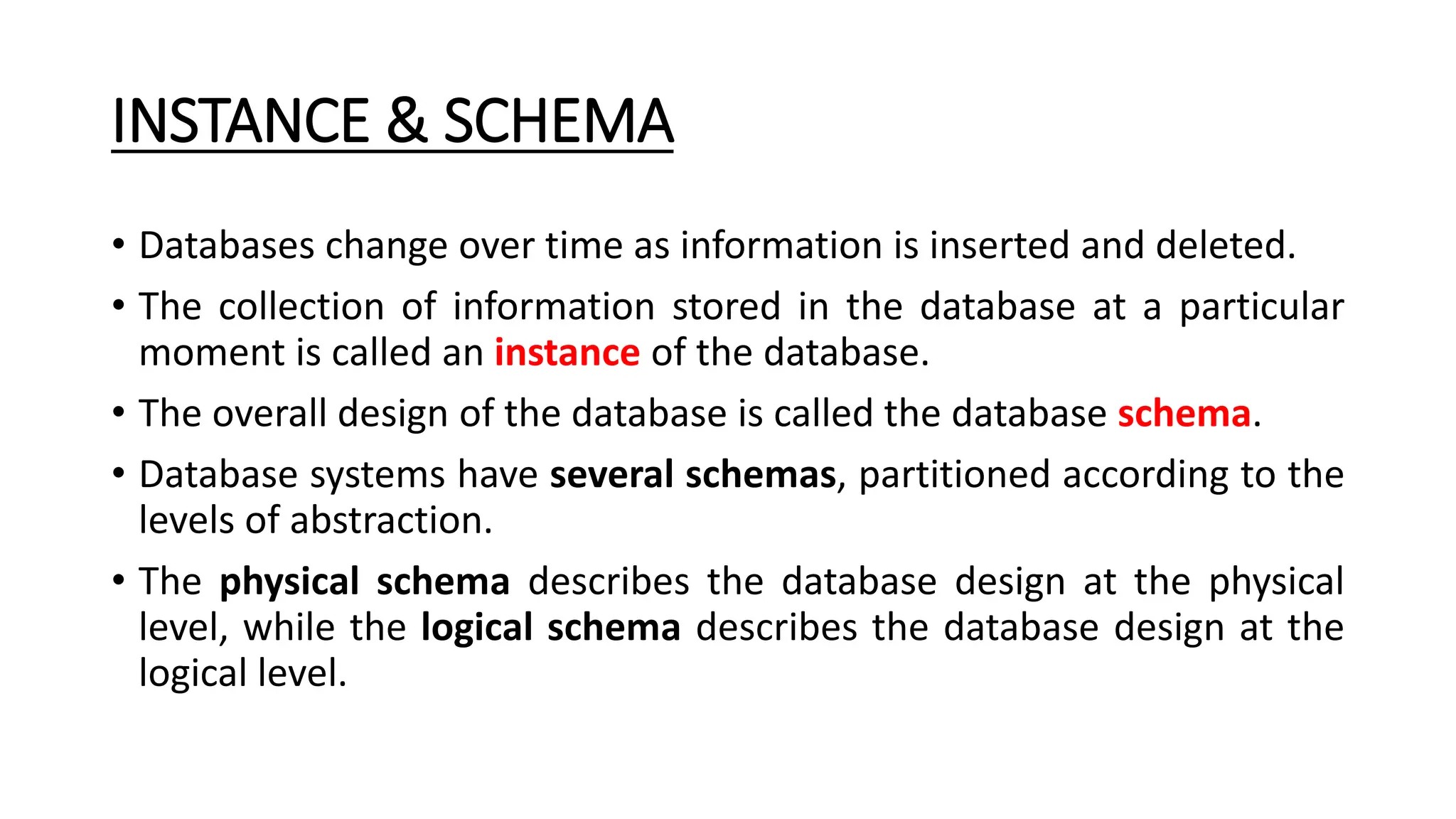
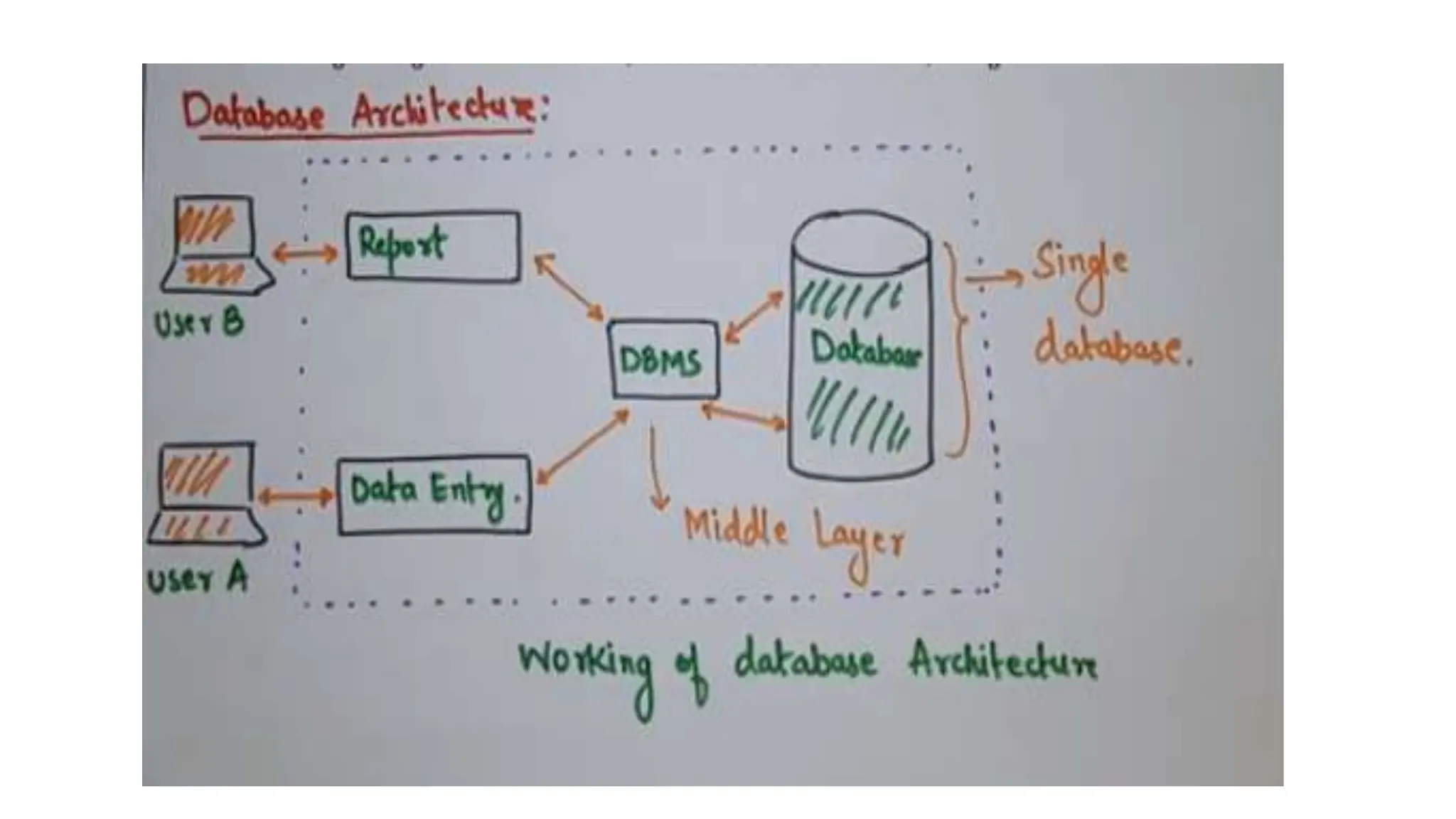
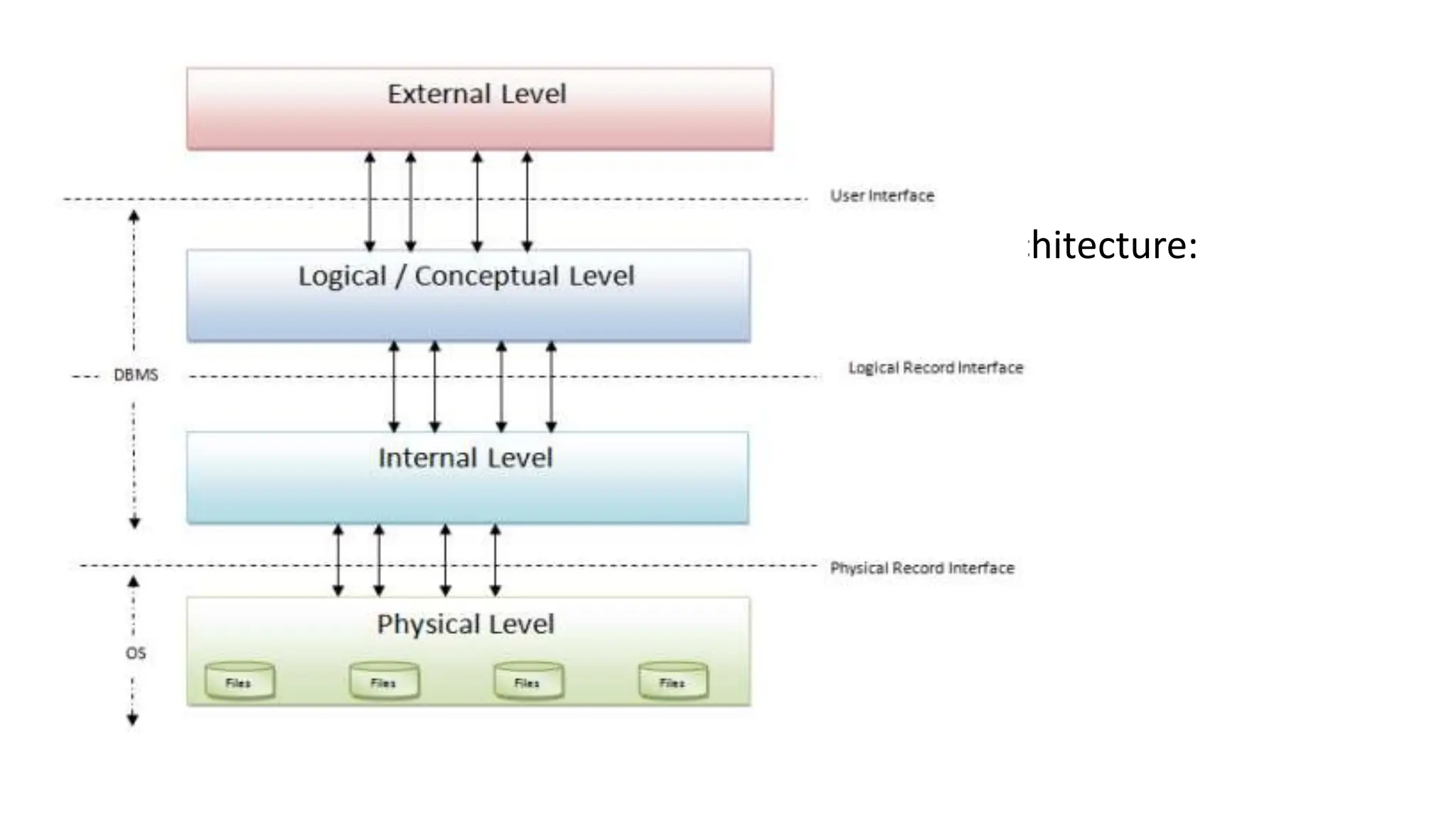
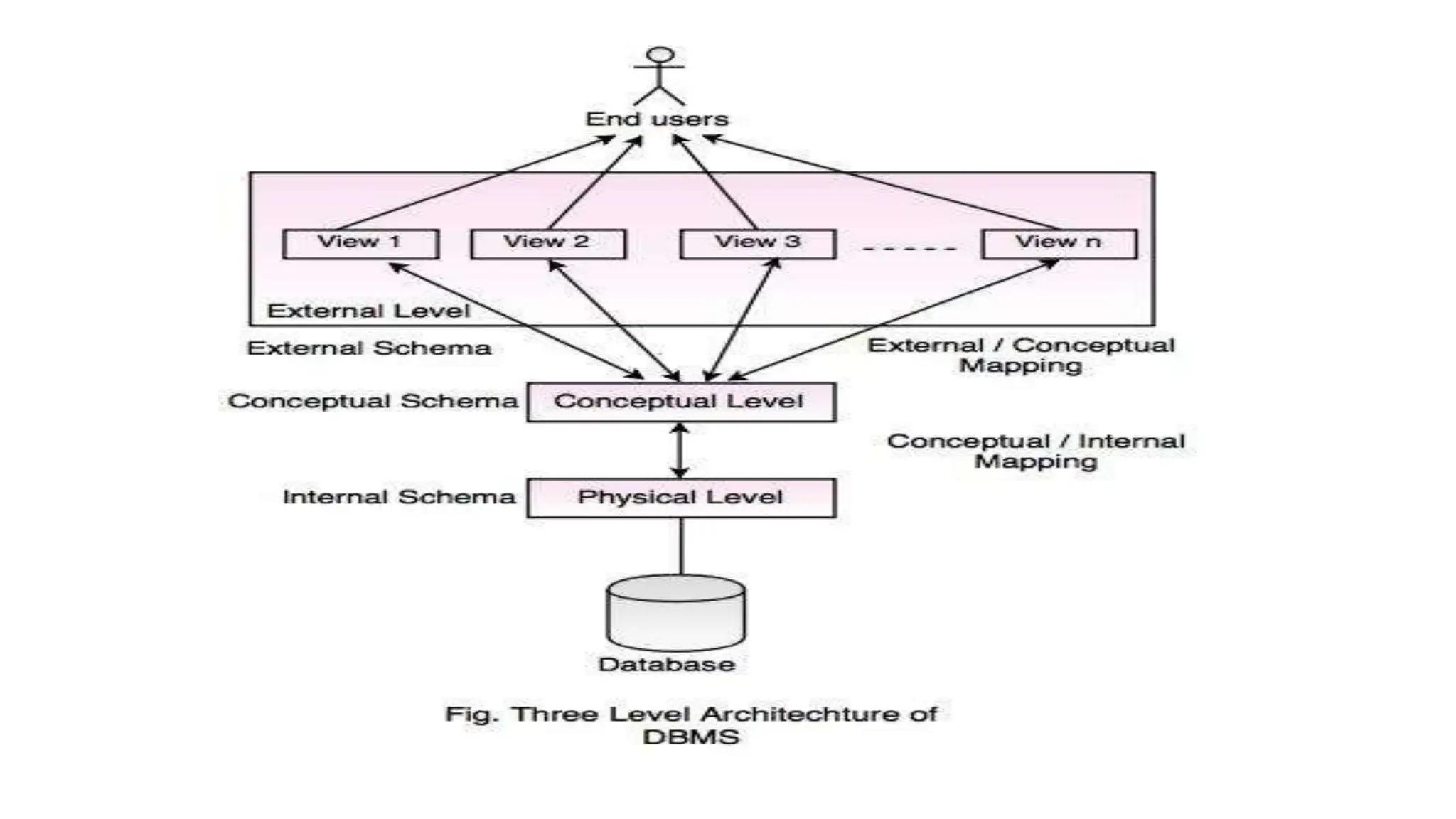
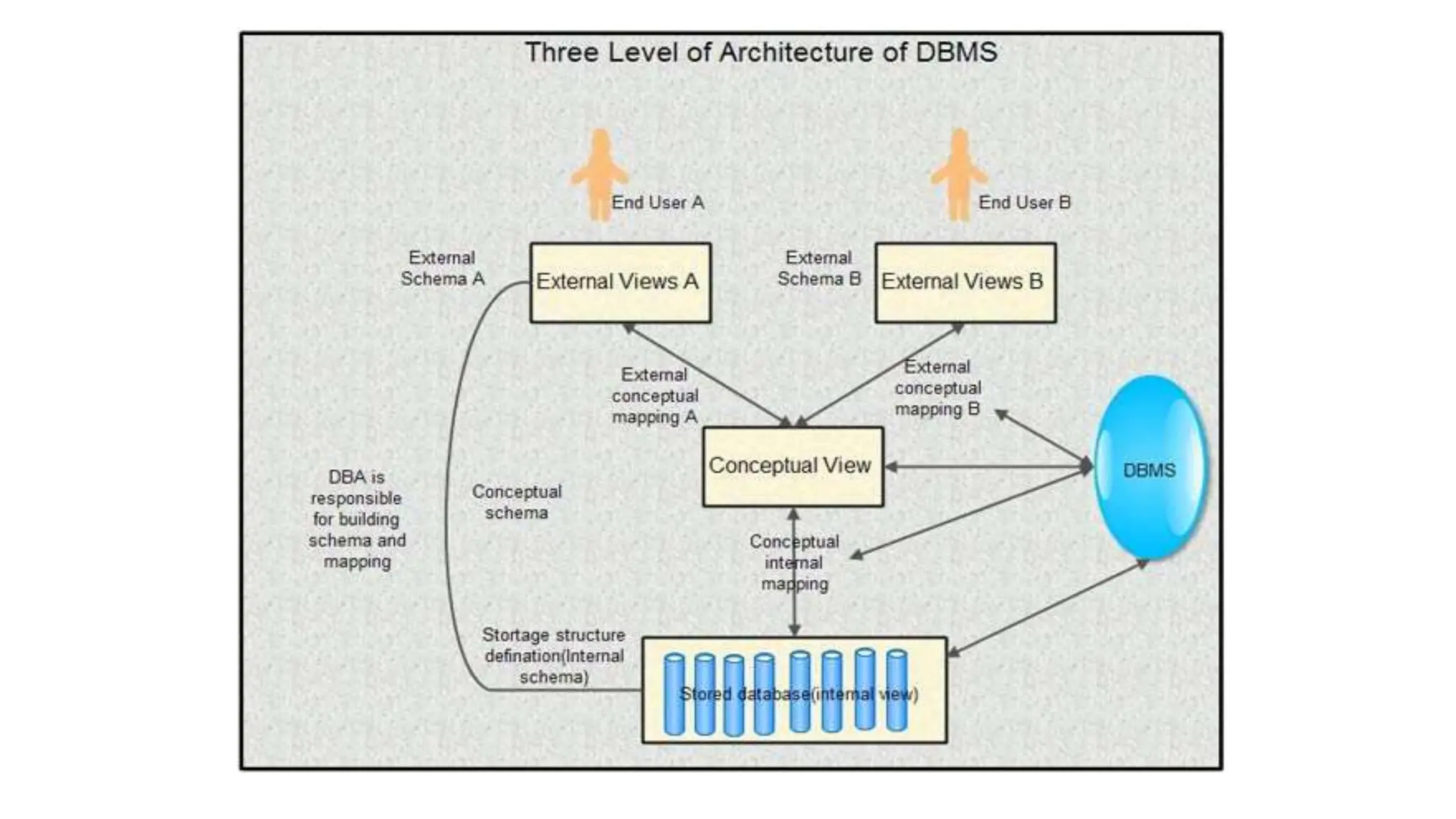
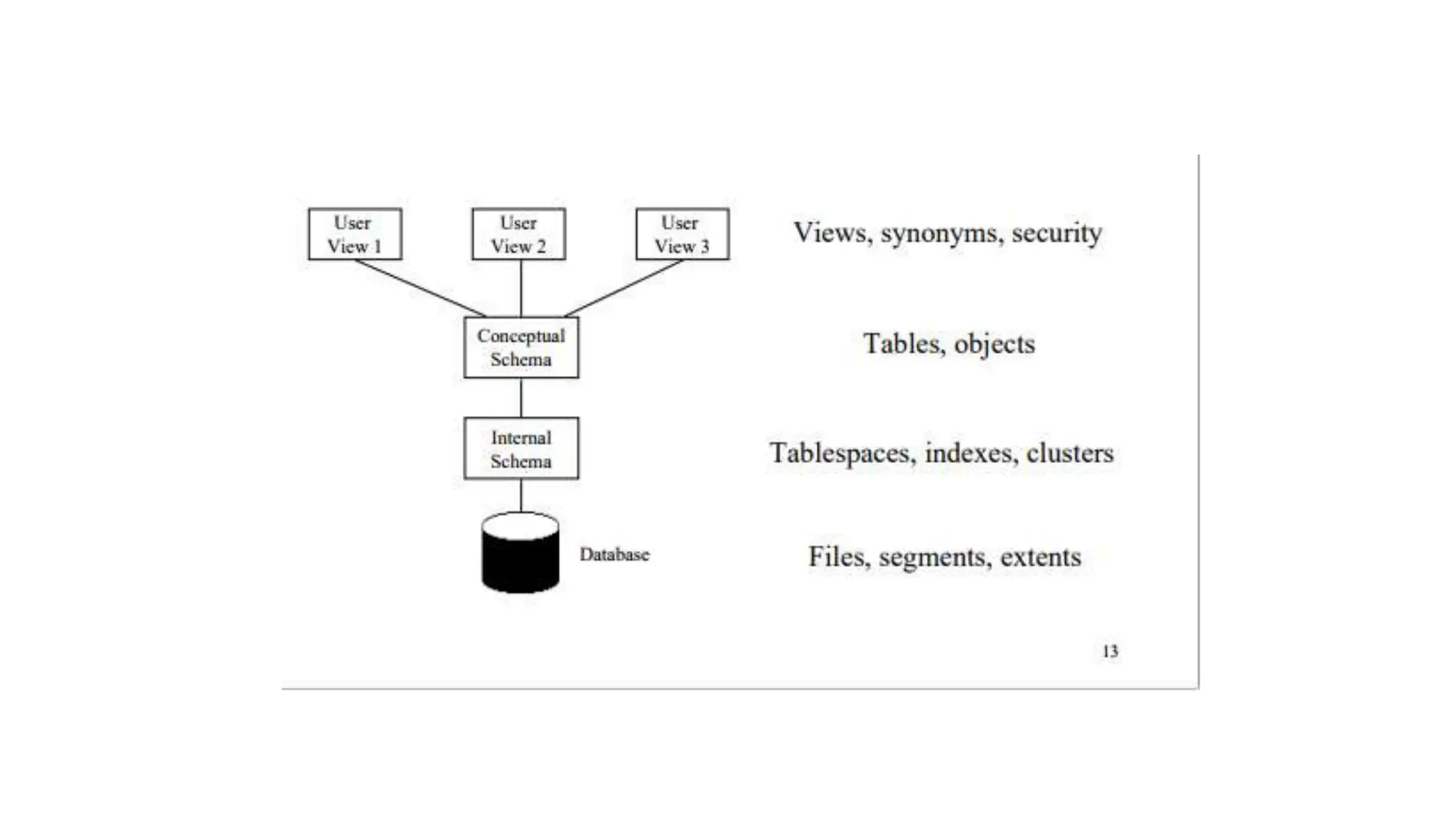
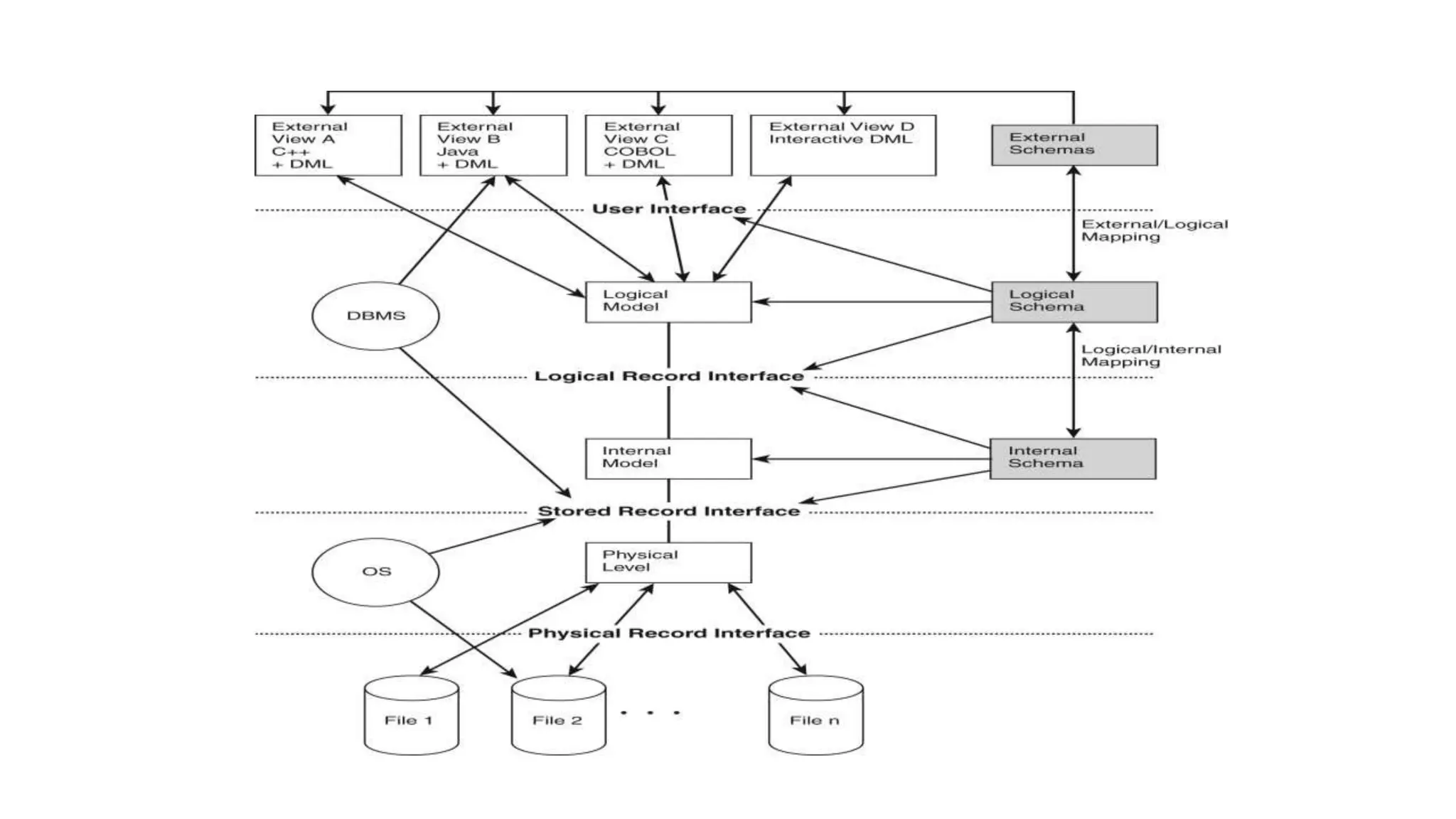
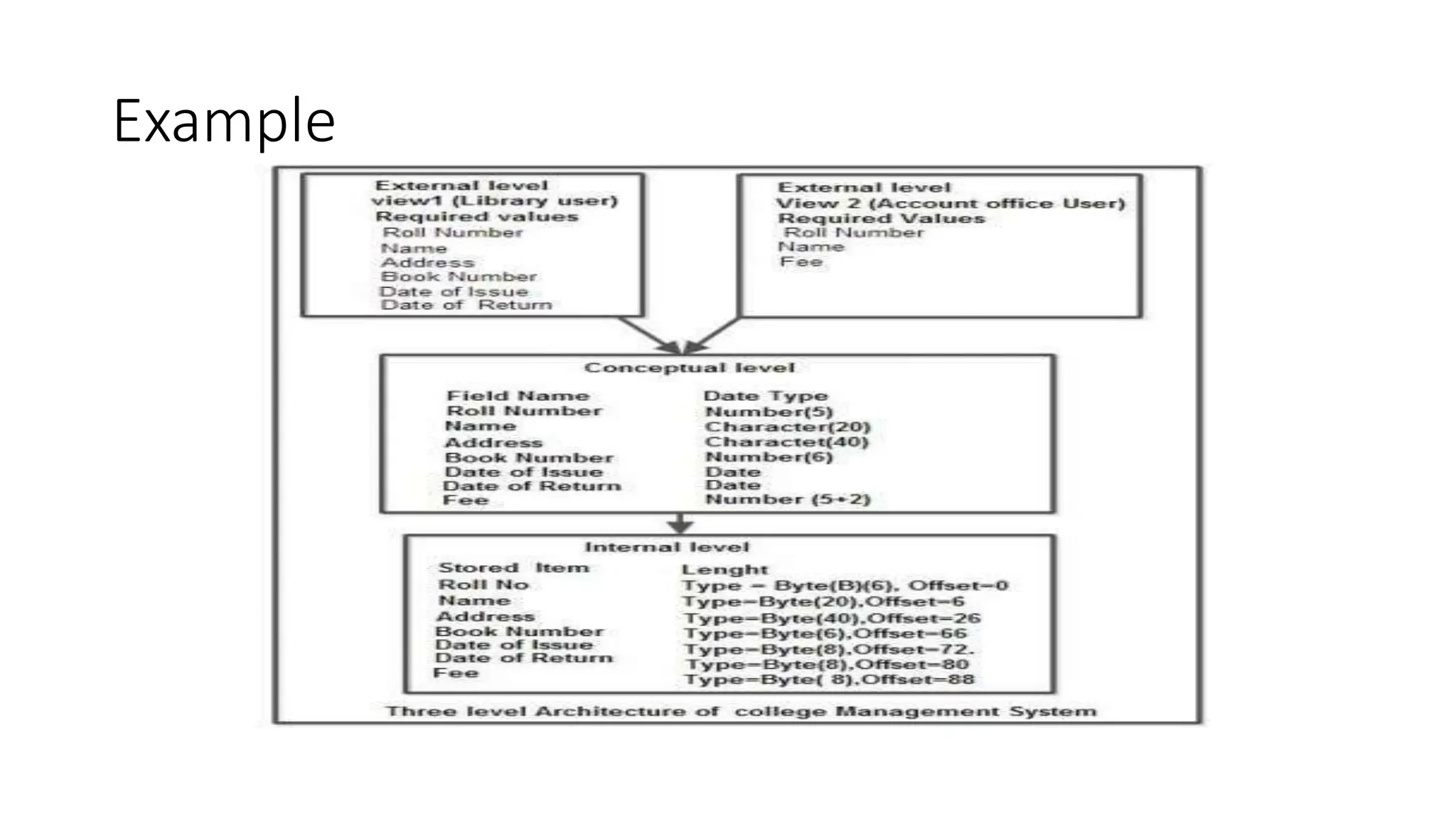
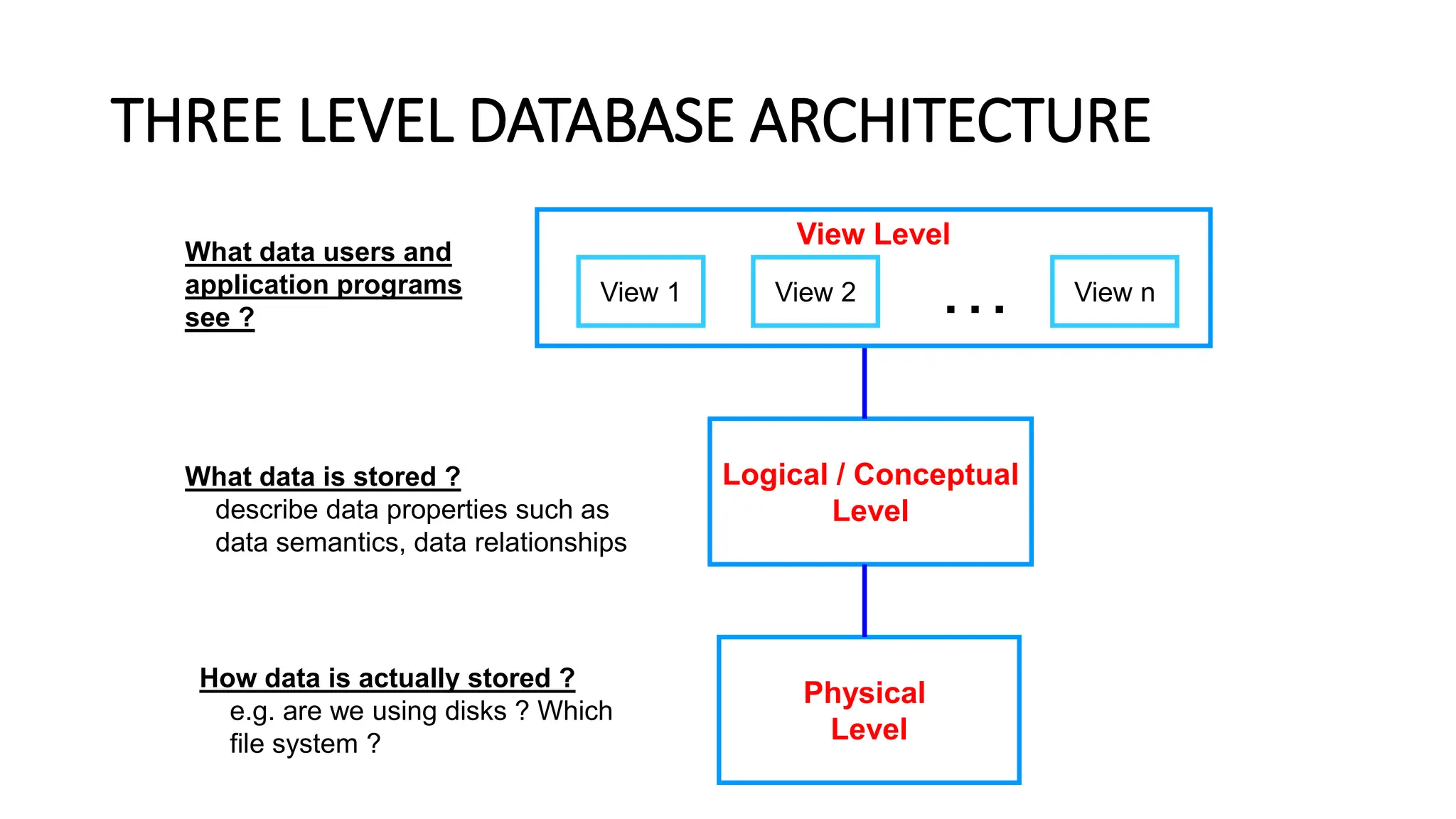
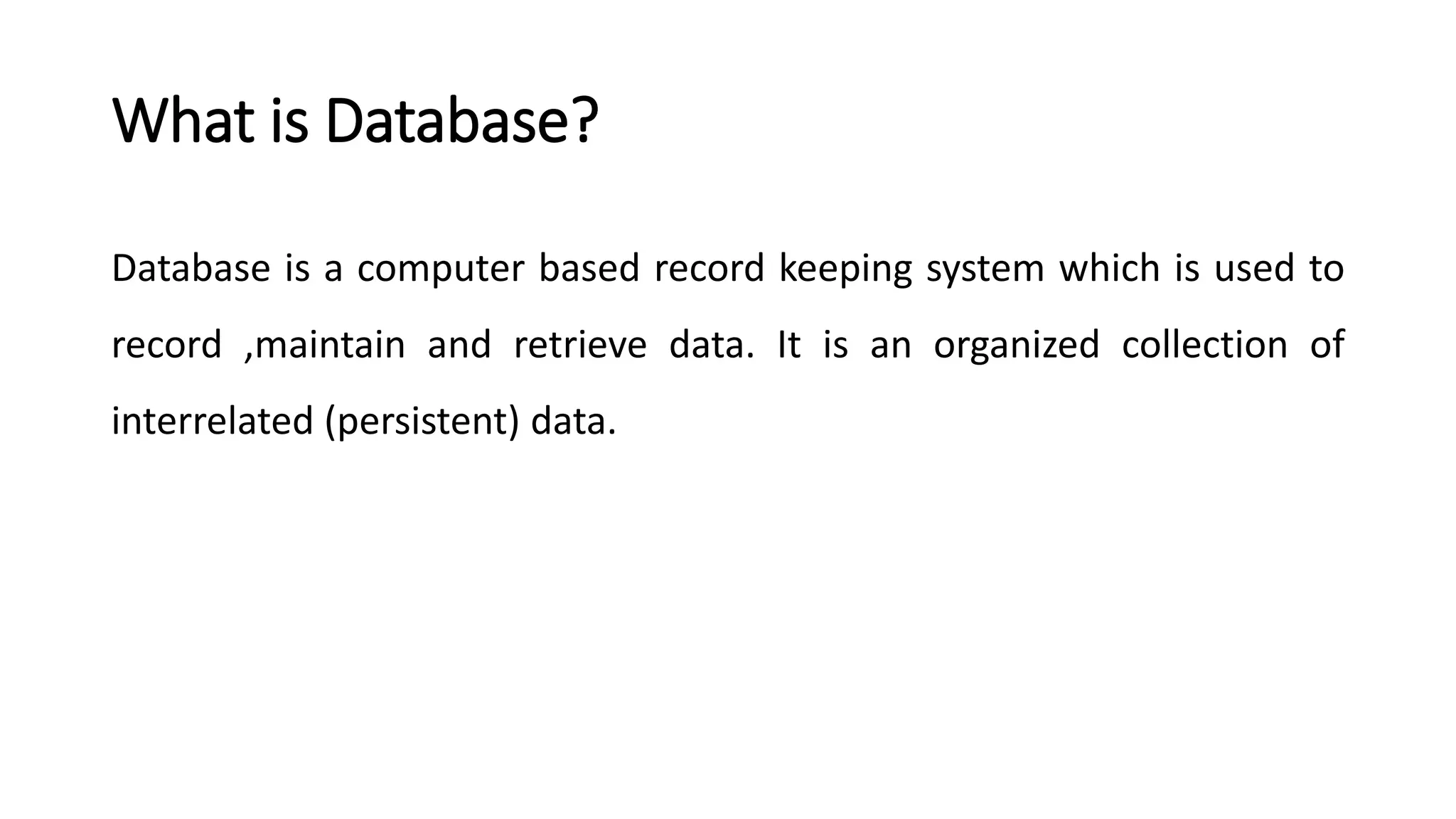
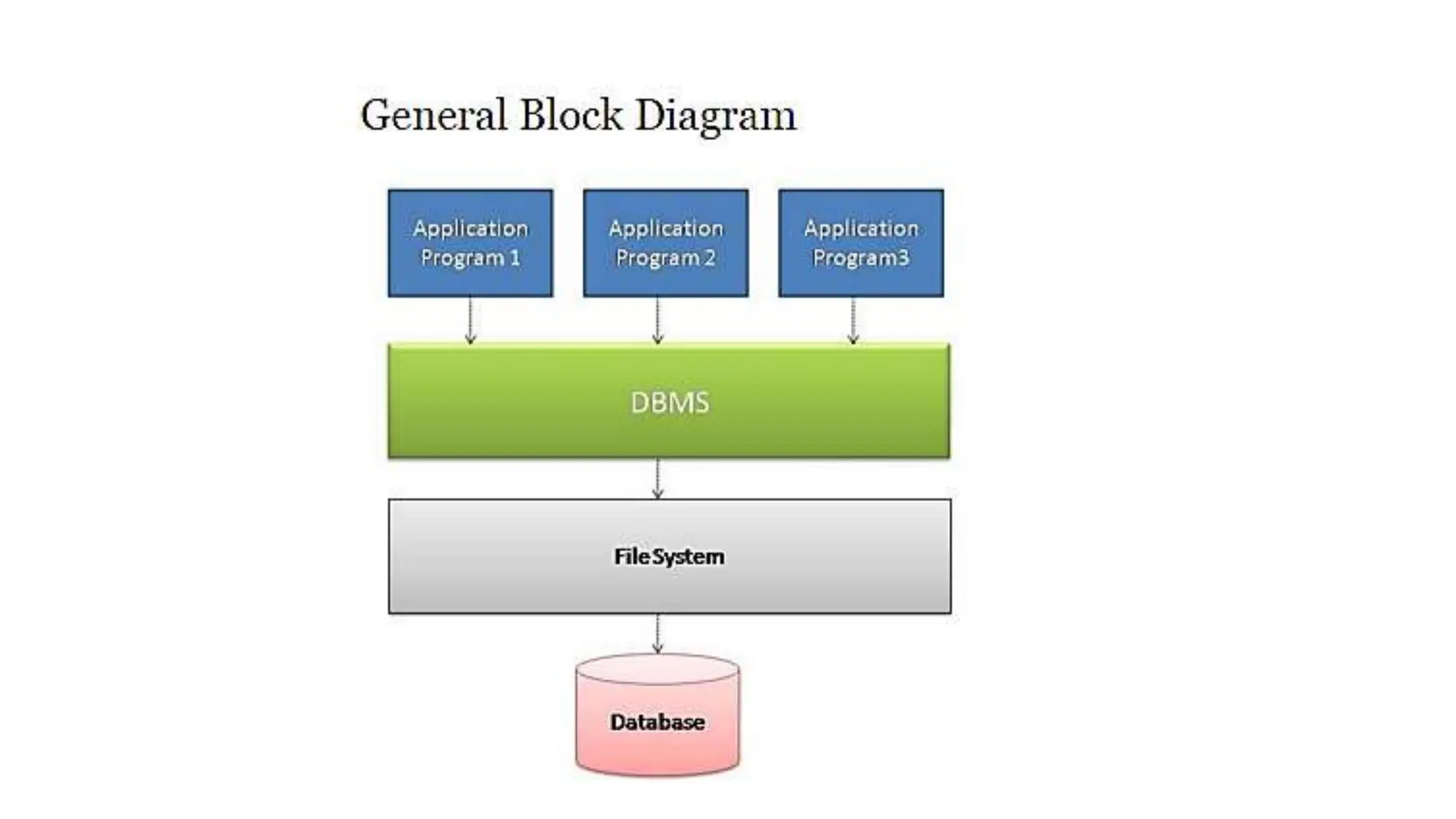
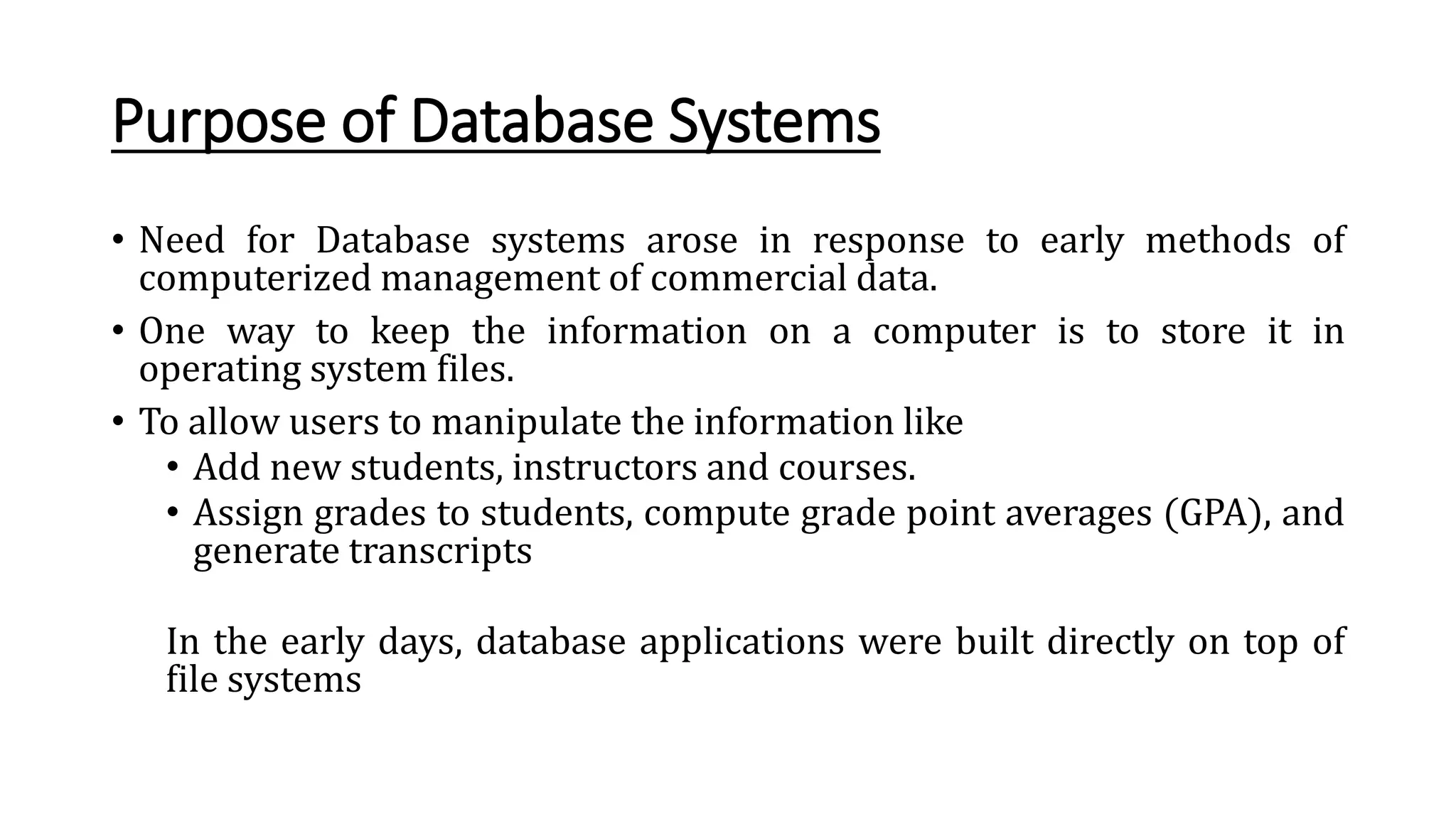
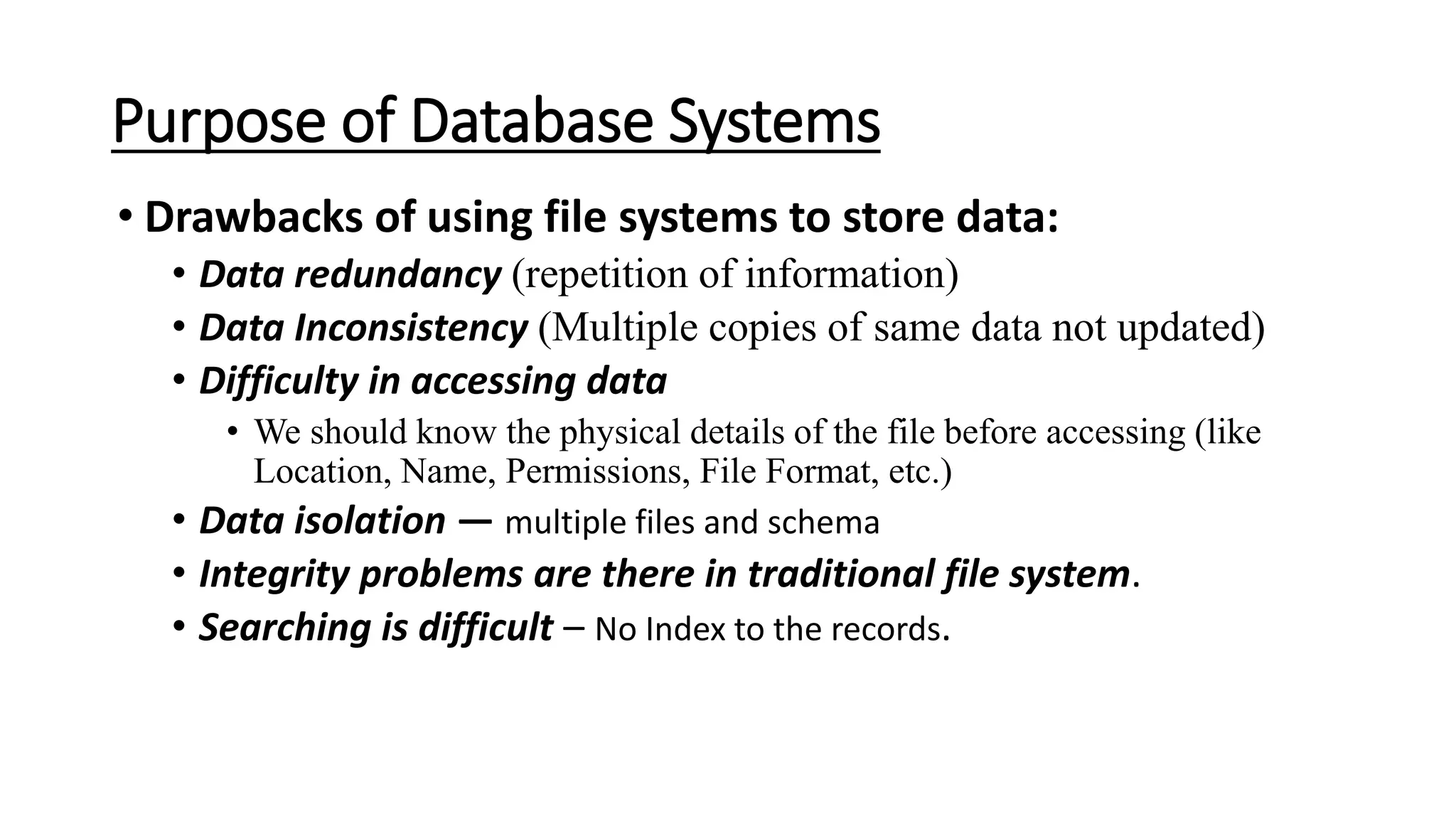
The document outlines the fundamental concepts of database systems, including what a database and a Database Management System (DBMS) are, and their roles in organizing, maintaining, and retrieving data. It discusses various components of DBMS, such as query processors, runtime database managers, and data managers, along with the types of database users and the hierarchical architecture of databases. Additionally, it emphasizes the issues related to traditional file systems and the advantages of databases in terms of data integrity, security, and user access management.





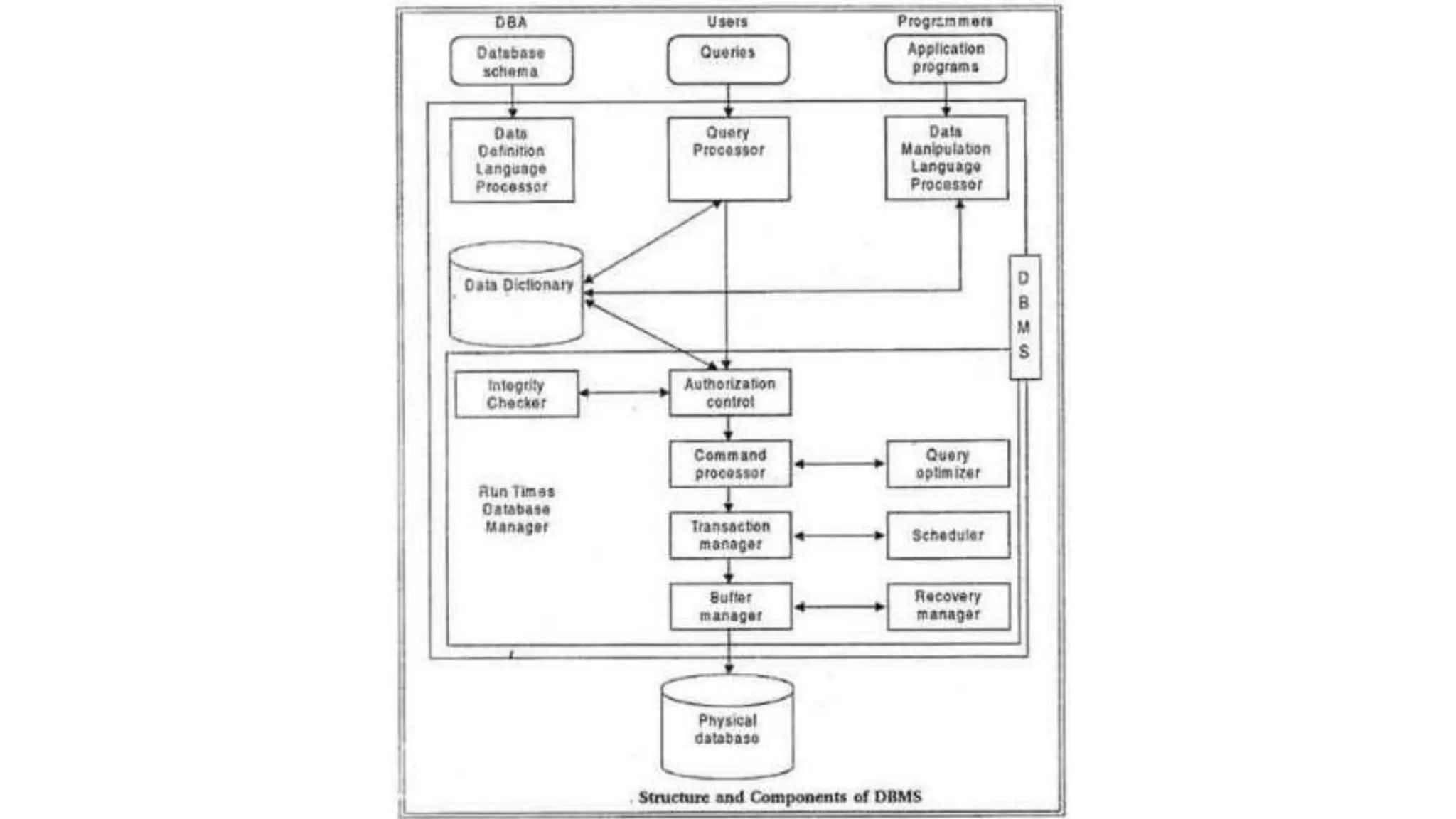
![Query Processor • It is used to interpret the online user query and converts into a form capable of being send to the data manager for execution. • The query processor use the data dictionary to find the structure of a database. • It is a program module that provides the interface between the database and the application programs/queries. • The Query Processor Components include – • Data Definition Language(DDL) Compiler(Create, Alter[Add, Drop, Modify], Drop, Describe) • Data Manipulation Language (DML) compiler(Insert, Update, Select) • Query evaluation engine](https://image.slidesharecdn.com/dbmsunit1-240709160856-0aafe3e0/75/Introduction-of-database-management-system-12-2048.jpg)