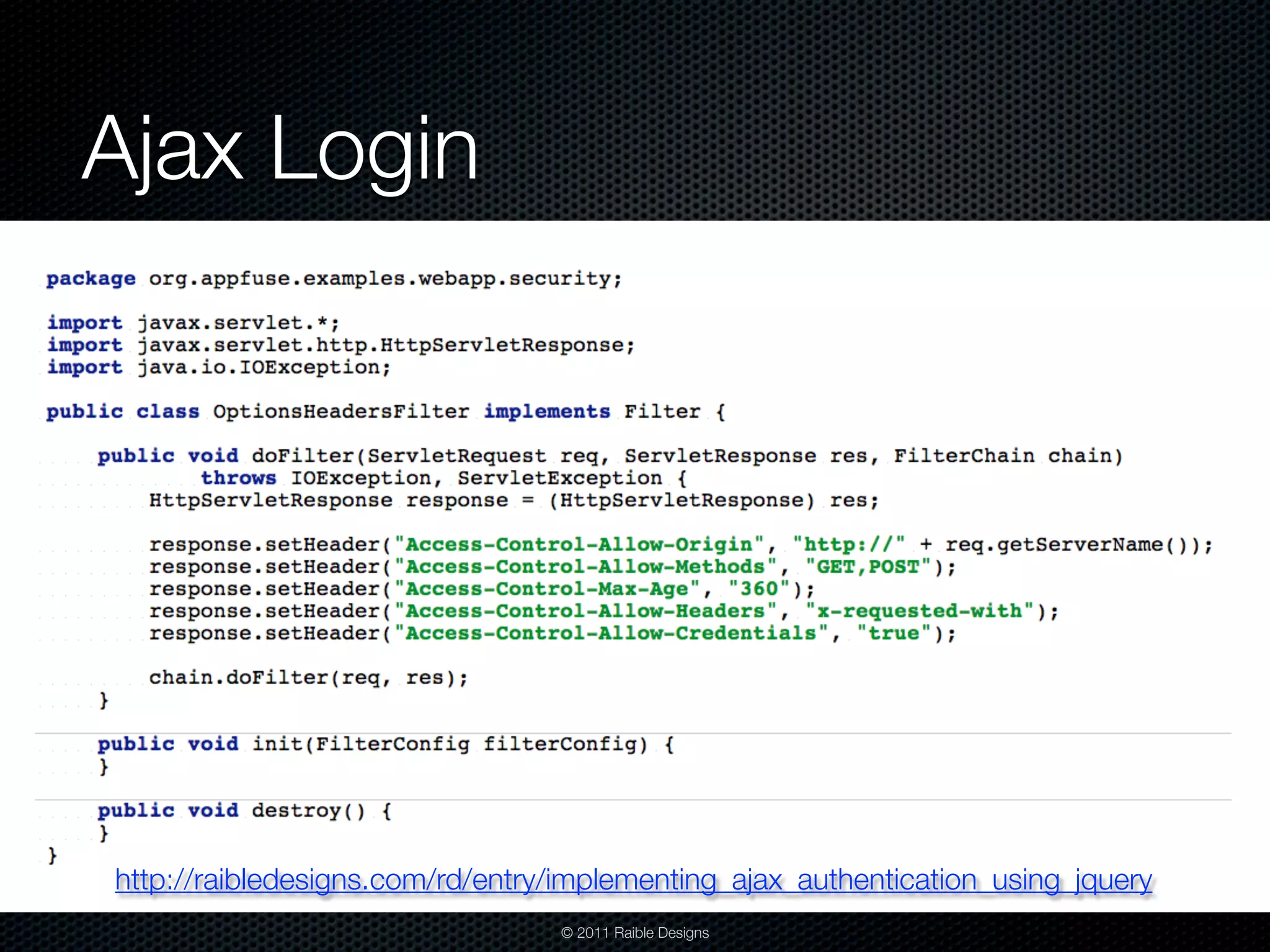
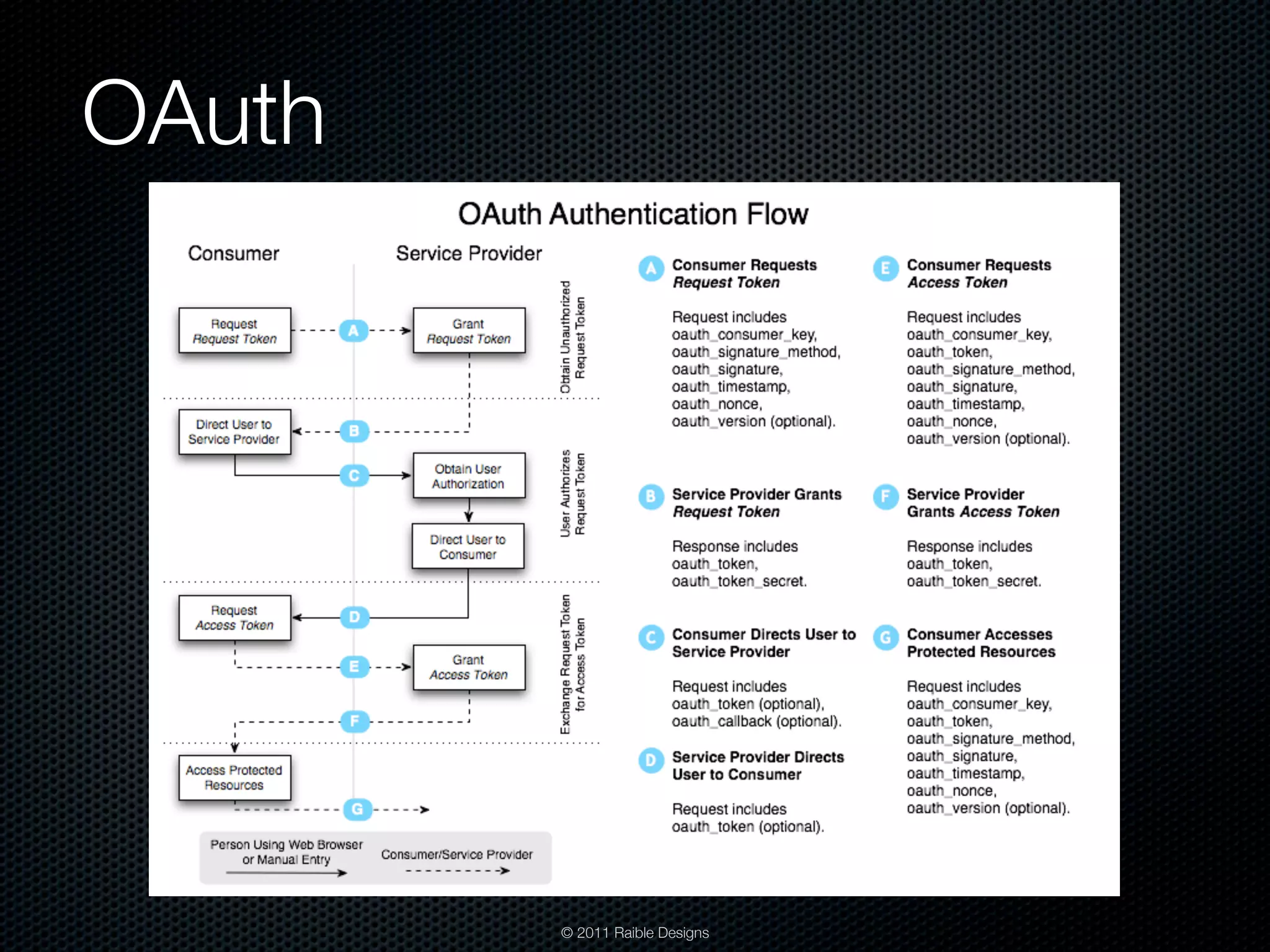
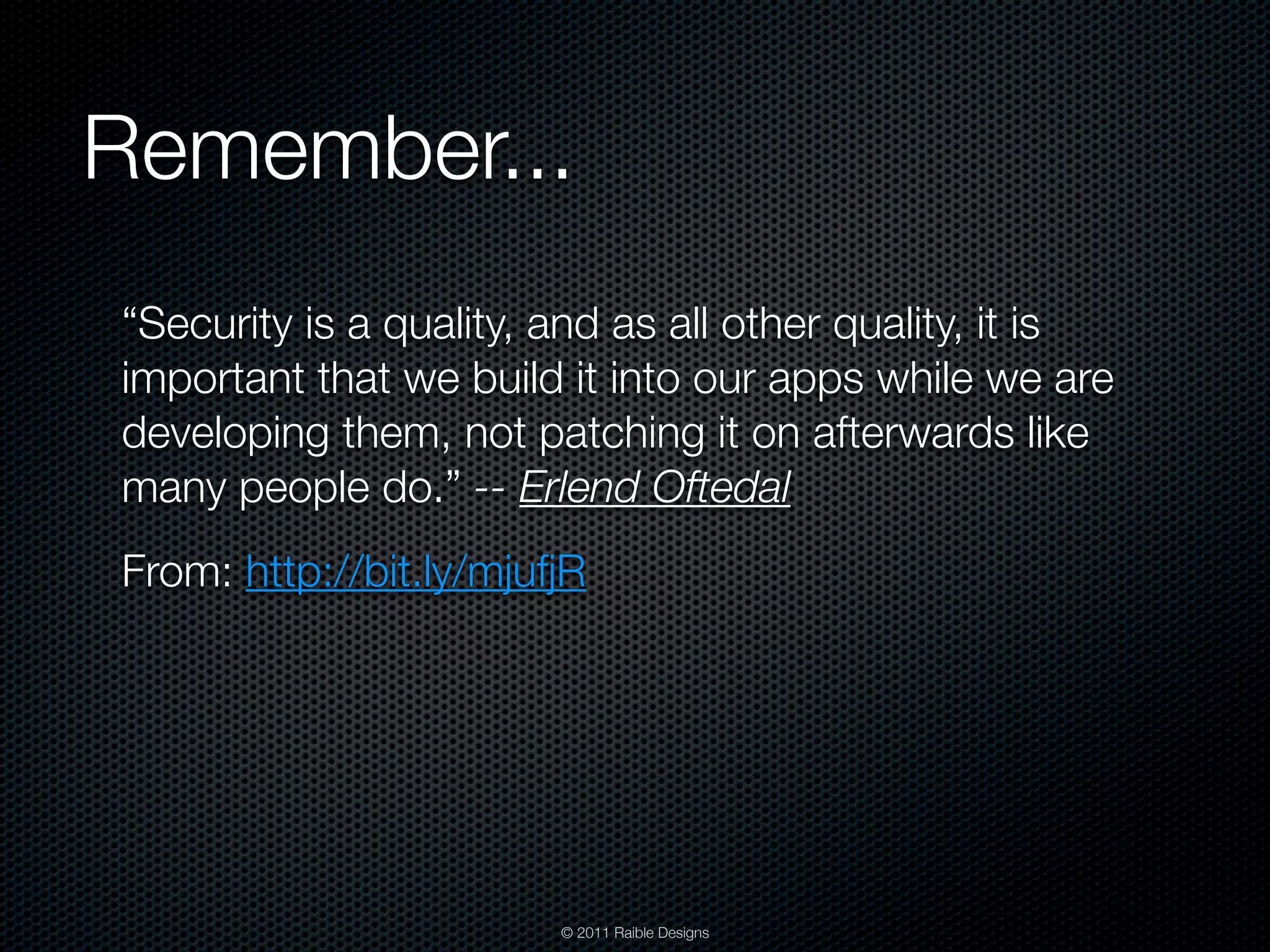
The document discusses Java web application security, outlining agenda topics including security development, penetration testing, and protecting applications. It explores frameworks like Java EE 6, Spring Security, and Apache Shiro, detailing their features and limitations. Additionally, it emphasizes the importance of integrating security in the development process rather than applying patches afterward.










![Securing Methods <global-method-security secured-annotations="enabled"/> @Secured("IS_AUTHENTICATED_ANONYMOUSLY") public Account readAccount(Long id); @Secured("IS_AUTHENTICATED_ANONYMOUSLY") public Account[] findAccounts(); @Secured("ROLE_TELLER") public Account post(Account account, double amount); <global-method-security jsr250-annotations="enabled"/> © 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityjazoon2011-110623122132-phpapp01/75/Java-Web-Application-Security-Jazoon-2011-15-2048.jpg)
![Securing Methods 3.0 <global-method-security pre-post-annotations="enabled"/> @PreAuthorize("isAnonymous()") public Account readAccount(Long id); @PreAuthorize("isAnonymous()") public Account[] findAccounts(); @PreAuthorize("hasAuthority('ROLE_TELLER')") public Account post(Account account, double amount); © 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityjazoon2011-110623122132-phpapp01/75/Java-Web-Application-Security-Jazoon-2011-16-2048.jpg)

![Apache Shiro Filter defined in web.xml shiro.ini loaded from classpath [main], [urls], [roles] Cryptography Session Management © 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityjazoon2011-110623122132-phpapp01/75/Java-Web-Application-Security-Jazoon-2011-18-2048.jpg)