The paper discusses a hardware implementation of speech data encryption and decryption using the AES algorithm along with speech recognition techniques. It elaborates on using FPGA and ASIC for enhanced security in data transfer across various sectors, detailing the design, functionality, and results of both encryption and speech recognition processes, while highlighting resource optimization achieved during implementation. The conclusion suggests further improvements in speech recognition accuracy and design efficiency for high-end applications.
![FPGA and ASIC Implementation of Speech Encryption and Decryption using AES Algorithm with Speech Recognition Jagannatha K.B, Yogesh Y.L, Vadiraja Desai H.S, Shreyas G.S, Shivananad Hachadad Department of ECE, BMSIT&M Bangalore-560064, India Email id: jagan@bmsit.in Abstract - With increasing technology development in field of communication and Electronic devices, there is a need for better security service for information transfer in Medical Sectors, Banking, Financial and in other IoT applications etc. Fight against security attacks is of prime importance. Through Cryptographic techniques we can provide Authenticity as well as Confidentiality for the user data. In this paper, hardware implementation has been described for a real-time application of speech data encryption and decryption using AES algorithm along with the speech recognition using cross correlation technique. Verilog programming environment is used for AES cryptography whereas MATLAB is used for Speech recognition. ASIC design on AES core is implemented using Cadence tools. Number of gates, area and power used by AES core design has been drastically reduced by specifying wide range of constraints during front end designing. In Backend designing, layout of AES design, which is the physical geometric representation is also developed. Keywords— Advanced Encryption Standard (AES), Field programmable gate-array (FPGA), Application specific integrated circuit (ASIC), Speech Recognition, Cross-Correlation I. INTRODUCTION Security and privacy happens to be the two major aspects of ever-growing speech communication system. Shadow Brokers, WannaCry, Goldeneye, Cloudbleed are some of the Biggest Cybersecurity Disasters so far. Speech cryptography is the method of sending information which has been spoken in a masked way by carrying out encryption of data at transmitter end and decryption at receiver end. Cryptography is a method used to detect the masked messages. Encryption involves scrambling of the original data, and the reverse process constitutes decryption [2]. Speech recognition comes under the field of computing language which is used to develop methods and technology which can be used for enabling the recognition and translation of spoken language into text by the computer [6]. The speech file obtained will be encrypted on an FPGA. Then the encrypted file will be transferred to another FPGA for decryption which is in turn transferred to a computer in which original speech is recovered using the MATLAB. Cross correlation technique can also be used to carry out speech recognition through MATLAB [7]. Block diagram which describes the functionality of the system is as shown in figure 1. Samples of Speech signal is acquired using MATLAB and are stored in .txt file. These samples are passed on to an FPGA module(NEXYS 4 DDR fpga) to carry out the encryption. Receiver side represents the FPGA decryption module(NEXYS 4 DDR fpga) to which the encrypted samples are sent. Both fpga modules can be connected through RS232 communication link [4]. Decrypted samples represents are the original speech samples. If these samples are read through MATLAB at specified bit rate, user speech is obtained. Cross correlation technique is used to pass this user speech through speech recognition system . This paper is organized as follows where Section II gives a brief introduction of Cryptography, AES and Speech Recognition. Section III describes the simulation results obtained with respect to MATLAB and FPGA. The ASIC implementation is discussed in section IV. The paper is concluded in section V. International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 180 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-1-2048.jpg)
![Figure 1. Block diagram of the proposed system II. DESIGN A. Cryptography Cryptography is defined as the method of creating codes which allow the information to be hidden. It converts the original data of the user into a unreadable format for an unauthorized user, due to which the unauthorized readers cannot decode it .Information security field makes use of cryptography in different aspects. A key is very essential to decrypt the user information. Integrity and privacy of the information is conserved both during transmission and storage. Symmetric and Asymmetric Cryptography happens to be the two types of cryptography. Asymmetric cryptography or public key cryptography, uses both public and private keys for encryption and decryption of data. Encryption of plain text and decryption of cipher text is done using the same symmetric key algorithms. AES happens to be a Symmetric Key cryptographic algorithm. B. AES algorithm AES works on a 4 × 4 column-major order matrix of bytes, which are called "state". Depending on the version used to convert the plain text into the cipher text,the key size varies. The number of rounds constituting repetition are as follows: Ten rounds for 128-bit keys. Twelve rounds for 192-bit keys. Fourteen rounds for 256-bit keys. Each round contains several processing steps, where each step contains four similar but different stages which includes one that depends on the key for encryption . Reverse set of rounds are applied to convert cipher text back to the plain text by using the same encryption key [5]. Four steps of AES are as follows:- 1. SubBytes—It is a substitution step, where each byte is replaced with an another byte based on the predefined S-box. 2. ShiftRows—Here four rows will be left shifted cyclically by 0 ,1 ,2 and 3 bytes respectively . 3. MixColumns—It is a mixing operation, galois field multiplication takes place on each column of the state, generating a new state as output . 4. AddRoundKey—In this step, Bitwise xor operation is carried out between each byte of the state and the round key. Since, AES-128 bit version is used here, initial 128 bit key is expanded to 1408 bits needed for 10 rounds of operation using Key expansion algorithm.AES utilizes key expansion process in which all round keys are generated from single 128-bit cipher key to create round key for each round. The keys that are generated are of 128-bits length each. All the rounds are symmetric in nature and key expansion process is used to eliminate the symmetry by having round dependent round constants. The possibility of International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 181 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-2-2048.jpg)
![equivalent keys is eliminated by nonlinearity of key expansion. There is no need for the mixing transformation in the last round of encryption. The Last round of encryption module outputs a 128-bit cipher text. Decryption happens to be the inverse process of encryption which involves inverse round transformations which are applied to cipher text in order to get back the original data. Flow is described in the Figure 2 below. Figure 2. AES-128 bit Encryption and Decryption Flow C. Speech Recognition Speech Recognition is defined as the method of capturing the spoken words using a microphone and hence converting the voice signal into a digitally stored set of data. Speech recognition is used widely in most of the security project where there is a need to tell your password to devices like computer to provide access to system applications. The measure of similarity of two series as a function of displacement of one relative to the other is called as Cross correlation [8]. It can also be called as the sliding dot-product or the sliding inner-product. It is commonly utilized for searching a long signal for a shorter one. Pattern recognition for single particle analysis also finds applications in cross correlation. The xcorr function of MATLAB happens to be a Cross-correlation function for a random process which includes autocorrelation. Syntax for Correlation in MATLAB can be written as r = xcorr(x,y) where r = xcorr(x,y) returns the cross-correlation of two discrete-time sequences which are named x and y. D. Algorithm describing Speech Recognition using Cross- Correlation technique Consider sample as voice where x=voice Read and compute x and store in y1. Consider total of 4 samples containing different voice data [8]. 1) z1=xcorr(x.y1), m1=max(z1) 2) Repeat steps 1 for all 4 samples.
3) Consider a=[m1 m2 m3 m4 m5] where m5=300 ,m5 is the threshold. 4) Compute m=max(a)
5) If m<=m1 read 1st file 6) elseif m<=mi, read ith file where 1<i<5 7) else read denied file 8) End International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 182 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-3-2048.jpg)
![III. RESULTS AND DISCUSSION The functional design code was written using Verilog HDL (Hardware Description Language)and synthesised in Vivado Design Suite. The proposed design has been implemented on NEXYS 4 DDR (XC7A100T-CSG324) boards [1] & [3]. VIO (Virtual Input Output) debugging tools were used in implementation. Simulation results of encryption module and decryption module are as shown in Figure 3. and Figure 4. respectively. The resource utilization details of FPGA by encryption system and decryption system are mentioned in Table 1. A. AES ENCRYPTION Figure. 3 Simulation Results of AES Encryption on NEXYS 4 DDR B. AES DECRYPTION Figure. 4 Simulation Results of AES Decryption on NEXYS 4 DDR. Resource Estimation Available Utilization LUT 2365 63400 3.73% FF 1548 12080 1.22% IO 1 210 0.48% BUFG 1 32 3.13% Table 1 - Resource Utilization Table with respect to NEXYS 4 DDR fpga International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 183 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-4-2048.jpg)
![C. Speech Recognition Results The graphs for comparison between the test and the sample audio files is derived using MATLAB [8]. Two of the test files and four of the sample files which has speech (Spoken word) of one to four are considered. One of the test file will have a match from four sample files and another test file has no match with any of the stored sample files. The loop starts which takes test file as input cross correlated with other samples and the output graph is displayed using MATLAB. So, after cross correlatiing with 4 other samples we will have four output graphs as shown below ) MATLAB.The results have been described in figure 5(a) below. Test.wav vs One.wav Test.wav vs Second.wav Test.wav vs Third.wav Test.wav vs Fourth.wav Figure 5(a). Speech Recognition Test Case 1 N ) y W MATLAB command prompt, the comparison will start and it will tell denied which means the file is not matching with any of the sample files.Results for this case is described in below figure 5(b). . Ten.wav vs one.wav Ten.wav vs second.wav Ten.wav vs third.wav Ten.wav vs fourth.wav Figure 5(b). Speech Recognition Test Case 2 Cross correlation technique works on pattern matching and is not the ideal solution for speech recognition. If two different signals with similar pattern undergo cross correlation it may give wrong results. So enhanced speech recognition system should be implemented [6]. International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 184 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-5-2048.jpg)
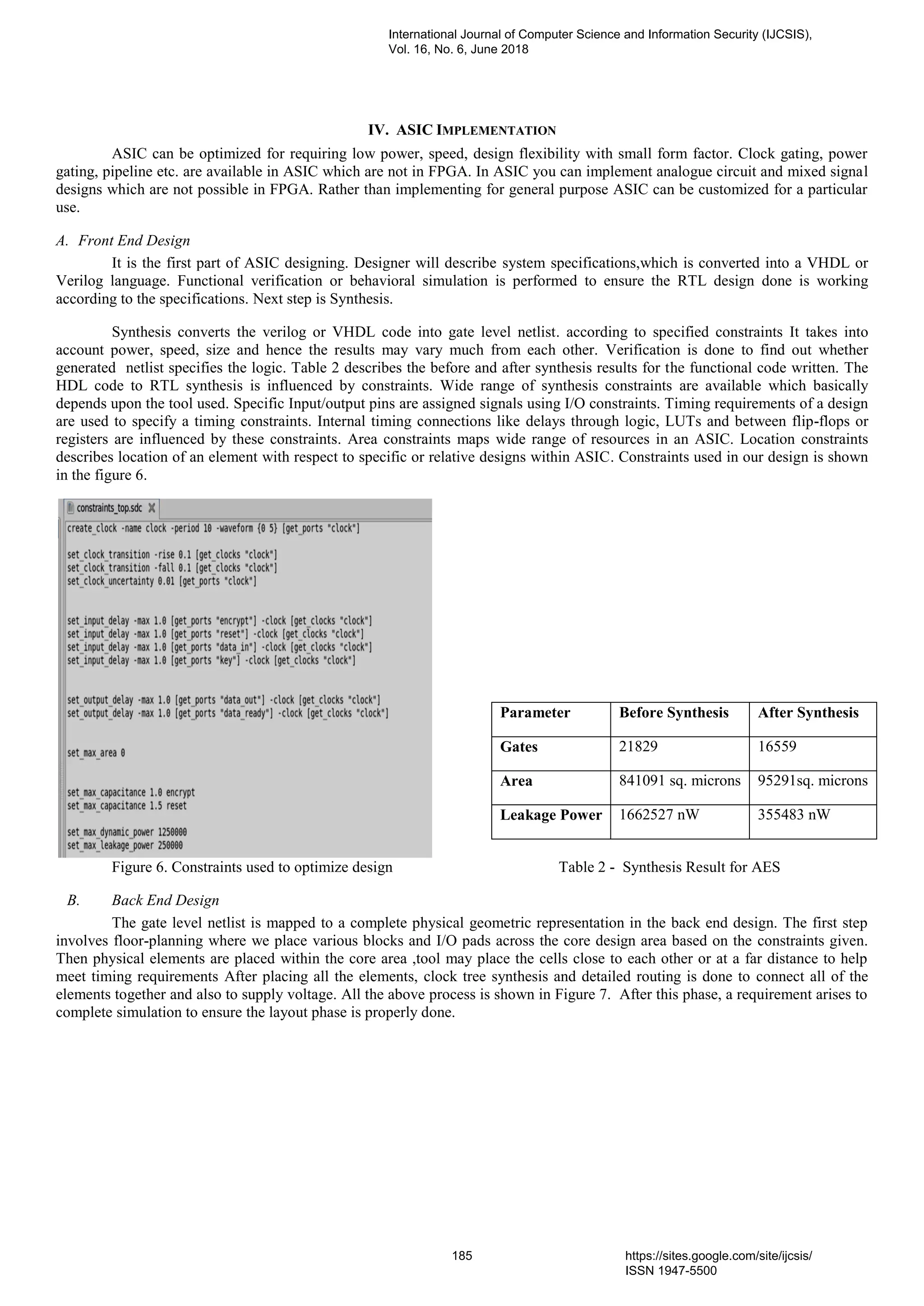
![(i) Floor Planning (ii) Placement (iii) Clock Tree Synthesis (iv) Routing Figure 7. Backend design GDSII (GDS2) file is produced as the end result of the Layout, it i used by the foundry to fabricate the silicon. The layout should be done according to the silicon foundry design rules. V. CONCLUSION In this paper, Speech data obtained through MATLAB has been encrypted and decrypted successfully using AES algorithm in verilog programming environment. Decrypted speech is recognised using cross correlation technique. AES has never been cracked and is considered most secure against any kind of brute force attacks. In ASIC designing, the constraints given for synthesis have reduced gates, area and leakage power by 24%,88% and 78% respectively, as described in table 2.So we need comparatively lesser amount of resources to implement the design, which makes the design smaller, faster as well as energy efficient. Layout of AES design is also developed in Backend design. In future we wish to develop more accurate speech recognition system and further optimization can be done for minimizing the required area, gates and power on ASIC for high end applications. REFERENCES [1] Lokireddi Phani Kumar, A. K. Gupta:"Implementation of Speech Encryption and Decryption using Advanced Encryption Standard", presented at IEEE International Conference On Recent Trends In Electronics Information Communication Technology, May 20-21, 2016, India [2] T.R. Devi," Importance of Cryptography in Network Security", presented at International Conference on Communication Systems and Network Technologies , Andhra Pradesh, 2013,India [3] Sneha Ghoradkar, Aparna Shinde:"AES Algorithm on FPGA based Image Encryption and Decryption", presented at International Journal of Science and Research (IJSR),2013 [4] Rourab paul, Sangeet Saha, Suman Sau, Amlan Chakrabart “R T b M FPGA Sy M k E RTOS ” IEEE D Sy 130-134, March 2012 [5] Shady Mohamed Soliman, Baher Magdyand Mohamed A. Abd El GhanyEfficient ,"Implementation of the AES Algorithm for Security Applications", Integrated Electronic Systems Lab, TU Darmstadt, Germany,2016. [6] "An Enhanced Speech Recognition System" By Suma Shankaranand, Manasa S, Mani Sharma, Nithya A.S, Roopa
K.S., K.V. Ramakrishnan, International Journal of Recent Development in Engineering and Technology,Volume 2, Issue 3, March 2014.
[7] Aseem saxena, Amit kumar saxsena,Shashank Chakravarthi,"Speech Recognition using MATLAB", presented at
International Journal of Advances In Computer Science and Cloud Computing, ISSN: 2321-4058 Volume- 1, Issue- 2, Nov-2013. [8] Anjalika Gupta, Prof. Pankaj Raibagkar, Dr. Anup Palsokar – “S q ” I J Current Trends in Engineering & Research (IJCTER) e-ISSN 2455–1392 Volume 3 Issue 6, June 2017 pp. 82 – 89
Scientific Journal Impact Factor : 3.468 International Journal of Computer Science and Information Security (IJCSIS), Vol. 16, No. 6, June 2018 186 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/23paper31051853ijcsiscamerareadypp-180710131811/75/FPGA-and-ASIC-Implementation-of-Speech-Encryption-and-Decryption-using-AES-Algorithm-with-Speech-Recognition-7-2048.jpg)