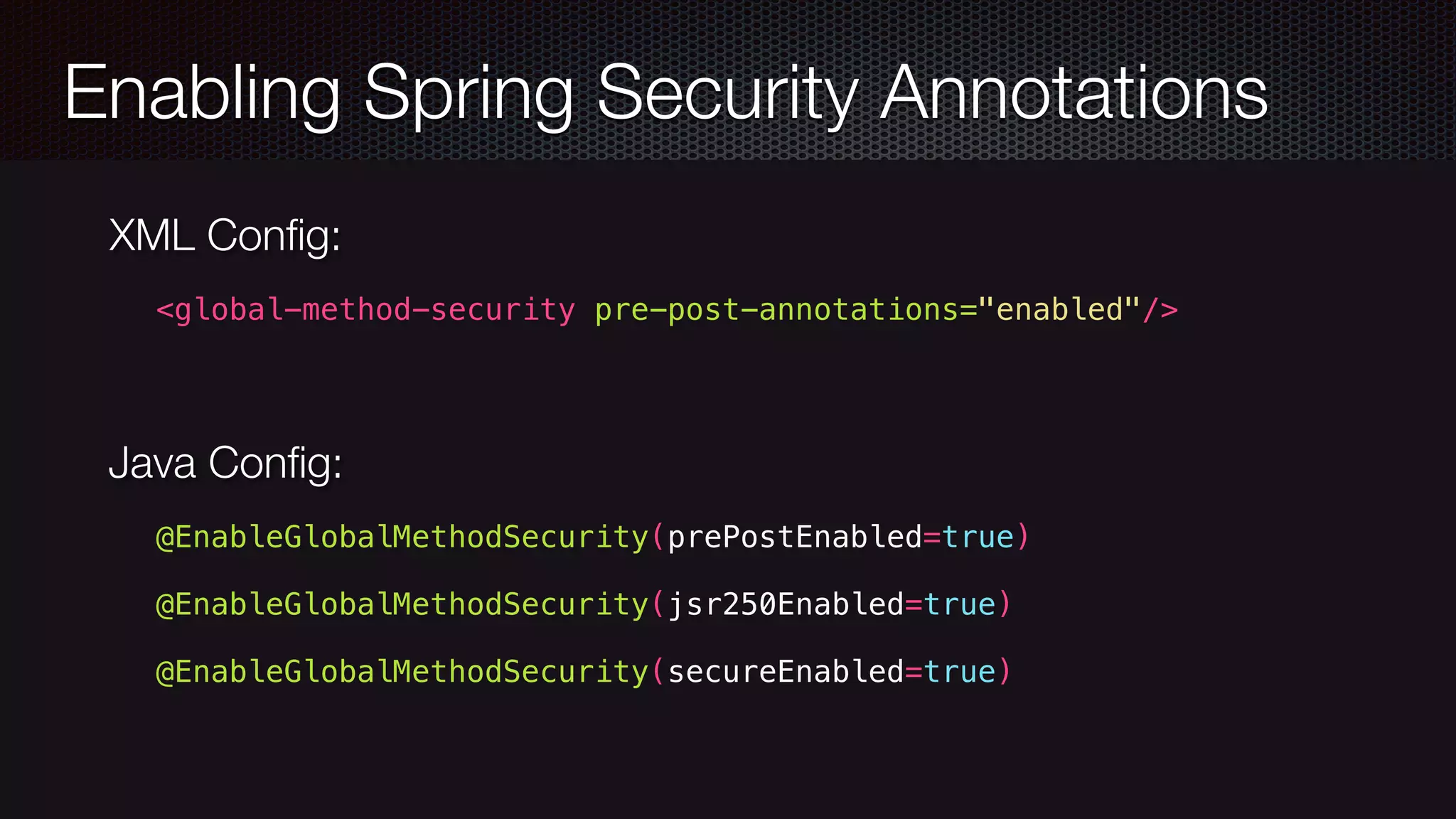
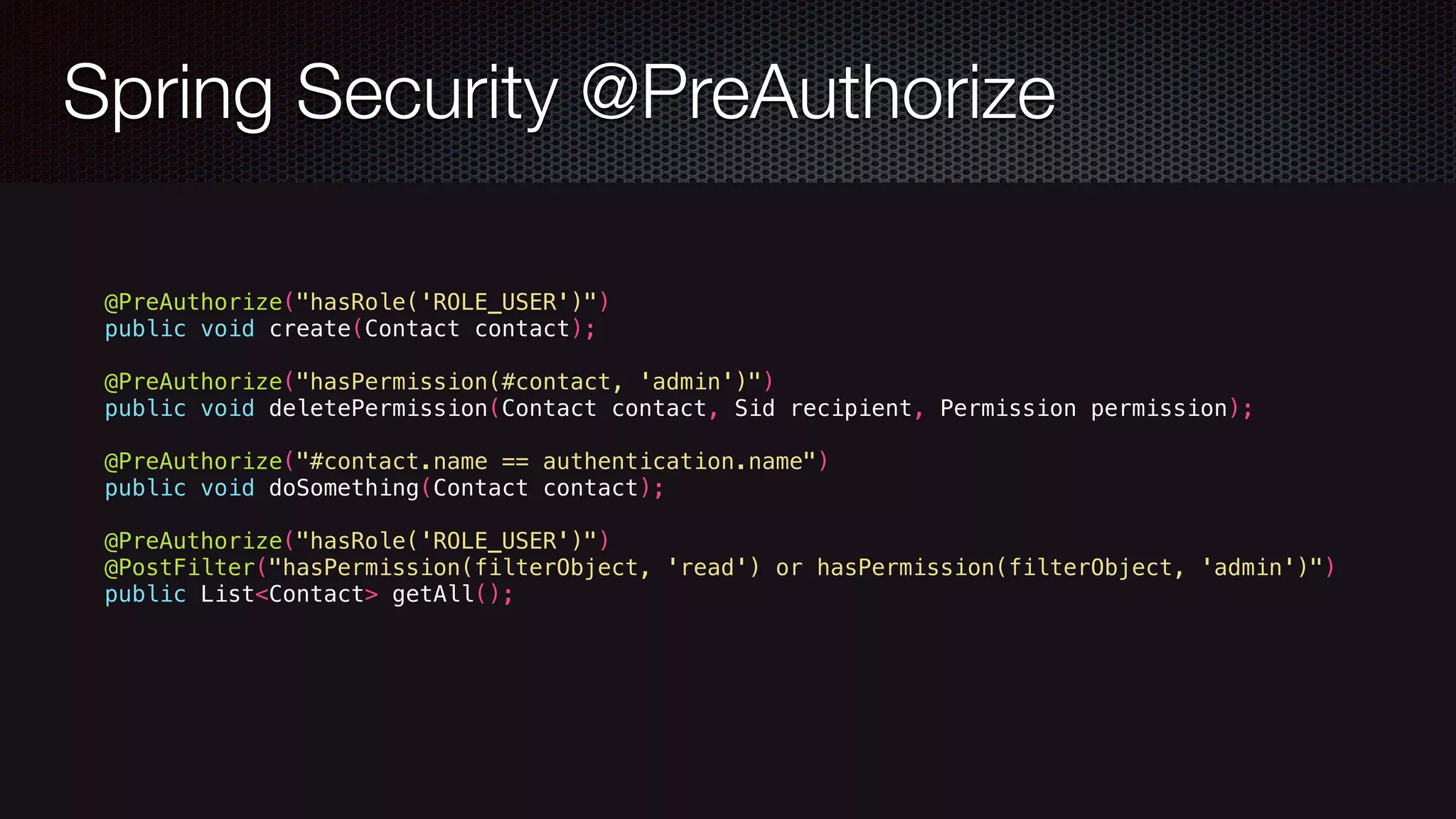
![Spring Security @Secured @Secured("IS_AUTHENTICATED_ANONYMOUSLY") public Account readAccount(Long id); @Secured("IS_AUTHENTICATED_ANONYMOUSLY") public Account[] findAccounts(); @Secured("ROLE_TELLER") public Account post(Account account, double amount)}](https://image.slidesharecdn.com/javawebapplicationsecurity-uberconf2015-150723200955-lva1-app6892/75/Java-Web-Application-Security-with-Java-EE-Spring-Security-and-Apache-Shiro-UberConf-2015-19-2048.jpg)
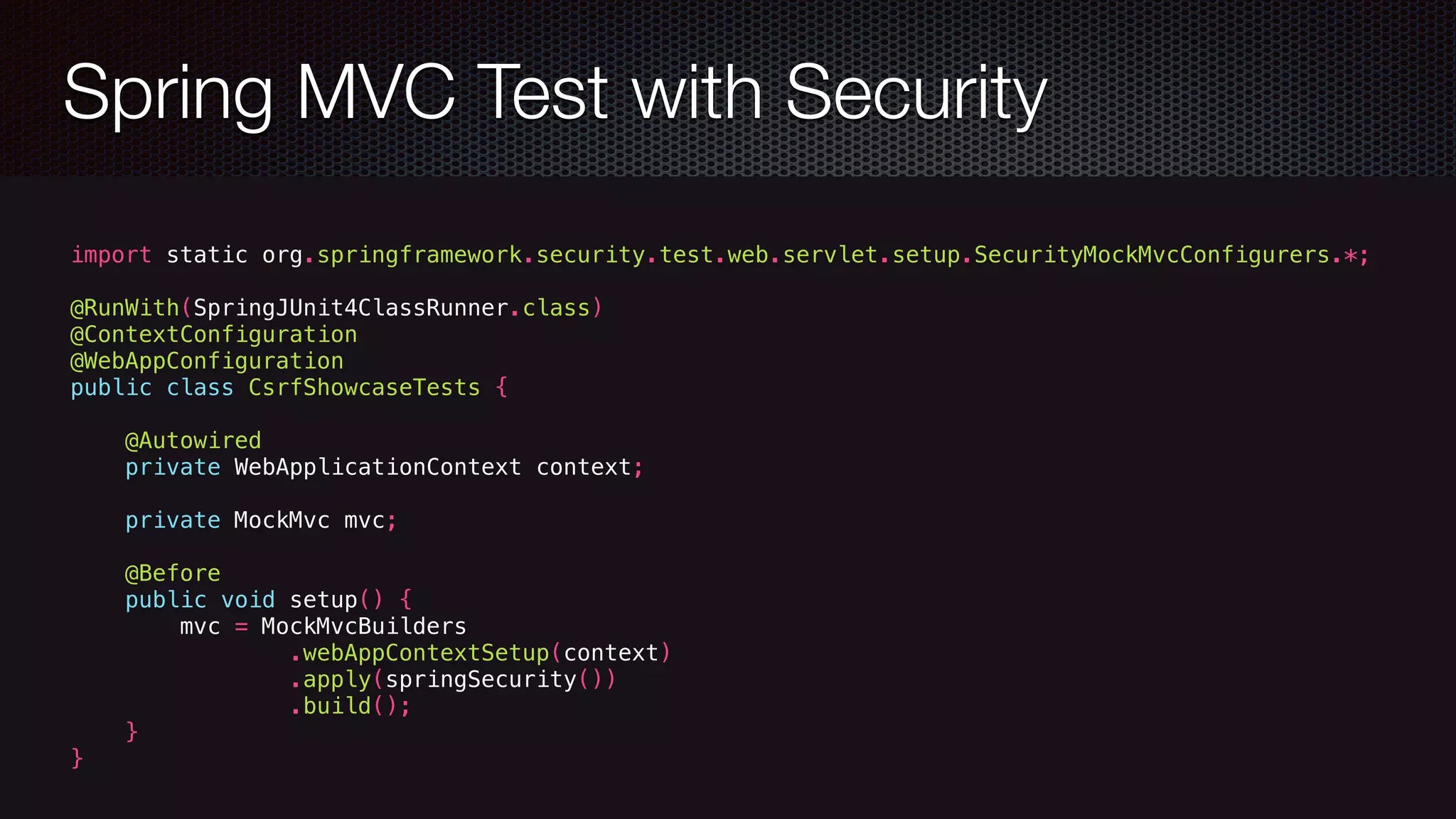
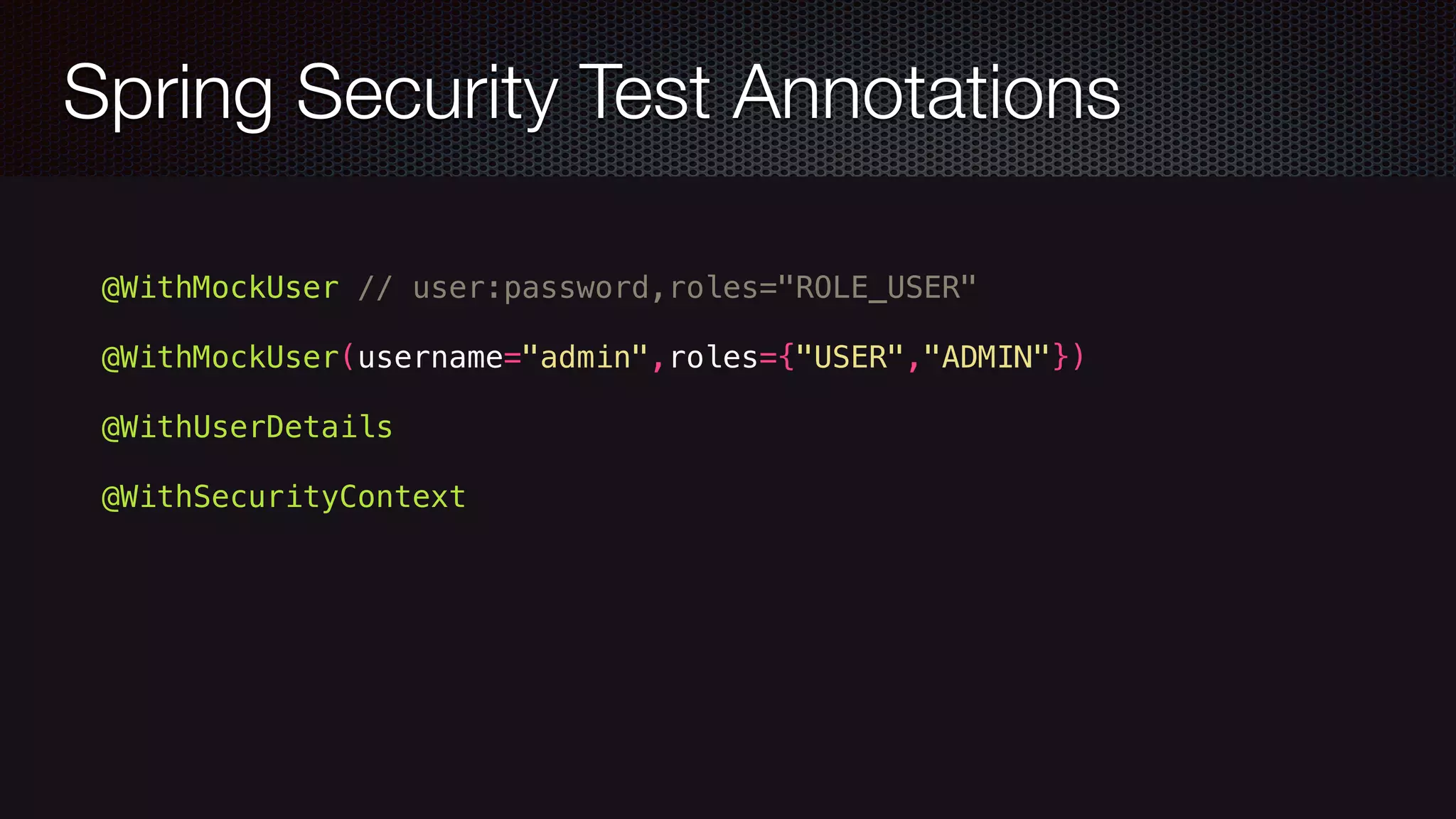
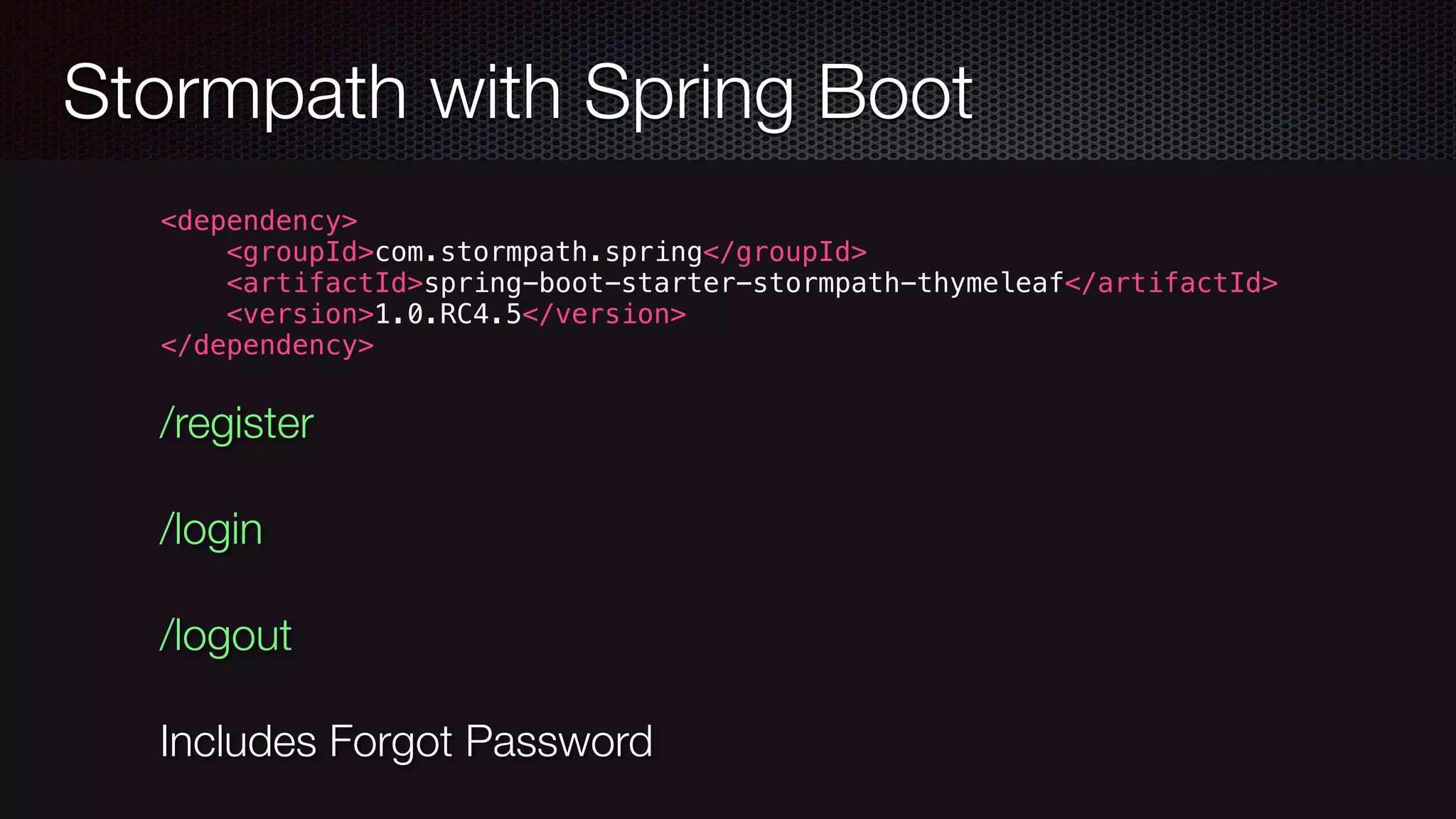
![Apache Shiro Filter defined in WebSecurityConfig URLs, Roles can be configured in Java Or use shiro.ini and load from classpath [main], [urls], [roles] Cryptography Session Management](https://image.slidesharecdn.com/javawebapplicationsecurity-uberconf2015-150723200955-lva1-app6892/75/Java-Web-Application-Security-with-Java-EE-Spring-Security-and-Apache-Shiro-UberConf-2015-23-2048.jpg)



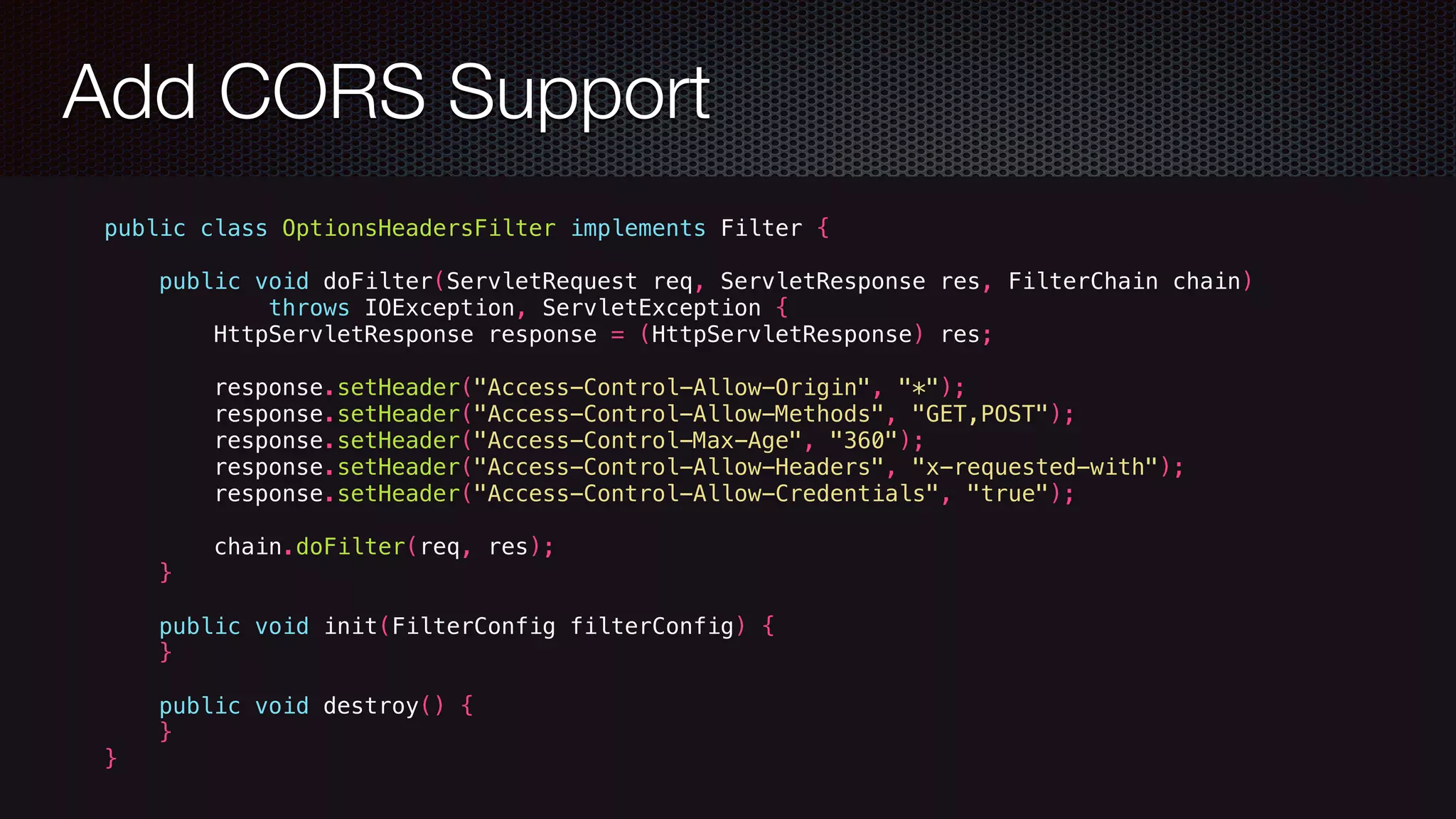


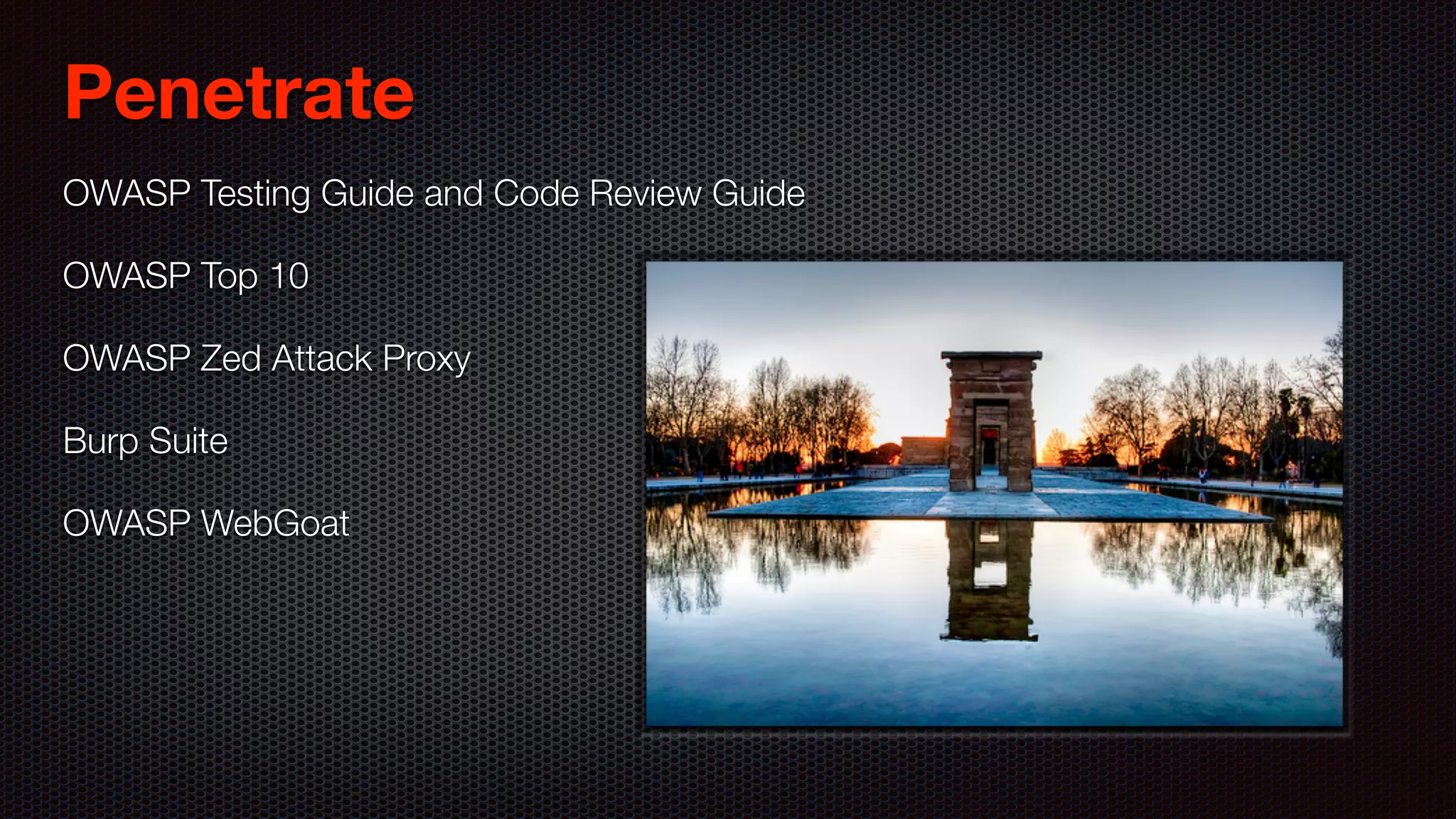


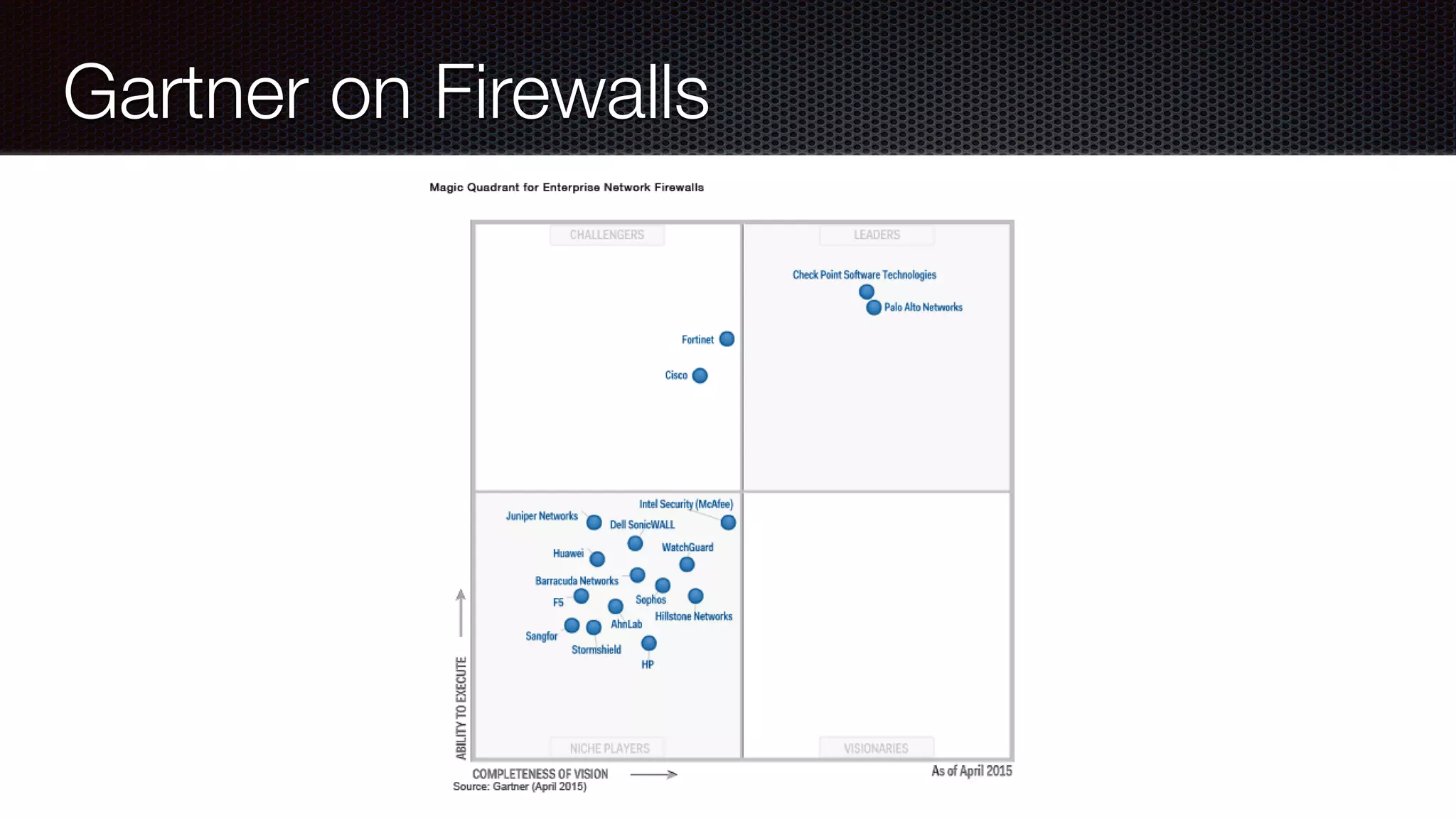
![Protect [SWAT] Checklist Firewalls IDS and IDPs Audits Penetration Tests Code Reviews with Static Analysis Tools](https://image.slidesharecdn.com/javawebapplicationsecurity-uberconf2015-150723200955-lva1-app6892/75/Java-Web-Application-Security-with-Java-EE-Spring-Security-and-Apache-Shiro-UberConf-2015-45-2048.jpg)
![[SWAT] Checklist http://software-security.sans.org/resources/swat](https://image.slidesharecdn.com/javawebapplicationsecurity-uberconf2015-150723200955-lva1-app6892/75/Java-Web-Application-Security-with-Java-EE-Spring-Security-and-Apache-Shiro-UberConf-2015-46-2048.jpg)